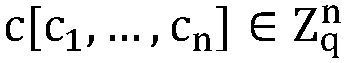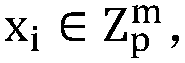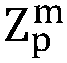Linear SVM model training algorithm for privacy protection based on vector homomorphic encryption
A homomorphic encryption, privacy protection technology, applied in the field of information technology security, can solve the problems of user privacy leakage, training data information is not private, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0051] A privacy-preserving linear SVM model training algorithm based on vector homomorphic encryption. It is assumed that the training data set X is a matrix composed of t z-dimensional vectors, and each piece of data in the training data set X has a label value representing a category. The label values are arranged in the order of each piece of data in the training data set X to form a data label vector y[y 1 ,...,y t ]. The linear SVM model training algorithm includes the following steps:
[0052] Step 1: The user uses the vector-based homomorphic encryption scheme VHE to encrypt the training data set, and sends the encryption result to the server. Include the following steps:
[0053] S1.1. Initialize the key matrix S[S 11 ,...,S wv ].
[0054] The user first determines the number of rows and columns of the key matrix S, and then randomly generates the values in the matrix.
[0055] S1.2. Encrypt the training data set X through the key matrix S to obtain the cip...
Embodiment 2
[0090] On the basis of Embodiment 1, when processing the polynomial kernel function containing the linear kernel function, the polynomial kernel function is first split into two parts: the linear kernel function and the nonlinear kernel function. Firstly, the linear kernel function is calculated under the ciphertext and the kernel function table of the plaintext is obtained, and then the value in the kernel function table is added to the value of the kernel function table under the plaintext by adding 1 again to complete the calculation of the polynomial kernel function. Because the linear kernel function part is calculated under the ciphertext, the training data set is in a confidential state, and the server still cannot obtain the information of the training data set after the operation of adding 1 and the power, so the SVM model of the polynomial kernel function can also be used Trained under ciphertext.
Embodiment 3
[0092] On the basis of Embodiment 1, when processing the Gaussian kernel function containing the linear kernel function, it is necessary to use the Euclidean distance between any two in the training data, and VHE can calculate the distance between two vectors under the ciphertext , so the calculation of the Gaussian kernel function can be split into two parts: the linear kernel function and the Gaussian function. First calculate the distance between any two vectors under the ciphertext, and then calculate the Gaussian function under the plaintext. Since the distance between vectors is calculated in ciphertext and the training data is kept secret, the server cannot deduce the specific values of the two vectors from the vector distance. Even if the Gaussian function is calculated in plaintext, the server still cannot get information about the training data. set of information.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com