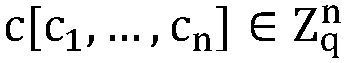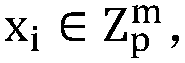Patents
Literature
44 results about "Information technology security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security, in information technology (IT), is the defense of digital information and IT assets against internal and external, malicious and accidental threats. This defense includes detection, prevention and response to threats through the use of security policies, software tools and IT services.
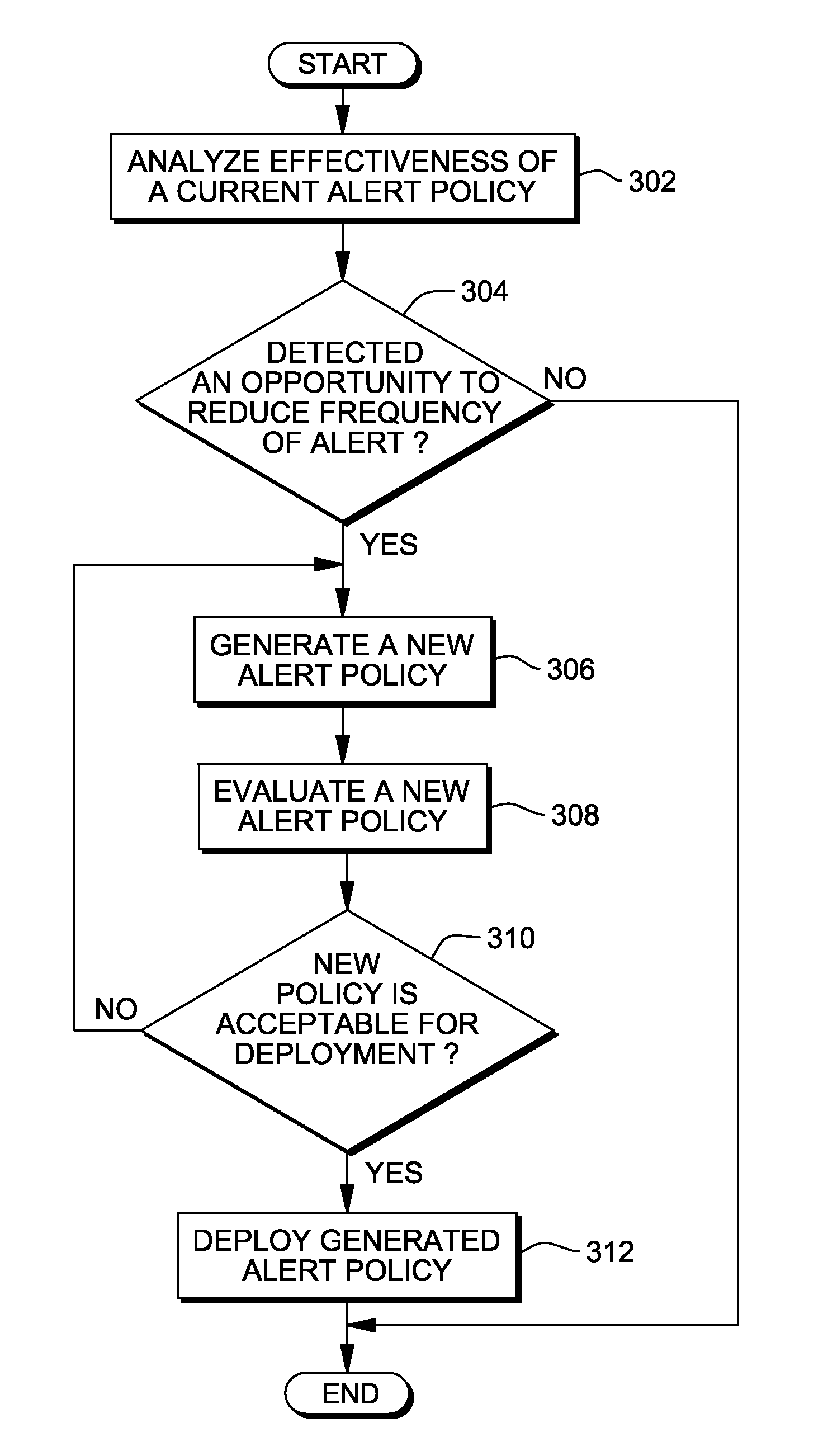
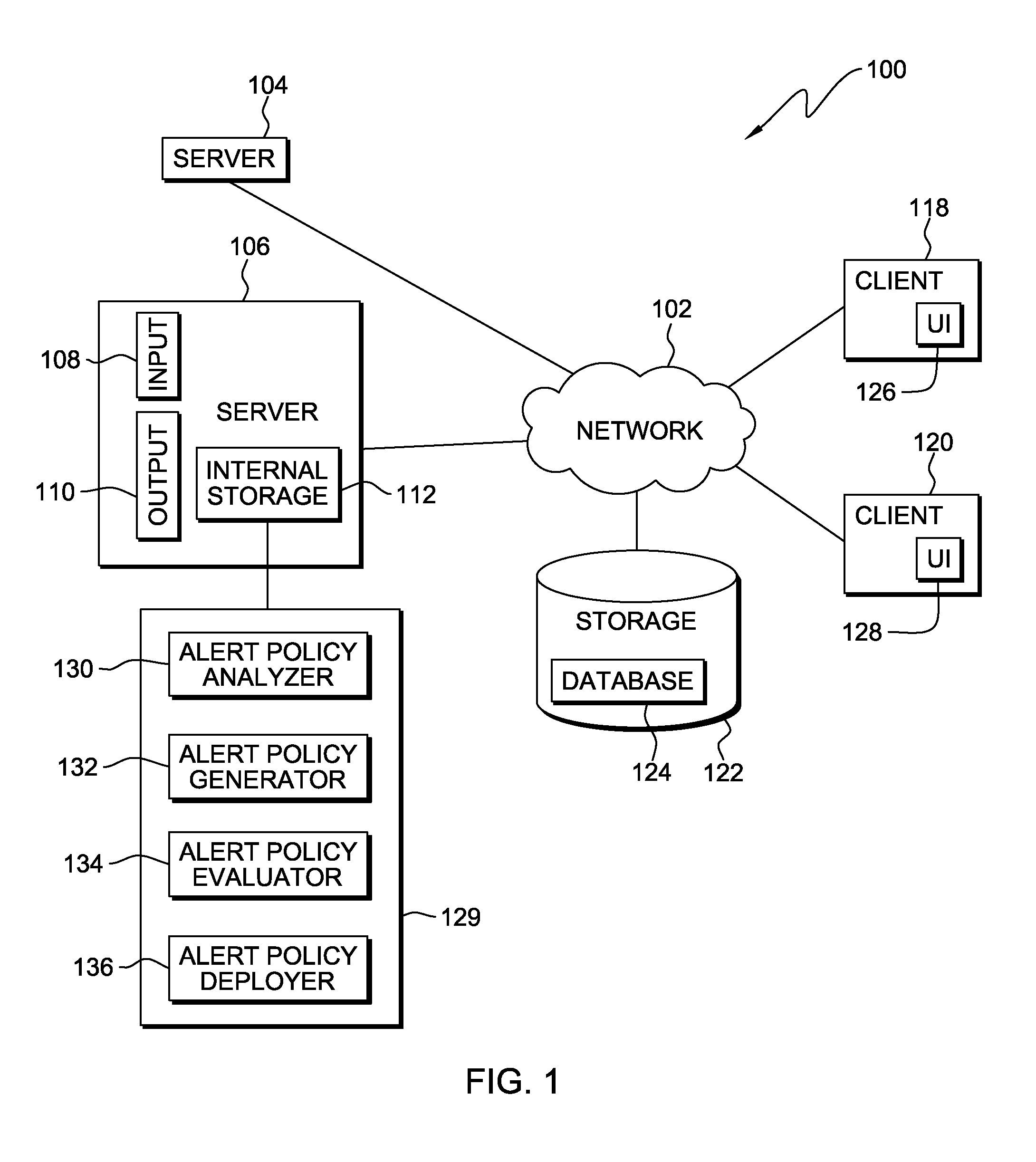
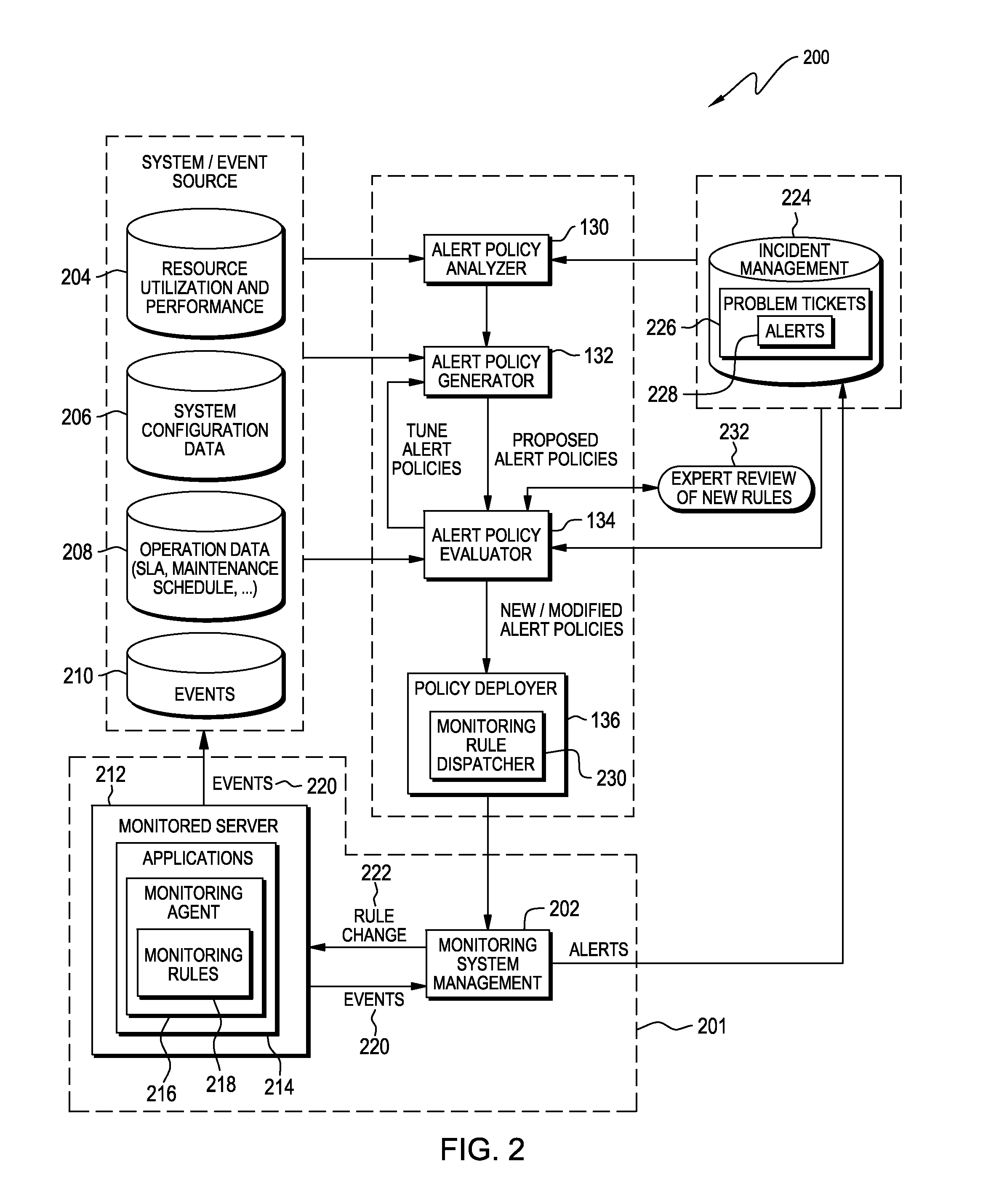
Reduction of alerts in information technology systems
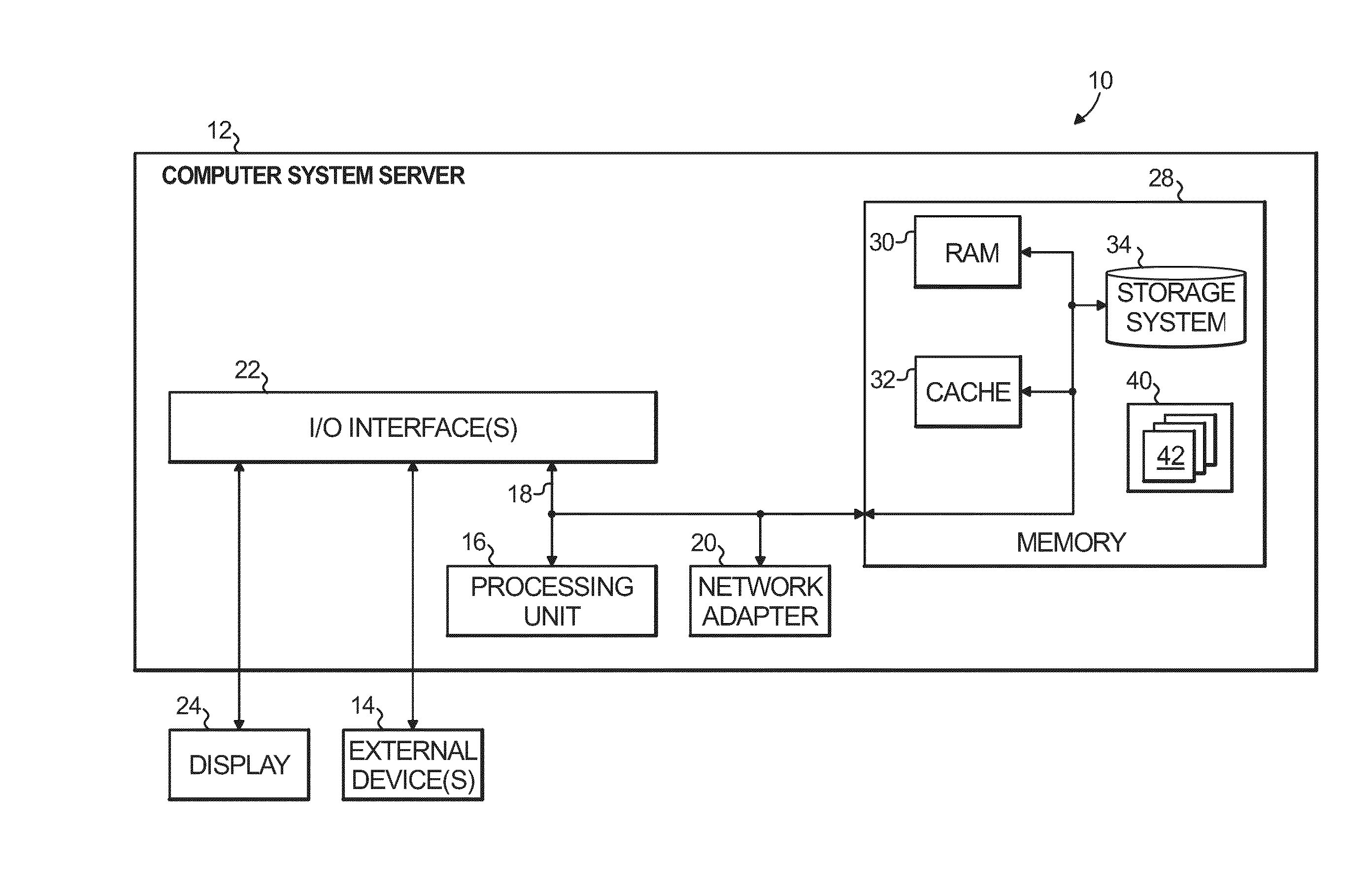
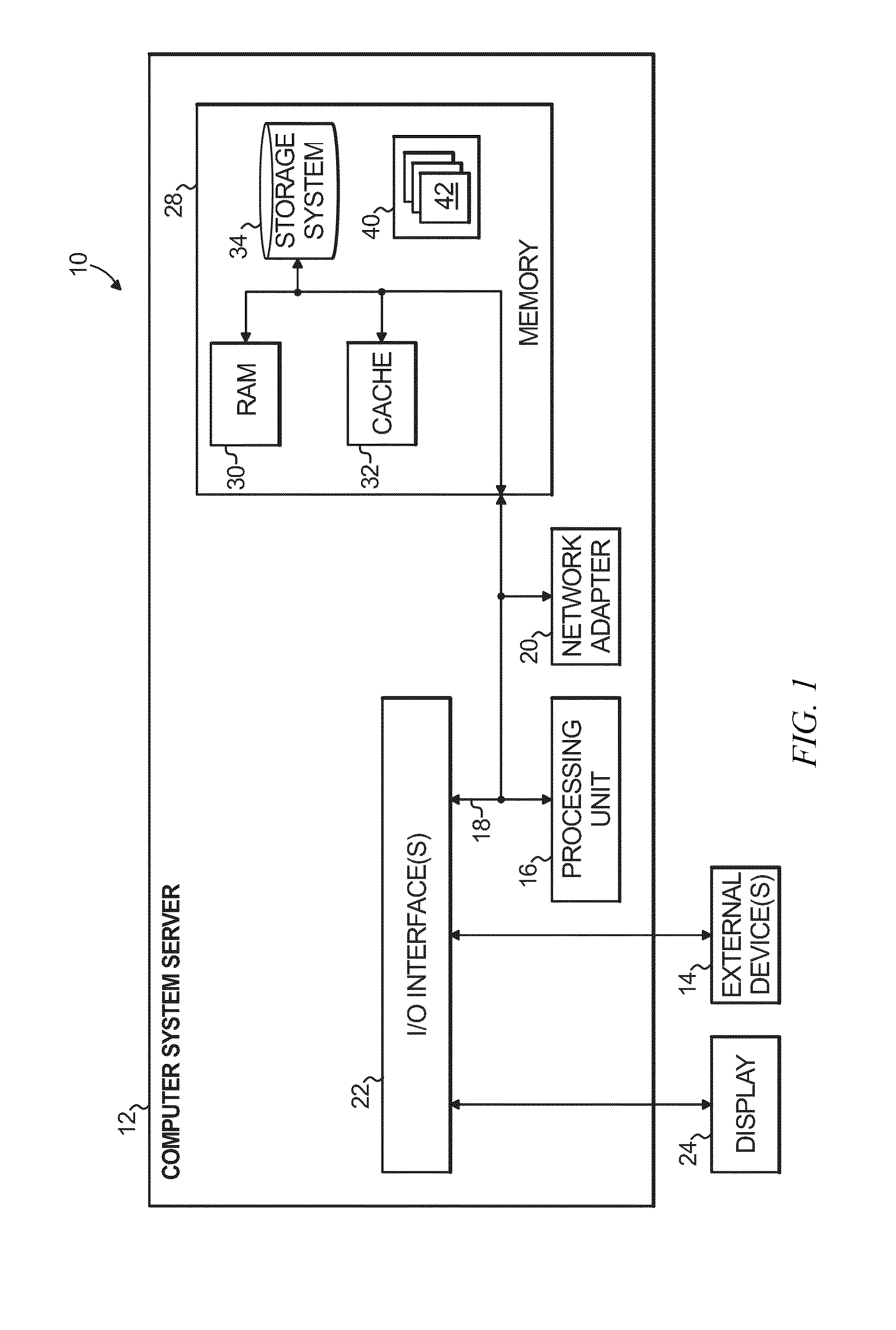
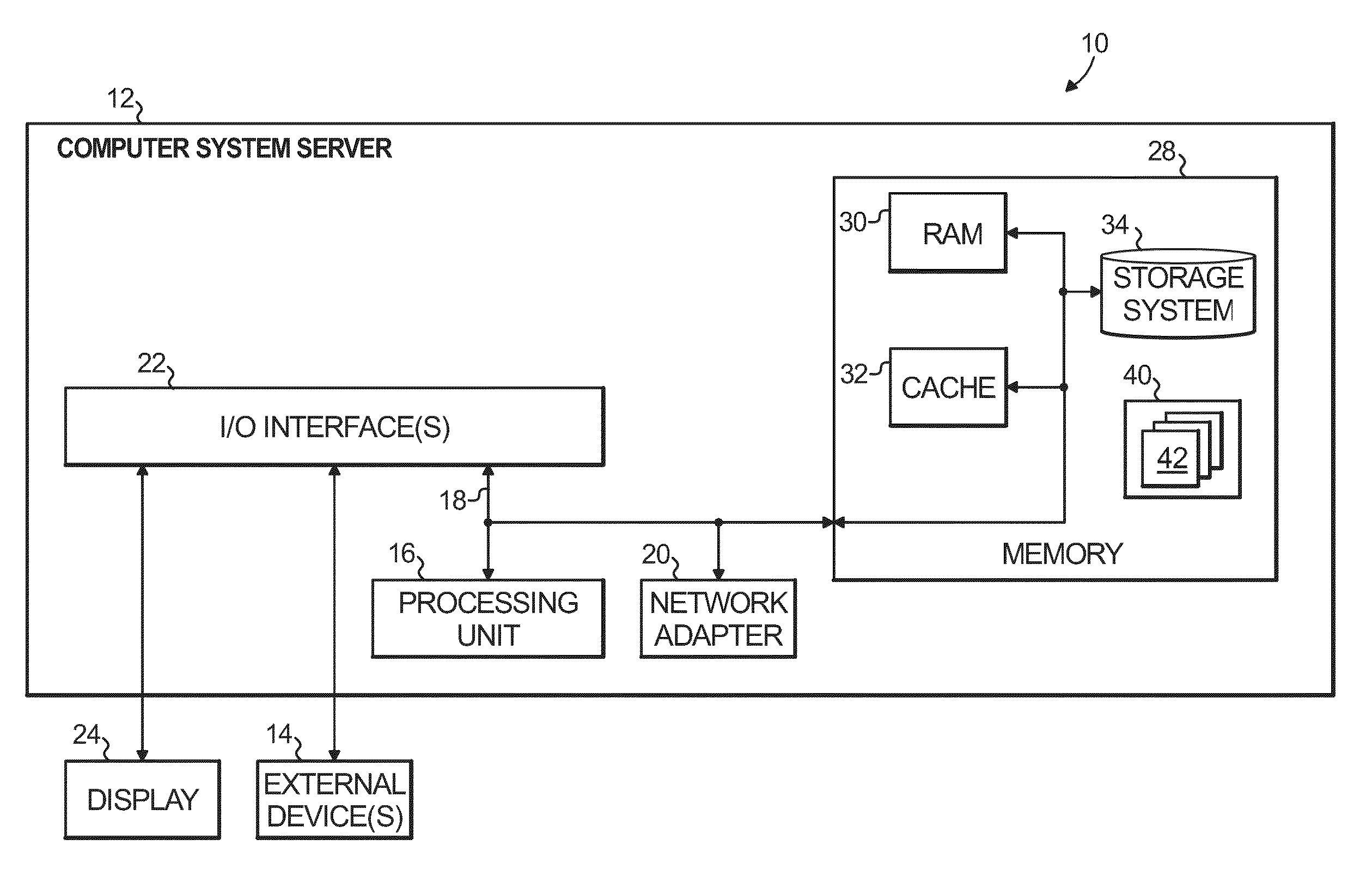
InactiveUS8380838B2Multiple digital computer combinationsNon-redundant fault processingService-level agreementStructure of Management Information
Aspects of the present invention dynamically reduce a frequency at which IT infrastructure automatically generates alerts. Historical data across a plurality of data sources in the IT infrastructure is analyzed. An opportunity to reduce the frequency at which the IT infrastructure automatically generates the alerts is identified. A new alert policy addressing the opportunity to reduce alert frequency is generated. An impact of the new alert policy on a set of predefined service level objectives (SLOs) and service level agreements (SLAs) is evaluated. The new alert policy is deployed in the IT infrastructure.
