Patents
Literature
113 results about "Complex data structures" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The complex type is a data table or structure that is sent to a BAPI when a query is run and more than one record needs to be sent. Complex data structures can easily be sent to SAP or received using Serialization or Deserialization methods.
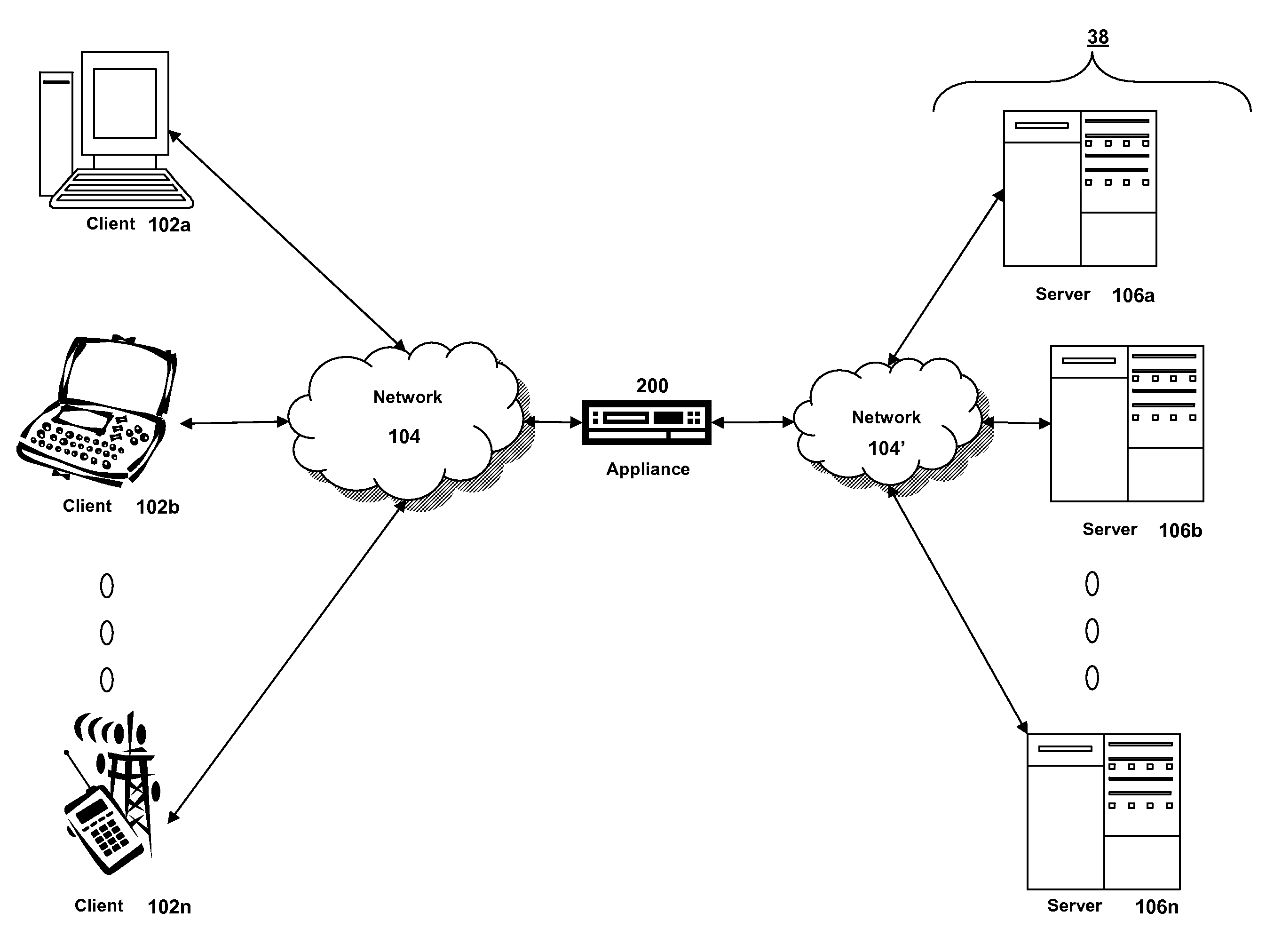
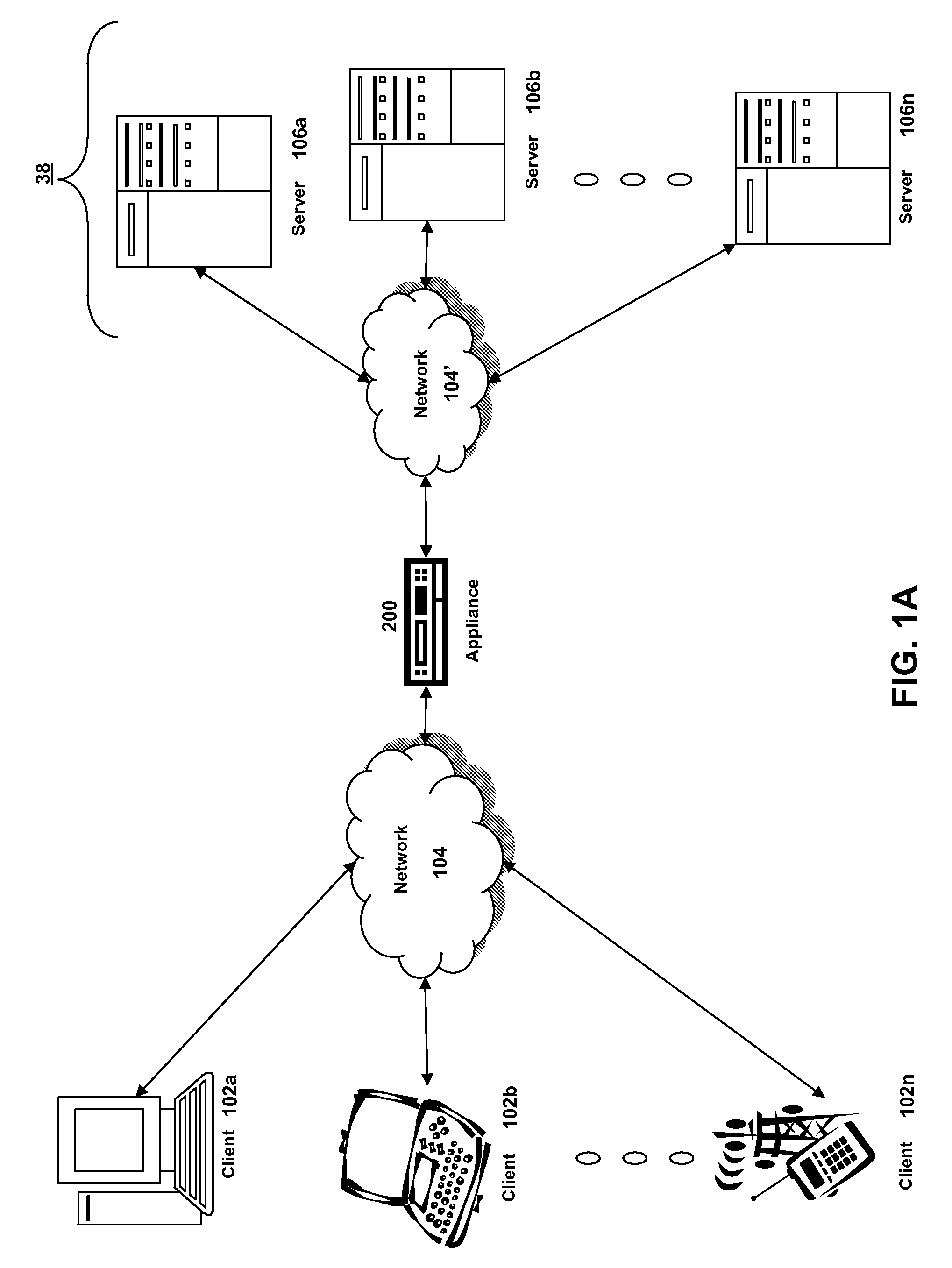
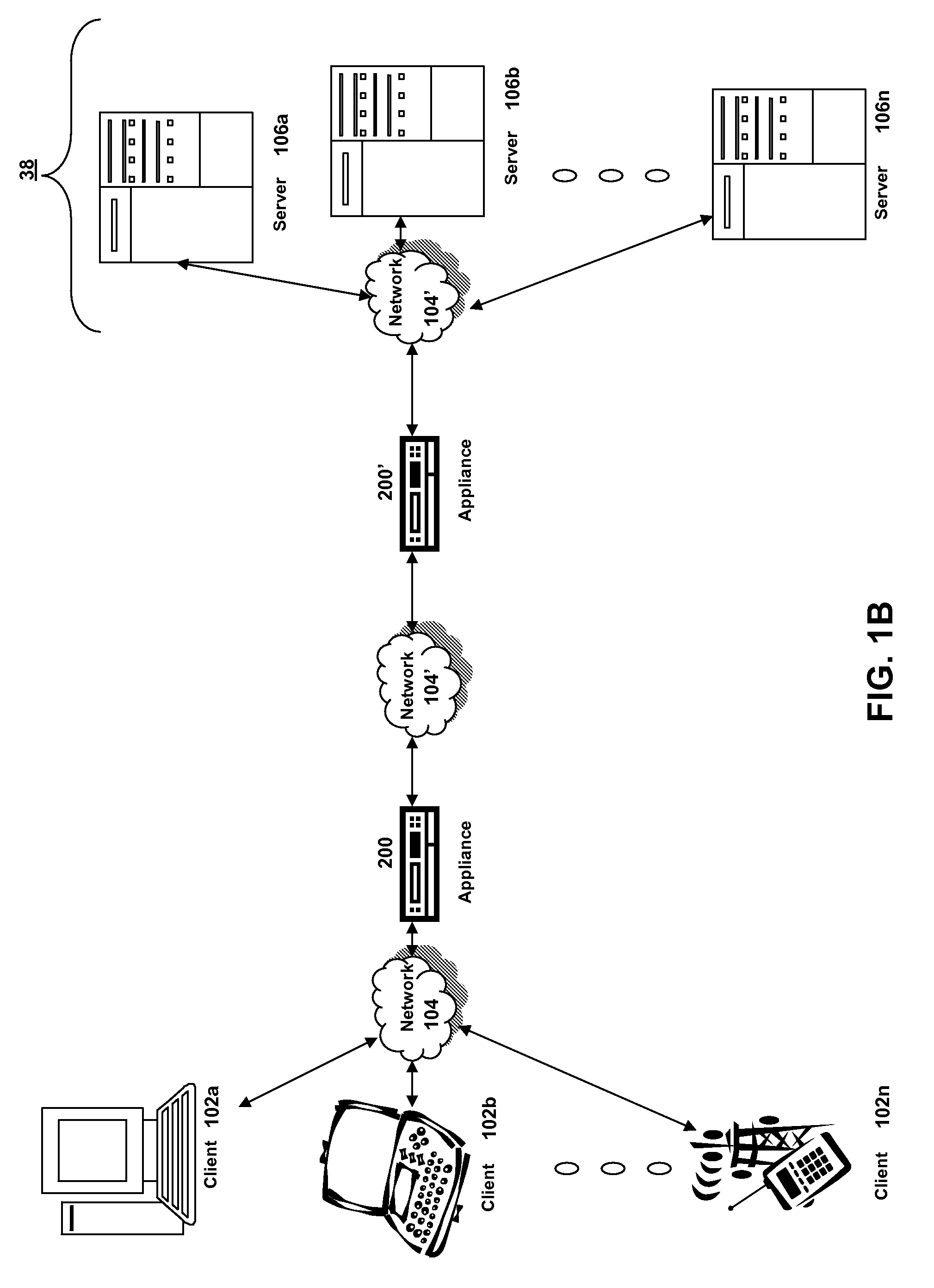
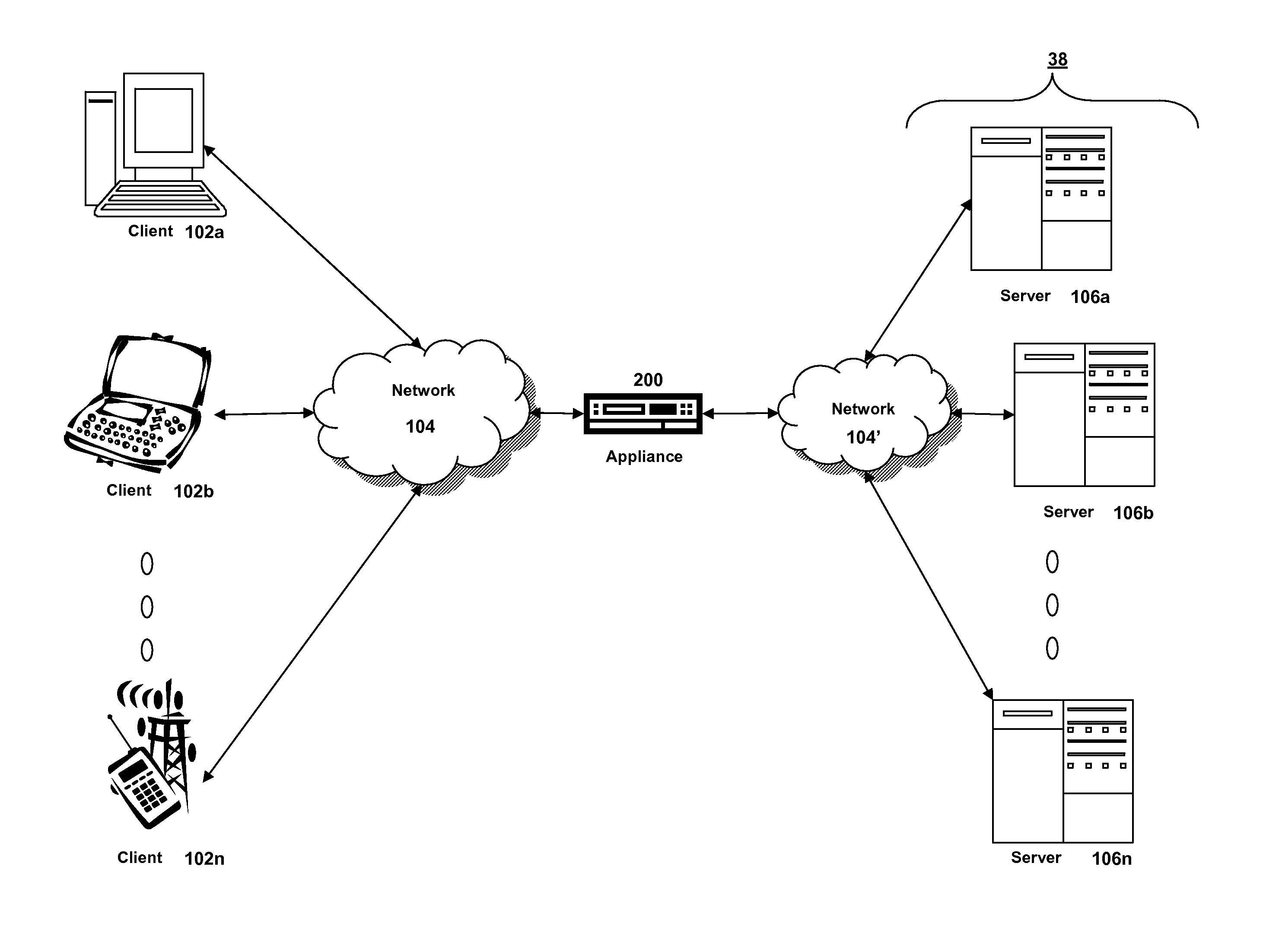
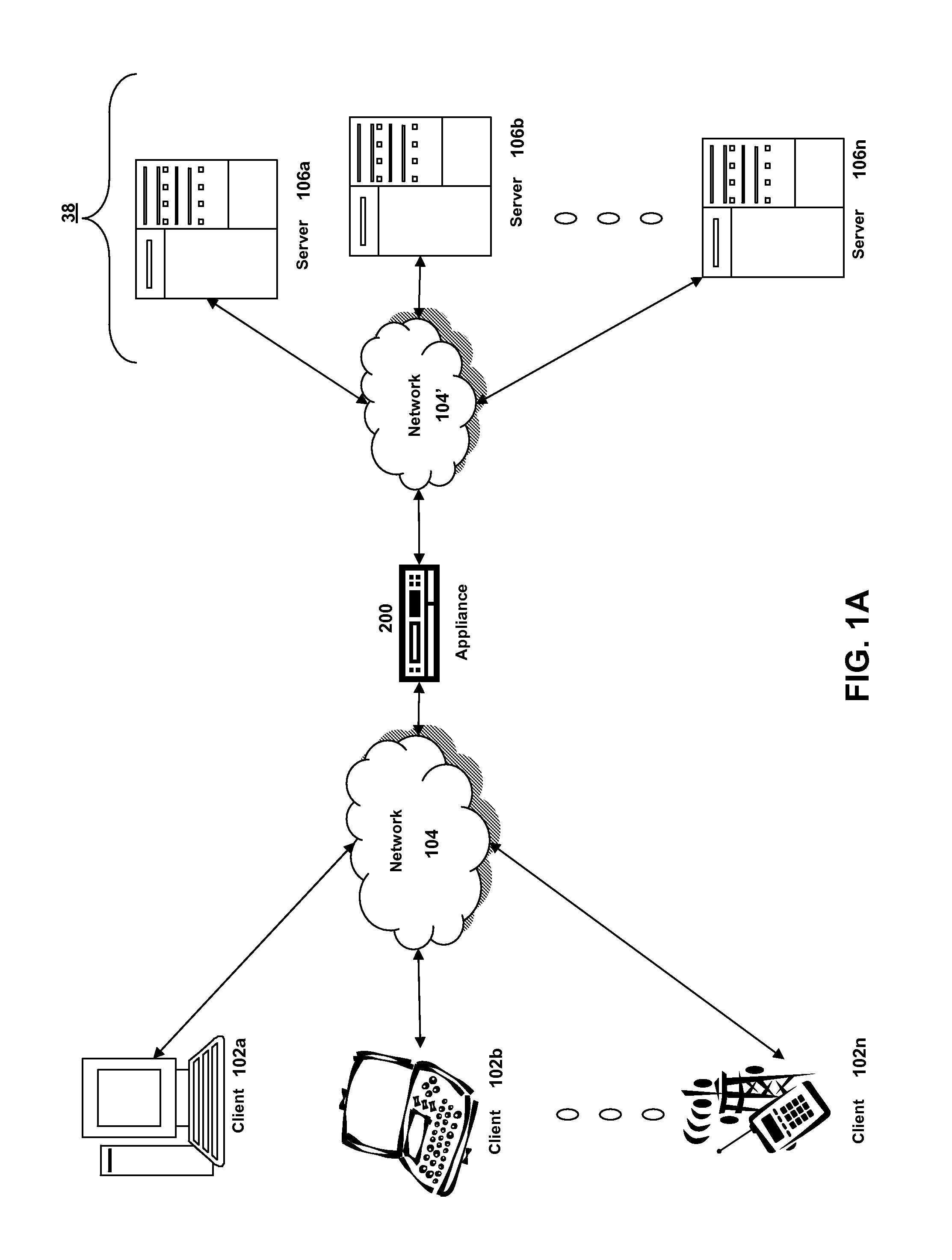
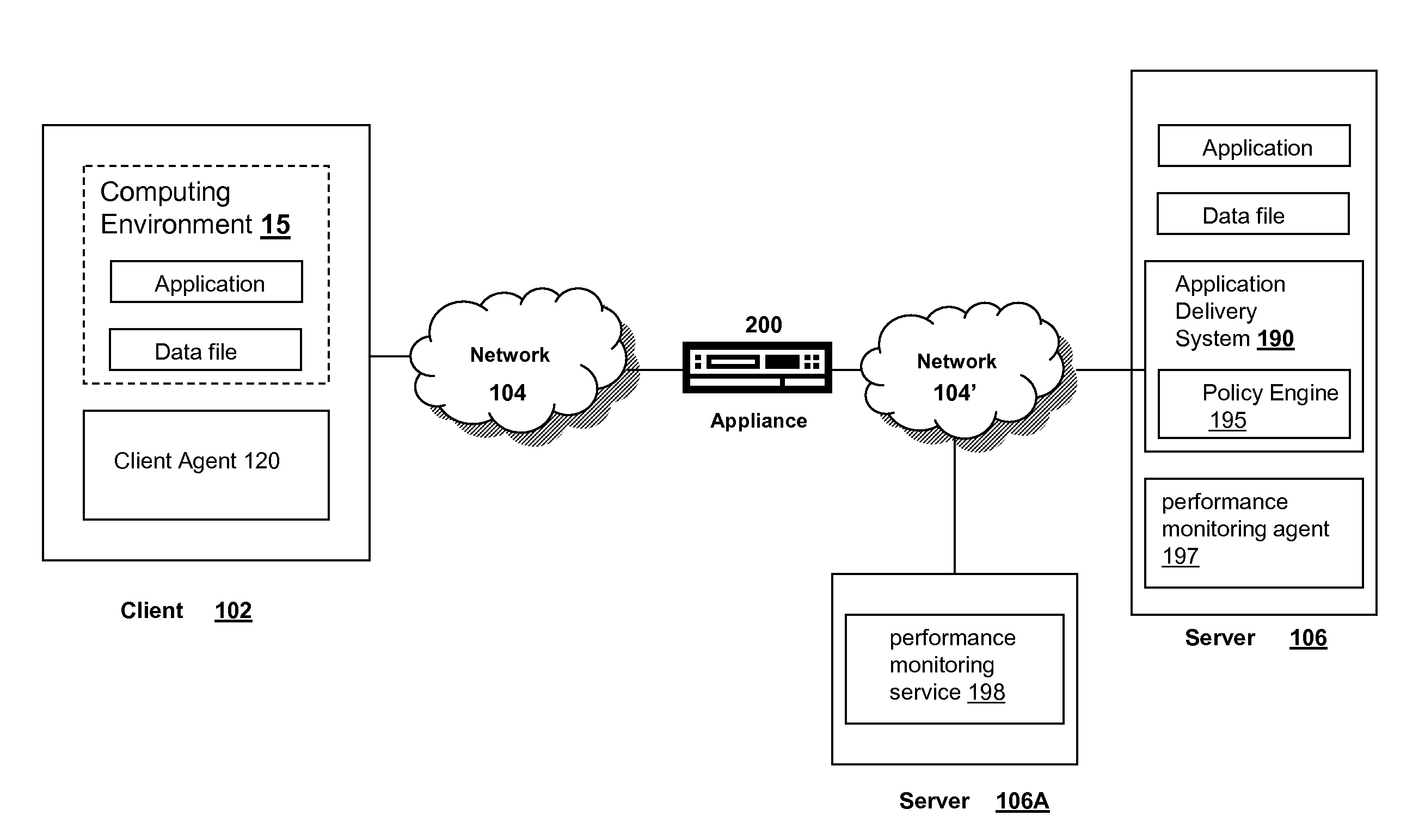
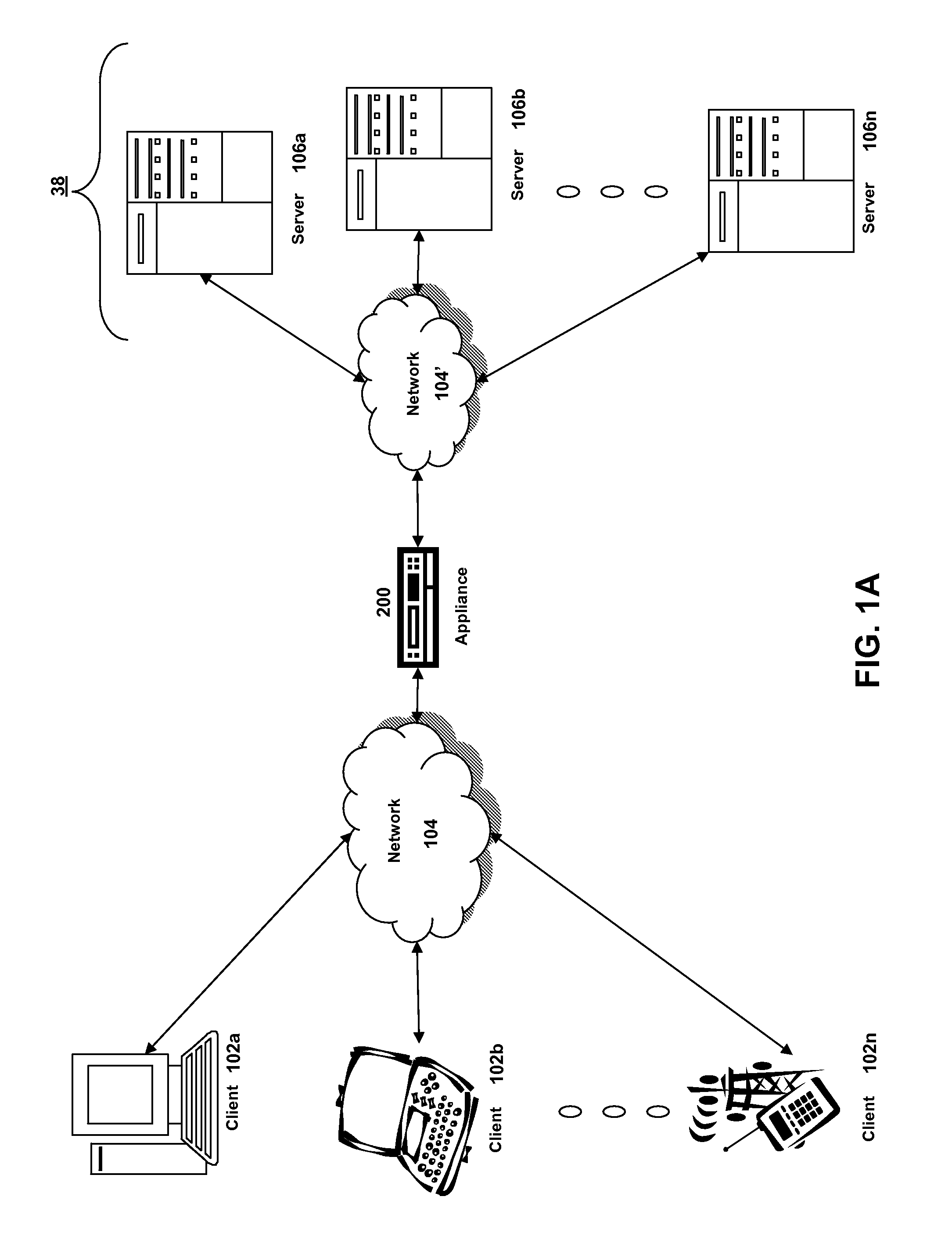
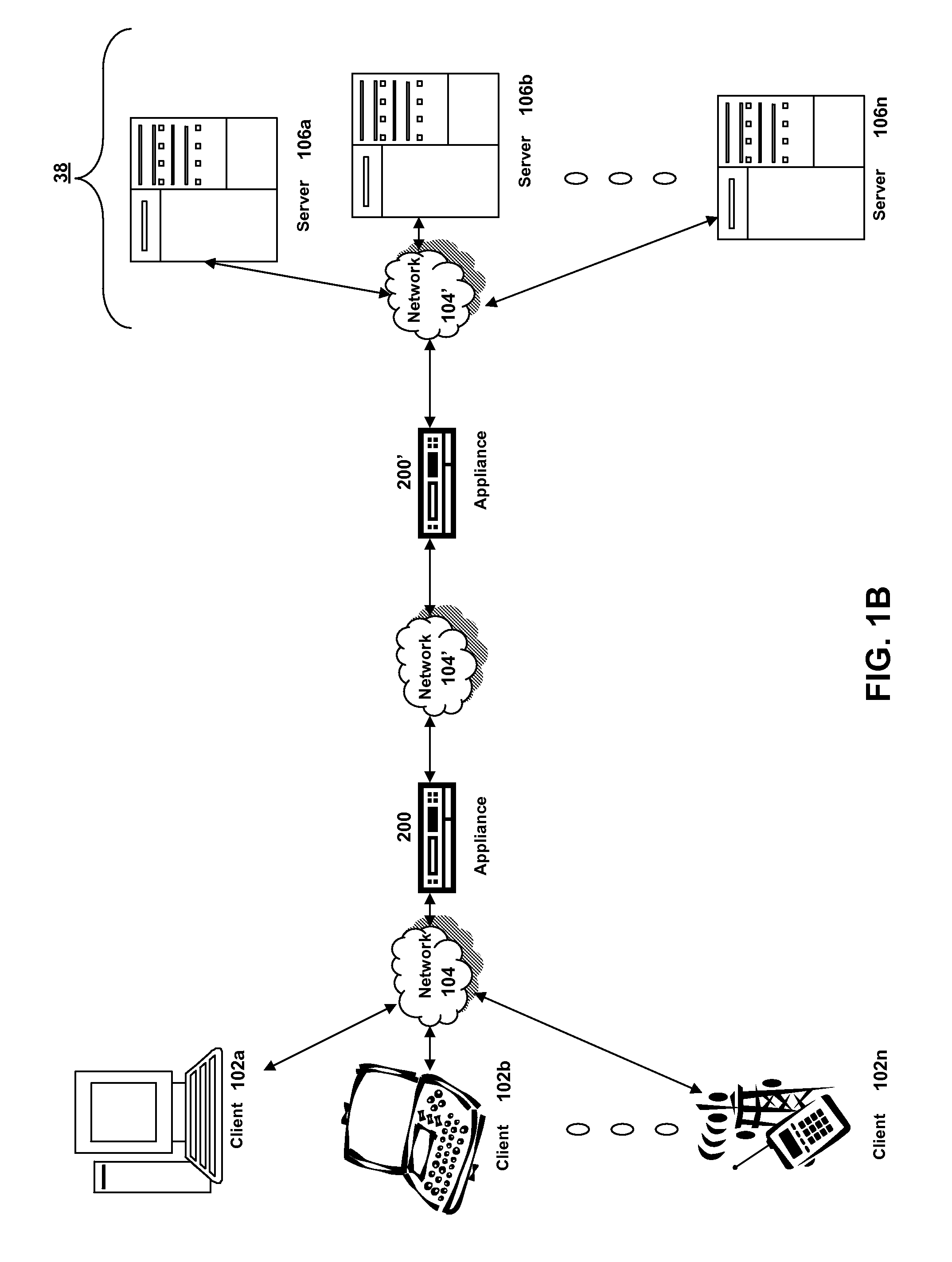
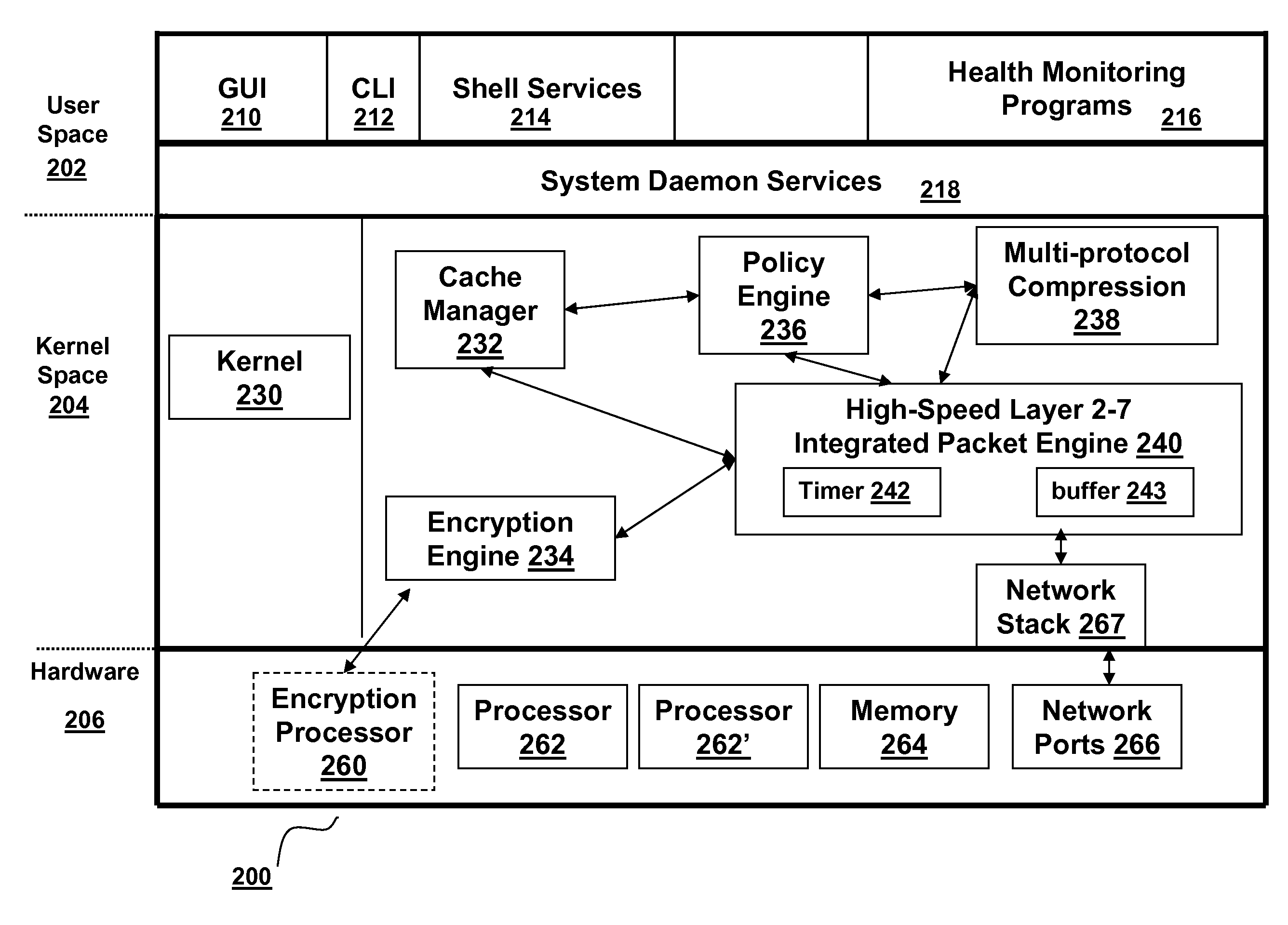
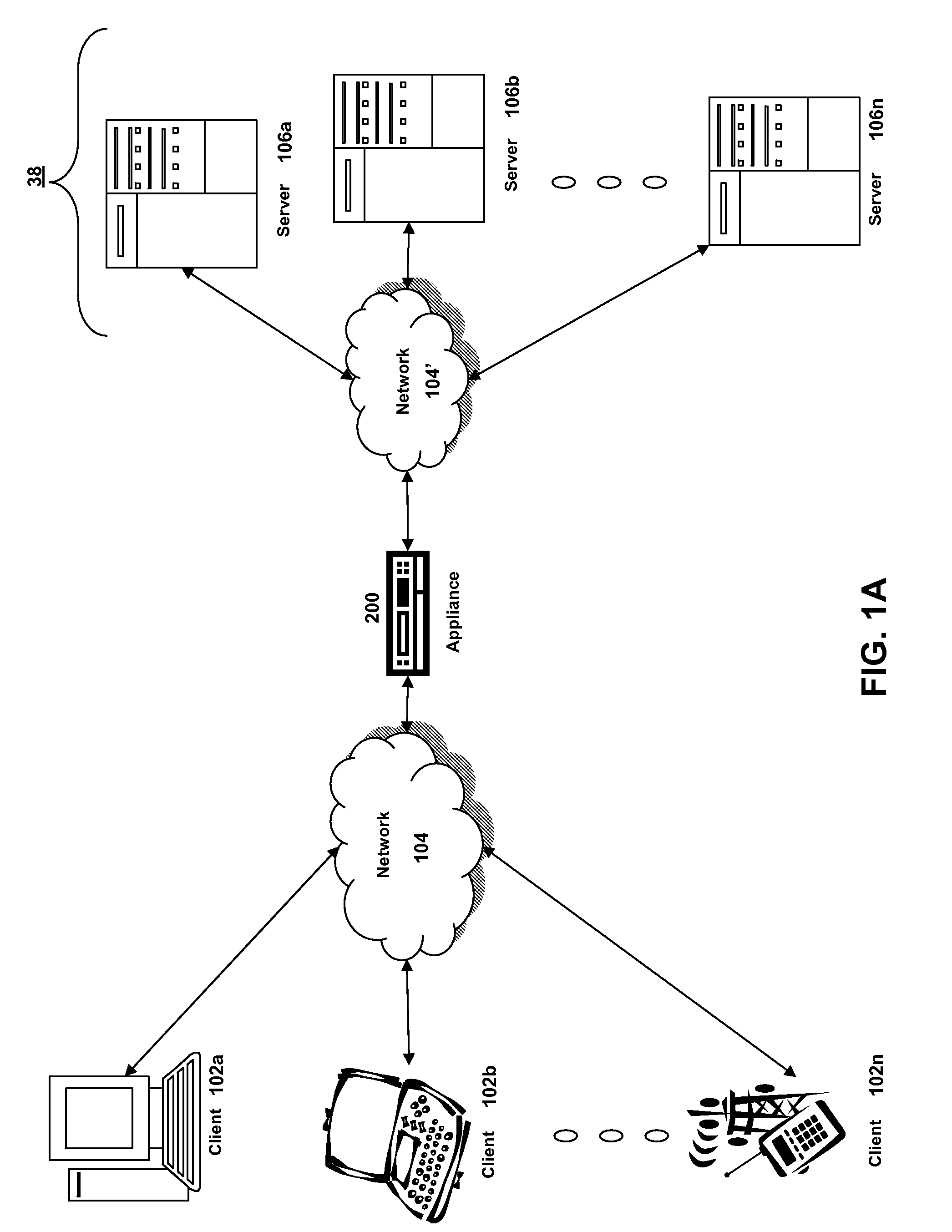
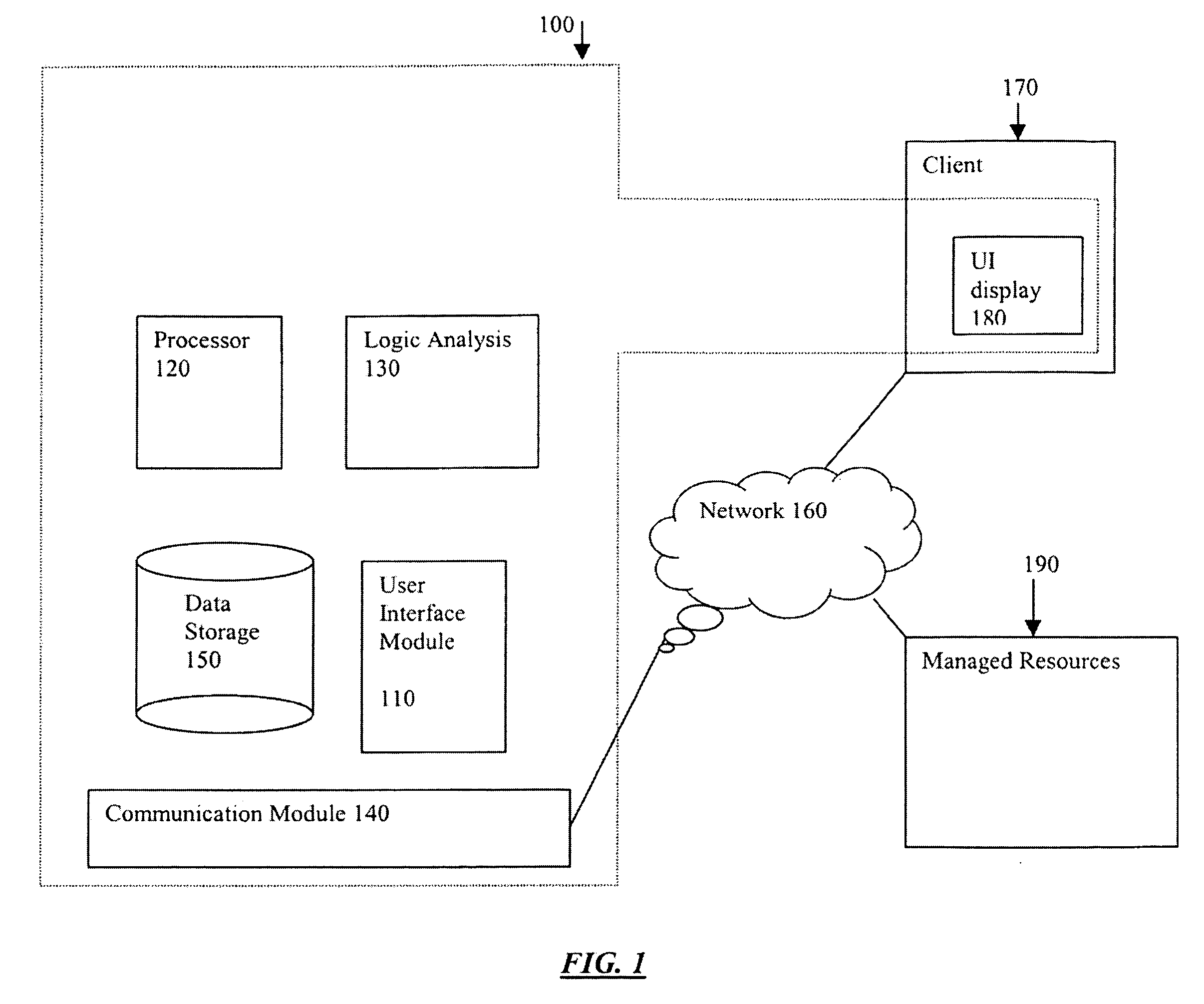
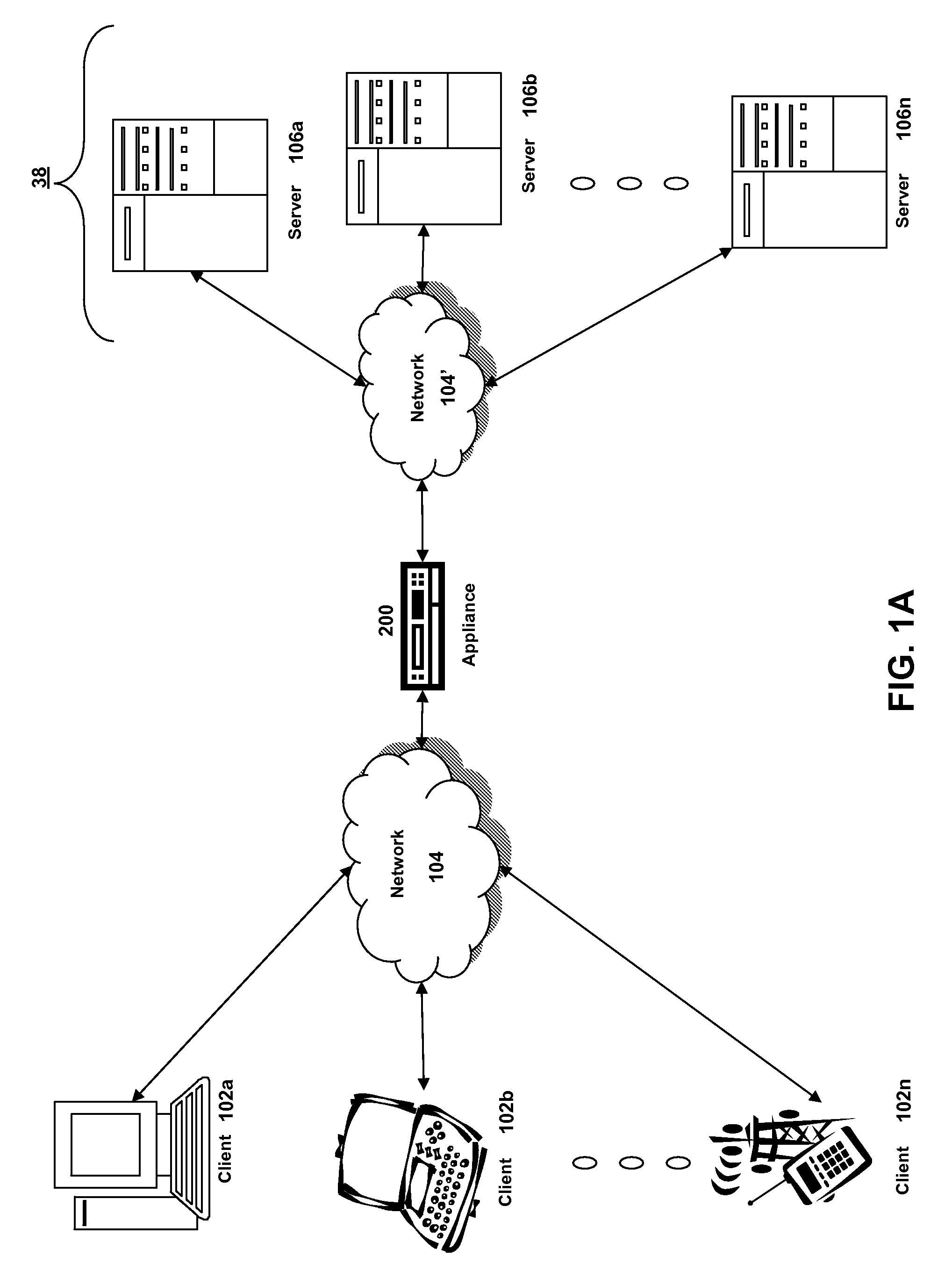
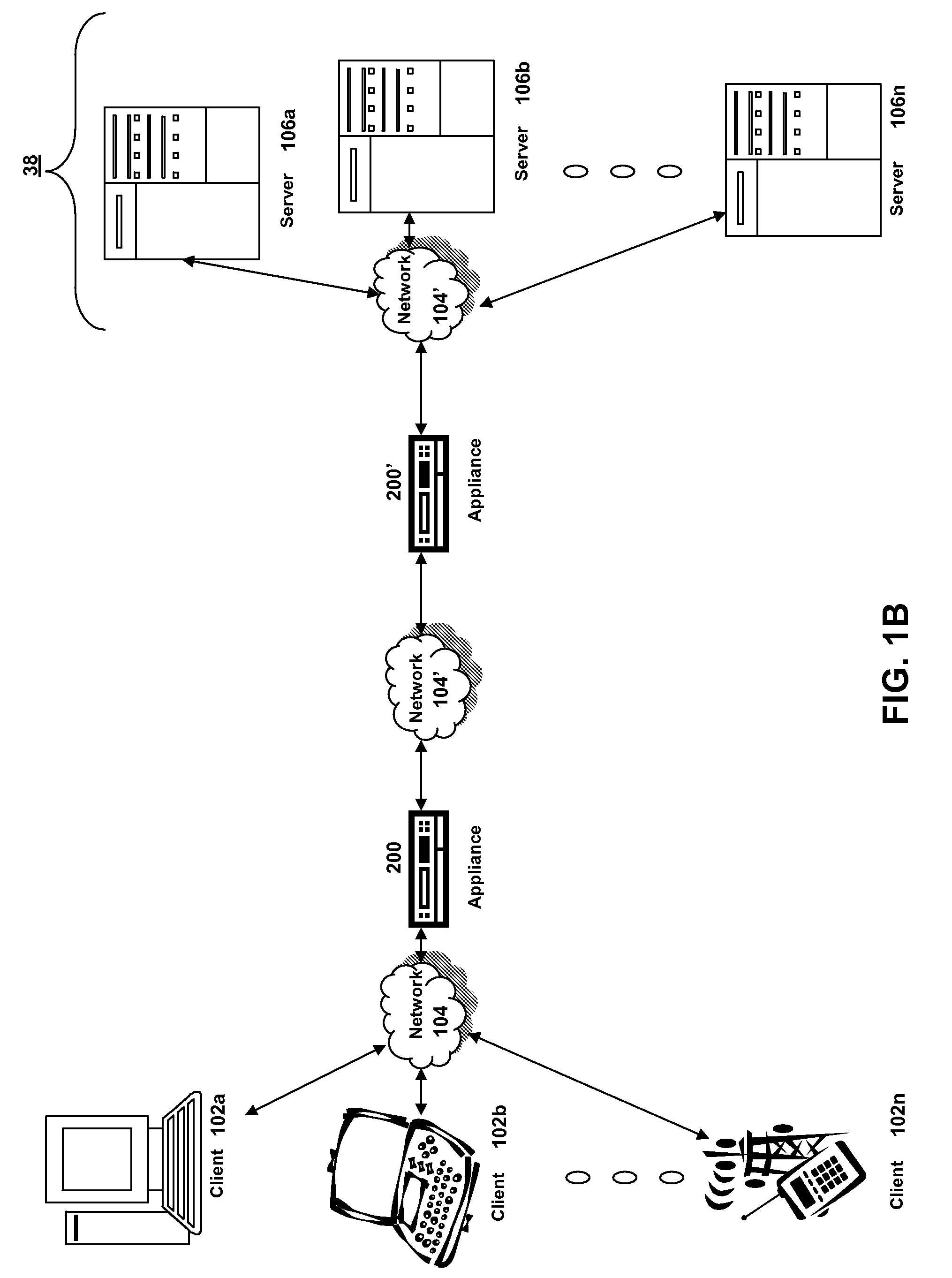
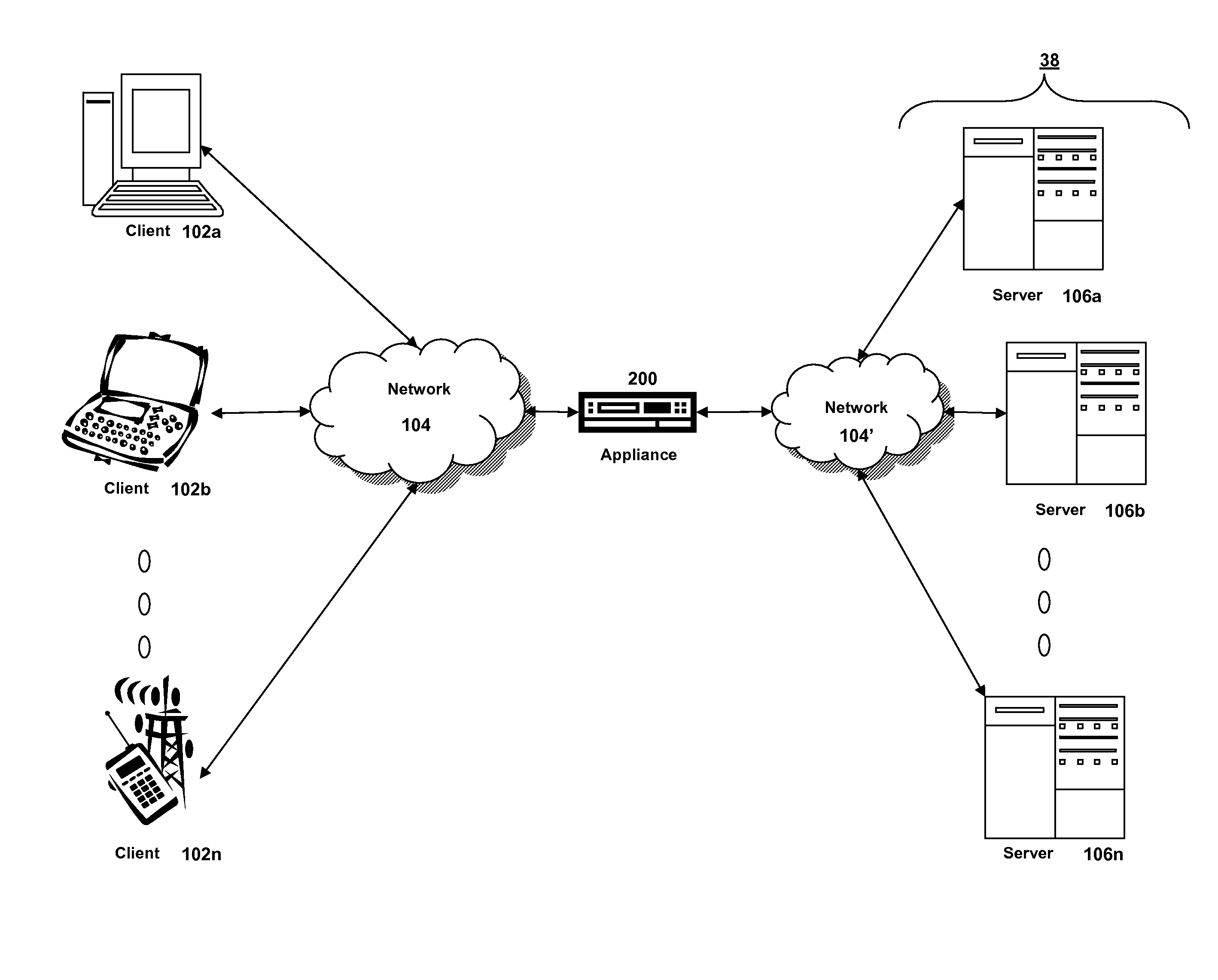
