Patents
Literature
336 results about "Conditional access systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Selective encryption for video on demand
InactiveUS7039938B2Analogue secracy/subscription systemsTwo-way working systemsConditional access systemsDigital content
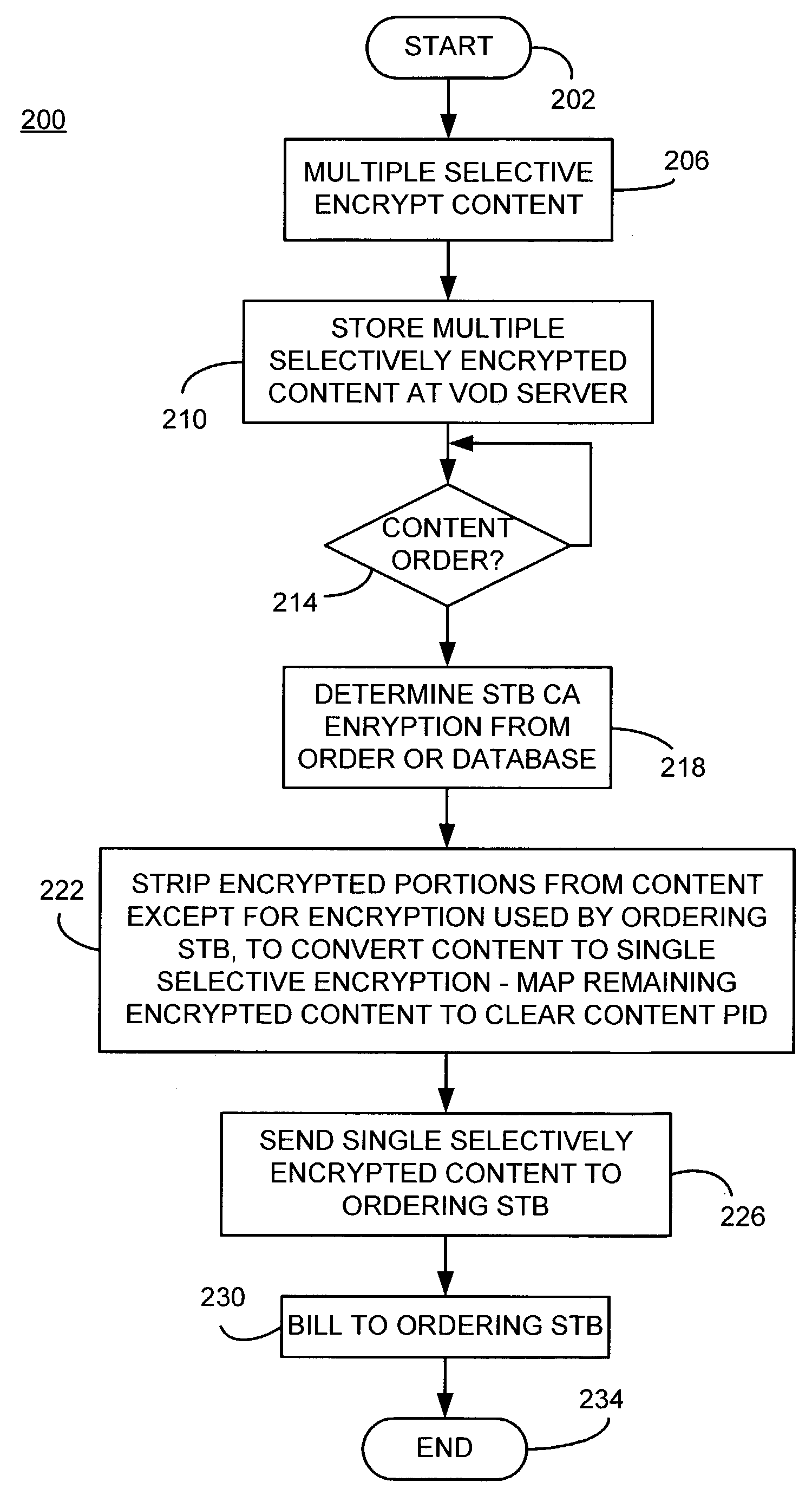
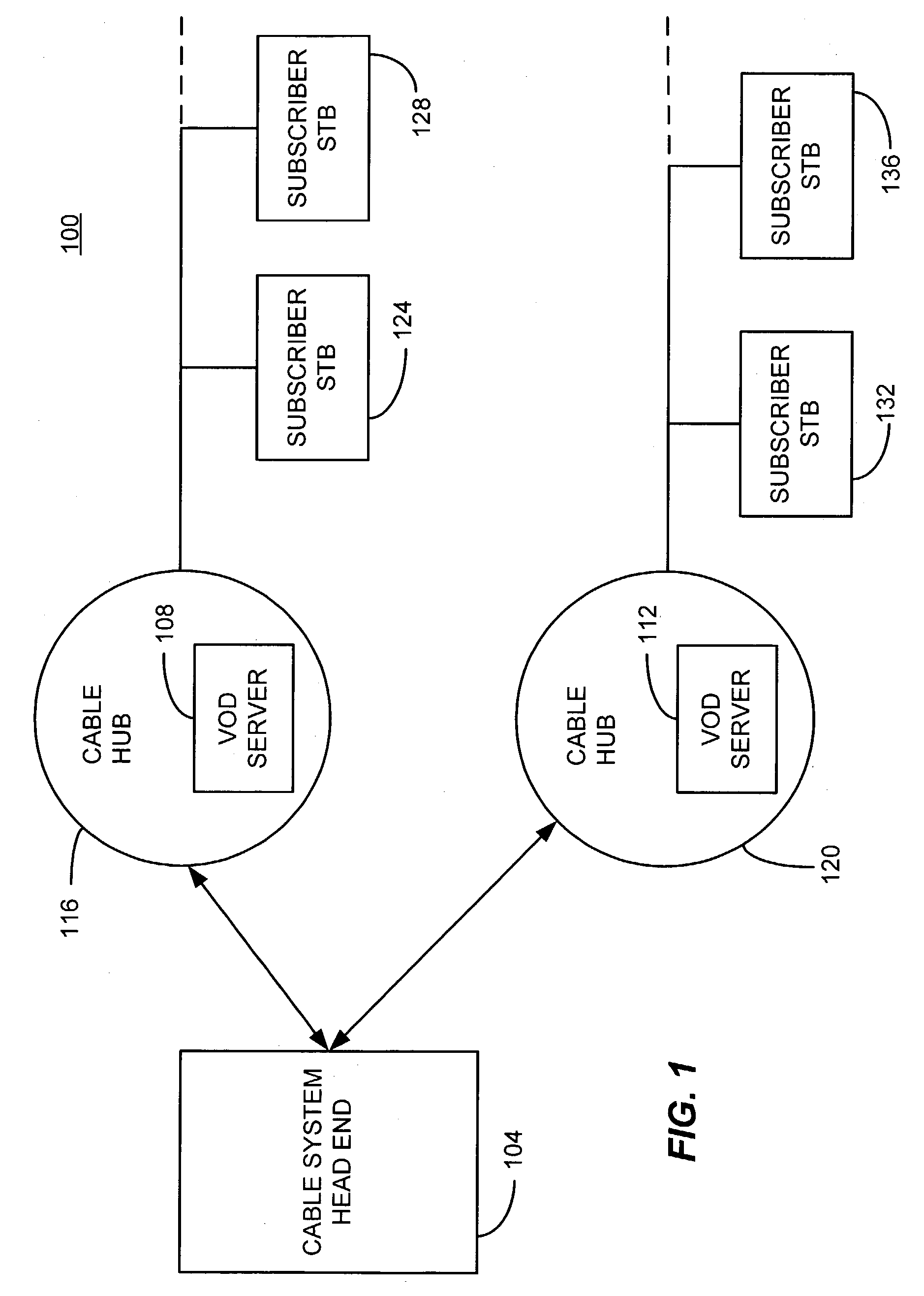
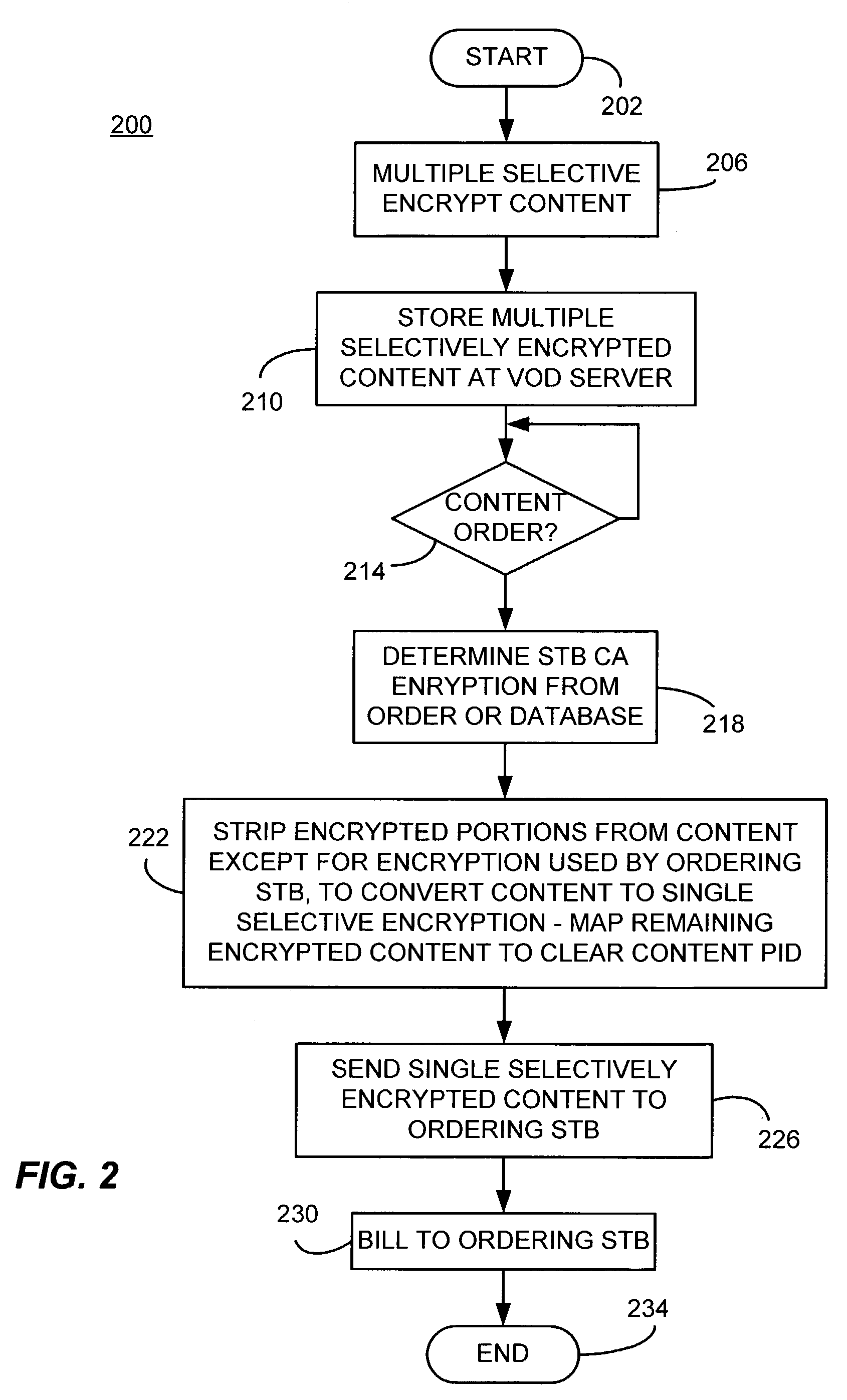
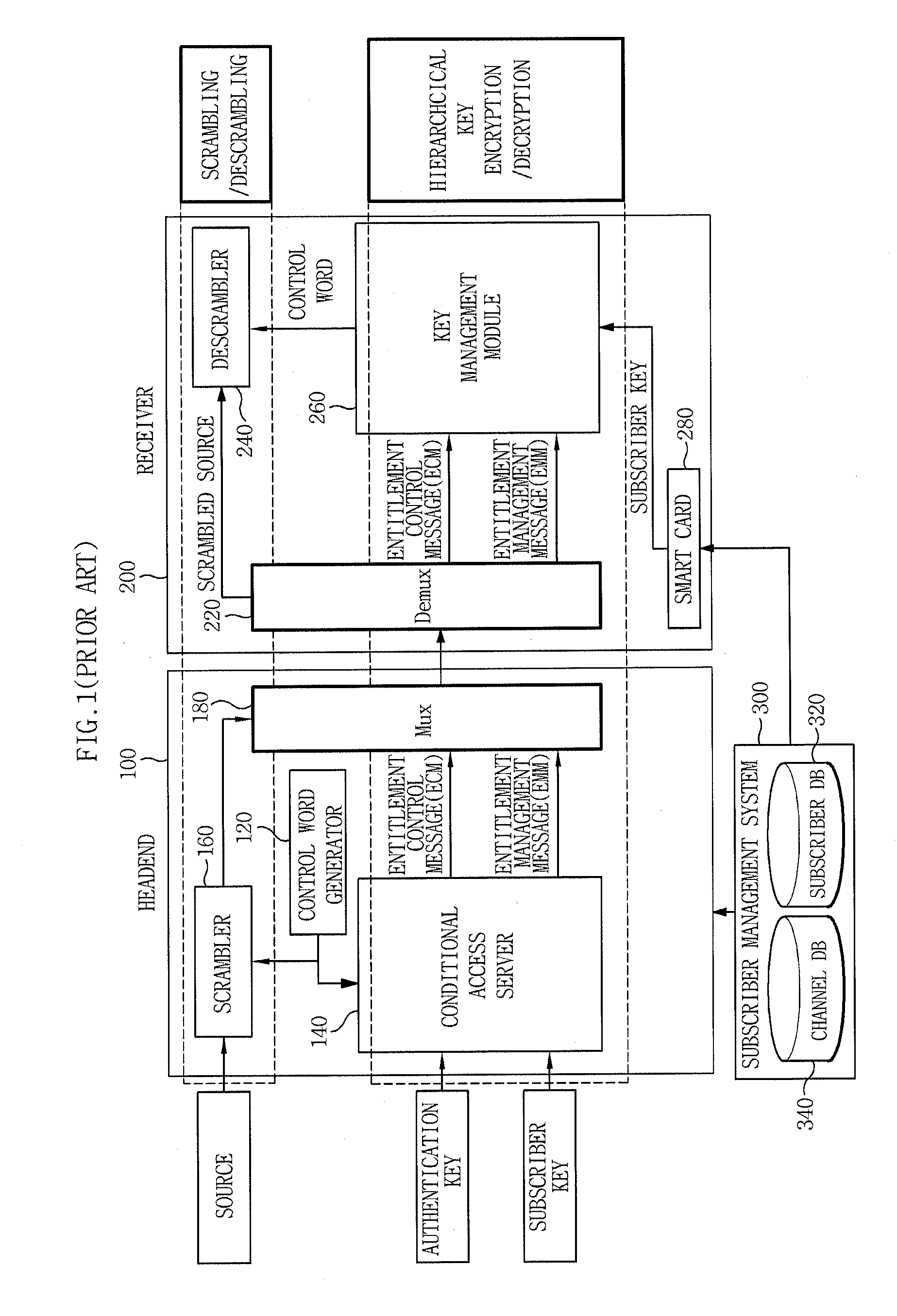
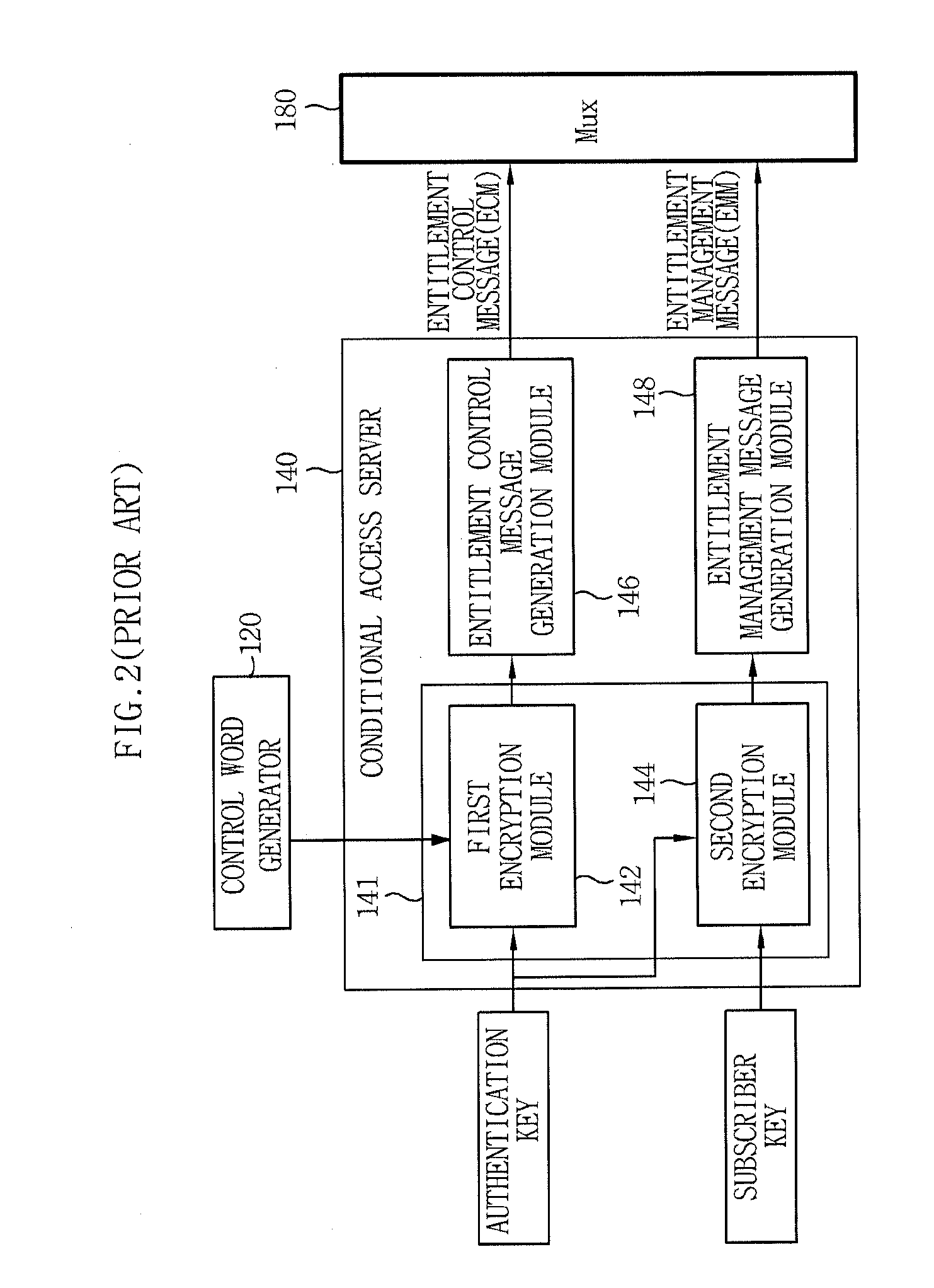
A video on demand (VOD) method, consistent with the invention involves storing multiple selective encrypted VOD content on a VOD server; receiving an order for the VOD content specifying delivery to a target decoder; determining what CA encryption system is associated with the order; stripping all encrypted segments from the multiple selectively encrypted content that are not associated with the order to produce single selectively encrypted VOD content; and sending the single selectively encrypted VOD content to the target decoder. The multiple selectively encrypted VOD content can be created by examining unencrypted data representing digital content to identify segments of content for encryption; encrypting the identified segments of content using a first encryption method associated with a first conditional access system to produce first encrypted segments; encrypting the identified segments of content using a second encryption method associated with a second conditional access system to produce second encrypted segments; and replacing the identified segments of content with the first encrypted content and the second encrypted content in the digital content, to produce the multiple selectively encrypted VOD content.
Owner:SONY CORP +1
Time-multiplexed multi-program encryption system
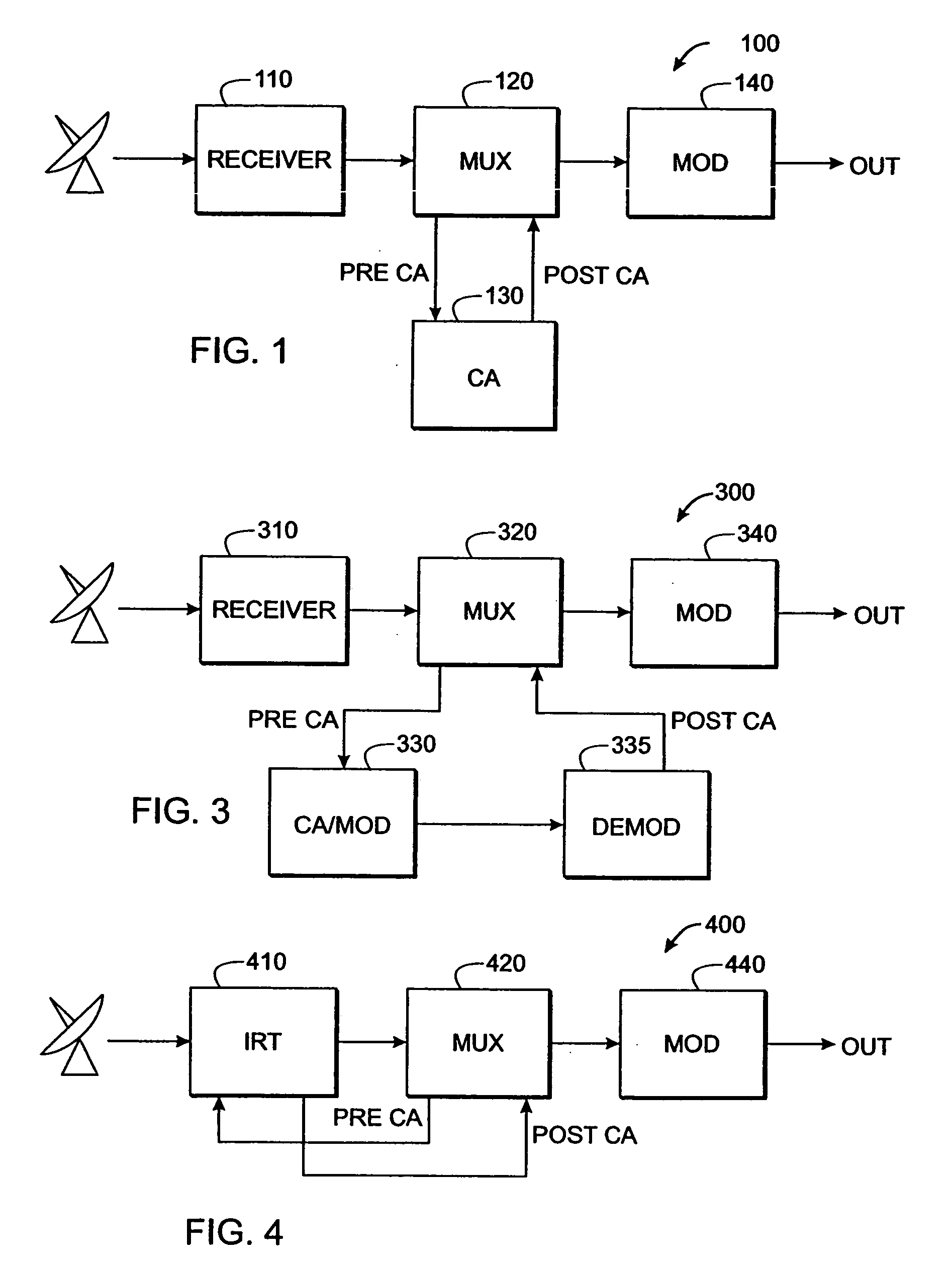
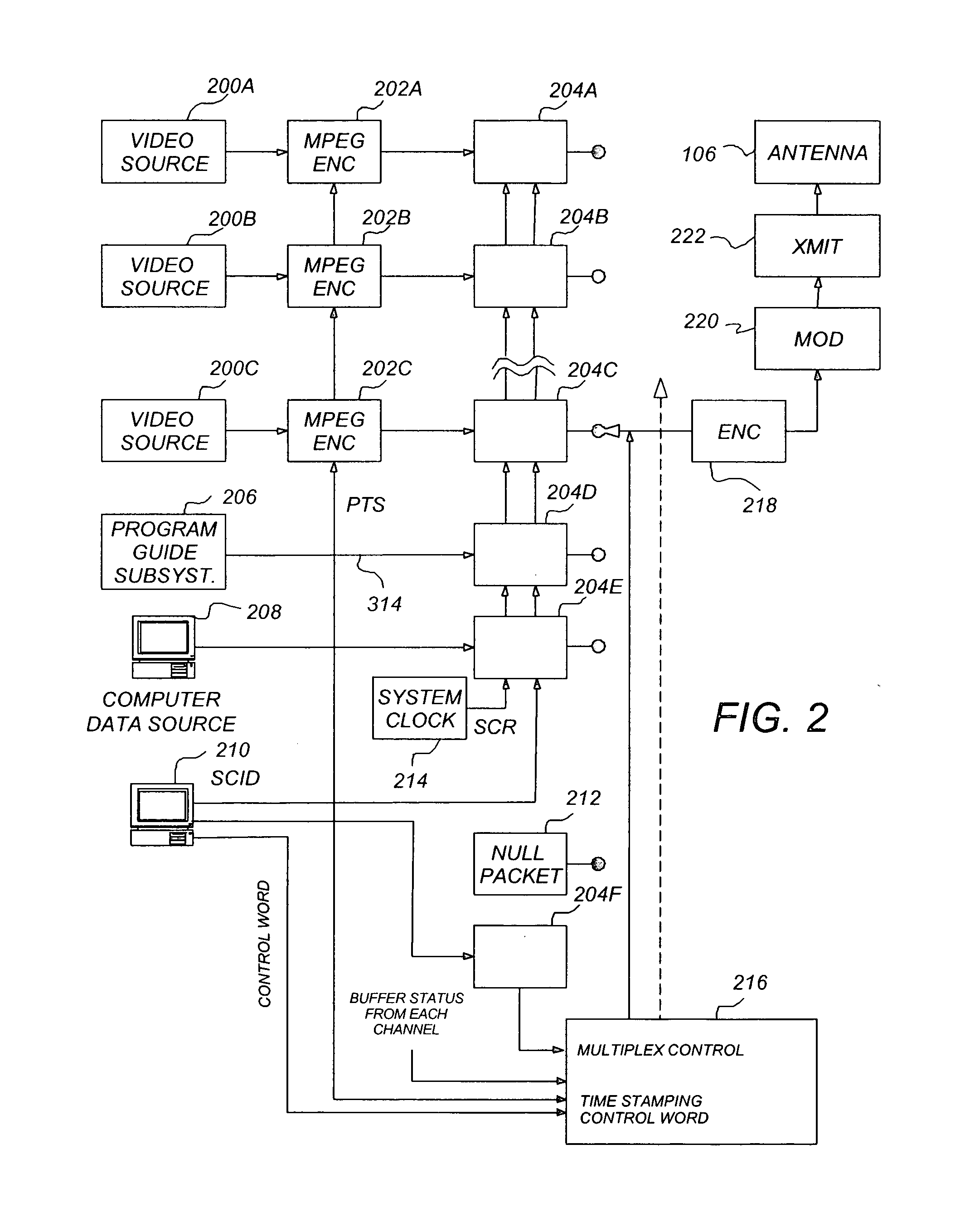
ActiveUS20050180568A1Increase the number ofImprove throughputPulse modulation television signal transmissionSecret communicationComputer hardwareRe sequencing
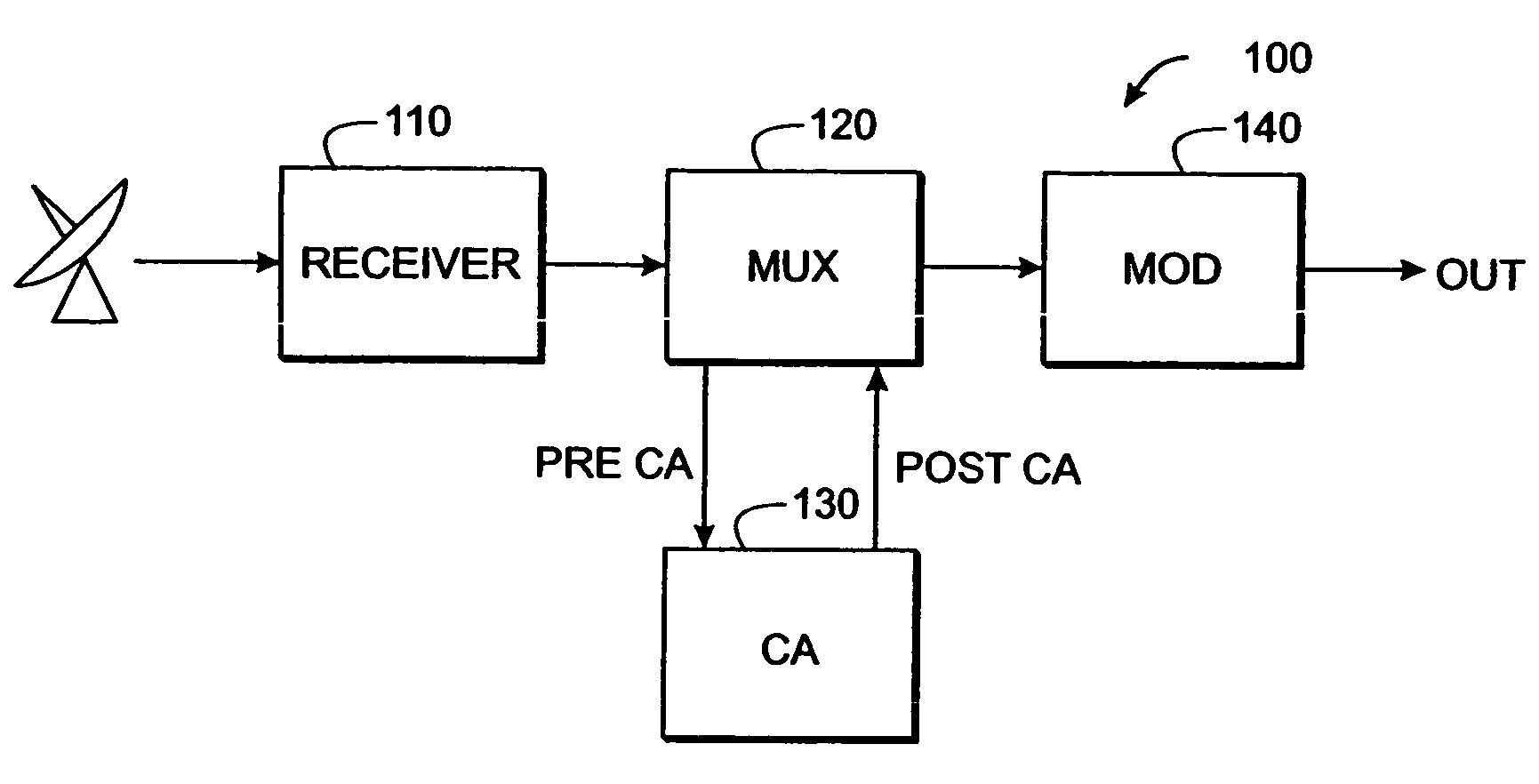
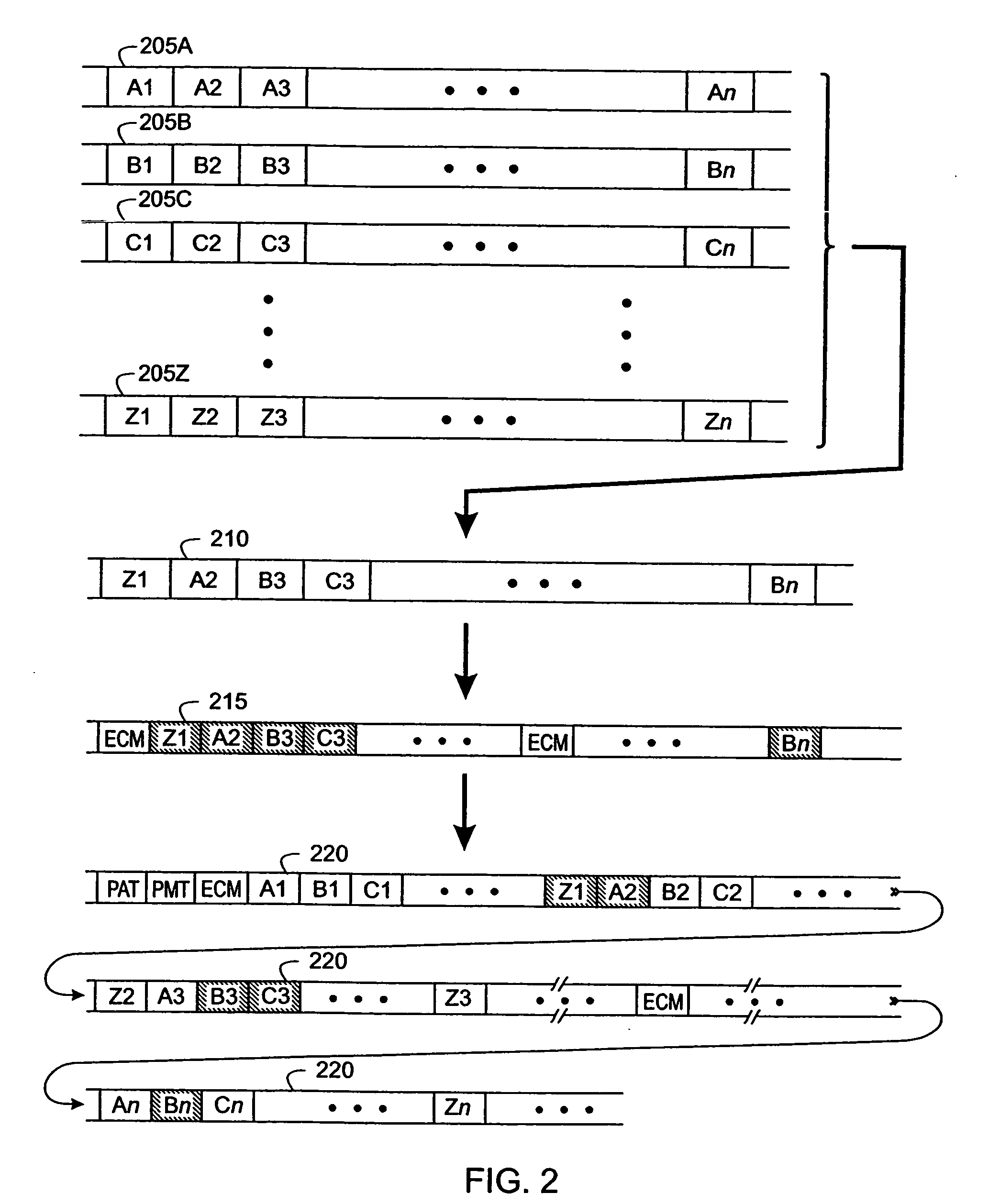
A system and method are described for greatly increasing the number of services that can be encrypted with existing conditional access equipment. The method is most useful when many digitally compressed programs are encrypted at the same time. Only the most critical components of each compressed video, audio, or data stream are selected and then sequenced into a single stream. Additional formatting causes this sequence of segments from multiple sources to appear as a single continuous stream to the conditional access system. Once this stream has been encrypted, it is demultiplexed and the components are restored and re-sequenced into their respective programs. Messages such as the Entitlement Control Messages that are inserted into the stream by the encryption system, are also adjusted and included with each of the reconstructed programs. The technique not only allows encryption systems to be designed using less encryption hardware, but also simplifies the management of encryption sessions, particularly in on-demand programming applications.
Owner:IMAGINE COMM
Authenticated Communication Between Security Devices
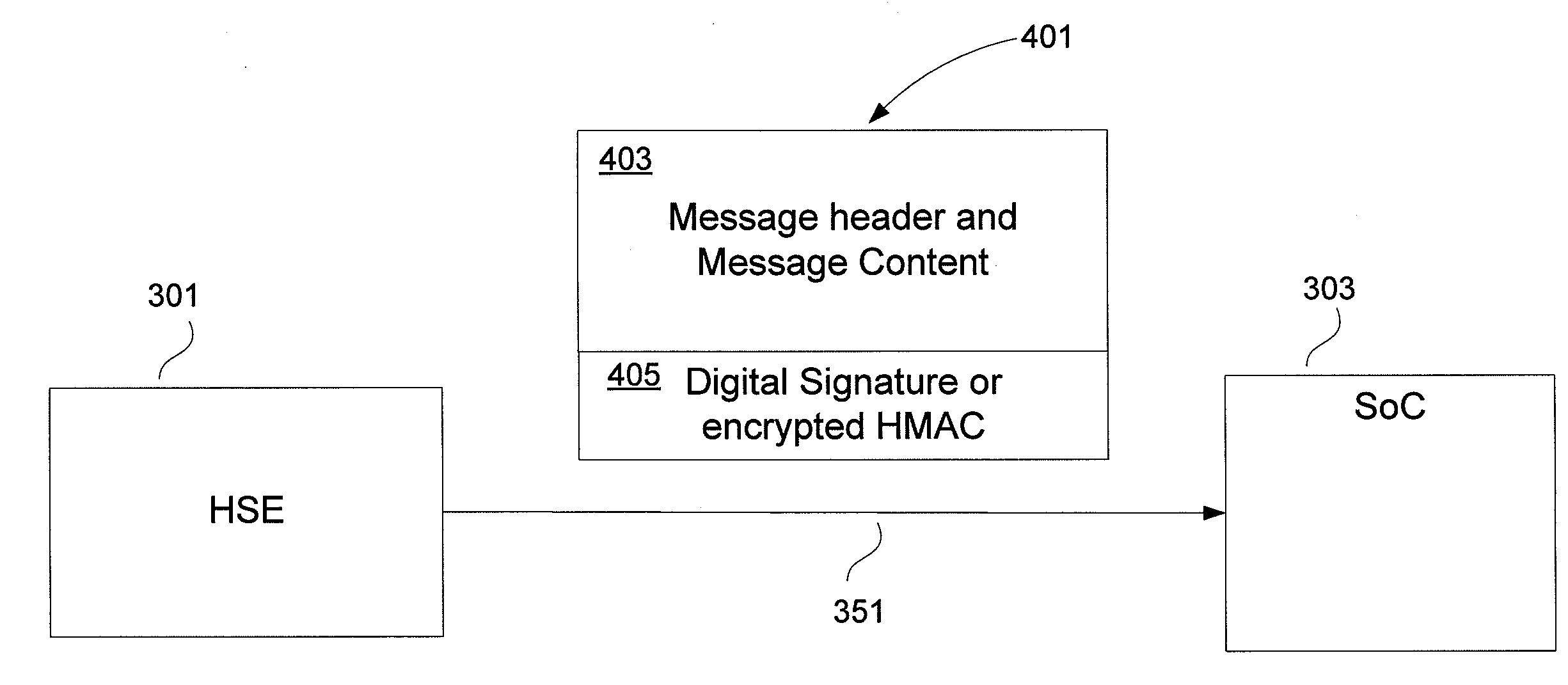
ActiveUS20100217985A1User identity/authority verificationTelevision systemsConditional access systemsDigital signature
Apparatuses, computer readable media, and methods establishing and maintaining trust between security devices for distributing media content are provided. Two security devices bind to establish an initial trust so that security information can be exchanged. Subsequently, trust is refreshed to verify the source of a message is valid. In an embodiment, the security devices may comprise a security processor and a system on a chip (SoC) in a downloadable conditional access system. Trust may be refreshed by a security device inserting authentication information in a message to another security device, where authentication information may assume different forms, including a digital signature (asymmetric key) or a hash message authentication code (HMAC). Trust may also be refreshed by extracting header information from the message, determining state information from at least one parameter contained in the header information, and acting on message content only when the state information is valid.
