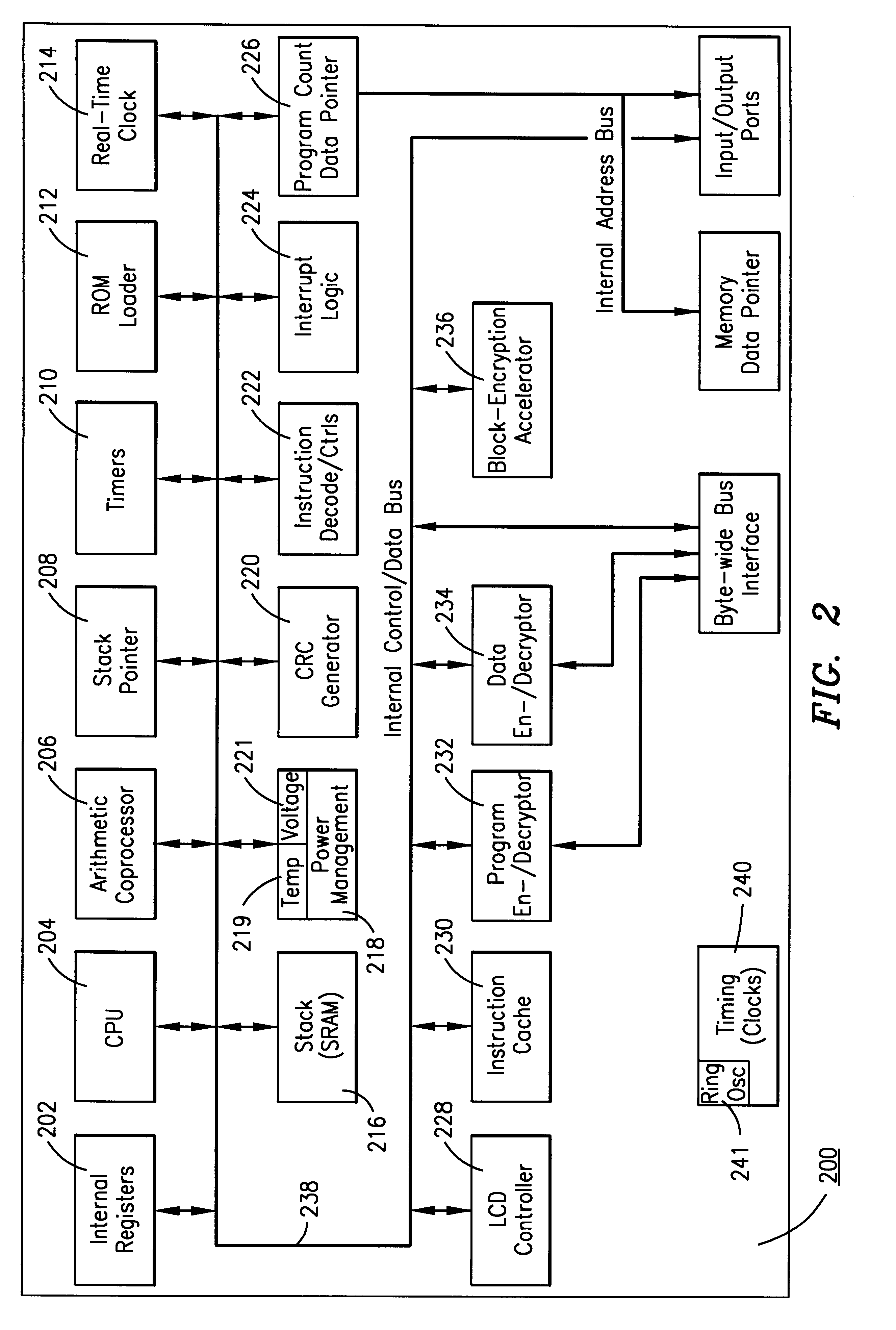
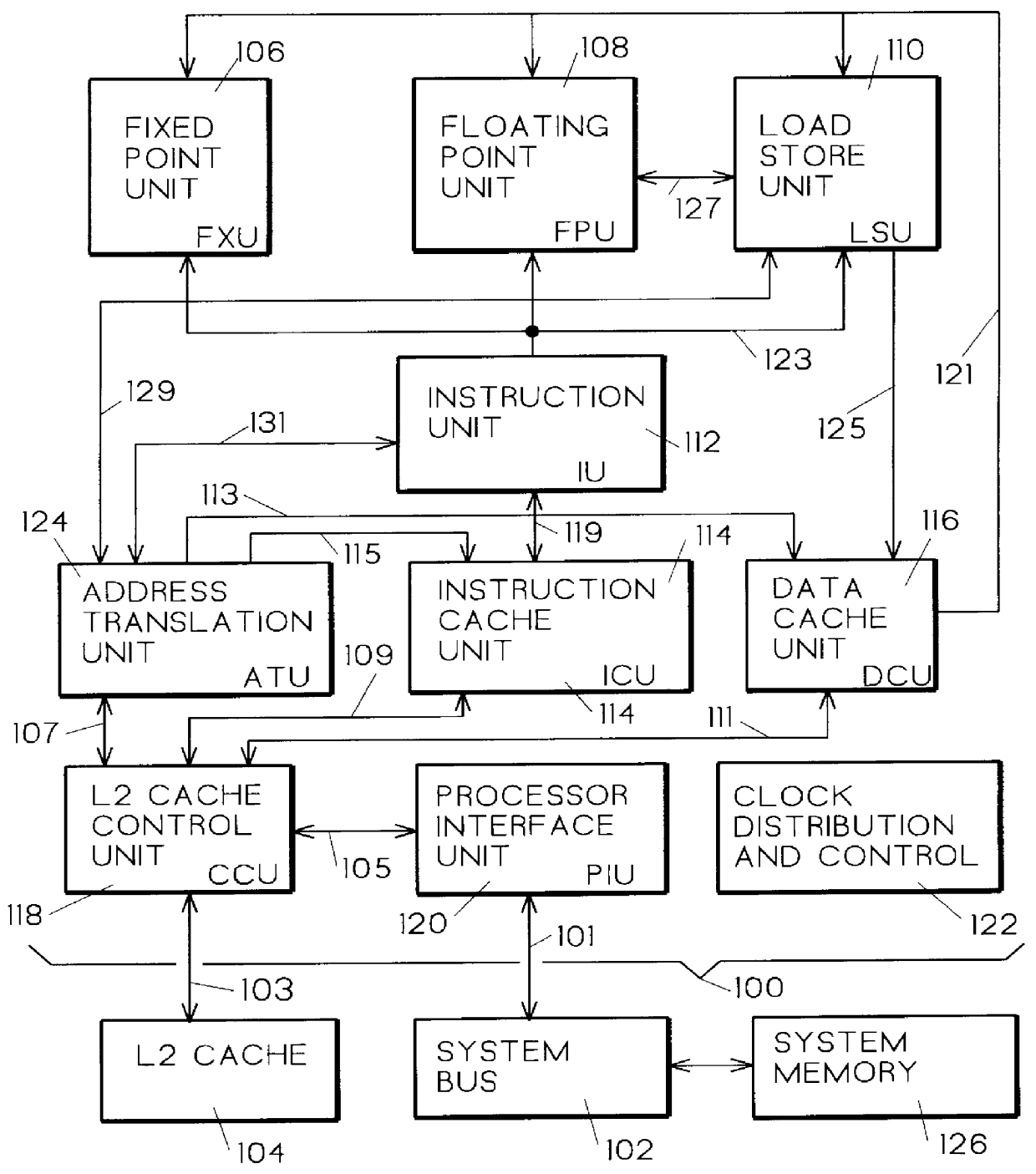
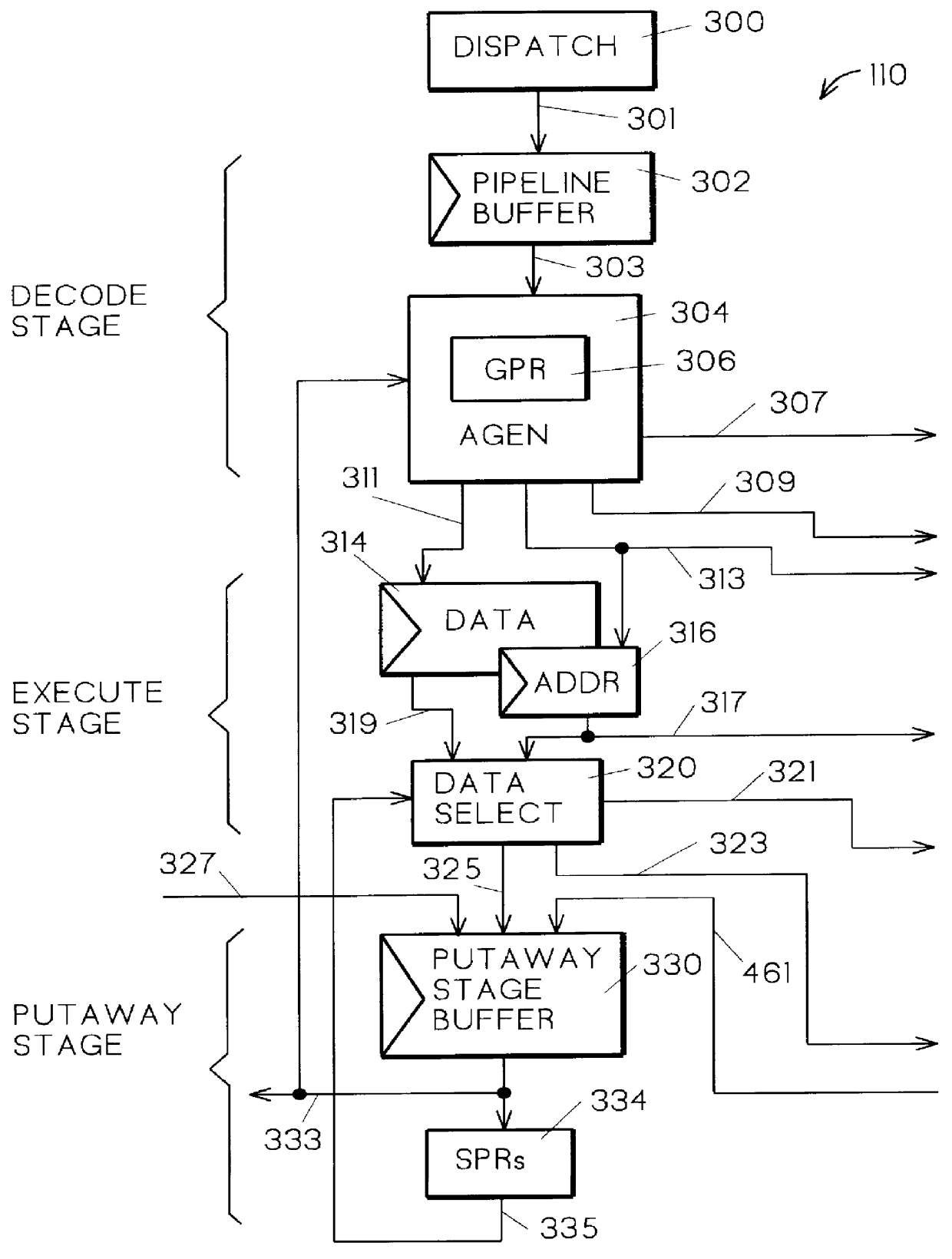
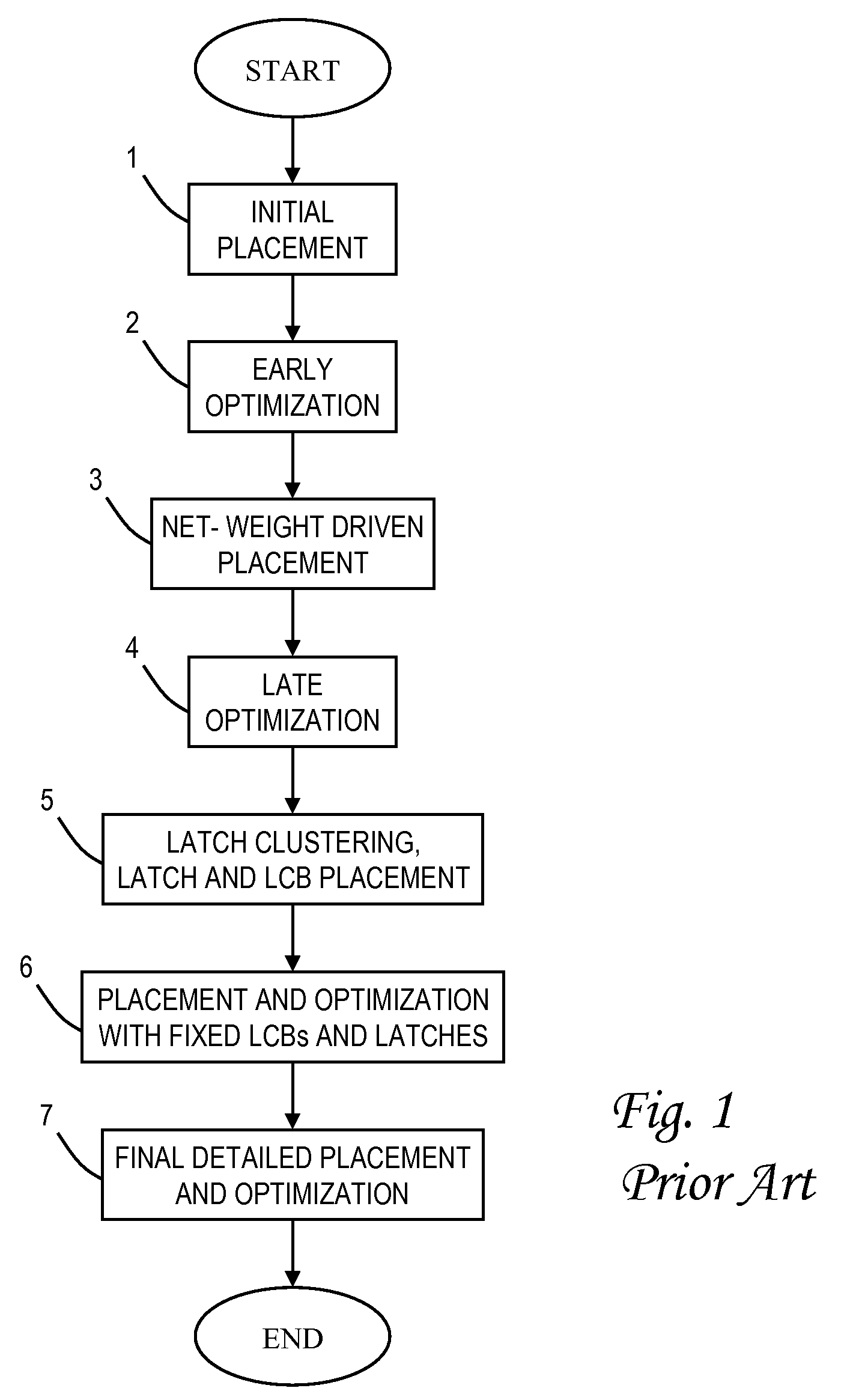
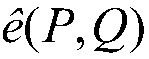Patents
Literature
61 results about "Microprocessor design" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
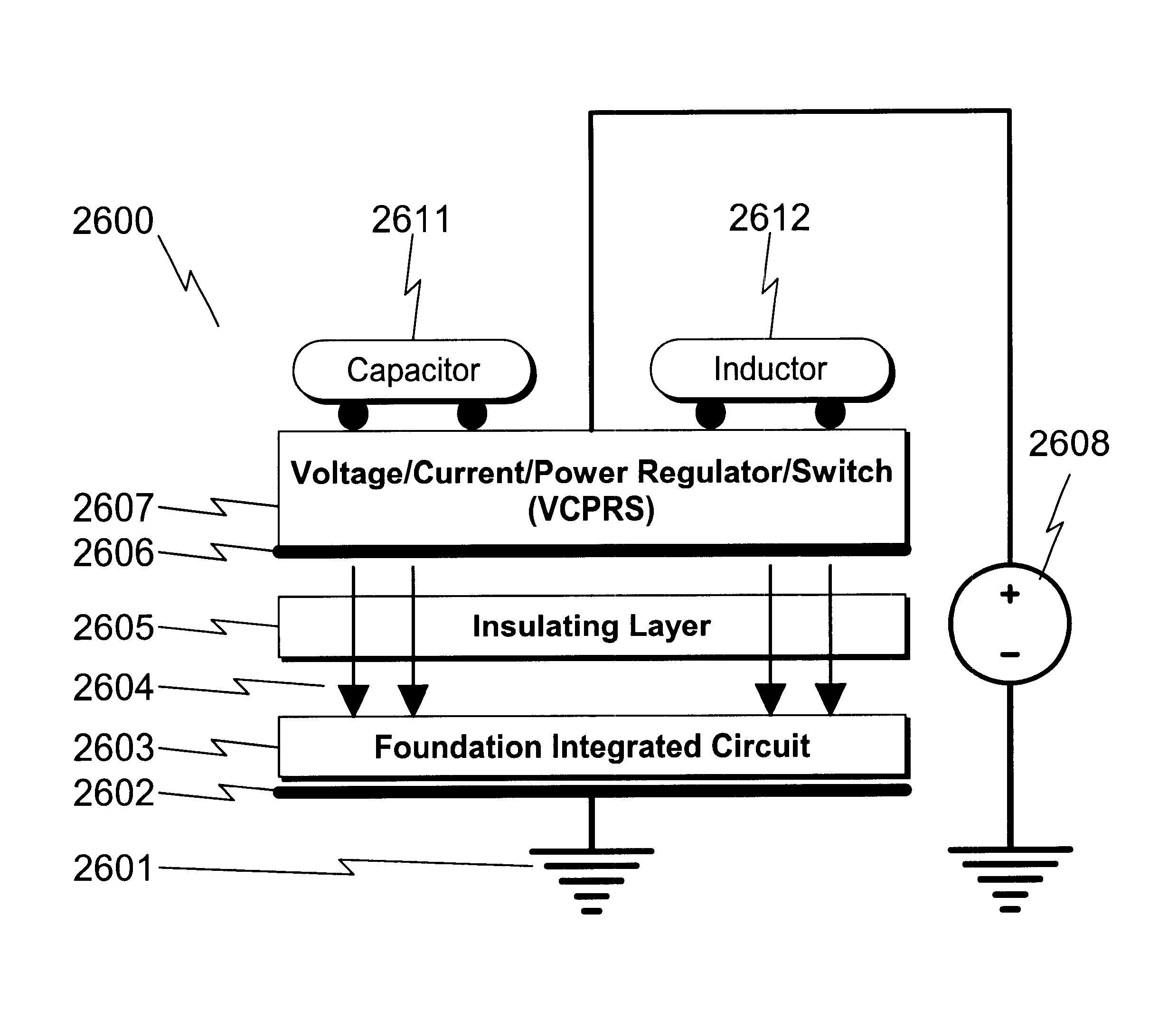
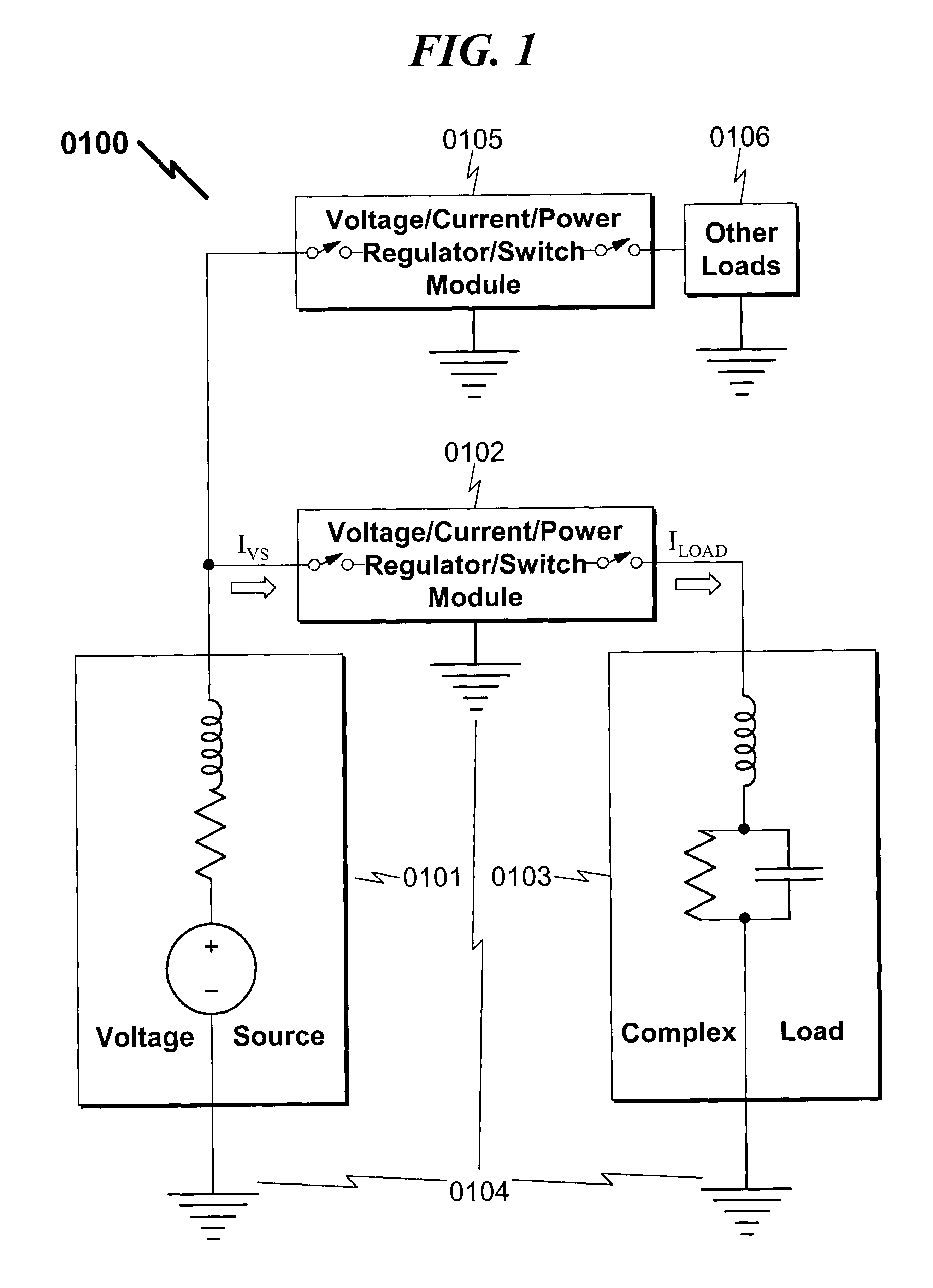
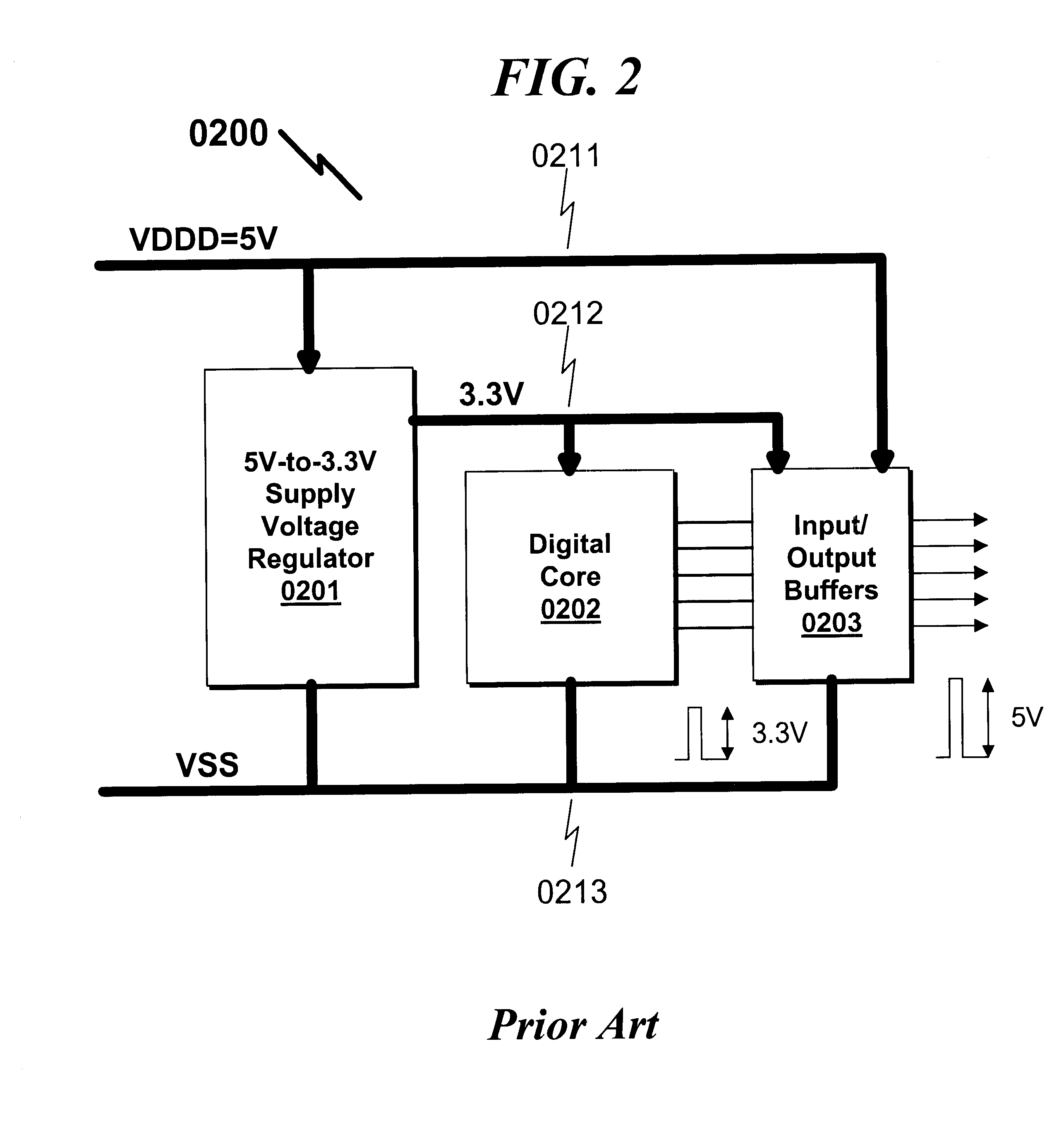
Integrated voltage/current/power regulator/switch system and method
InactiveUS6396137B1Minimal noiseGood PSRRSemiconductor/solid-state device detailsDc-dc conversionPower applicationPower capability
An integrated voltage / current / power regulator / switch (VCPRS) system and method are disclosed in which regulator / switch circuitry is vertically integrated on top of an existing integrated circuit. The present invention does not require additional integrated circuit chip area for the regulator pass device as is required in the prior art, and by virtue of its construction provides a significantly reduced on-resistance as compared to all prior art implementations. The present invention both stabilizes the power supply for large area integrated circuits and permits individual areas of the integrated circuit to have switched power capability, a highly desirable feature in low power and battery power applications. The present invention permits an increase in the power supply rejection ratio (PSRR) for digital, analog, and especially mixed-signal integrated circuit designs by permitting various circuit blocks to have localized power regulation that is obtained from a common power supply plane within the integrated circuit framework. Finally, the present invention appears to be the only economically practical method of addressing the power supply regulation requirements of modern and future integrated microprocessor designs.
