Utilizing component targets in defining roles in a distributed and integrated system or systems
A definition and role technology, applied in the field of distributed computer systems, can solve problems such as restricting the use of the system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
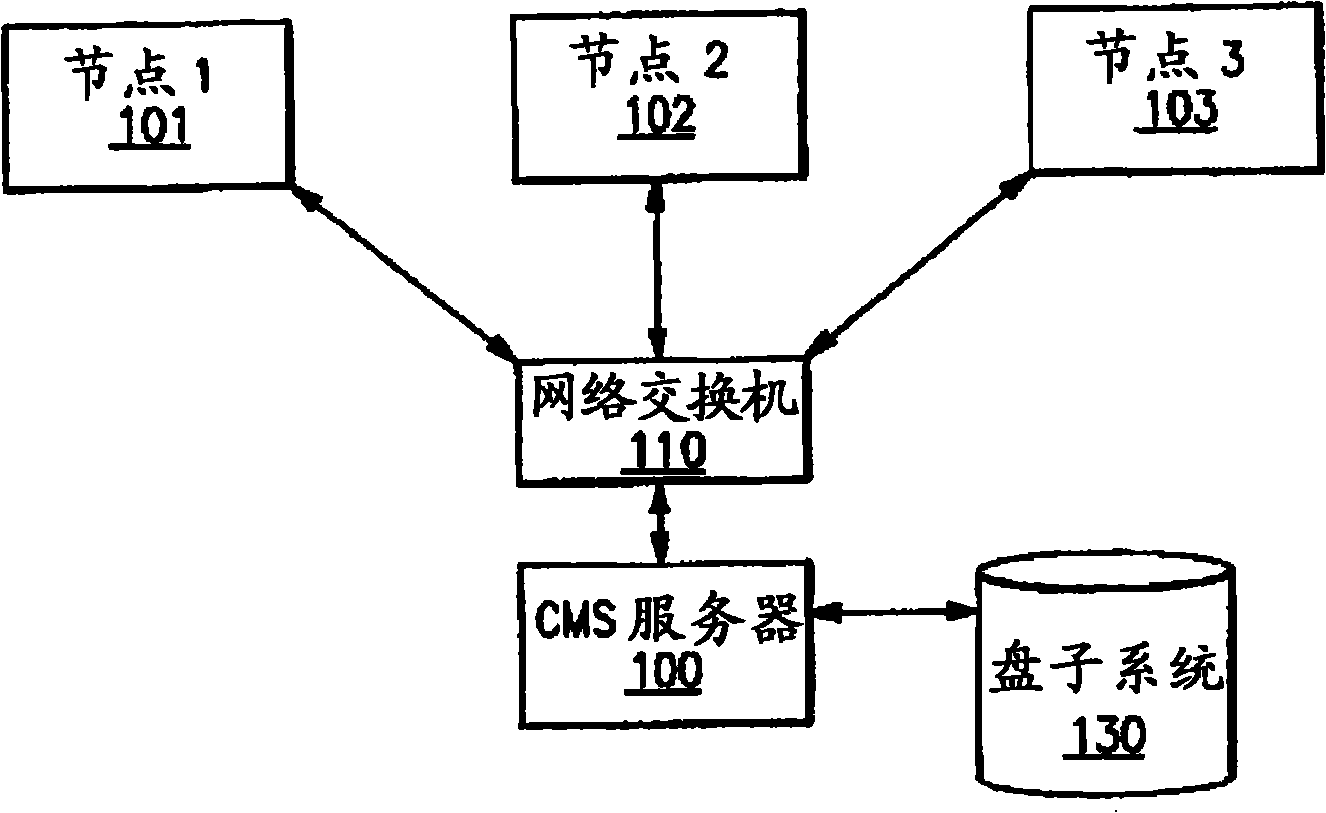
[0016] figure 1 A general cluster system environment is shown. The environment includes a central management server 100, preferably an IBM Cluster Management Server (CMS), and a set of nodes 101, 102, 103 in the cluster, preferably IBM's P-Series servers. These nodes are usually the target of administrative tasks. figure 1 Also shown are network switches, cabling and protocol stacks, designated 110, which are used by the various nodes and the CMS to communicate, and persistent storage 130, which is typically multiple disks similar to an IBM 2107 storage system driver.