Owner:GLOBALFOUNDRIES INC
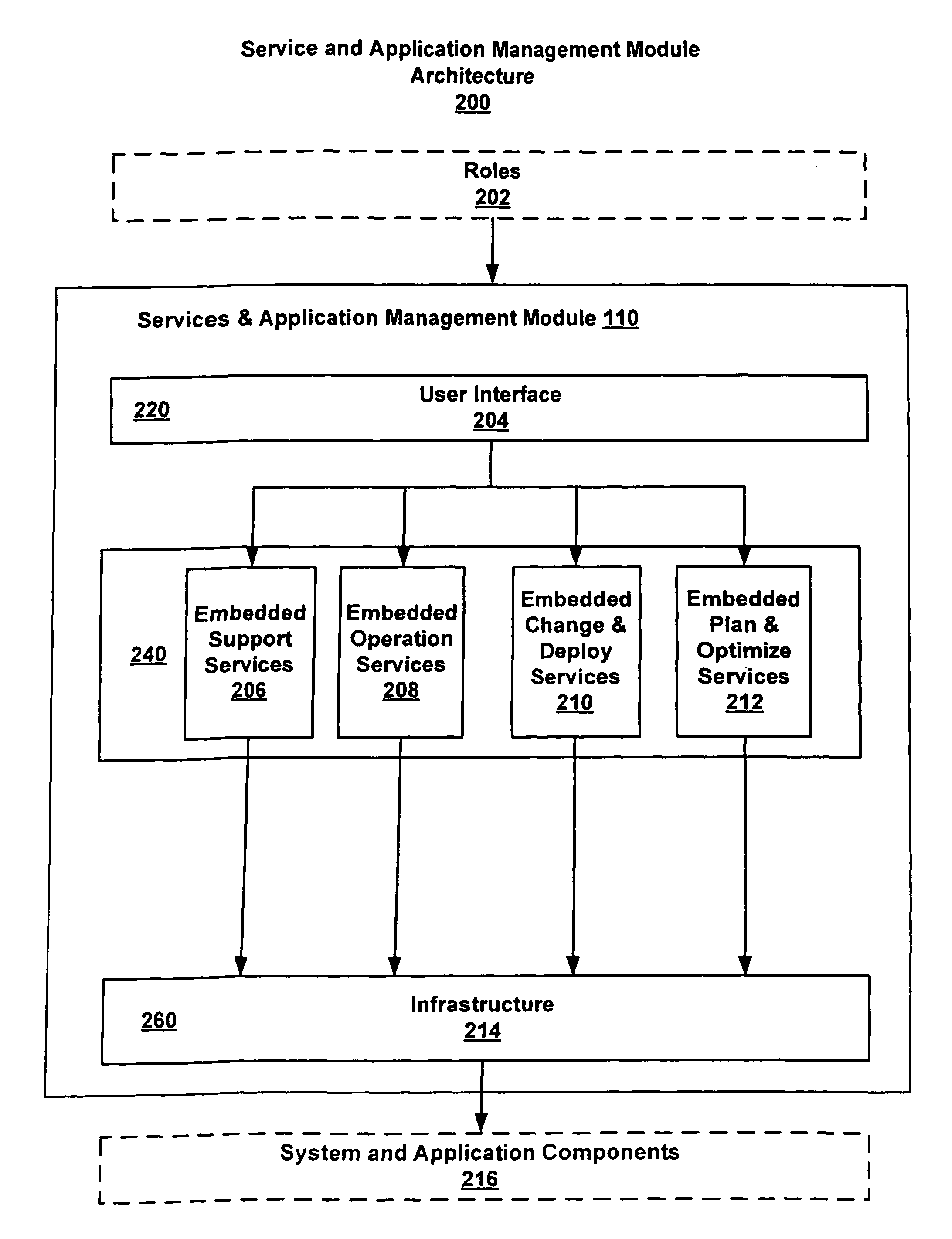
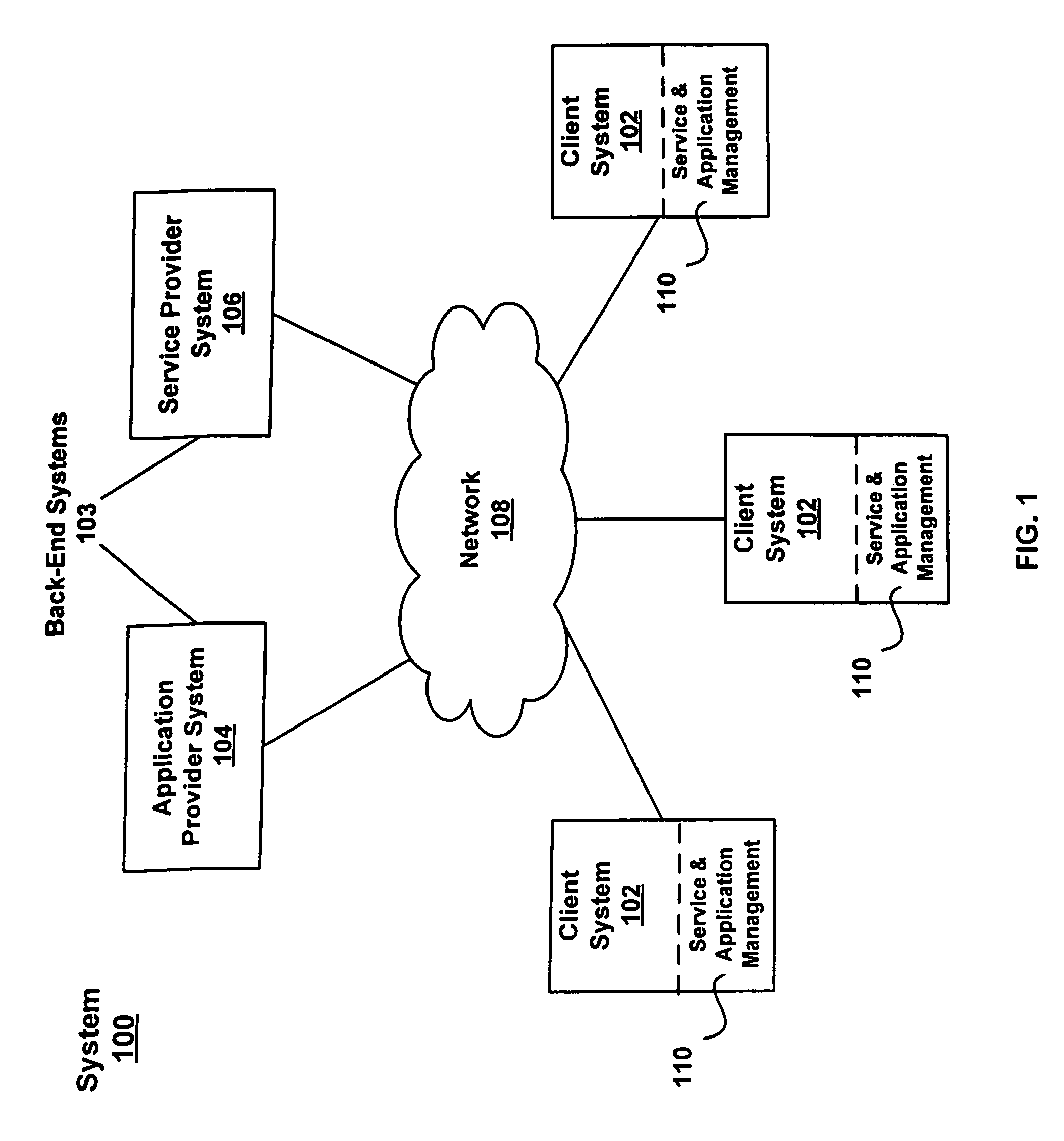
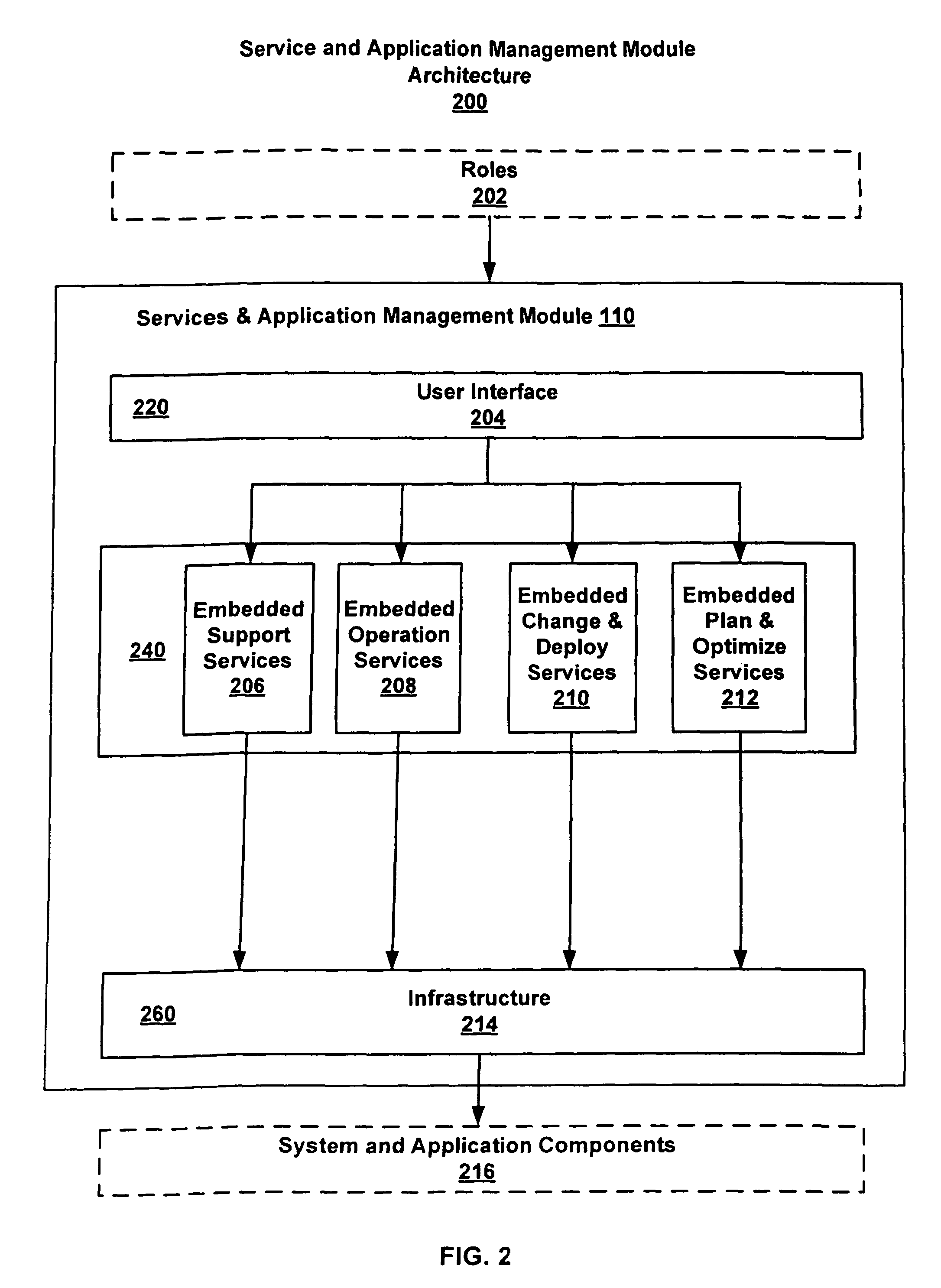
Service and application management in information technology systems
ActiveUS7930681B2Reduce investmentImprove functionalityError detection/correctionMultiprogramming arrangementsApplication portfolio managementApplication software
Systems and techniques for managing services and applications of a client system, such as an enterprise computer system, reduce the operational workload and optimize daily support process by deliverying embedded services in client system with direct connection of services into a back-end system so that back-end system processes can analyze client system information and provide detailed reports and analyses and with continuous (or regular) data exchange between client system and backend system to ensure efficient client system software processes. The embedded services can include support, operation, change and deploy, and plan and optimize services. The output of at least one of these services can be pushed to and displayed in a graphical user interface. A fact sheet provided with he graphical user interface contains on one page all the information that is needed to clearly show who is responsible for handling information technology problems, incidents, tasks, and service requests.
Owner:SAP AG
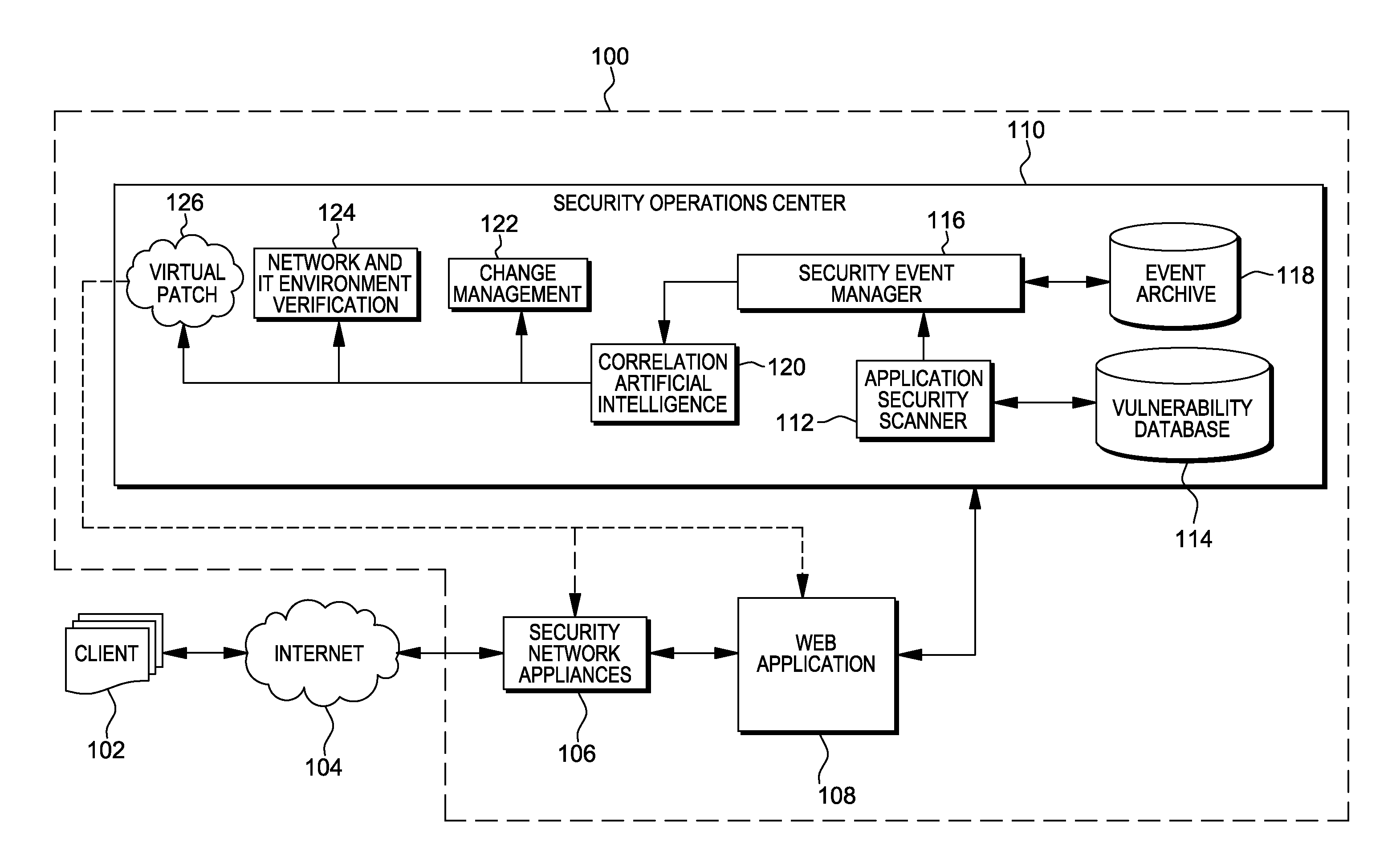
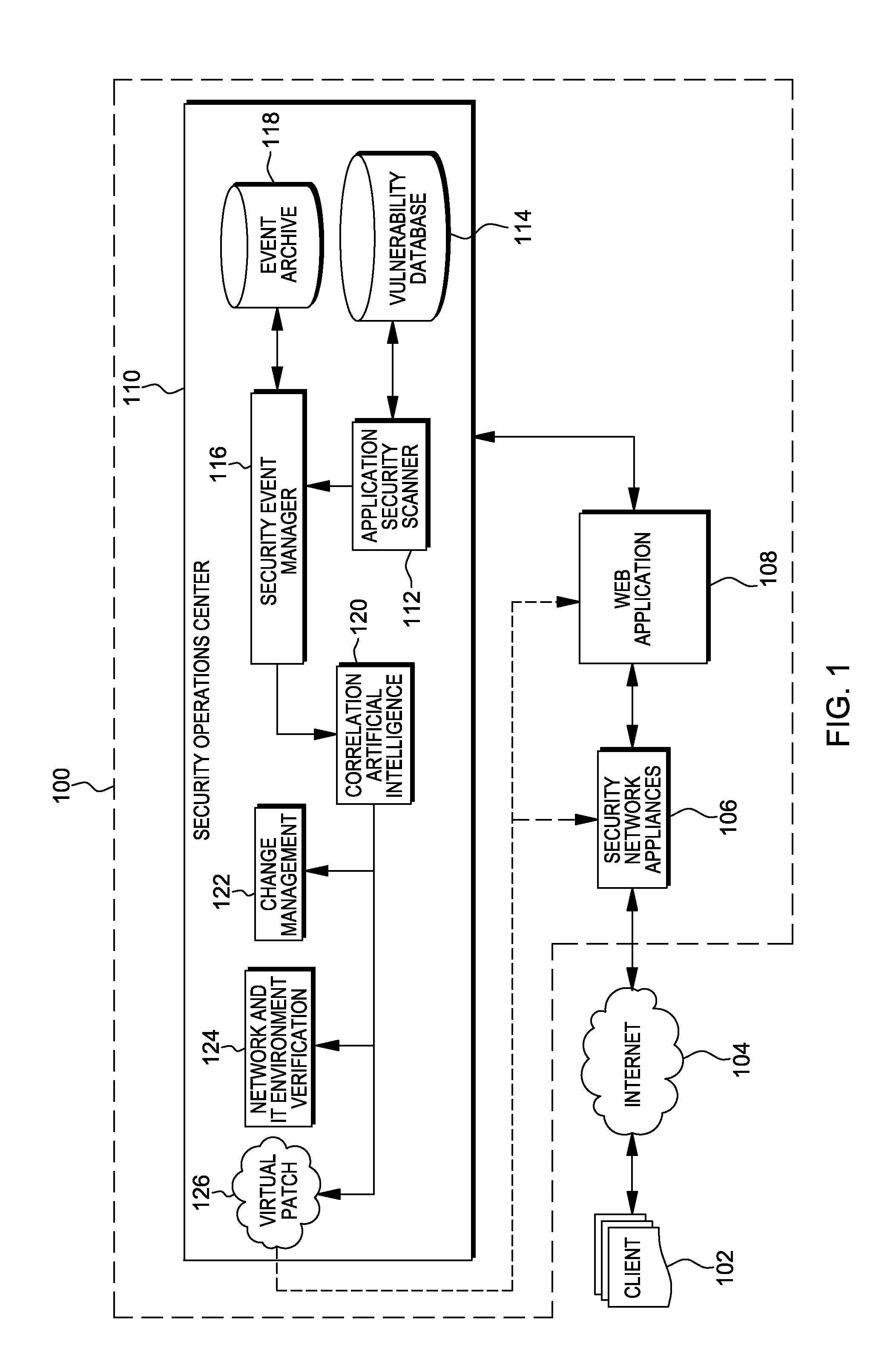
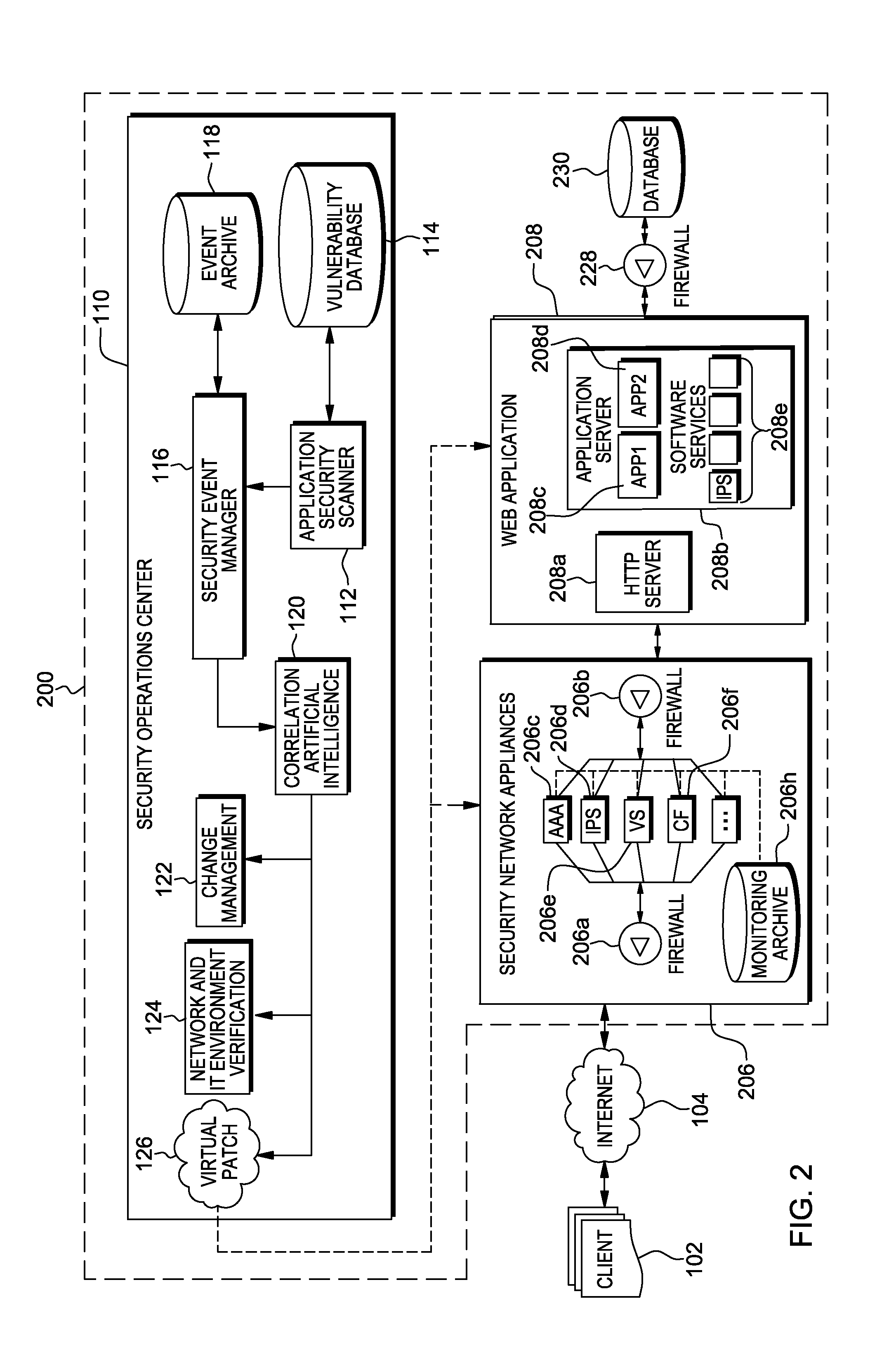
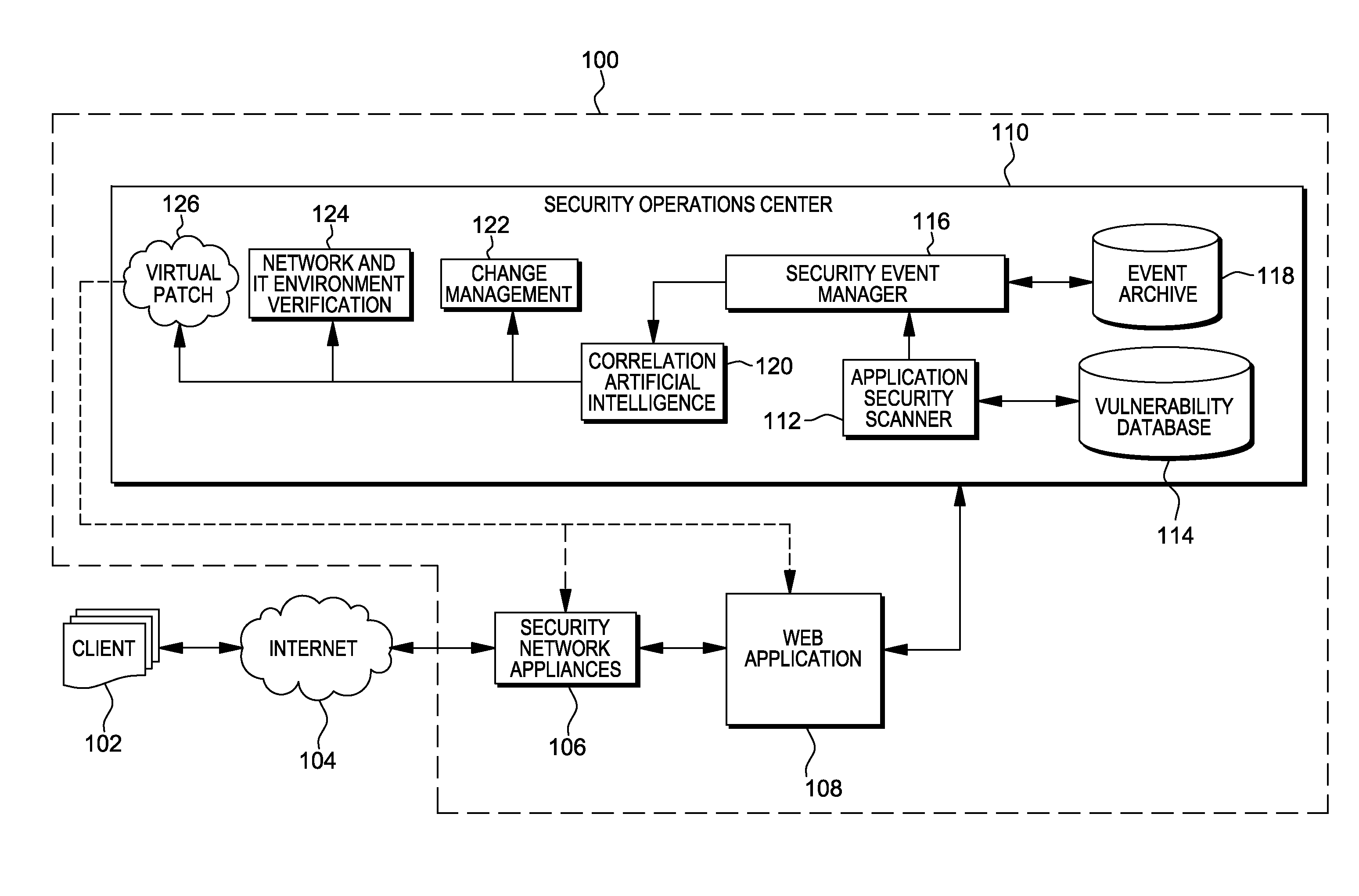
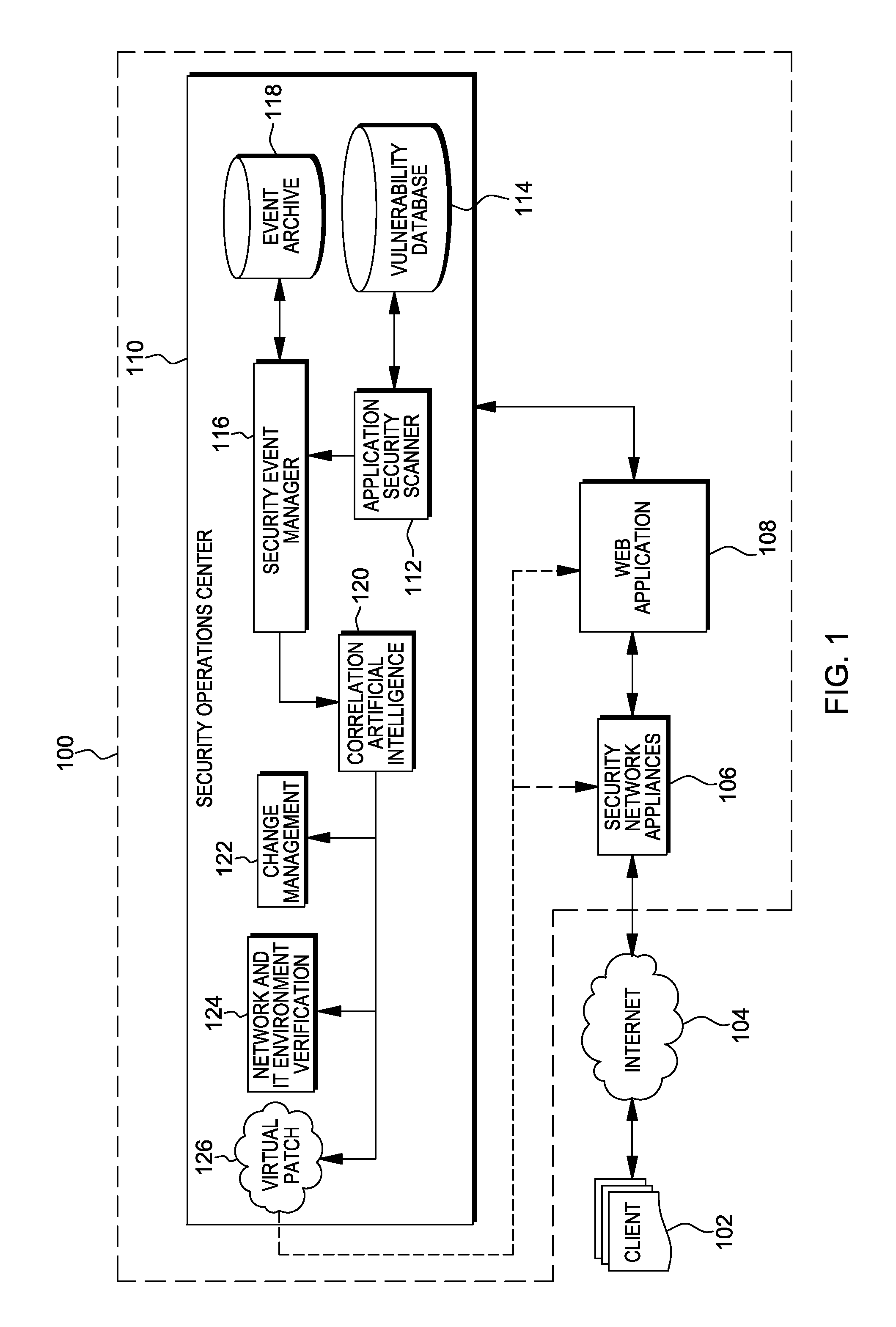
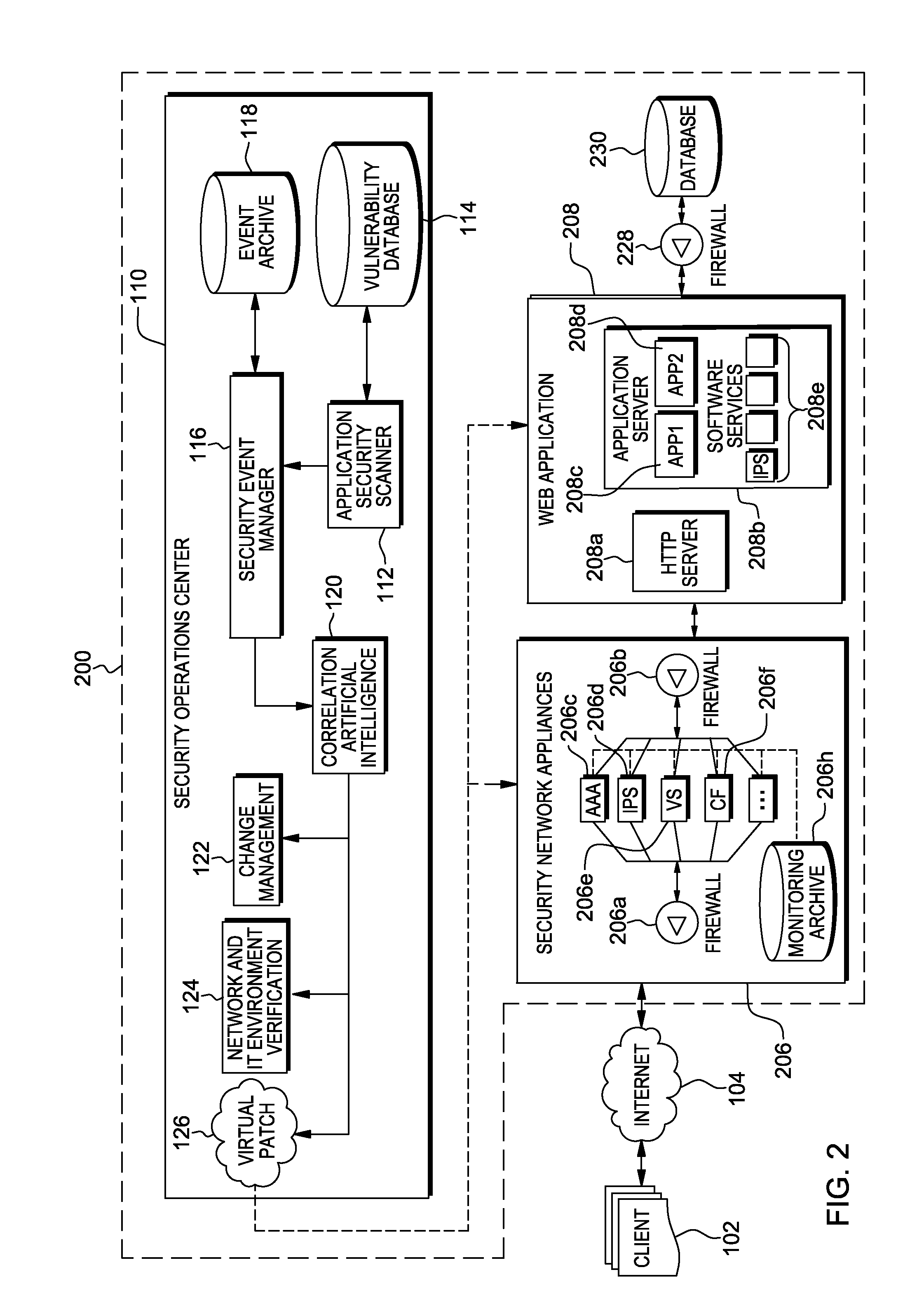
Web application exploit mitigation in an information technology environment
ActiveUS20130086688A1Improve protectionMemory loss protectionUnauthorized memory use protectionEnd to end securityProgram management
Methods, systems, and computer program products are provided herein for facilitating security in an information technology environment. Web application security vulnerabilities are discovered and addressed by means of virtual patches deployed to components of the information technology environment. An intelligent feedback loop is created to fill the void in the security of the web application when implemented in the specific information technology environment, thereby providing end-to-end security application management through dynamic, pre-emptive, and proactive security awareness and protection in the information technology environment. As new web application security vulnerabilities are discovered, the vulnerability is diagnosed and resolved to preemptively prevent exploitation of the security vulnerability.
