Patents
Literature
112 results about "Identity correlation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In information systems, identity correlation is a process that reconciles and validates the proper ownership of disparate user account login IDs (user names) that reside on systems and applications throughout an organization and can permanently link ownership of those user account login IDs to particular individuals by assigning a unique identifier (also called primary or common keys) to all validated account login IDs.
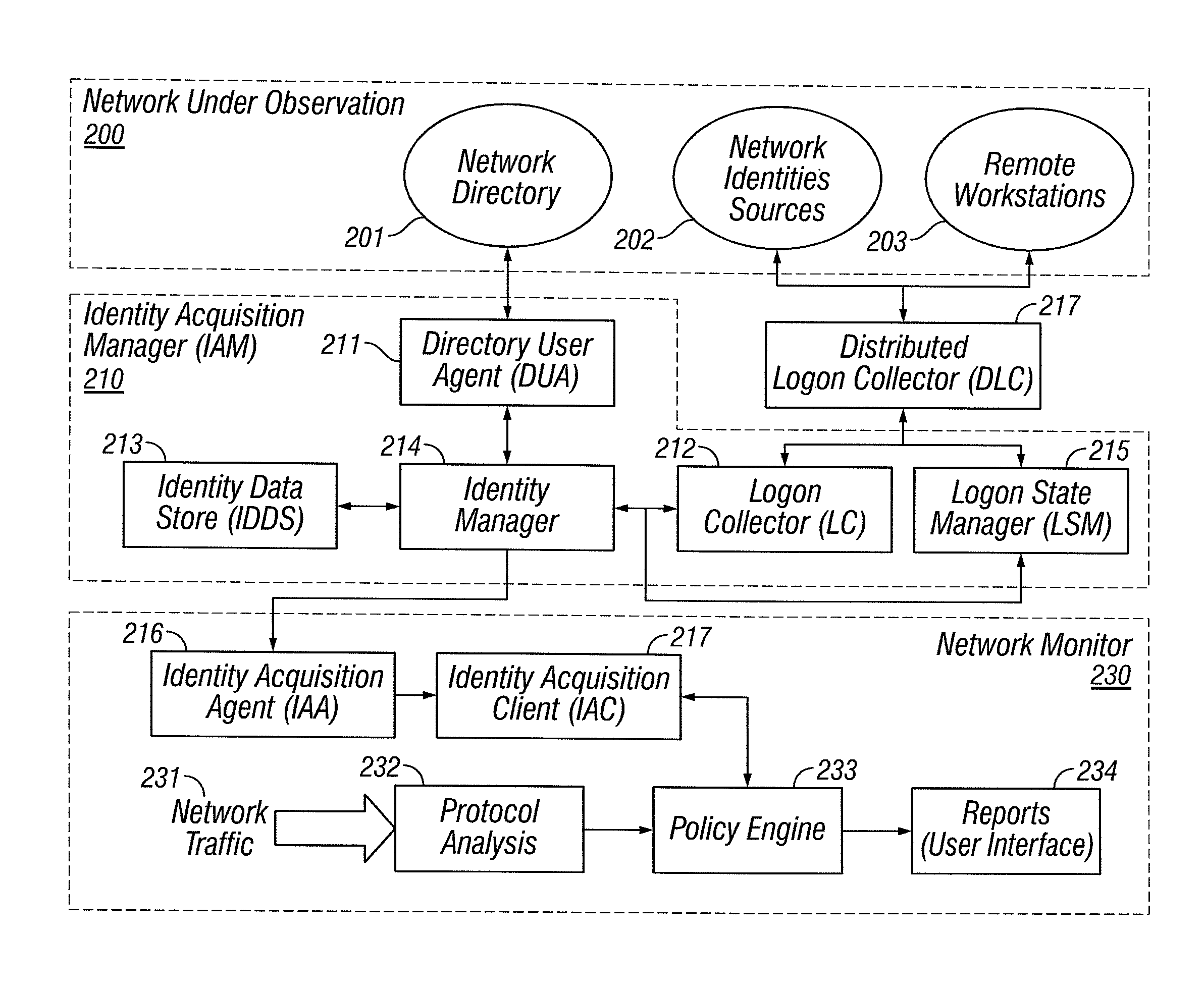
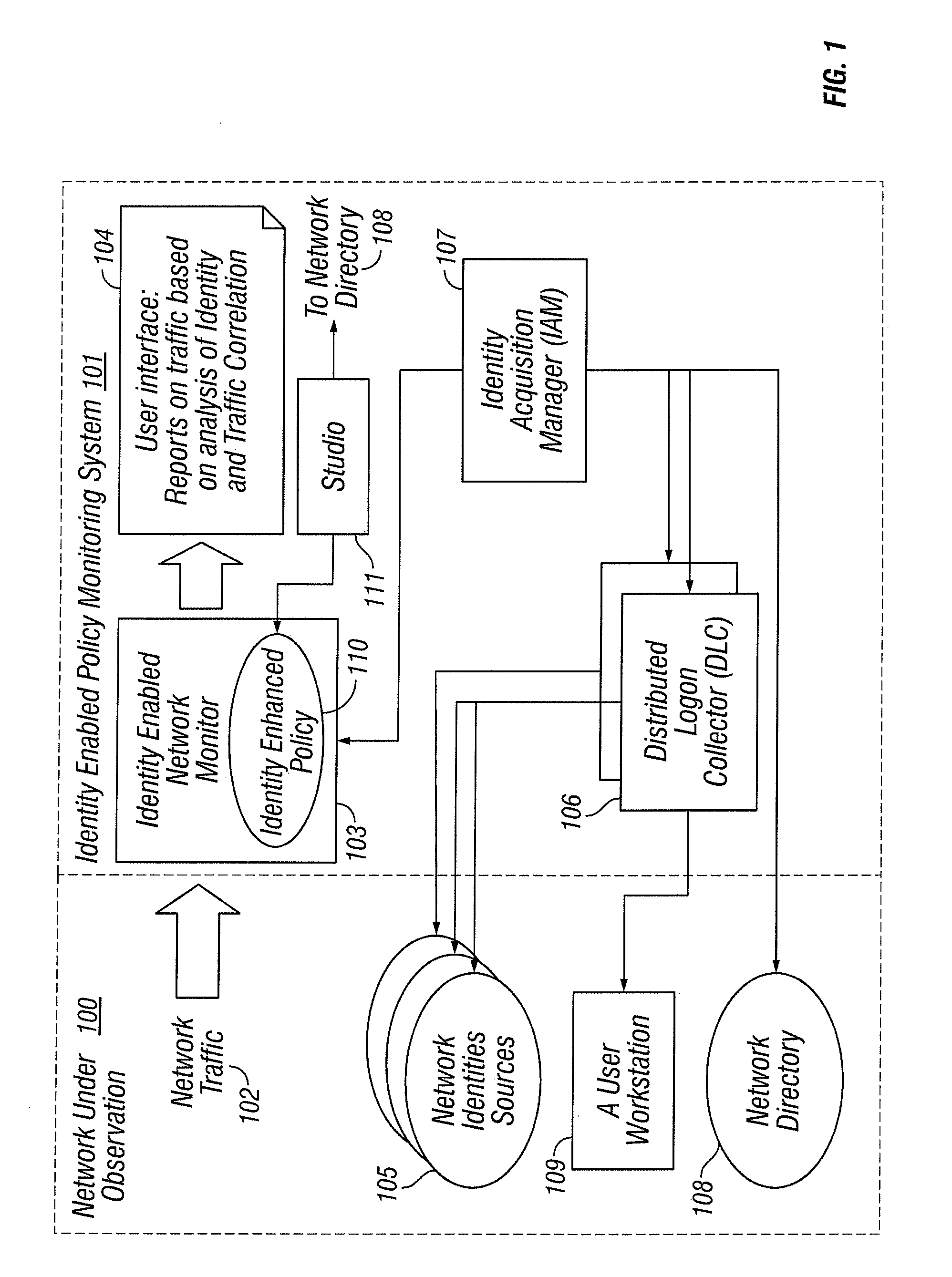
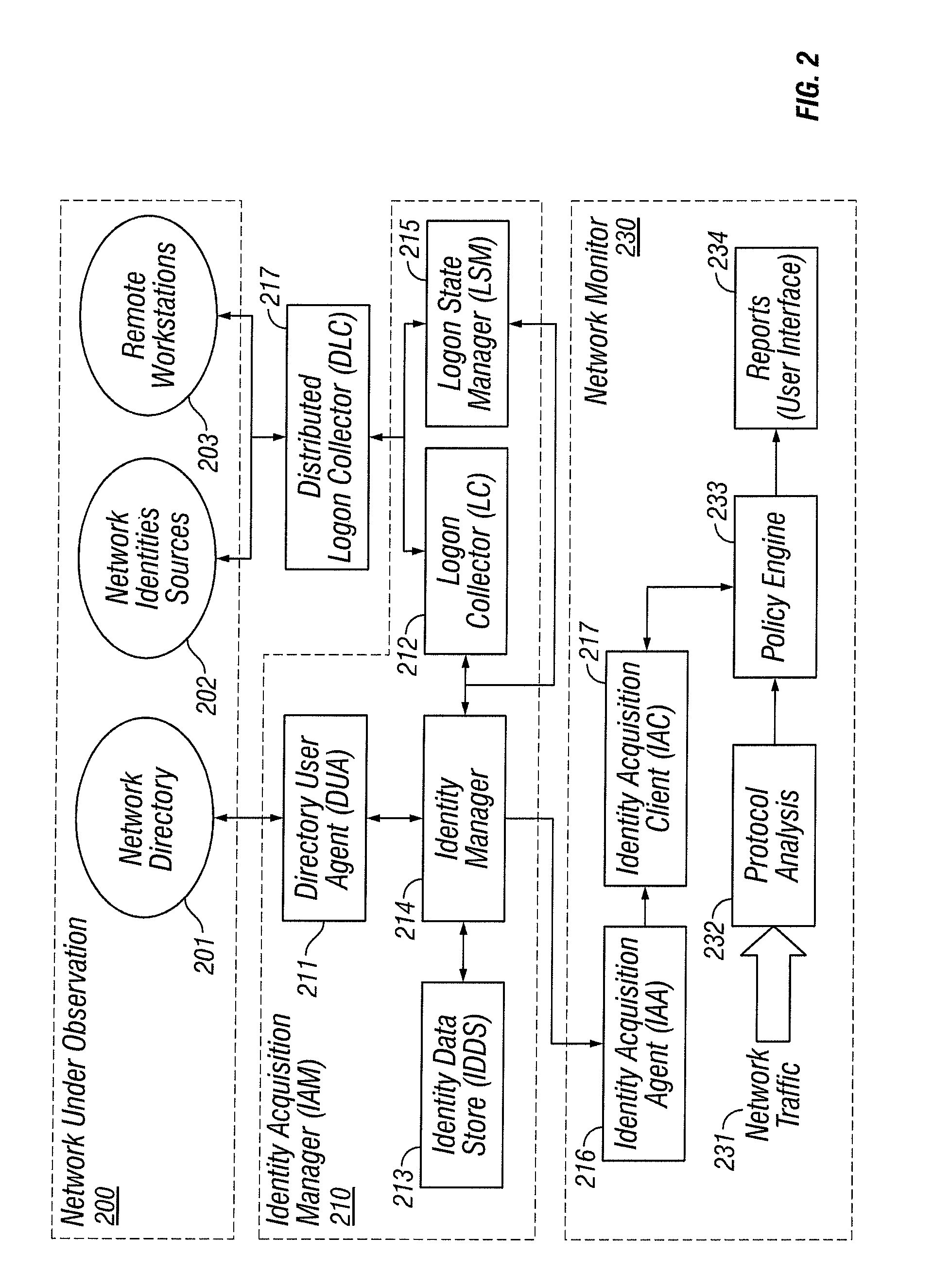
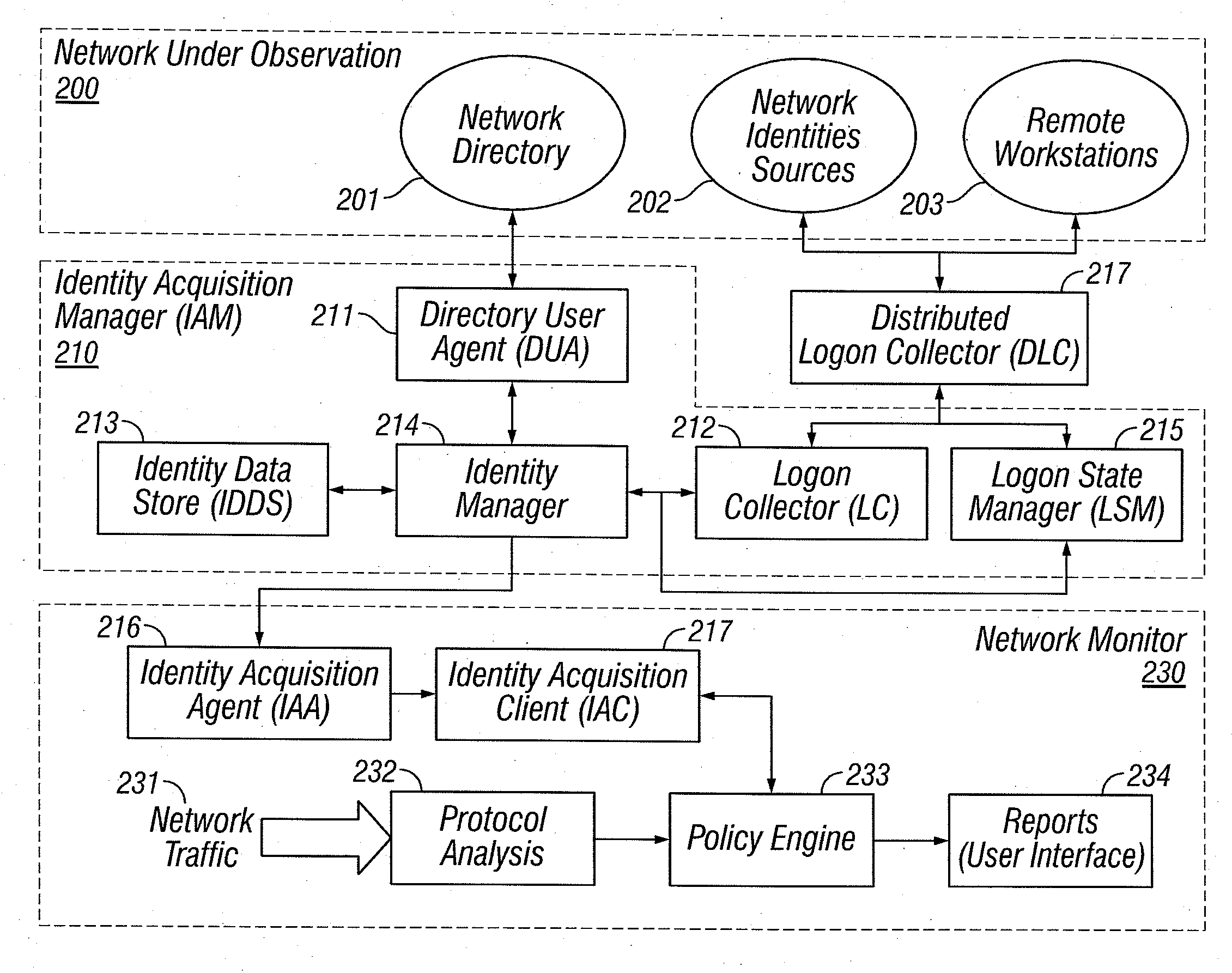
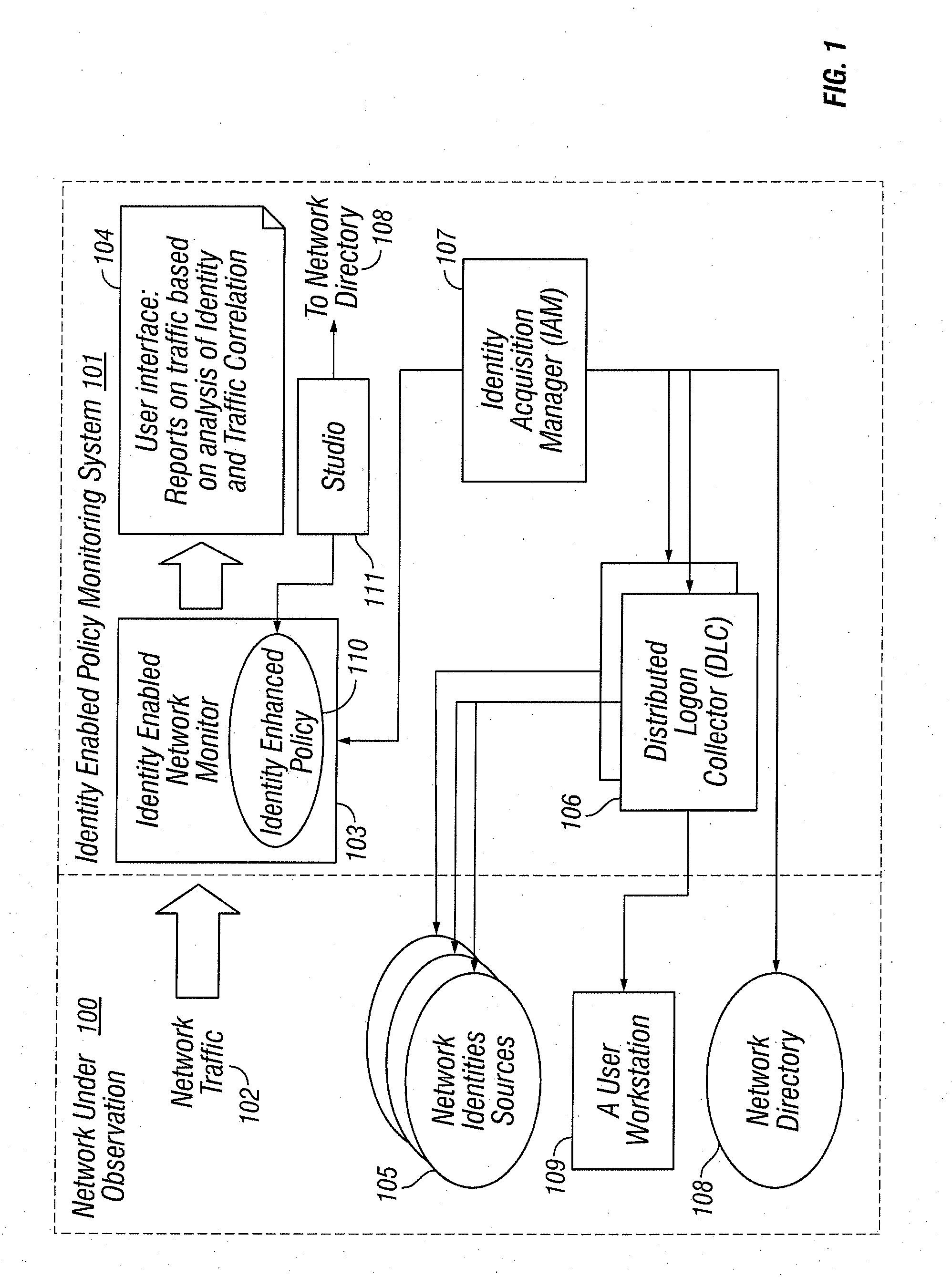
Identities correlation infrastructure for passive network monitoring
ActiveUS8584195B2Policy language is enhancedDigital data processing detailsComputer security arrangementsWorkstationPassive network monitoring
User names and user groups serve as the basis of a formal policy in a network. A passive monitor examines network traffic in near real time and indicates: which network traffic is flowing on the network as before; which users or user groups were logged into workstations initiating this network traffic; and which of this traffic conforms to the formal policy definition. In one embodiment of the invention, users and user groups are determined by querying Microsoft® Active Directory and Microsoft® Windows servers, to determine who is logged onto the Microsoft® network. Other sources of identity information are also possible. The identity information is then correlated with the network traffic, so that even traffic that does not bear on the Microsoft® networking scheme is still tagged with identity
Owner:MUSARUBRA US LLC
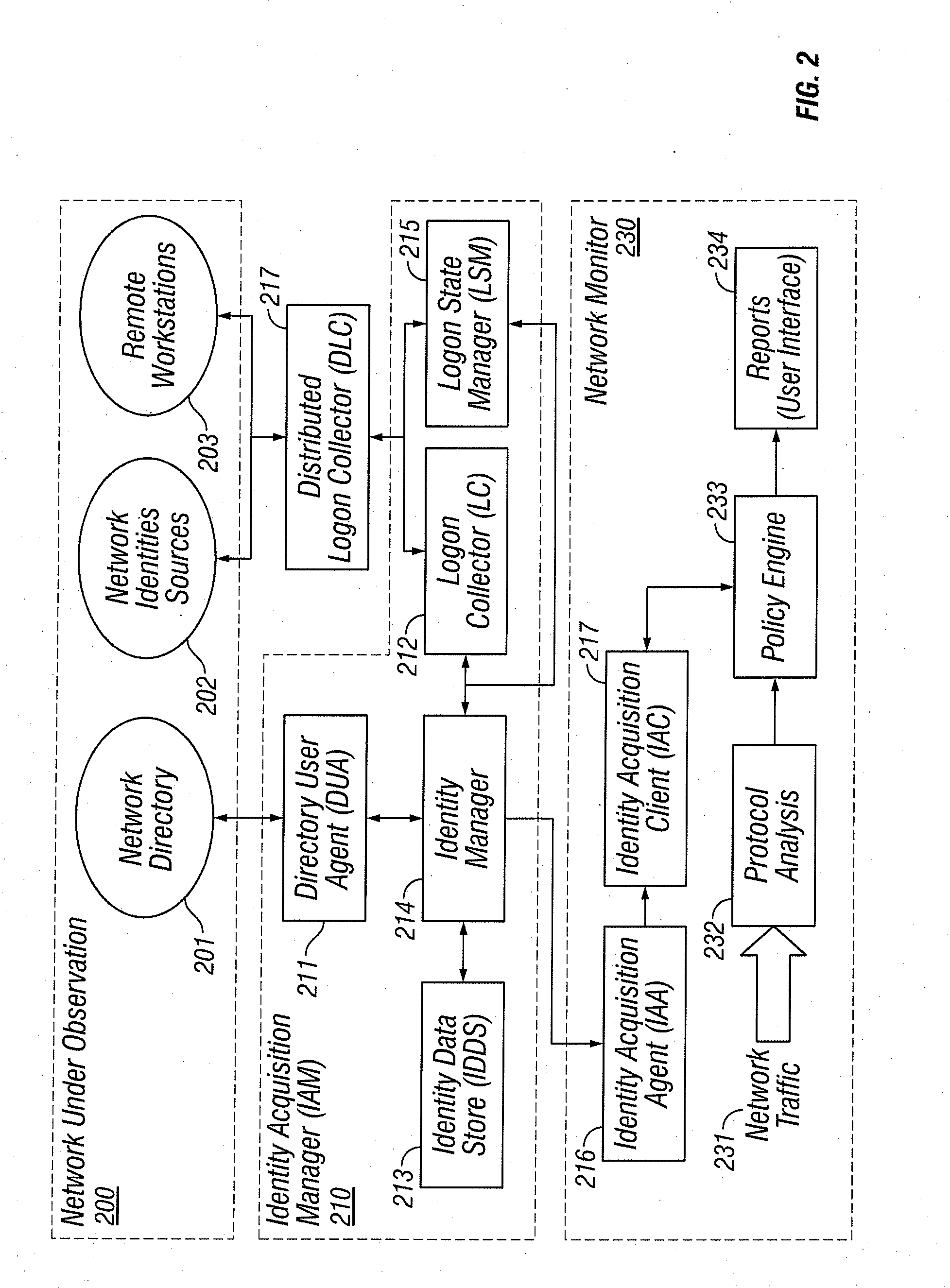
Identities Correlation Infrastructure for Passive Network Monitoring
ActiveUS20080109870A1Policy language is enhancedDigital data processing detailsComputer security arrangementsTraffic capacityPassive network monitoring
User names and user groups serve as the basis of a formal policy in a network. A passive monitor examines network traffic in near real time and indicates: which network traffic is flowing on the network as before; which users or user groups were logged into workstations initiating this network traffic; and which of this traffic conforms to the formal policy definition. In one embodiment of the invention, users and user groups are determined by querying Microsoft® Active Directory and Microsoft® Windows servers, to determine who is logged onto the Microsoft® network. Other sources of identity information are also possible. The identity information is then correlated with the network traffic, so that even traffic that does not bear on the Microsoft® networking scheme is still tagged with identity
Owner:MUSARUBRA US LLC
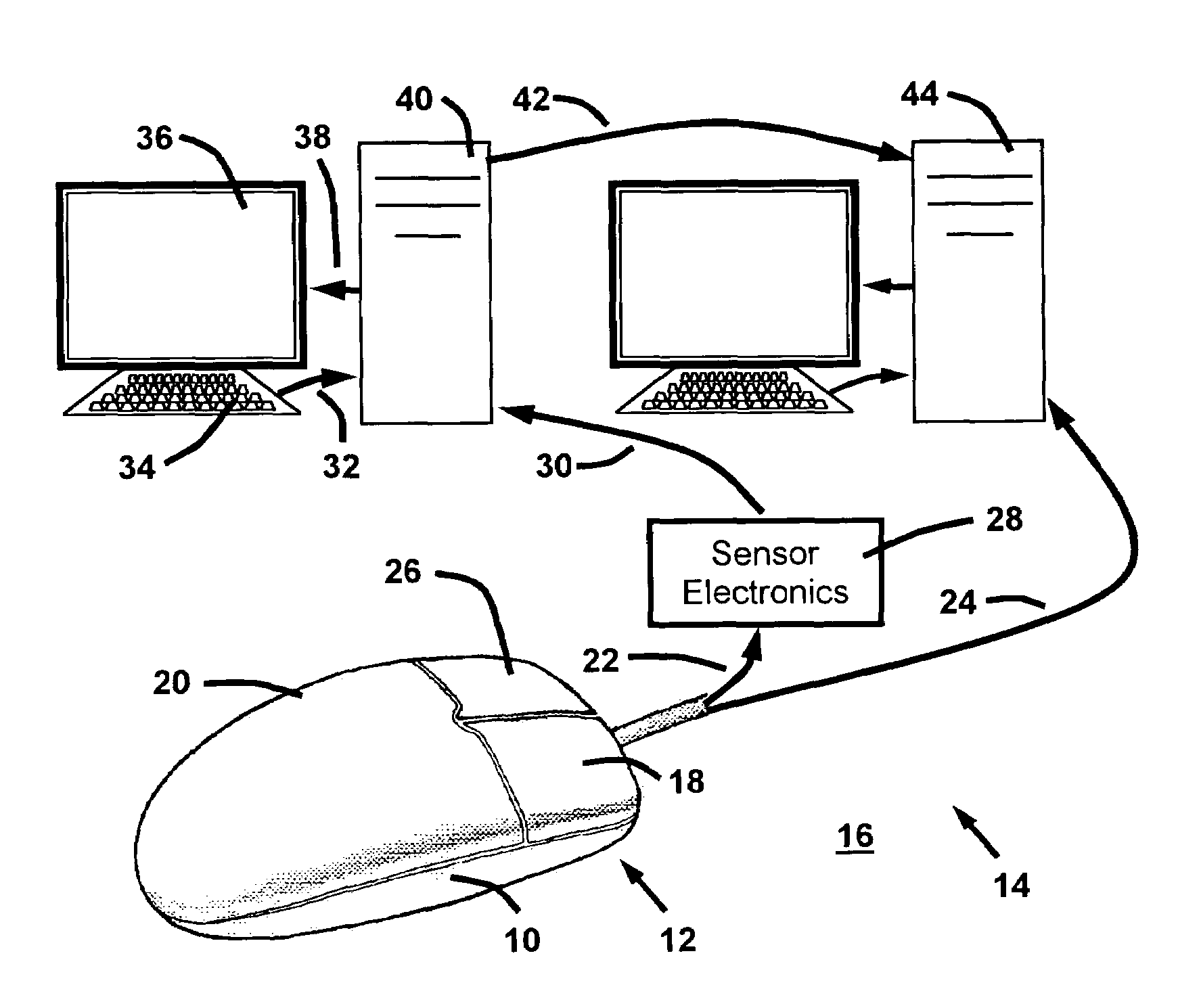
Input device to continuously detect biometrics
ActiveUS7245218B2Electric signal transmission systemsImage analysisPattern recognitionFinger pressure
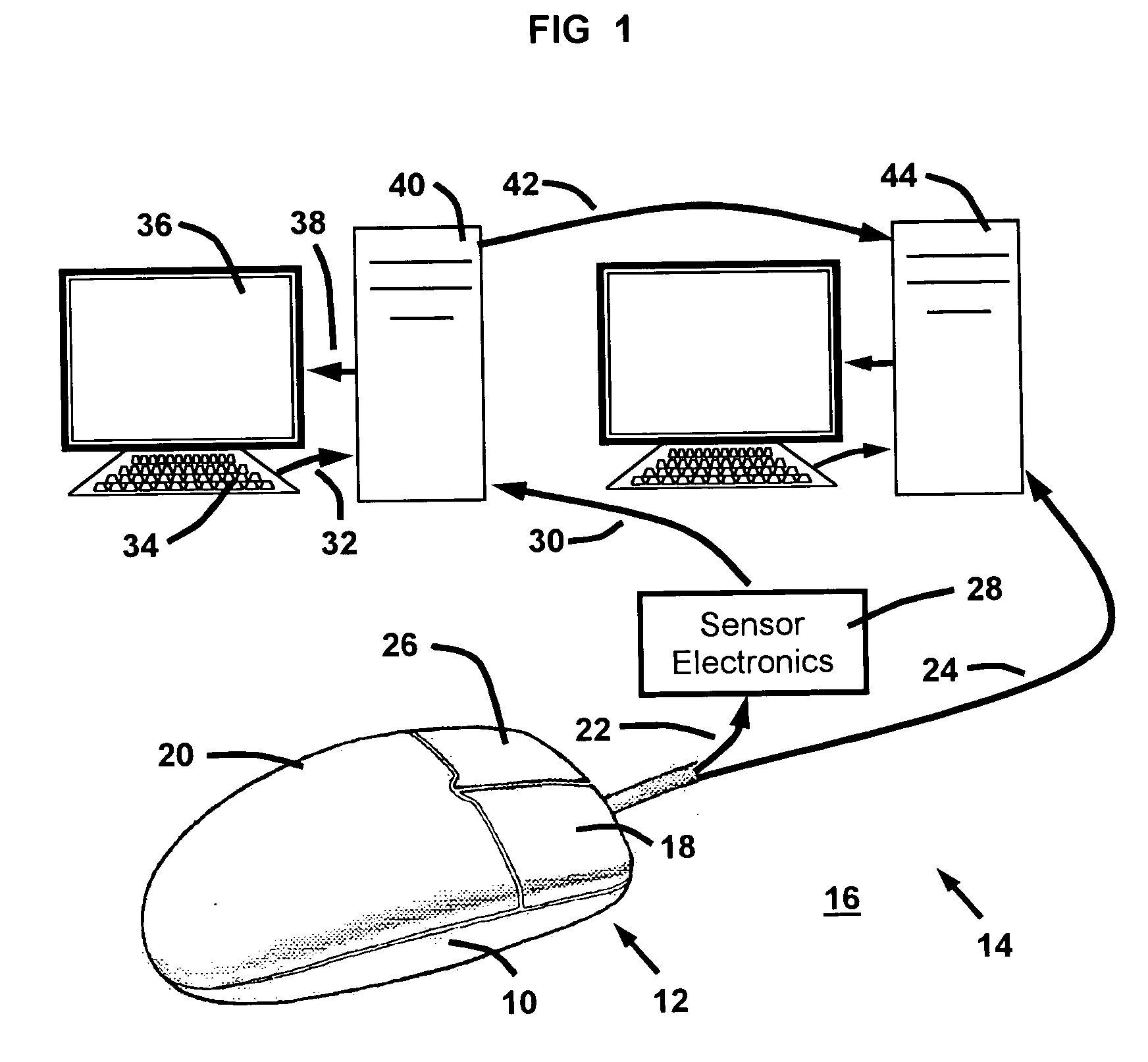
A method and system for correlating control surface finger pressures to identifying biometric characteristics of a user from a computer input device, such as a mouse. Pressure sensors attached to a computer mouse sense the biometric characteristics, which are correlated to identifying biometric characteristics using a correlation model. The correlation model is derived from a registration process in which a baseline biometric attribute-to-identity correlation is rendered based on statistical analysis of registration signals generated by users. During routine use, the correlation model is use to continuously authenticate the identity of the user from surface finger pressures on the computer mouse.