Owner:KLUGHART KEVIN MARK
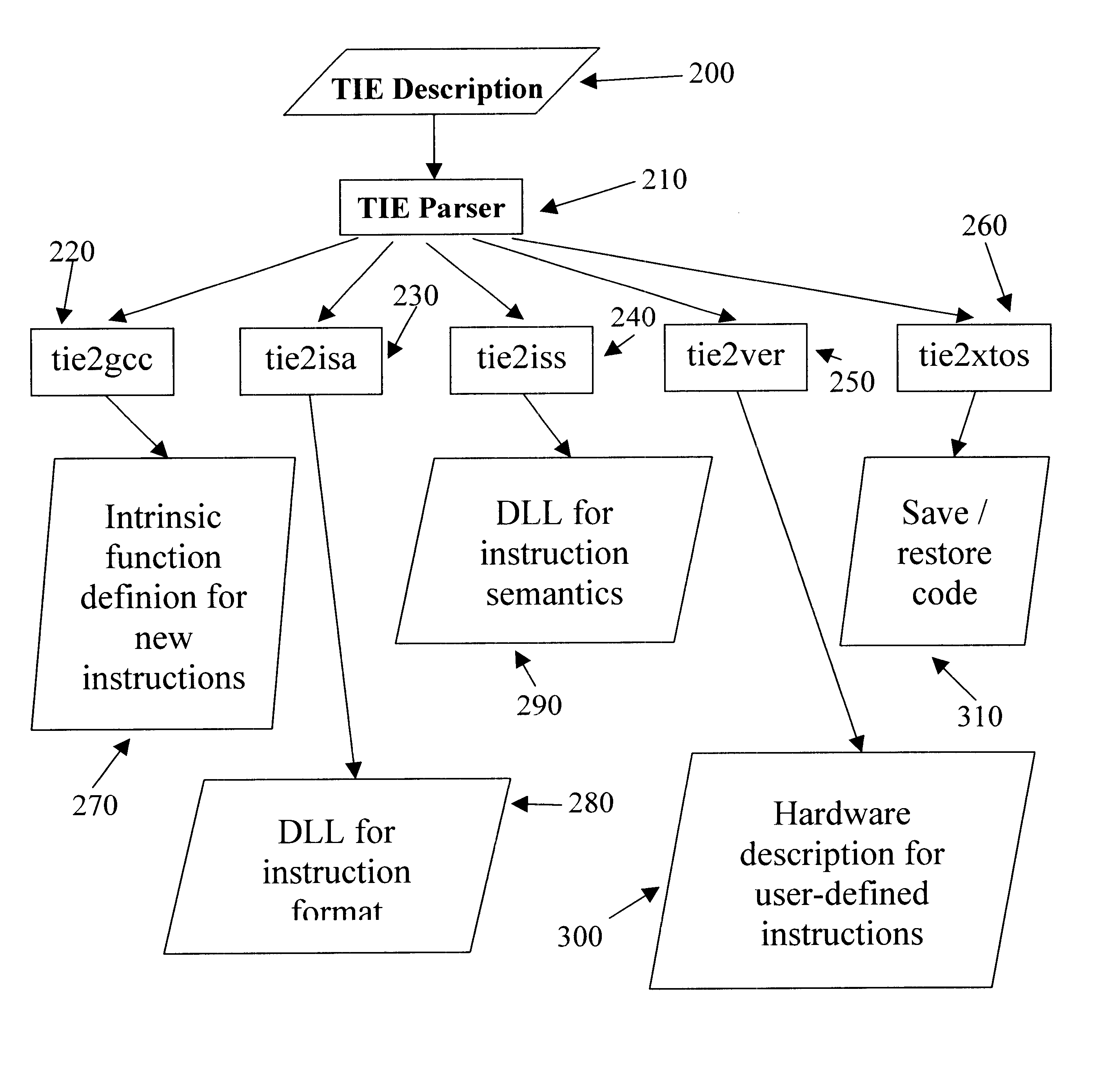
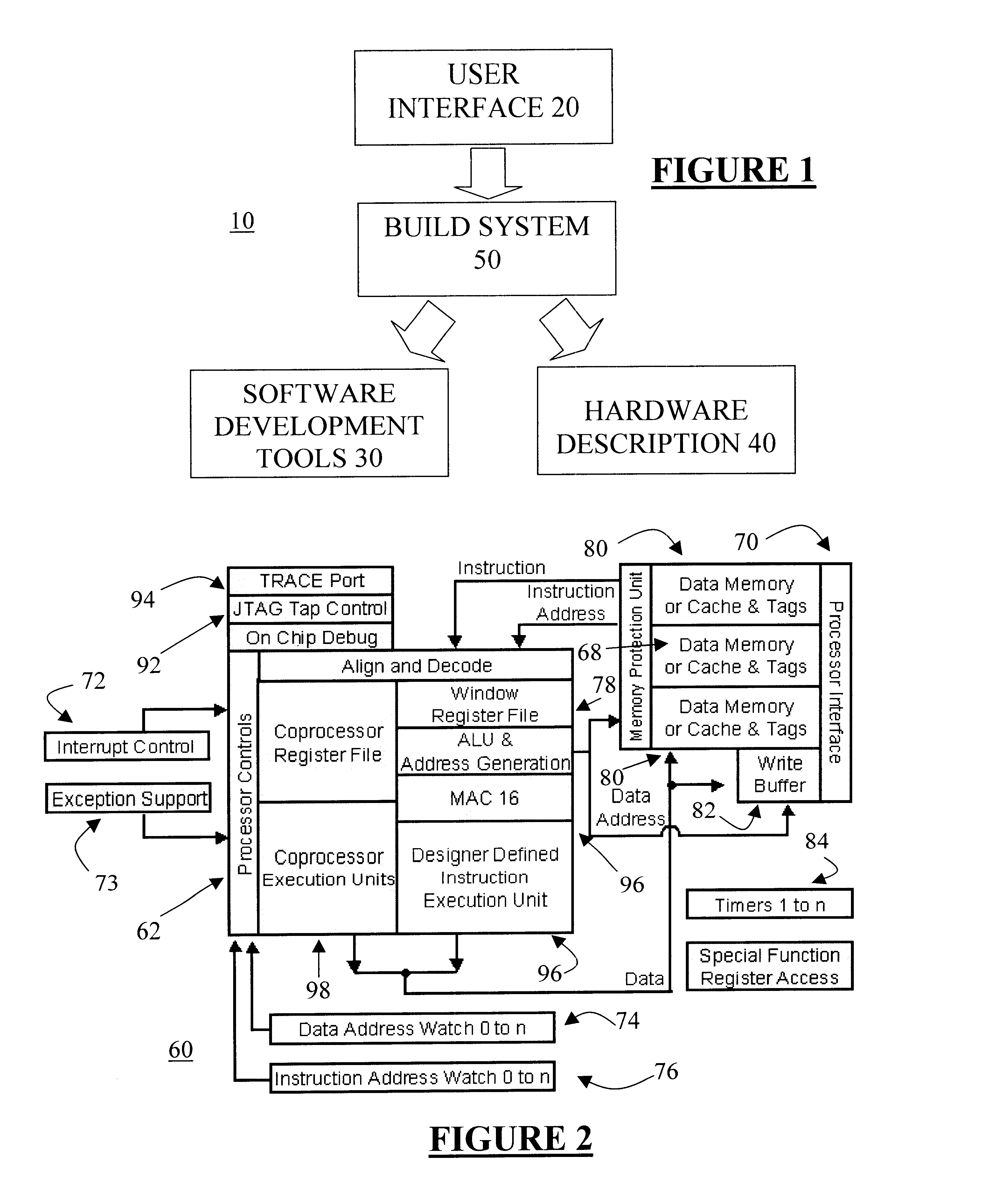
Adding complex instruction extensions defined in a standardized language to a microprocessor design to produce a configurable definition of a target instruction set, and hdl description of circuitry necessary to implement the instruction set, and development and verification tools for the instruction set
InactiveUS6477697B1Fast and reliable developmentGeneral purpose stored program computerCAD network environmentApplication softwareProcessor design
An automated processor design tool uses a description of customized processor instruction set extensions in a standardized language to develop a configurable definition of a target instruction set, a Hardware Description Language description of circuitry necessary to implement the instruction set, and development tools such as a compiler, assembler, debugger and simulator which can be used to develop applications for the processor and to verify it. The standardized language is capable of handling instruction set extensions which modify processor state or use configurable processors. By providing a constrained domain of extensions and optimizations, the process can be automated to a high degree, thereby facilitating fast and reliable development.
Owner:TENSILICA
Integrated circuit having hardware circuitry to prevent electrical or thermal stressing of the silicon circuitry
InactiveUS6330668B1Digital data processing detailsAnalogue secracy/subscription systemsElectricityEngineering
An integrated circuit, such as a microprocessor, which incorporates hardware mechanisms to prevent the circuitry from operating outside the proper bounds of design. The hardware circuitry prevents the microprocessor circuitry from being forced to operate at clock speeds that are greater than it is designed for, from operating at temperatures above or below that which it is designed for, and from being forced to operate at voltages that are above or below voltages that the microprocessor is designed to operate at.
Owner:MAXIM INTEGRATED PROD INC
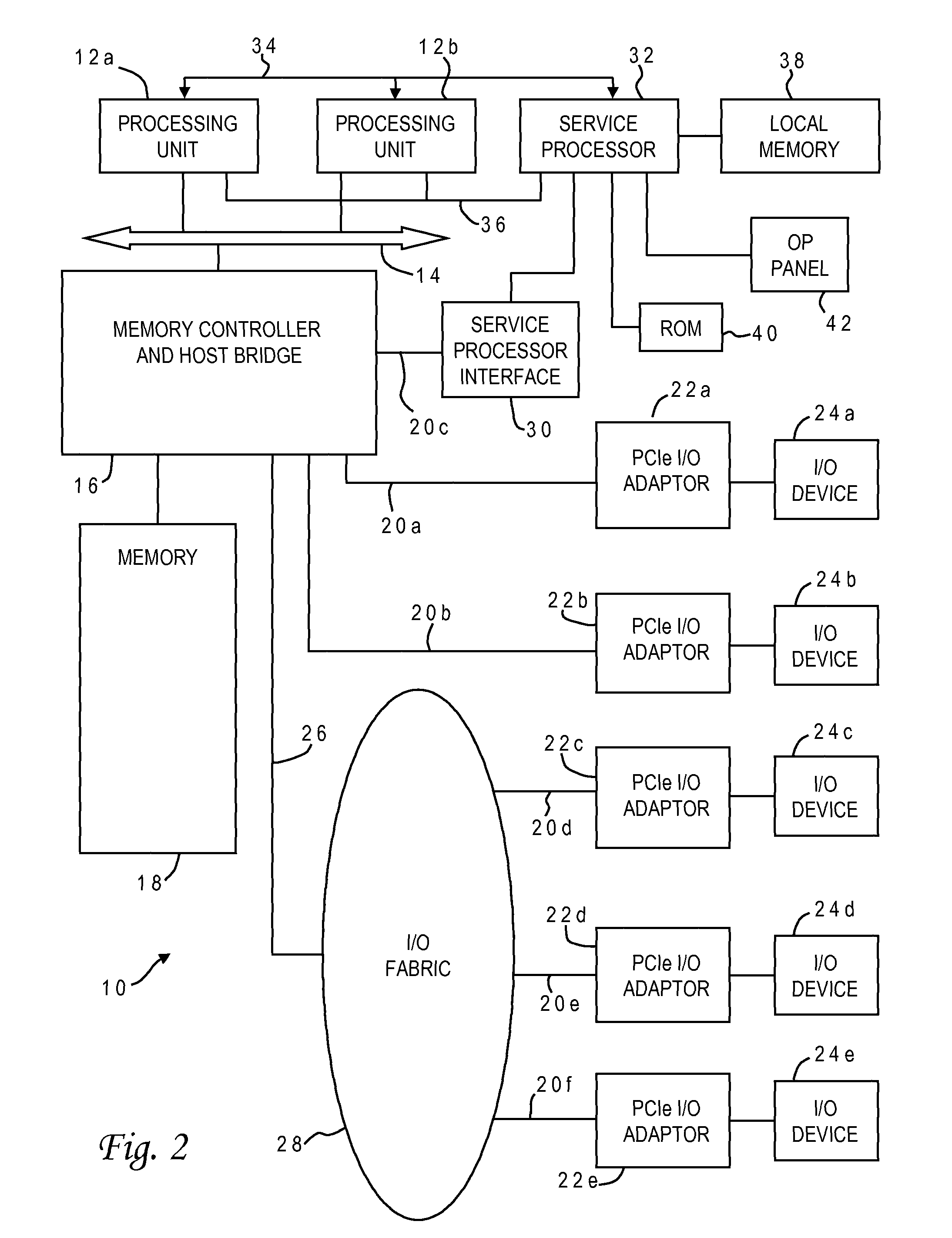
Method and apparatus for configurable multiple level cache with coherency in a multiprocessor system
A coherency controller for configurable caches. A base microprocessor design accommodates system configurations both with and without L2 cache tag and data arrays installed. Second level cache control logic exists within the microprocessor chip, and when the external second level cache tag and data arrays are removed their inputs to the microprocessor are tied to an inactive state. A configuration switch is set in the second level cache controller that causes snoop requests from a system bus to get reflected onto a first level cache snooping path. The first level cache status is then fed back to the second level cache controller, in a manner consistent with the timing required for support of a second level cache search, and fed into the second level cache status signal generation logic, effectively making the second level cache controller believe that the second level cache still exists for snooping. All other actions remain the same in the second level cache controller providing an effective and simple method for supporting snooping bus protocols. A result is that now every bus request snoops the first level cache without knowledge of presence of an L2 cache. This environment is provided to support entry level single processor configurations where the snooping requests only amount to input / output traffic.
Owner:IBM CORP
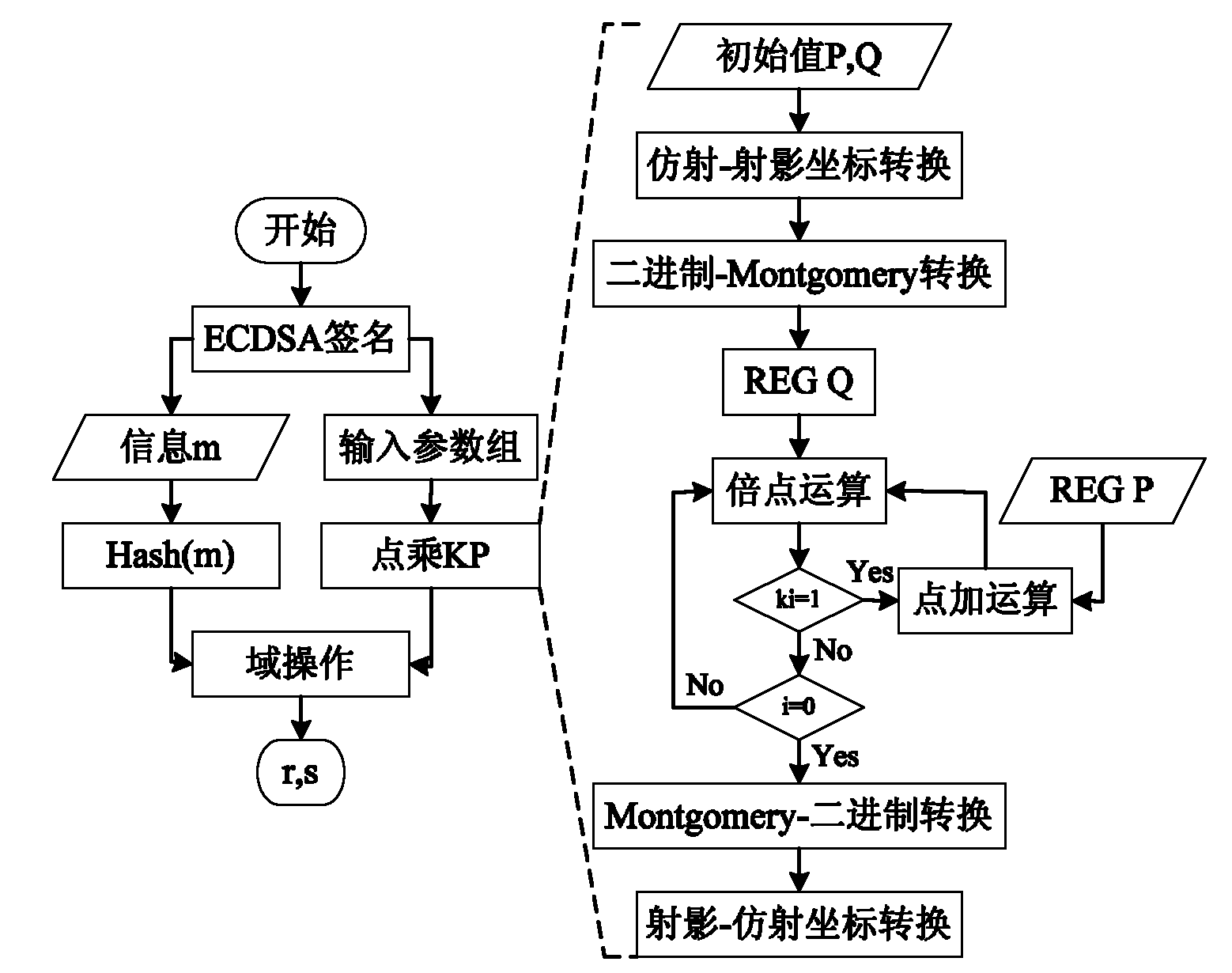
Method for processing RSA password based on residue number system and coprocessor
ActiveCN102231102AImprove decryption performanceImprove parallelismComputations using residue arithmeticCoprocessorPassword
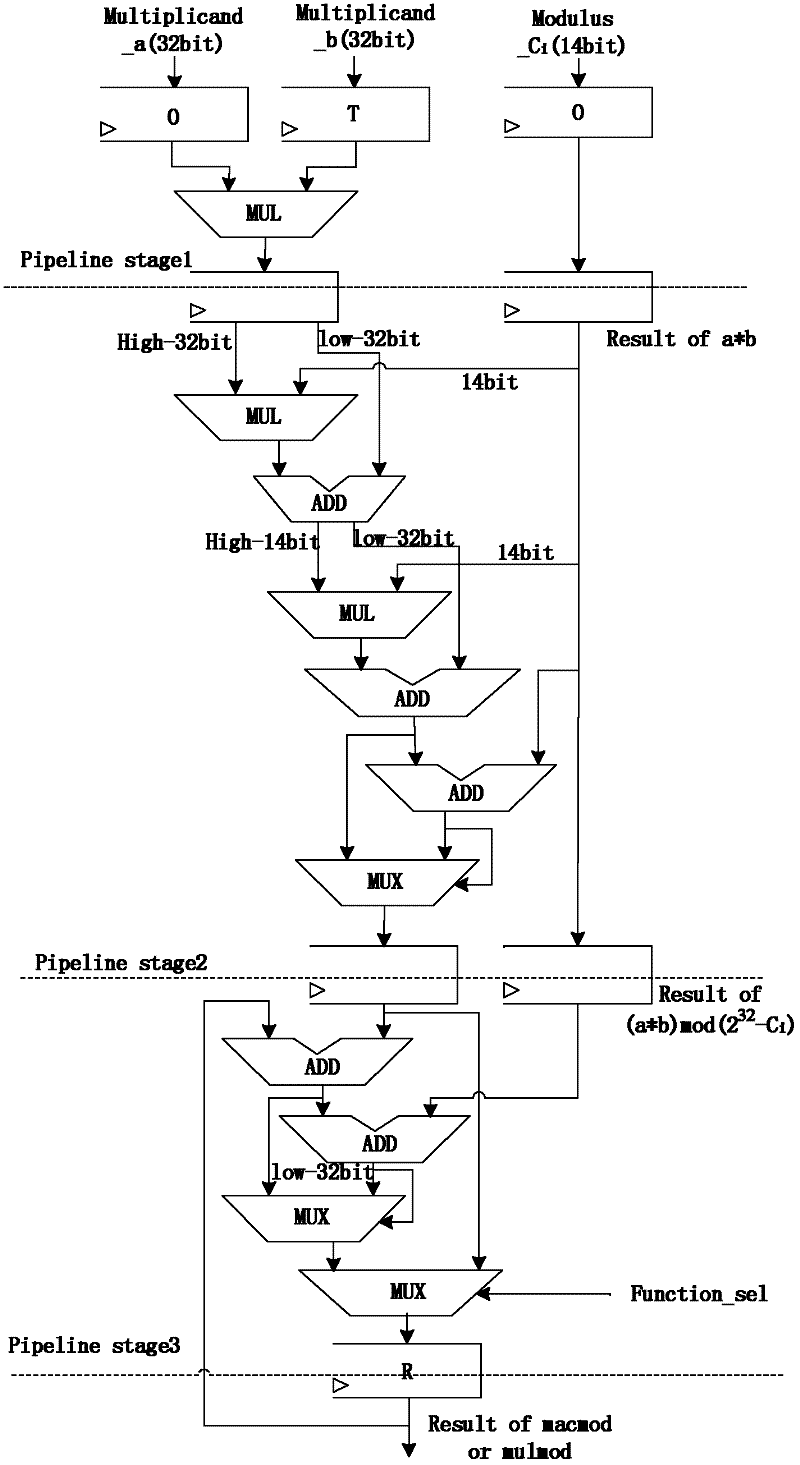
The invention relates to information technology security and microprocessor design. Aiming at increasing RSA (Ron Rivest, Adi Shamirh and LenAdleman) modular multiplication operation speed and improving RSA encryption and decryption performances, the invention provides the technical scheme as follows: a method for processing an RSA password based on a residue number system comprises the followingsteps of performs encryption and decryption operations by using an RSA algorithm and performing large-number modular exponentiation of the RSA algorithm by using an L-R (Left-Right) binary scanning modular power algorithm; an improved Montgomery algorithm is specifically as follows: 1024-bit large numbers with are expressed as numbers under the residue number system, namely two sets of 33 32-bit decimal numbers and one 32-bit number expressed under a redundancy base; an expression process is a mould solving process; the decomposed 32-bit decimal numbers respectively participate in 32-bit modular multiplication, modular multiplication accumulation and modular addition operation independently; furthermore, 32-bit data performs parallel execution operation without dependence; and the method disclosed by the invention is mainly applicable for the information technology security and microprocessor design.
Owner:PHYTIUM TECH CO LTD
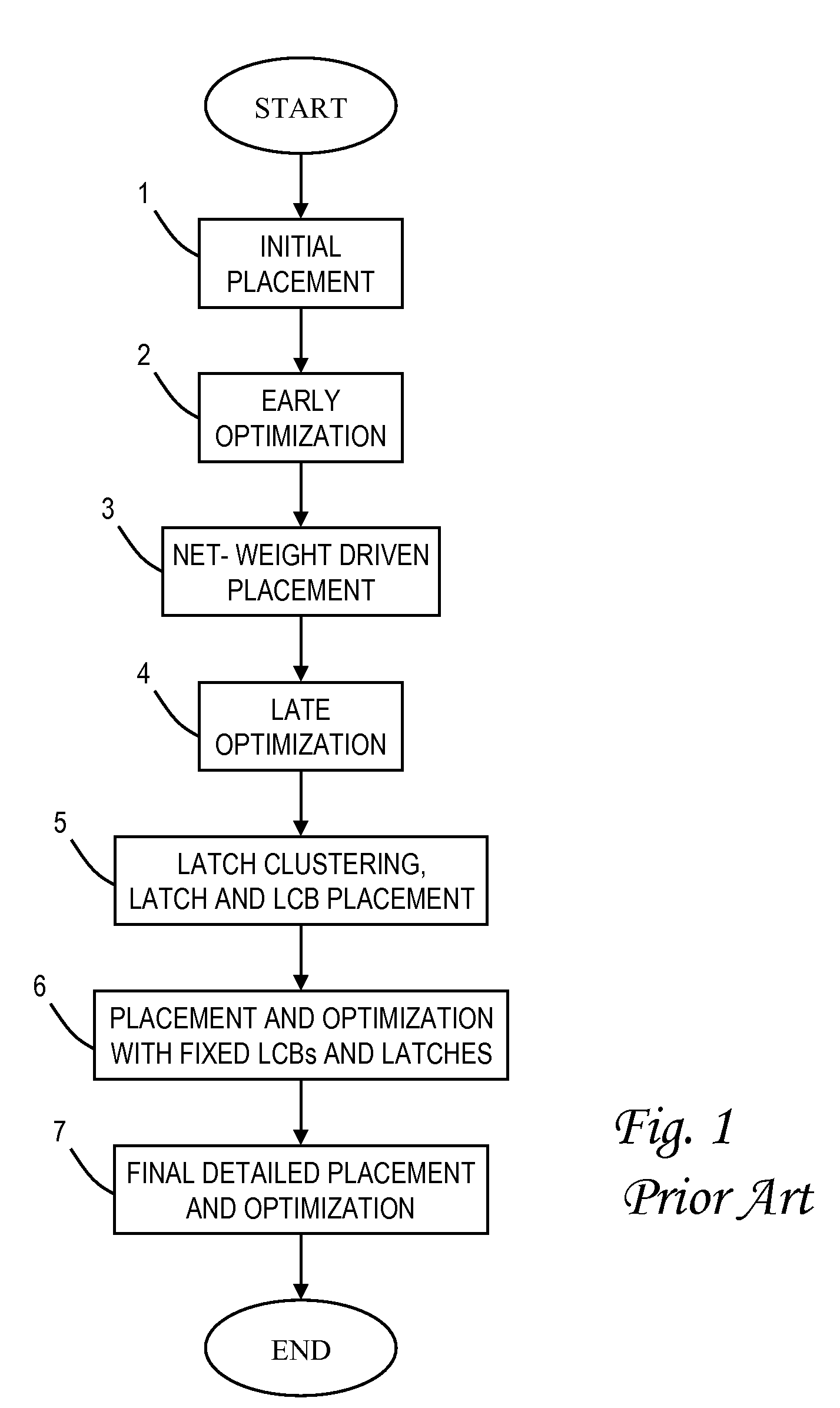
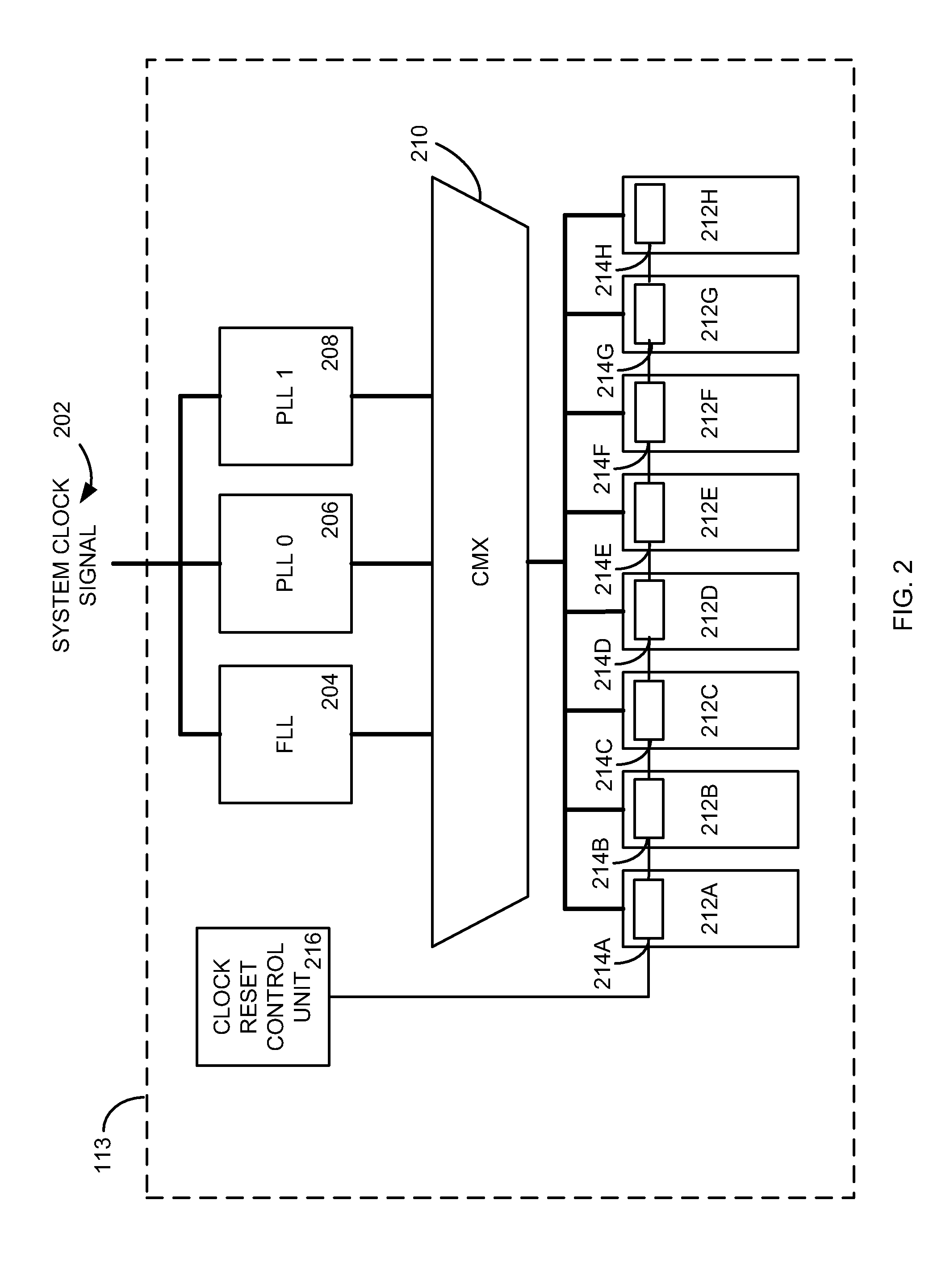
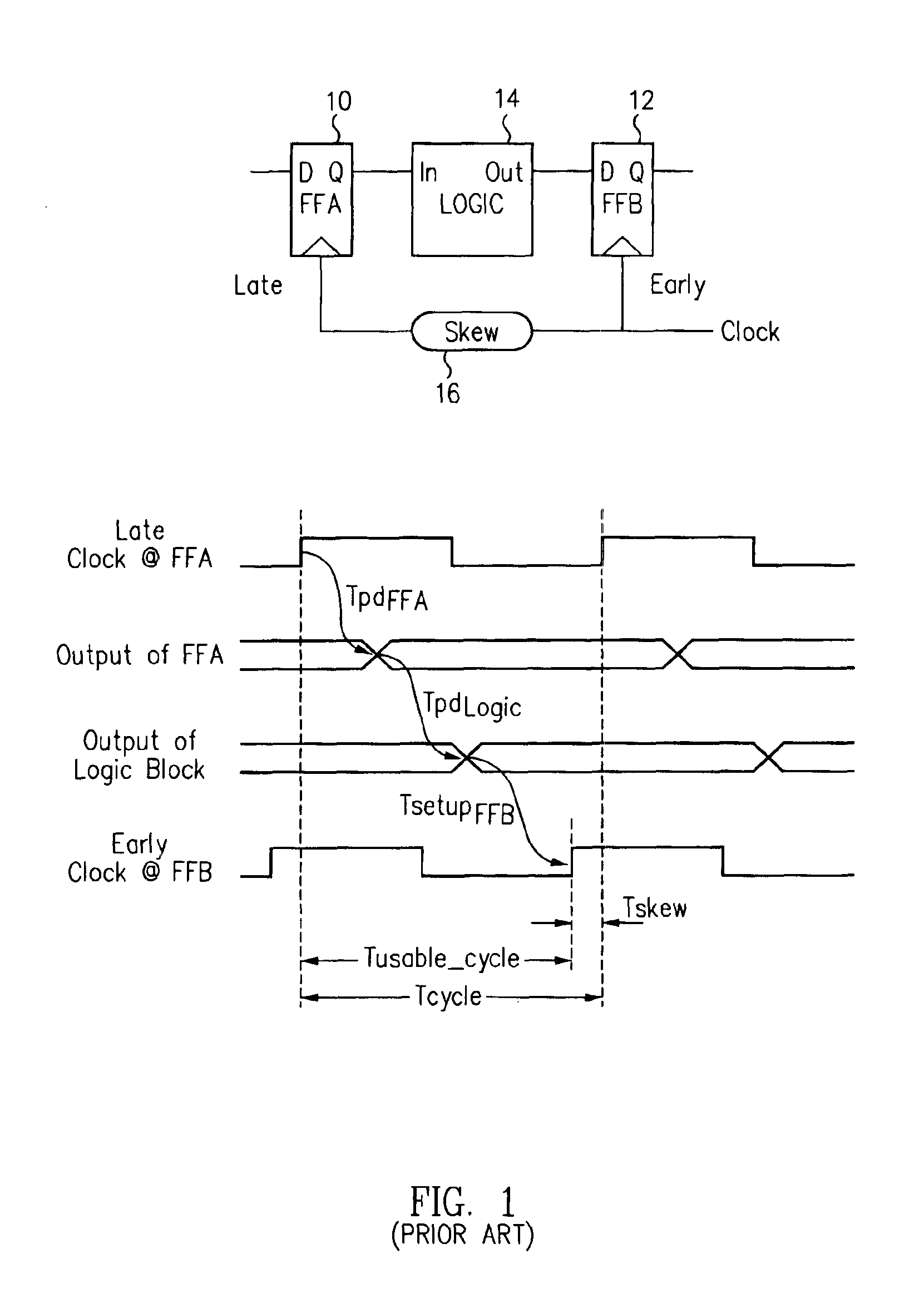
Clock power minimization with regular physical placement of clock repeater components
InactiveUS20090193376A1Improves clock powerReducing clock skewComputer aided designSpecial data processing applicationsCapacitanceModem device
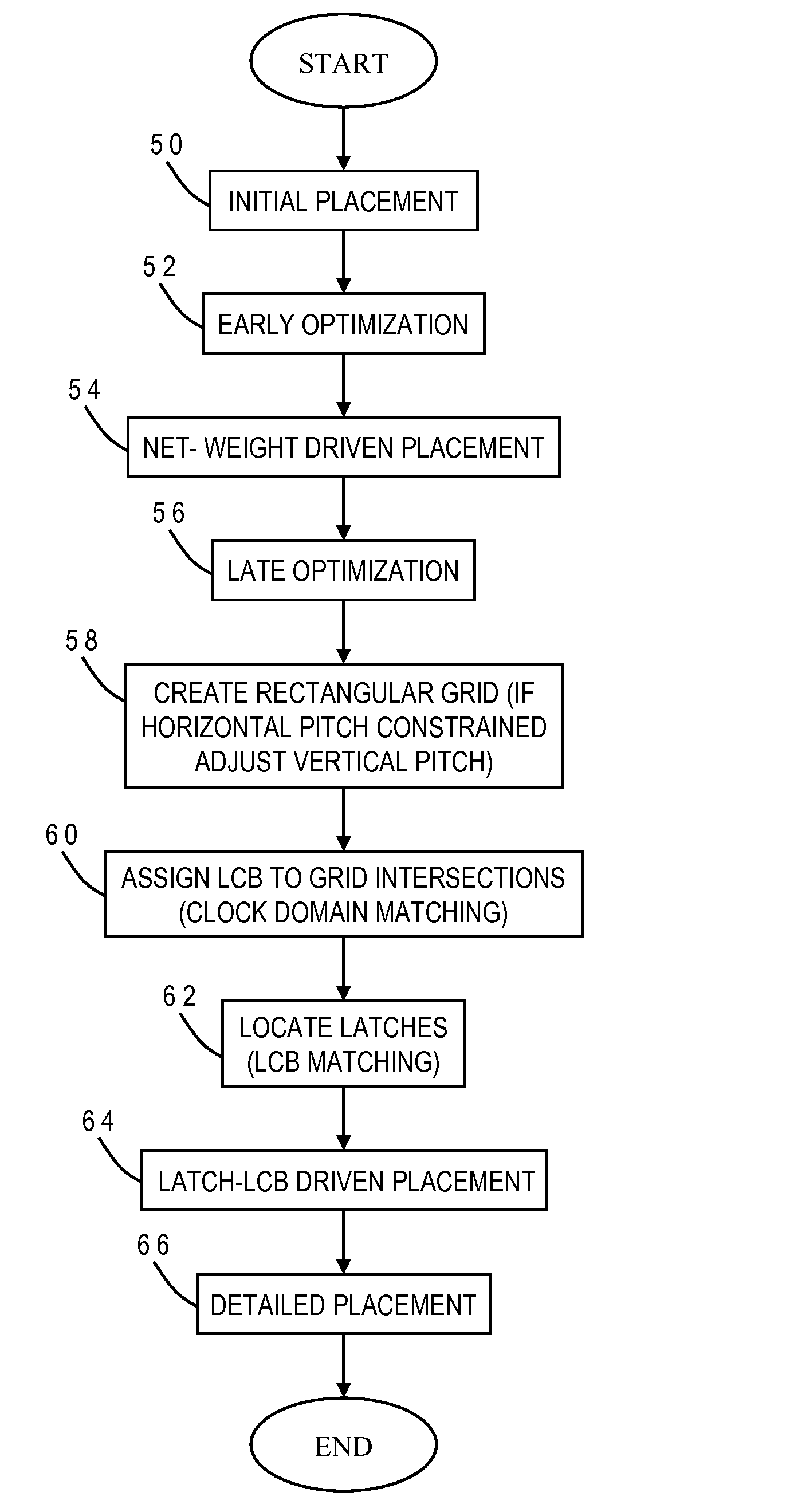
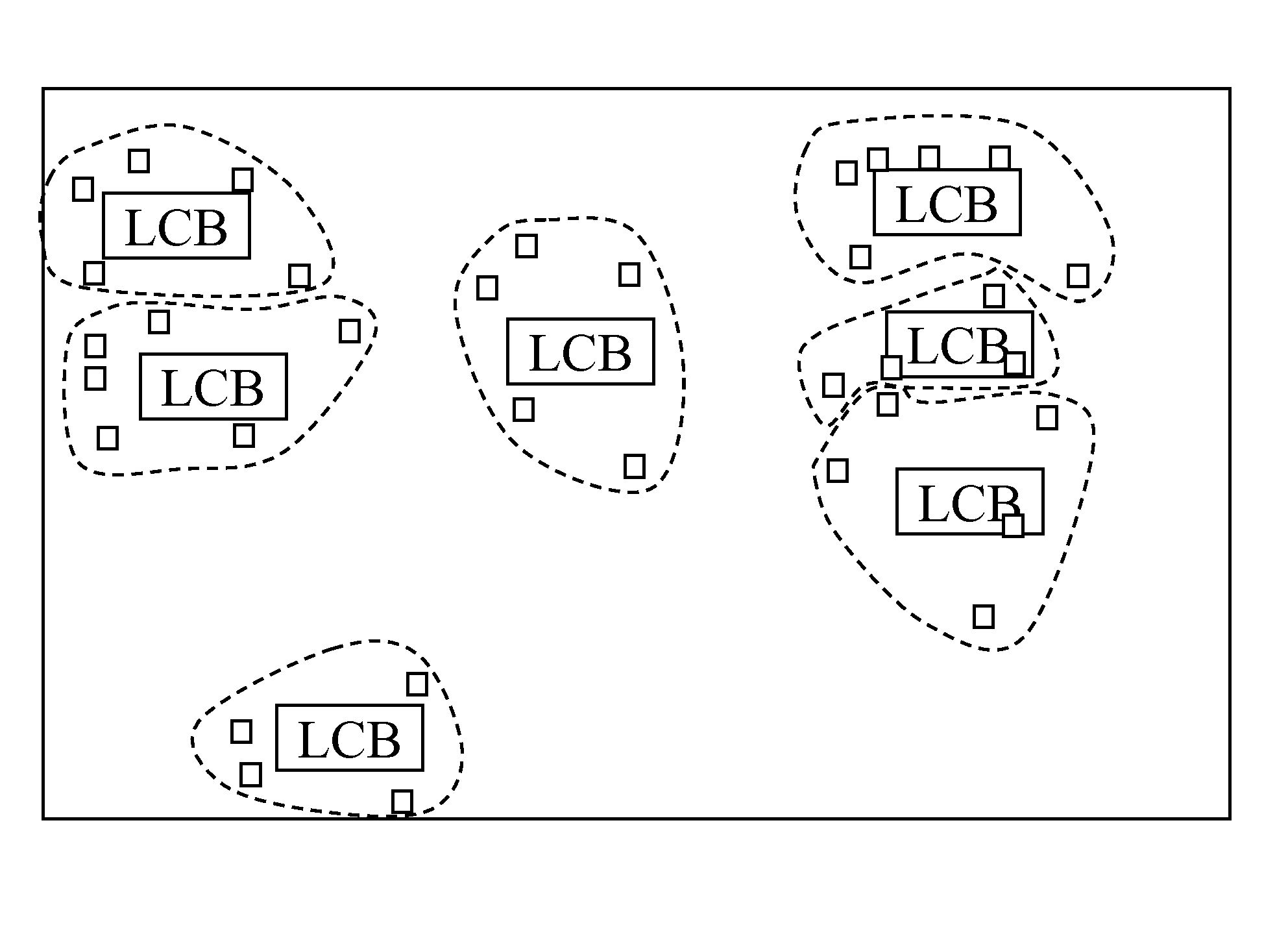
Power, routability and electromigration have become crucial issues in modem microprocessor designs. In high performance designs, clocks are the highest consumer of power. Arranging clocking components with regularity so as to minimize the capacitance on the clock nets can help reduce clock power, however, it may hurt performance due to some loss of flexibility in physically placing those components. The present invention provides techniques to optimally place clock components in a regular fashion so as to minimize clock power within a performance constraint. A rectangular grid is created and clock distribution structures are assigned to the grid intersection points. Latches are then located around the clock distribution structures to minimize an overall distance for connections between the latches and respective clock distribution structures. The horizontal and vertical pitches of the grid may be independently adjusted to achieve a more uniform spread of the clock distribution structures.