Owner:FINJAN BLUE INC
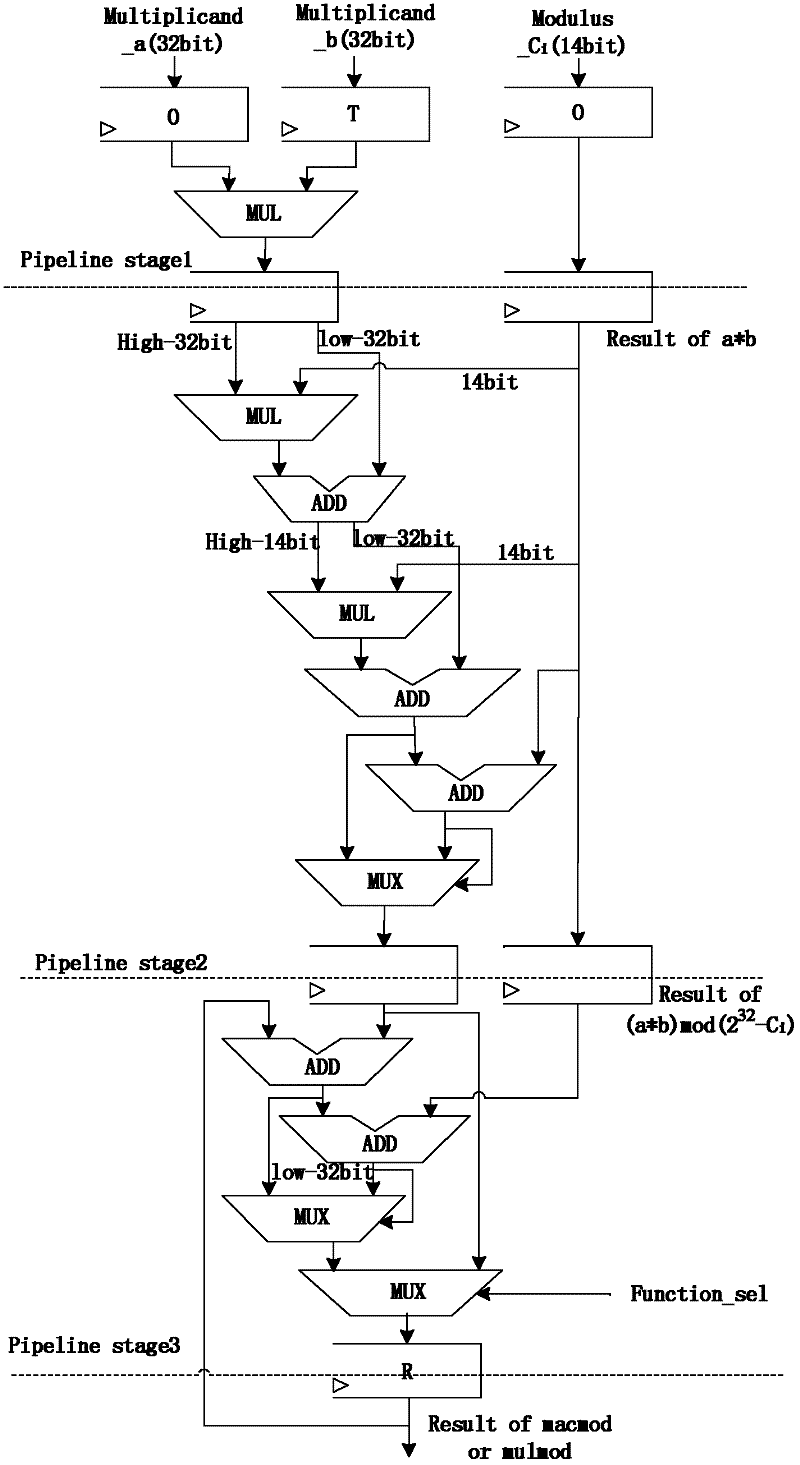
Method for processing RSA password based on residue number system and coprocessor
ActiveCN102231102AImprove decryption performanceImprove parallelismComputations using residue arithmeticCoprocessorPassword
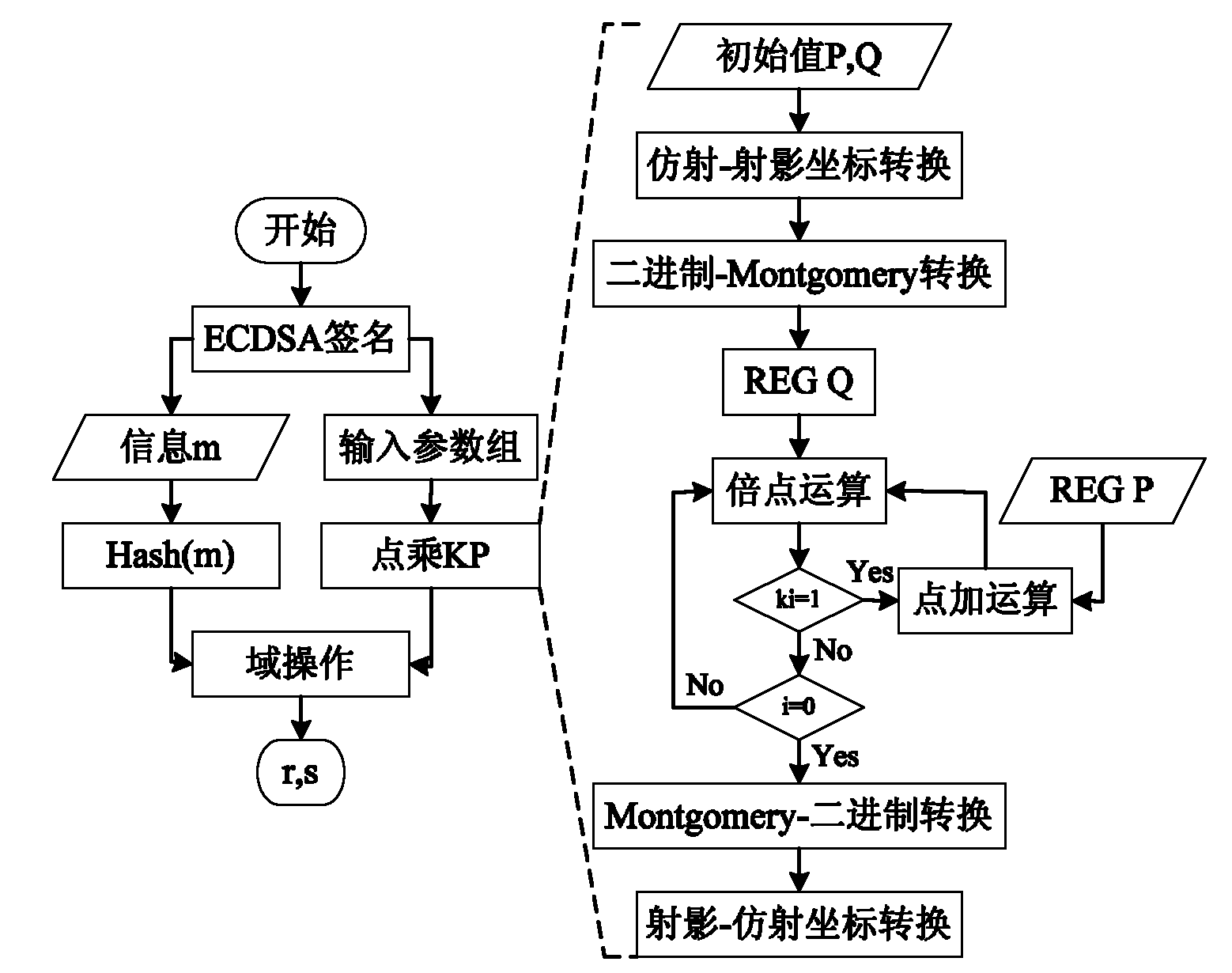
The invention relates to information technology security and microprocessor design. Aiming at increasing RSA (Ron Rivest, Adi Shamirh and LenAdleman) modular multiplication operation speed and improving RSA encryption and decryption performances, the invention provides the technical scheme as follows: a method for processing an RSA password based on a residue number system comprises the followingsteps of performs encryption and decryption operations by using an RSA algorithm and performing large-number modular exponentiation of the RSA algorithm by using an L-R (Left-Right) binary scanning modular power algorithm; an improved Montgomery algorithm is specifically as follows: 1024-bit large numbers with are expressed as numbers under the residue number system, namely two sets of 33 32-bit decimal numbers and one 32-bit number expressed under a redundancy base; an expression process is a mould solving process; the decomposed 32-bit decimal numbers respectively participate in 32-bit modular multiplication, modular multiplication accumulation and modular addition operation independently; furthermore, 32-bit data performs parallel execution operation without dependence; and the method disclosed by the invention is mainly applicable for the information technology security and microprocessor design.
Owner:PHYTIUM TECH CO LTD
Web application exploit mitigation in an information technology environment
ActiveUS8572750B2Improve protectionMemory loss protectionError detection/correctionEnd to end securityProgram management
Methods, systems, and computer program products are provided herein for facilitating security in an information technology environment. Web application security vulnerabilities are discovered and addressed by means of virtual patches deployed to components of the information technology environment. An intelligent feedback loop is created to fill the void in the security of the web application when implemented in the specific information technology environment, thereby providing end-to-end security application management through dynamic, pre-emptive, and proactive security awareness and protection in the information technology environment. As new web application security vulnerabilities are discovered, the vulnerability is diagnosed and resolved to preemptively prevent exploitation of the security vulnerability.
