Cryptographic algorithm realization protecting method used for defending energy analysis attacks
An energy analysis attack and cryptographic algorithm technology, applied in the protection of cryptographic algorithms for defense against energy analysis attacks, and the protection of cryptographic algorithms, which can solve problems such as large time and space overhead, high design and deployment costs, and application difficulties.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
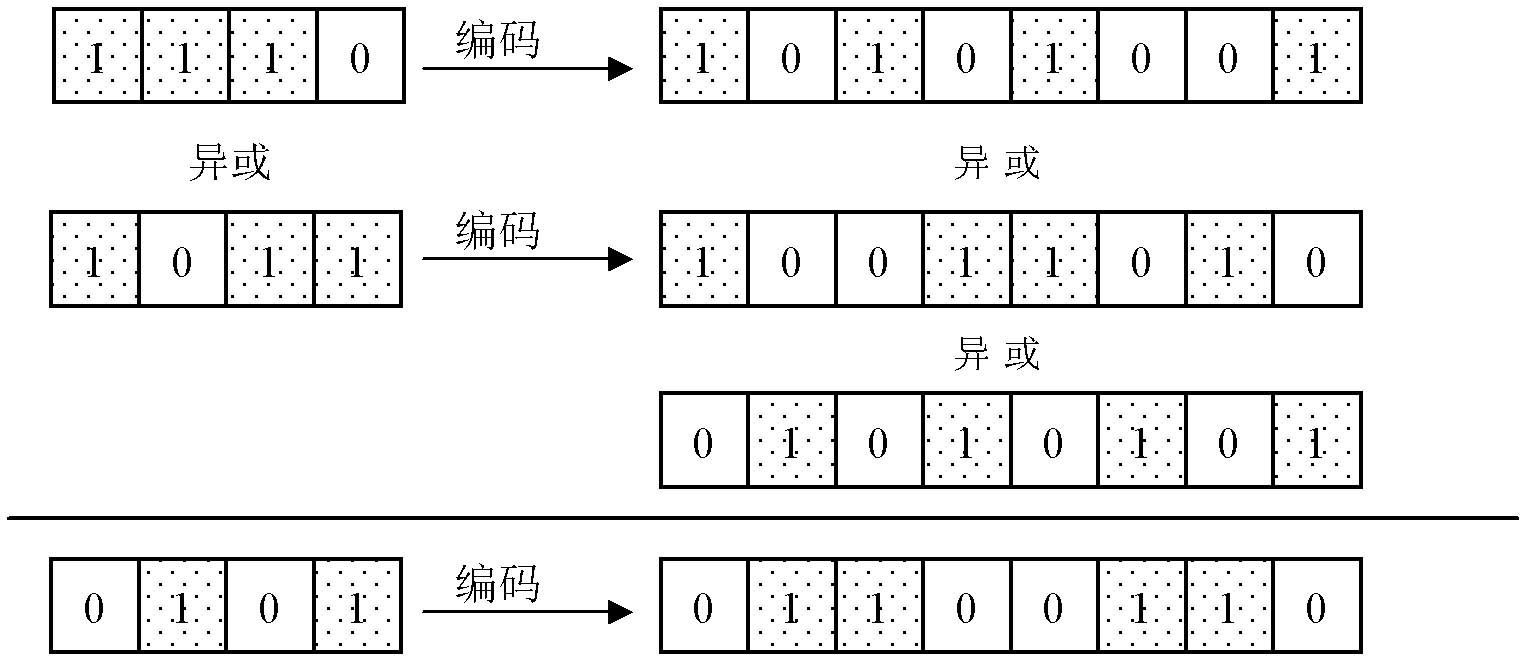
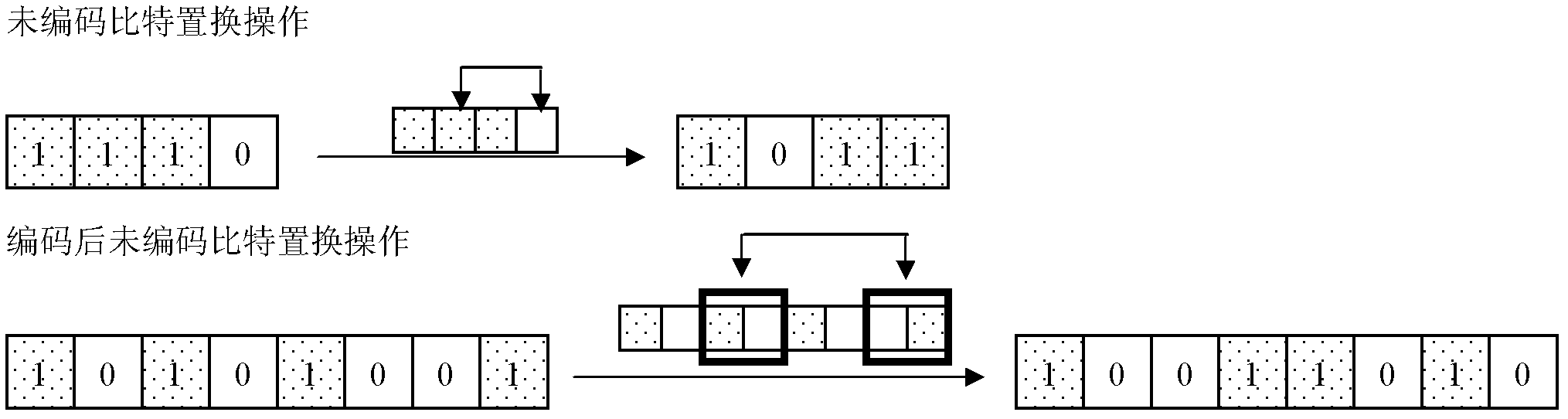
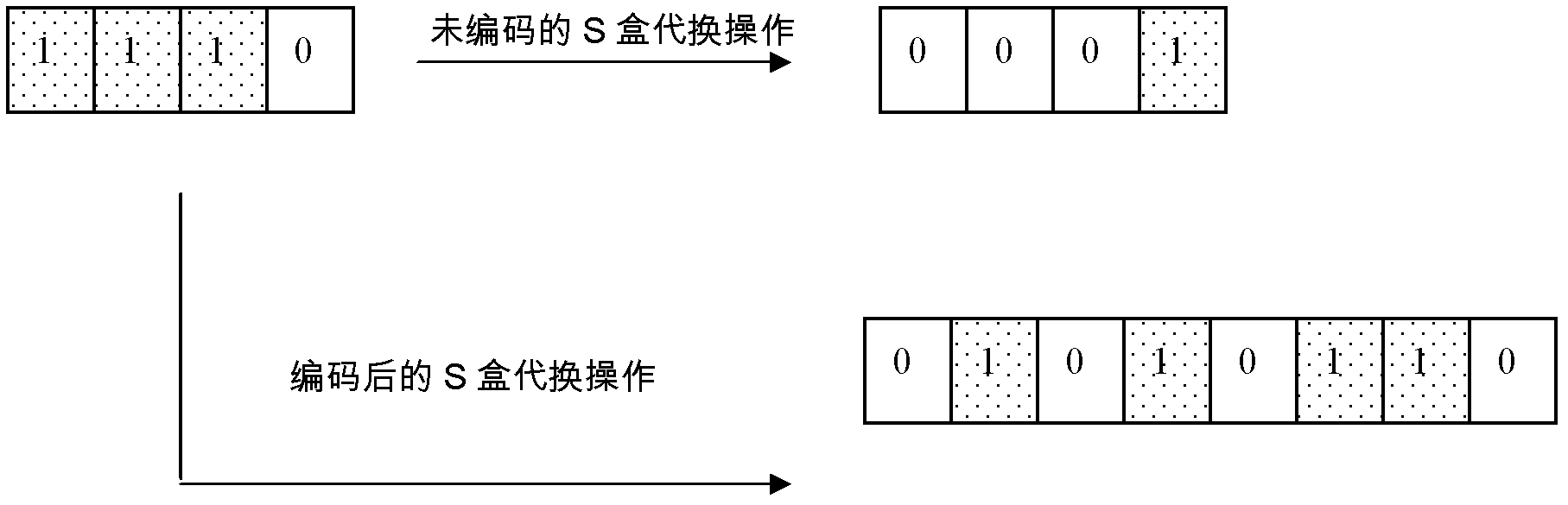
[0072] In the specific application of this defense method, abnormal data may be encountered, that is, data that does not conform to the coding rules, and this situation becomes an abnormal situation. It corresponds to the normal situation. The specific implementation of the defended method is introduced for the normal situation and the abnormal situation respectively.
[0073] normal circumstances
[0074]This defense measure provides protection for the intermediate value of the cryptographic algorithm, and protects all or part of the intermediate value in the operation process according to the security requirements. For example, under low security requirements, only the intermediate values of the first several rounds and the last several rounds of the algorithm can be protected, and the remaining intermediate values are not protected. Under higher security requirements, the intermediate value of each round of the algorithm can be protected. The defense method encodes t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com