Owner:COMCAST CABLE COMM LLC
Service activation of set-top box functionality using broadcast conditional access system
InactiveUS20060041903A1Digital data processing detailsAnalogue secracy/subscription systemsConditional access systemsBiological activation
A method, apparatus, and article of manufacture provide the ability to activate functionality in a set-top box. A feature authorization message is received in a set-top box. The feature authorization message comprises one or more rules to be evaluated (wherein each of the rules comprises one or more tests for a status of one or more conditional access module attributes), one or more event requirements for rule evaluation, and one or more features that are dependent by the rule evaluation result (wherein each of the one or more features represents a set of one or more abilities of hardware and / or software of the set-top box). When one or more of the event requirements have been met, the one or more rules are evaluated to obtain a result. The ability to use the one or more features are then set based on the result.
Owner:THE DIRECTV GROUP
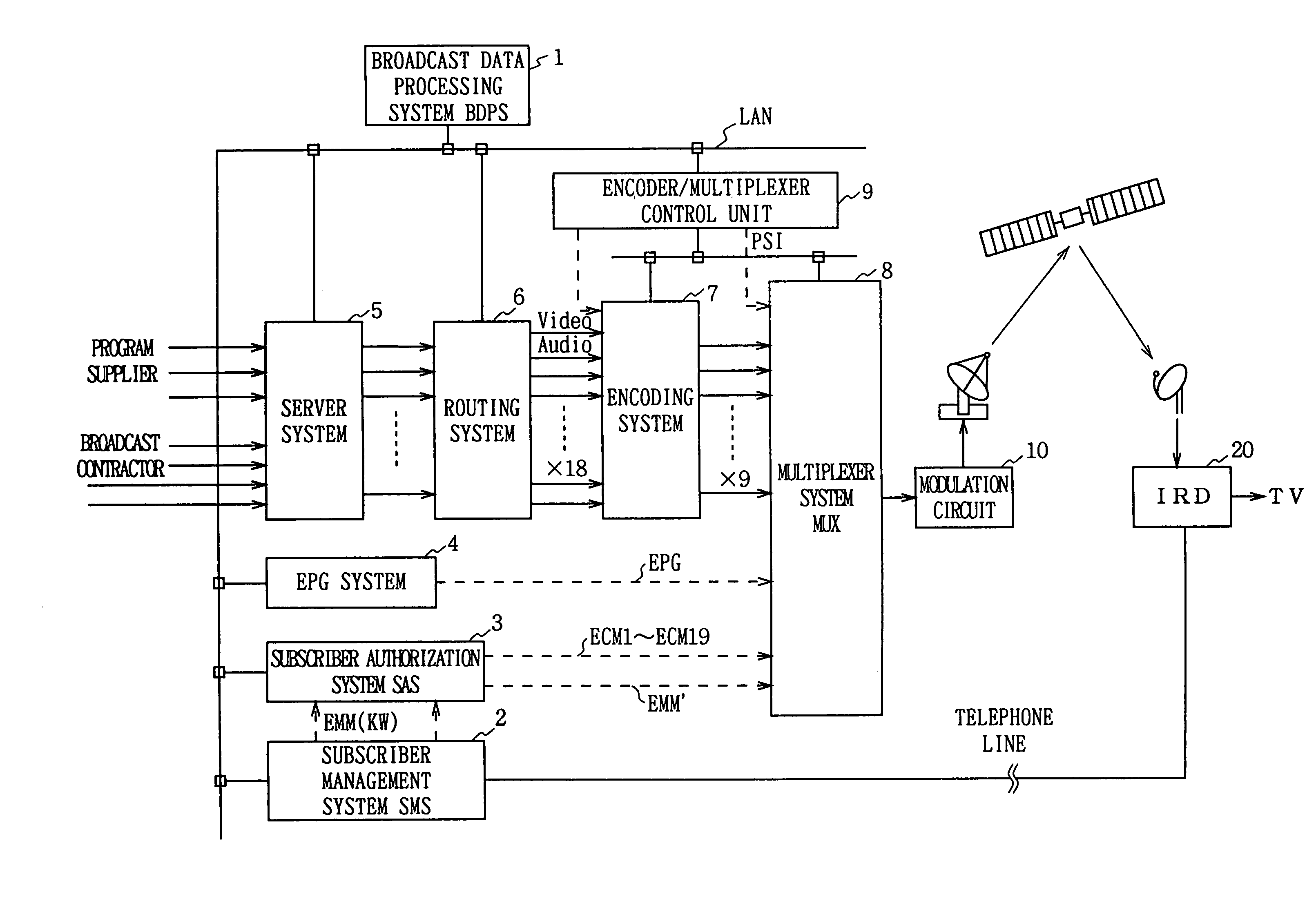
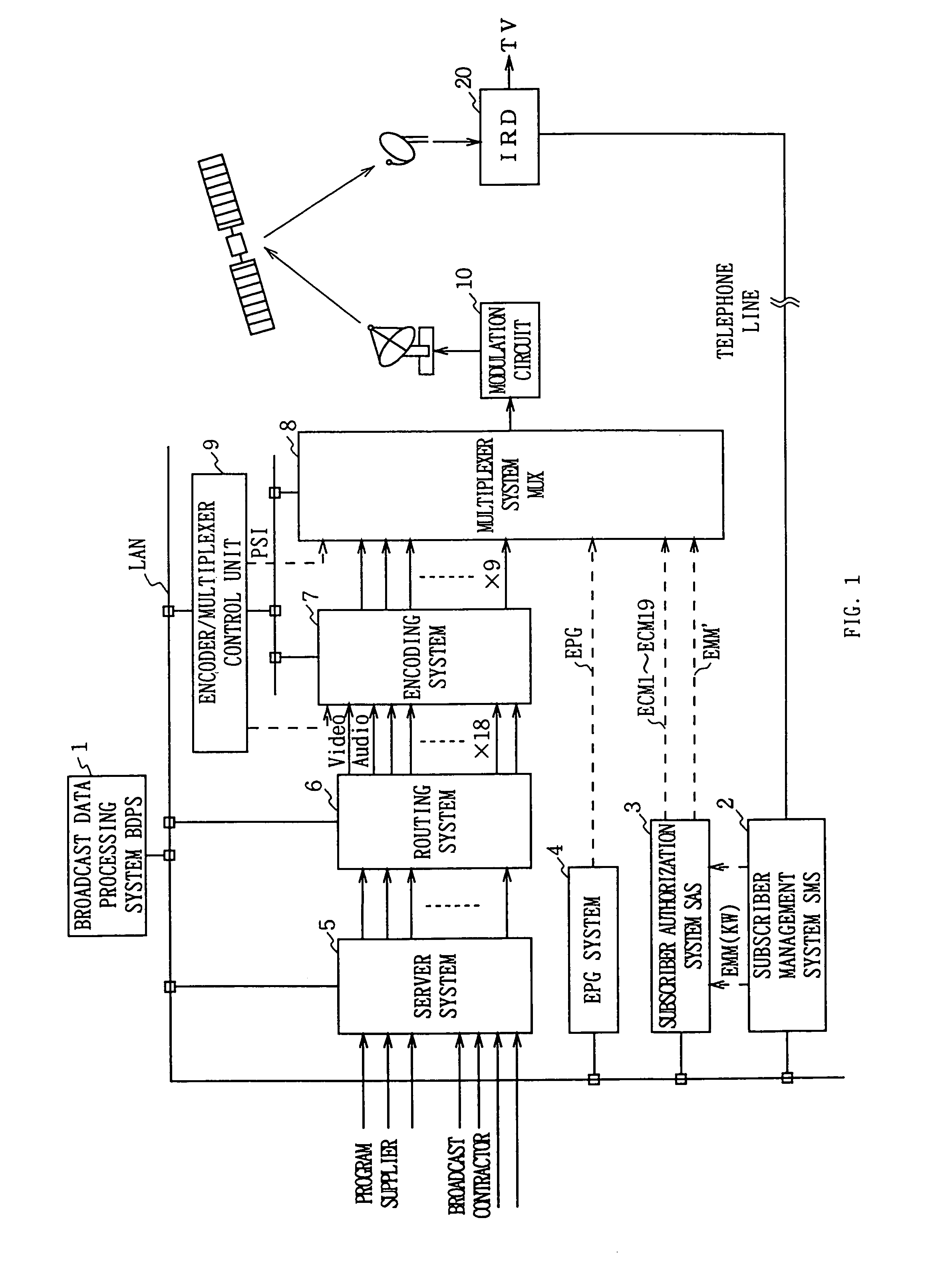
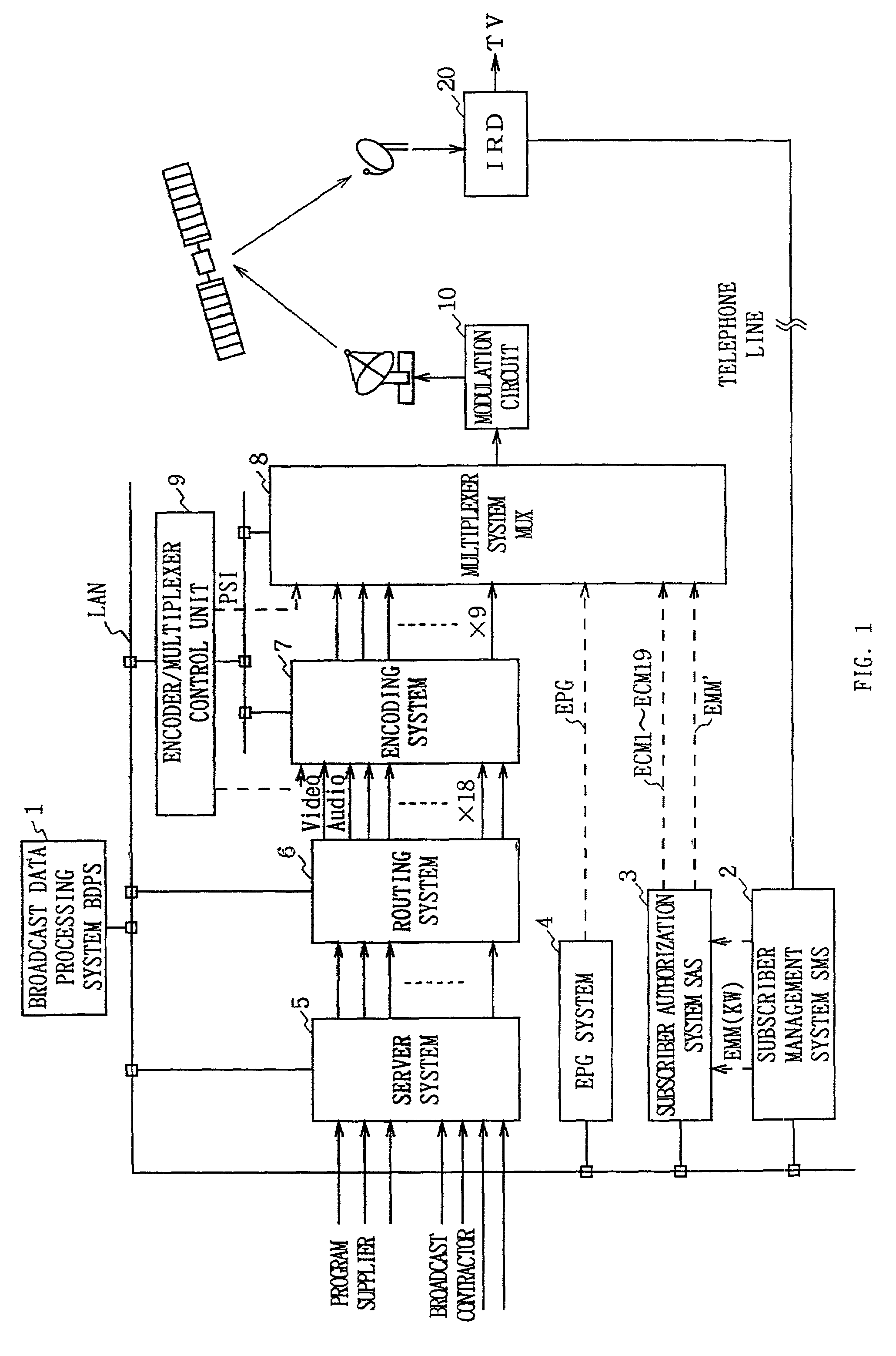
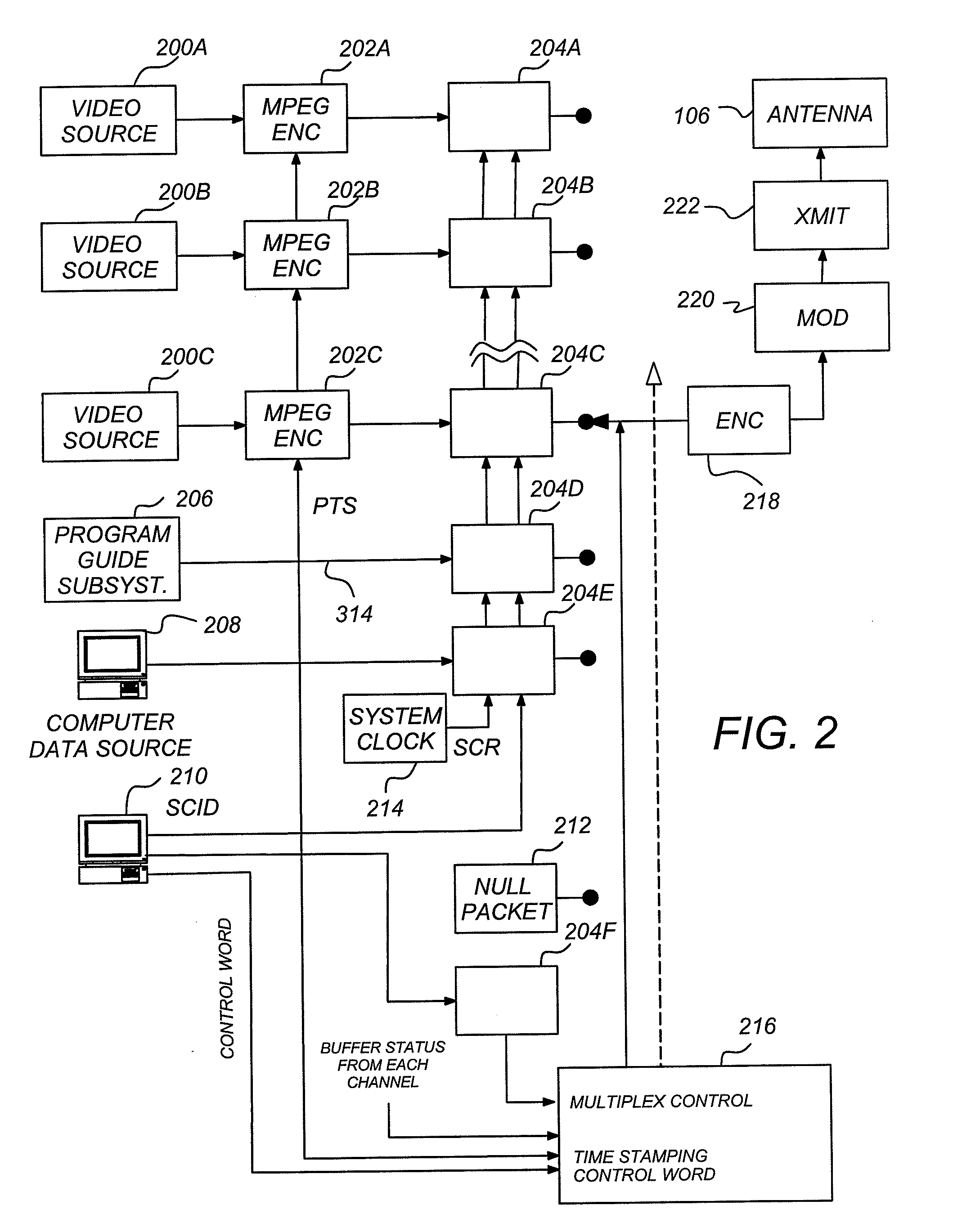
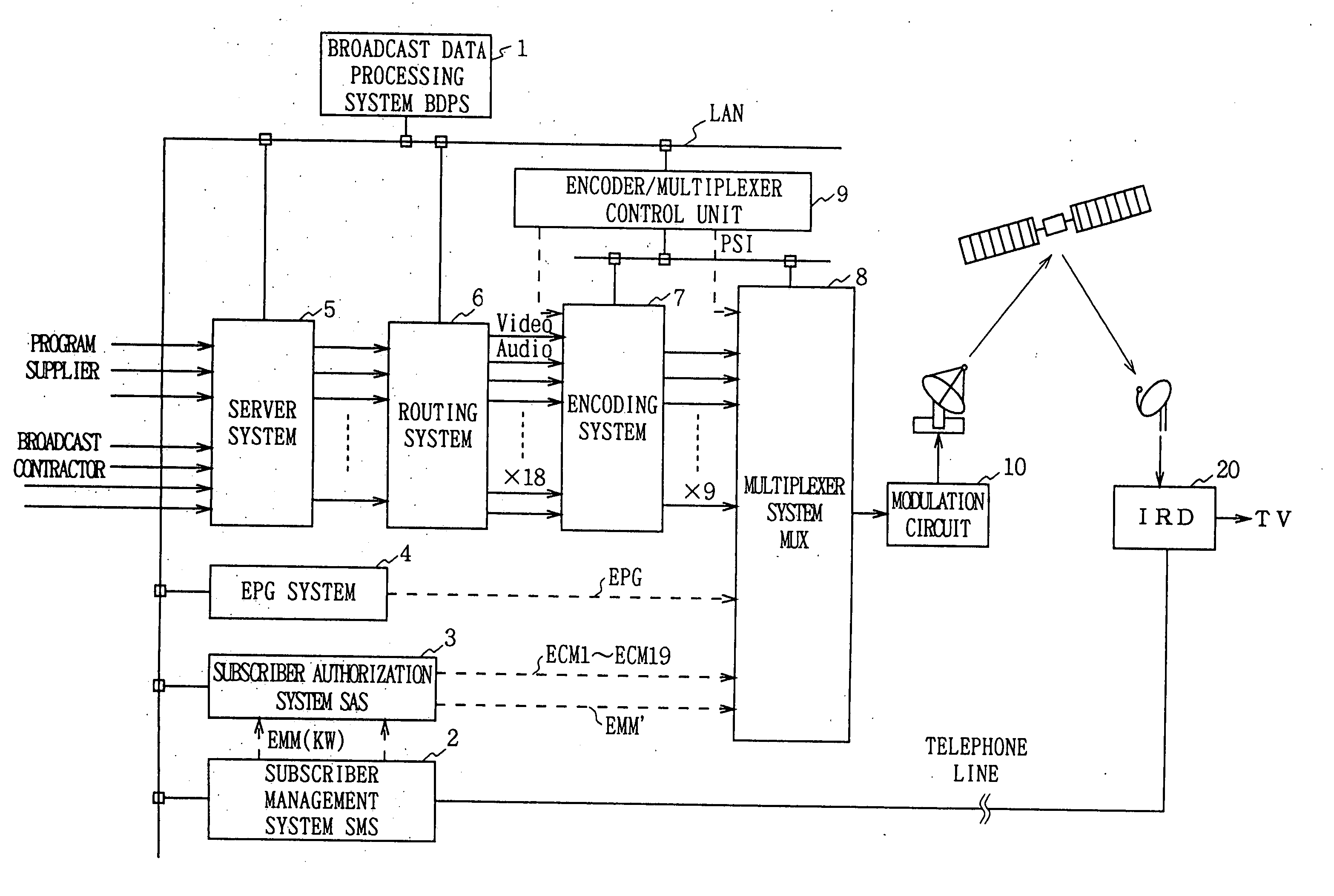
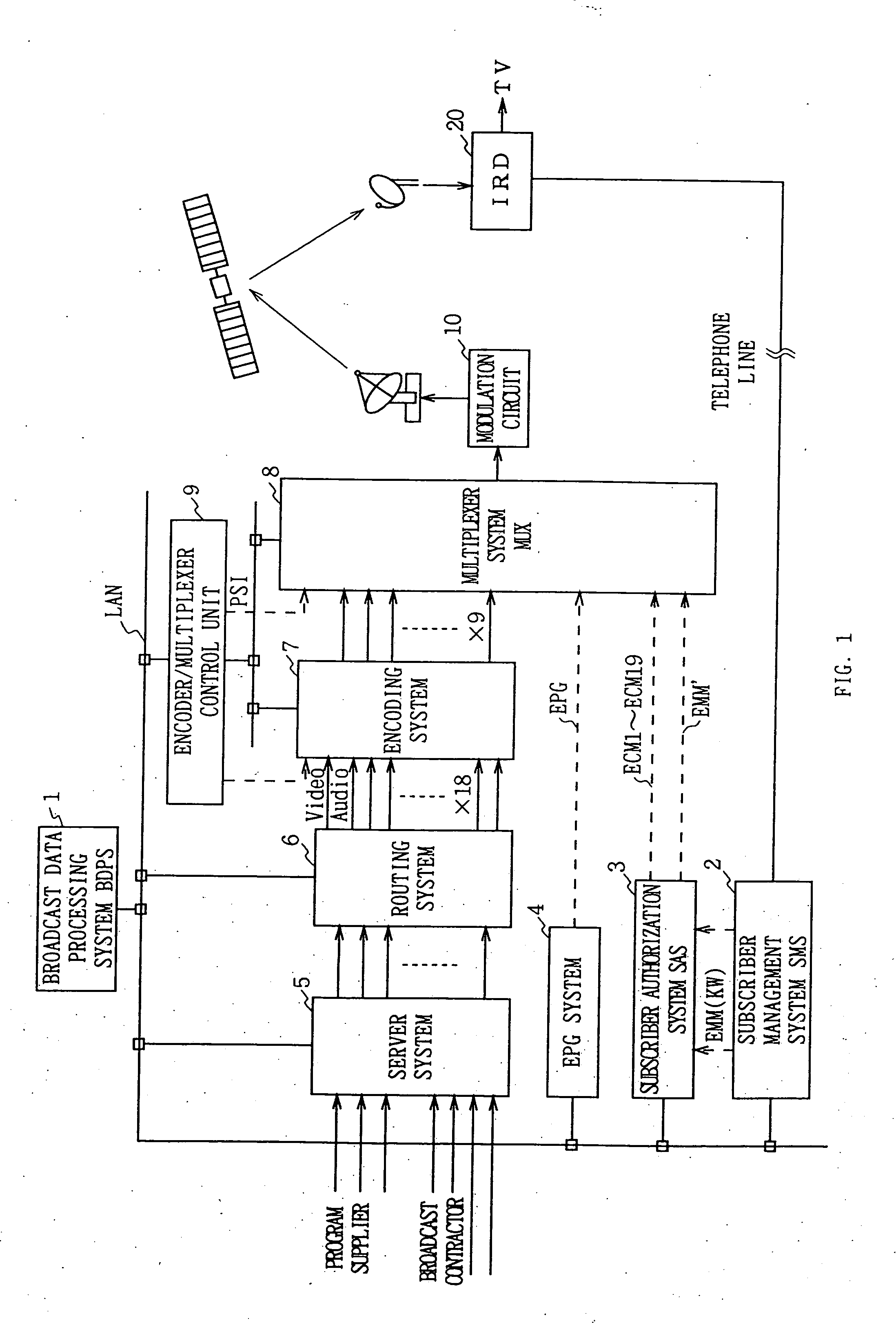
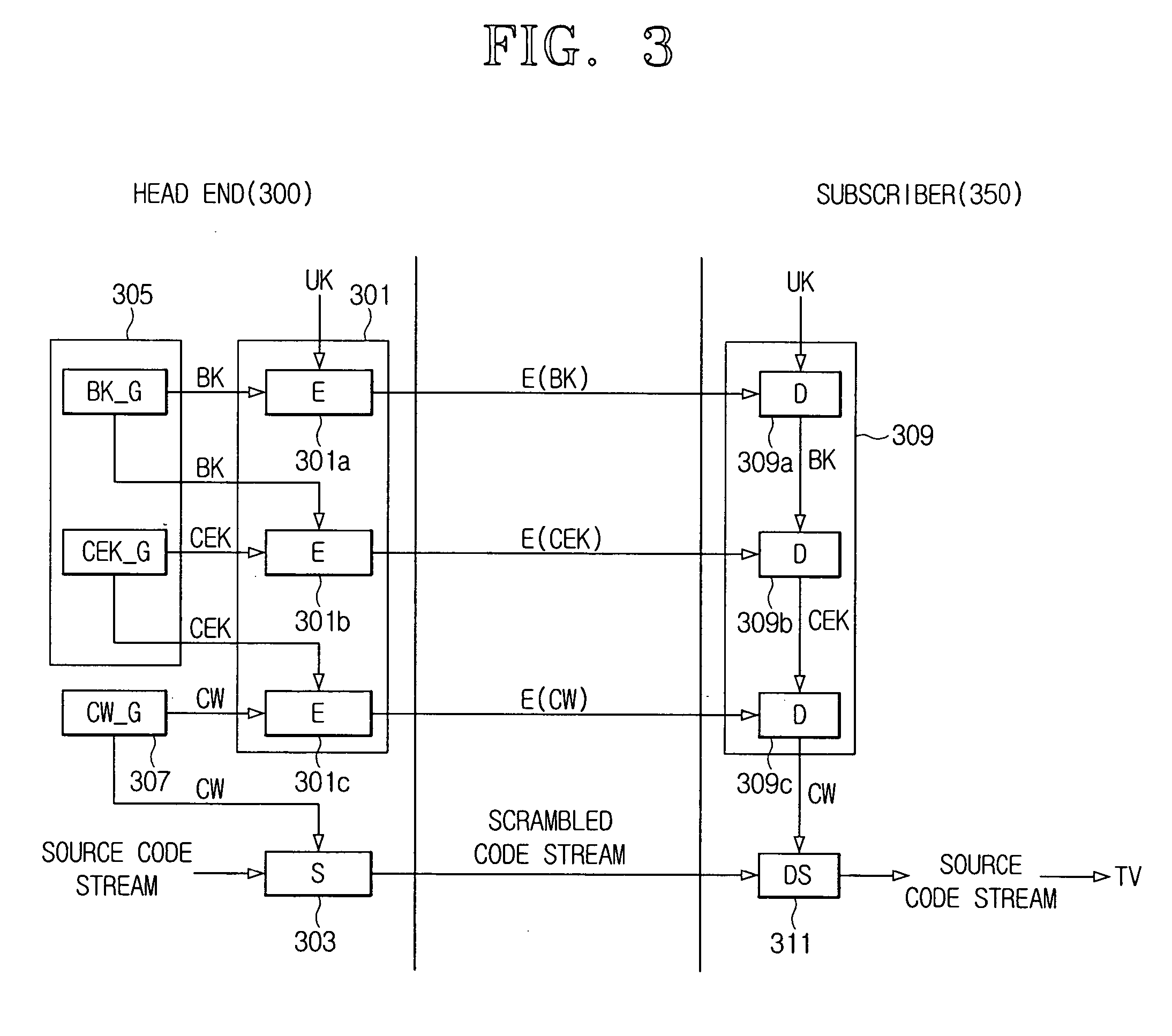
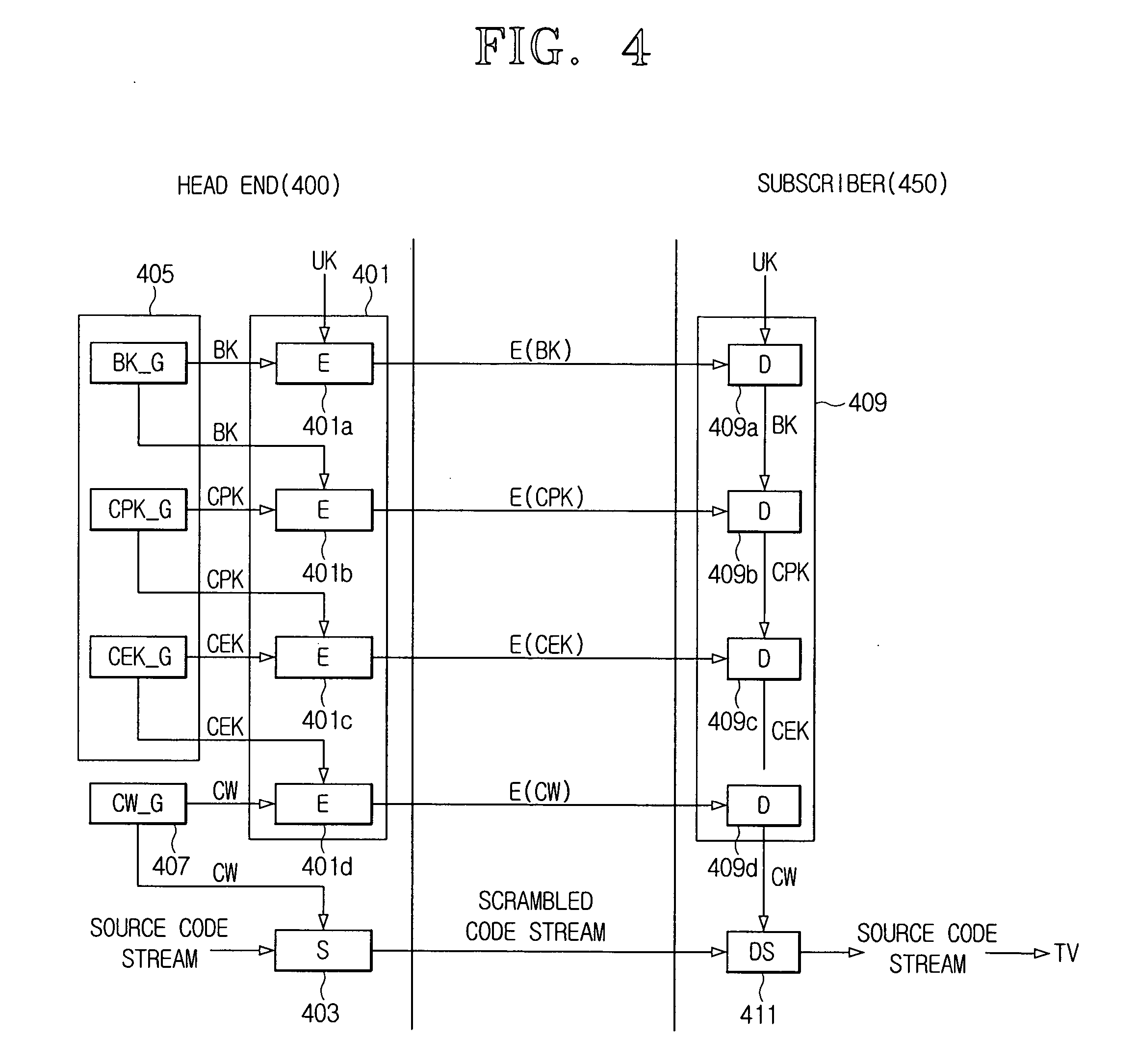
Data multiplexing device, program distribution system, program transmission system, pay broadcast system, program transmission method, conditional access system, and data reception device
InactiveUS7023992B1Minimize device configurationPrevent overflowPulse modulation television signal transmissionTime-division multiplexMultiplexingConditional access systems
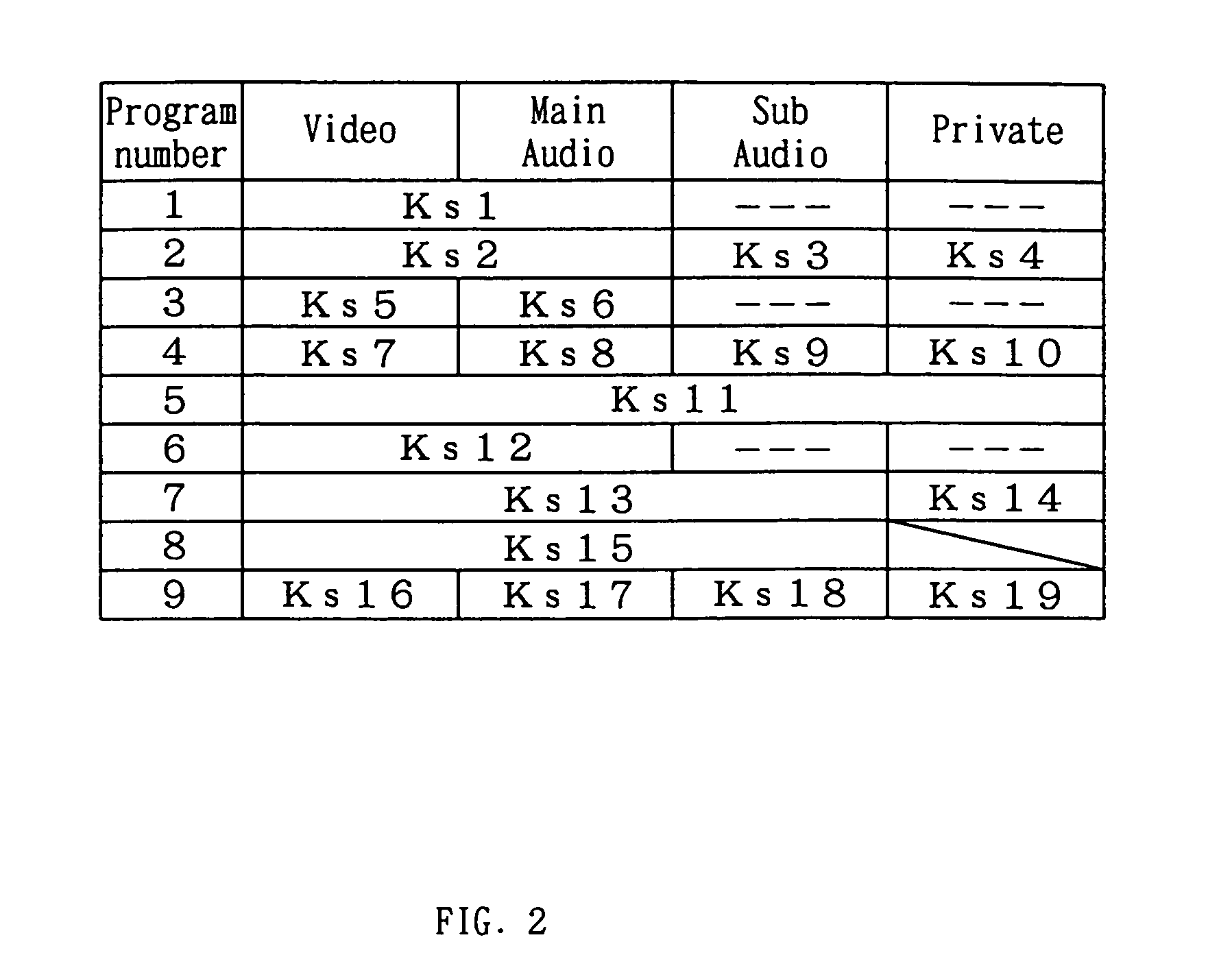
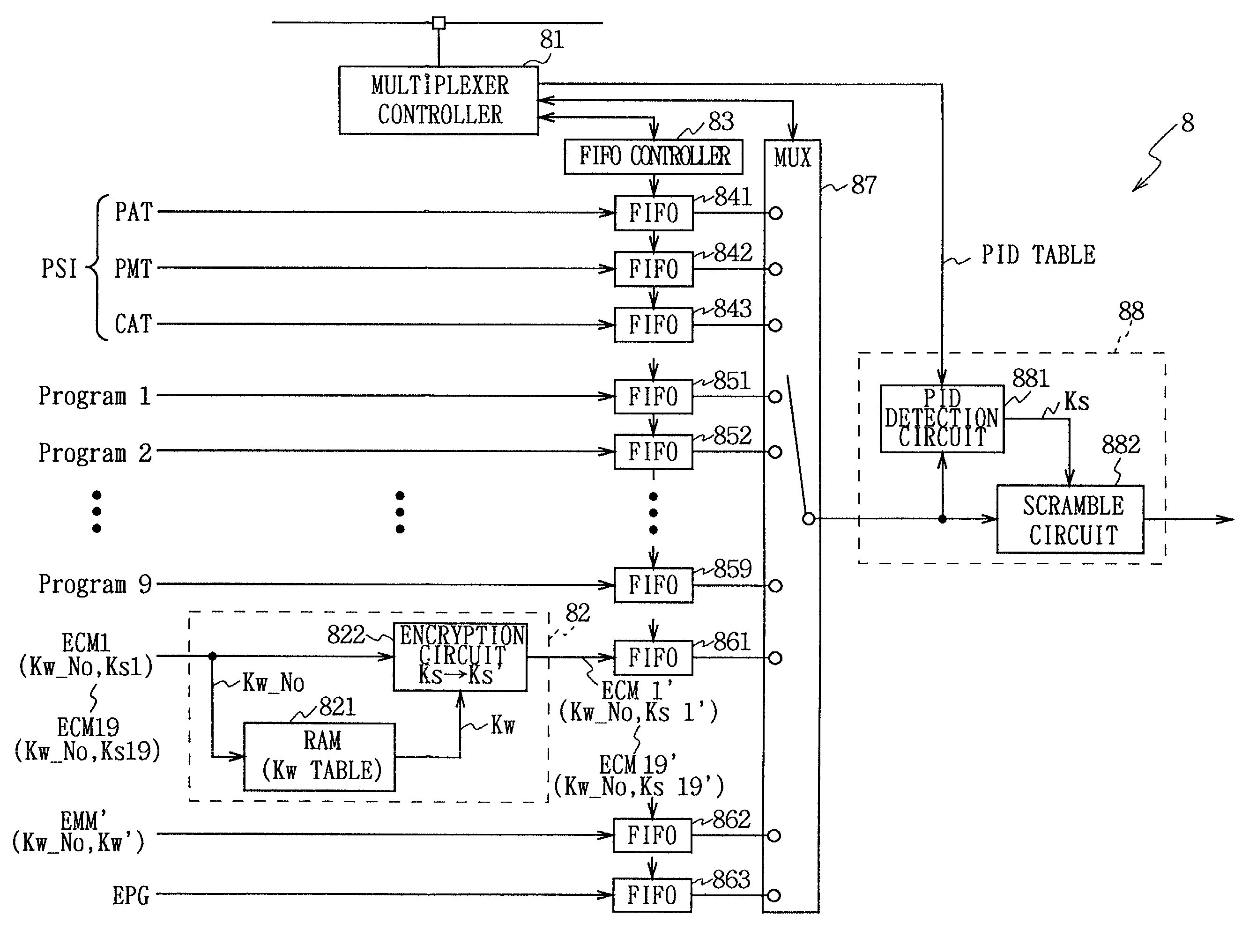
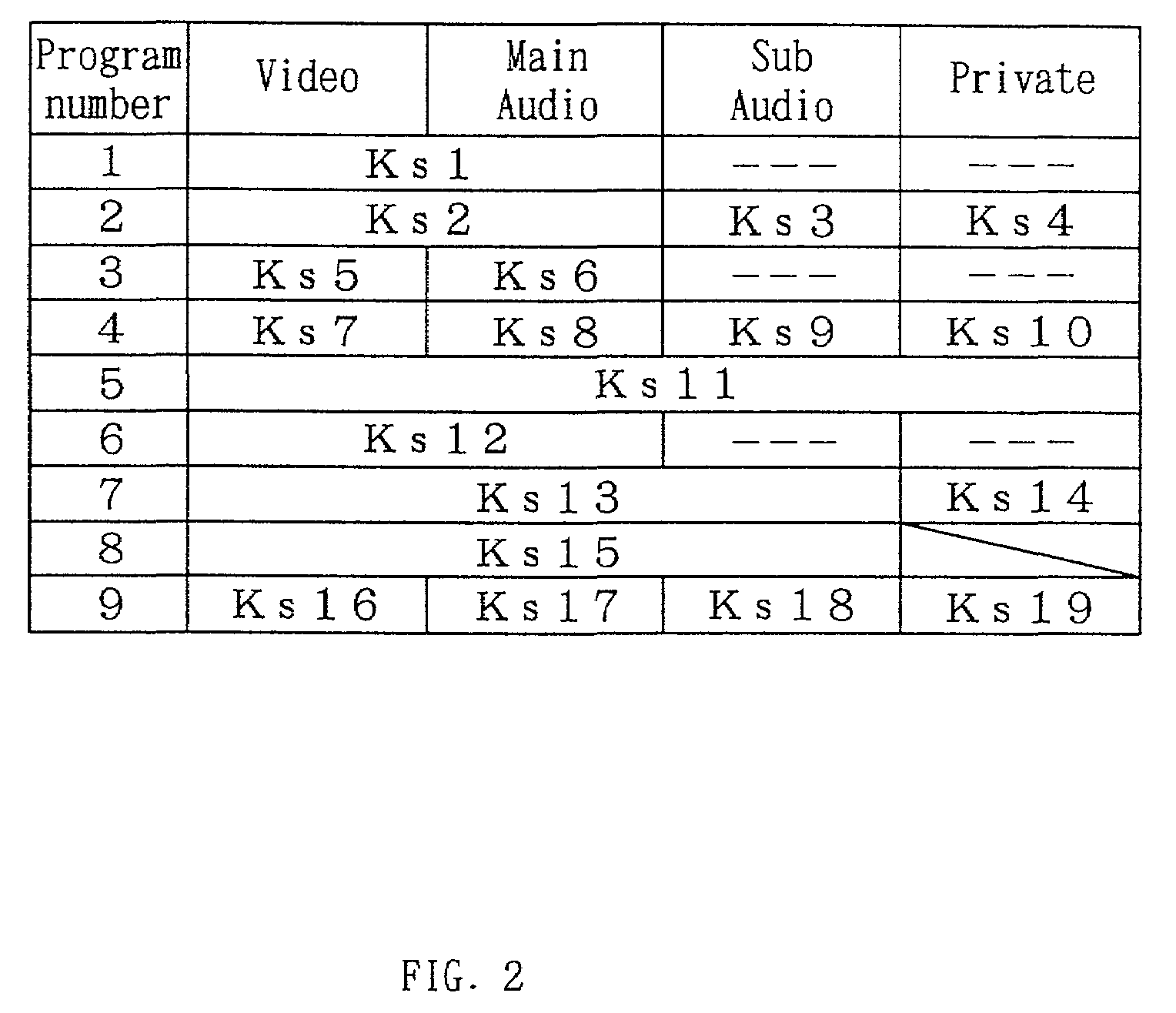
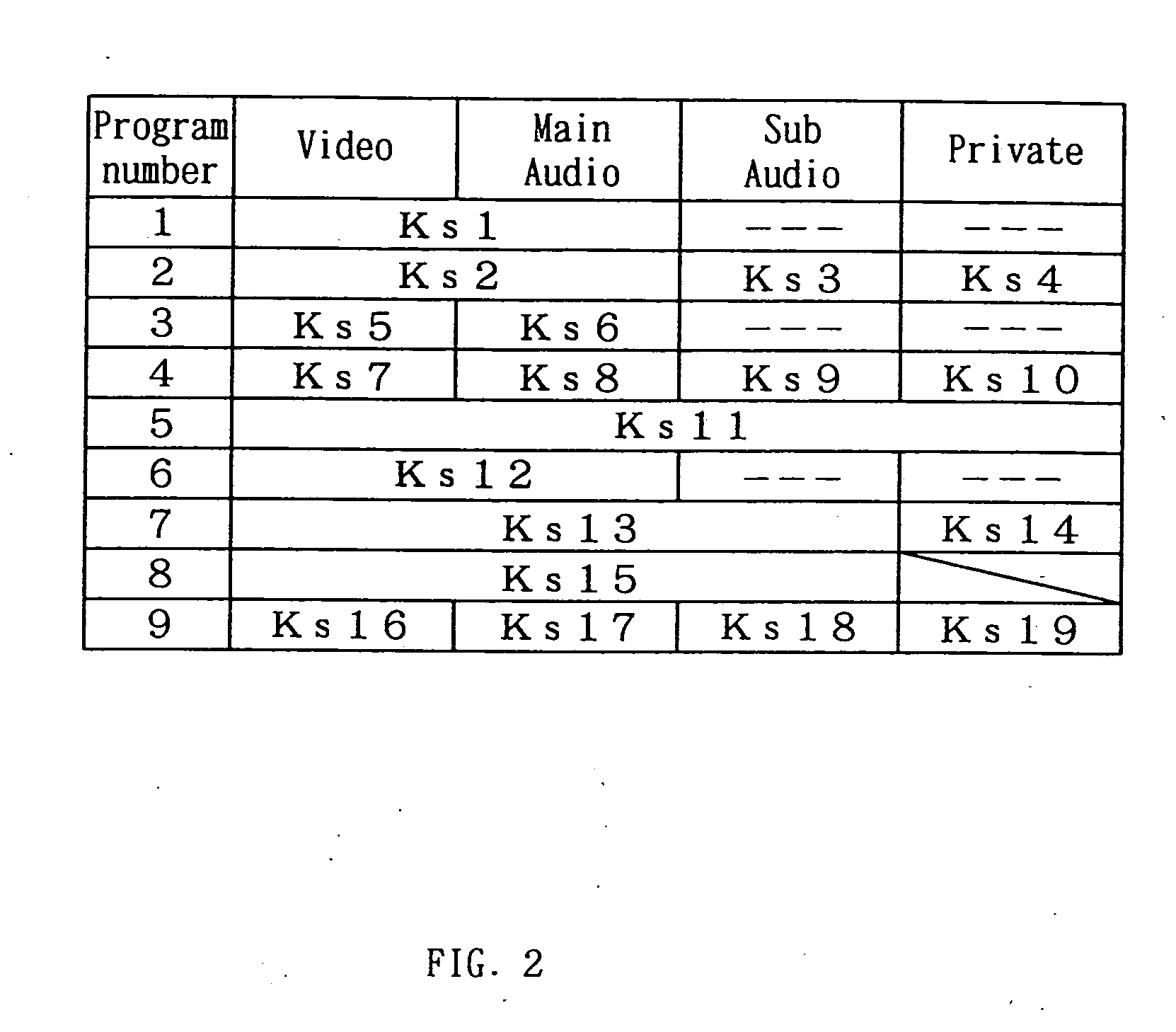
In a data multiplexing device which multiplexes and transmits the transport stream packets of program data consisting of a plurality of data elements constructed in the form of transport stream packets, a program distribution system, a program transmission system, a pay broadcast system, a program transmission method, a conditional access system, and a data reception device according to the present invention, by generating a scramble key Ks corresponding to one or more data elements among the plurality of data elements constituting a program and by scrambling each data element, an audience can subscribe for each data element.