Owner:FINJAN BLUE INC
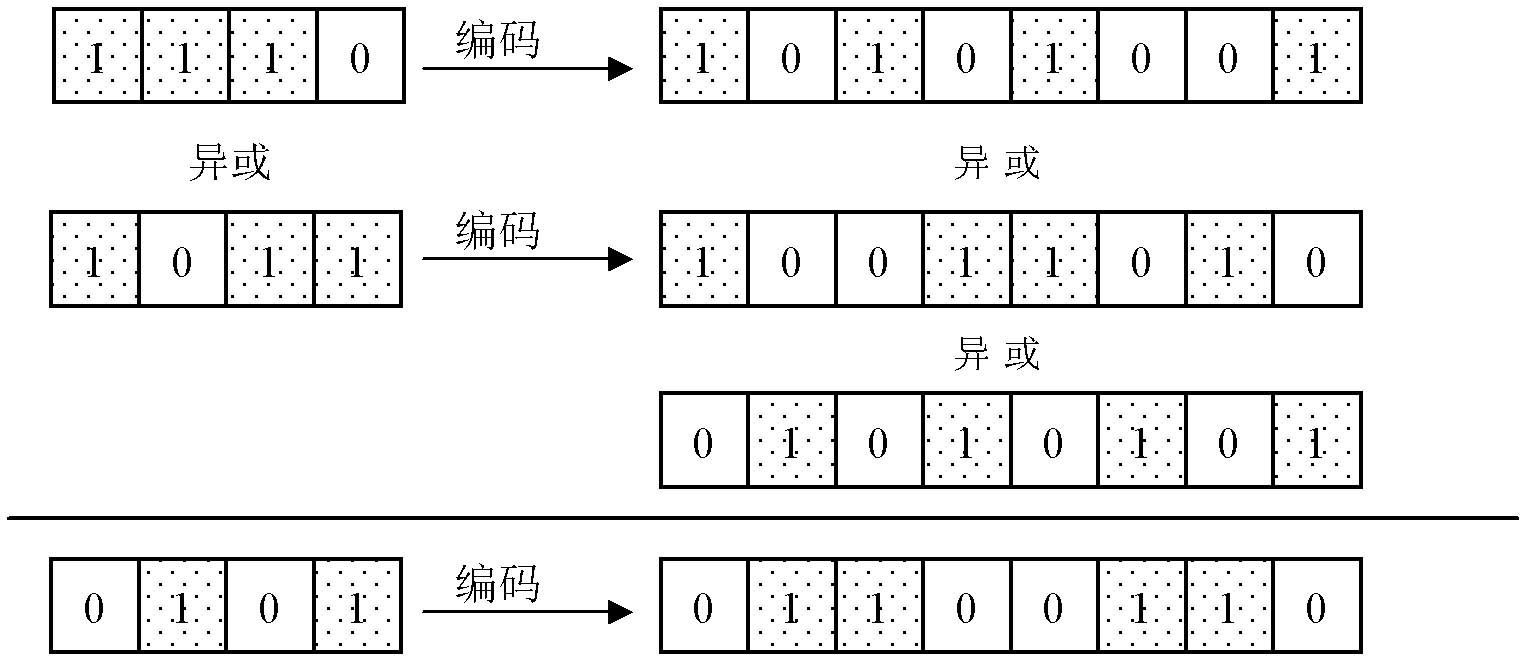
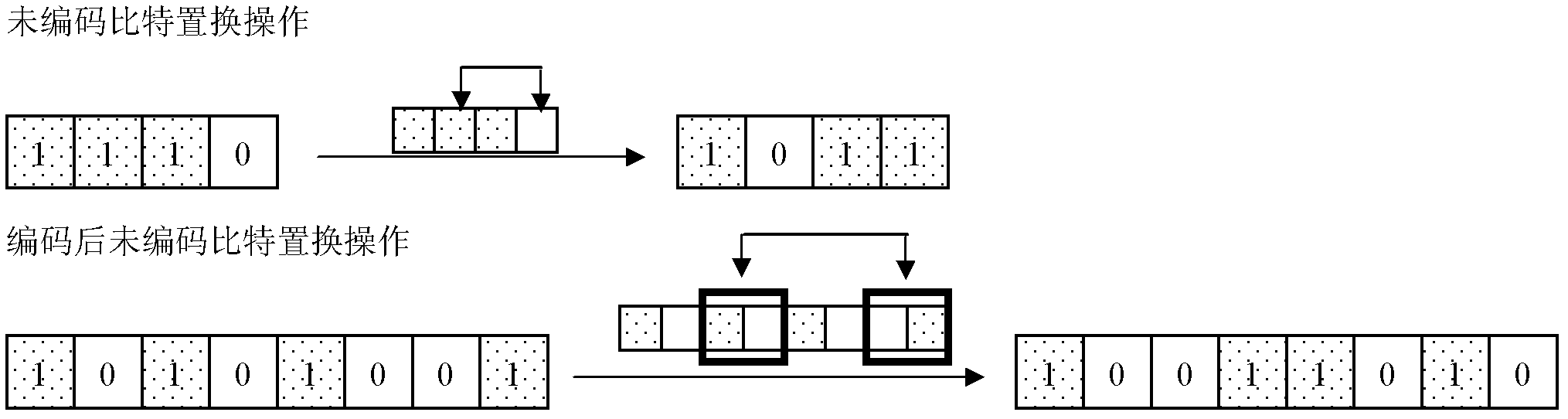
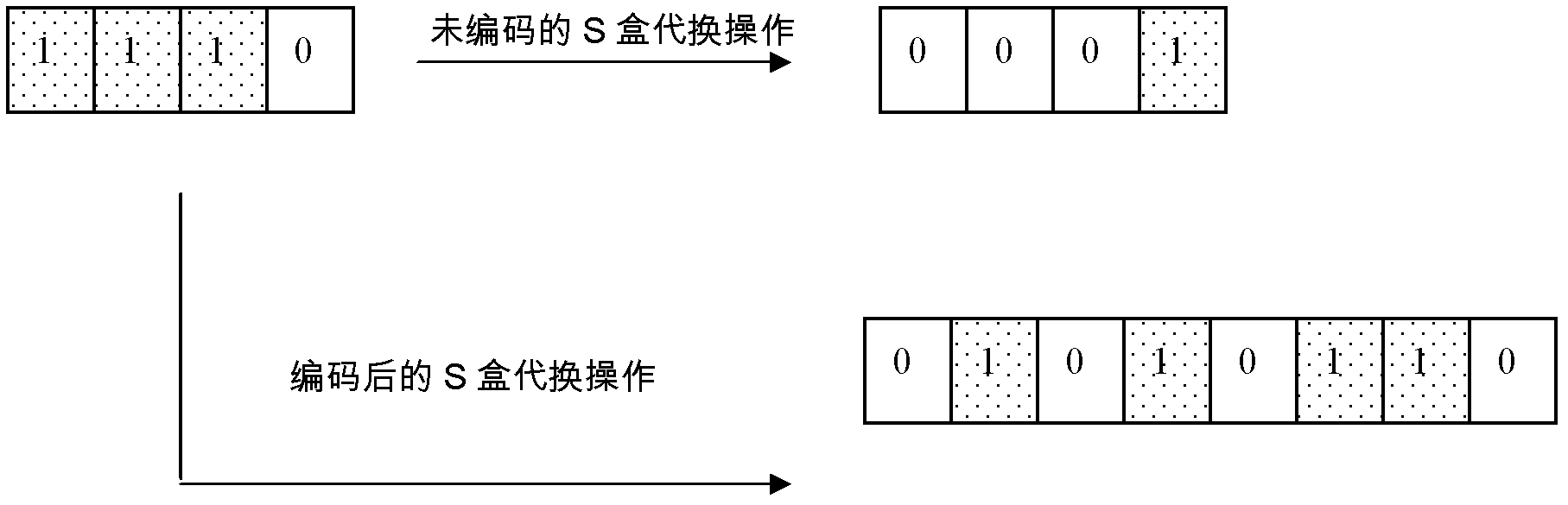
Cryptographic algorithm realization protecting method used for defending energy analysis attacks
InactiveCN102571331AIncrease success rateKey distribution for secure communicationPower analysisEncryption decryption
The invention discloses a cryptographic algorithm realization protecting method used for defending energy analysis attacks, and belongs to the field of information technology safety. According to the method, intermediate values of a cryptographic algorithm are protected through adding proper encoding and decoding steps to an execution process of the cryptographic algorithm. The method comprises the steps that firstly, before the algorithm, all data participating in the operation, including plain texts, secret keys and possible initial vectors, are encoded; afterwards, in the running process of the algorithm, cryptographic computing is conducted by using the encoded data and corresponding operations according to the steps of the cryptographic algorithm, so as to complete the encryption-decryption process; and finally, after the algorithm is finished, encoded result data are decoded, and normal output of the algorithm is obtained. The method has the advantages that only the intermediate values of the cryptographic algorithm are encoded, so as to guarantee that information is not leaked by the intermediate values; the input and the output of the algorithm are not changed, so that a running result of the algorithm is guaranteed to be accurate; and meanwhile, safety performance higher than that of a mask defense measure can be obtained, and the performance cost is lower.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
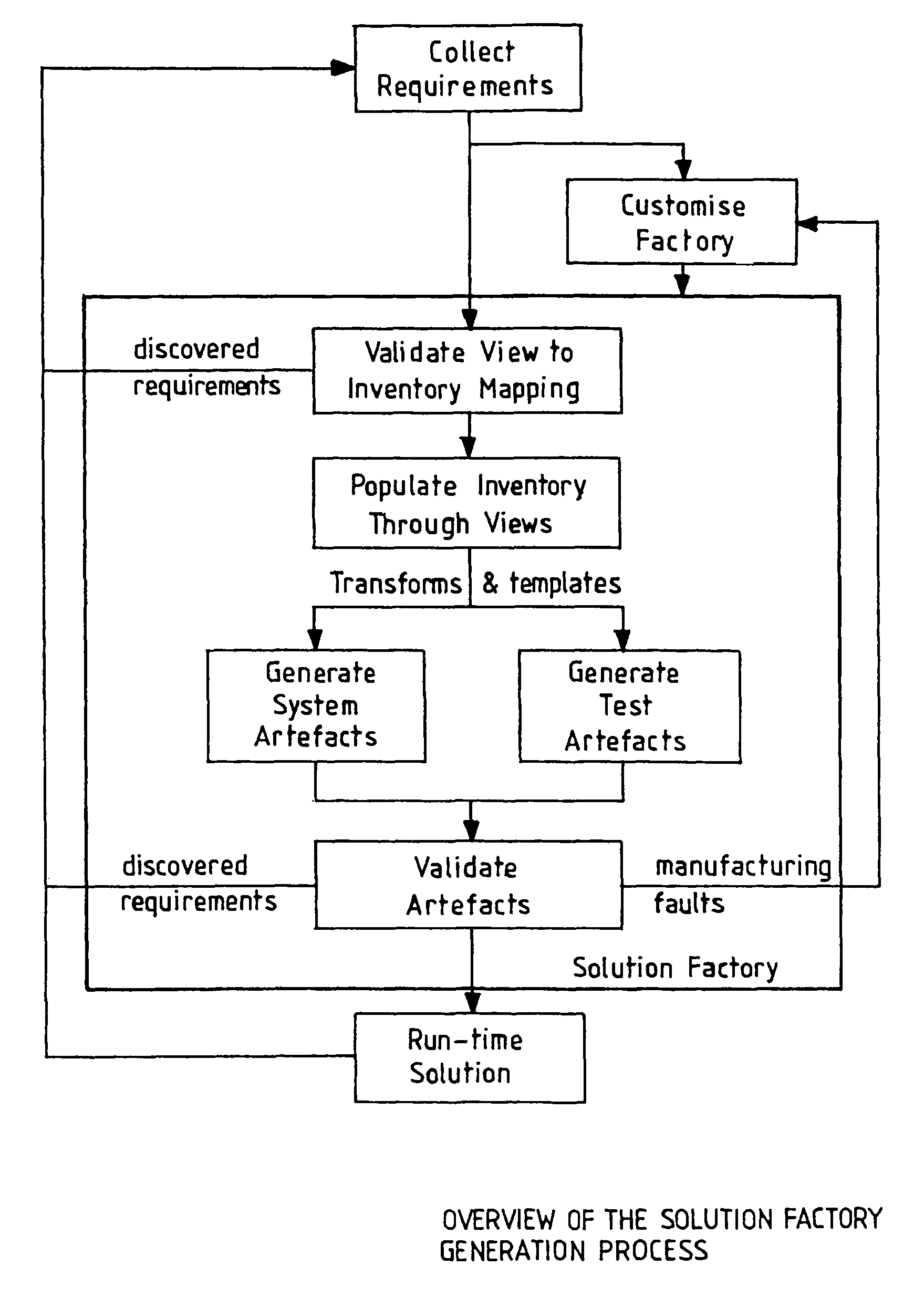
Integration of software into an existing information technology (IT) infrastructure
InactiveUS7949997B2Software designProgram loading/initiatingInformation technology educationStructure of Management Information
A method and apparatus for integrating a software application into an information technology (IT) infrastructure. An inventory is created using a Model-Driven Architecture (MDA) approach from the Object Management Group (OMG). The inventory includes information about: each component of the IT infrastructure, the software application, how each component communicates with each other component, and how the software application communicates with each component. Each element of information in the inventory has a single source and owner. The inventory is used to analyze the IT infrastructure and the software application during integrating the software application. From contents of the inventory, using the MDA approach from the OMG, artifacts that execute the integration are generated, and test programs are generated to verify that the integration is complete and correct. The inventory is progressively updated during and after the integration as more information about the IT infrastructure or the software application is developed.
Owner:INT BUSINESS MASCH CORP
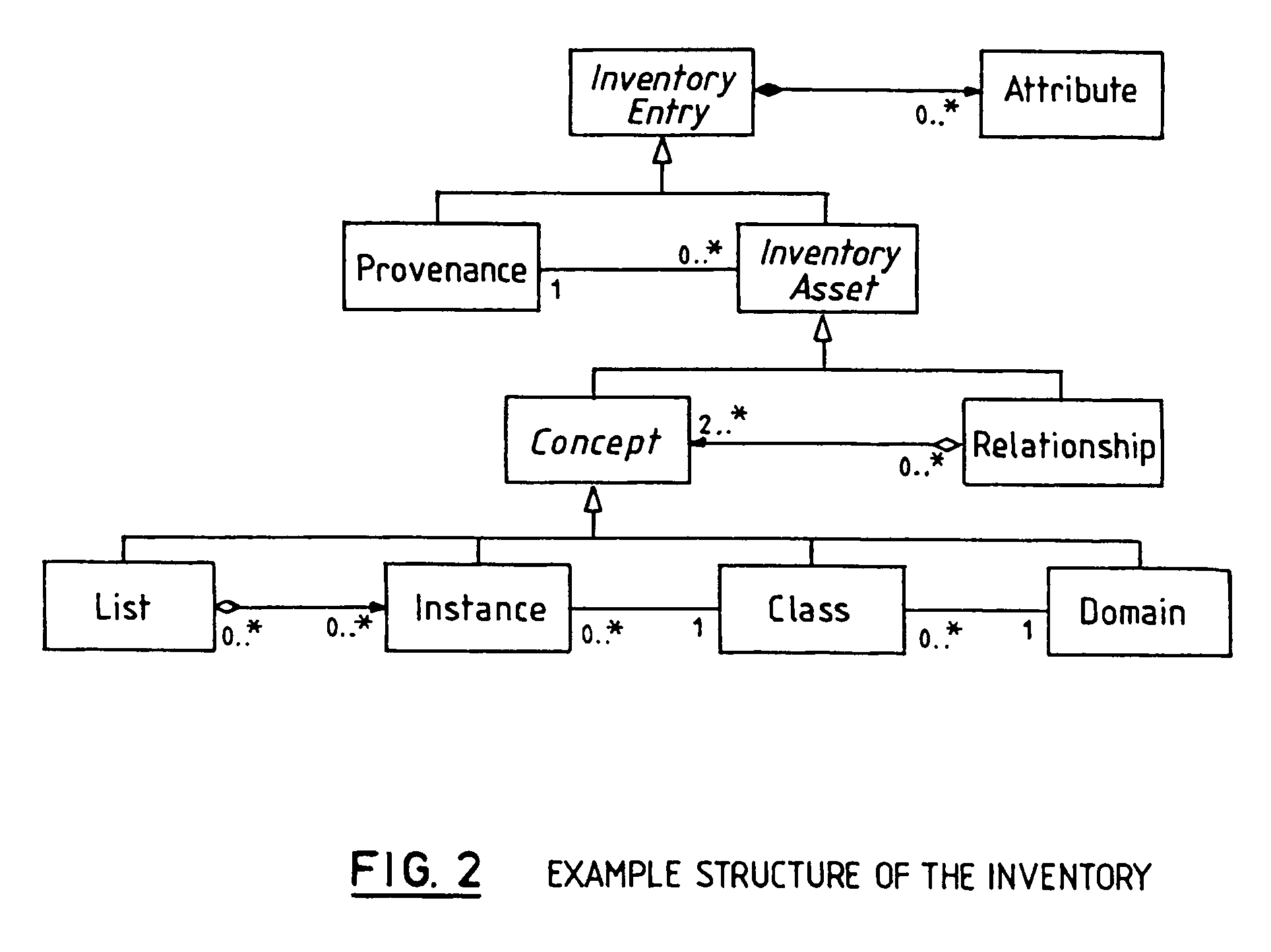
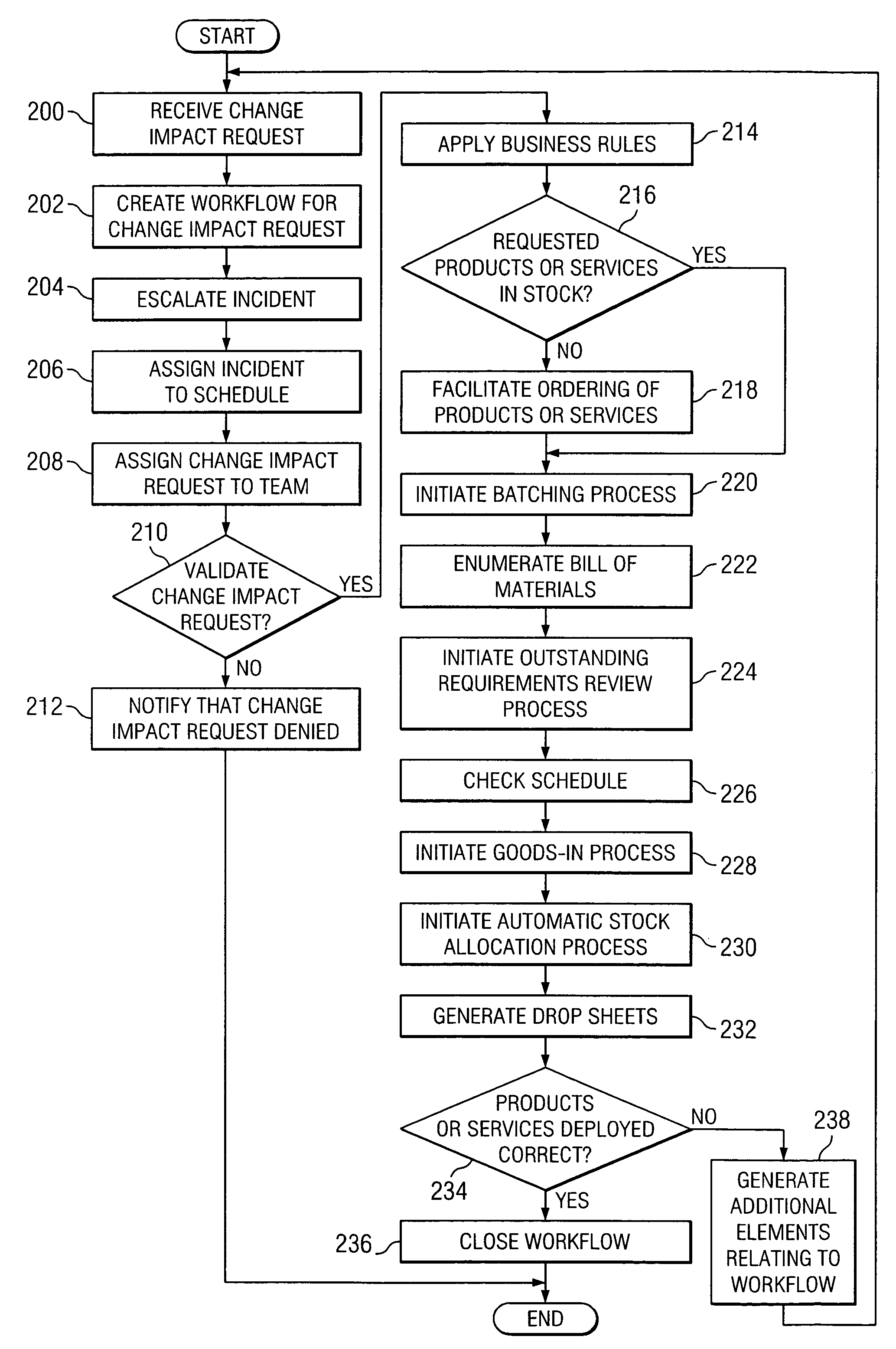
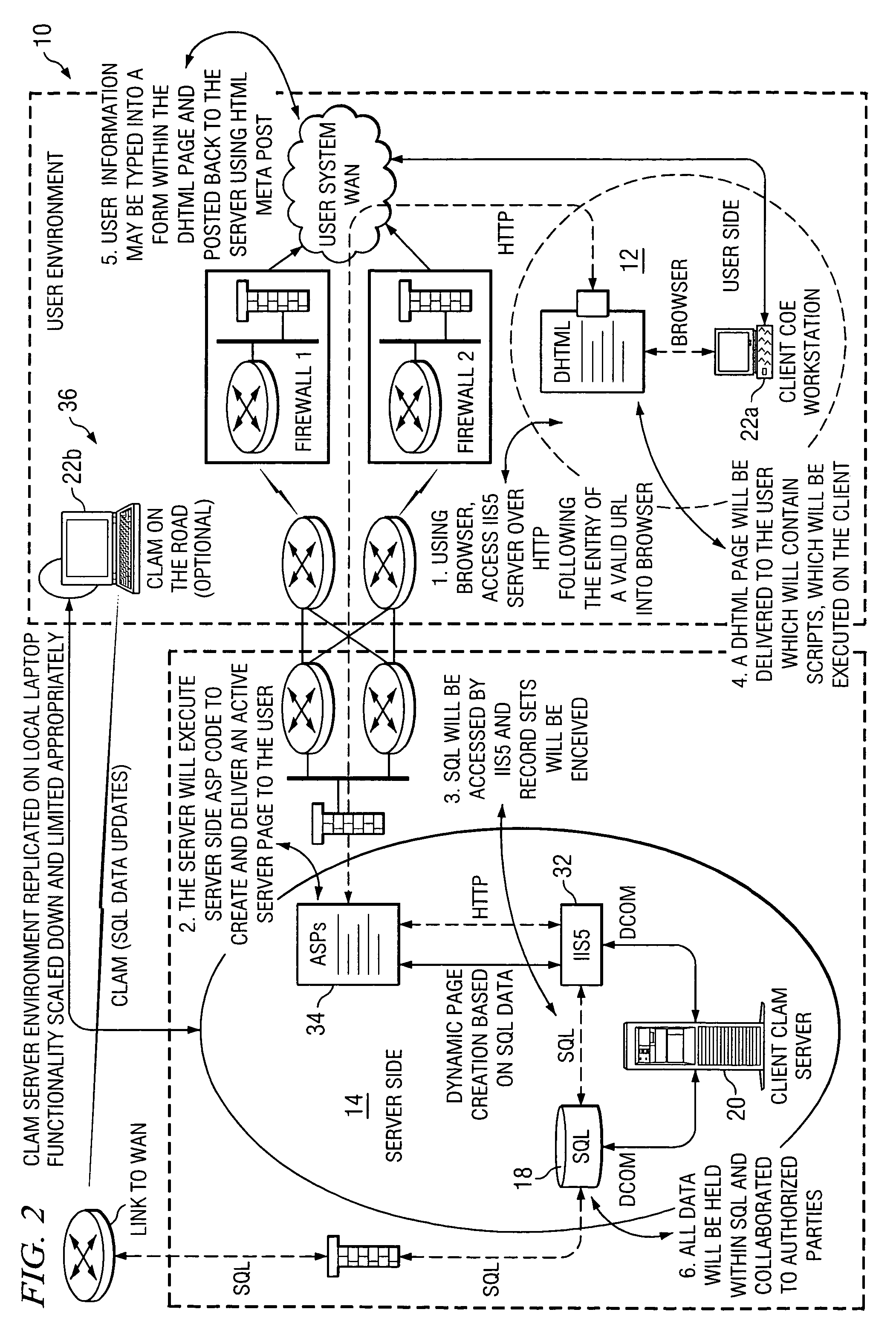
Managing information technology (IT) infrastructure of an enterprise using a centralized logistics and management (CLAM) tool
InactiveUS8285578B2Disadvantages can be reduced eliminatedReducing and eliminating ambiguity and misunderstandingInstrumentsLogistics managementKnowledge management
In one embodiment, a process for managing information technology (IT) infrastructure of an enterprise includes: (1) capturing and storing IT infrastructure information regarding the IT infrastructure of the enterprise; (2) defining a plurality of roles within the enterprise, each role specifying a particular job function within the enterprise; (3) associating items of IT infrastructure with roles within the enterprise such that each role is associated with one or more predetermined items of IT infrastructure; (4) assigning roles to one or more employees of the enterprise such that each of the one or more employees is associated with one or more roles and is assigned the one or more predetermined items of IT infrastructure associated with each of these one or more roles; (5) automatically modeling a change in the IT infrastructure for one or more impacted employees; and (6) automatically initiating deployment of one or more IT infrastructure assets for the one or more impacted employees by organizing delivery of the one or more IT infrastructure assets to the one or more impacted employees to implement the change modeled.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Linear SVM model training algorithm for privacy protection based on vector homomorphic encryption
ActiveCN108521326AGuaranteed confidentialityPrivacy protectionCharacter and pattern recognitionCommunication with homomorphic encryptionPlaintextData set
The invention discloses a linear SVM model training algorithm for privacy protection based on vector homomorphic encryption and belongs to the field of information technology security. The method comprises the following steps: step 1, a user encrypts a training data set by using a vector-based homomorphic encryption scheme VHE and sends the encryption result to a server; step 2, the server calculates the encryption result, obtains a ciphertext linear kernel function matrix and returns the ciphertext linear kernel function matrix to the user; step 3, the user decrypts the ciphertext linear kernel function matrix to obtain a plaintext linear kernel function matrix and sends the plaintext linear kernel function matrix to the server; step 4, the server adopts a ciphertext SMO algorithm to train the plaintext linear kernel function matrix and returns the training result to the user.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
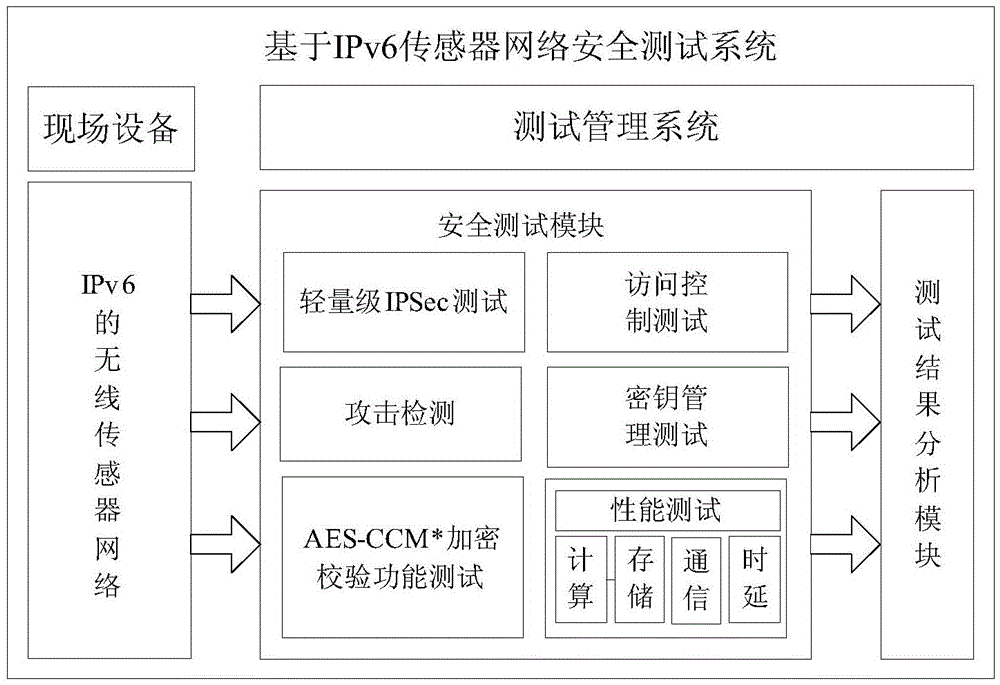
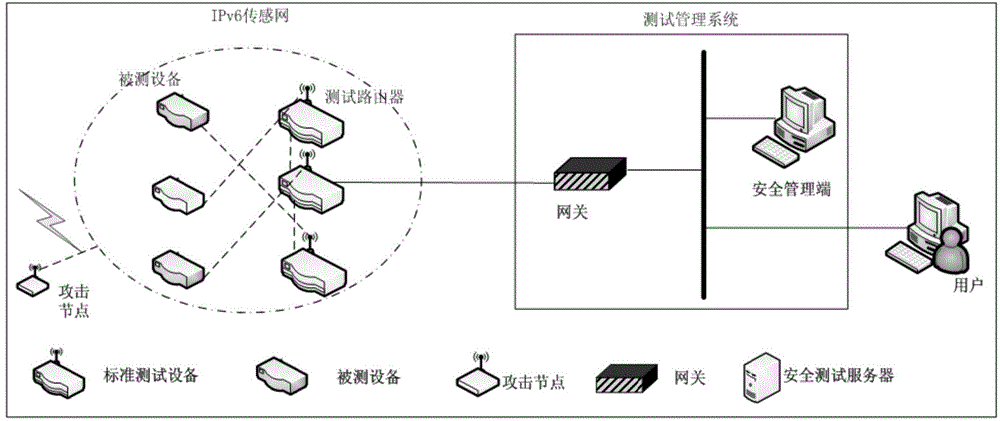
Safety test system based on IPv6 wireless sensor network
ActiveCN104837150ASimple configurationEasy to operateSecurity arrangementTest managementNetwork attack
The invention discloses a safety test system based on an IPv6 wireless sensor network. The system comprises a safety management terminal, a gateway and an IPv6 sensor network. A test management system is formed by the safety management terminal and the gateway, and is integrated with safety test mechanisms, such light-weight IPSec, access control, key management, AES-CCM* encryption and verification, etc. The test management system also has an IPv6 sensor network attack detection function, and is capable of analyzing the performance of the network after the safety functions are added, so that safety test management is achieved. The safety test system provided by the invention is simple to configure and easy to operate in a test process, and is capable of detecting whether the safety functions in the IPv6 sensor network are realized and meet requirements according to corresponding standards of safety. Besides, the safety test system is capable of determining an assessment assurance level, specified in the information technology safety assessment criteria, of the IPv6 sensor network according to the test result.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
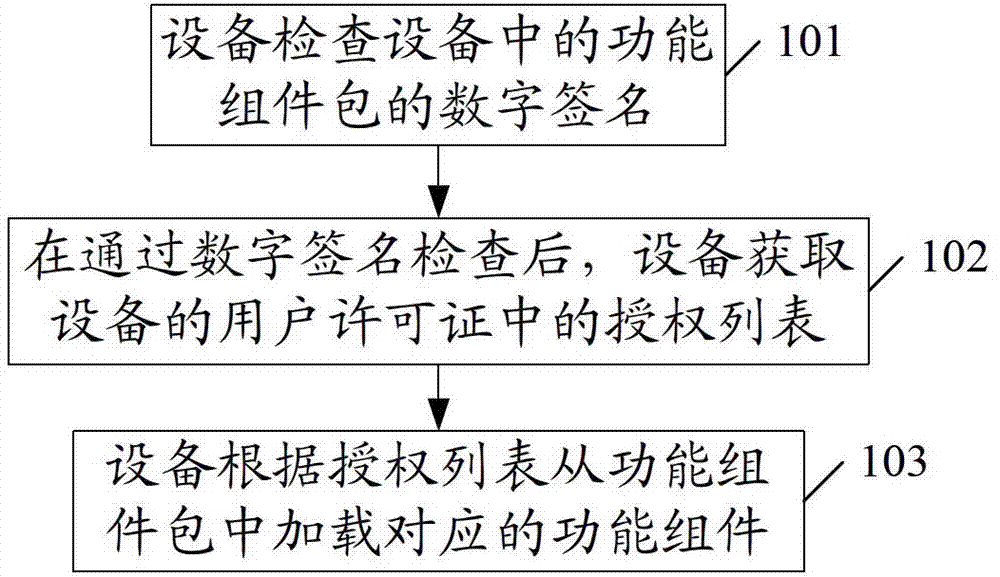
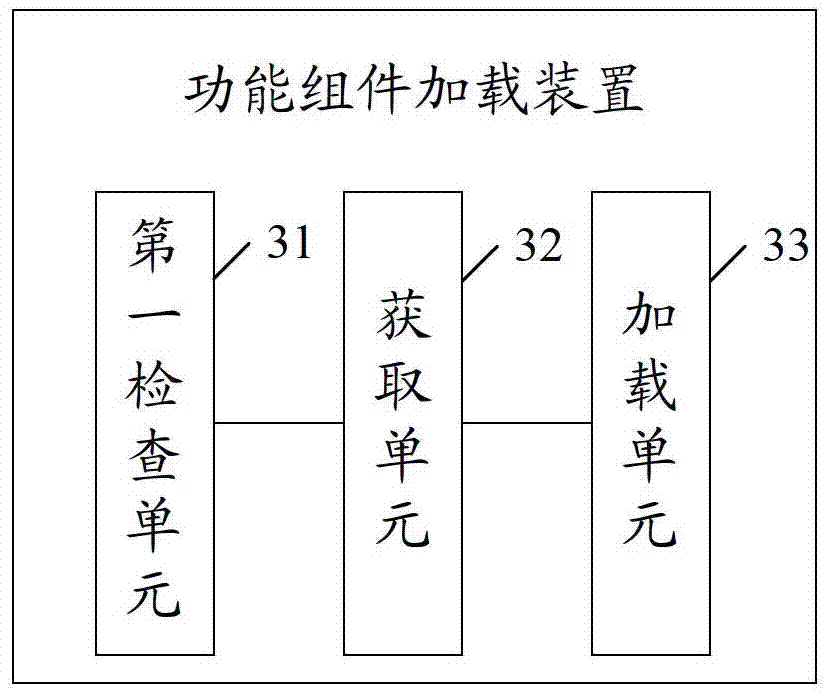
Functional component loading method and device
ActiveCN102930184AImprove integrityImprove information technology securityProgram/content distribution protectionComputer hardwareDigital signature
The embodiment of the invention discloses a functional component loading method and device, which relate to the field of electronic equipment, are capable of carrying out effective authorization control on equipment functions and can improve the information technology safety of equipment manufacturers. The method comprises the following steps of examining a digital signature of a functional component packet in equipment; acquiring an authorization list in a user license of the equipment after examining the digital signature; and loading a correspondent functional component from the functional component packet according to the authorization list. The method and the device are mainly applied to the loading process of functional components of the electronic equipment.