Owner:IKEHARA CURTIS SATORU +1
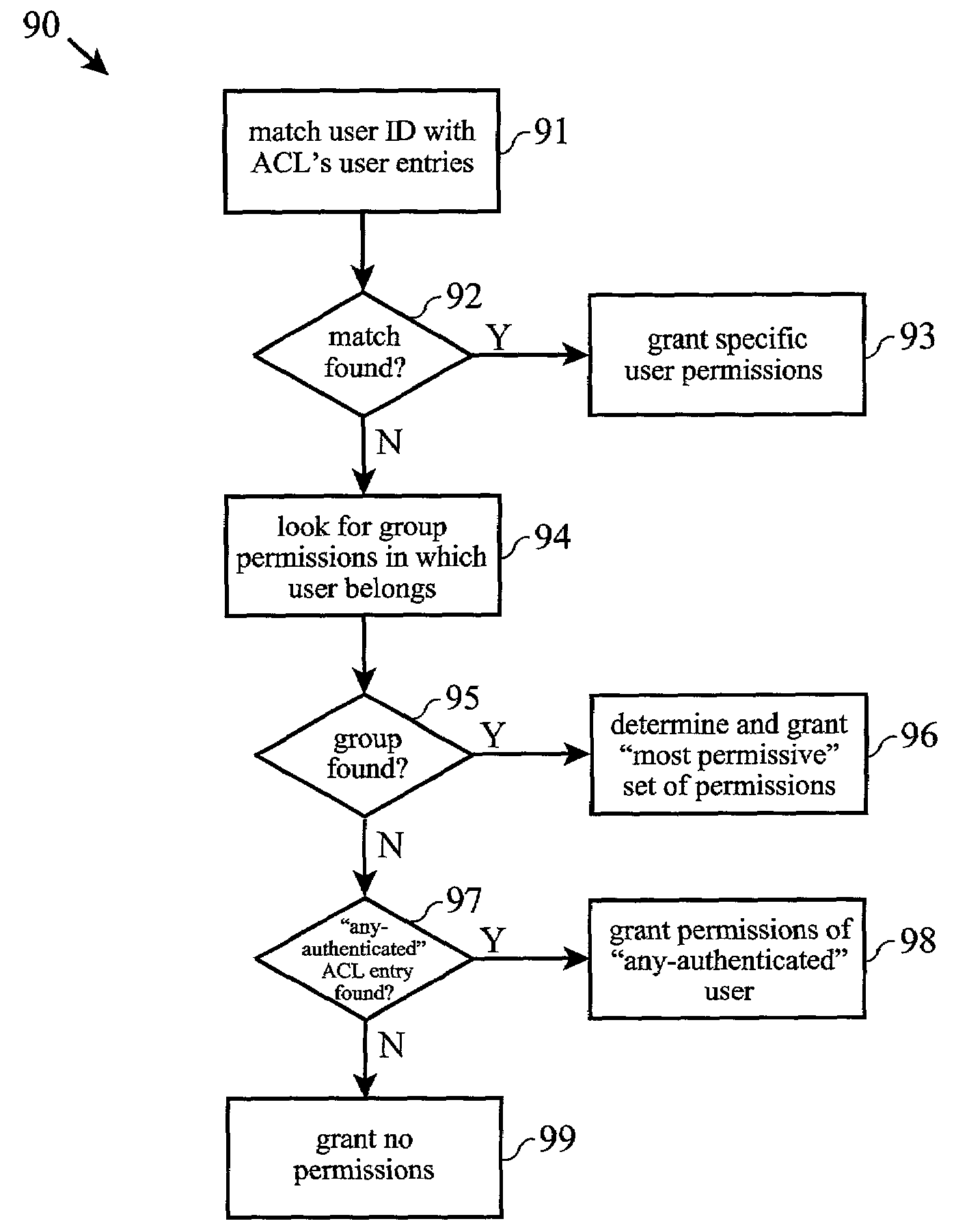
Grouped access control list actions
ActiveUS7380271B2Simple definitionSimplified managementDigital data processing detailsUser identity/authority verificationAccess methodOperational definition
Access Control Lists (ACLs) are used to describe the permitted actions (permissions) on protected network computer system resources or objects associated with an client or user identity. An identity may be an individual user or group of users. The actions are used to represent the different access methods available on a particular projected object or resource. A new action grouping mechanism is provided which tags each action with an action group name. The grouping of actions facilitates a larger permission set to be defined in an ACL, whereas action permission indicators can be reused for unique action definitions within various action groups. This effectively extends the finite total number of permissions available within a security system, allows a more descriptive and extensible permission mechanism in an Access Control List, as well as aiding in the simplification of management and definition of security policies.
Owner:SAILPOINT TECH HLDG INC
Method and apparatus for controlling multiple logical data flow in a variable data rate environment
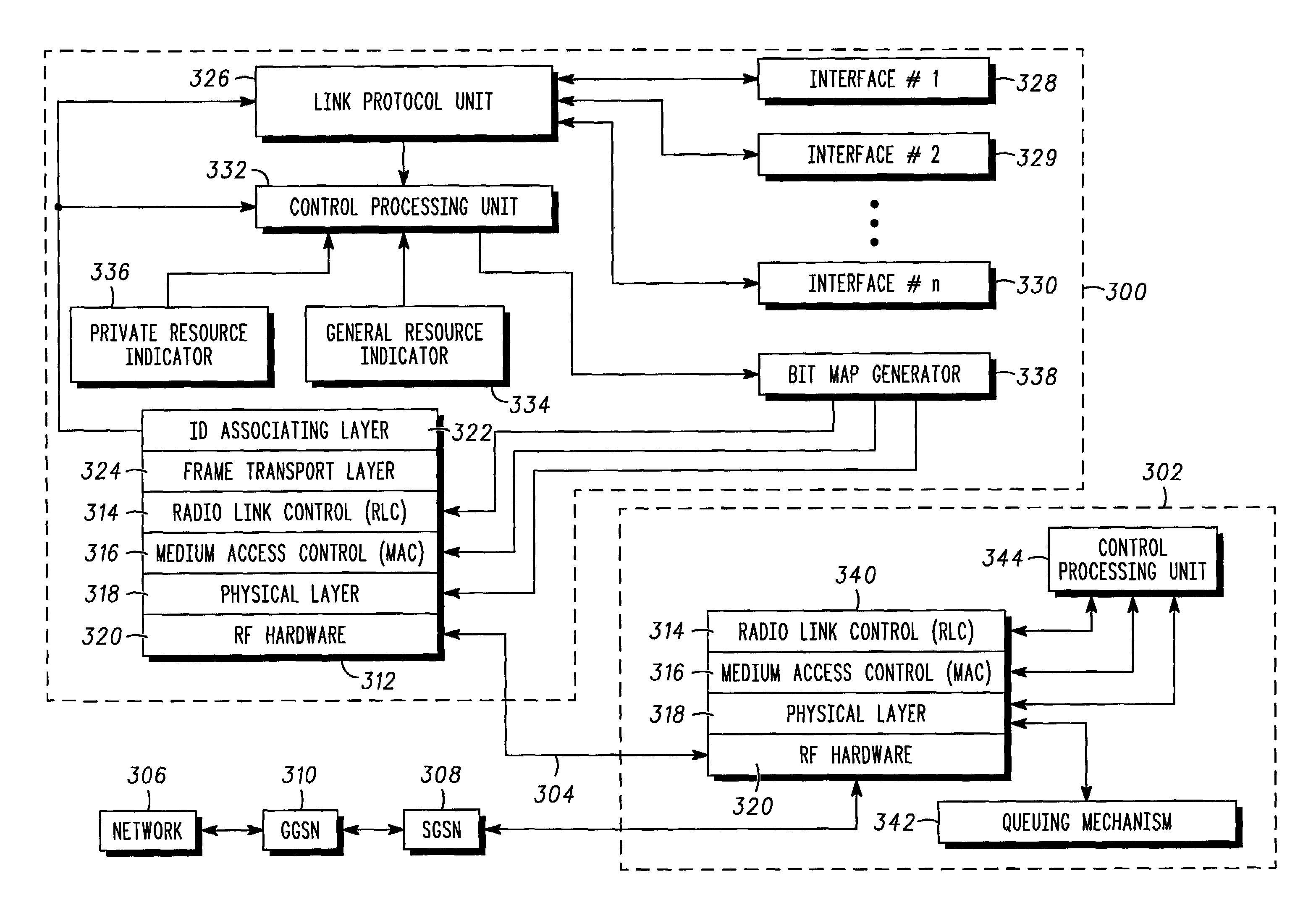
A method and apparatus that enables incremental control the flow of downlink data on an external interface-by-interface basis, reducing the risk of repeatedly exhausting internal memory resources. A mobile device (300), having a plurality of device interfaces (328–330) for transmitting data received from a network (306) through a network controller (302), includes an identity associating layer (322) that associates identifiers with packet data protocol contexts corresponding to the plurality of device interfaces. A general resource indicator (334) generates a first indication in response to system memory of the mobile device being substantially exhausted, and a private resource indicator (336) generates a second indication in response to private resources corresponding to the plurality of device interfaces being substantially exhausted. A control processing unit (332) generates a flow control indication signal in response to the first indication, the second indication, flow control information corresponding to the plurality of interfaces, and the identifiers associated by the identity associating layer. A bit-map generator (338) generates a bit-map, based on the flow control indication signal, that is transmitted to the radio network controller, which interprets the bit-map to discretely control transmission of data from the radio network controller to the plurality of device interfaces.
Owner:GOOGLE TECH HLDG LLC
System and method for user identity portability in communication systems
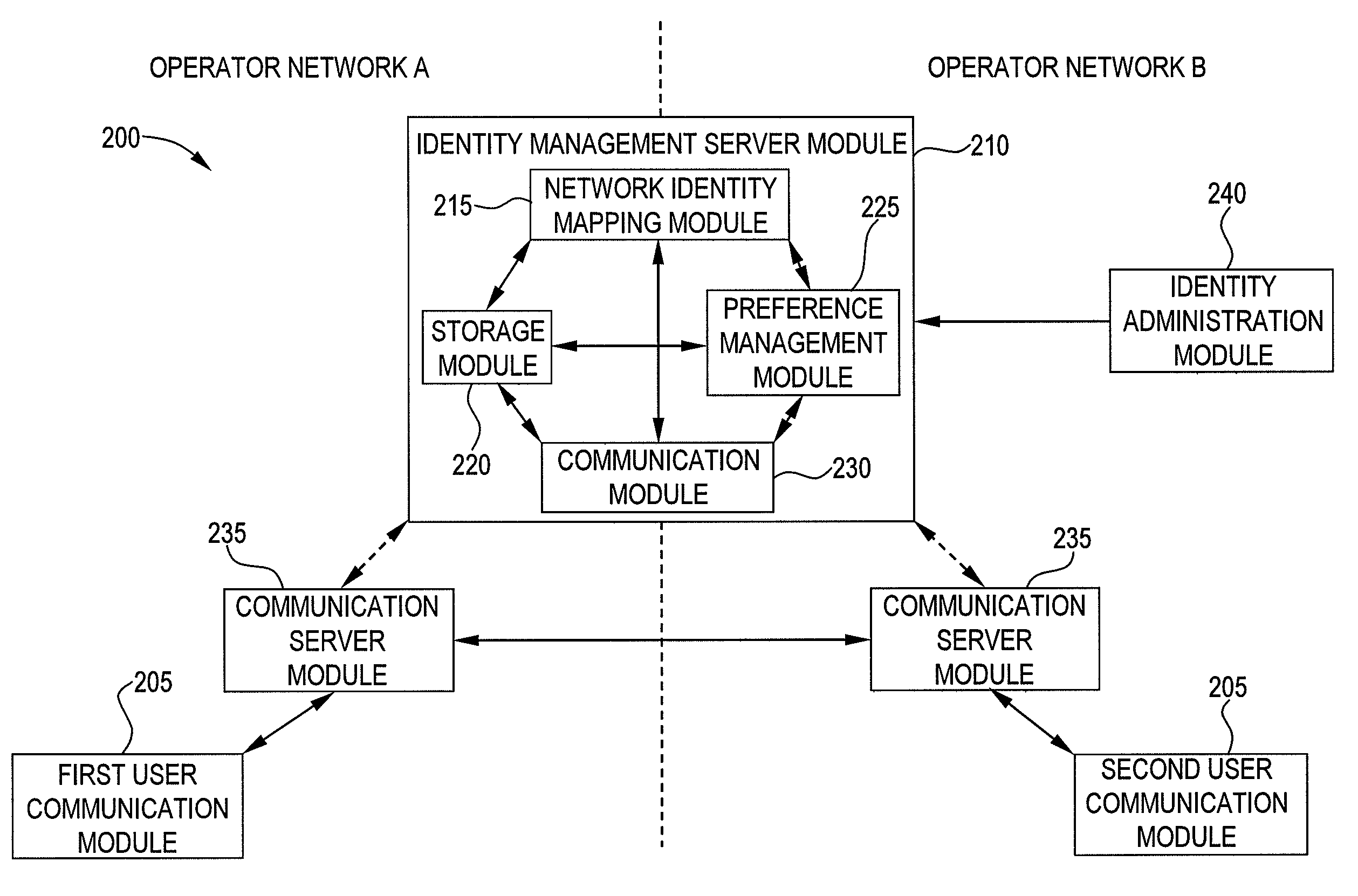
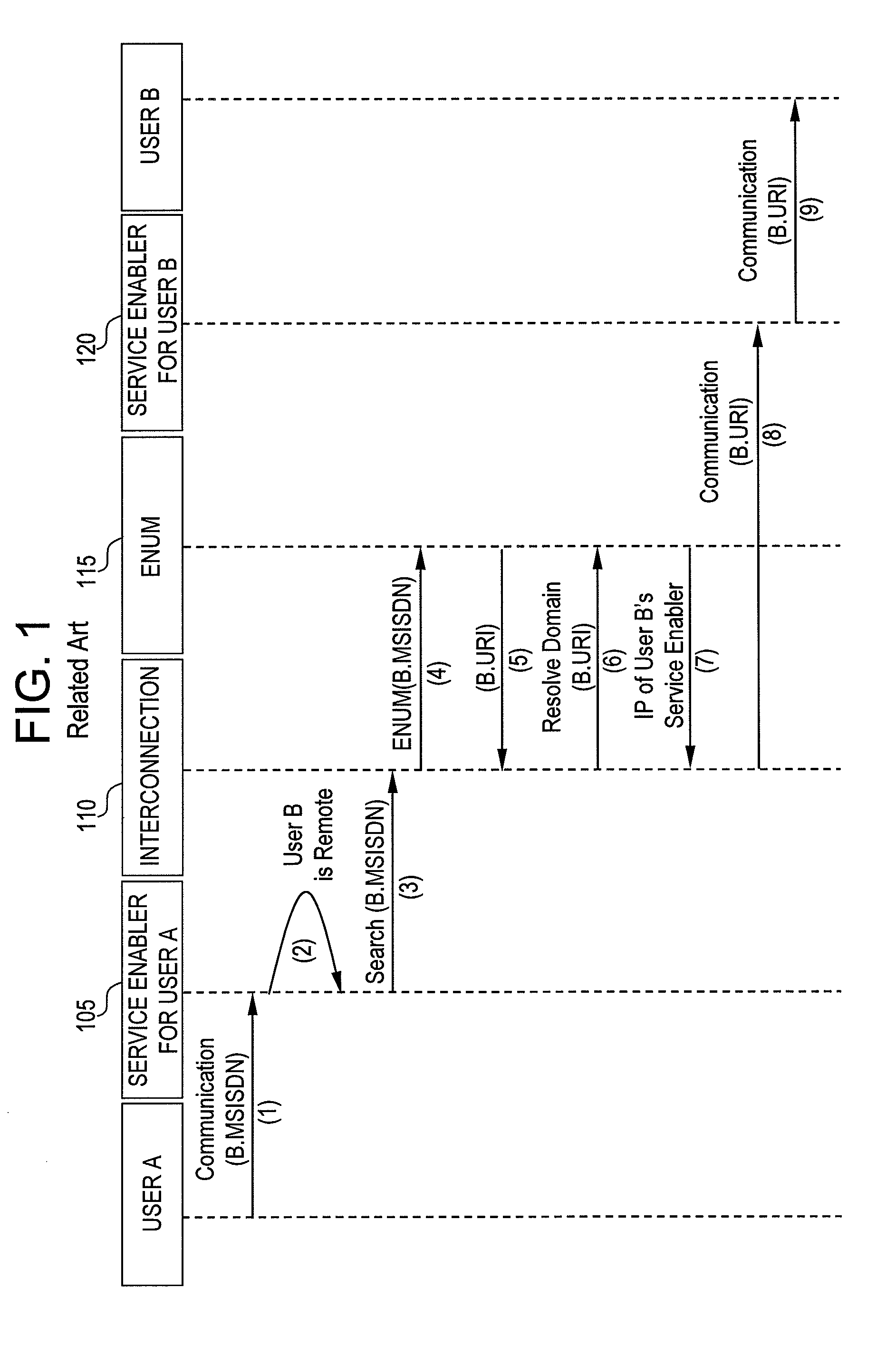
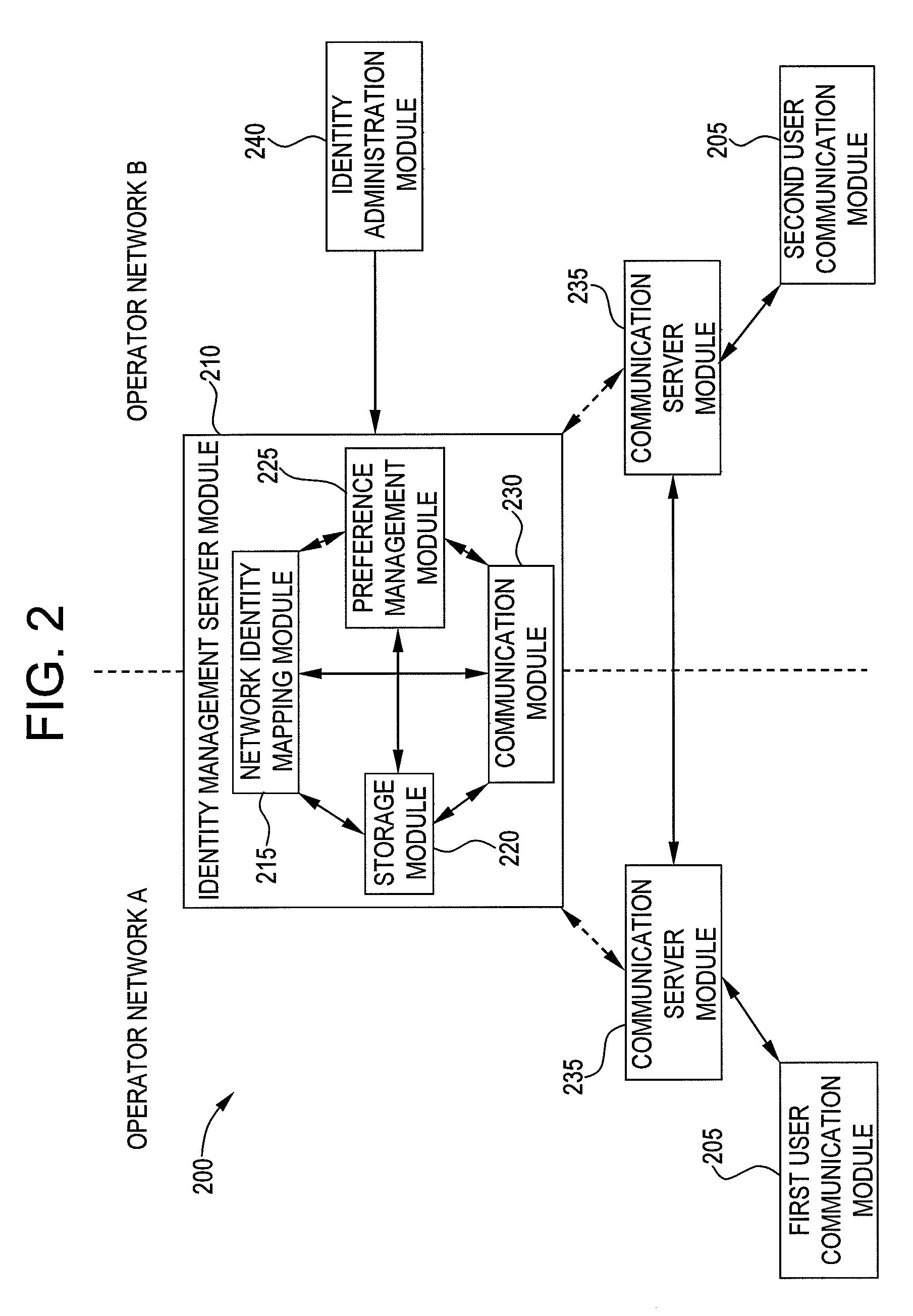
InactiveUS20080130523A1Maintain privacySpecial service provision for substationMultiplex system selection arrangementsCommunications systemInternet privacy
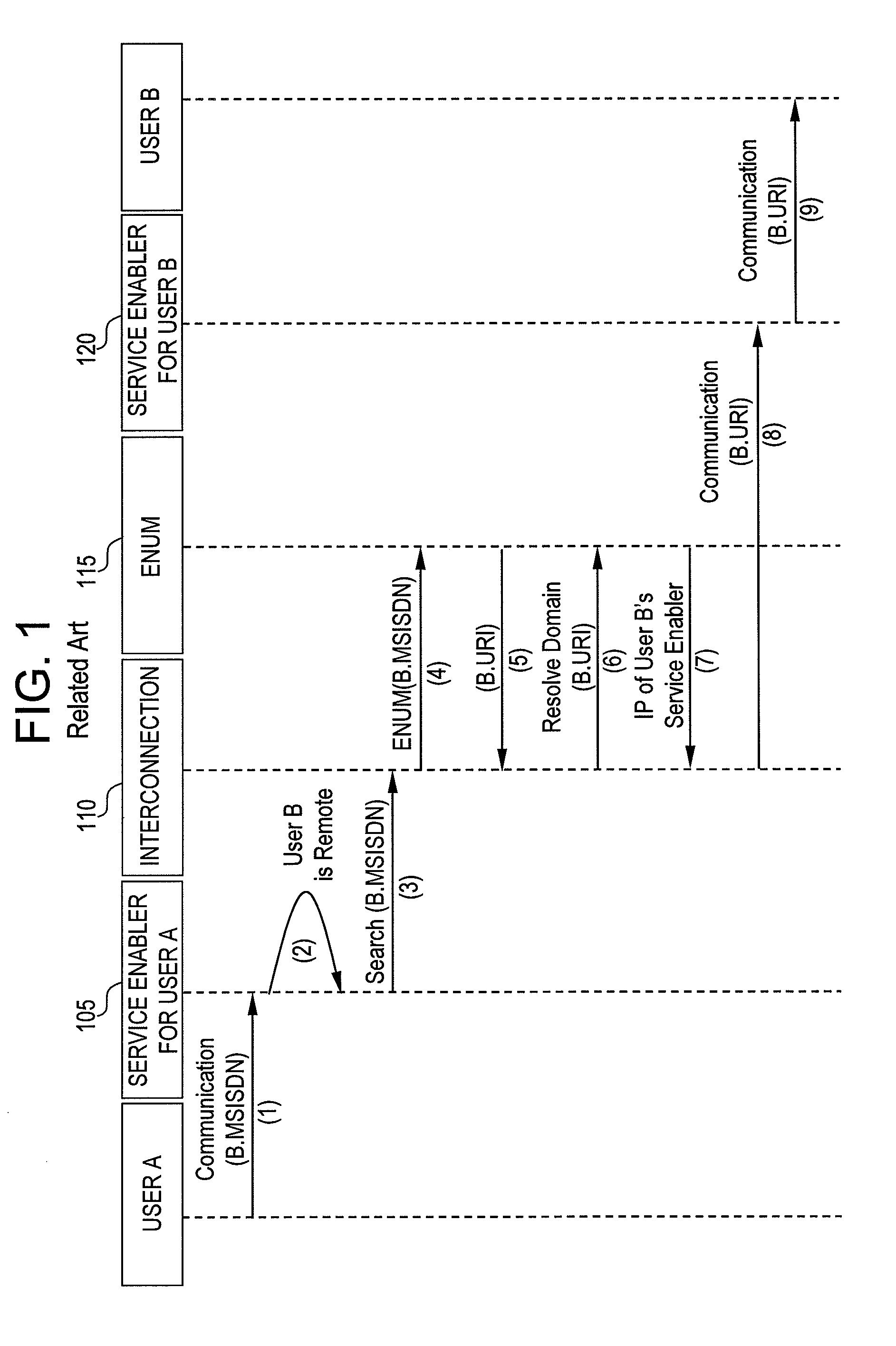
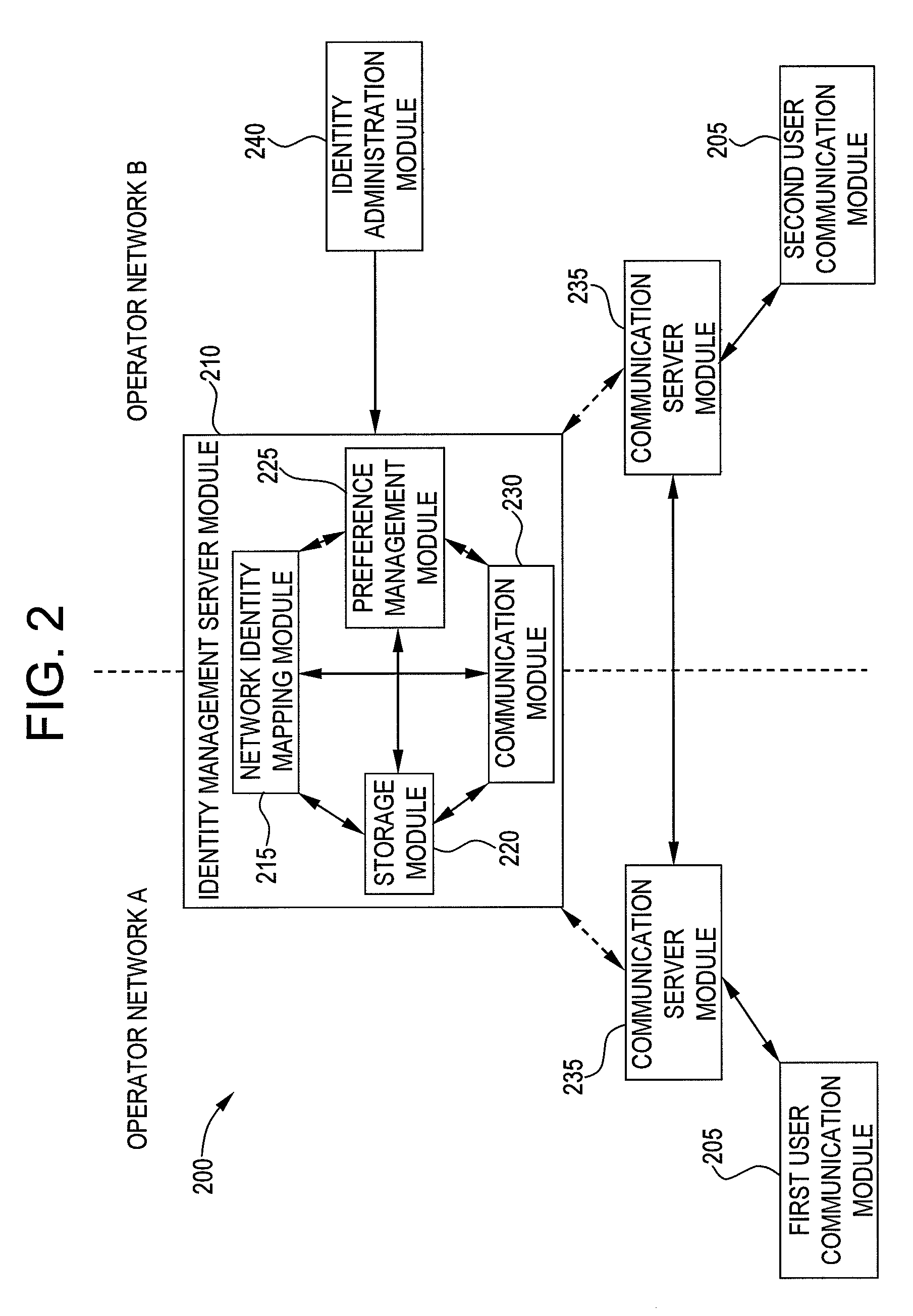
Exemplary embodiments of the present invention are directed to a system and method for user identity portability in communication systems. The present invention can provide user identity portability across communication networks that do not necessarily impose a phone number as the identity, addressing, or routing identifier. According to exemplary embodiments, a user identified by any suitable user identifier can switch network operators (e.g., from operator A to operator B) and retain their user identifier. For example, an identity server can support reverse lookup ENUM usage for URI and other identity correlation. Thus, all communication contacts that the user had while with operator A can seamlessly continue communications with the user even after the user switches to operator B.