Owner:SONY CORP
Data multiplexing device, program distribution system, program transmission system, pay broadcast system, program transmission method, conditional access system, and data reception device
InactiveUS7113523B1Simple circuit configurationData augmentationTelevision system detailsTelevision system scanning detailsMultiplexingConditional access systems
In a data multiplexing device which multiplexes and transmits the transport stream packets of program data consisting of a plurality of data elements constructed in the form of transport stream packets, a program distribution system, a program transmission system, a pay broadcast system, a program transmission method, a conditional access system, and a data reception device according to the present invention, by generating a scramble key Ks corresponding to one or more data elements among the plurality of data elements constituting a program and by scrambling each data element, an audience can subscribe for each data element.
Owner:SONY CORP
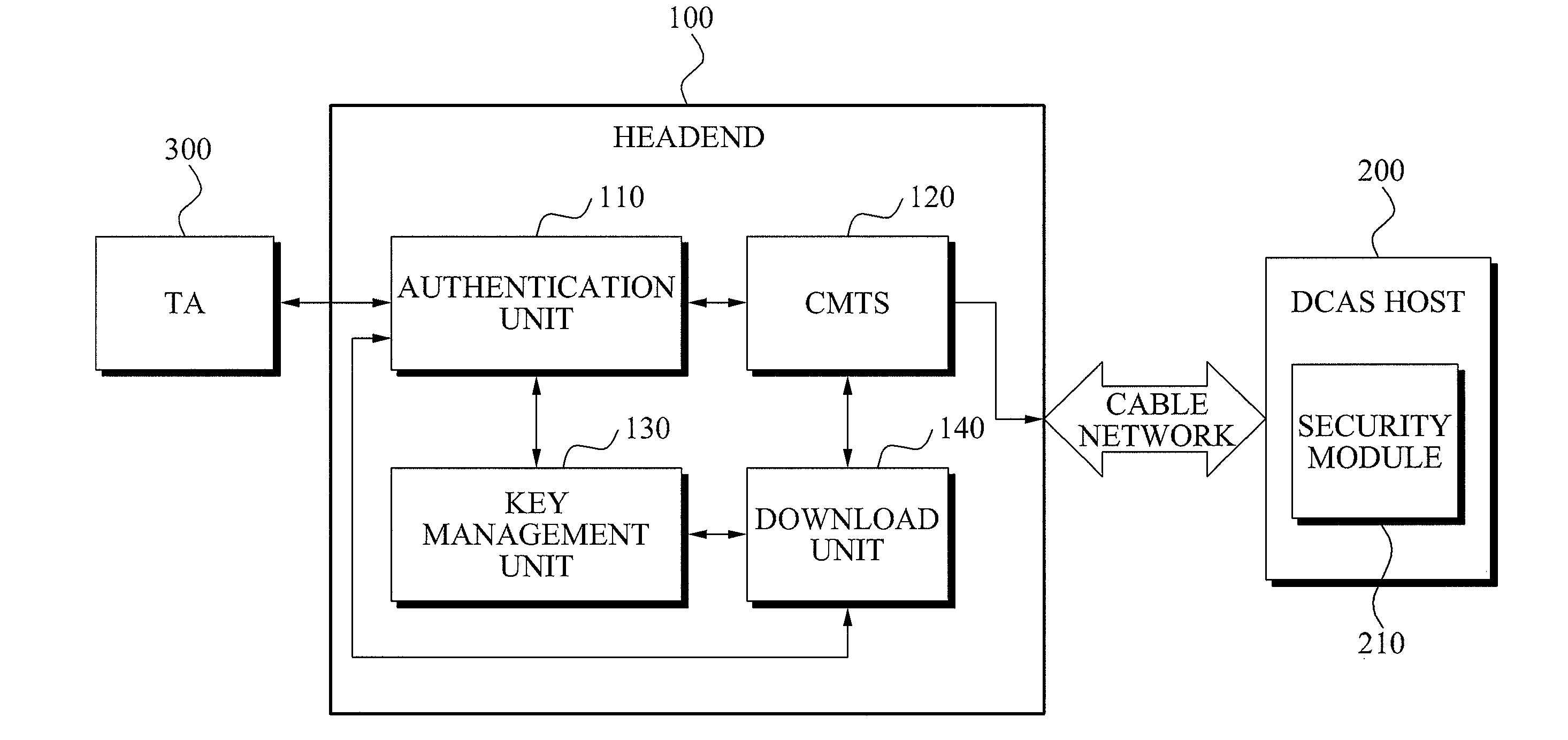
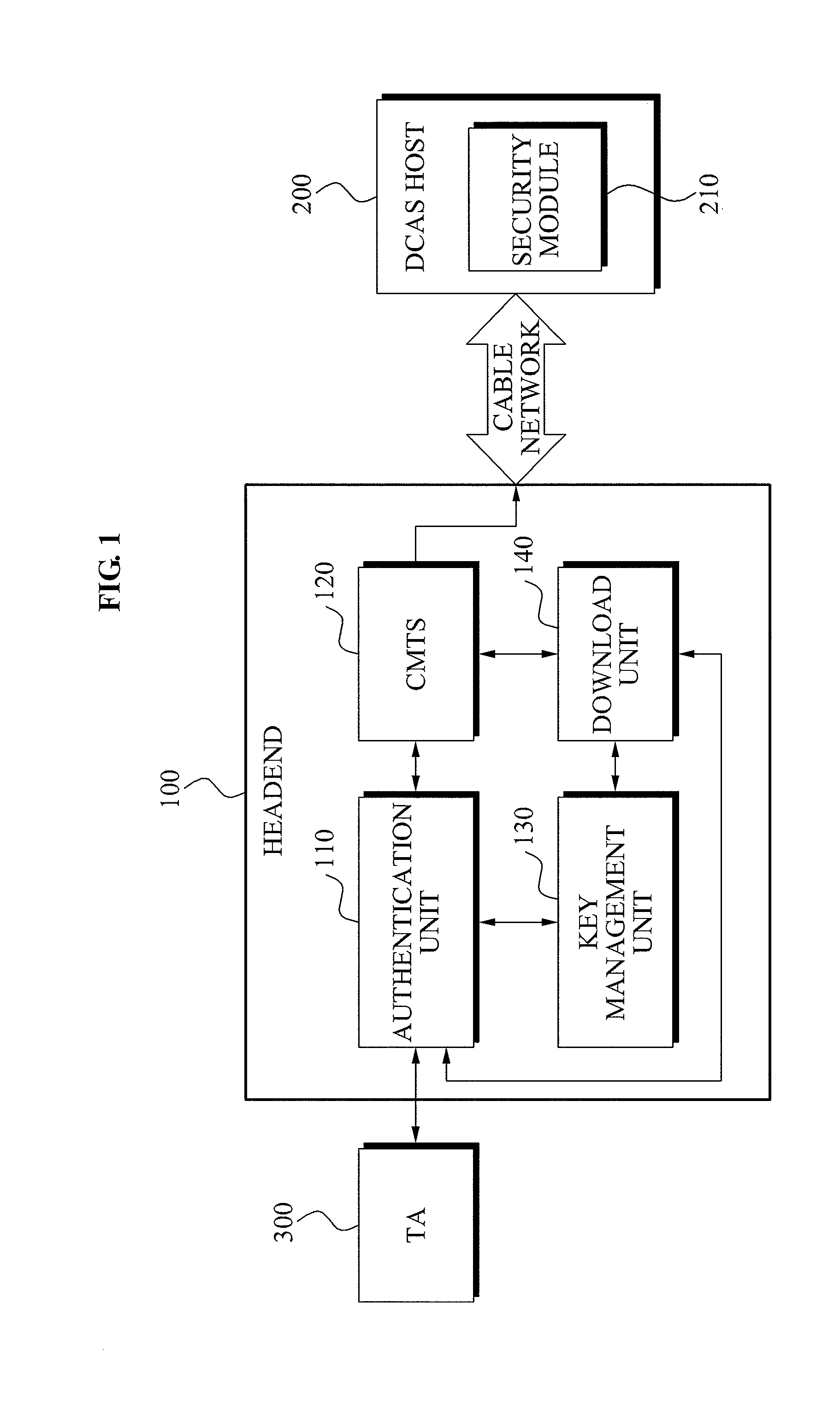
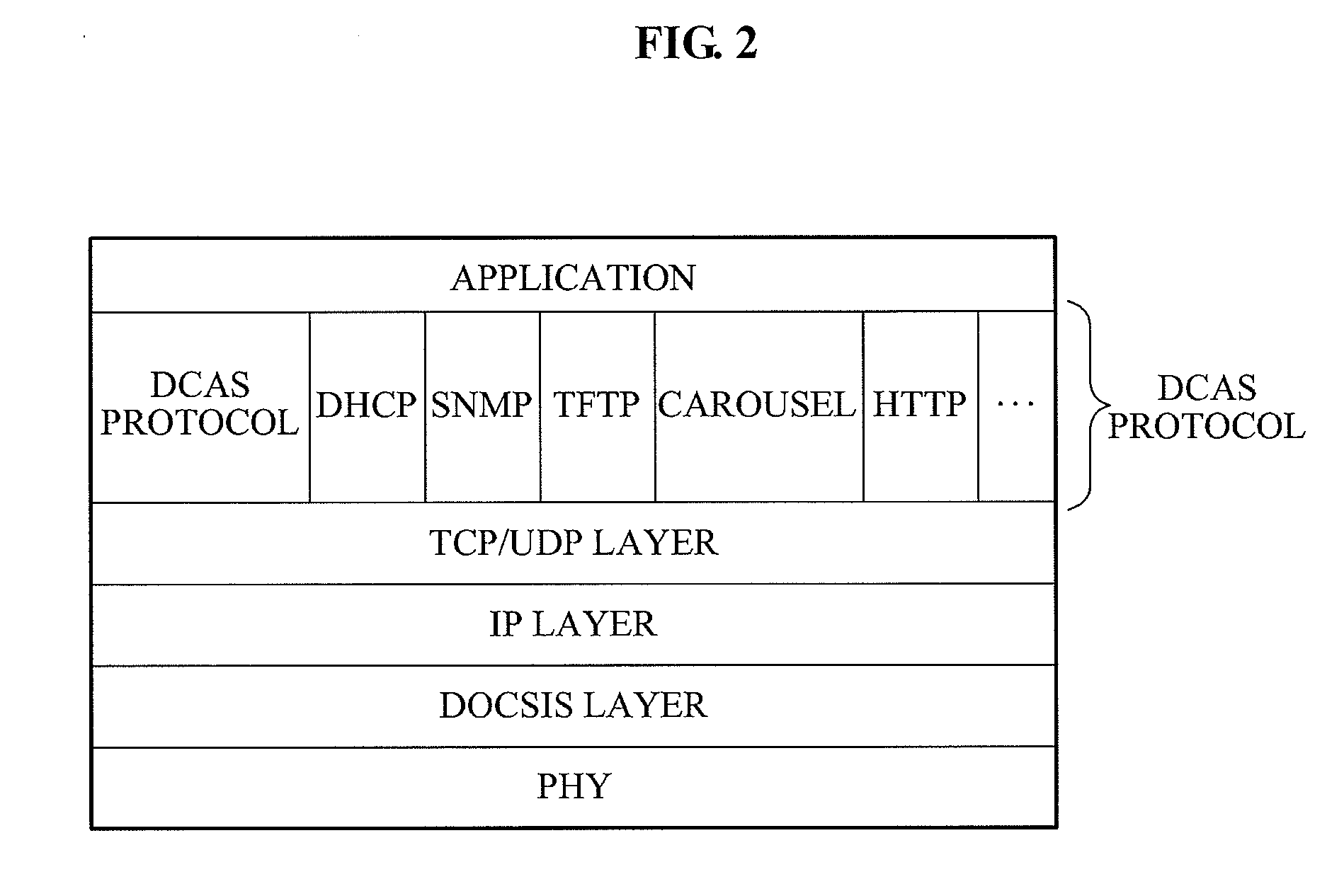
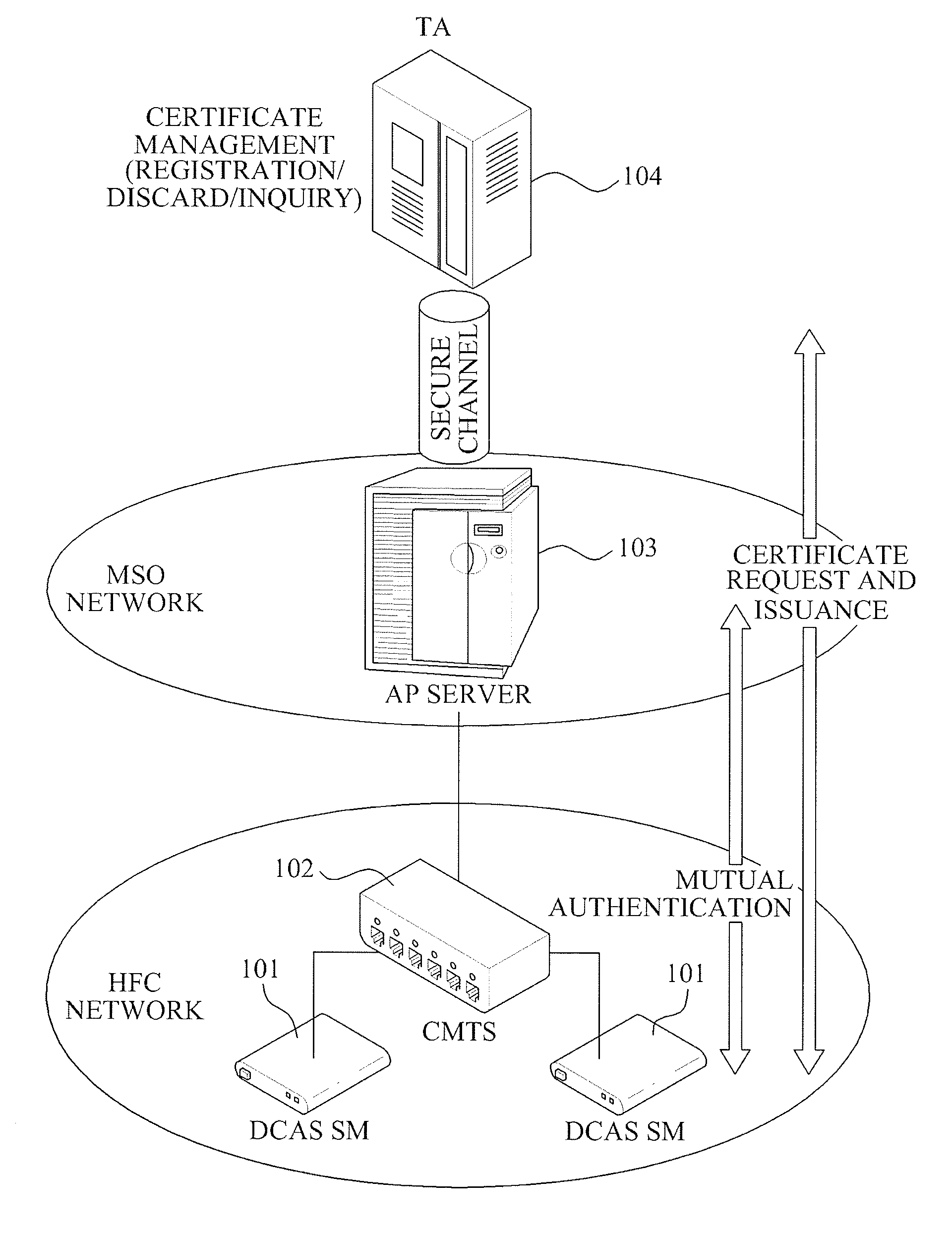
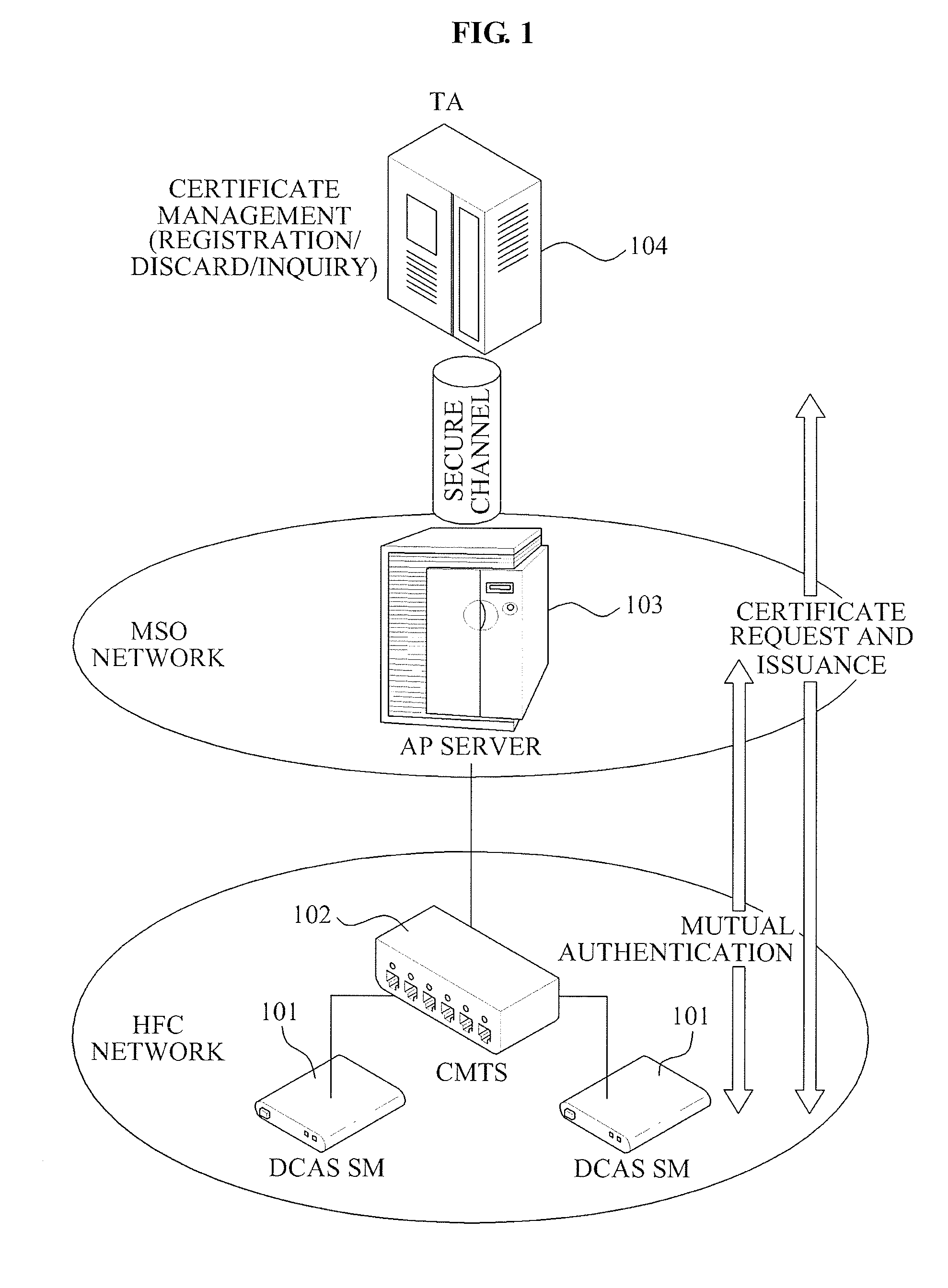
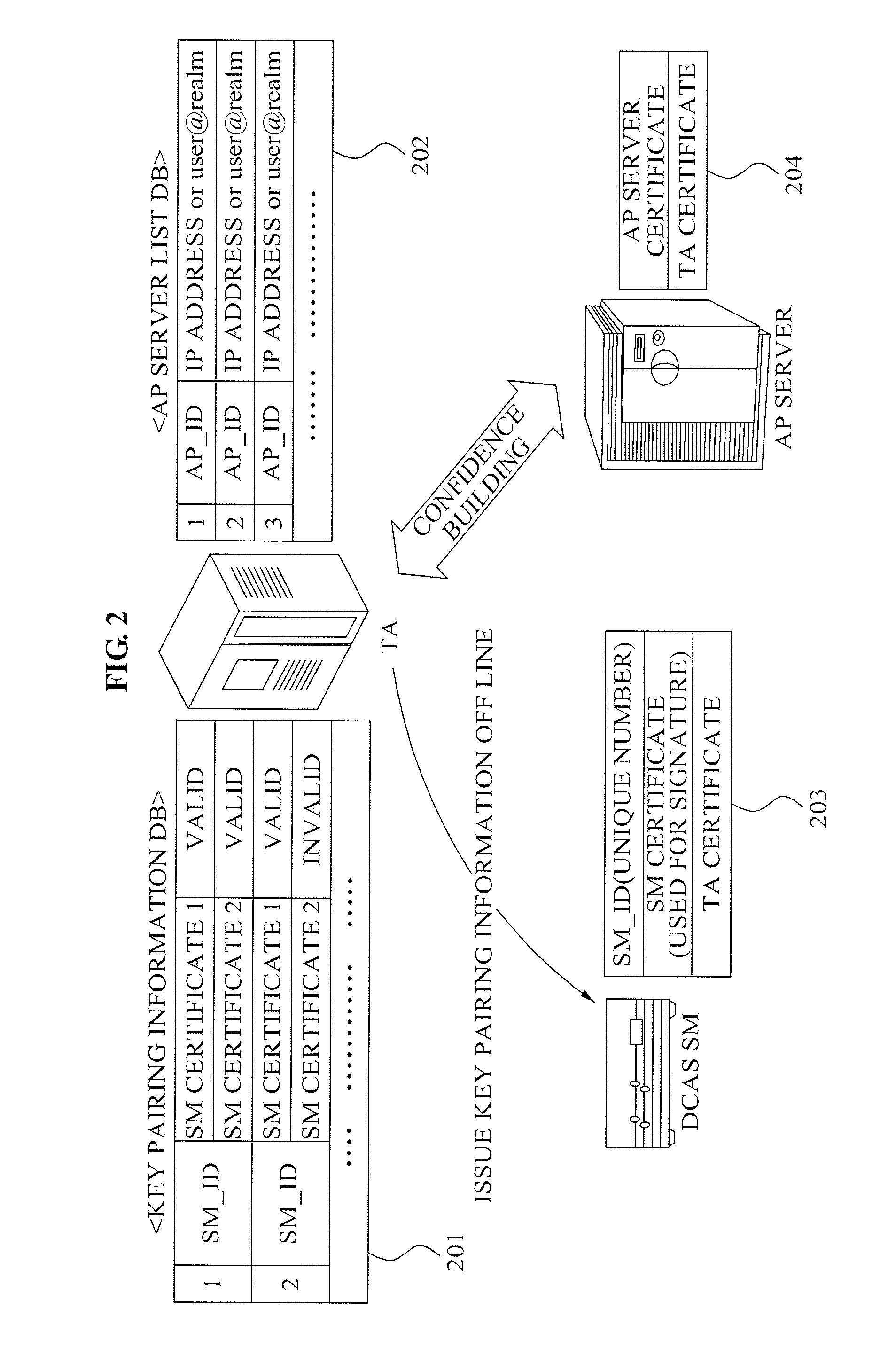
Mutual authentication apparatus and method in downloadable conditional access system
InactiveUS20100161966A1Key distribution for secure communicationUser identity/authority verificationTrusted authorityDownloadable Conditional Access System
A mutual authentication method in a Downloadable Conditional Access System (DCAS) is provided. The mutual authentication method may receive authentication-related information about authentication between an authentication unit and a security module (SM) from a Trusted Authority (TA), generate an authentication session key using the authentication-related information, transmit the authentication session key by the authentication unit to the SM through a Cable Modem Termination System (CMTS), and control a Conditional Access System (CAS) software to be downloaded to the SM from the authentication unit, when the authentication is completed by the authentication session key.