Owner:IBM CORP
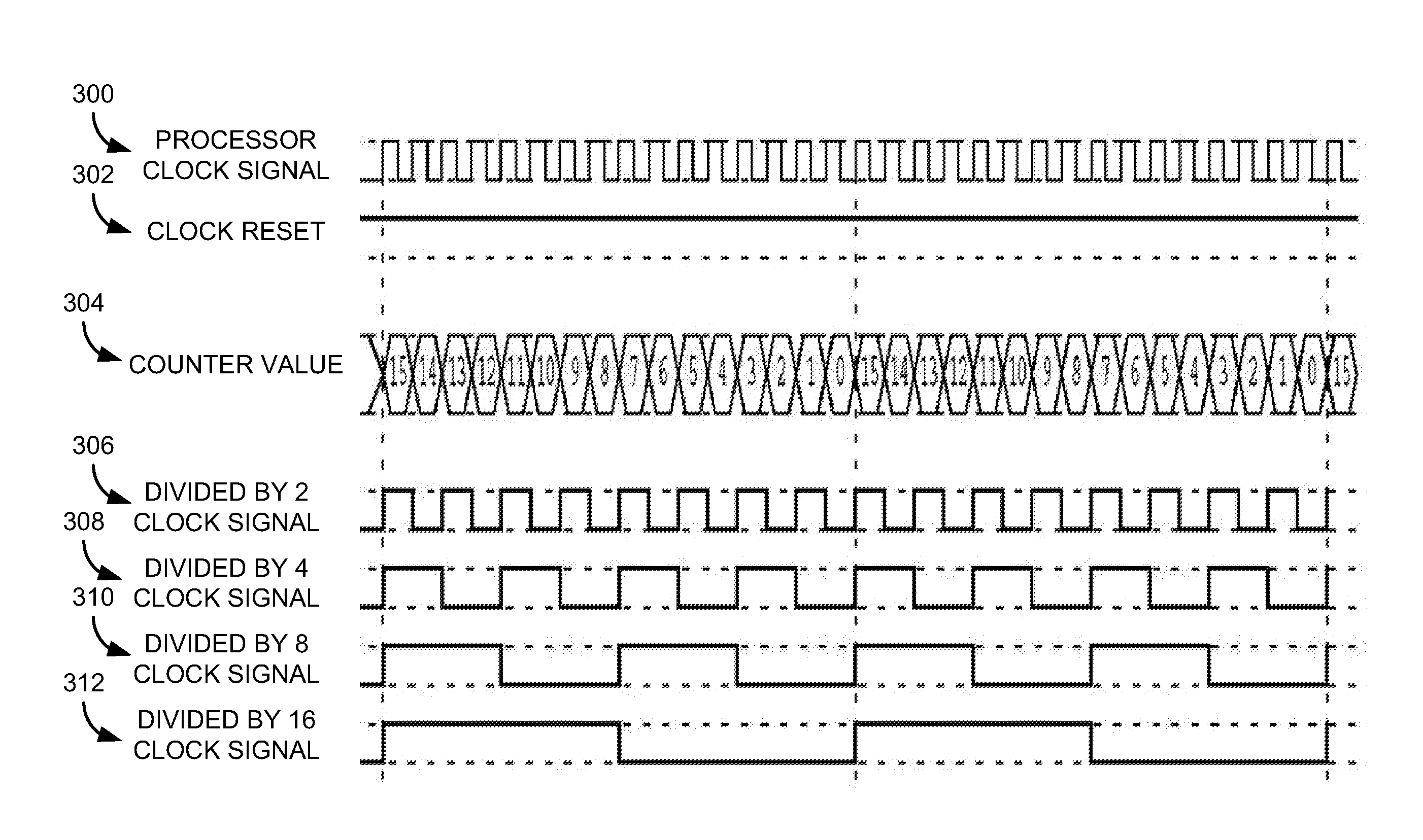
Method and apparatus for distributed generation of multiple configurable ratioed clock domains within a high speed domain
ActiveUS20140082396A1Generating/distributing signalsTransmission path multiple useClock rateComputer science
Implementations of the present disclosure involve an apparatus and / or method for providing one or more clock signals within a processing device. In particular, one or more counter devices may be integrated into a microprocessor design that operates on a system clock signal to provide ratioed synchronous clock signals for use by the microprocessor. Additionally, one or more synchronization pulse signals are also generated from the one or more counter devices to facilitate communication between domains of the microprocessor that may operate on separate clock frequencies. Such synchronization pulse signals may also provide for a virtual clock signal within a clock domain to create a low frequency logic cluster within a high frequency domain of the microprocessor. A synchronous, low frequency reset signal is also disclosed to synchronize the counting devices to the system clock without the need for an additional high frequency signal path in the microprocessor design.
Owner:ORACLE INT CORP
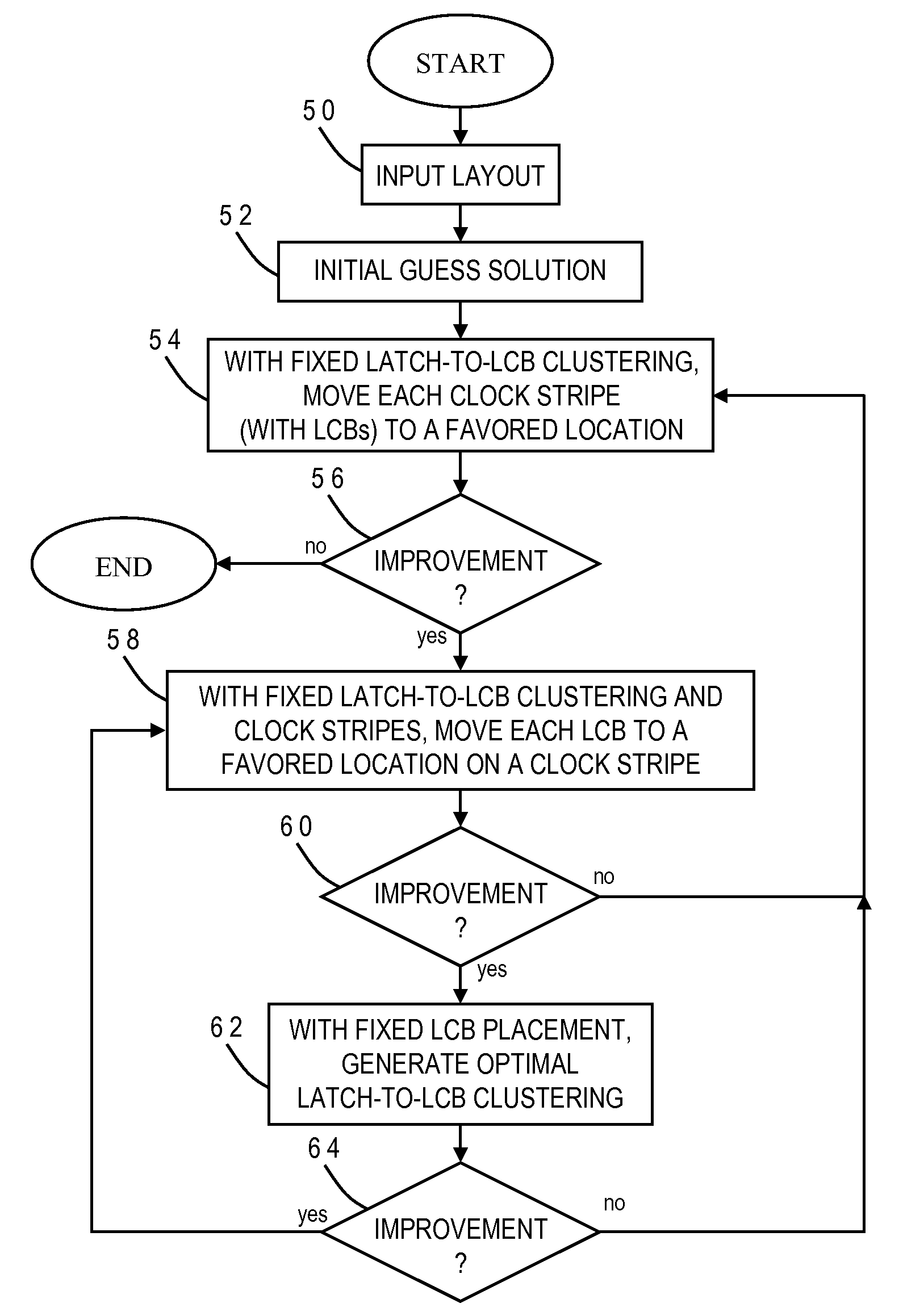
Regular local clock buffer placement and latch clustering by iterative optimization
InactiveUS20090193377A1Simple methodMore flexibility in the location of clock componentsComputer aided designSpecial data processing applicationsCapacitanceClock network
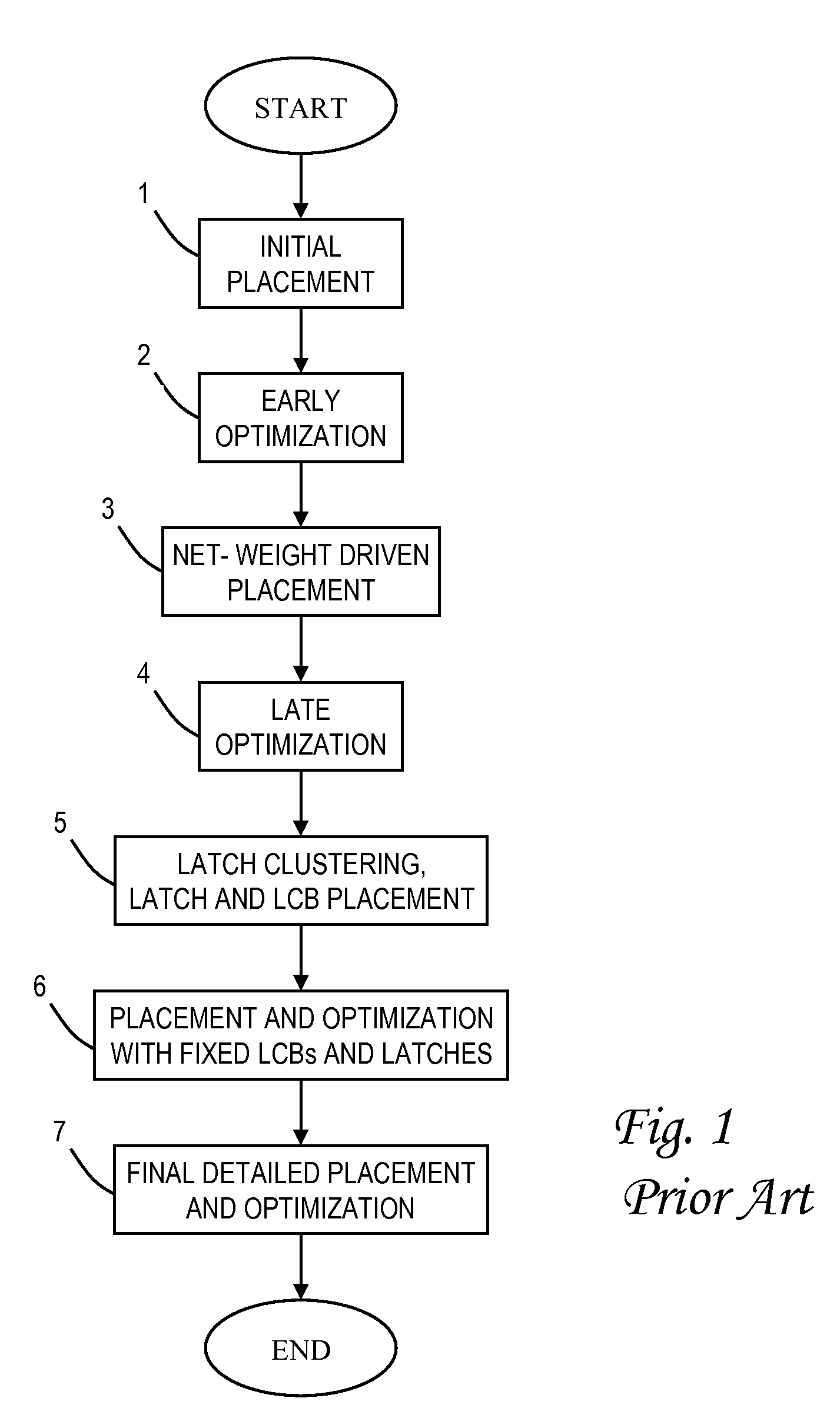
Power, routability and electromigration have become crucial issues in modem microprocessor designs. In high performance designs, clocks are the highest consumer of power. Arranging clocking components with regularity so as to minimize the capacitance of the clock nets can help reduce clock power, however, it may hurt performance due to some loss of flexibility in physically placing those components. The present invention provides techniques to optimally design a clock network by logically assigning clusters of the latches to respective clock distribution structures, placing clock pins at favored pin locations, and placing clock distribution structures directly underneath the clock pins. The clock distribution structures may be moved to favored distribution locations along the clock stripes, and new optimal clustering generated between the latches and the clock distribution structures. These three optimizations are preferably repeated iteratively to derive a local optimal solution for the clock network.
Owner:GLOBALFOUNDRIES INC
MPU FPGA verification device supporting stochastic instruction testing
ActiveCN101063979AFast testSoftware testing/debuggingSpecial data processing applicationsCommunication interfaceOperational system
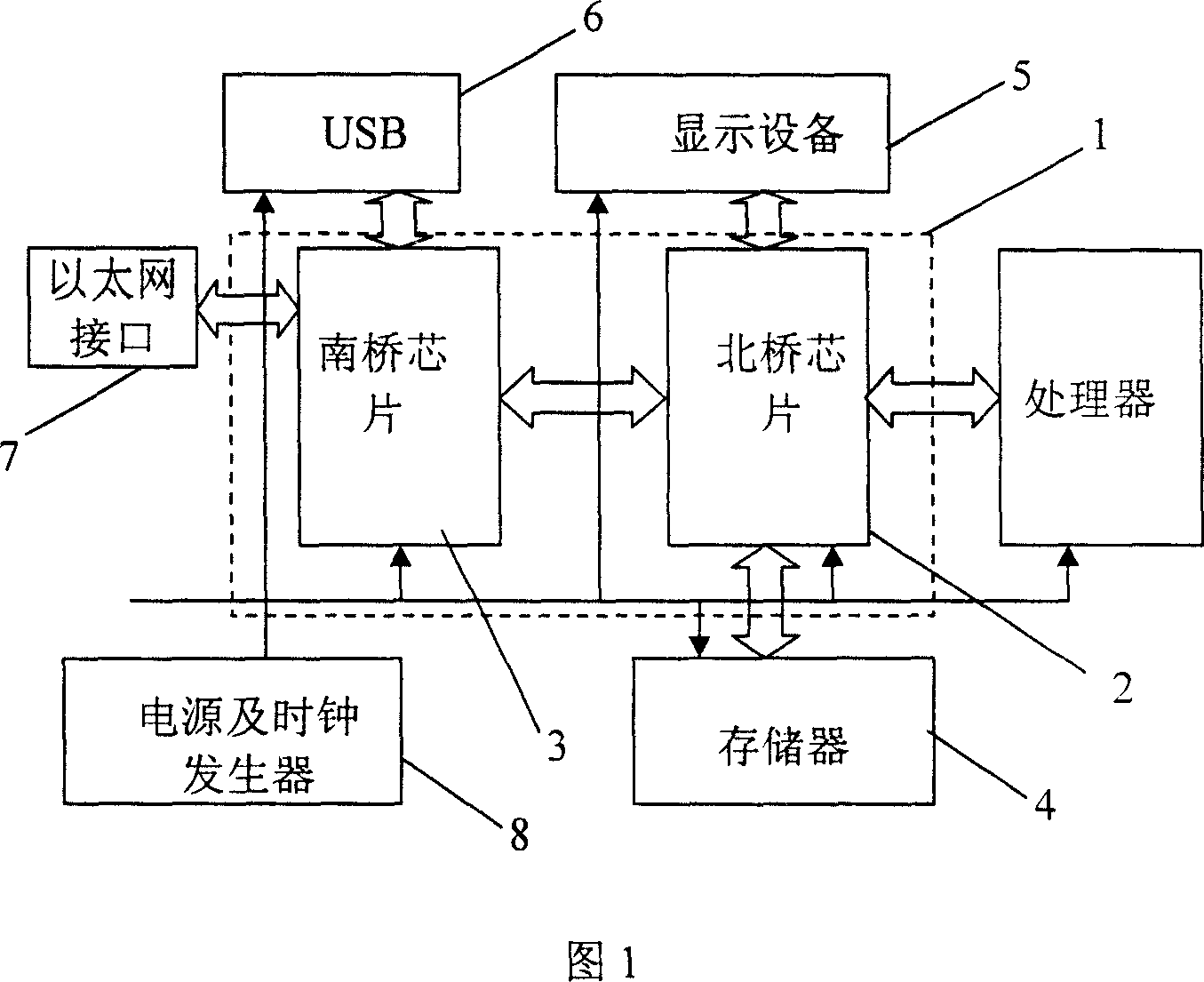
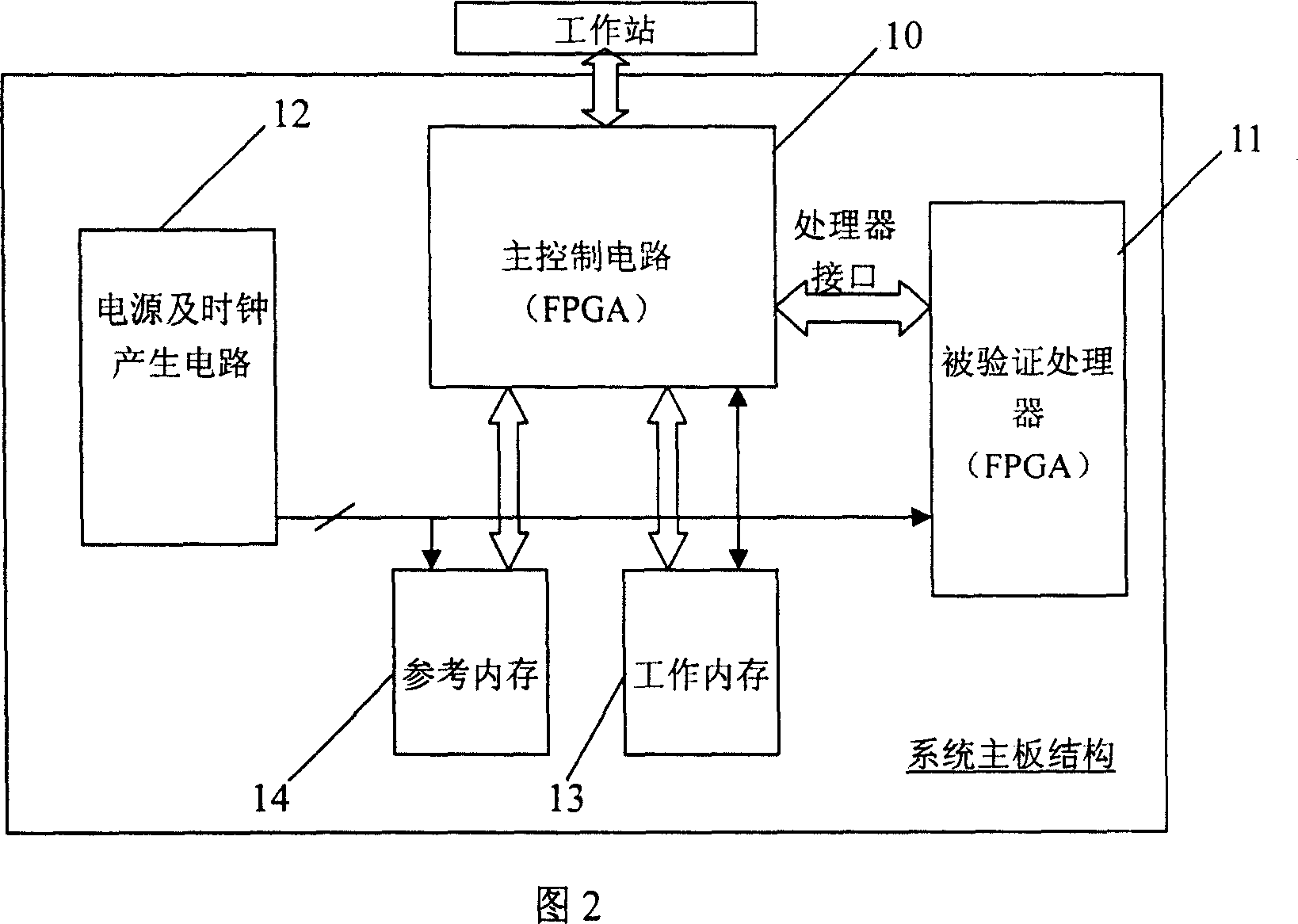
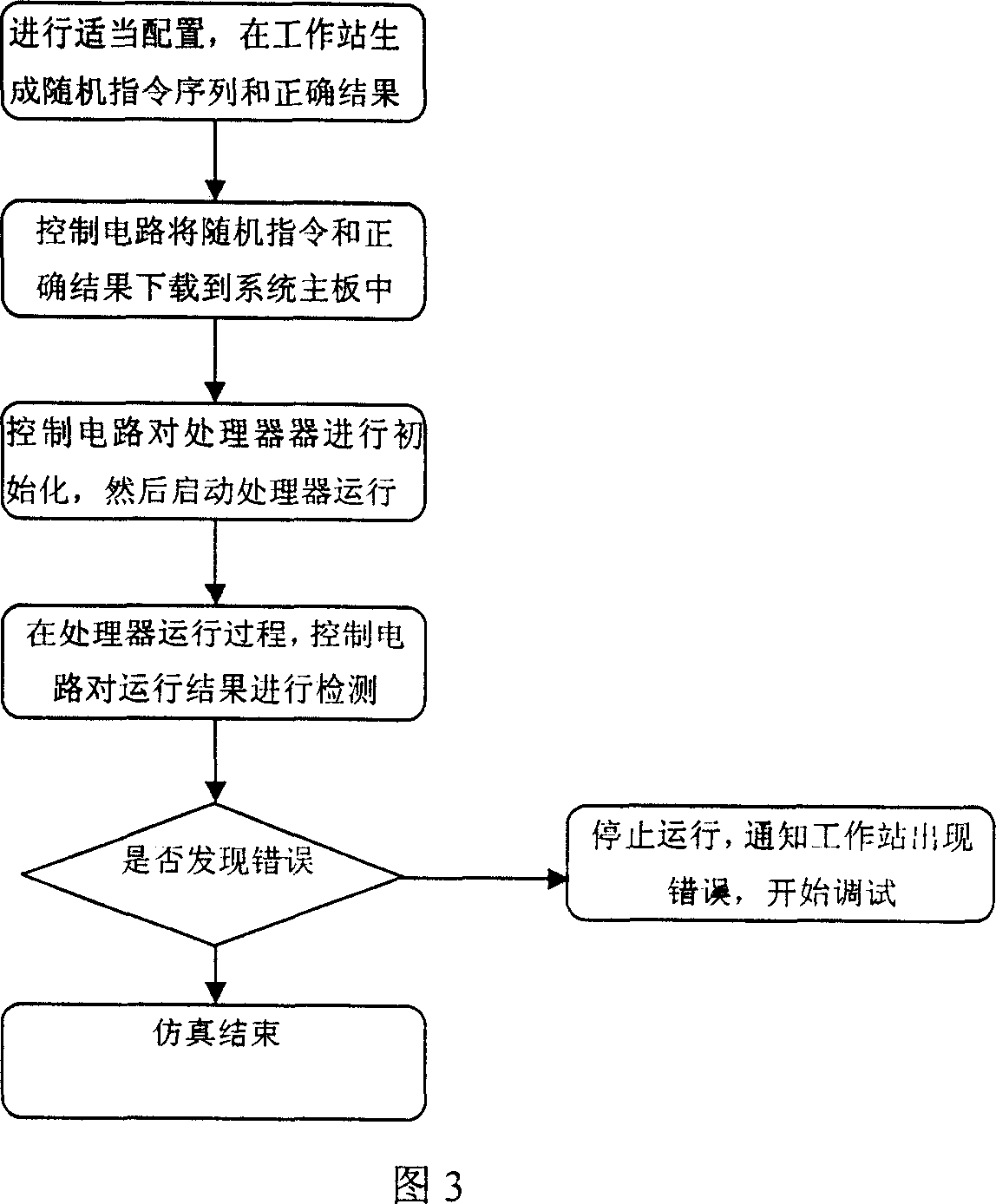
This invention discloses one artificial valuation FPGA physical prototype validation device through micro processor design, wherein the device comprises the following parts: one main control circuit with one processor interface for connection with validation micro processor; one power and clock generation circuit connected with micro process to be tested; one work memory and one reference memory connected to main control circuit through main control circuit memory interface, wherein the main control circuit has one communication interface with one outer work station.