Owner:NEUSTAR
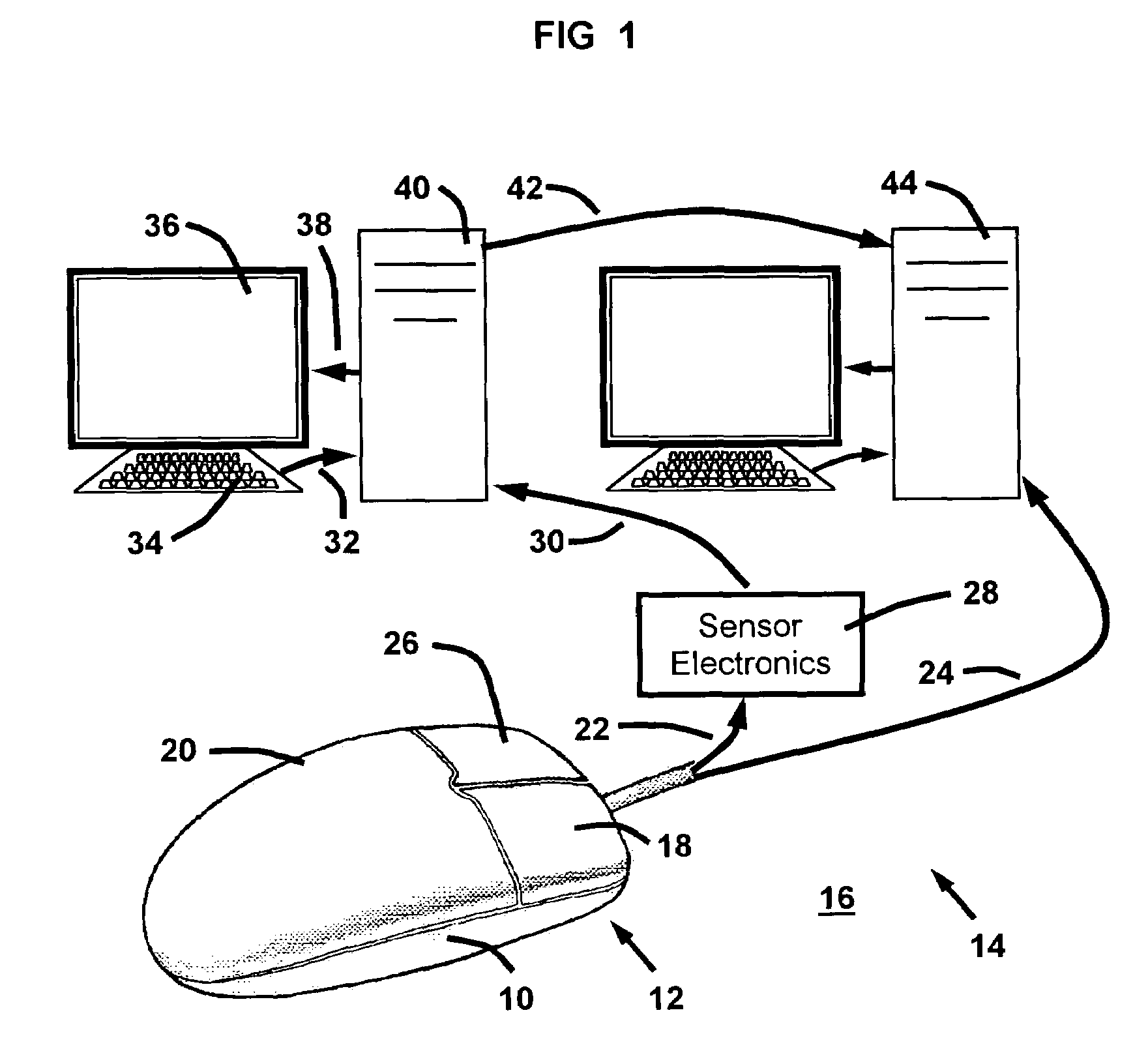
Input device to continuously detect biometrics
ActiveUS20050057339A1Eliminate dependenciesEliminate needElectric signal transmission systemsImage analysisIdentity correlationInput device
A method and system for correlating control surface finger pressures to identifying biometric characteristics of a user from a computer input device, such as a mouse. Pressure sensors attached to a computer mouse sense the biometric characteristics, which are correlated to identifying biometric characteristics using a correlation model. The correlation model is derived from a registration process in which a baseline biometric attribute-to-identity correlation is rendered based on statistical analysis of registration signals generated by users. During routine use, the correlation model is use to continuously authenticate the identity of the user from surface finger pressures on the computer mouse.
Owner:IKEHARA CURTIS SATORU +1
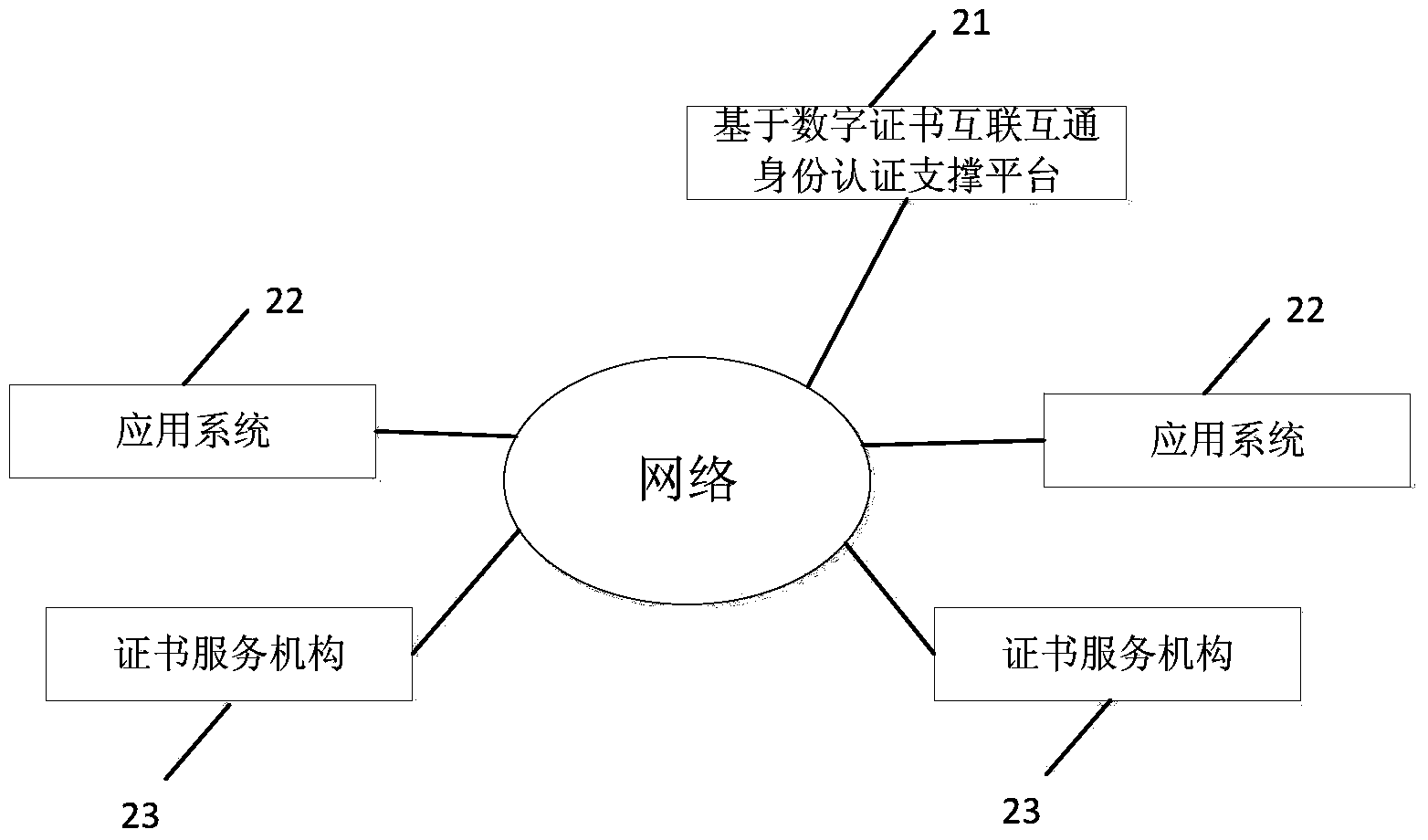
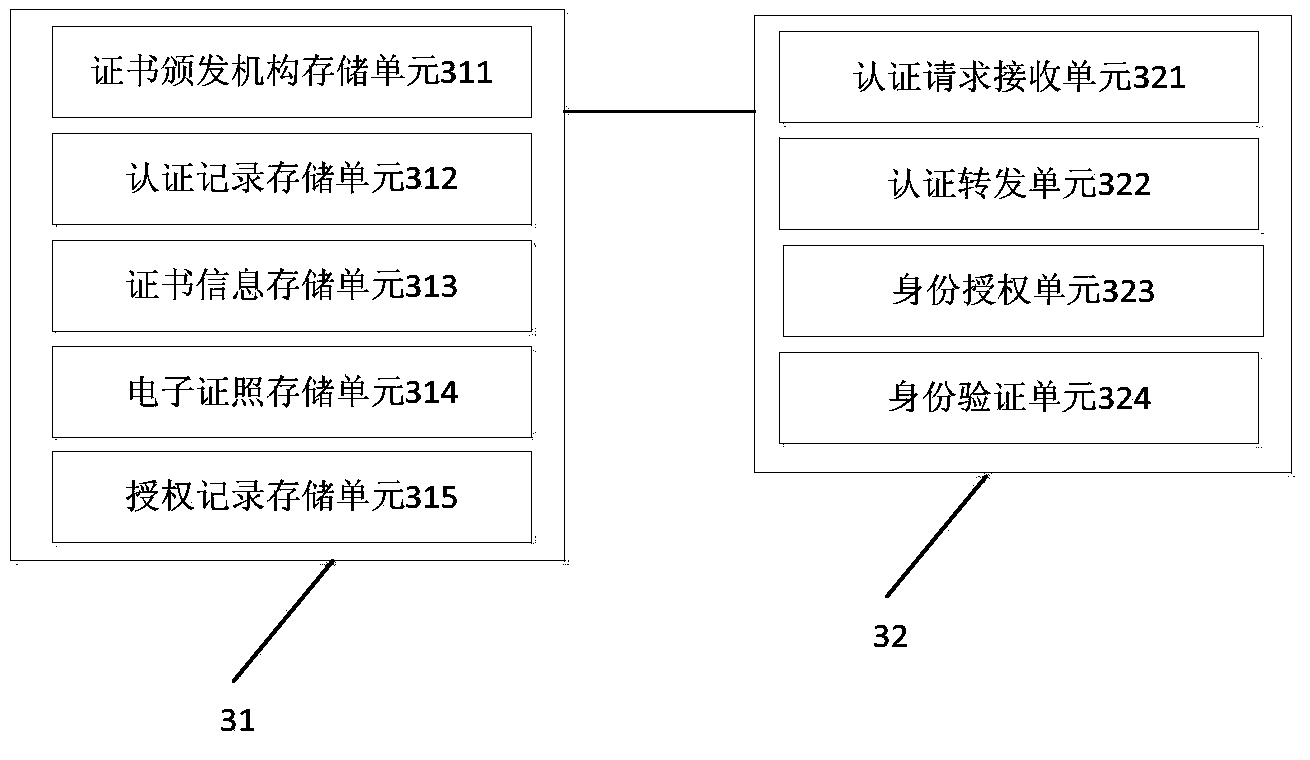
Identity authentication supporting platform and authentication method based on digital certificate interconnection and interworking
ActiveCN103475485AImprove docking efficiencySimplify the identity verification processUser identity/authority verificationDigital data authenticationInternet privacyEngineering
The invention discloses an identity authentication supporting platform and an authentication method based on digital certificate interconnection and interworking to solve the problems that an existing digital certificate is repeatedly issued and approved, and the using cost of a user is high and the using process is complex and to enable the identity of the virtual network to be relevant to the identity of the real world. The requests that digital certificate authentication needs to be carried out on application systems are centralized to the identity authentication supporting platform based on the digital certificate interconnection and interworking to be processed in a unified mode, the application systems are high in communicating efficiency, and the identity authentication procedures are simple and reliable. The identity authentication information based on the digital certificate interconnection and interworking can be shared, the digital certificate authentication does not need to be carried out on all application systems, and the identity authentication efficiency is improved.
Owner:ZHEJIANG ICINFO TECH
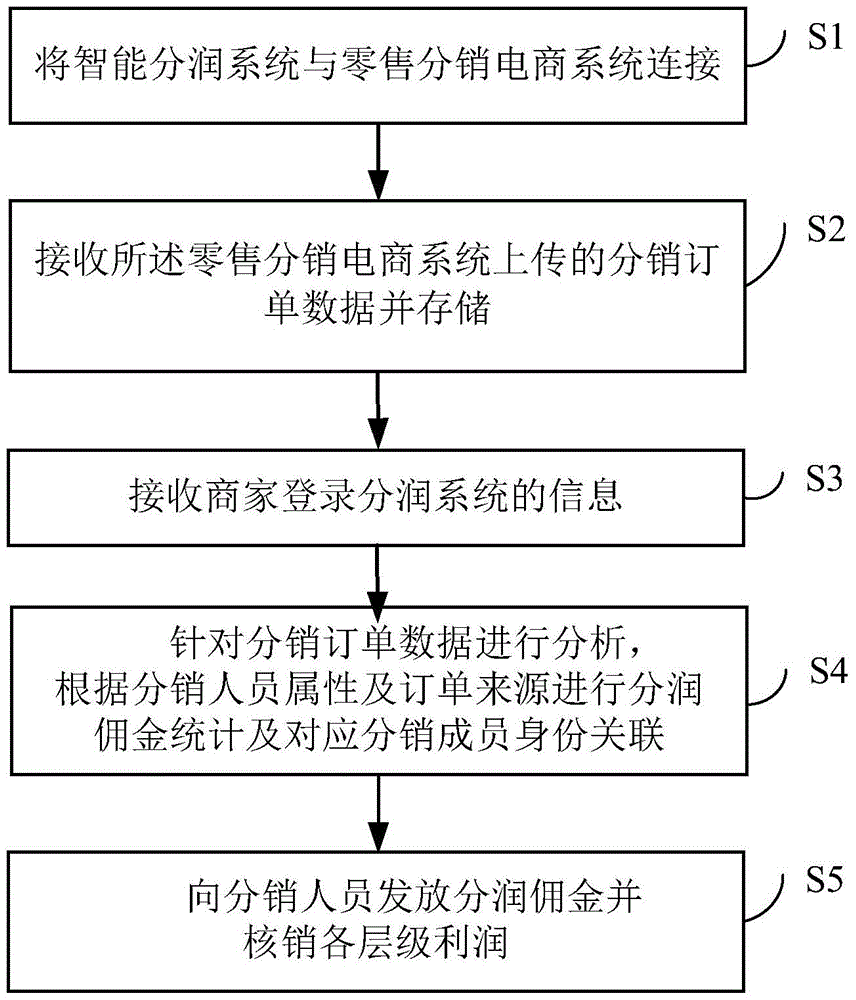
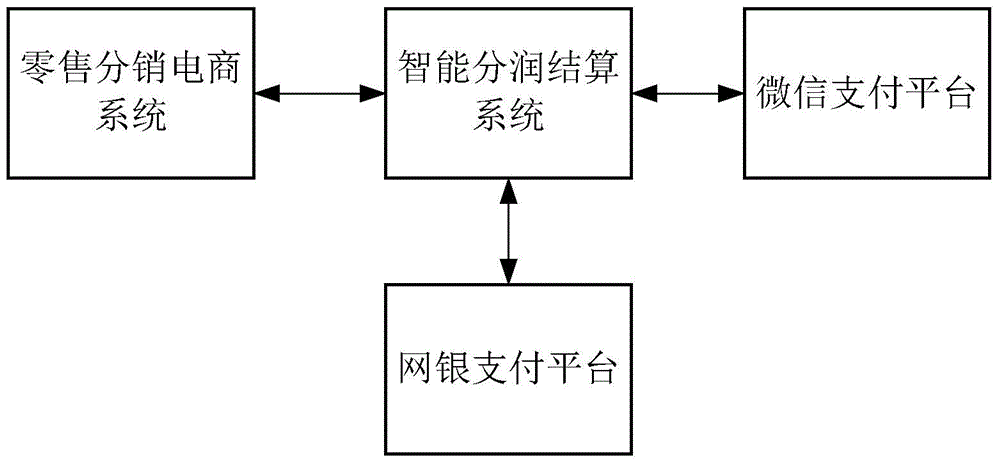
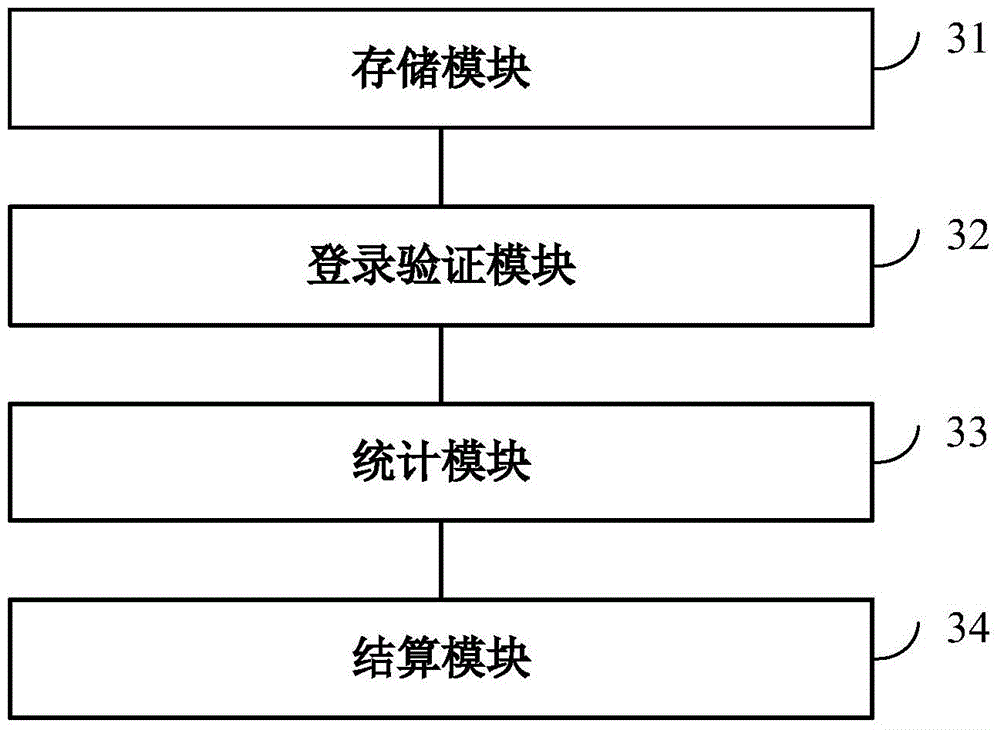
Intelligent profit sharing settlement method and system
InactiveCN105719088AFix error-prone problemsReduce frequent statistical accountingOffice automationBuying/selling/leasing transactionsE-commerceComputer science
The embodiment of the invention discloses an intelligent profit sharing settlement method and system.The method includes the steps that the intelligent profit sharing settlement system is connected with a retail distribution e-commerce system; distribution order data uploaded by the retail distribution e-commerce system is received and stored; information about the operation that a merchant logs into the profit sharing settlement system is received; the distribution order data is analyzed, and profit sharing commission statistics and corresponding distribution member identity correlation are conducted according to attributes of distribution members, order sources and basic profit sharing information; profit sharing commissions are distributed to the distribution members, and all layers of profits are canceled after verification.Thus, the problem that in an existing network marketing system, mistakes are easily made when enterprise financial staff frequently perform statistical accounting and manually distribute the commissions is solved.
Owner:SHENZHEN HUAYANG XINTONG TECH DEV LTD
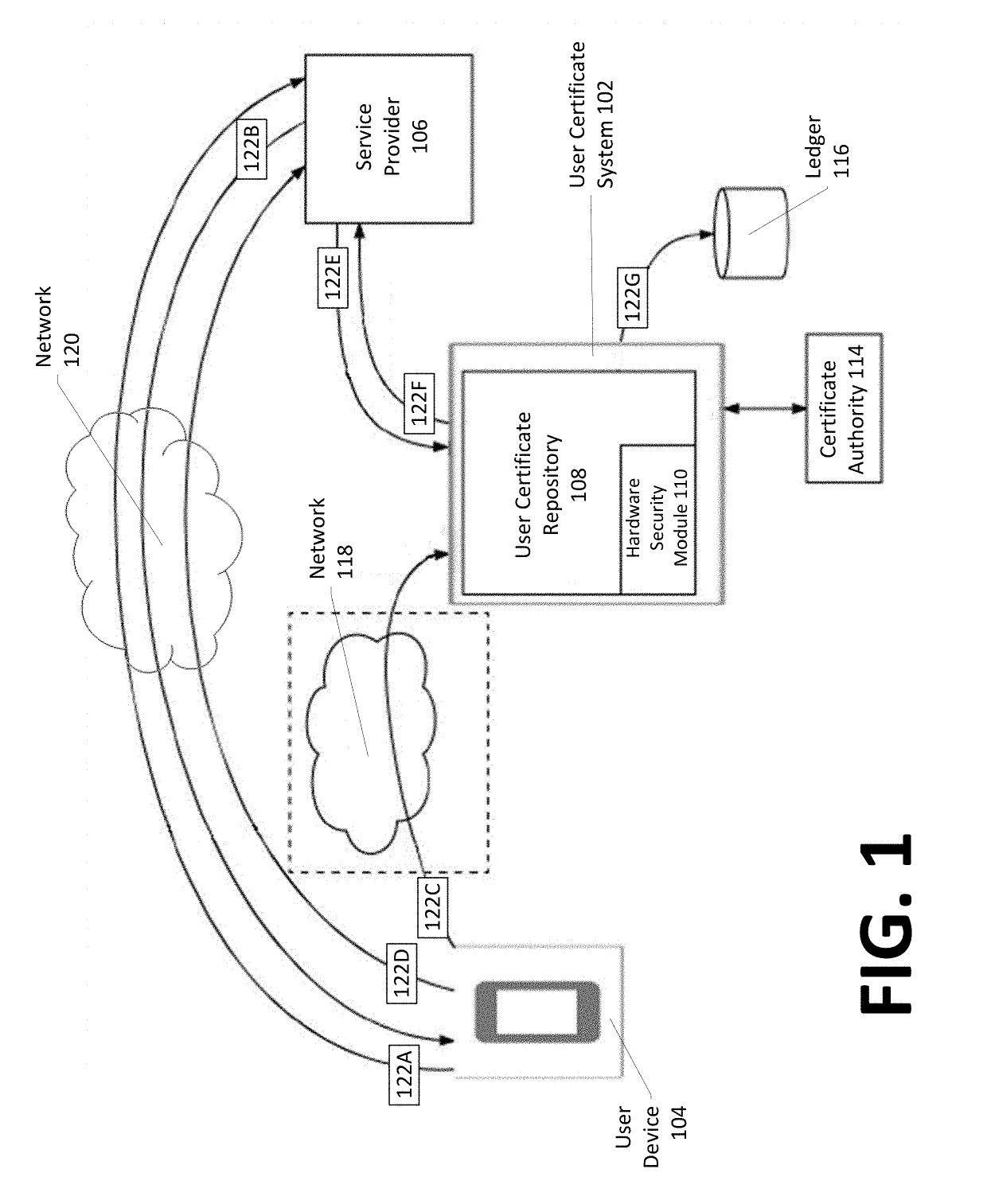
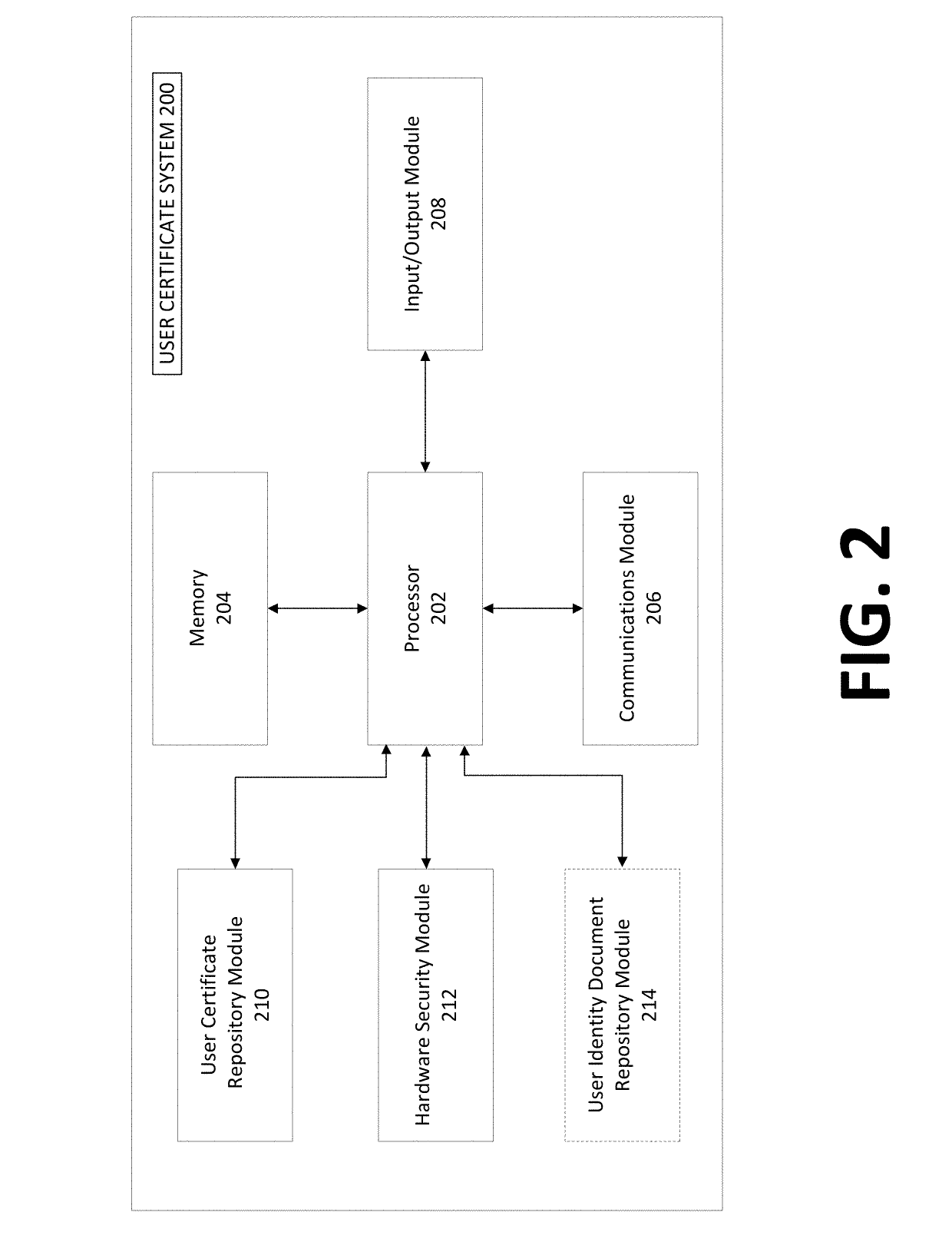
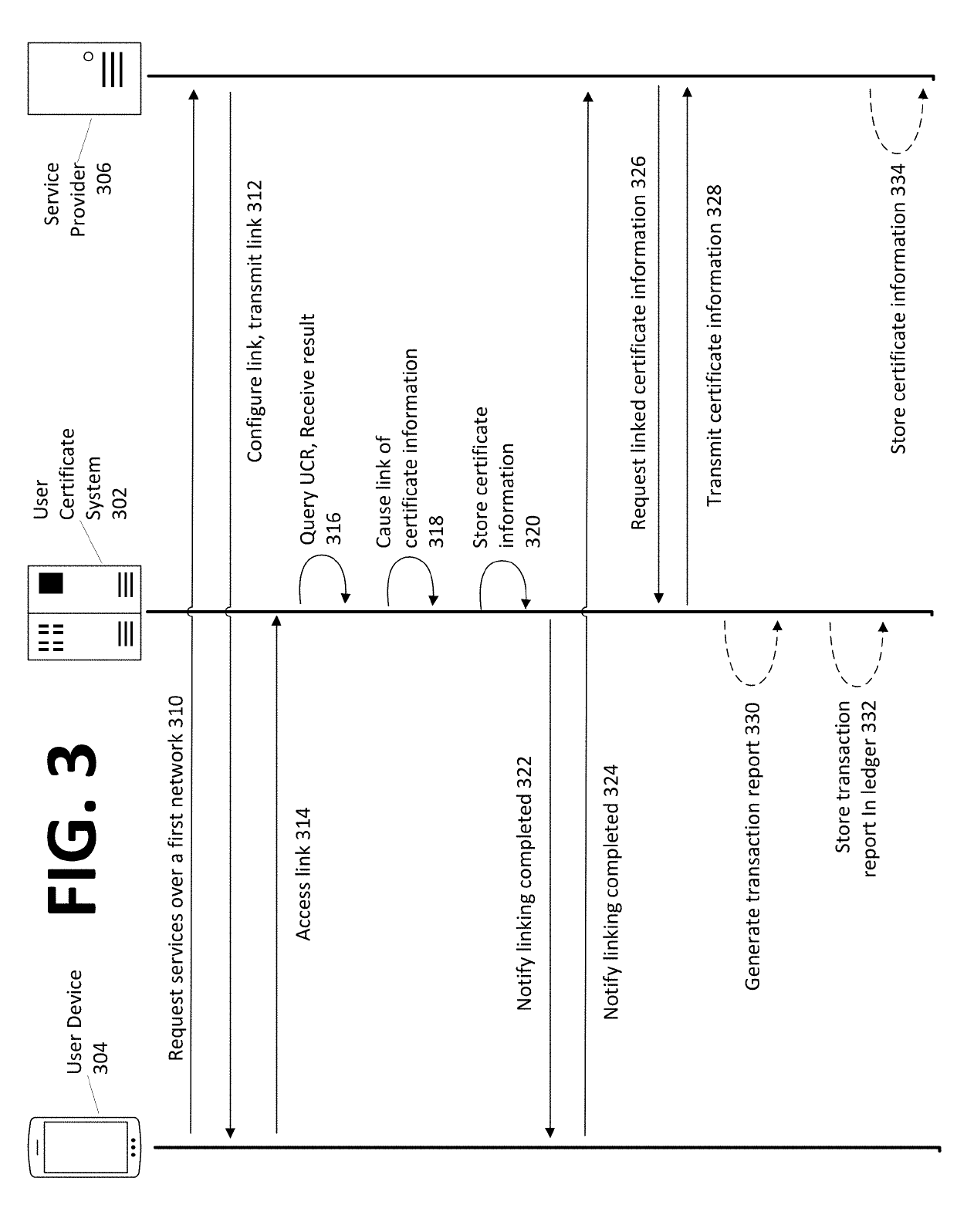
Identity-linked authentication through a user certificate system
InactiveUS20190140844A1Easy accessKey distribution for secure communicationUser identity/authority verificationInternet privacyHardware security module
Systems, methods, apparatuses, and computer readable media for facilitating user identity authentication to a service provider by linking, on a user certificate system, identity-linked information to certificate information, such that the certificate information may be used to generate an identity message that the service provider may verify to confirm a user identity. An exemplary method comprises receiving identity-linked information, retrieving public certificate information, retrieving, from a hardware security module, a private key, causing transmission, over a second network to the service provider, of a notification that an identity message is available for access, the identity message based on the retrieved public certificate information and the retrieved private key, and upon reception, from the service provider, of a request for the identity message, generating and transmitting the identity message, wherein the identity message comprises at least an encrypted portion of the identity message encrypted using at least the private key.