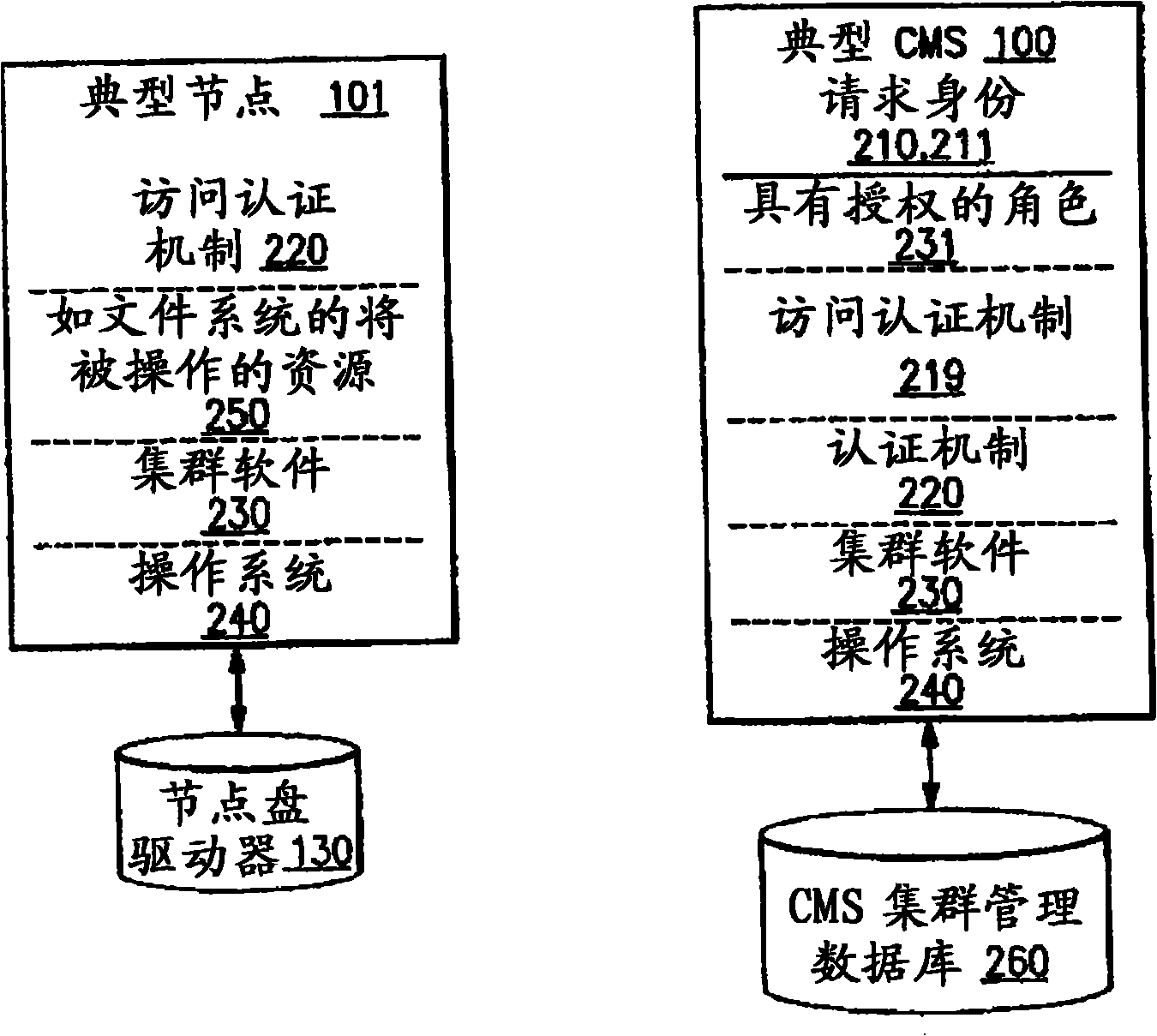
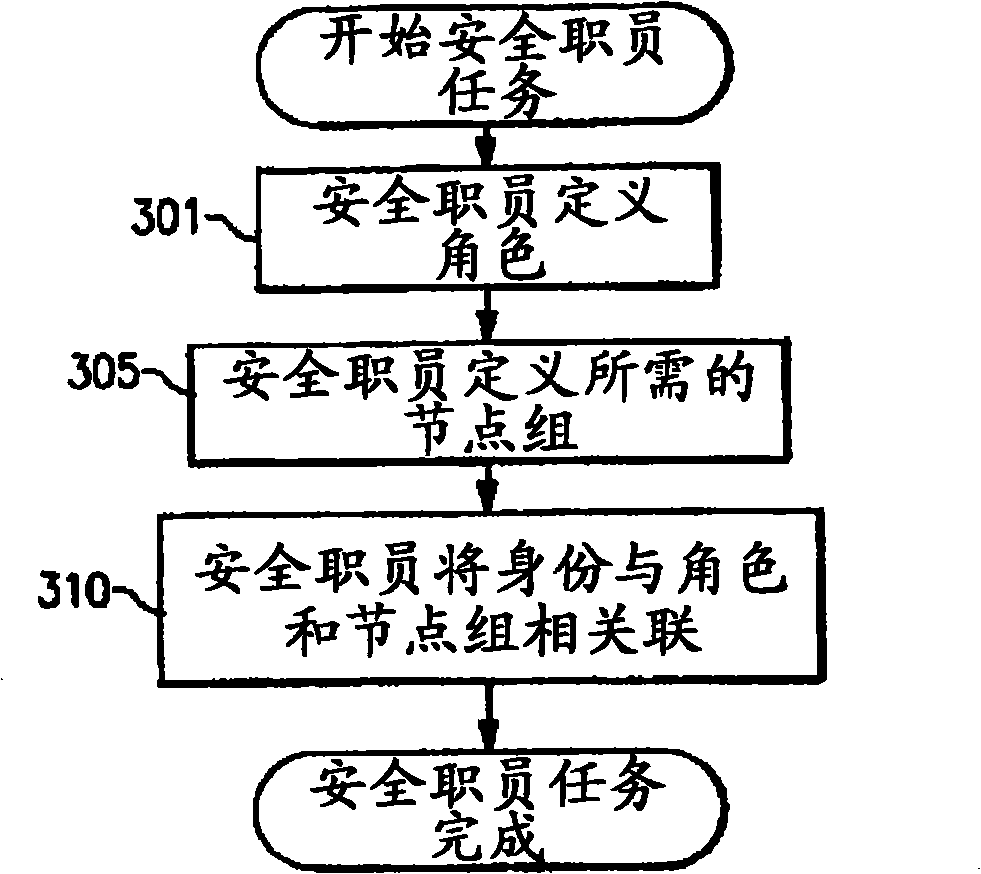
[0017] refer to figure 2 , at 210, 211 denote users or identities, which may for example be UNIX users with a UID structure as defined by the UNIX Open Group Standard. An authentication mechanism similar to MIT Kerberos is shown at 220, and a set of roles are shown at 231, 232, which are defined in the cluster as having the capability to perform one to N tasks. figure 2 The remote execution mechanism for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com