Owner:ELECTRONICS & TELECOMM RES INST
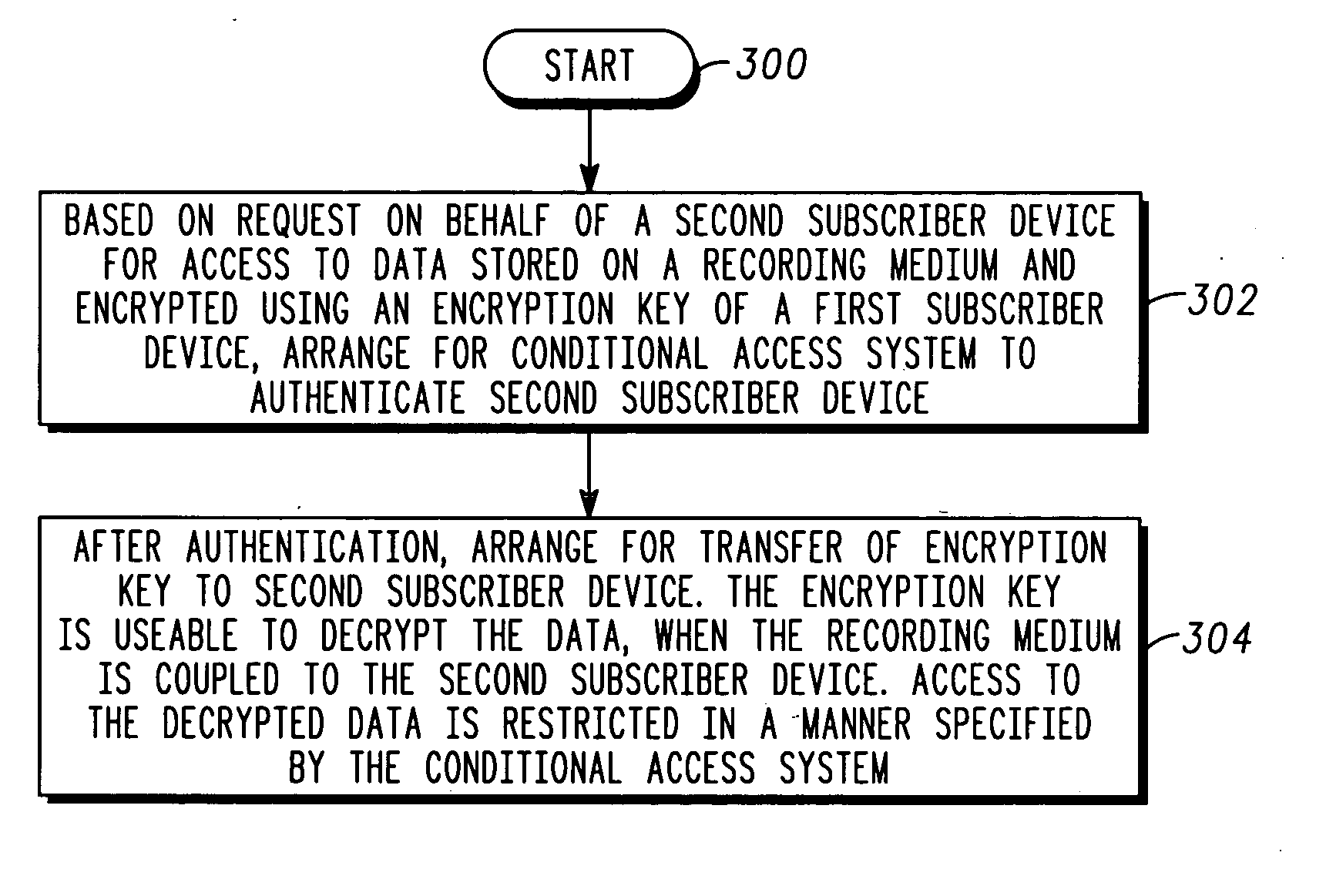
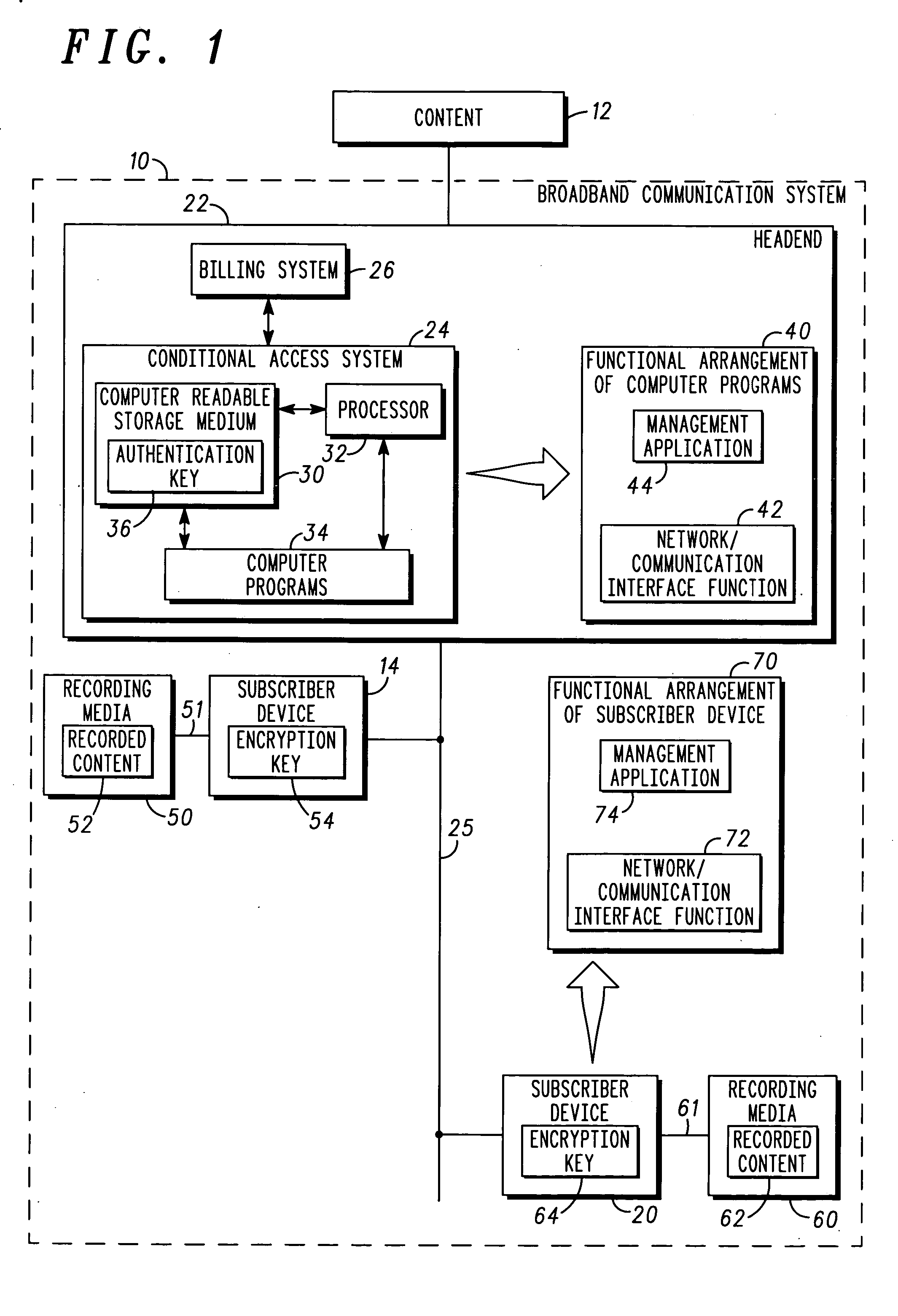
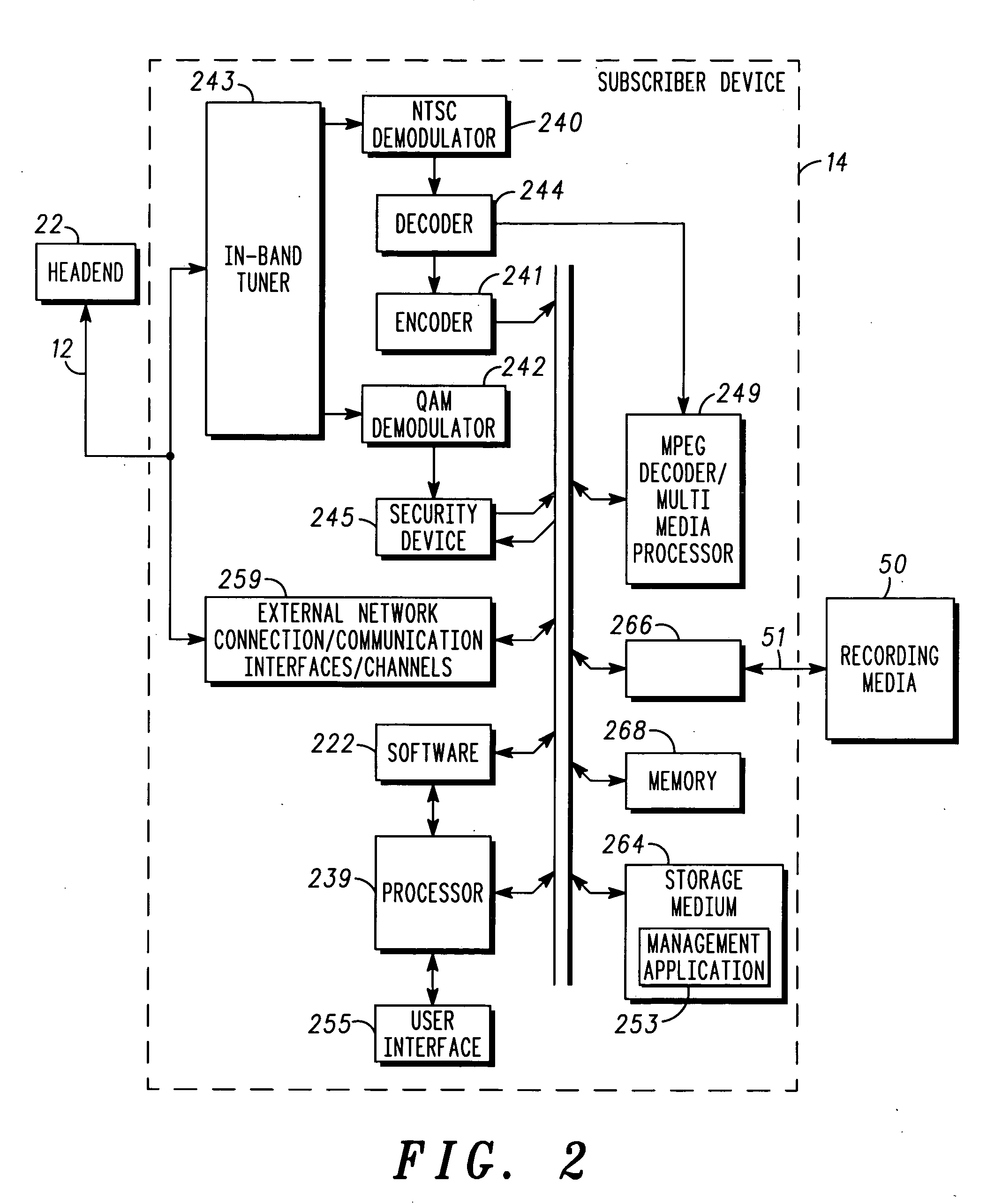
Method and apparatus for providing conditional access to recorded data within a broadband communication system
InactiveUS20050210500A1Analogue secracy/subscription systemsTwo-way working systemsComputer hardwareConditional access systems
A method (300) for providing conditional access to data. A conditional access system (24) is responsive to subscriber devices (14, 20), and the data (52) is stored on a recording medium (50) and encrypted using an encryption key (54) when the recording medium (50) is detachably coupled to a first subscriber device (14). The method includes: based on a request on behalf of a second subscriber device for access to the data, arranging (302) for the conditional access system to authenticate the second subscriber device; and arranging (304) for the conditional access system to transfer the encryption key to the second subscriber device. The encryption key is usable by the second subscriber device to decrypt the data when the recording medium is detachably coupled thereto, and access to the decrypted data by the second subscriber device is restricted in a manner specified by the conditional access system.
Owner:GENERAL INSTR CORP
Processing recordable content in a stream
ActiveUS20110010545A1Fast dynamic changeQuick changeDigital data processing detailsUser identity/authority verificationComputer networkConditional access systems
Methods and a systems are described for processing recordable content in a broadcast stream sent to a receiver, wherein said broadcast stream is protected in accordance with a conditional access system and wherein said receiver is configured for storing and consuming content in said broadcast stream in accordance with a digital rights management system. In this methods and systems recording information is sent in one or more entitlement control messages over a broadcast network to a receiver. Using the recording information in the entitlement control messages the receiver is able to store recordable events in a broadcast stream on a storage medium and to consume said recorded events in accordance with a digital rights management system.
Owner:IRDETO ACCESS
Apparatus and method for dynamic update of software-based IPTV conditional access system
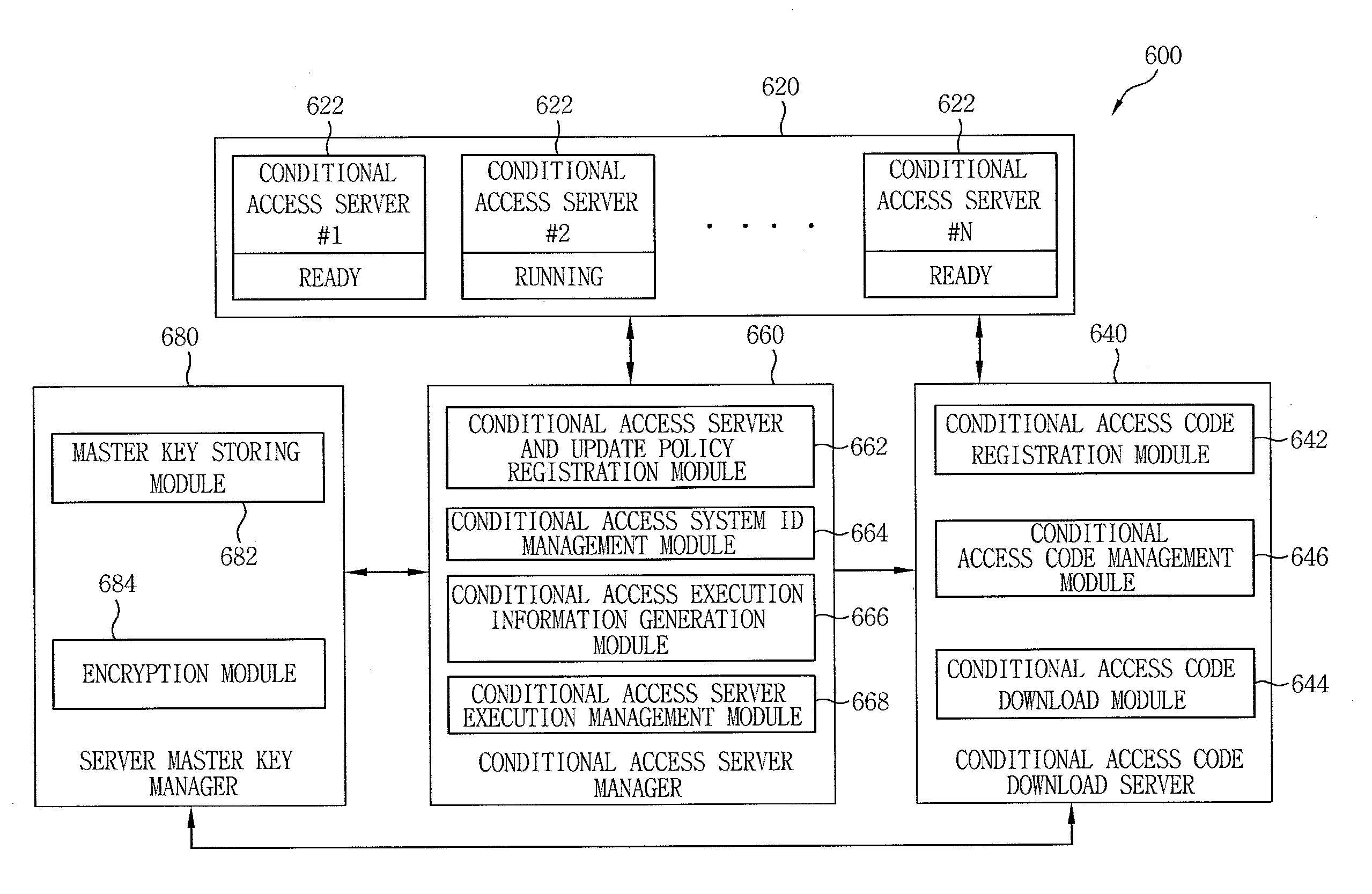
ActiveUS20110131413A1Improve securityAvoid risk of leakageDigital data processing detailsUser identity/authority verificationConditional access systemsMultiple criteria
The apparatus for dynamic update of a software-based IPTV conditional access system includes: a server master key manager managing a master key and encrypting a conditional access code ID; a conditional access server manager generating and managing a server list, linking and storing an update policy with the conditional access server IDs included in the server list, and controlling execution of the conditional access server; and a conditional access code download server generating an ID map of set of conditional access codes by combining the plurality of conditional access codes and the plurality of conditional access code IDs that are encrypted, and transmitting the ID map of set of conditional access codes and the conditional access code to a receiver.
Owner:ELECTRONICS & TELECOMM RES INST
Device pairing
InactiveUS8213613B2Increased flexibility of useEasy to provideAnalogue secracy/subscription systemsDigital data protectionConditional access systemsDevice status
Owner:THOMSON LICENSING SA
Method and apparatus of mutual authentication and key distribution for downloadable conditional access system in digital cable broadcasting network
InactiveUS20090144541A1Increase costIncrease in costUser identity/authority verificationProgram loading/initiatingDownloadable Conditional Access SystemConditional access systems
A method and apparatus of X.509 certificate-based mutual authentication and key distribution for a Downloadable Conditional Access System (DCAS) in a digital cable broadcasting network is provided for composing a software-based secure DCAS in various Conditional Access Systems (CASs) based on an embodiment form of Conditional Access (CA) application for CA of digital cable broadcasting.
Owner:ELECTRONICS & TELECOMM RES INST
Key distribution in a conditional access system
InactiveUS20040120529A1Reducing amount of information (length)Save a lotKey distribution for secure communicationUser identity/authority verificationCiphertextConditional access systems
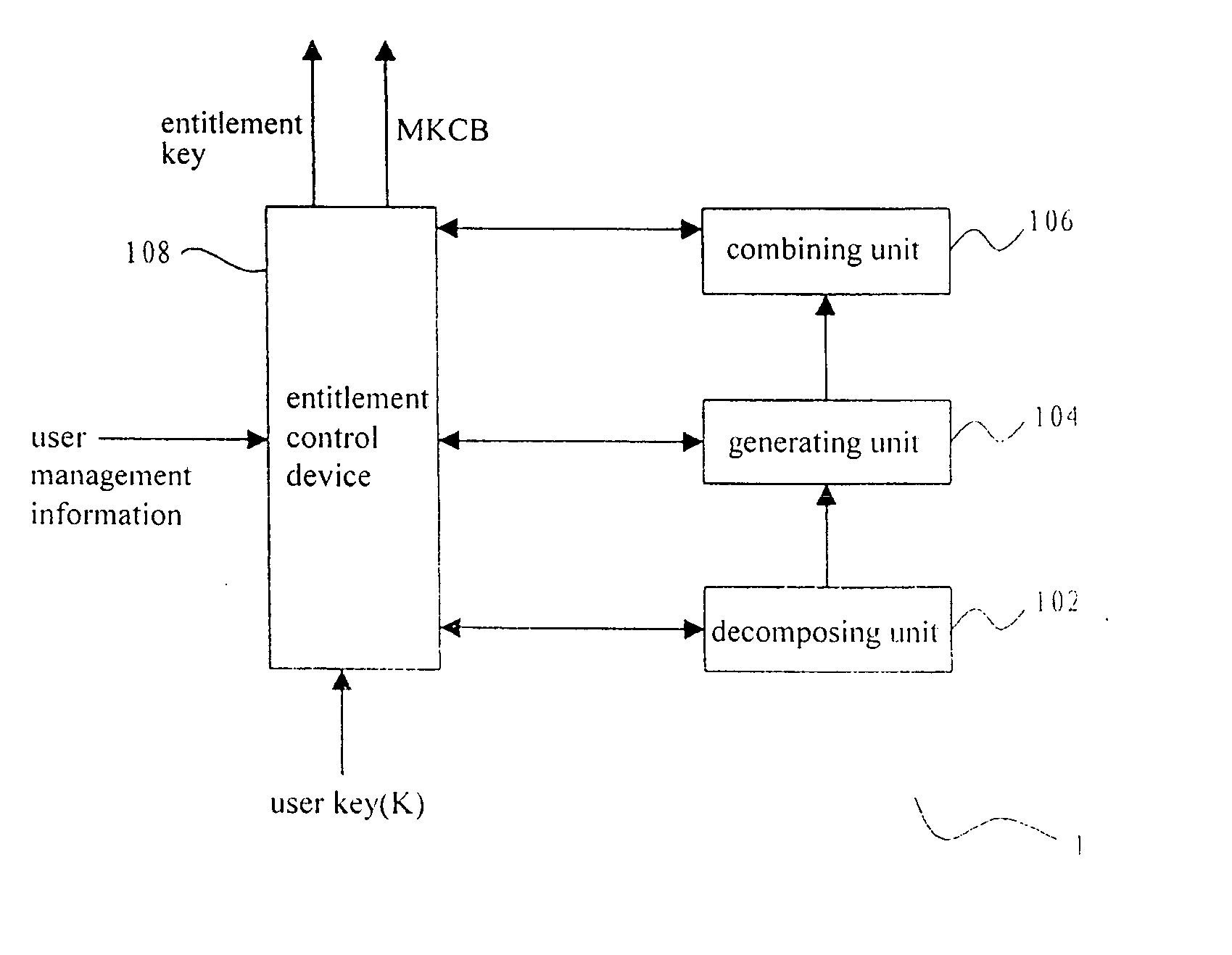
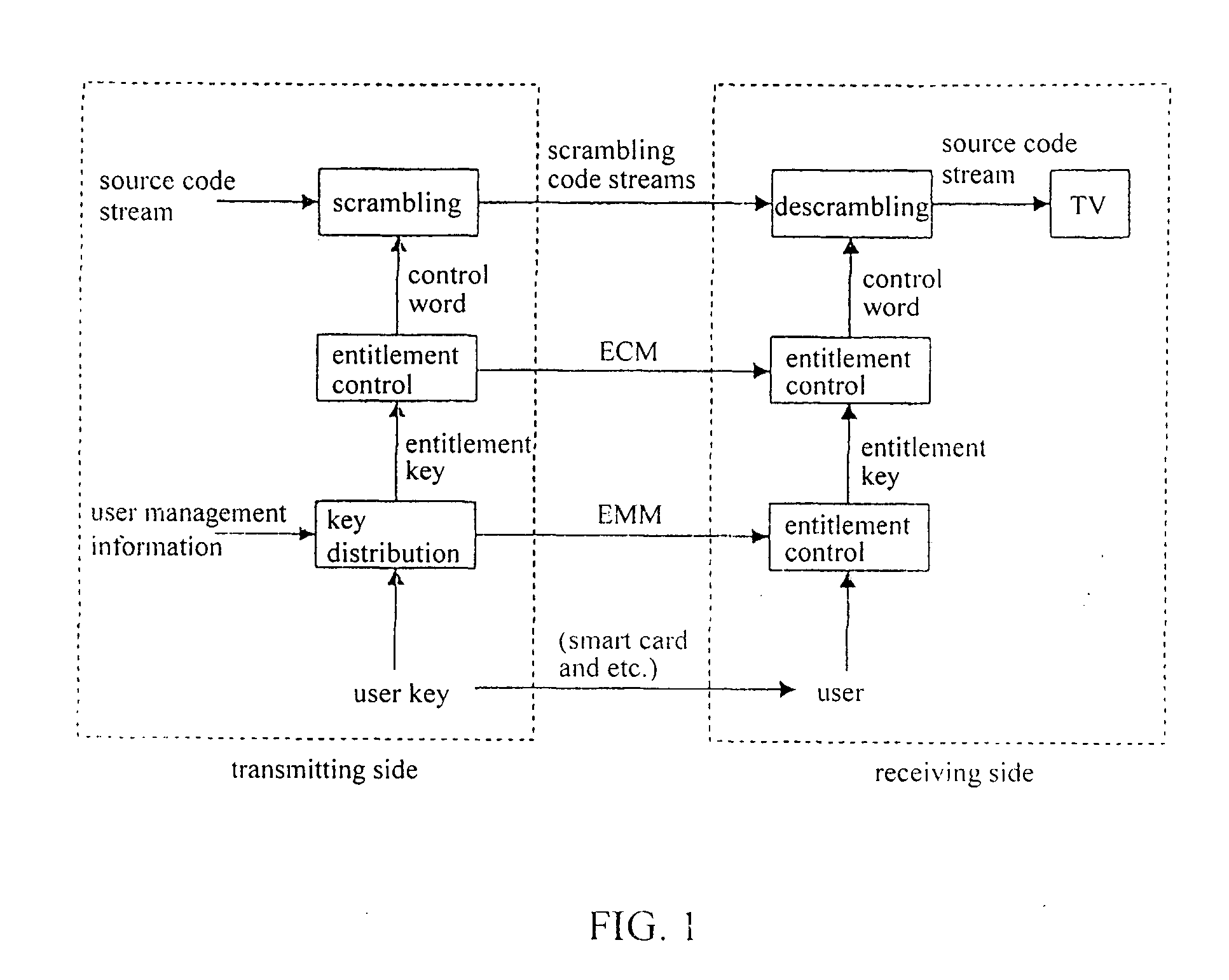
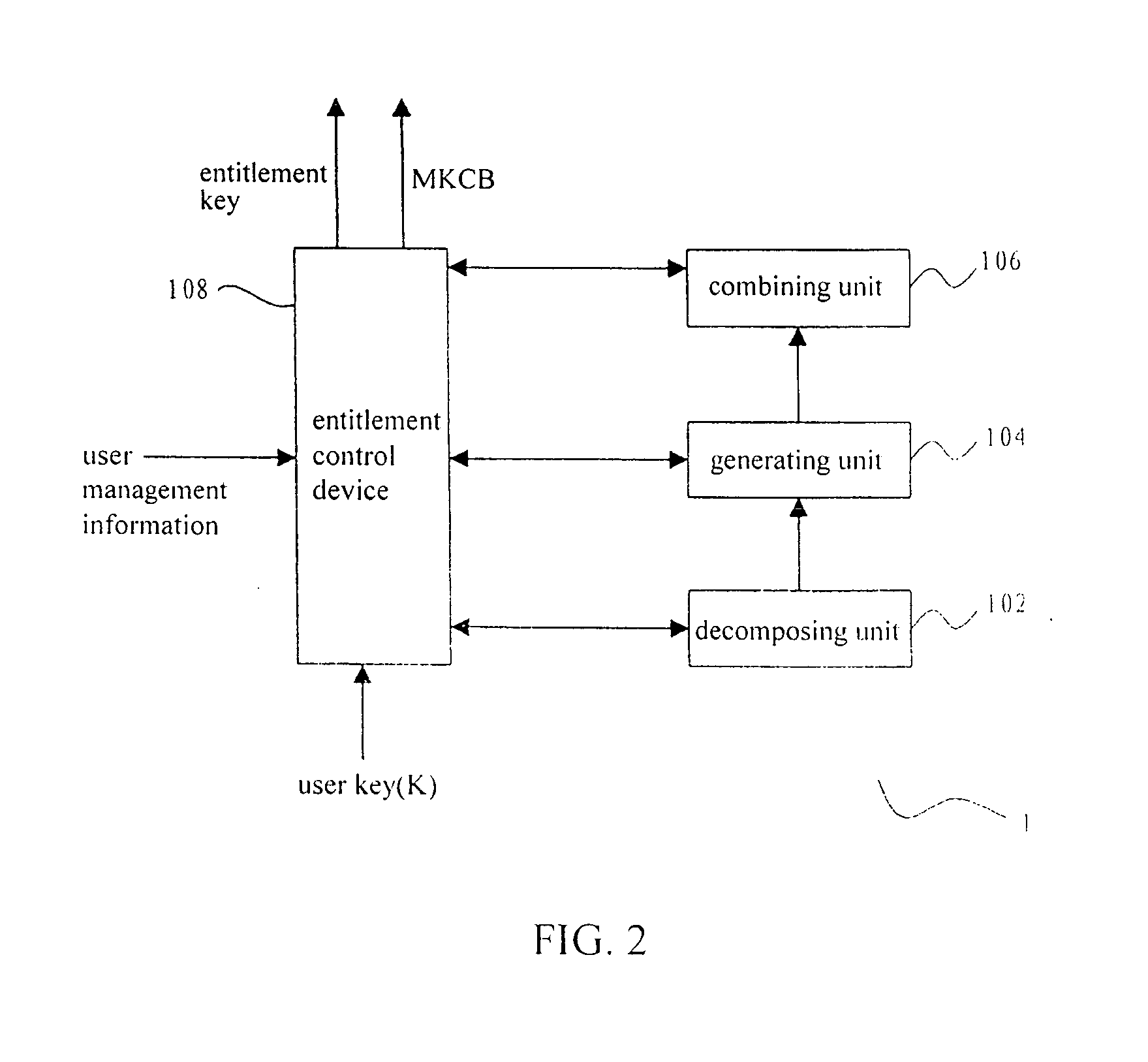
Methods and apparatus for key distribution in a conditional access system, assuming that the set of all user nodes which the system can accommodate is a complete set, and a subset is composed of all user nodes or part of user nodes. One method comprises: decomposing said subset into at least one secondary subset; assigning a different user key to each secondary subset, each said user key being transmitted to all users in a corresponding secondary subset; encrypting an entitlement key by using each said user key so as to generate a cipher text corresponding to each said secondary subset; and combining said cipher text to generate a media key control block and transmitting said media key control block to all users in said subset. Since a classification method of a binary tree and a multiple tree is used, the invention can save a lot of network resources.
Owner:IBM CORP
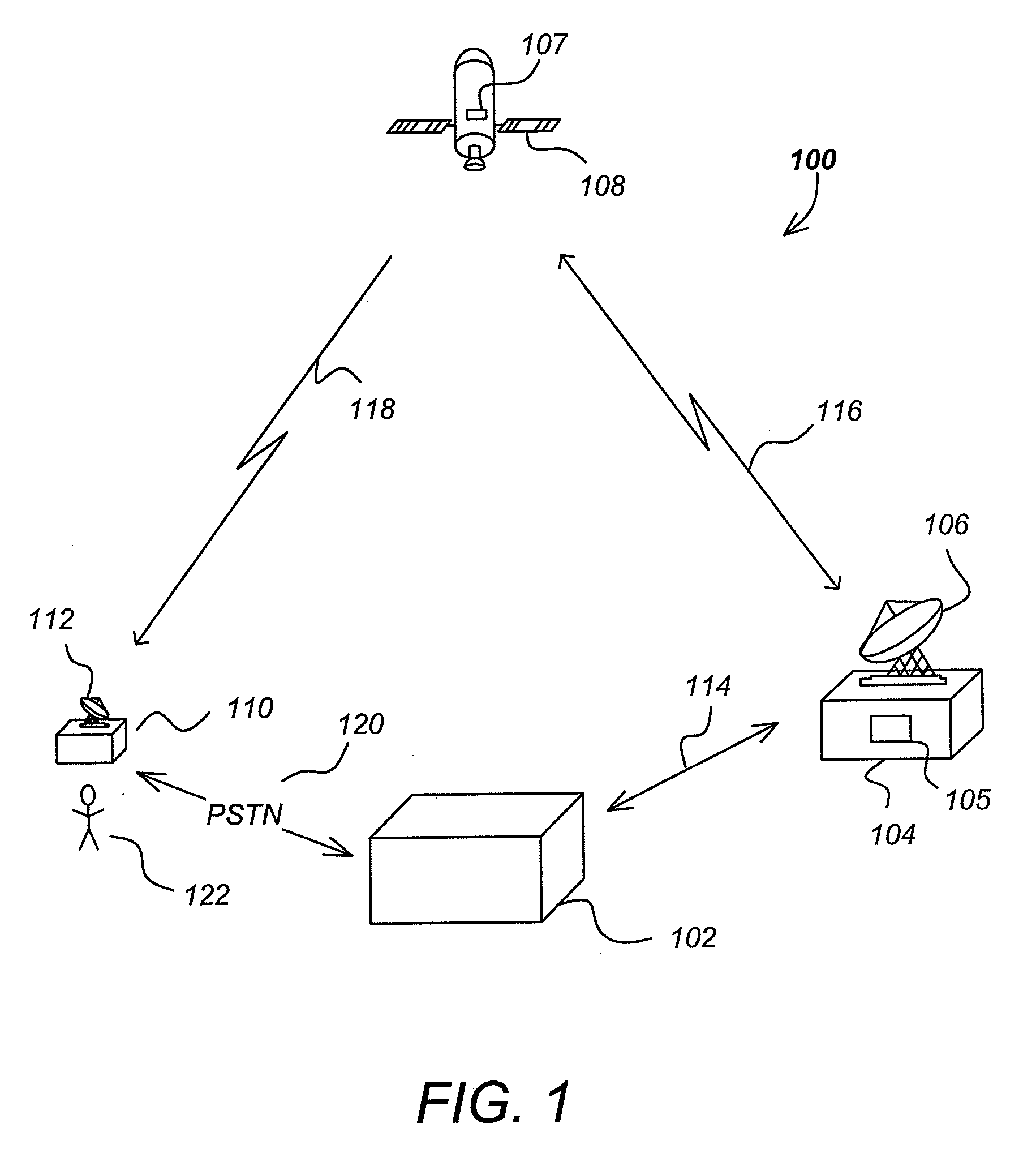
Conditional access system
InactiveUS20050201559A1Zapping can be fasterFast descramblingTelevision system detailsAnalogue secracy/subscription systemsData streamComputer network
A broadcast receiver includes a tuner / de-multiplexer 410, 420 for selectively tuning into at least one of a plurality of broadcast digital transport streams, and de-multiplex the tuned transport stream into a plurality of parallel de-multiplexed data streams in order to selectively provide at least one of de-multiplexed data streams. A de-multiplexed data stream 5 may be scrambled under control of a time-varying content key. The tuner / de-multiplexer extracts from the tuned transport stream for at least two scrambled de-multiplexed data streams a respective control word stream 510, 520, 530. Each control word represents an encrypted content key. A controller supplies control words 550 from the control word streams to the decryptor 450,560. The decryptor decrypts the control words and supplies the 10 corresponding content keys to the controller. The controller forms for each control word stream a corresponding content key stream 570, 580, 590 and stores for each content key stream at least a latest content key in a memory. The controller provides for a selected de-multiplexed data stream the corresponding content keys from the memory to a de scrambler to enable the de scrambler to descramble the data stream.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
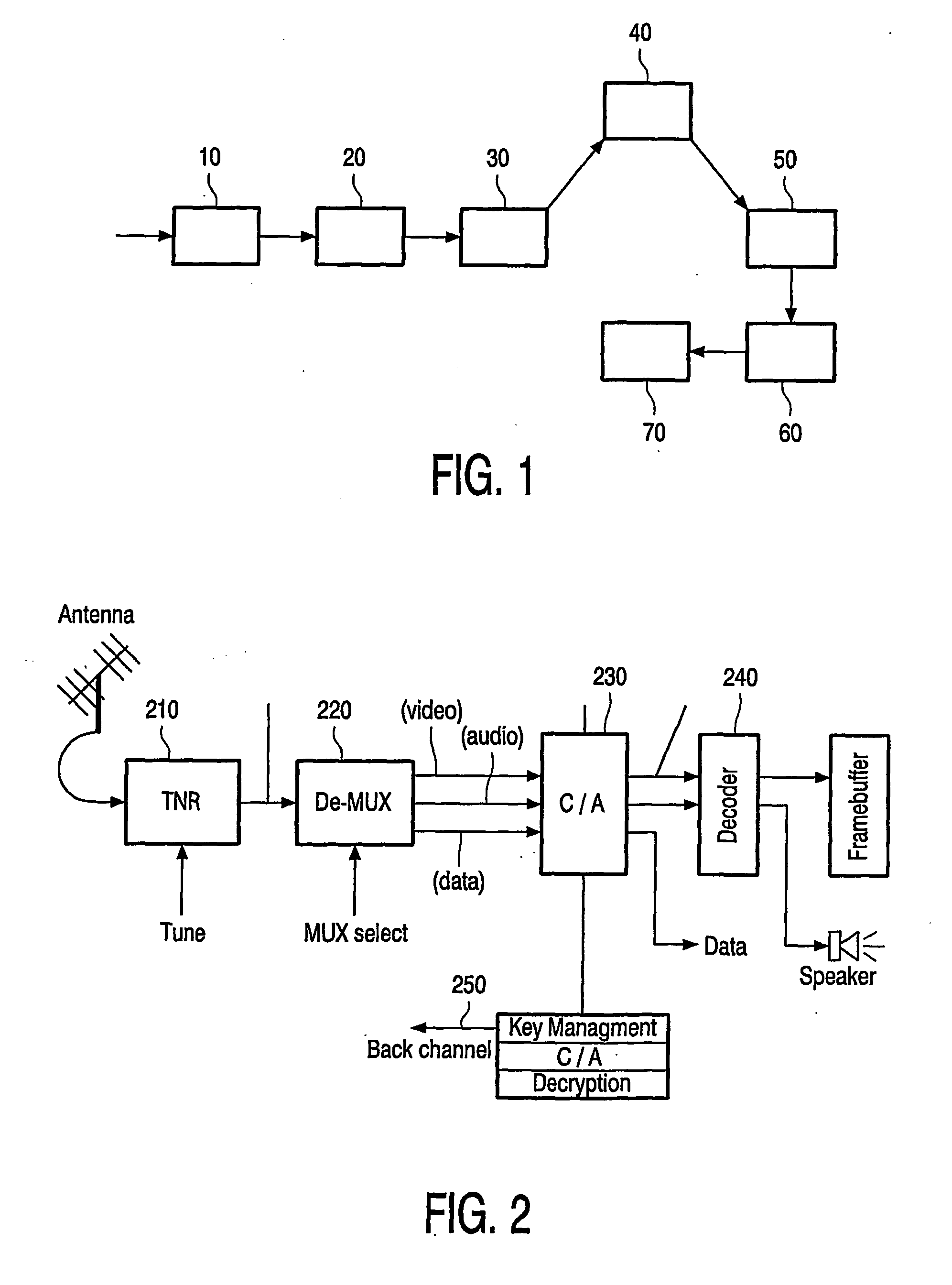
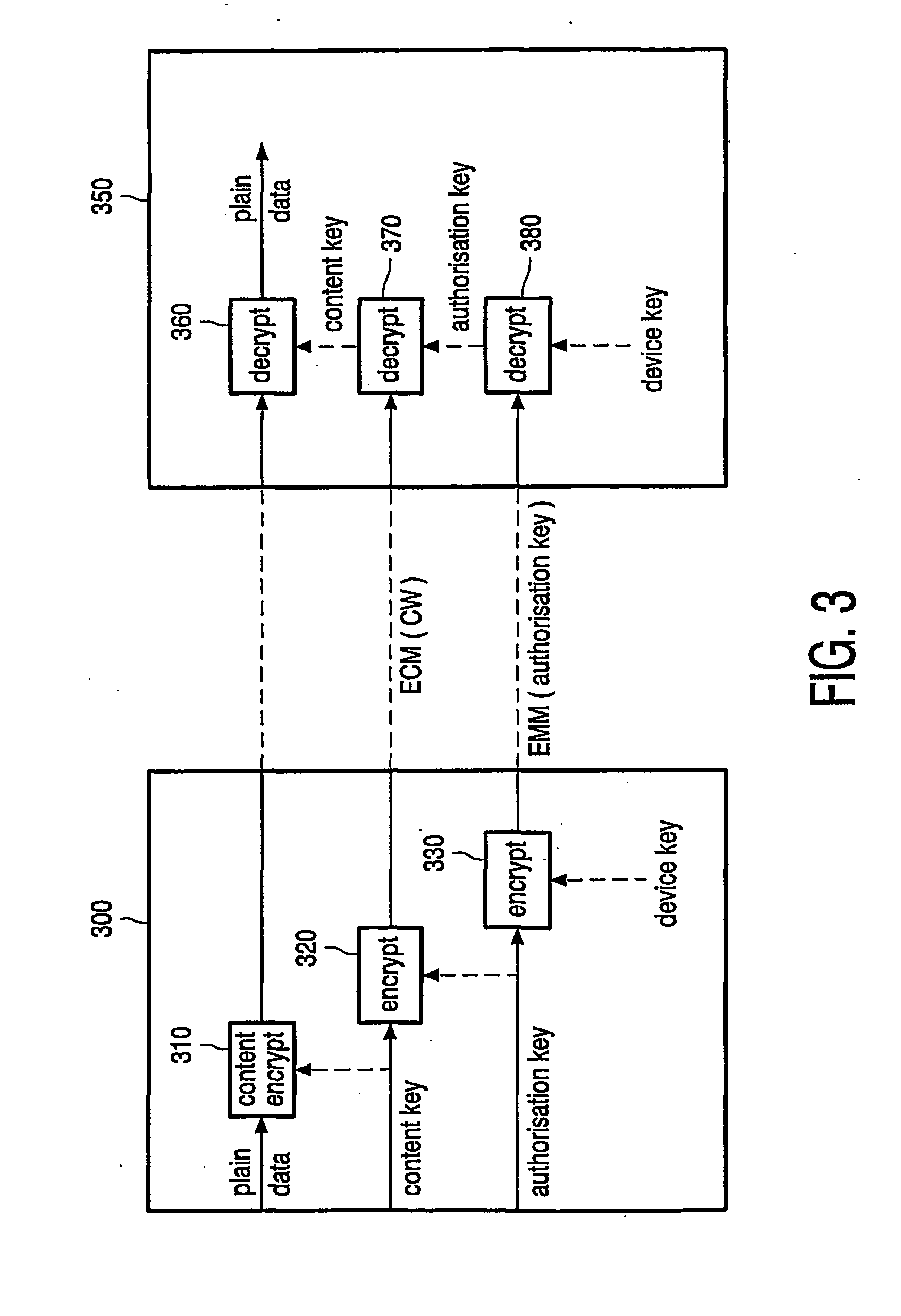
Digital media conditional access system for handling digital media content
ActiveUS20050249350A1Television systemsSelective content distributionConditional access systemsService provision
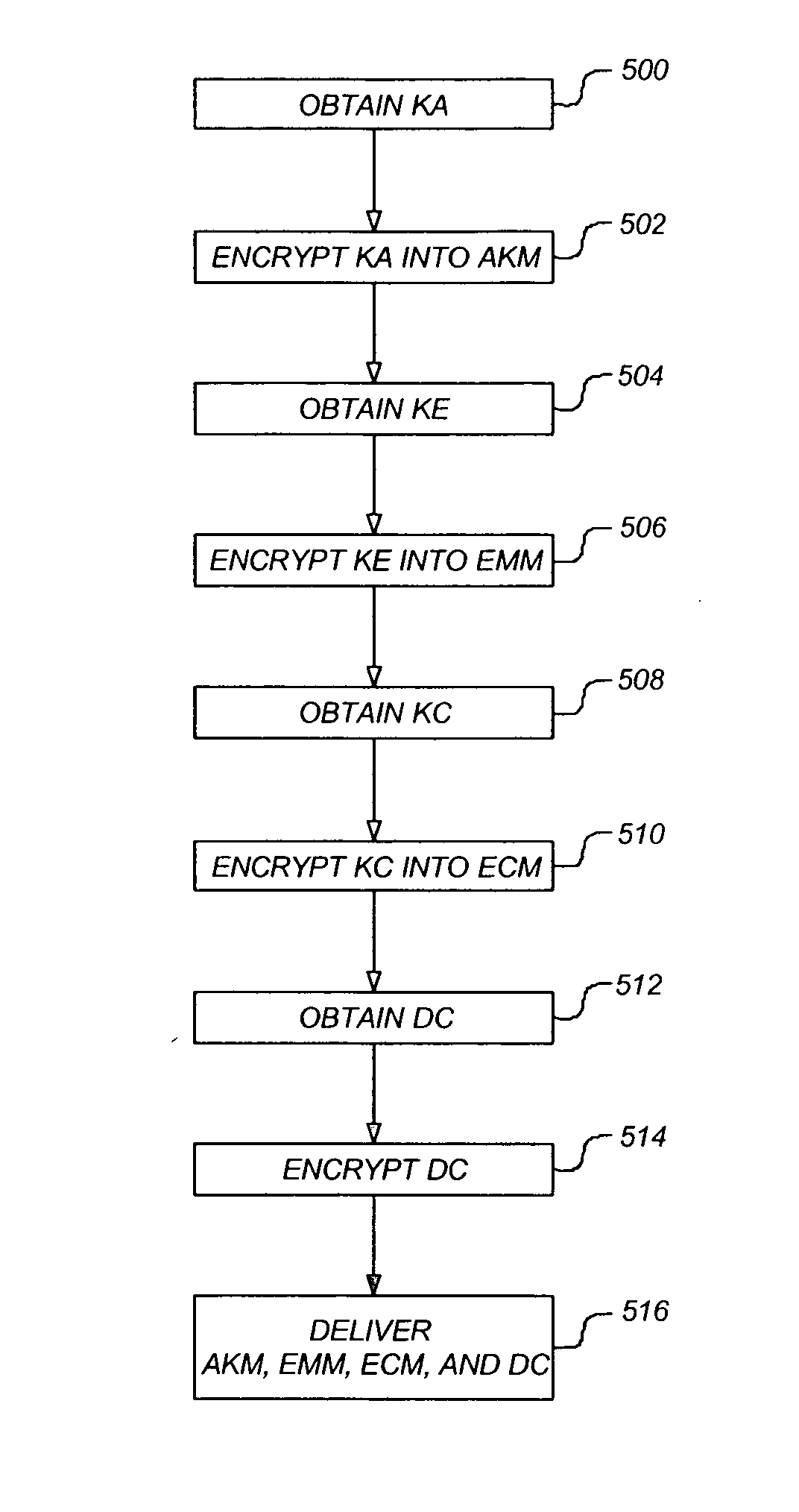
A method, apparatus, and article of manufacture provide the ability to process digital media content. A secret key (Ka) is obtained and encrypted into an authorization key message (AKM) message. One or more entitlement keys (Ke) are then obtained and encrypted using the secret key (Ka) as an encryption key into an entitlement management message (EMM). One or more media content encryption keys (Kc) are obtained and encrypted using one or more of the entitlement keys (Ke) as encryption keys into an entitlement control message (ECM). Digital media data content (Dc) is then obtained and encrypted using the one or more media content encryption keys (Kc). The AKM, EMM, ECM, and encrypted digital media data content are then delivered to a set-top box that is configured to provide digital media services with the content.