Owner:AVERON US INC
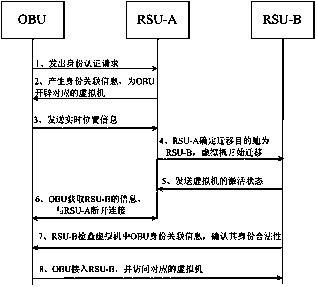
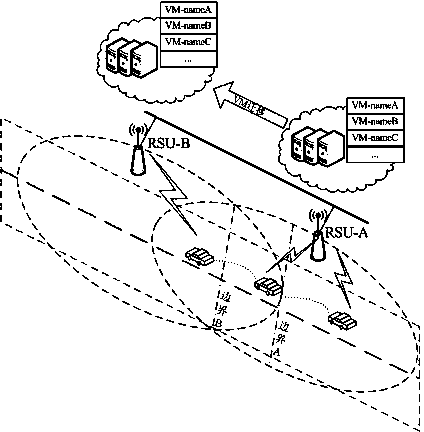
Vehicle identity authentication method based on virtual machine migration technology
ActiveCN103441847AEnsure consistencyQuick switchUser identity/authority verificationRelevant informationOn board
The invention relates to the field of identity authentication of an internet of vehicles and discloses a vehicle identity authentication method based on the virtual machine migration technology. The vehicle identity authentication method based on the virtual machine migration technology comprises the following steps that a mobile on board unit sends an identity authentication request to a road side unit with an identity certificate of the mobile on board unit as a credential, after determining the legitimacy of the identity of the mobile on board unit, the road side unit turns on a virtual machine corresponding to the mobile on board unit, and identity relevant information of the on board unit is stored in the corresponding virtual machine; based on the position information of the on board unit, the current road side unit can determine the migration address, corresponding to the virtual machine, of the on board unit, namely, the network address of a target road side unit; when the connection between the on board unit and the current road side unit is interrupted and the on board unit is connected to the target road side unit, and the target road side unit detects the corresponding relation between the identity relevant information stored in the current virtual machine which is turned on and the identification certificate of the on board unit which requests identity authentication so that the identity legitimacy of the on board unit can be determined; the on board unit can have access to the virtual machine corresponding to the migrated on board unit through the target road side unit.
Owner:GUANGDONG UNIV OF TECH
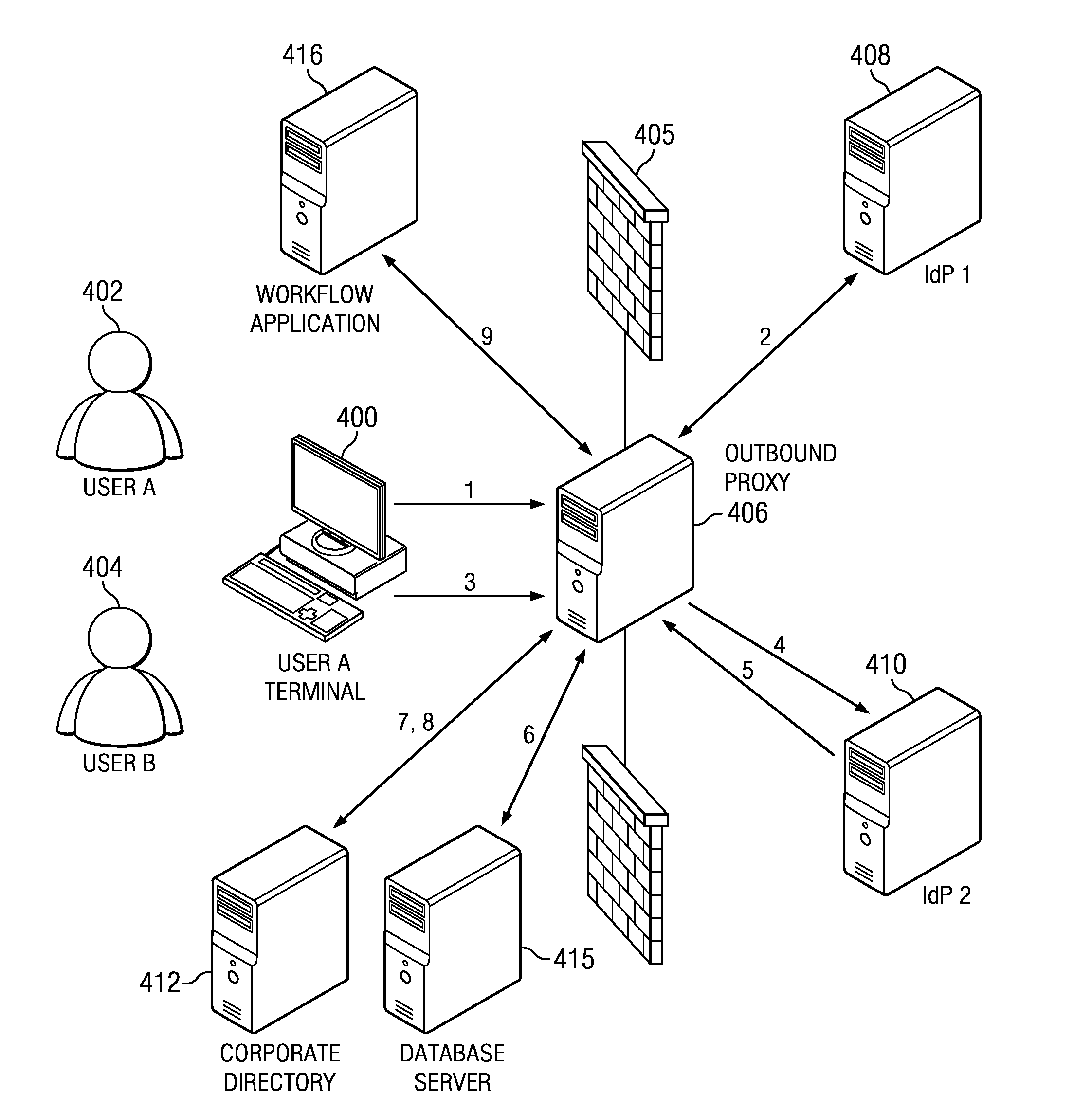
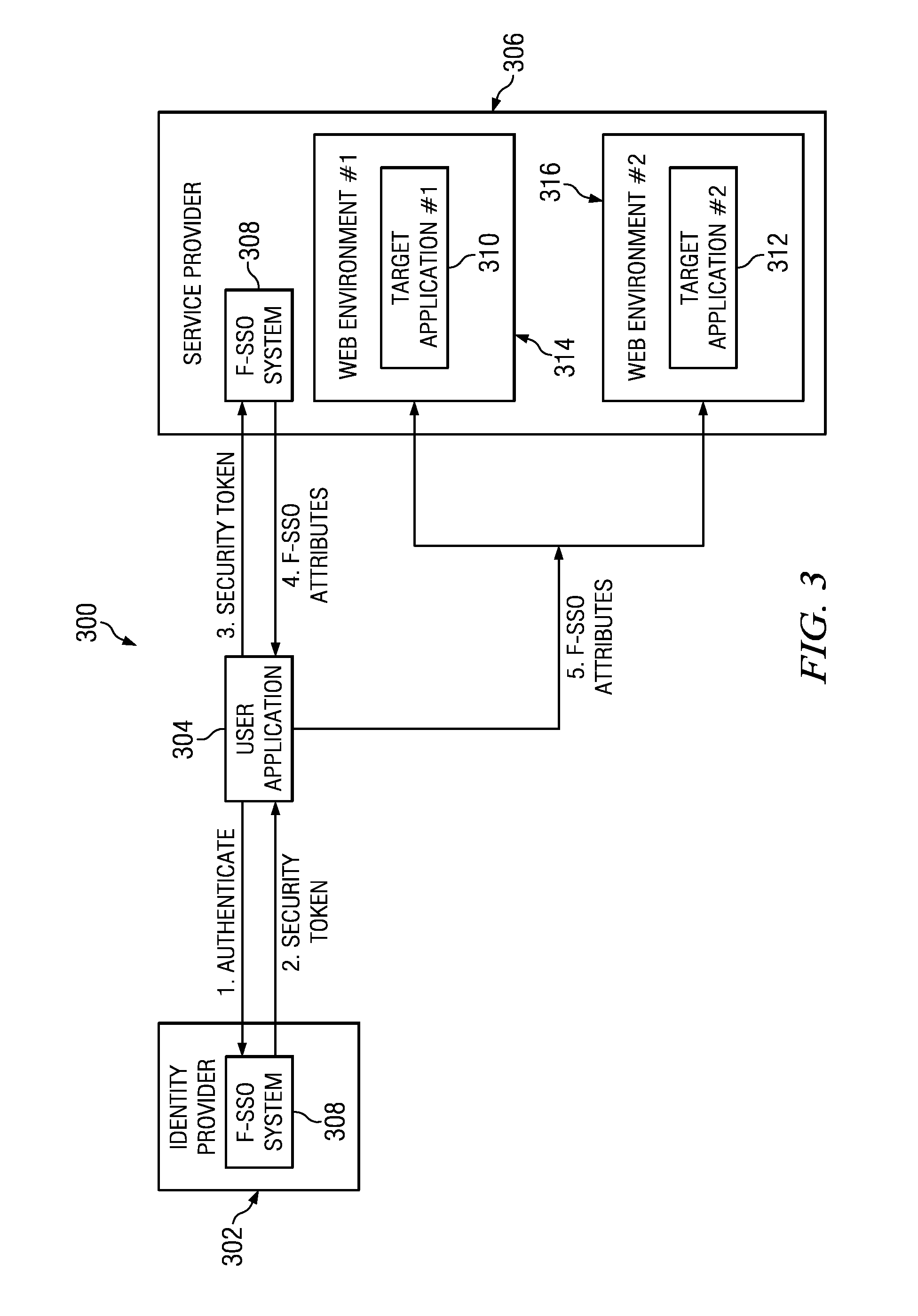
Unsecured asset detection via correlated authentication anomalies
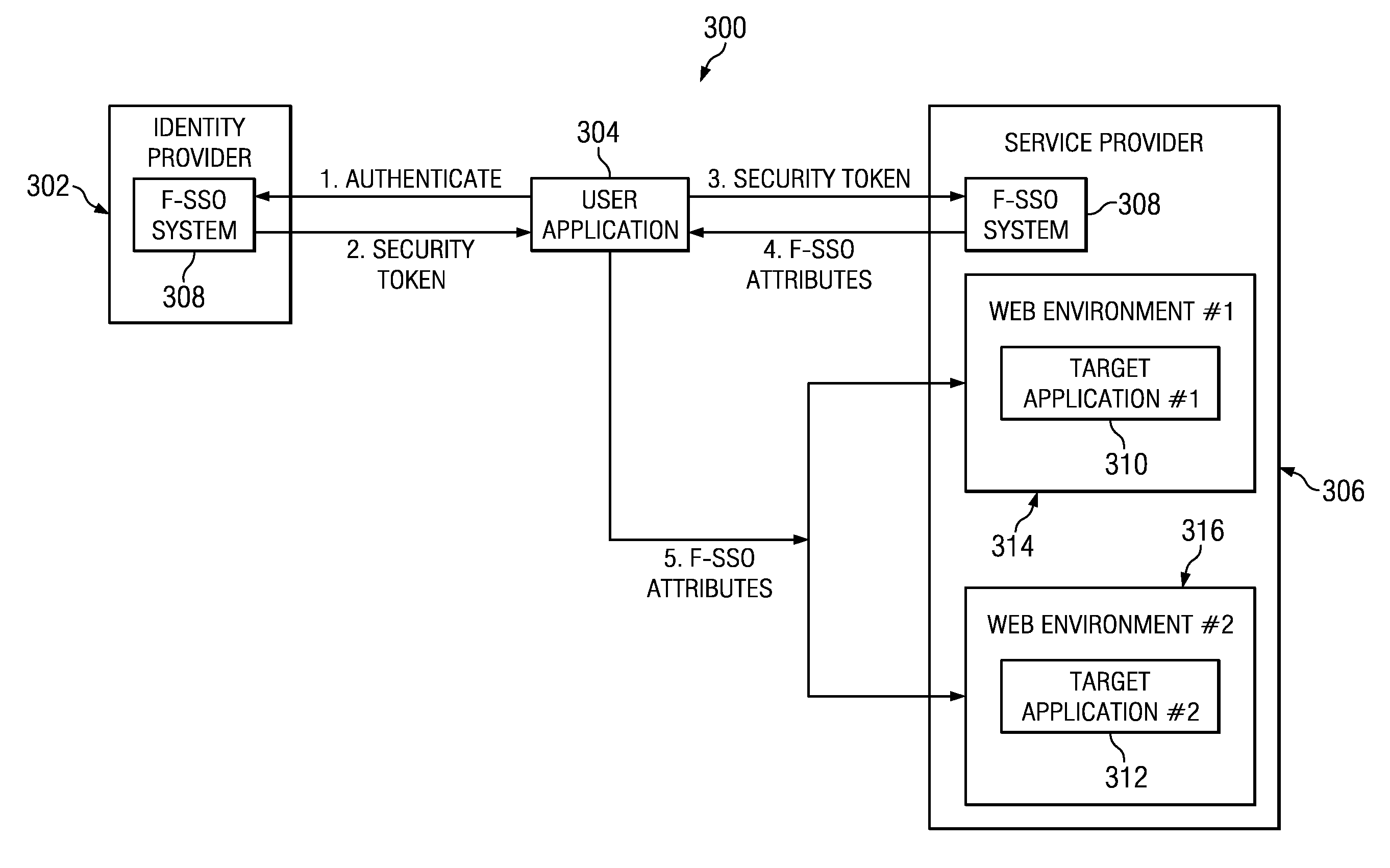
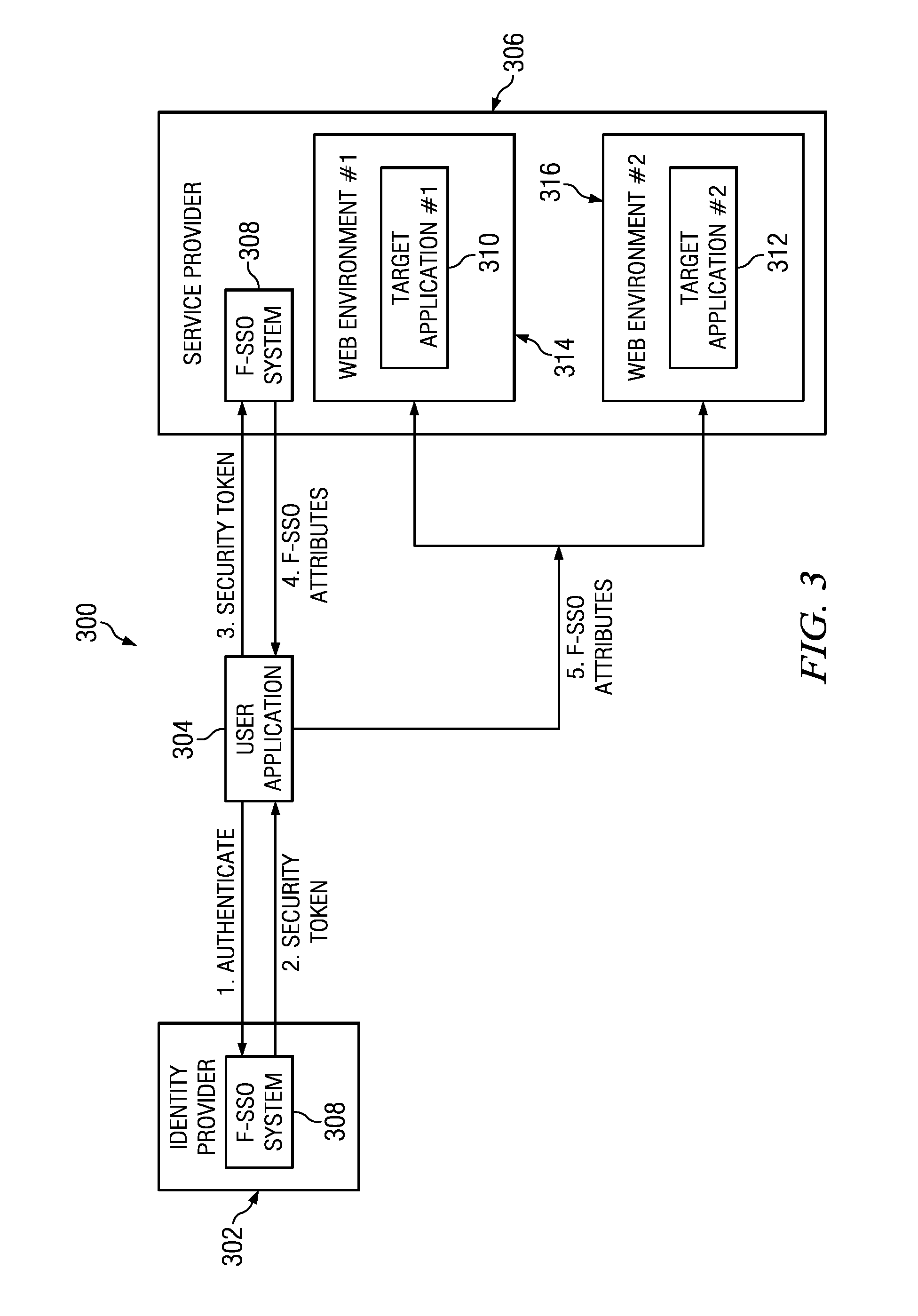
ActiveUS20140020077A1Anomaly detectionDigital data processing detailsUser identity/authority verificationWeb siteIdentity provider
A method, apparatus and computer program product for detecting that a computing device may not be secure based on inconsistent identity associations identified during Federated Single Sign-On (F-SSO). A detection proxy detects when a user with a particular session is accessing an identity provider (IdP) that is associated with an account that is not the current user's account. When a user performs a login to an F-SSO-enabled IdP, the proxy performs an F-SSO, and the results are compared with known aliases for that particular federation partner. If an anomaly is detected (e.g., the in-line device sees that a user logs into a web site as someone else), a workflow is initiated to perform a given action, such as blocking access, issuing an alert, or the like.
Owner:IBM CORP
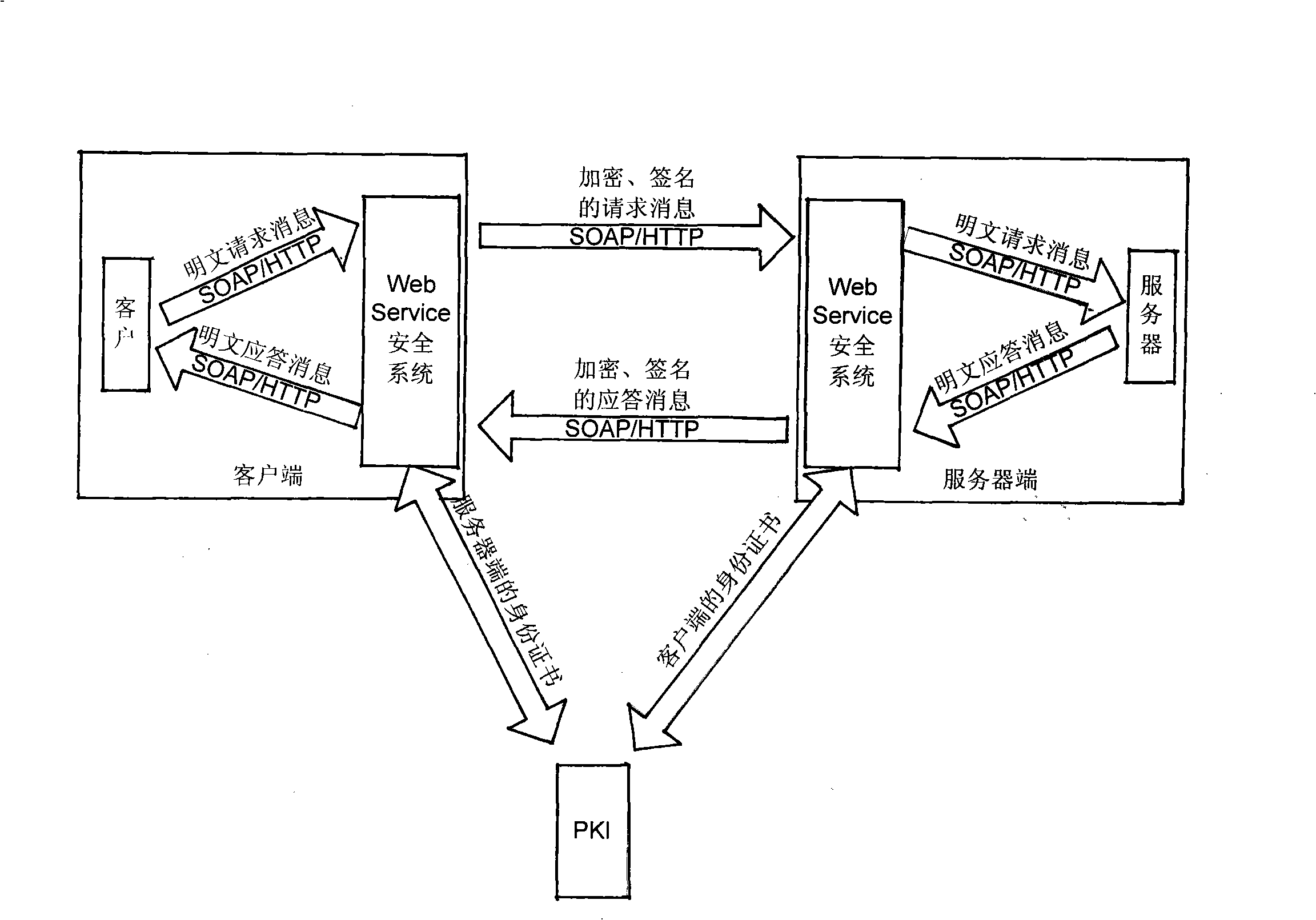
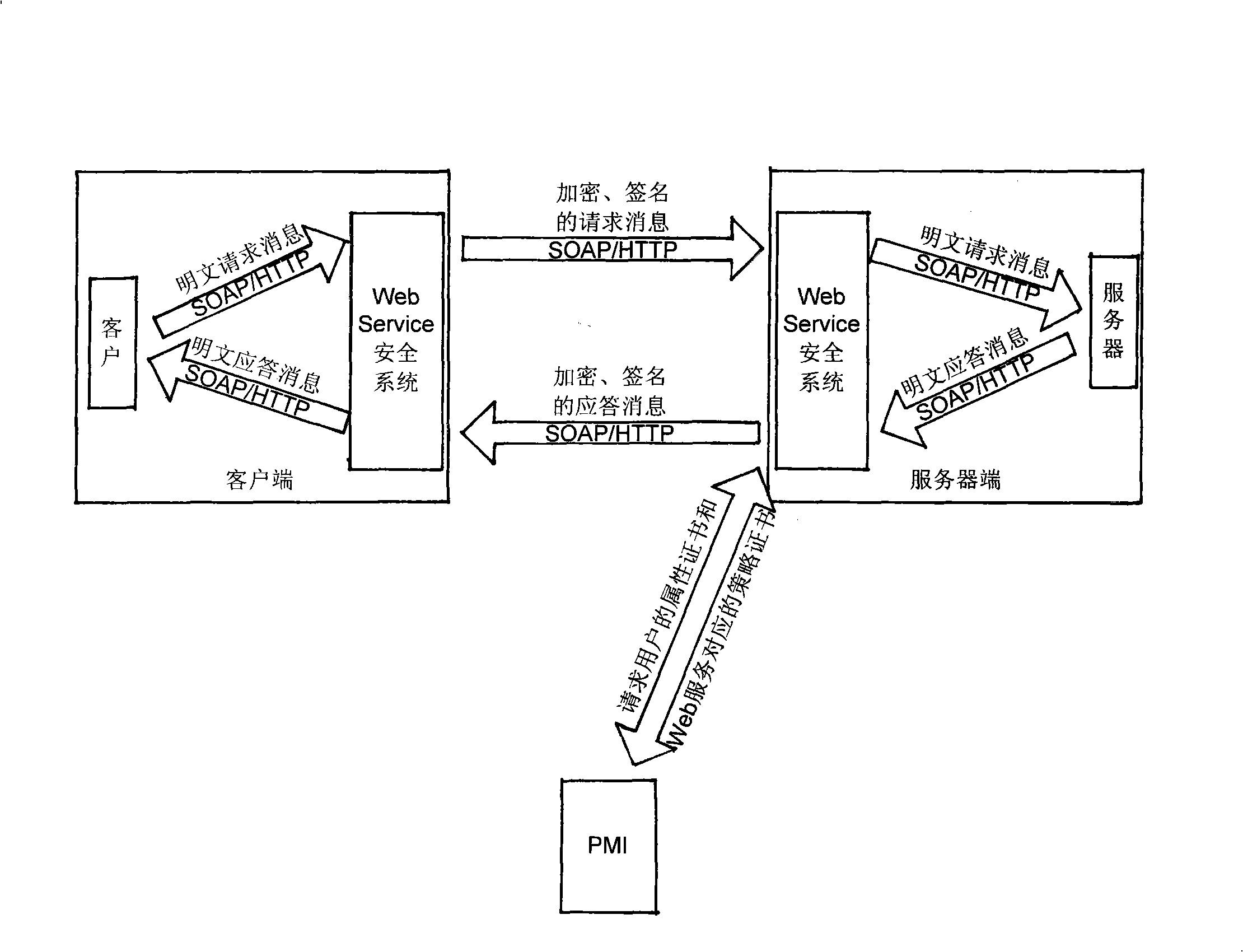
Web service security control mechanism based on PKI and PMI
InactiveCN101296230AQuick responseHigh precisionKey distribution for secure communicationUser identity/authority verificationConfidentialityWeb service
The invention discloses a safety control mechanism based on Web service of PKI and PMI, which comprises a PKI system, a PMI system and a safety system of Web service. Users apply for a letter of identification through the PKI system, and then apply for an attribute certificate according to the letter of identification to the PMI system. Through the attribute certificate, the user identification and one or more roles are related. The roles then are bond with one or more Web service through the strategy certificate pre-defined by the PMI system. Then when users use Web service, the safety system of web helps the PKI system to check the legality of an identification letter and helps the PMI system to check whether a user has the right to call the Web service or not. When all checks pass through successfully, the user can access the Web service so as to realize safety calling of Web service. The mechanism of the invention provides a set of identification authentication and access control systems with strong integrity, thereby ensuring the confidentiality, the integrity and the non-repudiation of calling information of Web service.