Owner:LOONGSON TECH CORP
Storage pre-alignment and EBCDIC, ASCII and unicode basic latin conversions for packed decimal data
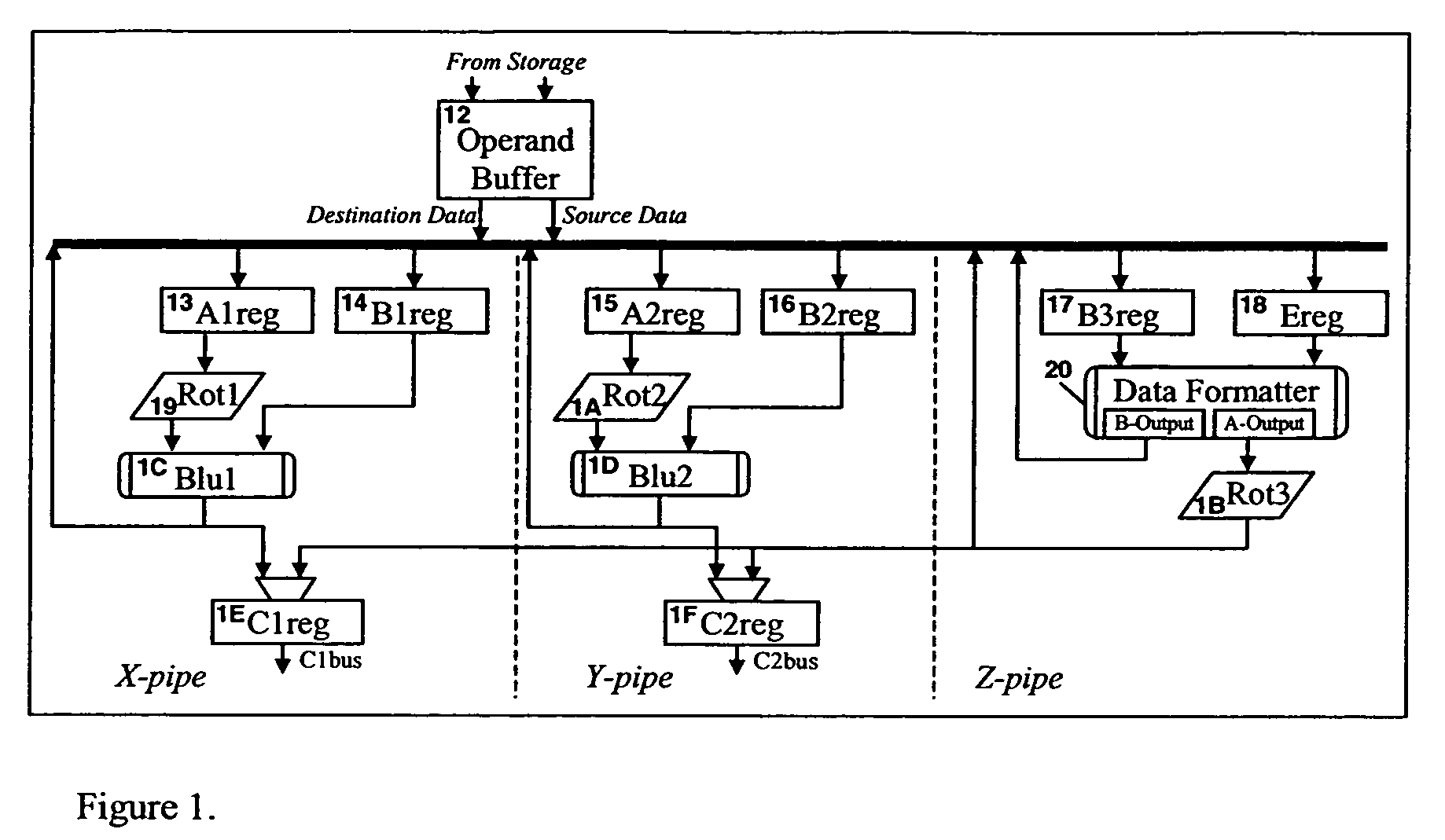
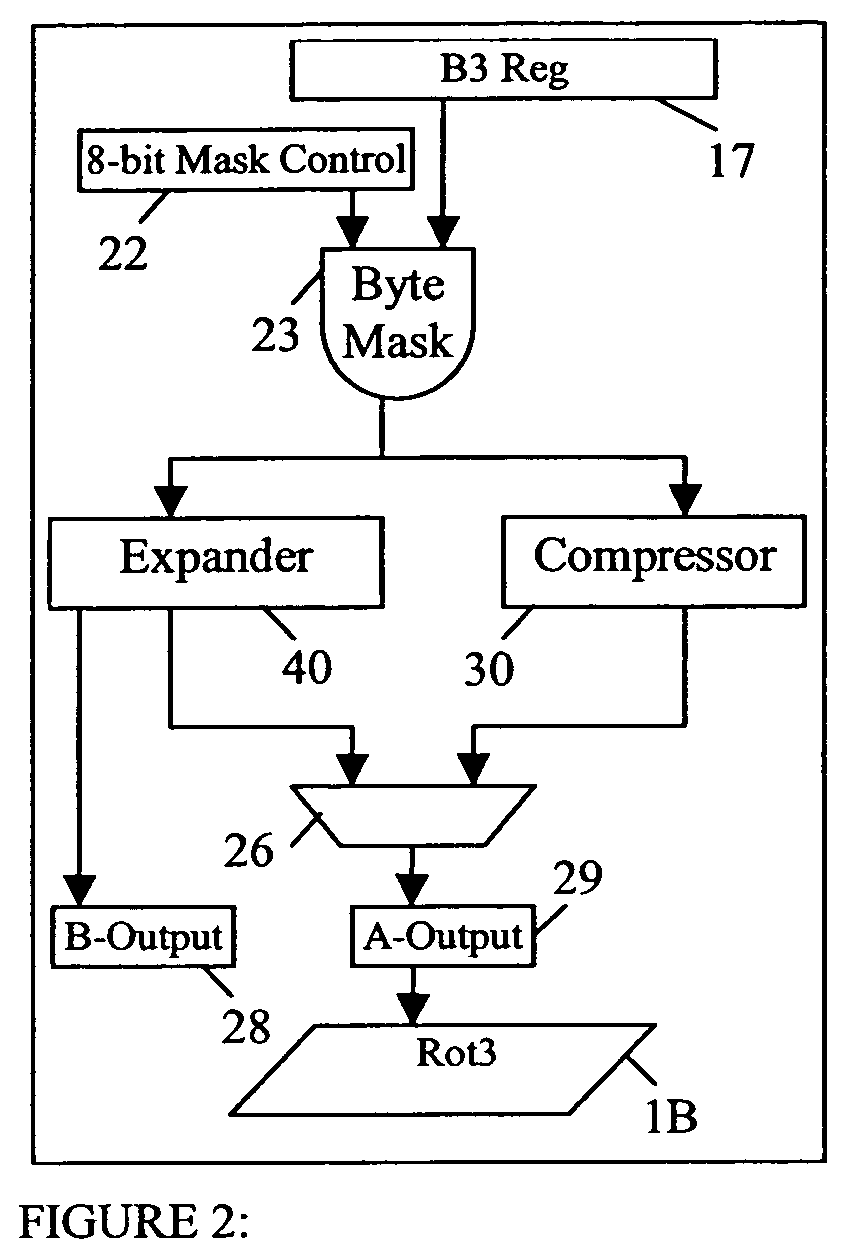
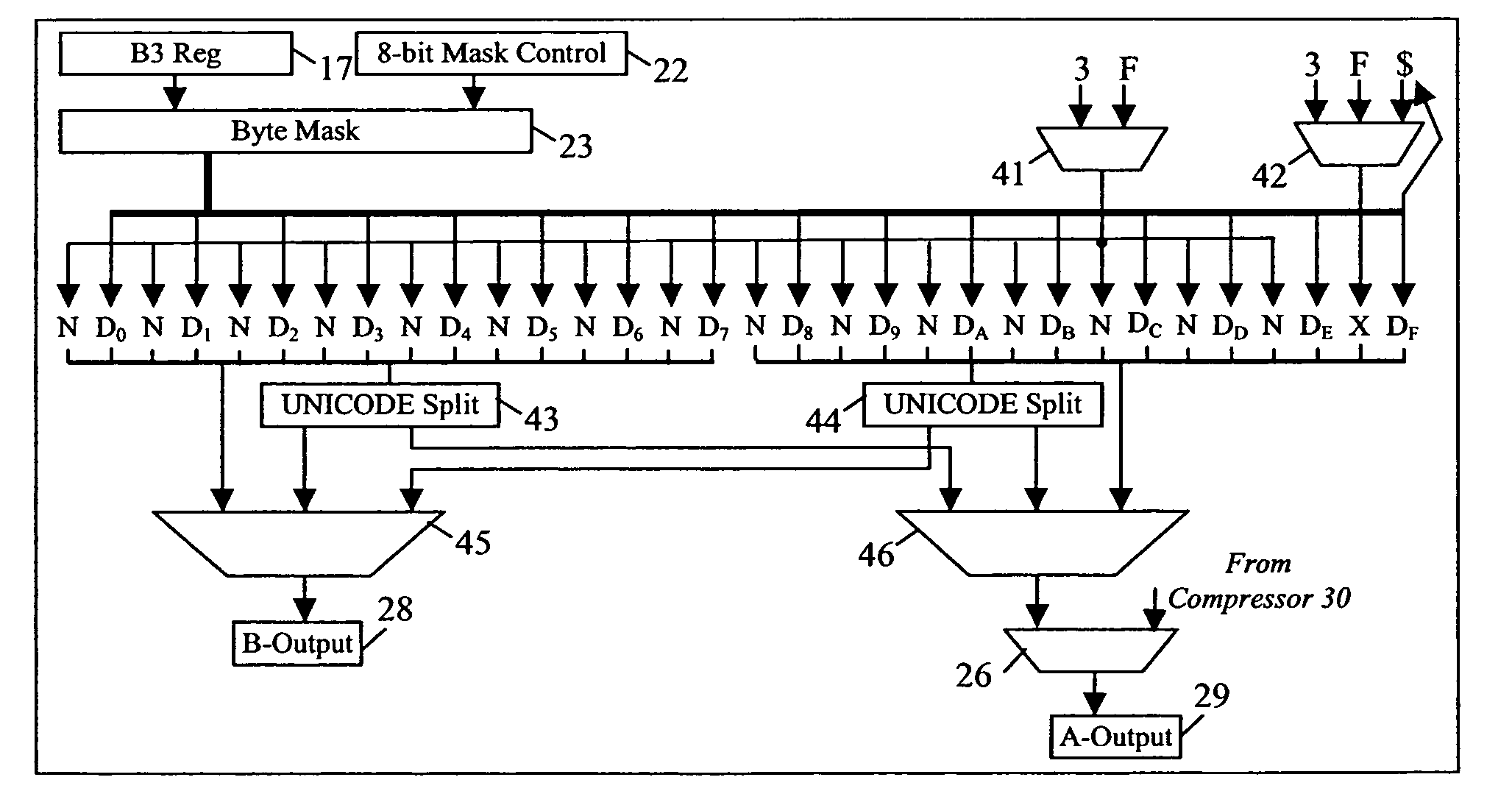
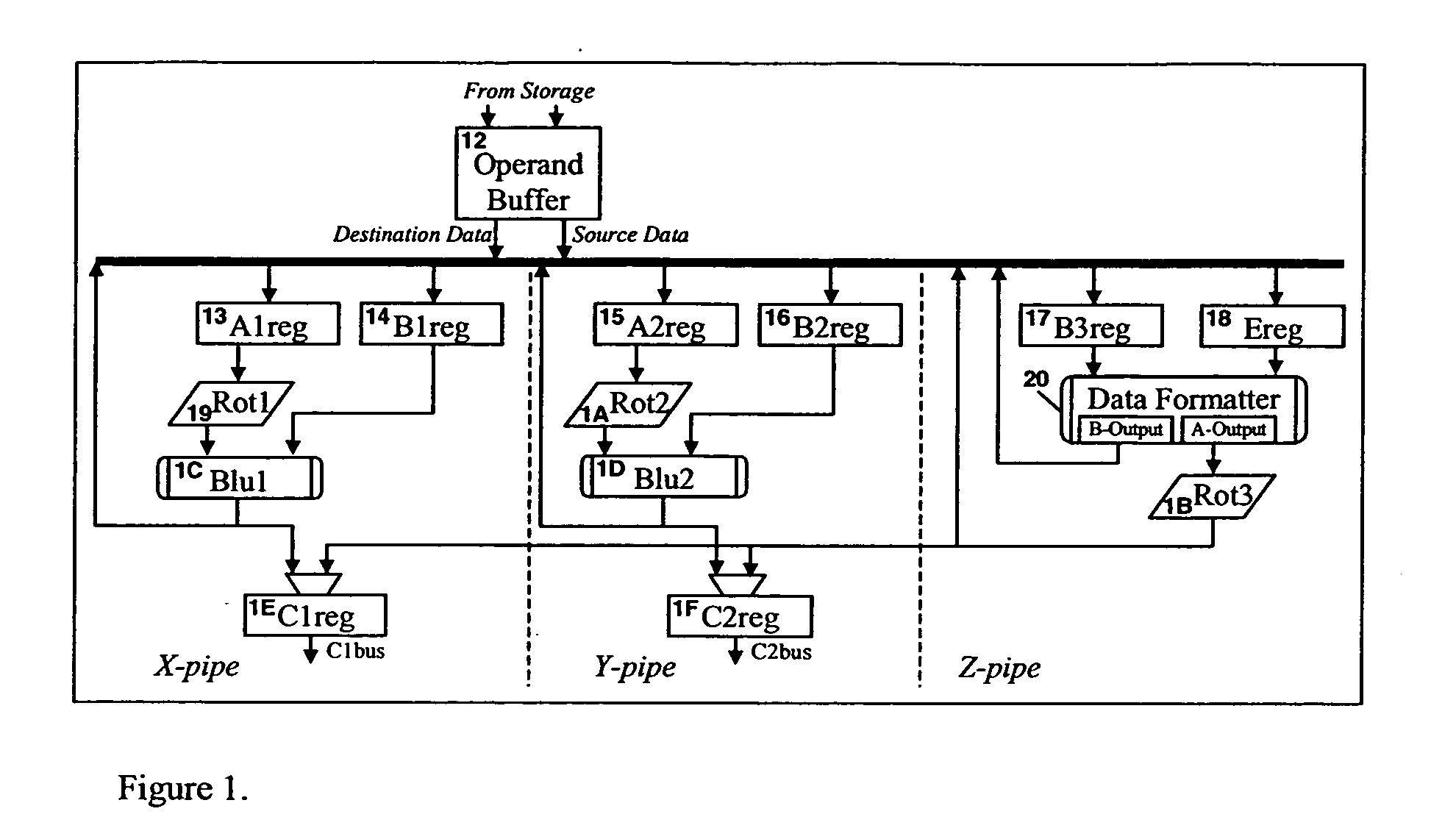
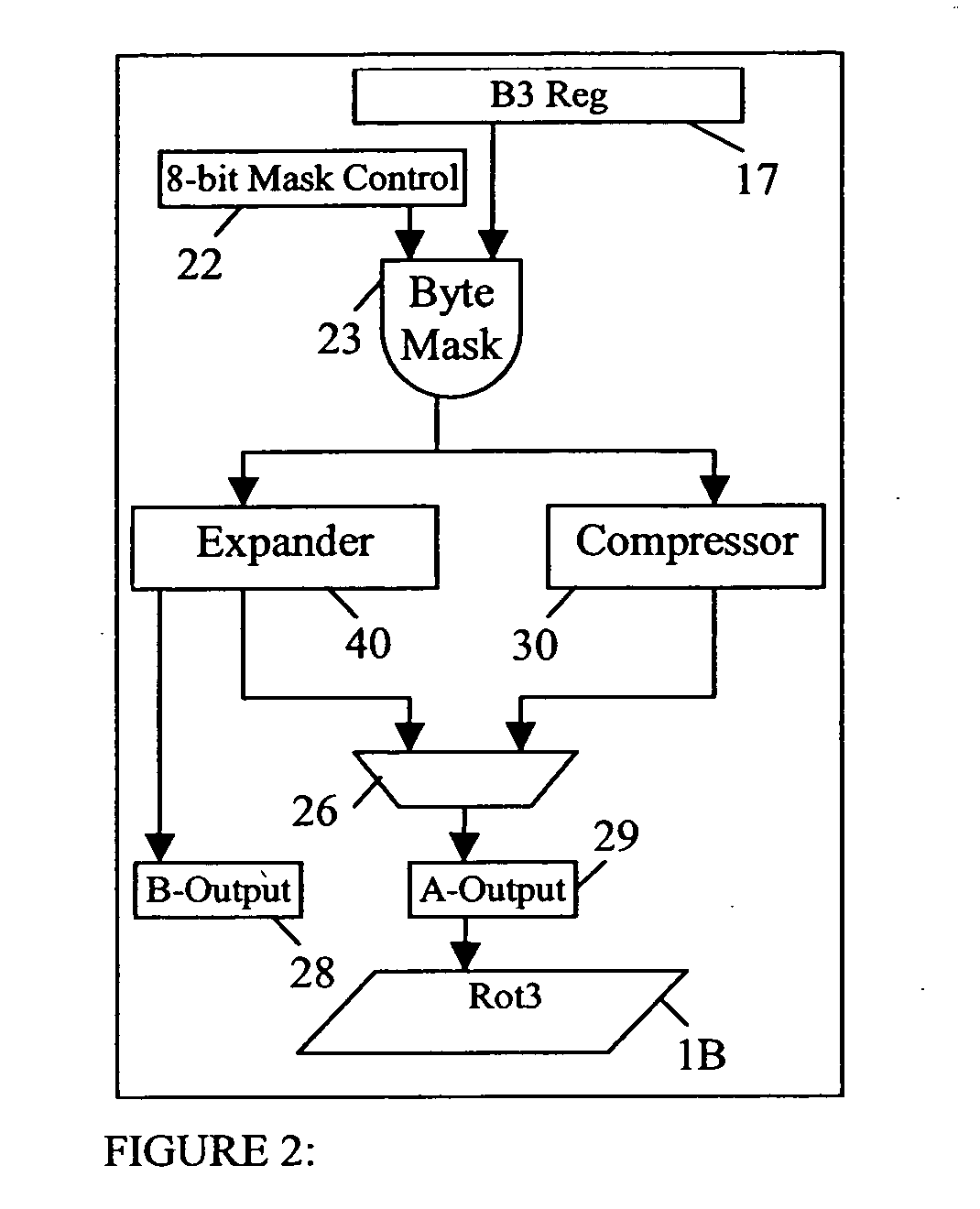
ActiveUS7167968B2Improve performanceReduce in quantityMemory adressing/allocation/relocationConcurrent instruction executionEBCDICOperand
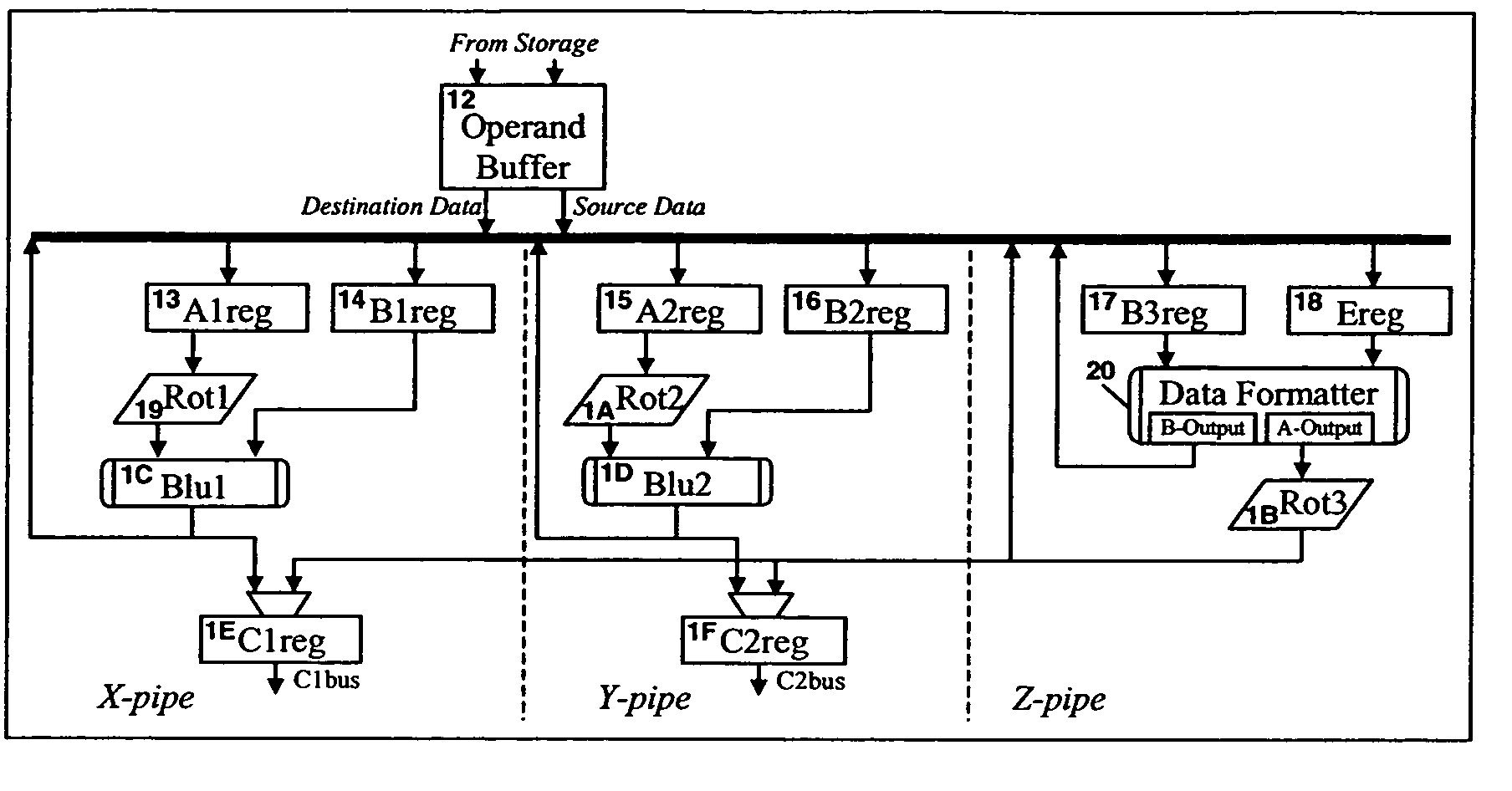
A method of pre-aligning data for storage during instruction execution improves performance by eliminating the cycles otherwise required for data alignment. The method can convert data between ASCII and Packed Decimal format, and between Unicode Basic Latin and Packed Decimal format. Conversion to Packed Decimal format is needed for decimal hardware in a microprocessor designed to generate decimal results. Converting from Packed Decimal to ASCII and Unicode Basic Latin is necessary to report Decimal Arithmetic results in a required format for the application program. To further improve performance, all available write ports in the fixed point unit (FXU) are utilized to reduce the number of cycles necessary to store results. To prevent data fetching of the unused destination data from slowing down instruction execution, the destination locations are tested for storage access exceptions, but the data for these operands are not actually fetched. A single read request from the FXU to the operand buffers effectively reads the entire destination address (up to 8 double-words of data) in a single cycle.
