Patents
Literature
101 results about "Truth table" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
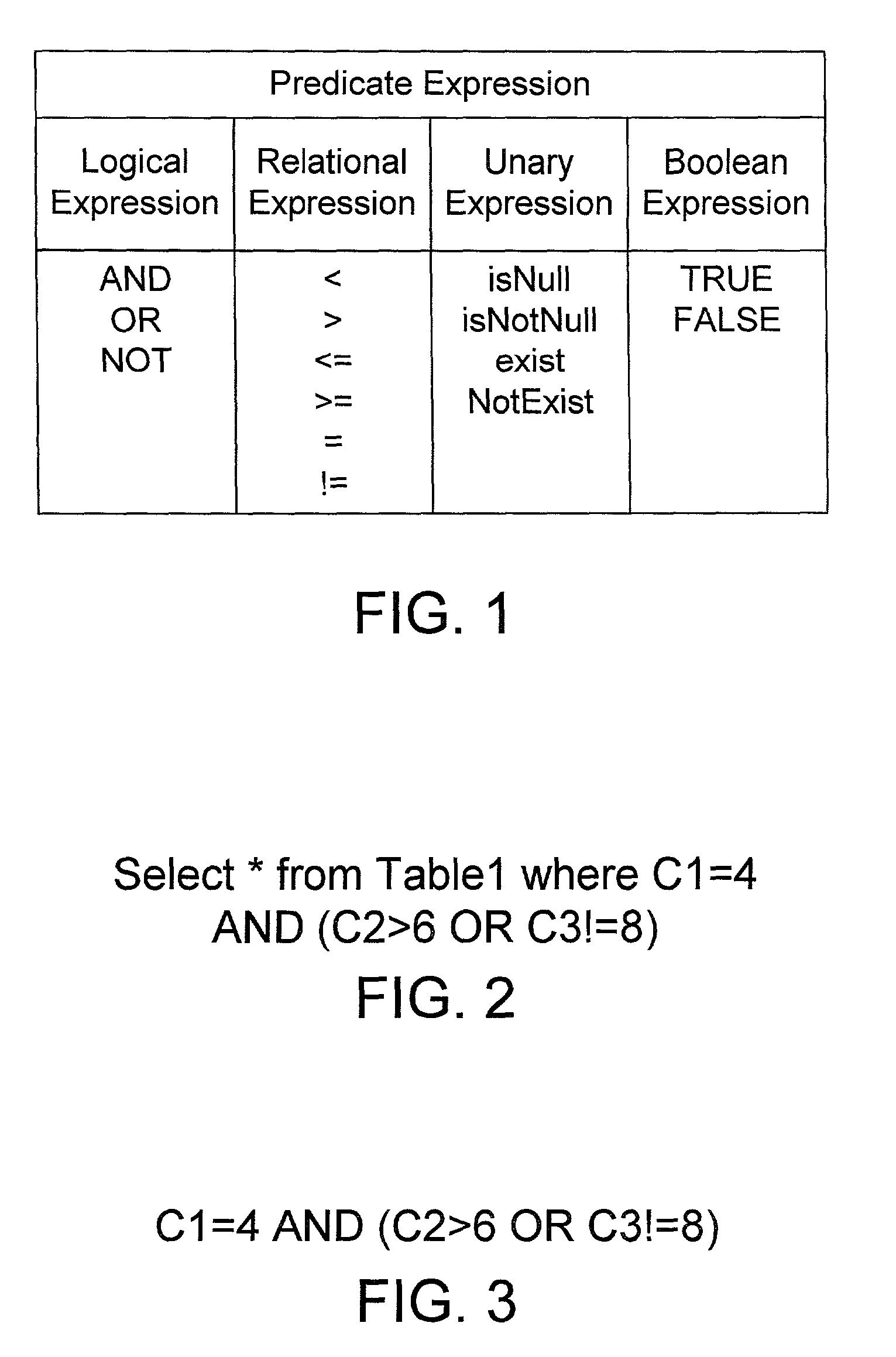
A truth table is a mathematical table used in logic—specifically in connection with Boolean algebra, boolean functions, and propositional calculus—which sets out the functional values of logical expressions on each of their functional arguments, that is, for each combination of values taken by their logical variables (Enderton, 2001). In particular, truth tables can be used to show whether a propositional expression is true for all legitimate input values, that is, logically valid.
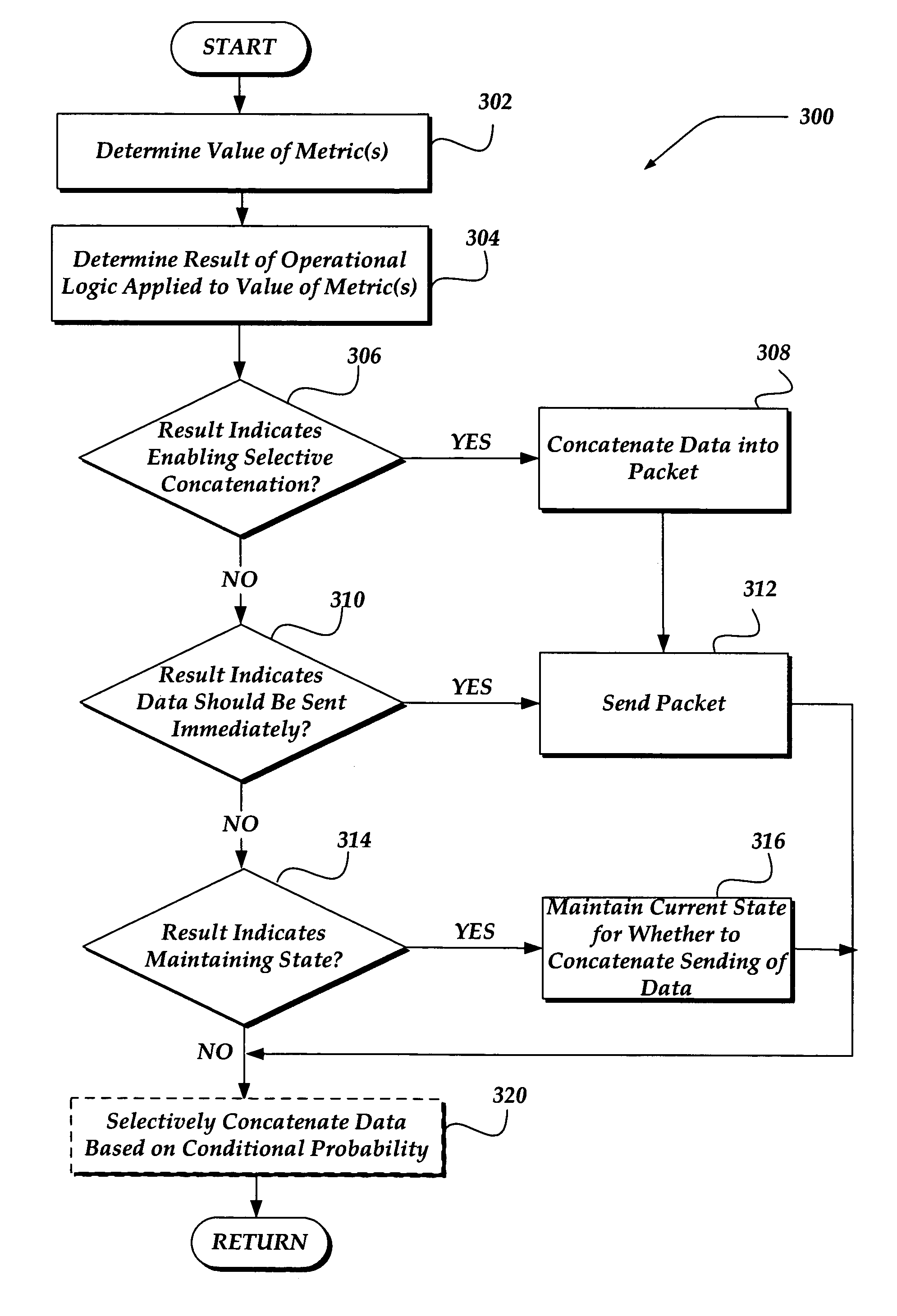
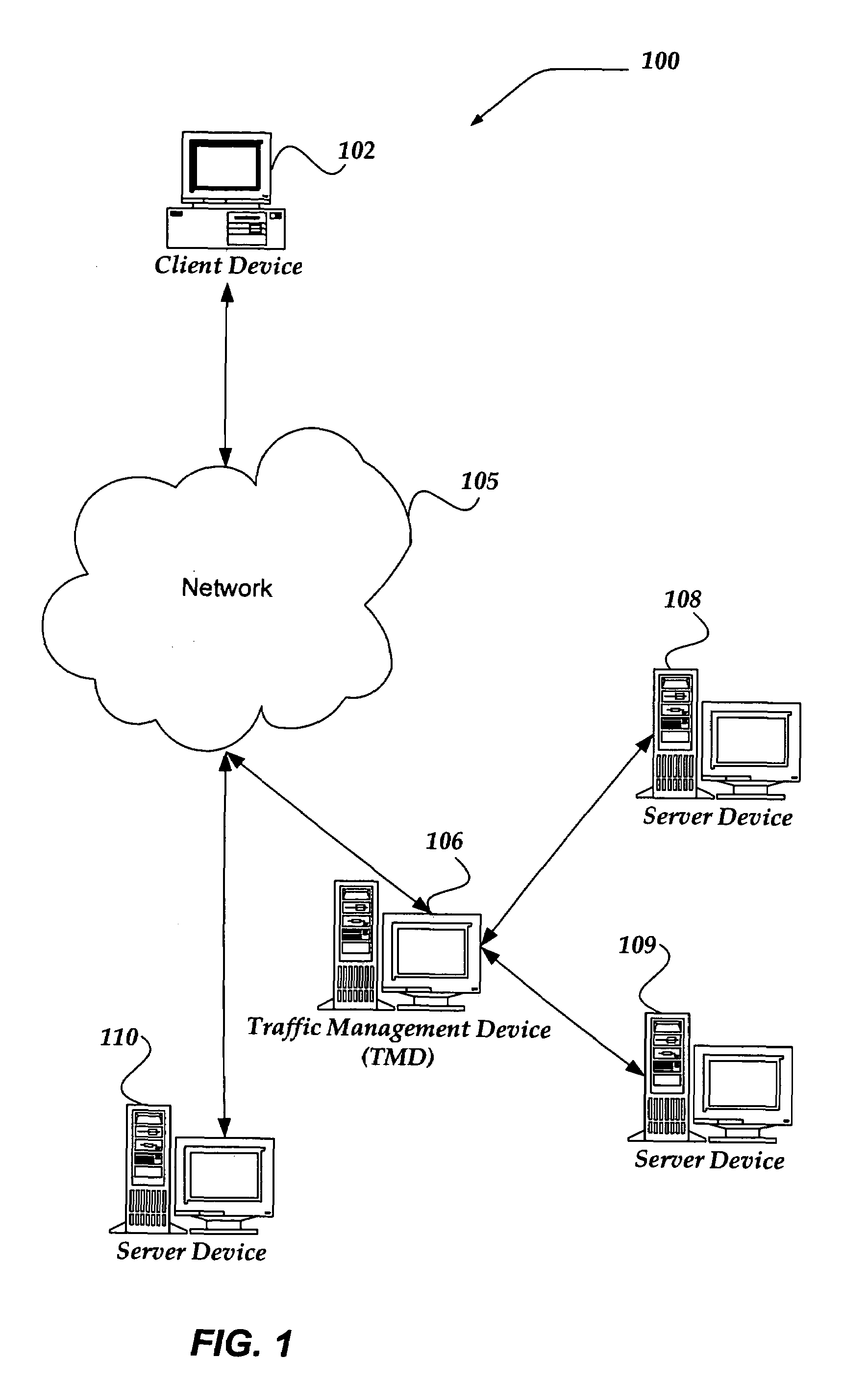
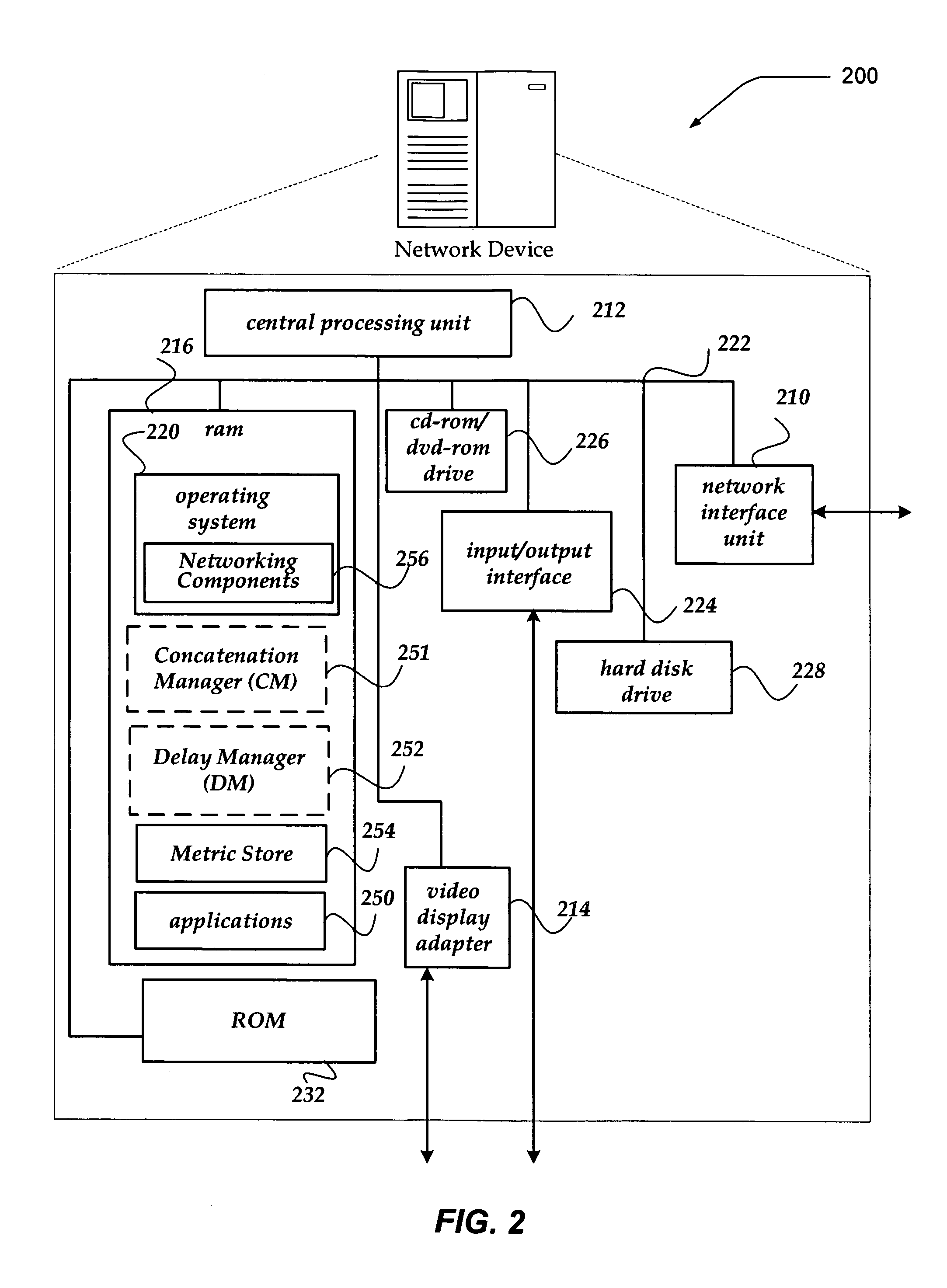
Selectively enabling network packet concatenation based on metrics
InactiveUS7873065B1Data switching by path configurationStore-and-forward switching systemsData connectionNetwork packet
A method, system, and apparatus are directed towards selectively concatenating data into a packet to modify a number of packets transmitted over a network based on a combination of network and / or send-queue metrics. In one embodiment, Nagle's algorithm is used for concatenating data into a packet. The concatenation may be selectively enabled based on heuristics applied to the combination of metrics. In one embodiment, the result may indicate that there should be a concatenation, or that data should be sent immediately, or that a current state for whether to concatenate or not should be maintained. The heuristics may include an expert system, decision tree, truth table, function, or the like. The heuristics may be provided by a user, or another computing device. In another embodiment, the concatenation may be enabled based on a conditional probability determined from the combination of metrics.
Owner:F5 NETWORKS INC
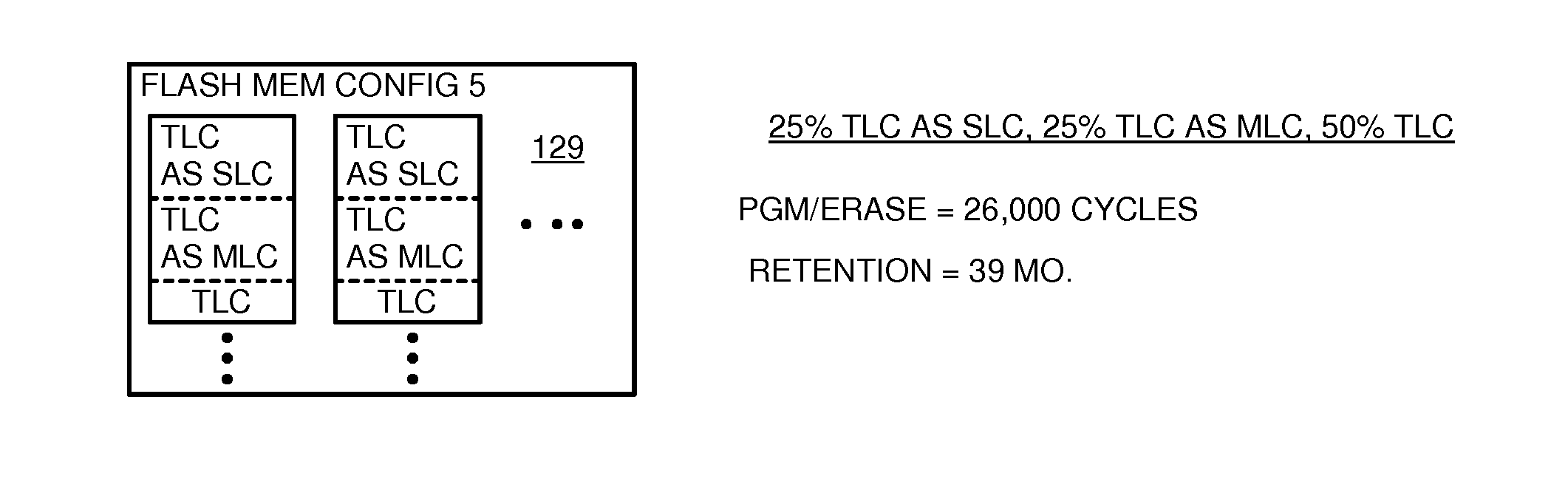
Endurance and retention flash controller with programmable binary-levels-per-cell bits identifying pages or blocks as having triple, multi, or single-level flash-memory cells
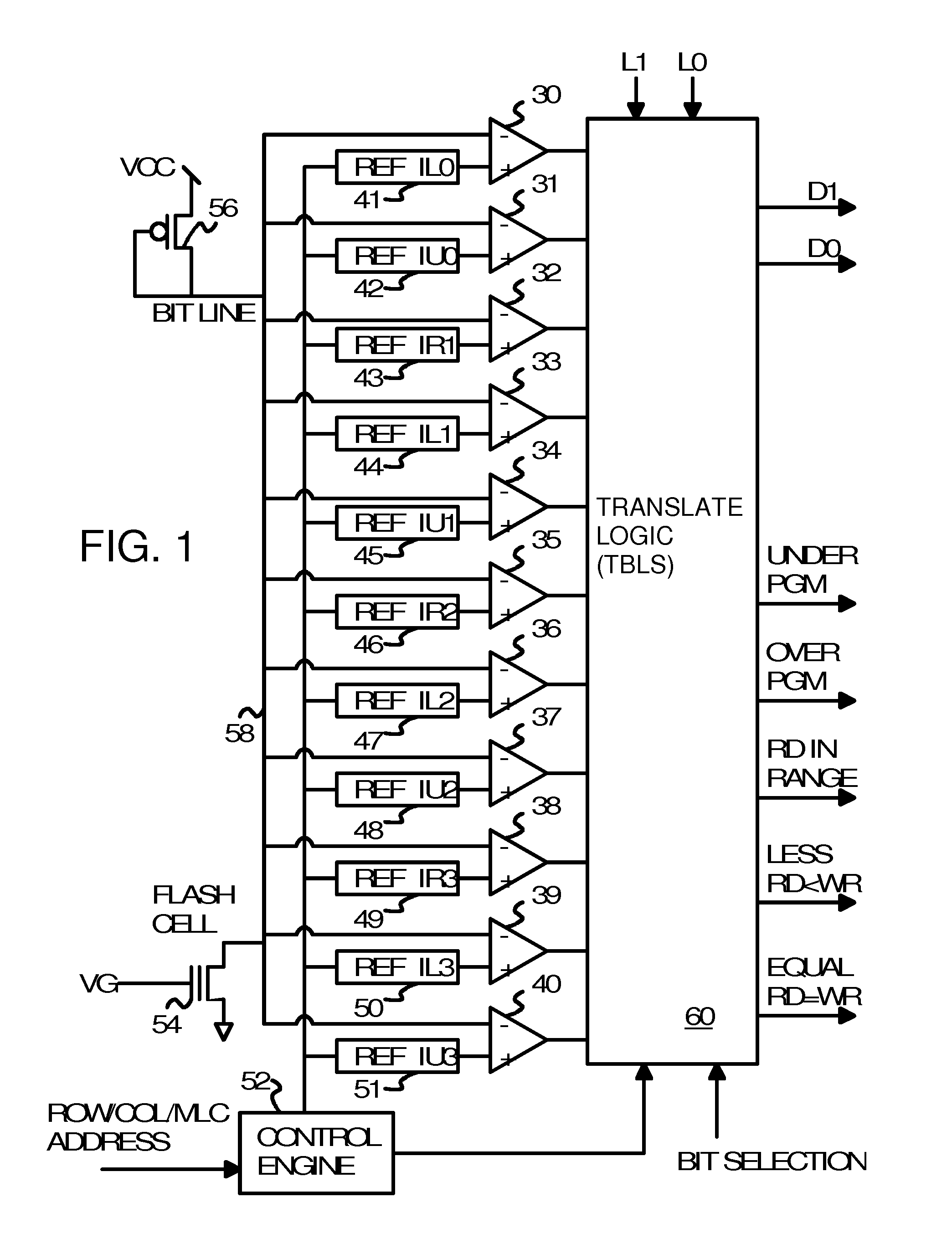
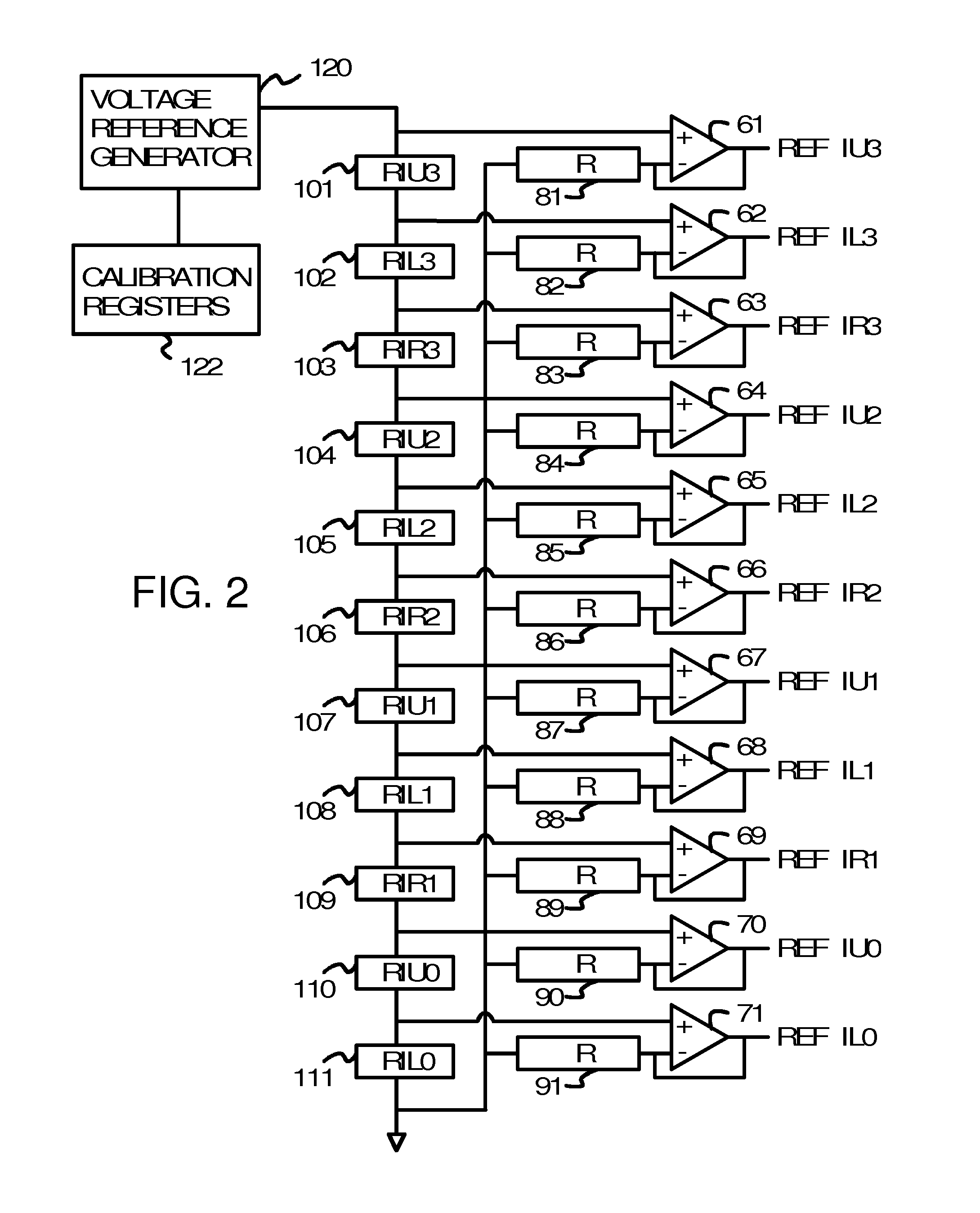
InactiveUS9123422B2Memory architecture accessing/allocationMemory adressing/allocation/relocationTruth valueRetention time
An retention flash controller reads assigned-level bits from a bad block / erase count table or from a page status table that indicate when flash memory cells operate as Triple-Level-Cell (TLC), Multi-Level-Cell (MLC), or Single-Level-Cell (SLC). Pages that fail as TLC or MLC are downgraded for use as SLC pages by changing the assigned-level bits. The level bits adjust truth tables used by translation logic that receives inputs from voltage comparators reading a bit line. The range of voltages for each logic level may be adjusted by the truth tables or by programmable registers. The programming voltage or programming pulses may be adjusted to increase endurance and the number of permitted program-erase cycles while reducing retention times before a refresh is needed of the flash cells. Mixed configurations of flash memory have MLC blocks and MLC as SLC blocks, or other combinations.