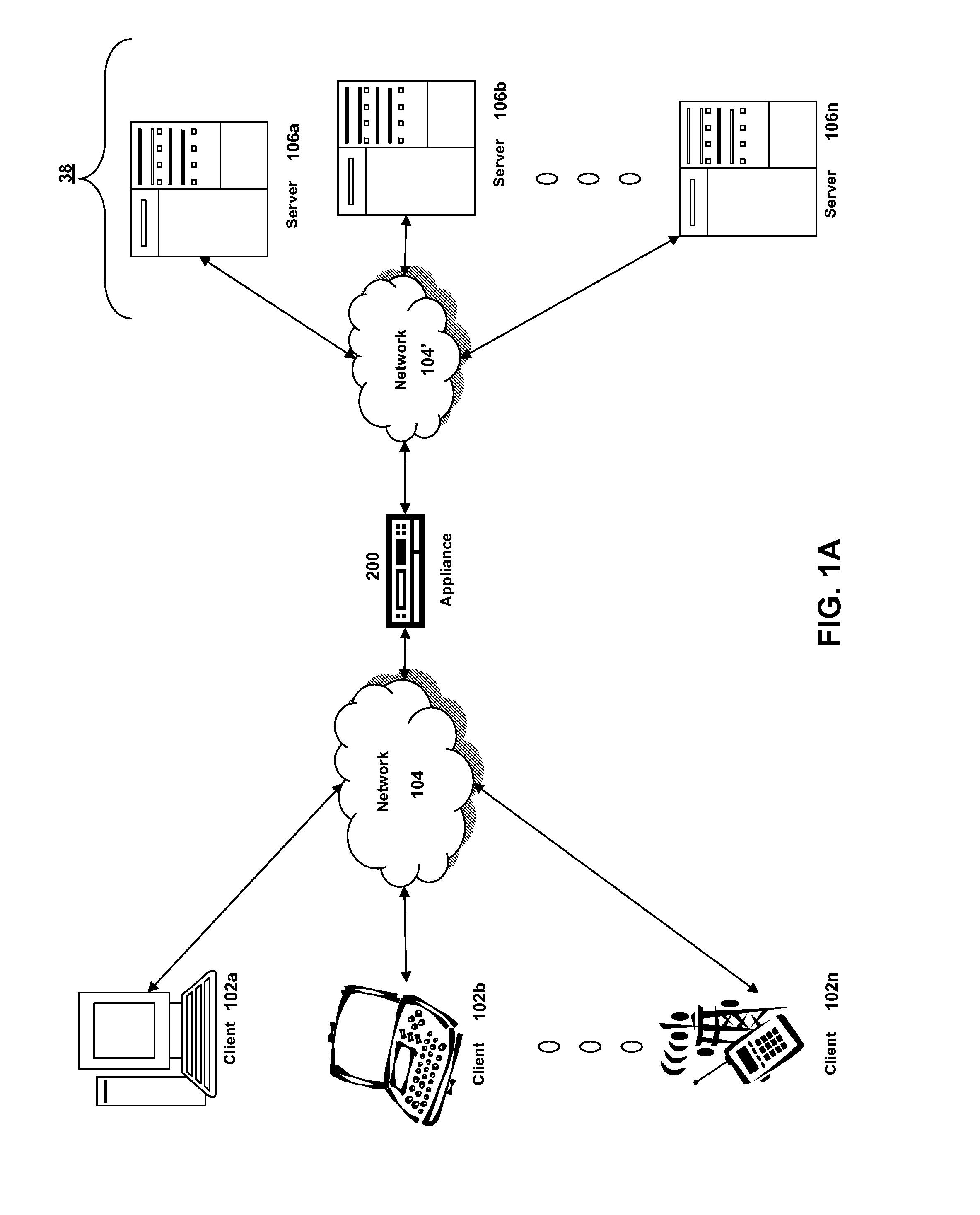
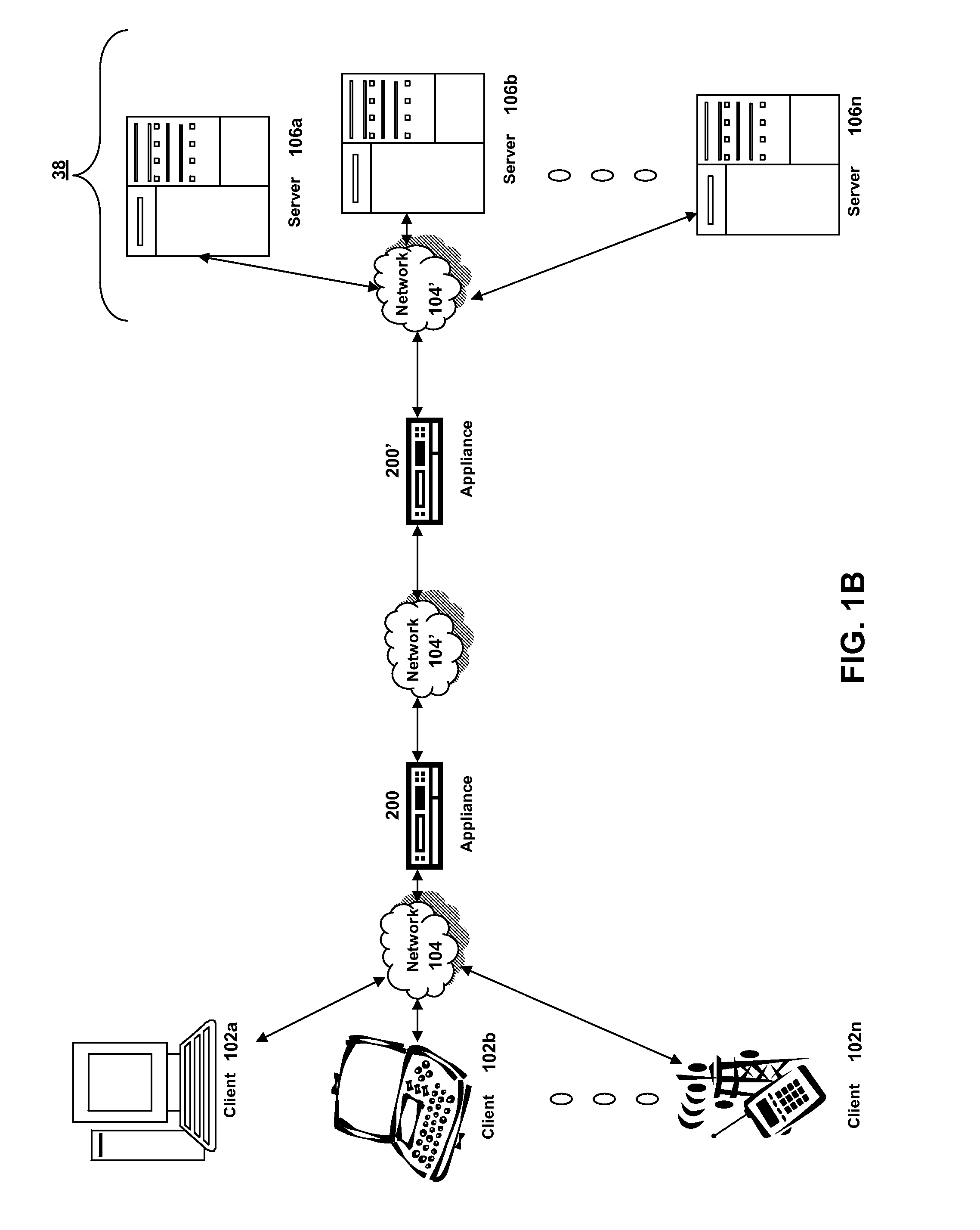
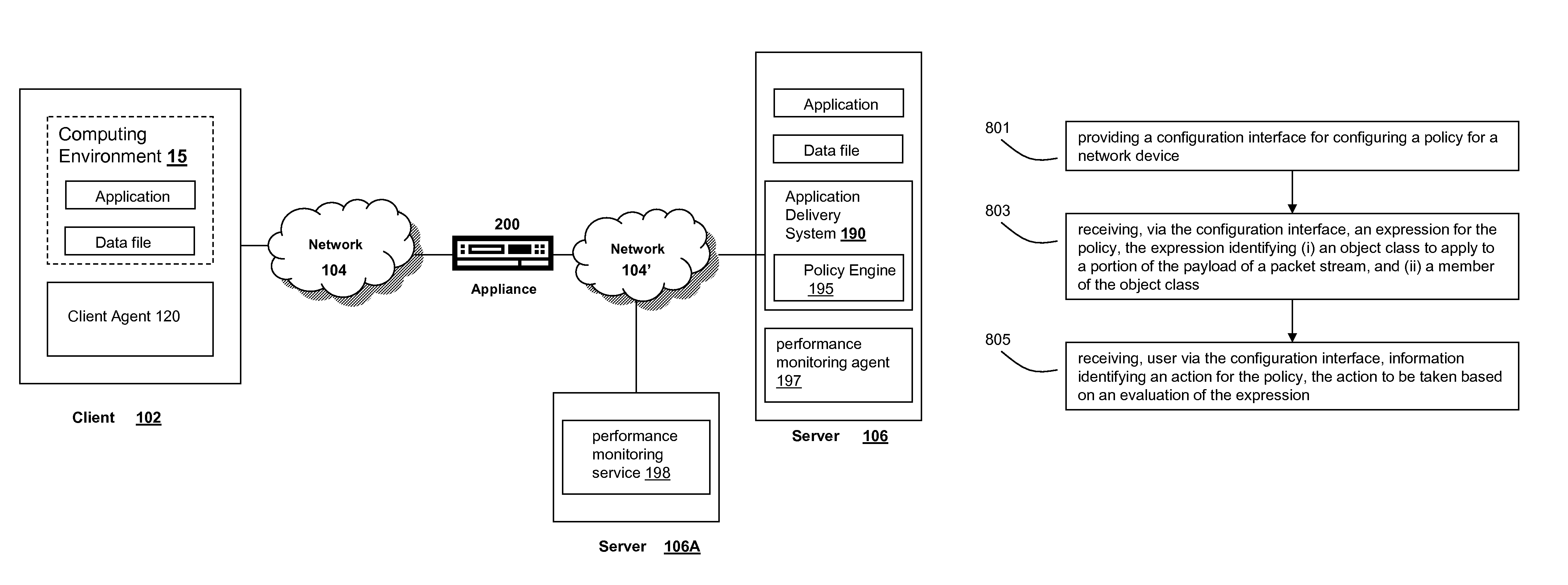
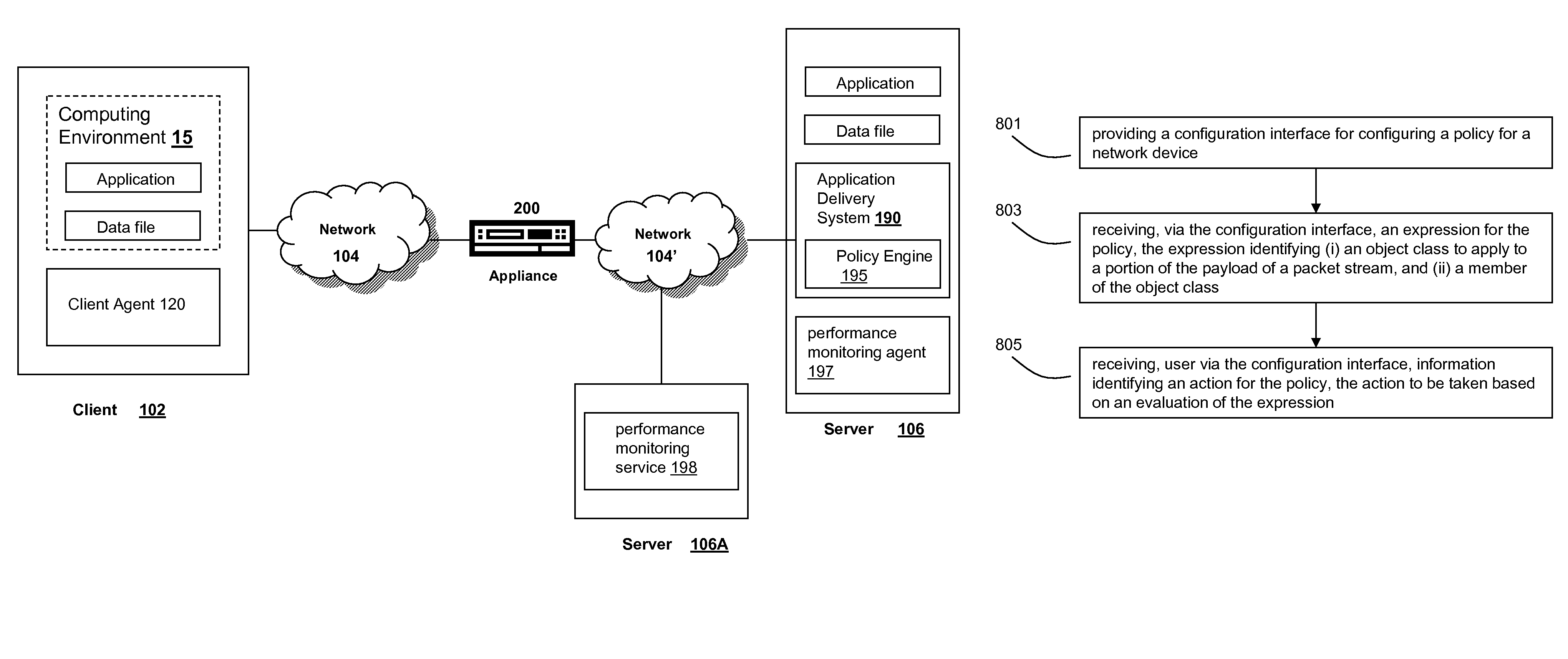
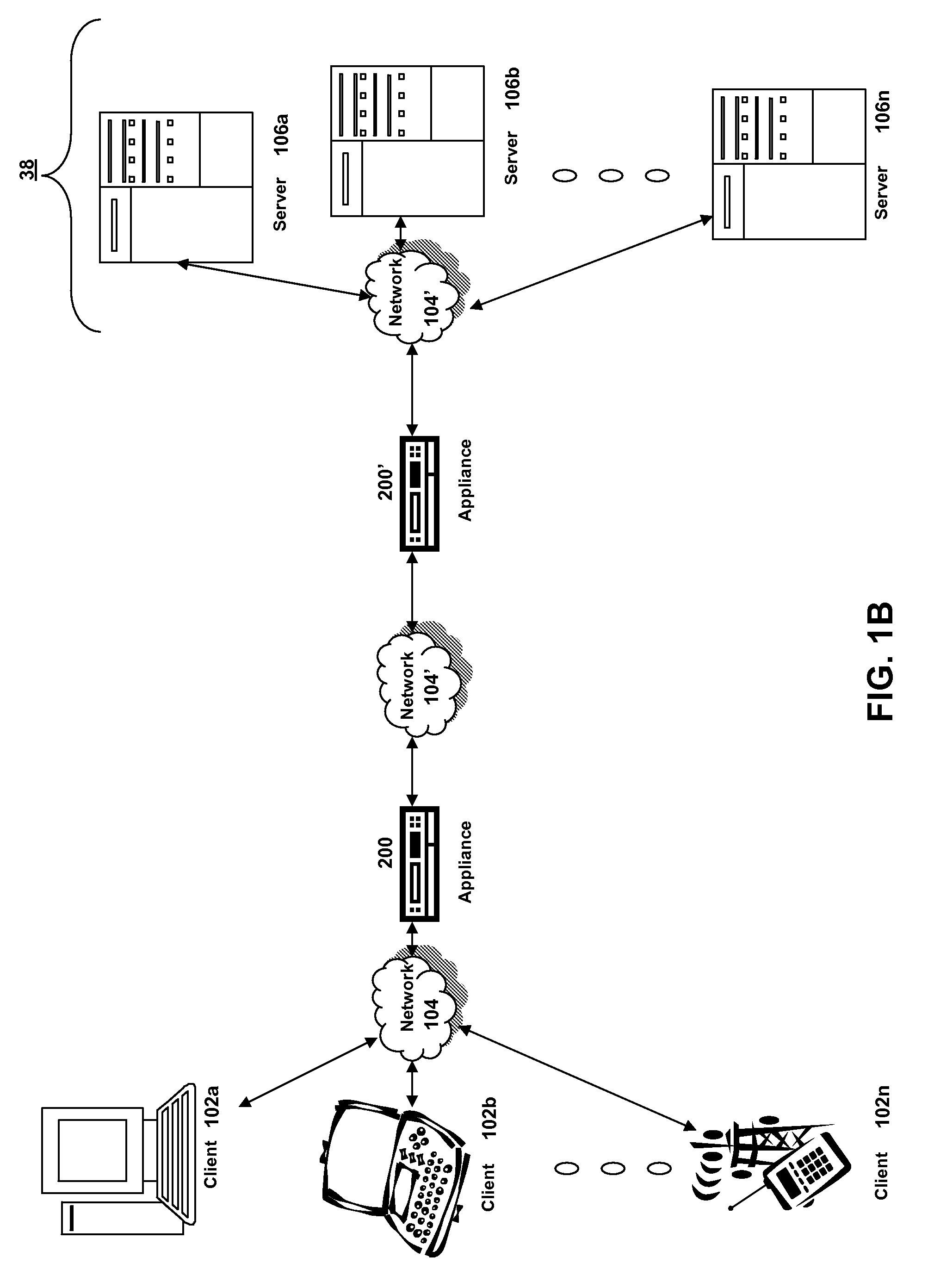
Systems and methods for providing stuctured policy expressions to represent unstructured data in a network appliance
ActiveUS20080225748A1Efficient configurationEfficient processingData switching by path configurationTraffic capacityData stream
Owner:CITRIX SYST INC
Systems and methods for configuring policy bank invocations
ActiveUS20100095018A1Efficient configurationEfficient processingError preventionTransmission systemsTraffic capacityData stream
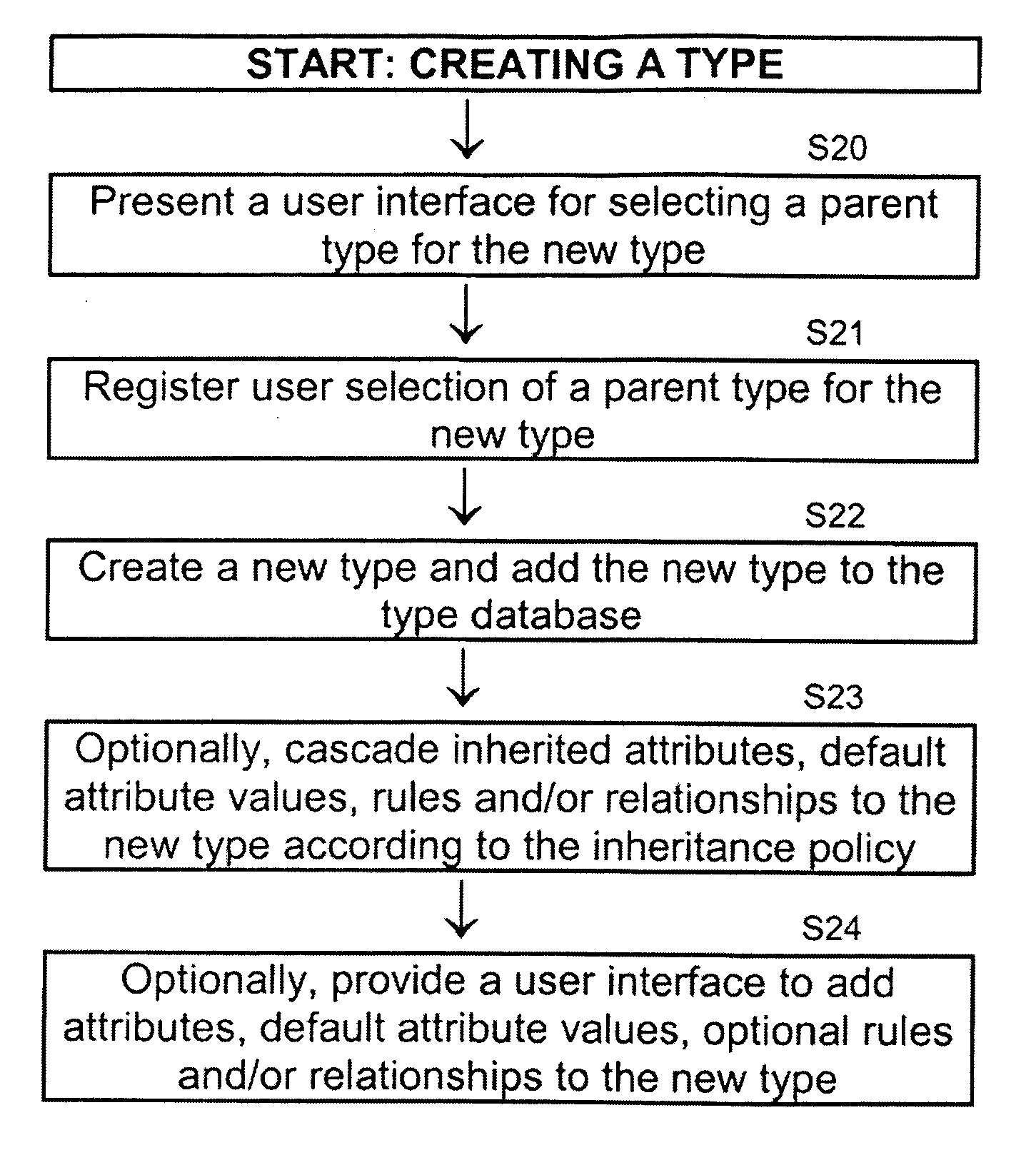
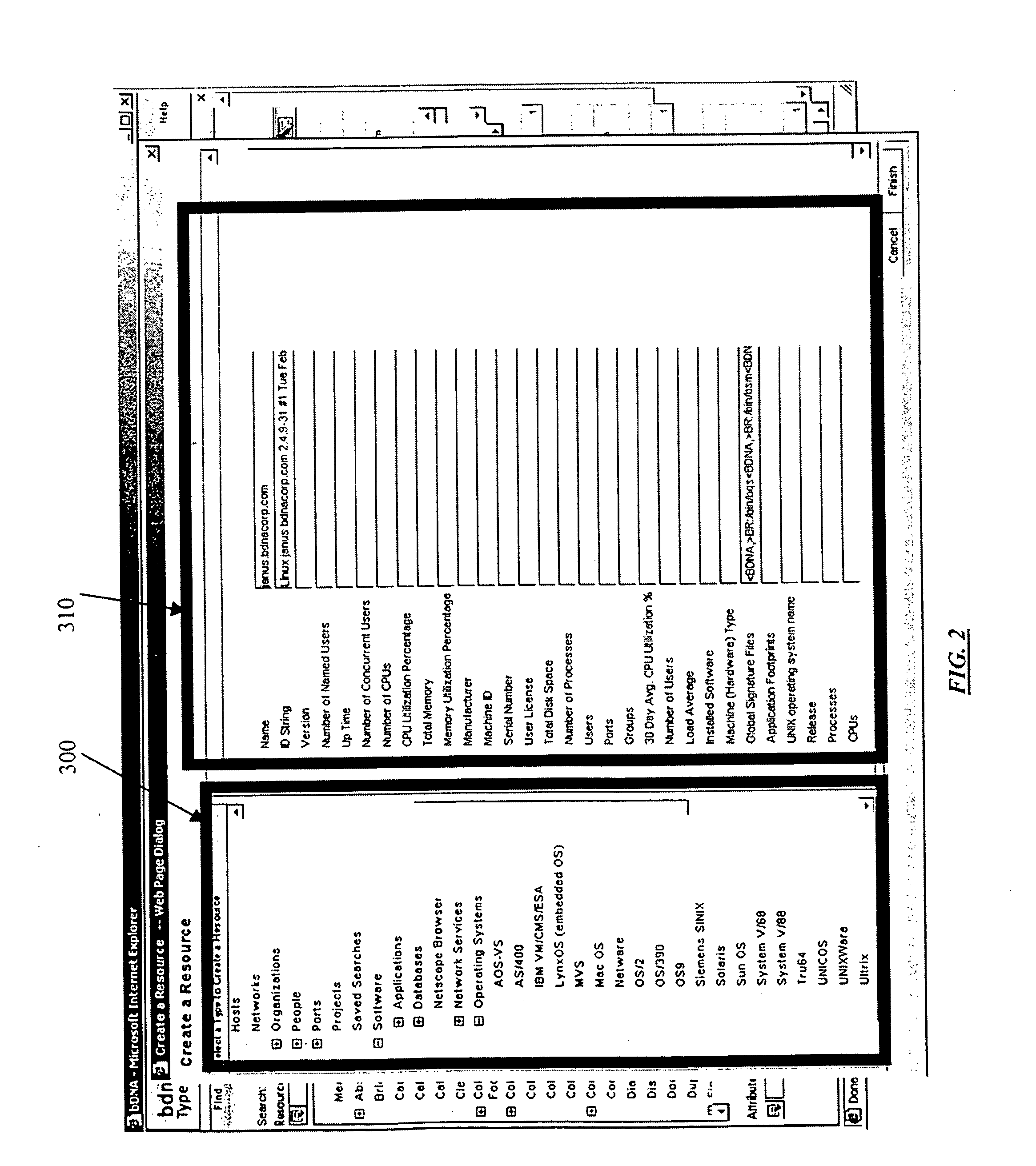
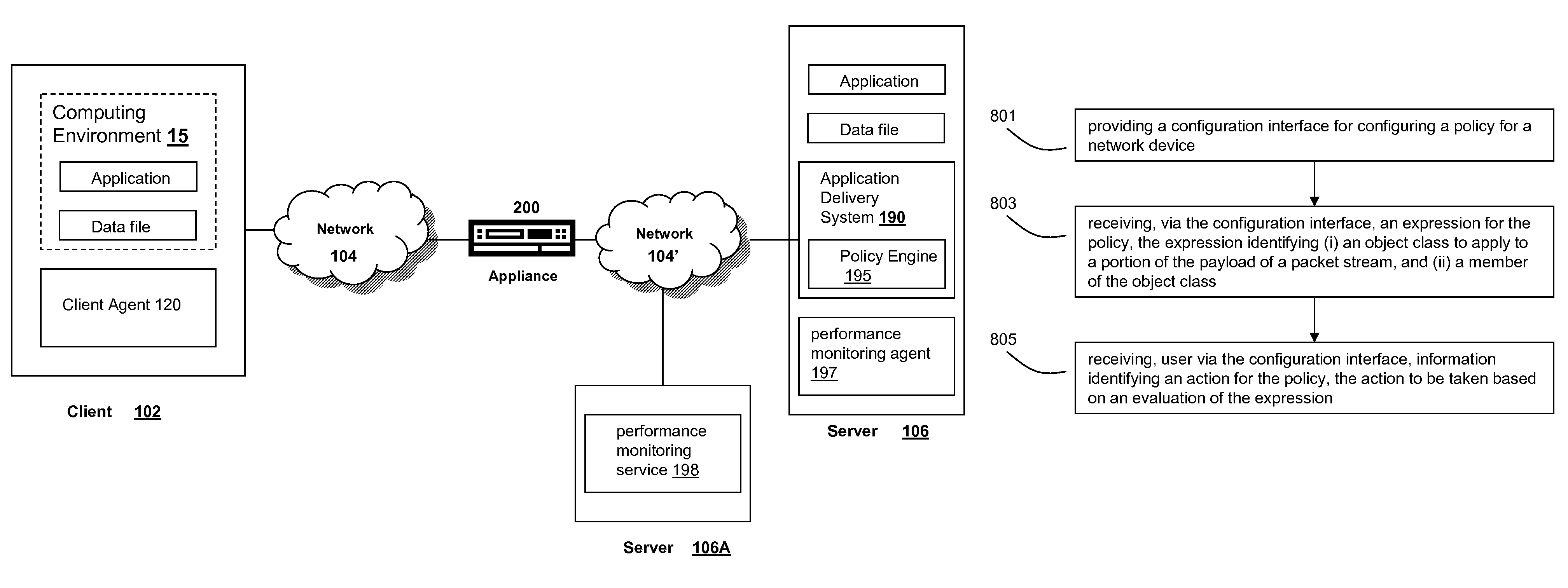
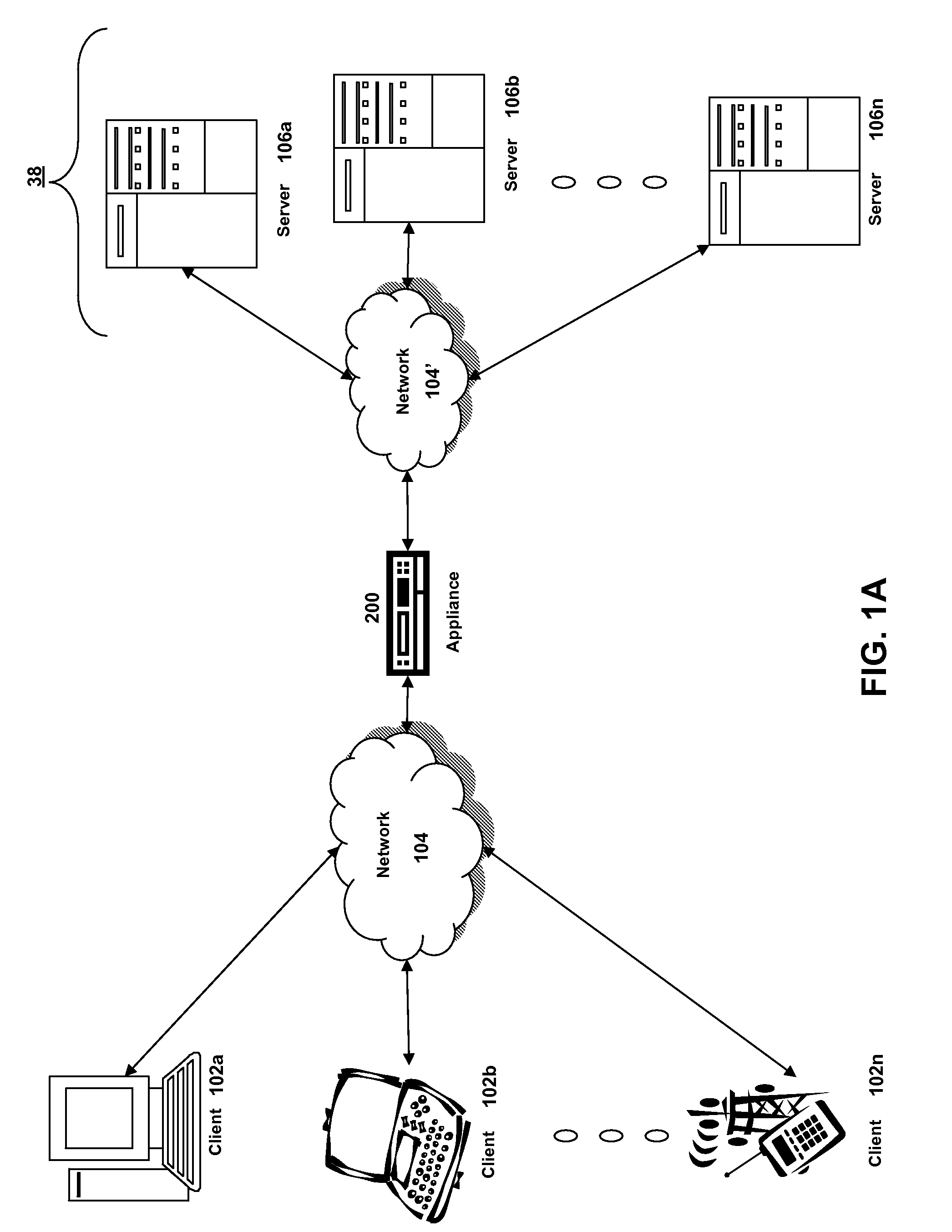
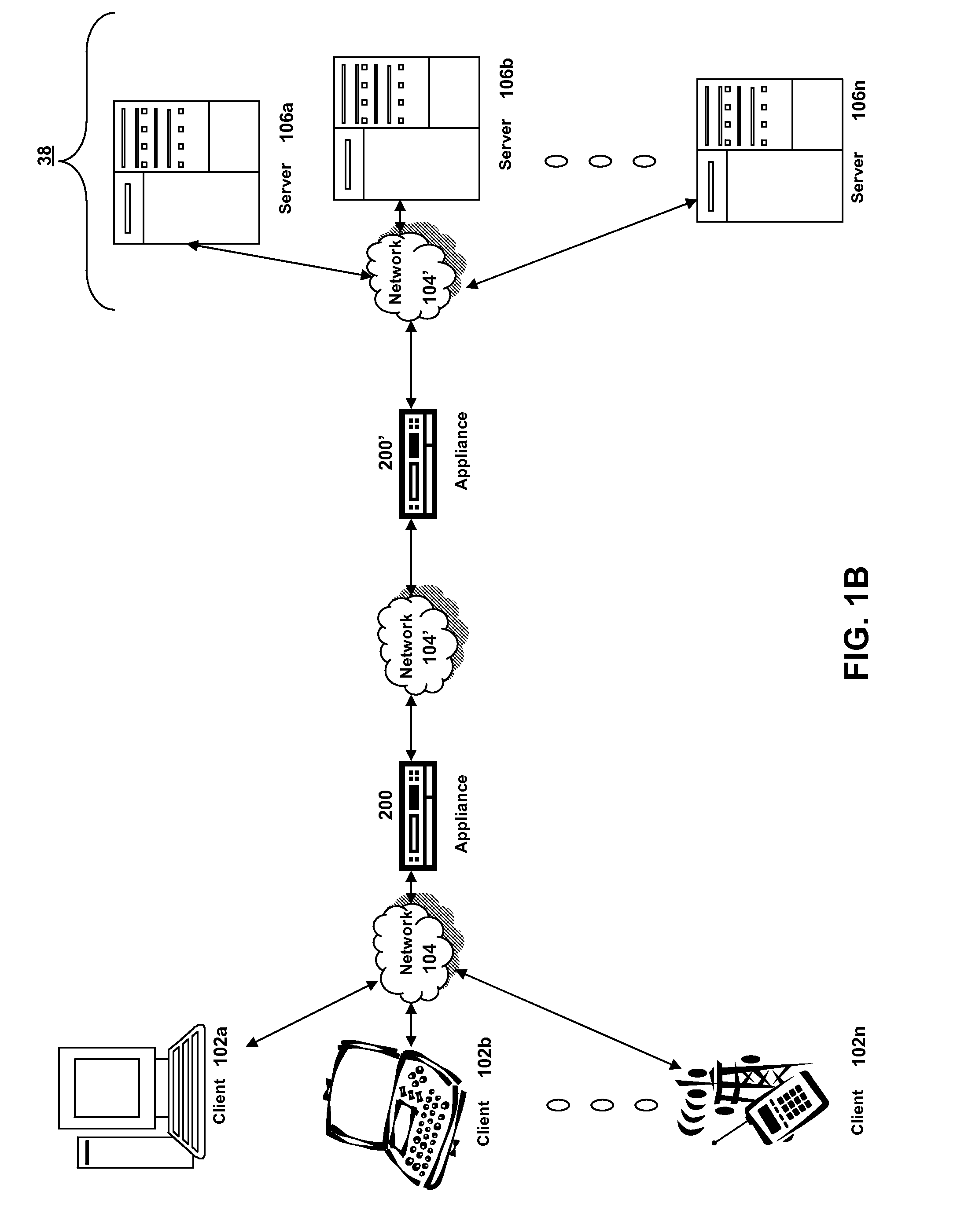
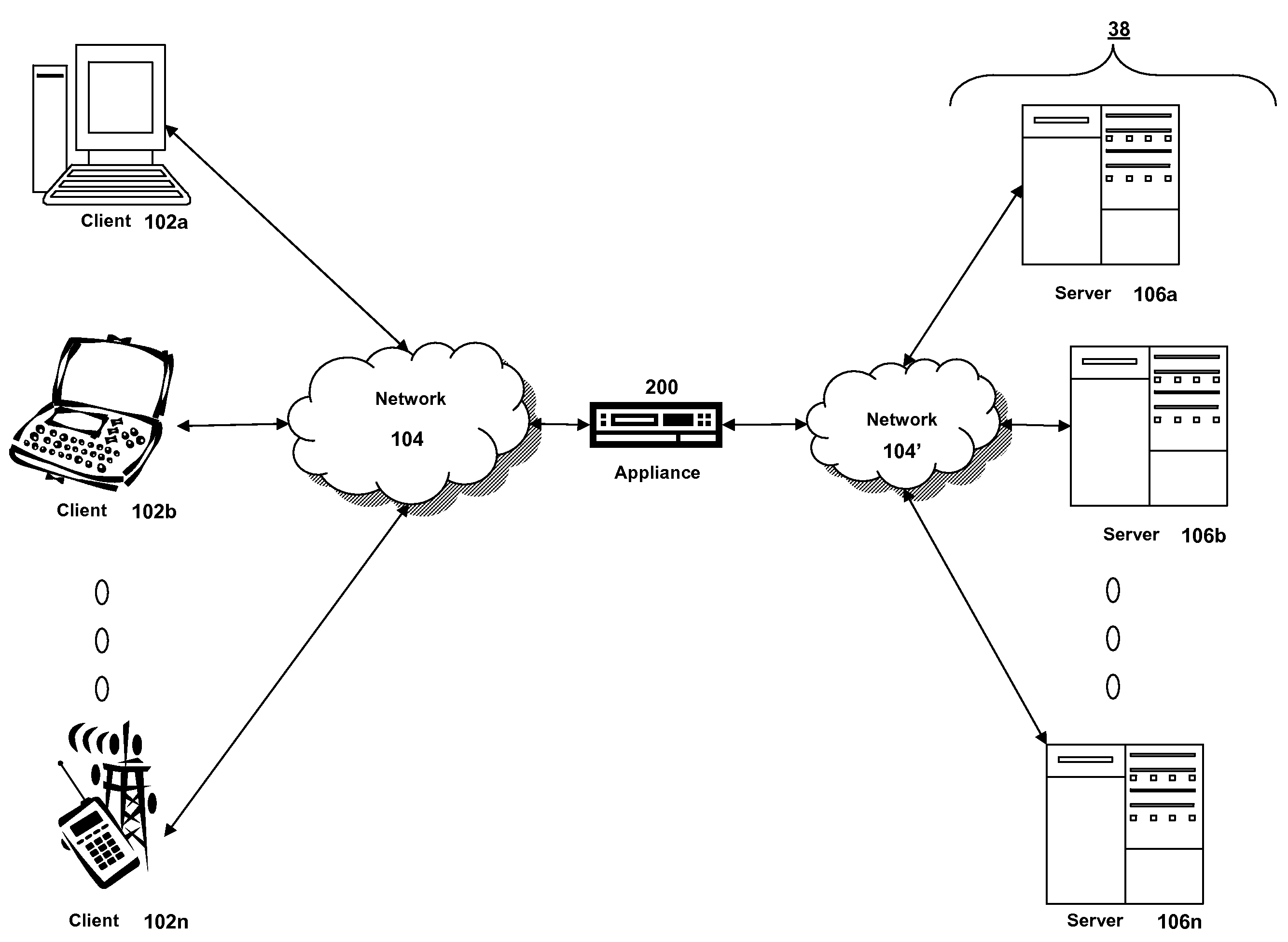