Owner:DIRECTV LLC
Access control of media services over an open network
InactiveUS20090019468A1More bandwidthStrong computing powerMultimedia data retrievalAnalogue secracy/subscription systemsConditional access systemsMaster key
To ensure that media services are only provided to those authorized users or receiving devices, various conditional access mechanisms are provided to secure that media services are only received in those authorized. Different from a prior art conditional access system, an entitlement control message containing a master key can be sent directly to an ordering box. Depending on implementation, a secure session may be established between a server and an ordering box, such that all secured information including a master key may be transported. Further an ordering box does not need to possess a key or keys needed to decrypt an entitlement control message, such key(s) may be transported from time to time in a secure session established between the server and the ordering box.
Owner:VUDU
Apparatus, method and system for providing a broadcasting service in a digital broadcasting system with a single frequency network
InactiveUS20060233359A1Key distribution for secure communicationPublic key for secure communicationConditional access systemsDigital broadcasting
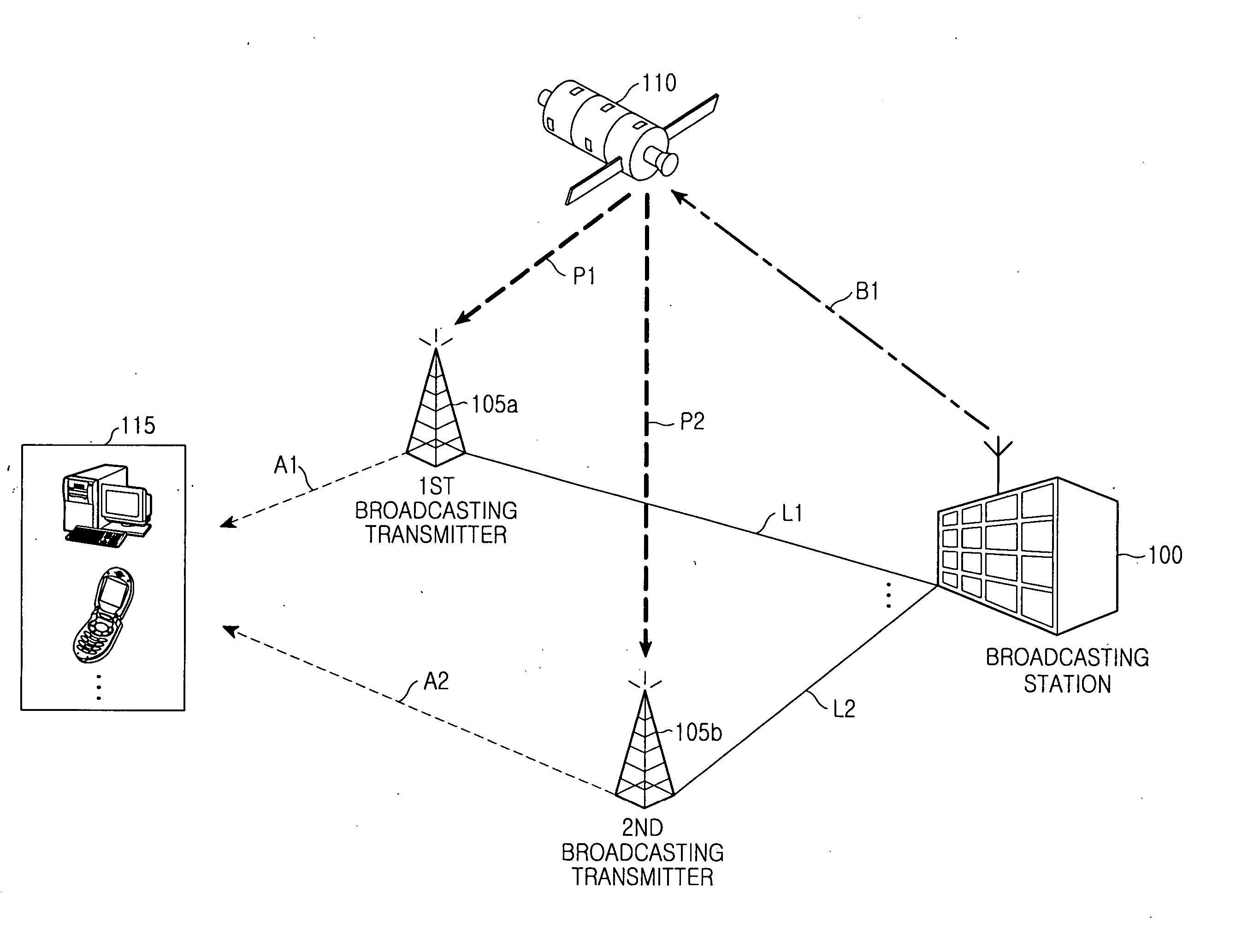
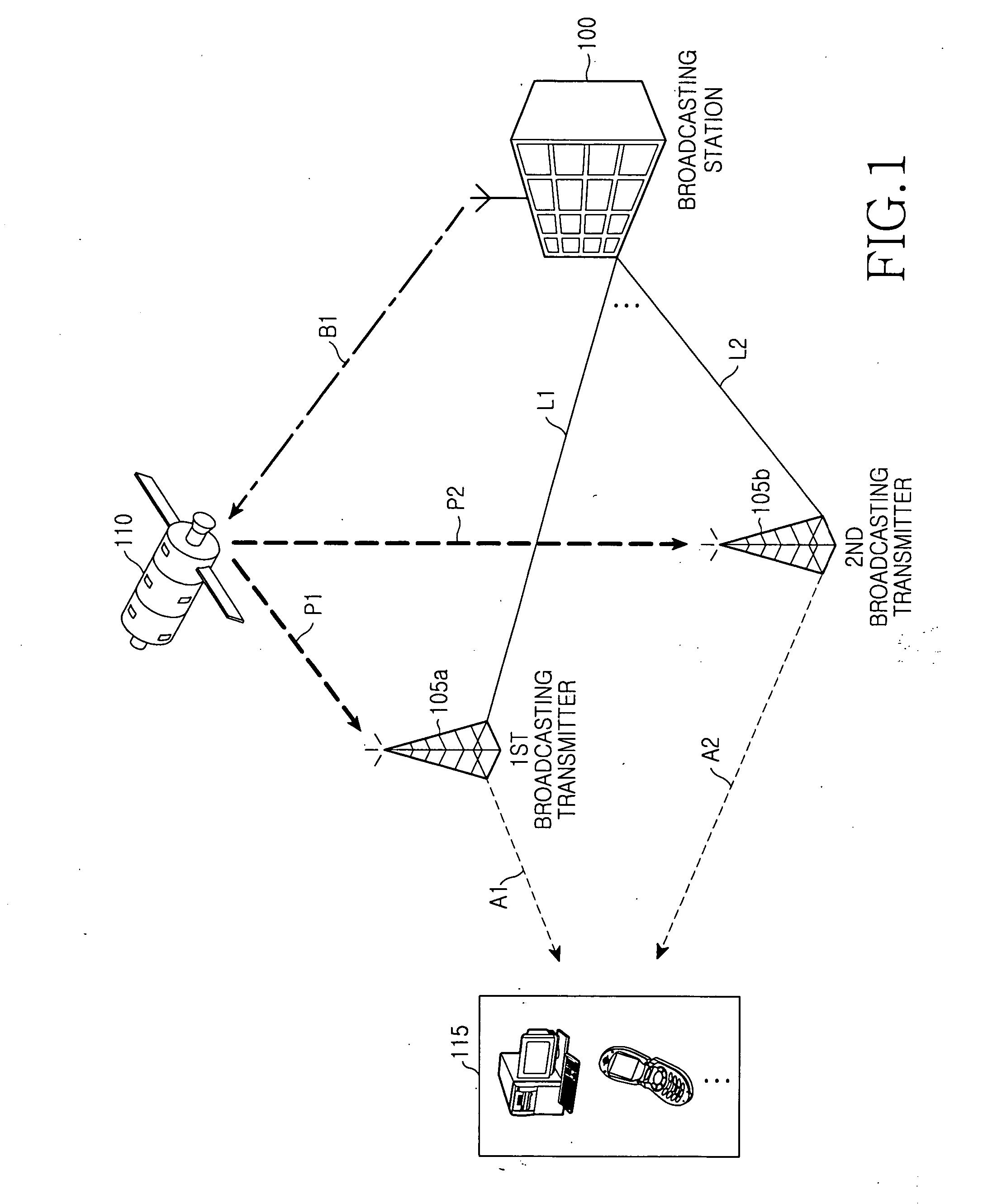
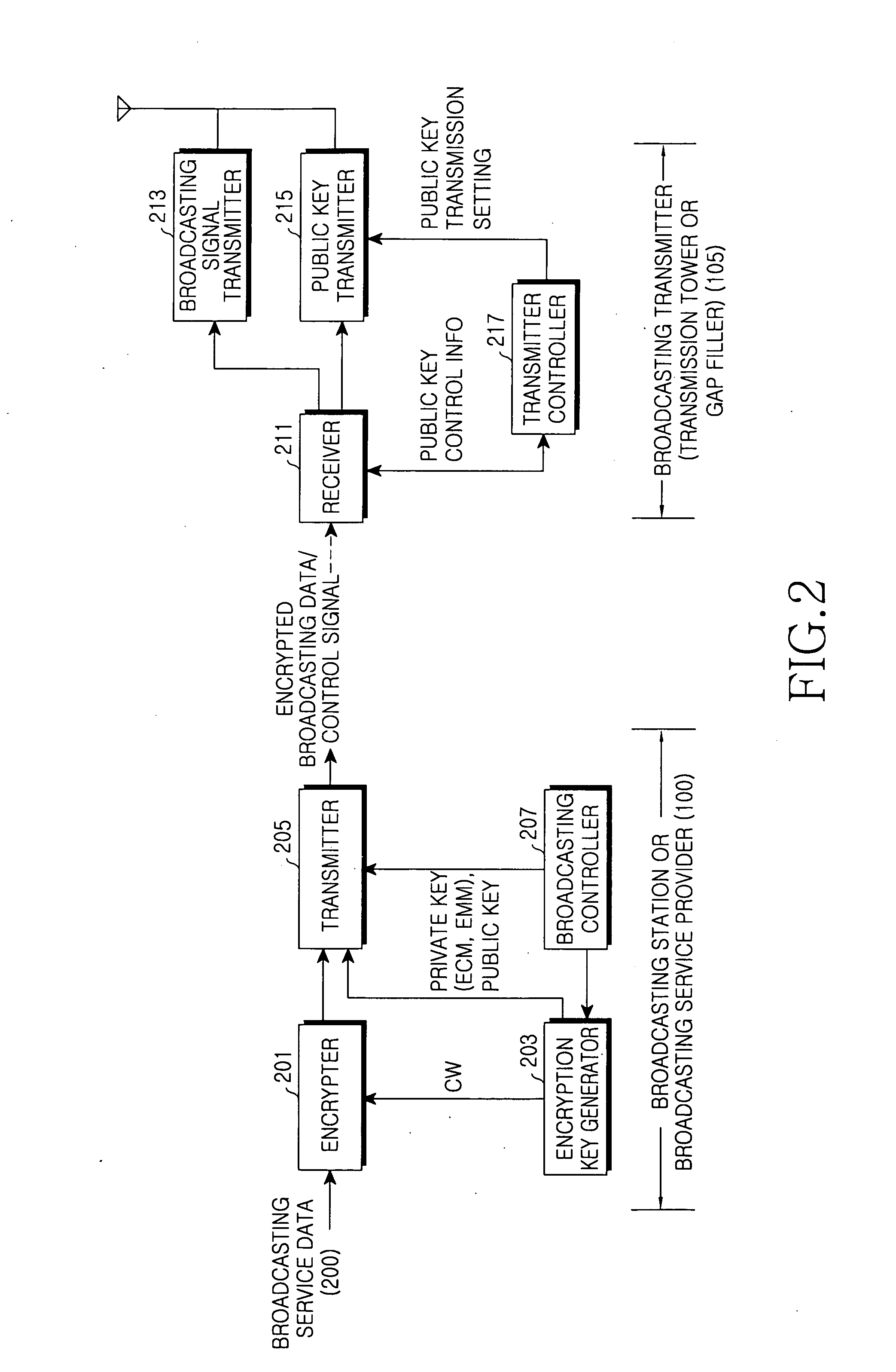
An apparatus, method, and system for providing a broadcasting service in a Digital Multimedia Broadcasting (DMB) system with a Single Frequency Network (SFN). Networks of shadow and non-shadow regions can be distinguished in the digital broadcasting system. A conditional access system can be used in the shadow region. A terminal can select a service network. A broadcasting providing server encrypts broadcasting service data, generates private and public keys into which predetermined encryption keys are divided to decrypt the encrypted broadcasting service data, sets at least one broadcasting transmitter for transmitting the private key and / or at least one broadcasting transmitter for transmitting the public key, and provides the encryption keys along with the encrypted broadcasting service data. Broadcasting transmitters transmit the encrypted broadcasting service data received from the broadcasting providing server and the private key using the SFN. At least one of the broadcasting transmitters further transmits the public key.
Owner:SAMSUNG ELECTRONICS CO LTD
Service activation of set-top box functionality using broadcast conditional access system
InactiveUS20090172722A1Analogue secracy/subscription systemsSelective content distributionConditional access systemsBiological activation
Owner:THE DIRECTV GRP INC
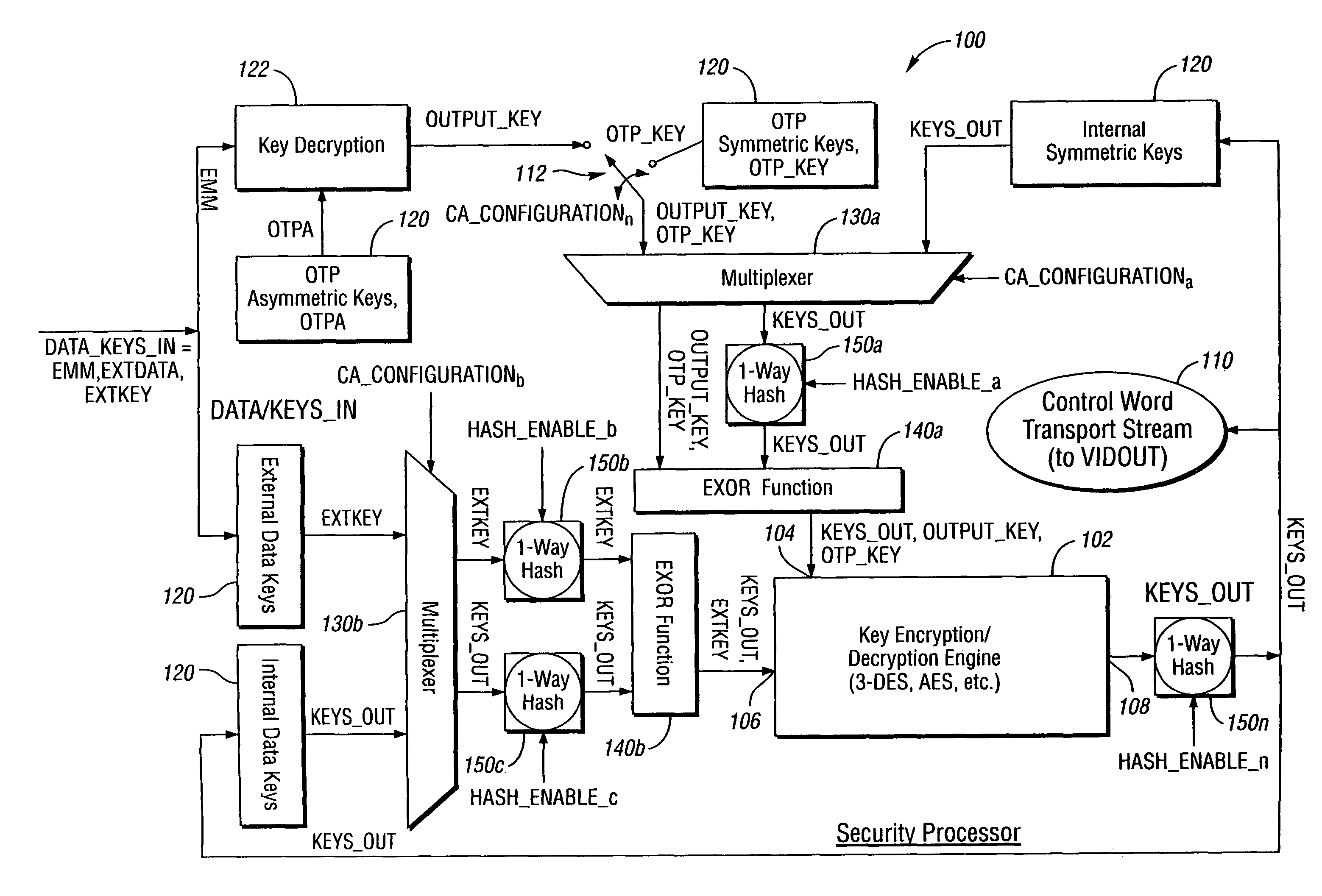
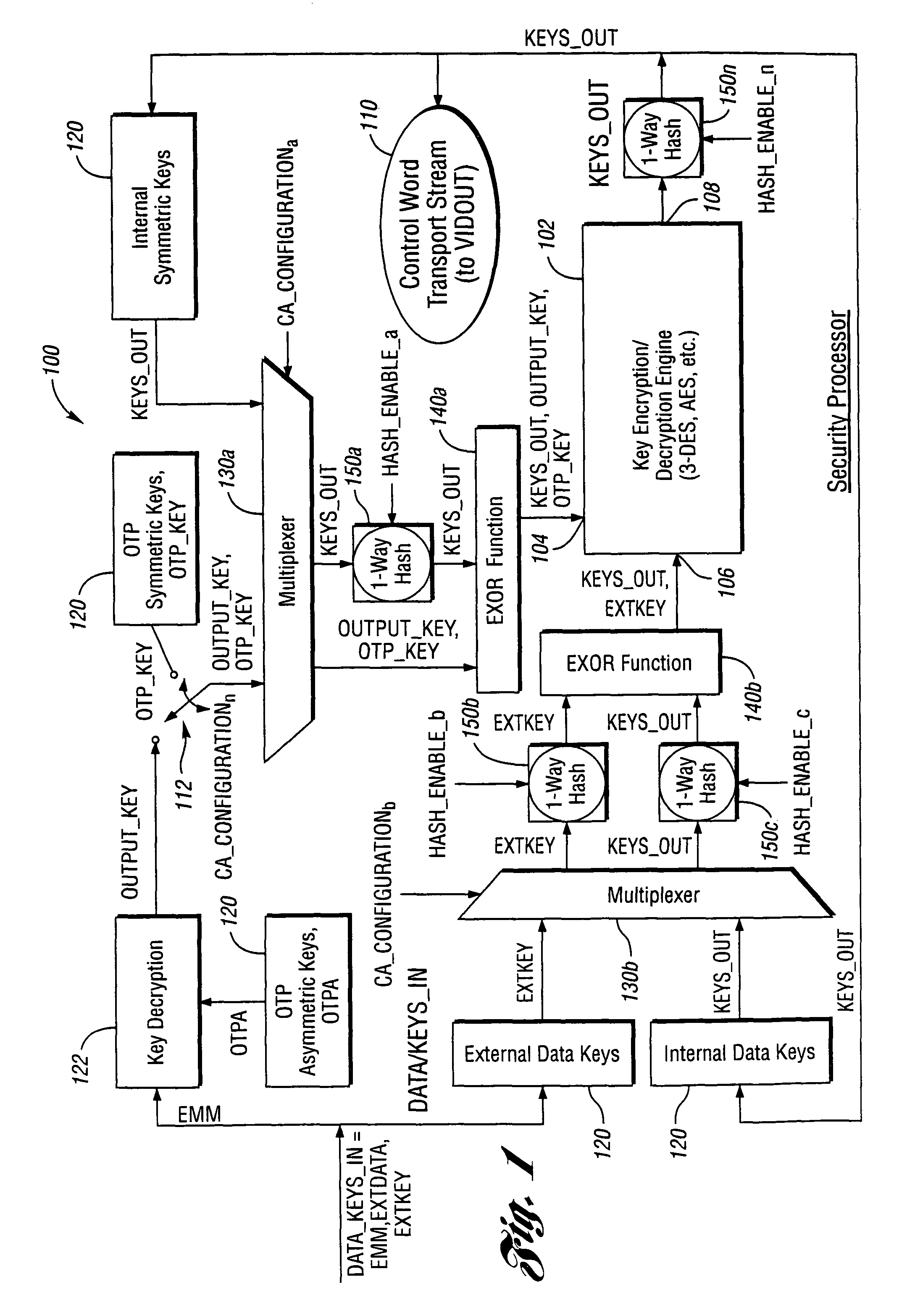
System and method for a variable key ladder
ActiveUS7933410B2Extend the life cycleDigital data processing detailsAnalogue secracy/subscription systemsConditional access systemsNetwork connection
A method of generating encryption and decryption keys for a multiple tier, variable key ladder (VKL) hierarchy includes determining a device key based on network connection and configuration data contained in conditional access system firmware, decrypting and extracting a session or category key from an input media stream or an Entitlement Management Message using the device key, and configuring a key ladder in response to at least one Entitlement Control Message (ECM), wherein the key ladder comprises the device key and at least one of (i) a program key, (ii) the session or category key, and (iii) at least one control word.
Owner:COMCAST CABLE COMM LLC
Conditional access system and method for limiting access to content in broadcasting and receiving systems
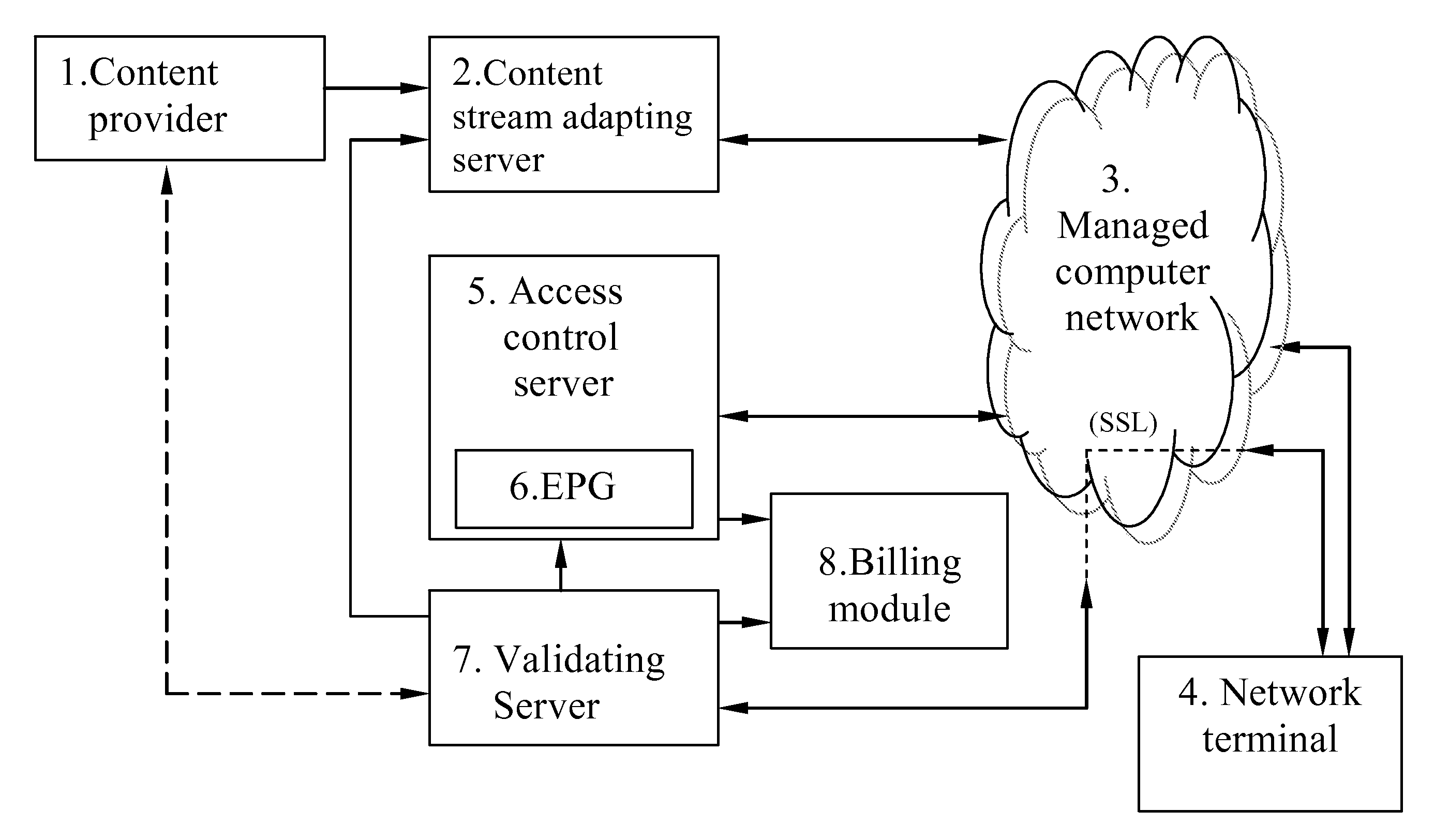
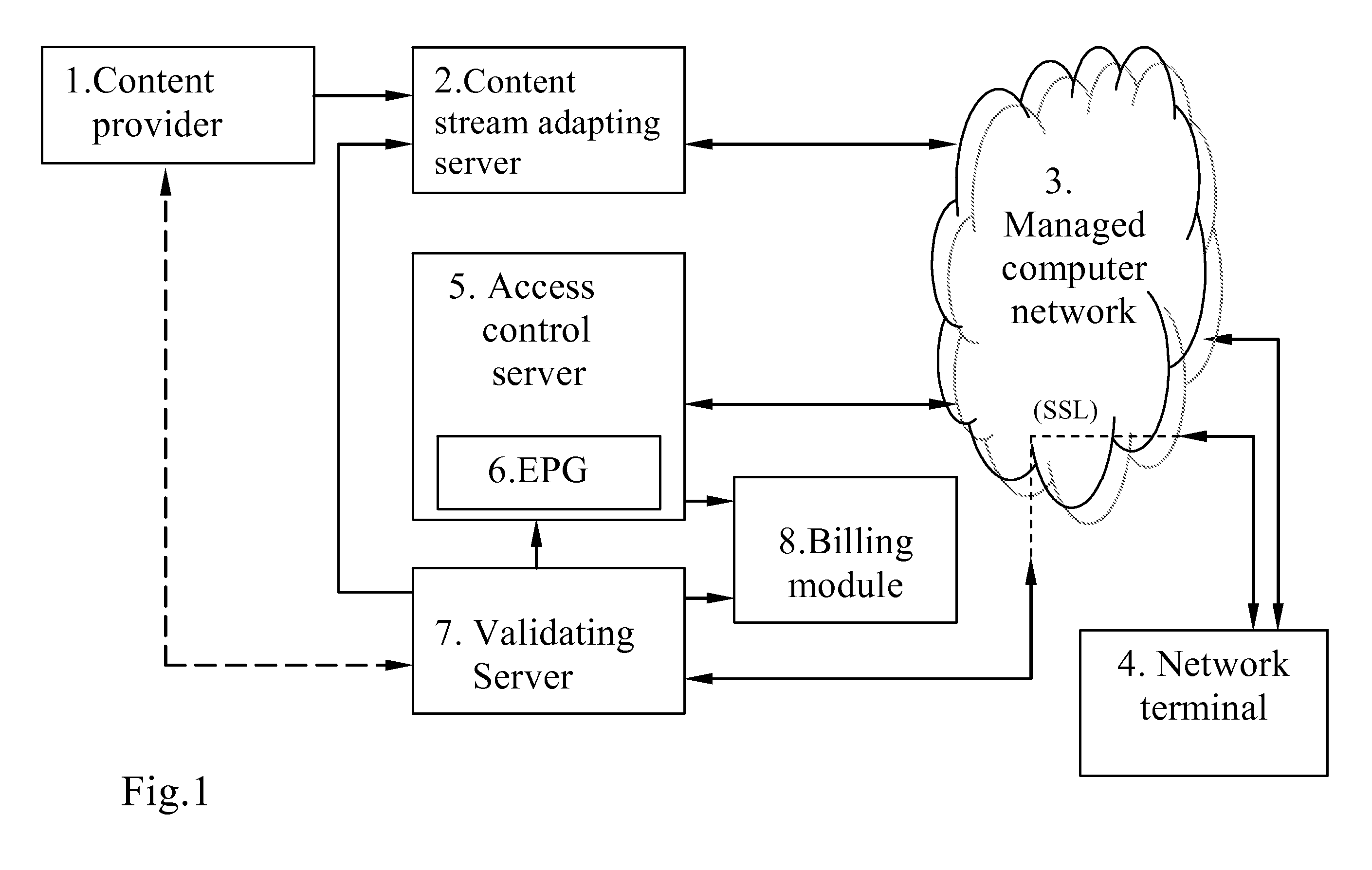
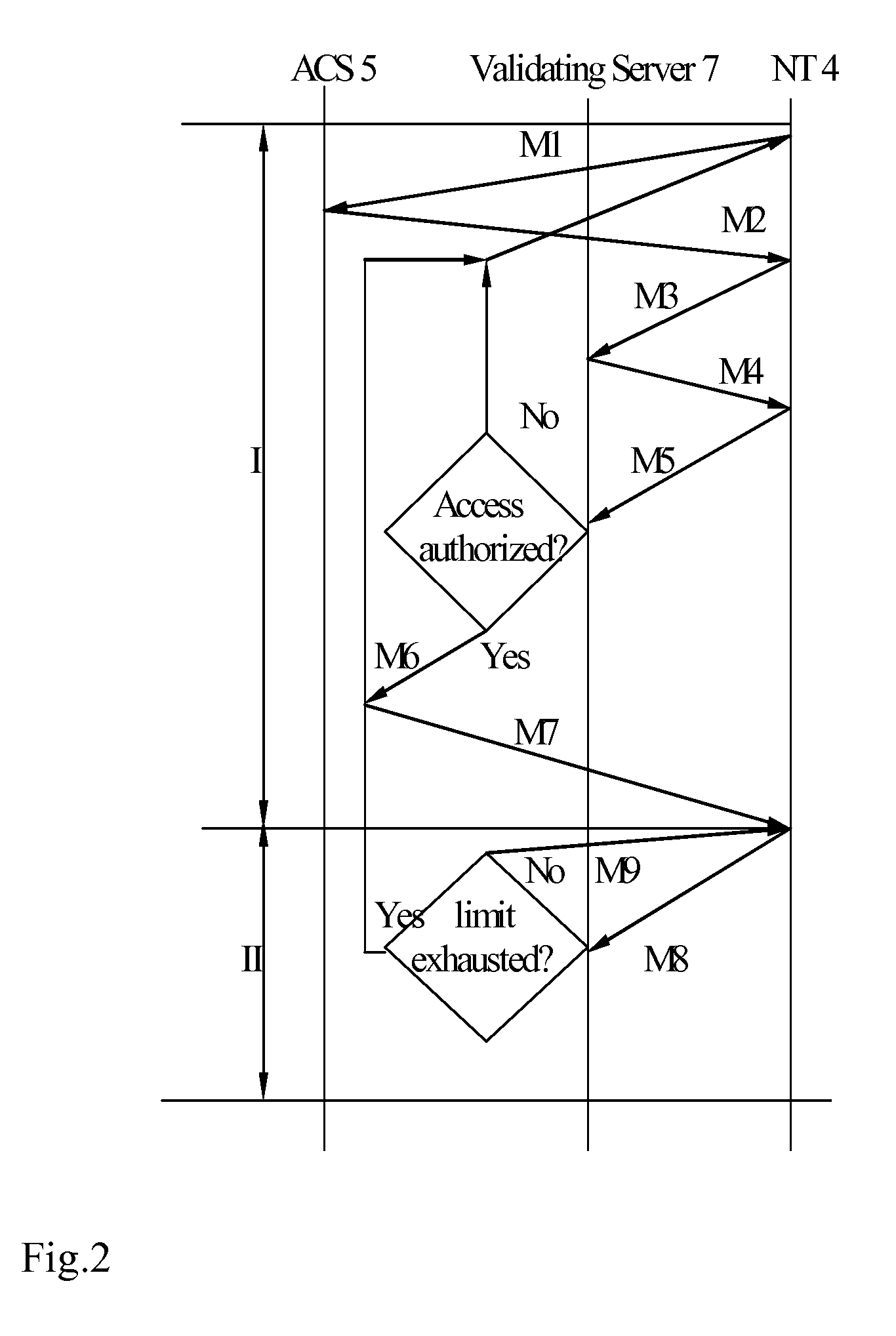
InactiveUS20100034389A1Keep full controlUser identity/authority verificationMultiple digital computer combinationsNetwork terminationIp address
A conditional access system and method provides conditional access by a subscriber's network terminal over a computer network to encrypted content of a content provider. The conditional access system includes a content stream adapting server that receives streams of encrypted content from the content provider, reformats the encrypted content streams using session keys into a format suitable for transmission by IP addressing, and assigns a unique IP address in the computer network to the reformatted encrypted content streams. An access control server provides access to the encrypted content streams under control of an operator of the computer network. A validating server provides the session keys to the content stream adapting server, receives from a subscriber a request for an encrypted content stream, validates the subscriber for access to the requested encrypted content stream and, upon validation of the subscriber, provides the subscriber's network terminal with the session keys for the selected encrypted content stream through a secure network channel and authorizes the access control server to provide access to the selected encrypted content stream by the network terminal of the subscriber. The content provider maintains control over distribution of the selected encrypted content stream through selective validation of subscribers at the validating server and may be paid directly for the selected content by the subscriber using a prepaid PIN code card issued by the content provider.
Owner:SAKHAROV OLEG VENIAMINOVICH +2
Data multiplexing device, program distribution system, program transmission system, pay broadcast system, program transmission method, conditional access system, and data reception device
InactiveUS20070143784A1Minimize device configurationPrevent overflowTelevision system detailsTime-division multiplexMultiplexingTransfer system
In a data multiplexing device which multiplexes and transmits the transport stream packets of program data consisting of a plurality of data elements constructed in the form of transport stream packets, a program distribution system, a program transmission system, a pay broadcast system, a program transmission method, a conditional access system, and a data reception device according to the present invention, by generating a scramble key Ks corresponding to one or more data elements among the plurality of data elements constituting a program and by scrambling each data element, an audience can subscribe for each data element.
