Method for processing RSA password based on residue number system and coprocessor
A technology of remainder system and processing method, which is applied in the direction of calculation using non-number system representation and calculation using residual algorithm, which can solve the problems of high data processing degree and difficult to obtain.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
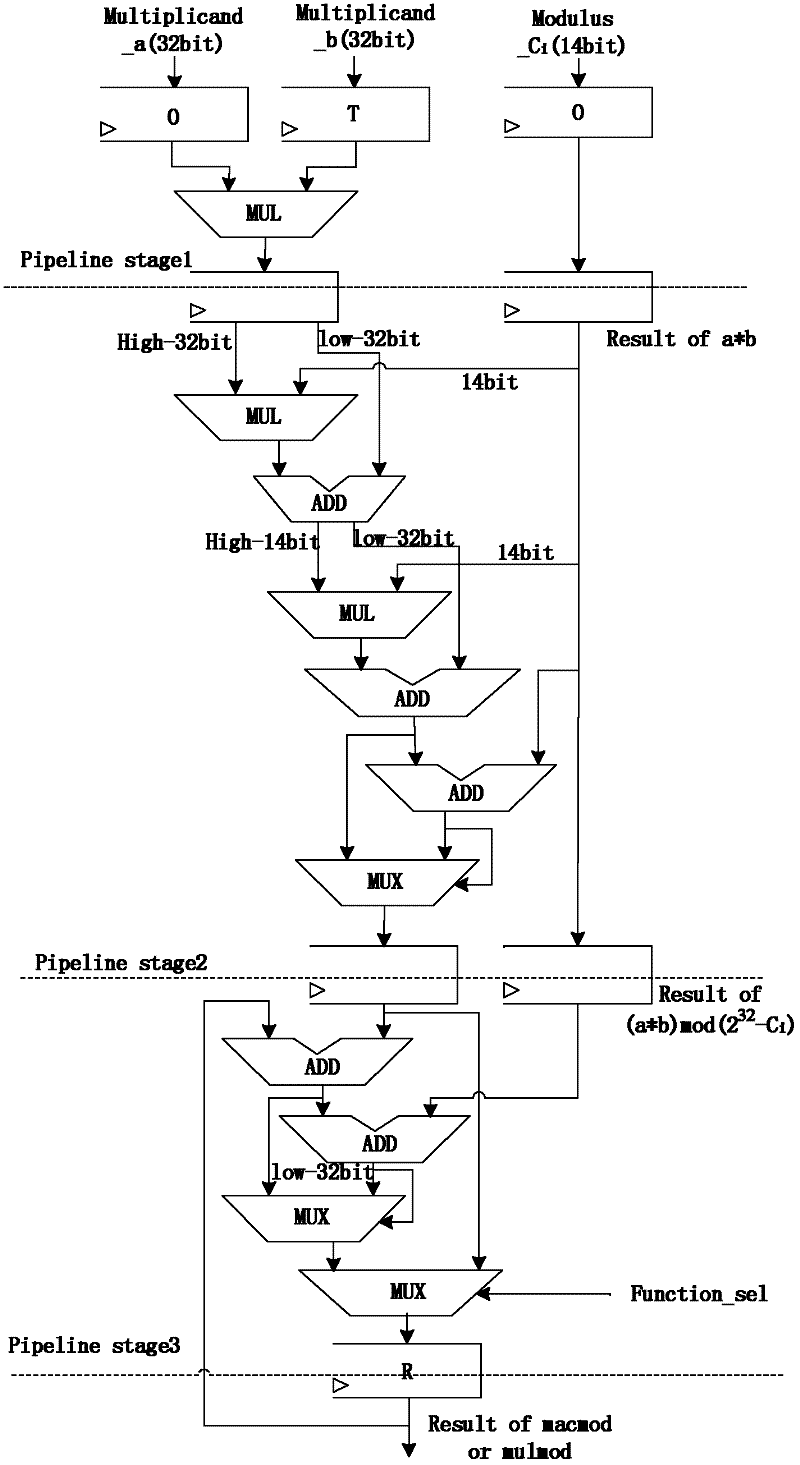
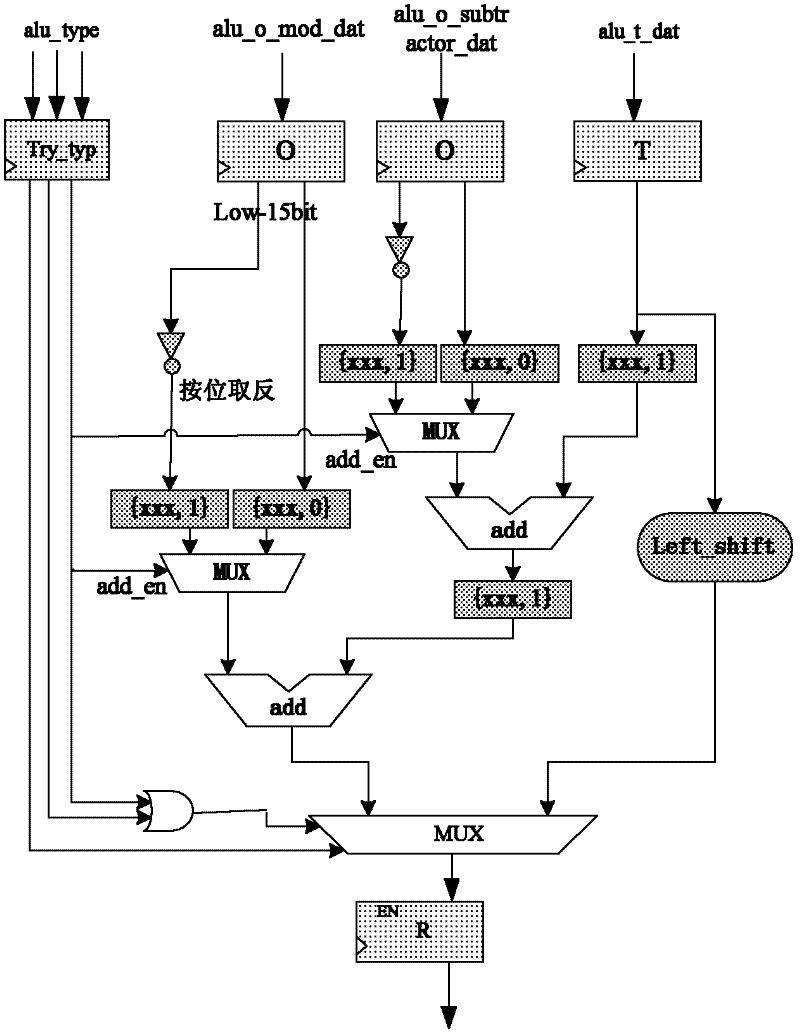
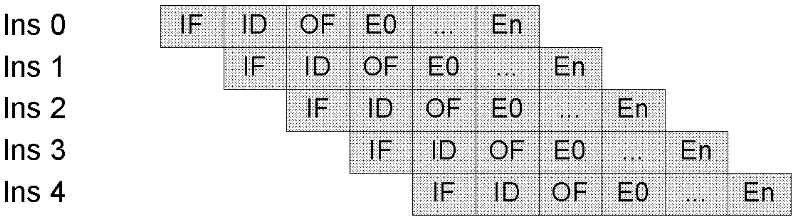
[0076] The Montgomery modular multiplication algorithm based on RNS (Residue Number System) is an effective implementation of the RSA algorithm. The basic operations in Montgomery's modular multiplication are addition and multiplication. The advantage of RNS is that addition, subtraction, and multiplication are very simple decimal operations, which can independently calculate each element in RNS, which enables the combination of Montgomery multiplication and RNS algorithm to achieve fast parallel processing.
[0077] The present invention is a cryptographic processor with a TTA-Like architecture, which makes full use of the parallelism of RNS to realize the RSA algorithm. By designing a special modular multiplication unit and utilizing the cascading between functional units, the RSA processing efficiency is effectively improved. decryption performance.
[0078] The present invention is an RSA cryptographic coprocessor based on the remainder system. Studies have shown that in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com