Owner:ZHEJIANG UNIV
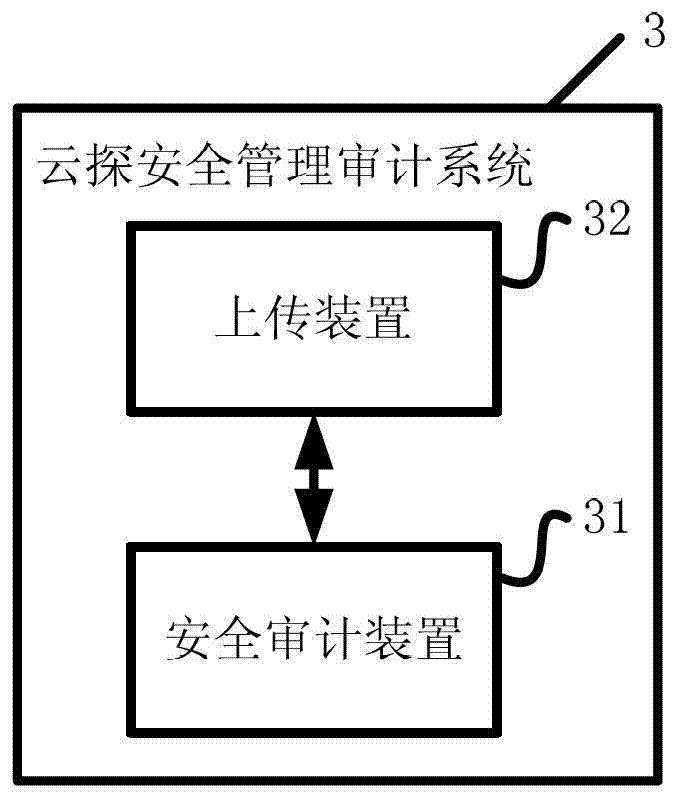
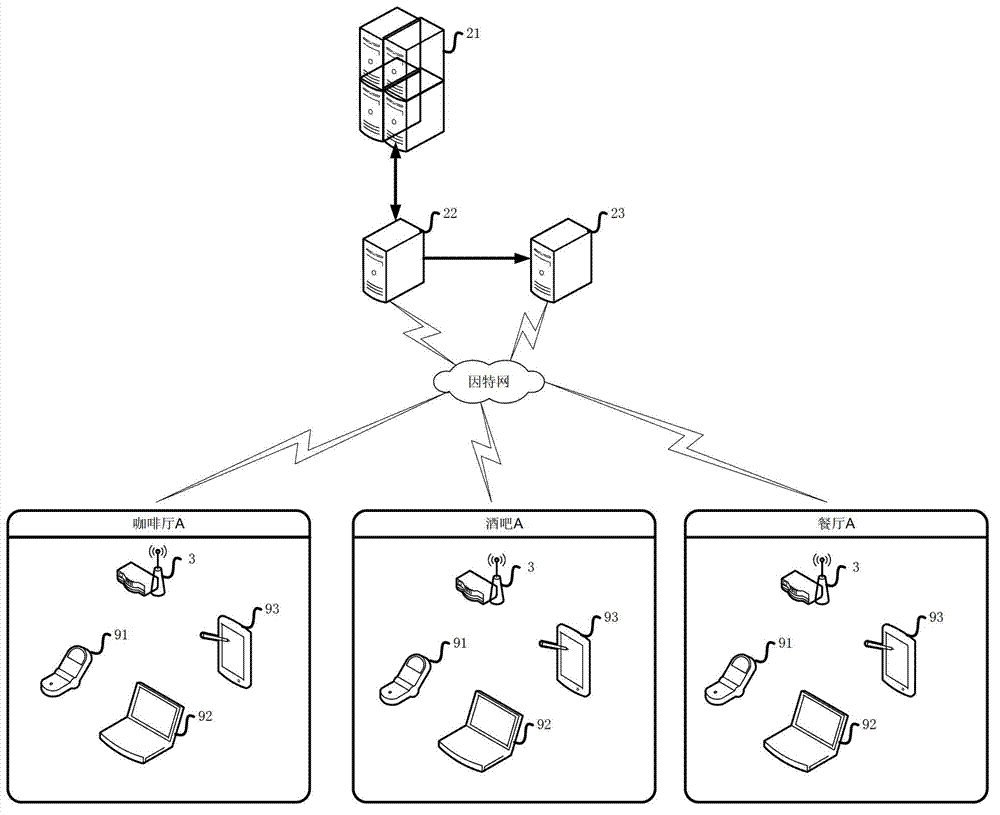
Cloud detection safety management auditing system
InactiveCN102857388AWith security audit functionMeet the requirements of public securityData switching networksSoftware systemOriginal data
The invention provides a cloud detection safety management auditing system. The cloud detection safety management auditing system comprises following modules: a software system, a hardware device and an updating device, wherein the software system and the hardware device are used for auditing a networking behavior by capturing an original data package; and the updating device is used for updating the original data package to a cloud storage center. The invention further provides a corresponding system which has a network safety auditing function, a public security requirement is satisfied by virtue of a data package capturing function, and wide small-sized online places are facilitated as well. An updating function of the original data package is added, the data are updated cloud centers through Internet, and thus, the support of history data is provided to the case handling and investigating of policemen. A plurality of identity authentication manners are provided, so that addresses of networking devices and personal real identities are associated together.
Owner:SHANGHAI YUNCHEN INFORMATION TECH
System and method for providing cellular access points
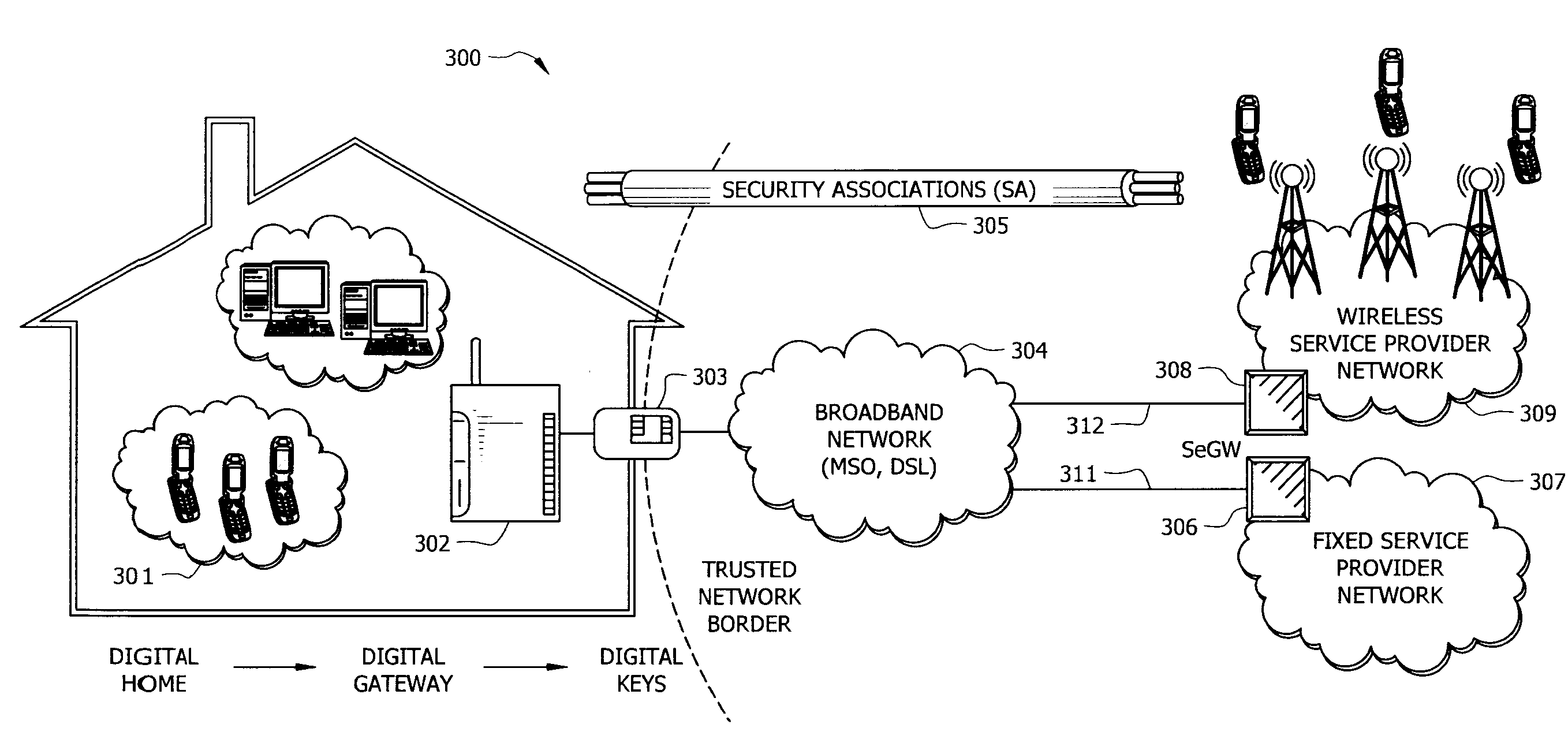
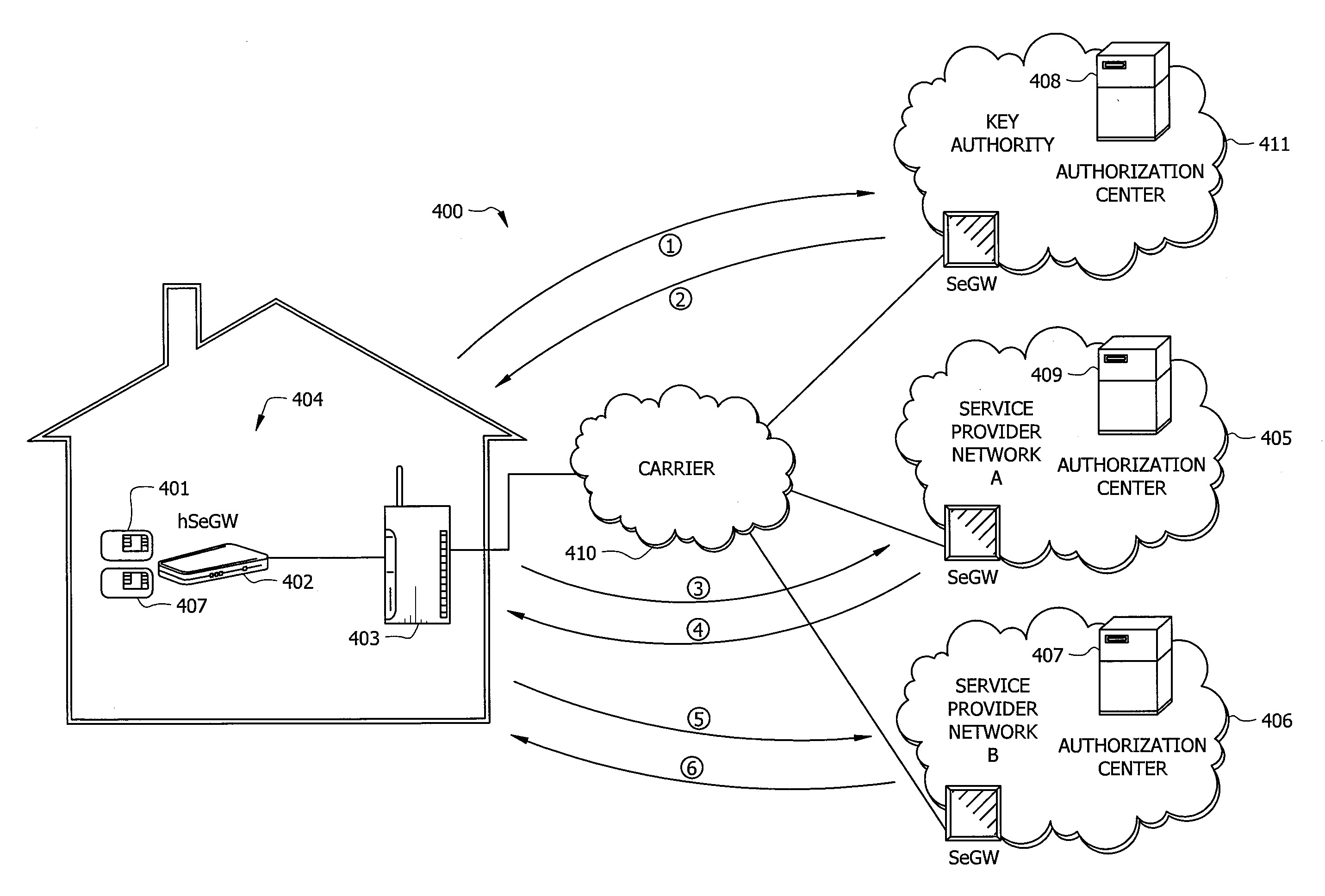
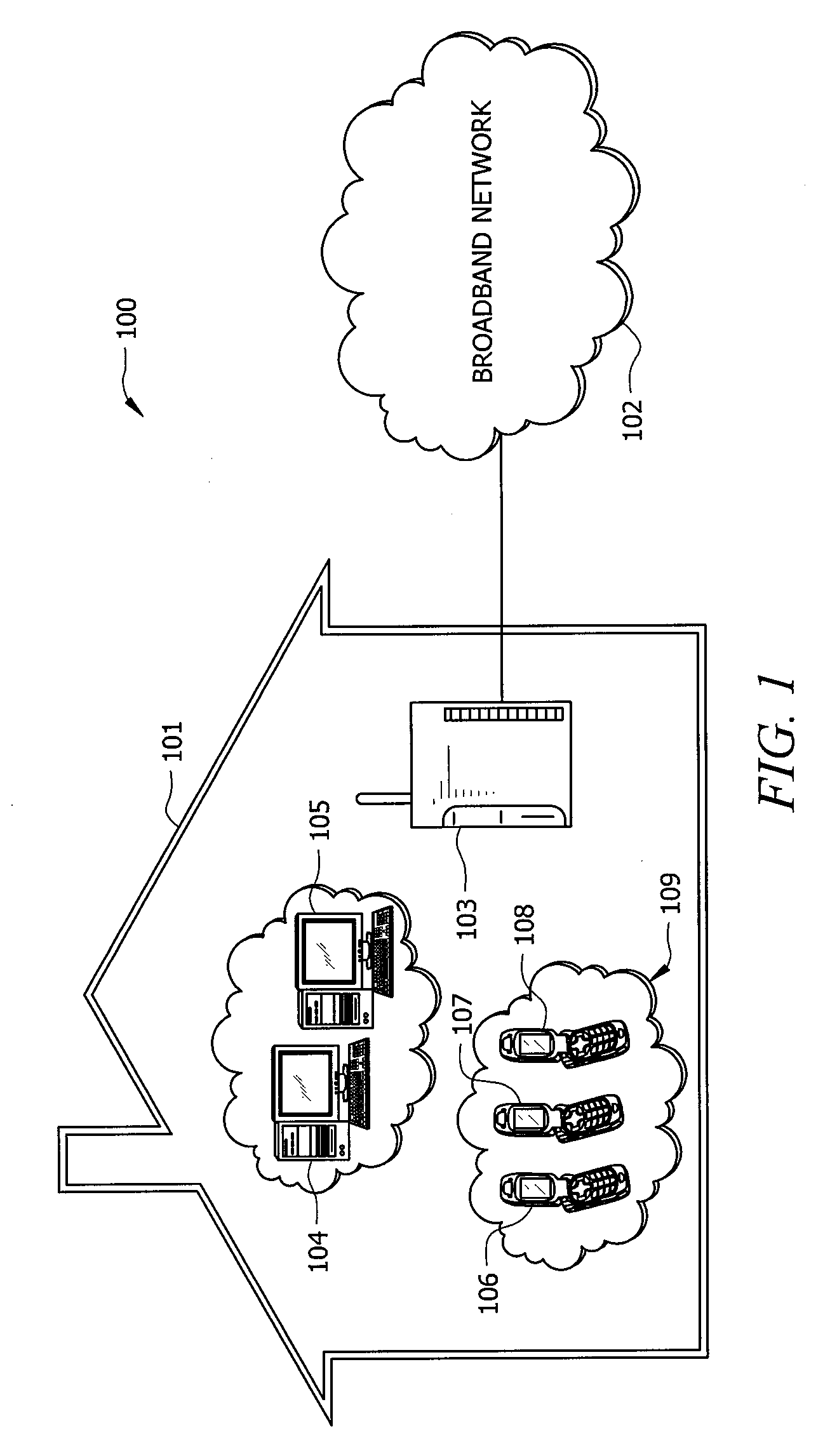
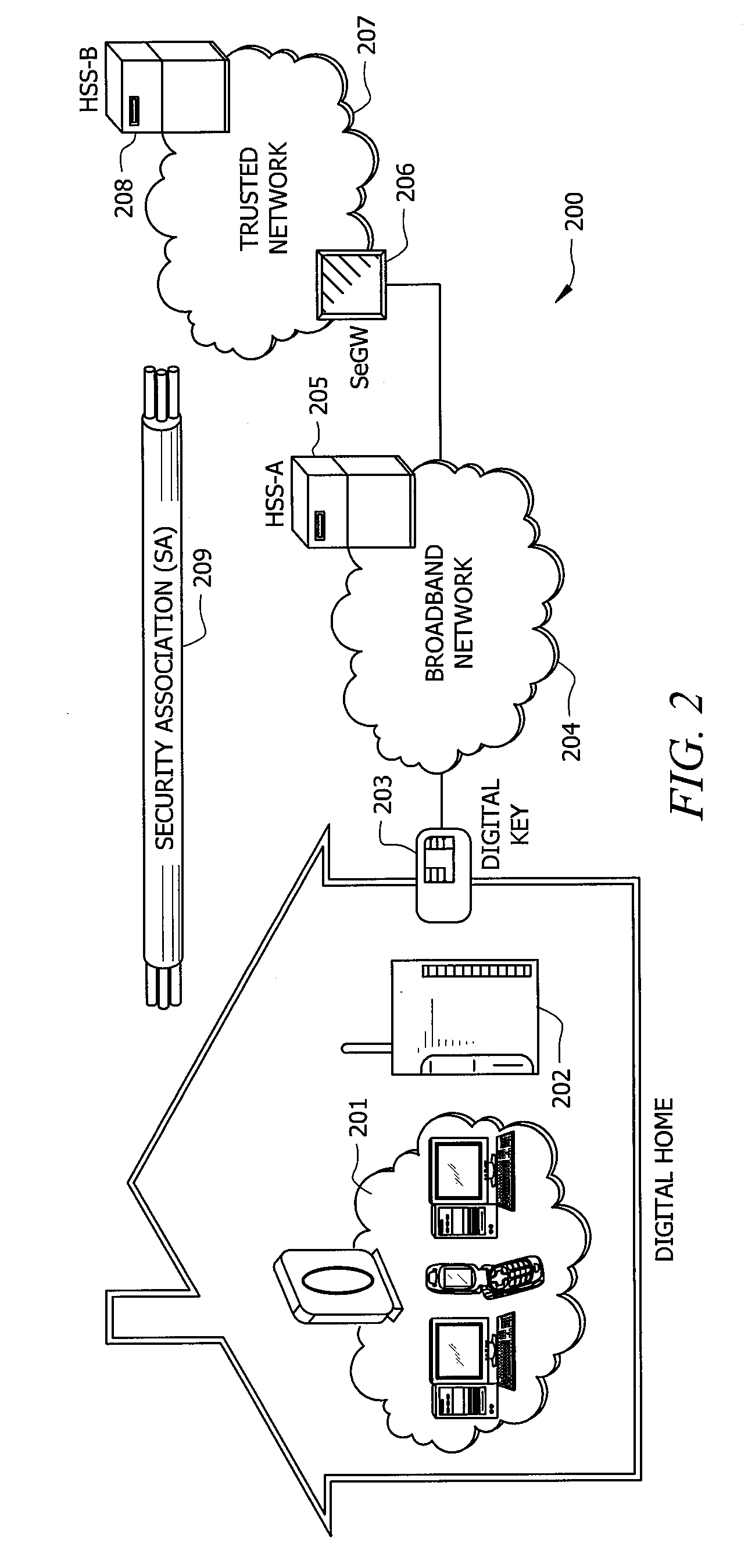
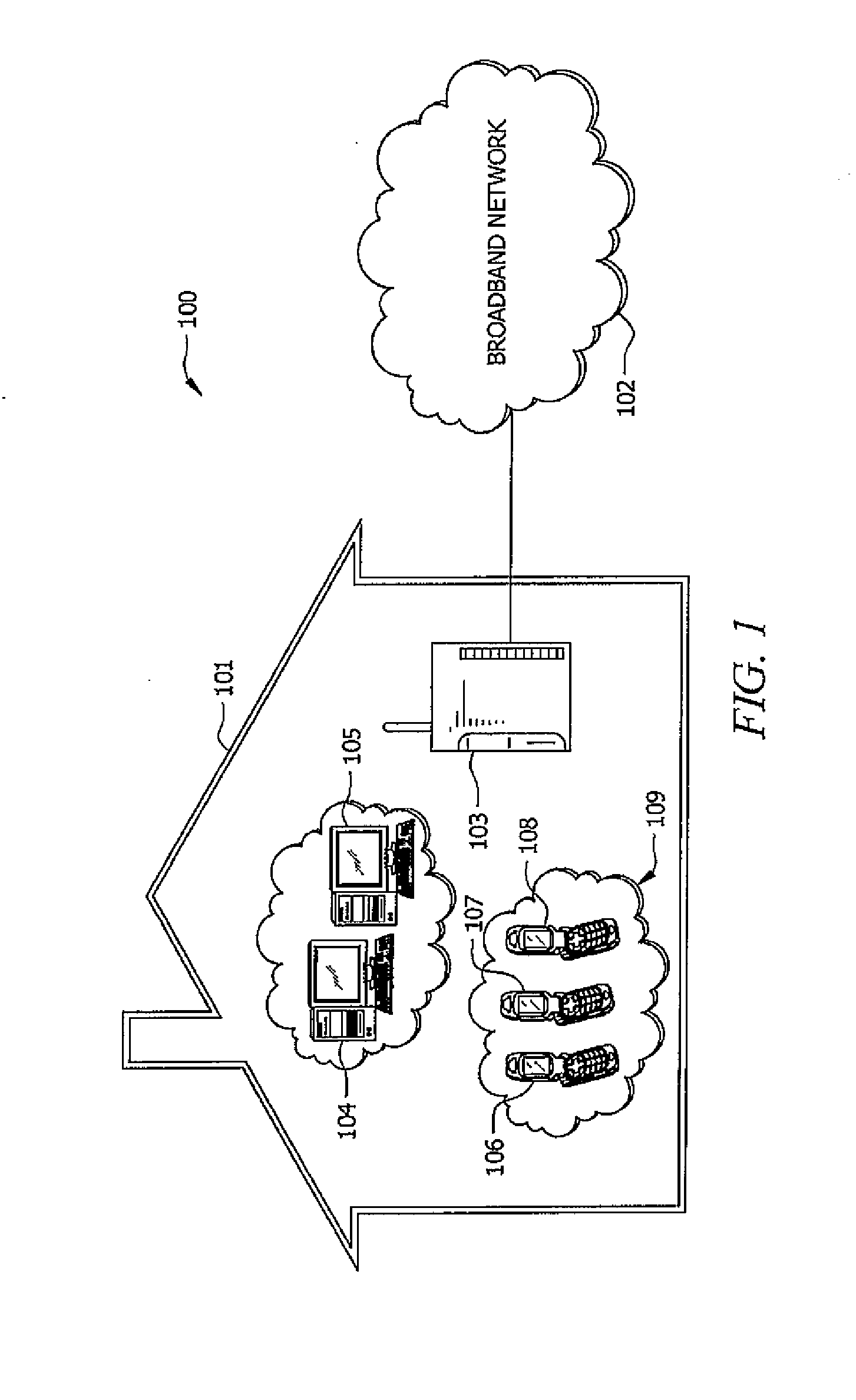
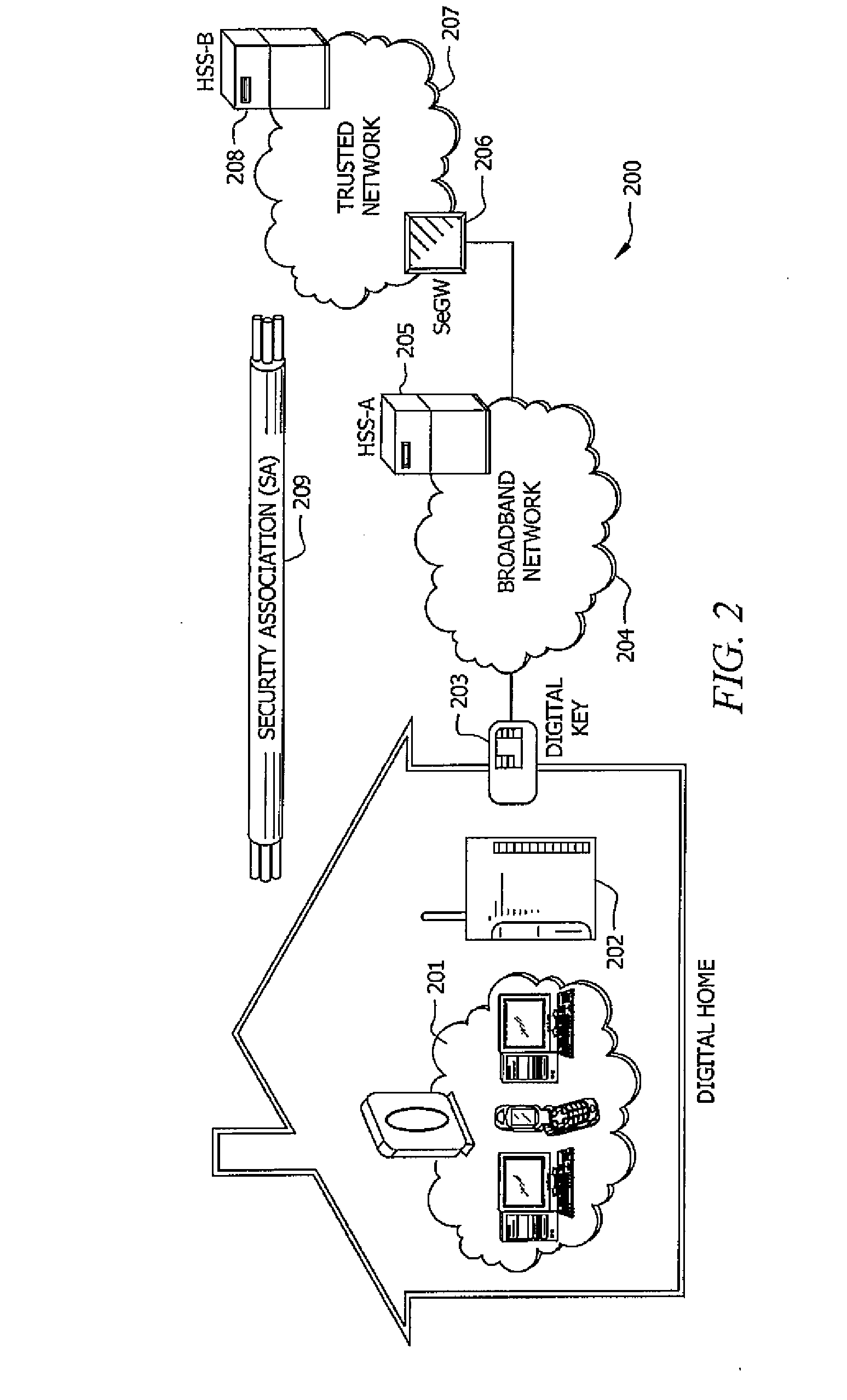
A system and method for providing a identity association between a subscriber in a private network and a provider over a public network is described. The system and method include a subscriber security gateway in the private network, the subscriber security gateway providing policy enforcement and signaling between the private network and the provider over the public network and at least one digital key associated with the provider and readable by the subscriber security gateway and operable to provide a identity association with the provider. A network device in the private network, the network device operable to establish a trusted media channel between the provider and the network device using the public network as a result of the signaling and policy enforcement at the subscriber security gateway using the digital keys, and a security gateway in the provider network, the security gateway including a registry for authenticating the user using the digital key and for maintaining a record of the subscriber's relationship with the provider.
Owner:CONTINEO SYST
System and method for creating a secure billing identity for an end user using an identity association
A system and method include a device connectable to a private network and designed to access to a public network, the device used to control identity associations for end user devices in the private network, wherein the device has an associated device key and is operable to receive additional keys associated with service providers, and a conditional access system associated with the device, the conditional access system operated by a key authority to manage the device key and to authenticate the service provider keys thereby allowing identity associations between the private network and the service providers.