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Systems and methods for managing application security profiles
ActiveUS20080229381A1Efficient configurationEfficient processingMemory loss protectionError detection/correctionTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
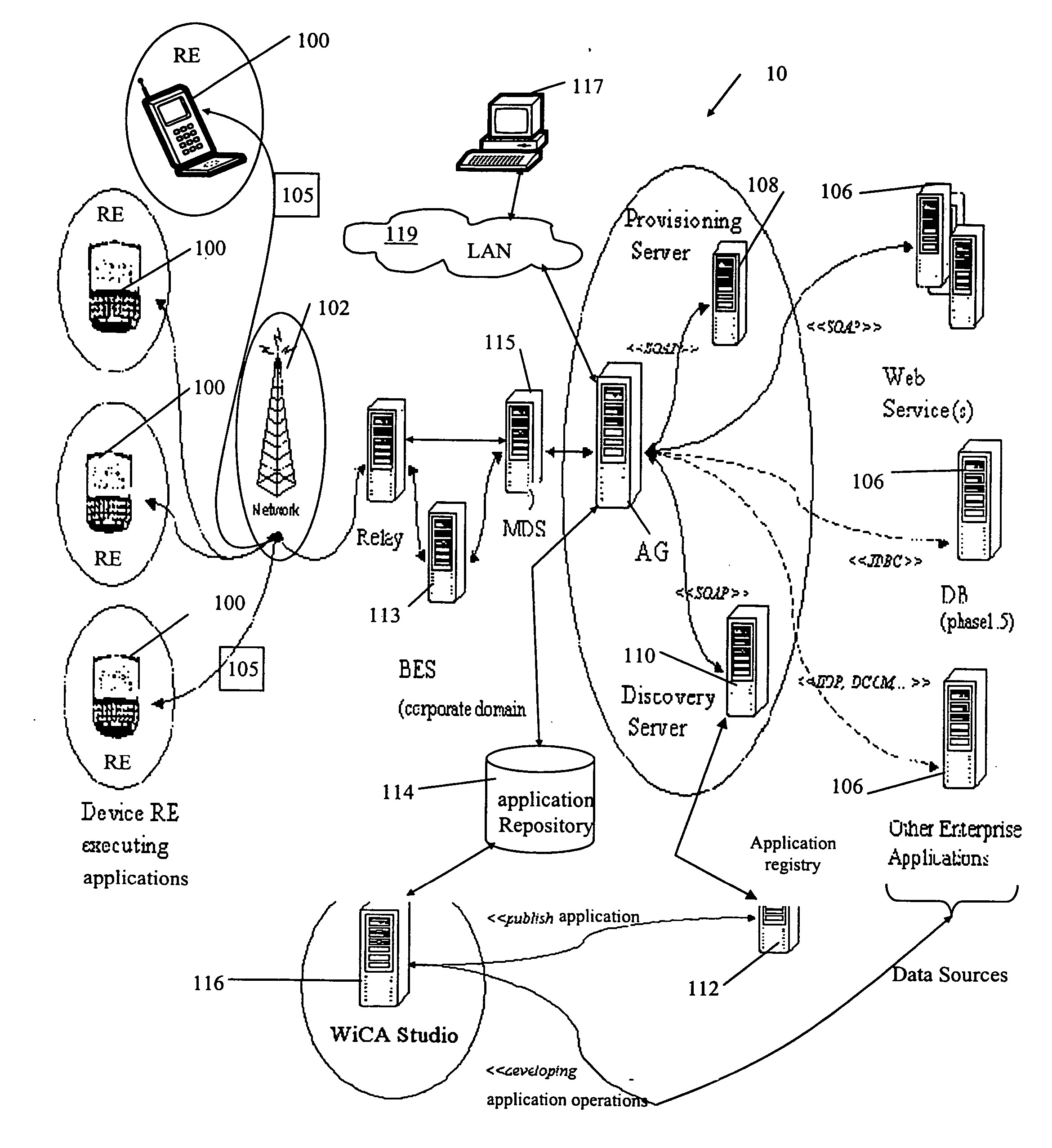
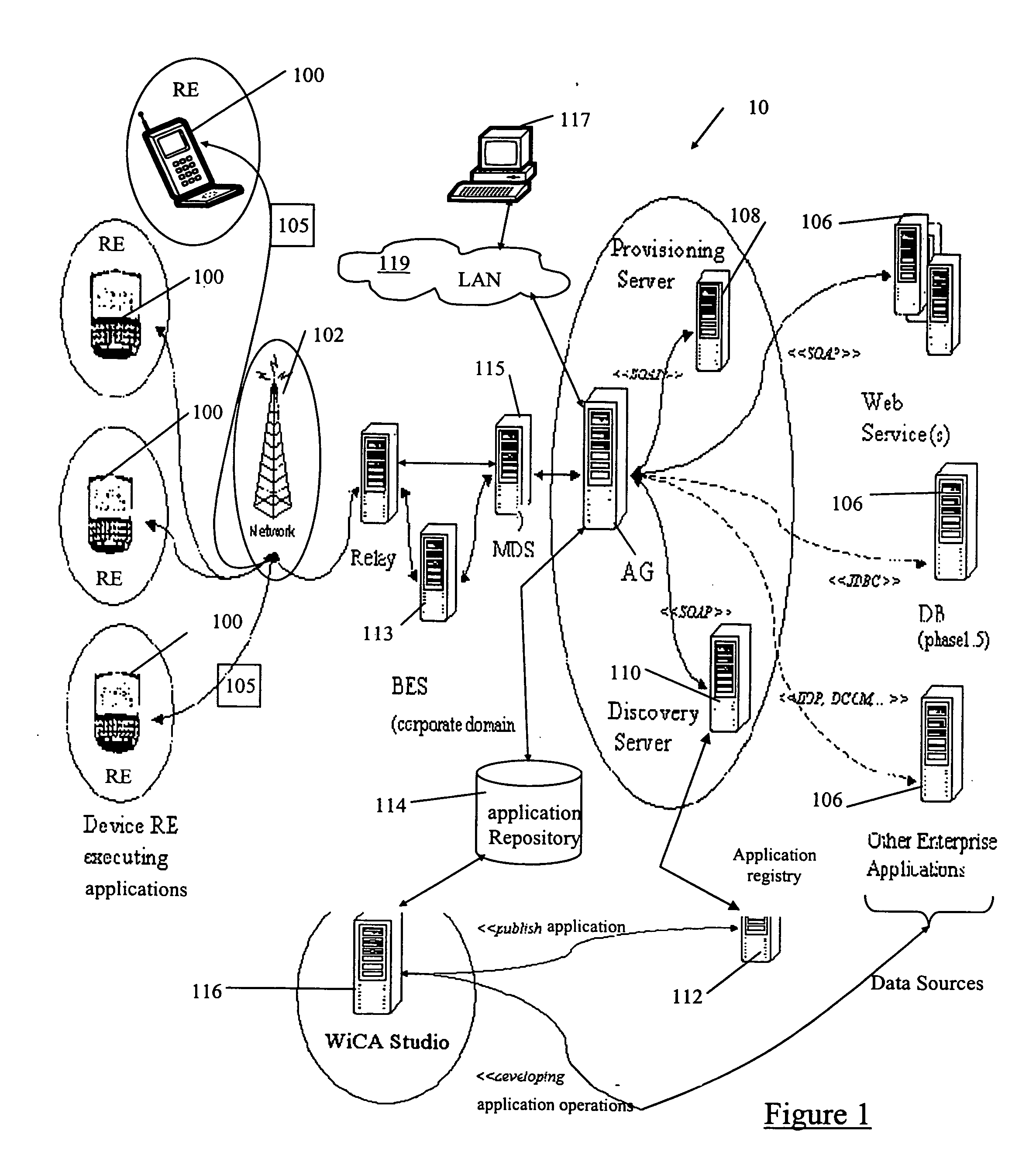
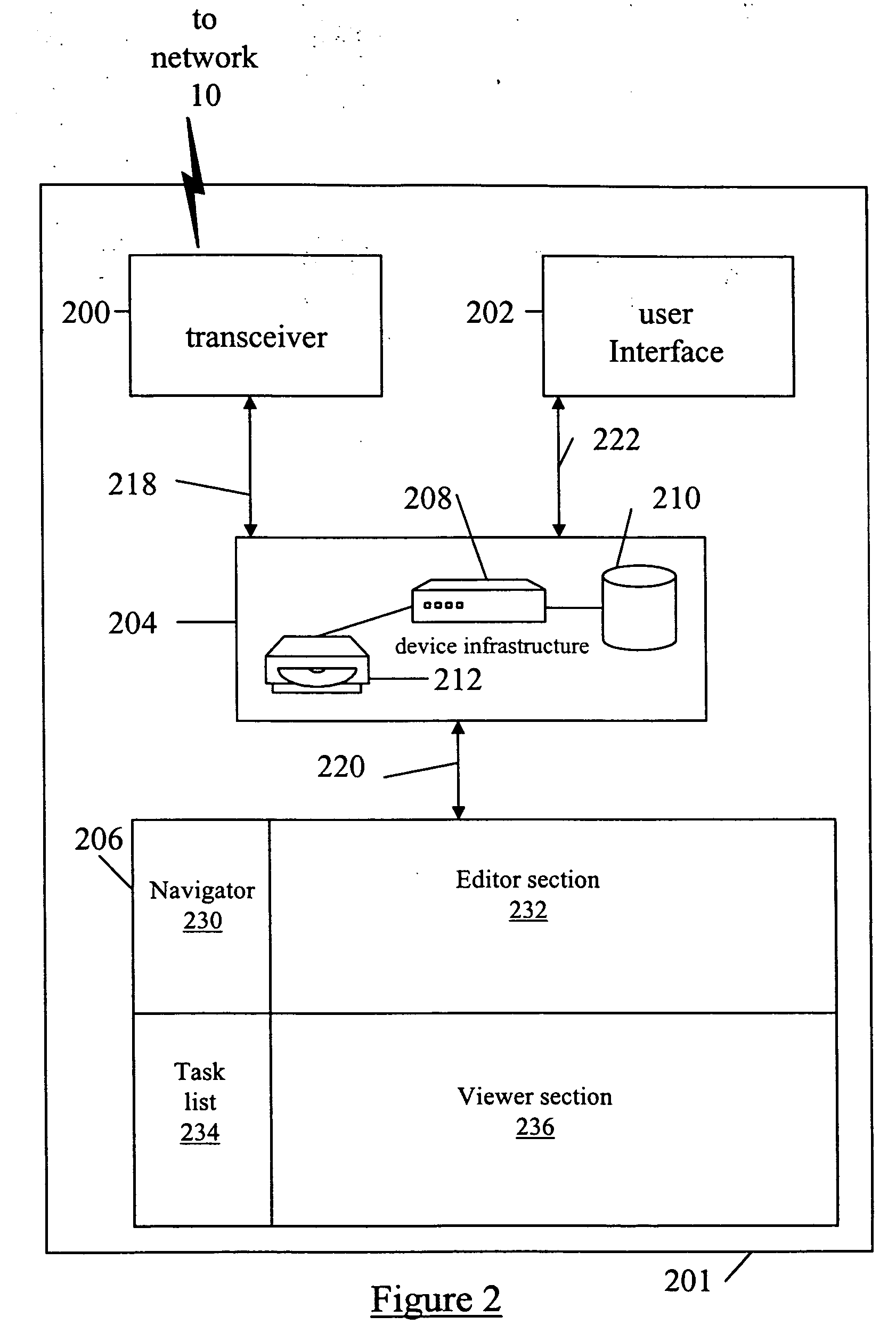
System and method for automated building of component based applications for visualizing complex data structures
InactiveUS20060236254A1Promote generationSmall sizeReverse engineeringProgram controlGraphicsGraphical user interface
A system and method for generating a screen component configured to visualize a data structure in a displayed screen on a graphical user interface of a device. The screen component for including in an application for execution on the device and having definitions expressed in a structured definition language for defining the visualization of the data structure. The visualized data structure related to data content associated with messages communicated over a network between the device and a data source. The system and method comprises: a parser module for analyzing a set of predefined message and data definitions expressed in a structured definition language to identify corresponding data structure and message details related to the messages, the predefined message and data definitions for including in the application; a screen template for providing a representative example of the screen to be displayed on the graphical user interface; and a screen component generation module for applying the predefined message and data details to the screen template to generate the screen component; wherein the predefined message and data definitions and the screen component are subsequently assembled in to the application.