Owner:IBM CORP
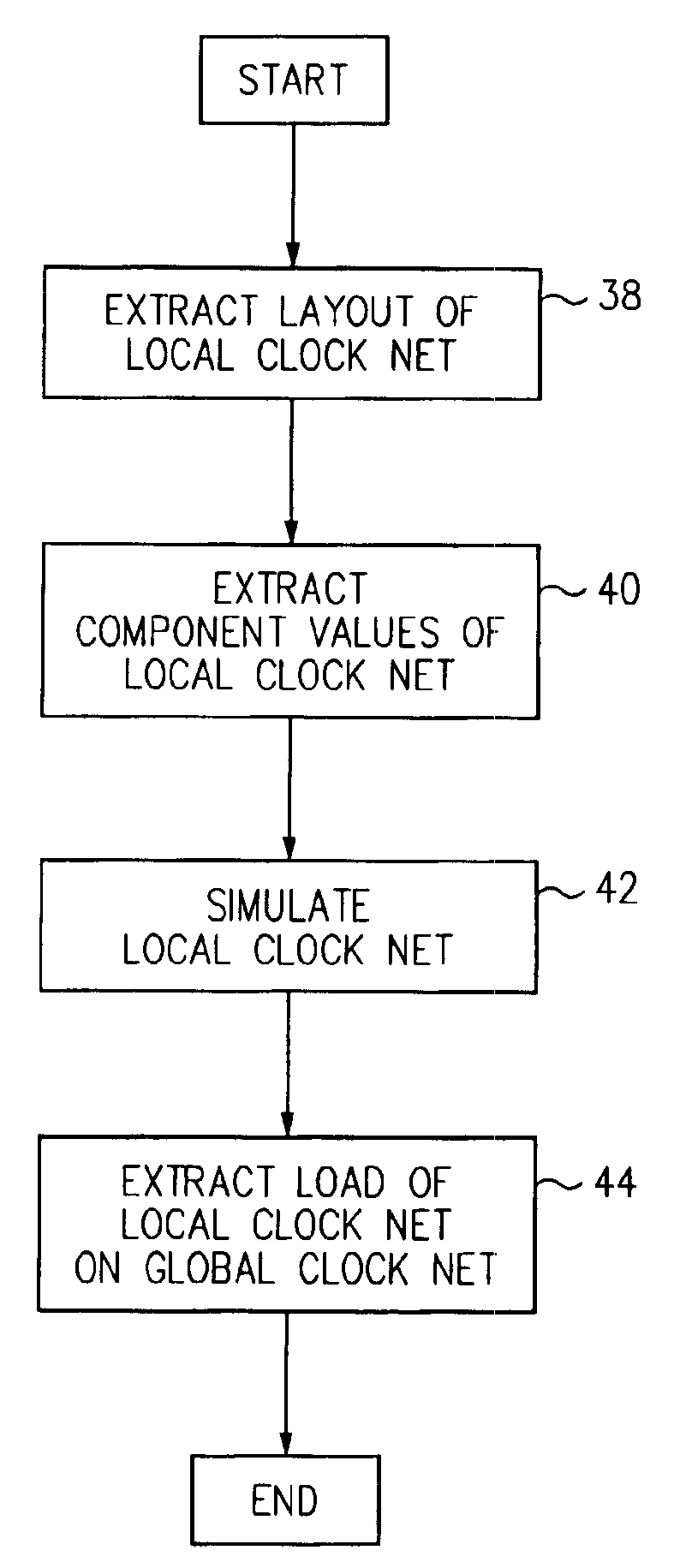
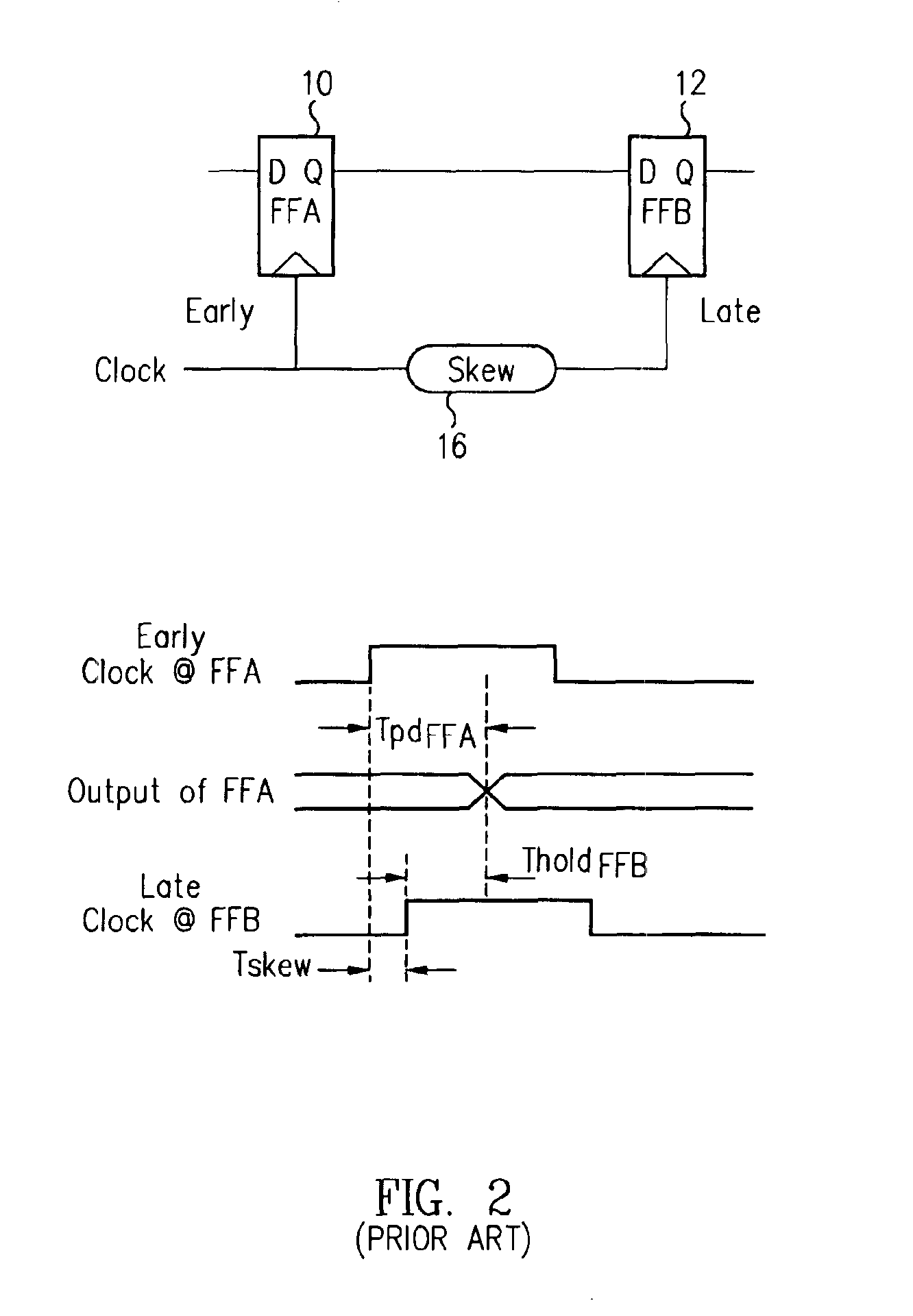
Clock skew verification methodology for grid-based design
InactiveUS6941532B2CAD circuit designSpecial data processing applicationsValidation methodsGrid based
A method and apparatus for determining clock insertion delays for a microprocessor design having a grid-based clock distribution. The method includes partitioning the complete clock net into a global clock net and a plurality of local clock nets, simulating a load for each of the local clock nets, simulating the global clock net, and combining the simulations to form the complete clock net. The method may further include evaluating the combination to determine whether the results converge and storing the simulation results in a Clock Data Model. When the results do not converge, the method re-simulates at least one of the local clock nets and re-simulates the global clock net. The Clock Data Model collects, manages, retrieves, and queries all of the simulation information. The method may further analyze the complete clock net to predict the clock skew for a given data transfer path for potential redesign.
Owner:ORACLE INT CORP
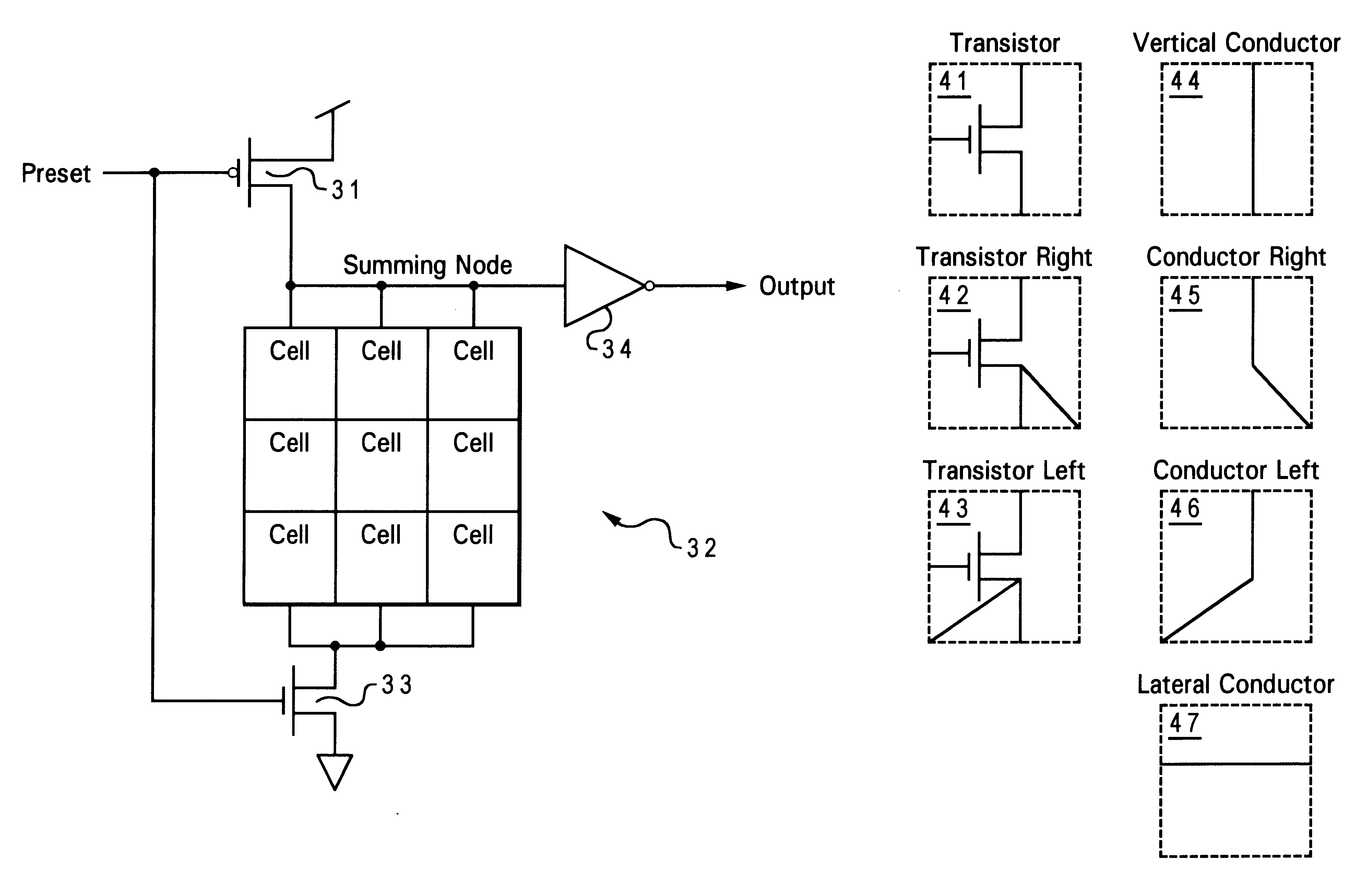
Method and apparatus for implementing logic using mask-programmable dynamic logic gates
InactiveUS6285218B1Logic circuits characterised by logic functionSemiconductor/solid-state device manufacturingProcessor designProgrammable logic array
A method and apparatus for implementing dynamic logic with programmable dynamic logic gates acts as a complement to programmable logic arrays (PLAs) used in high-speed microprocessor designs. A matrix of selectable cells provides powerful logic functions such as AND-OR gate capability with a minimum of inputs and transistors. By using programmable logic arrays and programmable dynamic gates, the efficiency of a logic block can be dramatically improved with little added circuit area.
Owner:IBM CORP
Device for real-time monitoring inside of processor
ActiveCN101187892ADoes not affect working statusHardware monitoringShift registerSystem configuration
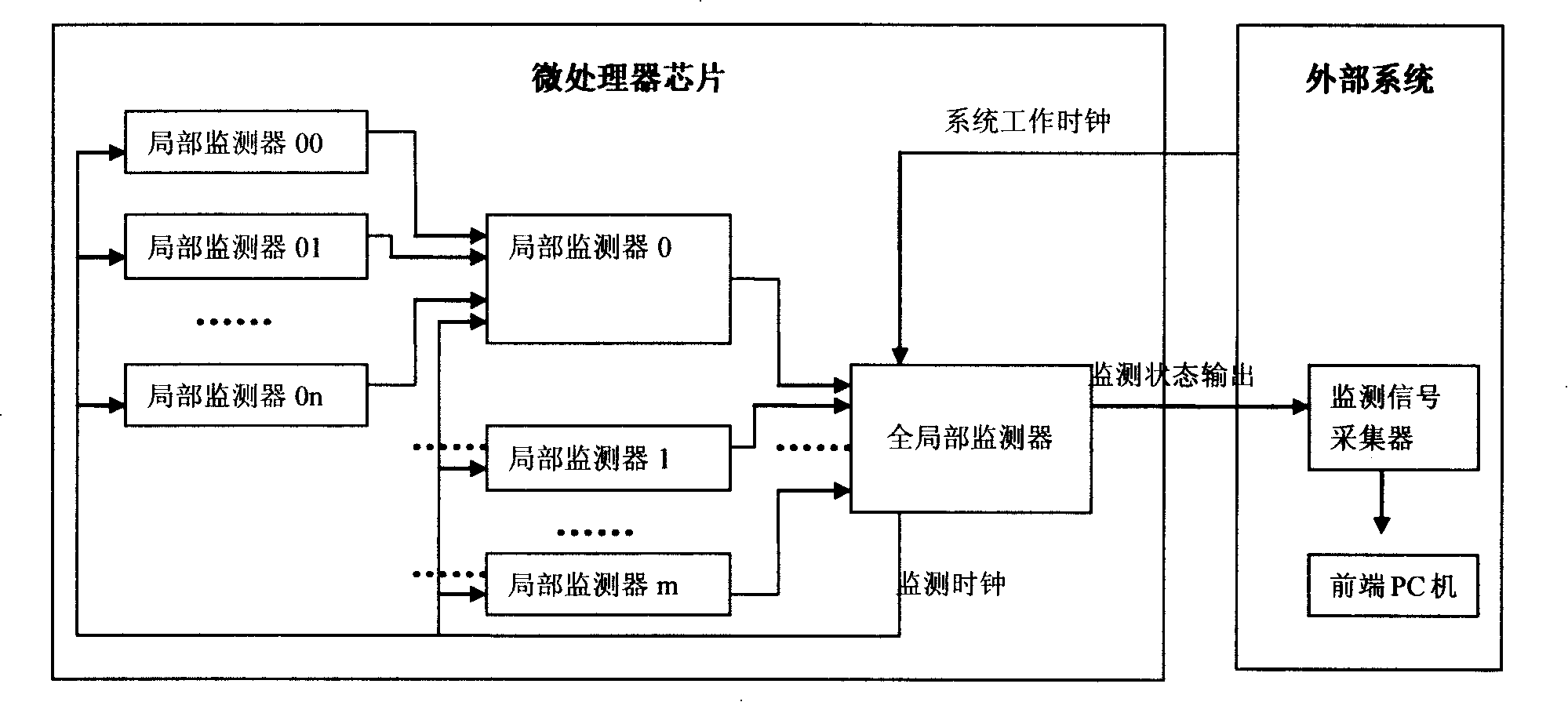
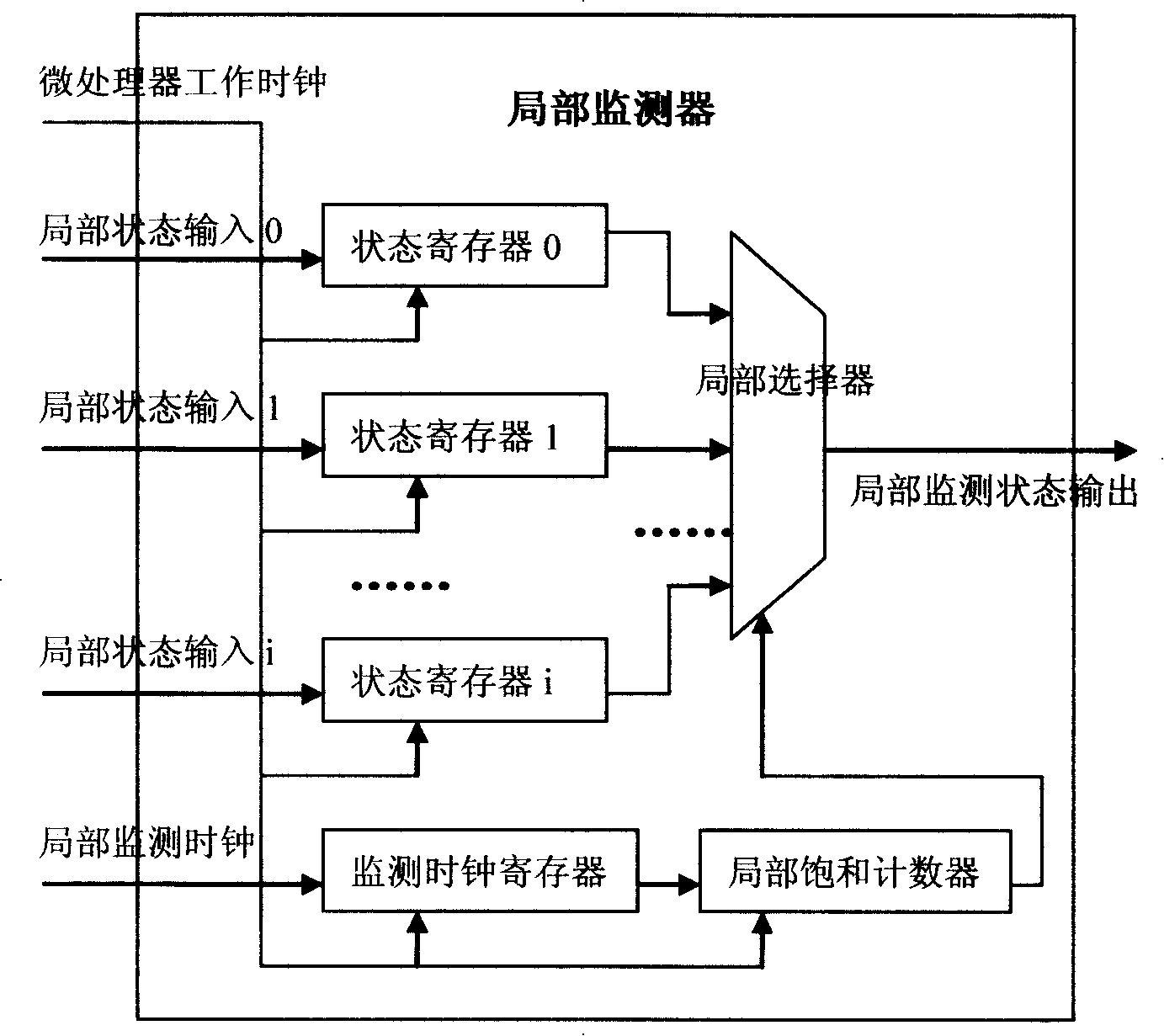
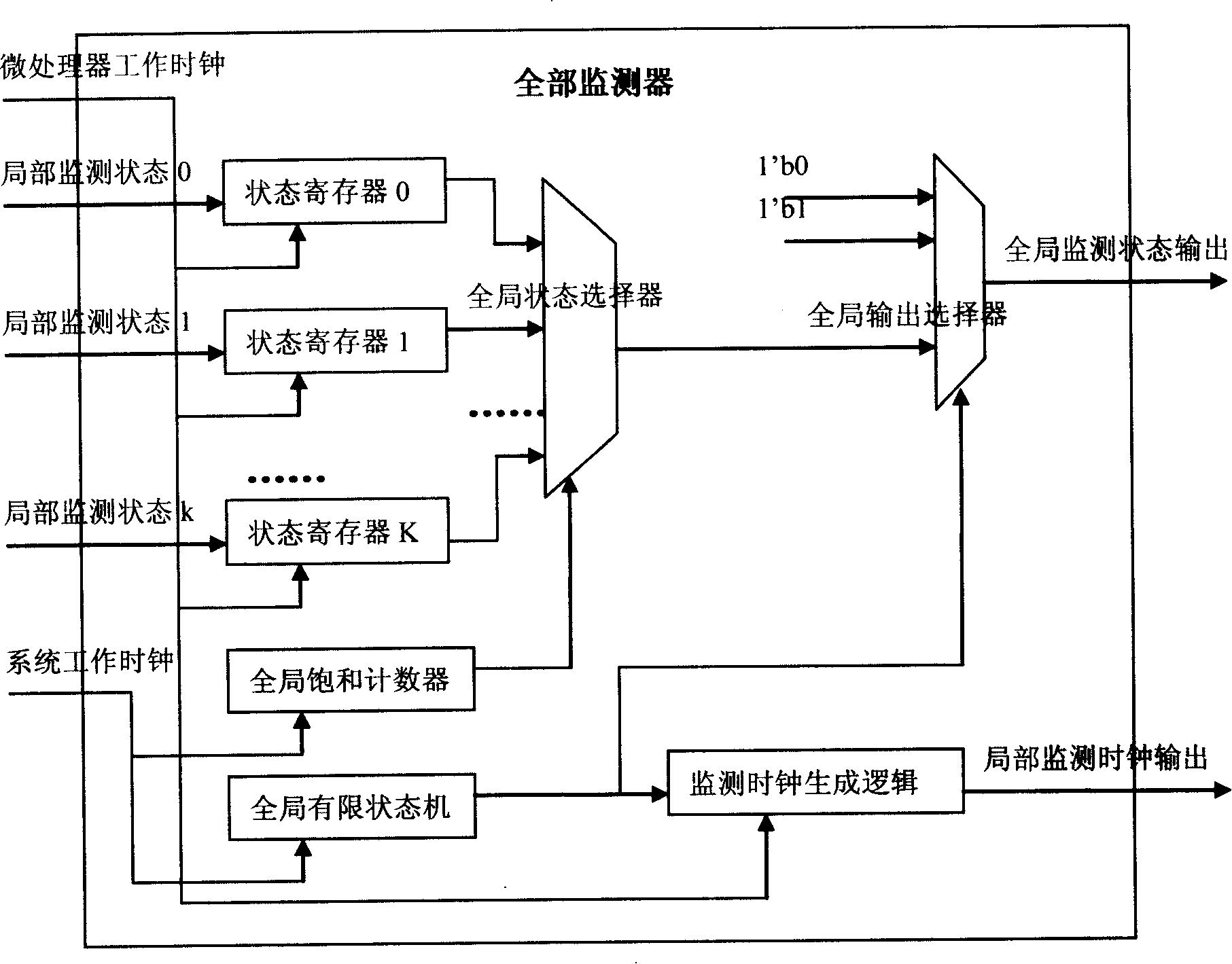
The invention discloses a device for detecting inner state of a micro processor in real time. During the design process of the micro processor, a plurality of partial monitors or a multi-level partial monitor and a global monitor are added, and the inner state information of the micro processor is serially output to a one-bit state-monitor output port with fixed cycle in circulating manner. The outer system is allocated with a signal-monitor collecting device which collects signal in the state-monitor output port of the micro processor, and is split-jointed into inner state information of the micro processor which has practical meanings through a shift memory, and is displayed on a front end PC machine finally. Small amount of hardware cost added in the design stage of the micro processor, real-time observability of the inner state of the micro processor under the situation of practical running mode of a chip is supported, and the shortcoming of measurable design technology of a traditional chip is compensated.
Owner:上海高性能集成电路设计中心
Switch reluctance machine (SRM) torque pulse control method and system of torque-current neutral network model
ActiveCN110022109AConvenient online controlElectric motor controlMotor control for motor oscillations dampingPulse controlActivation function
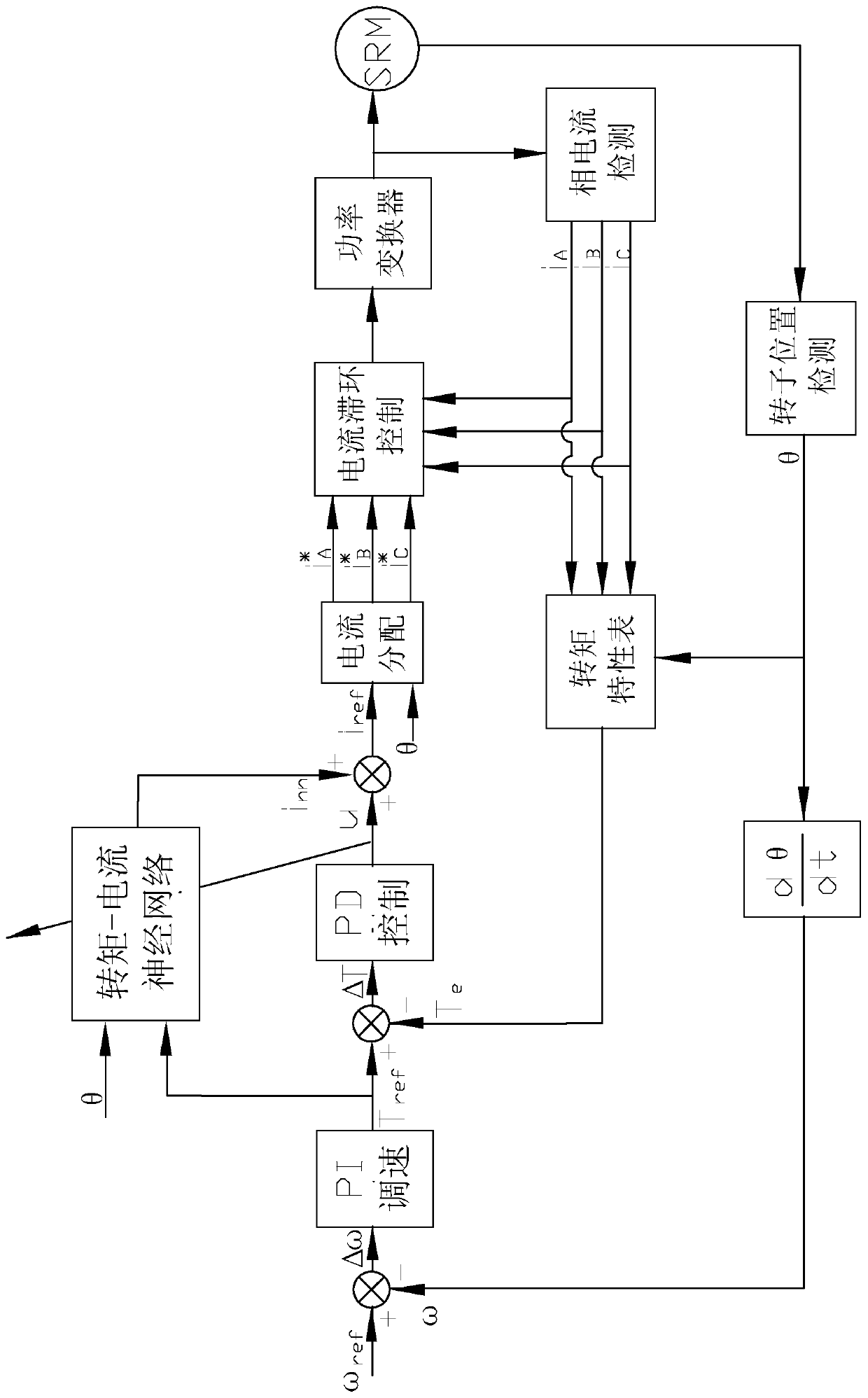
The invention relates to a switch reluctance machine (SRM) torque pulse control method and system of a torque-current neutral network model. According to the method, a torque-current conversion relation is obtained by an inductance model of an SRM, each phase control current is obtained by a current allocation function, so that torque pulse is prevented. According to a non-linear characteristic relation between the SRM torque and the current, a function of describing basic change rule of an SRM current is used as an implication layer simulation function, a torque-current neutral network modelof describing the strong non-linear characteristic of the SRM is designed, the total reference current corresponding to torque is calculated by self-learning of the torque-current neutral network model, a reference current corresponding to each phase is obtained by the current allocation function, and the SRM is controlled. A program storage device of a system microprocessor designed by the methodis provided with each program module for executing the method, each sensor signal on the SRM is connected to the microprocessor, and the SRM is connected and controlled by a power converter. By the method, effective control on torque pulse of the SRM is achieved.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Clock power minimization with regular physical placement of clock repeater components
InactiveUS8010926B2Increase powerReducing clock skewComputer aided designSpecial data processing applicationsCapacitanceControl theory
Power, routability and electromigration have become crucial issues in modern microprocessor designs. In high performance designs, clocks are the highest consumer of power. Arranging clocking components with regularity so as to minimize the capacitance on the clock nets can help reduce clock power, however, it may hurt performance due to some loss of flexibility in physically placing those components. The present invention provides techniques to optimally place clock components in a regular fashion so as to minimize clock power within a performance constraint. A rectangular grid is created and clock distribution structures are assigned to the grid intersection points. Latches are then located around the clock distribution structures to minimize an overall distance for connections between the latches and respective clock distribution structures. The horizontal and vertical pitches of the grid may be independently adjusted to achieve a more uniform spread of the clock distribution structures.