Owner:CONTINEO SYST
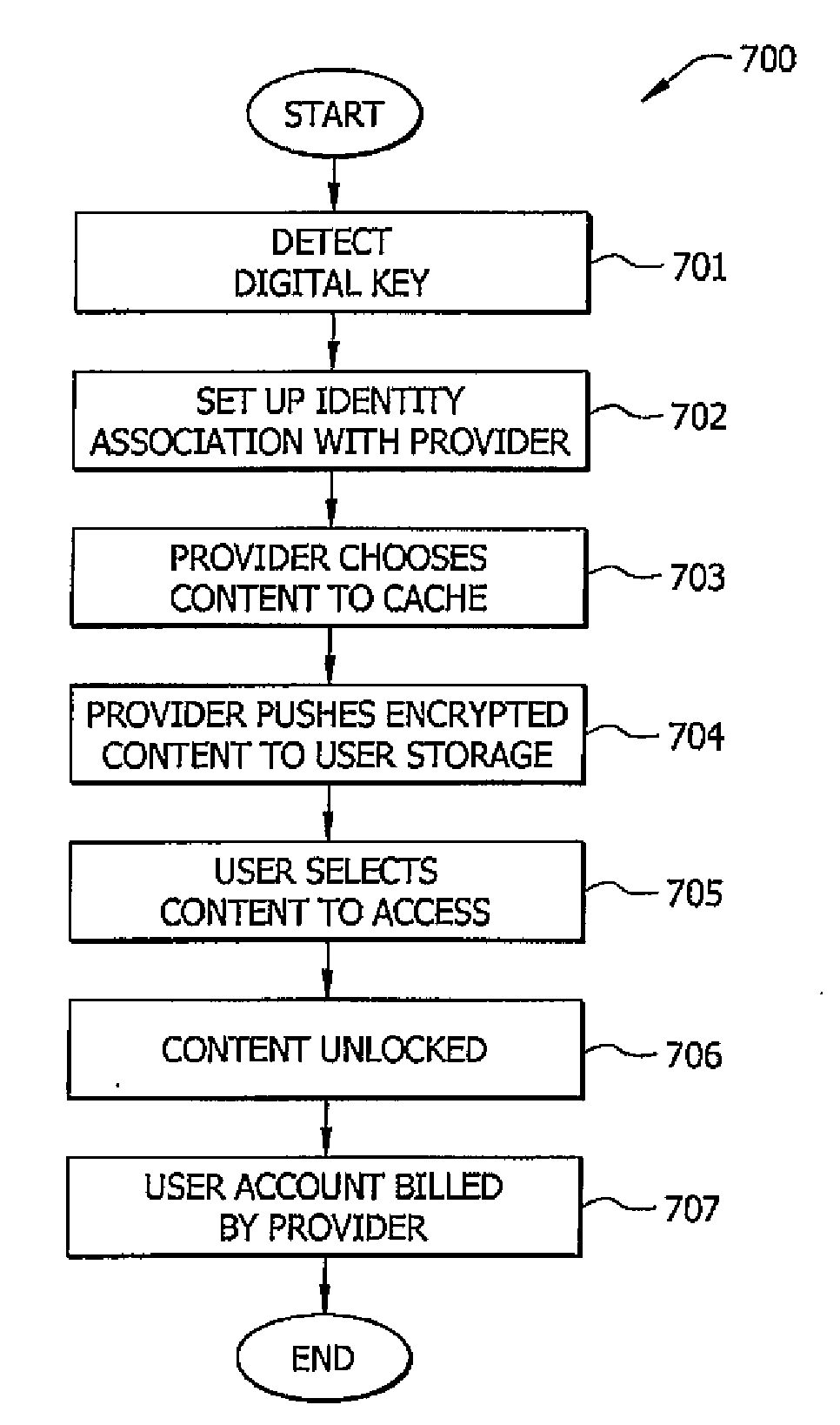
System and Method for Pre-Placing Secure Content on an End User Storage Device
InactiveUS20090249067A1Multiple keys/algorithms usageUnauthorized memory use protectionInternet privacyComputer terminal
A system and method for pre-placing content from a provider on an end user storage device is described. The system includes a device connected to an end user network and a public network and used to interface with one or more digital keys, where each digital key is able to control one or more identity associations. A storage device attached to the end user network and is able to receive content from the provider using the identity association with the provider. The content is encrypted on the storage device using a keys established by the provider, such that the end user can only decrypt and access the content by agreeing to terms established by the provider using the digital key and identity association with the provider.
Owner:CONTINEO SYST
Method and system for allocating IP address
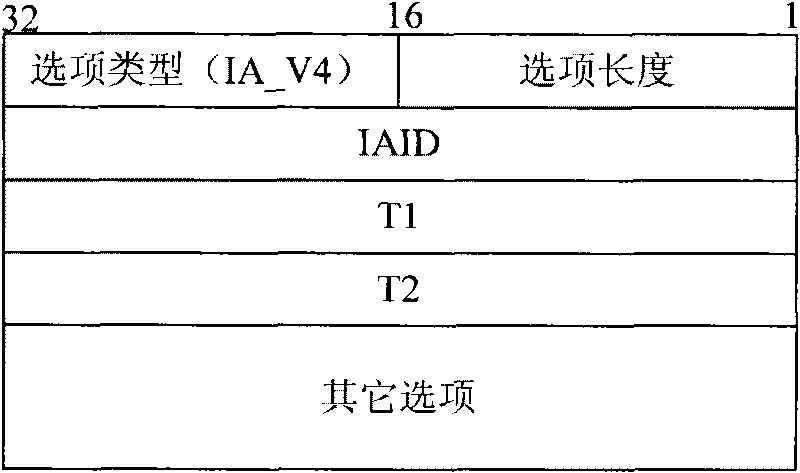
InactiveCN101707637AReduce dependenceFlexible and lightweight dynamic configurationTransmissionIp addressNetwork management
The invention discloses a method for allocating an IP address, comprising the following steps: sending a request message to a server of a dynamical host configuration protocol version 6 (DHCPv6) by a client which supports internet protocol version 4 (IPv4), requesting to allocate an IPv4 address, and carrying identity related (IA)-IPv4 options in the request message; and after the DHCPv6 server receives the request message, according to the (IA)-IPv4 options, allocating the IPv4 address for the client according to an address allocation strategy and sending the IPv4 address to the client. Under the environment of double protocol stacks of IPv4 and IPv6, the method leads the system to be capable of dynamically configuring the IPv4 address flexibly and easily, and reduces the dependency of the IPv4 service on a DHCPv4 protocol under the environment of the double protocol stacks; and simultaneously for a network manager, single DHCPv6 protocol is configured and used, thus being capable ofeffectively reducing the cost of operation and maintenance.
Owner:ZTE CORP
Method for obtaining IPV6ND address and broadband remote access server (BARS)
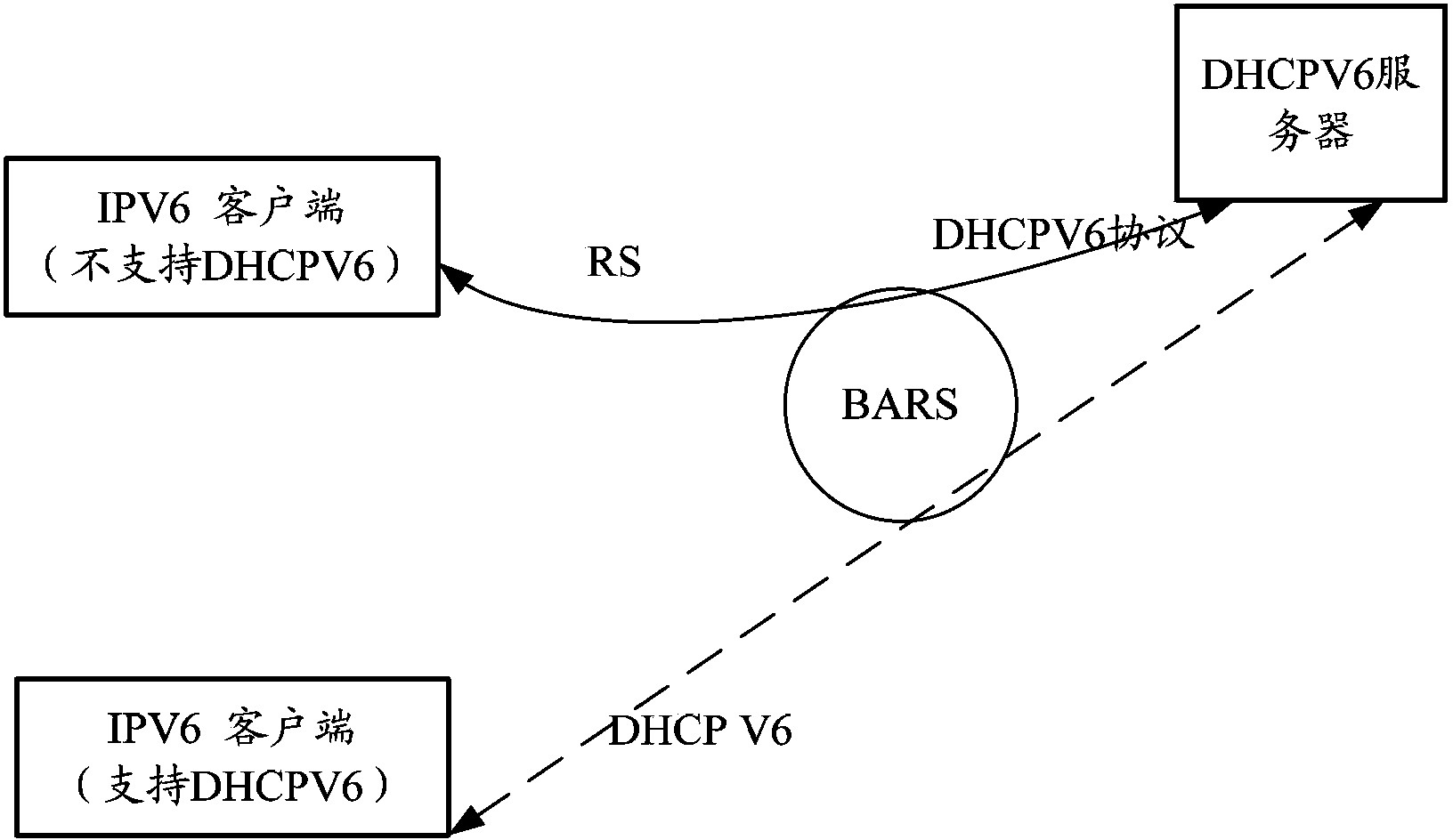
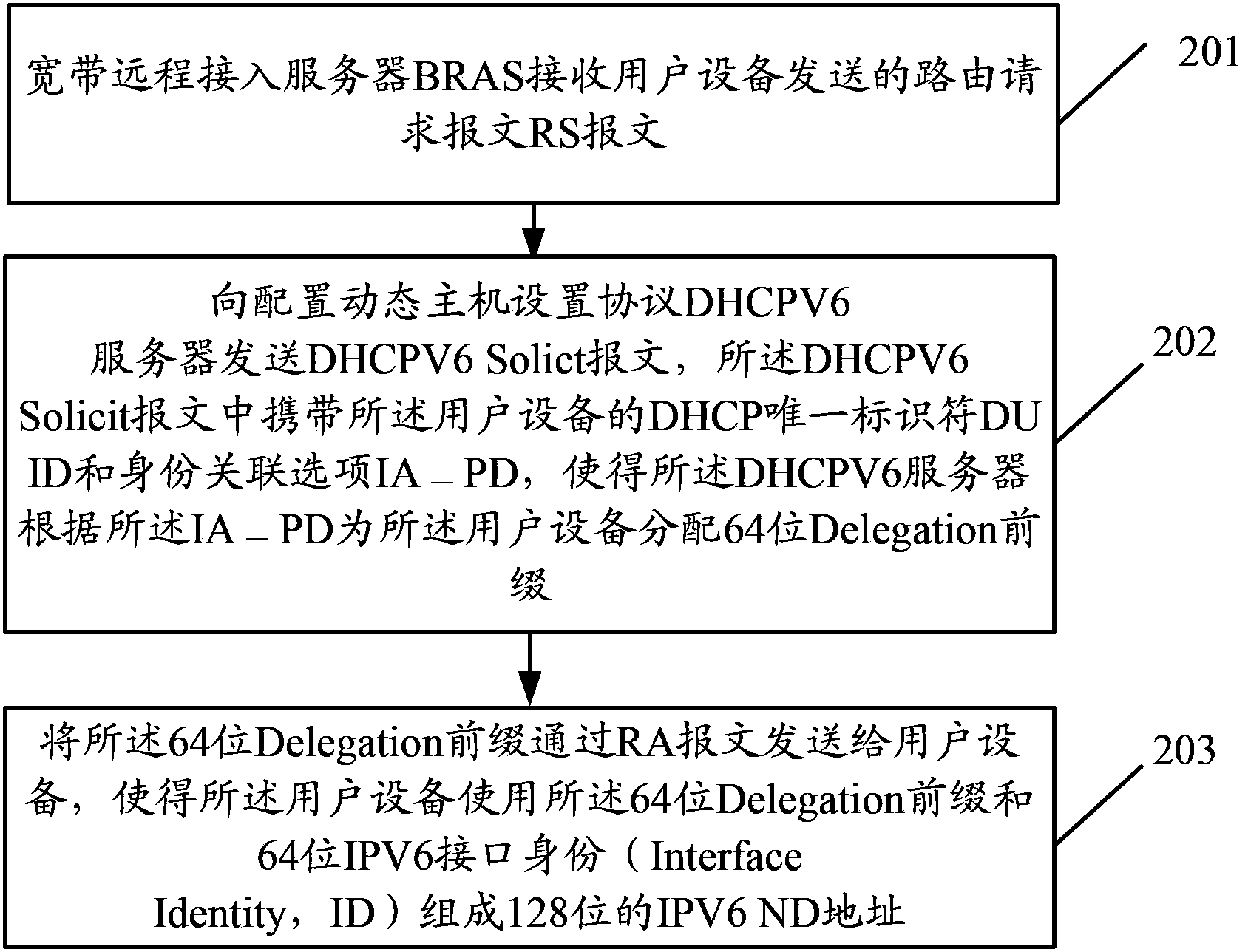
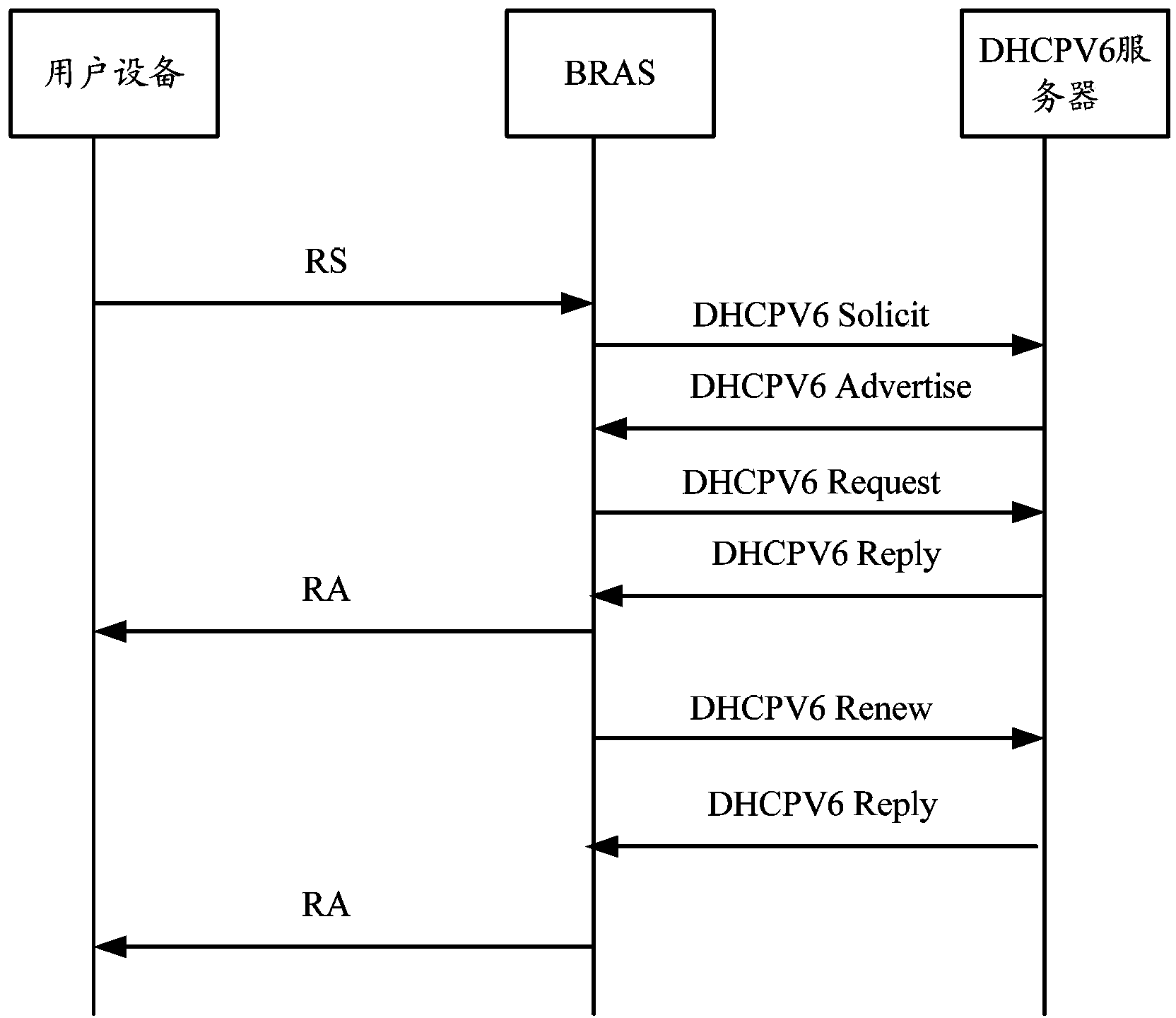
An embodiment of the invention discloses a method for obtaining an IPV6ND address and a broadband remote access server (BARS). The BARS receives a routing request (RS) message sent by a user device. A dynamic host configuration protocol version 6 (DHCPV6) server sends a DHCPV6Solicit message, wherein the DHCPV6Solicit message carries an unique device identifier (DUID) and identity relevance options IA_PD of the user device, so that the DHCPV6 server allocates a 64-bit Delegation prefixion for the user device according to the IA_PD. The 64-bit Delegation prefixion is sent to the user device through a random access (RA) message to enable the user device to use the 64-bit Delegation prefixion and a 64-bit IPV6 interface identity (ID) to form a 128-bit IPV6ND address, and when a network only supporting an IPV4 protocol can be updated and can support an IPV6 protocol or a Dual Stack, the dual stack can support the IPV4 and IPV6 protocols, and ND access and DHCPV6 access can be achieved only by updating the support of a DHCP Server and allocating an IPV6 prefixion.
Owner:XFUSION DIGITAL TECH CO LTD
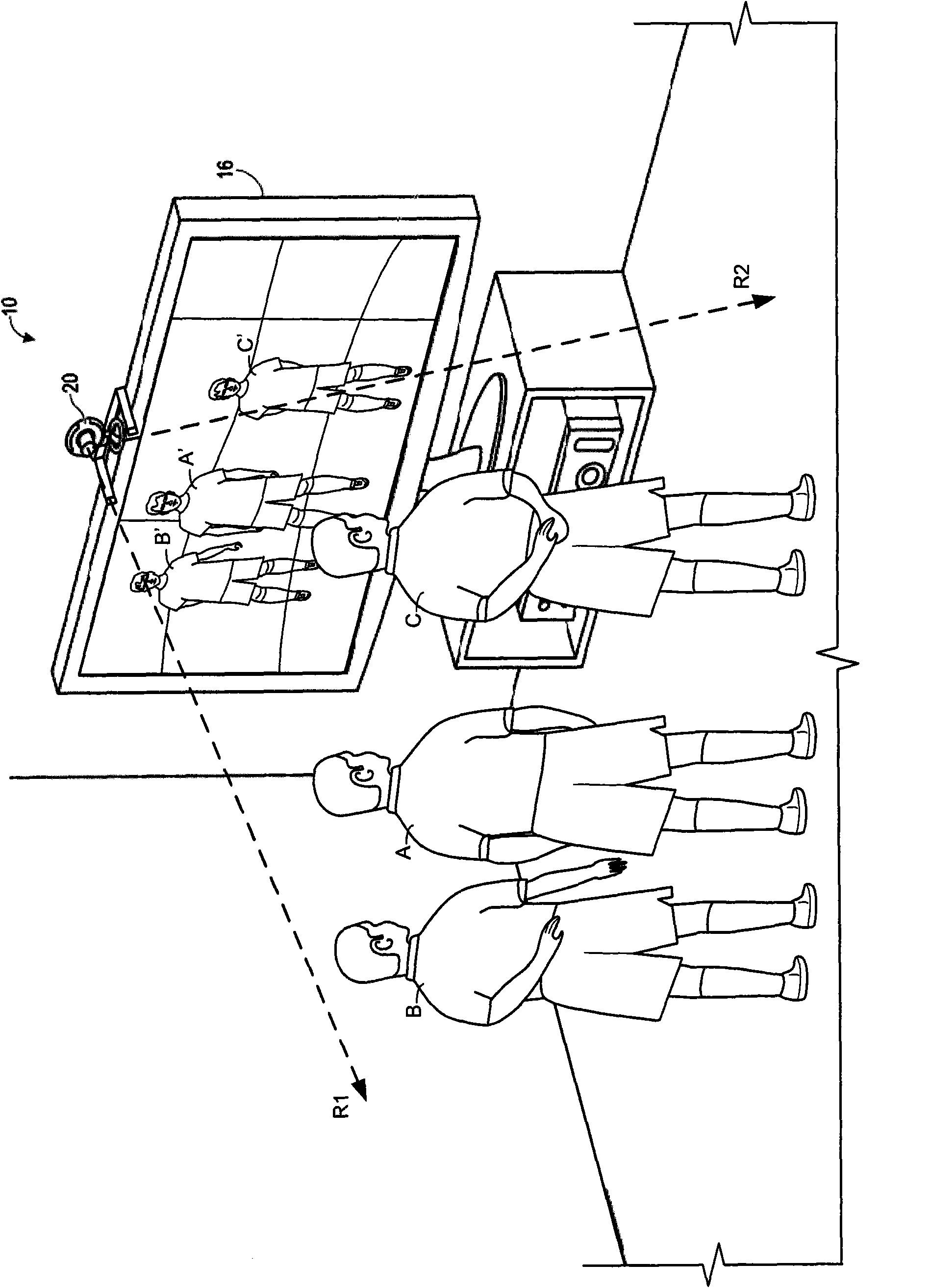
Voice-body identity correlation
ActiveCN102135882AReduced likelihoodDigital data information retrievalImage analysisHuman–computer interactionSpeech sound
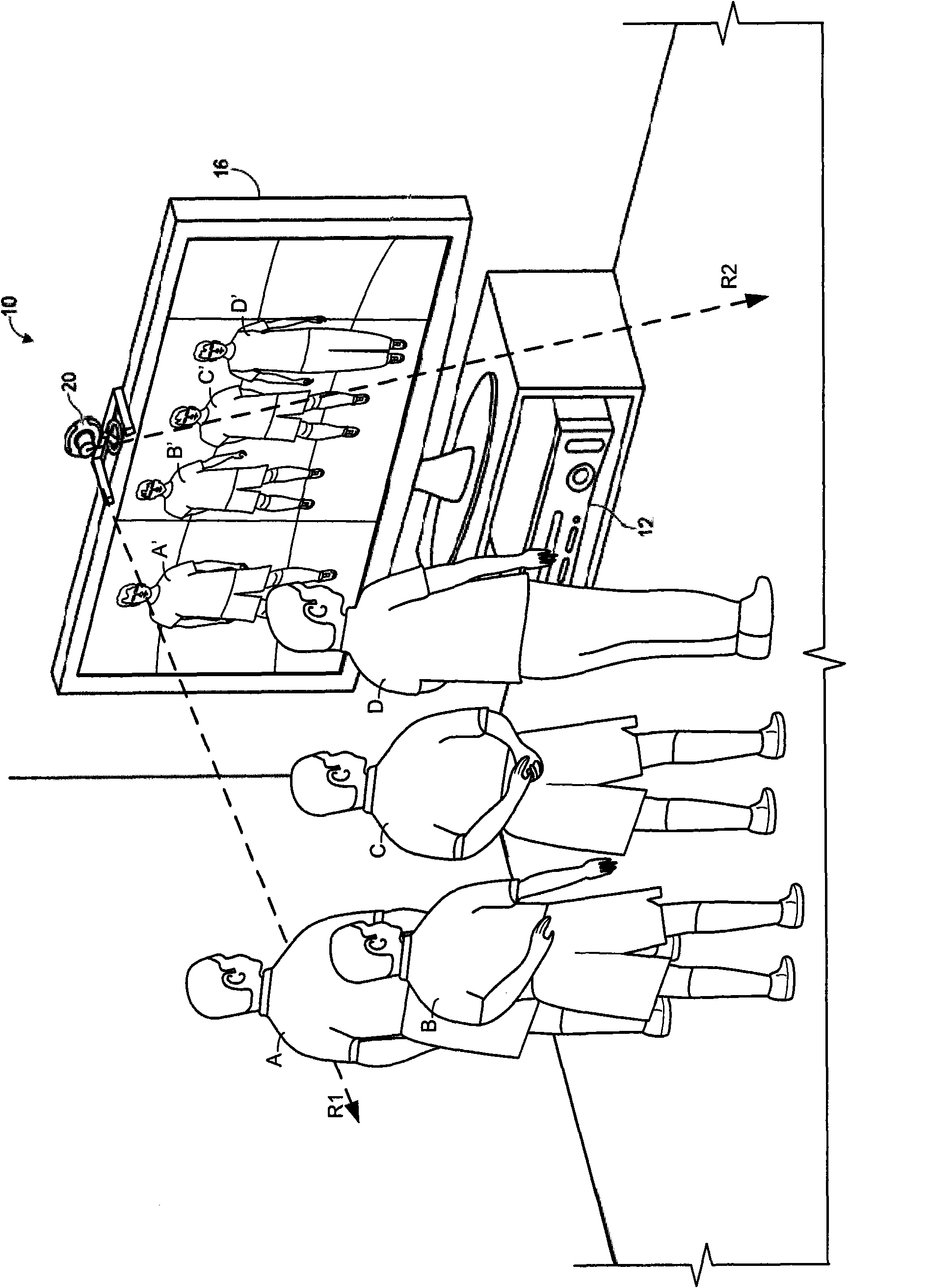
A system and method are disclosed for tracking image and audio data over time to automatically identify a person based on a correlation of their voice with their body in a multi-user game or multimedia setting.
Owner:MICROSOFT TECH LICENSING LLC
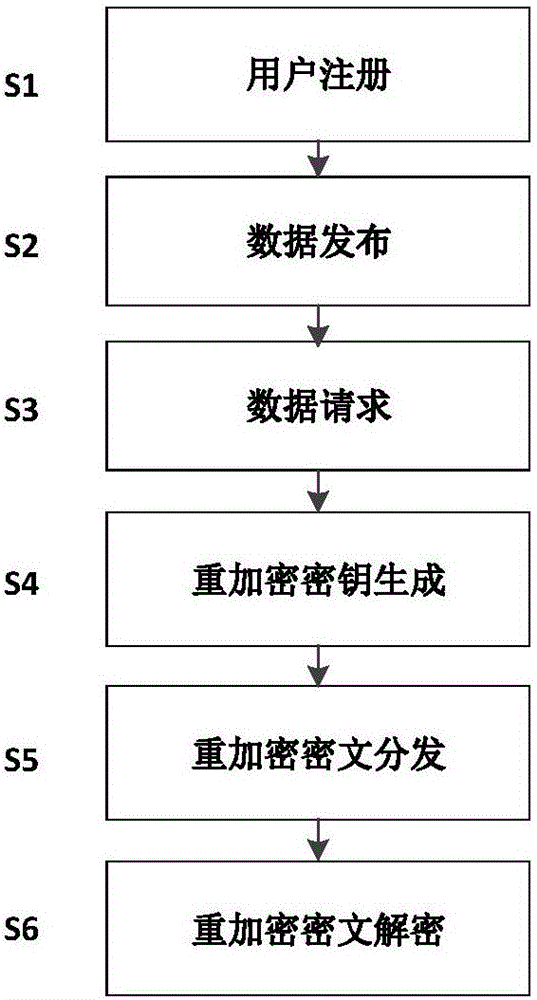
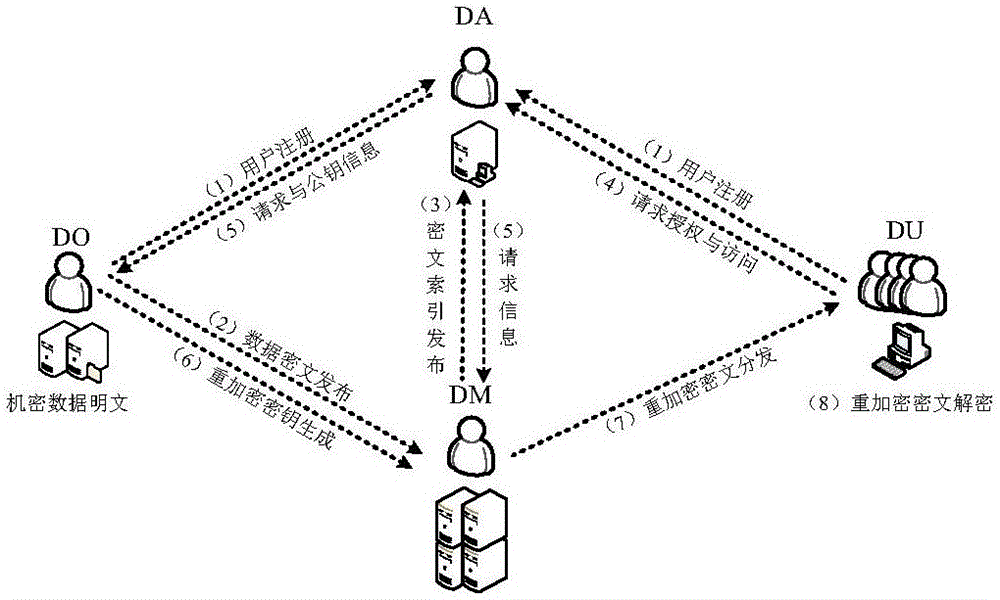
Storage method of confidential data
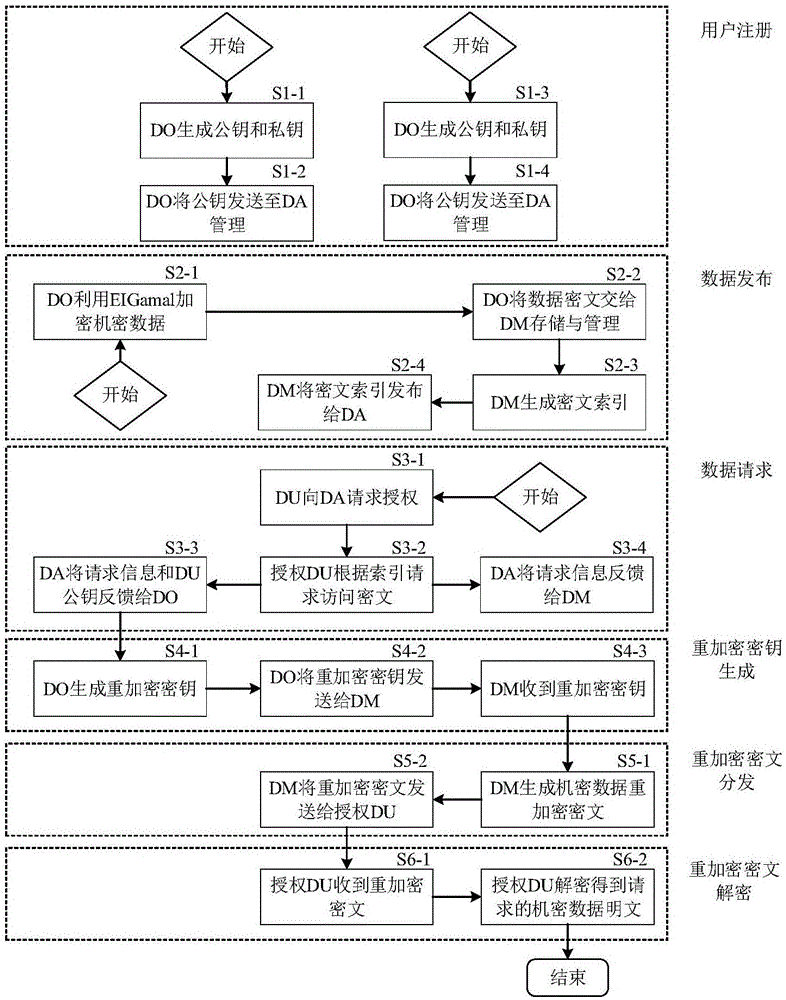
InactiveCN106789039ARestrictionsRealize depository separationKey distribution for secure communicationDigital data protectionCryptographic key generationCiphertext
The invention discloses a storage method of confidential data, wherein the storage method includes steps of 1), a data owner generates public and private key pairs by using a public key cryptographic algorithm; a data user applies public key cryptographic algorithm to generate the public and private key pairs associated with its identity; 2), a data storage administrator generates a ciphertext data index and publishes to a data authority administrator; 3), the data authority administrator feeds back a confidential data visit request to the data storage administrator; 4) an re-encryption key is generated; after receiving the data visit request, the data owner generates re-encryption key according to the public key information of the user, and sends to the data storage administrator; 5), re-encrypted ciphertext is distributed; the data storage administrator applies the re-encryption key to encrypt the confidential data ciphertext requested to visit by the secret key encryption data; the re-encrypted ciphertext is is acquired, and sent to the authorized data user. The method can easier realize the safe and high-efficient distribution of multiple users, and has high practicability.
