Attack behavior real-time tracking and analysis method for cyber range
An analysis method and real-time tracking technology, applied in electrical components, transmission systems, etc., can solve the problems of high false negative or false positive rate, inability to score, long time for matching judgment, etc. High efficiency and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described below in conjunction with accompanying drawing:
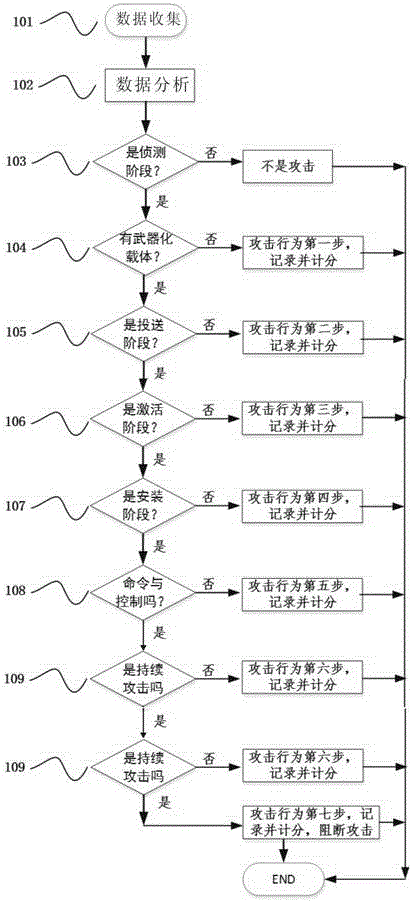
[0033] Such as figure 1 As shown, the attack behavior real-time tracking analysis method for network shooting range described in the present invention comprises the following steps:
[0034] (1) Data collection 101: Collect the link layer, network layer, and application layer data of all users in the network shooting range, and convert them into syslog format;
[0035] (2) Data Analysis 102: Use the "Program Behavior Algorithm" to analyze the collected data, find out the relationship between these data, mine the aggressive behavior with mutual relationship, and judge whether it is an intrusion or the Intrusion behavior is the basis for the first few steps in the attack kill chain;
[0036] (3) Determine whether the attack is the first step in the attack kill chain, that is, whether it is the detection stage 103, if yes, determine that the attack has reached the first step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com