Owner:SUPER TALENT TECH CORP
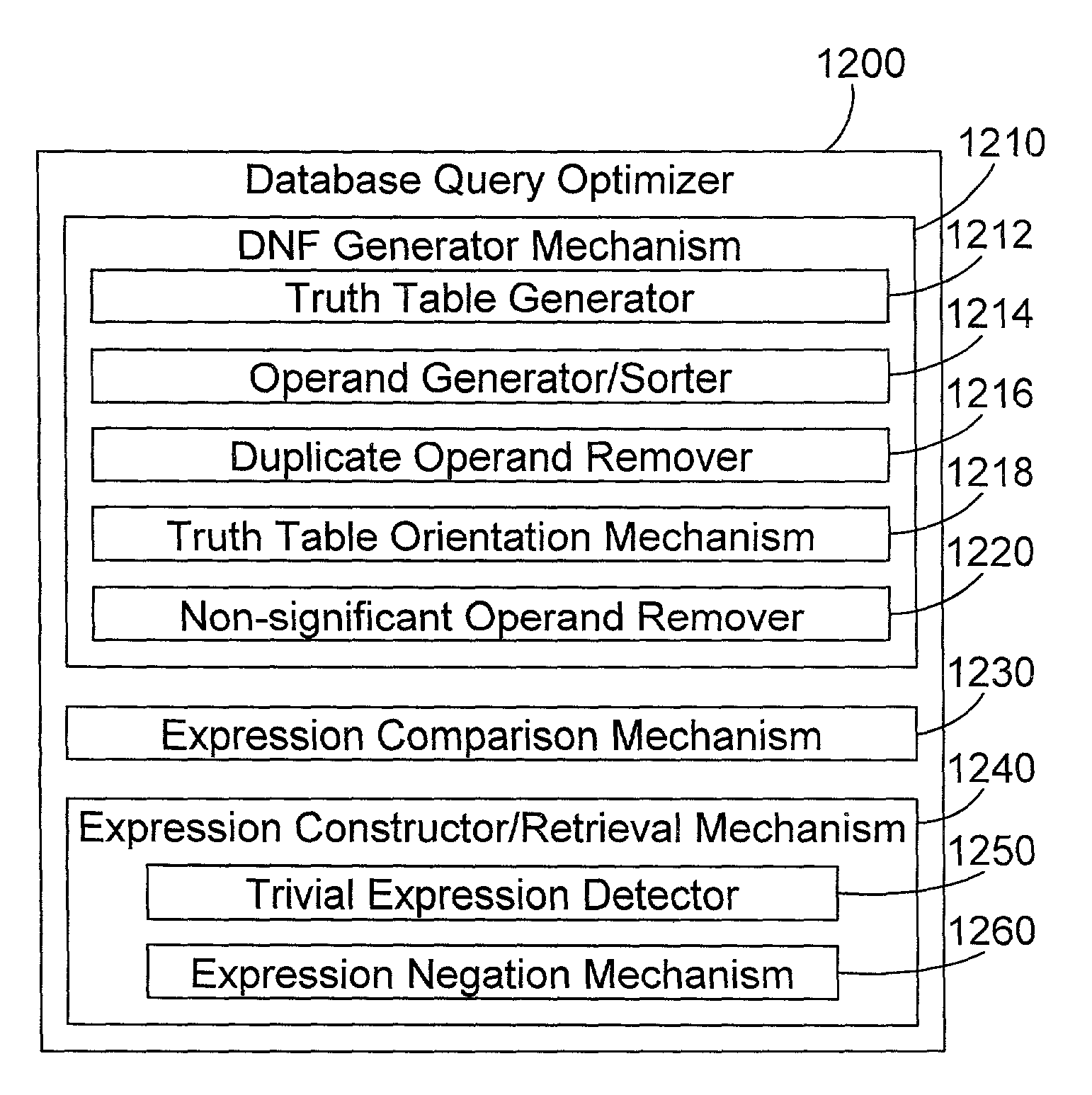
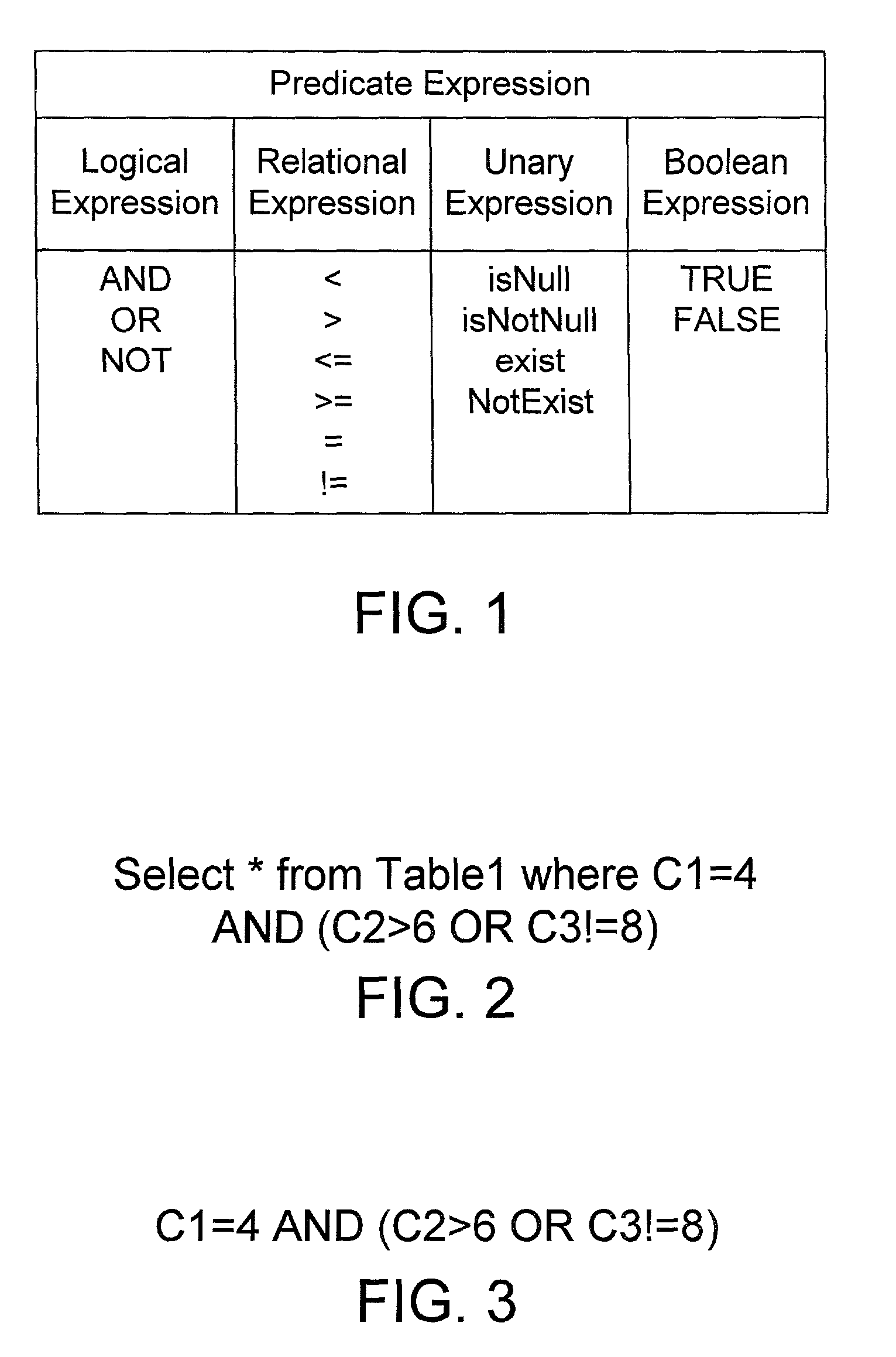
Database query optimization apparatus and method
InactiveUS6968330B2Easy constructionData processing applicationsDigital data information retrievalDatabase queryTruth value
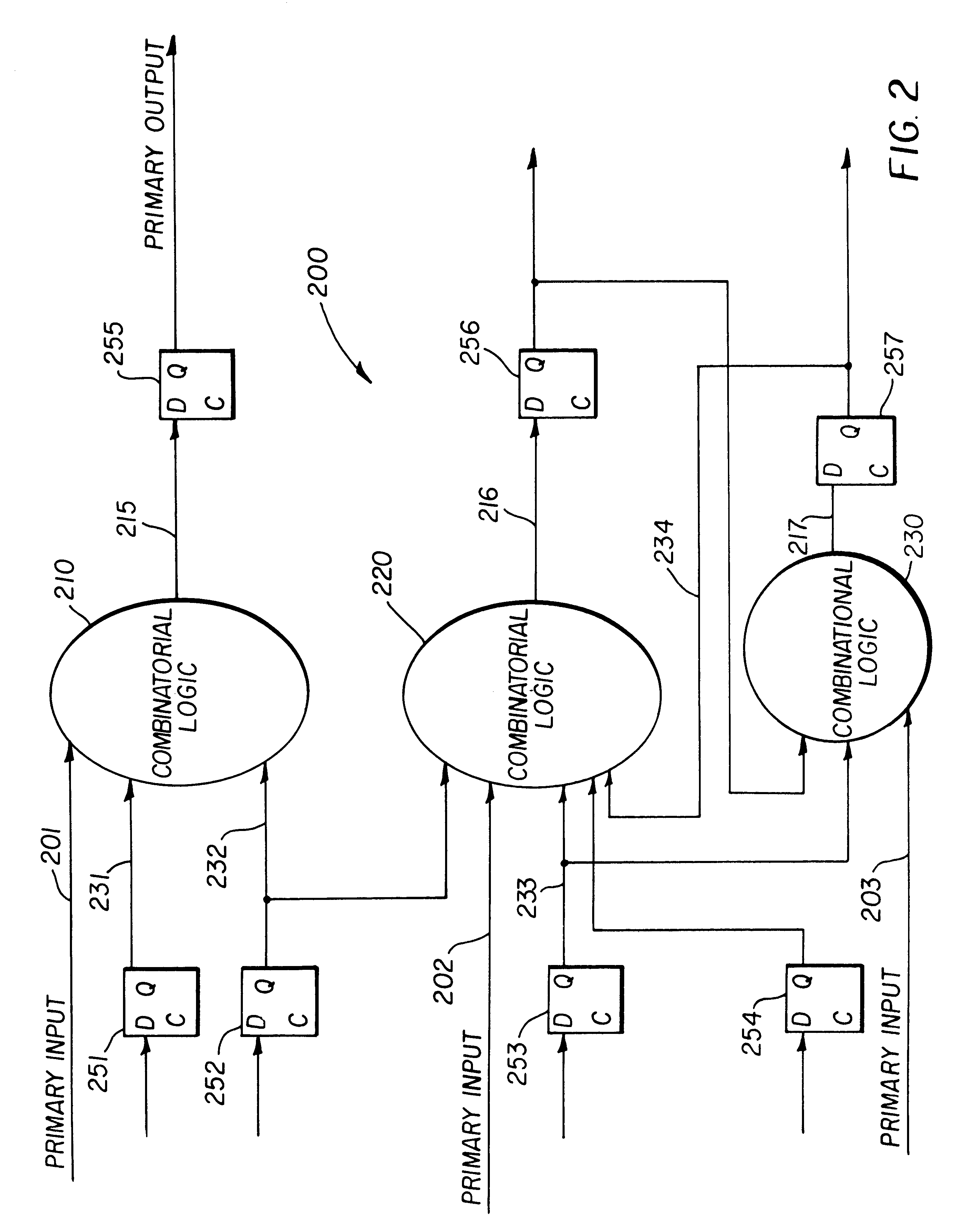
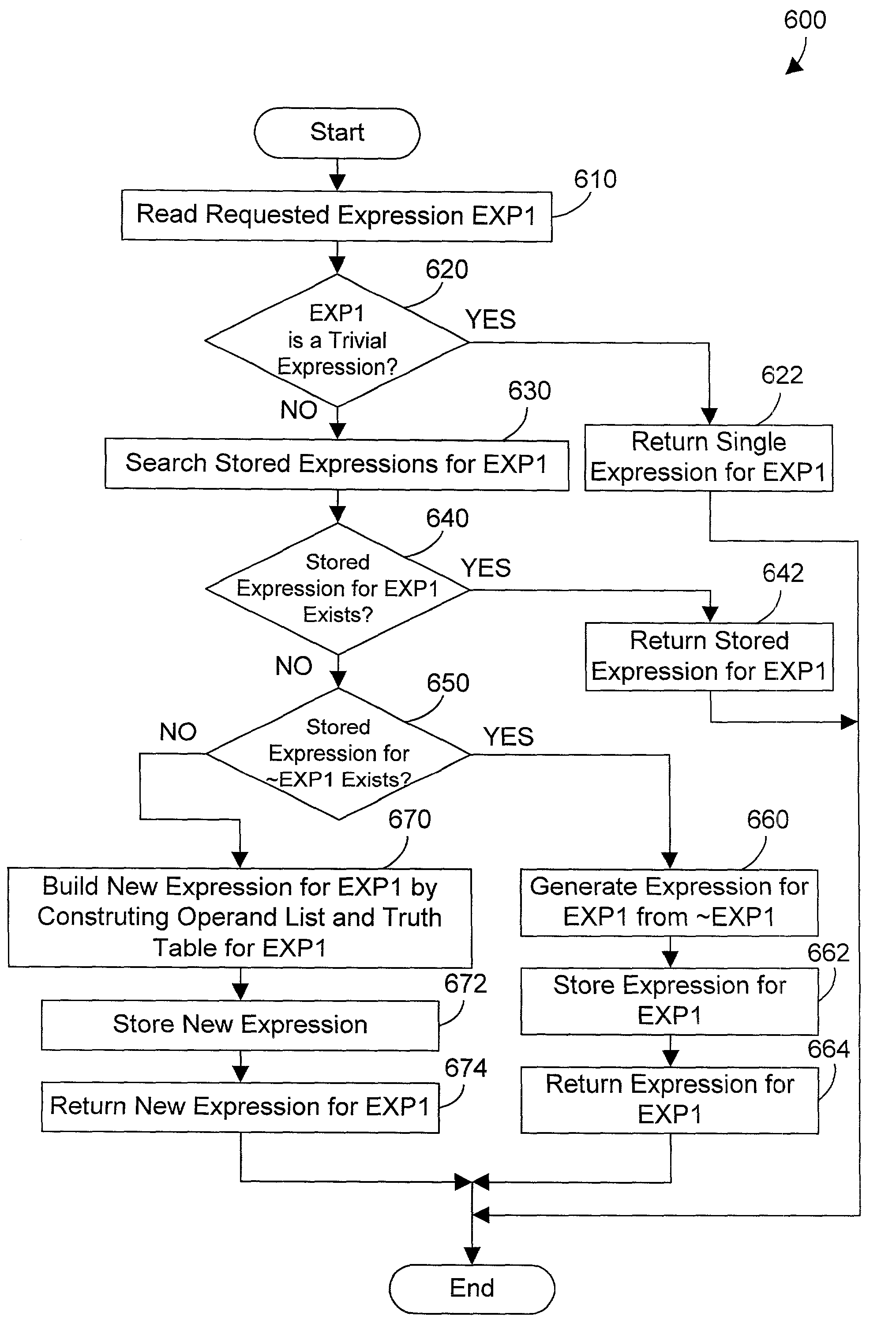
A database query optimizer processes an expression in a database query, and generates therefrom an operand list and a corresponding truth table that may be represented by a list of binary characters, where the operand list and corresponding truth table represent a disjunct normal form for the expression. Each expression is stored once it is processed into its operand list and corresponding list of binary characters. New queries are processed into component expressions, and each expression is checked to see if the expression was previously processed and stored as a processed expression. If so, the operand list and list of binary characters for the previously-stored expression may be used in processing the current expression. If there is no previously-stored expression that corresponds to the current expression, the previously-stored expressions are checked to see if any correspond to a complement of the current expression. If so, a new expression is easily constructed for the current expression by retrieving the list of binary characters that correspond to the complement expression, and inverting the bits in the list of binary characters. If there is no previously-stored expression that corresponds to the current expression or its complement, an operand list and corresponding list of binary characters are generated for the current expression. Logical operations between predicates in a query may be performed by performing mathematical operations on the lists of binary characters corresponding to each predicate expression. The end result is an operand list and corresponding list of binary characters that represents the entire expression in a query.
Owner:INT BUSINESS MASCH CORP
System and method for providing automated investment alerts from multiple data sources
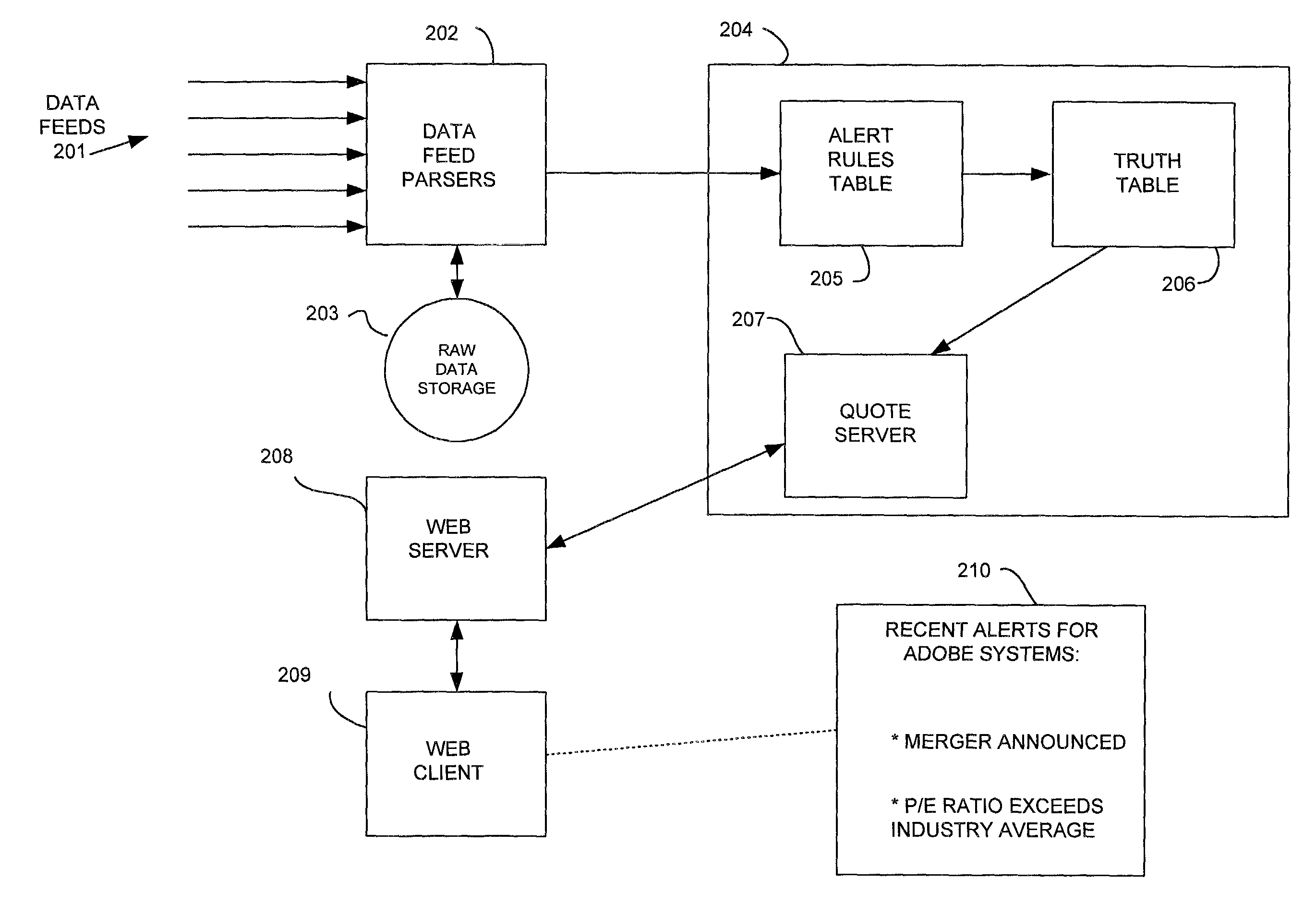
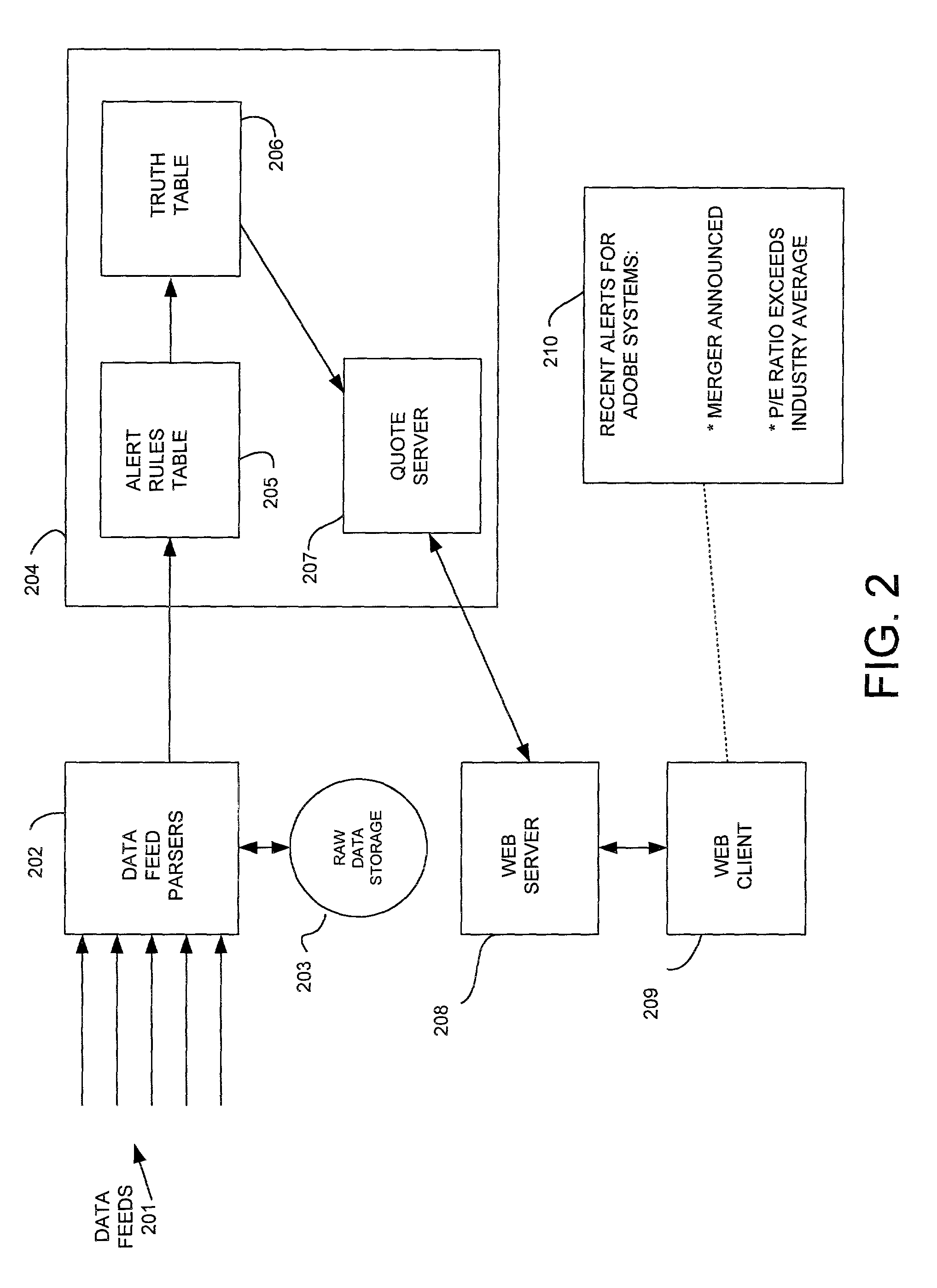
A system and method provides investors with meaningful information extracted from large volumes of available data for a particular stock, mutual fund, bond, or other investment. The system includes one or more computers that receive and process multiple data feeds to extract information relating to each type of investment. The processed data is compared to “alert rules” each corresponding to a predefined condition, and a truth table is established that identifies alerts that are true for each particular investment. An investor logs onto a web site and enters a stock ticker symbol or similar investment identifier. Computer software displays a web page including “alerts” that are presently true for that particular investment. The alerts can be predefined by financial experts to make them useful to novice investors. When an investor selects a particular investment, a display is generated showing all of the alerts that are true for that investment and allowing the user to get more information concerning the significance of the alerts. The alerts can be grouped into different categories according to their content or time sensitivity.
Owner:MICROSOFT TECH LICENSING LLC
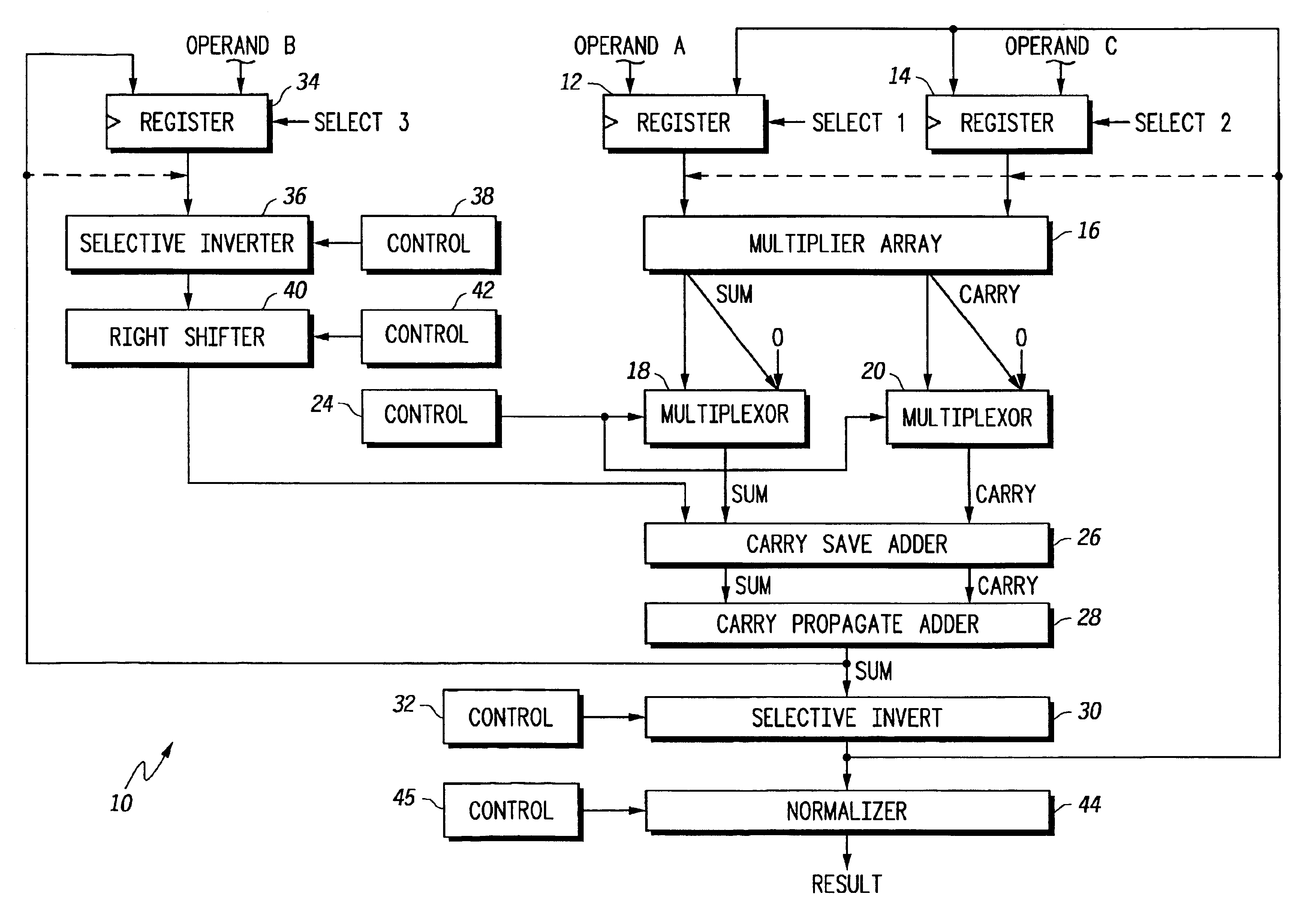
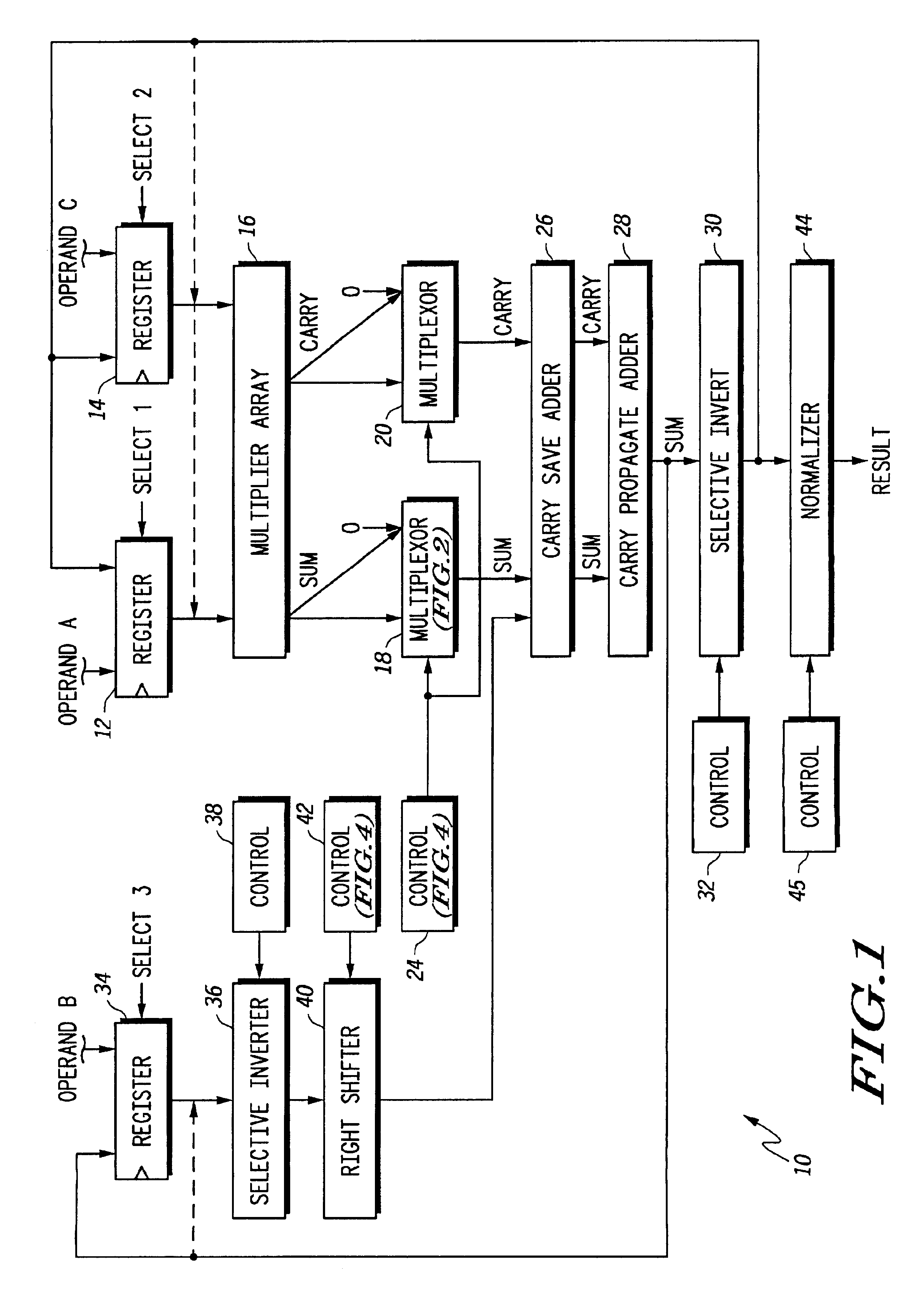
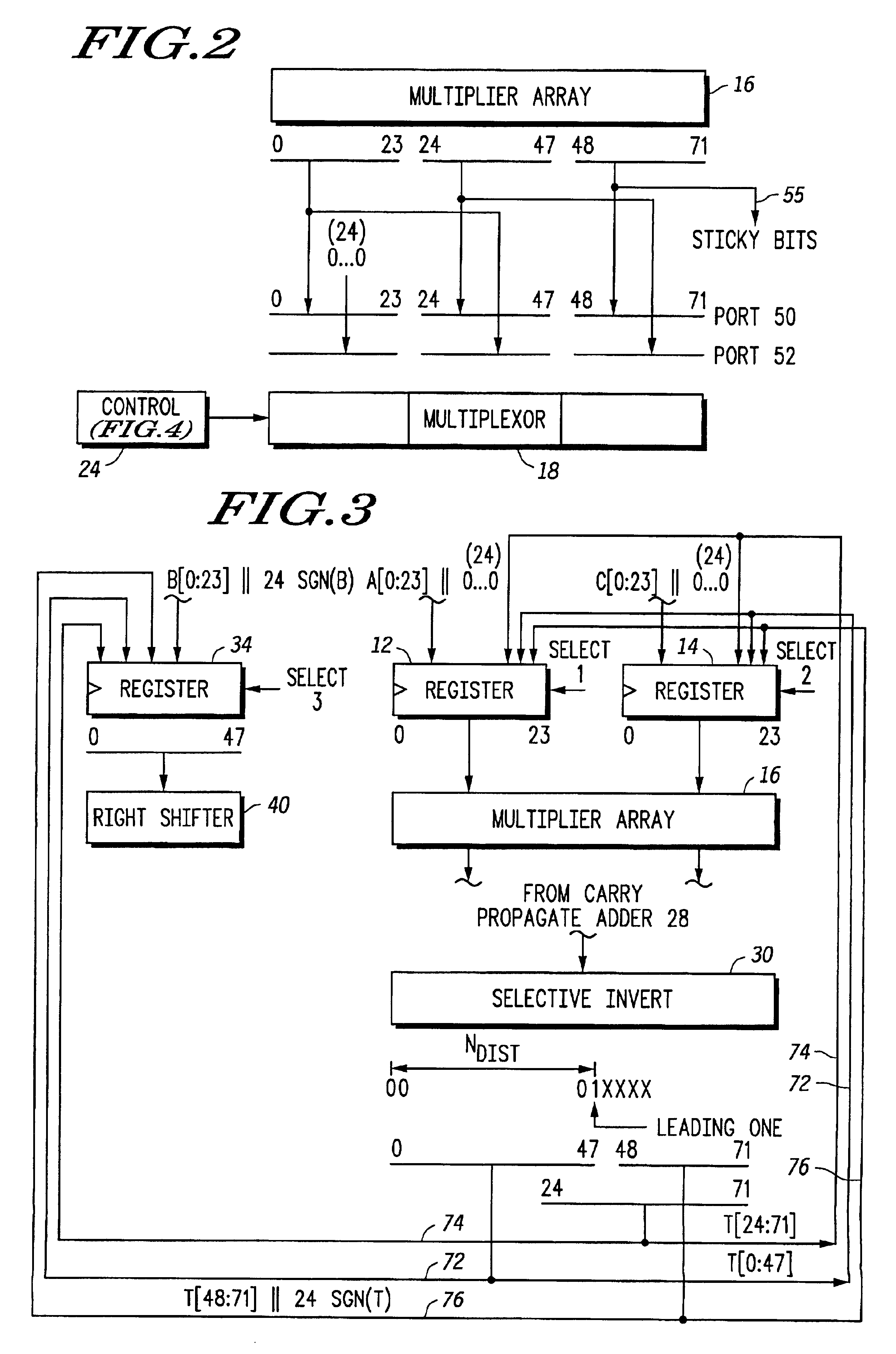
Floating point multiplier/accumulator with reduced latency and method thereof
A circuit (10) for multiplying two floating point operands (A and C) while adding or subtracting a third floating point operand (B) removes latency associated with normalization and rounding from a critical speed path for dependent calculations. An intermediate representation of a product and a third operand are selectively shifted to facilitate use of prior unnormalized dependent resultants. Logic circuitry (24, 42) implements a truth table for determining when and how much shifting should be made to intermediate values based upon a resultant of a previous calculation, upon exponents of current operands and an exponent of a previous resultant operand. Normalization and rounding may be subsequently implemented, but at a time when a new cycle operation is not dependent on such operations even if data dependencies exist.