Owner:SONY CORP
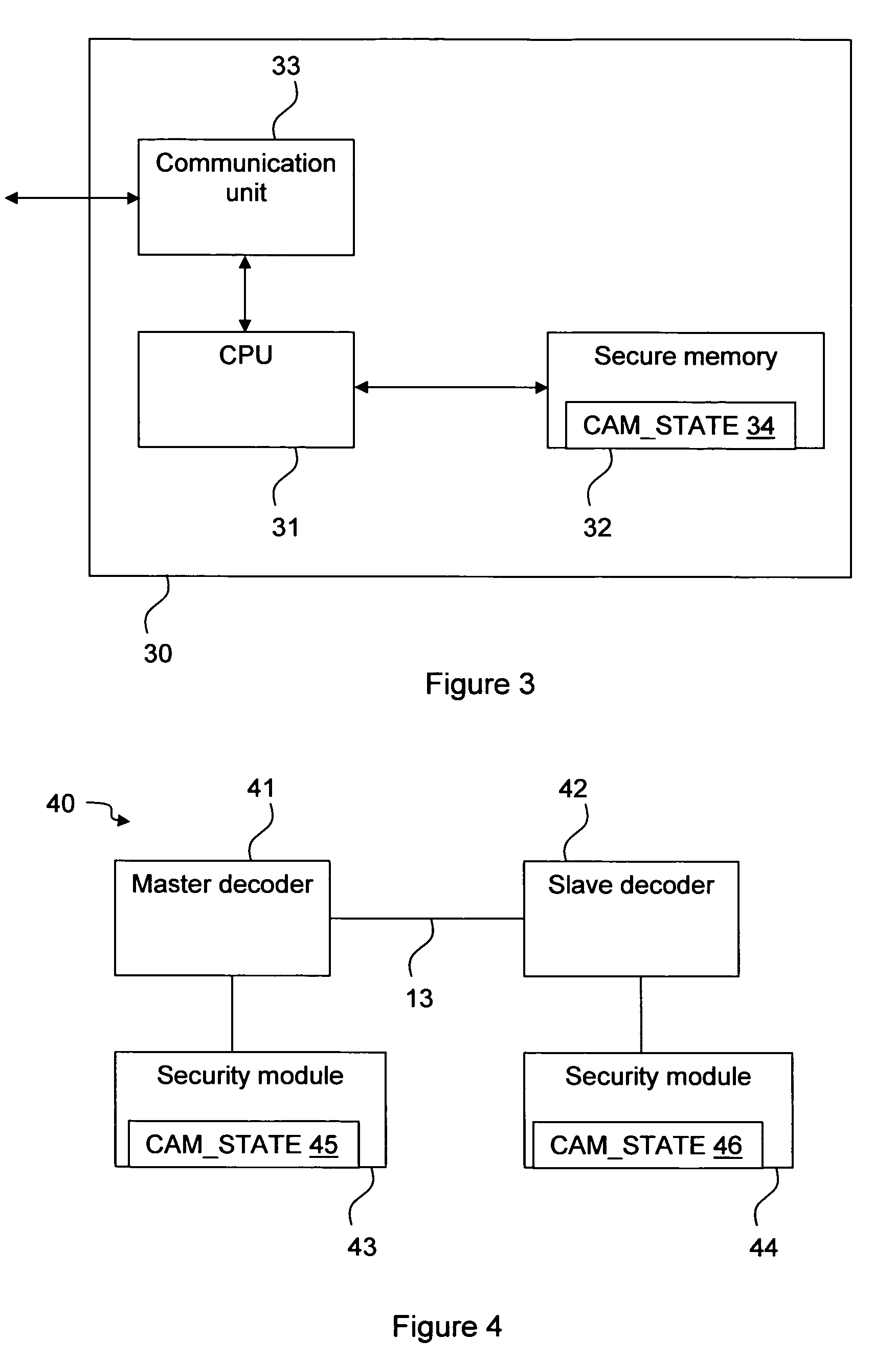
Device pairing
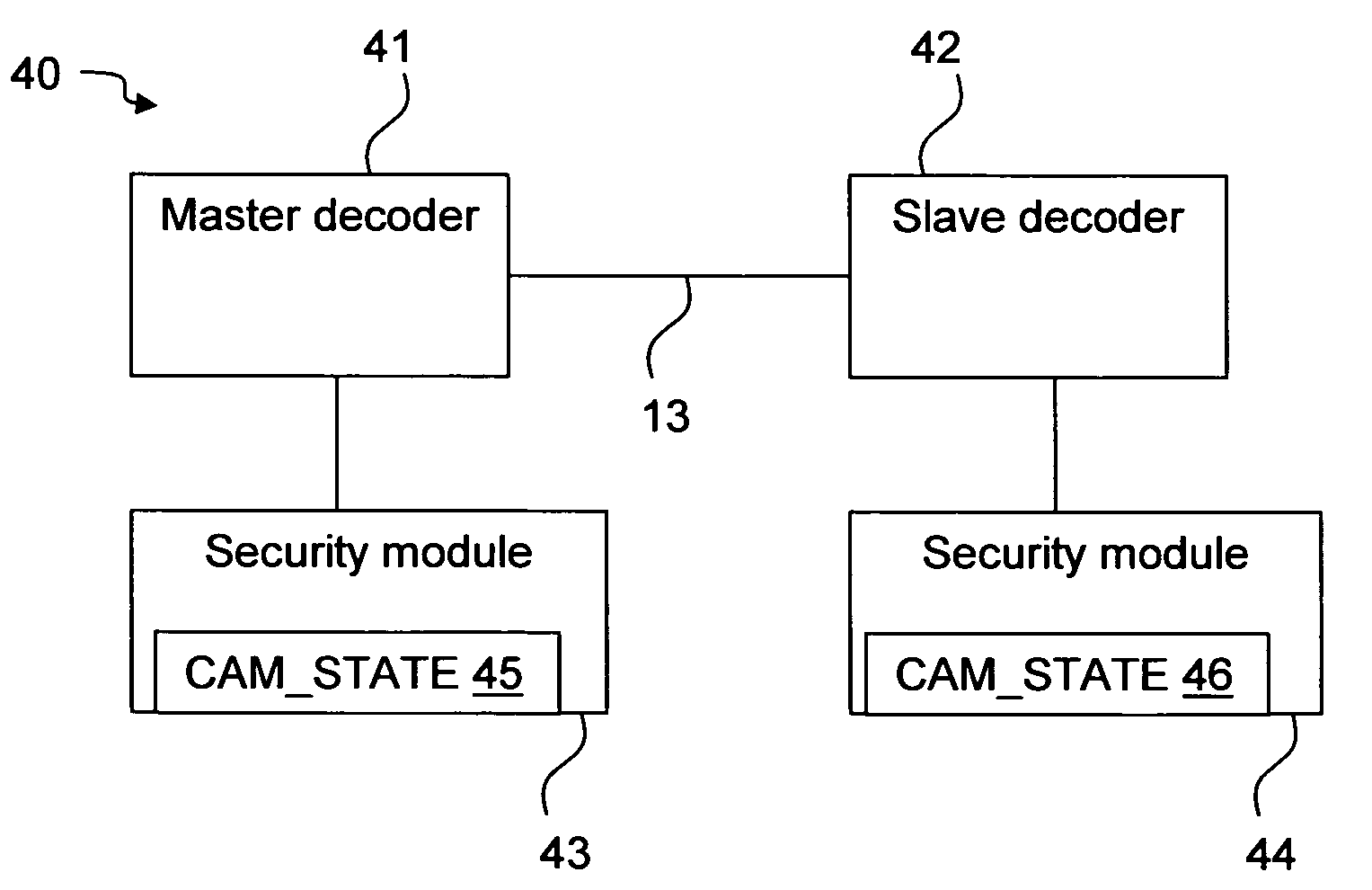
InactiveUS20060033840A1Improve securityIncreased flexibility of usePicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningComputer hardwareConditional access systems
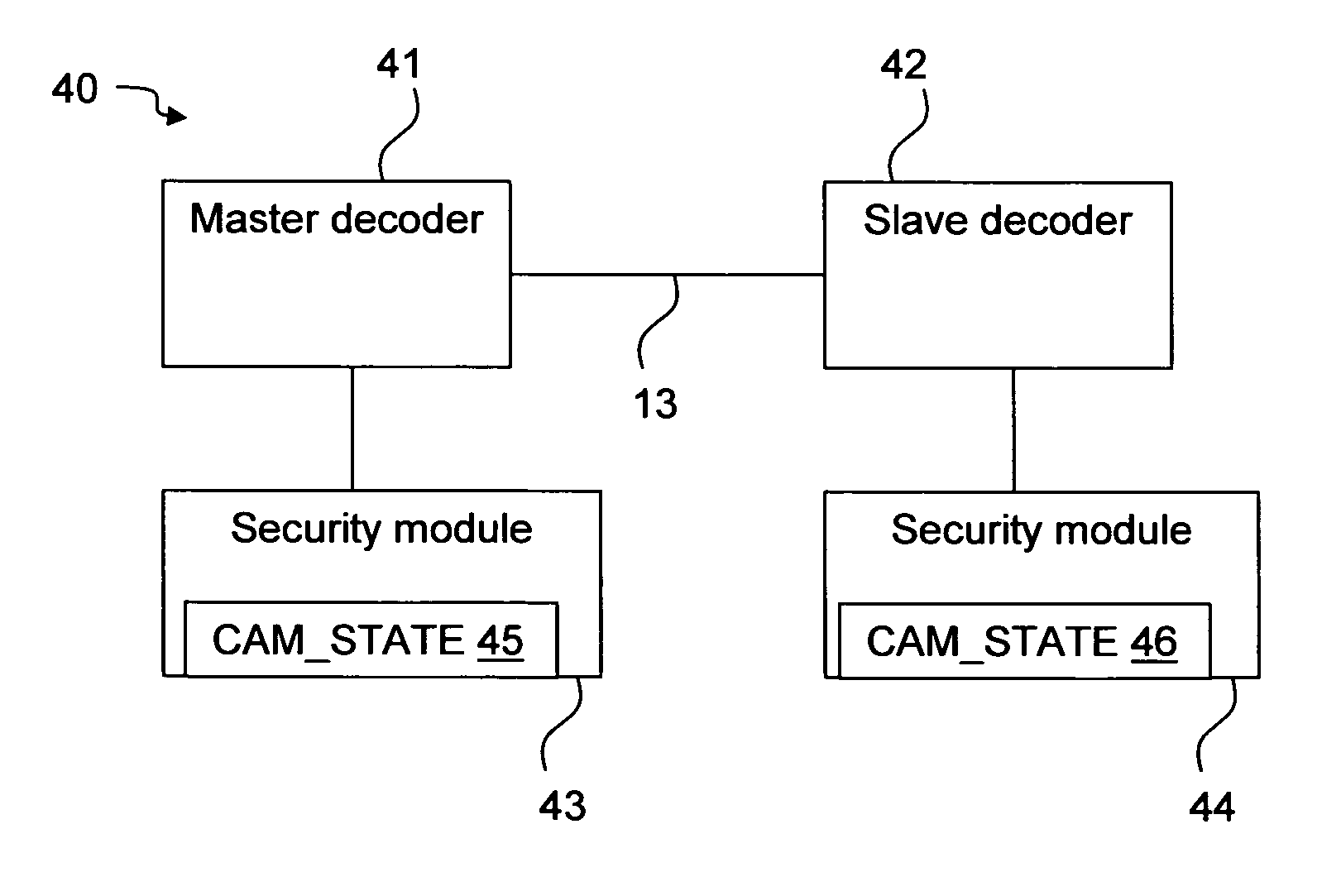
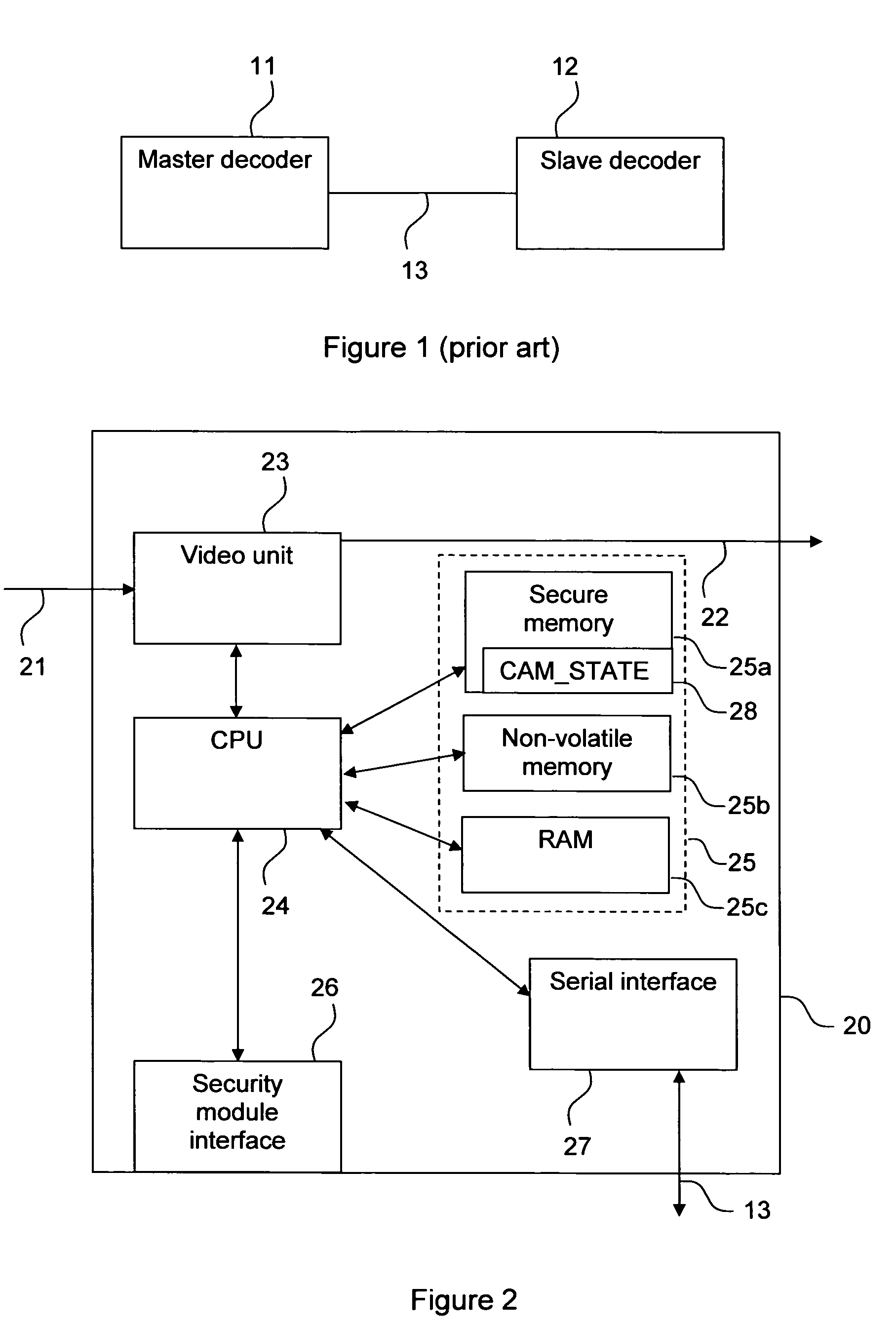
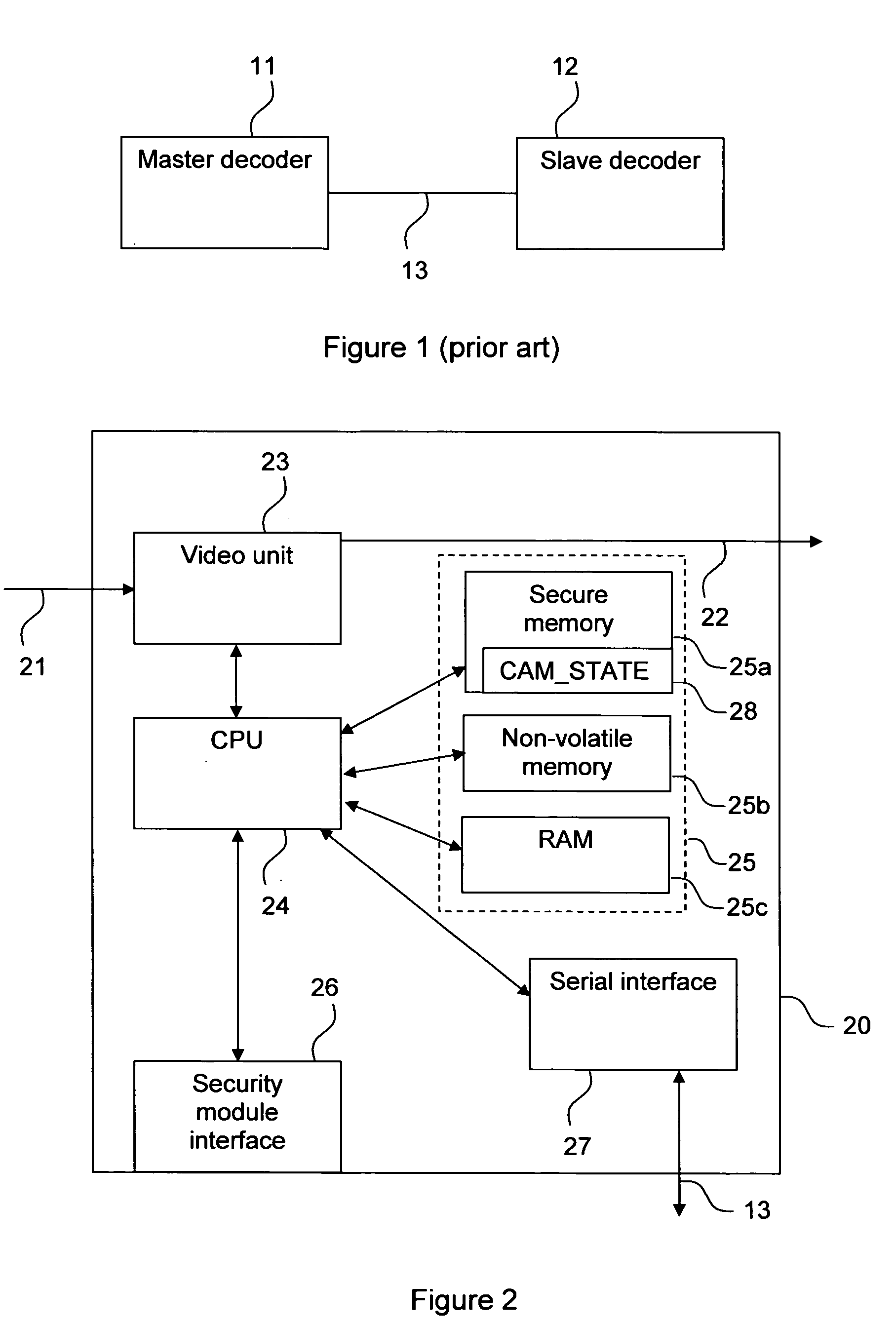
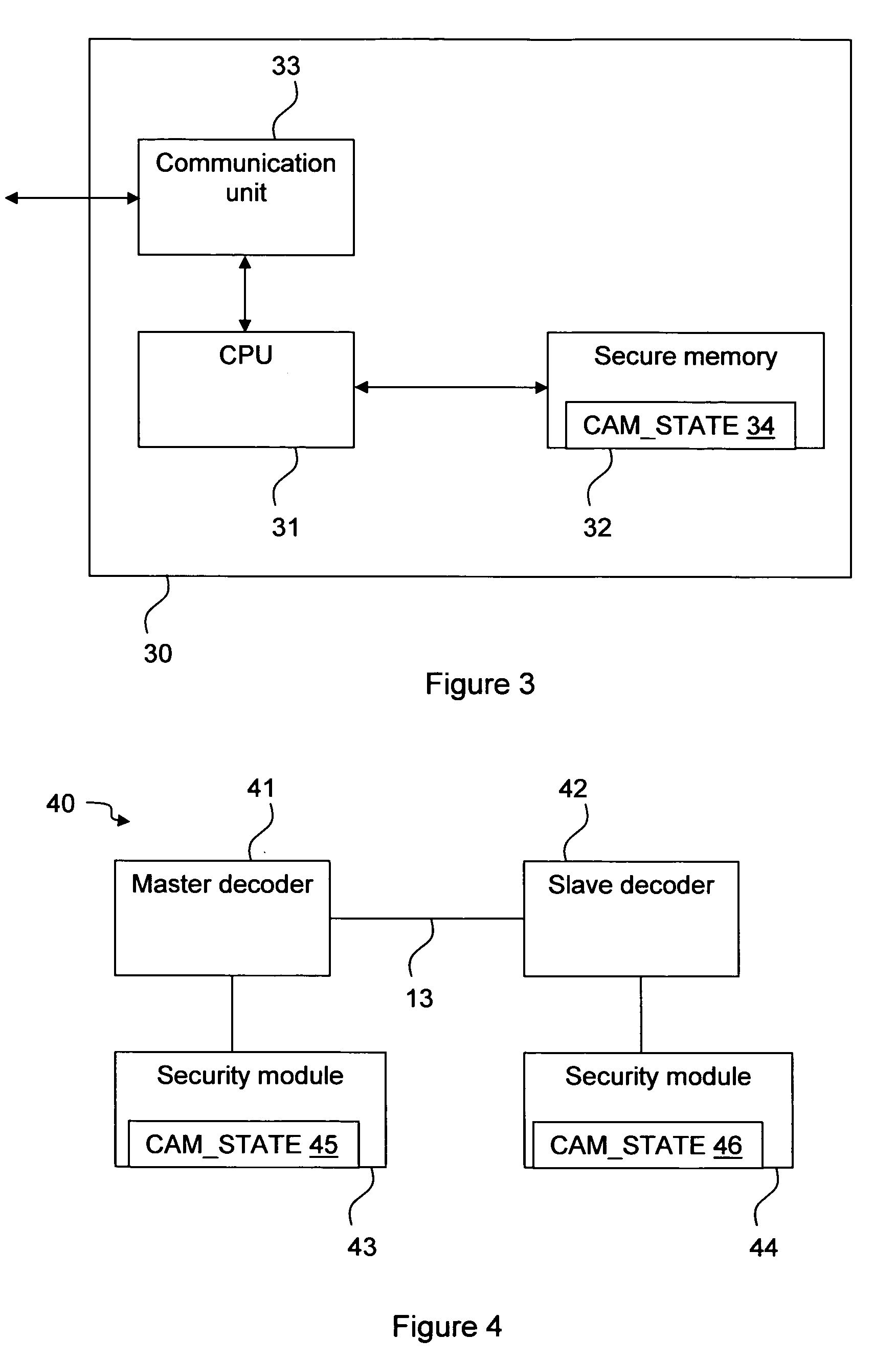
The invention relates to pairing a slave device with a master device, for example decoders in a conditional access system. There is provided a security module that stores a device state that indicates whether a decoder shall be a master or a slave decoder. There is also provided a method in a conditional access system of providing a device with a device state stored on a security module. It is detected that the security module is in connection with the device and the device state is transferred from the security module to the device. There is further provided a method of pairing a slave device with a master device. The slave device asks the master device to identify itself, the master device returns an identification, and if the slave device has not yet been paired with a master device, it checks the identity of the master device and, if the identity is verified pairs with the master device. There is also provided a first, slave, device for pairing with a second, master, device. The first device comprises an interface for sending an identification command to and receiving an identification message from the master device, and a processor for checking the identity of the second device and pairing the first device with the second device.
Owner:THOMSON LICENSING SA
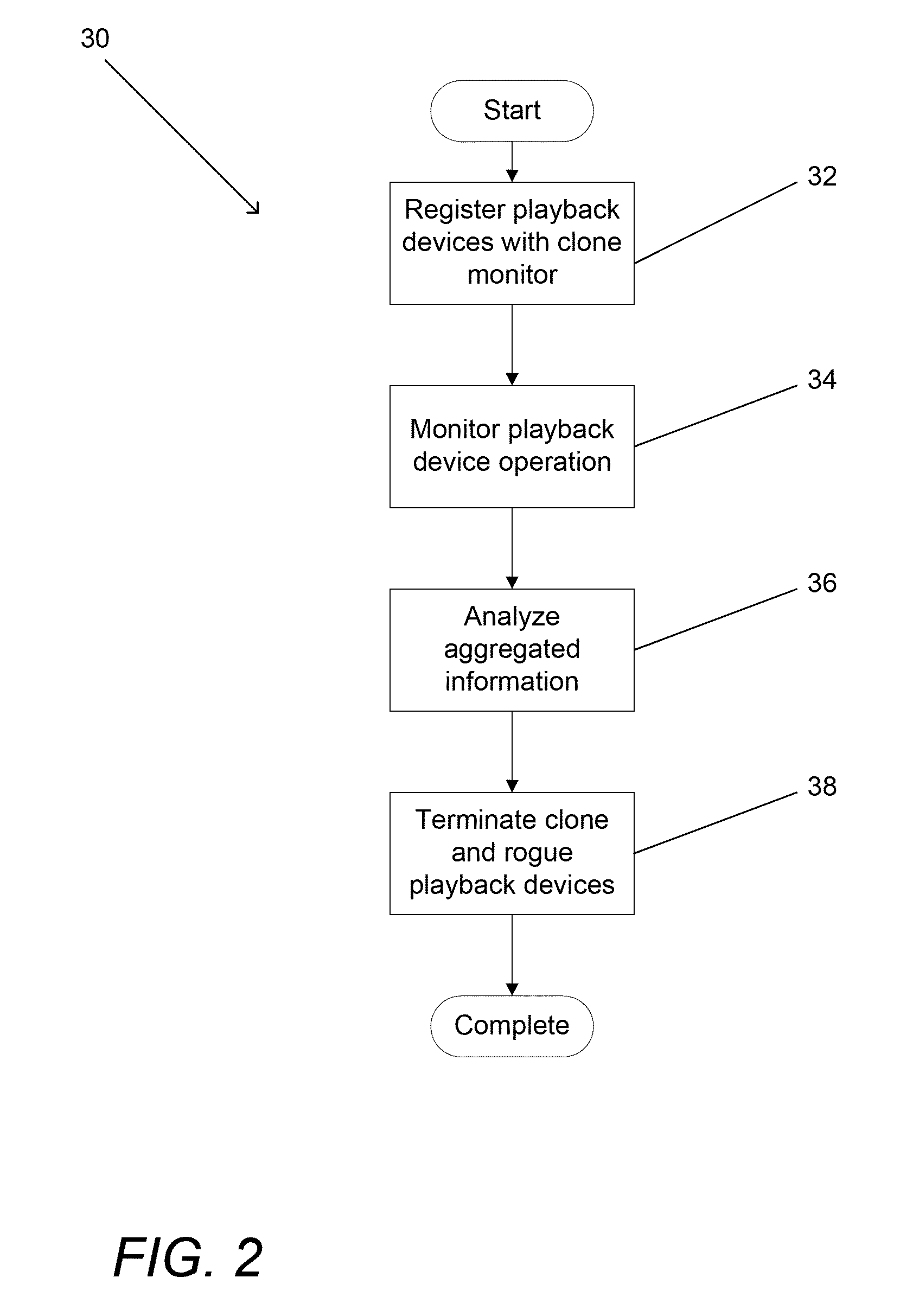
Systems and methods for detecting clone playback devices
ActiveUS20110030065A1Digital data processing detailsAnalogue secracy/subscription systemsDigital rights management systemDownloadable Conditional Access System
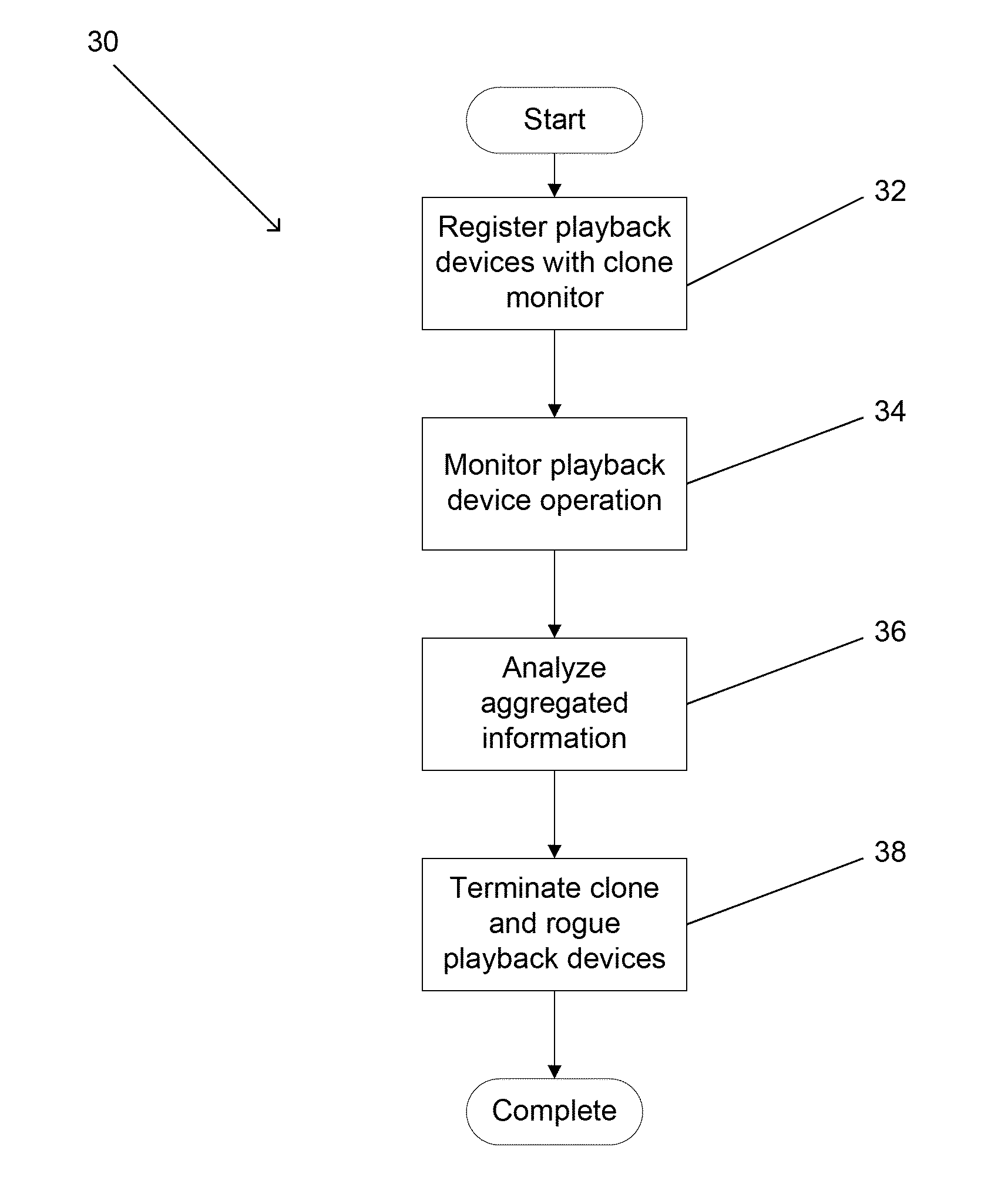
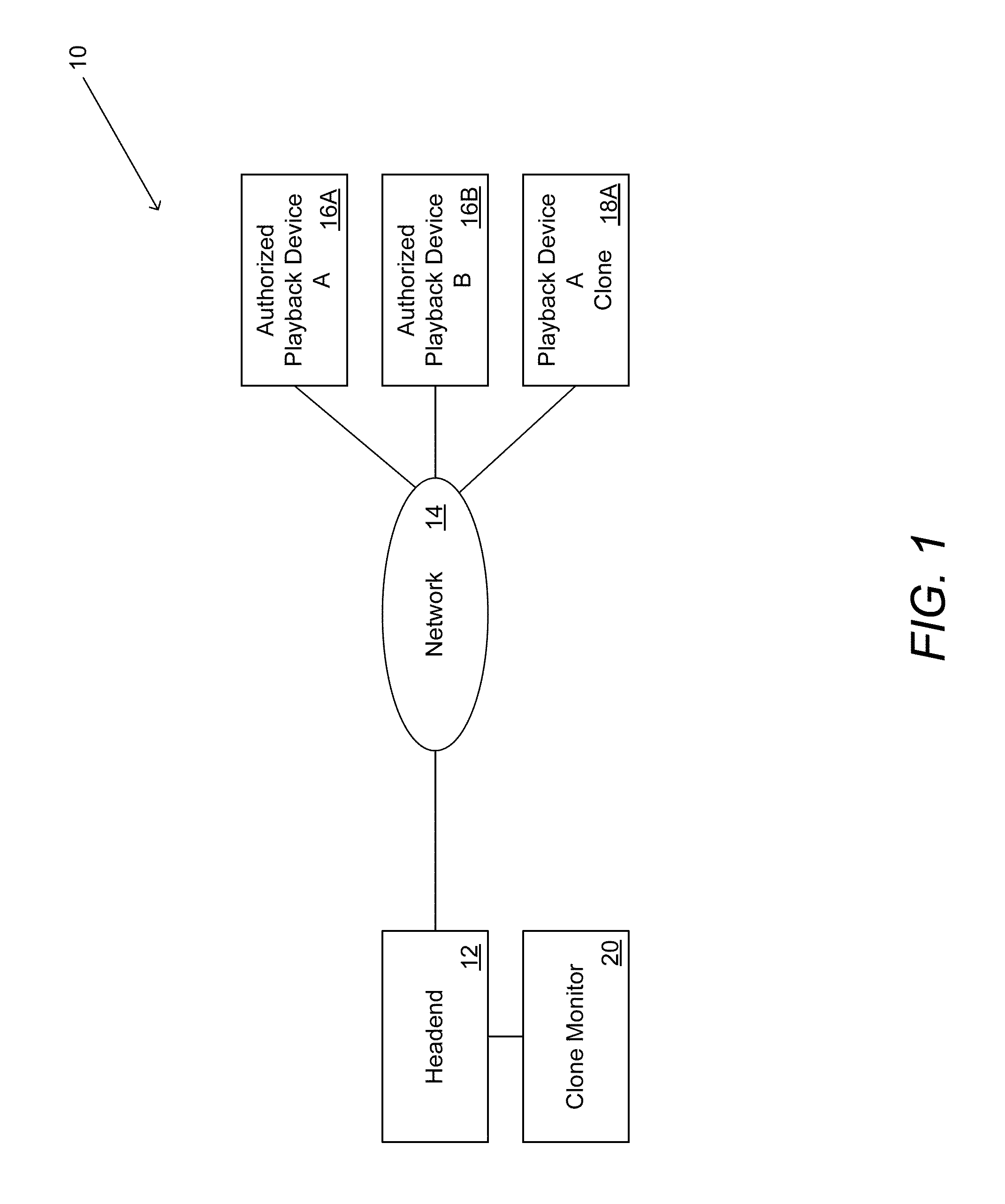
Systems and methods are described for aggregating information obtained from messages between playback devices and content protection systems, including but not limited to conditional access systems, downloadable conditional access systems, and digital rights management systems, that include a unique identifier and applying user modifiable rules to the aggregated information to identify abnormal behavior associated with the unique identifier including but not limited to one or more clone playback devices utilizing the unique identifier or a rogue playback device utilizing a unique identifier. One embodiment includes a plurality of playback devices connected to a headend via a network, where the headend includes at least one content protection system, and a clone monitor configured to register playback devices based upon a unique identification supplied by each playback device, when communicating with the at least one content protection system. In addition, the clone monitor is configured to aggregate information associated with each playback device over time, where the information is obtained from messages that are transmitted between the playback device and the headend and that include a unique identifier, and the clone monitor is configured to apply rules to the aggregated information to identify at least one pattern of abnormal behavior in the aggregated information associated with a specific unique identifier.
Owner:VERIMATRIX INC
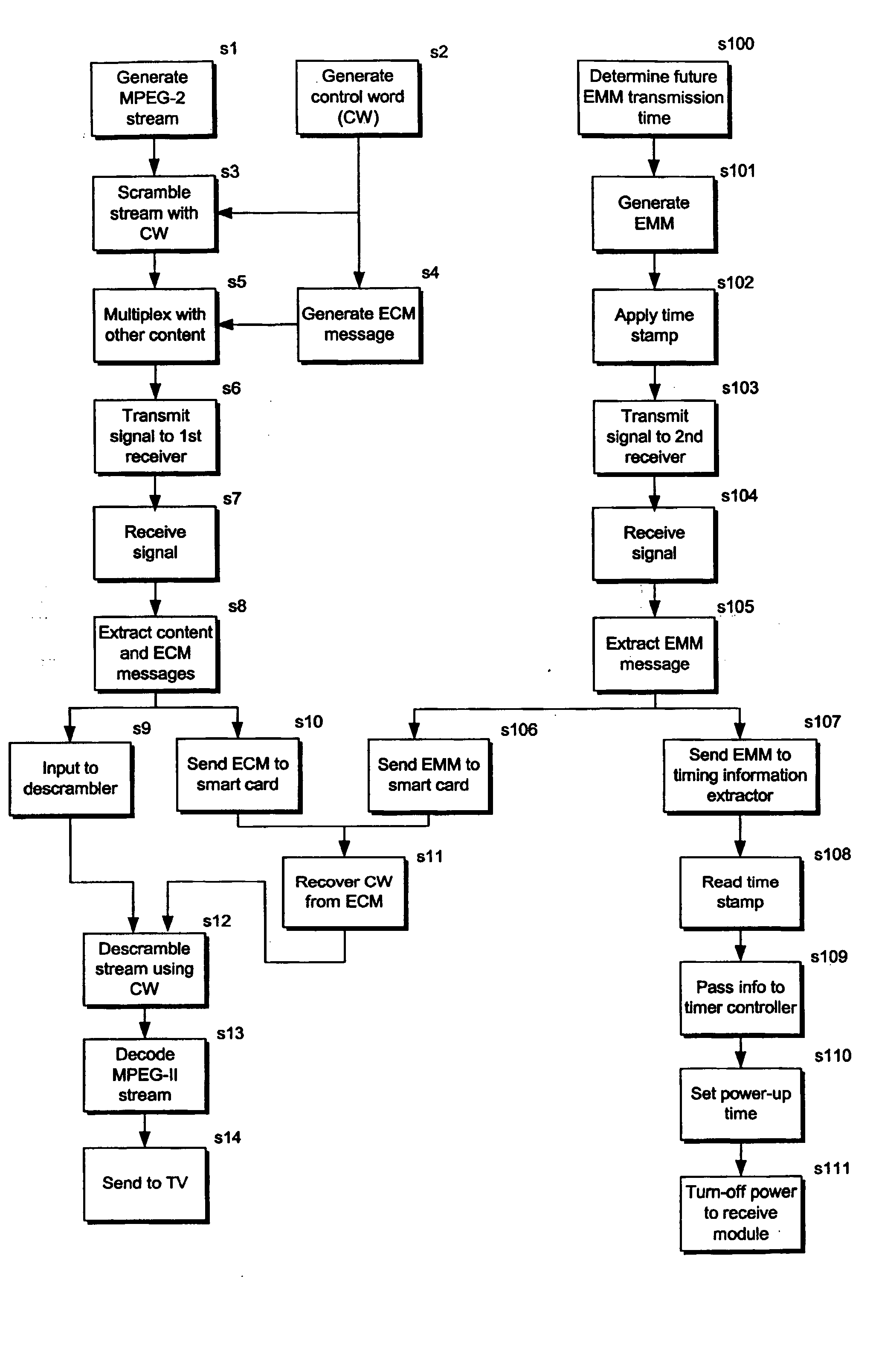
Conditional Access System
InactiveUS20070261076A1Save powerAnalogue secracy/subscription systemsSelective content distributionConditional access systemsComputer science
A conditional access system in which entilement management messages (EMMs) sent to a receiver include transmission time information for future EMMs. The transmission time information is used at the receiver to control the receiver so that it is powered on only when required to receive the future EMMs.
