Bloom Filter and open-source kernel-based method for defensing SYN Flood attack
A kernel and kernel layer technology, applied in the field of network security, can solve the problems of service requests not being responded to, consuming the bandwidth of the attacked network and the service resources of the attacked host, and not considering the interaction of the kernel layer of the operating system, so as to reduce errors. report rate, improve processing efficiency, and defend against attacks
Inactive Publication Date: 2011-01-26
XIANGTAN UNIV
View PDF3 Cites 20 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Denial of service attack (DoS) and distributed denial of service attack (DDoS) are currently commonly used network attack methods. This attack consumes the bandwidth of the attacked network and the service resources of the attacked host by sending a large number of forged service requests, thus making Normal service requests are unresponsive
Especially the SYN Flood attack, because it utilizes the inherent loopholes in the TCP / IP protocol (abbreviation of Transmission Control Protocol / Internet Protocol, Transmission Control Protocol / Internet Internet Protocol), so the existing protocol system is not immune to this attack
The current defense methods for this attack mainly include intrusion detection, packet filtering, limiting the number of semi-connections, shortening the time for operating systems to maintain semi-connections, using firewalls as intermediate agents for TCP connections, and methods of increasing resources, such as increasing network bandwidth. , increase servers and apply load balancing technology at the same time, etc., but the storage structure of data packets in these methods needs to be improved, and the interaction between the operating system kernel layer and the user layer is not considered, so that large-scale DDoS attacks are basically helpless
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
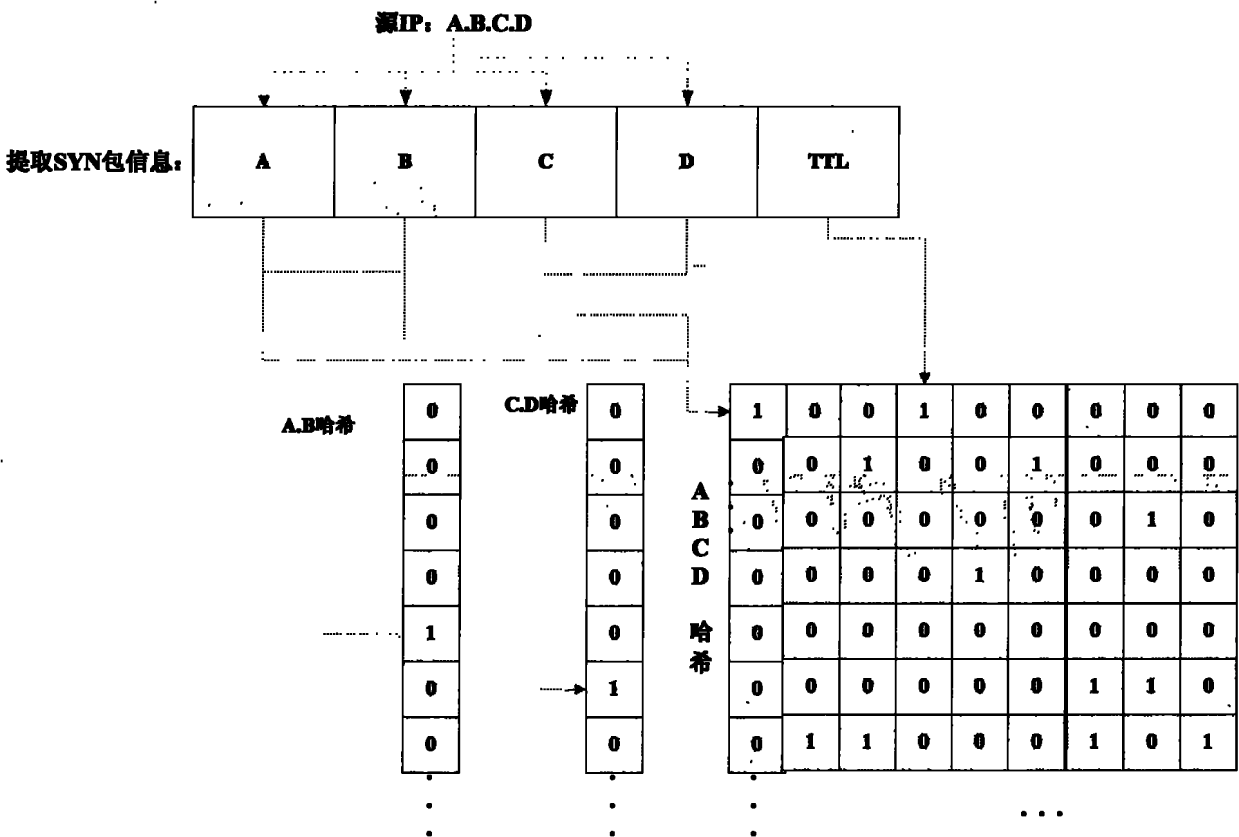
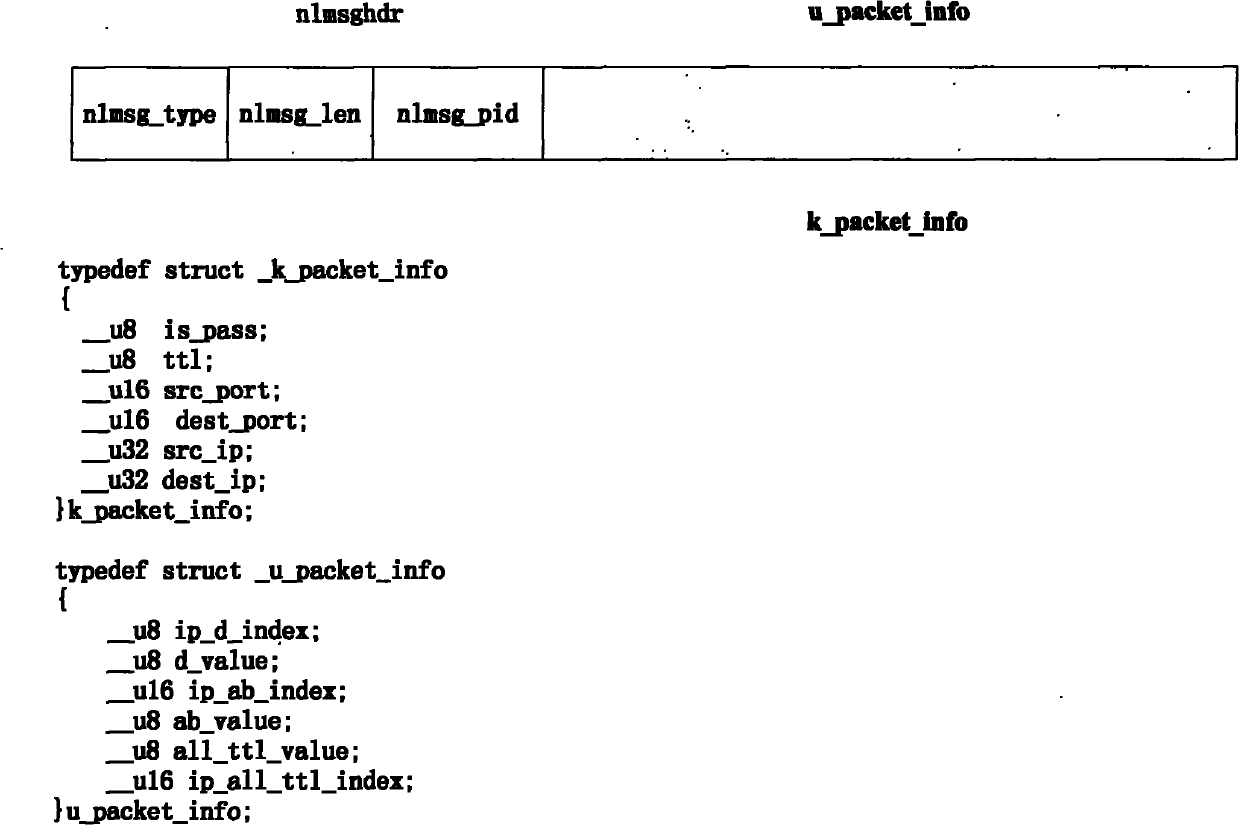