Owner:NORTH STAR INNOVATIONS
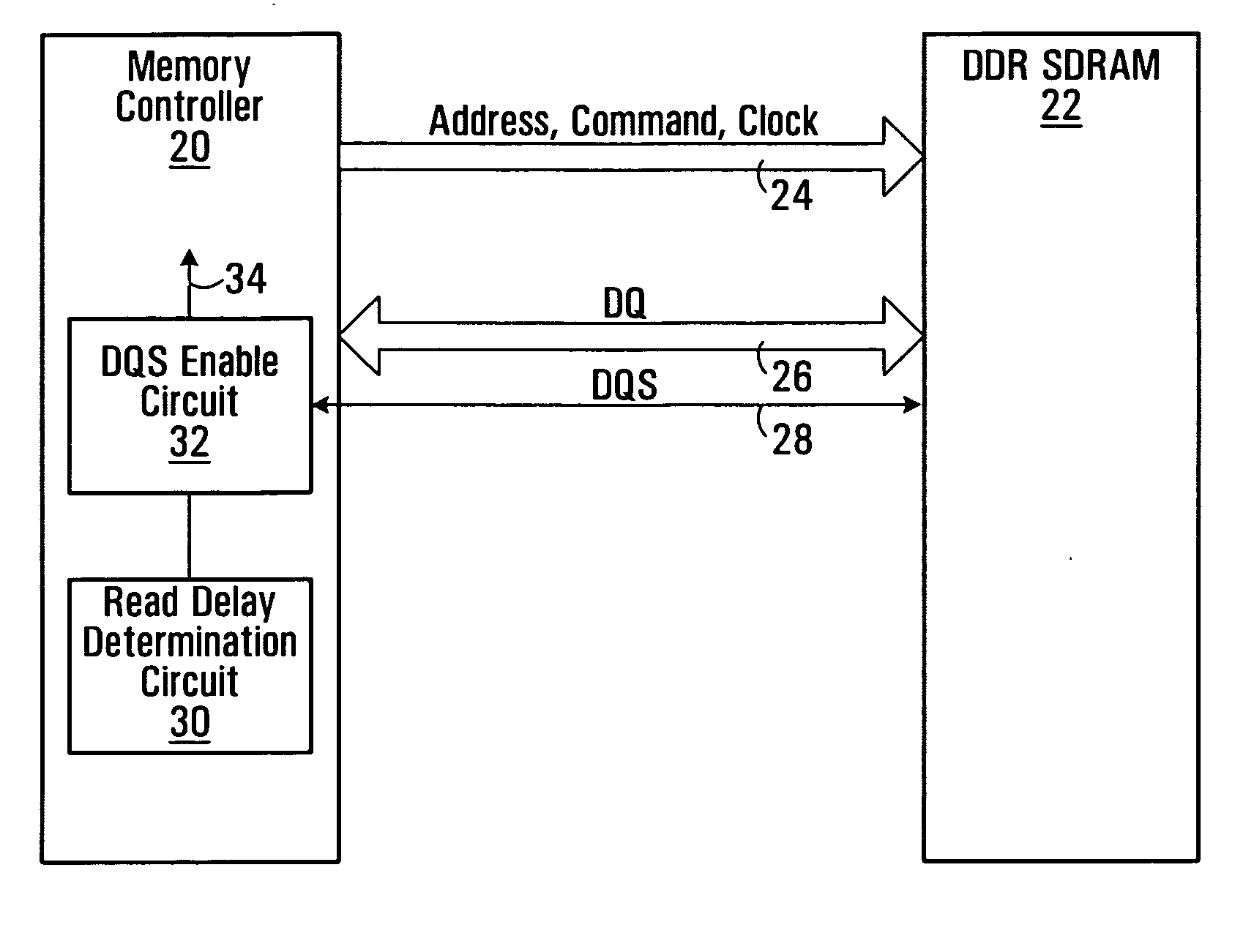
Synchronous memory read data capture
ActiveUS20080005518A1Simple and low latencyDigital storageMemory systemsLatency (engineering)Computer science
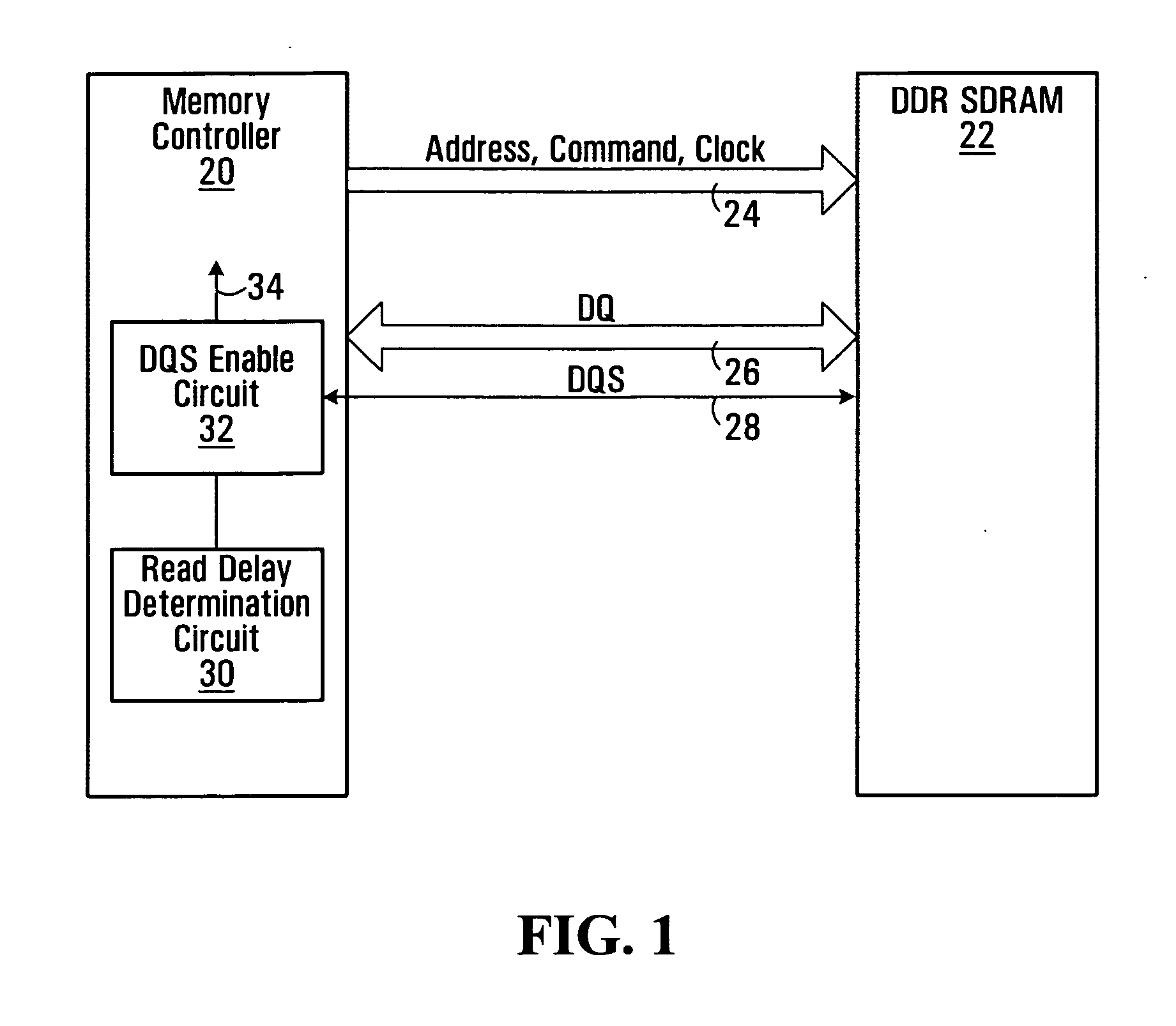
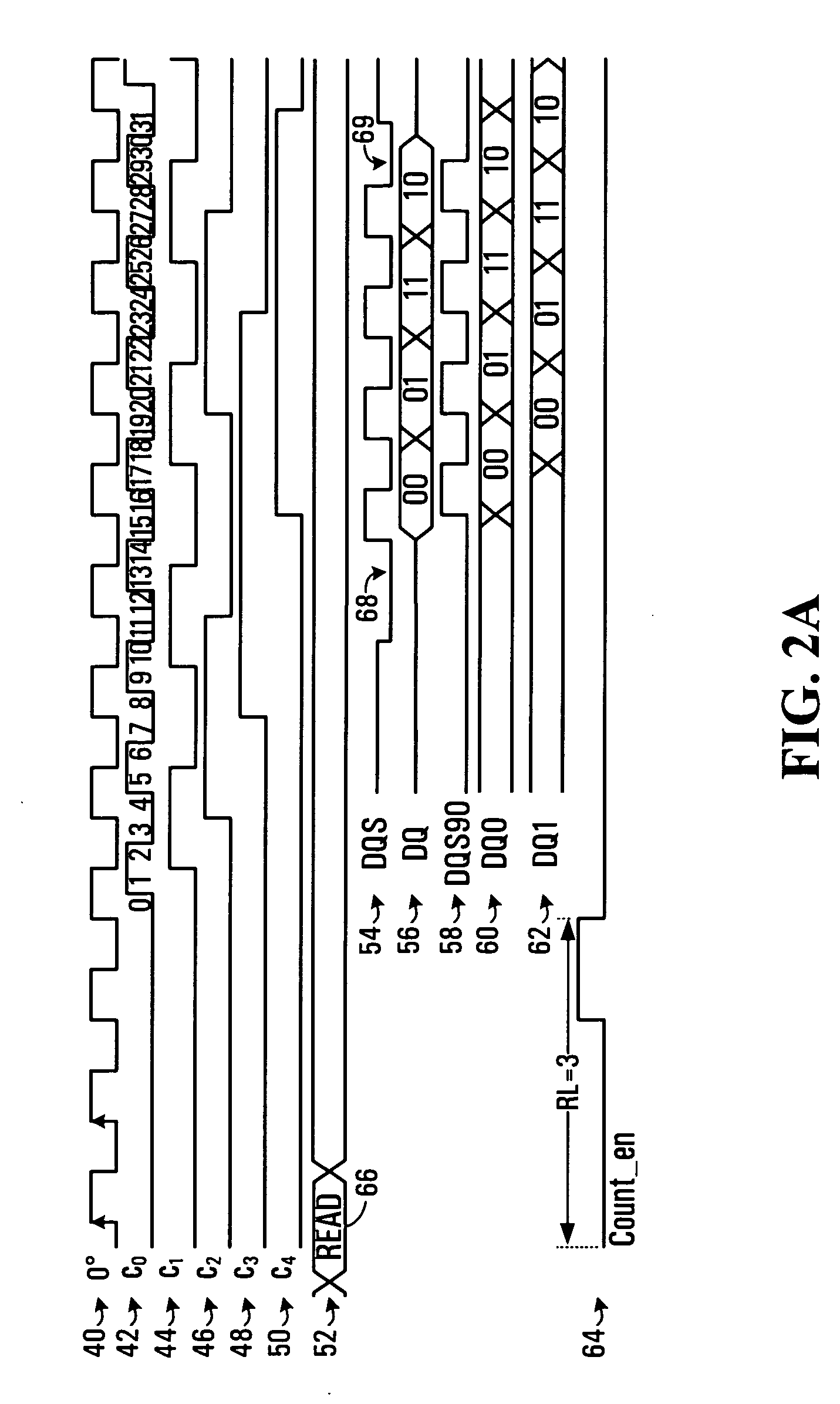
A method of snap-shot data training to determine the optimum timing of the DQS enable signal in a single read operation is provided. This is accomplished by first writing a Gray code count sequence into the memory and then reading it back in a single burst. The controller samples the read burst at a fixed interval from the time the command was issued to determine the loop-around delay. A simple truth table lookup determines the optimum DQS enable timing for normal reads. Advantageously, during normal read operations, the first positive edge of the enabled DQS signal is used to sample a counter that is enabled every time a command is issued. If the counter sample changes, indicating timing drift has occurred, the DQS enable signal can be adjusted to compensate for the drift and maintain a position centered in the DQS preamble. This technique can also be applied to a system that uses the iterative approach to determining DQS enable timing on power up. Another embodiment of the invention is a simple, low latency clock domain crossing circuit based on the DQS latched sample of the counter.
Owner:MOSAID TECH
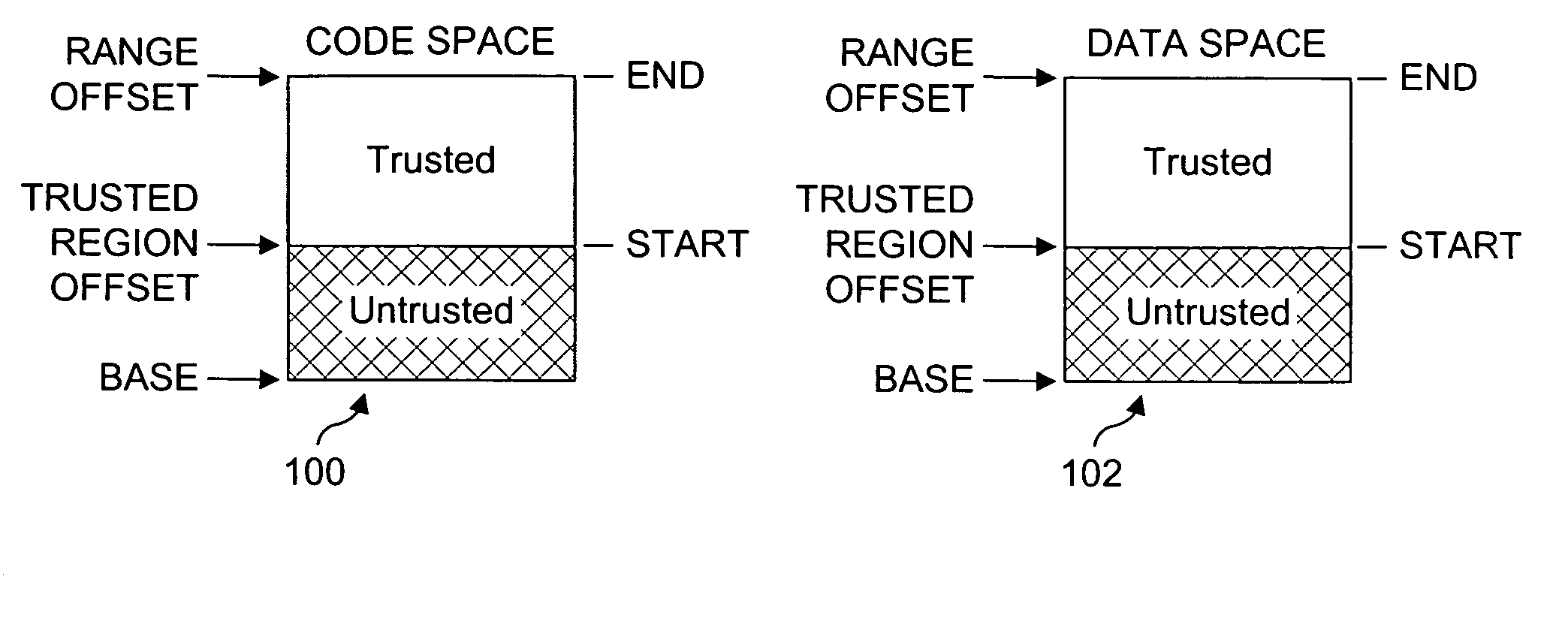
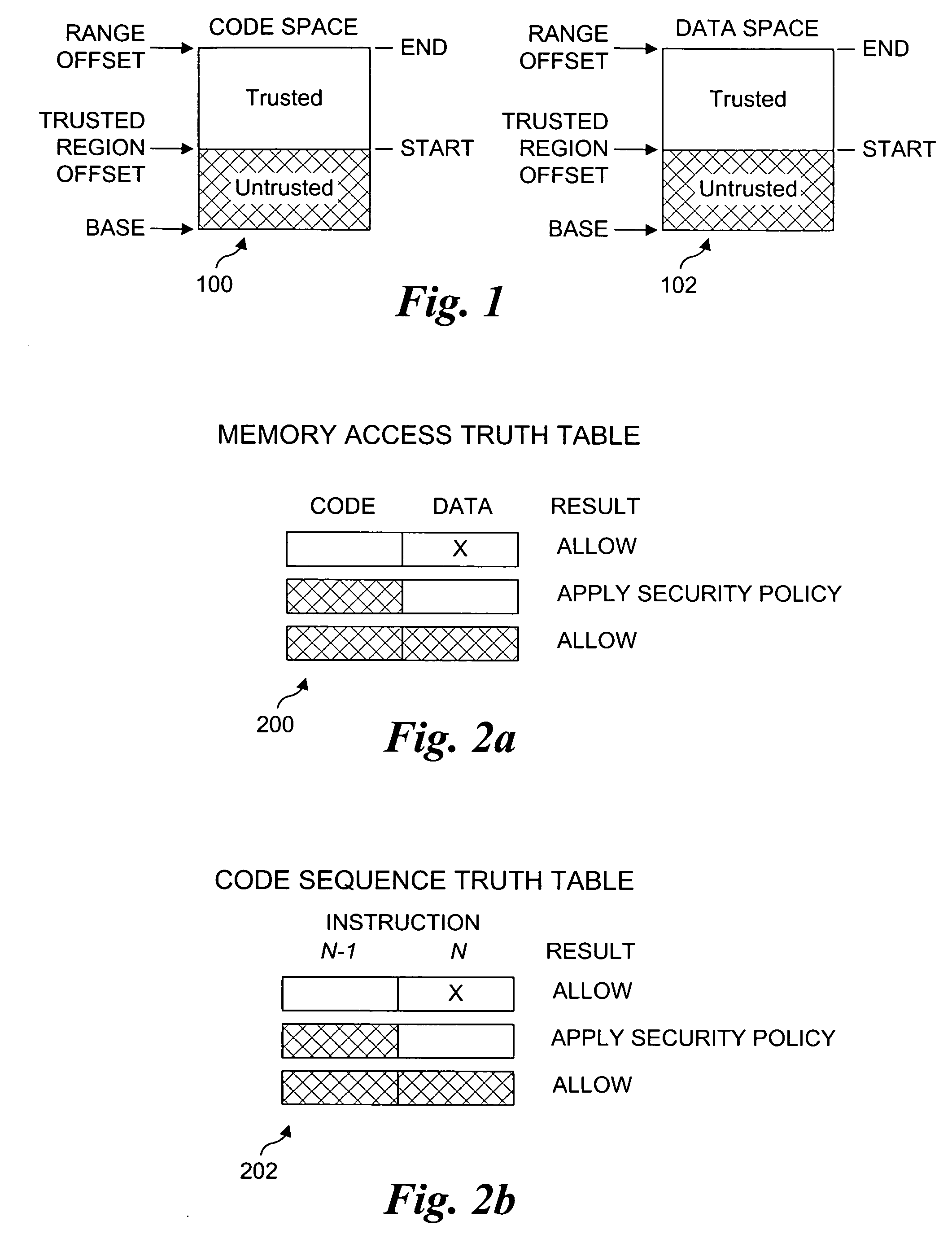
Processor extensions and software verification to support type-safe language environments running with untrusted code
Processor extensions and software verification to support type-safe language environments running with untrusted code. Code and data spaces are partitioned into trusted and untrusted regions. Type-safe code is loaded into the trusted region of the code space, while non-type-safe code is loaded into the untrusted region of the code space. The trusted region of the data space is allocated to the type-safe code. The untrusted region of the data space is allocated to the non-type-safe code. Hardware-based truth tables are employed for defining allowable and disallowable code sequences and memory access operations. For code sequences, allowable operations are based on the location (i.e., region) of a code sequence including a current instruction and a prior instruction. For memory access, the location of the requesting instruction and data requested are considered. Disallowed code sequence or memory access operations cause the processor to generate a safe access protection trap. In response to the safe access protection trap, a software-based dynamic verifier applies a security policy to determine whether to allow the operation to proceed.
Owner:INTEL CORP
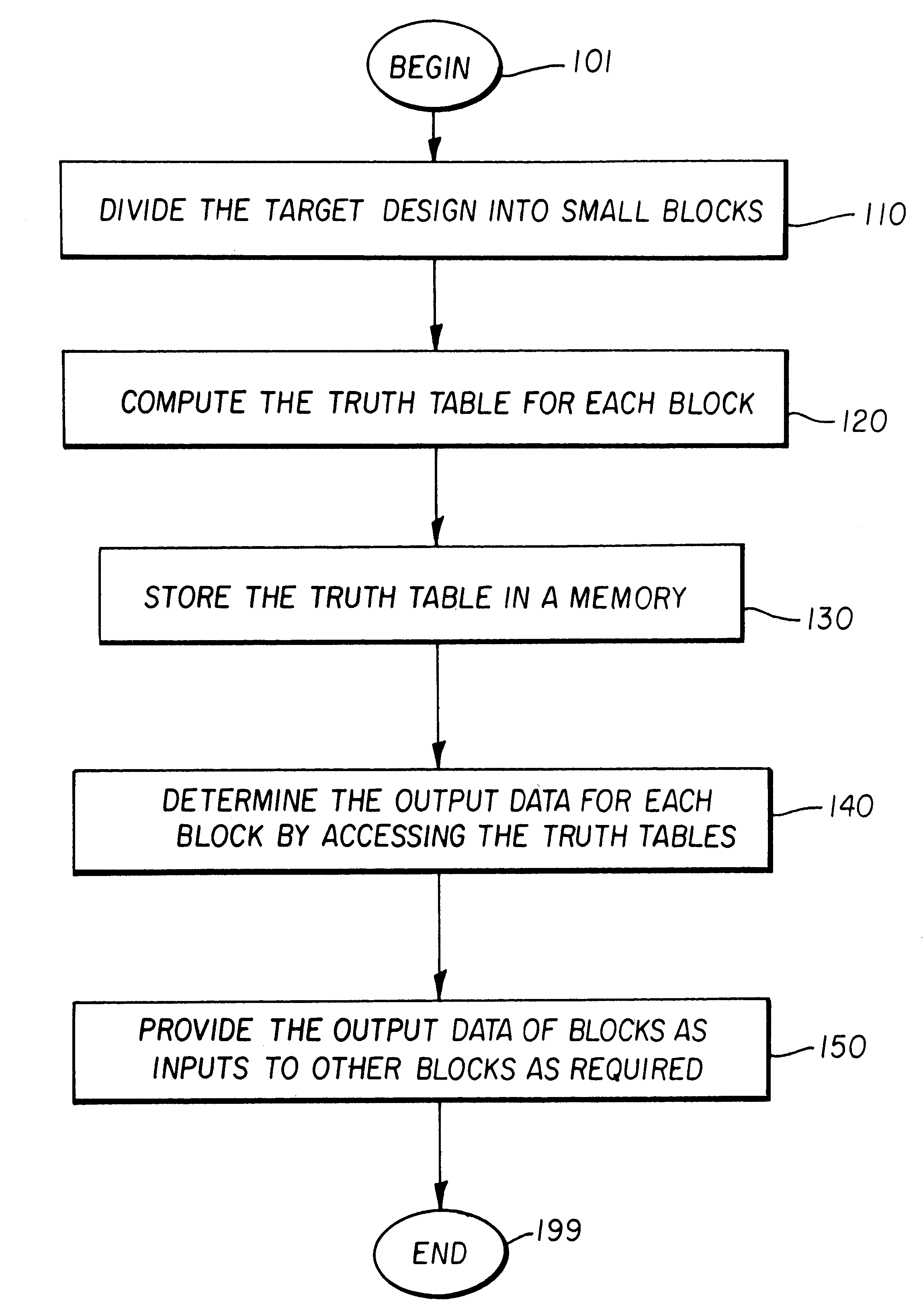
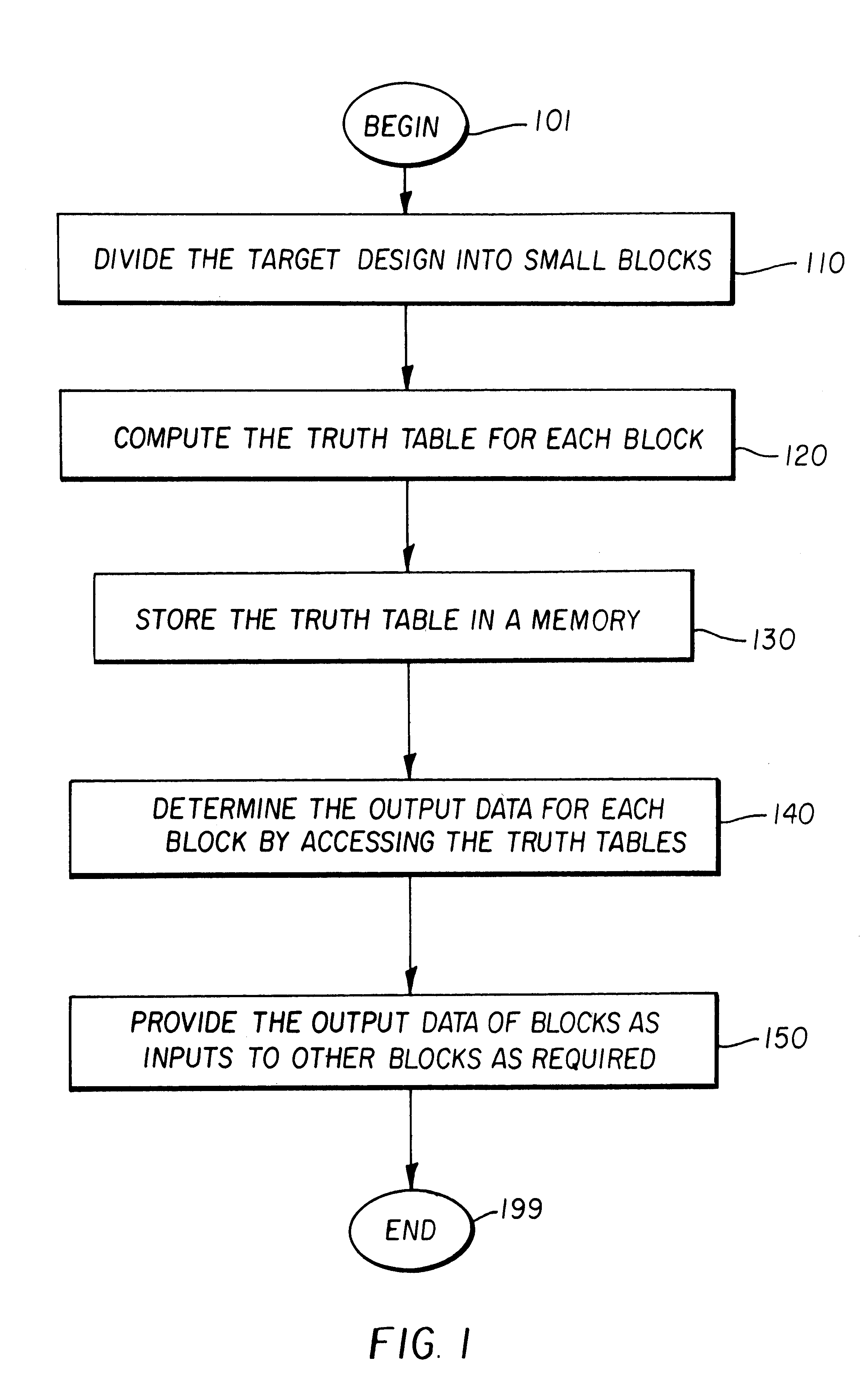
Functional verification system
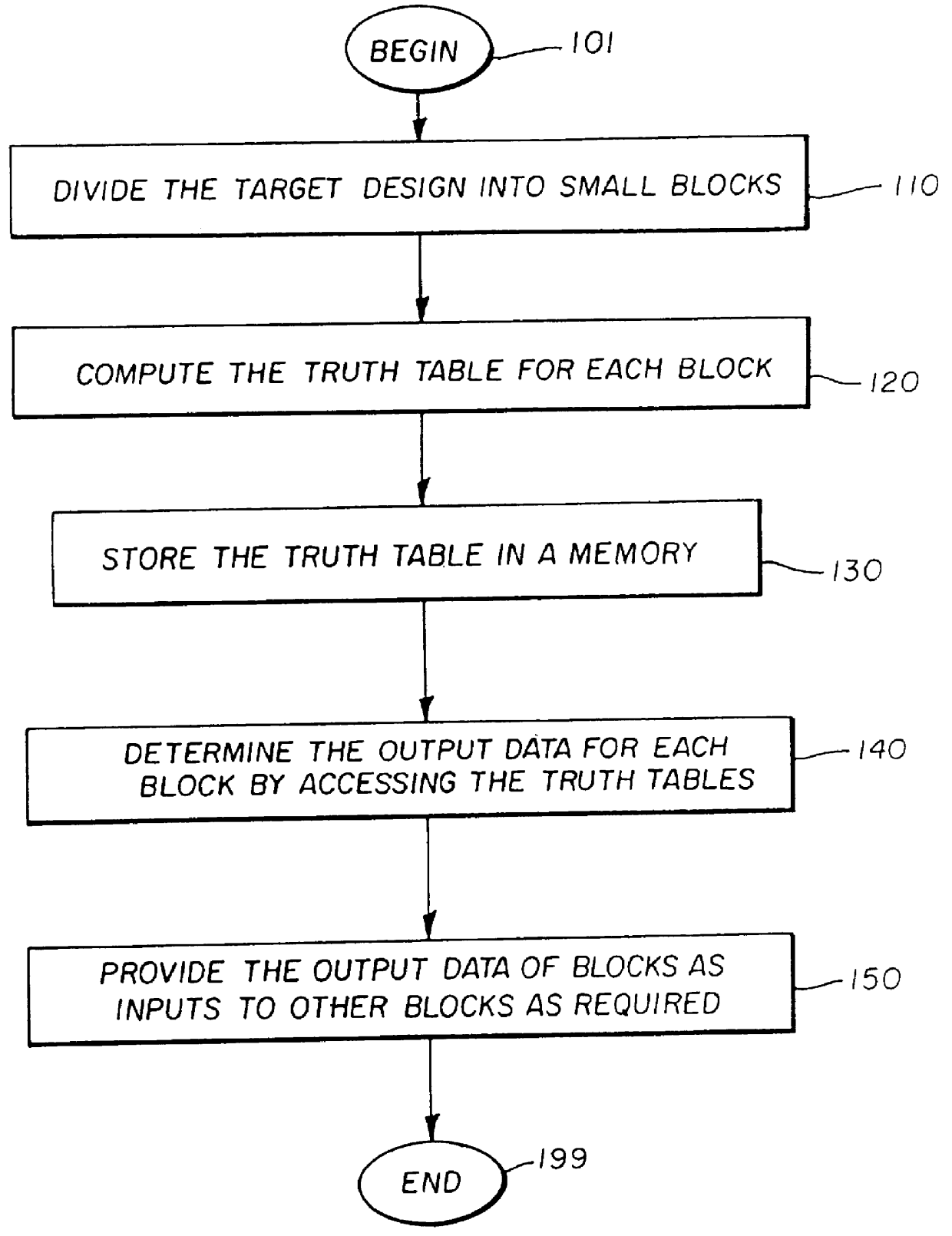
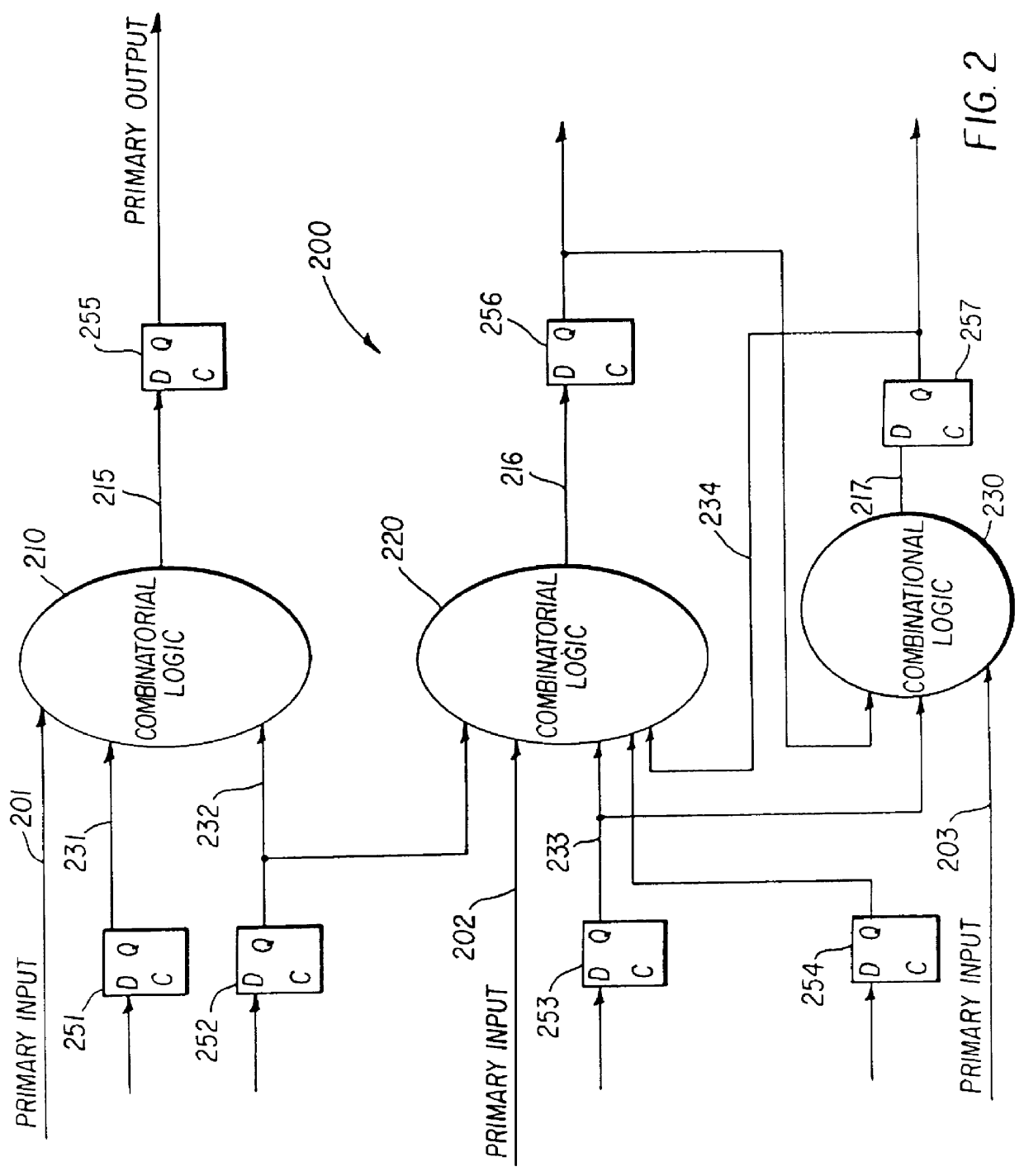
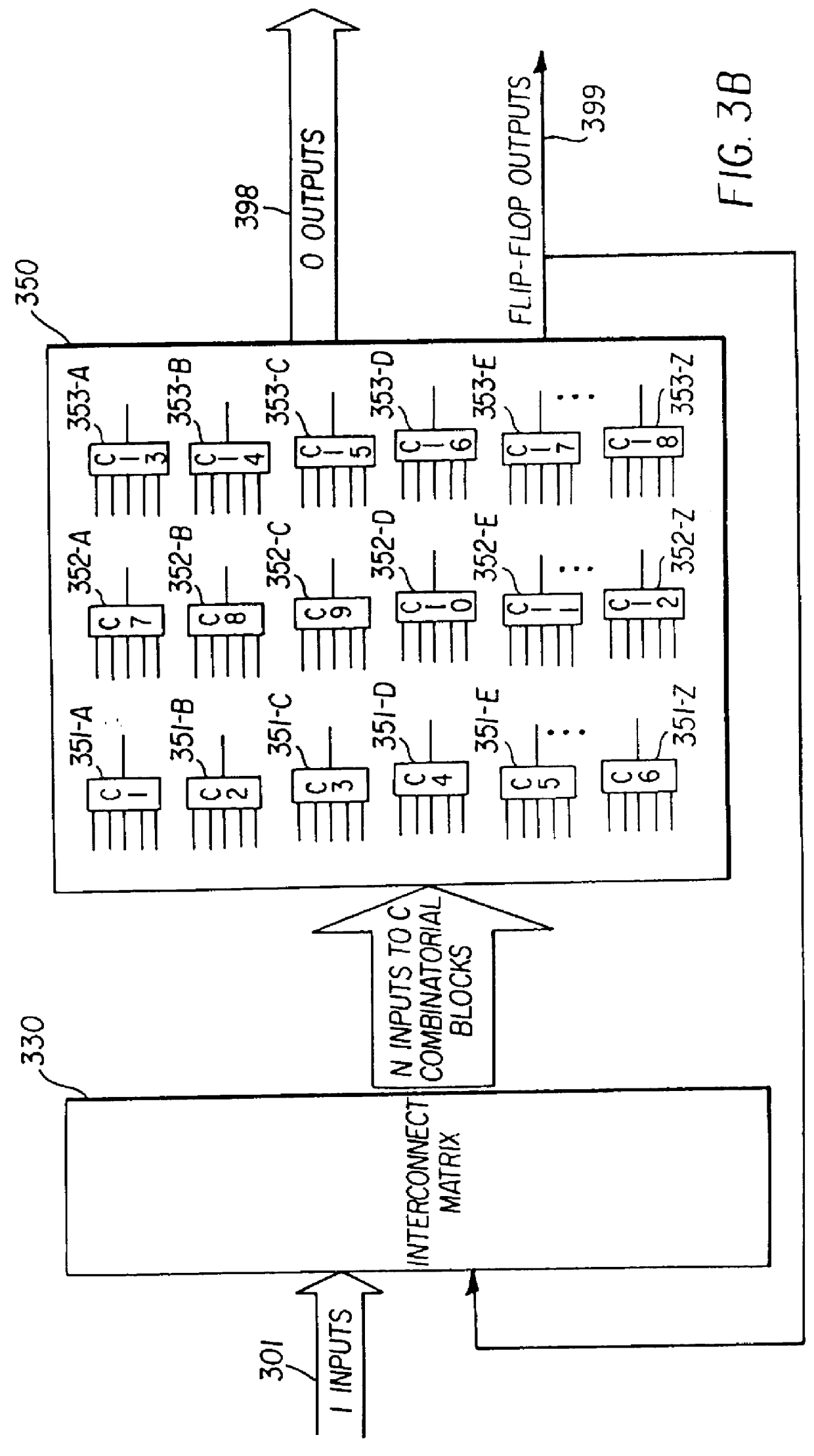
InactiveUS20030041308A1CAD circuit designSoftware simulation/interpretation/emulationStatic random-access memoryComputer architecture
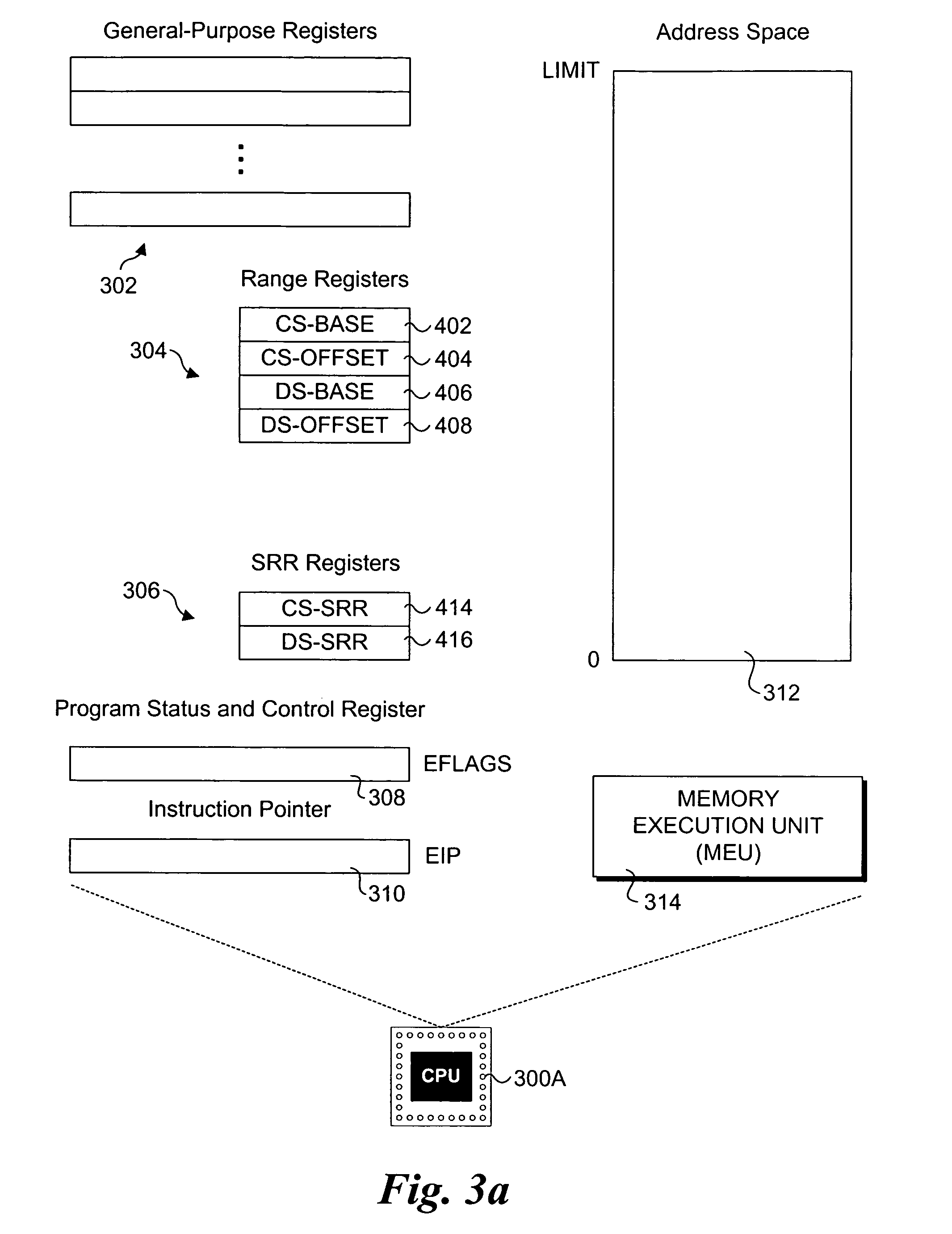
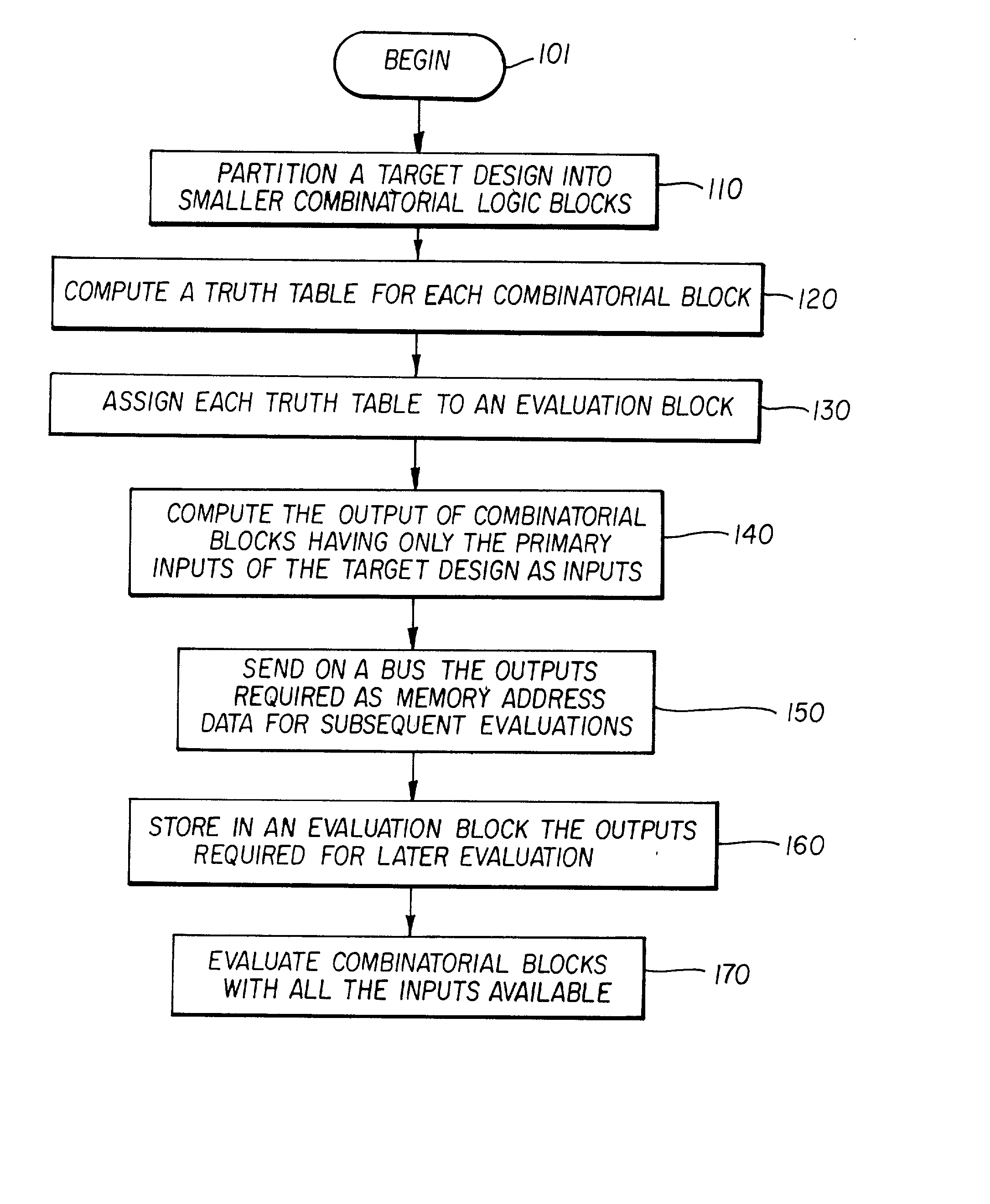
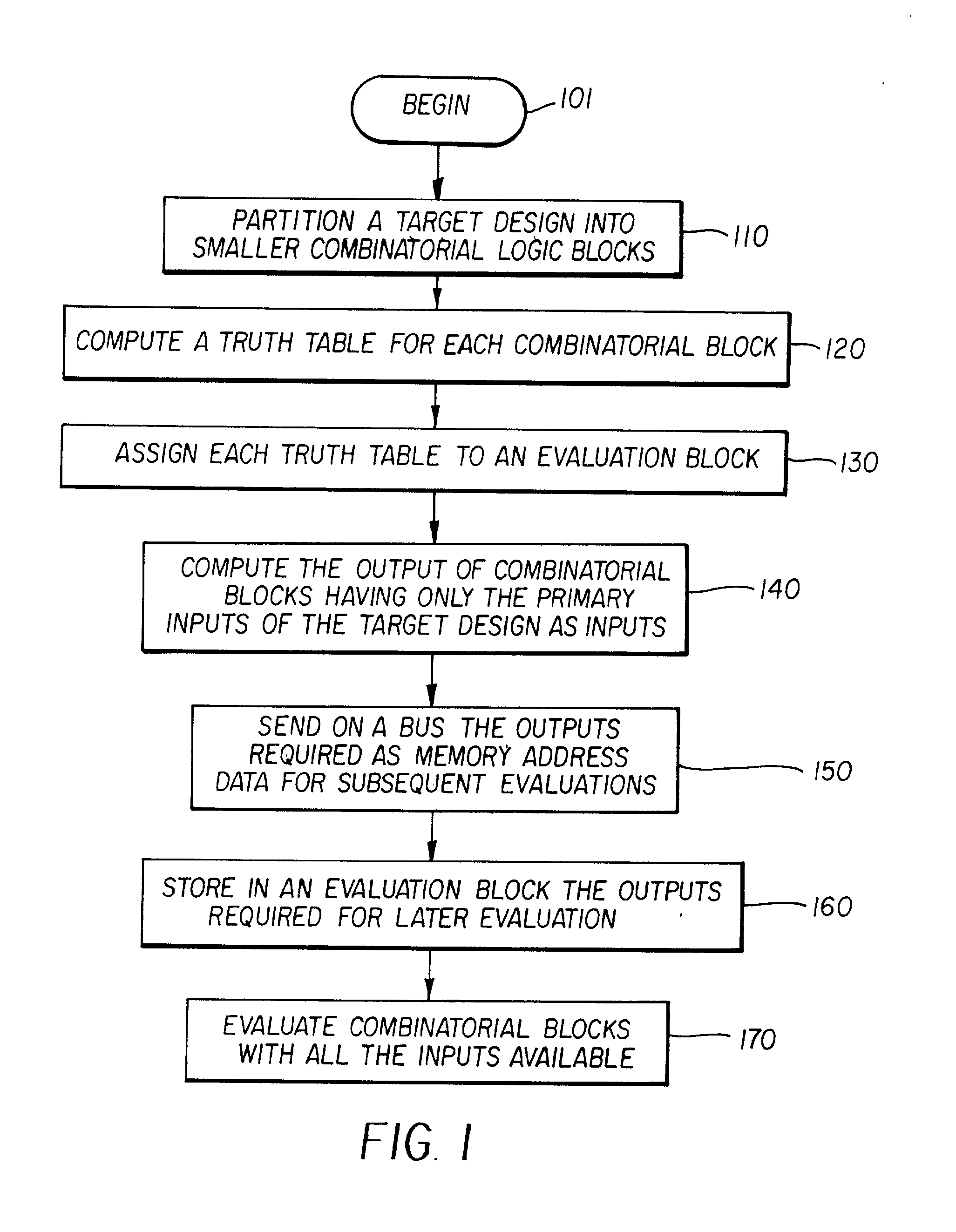
A functional verification system suited for verifying the function of non-cycle based integrated circuits (IC) design. The IC design is divided into a plurality of combinatorial blocks connecting sequential elements. Truth tables corresponding the divided blocks are computed and stored in a memory. The output values of the IC design are determined by evaluating the blocks. The evaluation typically entails one memory access as the truth tables are pre-computed and stored in a memory storage. Accordingly the output values are computed quickly. The storage is implemented using random access memories and a XCON is designed to ensure the dependencies are preserved during the evaluations.