Owner:NOKIA CORP
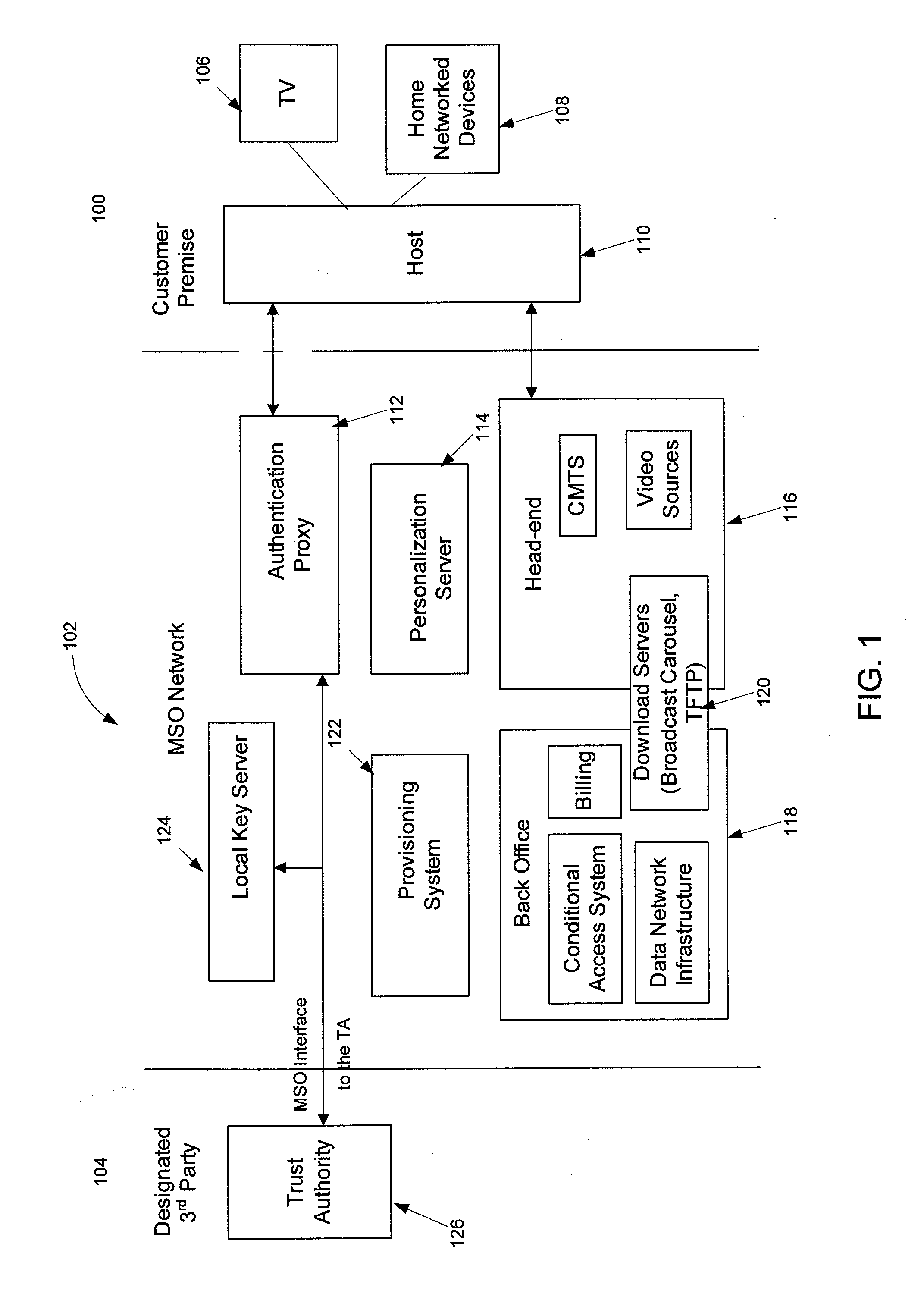
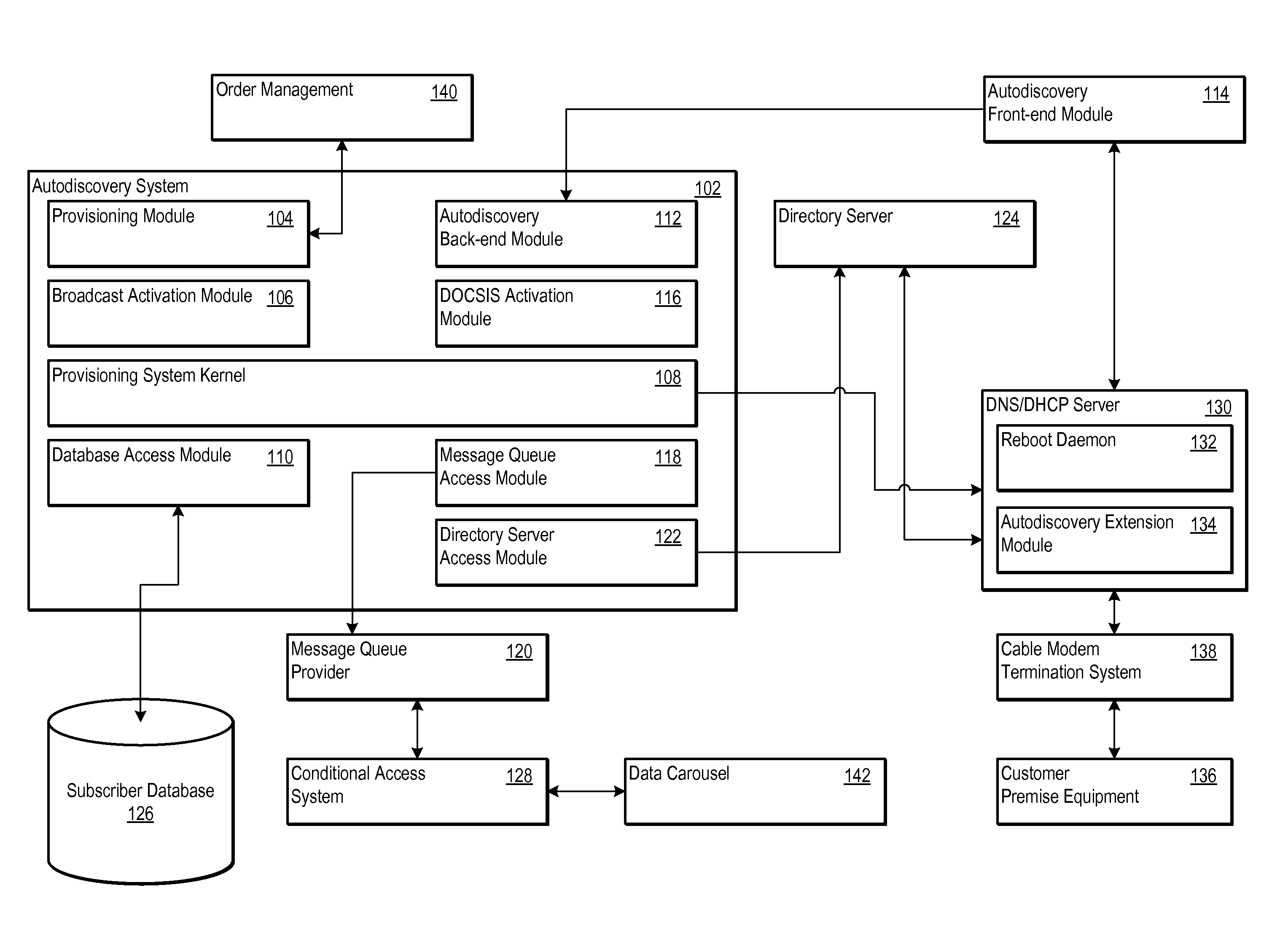
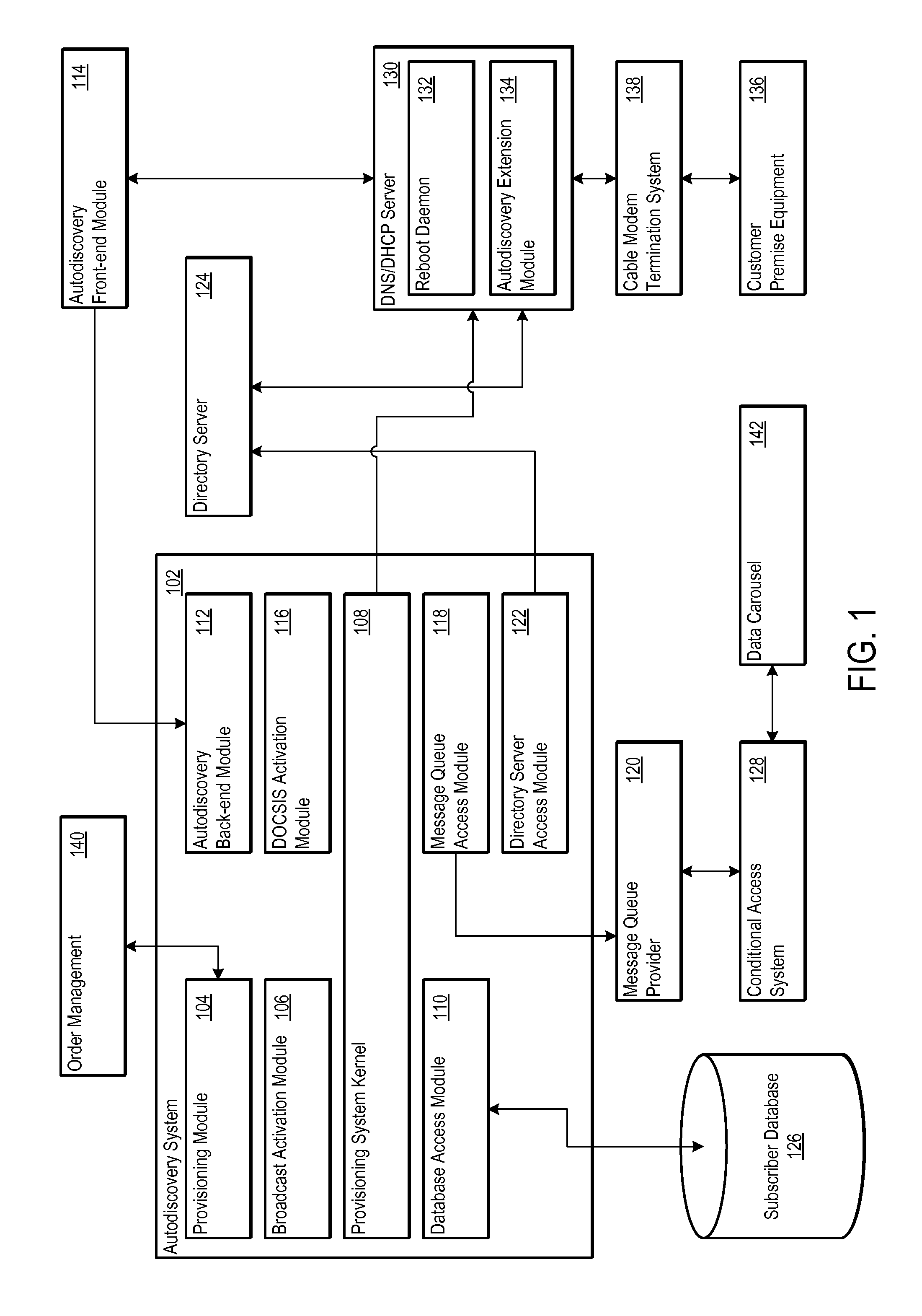
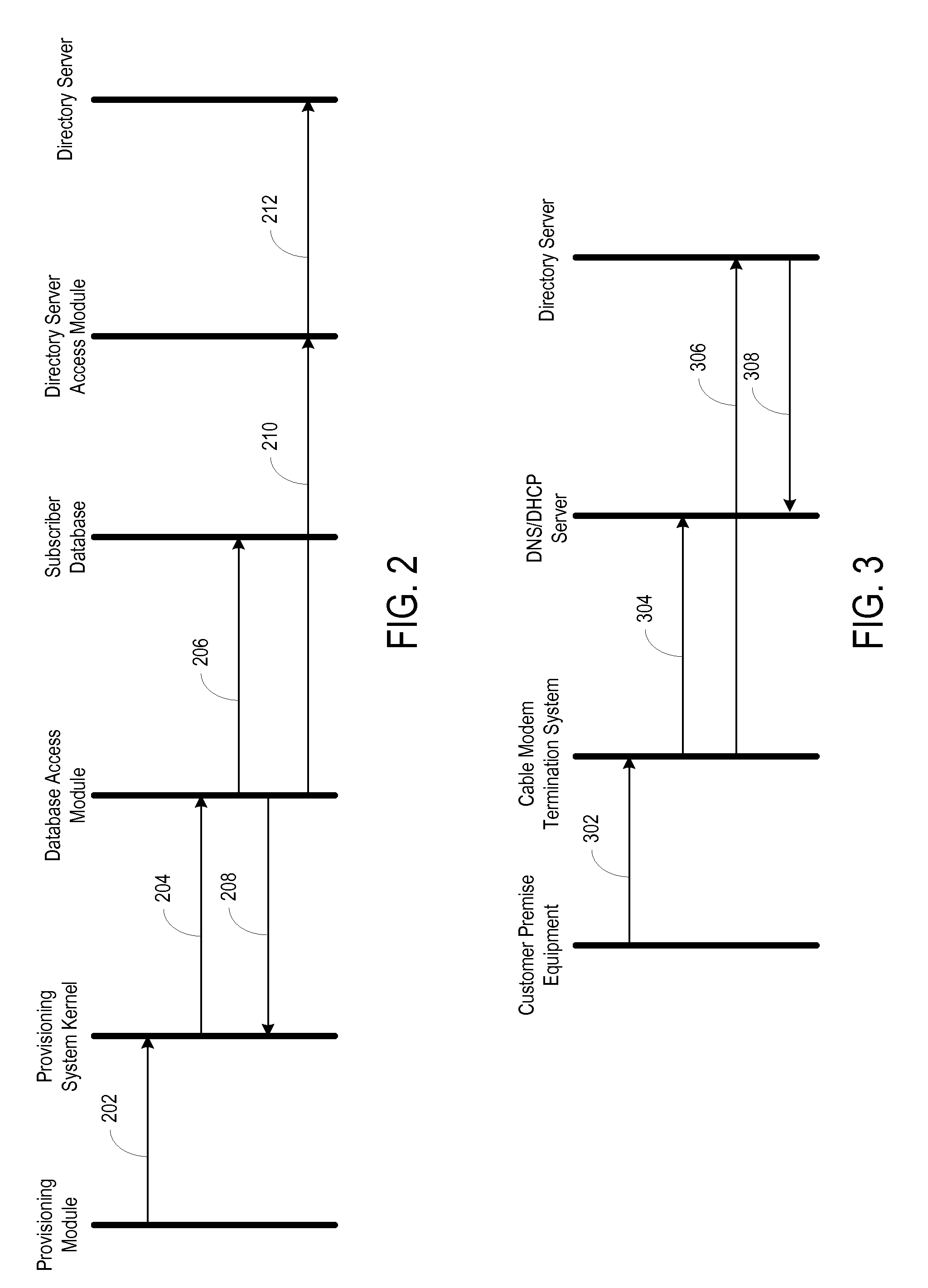
Network autodiscovery as a lever to decorrelated service activation through event driven architecture
ActiveUS20110058657A1Supervisory/monitoring/testing arrangementsSubstation equipmentConditional access systemsClient-side
An autodiscovery system provides content credentials to customer premise equipment through an event-driven architecture. The autodiscovery system includes several modules for implementing the event-driven architecture, such as an autodiscovery front-end module, an autodiscovery back-end module, and a broadcast activation module. The autodiscovery system may also include a subscriber database that stores subscriber records that identify subscribers associated with a level of service, a customer premise equipment identifier, or both. The modules of the autodiscovery system may also communicate with a conditional access system that communicates the content credentials to a data carousel. When the content credentials are made available on the data carousel, the autodiscovery front-end module may notify the customer premise equipment that the content credentials are ready for retrieval from the data carousel.
Owner:ACCENTURE GLOBAL SERVICES LTD
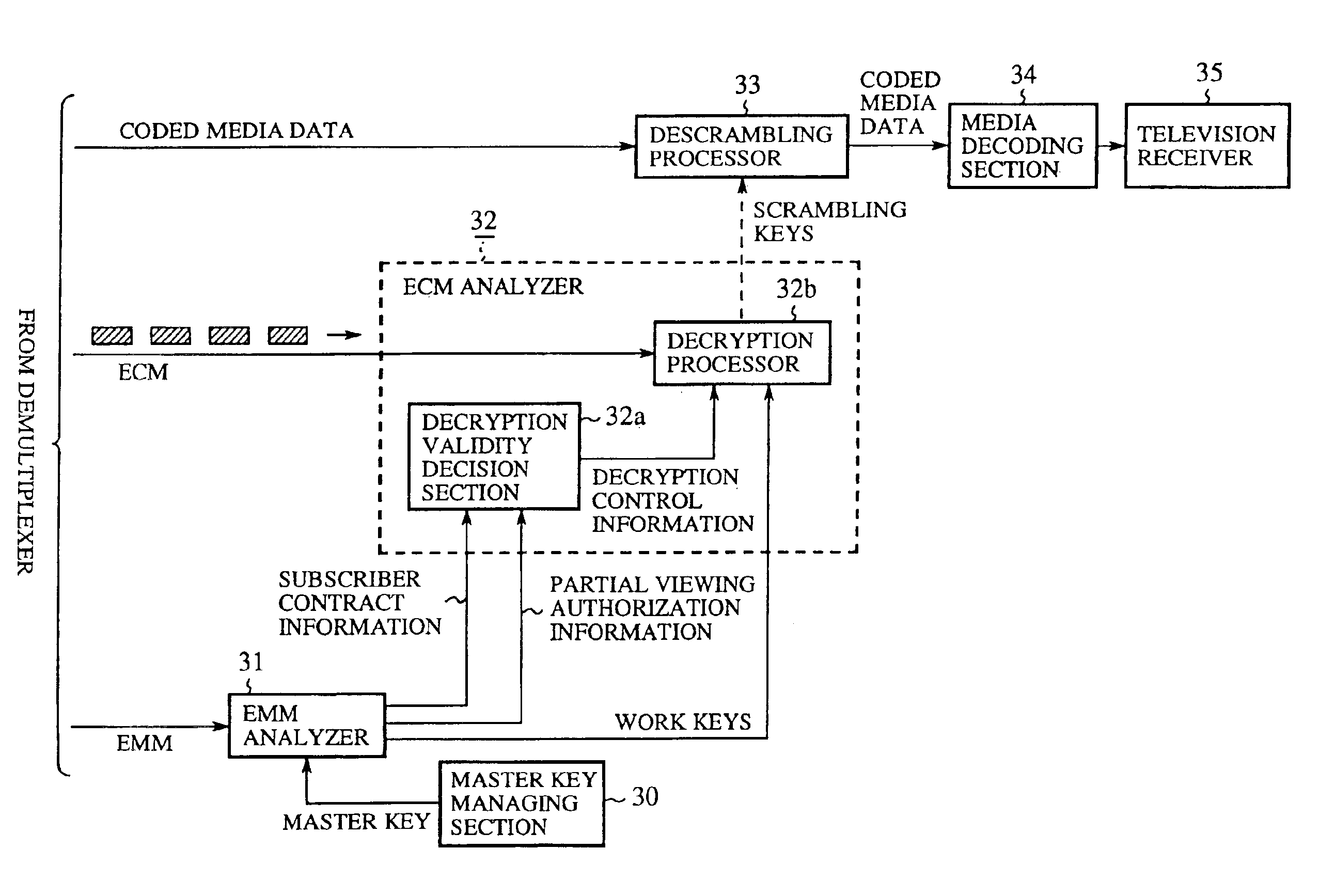
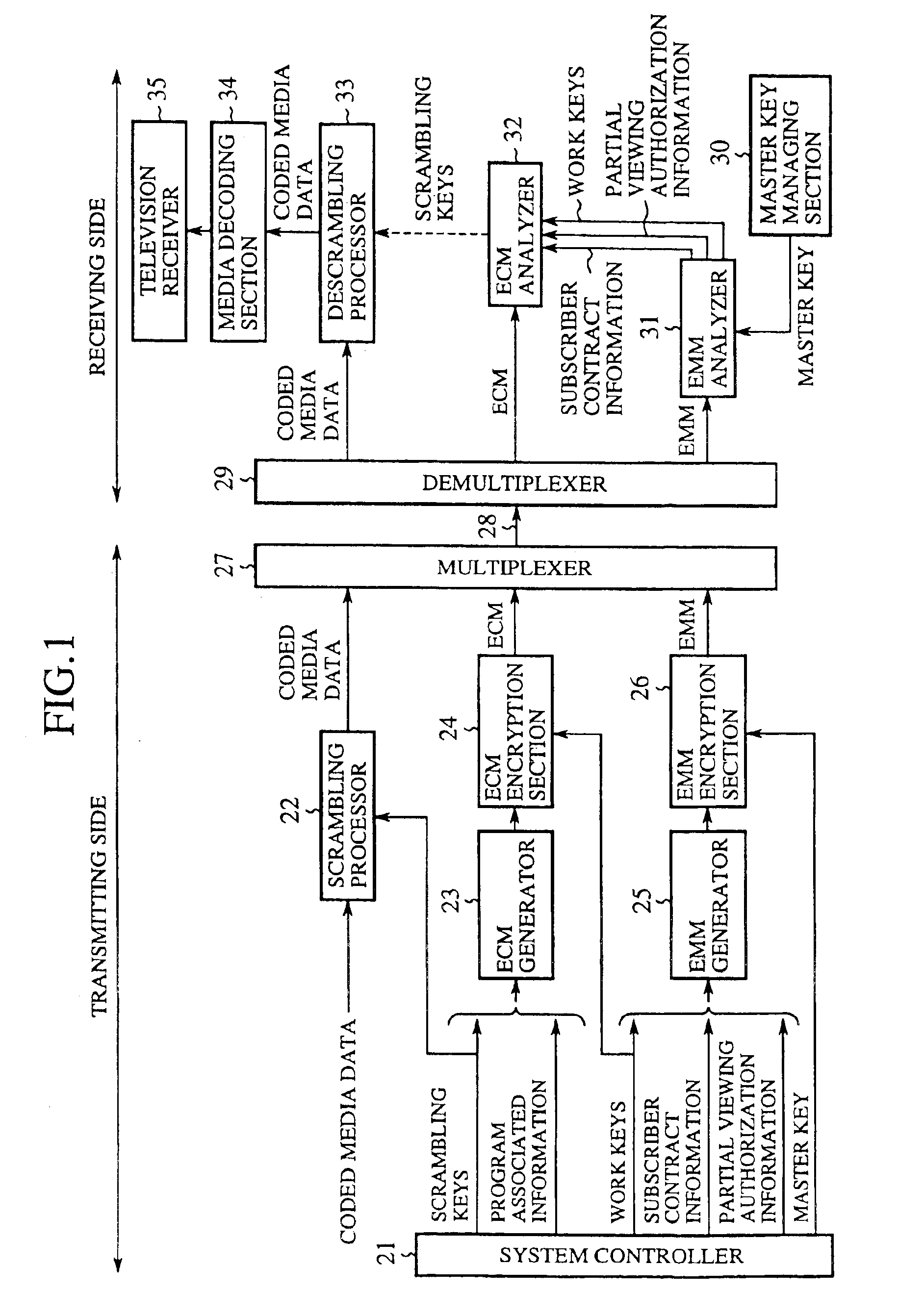
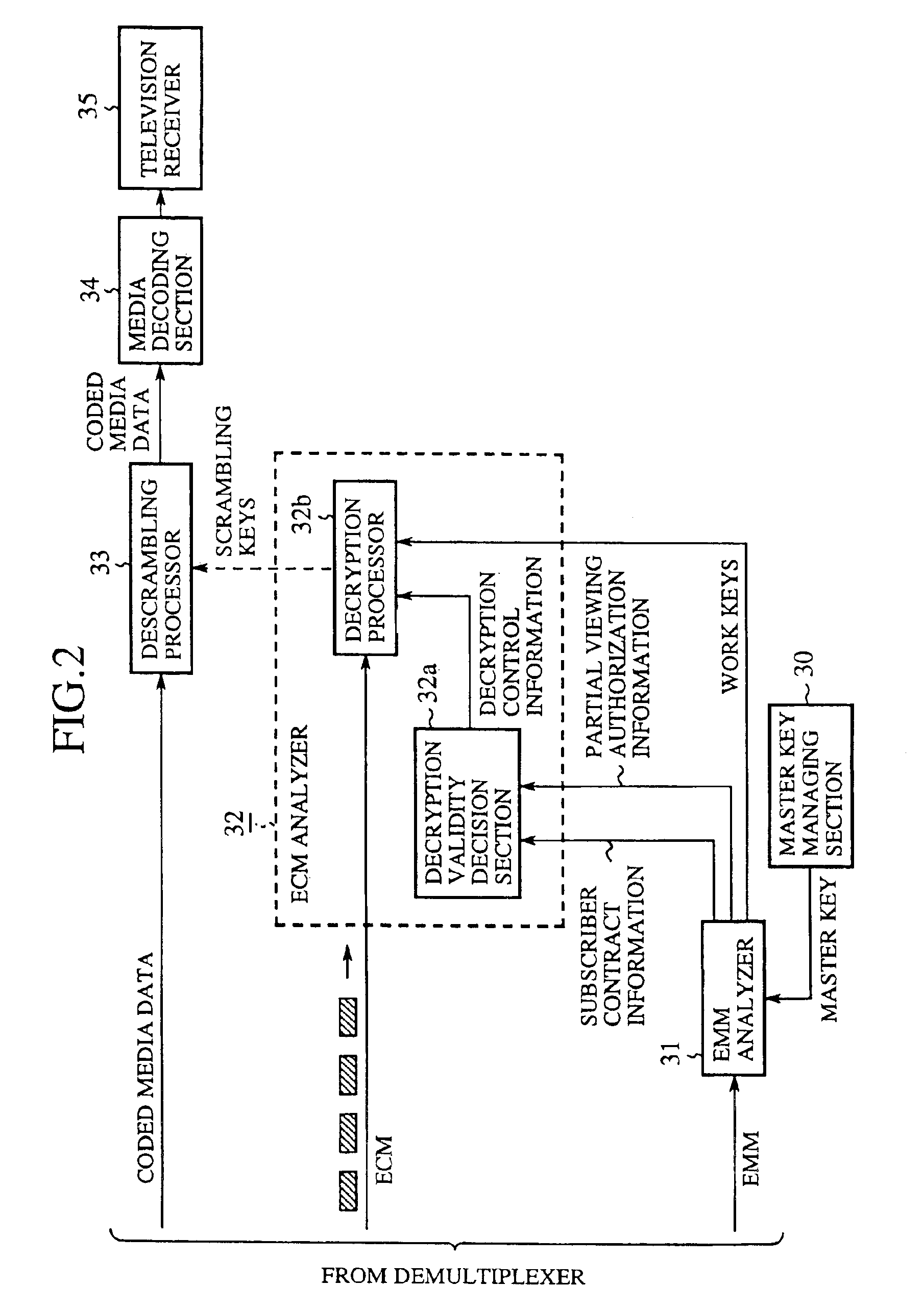
Conditional access system enabling partial viewing
InactiveUS6920222B1Increase desireAnalogue secracy/subscription systemsSelective content distributionConditional access systemsAuthorization
A conditional access system includes an EMM (Entitlement Management Message) analyzer for retrieving partial viewing authorization information. When the partial viewing authorization information permits partial viewing, ECM (Entitlement Control Message) is decrypted using work keys, and scrambling keys are intermittently retrieved from the ECM. This can solve a problem of a conventional conditional access system in that an unauthorized user's receiver cannot display pictures at all because the receiver cannot retrieve scrambling keys, and hence the user cannot enjoy a program even to such a degree as to perceive its feeling as in analog broadcasting systems, and thus the user cannot decide as to whether to make contract or not with viewing the program to some extent, which prevents the provider of the program from offering effective invitation to the user.
Owner:MITSUBISHI ELECTRIC CORP
Conditonal access system
InactiveUS20050022015A1Managing accessAvoid layeringError preventionDigital data processing detailsConditional access systemsSecurity framework
A conditional access system comprising a plurality of devices interconnected in a network, the devices being grouped in a first group and a second group, the devices of the first group operating in accordance with a first security framework and the devices of the second group operating in accordance with a second security framework, each device operating using a particular middleware layer, said middleware layer being arranged to authenticate another middleware layer of another device, said middleware layer being authenticated by the security framework in accordance with which the device operates.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Control of Enhanced Application Features Via A Conditional Access System
InactiveUS20070143854A1Digital data processing detailsUser identity/authority verificationConditional access systemsService provision
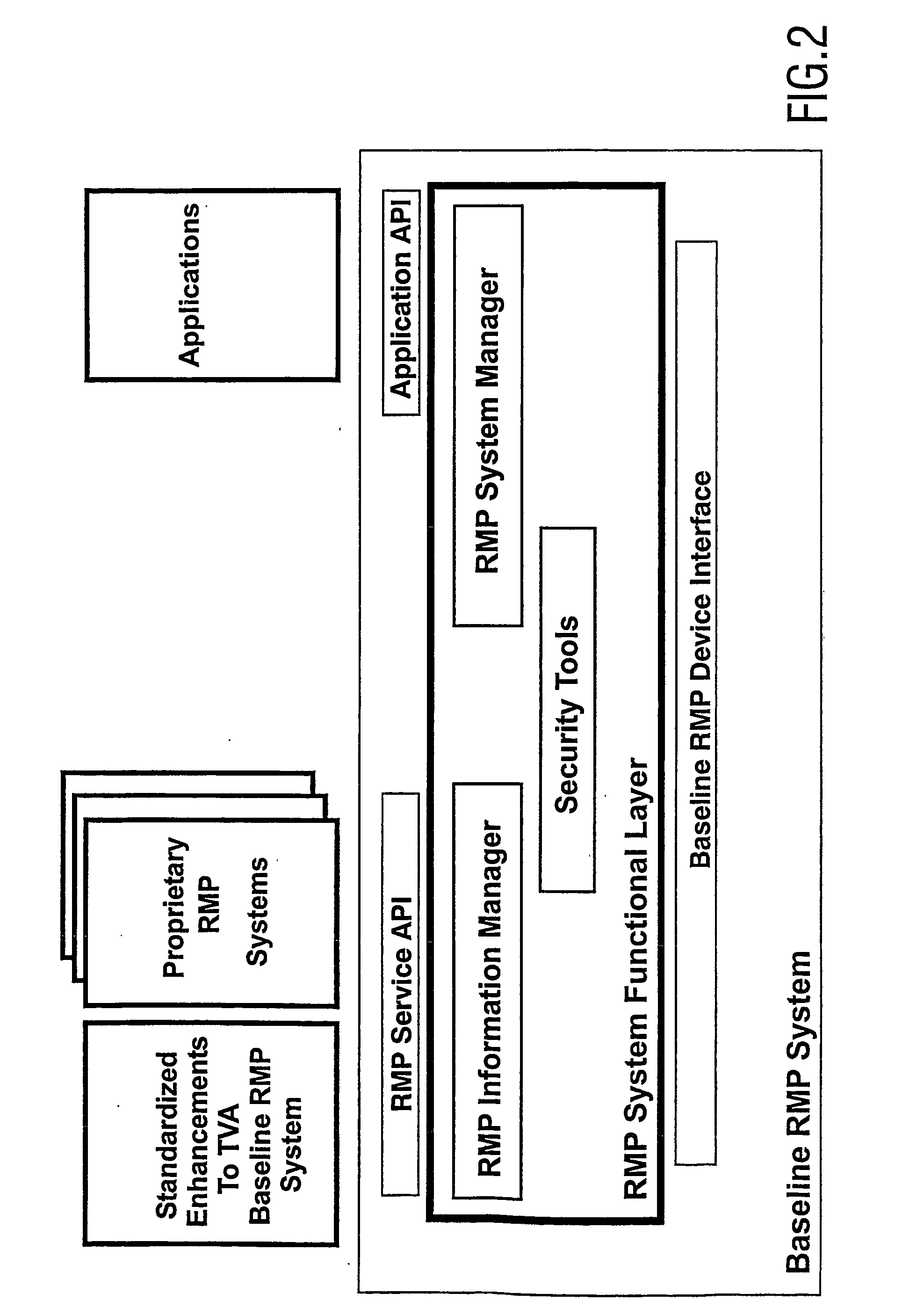
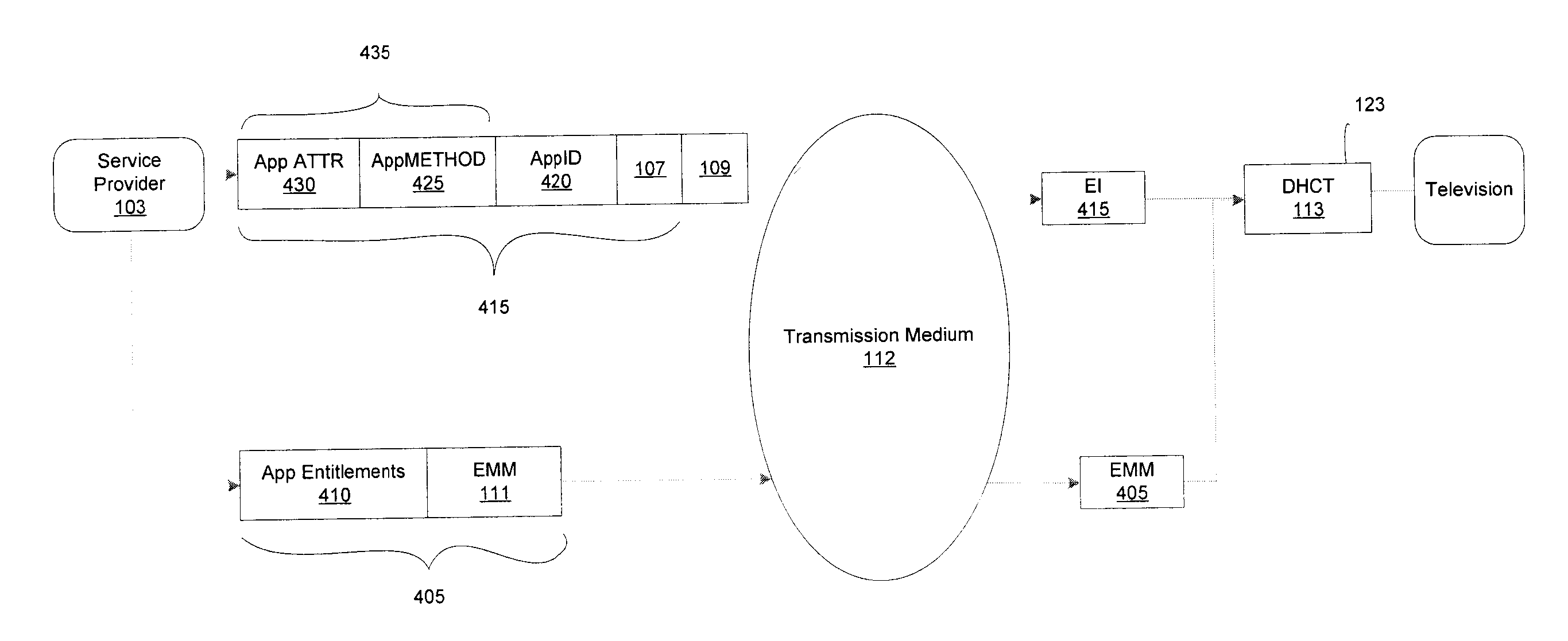
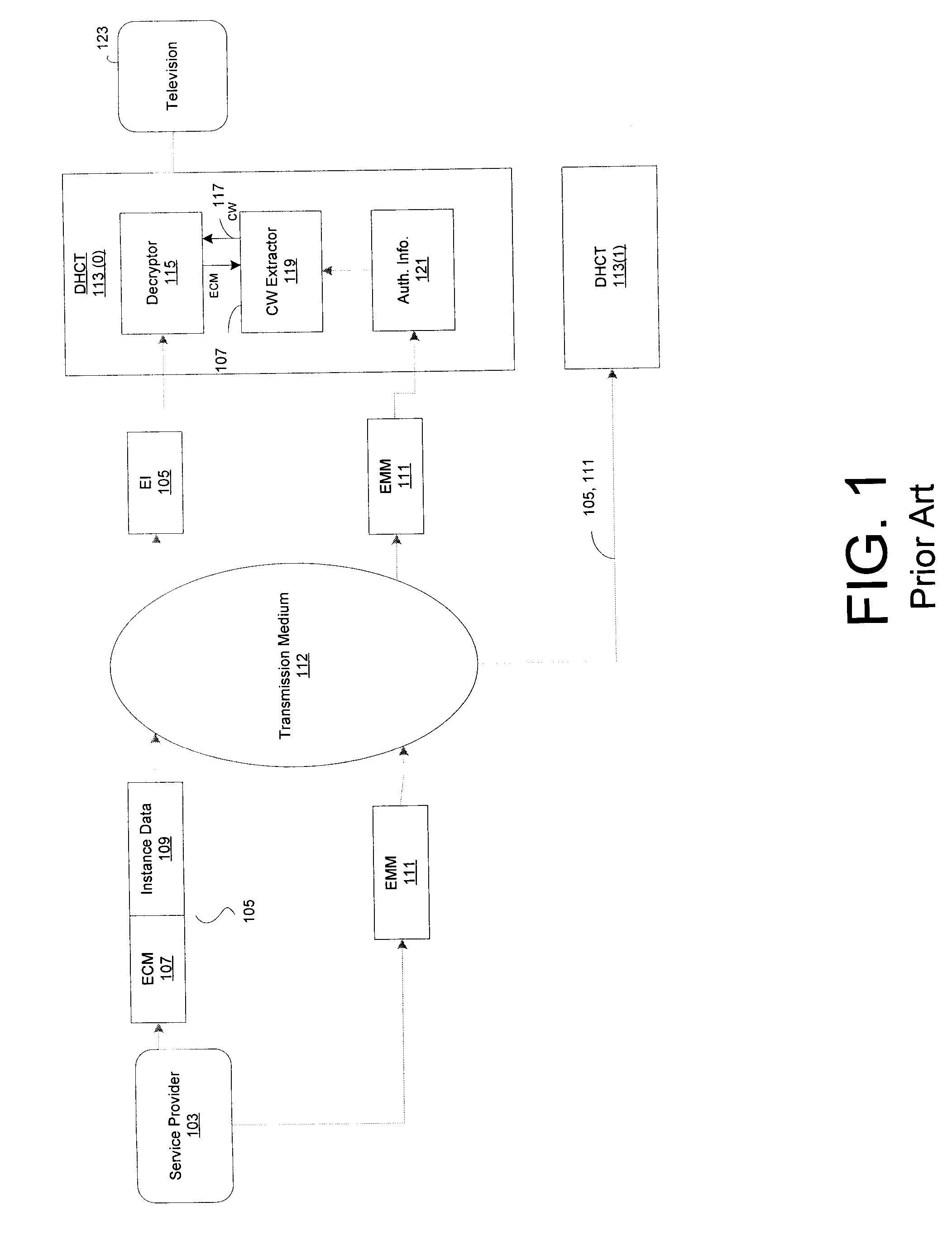
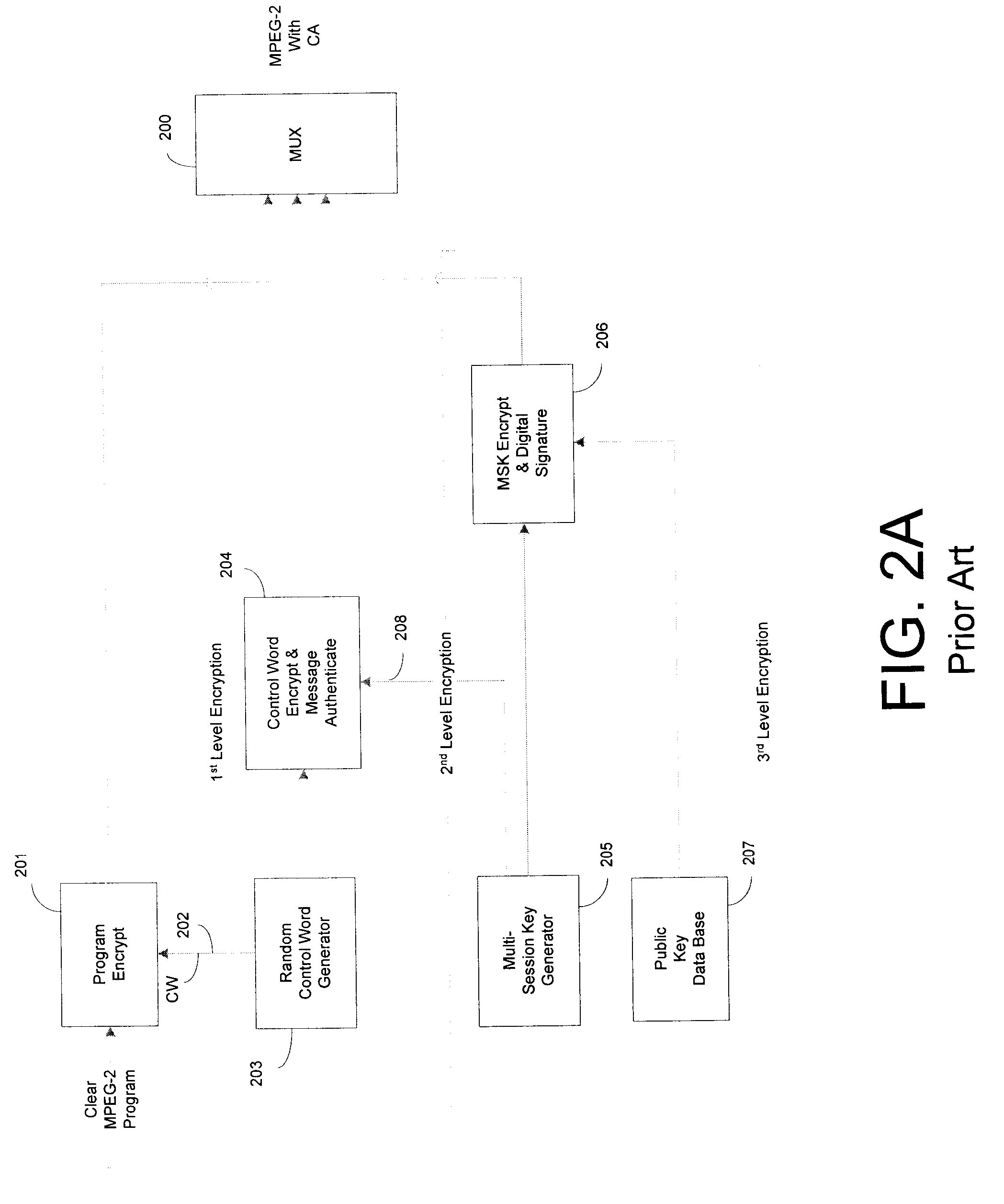
A service provider provides conditional access to data that is decrypted by authorized set-top boxes (DHCTs). The encrypted programs include encrypted enhanced programs by adding a field to entitlement management messages and corresponding entitlement control messages.