Owner:HUAWEI TECH CO LTD
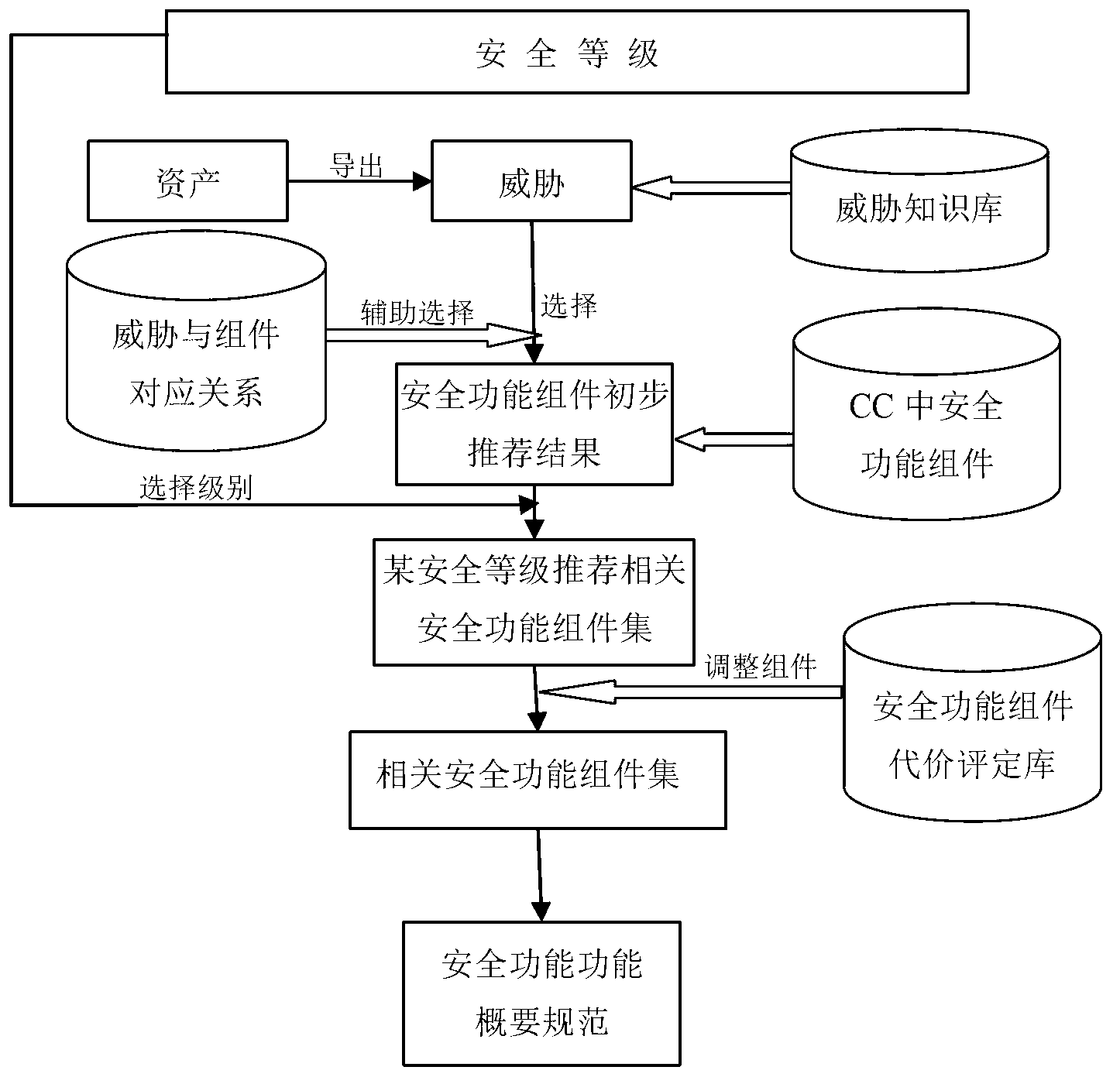
Software safety function component management method based on CC (the Common Criteria for Information Technology Security Evaluation)
InactiveCN102799816AReduce dependencyEasy to useComputer security arrangementsSoftware systemSoftware engineering
The invention discloses a software safety function component management method based on CC (the Common Criteria for Information Technology Security Evaluation), which is used for implementing recommendation and adjustment of a safety function component based on the CC at the demand analysis stage of software engineering. The method comprises the following steps of: performing abstract analysis and induction on description of threatening information in estimation documents in various fields based on a CC system, thus establishing a threat knowledge base; recommending a corresponding safety function component set for each threat knowledge in the threat knowledge base, and establishing a corresponding relationship between each threat knowledge and safety function components based on standard semantics; and establishing a safety function component cost evaluation table according to each safety function component type, and adjusting the components according to the content of the table. Compared with the prior art, the software safety function component management method points out the safety function component recommending and adjusting method based on the CC at the software requirement analysis stage, so that the software safety problem is considered at the initial stage of the development of a software system, the possibility of a security hole is reduced, and the software safety is improved.
Owner:TIANJIN UNIV
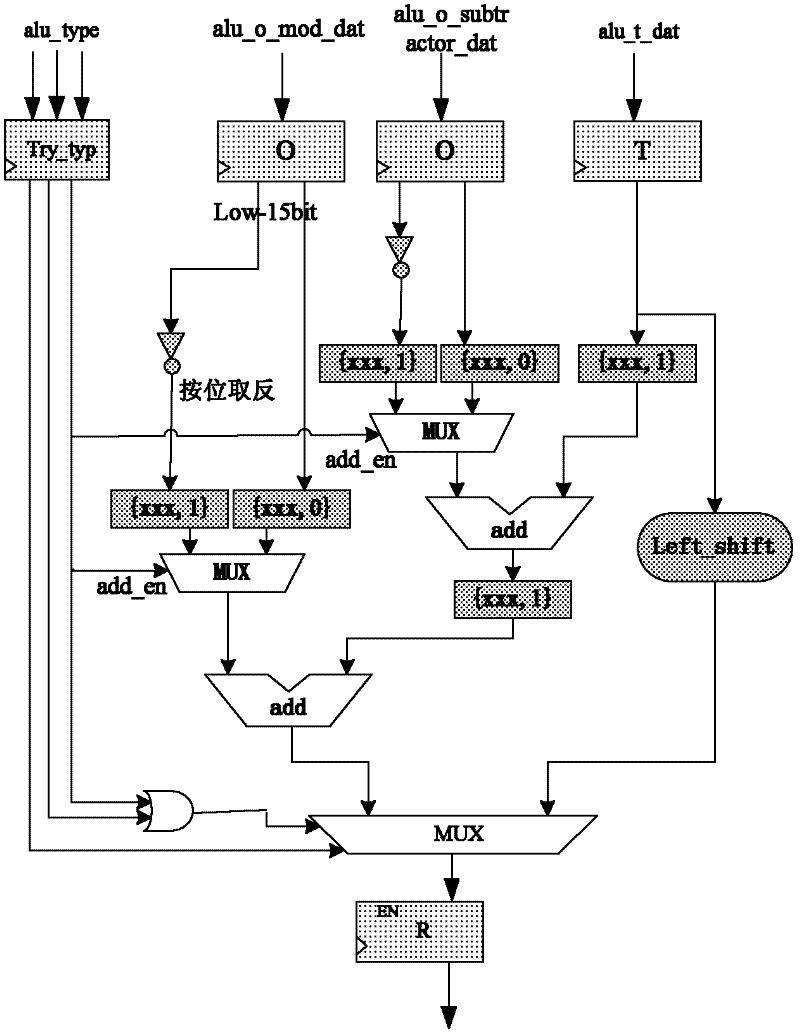
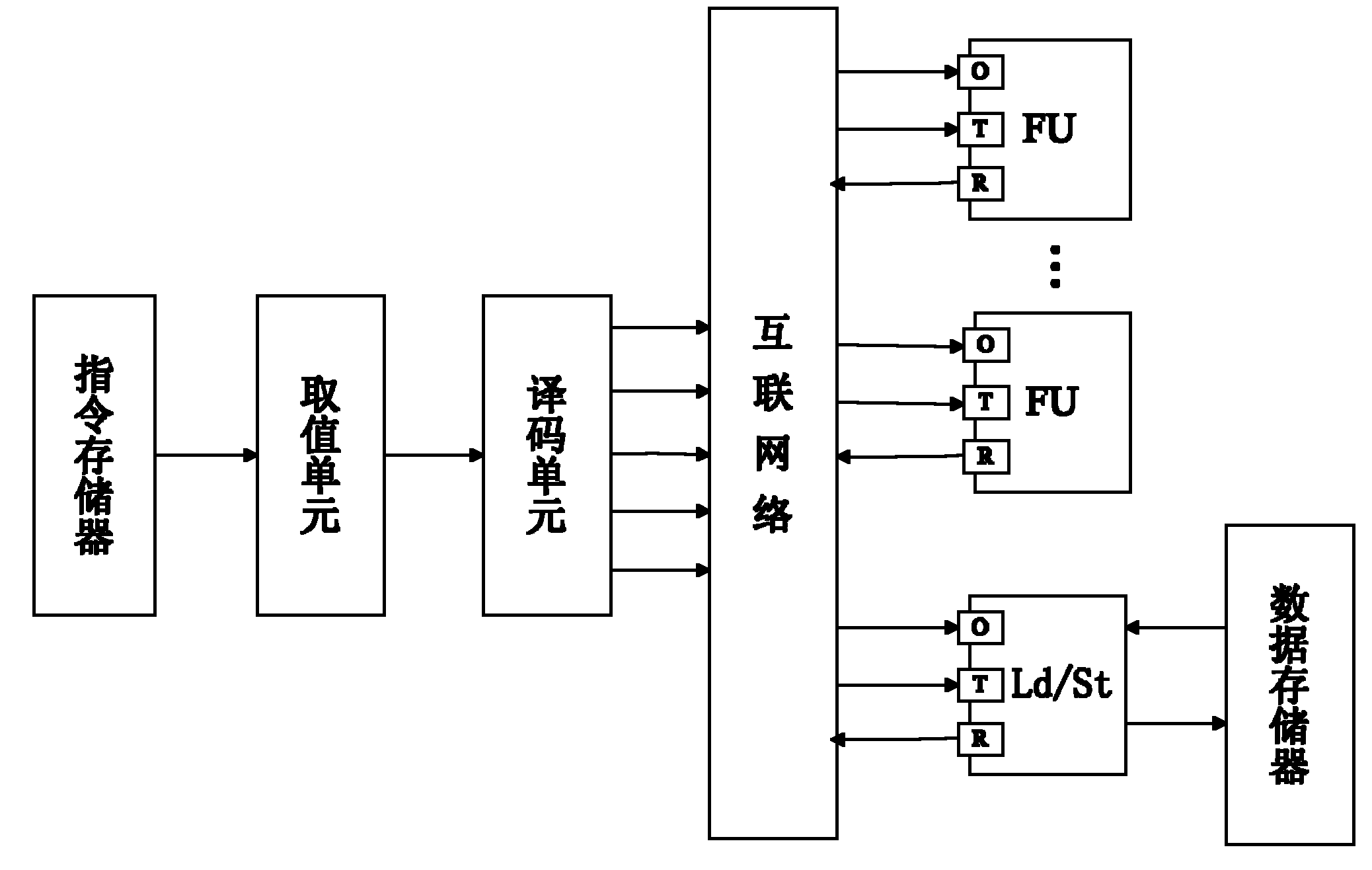
Elliptic curve cipher processor
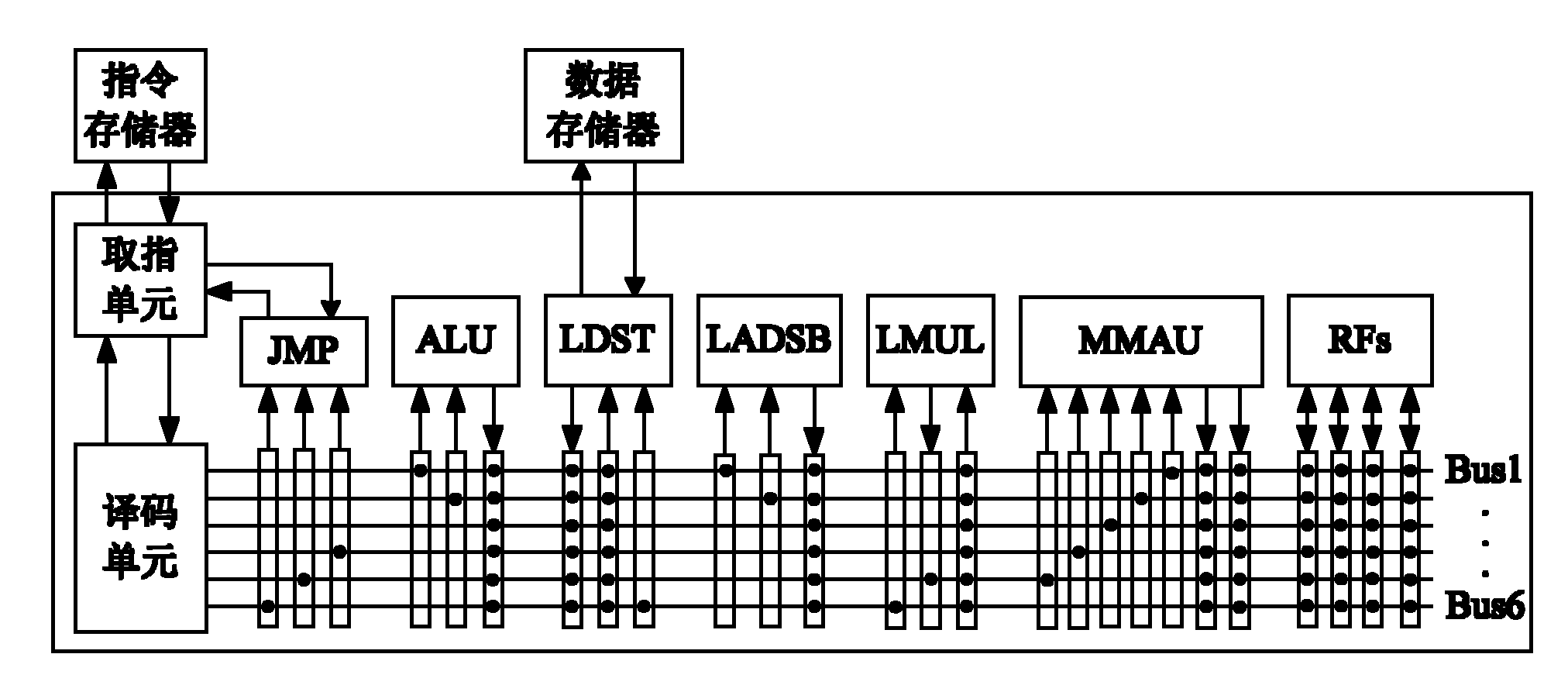
The invention discloses an elliptic curve cipher processor, and relates to the field of information technology security and micro-processor design. The processor is of a transport triggered architecture (TTA) structure, and the hybrid flow mechanism of the elliptic curve cipher processor comprises a transmission flow and a functional unit flow. The elliptic curve cipher processor comprises a command memory, a fetch unit, a decoding unit, a register file, a bus internetwork, a Socket and a functional unit, wherein the fetch unit fetches a command in the command memory; the command is decoded by the decoding unit; the decoded command is subjected to an error correction code (ECC) operation by selecting a corresponding functional unit through the bus internetwork; operation data required by the functional unit is acquired through the register file or the functional unit; and the functional unit is interconnected with the Socket through the bus internetwork. By utilizing the elliptic curve cipher processor, the operation speedup ratio is improved, the engineering change cycle is shortened, a software and hardware collaborative design is realized, and the problem of going against secondary development is solved.
Owner:TIANJIN UNIV
Automatic management method for IT (information technology) data center server system
InactiveCN104484262AReal-time releaseSave human resourcesHardware monitoringSpecial data processing applicationsInformatizationOperational system
The invention discloses an automatic management method for an IT (information technology) data center server system. The automatic management method comprises the following steps of collecting the state and the information of hardware of a server by using a chipset of the server; customizing operation system information collecting scripts and collecting operation system software and information of a relevant software running state machine by using a central processing unit according to collected states and information of the server; storing the information in a database; analyzing running states and running information of a server system by using the central processing unit according to the collected information; and timely issuing the analyzed common running state and analyzed common running information of the server system. By the automatic management method, manual daily work in the original IT informatization operation and maintenance is replaced, effective data analysis and support on IT operation, maintenance and management is realized, the scientificity and the efficiency of the IT operation, maintenance and management are improved, the human resources on operation and maintenance are saved, an auxiliary decision is provided, and the operation cost is reduced.