Owner:EVE
Functional verification of integrated circuit designs
InactiveUS6138266AImprove performanceIncrease in sizeElectronic circuit testingCAD circuit designStatic random-access memoryComputer architecture
A functional verification system suited for verifying the function of cycle based integrated circuits (IC) design. The IC design is divided into a plurality of combinatorial blocks connecting sequential elements. Truth tables corresponding the divided blocks are computed and stored in a memory. The output values of the IC design are determined by evaluating the blocks. The evaluation typically entails one memory access as the truth tables are pre-computed and stored in a memory storage. Accordingly the output values are computed quickly. The storage is implemented using random access memories and a XCON is designed to ensure the dependencies are preserved during the evaluations.
Owner:EVE
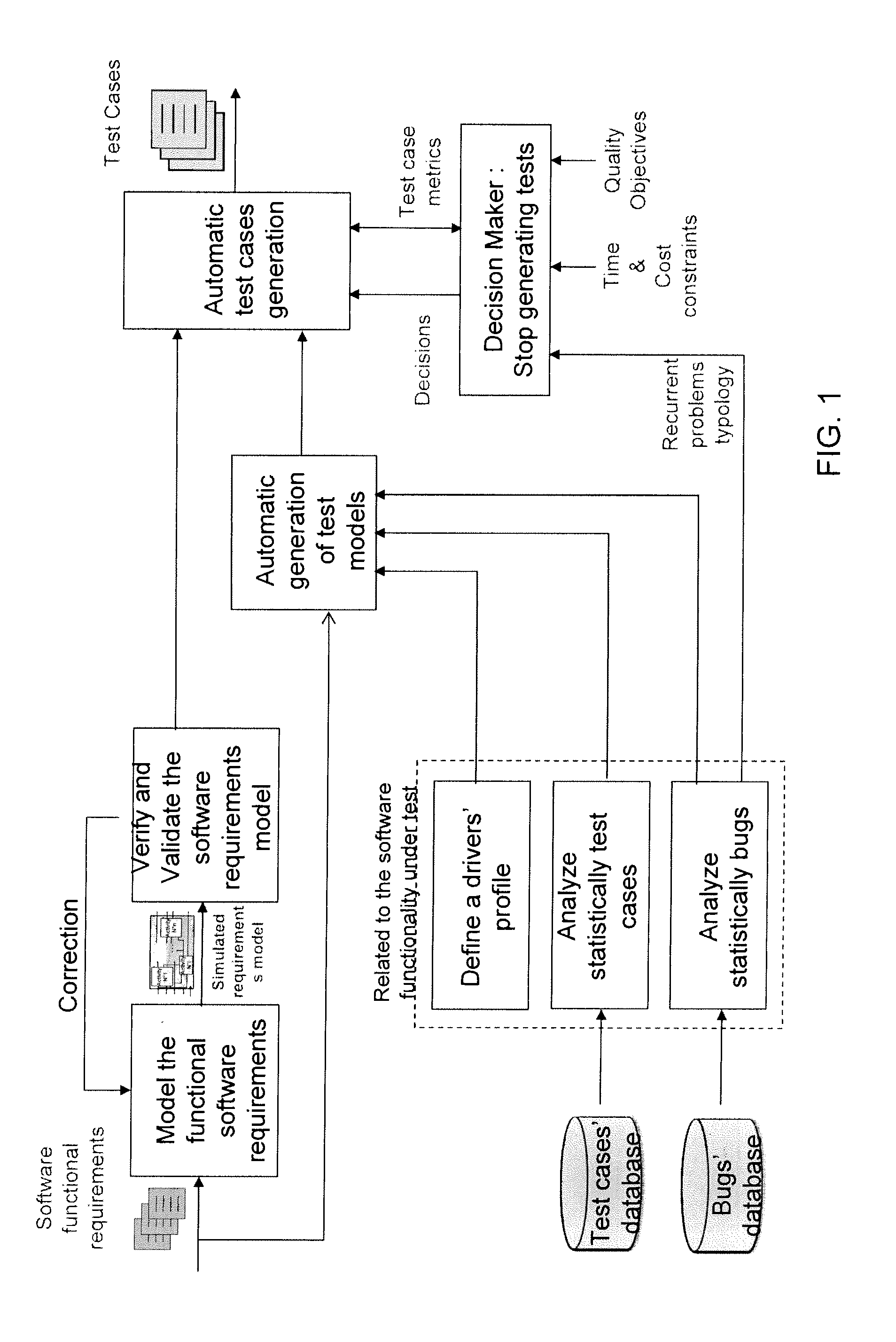
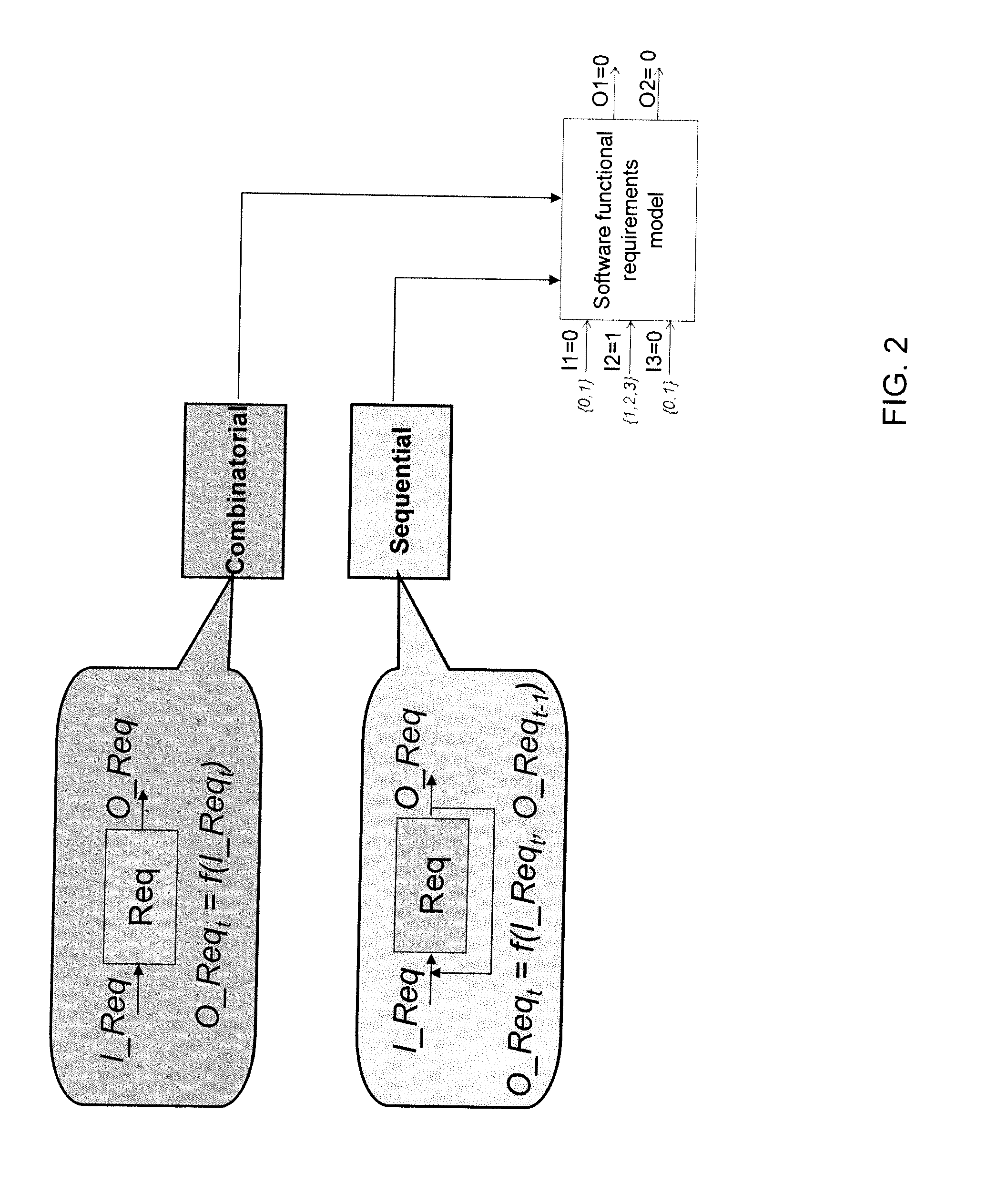
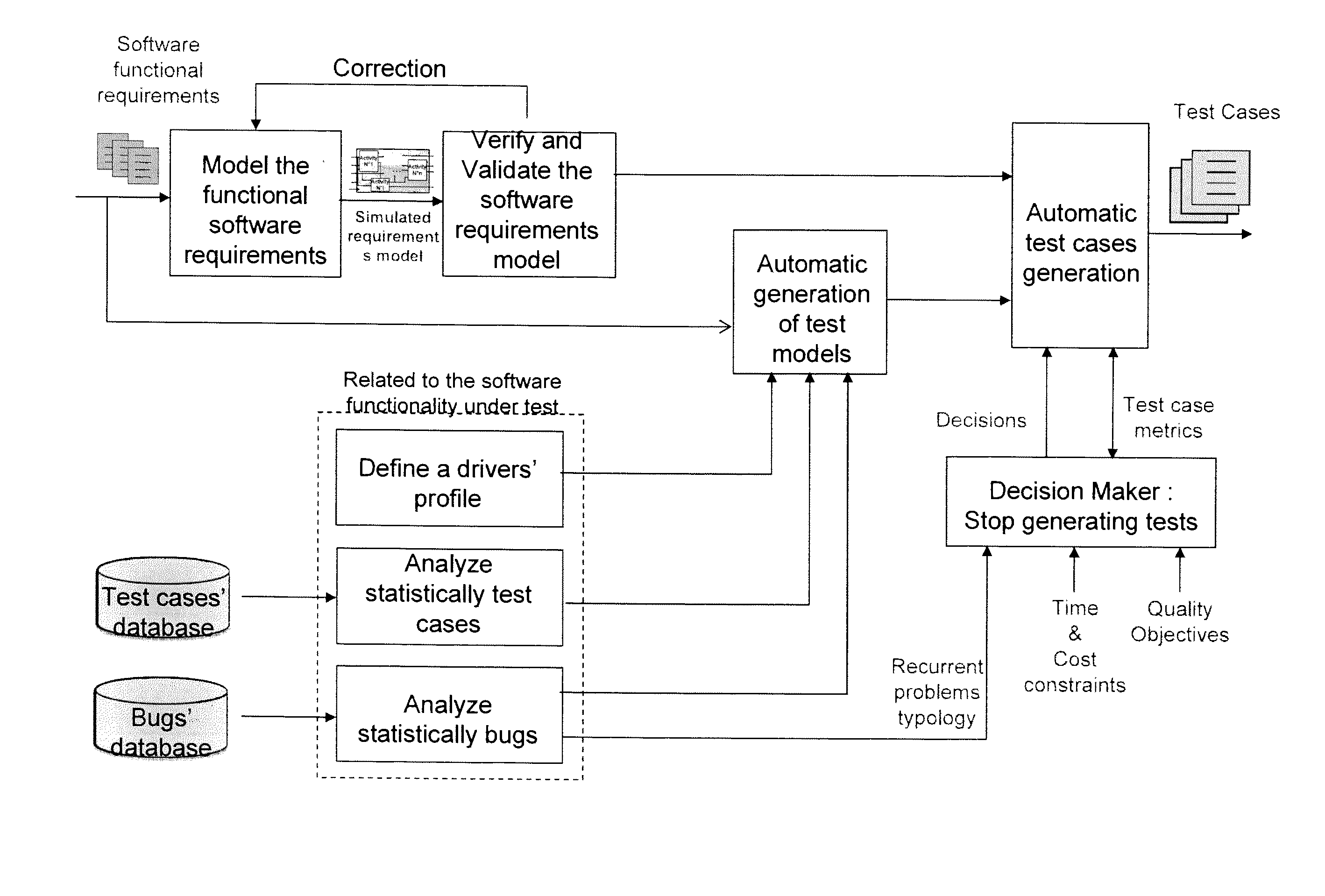
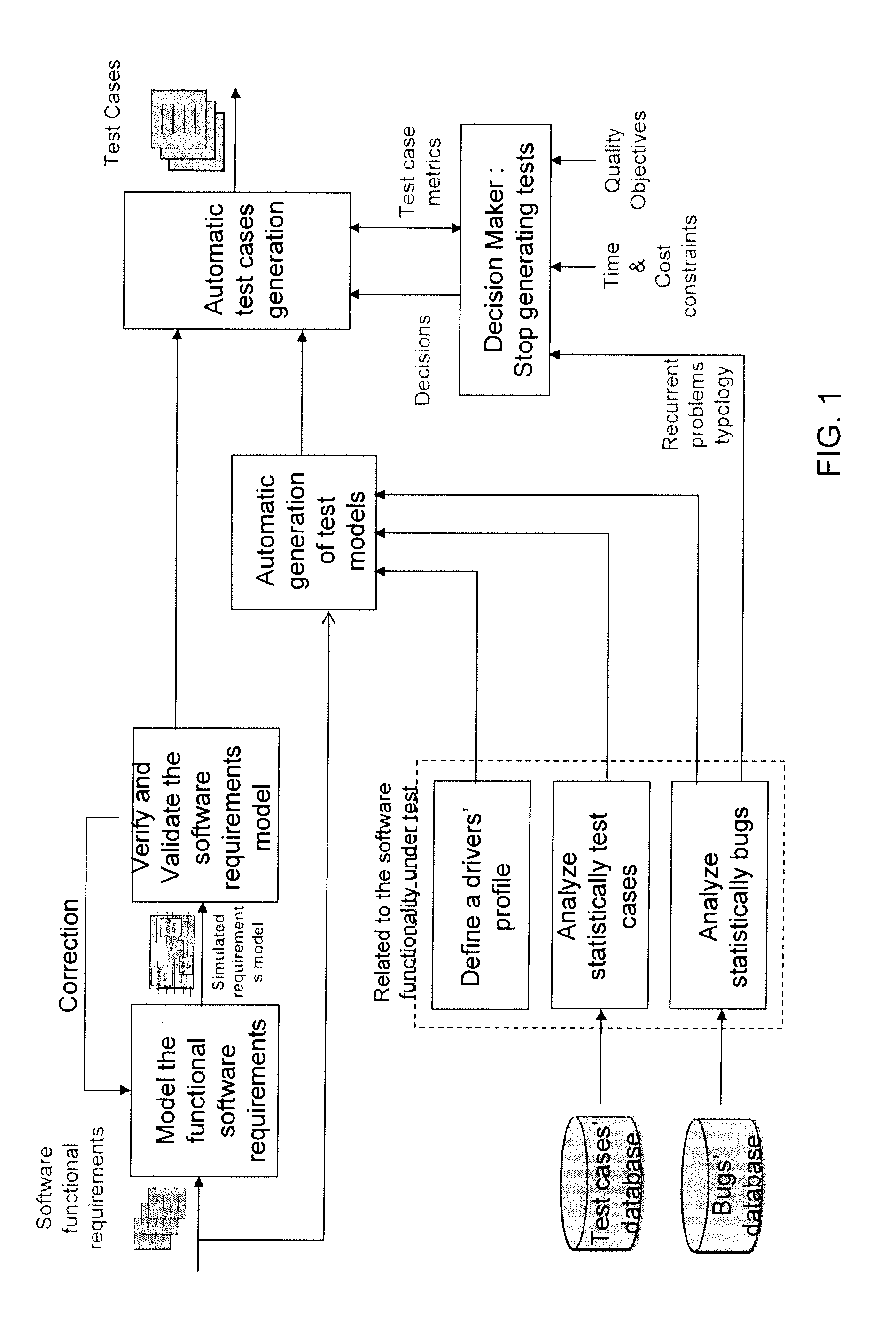
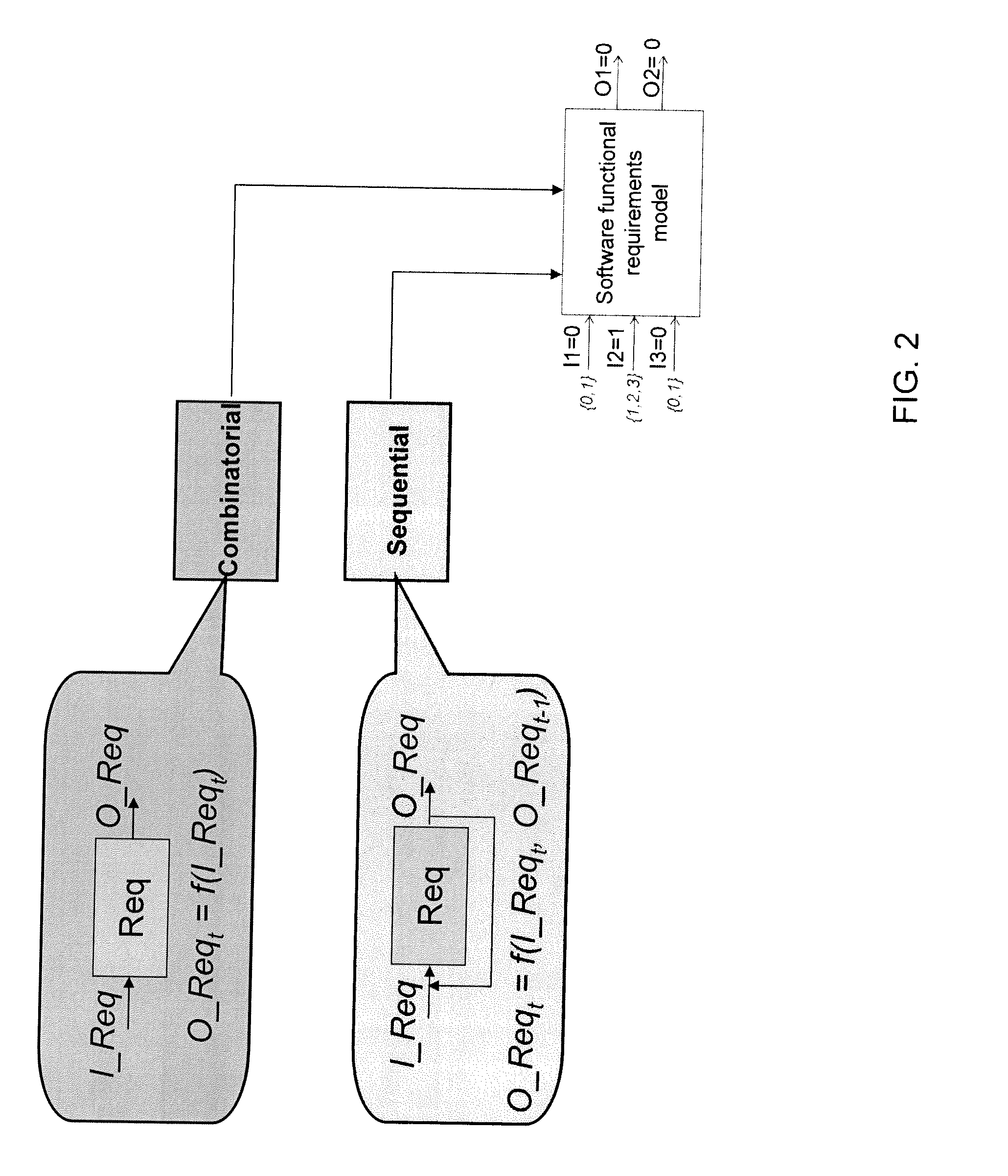
Method of automatically formulating test cases for verifying at least part of a piece of software
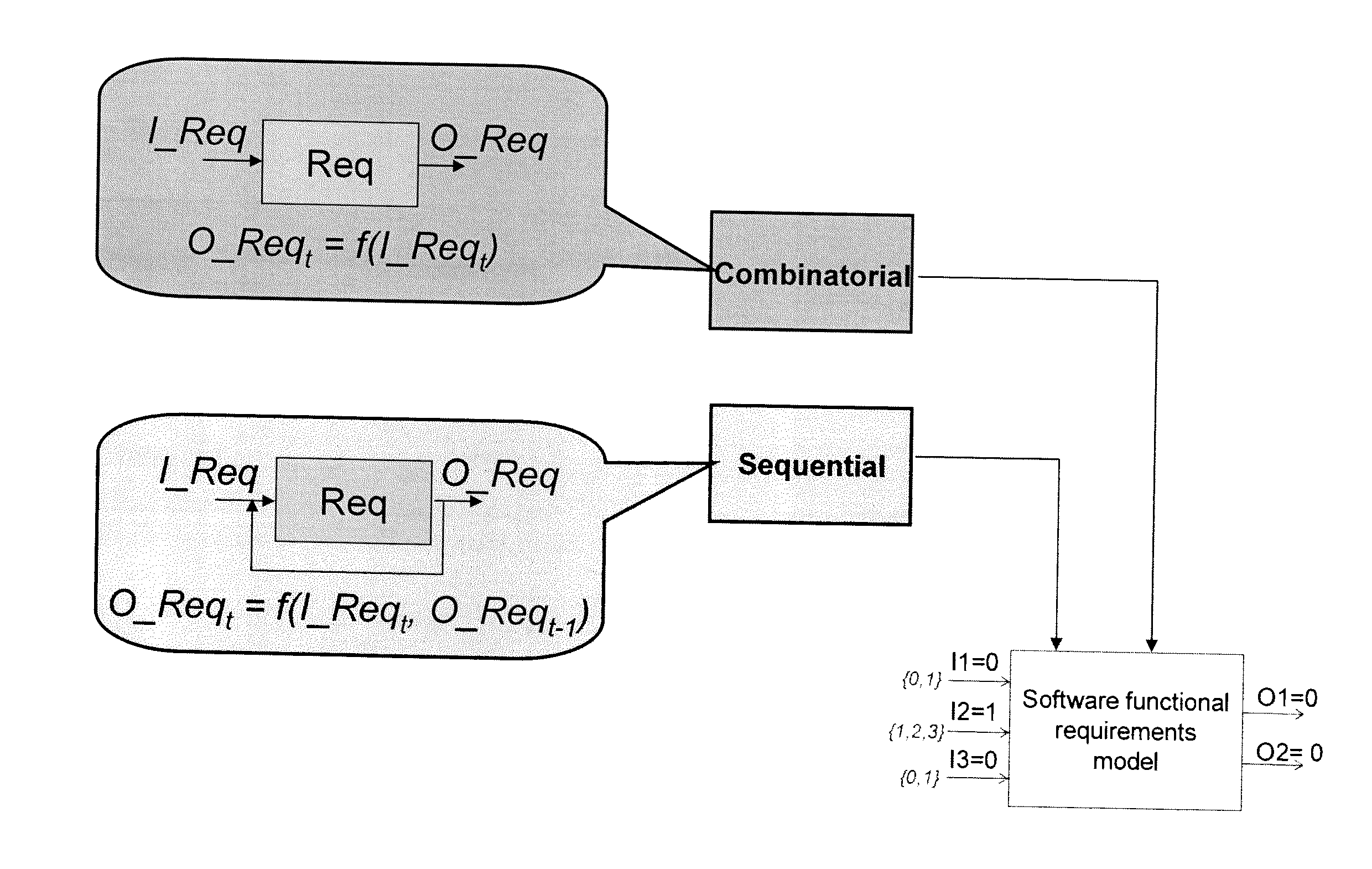
InactiveUS20110184689A1Reliable detectionMinimal interventionError detection/correctionSpecial data processing applicationsTruth valueTheoretical computer science
A method of automatic formulation by a computer of test cases for verifying at least one function of a piece of software in relation to a specification including requirements relating input values and output values of the software, the method including the steps of:distinguishing combinatorial requirements and sequential requirements;modeling combinatorial requirements by a truth table and sequential requirements by a finite state machine to obtain a modeled specification;establishing an operation matrix relating the input values of the software with a probability of them being in succession and a transition time between them;selecting the successions of input values to be tested by performing a Monte Carlo draw on the operation matrix;determining a test case including test rows relating each selected succession with the output values expected given the modeled specification;stopping the determination process when the test case being determined makes it possible to reach a predetermined threshold for at least one of the following criteria: verified percentage of function code, verified percentage of requirements, verification time, and verification cost.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
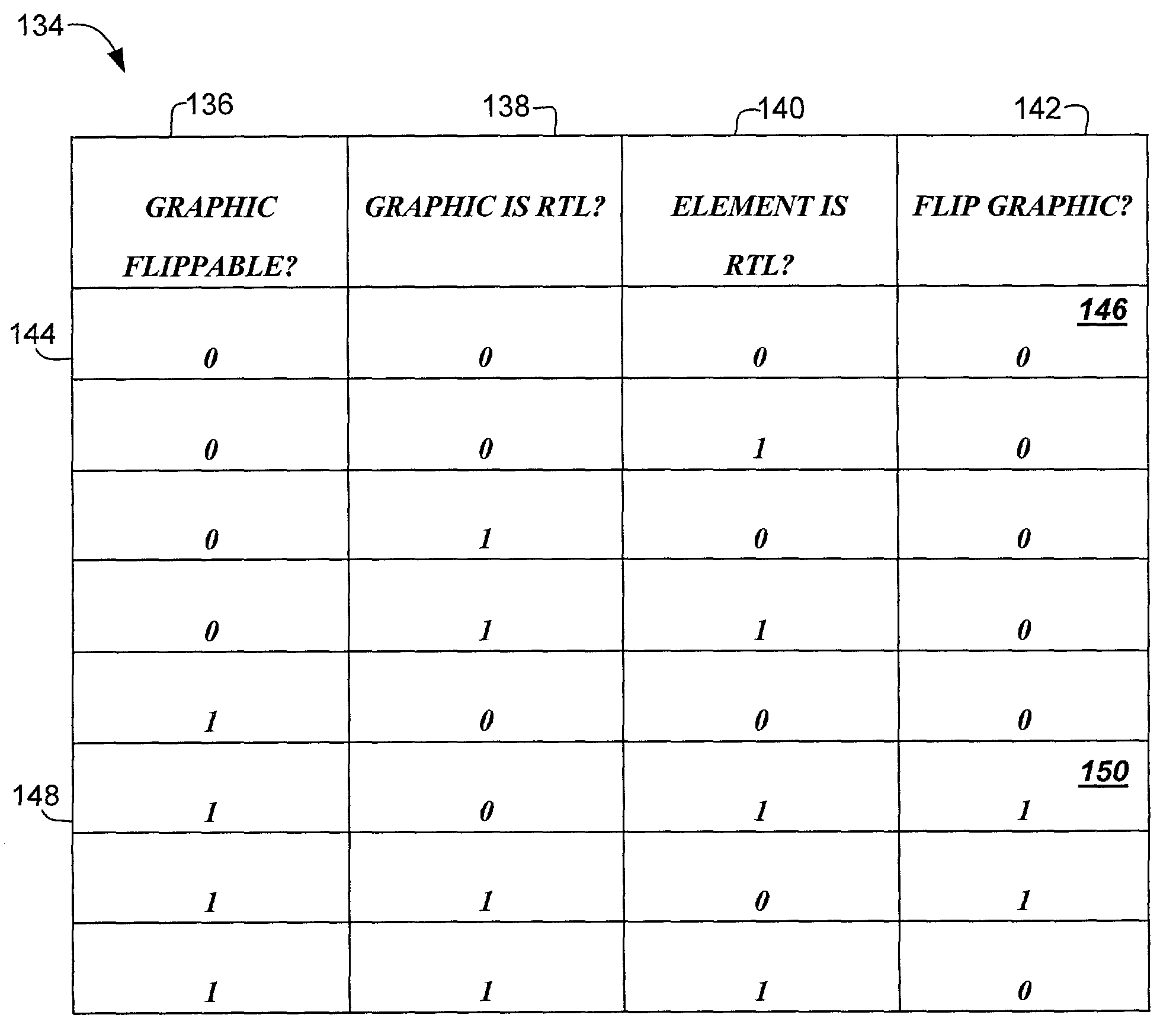
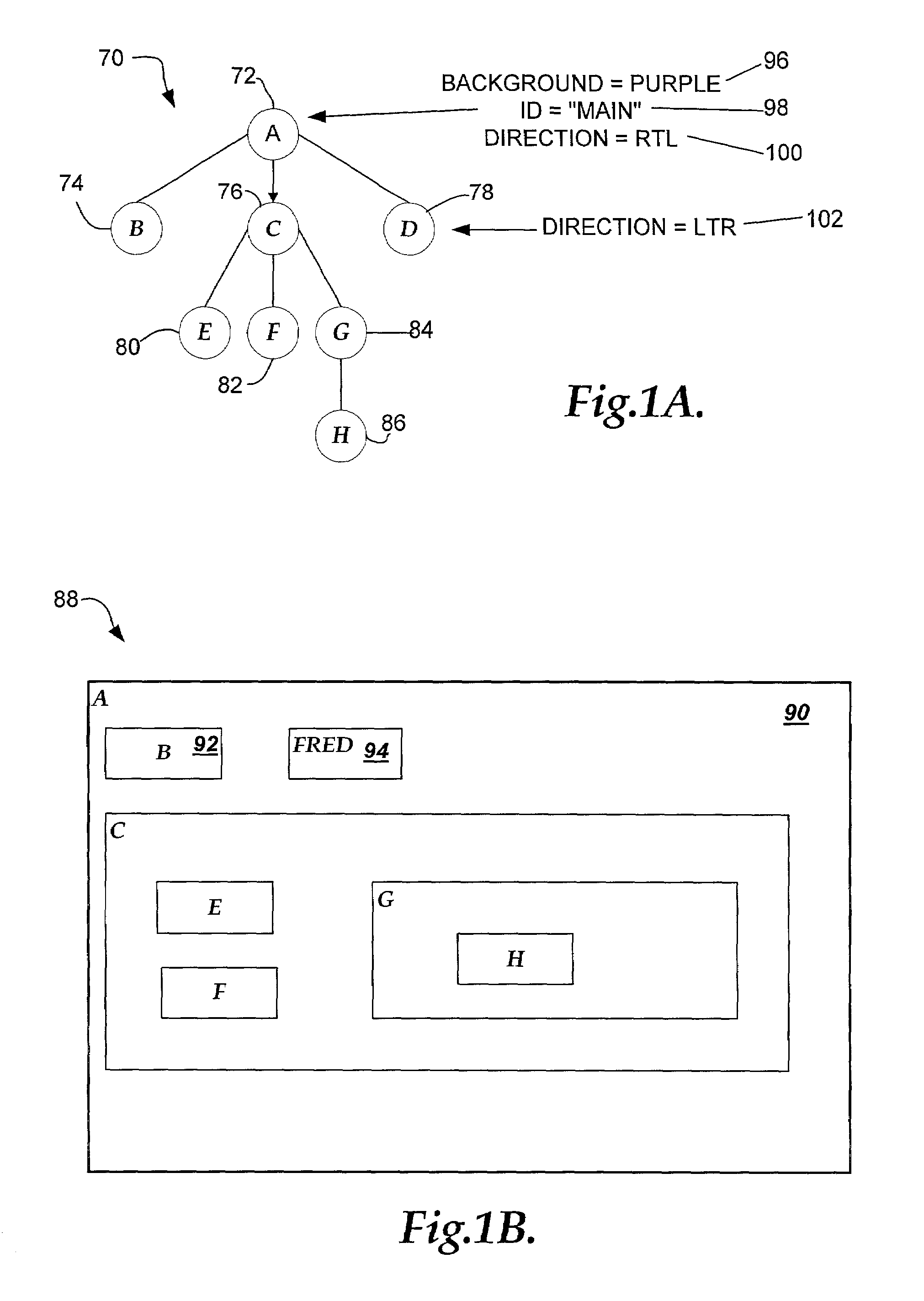
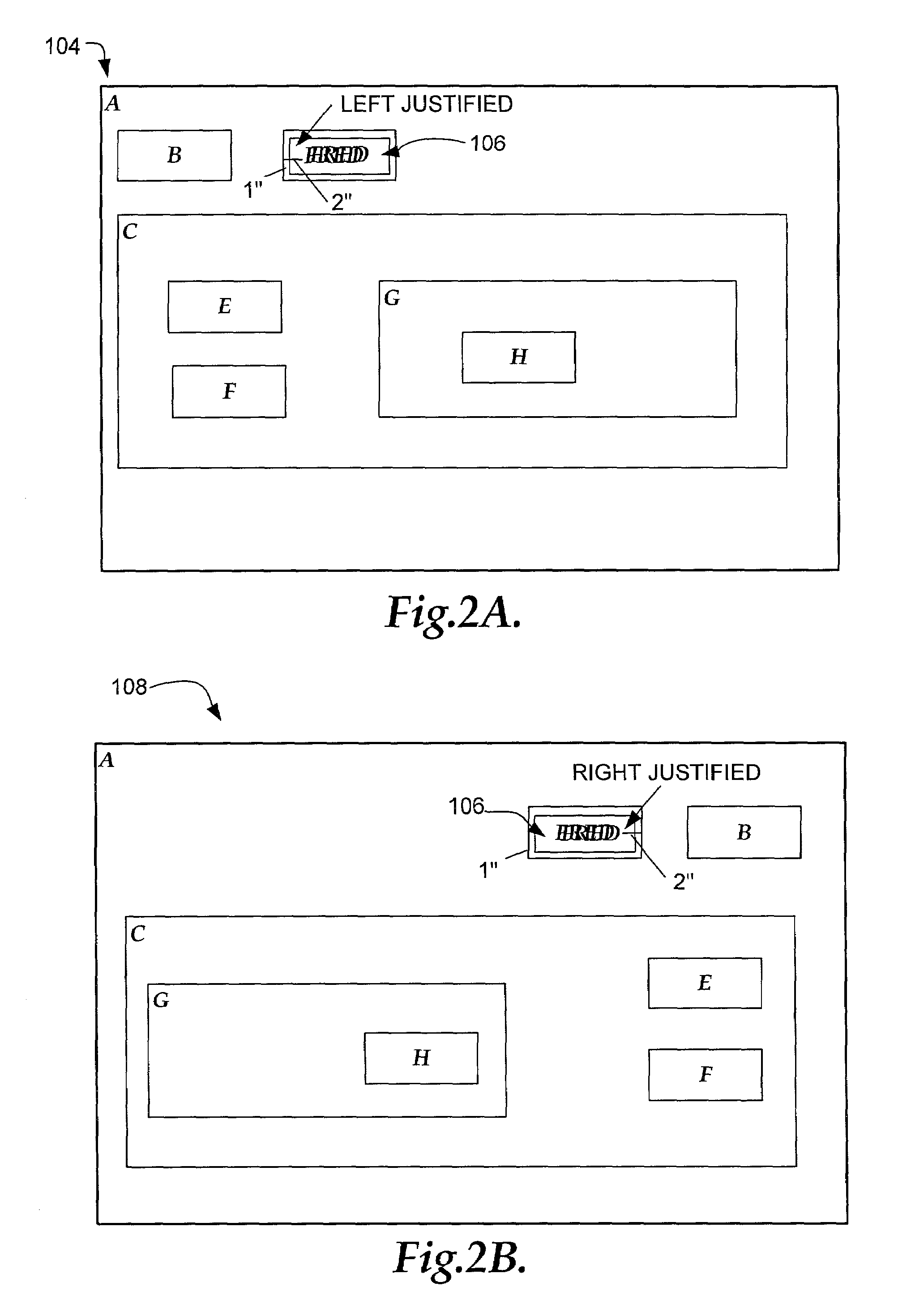
System and method for user interface mirroring utilizing a layout manager
InactiveUS7073137B2Maintain relationshipDigital computer detailsCathode-ray tube indicatorsGraphicsRoot element
A system and method for user interface mirroring are provided. User interface objects are defined according to an object hierarchy that defines a logical relationship between a root element and one or more child elements. Additionally, the root element includes a directional property that is inherited by the child elements. A layout manager obtains the logical relationship and the specified directional property and correlates a set of physical coordinates for each display object according to the directional property, while maintaining the logical relationship. A renderer renders each of the display objects according to the specified directional property, while maintaining a truth table for graphical resources that could be rendered in one or more directions.
Owner:MICROSOFT TECH LICENSING LLC
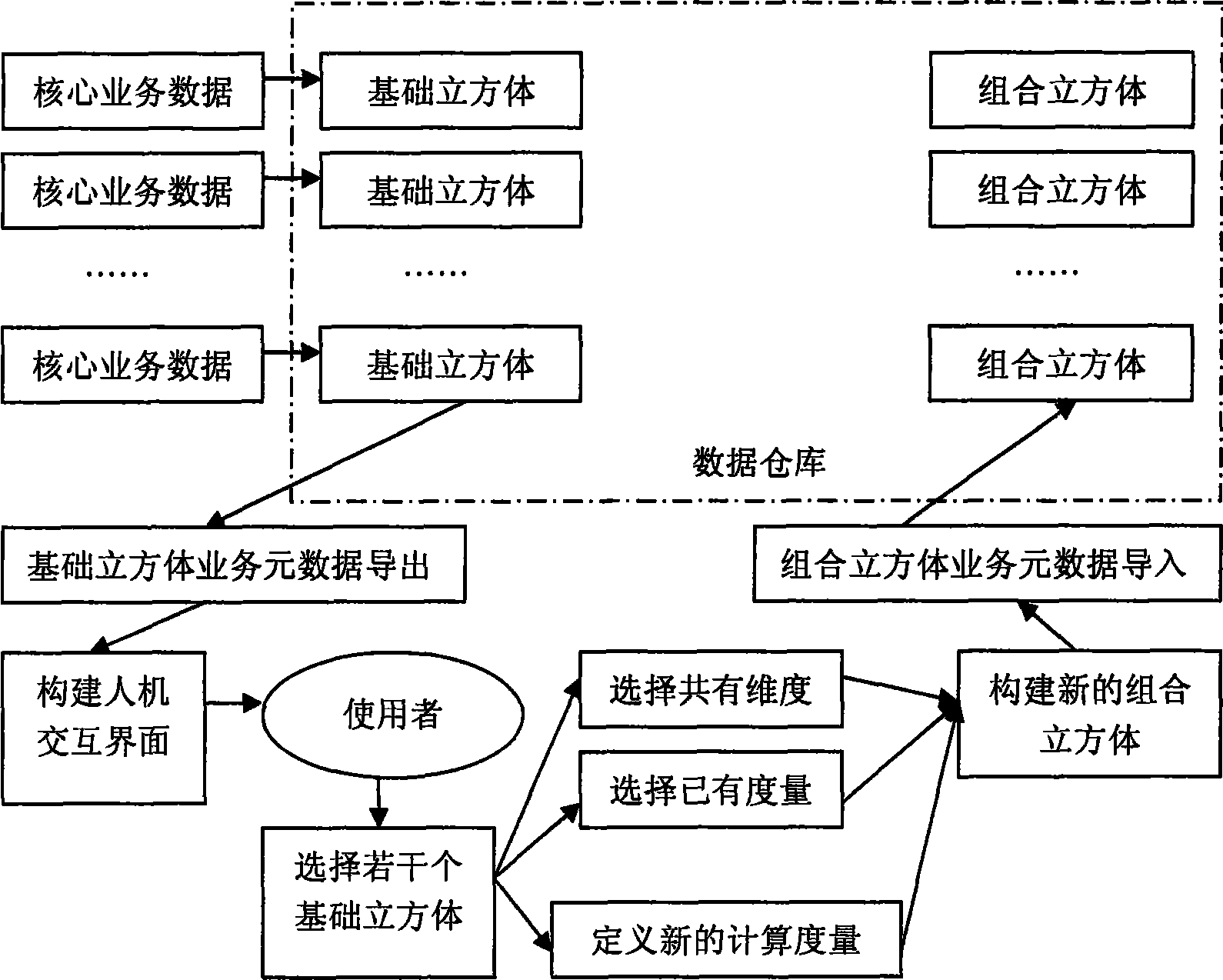
Method for quick-speed realizing data store house process based on metadata
InactiveCN101178732AReduce construction difficultyShort construction periodSpecial data processing applicationsData warehouseDatabase application