Owner:WUHAN UNIV
System and method for user identity portability in communication systems
InactiveUS7525930B2Special service provision for substationMultiplex system selection arrangementsCommunications systemInternet privacy
Exemplary embodiments of the present invention are directed to a system and method for user identity portability in communication systems. The present invention can provide user identity portability across communication networks that do not necessarily impose a phone number as the identity, addressing, or routing identifier. According to exemplary embodiments, a user identified by any suitable user identifier can switch network operators (e.g., from operator A to operator B) and retain their user identifier. For example, an identity server can support reverse lookup ENUM usage for URI and other identity correlation. Thus, all communication contacts that the user had while with operator A can seamlessly continue communications with the user even after the user switches to operator B.
Owner:NEUSTAR
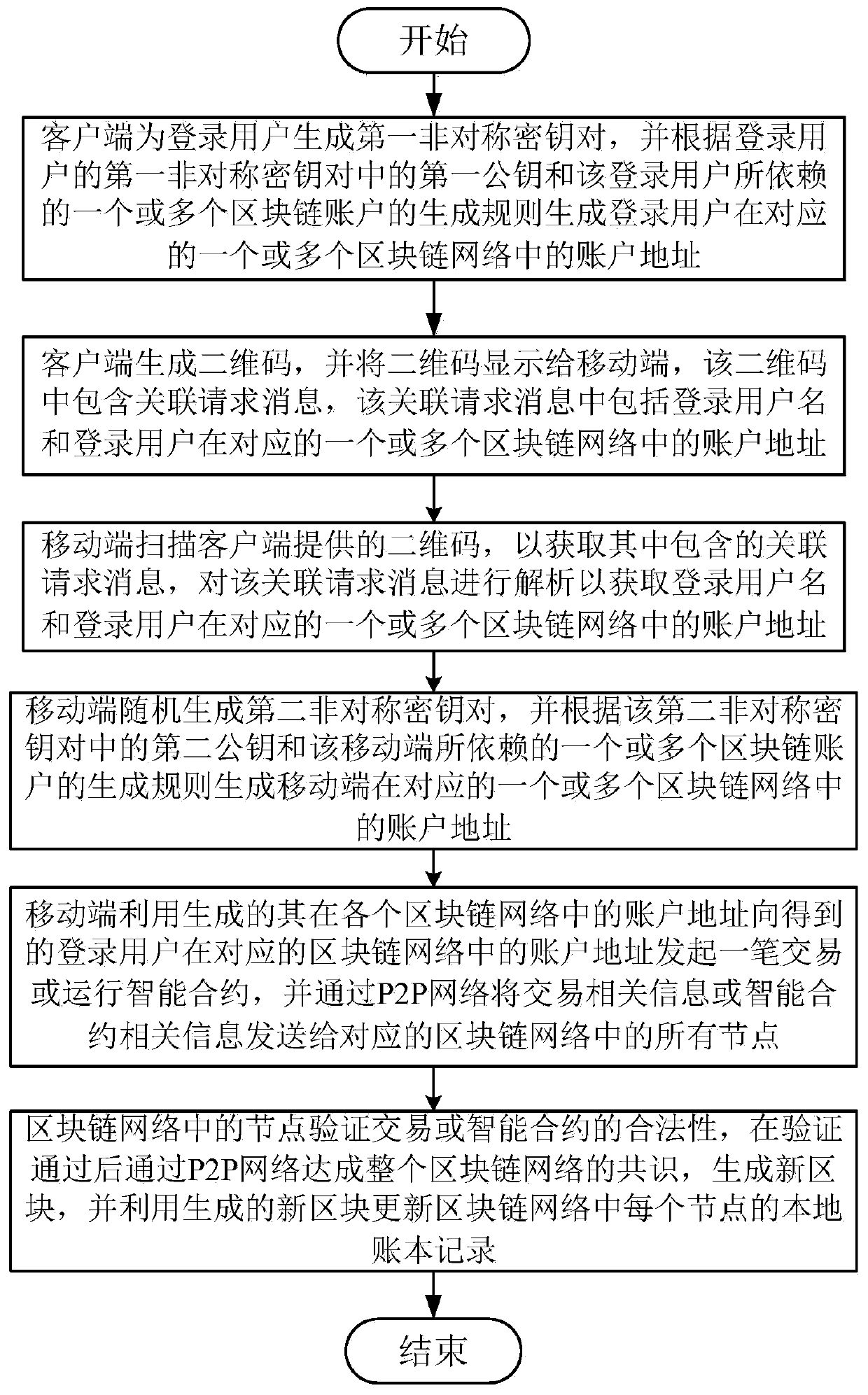
Identity association method based on block chain
ActiveCN111027036ATime-consuming and labor-intensive solutionSolve efficiency problemsDigital data authenticationRecord carriers used with machinesMobile endEngineering
The invention discloses an identity association method based on a block chain. The method comprises the following steps: a client generates a first asymmetric key pair for a login user, generates an account address of the login user in the corresponding one or more blockchain networks according to a first public key in a first asymmetric key pair of the login user and a generation rule of one or more blockchain accounts on which the login user depends; the client generates a two-dimensional code, the mobile terminal scans the two-dimensional code provided by the client to obtain an associationrequest message contained in the association request message, and analyzes the association request message to obtain the login user name and the account address of the login user in the correspondingone or more blockchain networks; the the mobile terminal randomly generates a second asymmetric key pair by, and generates the account address of the mobile terminal in the corresponding one or moreblockchain networks. According to the invention, the technical problems of time and labor consumption, low efficiency and poor security caused by the fact that association needs to be manually realized at the server in the existing method can be solved.
Owner:WUHAN ARGUSEC TECH
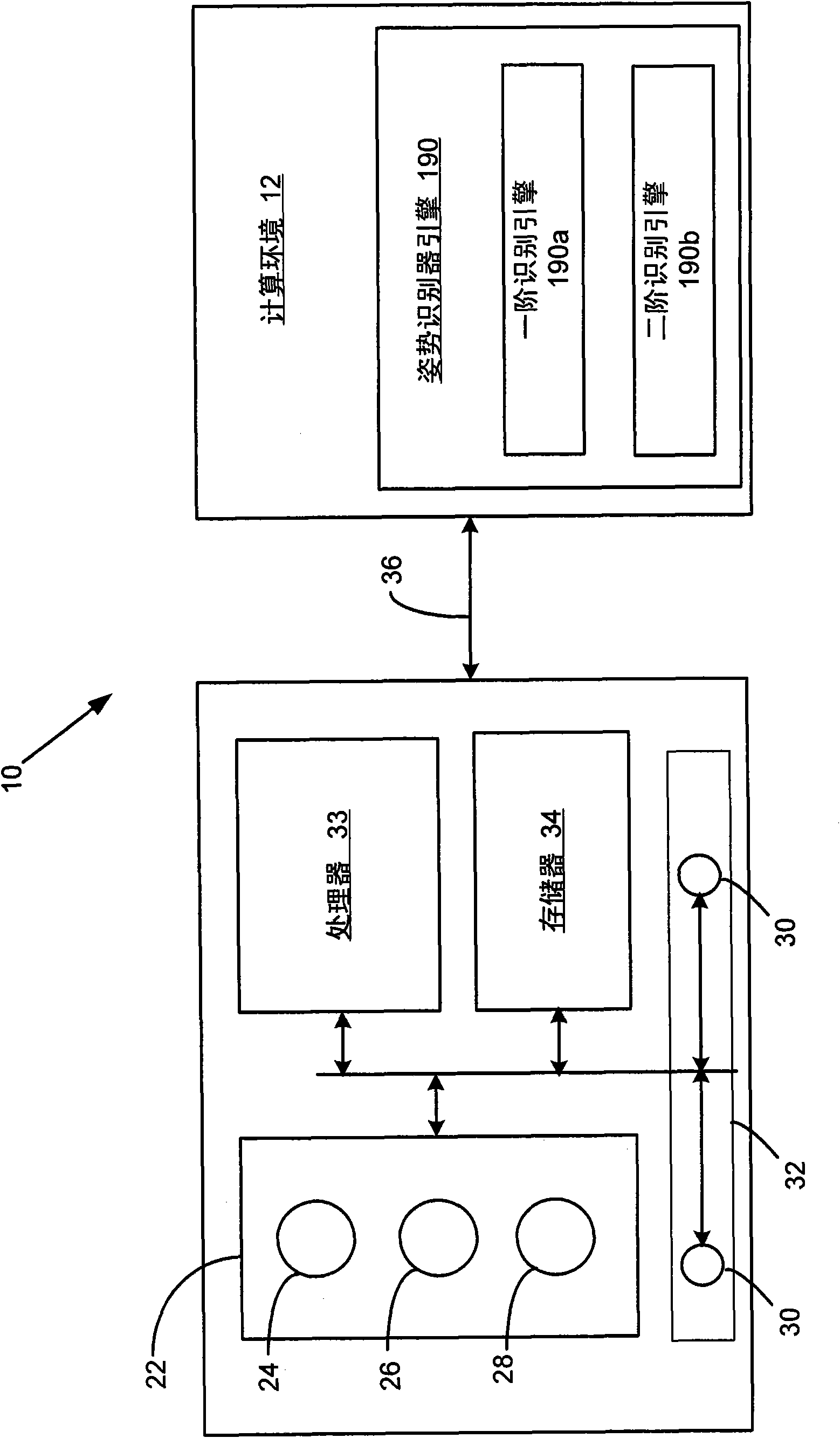
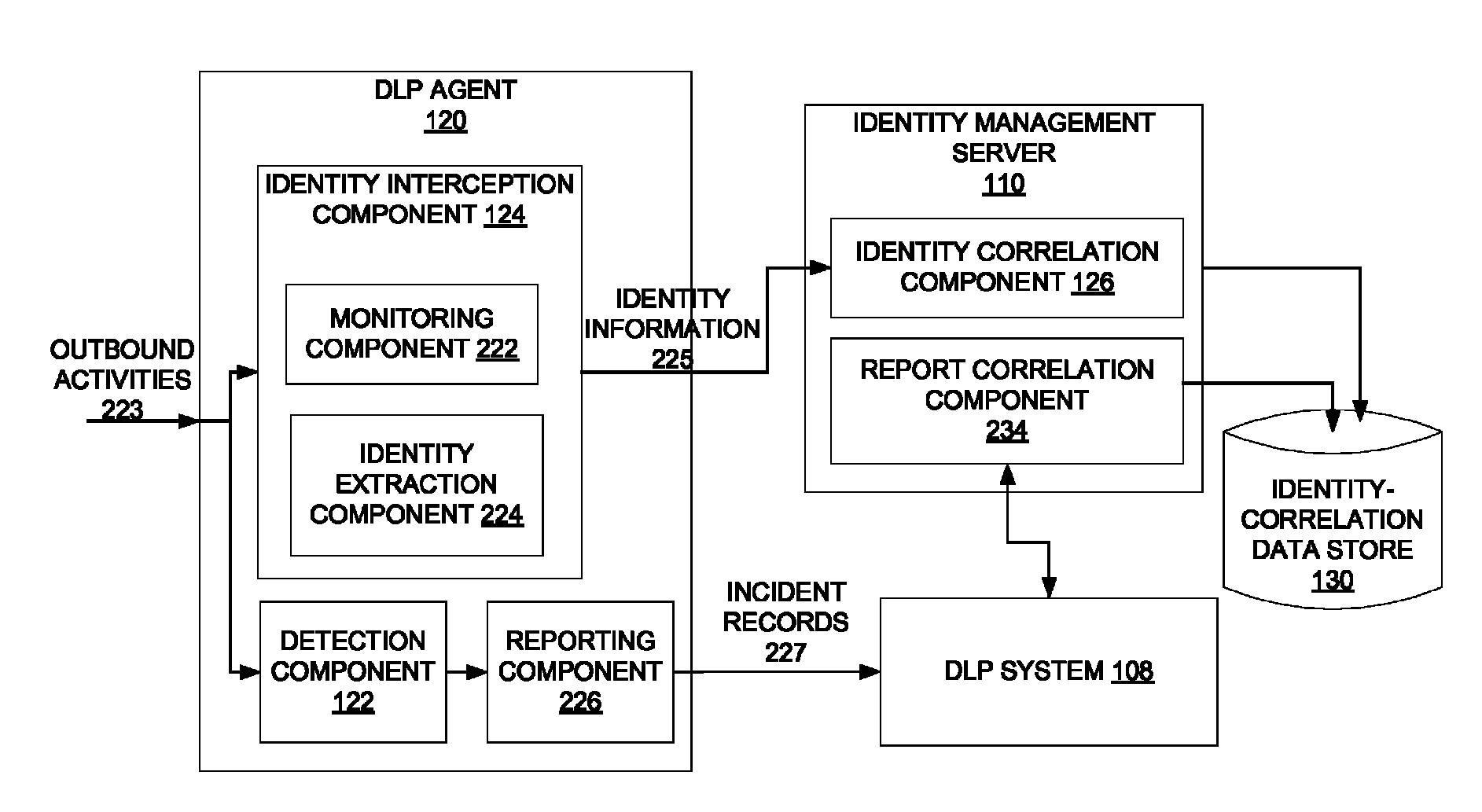
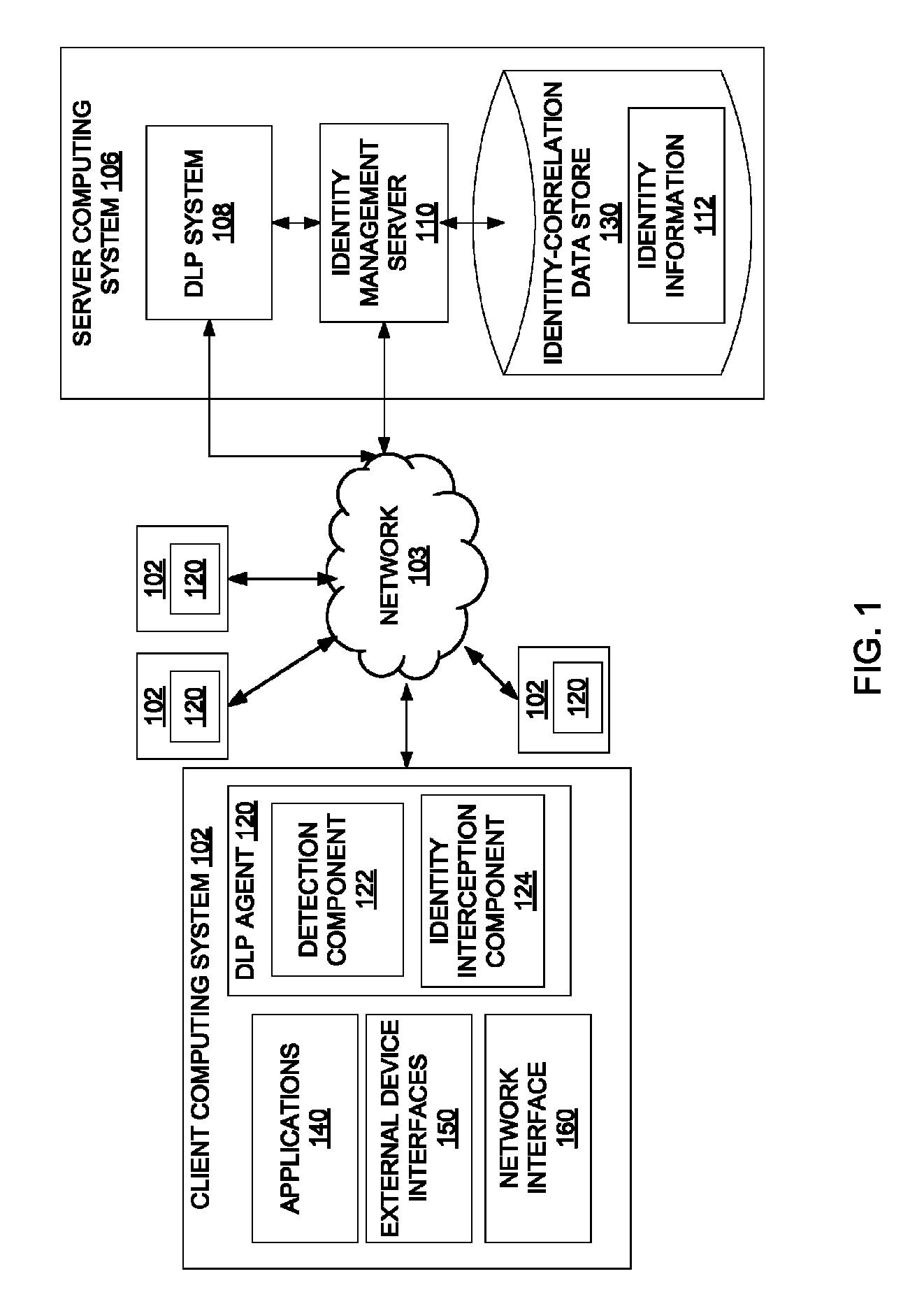
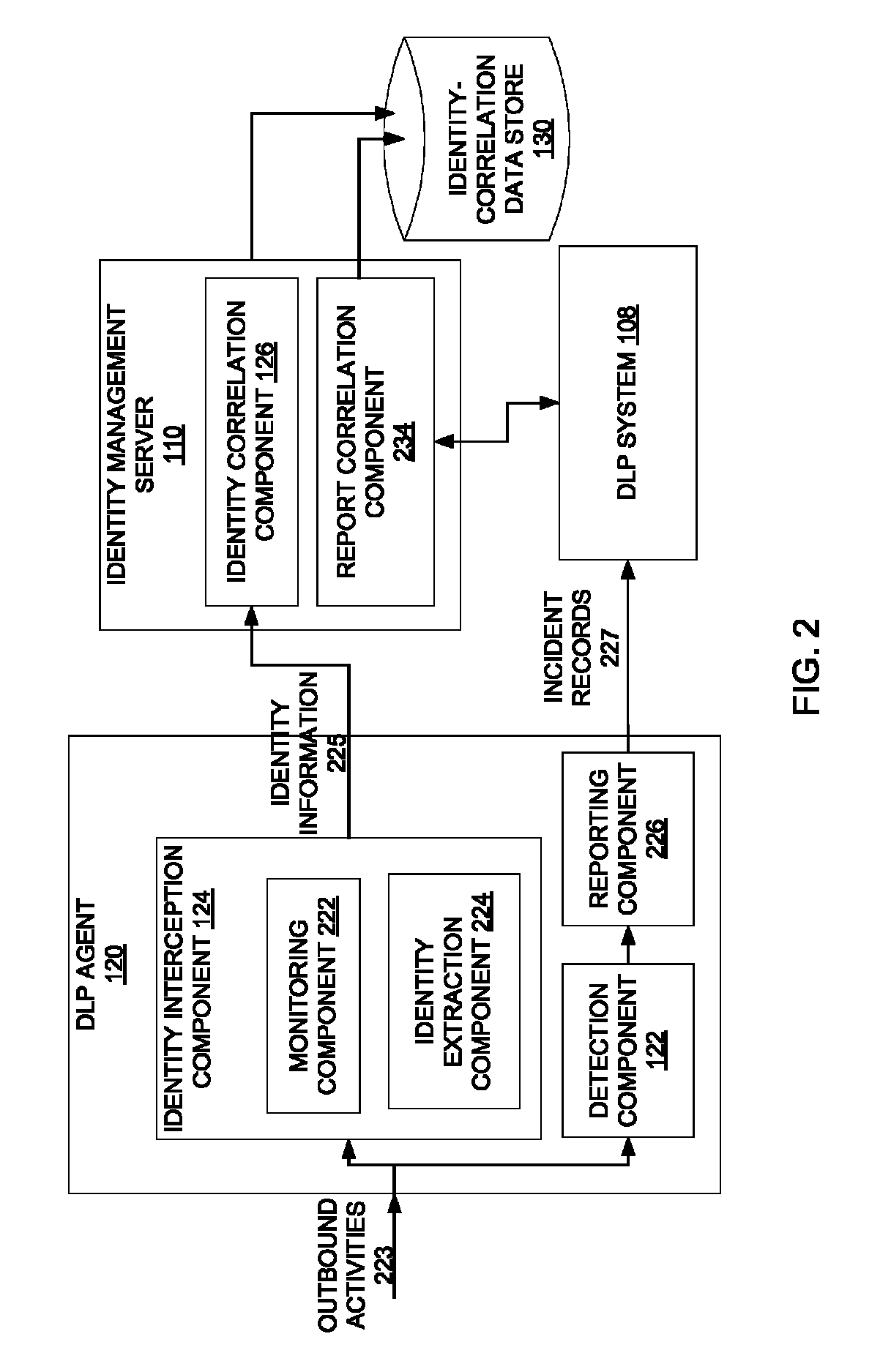
Dynamically populating an identity-correlation data store
ActiveUS8510446B1Digital computer detailsPlatform integrity maintainanceIdentity correlationInternal identifier
A method and apparatus for dynamically populating an identity-correlation data store and using the identity-correlation data store to correlate external identifiers and unique internal identifiers are described.
Owner:CA TECH INC
Unsecured asset detection via correlated authentication anomalies
ActiveUS8832857B2Digital data processing detailsAnalogue secracy/subscription systemsWeb siteIdentity provider
Owner:INT BUSINESS MASCH CORP
Method and apparatus for logoff of wireless IP access network association address
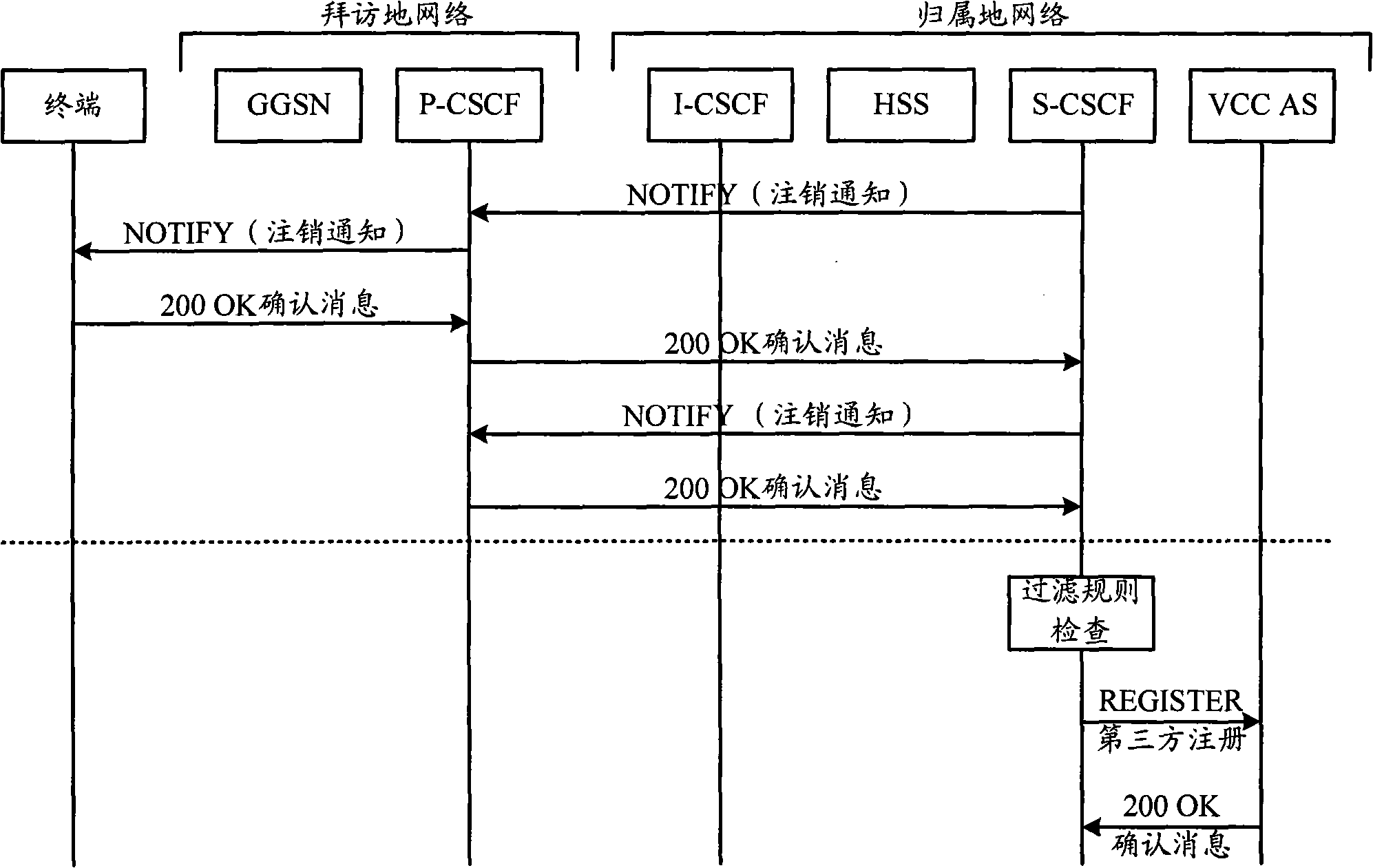
ActiveCN101299697AExtend call setup timeData switching by path configurationWireless network protocolsAccess networkIdentity correlation
The invention relates to the wireless communication field, specifically discloses a method and apparatus for logoff of wireless IP access network association address, which, after the terminal leaves the IP access network in an abnormal mode, can avoid the problem that when the terminal receives the call of the user common identification corresponding to the terminal, the call can also be distributed from the IP access network according to the IP access network association address associated to the user identification. In the invention, when the terminal leaves a first wireless IP access network, if the association address of the terminal at the first wireless IP access network is not logoff to the IMS network, the other currently available access networks are used to inform the IMS network to logoff the association address of the terminal at the first wireless IP access network. When the available wireless IP access network exists, the terminal initiates a re-registration process to the wireless IP access network, and transmits the information for logoff of the first wireless IP access network to the S-CSCF; and the S-CSCF logs off the association address of the terminal at the first wireless IP access network.
