Ciphertext conversion method in heterogeneous storage system, decryption method and decryption system
A technology of ciphertext conversion and heterogeneous storage, applied in transmission systems, digital transmission systems, and key distribution, which can solve the problems of not knowing other users, affecting work progress, and unable to designate authorized visitors.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
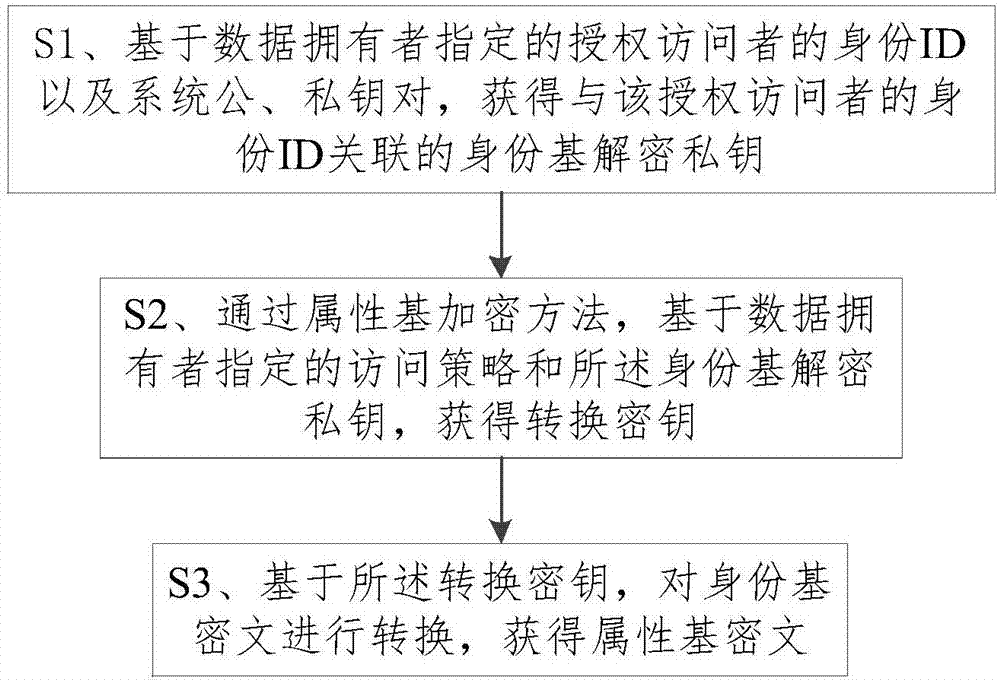
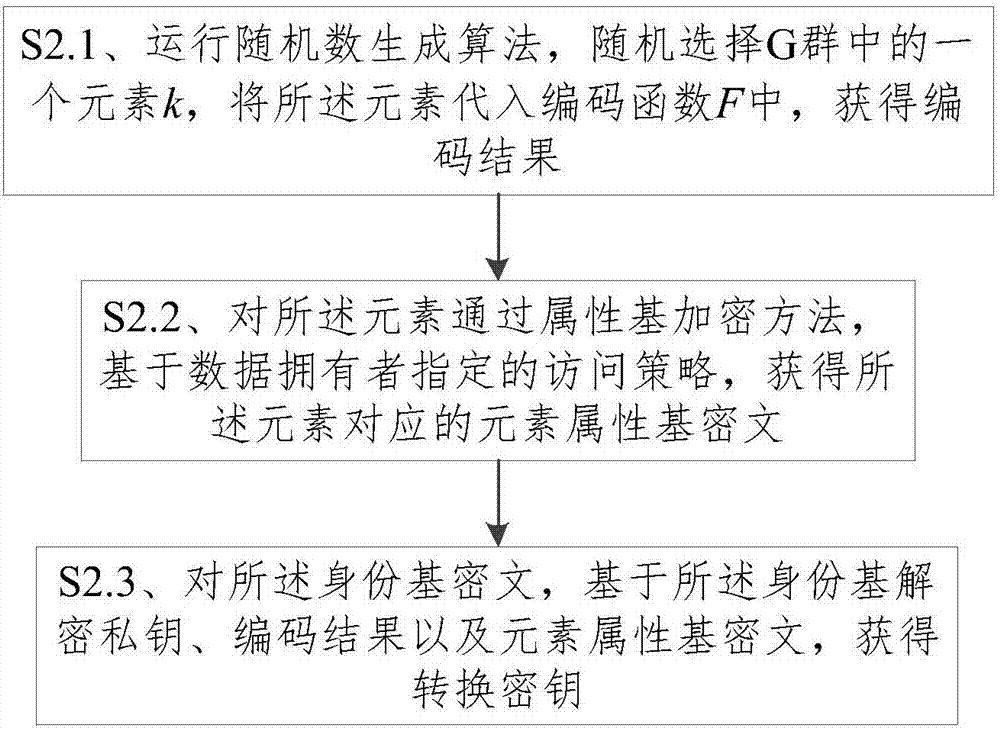
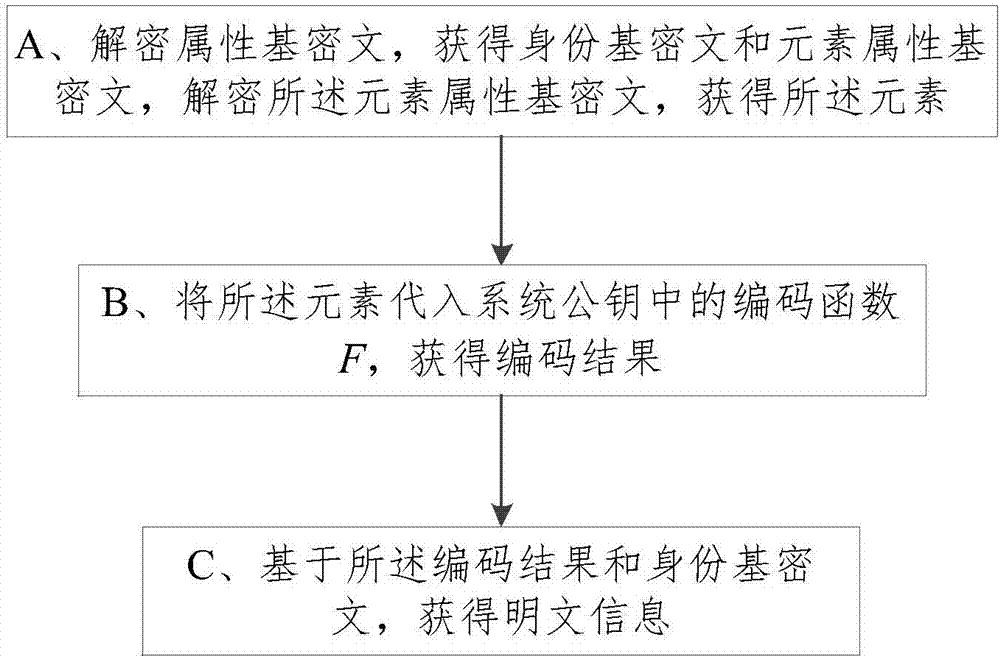
[0029] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
[0030] The following introduces the basic knowledge of mathematics and cryptography involved in the secure ciphertext conversion method:
[0031] 1. Bilinear pairing
[0032] Define a function mapping e(.,.), the group G that maps the elements in the group G T in, namely:
[0033] e: G×G→G T ;
[0034] For a large prime number p, the bilinear pairing satisfies the following properties:
[0035] (1), bilinear characteristics: for g, h∈G; a, b∈Z p ,Z p Represents the set {0, 1, 2, ..., p-1}, there is: e(g a , h b ) = e(g, h) ab ;
[0036] (2), non-degenerate: there is at least one element g in the G group, so that the calculated e(g, g) is G T a generator of a grou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com