The invention discloses a method that is based on a metadata and can quickly realize the database procedure. The invention parses and lists containing tolerance and dimensionality to existing one group of basic cube model in the database; users combine the basic cube with common dimensionality and utilize prior tolerance to create new counting tolerance according to the requirements; the invention leads the definition in the database to form the combining cube model; the invention proceeds the related combination to the truth database corresponding to the basic cube as the out keys corresponding to the common dimensionality according to the combining cube definition information confirmed by the users and form the new truth table or view as the data supporting to the cube combination. By adopting the invention, users can freely create multidimensional analysis model during the using procedure rather than the developers design and fulfill beforehand, thereby greatly enhancing the applying ability of the database application to the operation analyzing requirement and accelerating the database procedure.
Owner:JIANGSU ELECTRIC POWER CO
Functional verification of integrated circuit designs
InactiveUS6629296B1Improve performanceIncrease in sizeElectronic circuit testingCAD circuit designStatic random-access memoryComputer architecture
A functional verification system suited for verifying the function of cycle based integrated circuits (IC) design. The IC design is divided into a plurality of combinatorial blocks connecting sequential elements. Truth tables corresponding to the divided blocks are computed and stored in a memory. The output values of the IC design are determined by evaluating the blocks. The evaluation typically entails one memory access as the truth tables are pre-computed and stored in a memory storage. Accordingly the output values are computed quickly. The storage is implemented using random access memories and a XCON is designed to ensure the dependencies are preserved during the evaluations.
Owner:EVE
Database query optimization apparatus and method
InactiveUS20030100960A1Easy constructionEasy to operateData processing applicationsDigital data information retrievalDatabase queryTruth value
A database query optimizer processes an expression in a database query, and generates therefrom an operand list and a corresponding truth table that may be represented by a list of binary characters, where the operand list and corresponding truth table represent a disjunct normal form for the expression. Each expression is stored once it is processed into its operand list and corresponding list of binary characters. New queries are processed into component expressions, and each expression is checked to see if the expression was previously processed and stored as a processed expression. If so, the operand list and list of binary characters for the previously-stored expression may be used in processing the current expression. If there is no previously-stored expression that corresponds to the current expression, the previously-stored expressions are checked to see if any correspond to a complement of the current expression. If so, a new expression is easily constructed for the current expression by retrieving the list of binary characters that correspond to the complement expression, and inverting the bits in the list of binary characters. If there is no previously-stored expression that corresponds to the current expression or its complement, an operand list and corresponding list of binary characters are generated for the current expression. Logical operations between predicates in a query may be performed by performing mathematical operations on the lists of binary characters corresponding to each predicate expression. The end result is an operand list and corresponding list of binary characters that represents the entire expression in a query.