Owner:STATE GRID CORP OF CHINA +2
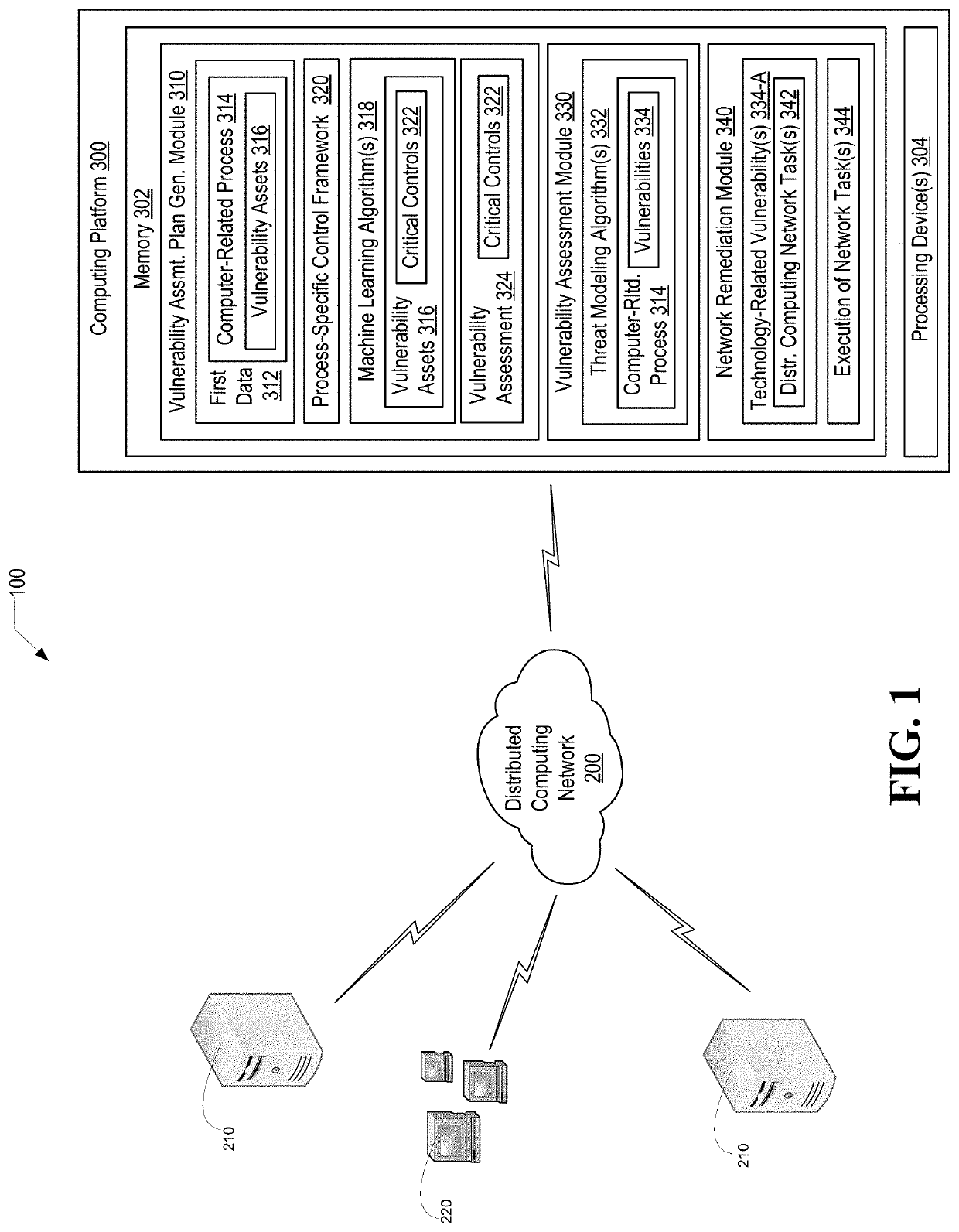
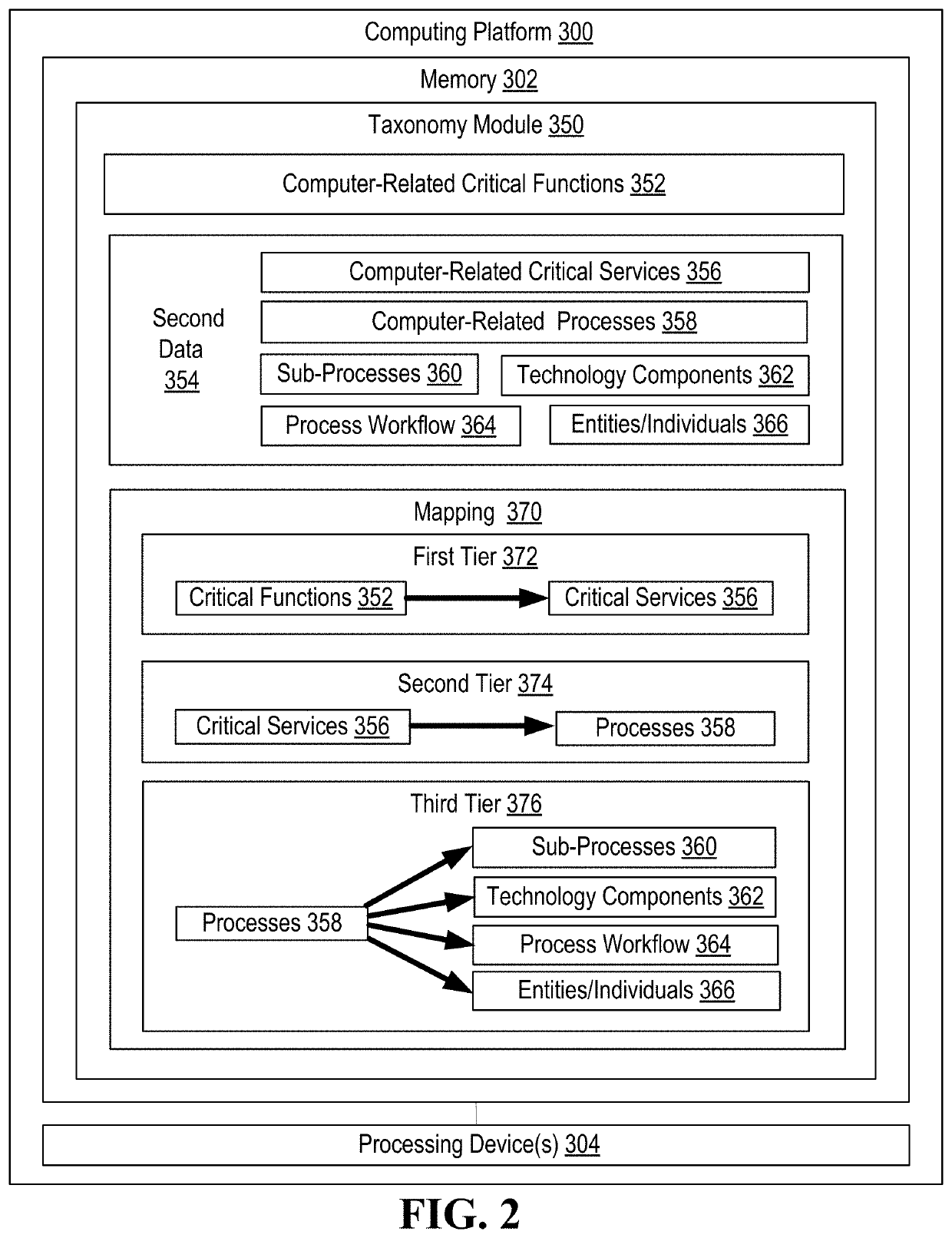
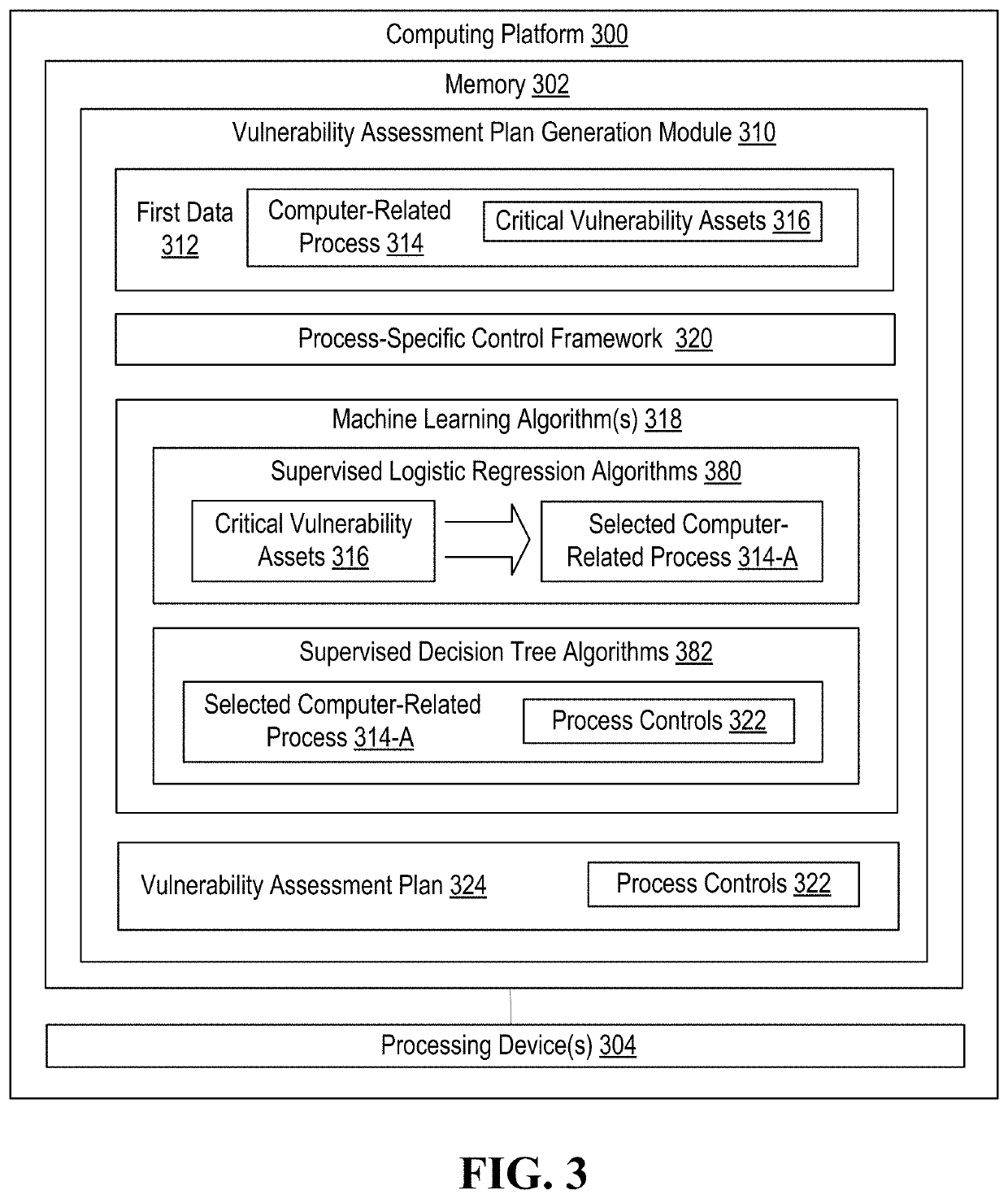
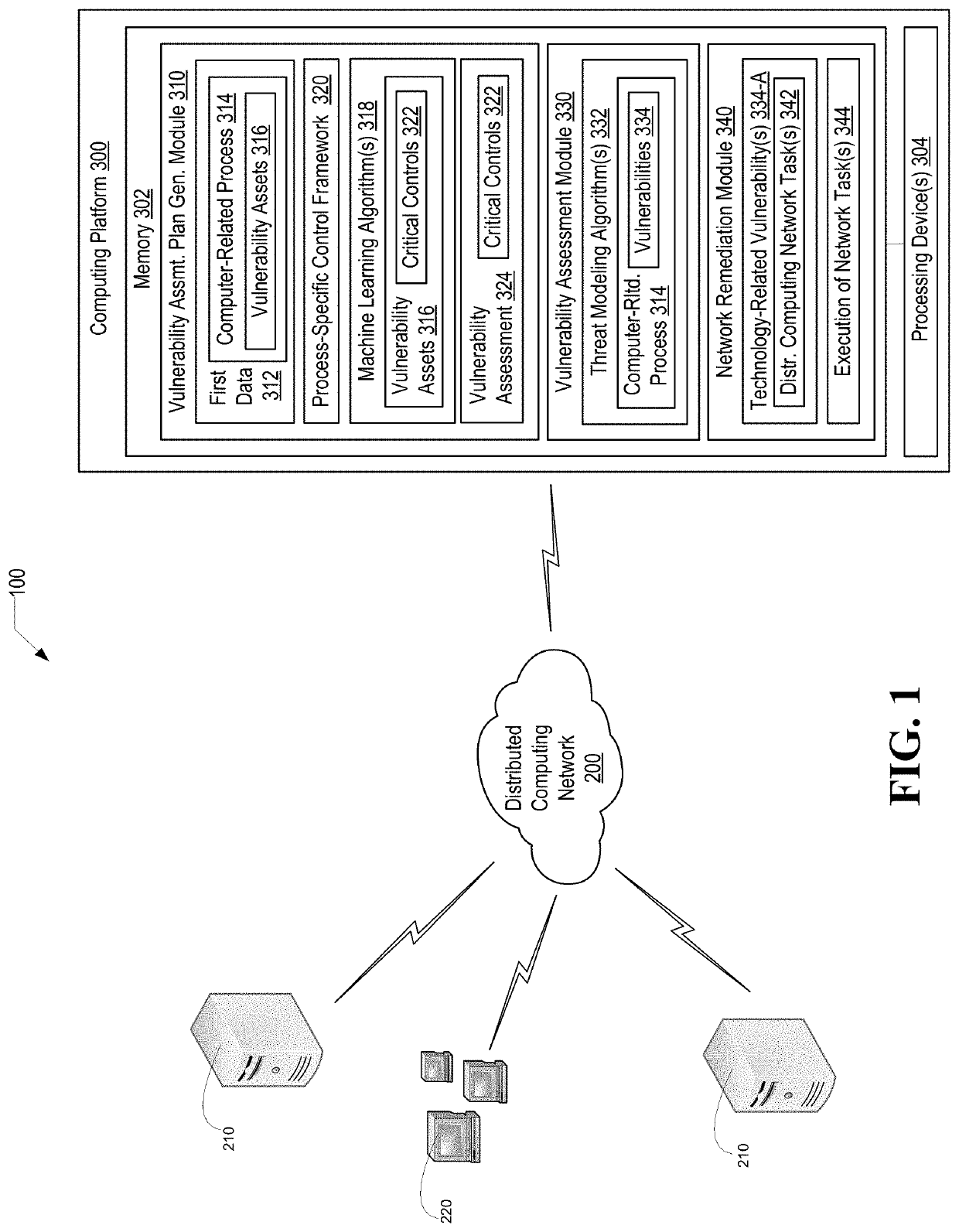
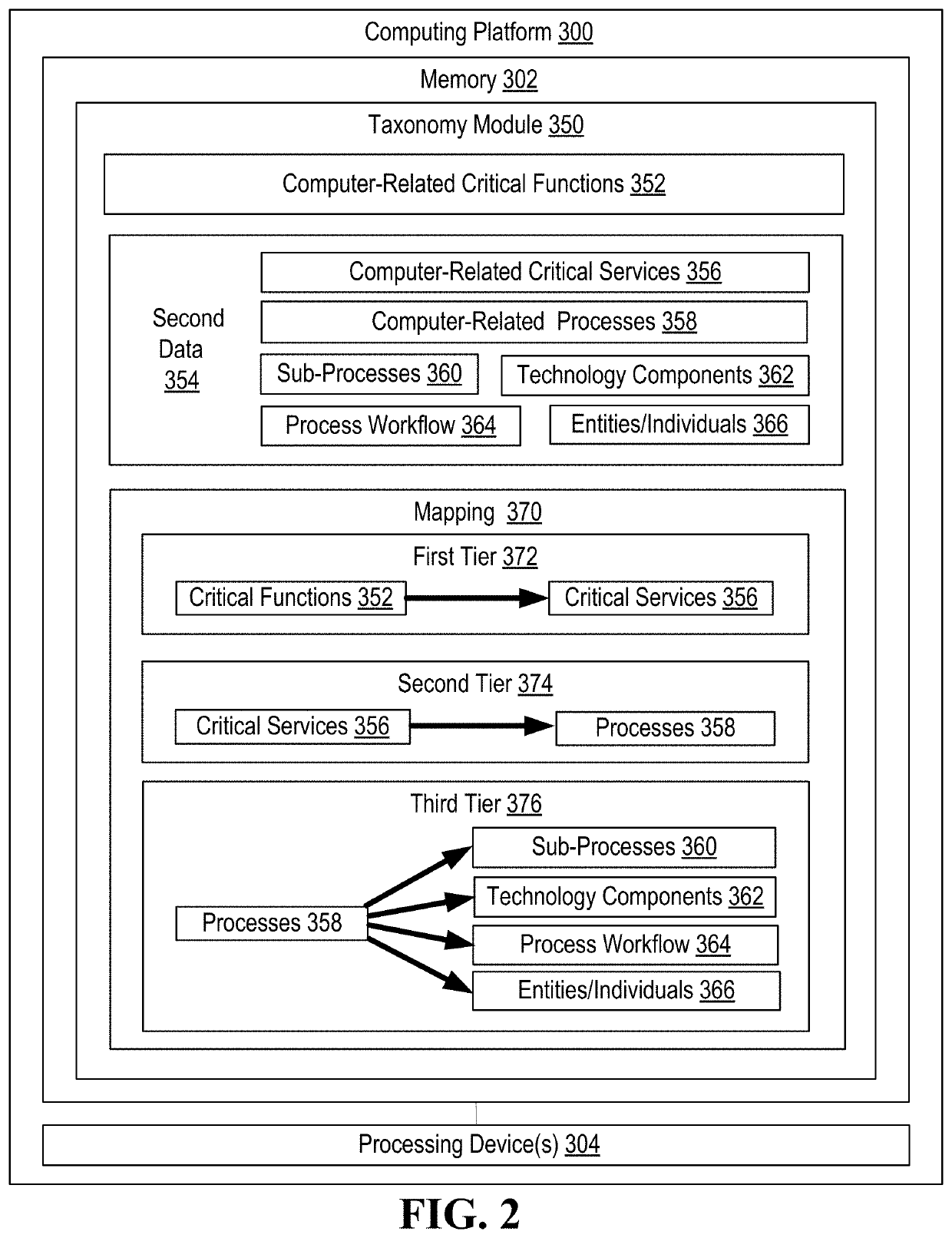
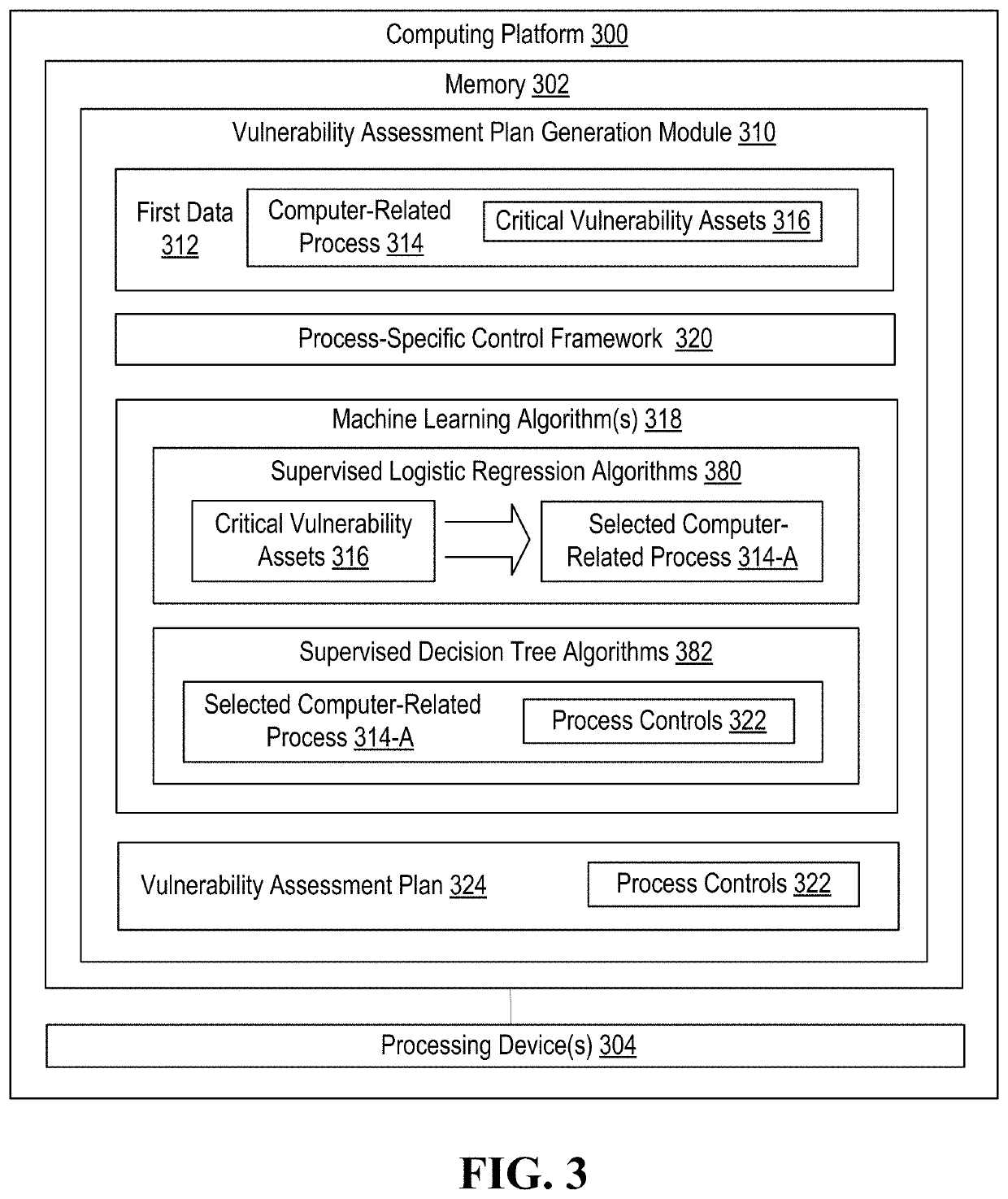
Information technology security assessment model for process flows and associated automated remediation
ActiveUS20200396240A1Well formedEnsemble learningKnowledge representationProcess assessmentCritical function
Information technology / cyber security for computer-related processes in which vulnerabilities are identified and, those vulnerabilities which are technology-related are automatically remediated by determining and executing network-based tasks. The most granular level of computer-related process assessment in made possible by reliance on a critical function / process taxonomy this is automatically generated and, as such, the present invention, identifies both technology and non-technology-related vulnerabilities.
Owner:BANK OF AMERICA CORP
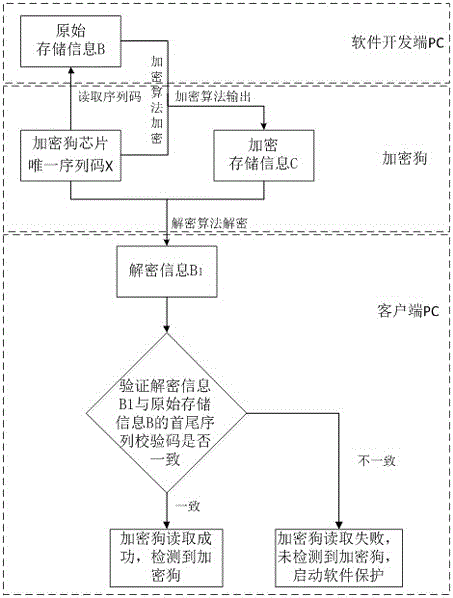
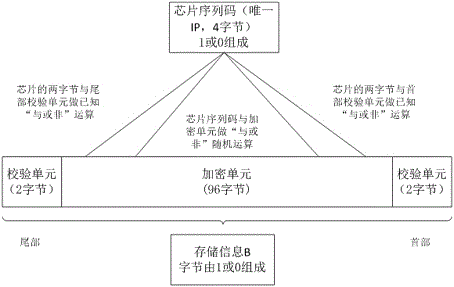
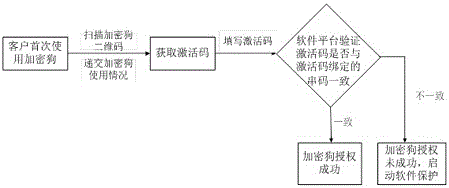
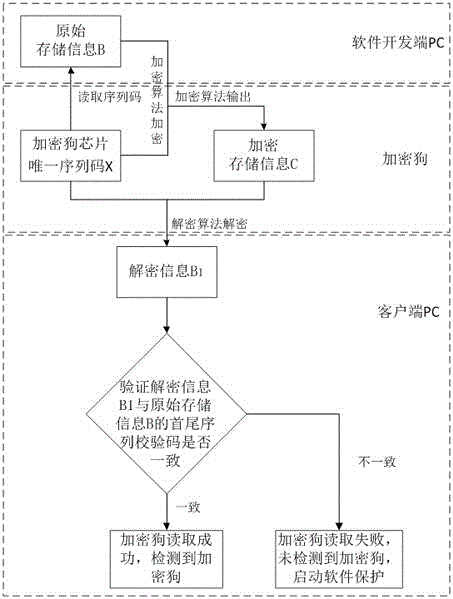
Software platform management method based on softdog
ActiveCN106650325AImprove securityOvercoming the disadvantages of being easily crackedProgram/content distribution protectionComputer hardwareIntellectual property
The invention relates to the field of information technology security, and in particular relates to a software platform management method based on a softdog. The software platform management method based on the softdog is as follows: a hardware sequence code encryption mode is adopted; namely, storage information is encrypted according to a uniqueness sequence code on a softdog chip; simultaneously, sequence code information check is added into the storage information; namely, when information is read, sequence code check of the chip is simultaneously read, and used for decrypting the storage information; furthermore, end-to-end matching with decrypted information is carried out; and thus, whether data of the softdog is read successfully or not can be verified. By means of the software platform management method disclosed by the invention, the storage information is encrypted based on the uniqueness sequence code on the softdog hardware chip; therefore, softdog hardware cannot be replicated; and thus, the purpose of protecting software having the proprietary intellectual property can be achieved.