The invention discloses a Bloom Filter and open-source kernel-based method for defensing an SYN Flood attack, which comprises the following steps of: 1, judging whether being subjected to the SYN-Flood attack; 2, establishing a Bloom Filter structure; 3, updating a credible IP address and TTL data of a kernel layer, and starting to filter a data packet of the kernel layer; 4, filtering a TCP SYN data packet according to the credible IP address and the TTL record by using the kernel layer; and 5, stopping filtering the data packet of the kernel layer. The method has the advantages that: 1, by improving an original structure of a Bloom Filter that a single bit array corresponds to a plurality of hash functions, a structure that a hash function corresponds to a bit array is adopted, so that the false alarm rate is effectively reduced, and the efficiency of storing and searching the data packet on the premise of ensuring the accuracy rate is improved; therefore, the method can effectively defense the SYN Flood attack; and 2, the problems that the kernel layer has high efficiency but is not suitable for processing complicated programs and a user layer is not compact with a kernel protocol stack are solved by the cooperative processing of combining the kernel layer and the user layer of an open-source operating system, so that the efficiency of processing the data packet is improved.
Description
technical field The invention relates to the technical field of network security, in particular to a method for defending against SYN Flood attacks (a kind of DDoS attack, namely TCP connection request flood attack) based on Bloom Filter (ie Bloom filter) and an open source kernel. Background technique Denial of service attack (DoS) and distributed denial of service attack (DDoS) are currently commonly used network attack methods. This attack consumes the bandwidth of the attacked network and the service resources of the attacked host by sending a large number of forged service requests, thus making Normal service requests are not responded to. Especially the SYN Flood attack, because it utilizes the inherent loopholes in the TCP / IP protocol (abbreviation of Transmission Control Protocol / Internet Protocol, Transmission Control Protocol / Internet Internet Protocol), so the existing protocol system is not immune to this attack . The current defense methods for this attack mai...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04L29/06
Inventor 唐欢容罗新高李宇欧阳建权
Owner XIANGTAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com