Owner:BLACKBERRY LTD
Systems and methods for configuring handling of undefined policy events
ActiveUS20080225753A1Efficient configurationEfficient processingDigital computer detailsData switching by path configurationTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Systems and methods for configuring flow control of policy expressions
ActiveUS20080225720A1Efficient configurationEfficient processingError preventionTransmission systemsTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
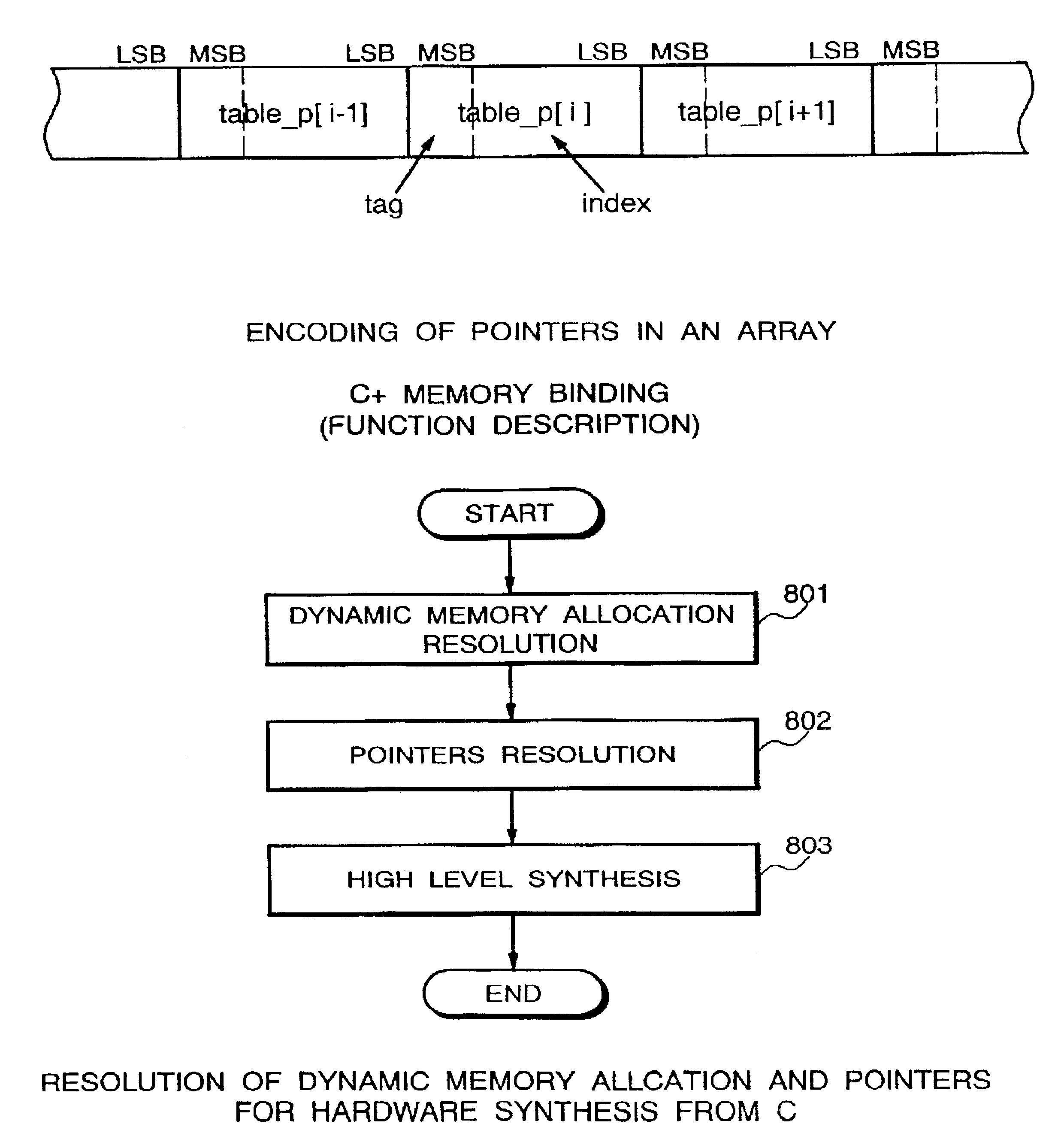
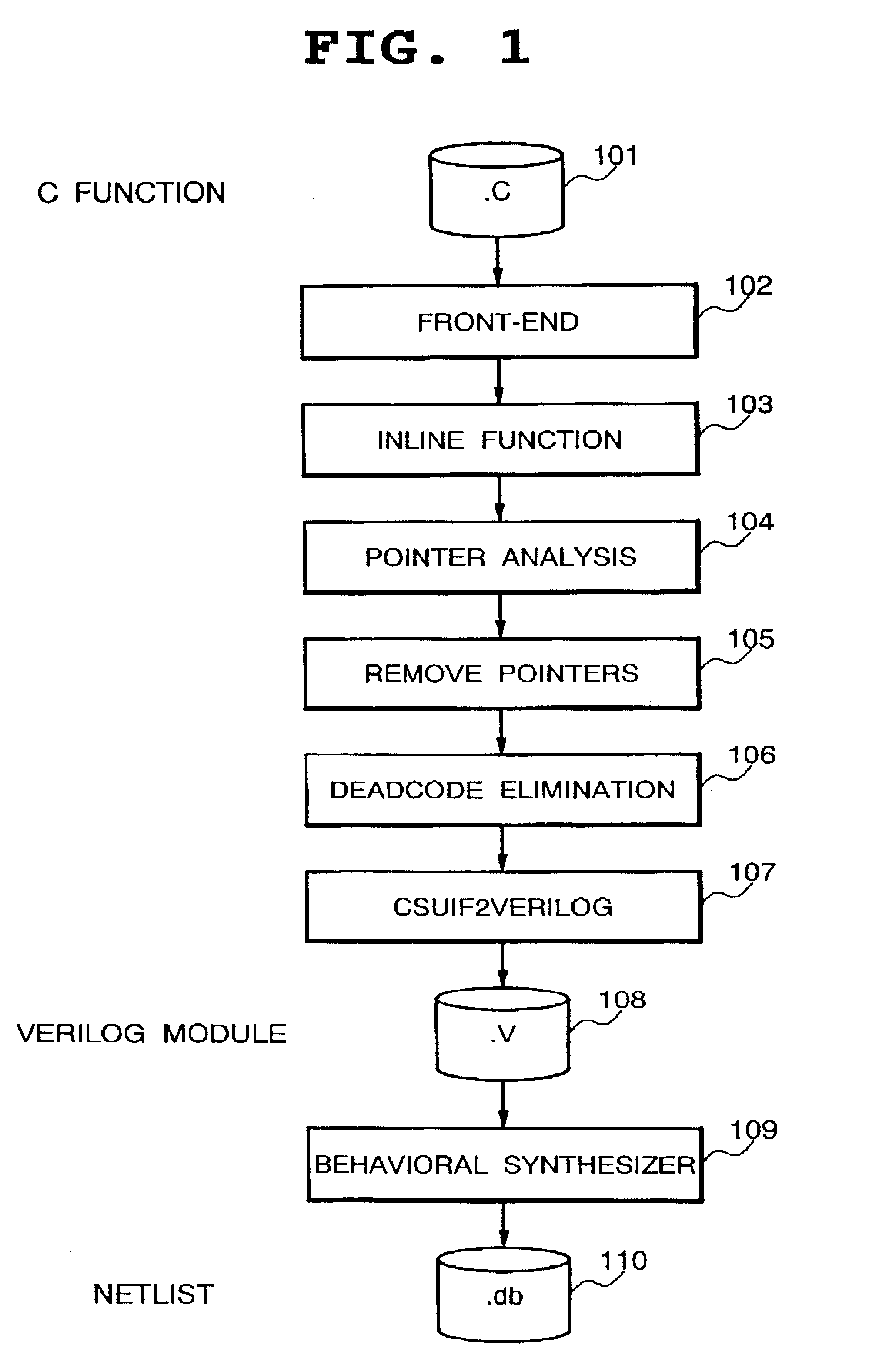
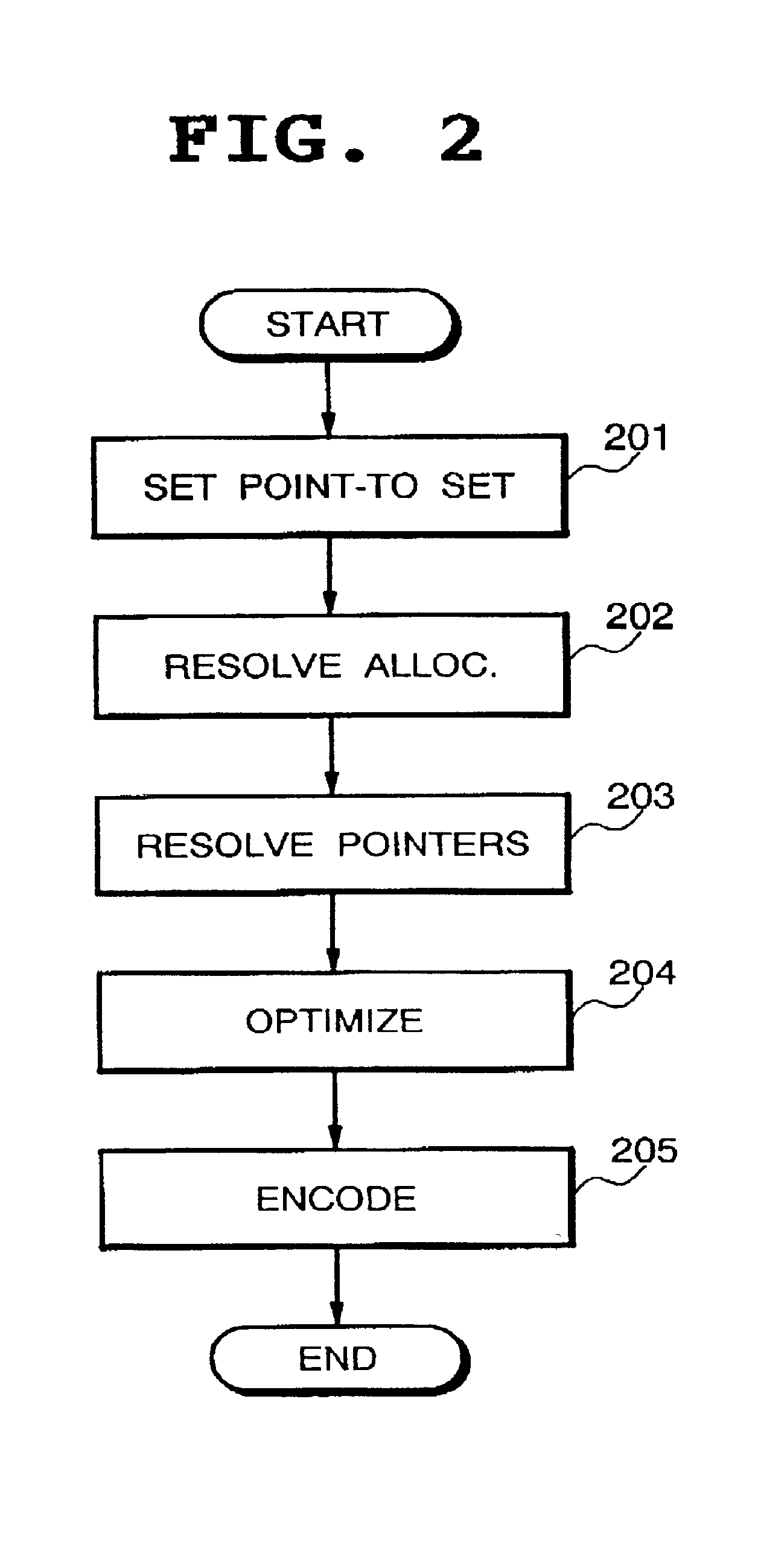
Resolution of dynamic memory allocation/deallocation and pointers
InactiveUS6467075B1CAD circuit designSoftware simulation/interpretation/emulationSoftware systemTheoretical computer science
One of the greatest challenges in C / C++-based design methodology is to efficiently map C / C++ models into hardware. Many of the networking and multimedia applications implemented in hardware or mixed hardware / software systems are making use of complex data structures stored in one or multiple memories. As a result, many of the C / C++ features which were originally designed for software applications are now making their way into hardware. Such features include dynamic memory allocation / deallocation and pointers used to manage data. This inventors present a solution for efficiently mapping arbitrary C code with pointers and malloc / free into hardware. This solution fits current memory management methodologies. It consists of instantiating a hardware allocator tailored to an application and a memory architecture. This work also supports the resolution of pointers without restriction on the data structures. An implementation using the SUIF framework is presented, followed by some case studies such as the realization of a video filter.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV +1
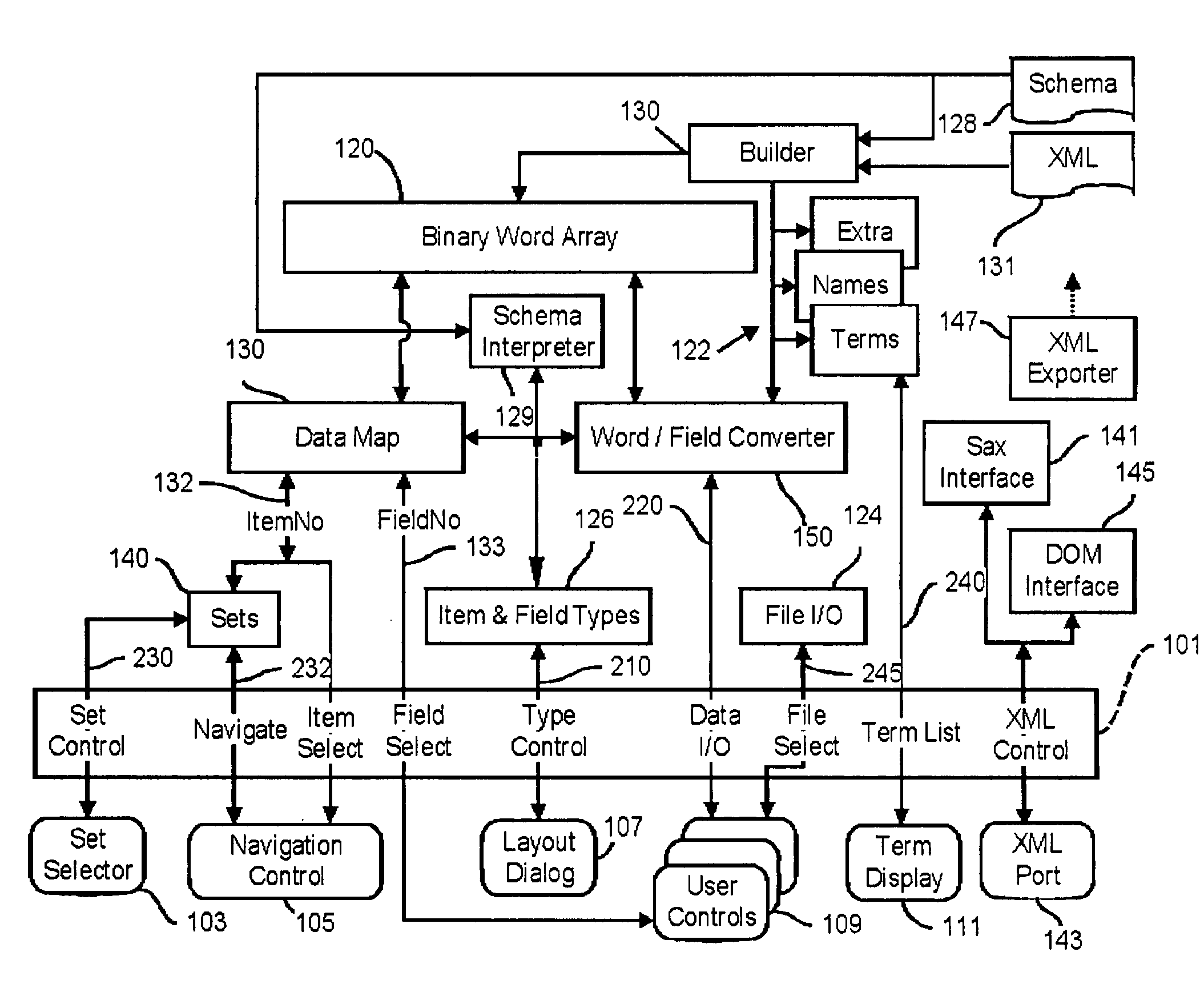
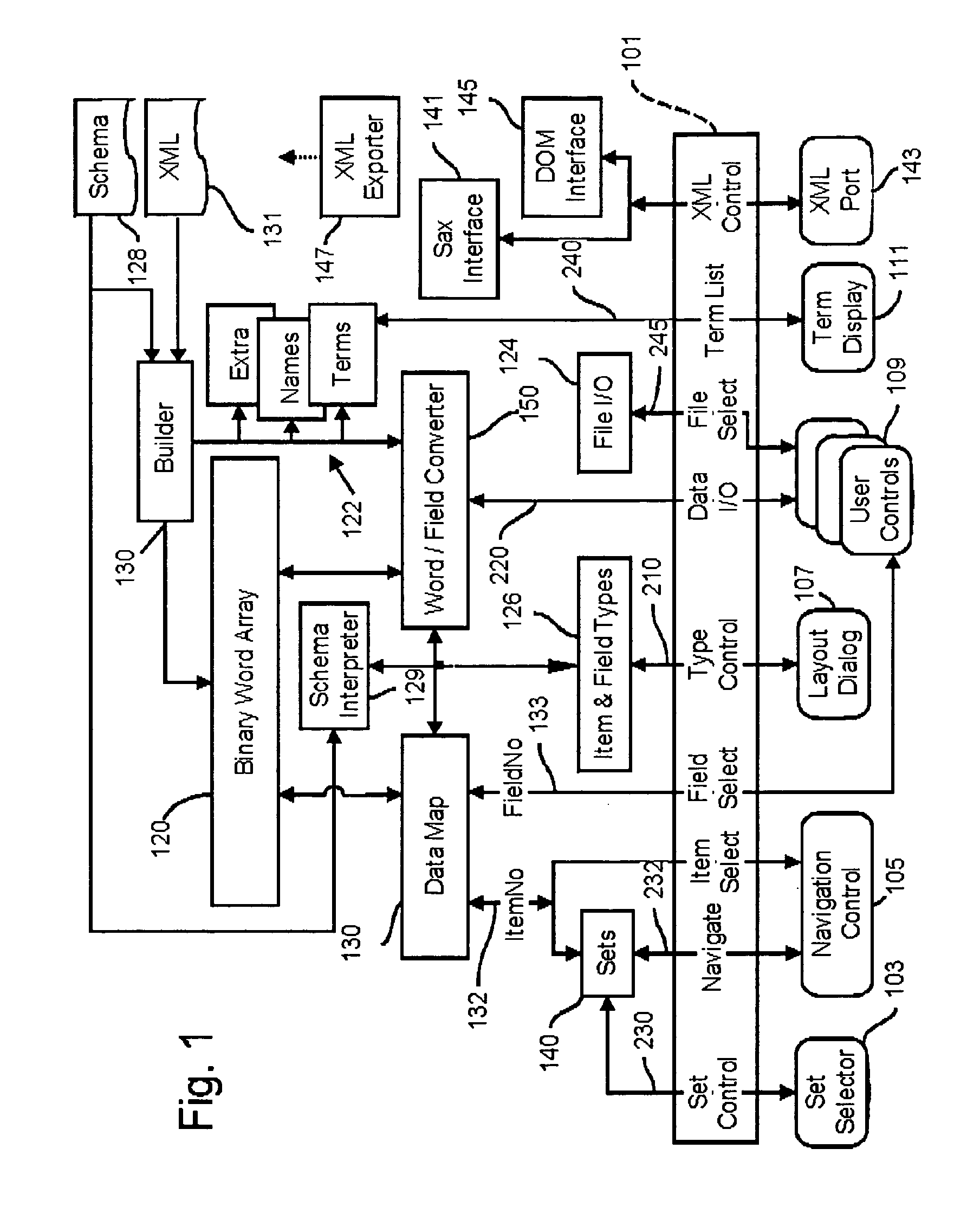
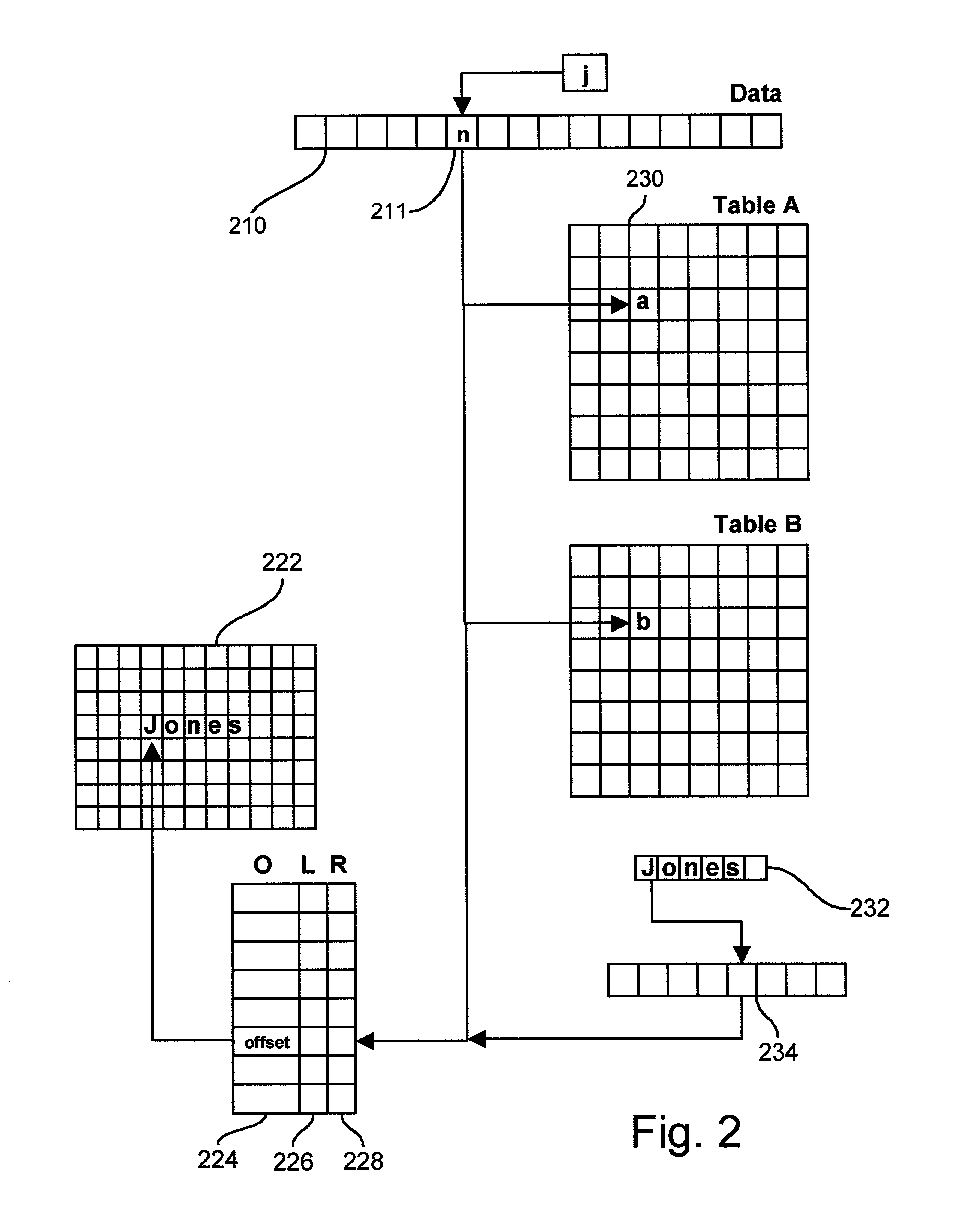
Methods and apparatus for storing and manipulating variable length and fixed length data elements as a sequence of fixed length integers
InactiveUS7178100B2Less transmission bandwidthEasy to handleData processing applicationsNatural language data processingArray data structureTheoretical computer science
Apparatus for storing and processing a plurality of data items each comprising supplied data values organized in one or more fields each of which stores typed data. Character strings and natural language text are converted to numerical token values in an array of fixed length integers and other forms of typed data (real numbers, dates, times, boolean values, etc.) are also converted to integer form and stored in the array. Stored metadata specifies the data type of all data in the integer array to enable each integer to be rapidly accessed and interpreted. When fixed length data types are present, the metadata specifies location, size and type of each fixed length element. When variable length data is stored in the integer array, size and location data stored in the integer array is accessed to rapidly and directly access the variable size data. The presence of implicit or explicit size information for each data structure, including variable size structures, speeds processing by eliminating the need to scan the data for delimiters, and by reducing the processing needed to perform memory allocation, data movement, lookup operations and data addressing functions. Data stored in the integer array is subdivided into items, and items are subdivided into fields. Items may be organized into more complex data structures, such as relational tables, hierarchical object structures, linked lists and trees, and the like, using special fields called links which identify other referenced items.
Owner:CALL CHARLES G
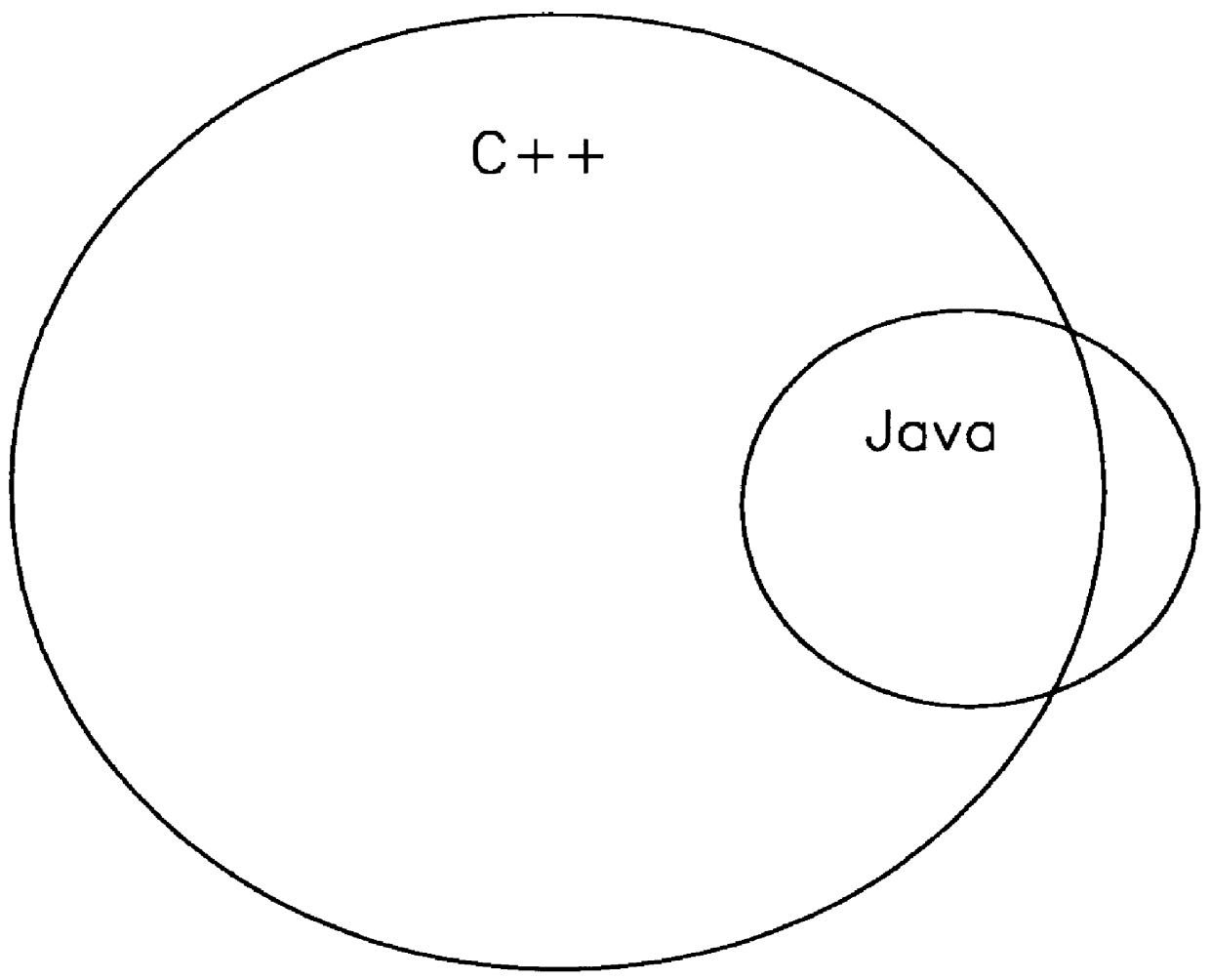
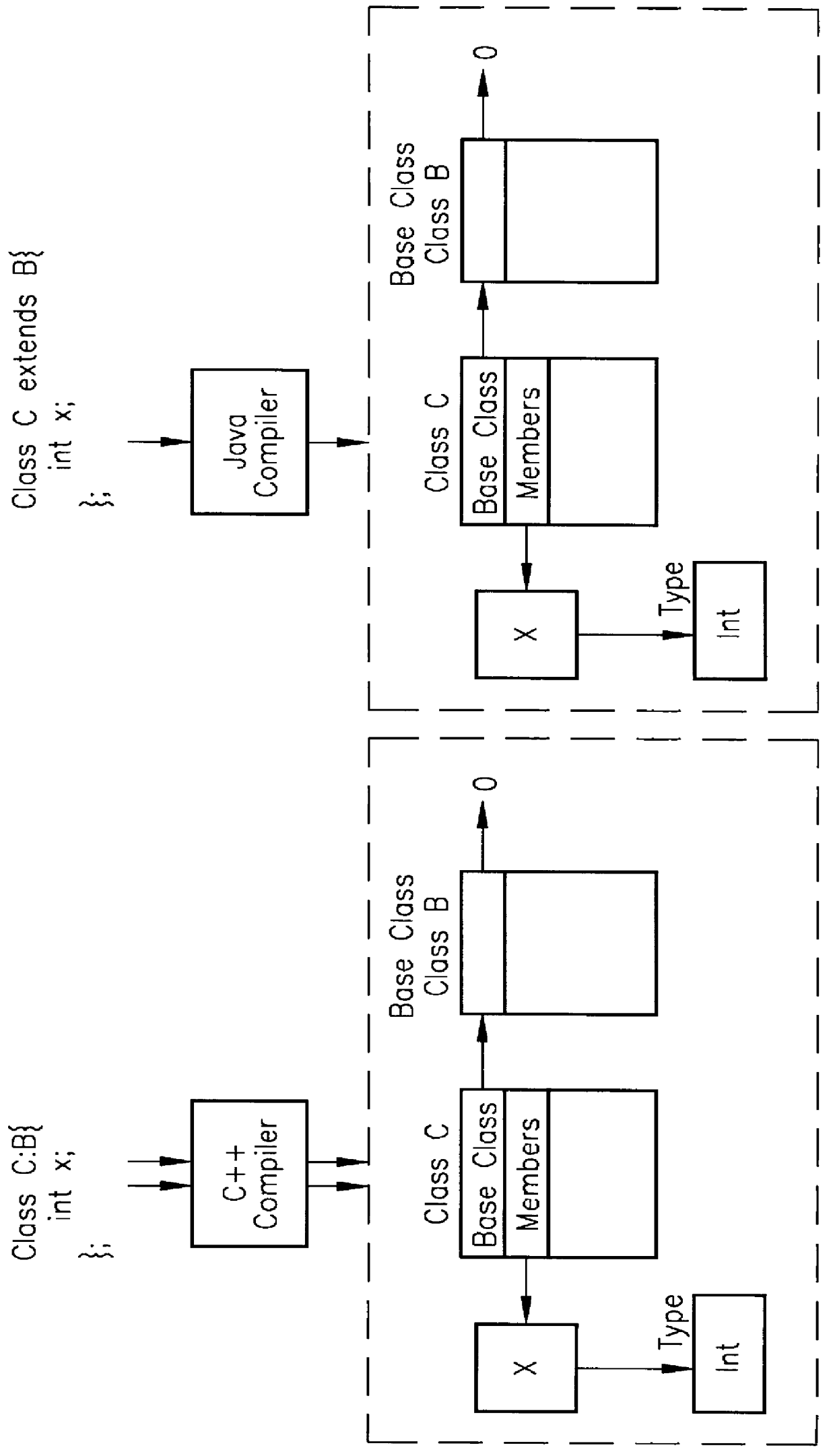
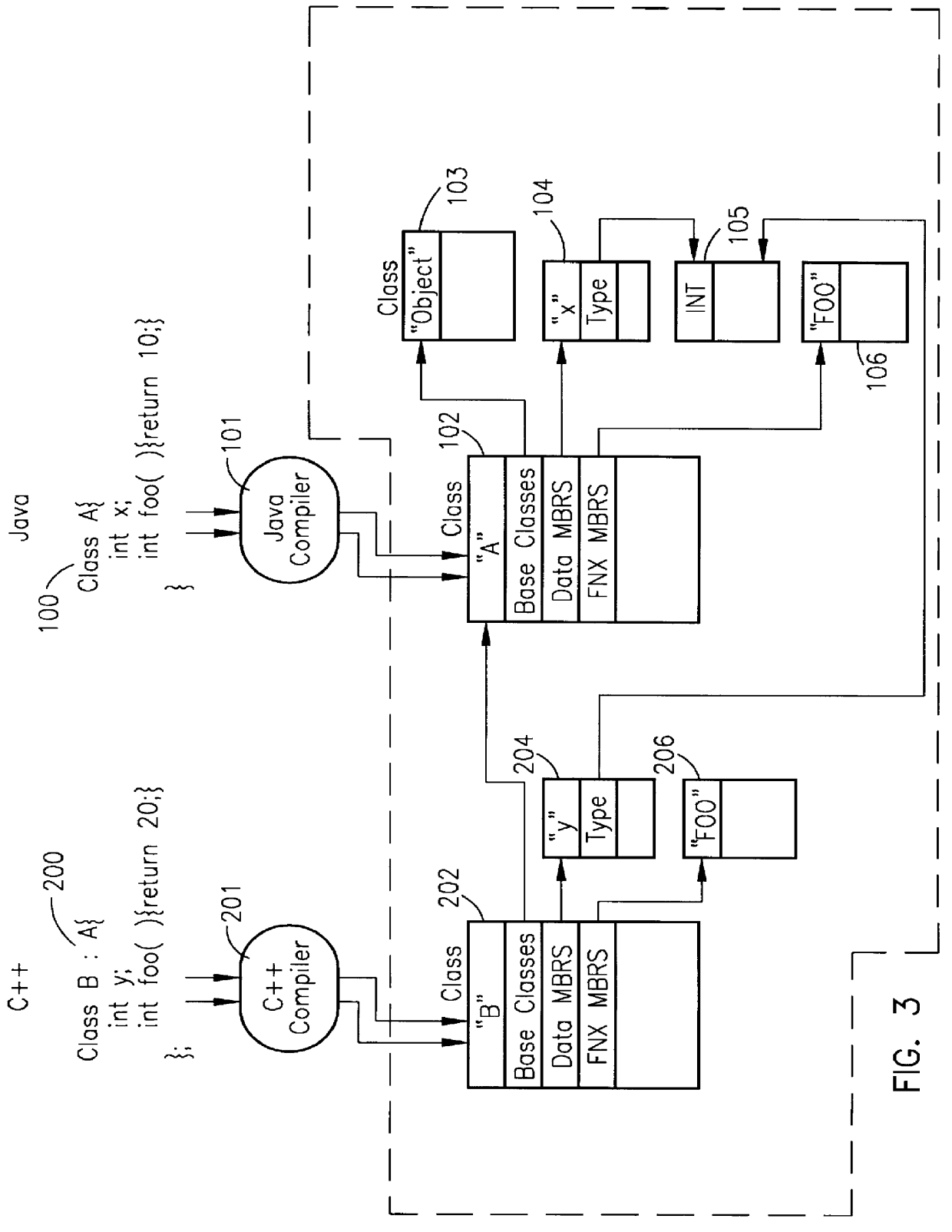
Data representation for mixed-language program development
InactiveUS6067413AReduce the burden onRealized benefitsMultiprogramming arrangementsSoftware designType conversionShared object
Method for enabling the simultaneous use of a first and a second programming language within a computer program, and apparatus to practice the method. To enable this sharing of languages, the present invention first provides for a common runtime representation of the data between the several languages in a program as a shared object model. The shared object model includes the layout of complex data structures (e.g., classes), the creation of data, the calling conventions, the destruction of data, the runtime representation of type information, dynamic function call dispatch, and dynamic type conversions. The use of a shared object model enables the sharing of the several compilers' internal representation of data between the different languages as a persistent shared symbol table. This shared internal data representation enables the several compilers to define their respective internal data representations in terms common to each of the compilers.