Owner:IBM CORP
Mobile phone
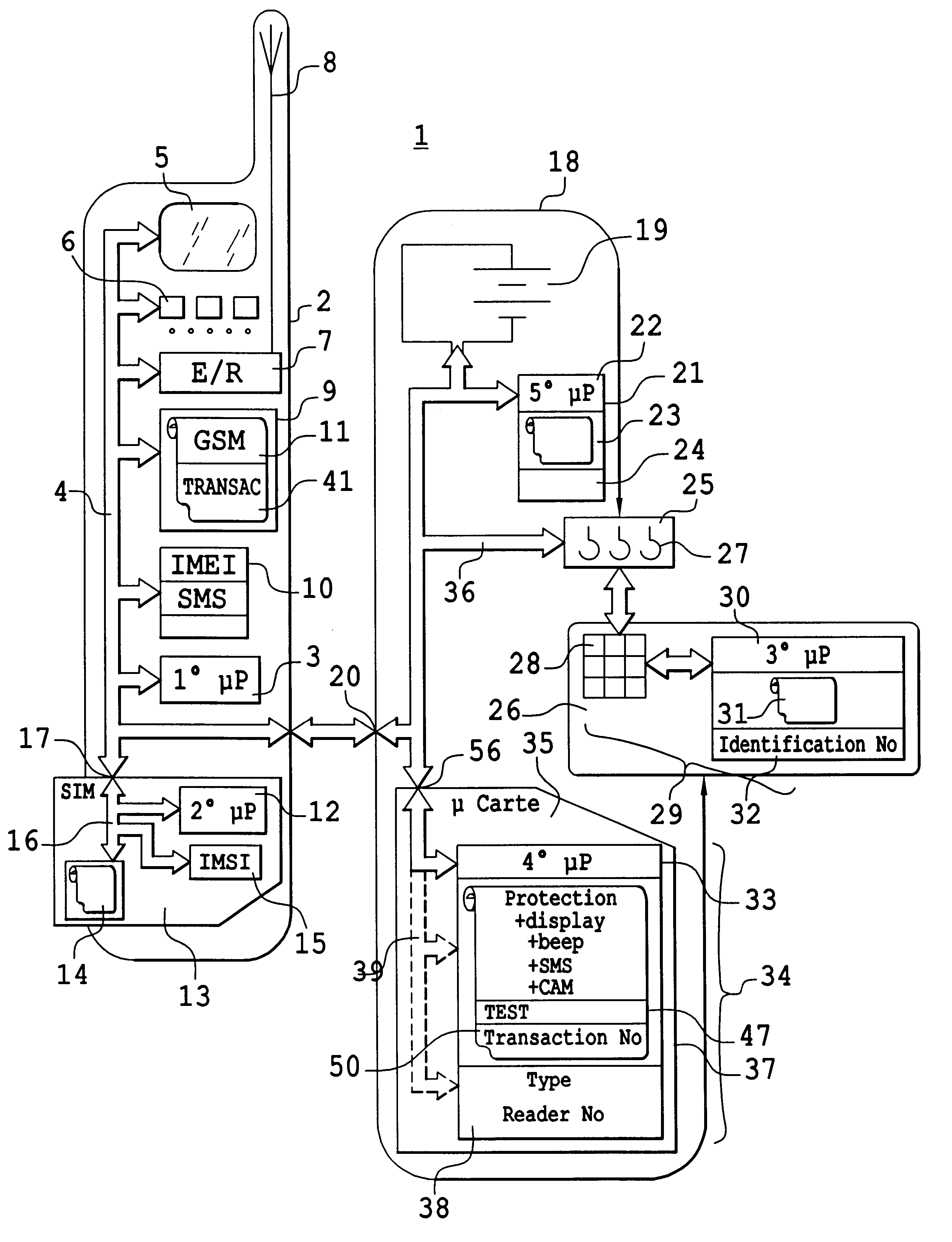
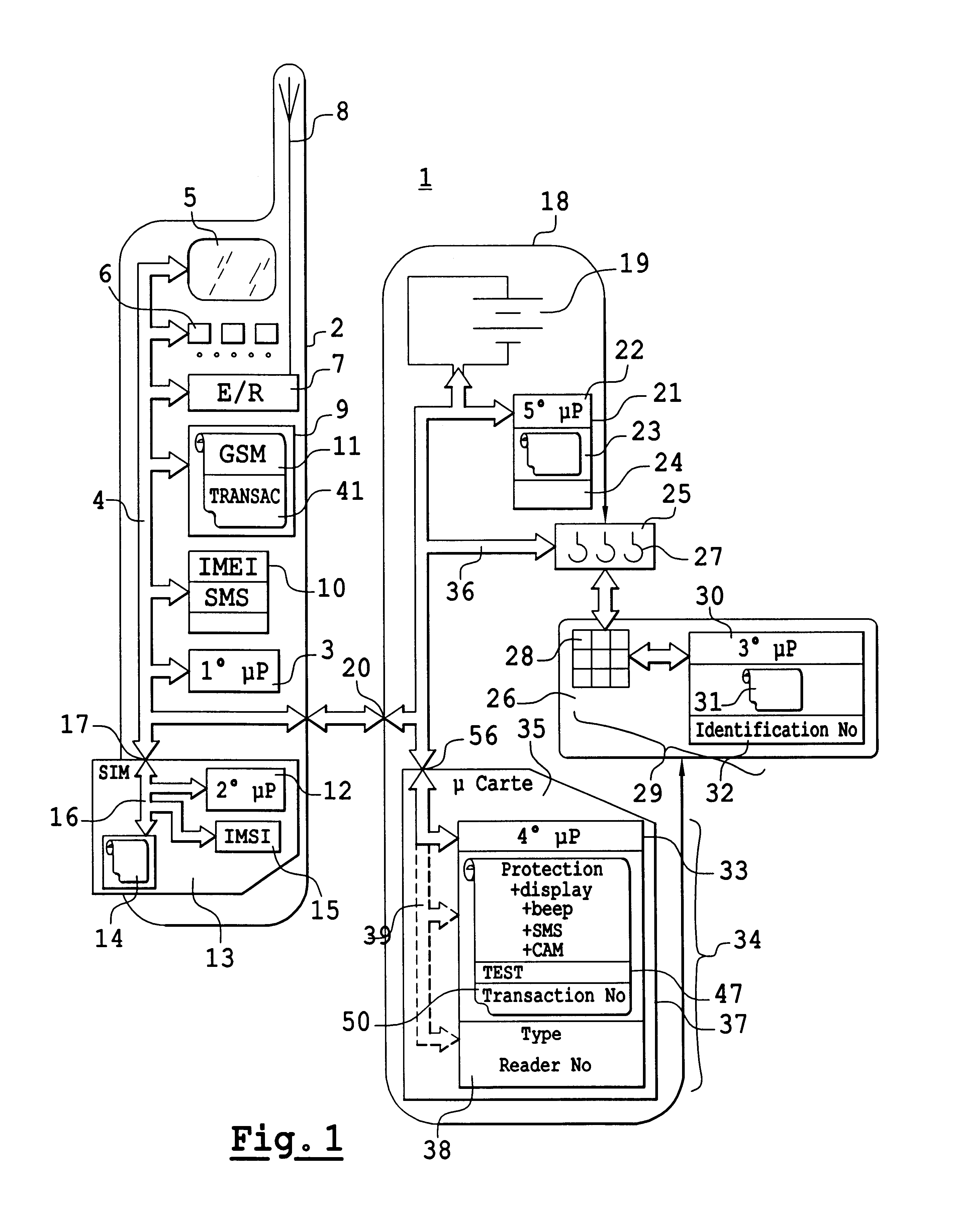
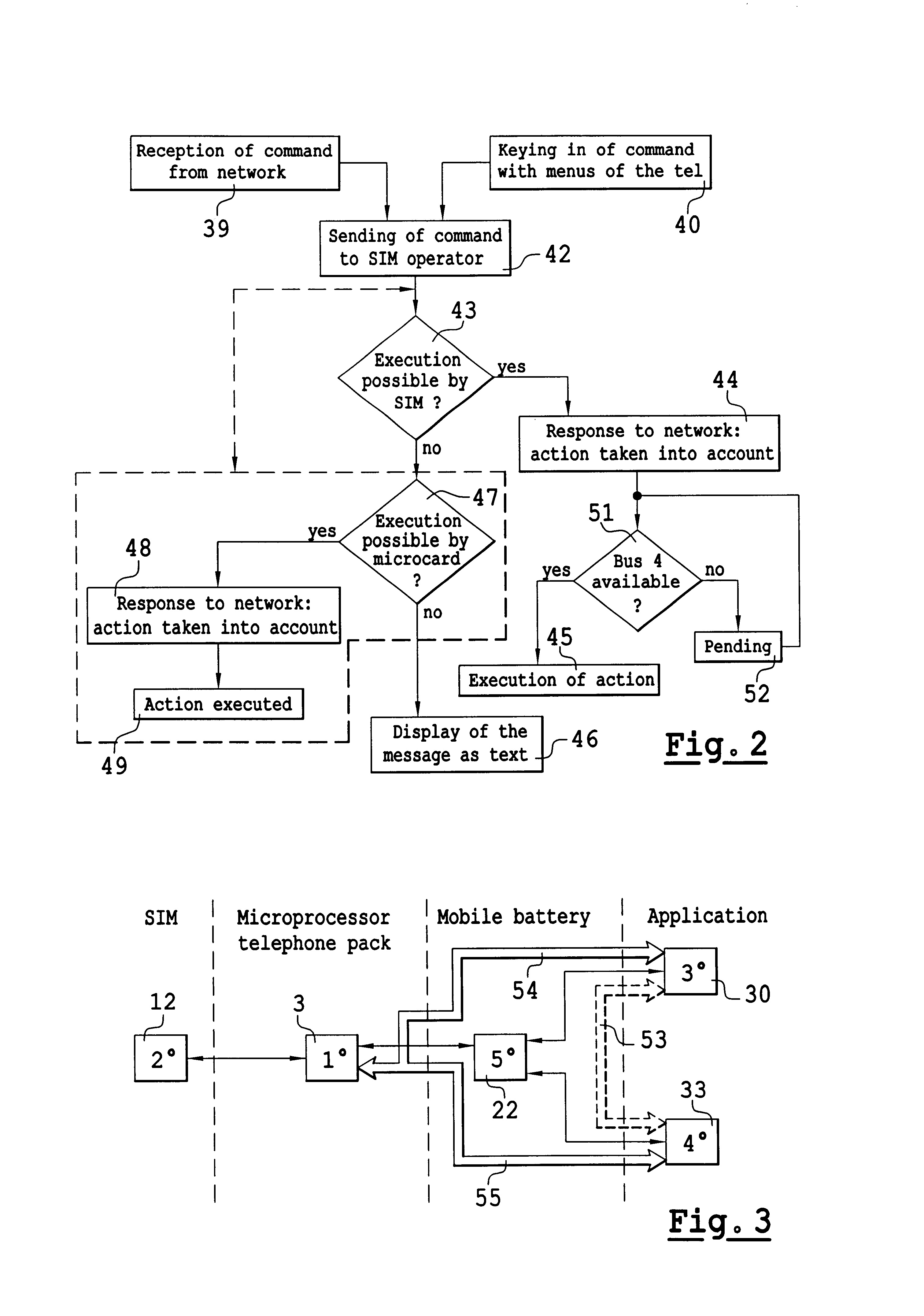
InactiveUS6766177B2Payment architectureRadio/inductive link selection arrangementsSmart cardCard reader
To resolve problems of communication between a mobile telephone provided with a smart-card reader and the circuits of a smart-card reader, it is planned to provide this mobile telephone with a fourth microprocessor designed to manage the communications of the mobile telephone with the smart card only. This fourth microprocessor then becomes, in competition with a SIM security circuit of the mobile telephone, a master of the microprocessor of the mobile telephone. To resolve the problem of competition resulting from the existence of these two master circuits, it is planned that one of the two will be called upon to execute a command and that it will execute this command if it falls within the commands that are executable by it. If this command is not executable by this first microprocessor, then it is transmitted to the microprocessor of the second master circuit so that this second master circuit executes it. By acting in this way, it is shown that it is very easy to update mobile telephones, even old models. To this end, it is enough to place especially the fourth microprocessor in a battery pack and interchange the battery pack with the original battery pack.
Owner:SAGEM SA
Regular local clock buffer placement and latch clustering by iterative optimization
InactiveUS8104014B2More flexibility in the location of clock componentsIncrease powerComputer aided designSoftware simulation/interpretation/emulationCapacitanceModem device
Owner:GLOBALFOUNDRIES INC
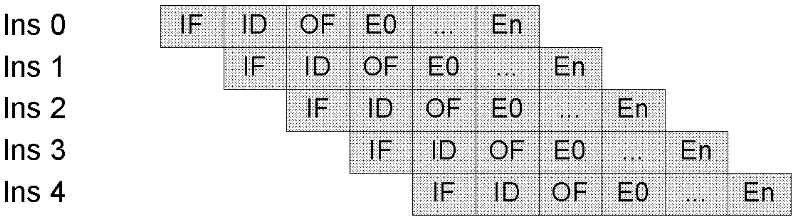
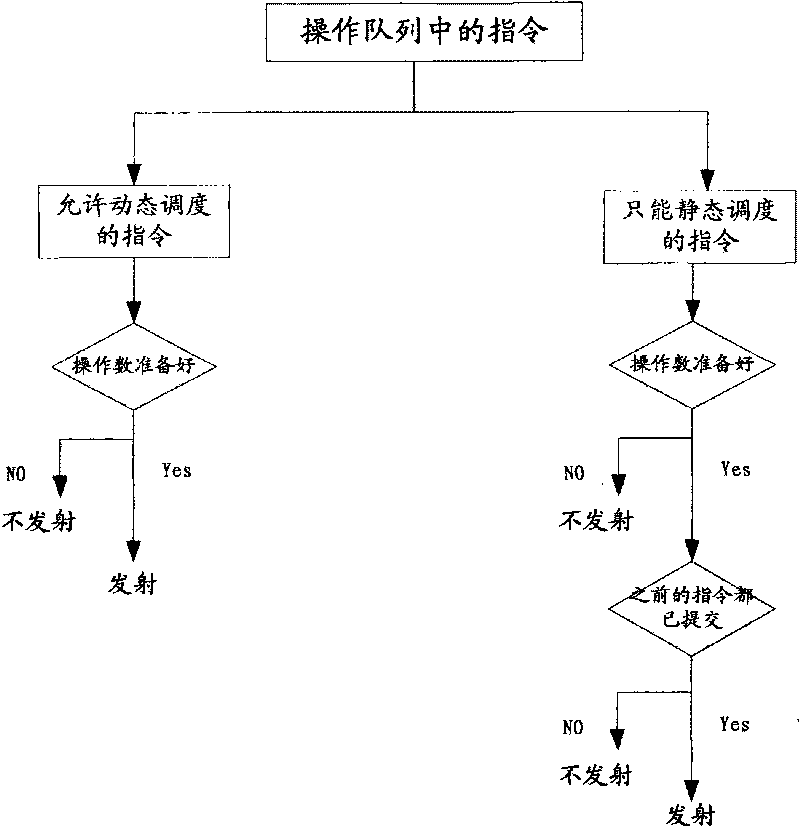
System and method for issuing instruction, processor and design method thereof
ActiveCN101706714AGuaranteed correctnessReduce complexityConcurrent instruction executionStatic dispatchOperand
The invention discloses a system and a method for issuing an instruction. The system comprises an instruction classifying module and an instruction issuing module, wherein the instruction classifying module classifies instructions in an operation queue; the instructions which can only be statically scheduled and sequentially executed in the operation queue are classified as static scheduling class instructions, and the instructions which can be dynamically scheduled and executed out of order in the operation queue are classified as dynamic scheduling class instructions; the instruction issuing module issues the static scheduling class instructions and the dynamic scheduling class instructions of which operands are prepared in the operation queue according to a static scheduling method and a dynamic scheduling method respectively. The system and the method indicate the instructions of which data dependency is not easy to judge, and statically schedule the instructions by aiming at the instructions. The execution method can ensure the correctness of program execution, and greatly reduces the complexity of microprocessor design. For the instructions of which the data dependency is easy to judge, the system and the method make full use of a flow line to improve performance of a processor by continuously adopting the method for dynamically scheduling the instructions.
Owner:LOONGSON TECH CORP
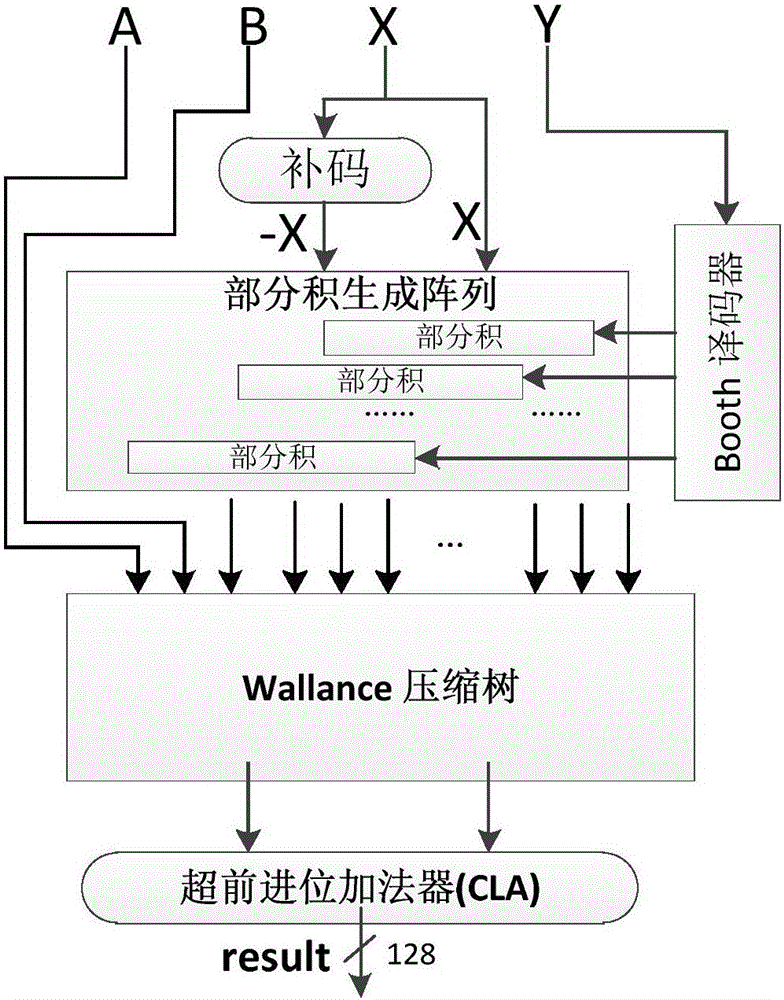
Optimized automatic bilinear pairing encryption method and device based on point blinding process
InactiveCN106100844AImprove securityImprove the performance of modular multiplicationPublic key for secure communicationUser identity/authority verificationRandom parametersHardware implementations
The invention relates to the field of information security and microprocessor design, and provides an optimized automatic bilinear pairing encryption method and device based on a point blinding process aiming at increasing the computing efficiency of algorithms from the perspective of hardware implementation, further saving computing resources, fundamentally reducing the encryption and decryption time and space consumption, simultaneously using reasonable anti-attack protection measures, effectively enhancing the security of bilinear pairing encryption, and providing a possibility for replacing a current mainstream encryption system by using the bilinear pairing encryption method. The technical scheme adopted by the invention is that the optimized automatic bilinear pairing encryption method based on the point blinding process comprises two steps namely encryption and decryption, and also comprises a step that a certificate authority (CA) gives a public key Kp=sPCA and a private key dA=sIDA in advance by using the feature that a random parameter s belongs to [1, p-1] and p is a prime field which is represented by a formula, wherein PCA is a public parameter, and IDA is identity information of a user; and it is assumed that a user B encrypts a message which is represented by a formula to a user A, a formula is a bilinear pairing, and both P and Q are input formal parameters. The optimized automatic bilinear pairing encryption method and device based on the point blinding process provided by the invention are mainly applied to information security occasions.
Owner:TIANJIN UNIV
Storage pre-alignment and EBCDIC, ASCII and unicode basic latin conversions for packed decimal data
ActiveUS20050246507A1Improve performanceReduce in quantityMemory adressing/allocation/relocationConcurrent instruction executionEBCDICOperand
A method of pre-aligning data for storage during instruction execution improves performance by eliminating the cycles otherwise required for data alignment. The method can convert data between ASCII and Packed Decimal format, and between Unicode Basic Latin and Packed Decimal format. Conversion to Packed Decimal format is needed for decimal hardware in a microprocessor designed to generate decimal results. Converting from Packed Decimal to ASCII and Unicode Basic Latin is necessary to report Decimal Arithmetic results in a required format for the application program. To further improve performance, all available write ports in the fixed point unit (FXU) are utilized to reduce the number of cycles necessary to store results. To prevent data fetching of the unused destination data from slowing down instruction execution, the destination locations are tested for storage access exceptions, but the data for these operands are not actually fetched. A single read request from the FXU to the operand buffers effectively reads the entire destination address (up to 8 double-words of data) in a single cycle.
Owner:IBM CORP
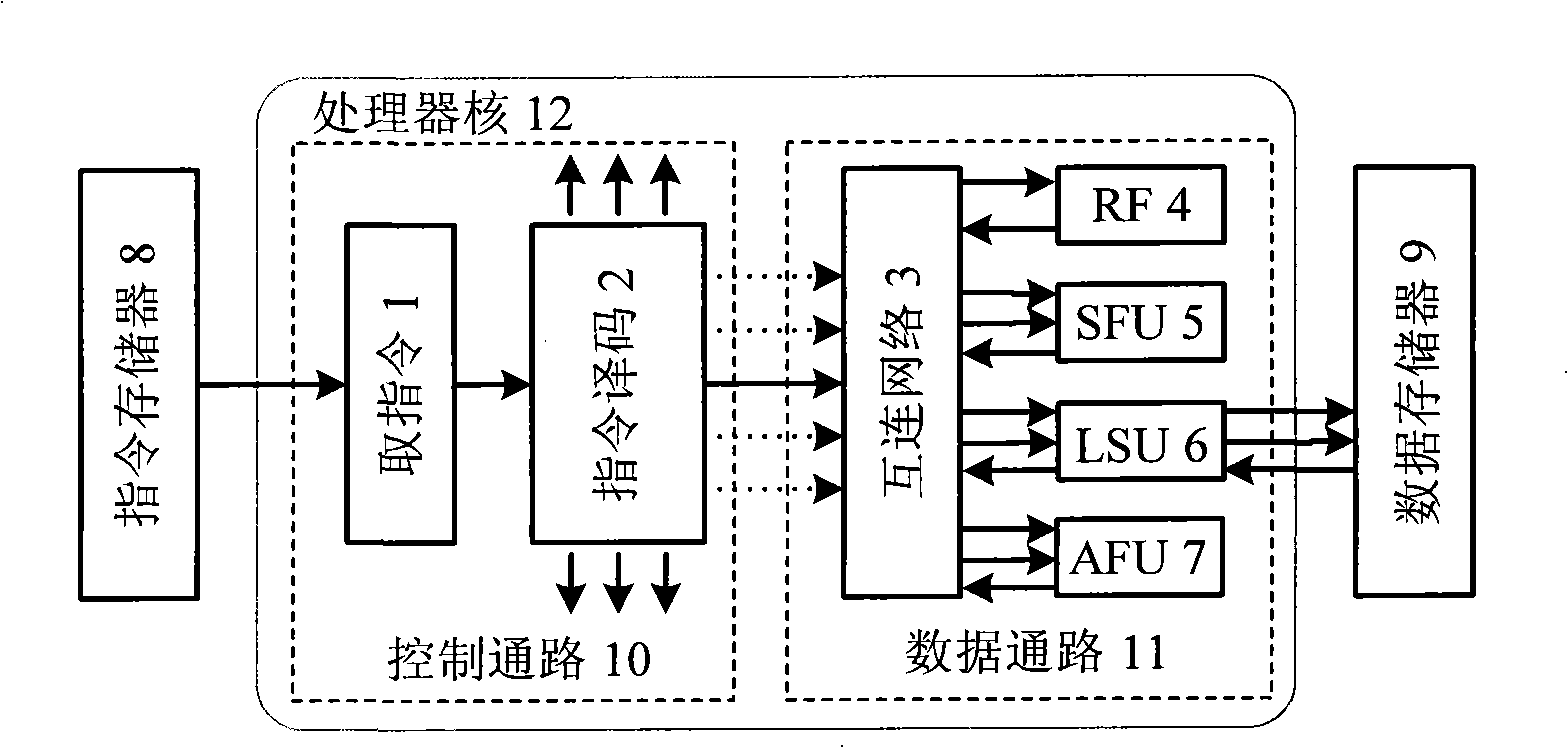
Asynchronous data triggering micro-processor architecture
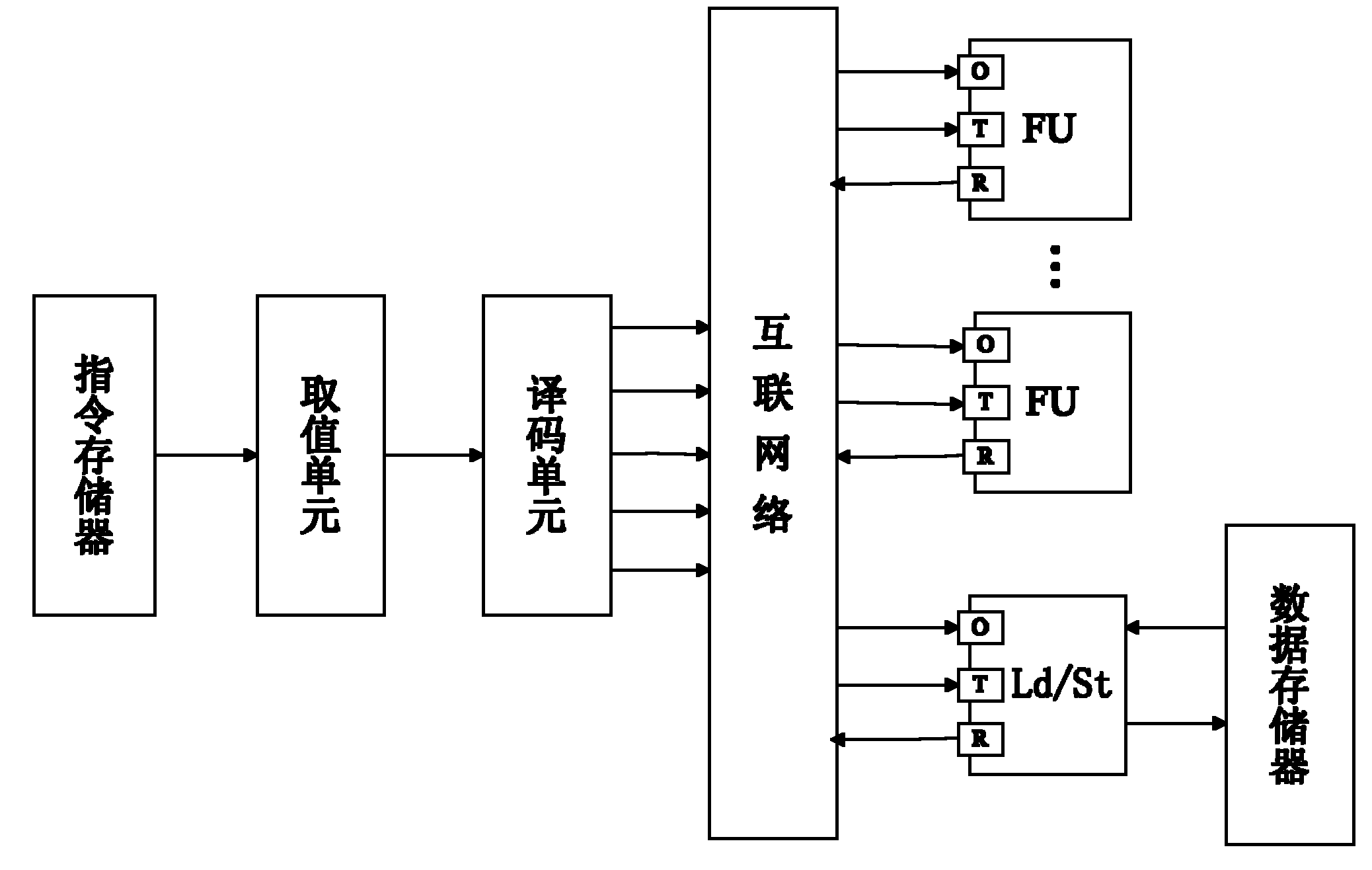
InactiveCN101403963AImprove performanceSimple structureConcurrent instruction executionInstruction memoryComputer architecture
The invention relates to a system structure of an asynchronous data triggered microprocessor, which consists of a data path and a control path; the data path consists of a register file and a functional unit, wherein, the functional unit is connected with a data storage device for carrying out reading and writing on the data storage device; the control path comprises an instruction fetching unit and a coding unit; wherein, the instruction fetching unit is connected with an instruction storage device for reading the instruction from the instruction storage device; meanwhile, the instruction fetching unit is also connected with the coding unit for sending the instruction obtained to the coding unit to carry out coding; the control path and the data path are connected by an interconnecting network, and the coding unit sends the instruction coding result to the needed functional unit by the interconnecting network. The invention combines a plurality of design methods of the microprocessors with the design technologies thereof, which has simpler structure and higher performance; low power consumption of the microprocessors can be realized on the two aspects of the system structure and the circuit in the invention, therefore, the technology of a custom instruction set processor does not need to excessively consider numerous problems which are originally faced.