Owner:杭州优稳自动化系统有限公司 +1
Optimizing risk-based compliance of an information technology (IT) system
InactiveUS20140366082A1Improve technical effectTransmissionSpecial data processing applicationsSecurity policyRisk IT
For each of a plurality of endpoints of an information technology system having a plurality of security policies, a probability of being safe of each of said endpoints is determined according to each of said security policies. Said determining takes into account probability of security compromise for a single violation of each given one of said security policies. A risk-aware compliance metric is determined for said information technology system based on each of said probabilities of being safe for each of said endpoints and each of said policies. At least one of an operation and a remediation is carried out on said information technology system based on said risk-aware compliance metric. Techniques for optimizing risk-aware compliance are also provided.
Owner:GLOBALFOUNDRIES INC
Optimizing risk-based compliance of an information technology (IT) system
For each of a plurality of endpoints of an information technology system having a plurality of security policies, a probability of being safe of each of said endpoints is determined according to each of said security policies. Said determining takes into account probability of security compromise for a single violation of each given one of said security policies. A risk-aware compliance metric is determined for said information technology system based on each of said probabilities of being safe for each of said endpoints and each of said policies. At least one of an operation and a remediation is carried out on said information technology system based on said risk-aware compliance metric. Techniques for optimizing risk-aware compliance are also provided.
Owner:GLOBALFOUNDRIES INC
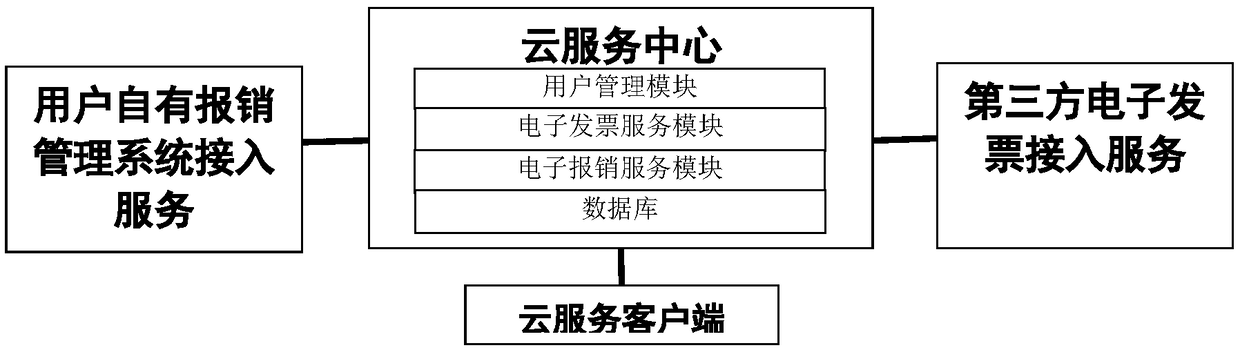
A cloud service reimbursement system based on electronic invoices
InactiveCN109447779AReduce energy consumptionEasy to storeFinanceBilling/invoicingThird partyInvoice
The invention relates to the fields of information technology security, financial management and cloud service, in particular to a cloud service reimbursement system based on electronic invoices. Thesystem comprises a cloud service center, a third-party electronic invoice access service module, a user own reimbursement system access service module and a cloud service client. According to the invention, the electronic invoice cloud service reimbursement management service is provided for the user through the cloud service client; the advantages of convenience, rapidness, paperless property, low energy consumption, easiness in storage, easiness in inquiry and the like brought by the electronic invoices are brought into full play, seamless connection of electronic invoice storage, collection, circulation, reimbursement and account entry is realized, and the problems that manual form filling and invoice pasting are required in traditional reimbursement, the electronic invoices are repeatedly submitted, and the reimbursement state of the electronic invoices cannot be synchronized in time, are solved.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
A CNN and RNN fusion model-based network heterogeneous concurrent steganography channel detection method
ActiveCN109729070ARealize detectionAvoid featuresError preventionMultiple keys/algorithms usageSteganalysisFeature Dimension
The invention belongs to the field of information technology security, and particularly relates to a CNN and RNN fusion model-based network heterogeneous concurrent steganalysis channel detection method. The method comprises the following steps of: extracting detection features of the multi-dimensional concurrent covert channel based on deep learning; learning the extracted detection characteristics; constructing a multi-dimensional concurrent covert channel detector and carrying out detection; According to the method, the defects of large feature dimension and incapability of expressing multi-layer data complex association caused by artificial design features based on experience or heuristic knowledge are avoided, and the detection of multi-dimensional concurrent covert communication of the network streaming media is realized by utilizing an automatic representation method for automatically mining feature association based on deep learning.
Owner:GANSU AGRI UNIV
Softdog device and secondary authorization management method based on softdog
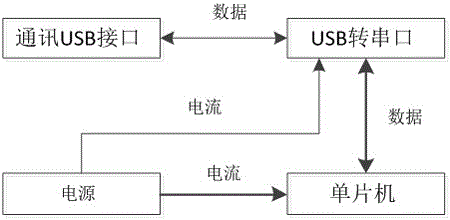
ActiveCN106650326AEnsure safetyAvoid wastingProgram/content distribution protectionIntellectual propertyWorkload
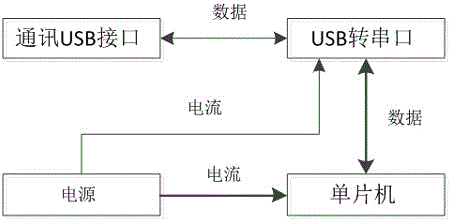
The invention relates to the field of information technology security, and in particular relates to a softdog device and a secondary authorization management method based on a softdog. A hardware and software combined softdog having a secondary authorization function comprises a USB interface, a USB-serial interface converter, a single-chip microcomputer and a power supply; and furthermore, the softdog has the secondary authorization management permission. The method comprises the following steps of awarding a mother softdog having the secondary authorization permission to an industry algorithm library; completing compiling and encapsulation of the industry algorithm library by using the mother softdog; activating the secondary authorization function by using the mother softdog, and authorizing a child softdog; copying the industry algorithm library into a child softdog workstation; and calling and using the copied industry algorithm library by using the child softdog. By means of the softdog device and the secondary authorization management method based on the softdog disclosed by the invention, the risk that the industry algorithm library having the proprietary intellectual property is leaked can be put an end; and information security is also ensured while the programming workload is greatly reduced.
Owner:杭州优稳自动化系统有限公司 +1
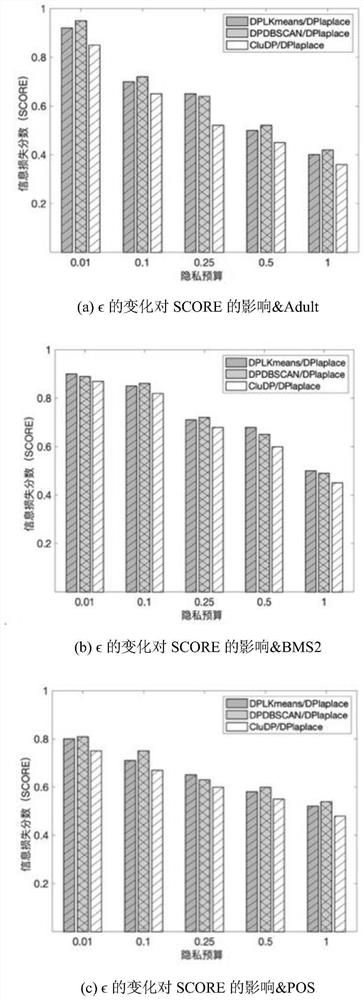
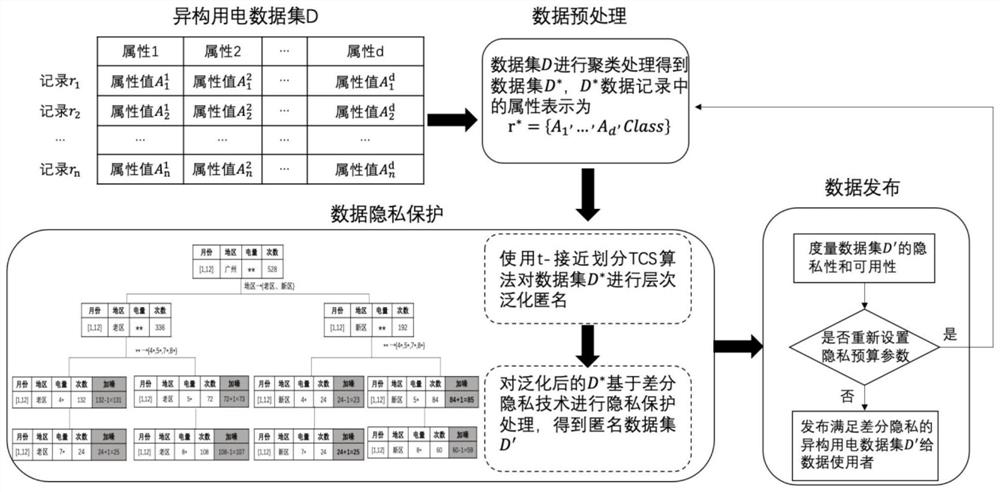
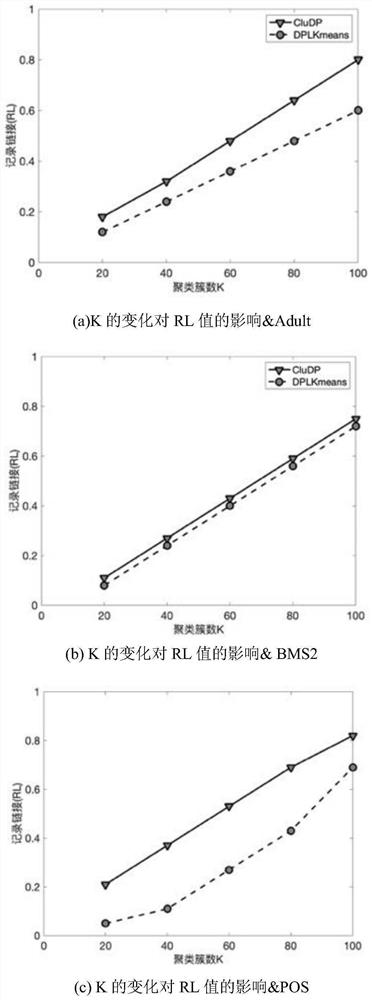
Heterogeneous power utilization data publishing method based on clustering anonymization and differential privacy protection
PendingCN114092729AGuaranteed privacyGuaranteed availabilityCharacter and pattern recognitionData setOriginal data
The invention discloses a heterogeneous power utilization data publishing method based on clustering anonymization and differential privacy protection, which relates to the field of information technology security, and aims to achieve the purpose of privacy protection of heterogeneous power utilization data, convert a clustering analysis problem into a classification problem, enabling the cluster structure of the original data to be subjected to generalization anonymity mechanism and noise addition processing at the same time by using the class label, and then publish the power transaction data set satisfying the belonging-differential privacy protection, realize flexible privacy protection cluster analysis, improve the accuracy of the published data for the cluster analysis, and meanwhile, ensure the privacy and availability of various types of data, and provide reliable data for power utilization data analysis.
Owner:CHINA SOUTHERN POWER GRID DIGITAL GRID RES INST CO LTD +2
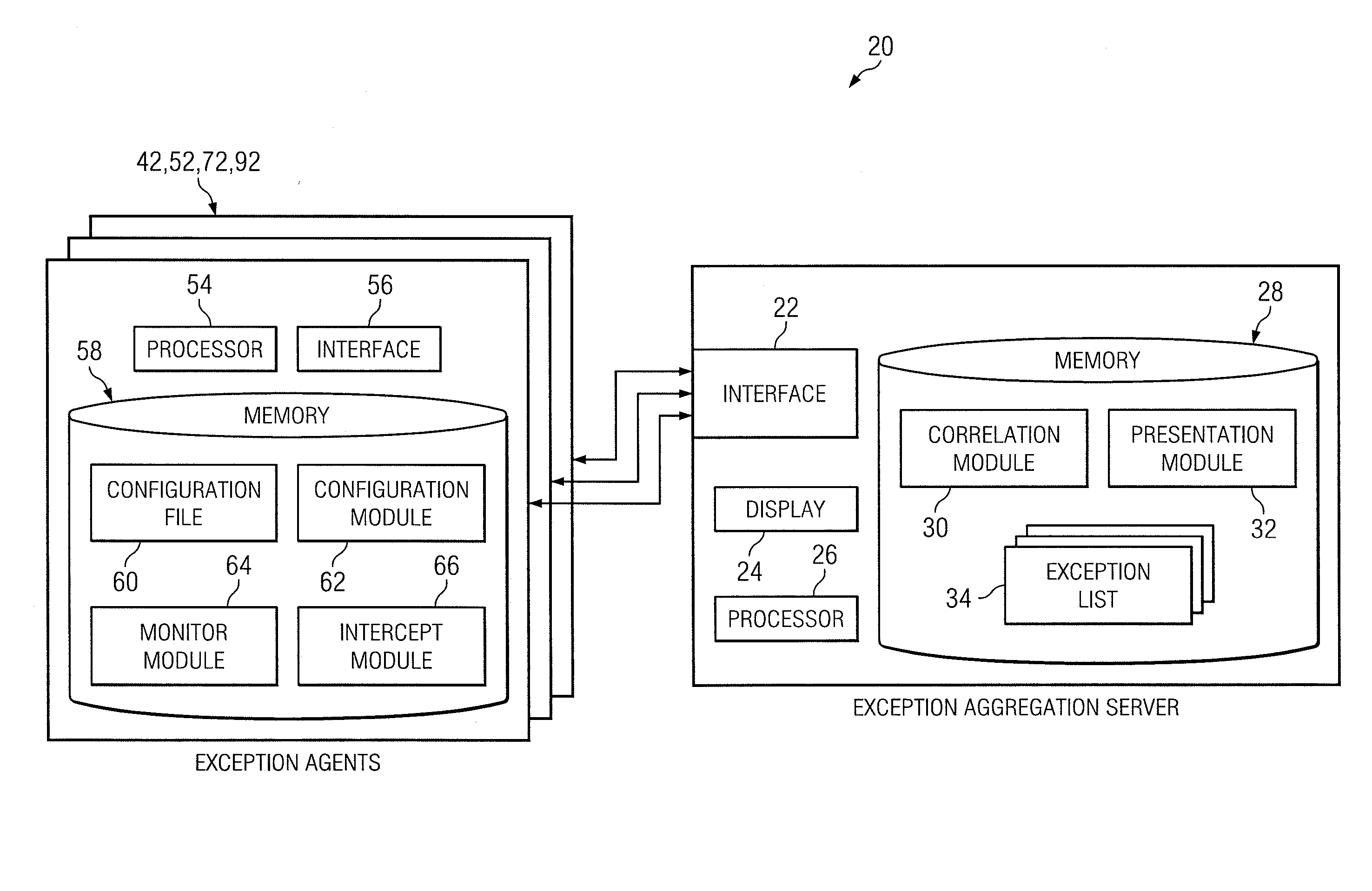
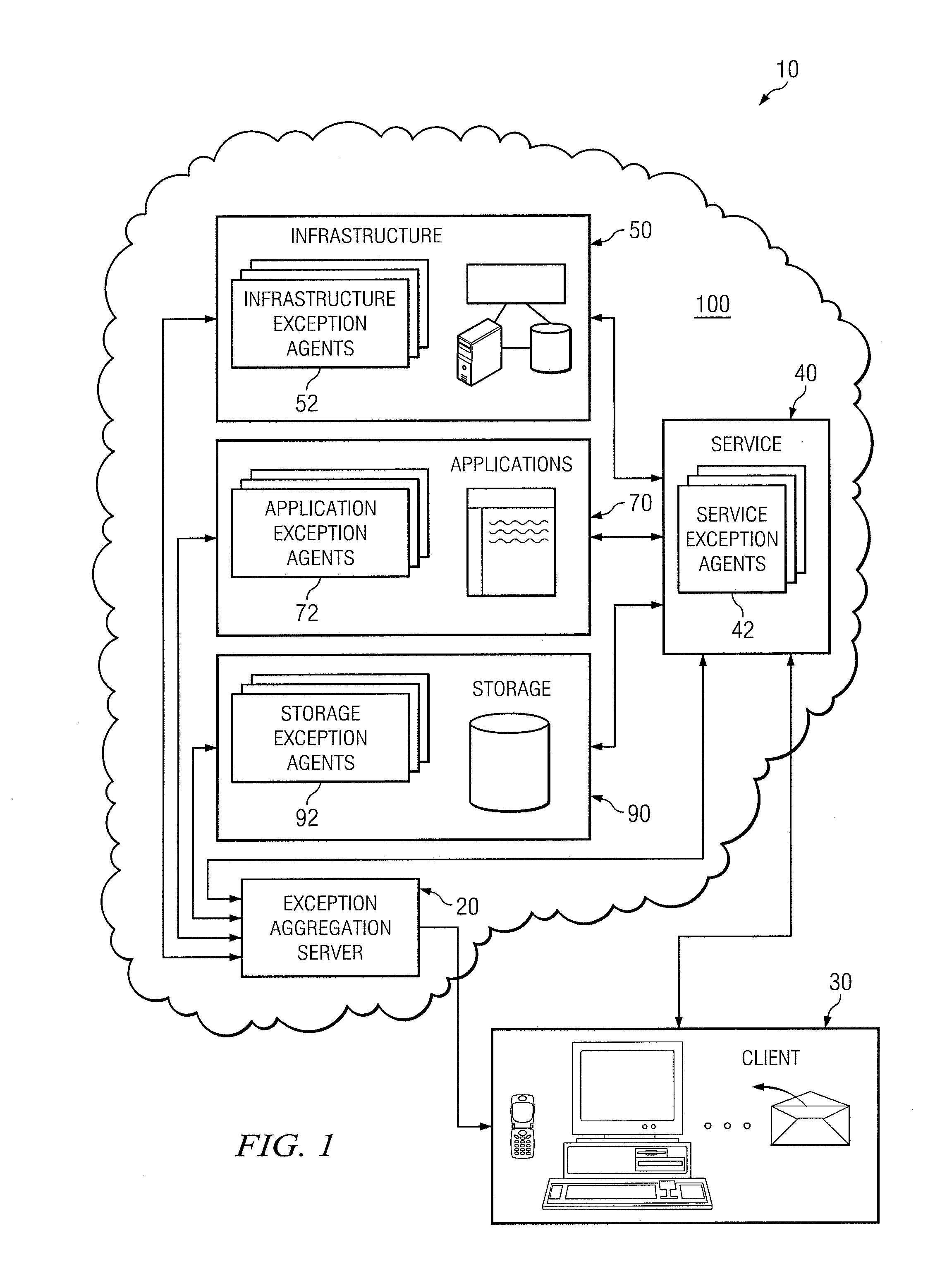
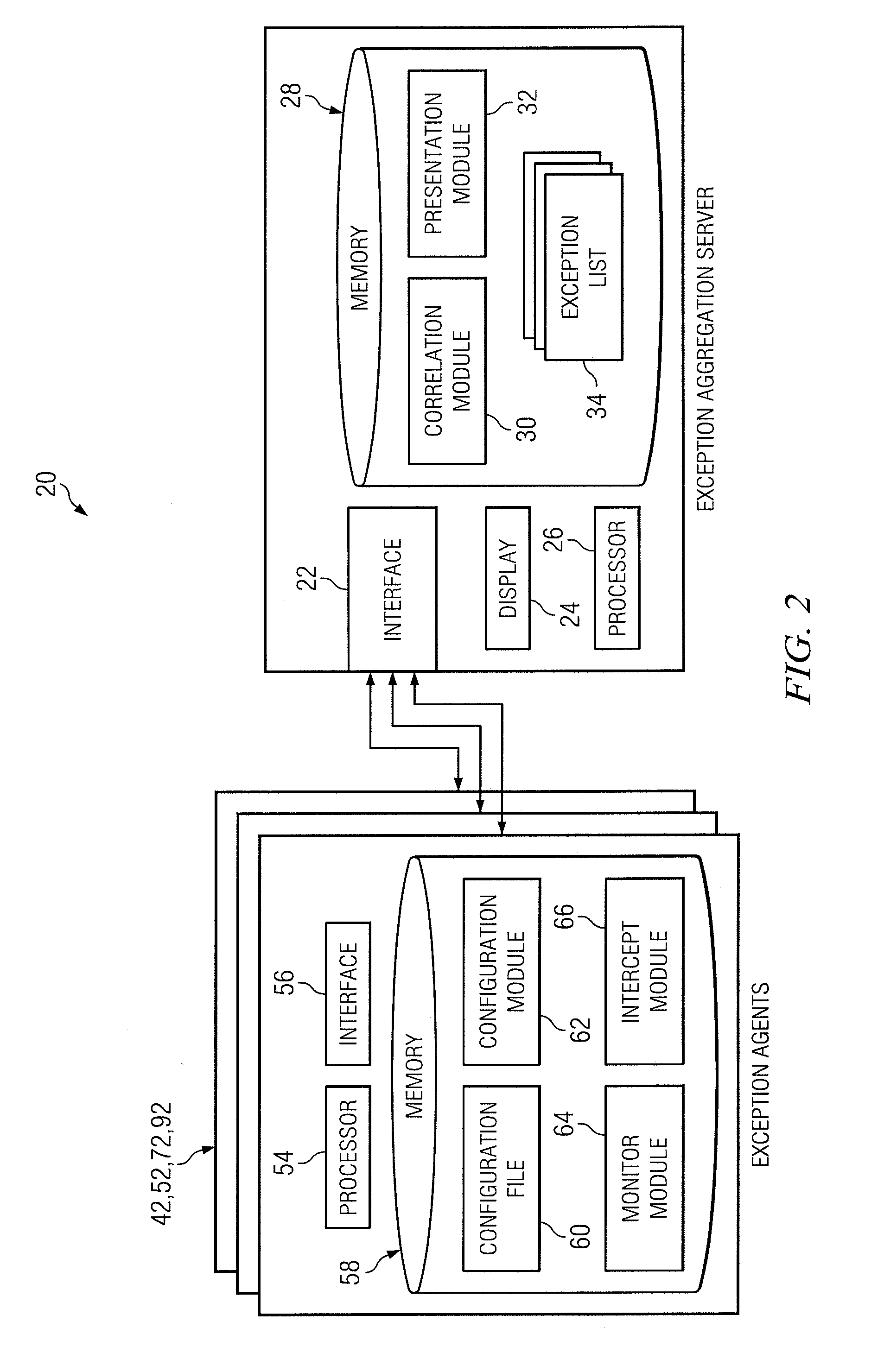
System and method of collecting and reporting exceptions associated with information technology services
ActiveUS8516295B2Promote disseminationEarly detectionNon-redundant fault processingInformation technology educationInformation technology operations
According to one embodiment of the present disclosure, a method of collecting and reporting exceptions associated with information technology services includes receiving exceptions associated with a service, including receiving exceptions associated with an infrastructure and exceptions associated with an application; formatting the exceptions into an exceptions list; correlating at least one of the exceptions associated with the infrastructure and at least one of the exceptions associated with the application to identify a service error condition; and storing the exceptions list and an identifier of the service error condition for presentation to a client associated with the service.
