Android application vulnerability detection method and system based on function control flow
A technology of vulnerability detection and control flow, applied in the field of communication, can solve problems such as high system load, achieve the effect of shortening inspection time, reducing requirements of testers, and improving analysis efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
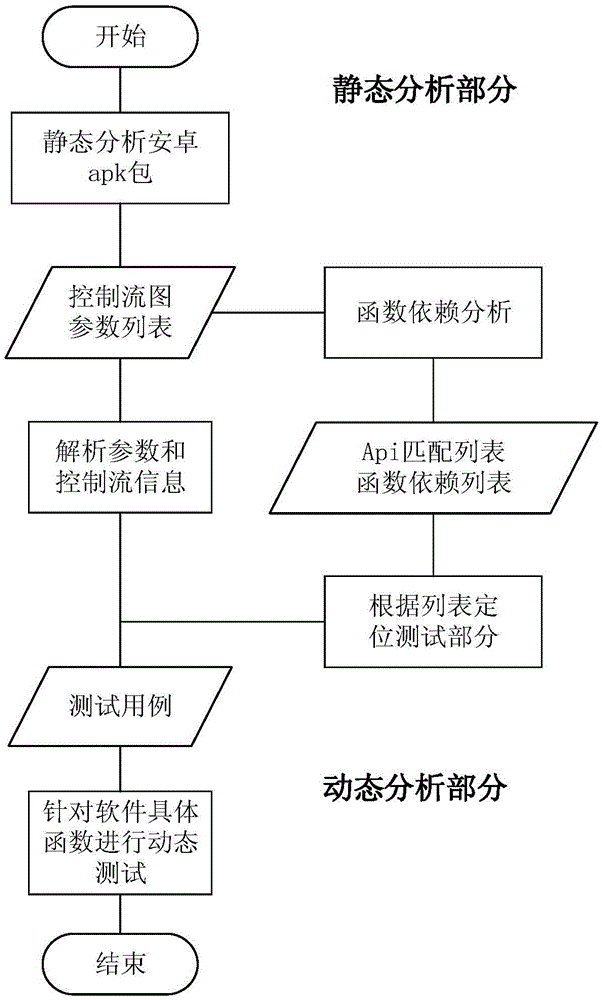
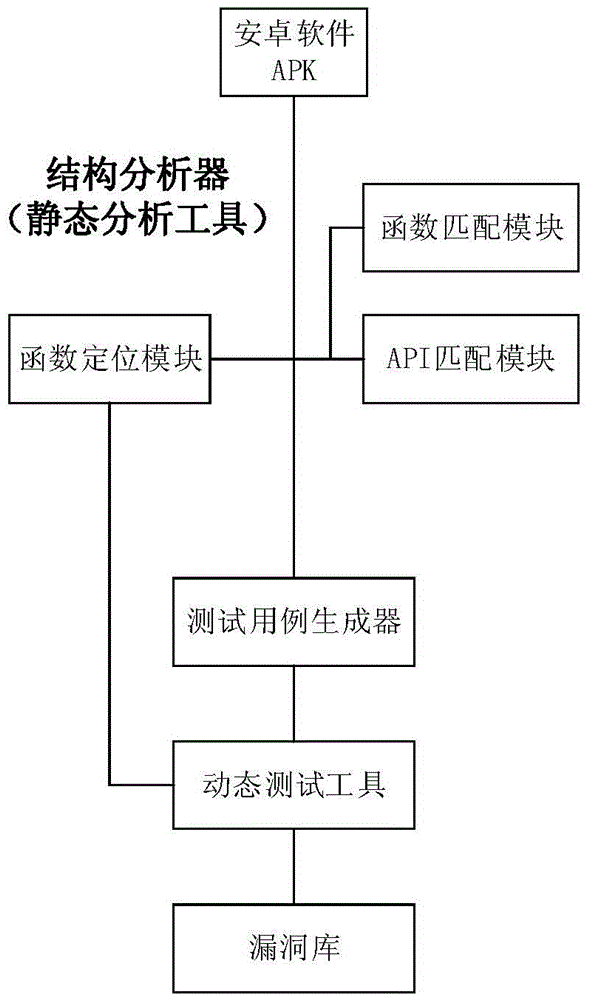
[0028] The invention will be described in further detail below in conjunction with the accompanying drawings.
[0029] The explanation of terms involved in the present invention includes:
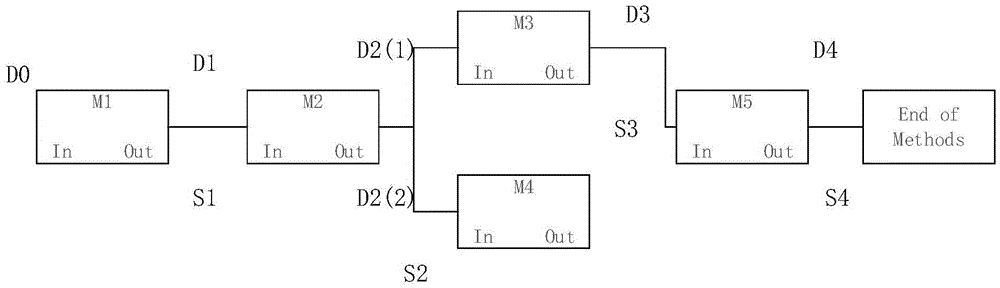
[0030] The function control flow graph refers to a linked list structure obtained through static analysis, which indicates the entry function of the program and the order in which the functions call each other, as well as the end exit of the program, which can be regarded as the function call operation sequence of each step of the program.
[0031] The test case generation method based on the function control flow chart of the present invention specifically includes:
[0032] Step 1: Apply static analysis technology to decompress the apk package to obtain the software source code, and analyze the source code. Due to the characteristics of Android software coding and its own system, it is necessary to analyze the ContentProvider, BroadcastReceiver, Service and The registration status of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com