Owner:戴葵
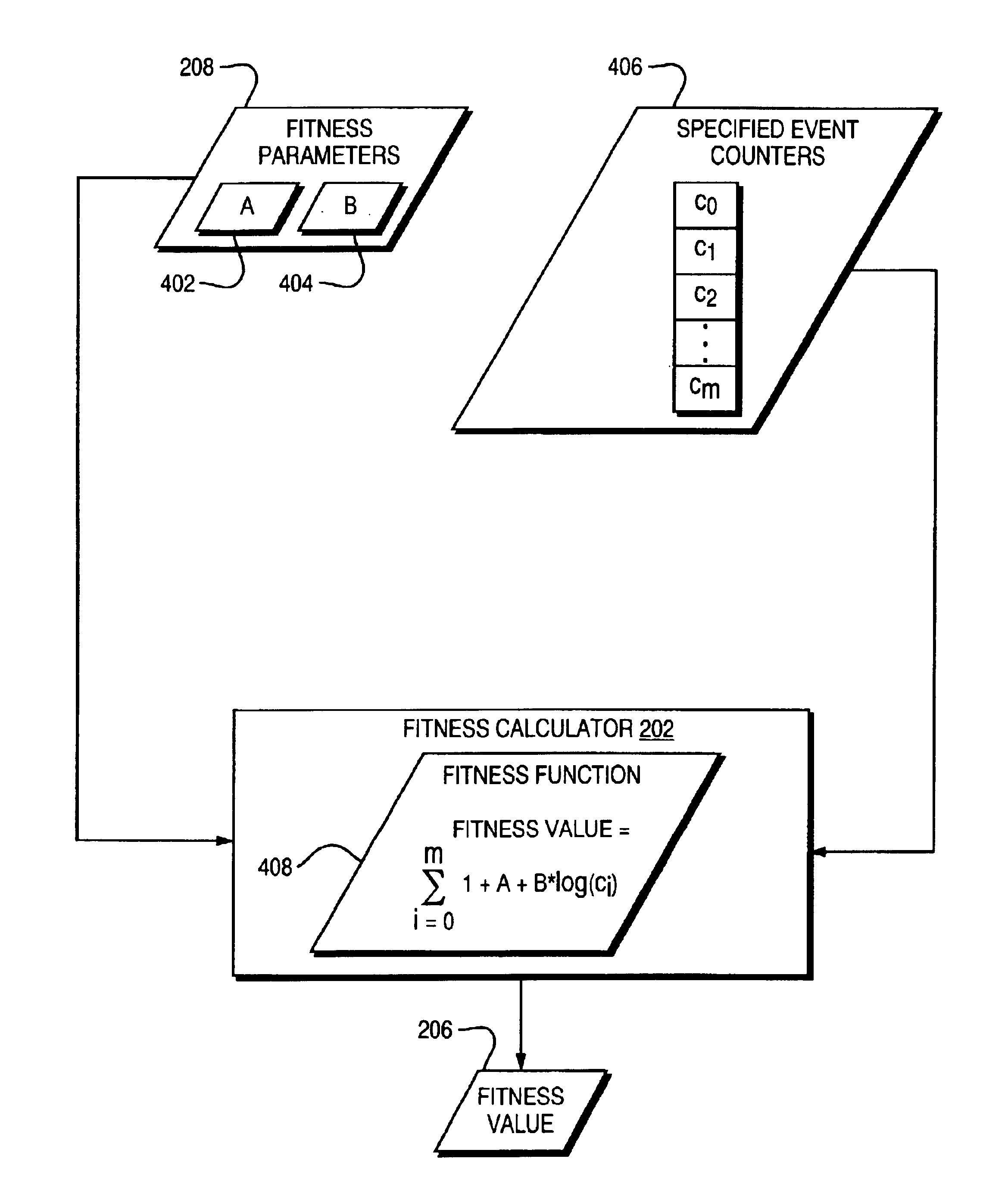
Random code generation using genetic algorithms
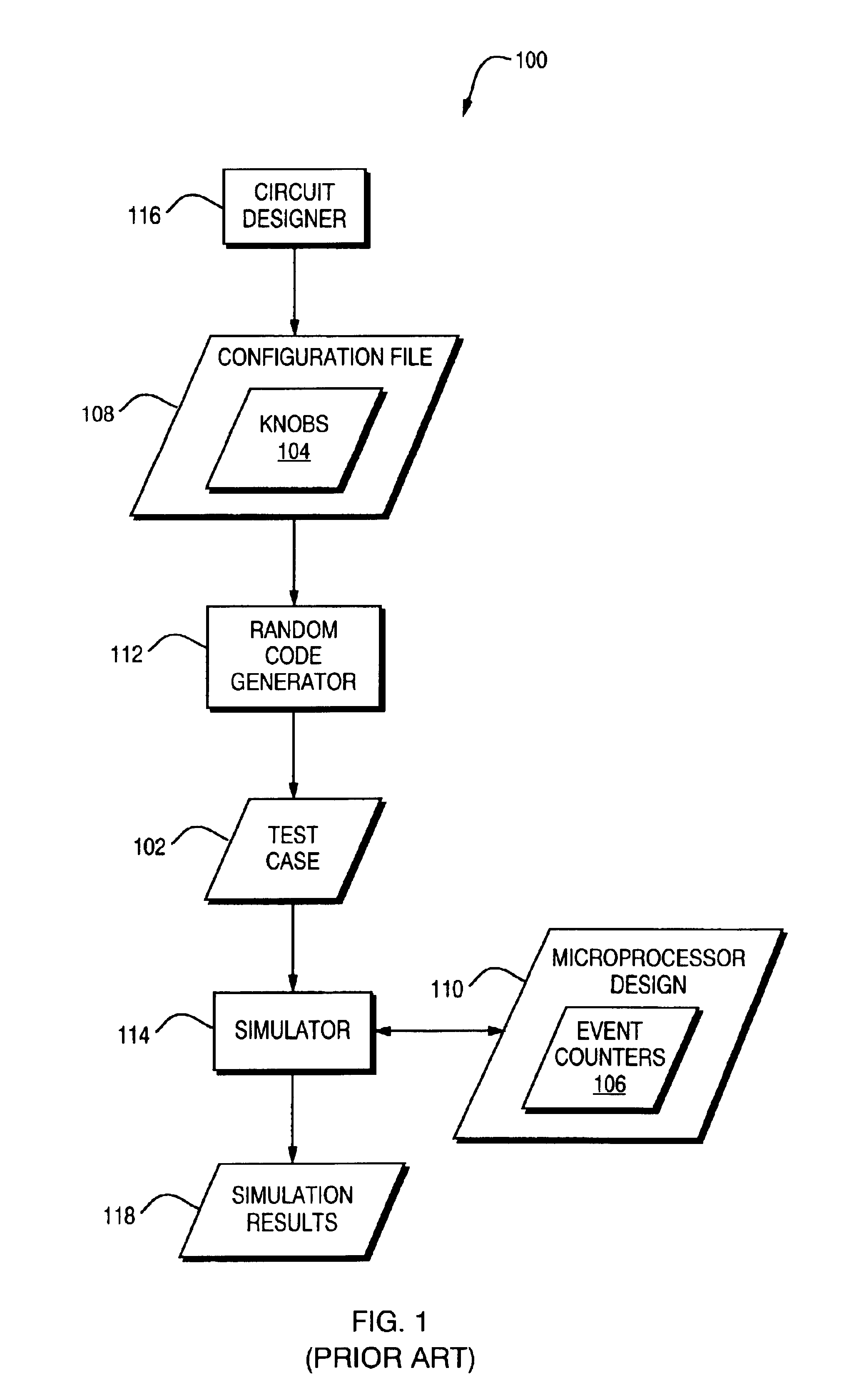
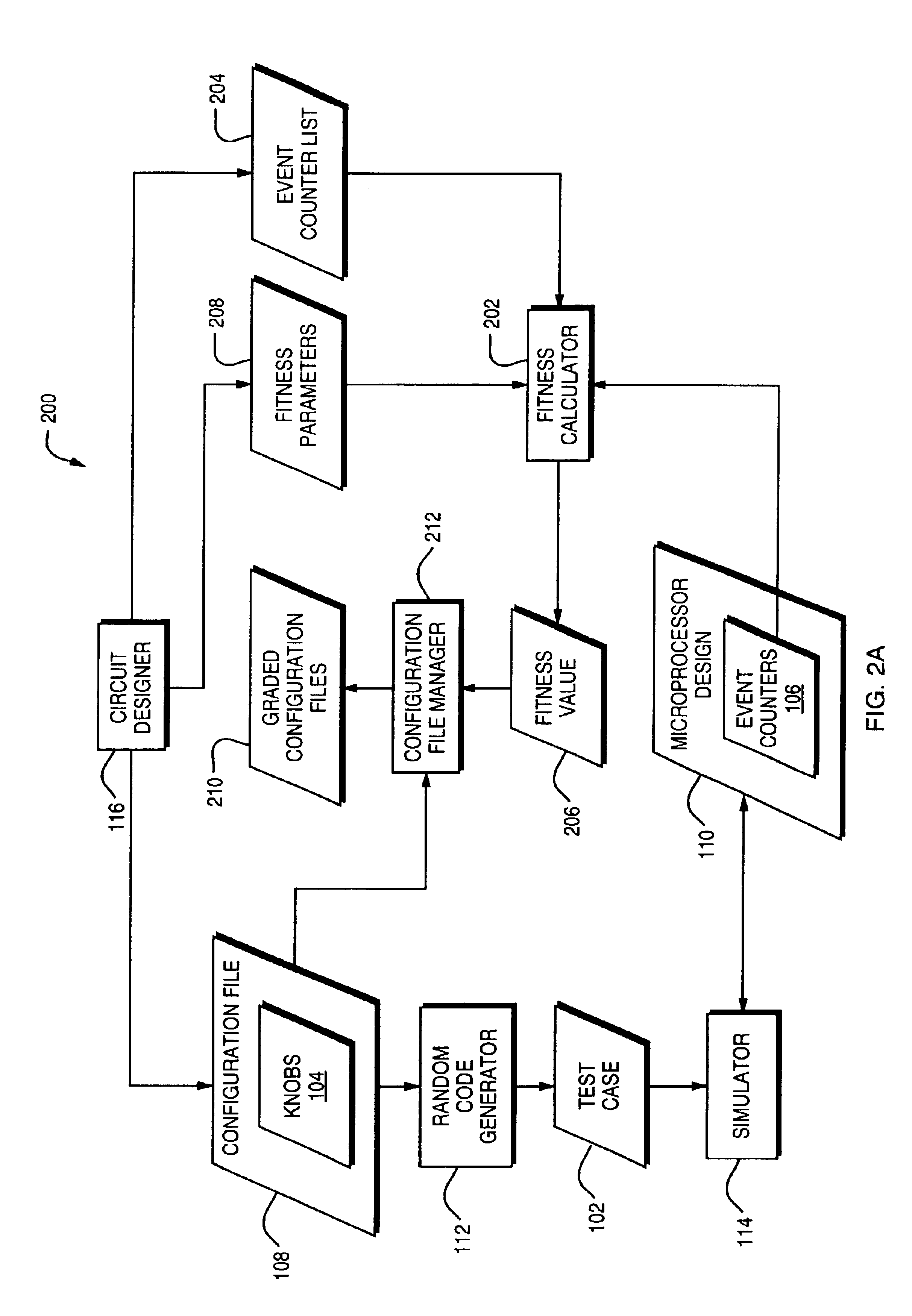
Techniques are disclosed for automatically generating test instructions for use in testing a microprocessor design. A configuration file includes a plurality of knobs which specify a probability distribution of a plurality of microprocessor instructions. A random code generator takes the configuration file as an input and generates test instructions which are distributed according to the probability distribution specified by the knobs. The test instructions are executed on the microprocessor design. The microprocessor behaviors that are exercised by the test instructions are measured and a fitness value is assigned to the configuration file using a fitness function. The configuration file and its fitness value are added to a pool of configuration files. A configuration file synthesizer uses a genetic algorithm to synthesize a new configuration file from the pool of existing configuration files. This process may be repeated to generate configuration files which increasingly exercise microprocessor behaviors which are of interest.
Owner:HEWLETT PACKARD DEV CO LP
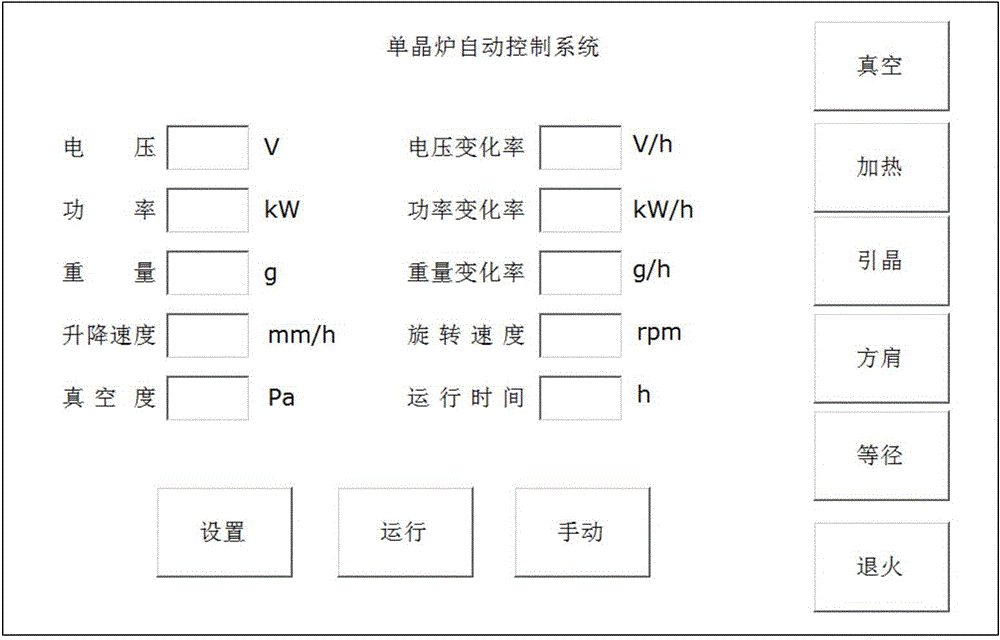
Automatic control system for Kyropoulos-process sapphire crystal growth
InactiveCN104911698AReduce dependenceReduce laborPolycrystalline material growthUsing seed in meltAutomatic controlControl system
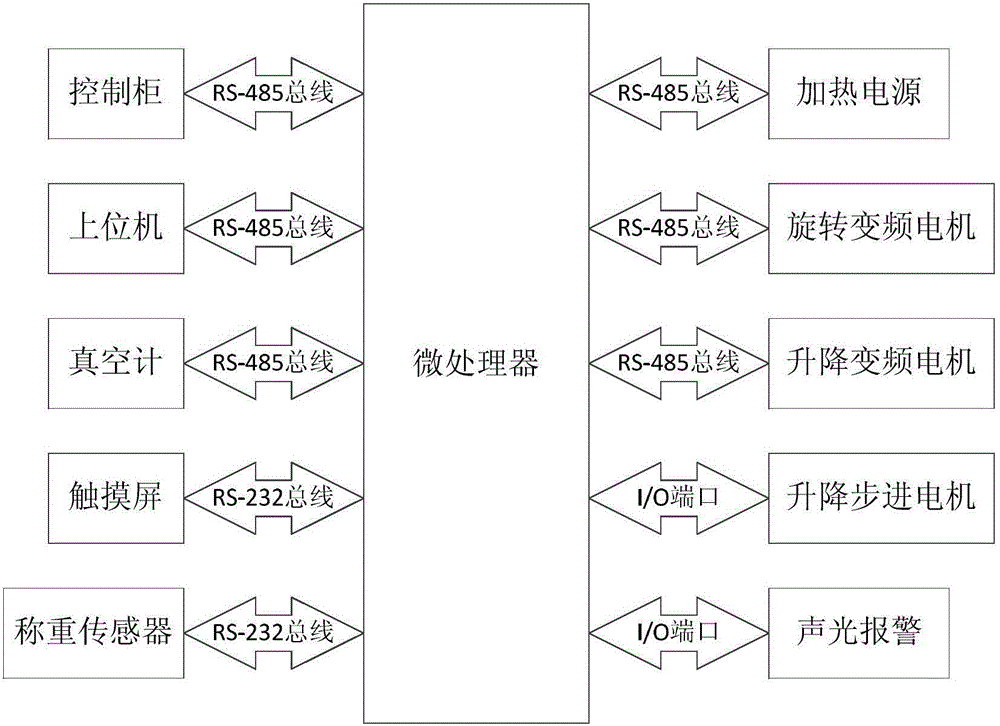
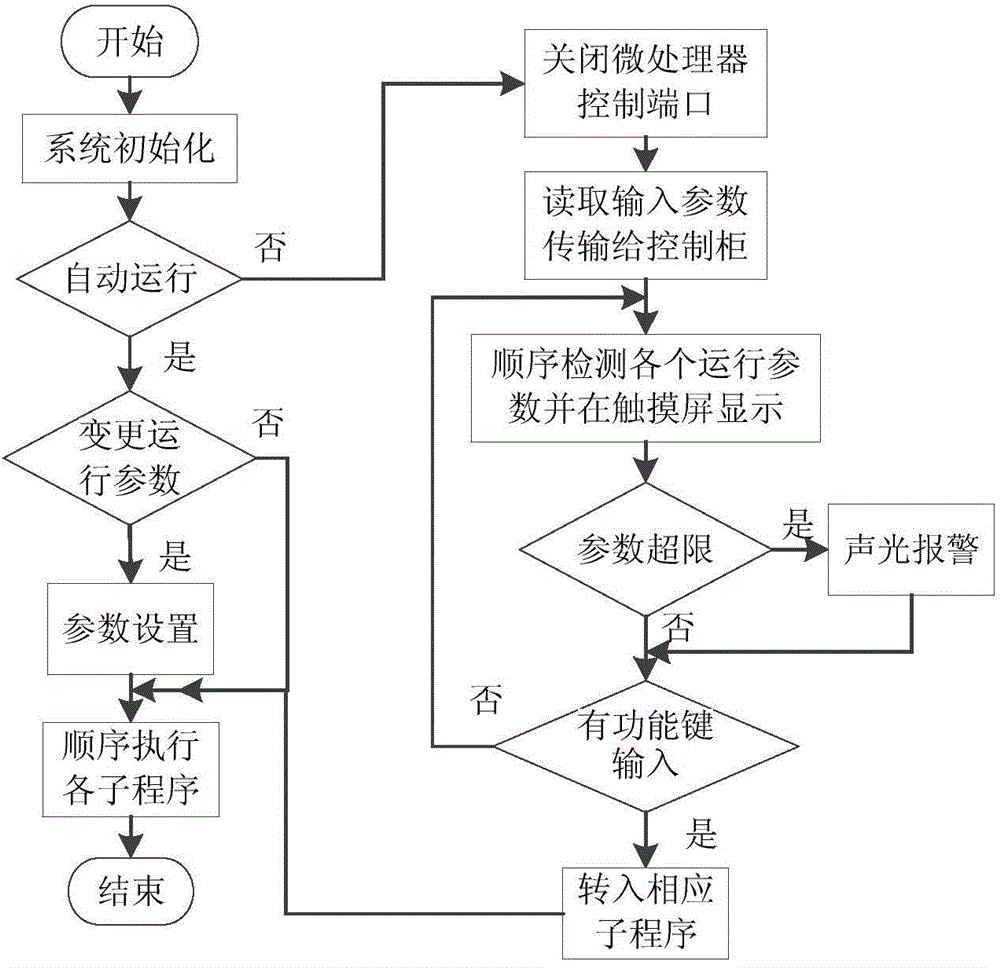
The invention relates to the field of automatic control in industrial production, particularly an automatic control system for Kyropoulos-process sapphire crystal growth. The invention is characterized in that the automatic control system mainly comprises a microprocessor, a touch screen, an audible and visual alarm circuit, a control cabinet, an upper computer, a vacuum meter, a heating power source, a rotary variable-frequency motor, an elevating variable-frequency motor, a weighing sensor and an elevating stepping motor, wherein the microprocessor is the core unit of the whole automatic control system, implements communication and control with the control cabinet, upper computer, vacuum meter, heating power source, rotary variable-frequency motor and elevating variable-frequency motor through an RS-485 bus, implements communication with the touch screen and weighing sensor through an RS-232 bus, and controls the operation of the elevating stepping motor and audible and visual alarm circuit through an I / O port. The multi-physical-quantity detection and control system in the Kyropoulos-process sapphire crystal growth process is designed on the basis of the embedded microprocessor, implements automatic control on the whole crystal growth process, lowers the dependence on the artificial intervention and technology capability of operating personnel in the crystal growth process, reduces the labor amount of the operating personnel, and enhances the standardability and crystal quality of the crystal growth operation process.
Owner:ZHEJIANG EAST CRYSTAL ELECTRONICS CO LTD
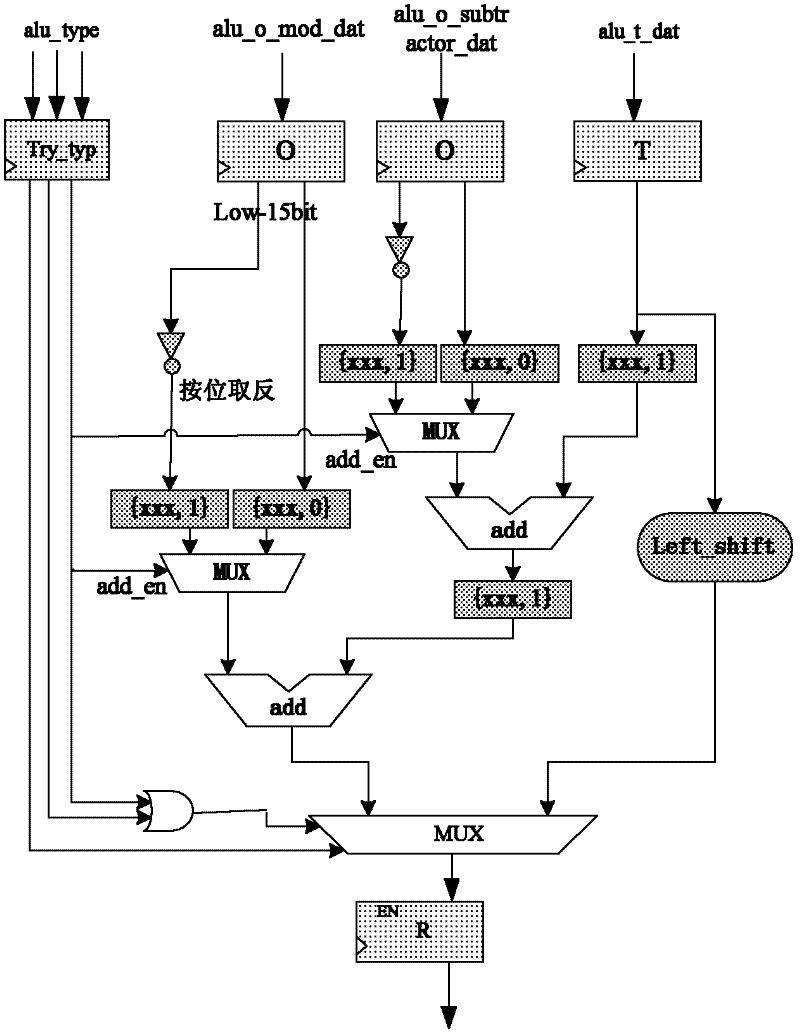
Optimal redundant arithmetic for microprocessors design
InactiveUS6848043B1Digital computer detailsConcurrent instruction executionOperandMicroprocessor design
Methods and apparatus for improving system performance using redundant arithmetic are disclosed. In one embodiment, one or more dependency chains are formed. A dependency chain may comprise of two or more instructions. A first instruction may generate a result in a redundant form. A second instruction may accept the result from the first instruction as a first input operand. The instructions in the dependency chain may execute separately from instructions not in the dependency chain.
Owner:INTEL CORP
Intelligent household system based on Internet of Things
InactiveCN105204455ARealize integrationSmart Home ServiceTransmission systemsTransmissionMicrocontrollerNetwork packet
The invention relates to an intelligent household system based on the Internet of things. The intelligent household system comprises a remote client, an intelligent router system and household WPAN (Wireless Personal Area Network). The WPAN is established among household devices via a microcontroller. An RF chip NRF24L01 which works in 2.4g (ISM frequency range) is combined with a microprocessor of the MSP430 series to design network nodes, and a solution scheme for the mini household WPAN is established. An intelligent route of the Linux system is used, the Internet is connected via a network packet to serial port, the intelligent household system can be controlled remotely by a user via a webpage and the like. security guard is integrated with intelligent service, and the intelligent household system has good development prospects.
Owner:HANGZHOU DIANZI UNIV
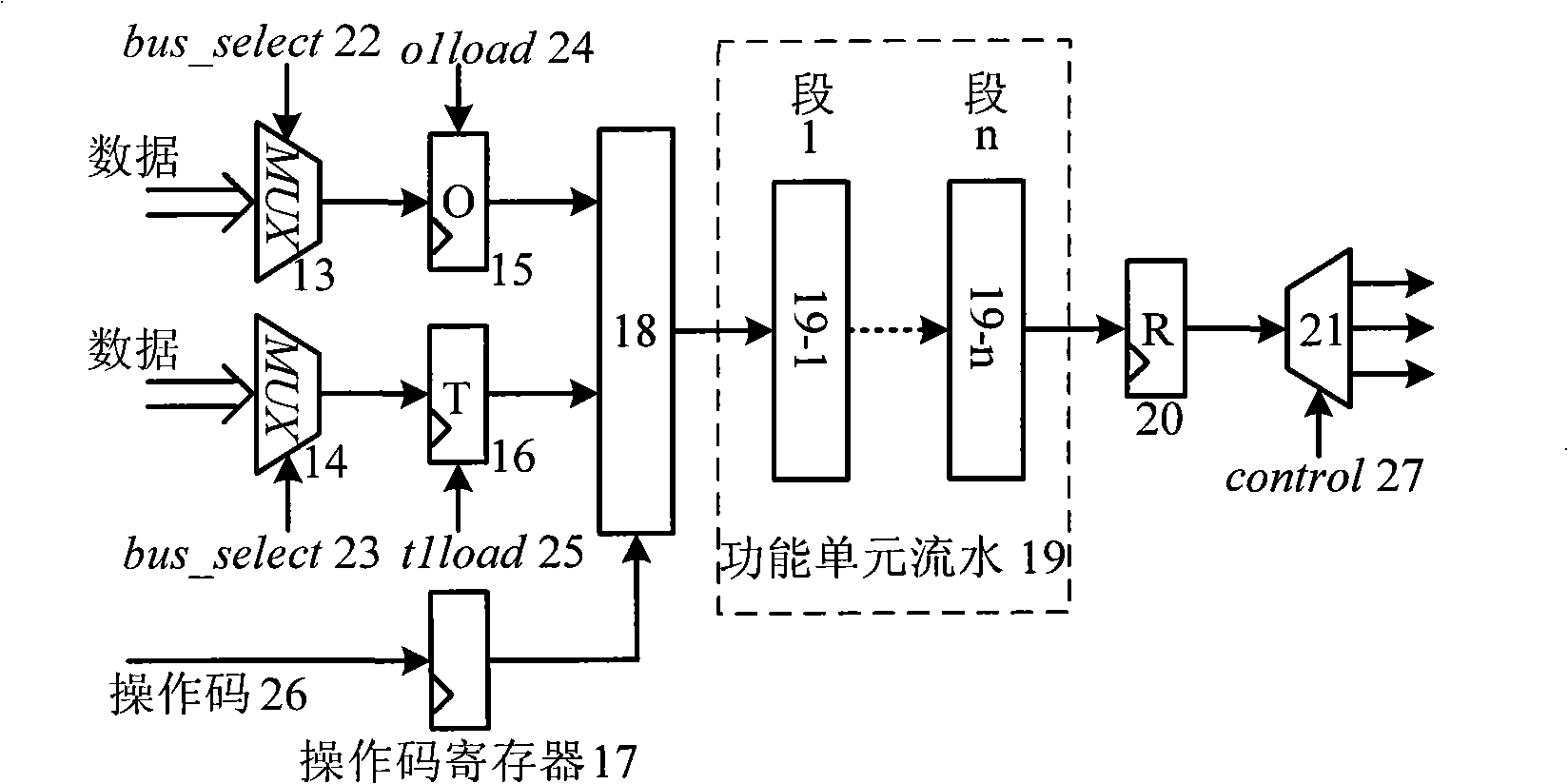
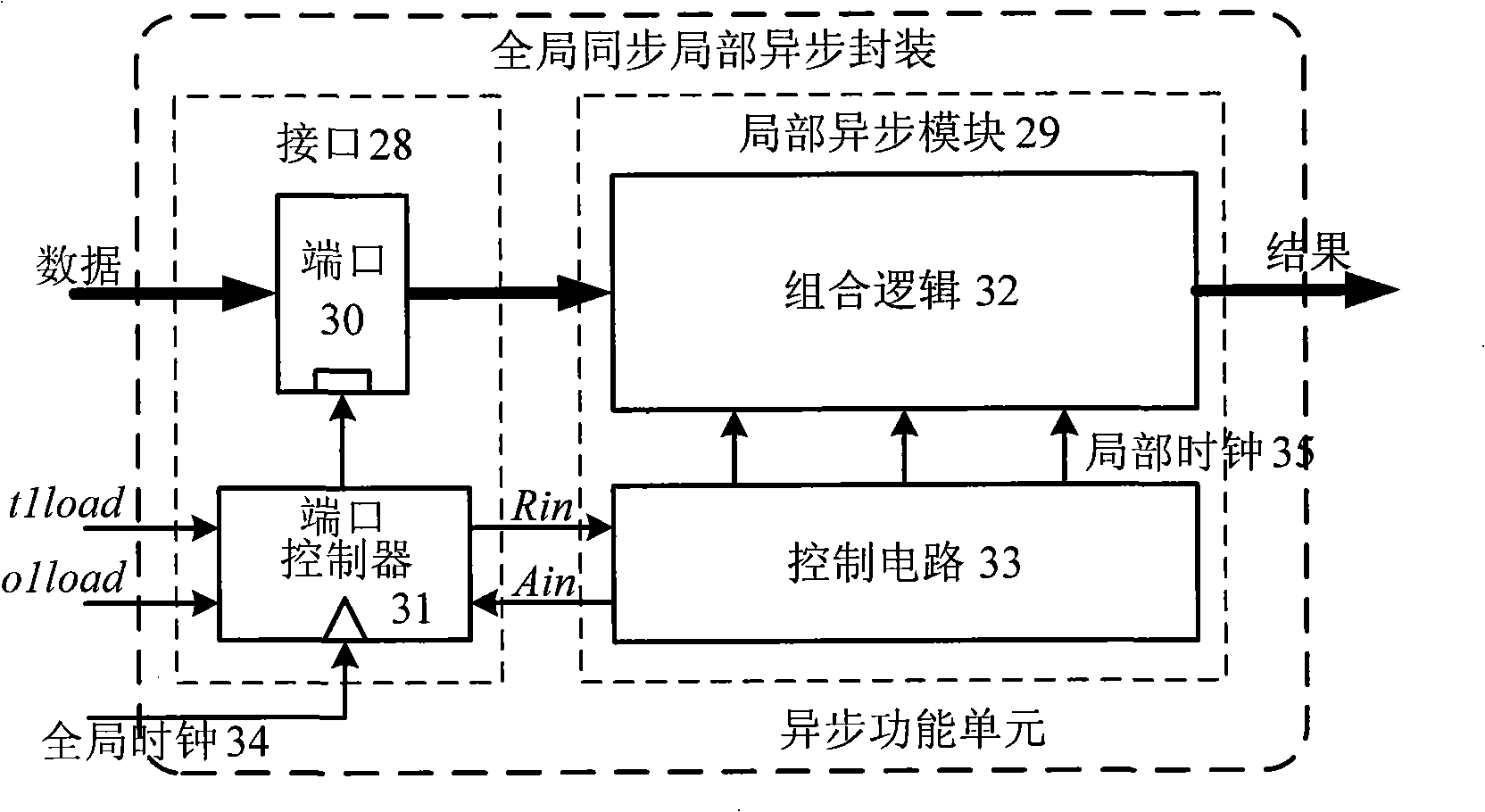
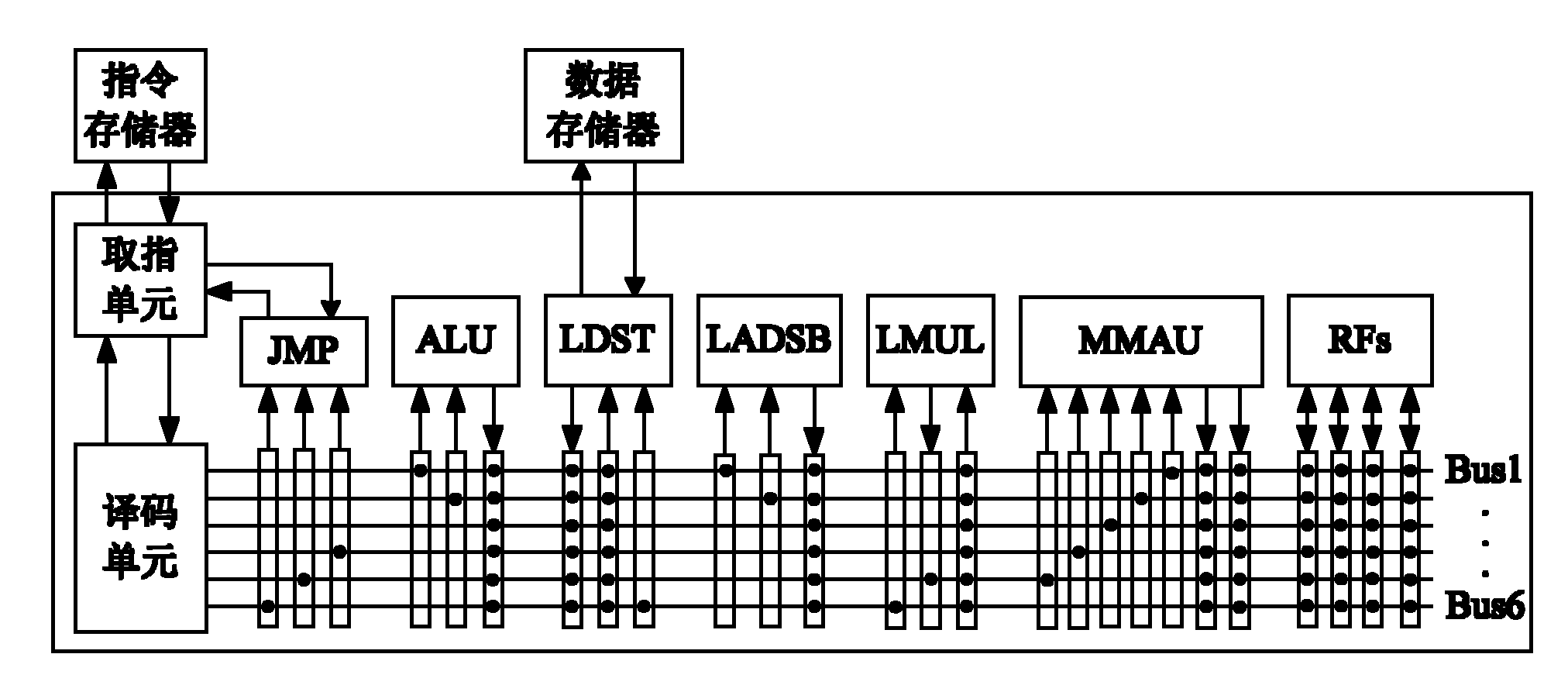
Elliptic curve cipher processor
The invention discloses an elliptic curve cipher processor, and relates to the field of information technology security and micro-processor design. The processor is of a transport triggered architecture (TTA) structure, and the hybrid flow mechanism of the elliptic curve cipher processor comprises a transmission flow and a functional unit flow. The elliptic curve cipher processor comprises a command memory, a fetch unit, a decoding unit, a register file, a bus internetwork, a Socket and a functional unit, wherein the fetch unit fetches a command in the command memory; the command is decoded by the decoding unit; the decoded command is subjected to an error correction code (ECC) operation by selecting a corresponding functional unit through the bus internetwork; operation data required by the functional unit is acquired through the register file or the functional unit; and the functional unit is interconnected with the Socket through the bus internetwork. By utilizing the elliptic curve cipher processor, the operation speedup ratio is improved, the engineering change cycle is shortened, a software and hardware collaborative design is realized, and the problem of going against secondary development is solved.