Owner:CISCO TECH INC +1
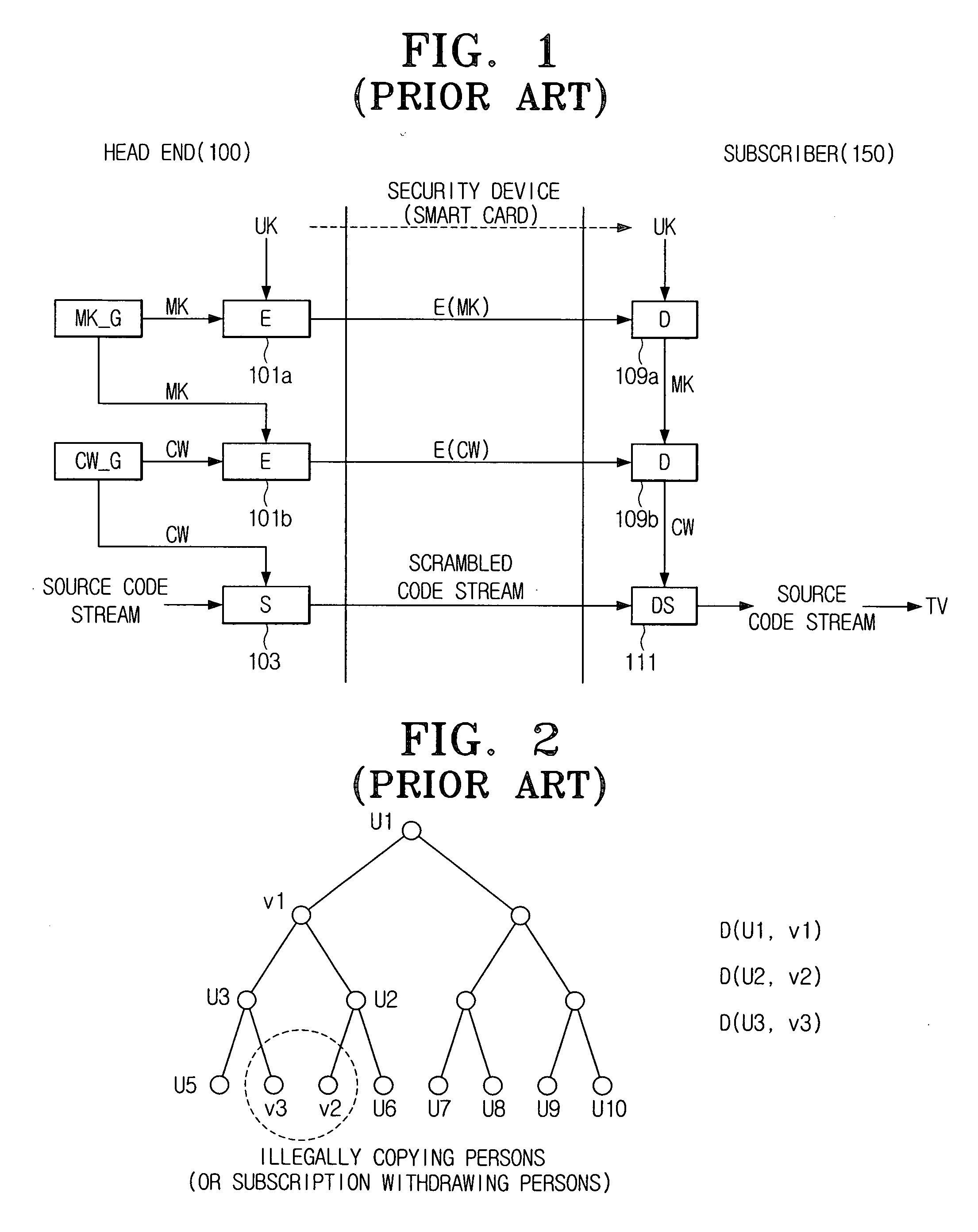
Security device and head end in conditional access system and method for controlling illegal use in the system
InactiveUS20060271950A1Reduce the burden onKey distribution for secure communicationPublic key for secure communicationControl systemConditional access systems
A security device and a head end of a conditional access system (CAS), and a method for controlling illegal use of the conditional access system, capable of minimizing the number of entitlement management messages (EMMs) to be distributed from a head end to a user are provided. Update keys encrypted with user keys and channel management keys encrypted with the update keys are utilized.
Owner:SAMSUNG ELECTRONICS CO LTD
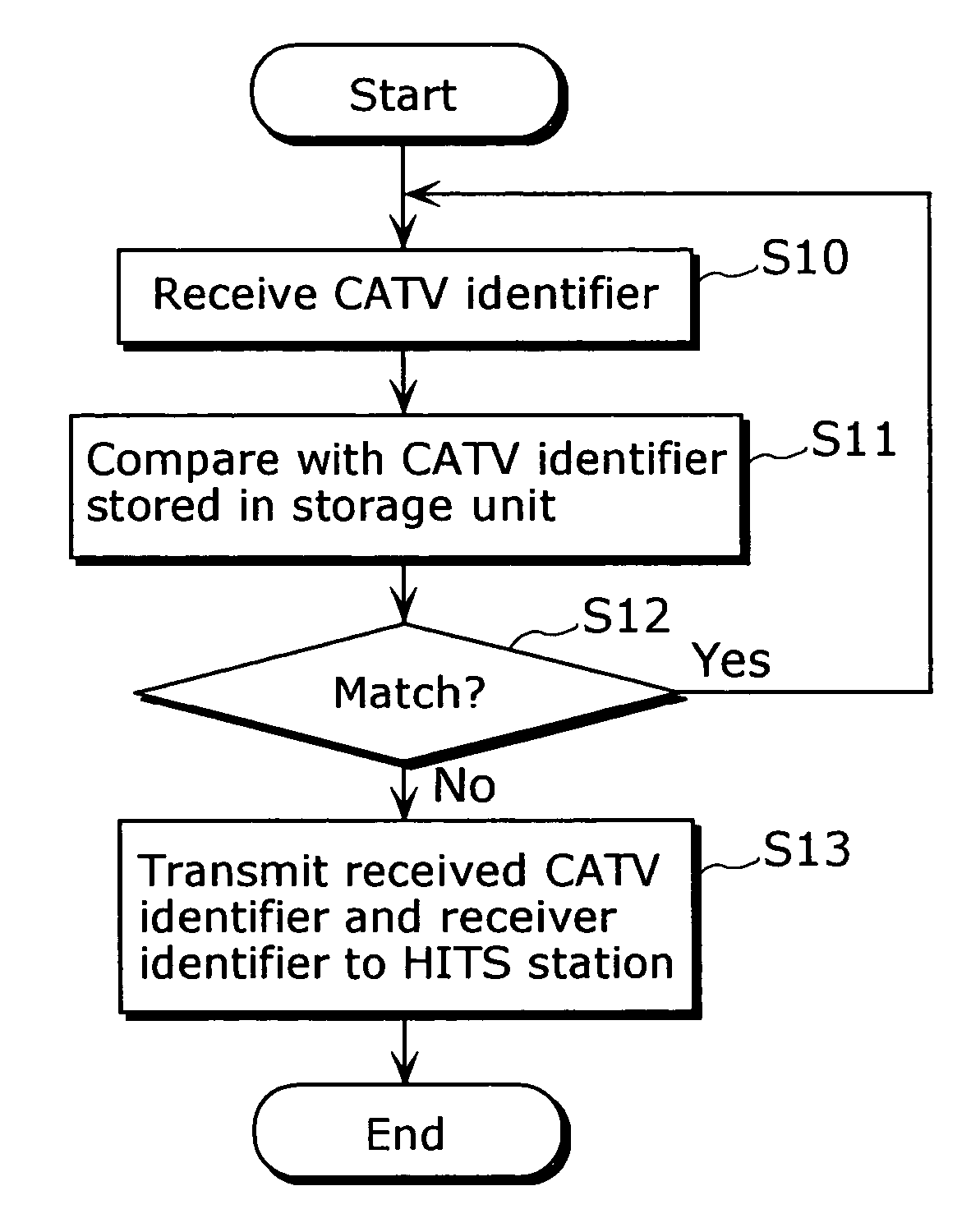
Conditional access system and receiver
InactiveUS20040093614A1GHz frequency transmissionAnalogue secracy/subscription systemsConditional access systemsSatellite
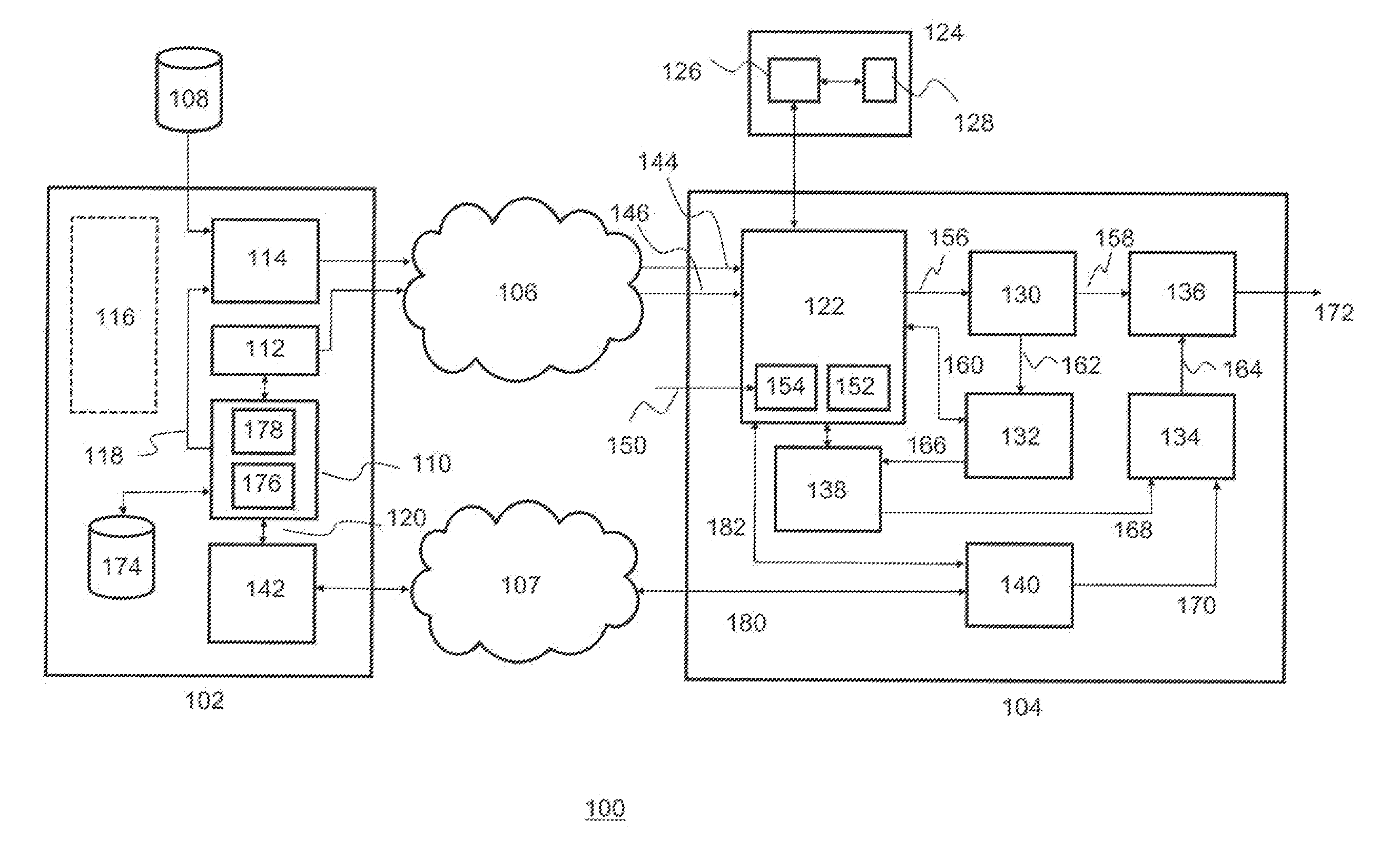
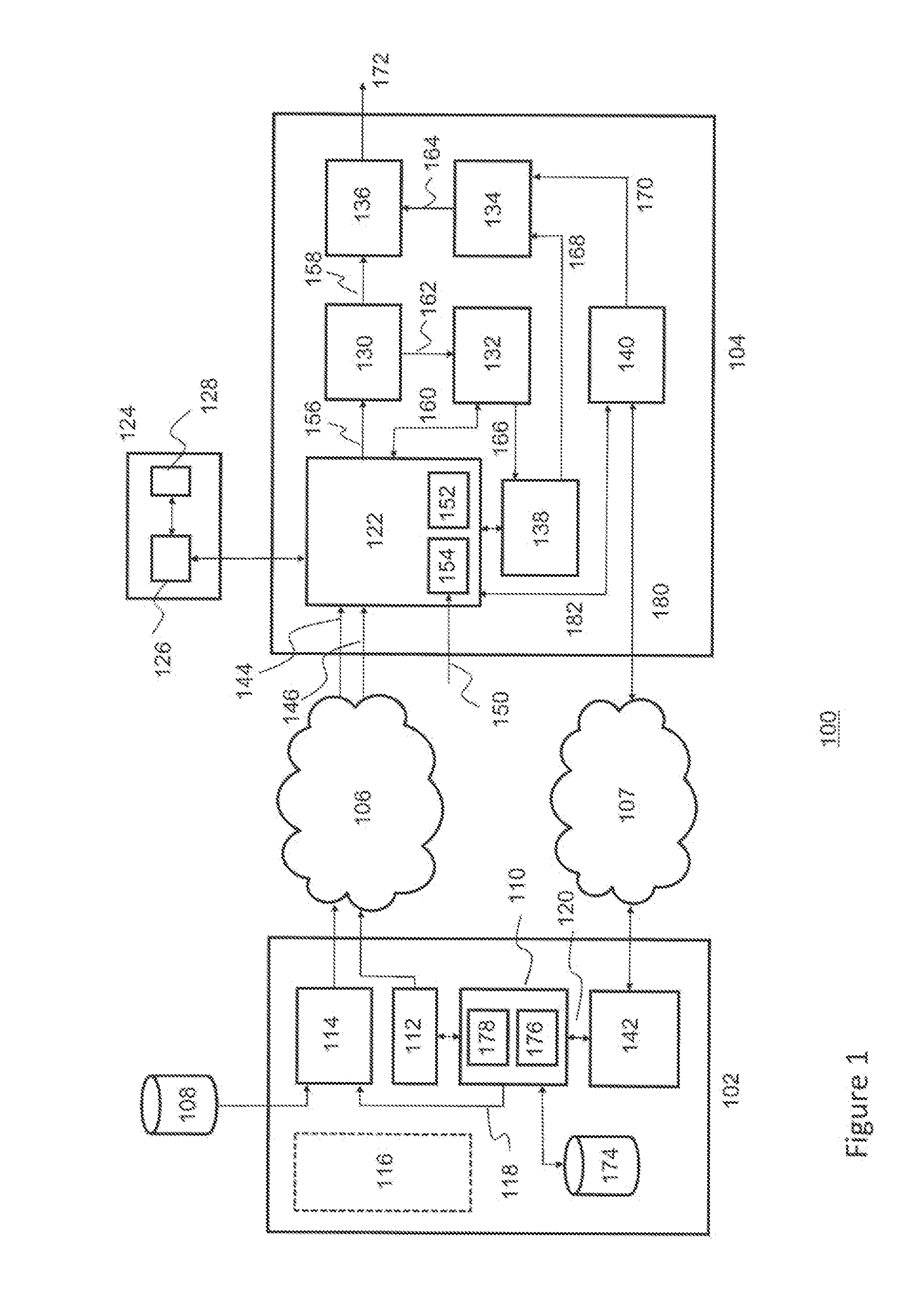
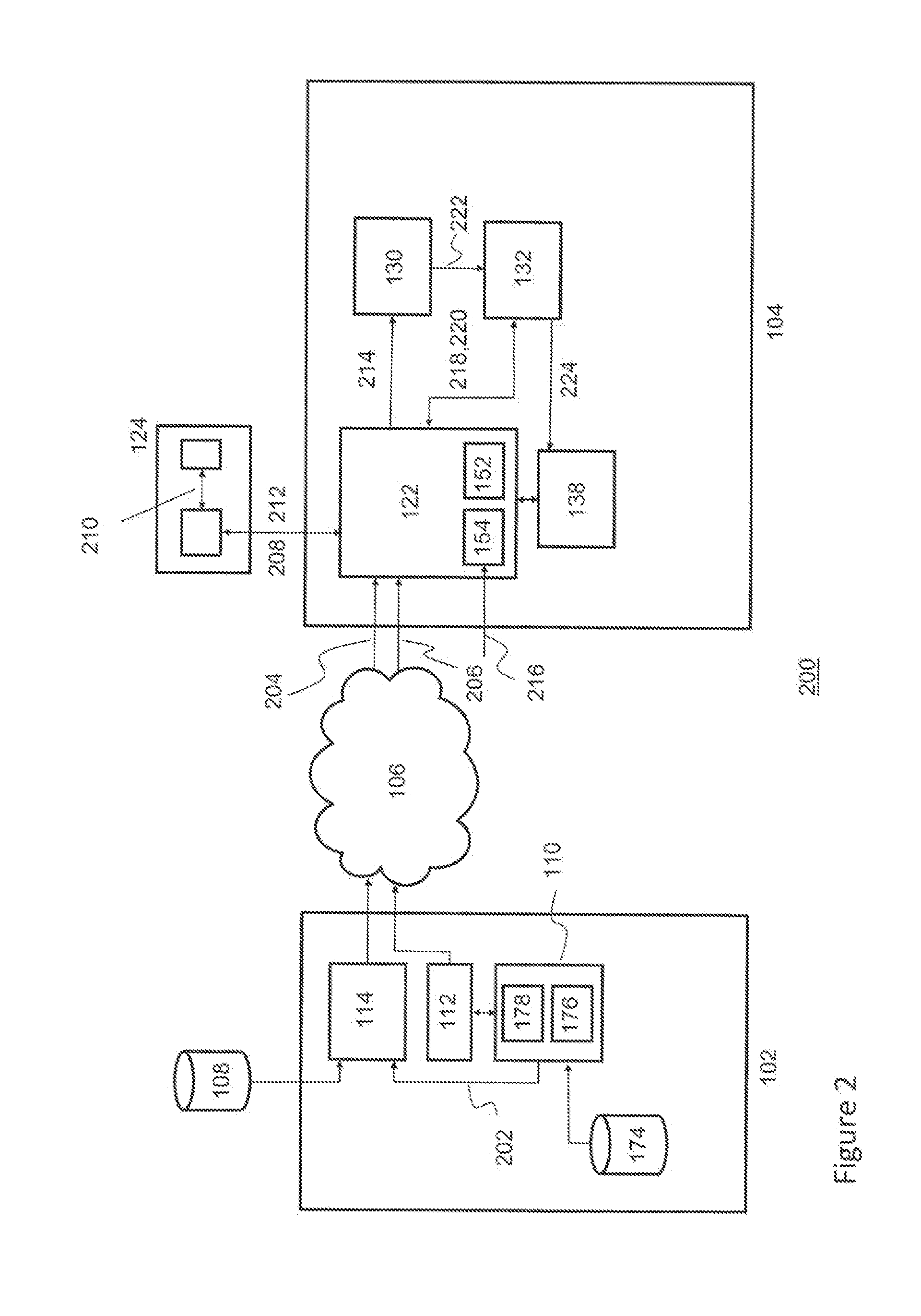
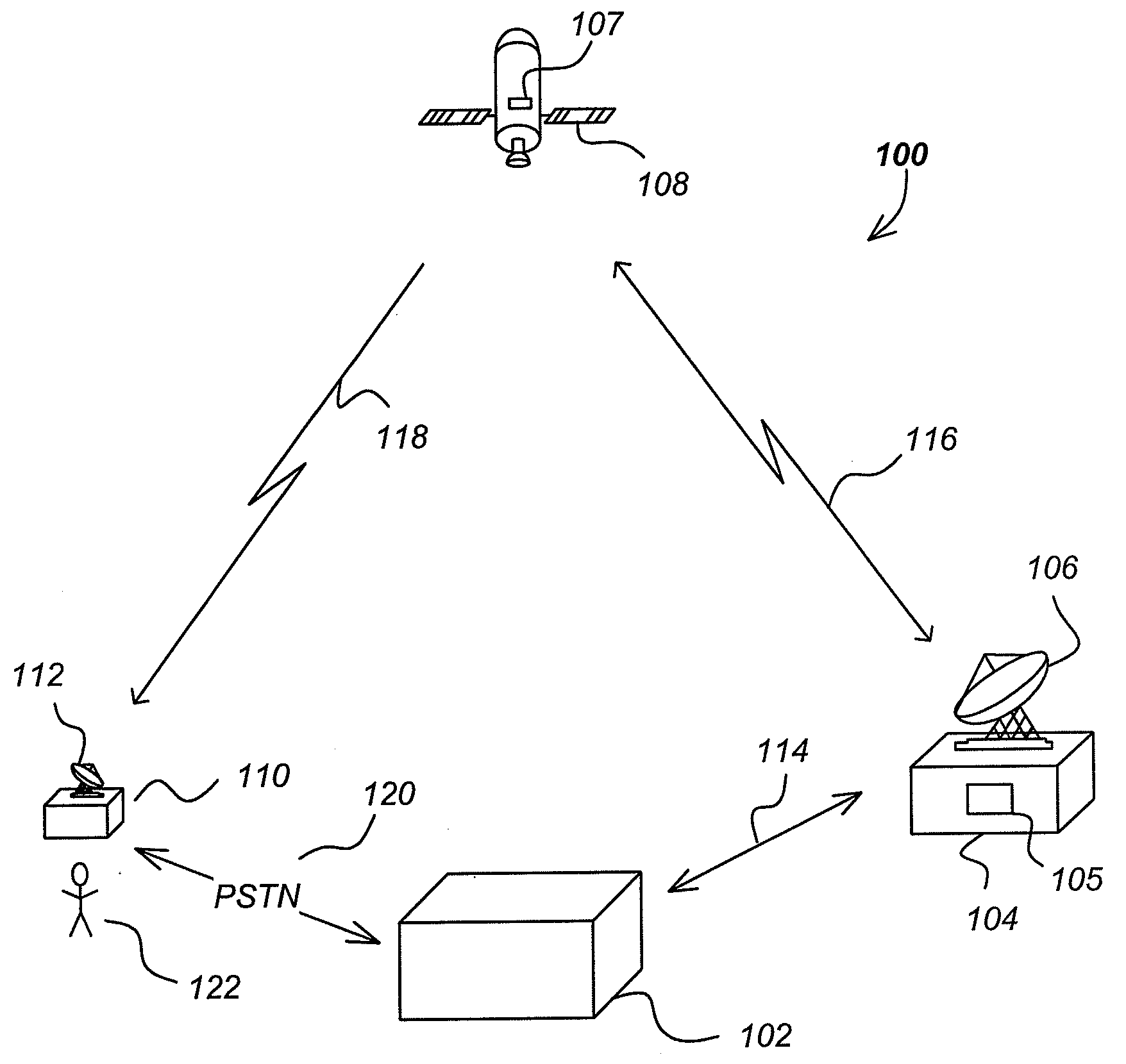
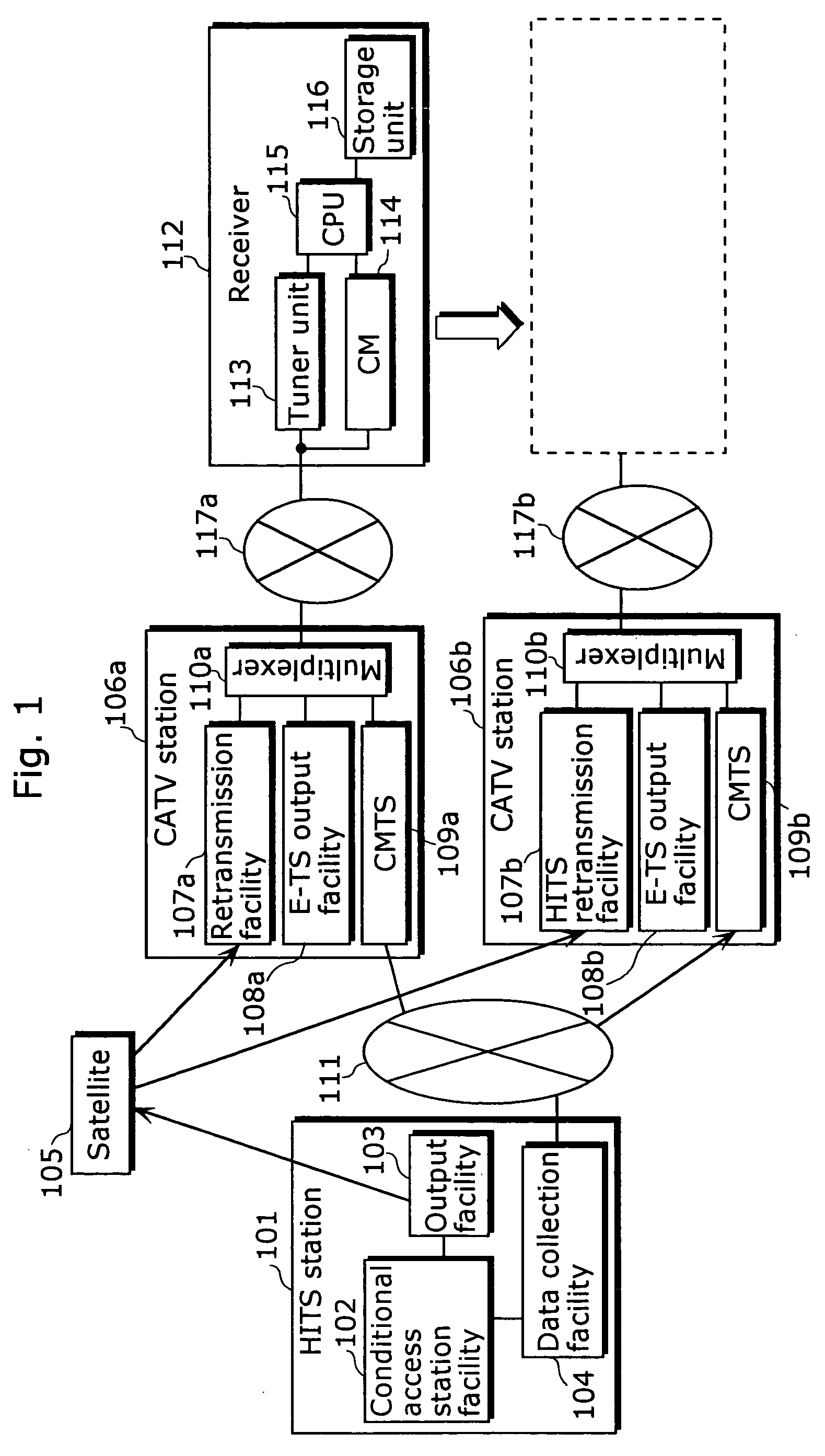
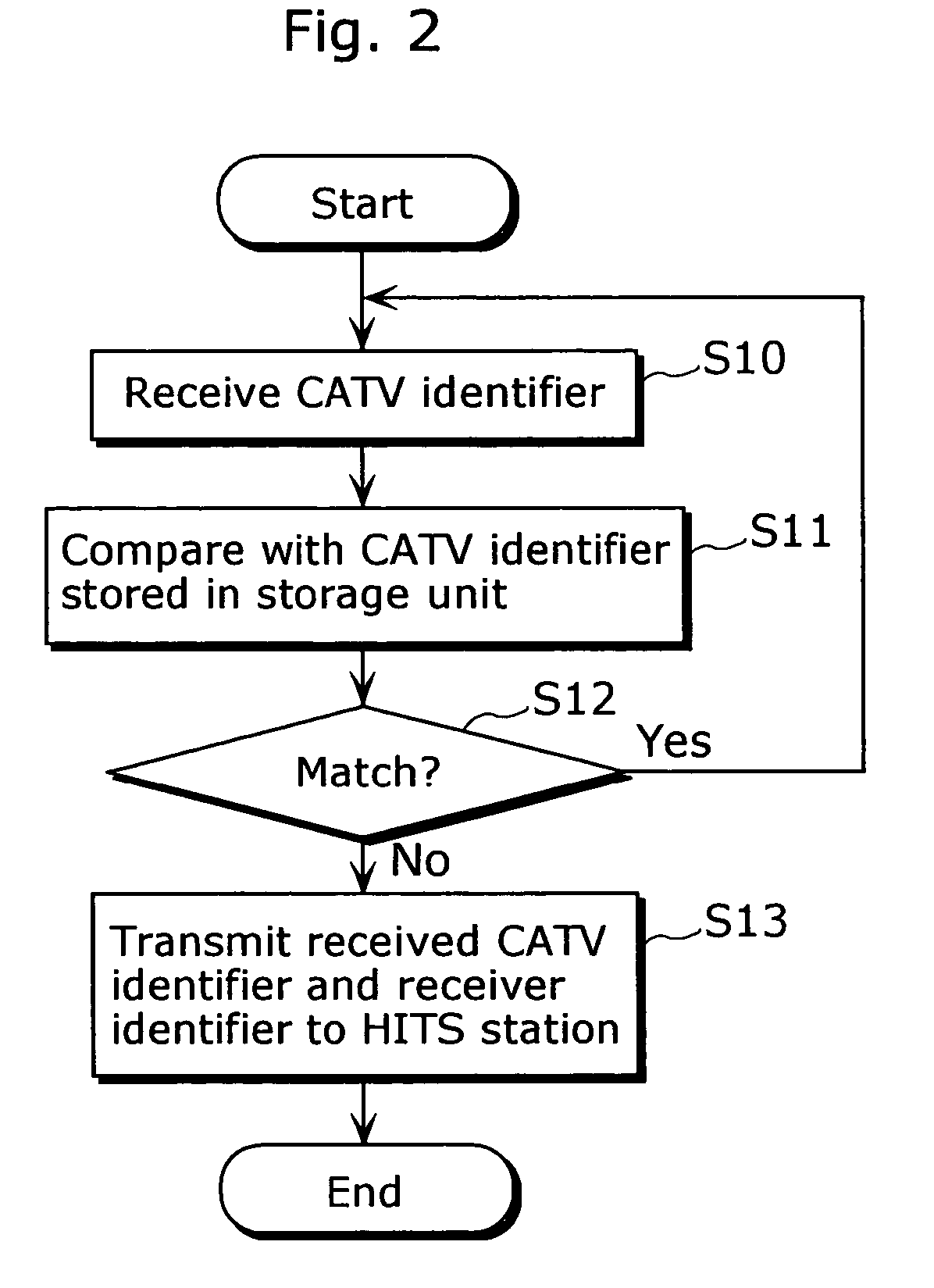
A conditional access system comprising: a HITS station 101 for transmitting a content to which only a receiver under contract for satellite TV subscriptions can have an access; a plurality of CATV stations 106a or the like for receiving and retransmitting the content transmitted from the HITS station 101; a receiver 112 for receiving the content retransmitted from the CATV station 106a, or the like. The receiver 112 includes: a storage unit 116 for storing a CATV station identifier for identifying the CATV station 106a with which the receiver 112 is under contract for satellite TV subscriptions, or the like; a cable modem 114 for receiving the CATV station identifier transmitted from the CATV station 106a or the like, judging whether or not the received CATV station identifier and the CATV station identifier stored in the storage unit 116 match, and transmitting, to the HITS station 101, relocation-between-stations information including a receiver identifier of the receiver 112 as well as the received CATV station identifier when judging that they do not match; and a CPU 115, and the like.
Owner:PANASONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com