Owner:OPEN INVENTION NEWTORK LLC
Systems and methods for configuring policy bank invocations
ActiveUS20080225722A1Efficient configurationEfficient processingMultiplex system selection arrangementsError preventionData packEngineering
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
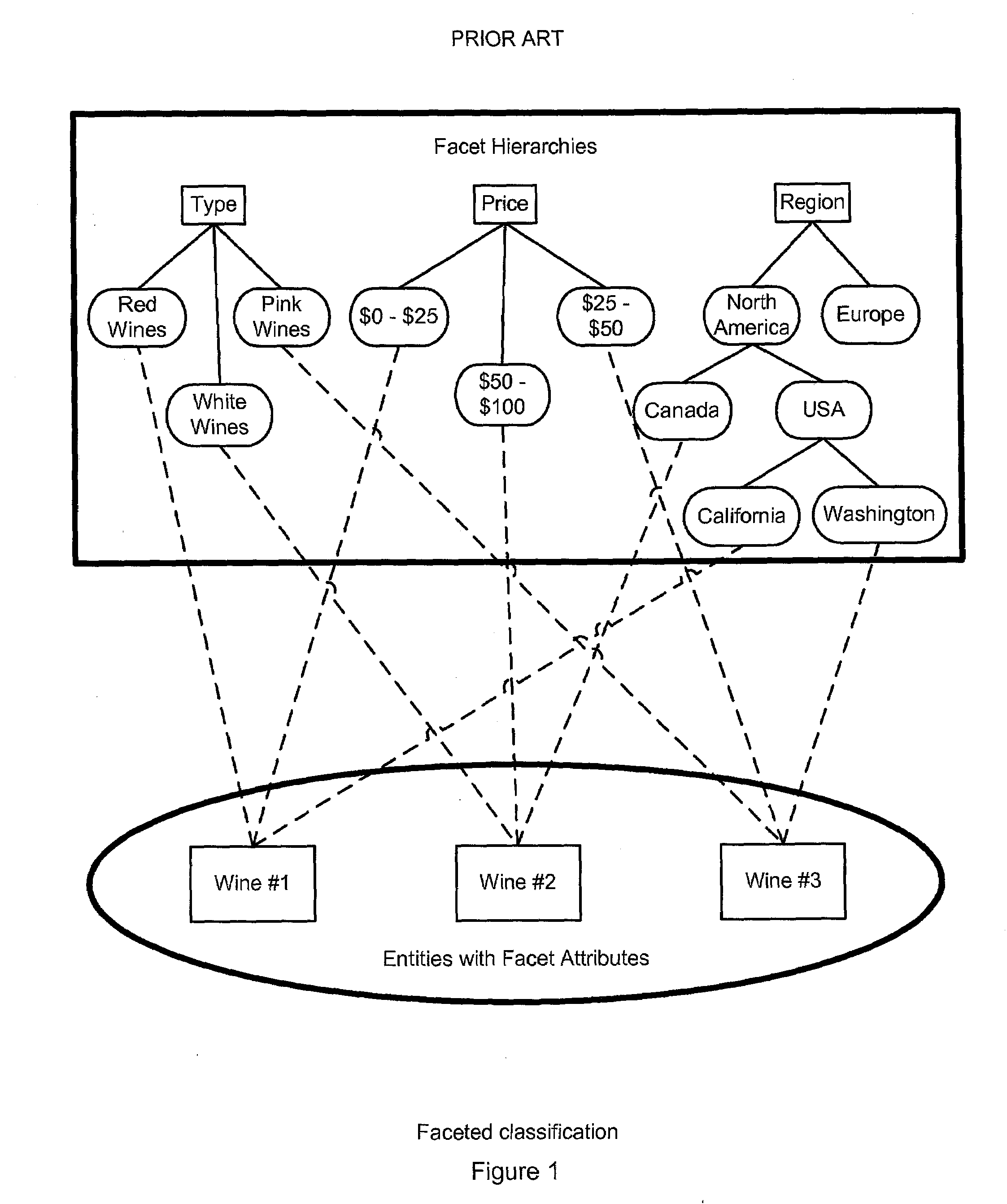
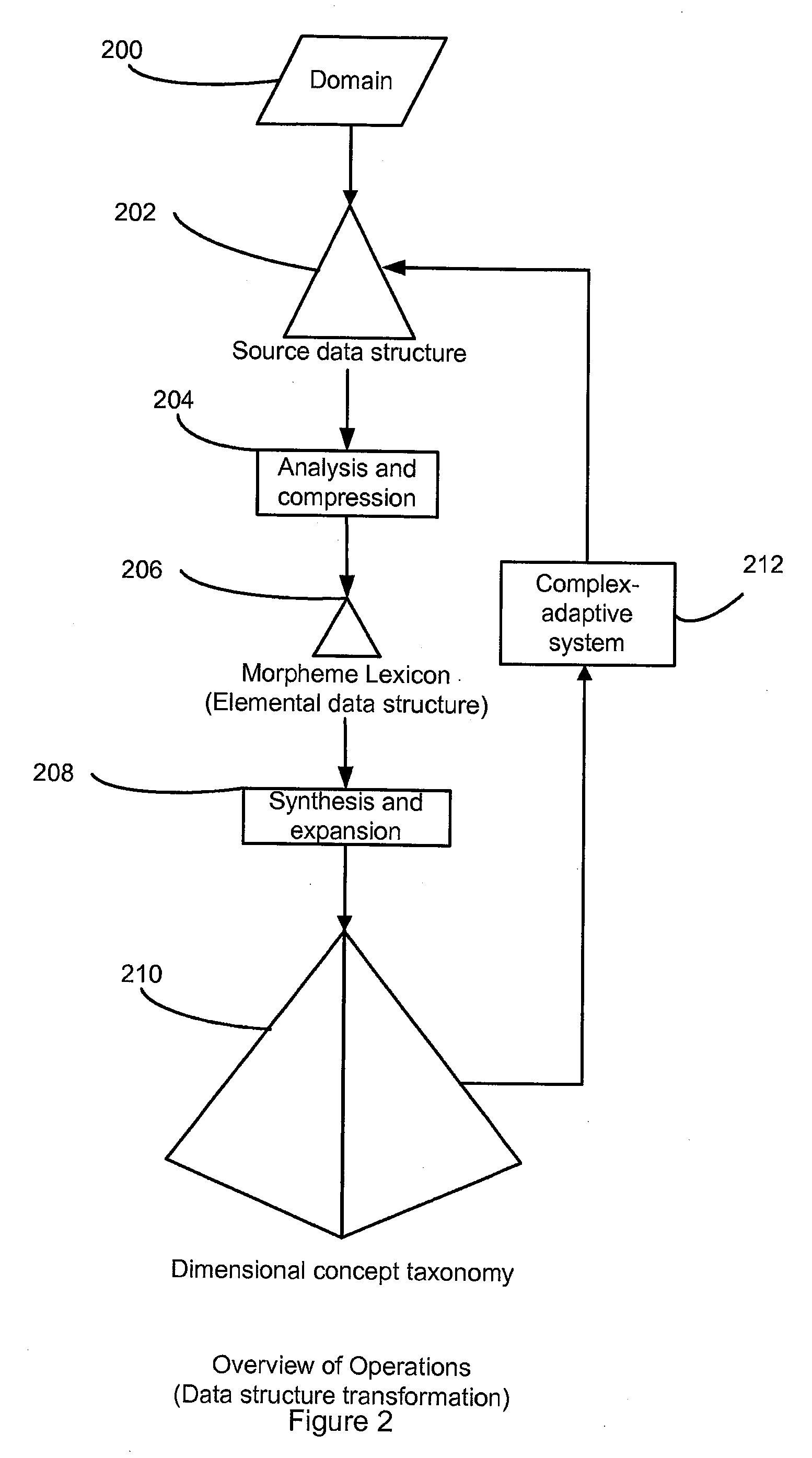
System, method and computer program for transforming an existing complex data structure to another complex data structure
ActiveUS20090300326A1Data processing applicationsDigital data processing detailsData setImplicit relationship
A method (system and computer program product) performs facet classification synthesis to relate concepts represented by concept definitions defined in accordance with a faceted data set comprising facets, facet attributes, and facet attributes hierarchies. Dimensional concept relationships are expressed between the concept definitions. Two concept definitions are determined to be related in a particular dimensional concept relationship by examining whether at least one of explicit relationships and implicit relationships exist in the faceted data set between the respective facet attributes of the two concept definitions.
Owner:PRIMAL FUSION INC
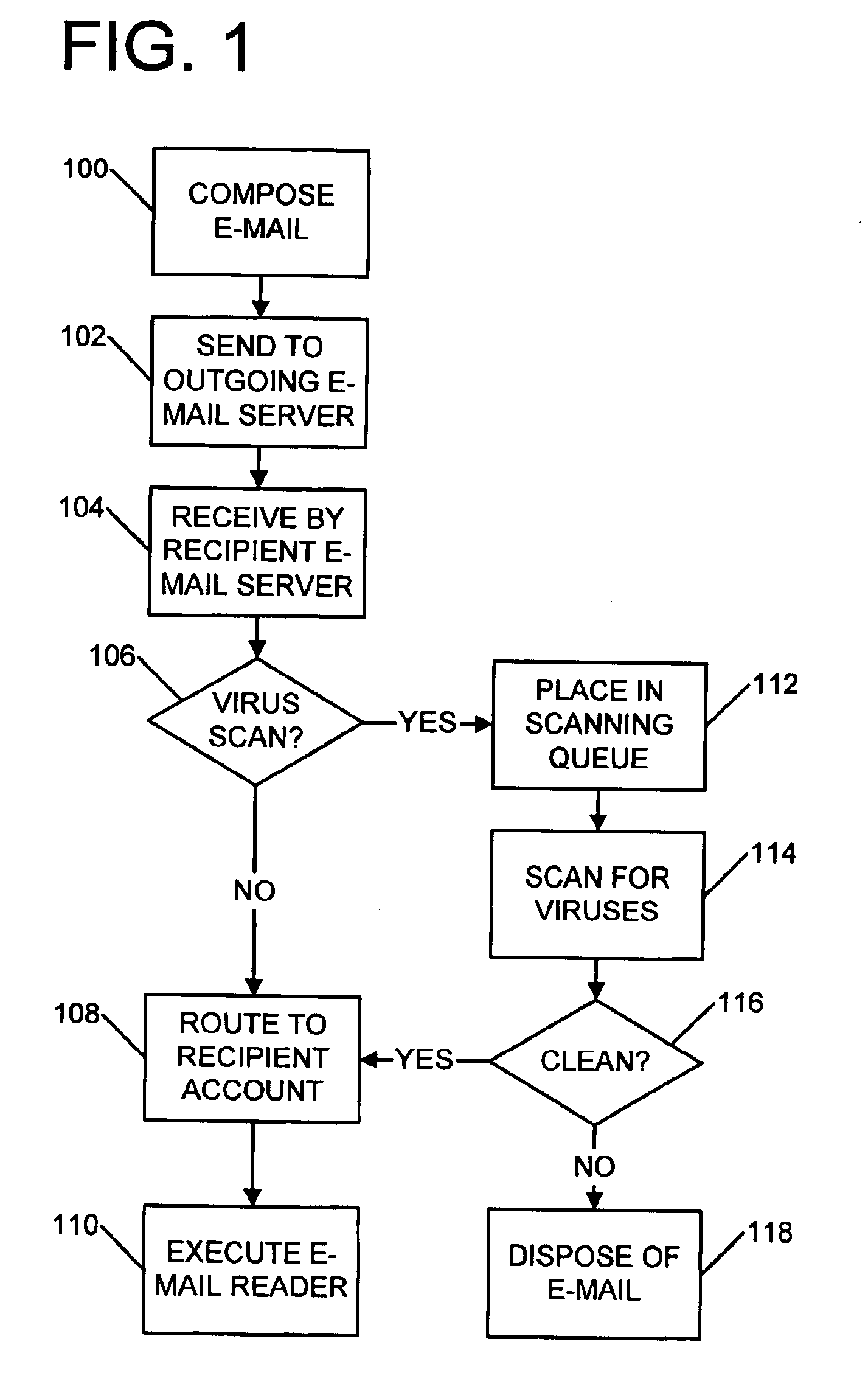
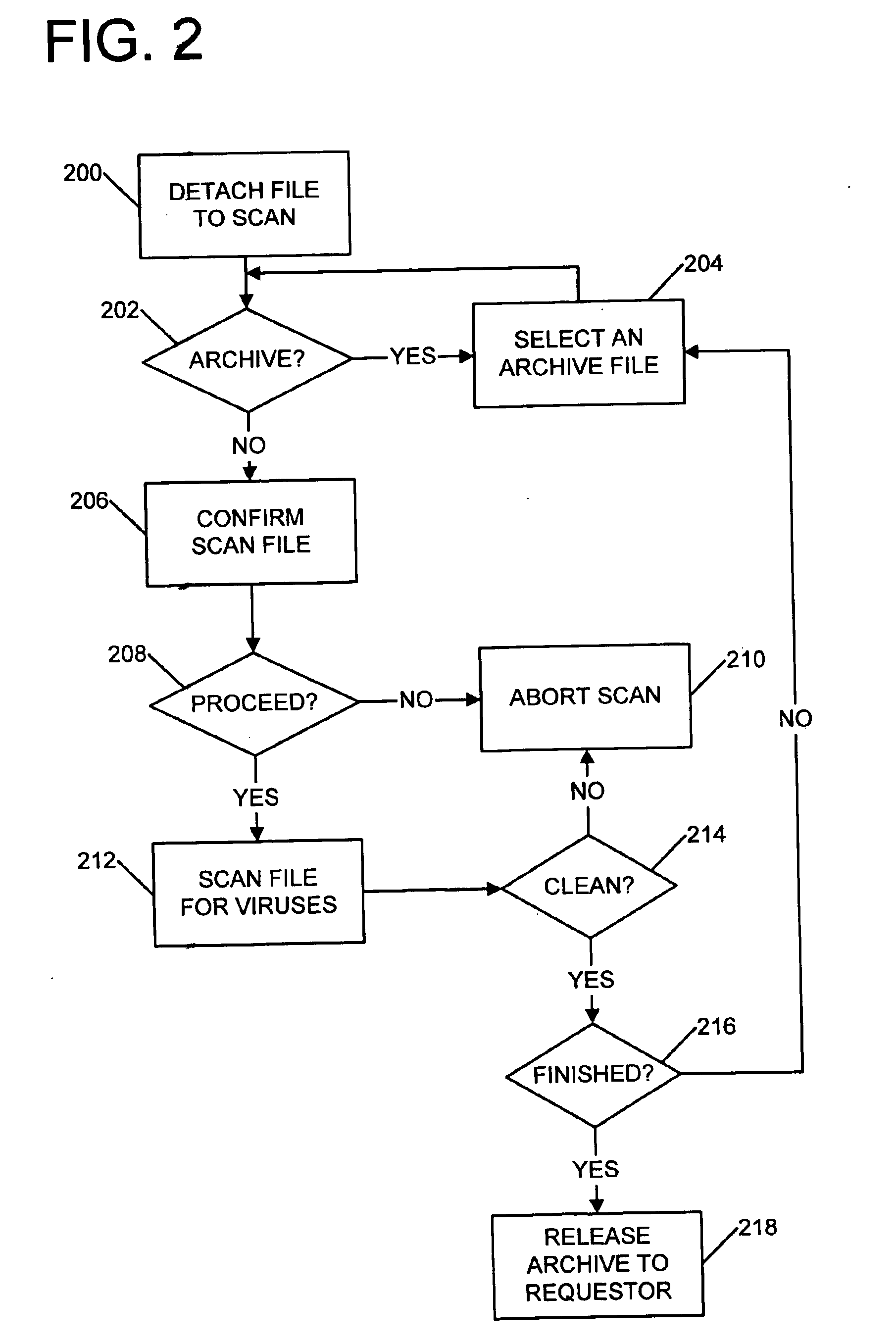
Priority-based virus scanning with priorities based at least in part on heuristic prediction of scanning risk
Anti-virus scanners can be deliberately disabled, inadvertently disabled, or simply slowed down to a point where the scanner becomes ineffective and the primary function of the scanning host device is disrupted when a suitably complex file is received by the scanning system for scanning. Archive files pose particular problems for scanners, since archives may contain very complex data structures, and require time consuming analysis. Virus scanners typically scan each element of an archive. Some virus scanners decompress each archive component for scanning. Virus developers have taken advantage of this scanning approach by creating complex archives designed to overwhelm a scanner, leaving a system unprotected or in a denial of service state. To counter such measures, when an archive (or other file) is passed to a scanner, various heuristics are applied to the archive so as to determine a risk-based scanning priority for the archive. Priorities can include normal priority, low priority for archives having suspicious characteristics, and discard without scanning for archives appearing to be constructed so as to overwhelm a scanner. Normal priority scans can occur immediately, while low priority scans can be relegated to only occurring while the scanning system is otherwise idle.
Owner:MCAFEE LLC
Method and/or system for flexible data handling
InactiveUS20080091491A1Power flexibleEasily and flexibly extendDigital data information retrievalDigital data processing detailsComplex data structuresInformation system
Methods and / or systems for representing and / or managing and / or querying data in an information system that allows non-programmer users to make additions of and / or modifications to data items while optionally preserving an underlying potentially complex data structure and preserving the ability to perform flexible and powerful queries and relationships in the data.
Owner:BNDENA
Systems and methods for configuring handling of undefined policy events
ActiveUS7853679B2Efficient configurationEfficient processingDigital computer detailsData switching by path configurationTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
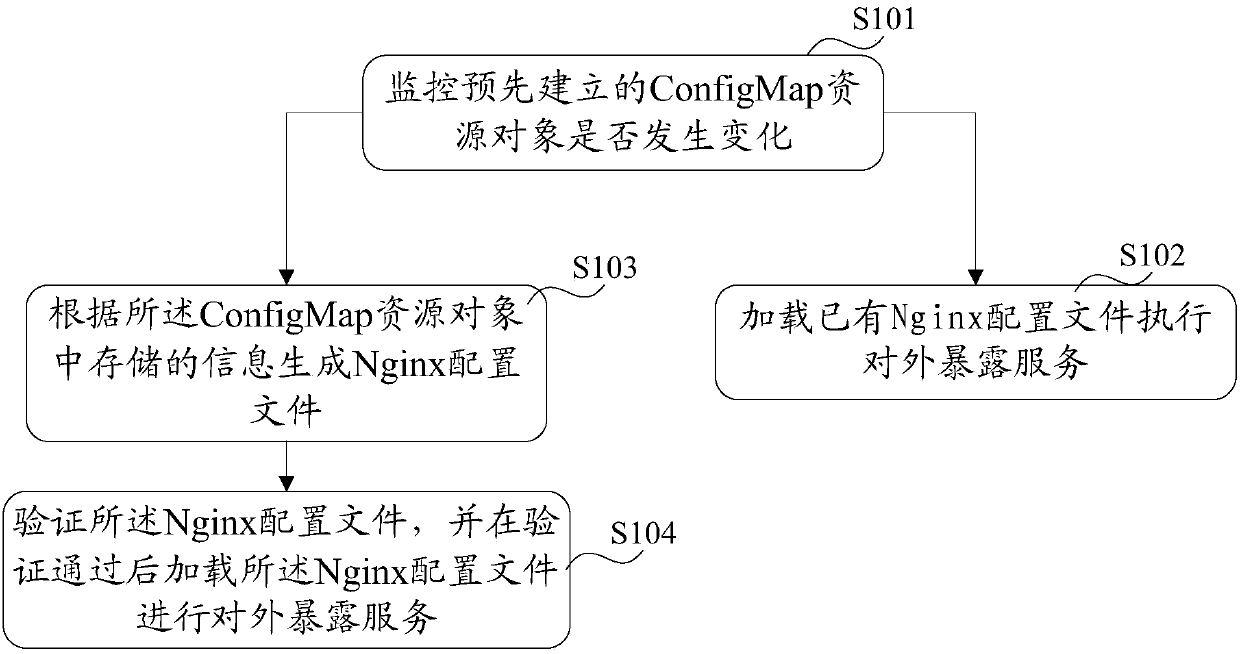
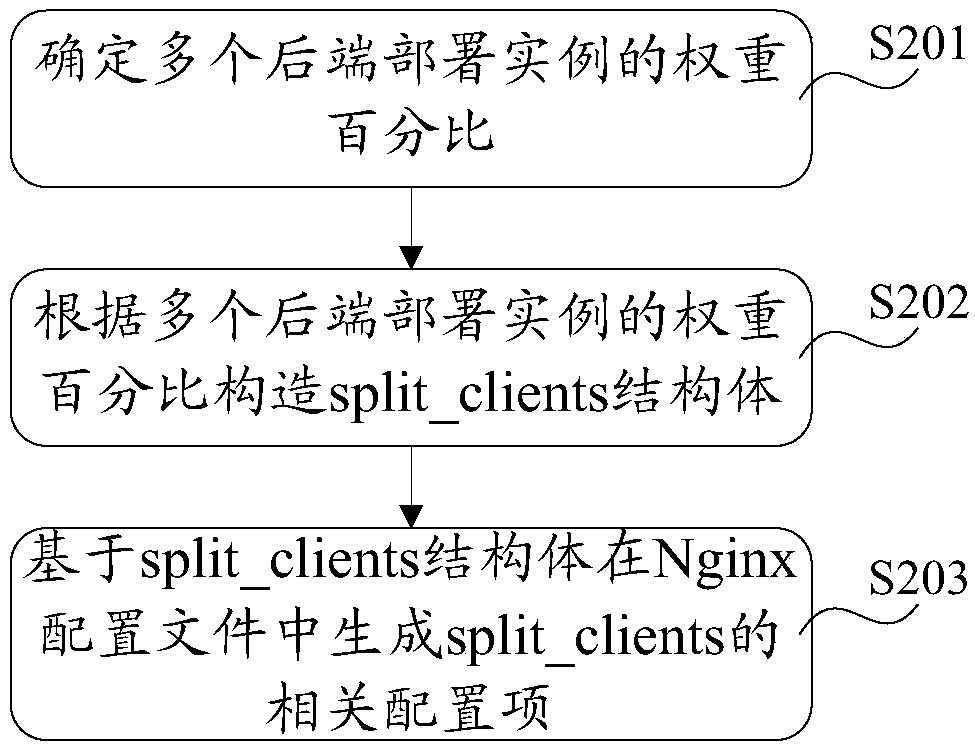
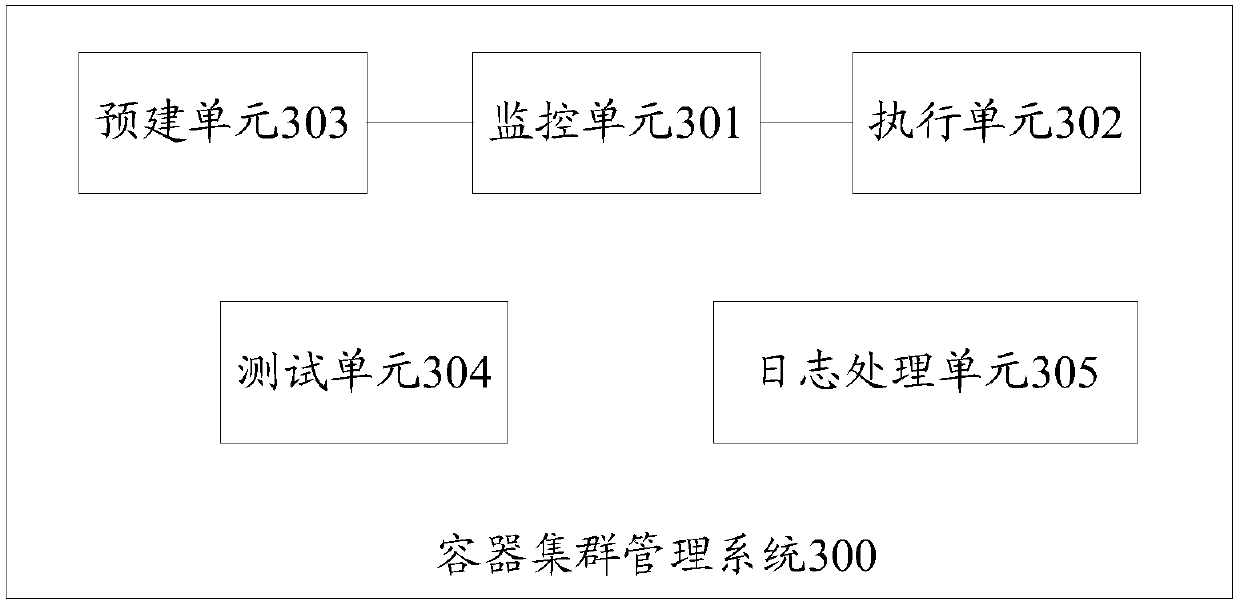
Container cluster management system and application method thereof
ActiveCN108039975AReduce complexityMake sure the configuration takes effectData switching networksConfiguration itemManagement system
The invention provides a container cluster management system and an application method thereof. Through storing an Nginx forwarding rule and configuration items in a pre-established ConfigMap resourceobject, and monitoring the ConfigMap by a ConfigMap controller, when the ConfigMap resource object changes, a Controller generates an Nginx configuration file of according to information stored in the ConfigMap and then verifies and loads the Nginx configuration file to ensure that the configuration is effective, so that an external exposure service is achieved. When the external exposure serviceis achieved through combination with functions provided by Nginx, the load balancing purposes of seven layers and four layers are considered, the resource object and a complex data structure do not need to be additionally introduced, and the complexity of the container cluster management system is reduced when the external exposure service is achieved.