Owner:NOKIA TECHNOLOGLES OY
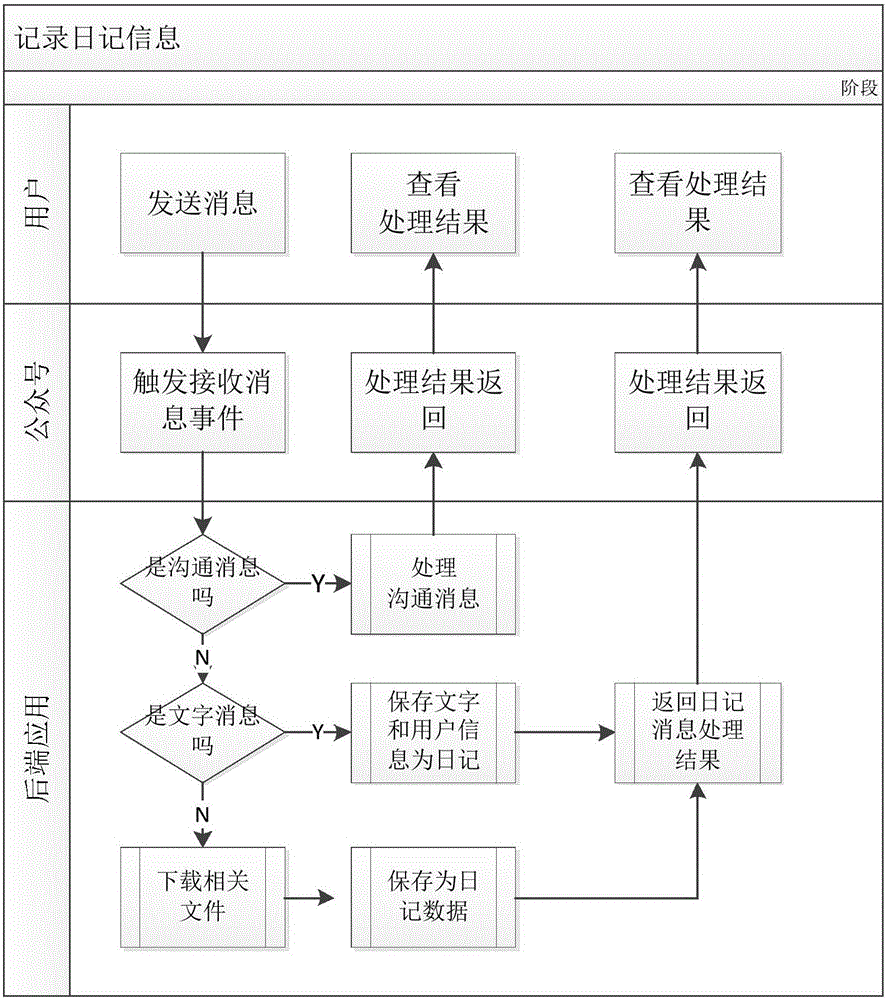
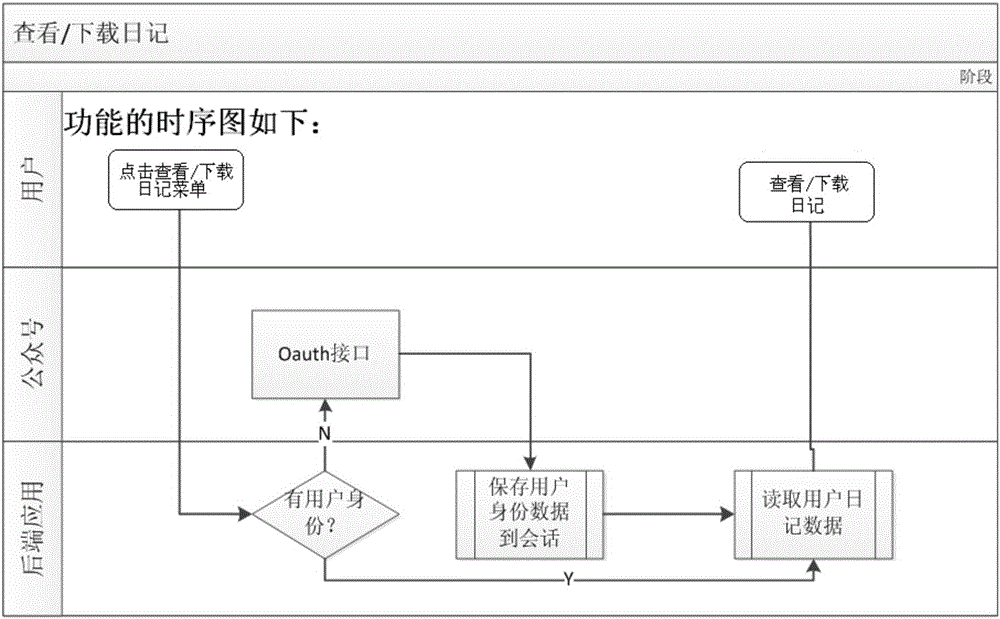
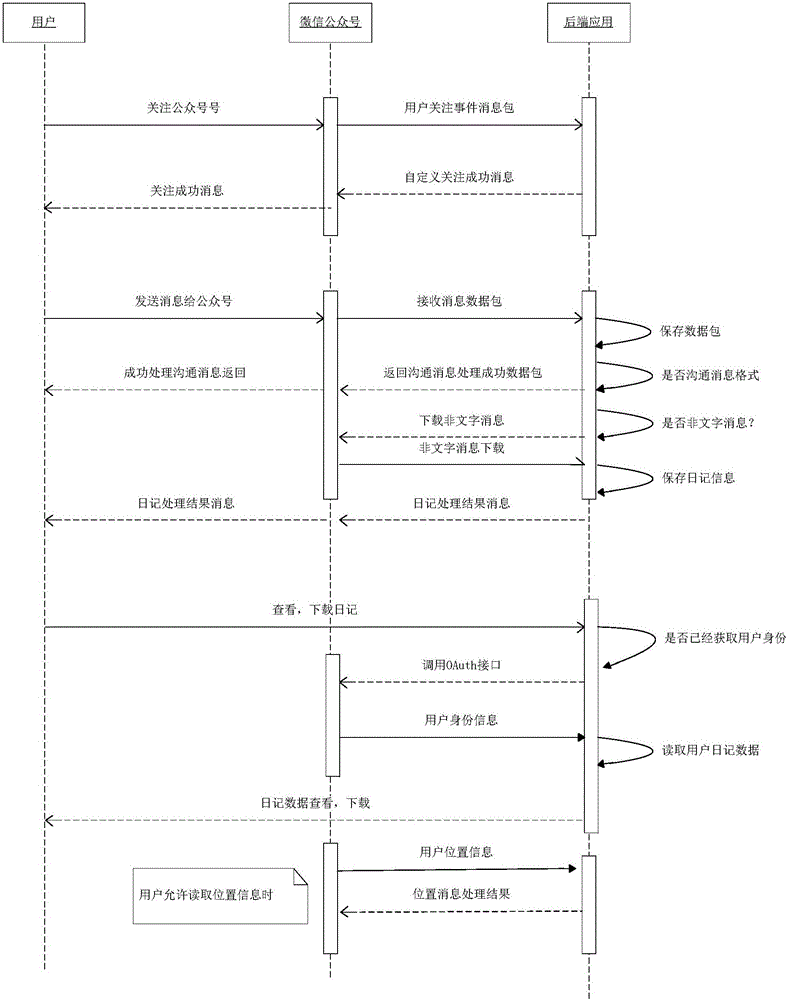
Method for establishing and managing electronic diary by using WeChat platform
InactiveCN105893580AReduce trafficLoss will not causeData switching networksSpecial data processing applicationsTraffic capacityPublic account
The invention discloses a method for establishing and managing an electronic diary by using a WeChat platform. The method comprises the following steps of paying attention to a public account having an electronic diary function by utilizing WeChat; sending diary information to the public account; saving the diary information to a cloud storage server and enabling the diary information to be associated with the identification of a user; storing the diary information as a diary of the user; obtaining position data of the user through an API (Application Program Interface) at the same time if the public account is authorized to read position information by the user, and storing the position data together with the diary information; enabling the user to check / download the diary at any time through a menu of the public account, and also enabling the diary to be directly published through a public account operator. The method for establishing and managing the electronic diary by using the WeChat platform, disclosed by the invention, is based on the WeChat platform, installation of software is not needed, the flow is saved, the use is easy, the privacy safety is ensured, the data are safer as cloud storage is adopted, and the user experience is good; in addition, the method is also applicable to QQ and other social platforms having public accounts and APIs, and the method comprises the steps of paying attention to QQ having an electronic diary function or the public accounts of other social software and then carrying out the same operation.
Owner:北京汇康益生科技有限公司 +1
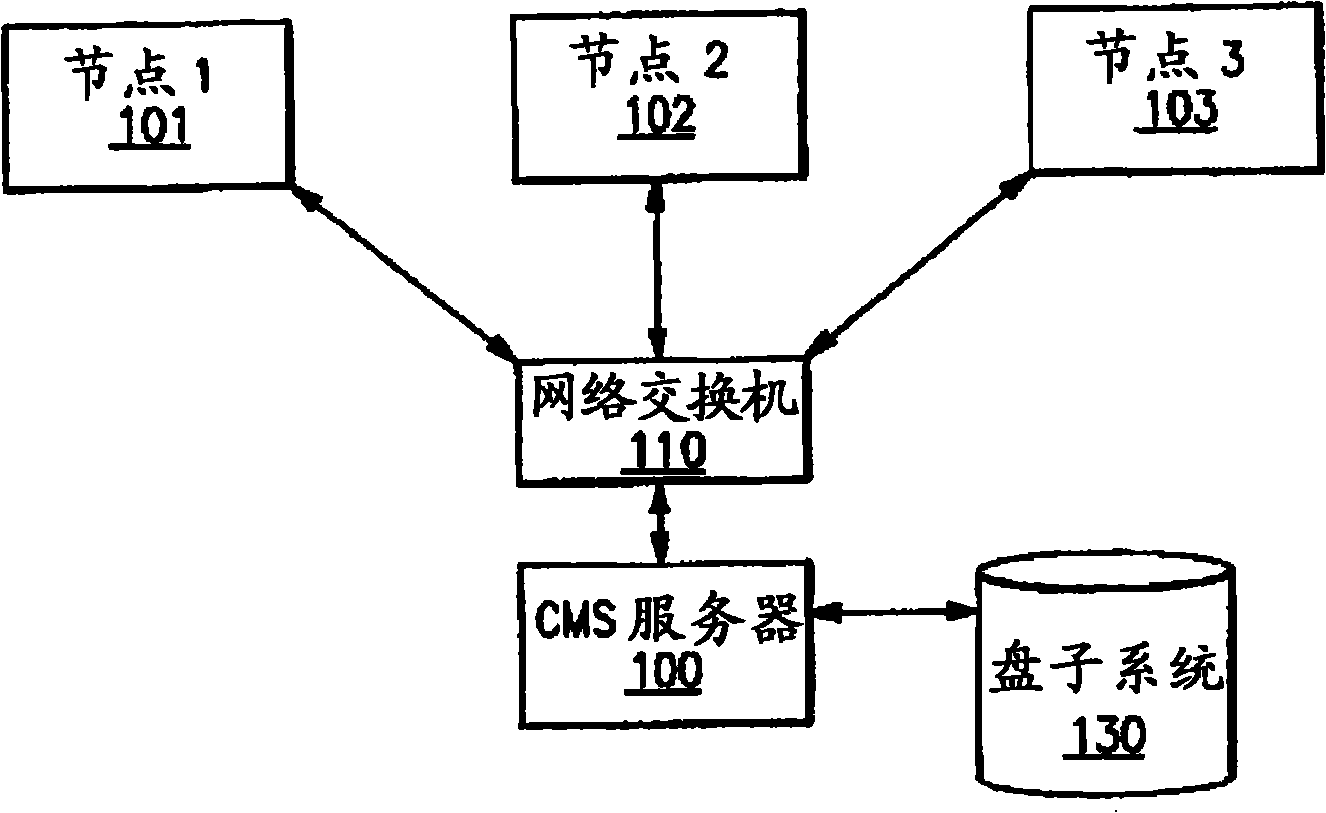
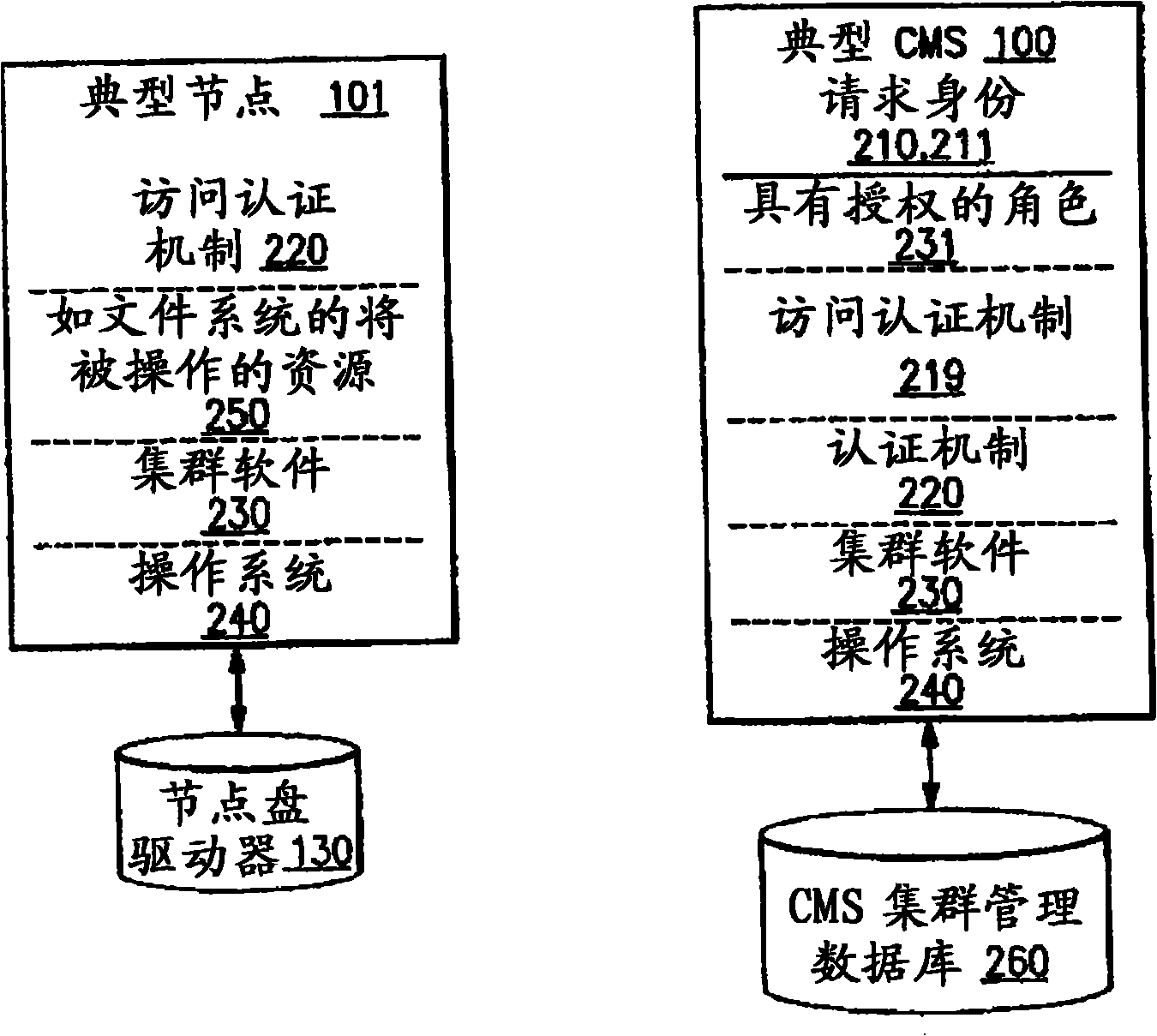
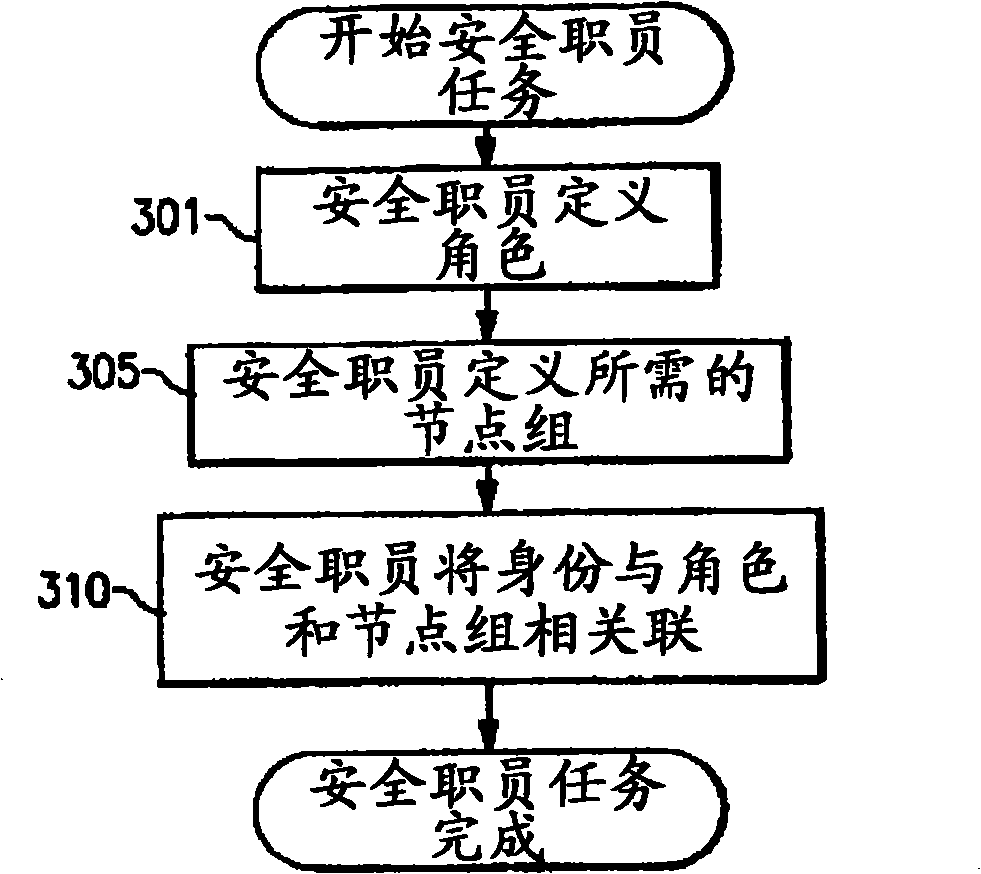
Utilizing component targets in defining roles in a distributed and integrated system or systems
InactiveCN101341467AMultiprogramming arrangementsDigital data protectionCentralized managementAuthorization
Disclosed are methods of and systems for creating roles on a centralized management server that include one to many authorizations for a given identity as well as the component targets they will be authorized for. The authorizations are defined based on the intersection of the task and the component for which it will act on. This combined authorization is then associated with specific identities. When a task is to be initiated, the central management server determines if the identity has been authorized for that task and for which components it can execute that task against. The infrastructure then generates the appropriate sub commands and only executes those sub commands against the authorized components contained in the list of requested components from the initiation request.
Owner:INT BUSINESS MASCH CORP
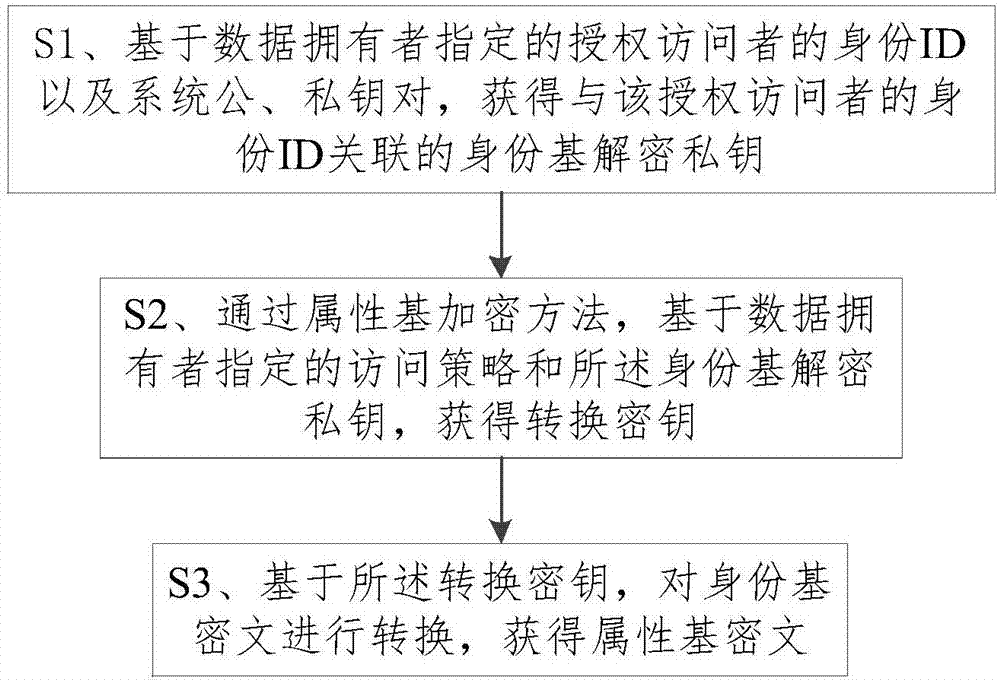
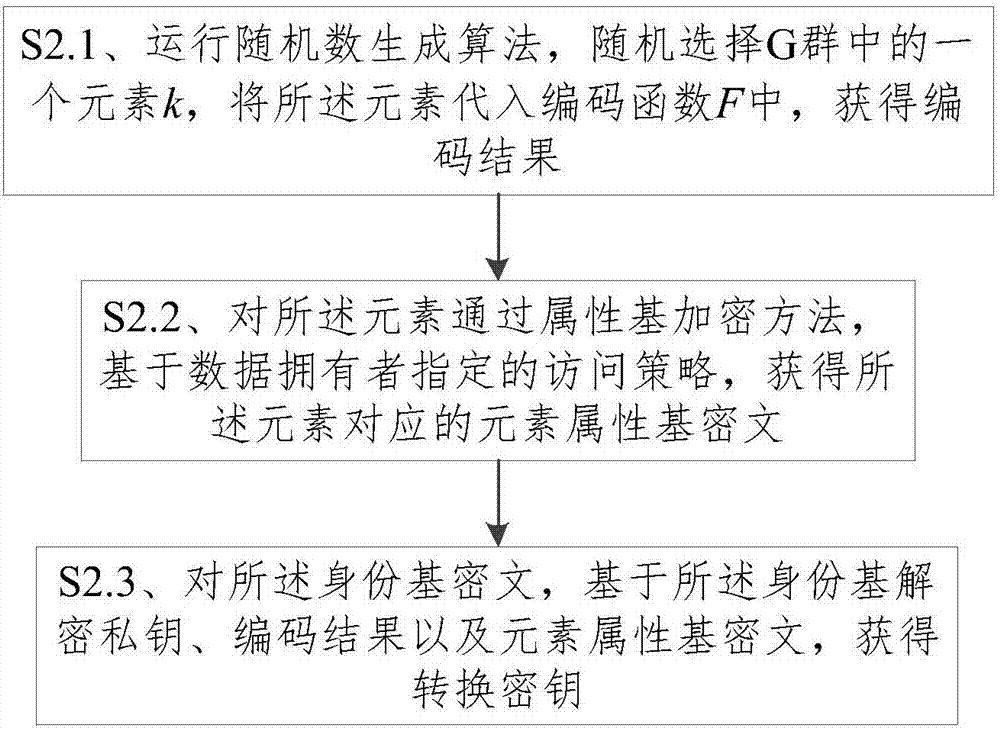
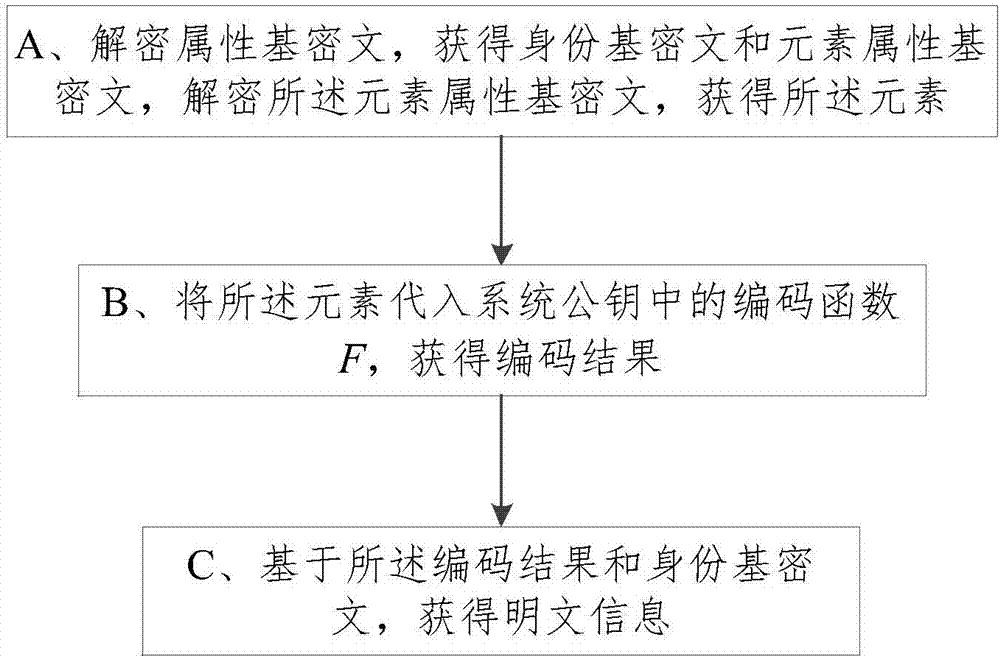
Ciphertext conversion method in heterogeneous storage system, decryption method and decryption system
ActiveCN107086912ASafe and effective wayKey distribution for secure communicationPlaintextCiphertext
The invention provides a ciphertext conversion method in a heterogeneous storage system, a decryption method and a decryption system, wherein the ciphertext conversion method comprises the steps of: on the basis of the identity ID of an authorized visitor appointed by a data owner, and the public key pair and the private key pair of the system, obtaining an identity-based decryption private key associated with the identity ID of the authorized visitor; on the basis of the access strategy appointed by the data owner and the identity-based decryption private key, obtaining a conversion key through an attribute-based encryption method; and, on the basis of the conversion key, converting an identity-based ciphertext to obtain an attribute-based ciphertext. By means of the ciphertext conversion method in the heterogeneous storage system, the decryption method and the decryption system provided by the invention, on the premise that a plaintext is not leaked, the identity-based ciphertext is converted into the attribute-based ciphertext; the fact that two encryption systems independently operate and are not influenced mutually can be ensured; and thus, a safe and effective way is provided for sharing secret data by users of two sets of storage systems having different encryption algorithms.
Owner:STATE GRID CORP OF CHINA +2
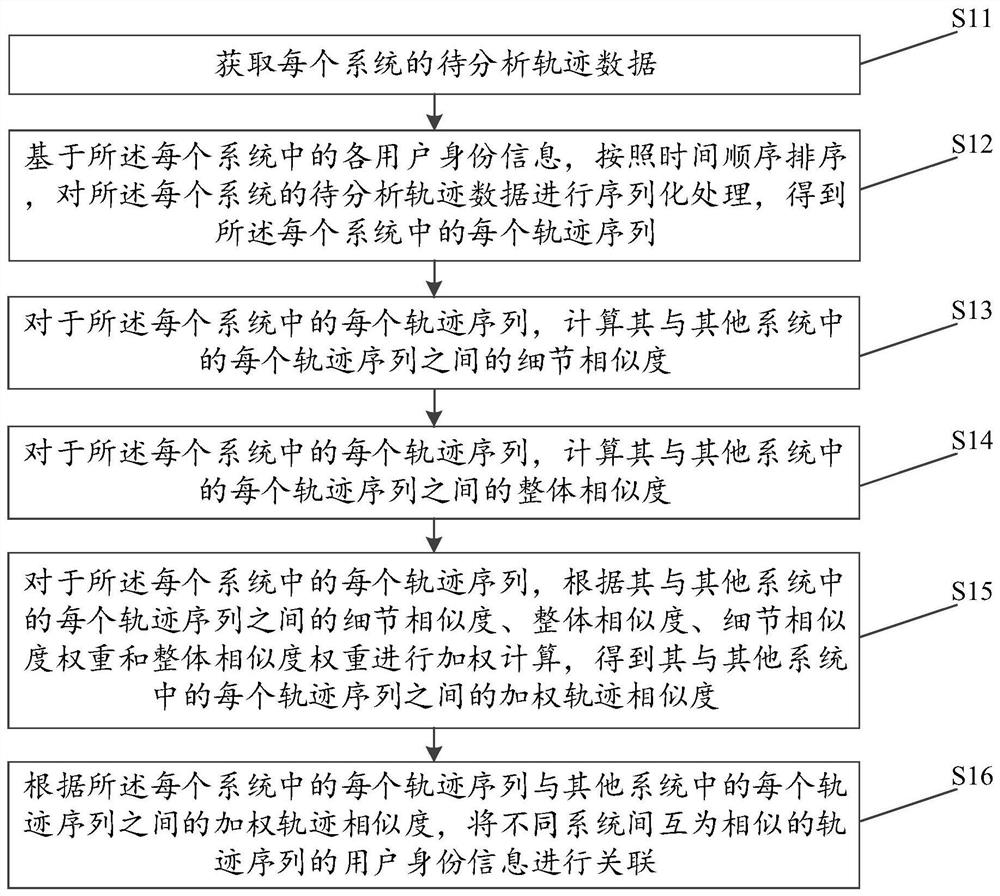
Identity association method and device based on track similarity, equipment and storage medium
ActiveCN111651527ADistinguish detail conflictsEnsure matching correctnessRelational databasesSpecial data processing applicationsEngineeringSerialization
The invention discloses an identity association method and device based on track similarity, equipment and a storage medium, and the method comprises the steps: carrying out the serialization of to-be-analyzed track data of each system, and obtaining each track sequence in each system; calculating detail similarity and overall similarity between each track sequence in each system and each track sequence in other systems; for each track sequence in each system, performing weighted calculation according to the detail similarity and the overall similarity between the track sequence in each systemand each track sequence in other systems to obtain weighted track similarity between the track sequence in each system and each track sequence in other systems; and according to the weighted trajectory similarity between each trajectory sequence in each system and each trajectory sequence in other systems, associating the user identity information of the mutually similar trajectory sequences between different systems. By adopting the method and the device, the identity information corresponding to the mutually similar tracks among different systems can be accurately associated.
Owner:GOSUNCN TECH GRP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com