Owner:IBM CORP
Method for monitoring fuse burning yield rate in chip test
ActiveCN105470159ATimely detection of abnormalities in yield rateAvoid irreversible lossSemiconductor/solid-state device testing/measurementTruth valueTruth table
The invention provides a method for monitoring the fuse burning yield rate in chip test, comprising the following steps: S1, a fuse truth table is established, wherein the fuse truth table contains the corresponding relation between the reference voltage measured value ranges of chips and fuses needing to be burnt out; S2, a chip is tested, and the reference voltage measured value of the chip is monitored; S3, the reference voltage measured value falls into a specific reference voltage measured value range, the chip is qualified if the reference voltage measured value falls into a reference voltage target range to which the reference voltage standard value belongs, and the chip fuses corresponding to the specific reference voltage measured value range are burnt out according to the corresponding relation between the reference voltage measured value ranges and the fuses needing to be burnt out in the fuse truth table if the reference voltage measured value is beyond the reference voltage target range; and S4, the fuses are burnt again if the fuses are not burnt out. By using the method of the invention, the fuse burning adjustment process in chip test can be monitored in real time.
Owner:WUXI ZHONGWEI TENGXIN ELECTRONICS
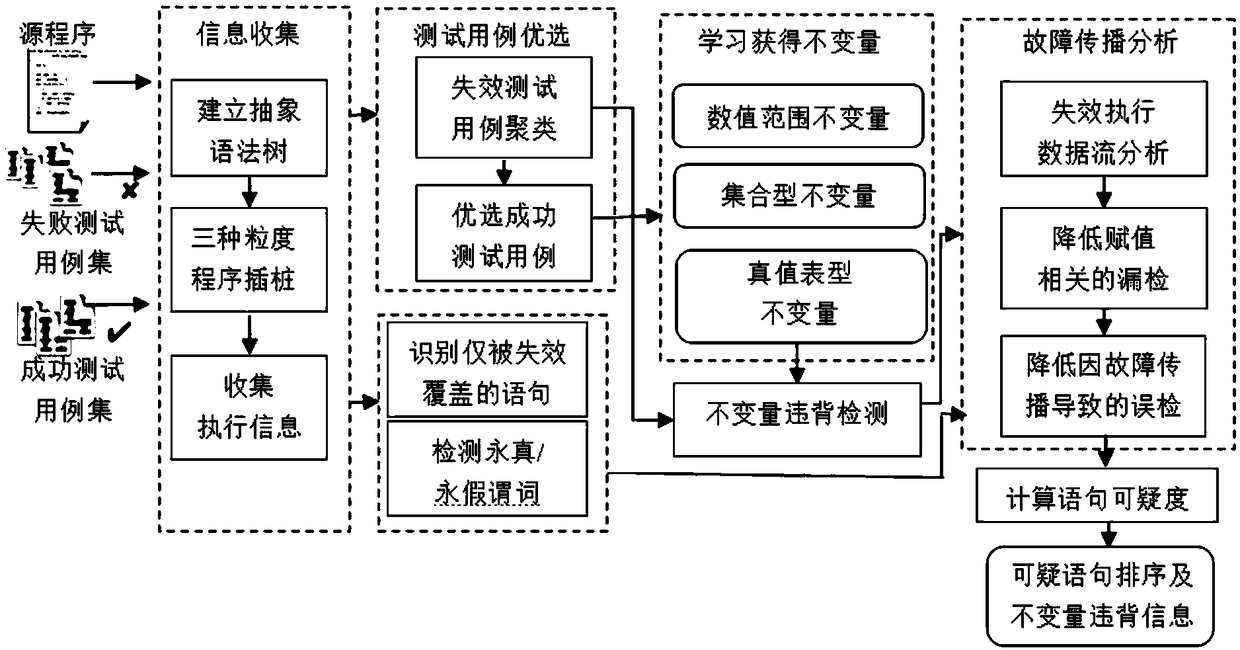
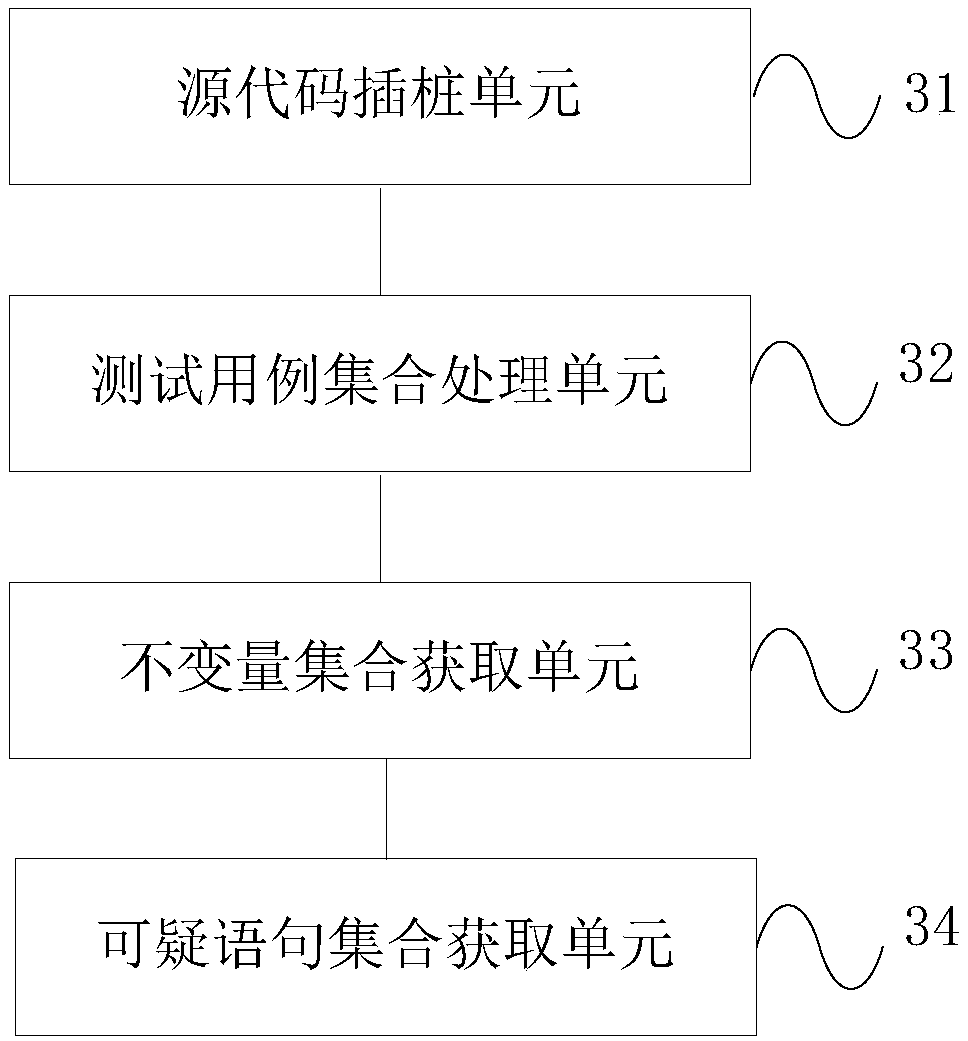
A method and apparatus for software fault location based on program invariants
ActiveCN109144882AImprove accuracyOvercome the problem of missing detection of logical expression defect locationSoftware testing/debuggingTruth valueSoftware fault
The invention discloses a software fault locating method and a device of program invariant. The method comprises the following steps that: the source code of the target software is inserted at the level of sentence, value and logical expression, and the source code after insertion is executed by a preset test case set to obtain the execution information; the source code of the target software is inserted at the level of sentence, value and logical expression; the preset failure test case set is clustered and the successful test case set is selected which is helpful to distinguish the defectivestatements for each clustering; the execution information of the preferred successful test case set is learnt, the program invariant set is obtained, including the set type, truth table type and floating point type range invariant; according to the execution information of the failed test case set and the program invariant set, the invariant violation is detected, and the suspicious statement setis obtained; dependency analysis is used to filter out invariant violation error caused by fault propagation, and invariant violation at each sentence is statistically analyzed to calculate sentencesuspicion. The invention improves the accuracy of software fault location, and overcomes the problem of missing detection of logical expression defect location.
Owner:HARBIN INST OF TECH
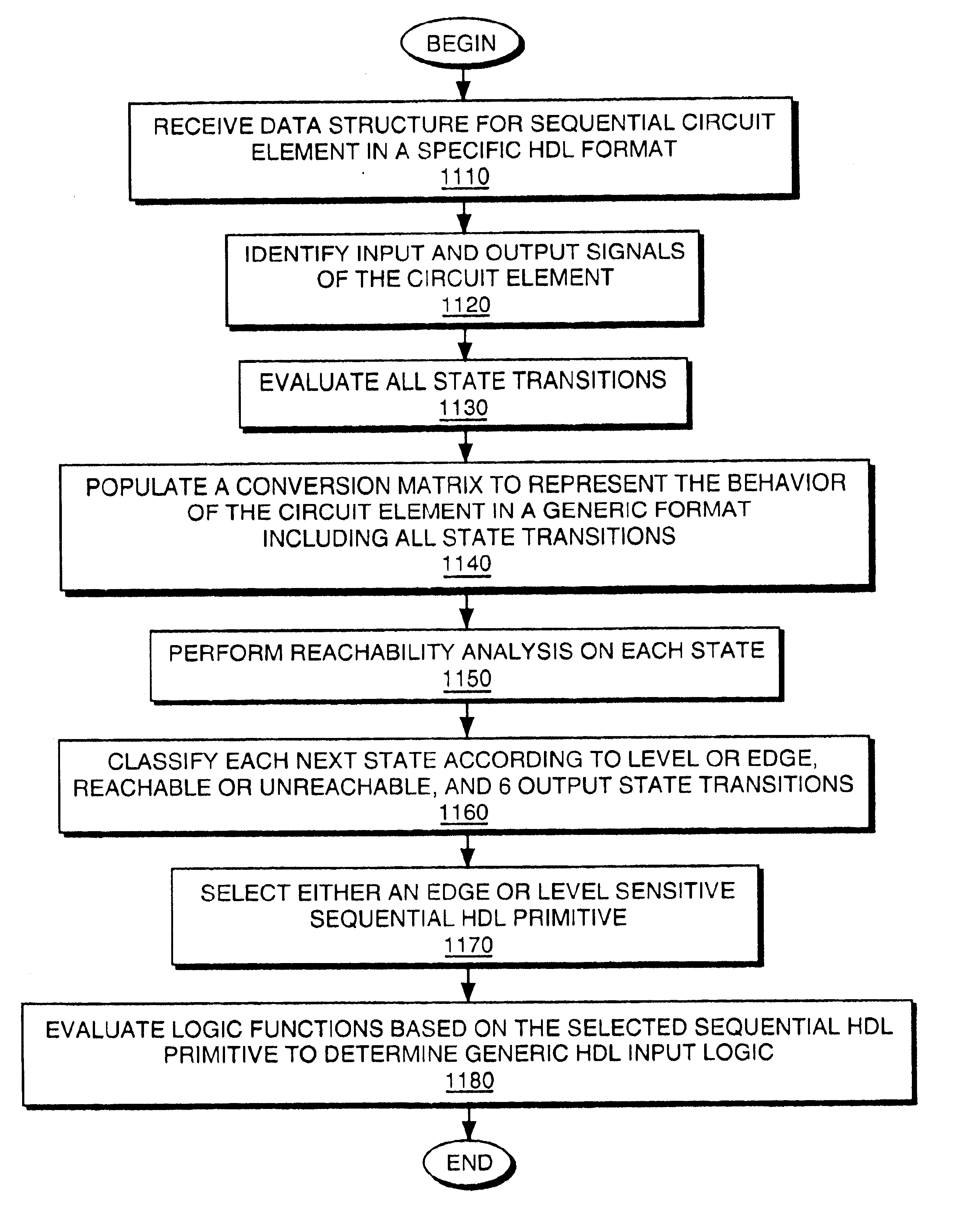
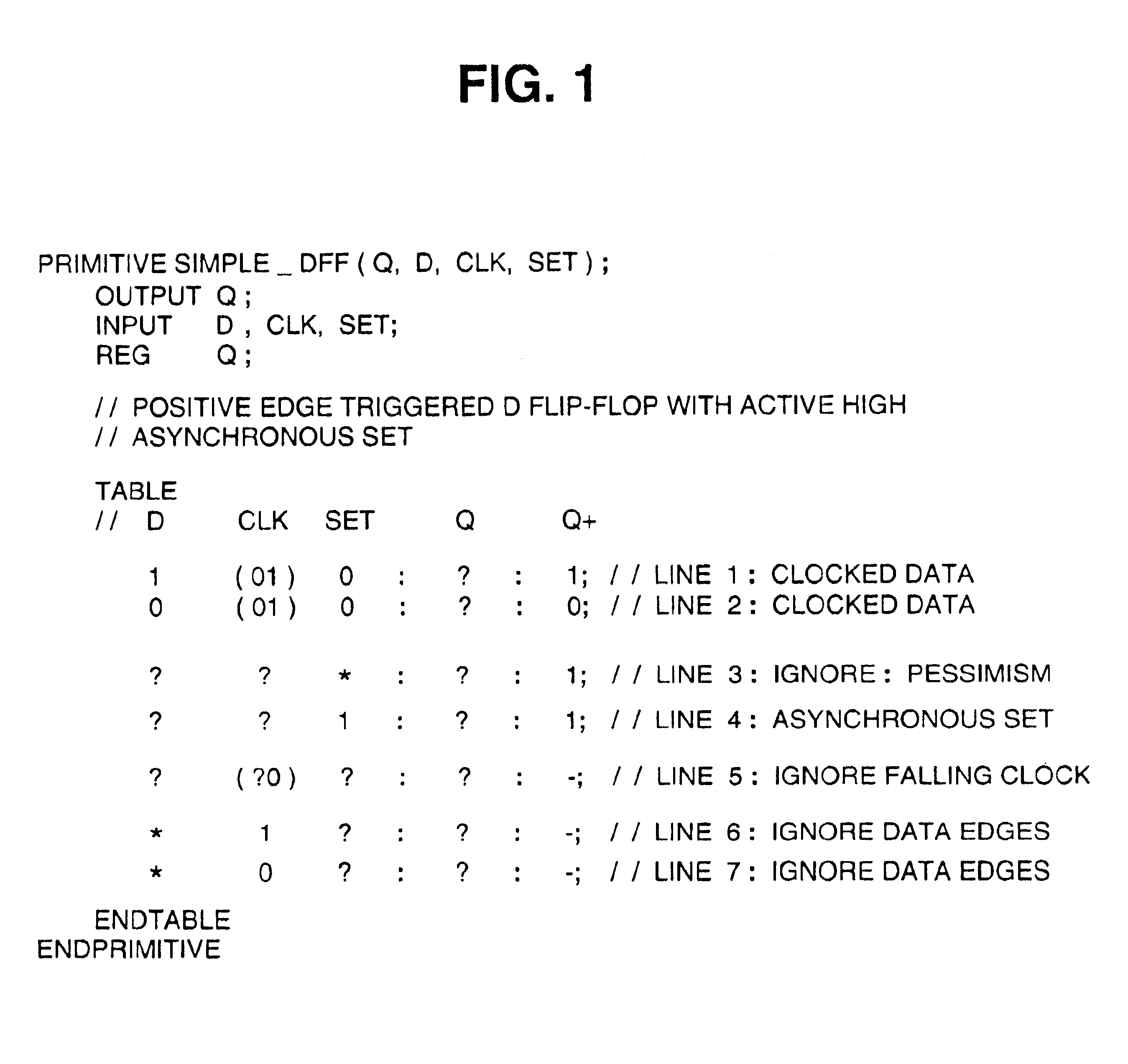
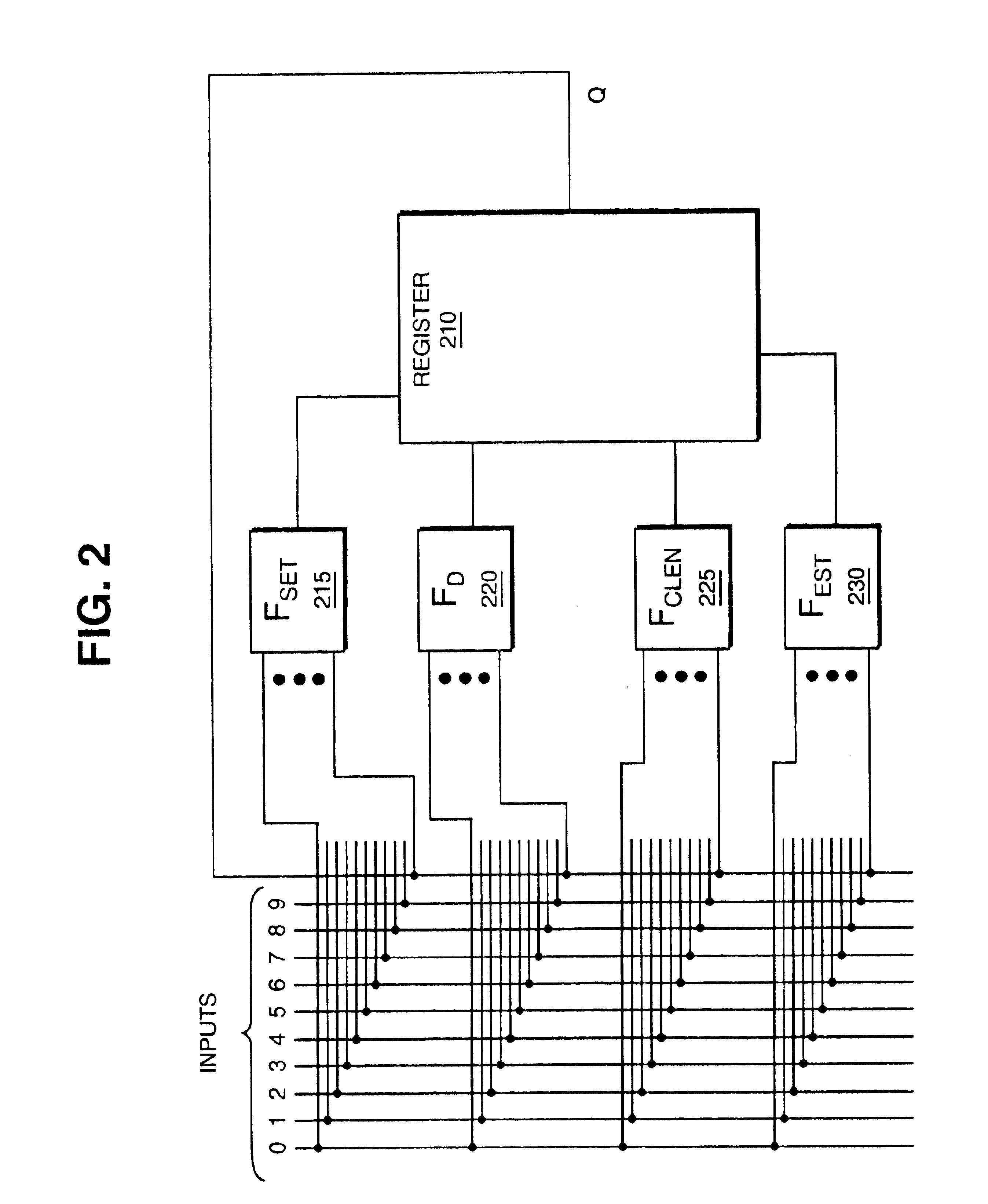
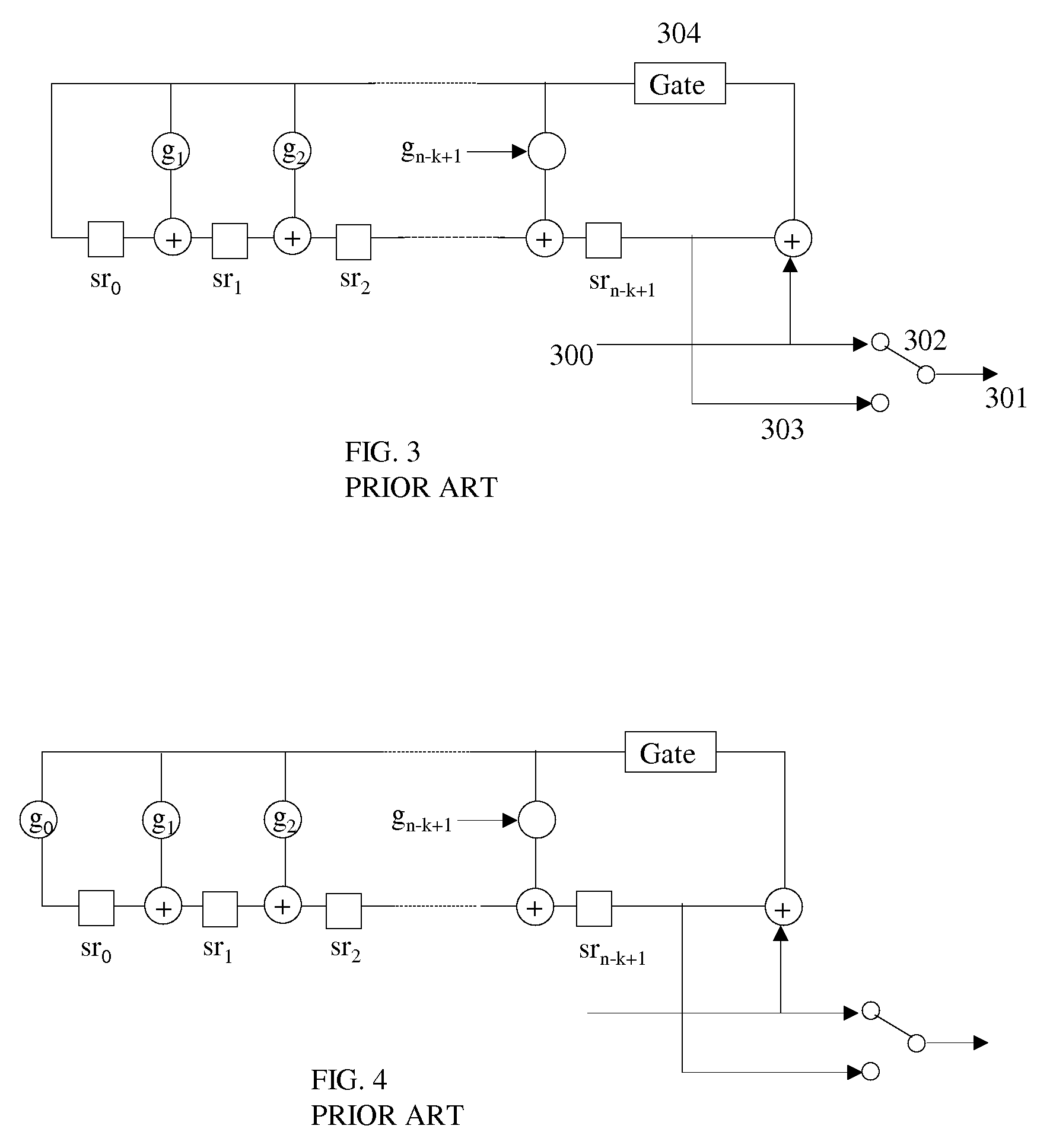
Conversion of an HDL sequential truth table to generic HDL elements
An HDL conversion process receives a data structure representing the behavior of a circuit element. The circuit element is sequential and the data structure is defined in a hardware description language (HDL) using a specific format. The conversion process generates a conversion matrix from the data structure. The conversion matrix represents the behavior of the circuit element in a generic format. The conversion process then determines a generic HDL register and a plurality of generic HDL input logic for the generic HDL register to replicate the behavior represented by the data structure based on the conversion matrix.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
Multi-value digital calculating circuits, including multipliers
InactiveUS7562106B2Limit overall switching delayIncrease heightComputation using non-contact making devicesDigital computer detailsBinary multiplierTruth value
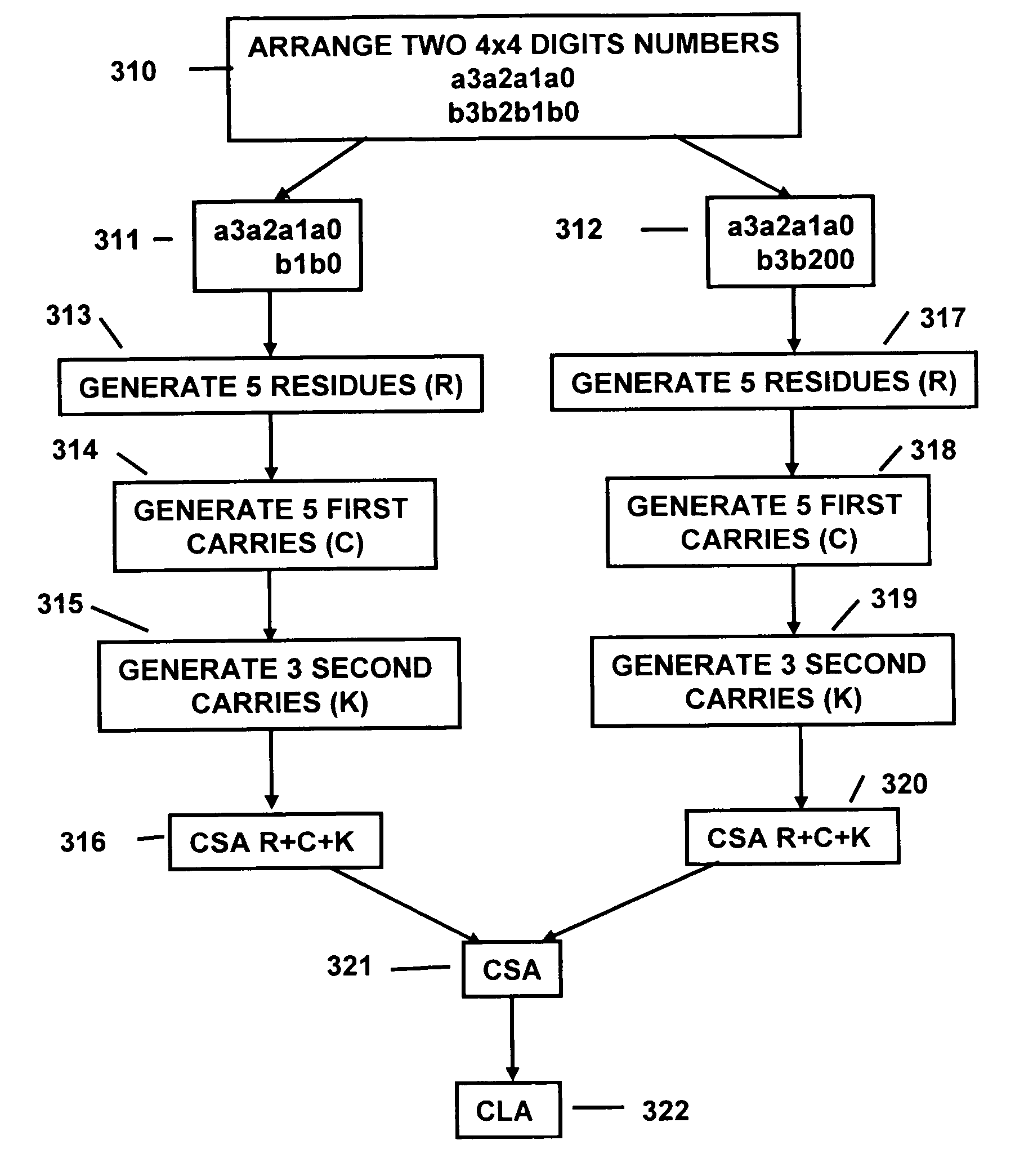
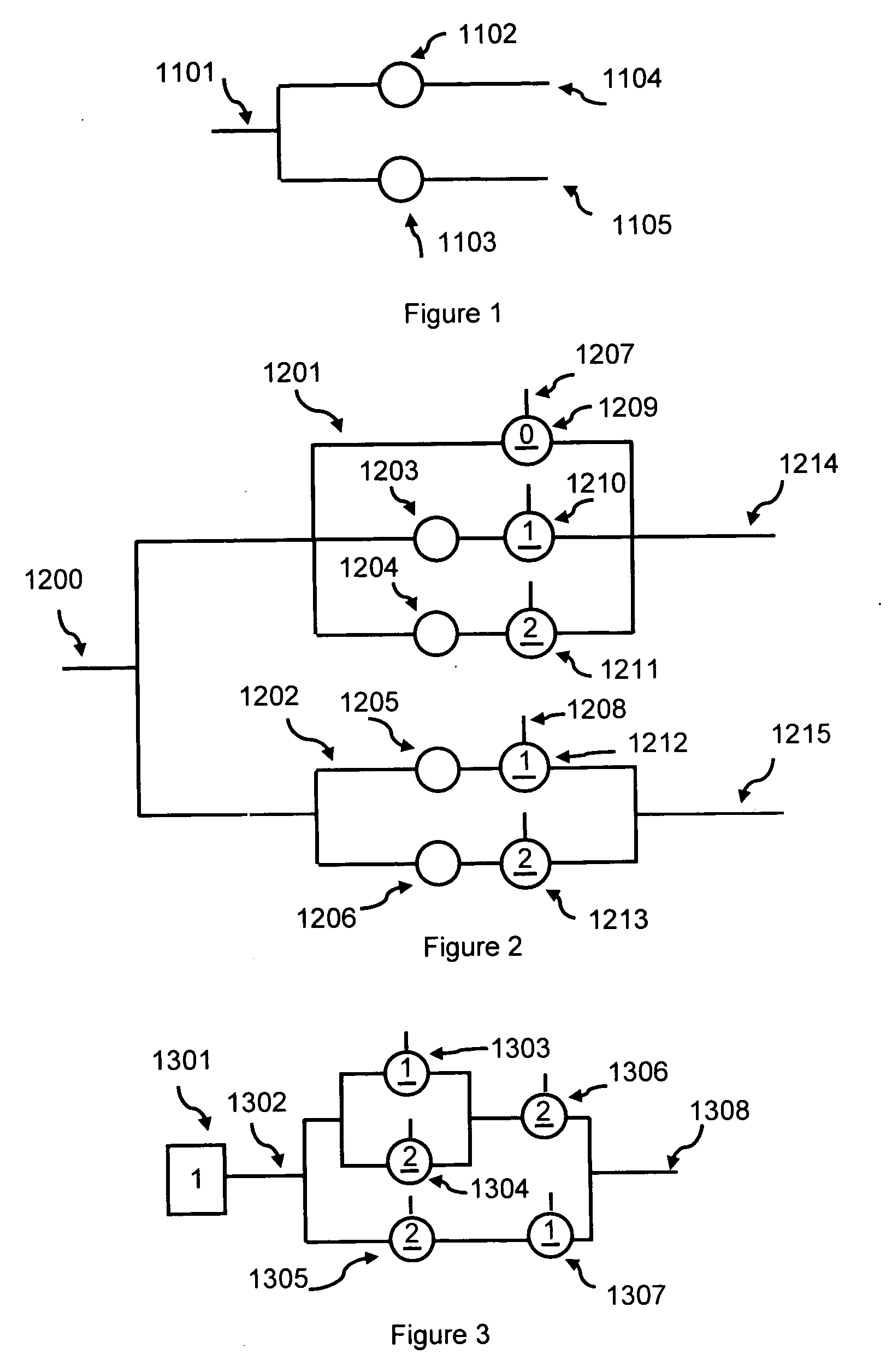
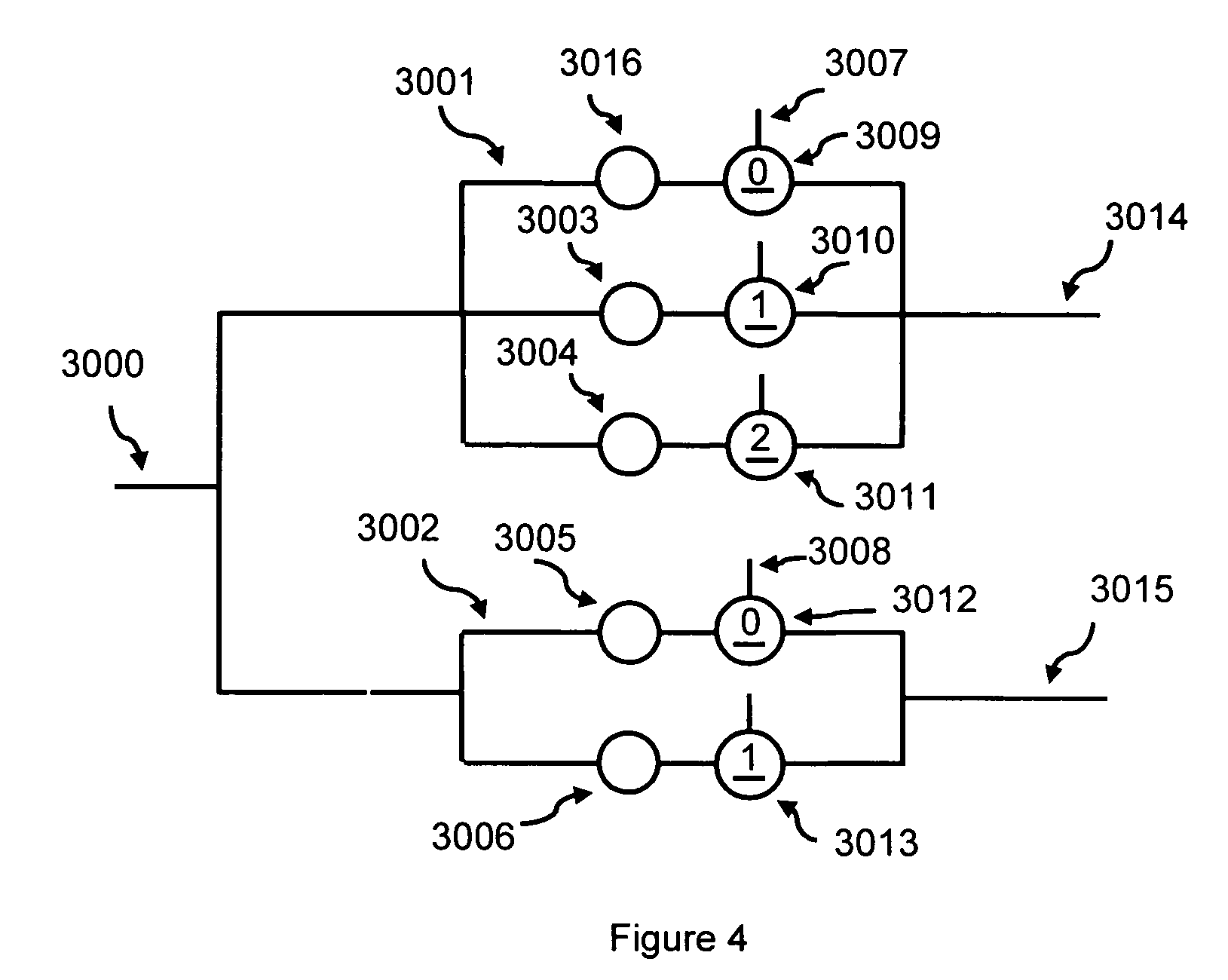
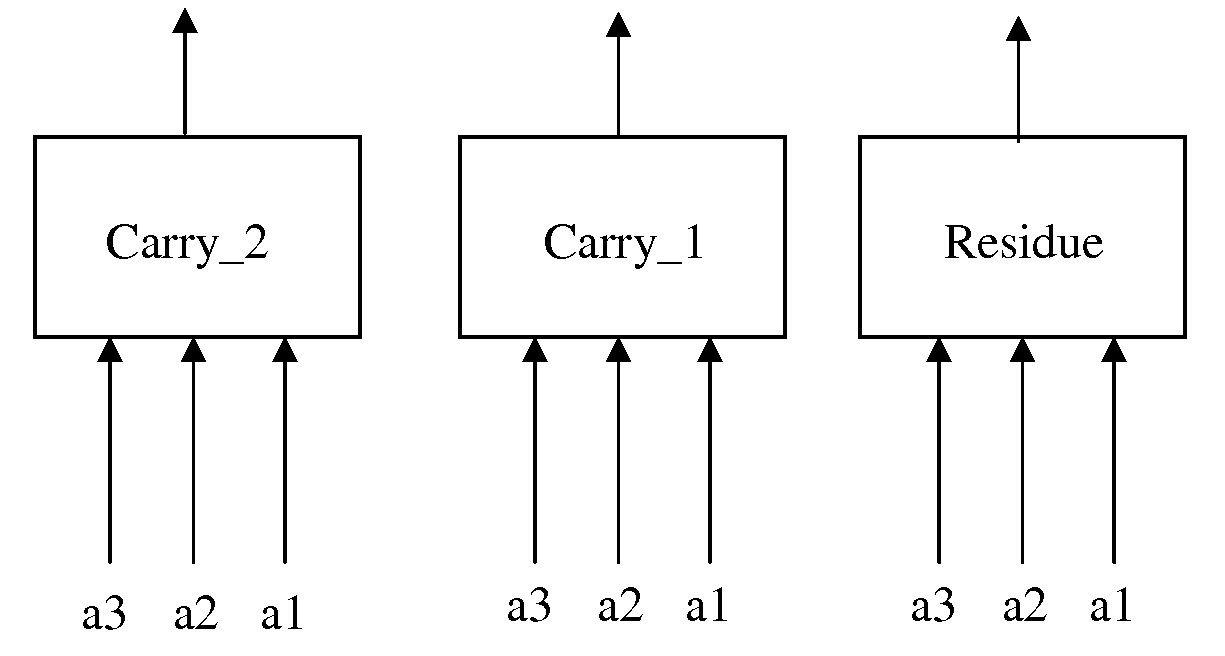