Owner:BEIJING SOHU NEW MEDIA INFORMATION TECH
Systems and methods for using object oriented expressions to configure application security policies
ActiveUS20080225719A1Efficient configurationEfficient processingError preventionTransmission systemsTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Systems and methods for configuring flow control of policy expressions
ActiveUS7853678B2Efficient configurationEfficient processingError preventionTransmission systemsTraffic capacityData stream
Owner:CITRIX SYST INC
Systems and methods for using object oriented expressions to configure application security policies
ActiveUS7870277B2Efficient configurationEfficient processingMultiple digital computer combinationsTransmissionTraffic capacityData stream
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
Systems and methods for managing application security profiles
ActiveUS8490148B2Efficient configurationEfficient processingMemory loss protectionError detection/correctionData streamUnstructured data
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
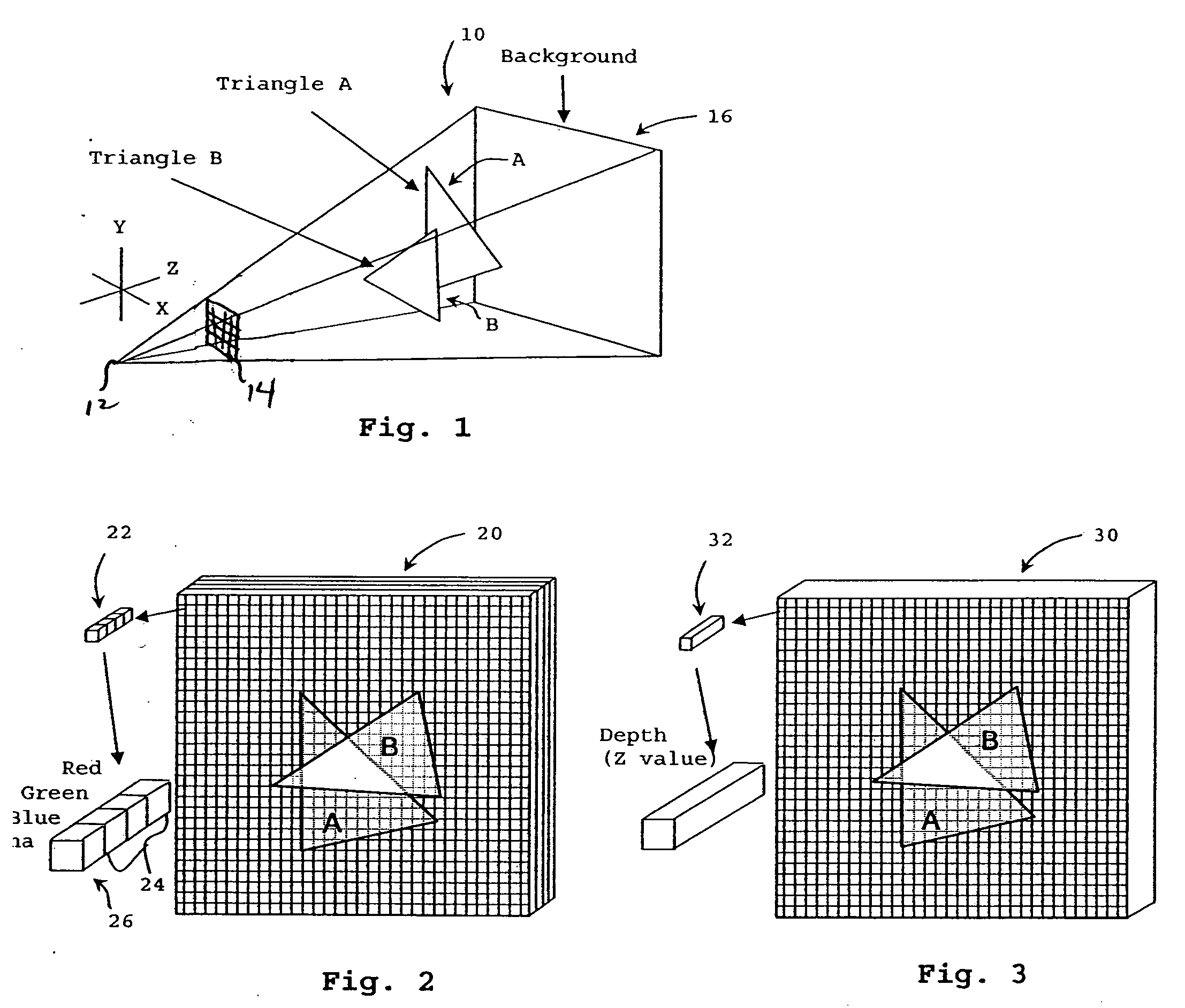
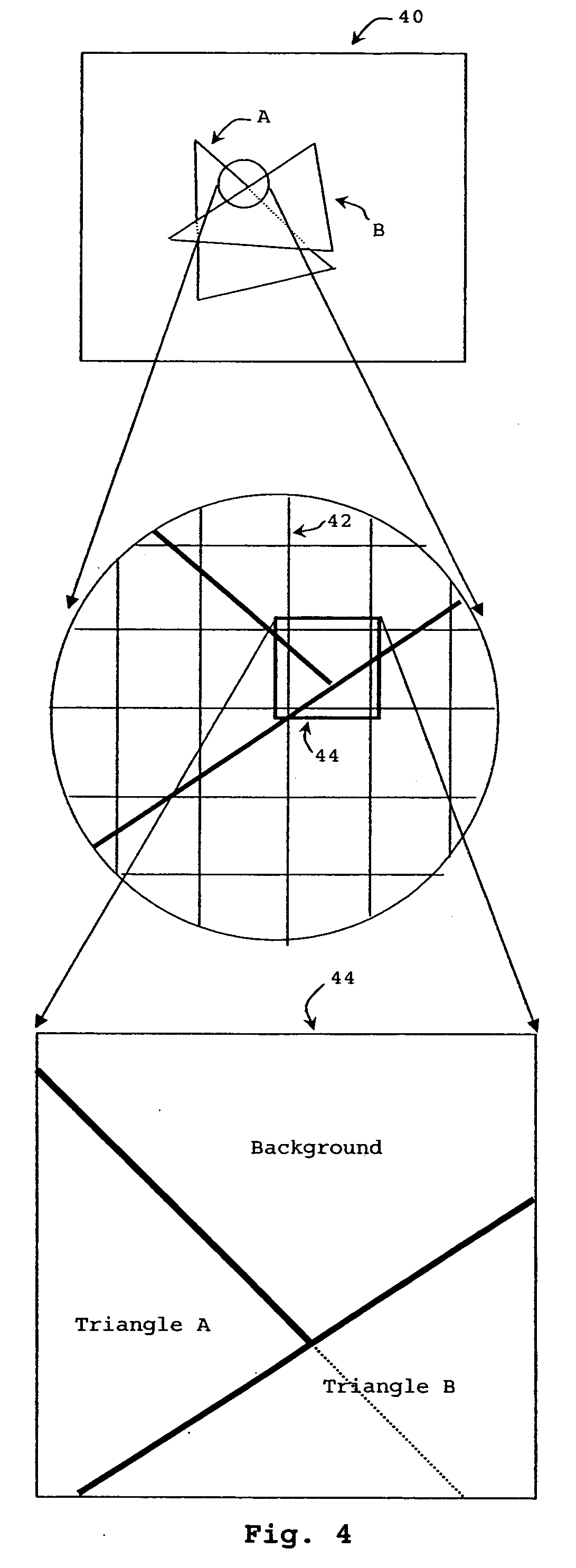
Image rendering with multi-level Z-buffers
InactiveUS20050162435A1Proceed very rapidlyCathode-ray tube indicatorsElectric digital data processingComputer graphics (images)Imaging data
In an image processor, images are rendered into a plurality of frame buffers and corresponding Z-buffers by depth and the plurality of frame buffers are later combined to form the rendered image. The rendering can be implemented in hardware, software or a combination, for real-time or near real-time rendering of images. The plurality of frame buffers can be processed in parallel using a plurality of frame processors. The rendering can be performed on a stream of polygons received in an arbitrary order so that presorting the polygons is not required. Complex data structures and processing are not required, allowing a rendering process to proceed quickly, which is needed where the rendering must be done in real-time or near real-time for full- or nearly full-motion video. The image processor is provided with an indication of the number of frame buffers in the plurality of frame buffers. With this indication, the image processor can make the program memory allocations if needed and will process the image data with the required fidelity. The number of frame buffers used might vary as needed for different fidelities and images.
Owner:ELECTRONICS ARTS INC
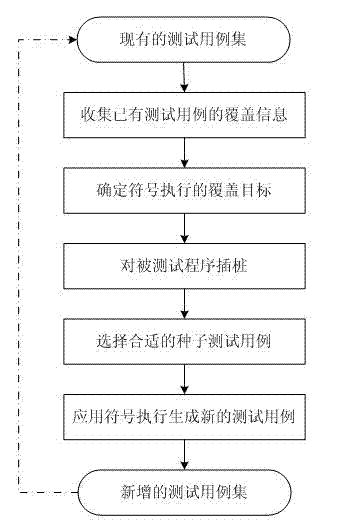
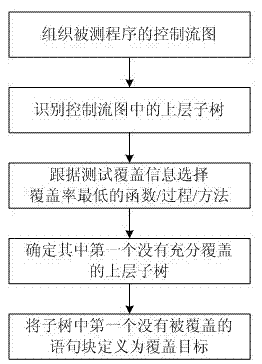
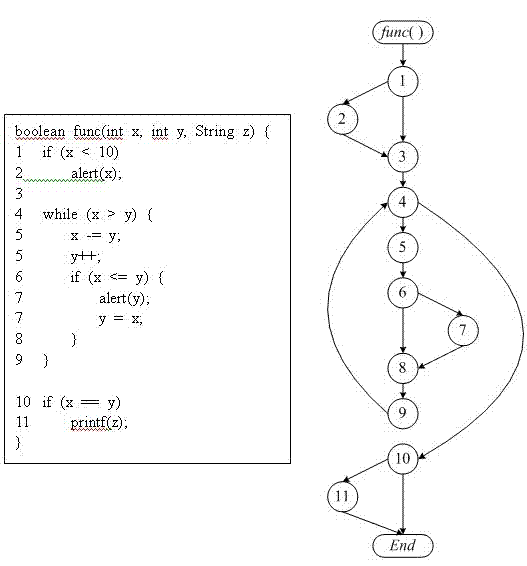
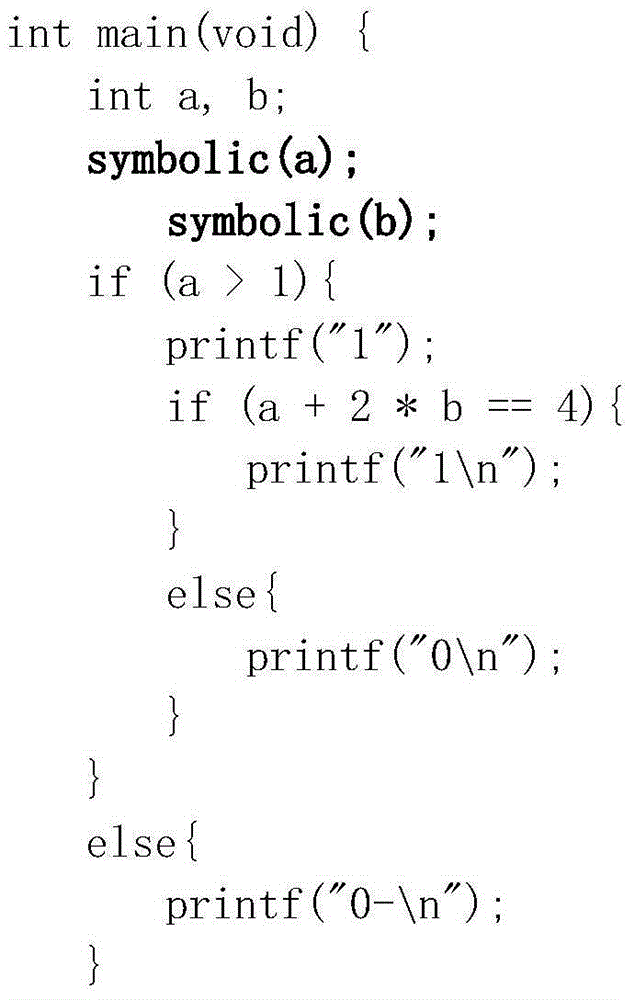
Symbolic-execution-based method for generating test cases with feedback
InactiveCN102736979AReduce problem sizeReduce in quantitySoftware testing/debuggingSoftware development processAutomatic testing
The invention discloses a symbolic-execution-based method for generating test cases with feedback. The method comprises the following steps of: (1) executing the conventional test cases, and collecting information covered by the test cases; (2) determining a symbolic execution covering object according to a control flow diagram of a tested program; (3) instrumenting the tested program, and implanting a symbolic execution control code; (4) selecting a proper seed test case from the conventional test case set; (5) generating a new test case for the covering object by using a symbolic execution method, and supplementing the new test case into the test case set; and (6) repeating the steps until a given test case generation aim is fulfilled. The method can be widely applied to automatic test in a software development process, and is used for automatically generating the test cases, so that the problem of constraint condition explosion of independent symbolic execution is solved, and efficiency is improved; and in addition, other generation methods can be combined, so that the problem that complex data structures cannot be processed by the symbolic execution method can be alleviated.
Owner:NANJING UNIV
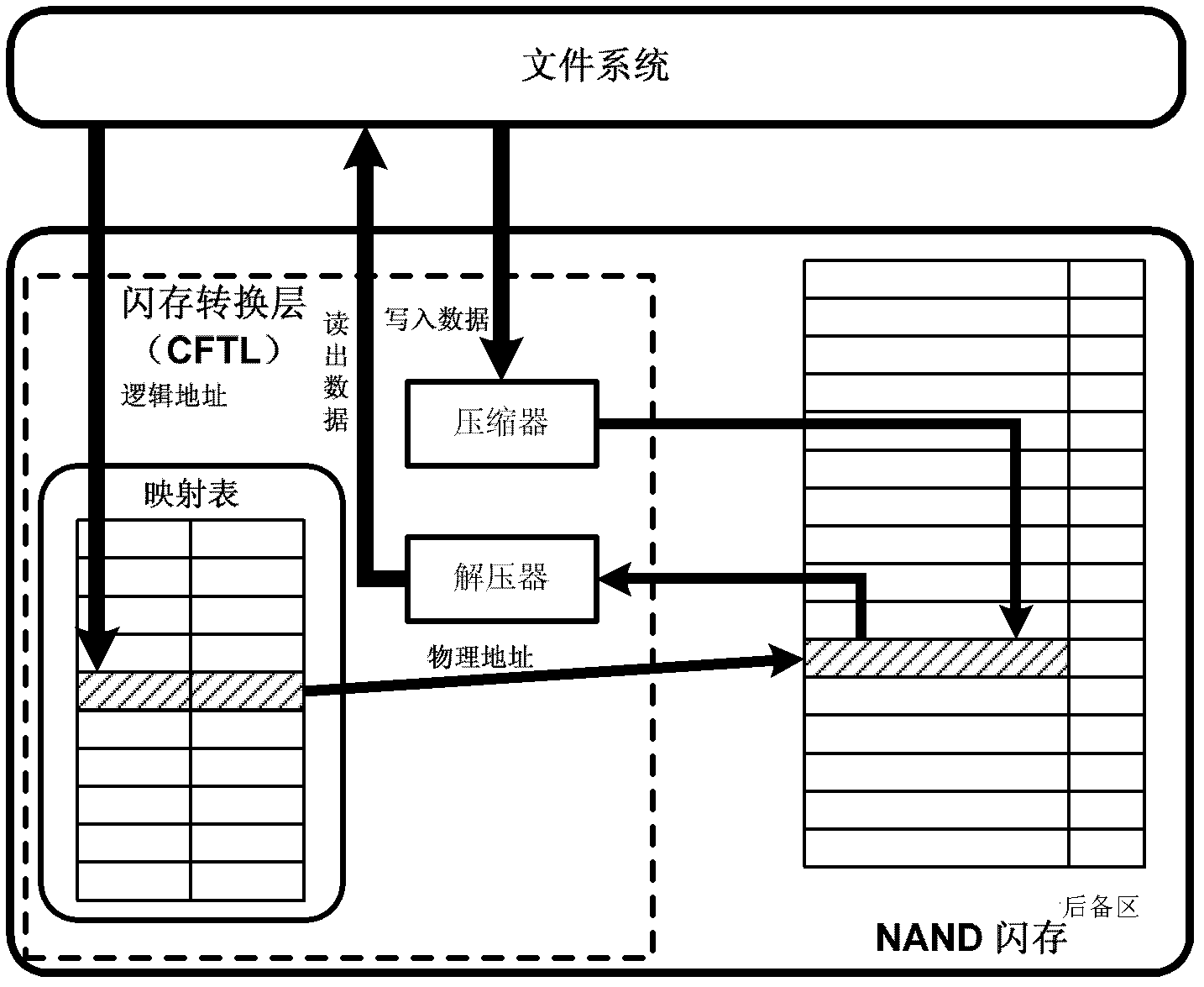
Solid state disk and access method
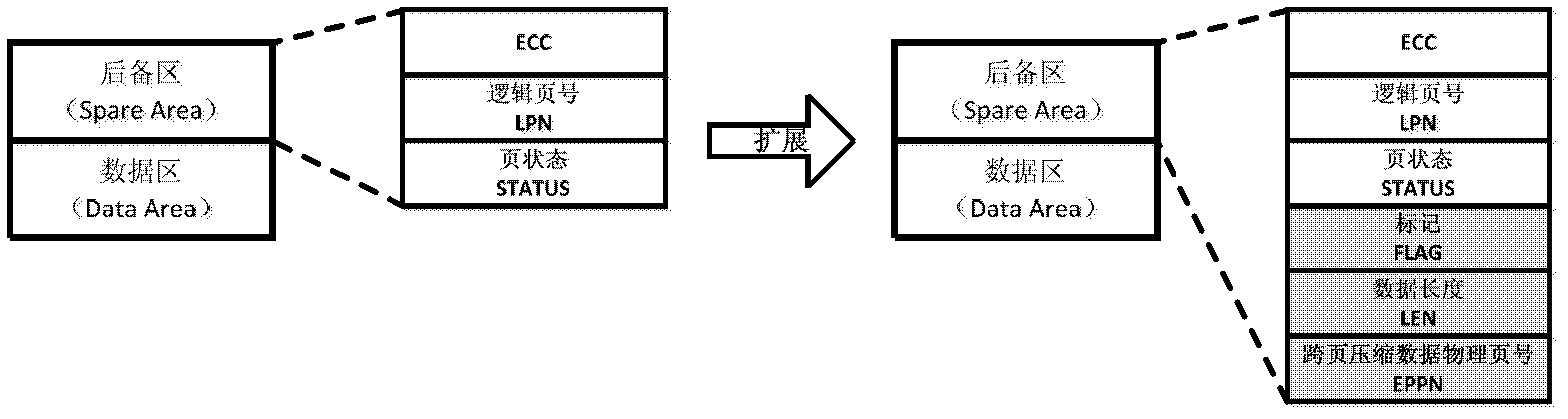
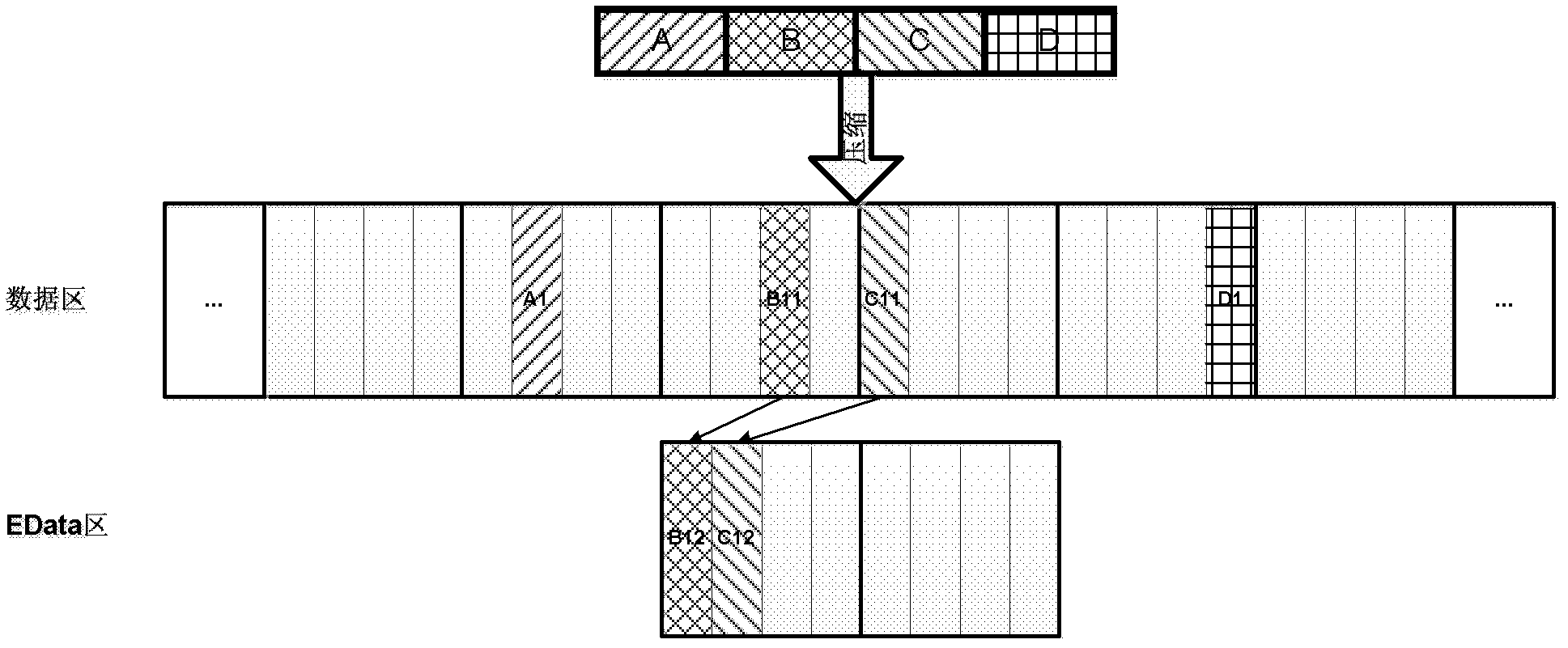
ActiveCN102662856AReduce data volumeEasy to read and writeMemory adressing/allocation/relocationAccess methodRelevant information
The invention provides a solid state disk which compresses data through a flash memory conversion layer and stores relevant information of compressed data in a back-up area of a flash memory physical page. The solid state disk can reduce data quantity written into and read from the flash memory solid disk of each time, reduces times of erasure operation caused by writing operation simultaneously, and prolongs service life. In addition, a read-write process of data is simple and convenient, a complex data structure is not added, a buffering area is not added either, a mapping table in a traditional flash memory conversion layer is not required to be modified, and cost of a data read-write process is guaranteed to be low.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI +1
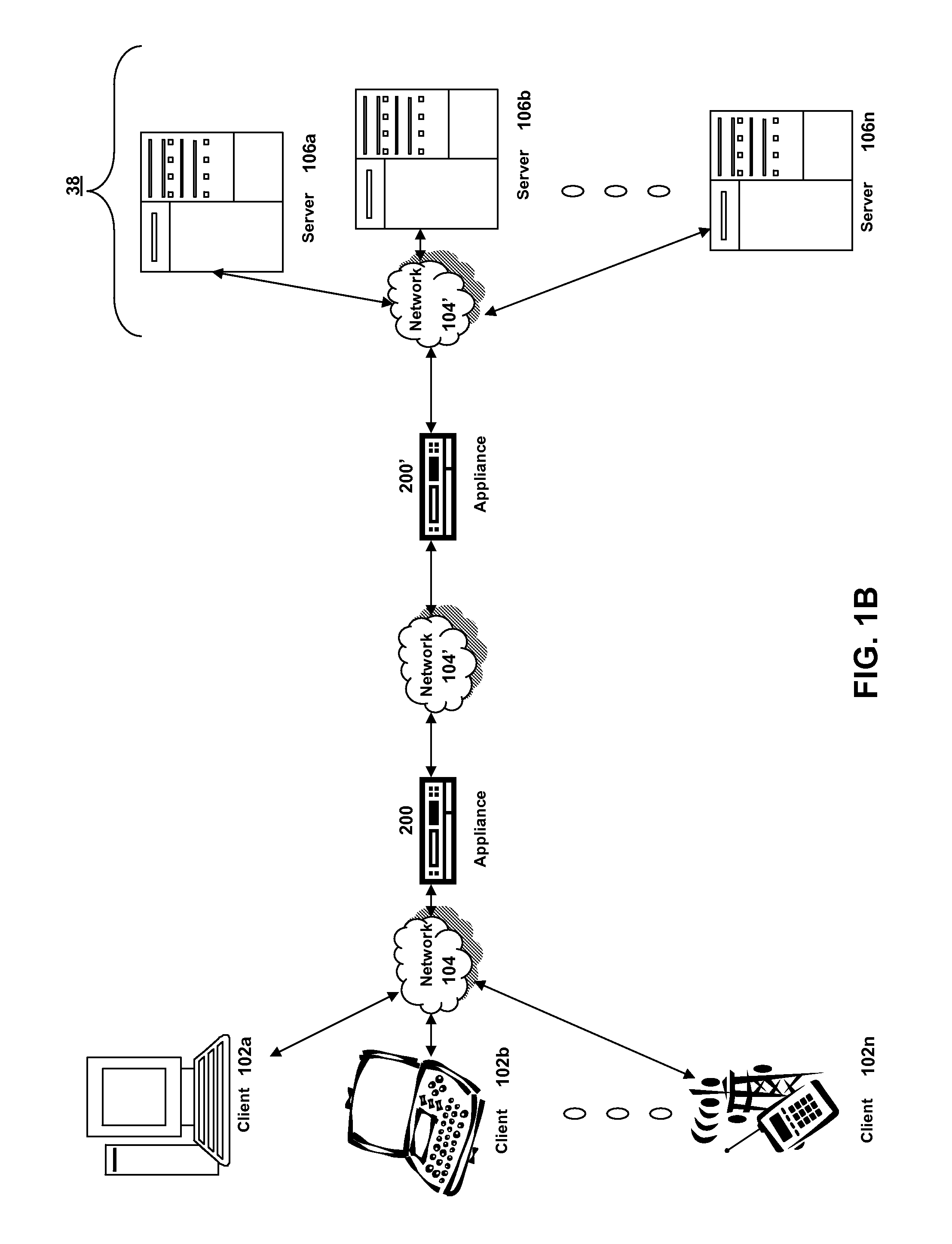
Systems and methods for providing structured policy expressions to represent unstructured data in a network appliance
ActiveUS7865589B2Efficient configurationEfficient processingError preventionFrequency-division multiplex detailsData packLoad Shedding
Systems and methods for configuring and evaluating policies that direct processing of one or more data streams are described. A configuration interface is described for allowing users to specify object oriented policies. These object oriented policies may allow any data structures to be applied with respect to a payload of a received packet stream, including any portions of HTTP traffic. A configuration interface may also allow the user to control the order in which policies and policy groups are executed, in addition to specifying actions to be taken if one or more policies are undefined. Systems and methods for processing the policies may allow efficient processing of object-oriented policies by applying potentially complex data structures to unstructured data streams. A device may also interpret and process a number of flow control commands and policy group invocation statements to determine an order of execution among a number of policies and policy groups. These policy configurations and processing may allow configuration and processing of complex network behaviors relating to load balancing, VPNs, SSL offloading, content switching, application security, acceleration, and caching.
