Log-based complex software system abnormal behavior detection method
A software system and detection method technology, applied in software testing/debugging, error detection/correction, hardware monitoring, etc., can solve problems such as inability to obtain the root cause, inability to accurately distinguish abnormal log statements, and disadvantageous resolution of exceptions, etc. Complete anomaly detection and localization method, convenient for anomaly troubleshooting and modification, and the effect of clear operation logic relationship
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
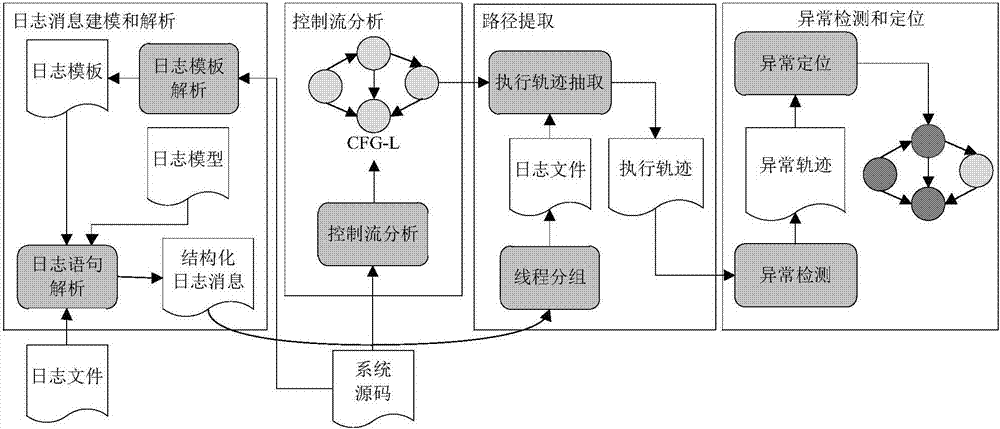
[0023] With the rapid development of science and technology, the scale of modern software systems has become larger, their functions more complete, and their structures more complex. In this case, once the software system fails, it may lead to a series of chain effects. At present, the abnormal behavior detection of some large-scale software systems mainly relies on manual investigation. This method is not timely, lacks pertinence, low efficiency and incompleteness in locating problems. In the prior art, there are also methods for detecting system abnormal behaviors based on analyzing logs, but these methods can only analyze the log statements when the system is abnormal, and it is difficult to obtain the log traces that lead to the exception, and it is impossible to analyze the abnormal behavior according to the abnormal log statements. Tracking, and clustering algorithms are used in some methods, and the clustering methods have certain instability.
[0024] In view of the a...
Embodiment 2
[0031] The log-based abnormal behavior detection method of a complex software system is the same as in embodiment 1. In step 1, analyze the source code of the software system to obtain the reachability relationship between log print statements, specifically including the following steps:
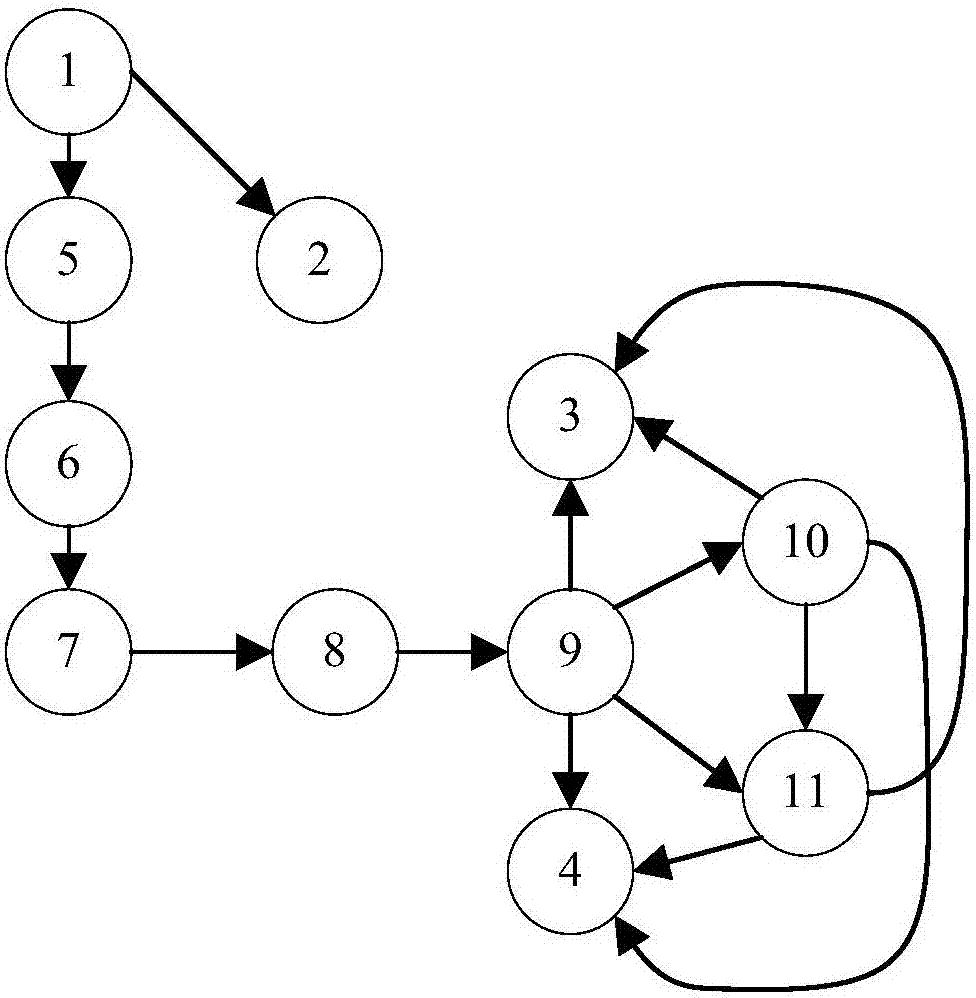
[0032] 1.1 Define the representation of control flow graph, reachability graph and log template
[0033] Definition 1: Control flow graph with function calls (Control flow graph with function calls): The control flow graph with function call information uses G F =(V F ,E F ) means that:
[0034] V F Represents the set of nodes in the control flow graph {v f1 ,v f2 ,...,v fn}, where each node is a base node, a log node, or a function call node.
[0035] E. F Represents the set of edges connecting vertices in the control flow graph {(v fi ,v fj ),(v fk ,v fl ),...}, each edge consists of a pair of ordered nodes (v fi ,v fj ) indicates that it is a control path or a path from v fi ...
Embodiment 3
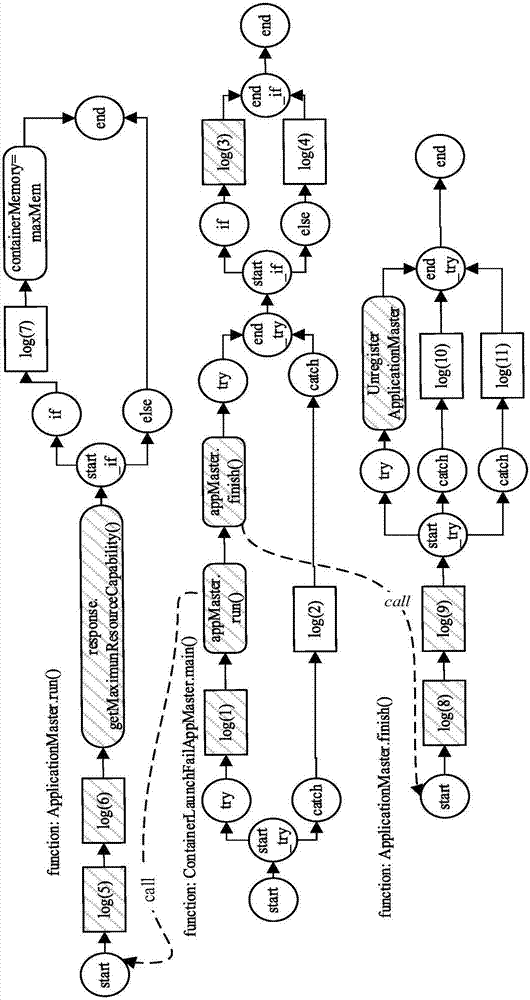
[0054] The log-based abnormal behavior detection method of a complex software system is the same as in embodiment 1-2. In step 2, the log statement is parsed, and the log template with the highest matching degree is associated with the log statement, specifically including the following steps:
[0055] 2.1 Define the representation of log messages and logs
[0056] Definition 3: Log Message (Log Message): It is a complete line of information describing the execution events of a specific system in a log file. The log message lm is represented by a five-tuple: lm=(ln,tm,lv,pv,ct) ,in:
[0057] ln indicates the line number of the log message in the log file, which is used to locate the exception.
[0058] tm represents the timestamp of the log message.
[0059] lv indicates the level of the log message, which can be DEBUG, INFO, WARN, ERROR and FATAL.
[0060] pv=(ls, tid) indicates the source information of the log message, where ls is the log template for printing the log st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com