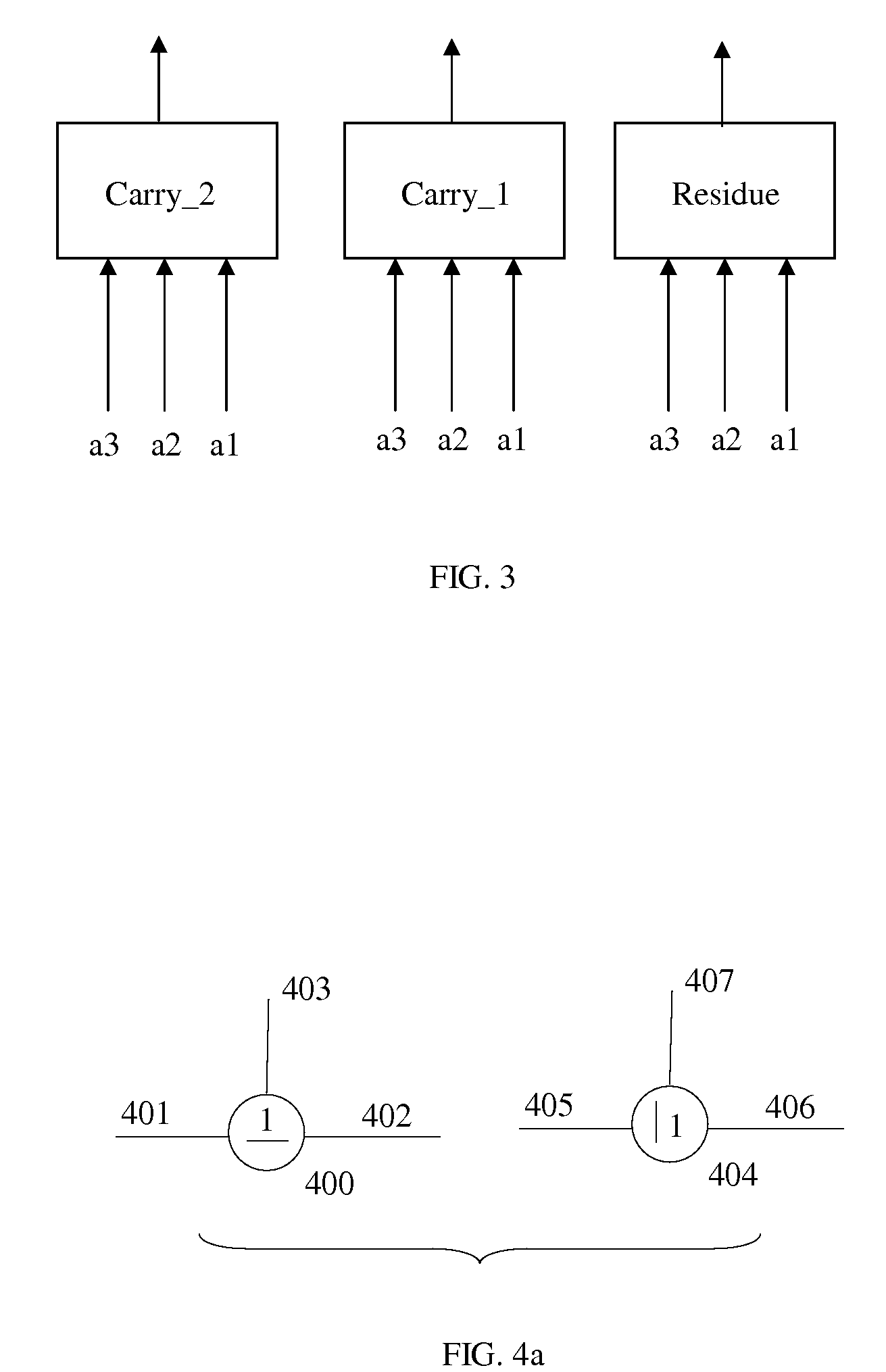
Apparatus and method for performing multi-value arithmetic operations are disclosed. Multi-value signals can be added, subtracted and multiplied using a first truth table to generate a residue and a second truth table to generate a carry. Additionally, method and apparatus to efficiently perform the function a0b1+a1b0 on multi-value signals are disclosed. Also an efficient method of processing large binary signals is disclosed.
Owner:TERNARYLOGIC
Logic test method and device suitable for reactor protection system
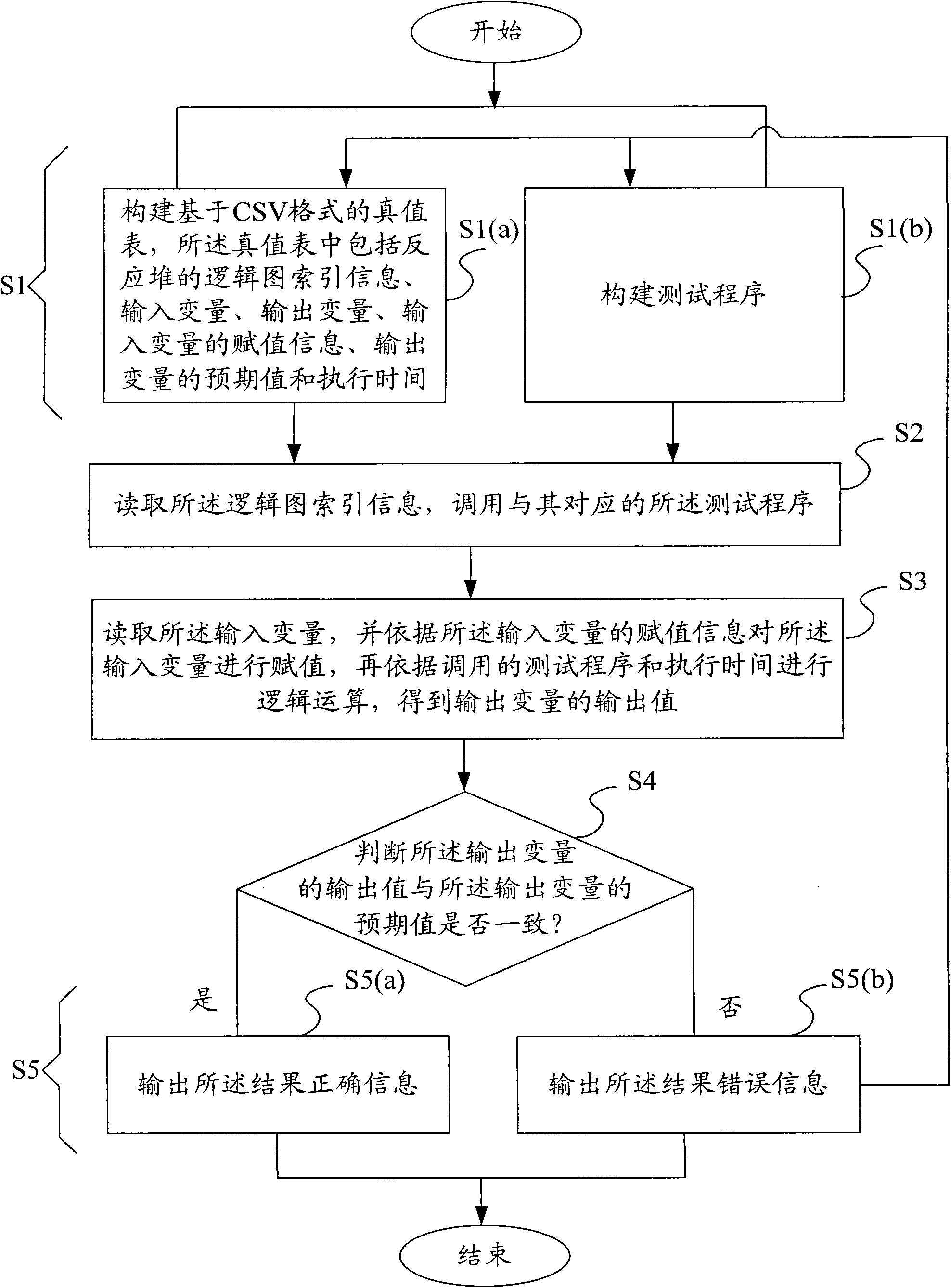
ActiveCN102024504AEasy to modifyEasy to adjustNuclear energy generationNuclear monitoringTruth valueEngineering
The invention relates to a logic test method and device suitable for a reactor protection system. The logic test method comprises a construction step, a call step, an operation step and a judgment step, wherein the construction step is as follows: constructing test programs and a truth table based on a comma separated values (CSV) format, wherein the truth table comprises the logic diagram index information of the reactor protection system, an input variable, an output variable, the voluation information of the input variable, the input variable of the output variable, and an execution time; the call step is as follows: reading the logic diagram index information, calling the test programs corresponding to the logic diagram index information; the operation step is as follows: reading the input variable and carrying out voluation on the input variable in accordance with the voluation information of the input variable, and carrying out logic operation in accordance with the called test program and the execution time so as to obtain the output value of the output variable; and the judgment step is as follows: judging whether the output value of the output variable is consistent with the expected value, if yes, outputting correct result information, and if no, outputting wrong result information. In the logic test method, the test is carried out by constructing the truth table based on the CSV format and the test program, thus being convenient for modification and regulation, and avoiding human errors.
Owner:中广核工程有限公司 +2
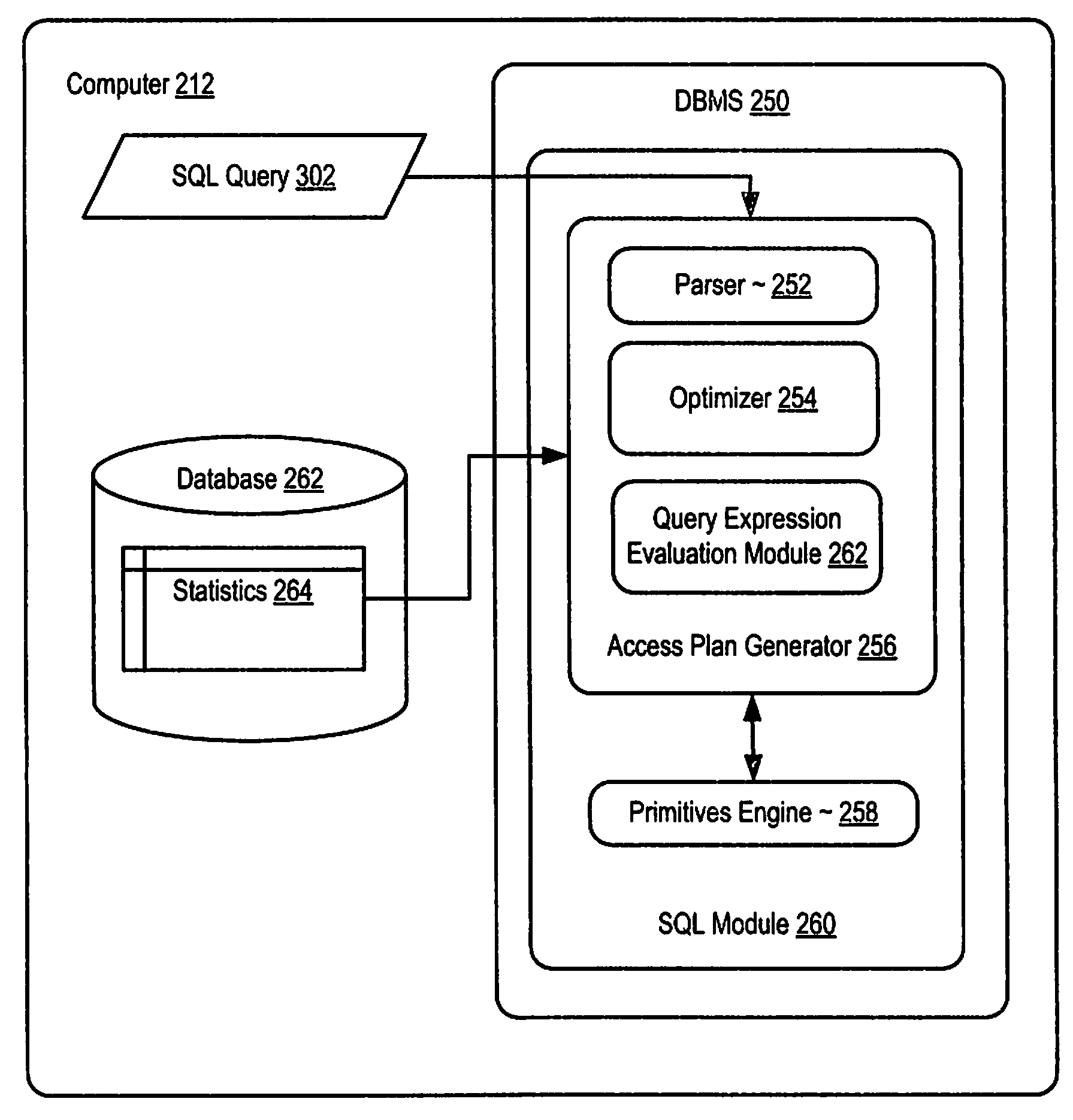
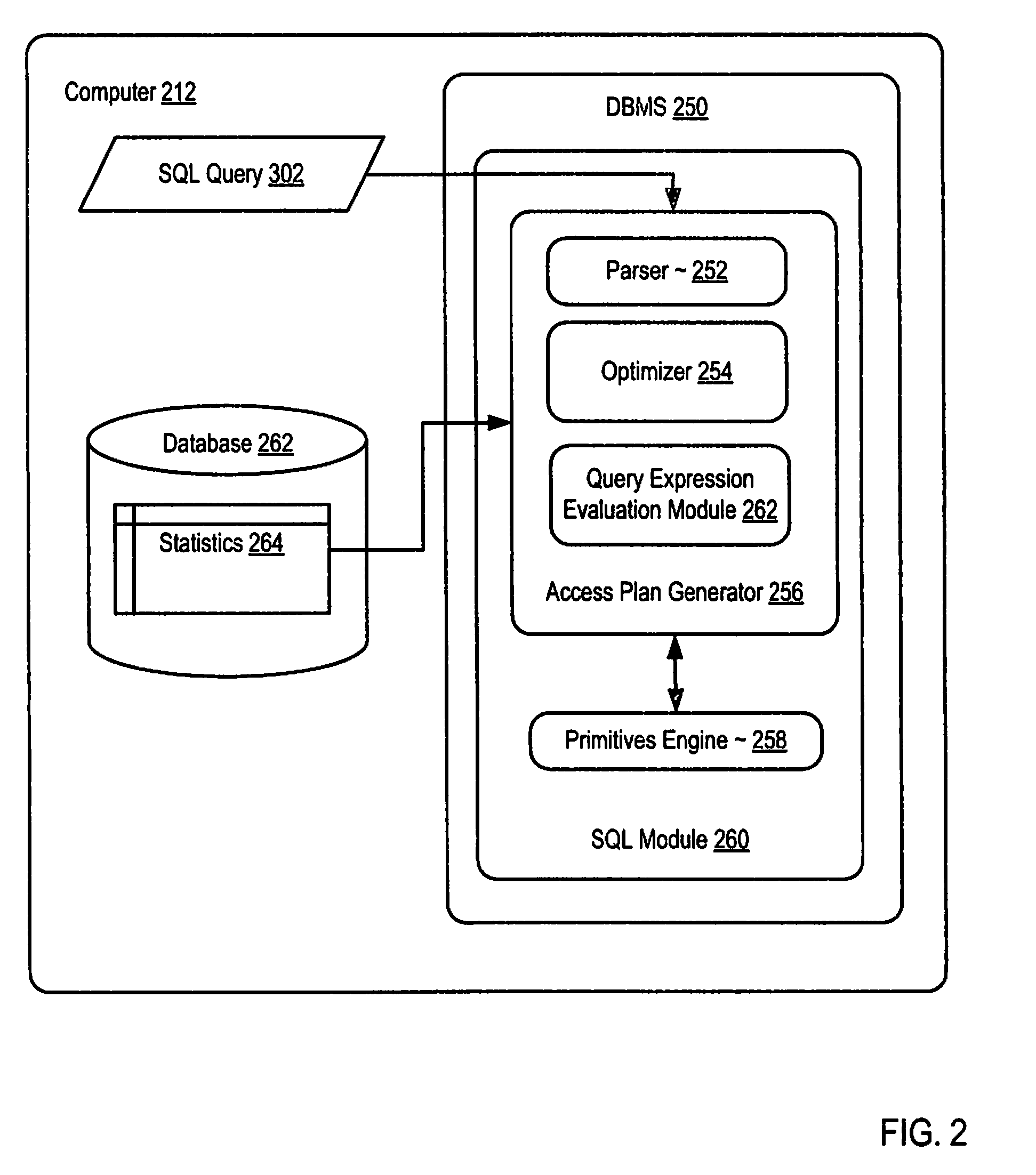
Query Expression Evaluation Using Sample Based Projected Selectivity
InactiveUS20080235181A1Digital data information retrievalSpecial data processing applicationsTruth valueQuery optimization
Methods, systems, and computer program products are provided for query expression evaluation for query optimization. Embodiments include receiving a query including a plurality of predicates; creating a truth table representing the possible solutions to the query; identifying a plurality of intersections of the truth table, the plurality of intersections including each predicate of the query; assigning a selectivity factor to each predicate; determining in dependence upon the selectivity factors for each predicate a selectivity rating for each of the intersections of the truth table; selecting one or more of the intersections in dependence upon the selectivity rating; and determining in dependence upon the selected intersections a percentage of rows in a database table returned by the query; and providing the percentage of rows in the database table to an access plan generator for query optimization.
Owner:IBM CORP
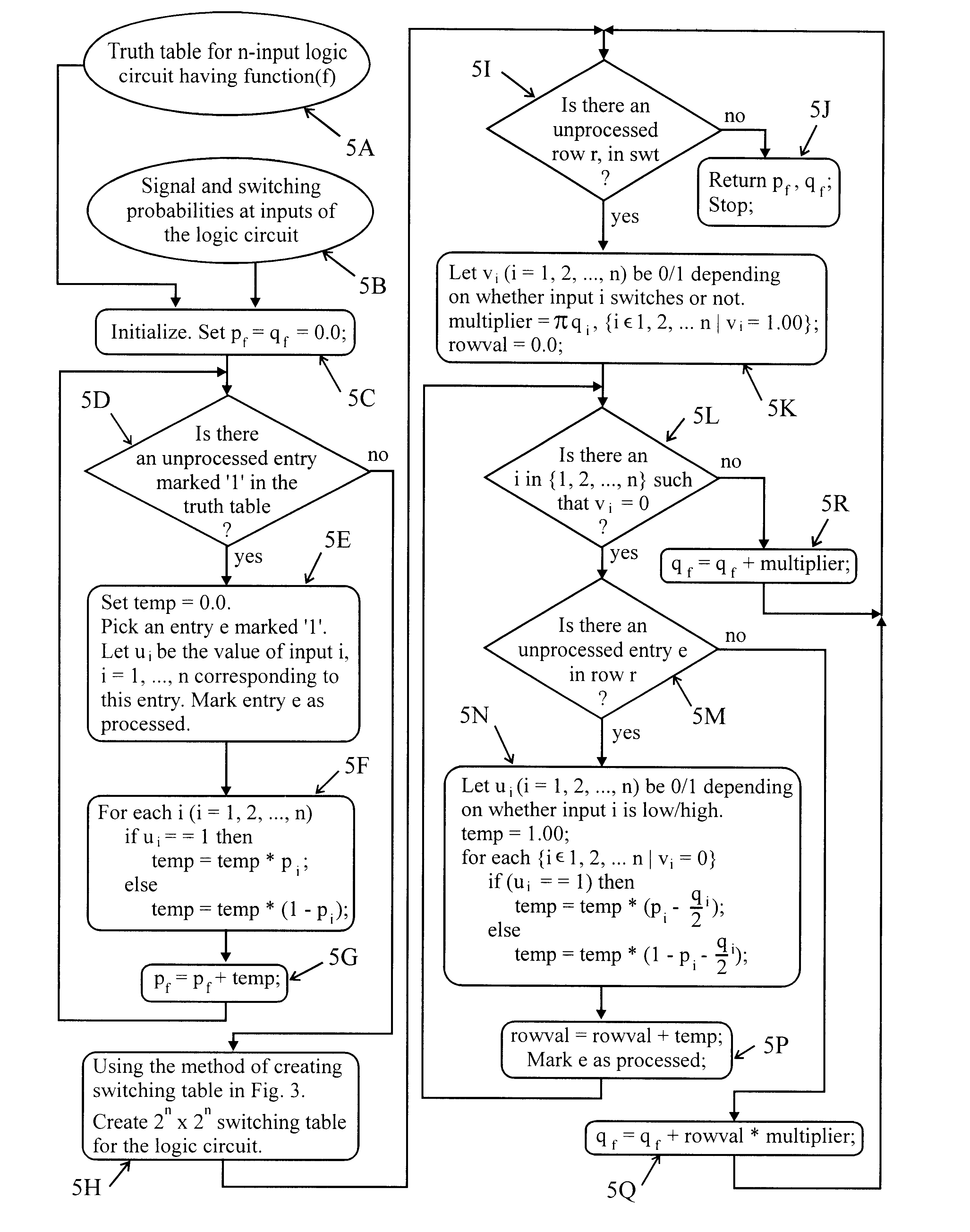
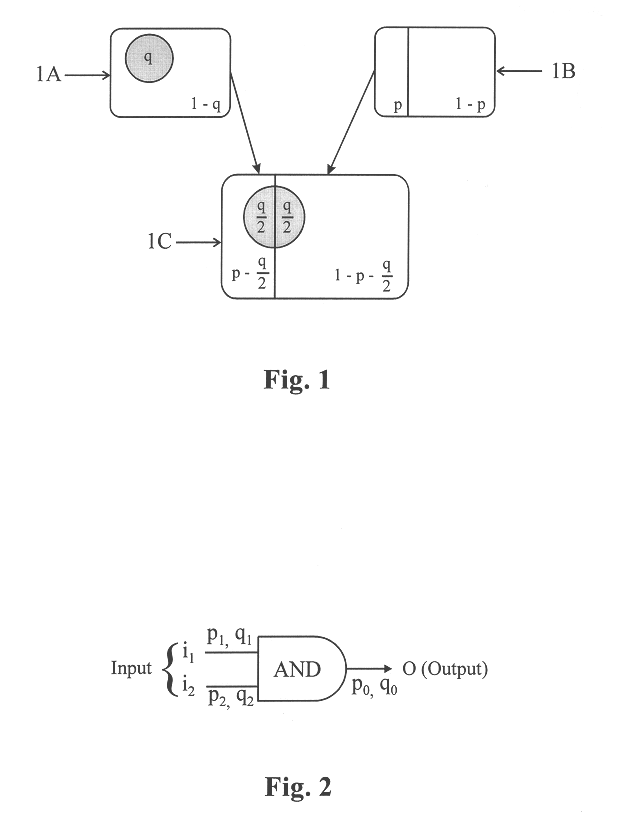
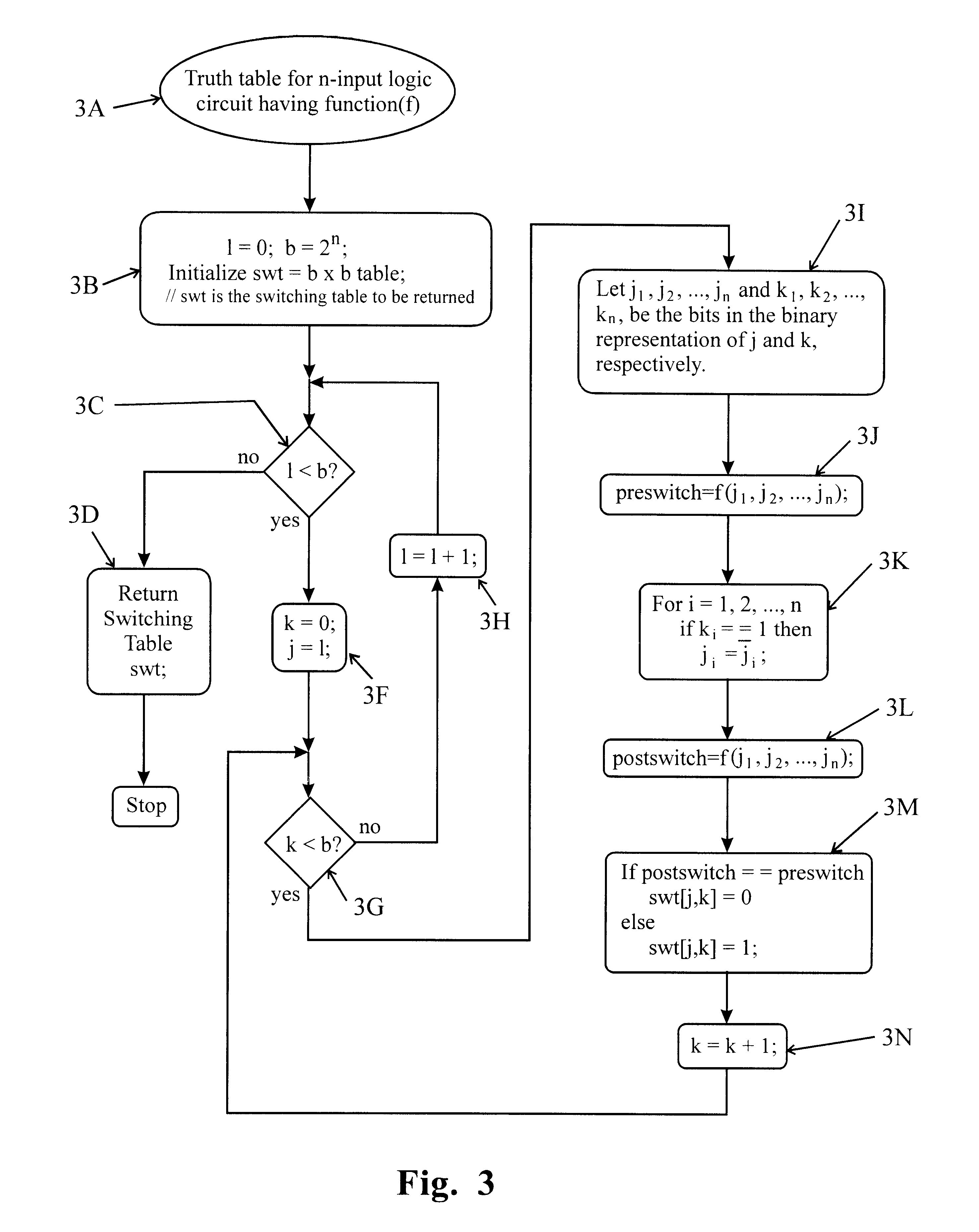
Method for propagating switching activity information in digital combinatorial networks
A method is provided for computing signal and switching probabilities at an output of a logic circuit in a network having multiple logic circuits. The method for computing the signal and switching probabilities includes steps of creating a truth table for a logic circuit where the truth table has entries respectively corresponding to signals at inputs of the logic circuit, choosing in sequence one of entries each representing switching of a signal at the output of the circuit, determining whether a signal at an input corresponding to the chosen entry is at logic high, assigning an event probability representing that the signal is at logic high, and accumulating event probabilities respectively assigned to signals at inputs corresponding to the chosen entries to produce the signal probability at the output of the circuit.