Owner:CITRIX SYST INC
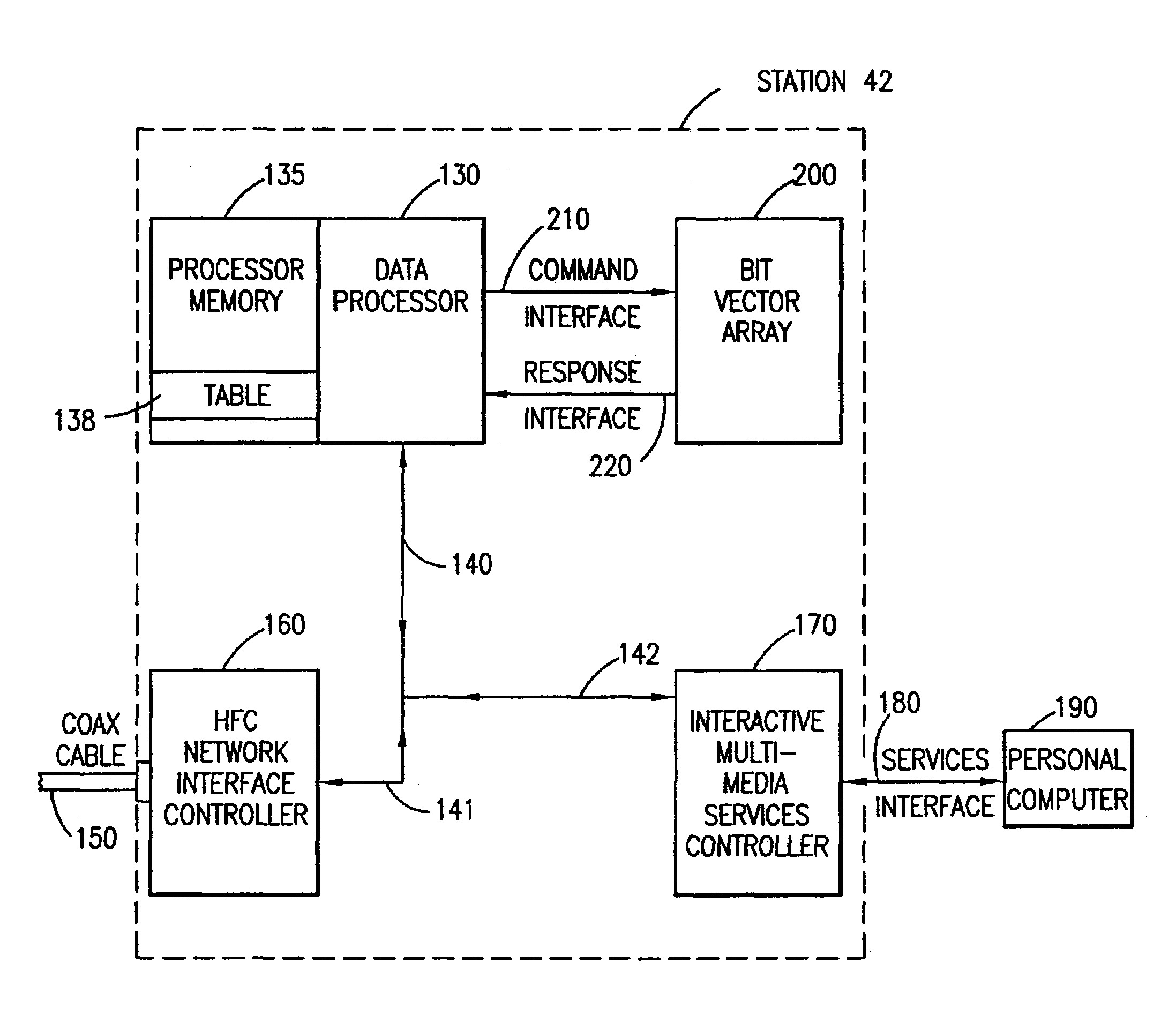
Method and apparatus for bit vector array
InactiveUS7284260B2Controls contentionGeneral purpose stored program computerStar/tree networksVector elementParallel processing
A bit vector array apparatus provides a high speed method for processing network transmission controls. Complex data structures for controlling network access are represented in the simplest possible form as single bit vector elements. The bit vector elements are combined into bit vectors comprised of 32 single bit vector elements. The bit vectors are processed in parallel in the bit vector array apparatus, which is comprised of special-purpose bit manipulation functions to expedite the processing.
Owner:INT BUSINESS MASCH CORP
Method and system for network load balancing with a compound data structure
The invention provides for employing a complex data structure to optimize the retrieval of data over a network. The complex data structure includes two separate sub-data structures (Trie and List) that separately reference the same data objects in a data store. The Trie sub-data structure is used to fulfill a single data object request. The List sub-data structure is employed with function requests related to several data objects. Each data object is associated with a parent object that includes a list of every reference to the data object in both the Trie and List sub-data structures. A collector object is a type of data object that is associated with a member object and which includes a list of other related data / collector objects. When data associated with the collector object is requested, other data associated with the other data / collector objects on the member object list are automatically retrieved.
Owner:F5 NETWORKS INC
System and method for automated mapping of data types for use with dataflow environments
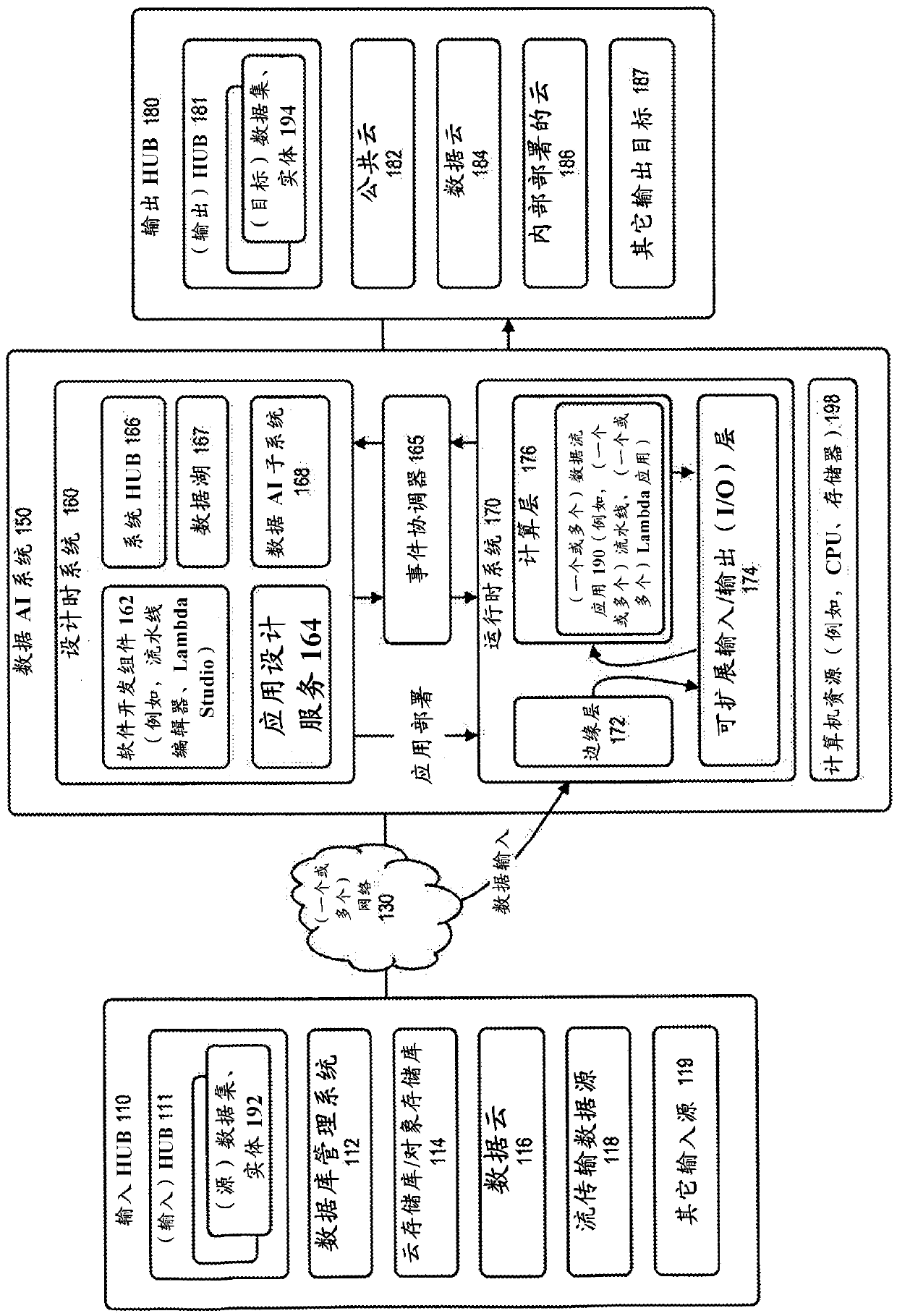
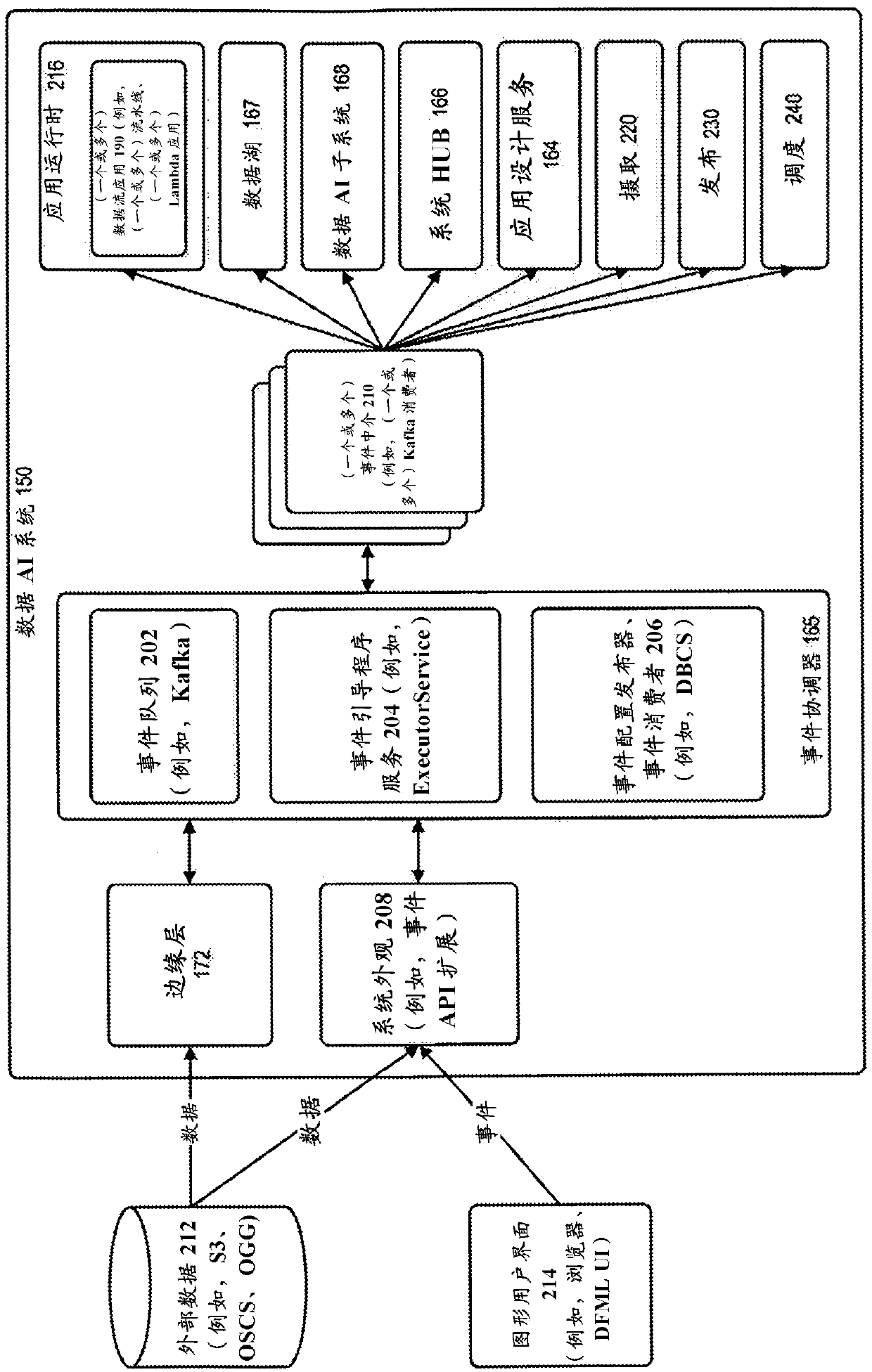
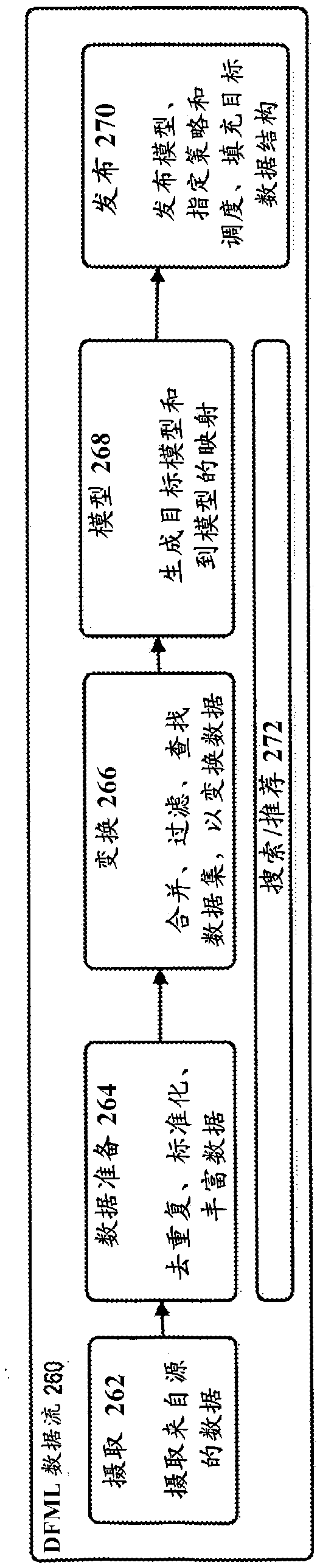
In accordance with various embodiments, described herein is a system (Data Artificial Intelligence system, Data Al system), for use with a data integration or other computing environment, that leverages machine learning (ML, DataFlow Machine Learning, DFML), for use in managing a flow of data (dataflow, DF), and building complex dataflow software applications (dataflow applications, pipelines). Inaccordance with an embodiment, the system can provide support for auto-mapping of complex data structures, datasets or entities, between one or more sources or targets of data, referred to herein insome embodiments as HUBs. The auto-mapping can be driven by a metadata, schema, and statistical profiling of a dataset; and used to map a source dataset or entity associated with an input HUB, to a target dataset or entity or vice versa, to produce an output data prepared in a format or organization (projection) for use with one or more output HUBs.
Owner:ORACLE INT CORP
Distributed automatic test case generation method based on dynamic symbolic execution
ActiveCN105117341AAchieve independenceEasy to analyze and processSoftware testing/debuggingTest efficiencySemantics
The invention belongs to a distributed automatic test case generation method based on dynamic symbolic execution in the technical field of software test case automatic generation. The method comprises the following steps of: configuration of a test device, pre-processing of a program under test, extraction of a path constraint condition, and automatic generation of the test case. According to the invention, the program under test is separated from a test case automatic generation tool, and the program under test can run on a real platform in test, thus, the collected path constraint condition follows own semantics of the program, is accurate, and is helpful for analyzing complex data structures, thereby improving reliability and validity of test; moreover, multiple programs under test can be tested at the same time, and multiple parallel multi-path selection methods are provided. Therefore, the distributed automatic test case generation method based on dynamic symbolic execution has the characteristics of running the program under test on the real platform, having high reliability, being capable of performing multiple tests at the same time, effectively improving test reliability, test accuracy and test efficiency, having high utilization rate of test tools, and so on.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Software defect prediction method based on kernel principal component analysis and extreme learning machine
InactiveCN107346286AEasy to measureBiological neural network modelsCharacter and pattern recognitionOriginal dataCharacteristic space
The invention discloses a software defect prediction method based on kernel principal component analysis and extreme learning machine. Aiming at the problems that irrelevant module features damage defect prediction model performances in prediction of software defect quantity and the original defect data cannot be accurately represented by the original characteristics, the method disclosed by the invention comprises the following steps: projecting original data into a potential characteristic space through nonlinear mapping by adopting kernel principal component analysis, so that the mapped characteristics are capable of accurately characterizing the complex data structure and increasing the linear separability probability of data in the space; and extracting the representative characteristics of the data, and finally establishing a defect prediction model by adopting an extreme learning mechanism according to the data after characteristic extraction.
Owner:WUHAN UNIV
Table connection optimizing method based on heterogeneous system, CPU and accelerator
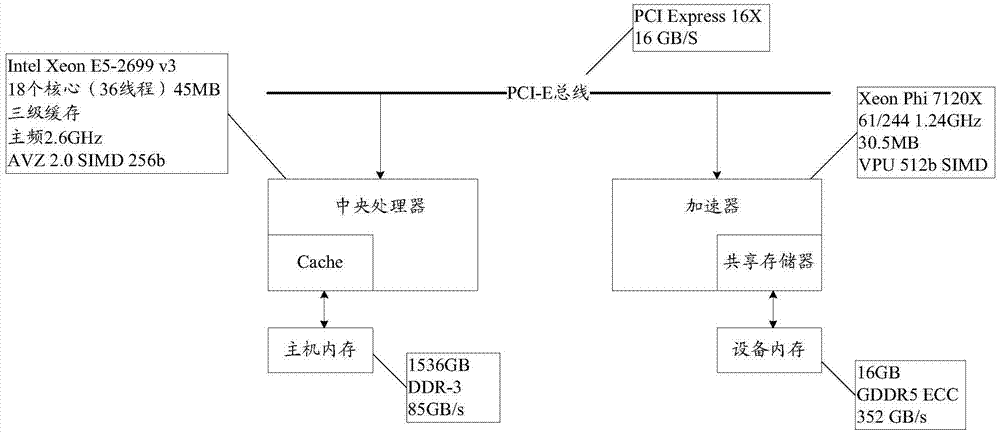
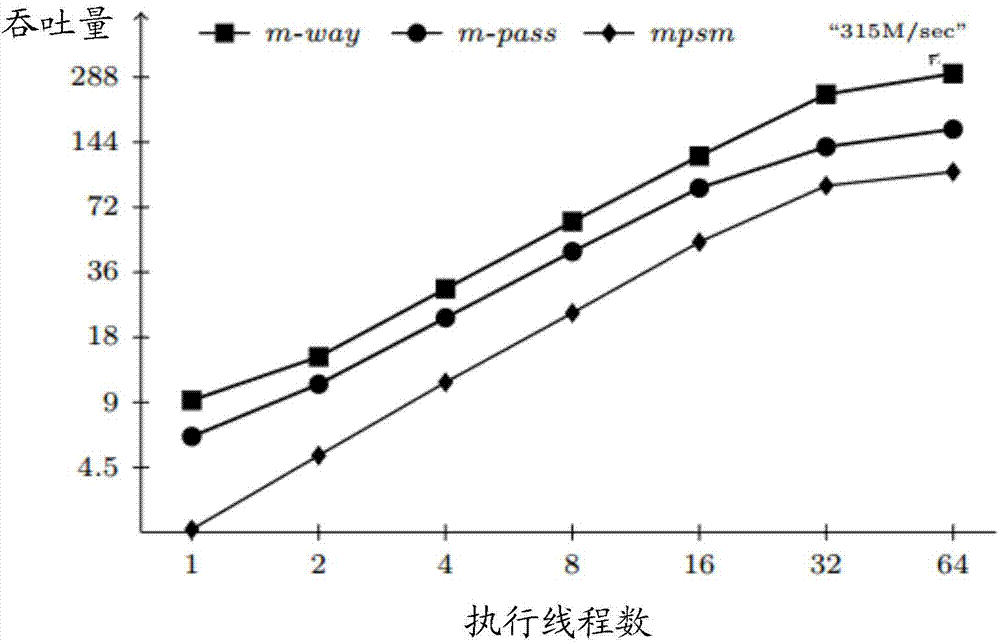
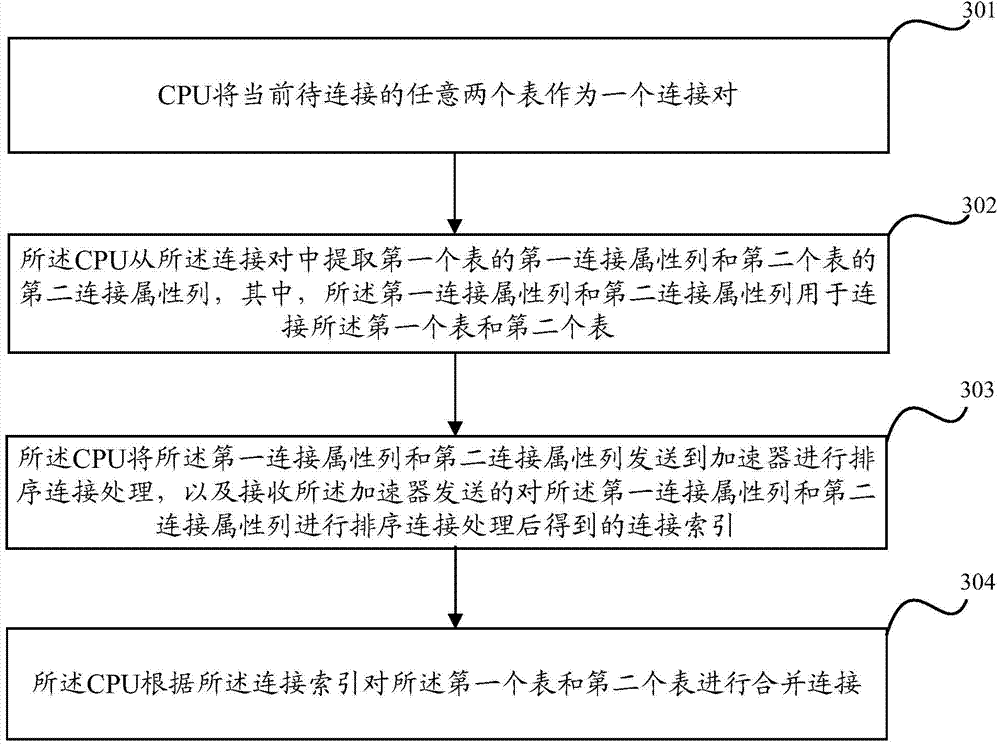
ActiveCN104731729ASolve the situation of unequal computing powerElectric digital data processingHigh densityParallel computing
The invention discloses a table connection optimizing method based on a heterogeneous system, a CPU and an accelerator. According to the table connection optimizing method based on the heterogeneous system, through the combination of the advantages of the CPU and the accelerator, complicated logic control such as task distribution and scheduling and complicated data structure processing such as table disassembly and reconstruction of a tuple are completed by the CPU; high-density calculation for connection of two tables is completed by the accelerator having ultrahigh parallel calculation capacity; in this way, the table connection optimizing method is effectively adaptive to the different hardware features of the CPU and the accelerator, and the problem that calculation capacities are not coordinate under a heterogeneous platform is solved.
Owner:HUAWEI TECH CO LTD
Implementation method and system for visual matching and real-time displaying
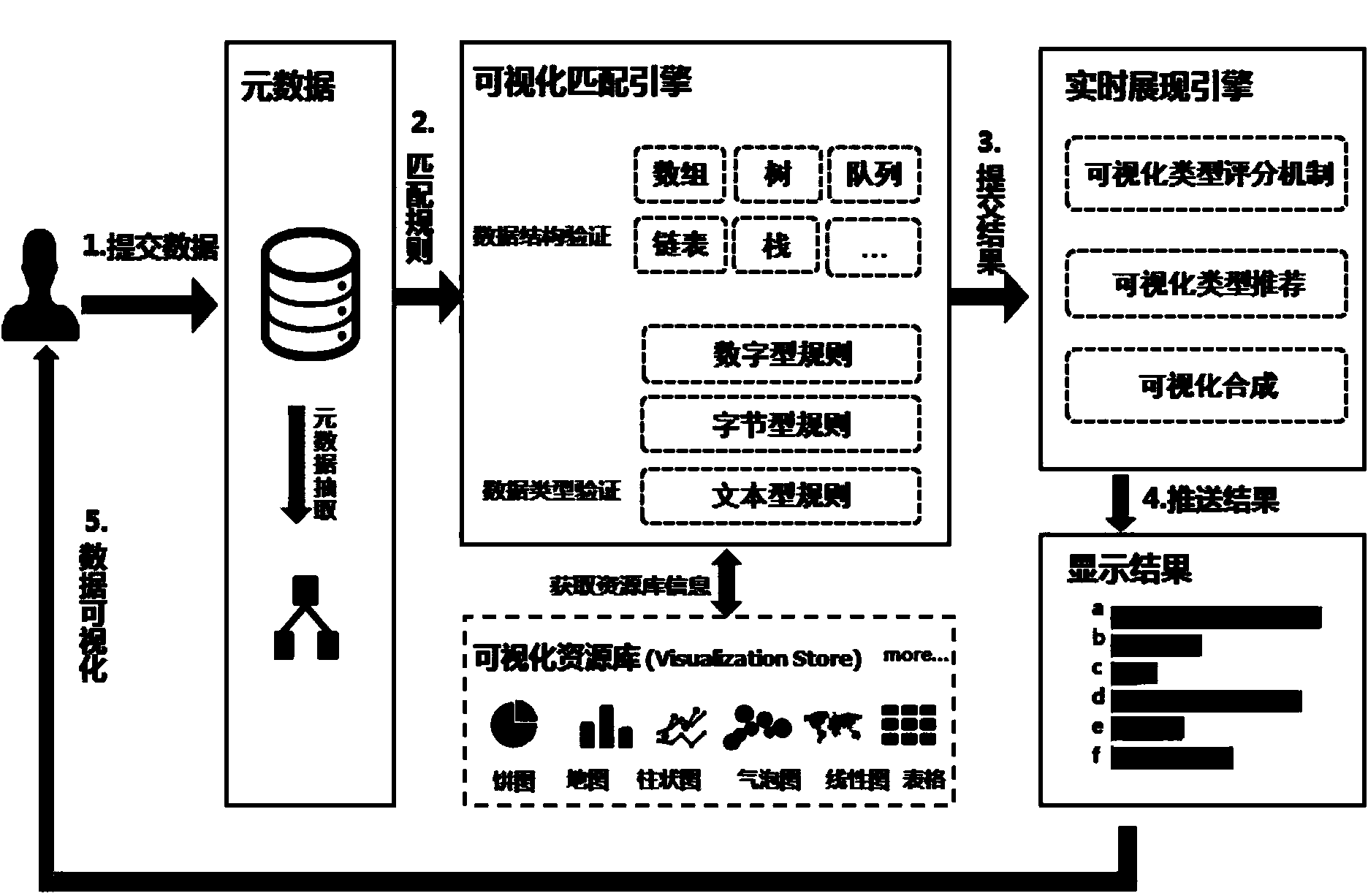
ActiveCN104166681AQuick match visualization rulesShield artificial factorsSpecial data processing applicationsGraphicsVisual matching
The invention discloses an implementation method and system for visual matching and real-time displaying. The method comprises the steps that first, the metadata of user data are extracted; second, comparison verification is conducted on the metadata and a visual matching engine rule, and various visual types corresponding to the metadata are obtained; third, one or more visual types are recommended to a user through a real-time display engine; fourth, graphs are synthetized to conduct visual graph display according to the visual type chosen by the user. According to the implementation method and system, intervention of complex data structures can be removed, a quick matching visual rule is provided, various reasonable visual display modes are recommended for the user according to marks, and artificial factors are shielded. The user does not need to judge which kind of visual type is more suitable, and a visual type marking mechanism can recommend the visual display mode to the user in real time.
Owner:CETC CHINACLOUD INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com