Owner:CA TECH INC
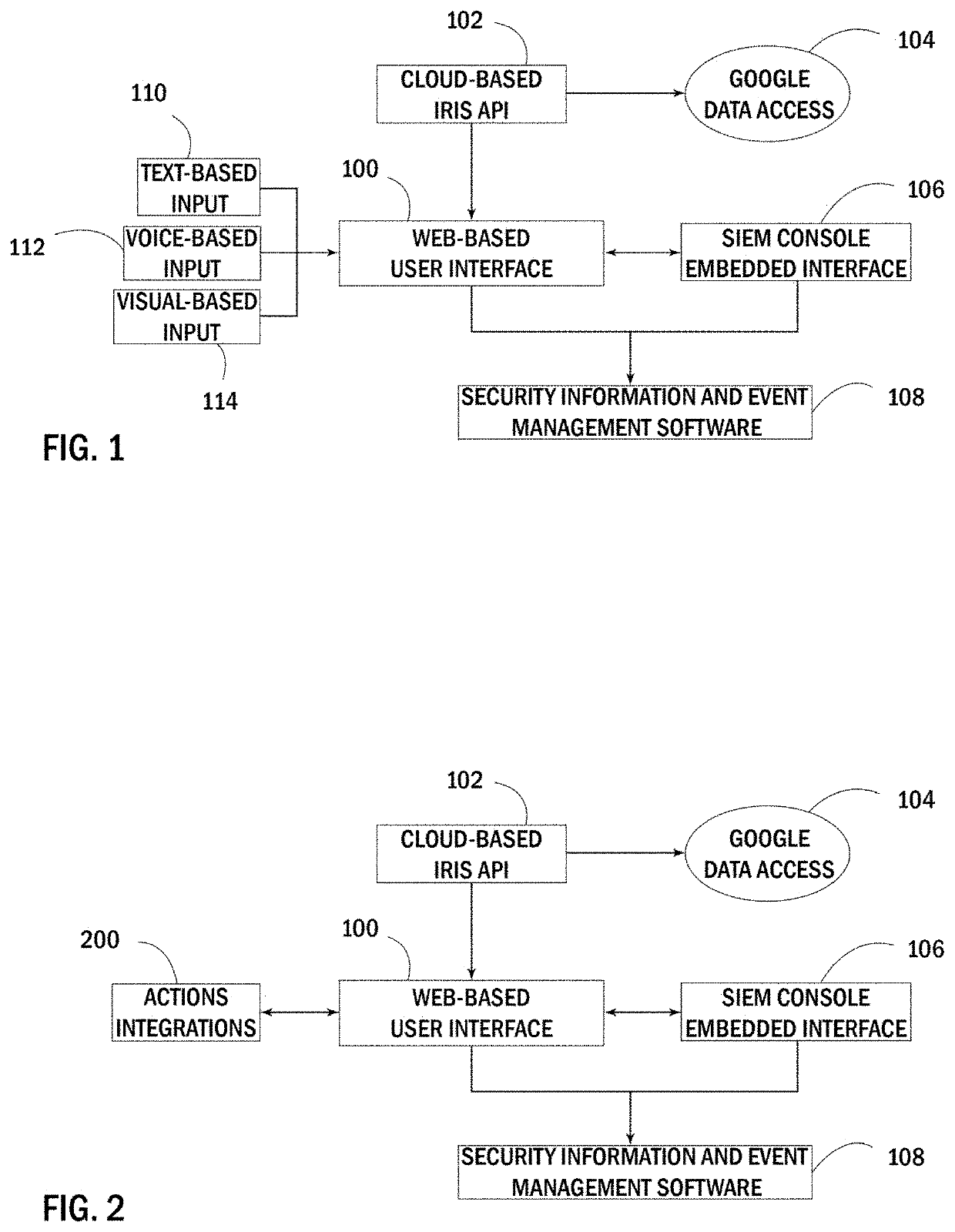
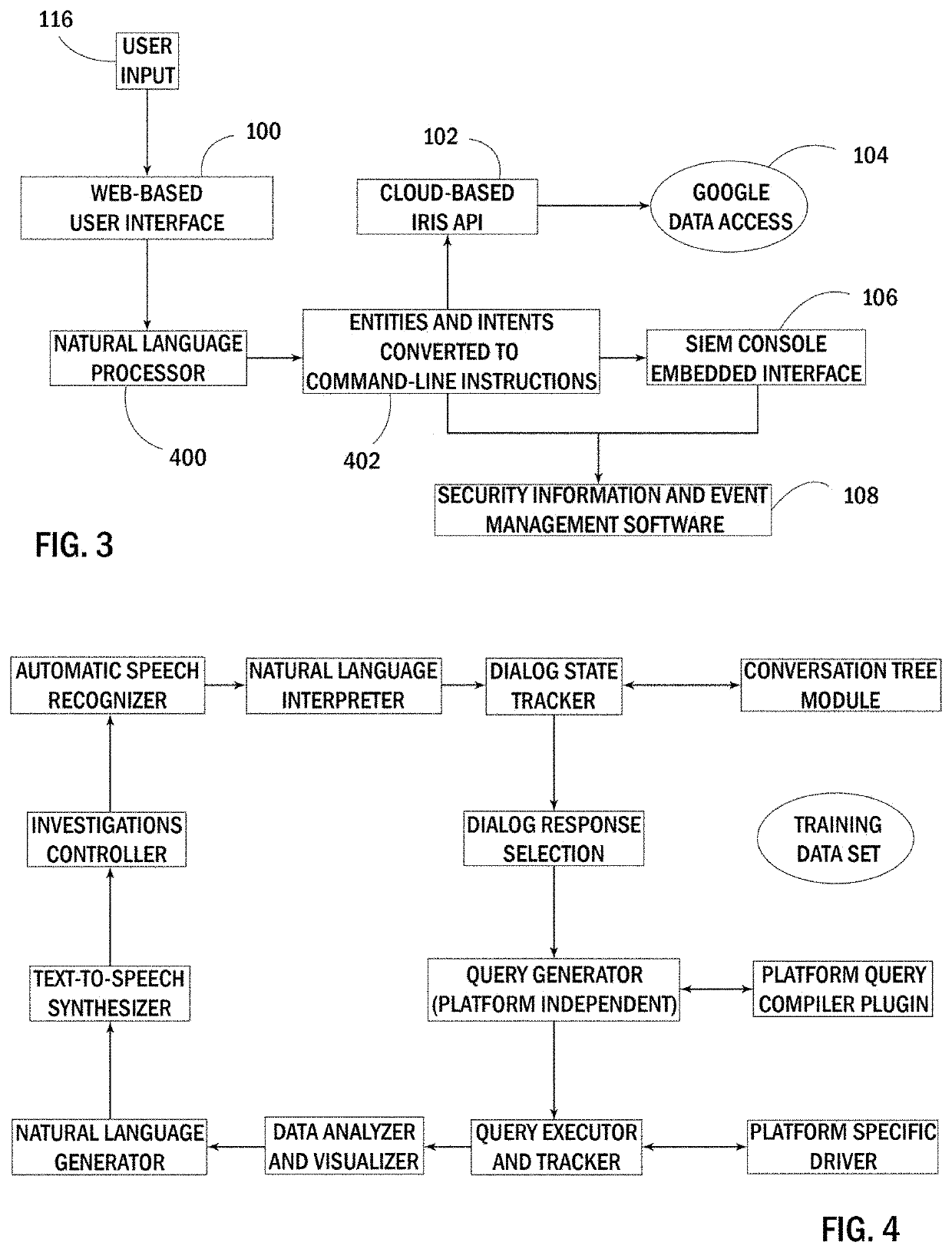
Artificial intelligence-assisted information technology data management and natural language playboook system
ActiveUS20200175077A1Improve clarityImprove understandingHardware monitoringPlatform integrity maintainanceSecurity information and event managementBusiness enterprise
The artificial intelligence-assisted information technology data management and natural language playbook system disclosed herein is designed to support current enterprise information technology security personnel by providing a faster and easier method for finding information or anomalies in current system data and logs. Enterprise security divisions often use multiple security information and event management (SIEM) software platforms to monitor their personnel data and logs, though even the use of such platforms requires advanced knowledge and skill on behalf of the user. The current system allows security users of all skill levels to interact using natural language processing with the system and effectively investigate such data and logs. The system assists such users by interacting with these SIEM platforms on their behalf and providing the users with access to pre-programmed natural language inquiry sequences, called “playbooks,” and easily customizable output displays. The software is entirely web-based, though can be integrated into current SIEM consoles for streamlined use.
Owner:QUERY AI INC
Authentication process of ERP management system of chemical enterprise
InactiveCN110728521AQuick to useReach an interactive exchangeProtocol authorisationUser authenticationComputer science
The invention discloses an authentication process of an ERP management system of a chemical enterprise, and belongs to the technical field of information technology security. The authentication process of the ERP management system of the chemical enterprise is realized mainly through three steps of user registration, user authentication and WeChat authentication. According to the method, before registration, the administrator is not directly registered like other software, but is contacted firstly, so that the administrator helps the user to register, the user can use the software quickly andconveniently, the administrator can provide technical support for the client, and interactive communication between the user and the client is achieved. According to the invention, the applet is docked in the software, so that the client of the user can pay on the system and send the applet two-dimensional code to the client after receiving the goods, the cost is saved, and the working efficiencyis improved.
Owner:永诚恒易网络科技股份有限公司
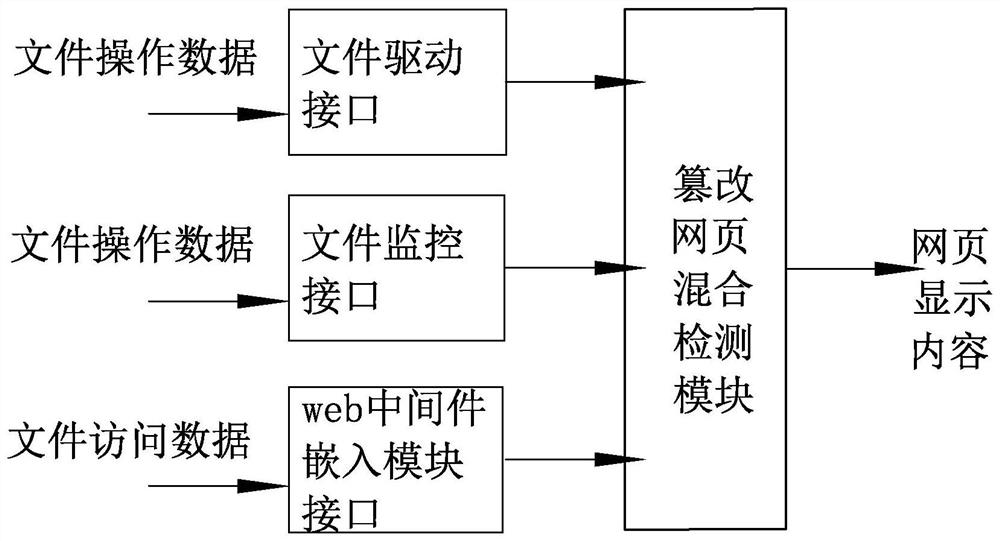
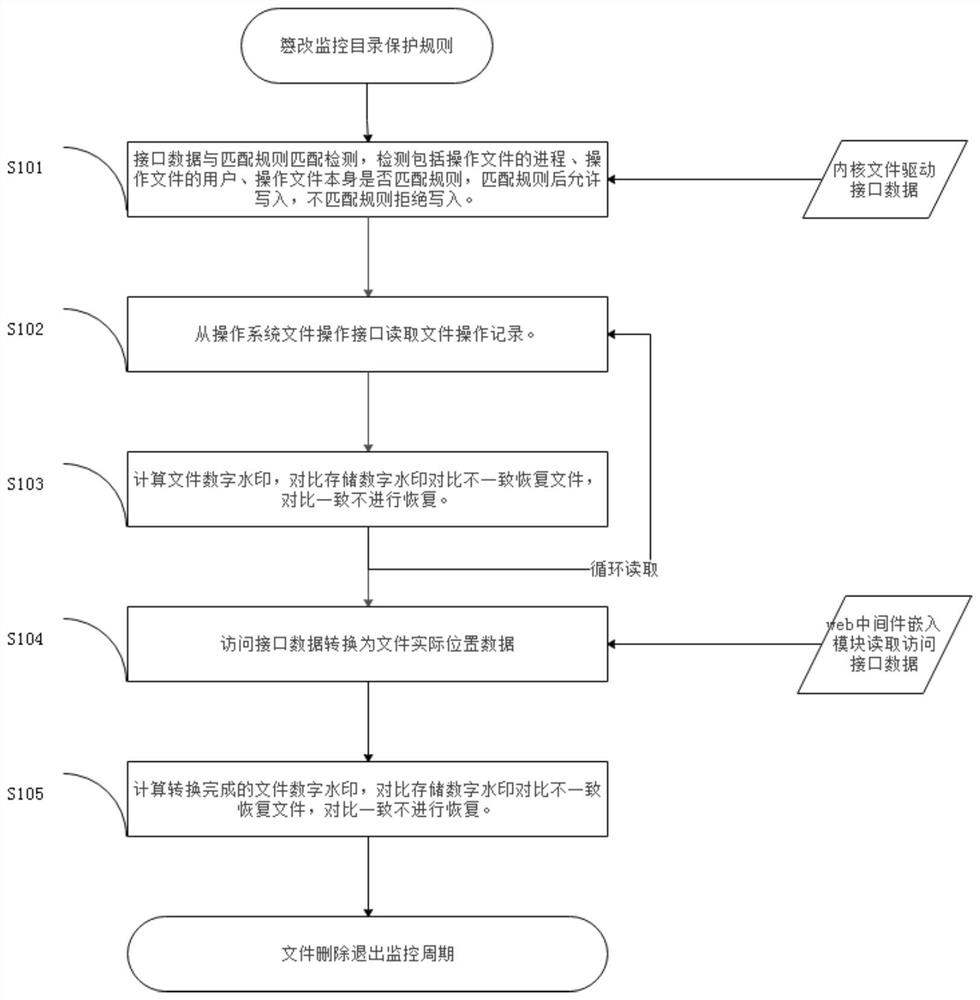
Tampered webpage mixed detection technology
PendingCN113221194AMonitor correctnessMonitor correctness in real timeDigital data protectionEngineeringWeb page
The invention relates to the field of information technology security, in particular to a tampered webpage mixed detection technology which at least comprises a detection method for file operation data and a detection method for access data. The detection method for the file operation data comprises a modification operation detection step and a write-in operation detection step. The state of the file in the whole release access process is monitored at the same time, the correctness of the file is monitored in real time in the three states of uploading, storage and access of the webpage file, information such as content attributes of the file is monitored in the whole period when the file is used, the change of the file is found in time, and the situation that the page is tampered to be accessed is avoided.
Owner:云尖(北京)软件有限公司
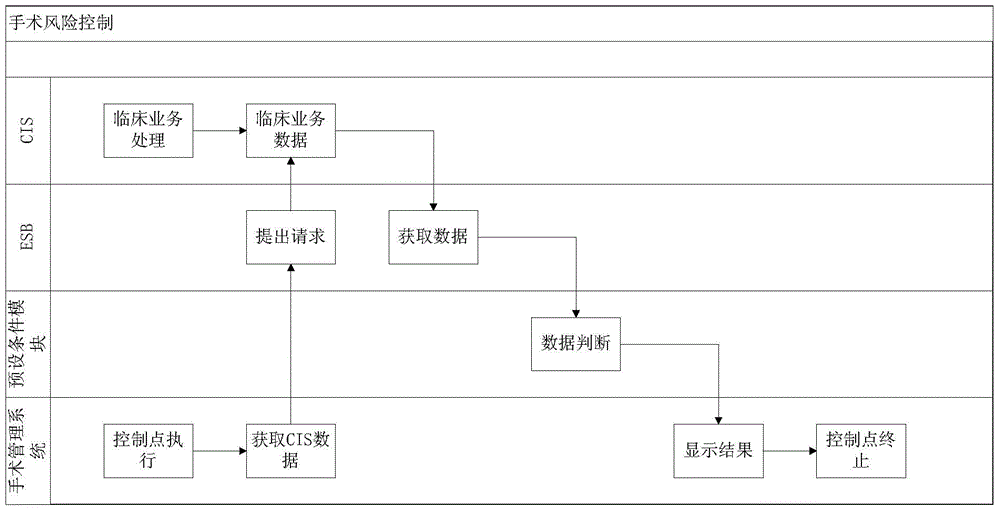
Perioperative safety management method using information technology
InactiveCN105719212AAvoid distractionsReduce surgical riskData processing applicationsRisk ControlComputer science
The invention provides a perioperative safety management method using information technology. The method includes setting key points for perioperative risks currently existing in a hospital by means of information technology, reexamining through different medical behaviors or related doctor ordered information, and forming a complete information management and control chain. The method described in the invention reduces the operation risks caused by information islands or information asymmetry on the basis of original artificial risk control, acquires and updates the state of the perioperative risk points in real time by monitoring the different medical behaviors or related doctor ordered behaviors, and conducts management and control and warning for an operation meeting a preset early warning standard, thereby achieving the purpose of complete operation risk control.
Owner:王剑云 +1
Information technology safety monitoring system
InactiveCN107464394ARealize acquisitionAvoid destructionFire rescueAlarmsInformation processingMonitoring system
The invention discloses an information technology safety monitoring system which comprises an information acquisition system and an information processing system, wherein an output end of the information acquisition system is electrically connected with an input end of the information processing system; the information acquisition system comprises a fire smoke sensor, a sound volume sensor, a pressure sensor, a face recognition device, a temperature sensor, an information integration device and an information transmitting module; an output end of the fire smoke sensor is electrically connected with an input end of the information integration device; an input end of the information integration device is electrically connected with an output end of the sound volume sensor, an output end of the pressure sensor, an output end of the face recognition device and an output end of the temperature sensor. With the adoption of the information acquisition system and the information processing system, the monitoring efficiency of the monitoring system is improved, so that the monitoring capacity of the system is improved; and the defects in the existing monitoring system are overcome.
Owner:天复(东莞)标准技术有限公司
Information technology security assessment model for process flows and associated automated remediation
Information technology / cyber security for computer-related processes in which vulnerabilities are identified and, those vulnerabilities which are technology-related are automatically remediated by determining and executing network-based tasks. The most granular level of computer-related process assessment in made possible by reliance on a critical function / process taxonomy this is automatically generated and, as such, the present invention, identifies both technology and non-technology-related vulnerabilities.
Owner:BANK OF AMERICA CORP
Trusted device and trusted system
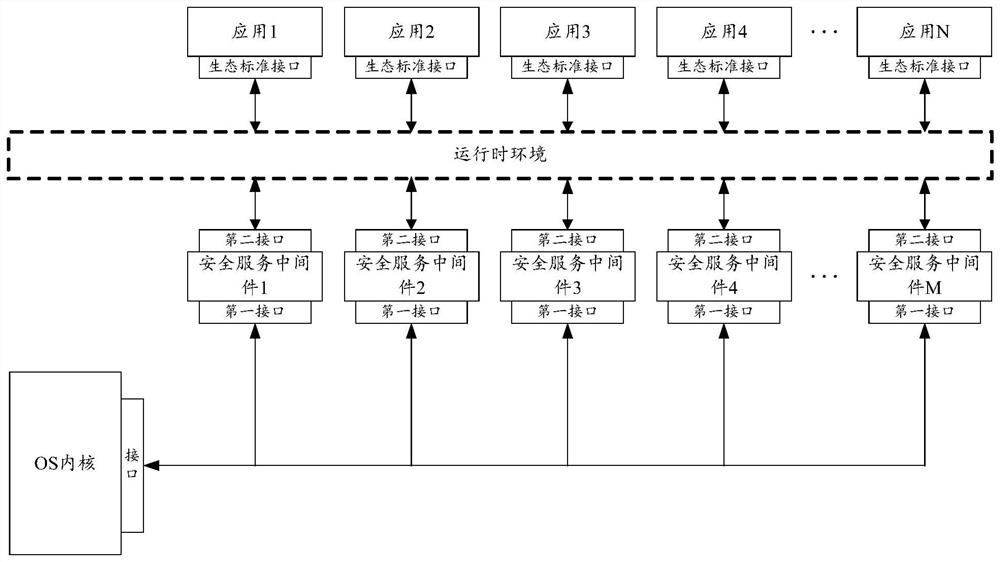
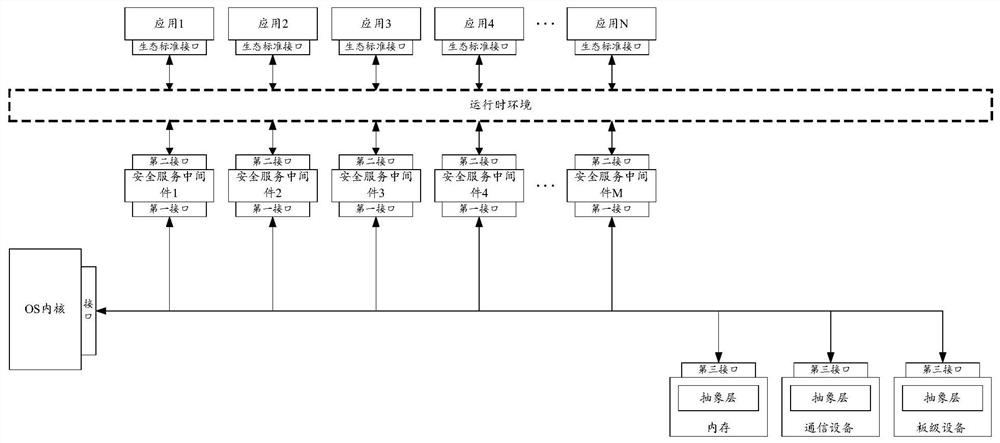
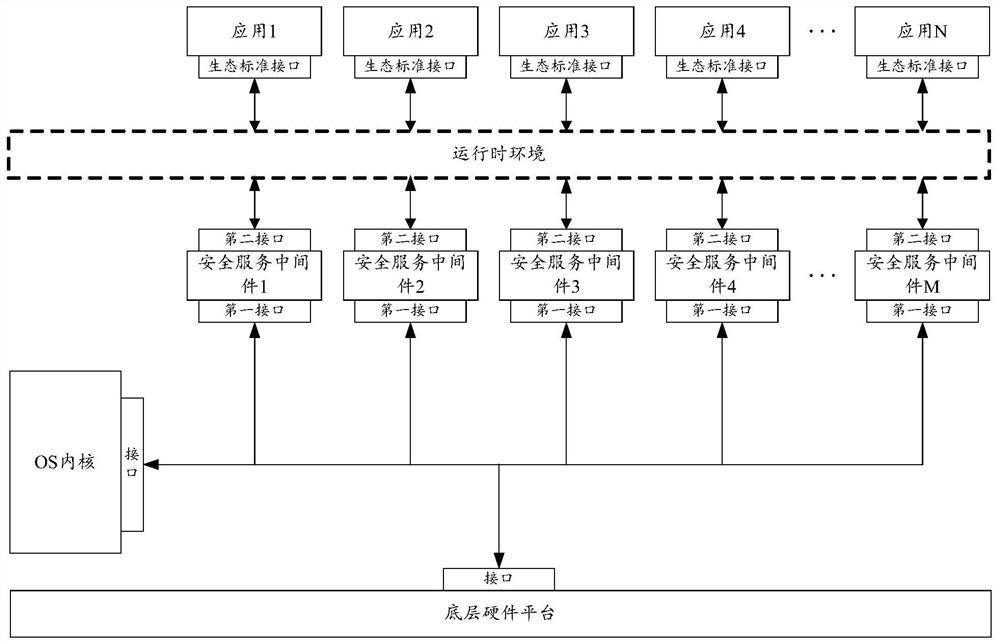
InactiveCN112685708AEfficient integrationReduce safety concernsDigital data protectionDigital data authenticationOperational systemSoftware engineering
The embodiment of the invention provides a trusted device and a trusted system. The trusted device comprises an operating system OS kernel and a plurality of security service middleware. The OS kernel comprises a first group of interfaces, and the first group of interfaces comprises interfaces provided for the plurality of security service middleware; the plurality of pieces of security service middleware respectively comprise a second group of interfaces, the second group of interfaces comprises a first interface and a second interface provided for a runtime environment or an upper-layer application, and the plurality of pieces of security service middleware interact with the OS kernel through the first interface included in the plurality of pieces of security service middleware, the first group of interfaces and the second group of interfaces meet the security requirements of the same target standard, and the target standard belongs to the information technology security evaluation standard.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com