Owner:GOOGLE LLC
Multi-value digital calculating circuits, including multipliers
InactiveUS20060031278A1Limit overall switching delayIncrease heightComputation using non-contact making devicesDigital computer detailsTruth valueBinary multiplier
Apparatus and method for performing multi-value arithmetic operations are disclosed. Multi-value signals can be added, subtracted and multiplied using a first truth table to generate a residue and a second truth table to generate a carry. Additionally, method and apparatus to efficiently perform the function a0b1+a1b0 on multi-value signals are disclosed. Also an efficient method of processing large binary signals is disclosed.
Owner:TERNARYLOGIC
Method of automatically formulating test cases for verifying at least part of a piece of software
InactiveUS8612171B2Reliable detectionMinimal interventionError detection/correctionSpecial data processing applicationsTruth valueTheoretical computer science
A method of automatic formulation by a computer of test cases for verifying at least one function of a piece of software in relation to a specification including requirements relating input values and output values of the software, the method including the steps of:distinguishing combinatorial requirements and sequential requirements;modeling combinatorial requirements by a truth table and sequential requirements by a finite state machine to obtain a modeled specification;establishing an operation matrix relating the input values of the software with a probability of them being in succession and a transition time between them;selecting the successions of input values to be tested by performing a Monte Carlo draw on the operation matrix;determining a test case including test rows relating each selected succession with the output values expected given the modeled specification;stopping the determination process when the test case being determined makes it possible to reach a predetermined threshold for at least one of the following criteria: verified percentage of function code, verified percentage of requirements, verification time, and verification cost.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
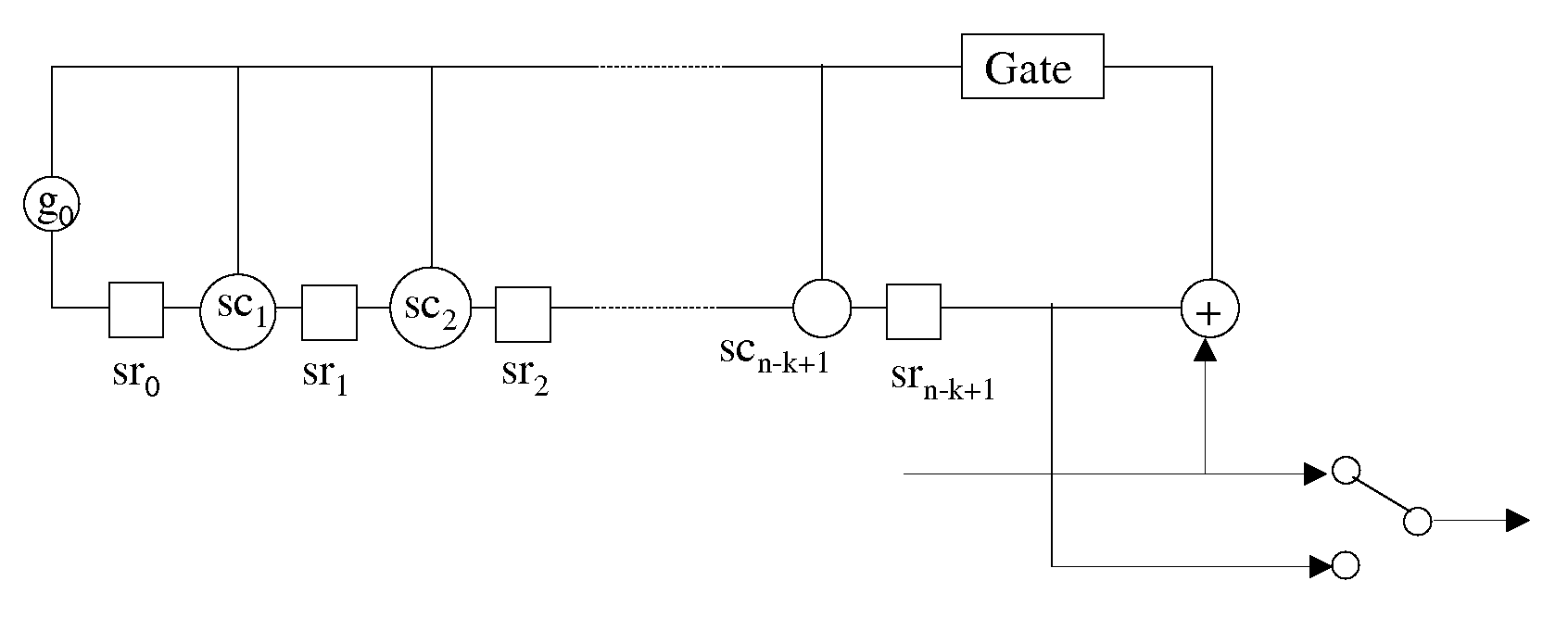
Methods and apparatus in finite field polynomial implementations
InactiveUS20070208796A1Reduced clock speedLess componentsDigital data processing detailsDigital computer detailsMulti inputTruth value
Methods and apparatus reducing the number of multipliers in Galois Field arithmetic are disclosed. Methods and apparatus for implementing n-valued Linear Feedback Shift Register (LFSR) based applications with a reduced number of multipliers are also disclosed. N-valued LFSRs with reduced numbers of multipliers in Fibonacci and in Galois configuration are demonstrated. Multiplier reduction methods are extended to n-valued functions with more than 2 inputs. Methods to create multiplier reduced multi-input n-valued function truth tables are disclosed. Methods and apparatus to implement these truth tables with a limited number of n-valued inverters are also disclosed. Scrambler / descrambler combinations with adders and multipliers over GF(2p) are provided. Communication, data storage and digital rights management systems using multiplier reduction methods and apparatus or the disclosed scrambler / descrambler combination are also provided.
Owner:LABLANS PETER
Design method for no-carry and non-dislocation n value arithmetic device
The invention relates to non carry borrow n value arithmetic device design method. It uses depreciation design method, divides the n value arithmetic Ph(N) truth table Lk(n) into a set of primitive table BLh(n) superposing type, respectively designs out arithmetic primitive Ah(n), uses superposing type to superpose each arithmetic primitive Ah(n) to form n value arithmetic device Ph(n). The invention has conventionalization and standardization design process, suits for fast or auto design, base device reconstruction and multiplexing. This method can be used in various non carry borrow n value arithmetic devices design.
Owner:SHANGHAI UNIV
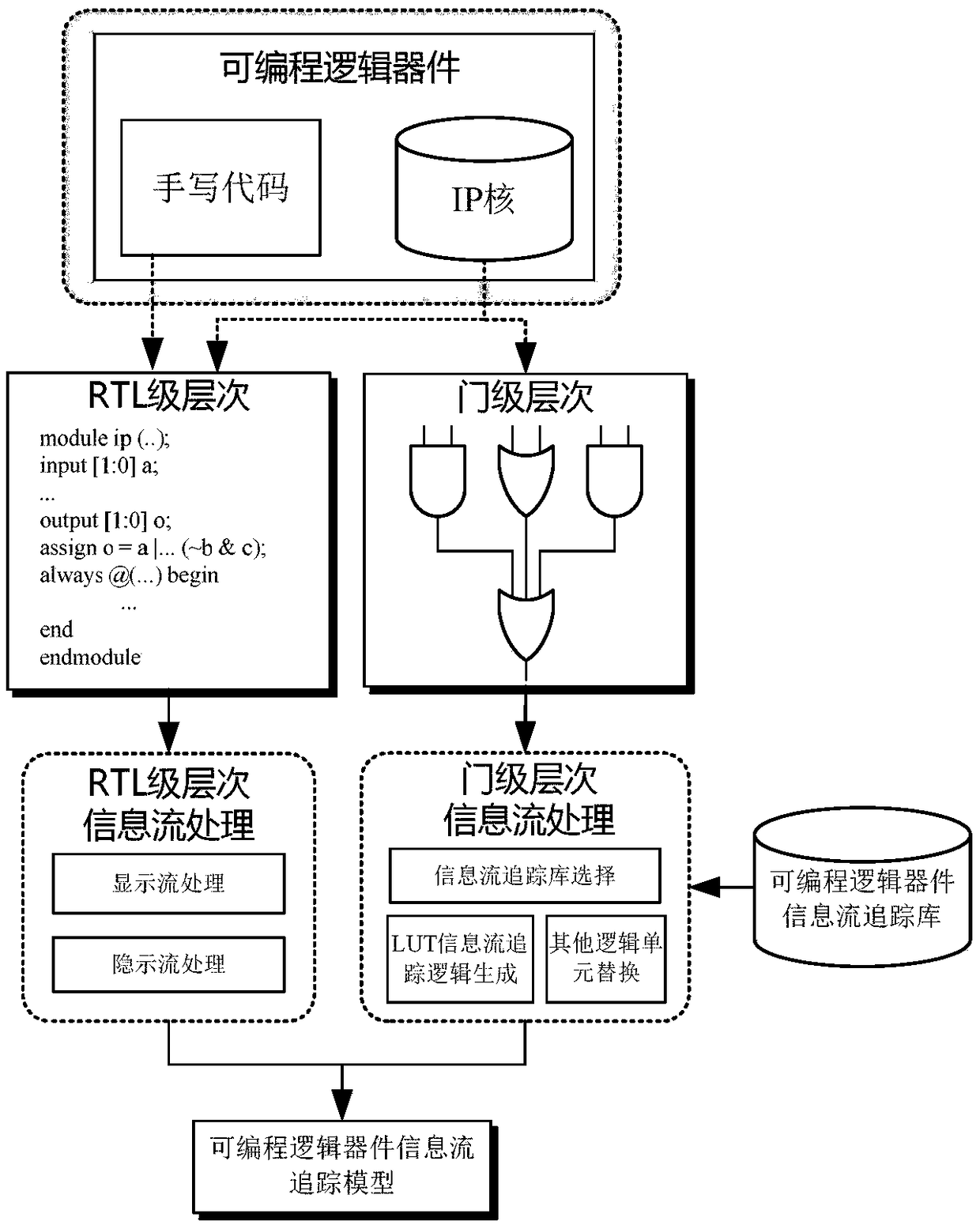
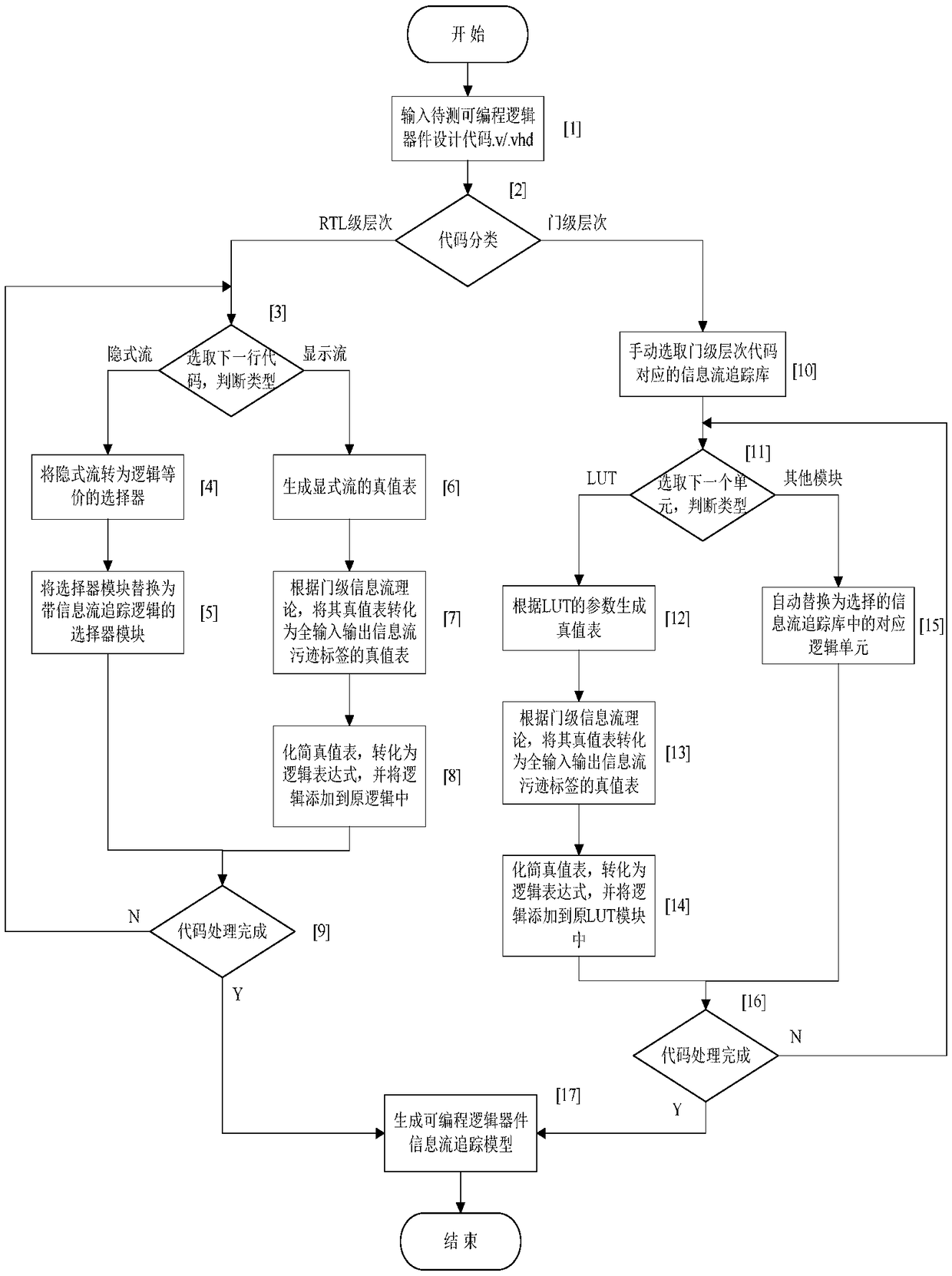
Information flow tracking model generation method of a programmable logic device
ActiveCN109492337AHigh precisionCAD circuit designSpecial data processing applicationsTruth valueTracking model
The invention relates to a high-precision information flow tracking model generation method. The method includes inputting programmable logic device codes; identifying instantiated module names in thecodes; matching the module name with a module name in a netlist library corresponding to the programmable logic device, if the module name is consistent with the module name in a netlist library corresponding to the programmable logic device, determining that the code is a gate level, otherwise, determining that the code is an RTL level, processing display flow in the RTL level, traversing all inputs, calculating assignment statement output, and converting a result into a truth table; inputting an original truth table by using a gate-level information flow theory, and generating a truth tableof full-input / output information flow stain labels; and using the Carnot graph simplified truth table to convert the truth table into information flow tracking logic, and processing implicit flow inthe RTL level, thereby realizing information flow processing of RTL level codes, and processing the gate-level hierarchical information flow. The RTL-level hierarchical codes and the gate-level hierarchical codes in the programmable logic device are classified and subjected to information flow tracking processing respectively, and a programmable logic device information flow tracking model is generated.
Owner:BEIJING INST OF COMP TECH & APPL
Multi-Input, Multi-State Switching Functions and Multiplications
InactiveUS20090077151A1Reduce component countReduce the possibilityComputation using non-contact making devicesMulti inputDigital signal processing
Methods to create an implementation for a multi-input n-state logic function with at least one inverter at an input by modifying the truth table according to the inverter into a reduced truth table are provided. Implementations of the reduced truth table by gates and inverters are also disclosed. Applying reduced truth tables in n-state multiplications are also provided. N-state multiplications may be used in filters, Digital Signal Processing or in Linear Feedback Shift Registers (LFSRs). Using implementations of reduced truth tables in n-state multiplications are disclosed.
Owner:LABLANS PETER
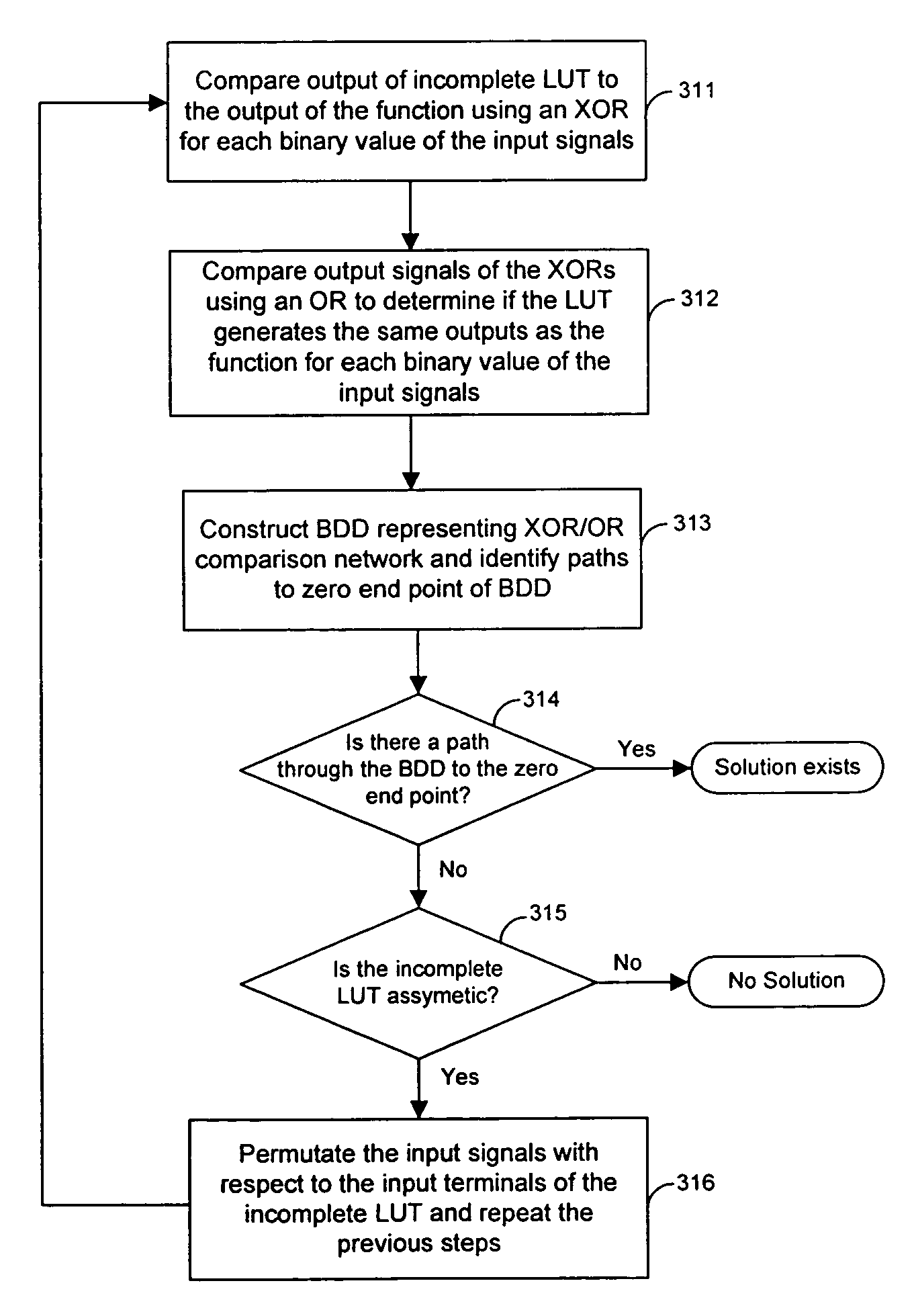
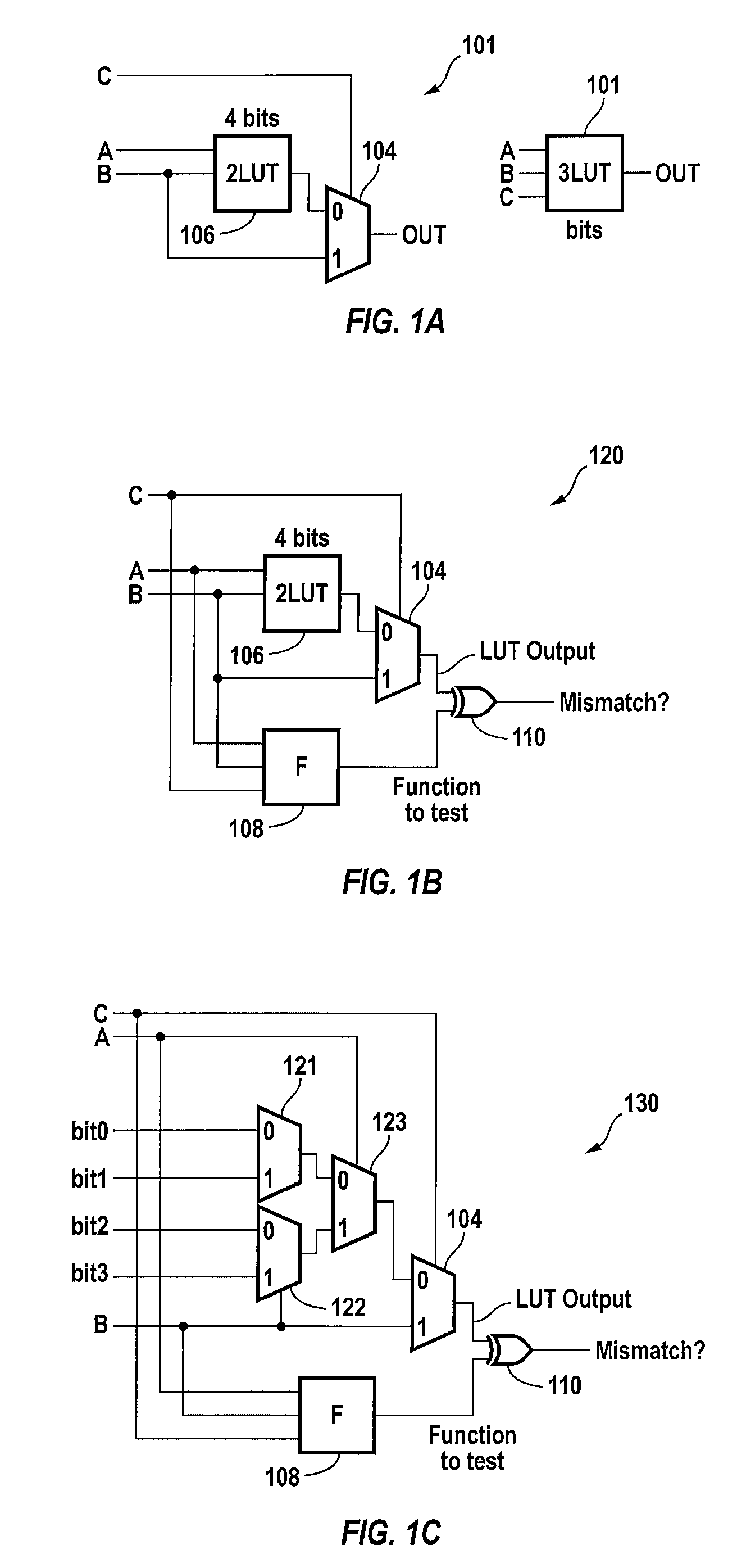
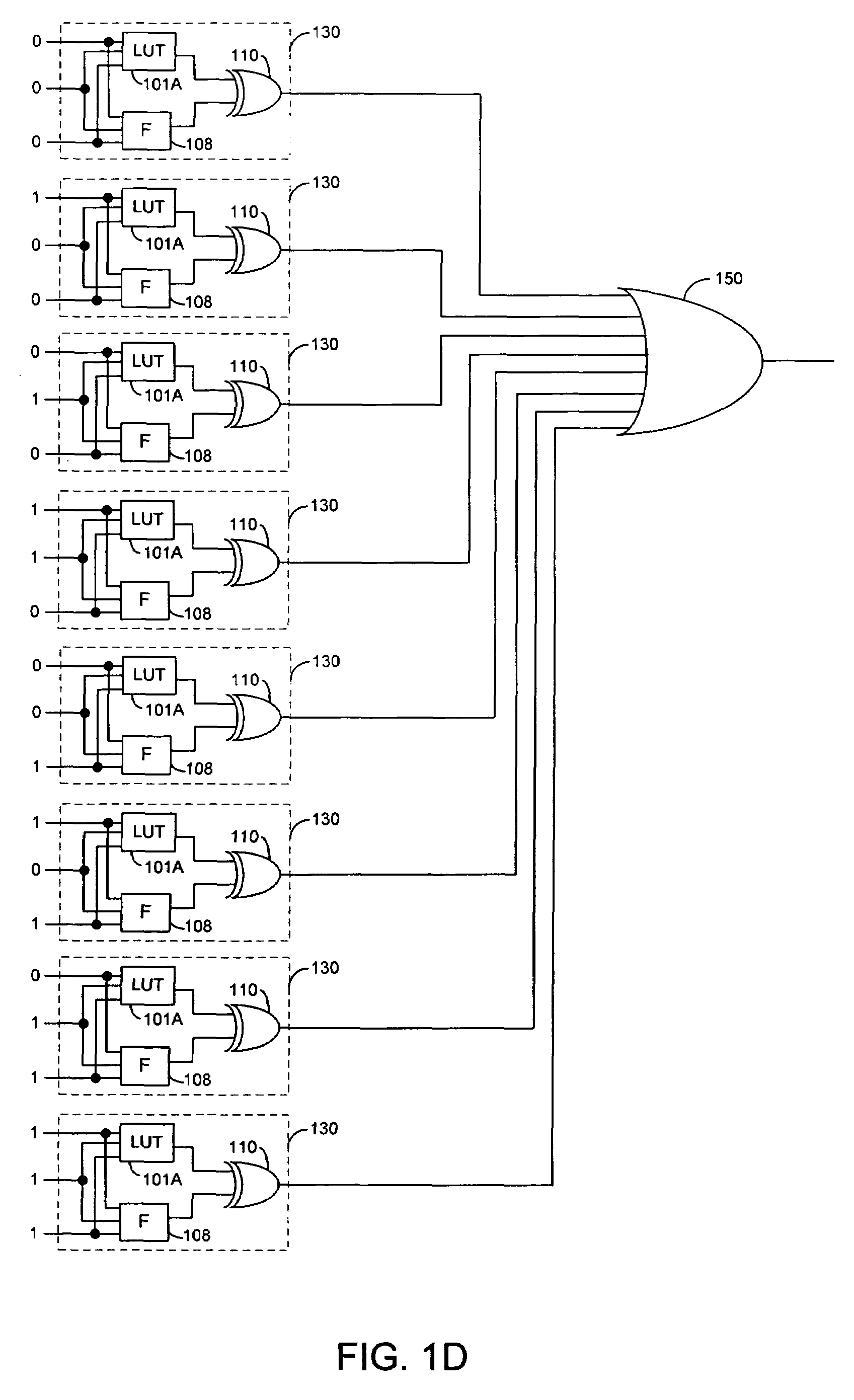
Technology mapping techniques for incomplete lookup tables
Technology mapping techniques for determining whether a function can be implemented using an incomplete lookup table (LUT) are provided. For example, the output of a function is compared to the output of an incomplete LUT for each binary value of the function's input signals and for each binary value of the bits stored in the incomplete LUT. For a LUT that is functionally asymmetric, the process can be repeated for multiple permutations of the input signals with respect to the input terminals of the LUT. As another example, the user function is converted into a network of multiplexers and complete LUTs, which are analyzed to determine if an incomplete LUT can implement the function. As another example, a truth table is constructed for a function. The truth table variables are then tested one by one as candidates for each input position using co-factoring and dependency checking.
Owner:ALTERA CORP
Integrated circuit (IC) optimization using Boolean resynthesis
ActiveUS10740517B1More optimization opportunitySmall and runtime costComputer aided designSpecial data processing applicationsParallel computingTheoretical computer science
Systems and techniques are described for circuit optimization using Boolean resynthesis. Features described in this disclosure include (i) a theory of Boolean filtering, to drastically reduce the number of gates processed and still retain all possible optimization opportunities, (ii) a weaker notion of maximum set of permissible functions, which can be computed efficiently via truth tables, (iii) a parallel package for truth table computation tailored to speedup Boolean methods, (iv) a generalized refactoring engine which supports multiple representation forms and (v) a Boolean resynthesis flow, which combines these techniques.
Owner:SYNOPSYS INC
Form vector-based reduction method for multi-input multi-output truth table
PendingCN110263368ACorrectness statementGuaranteed to minimizeSpecial data processing applicationsMulti inputTruth value
The invention discloses a form vector-based reduction method for a multi-input multi-output truth table, and belongs to the technical field of logic circuit optimization. The technical problem to be solved is to provide a form vector-based reduction method for a multi-input multi-output truth table. The technical scheme for solving the technical problem comprises the following steps: 1, converting a truth table into a decision form background; 2, solving all single-attribute non-zero form vectors according to the conditional form background and the decision form background, and respectively storing the vectors into a conditional form vector set and a decision form vector set; 3, for any conditional form vector and decision form vector, if a rule reduction condition is met, calculating a heuristic operator of the corresponding conditional form vector, and storing the conditional form vector completing the rule extraction operation into a redundant form vector set. The method is used for optimizing the logic relation between the input and the output of the digital logic circuit.
Owner:TAIYUAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com