Owner:TIANJIN UNIV
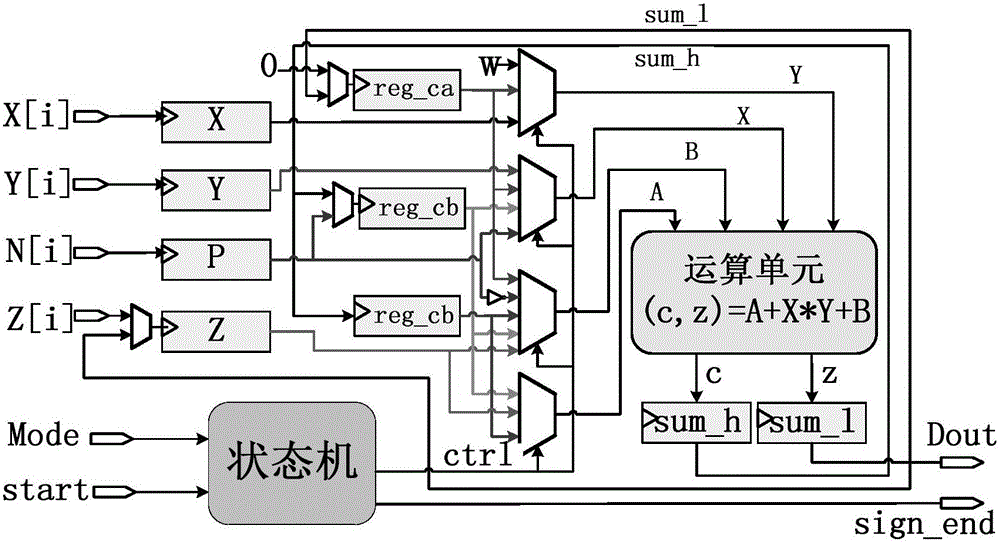
Double-core parallel RSA password processing method and coprocessor
InactiveCN105871552AImprove computing efficiencyReduce areaPublic key for secure communicationCryptographic attack countermeasuresPlaintextDual core
The present invention relates to the field of information security and microprocessor design, in order to realize the conversion of modular multiplication into simple decimal addition and multiplication through FIOS modular multiplication algorithm, fully reduce the area of modular multiplication operation unit, and effectively avoid writing back a large amount of intermediate data process. From the perspective of hardware implementation, it improves the computational efficiency of the algorithm and further saves computational resources, fundamentally reduces the time and space overhead of encryption and decryption, and effectively improves the encryption and decryption performance of RSA. The technical solution adopted by the present invention is that, before encryption, a dual-core parallel RSA encryption processing method needs to rely on a certificate authority (CA) as a trusted third party to be responsible for the generation, storage, maintenance, and revocation of the user's private key and public key certificate Link, when encrypting, user B executes the operation c=m e (modN) and send the encrypted information c to user A; when decrypting, user A uses his own private key d to perform operations on the ciphertext c to recover the plaintext. The invention is mainly applied to information security processing.
Owner:TIANJIN UNIV
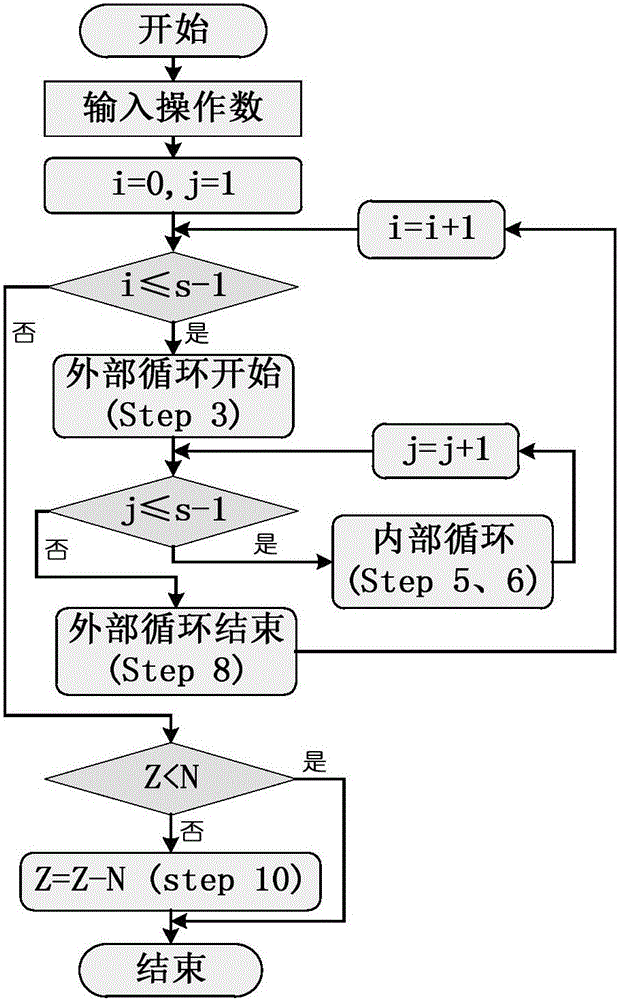
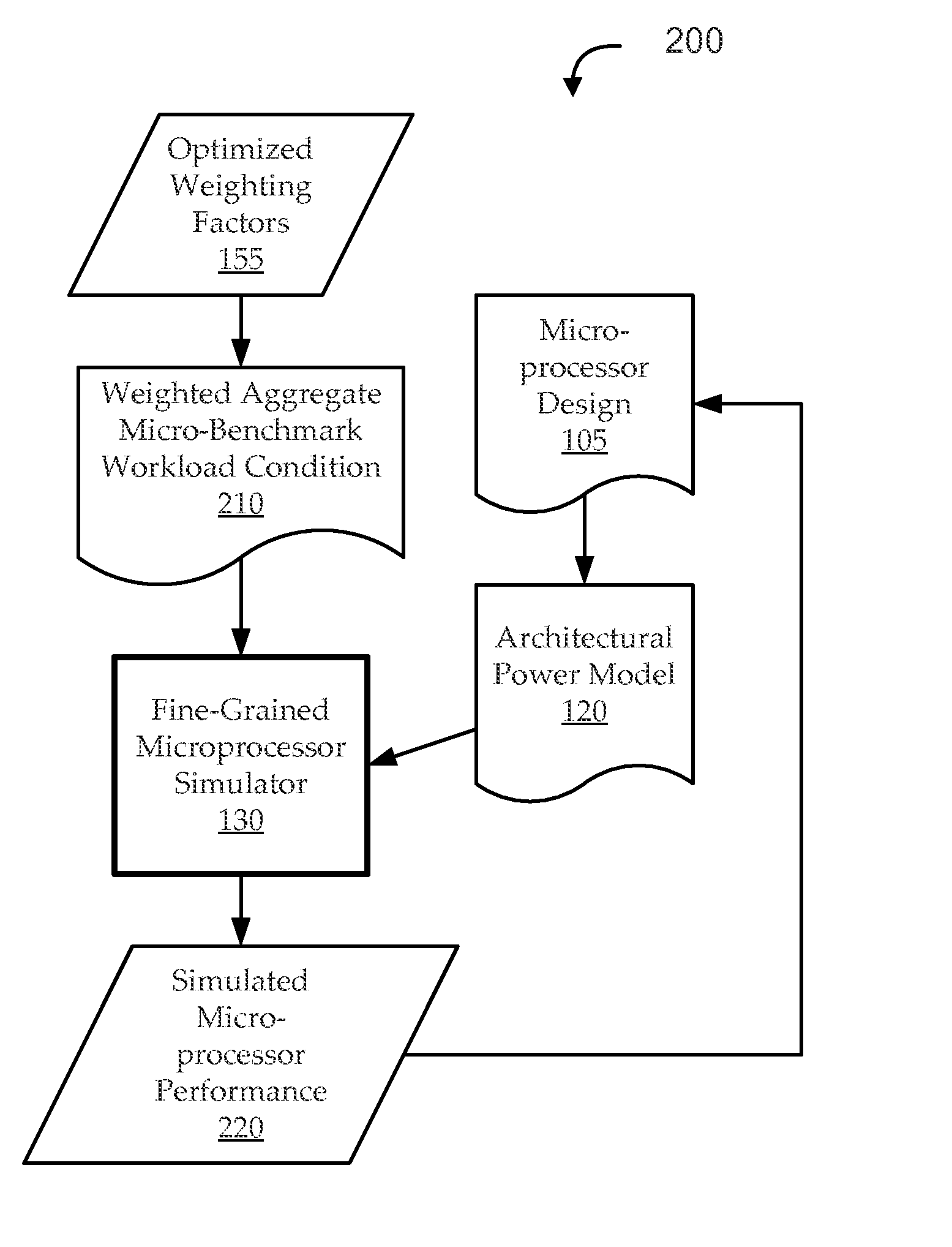
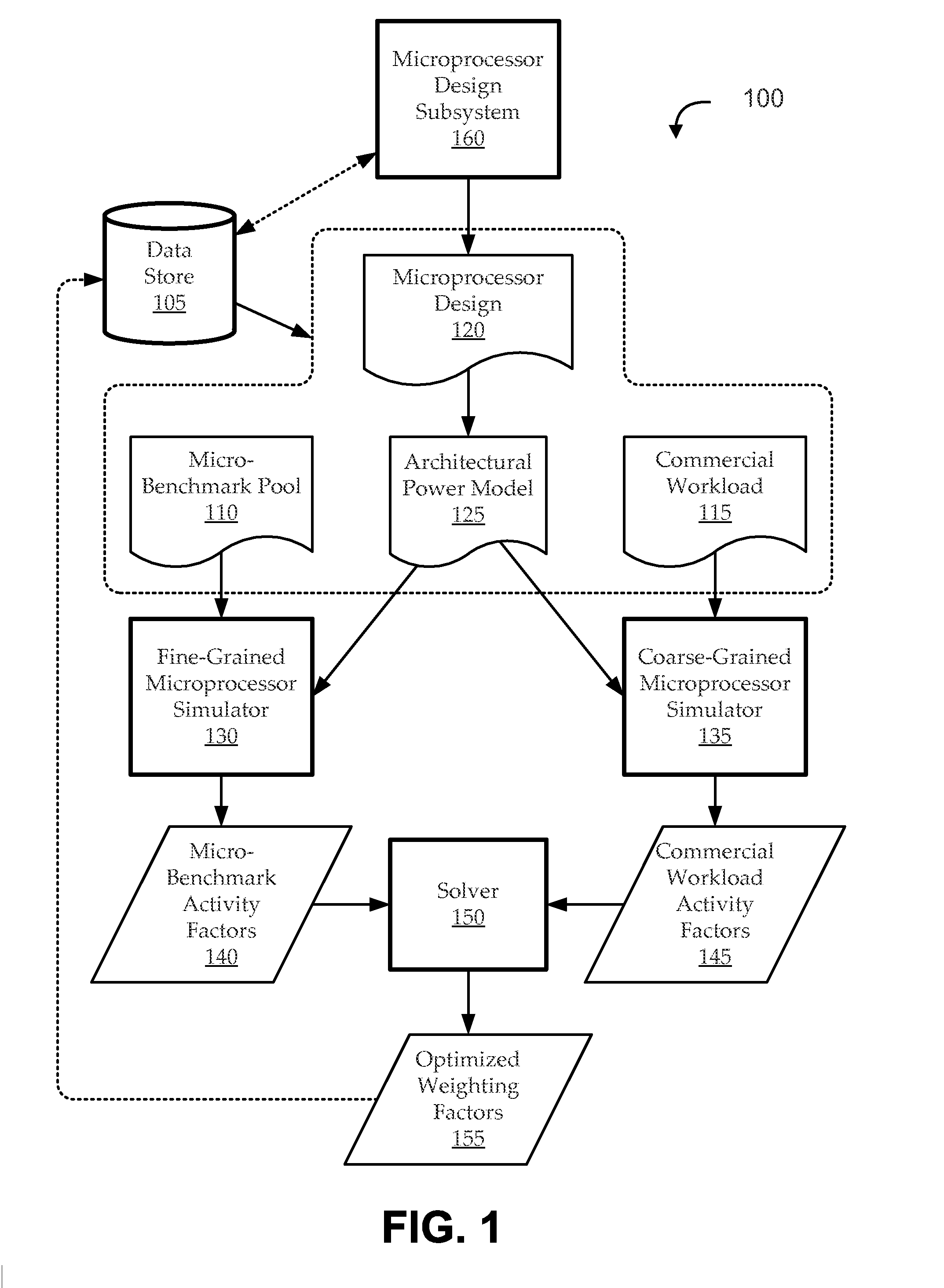
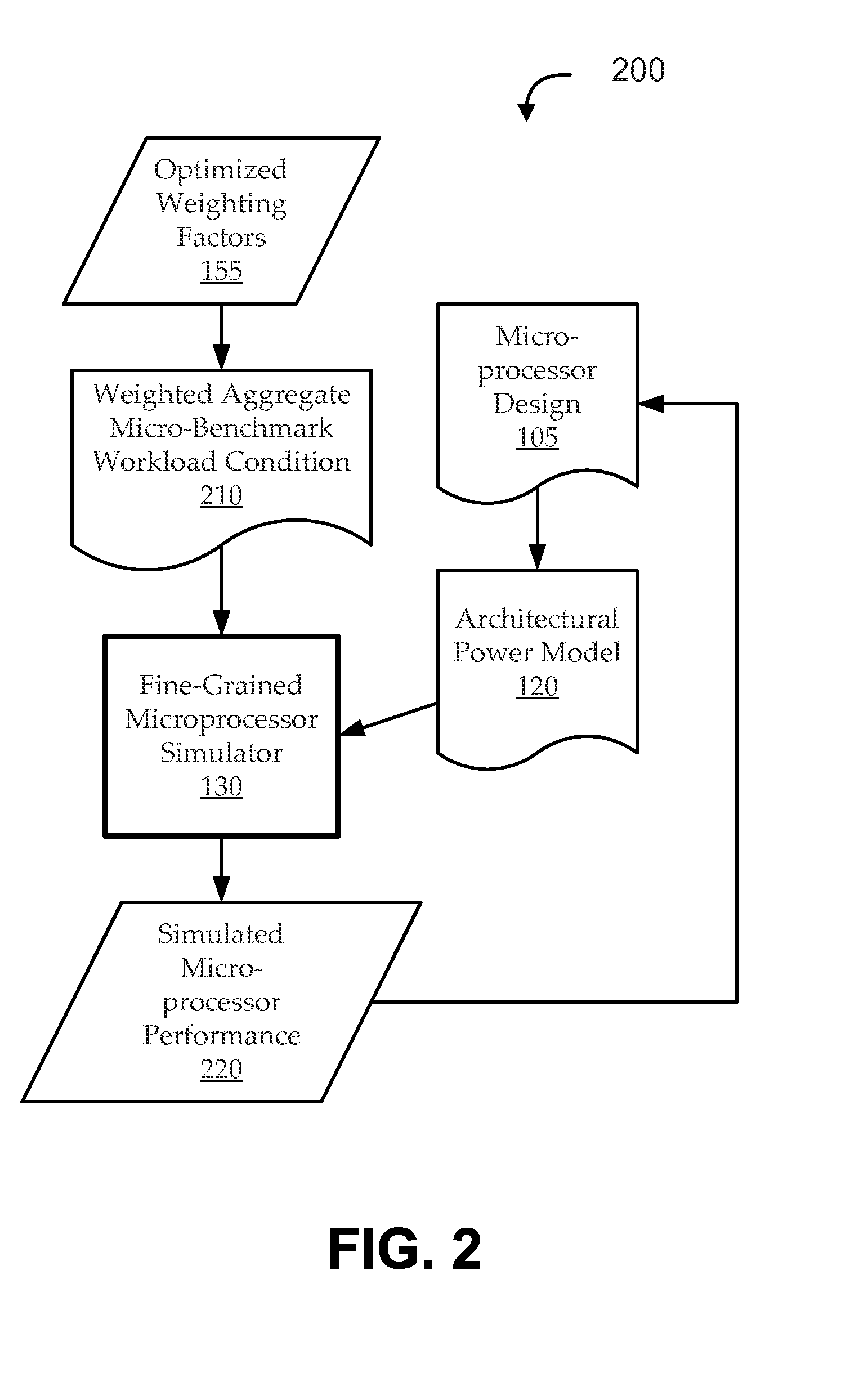
Micro-benchmark analysis optimization for microprocessor designs
ActiveUS20150347666A1Effective simulationEfficient designDesign optimisation/simulationCAD circuit designWorkloadProcessor design
Embodiments include systems and methods for optimization of micro-benchmark analysis for microprocessor designs. For example, embodiments seek to generate a suite of micro-benchmarks and associated weighting factors, which can be used to effectively define a weighted aggregate workload condition for a fine-grained (e.g., RTL) simulation in a manner that is a sufficient proxy for predicted commercial workload conditions. The suite of micro-benchmarks can be appreciably more efficient to simulate than the commercial workload, so that using the suite of micro-benchmarks as a proxy for the commercial workload can provide many benefits, including more efficient iterative design.
Owner:ORACLE INT CORP
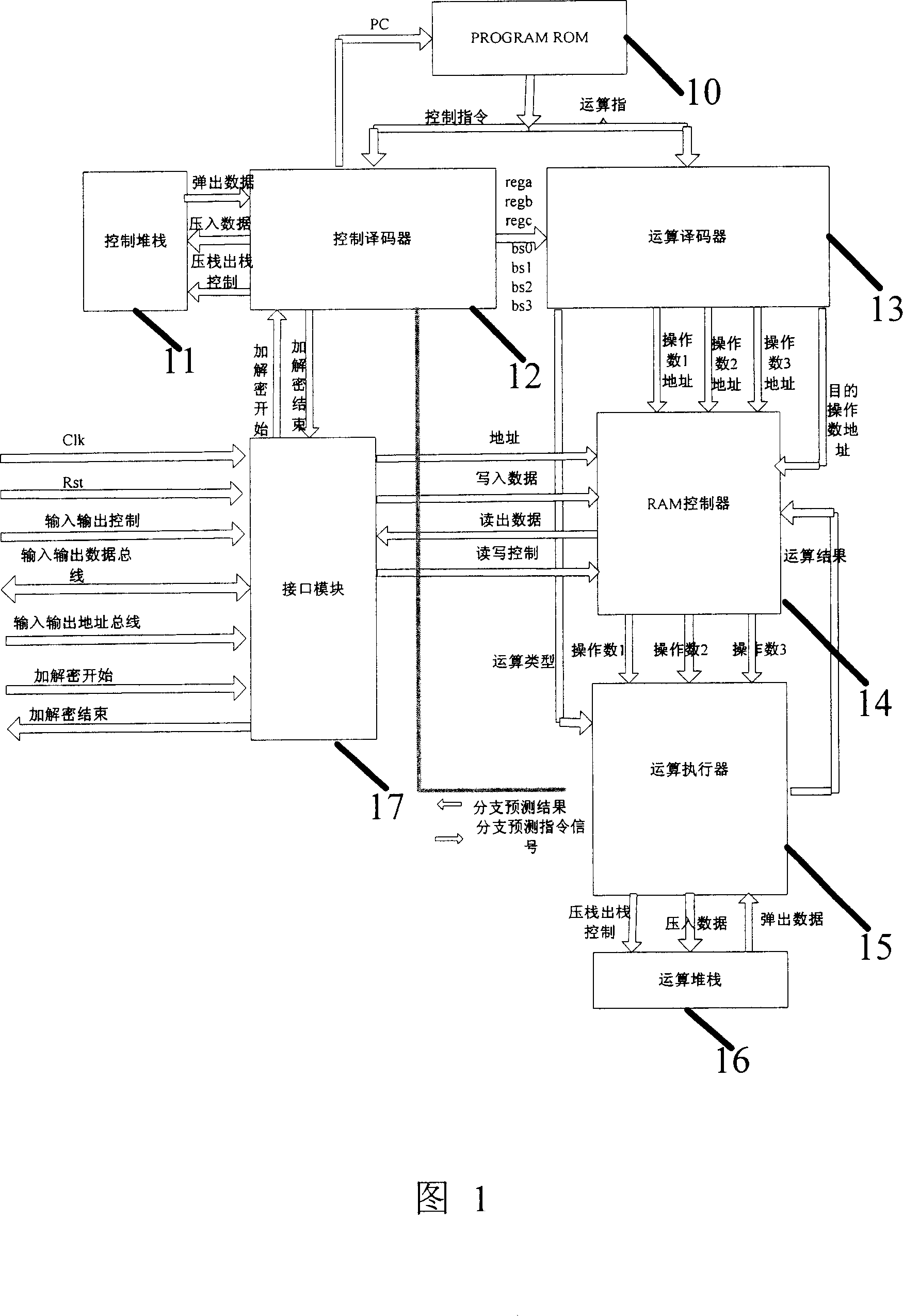
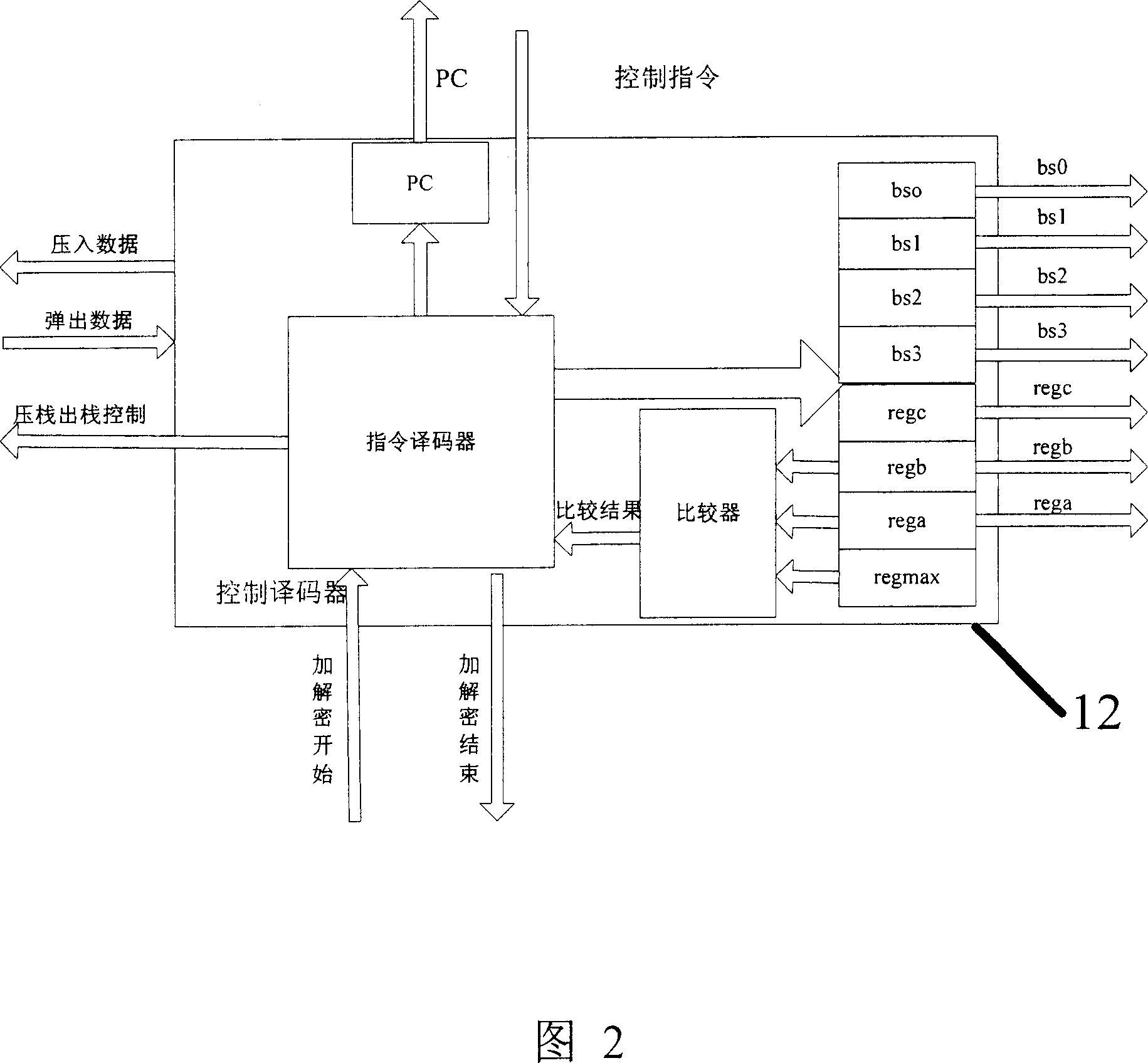
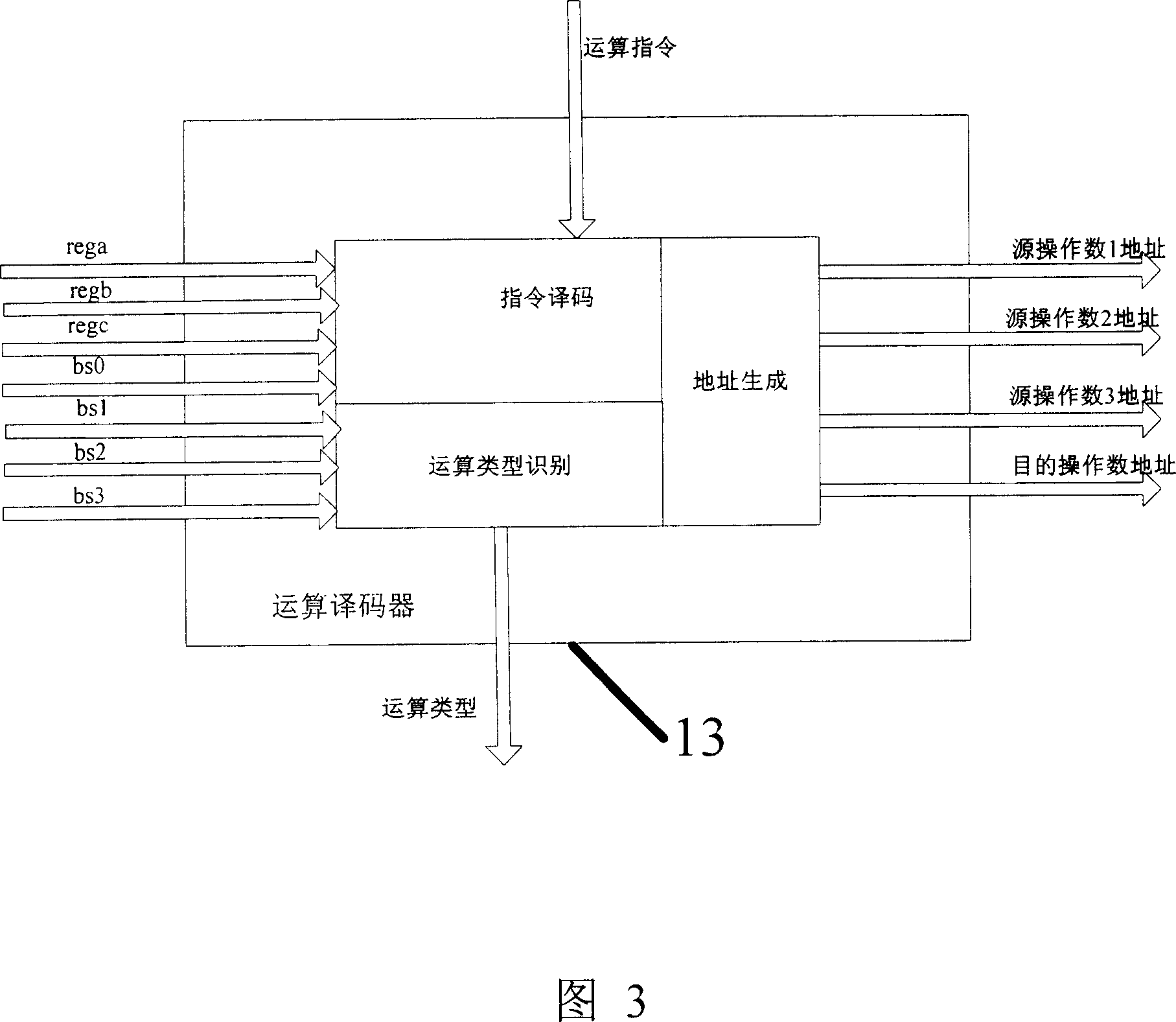
Programmable security processor
InactiveCN1959694AEasy to implementShorten the timeMultiple keys/algorithms usageInternal/peripheral component protectionEmbedded applicationsComputer module
A programmable safety processor consists of program storage, control stack, control decoder, operation decoder, RAM controller, operation executor, operation stack and interface module. It is featured as supporting programmable structure, setting with some basic operation units and utilizing program control and said basic operation unit to realize multiple ciphering deciphering / algorithm.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
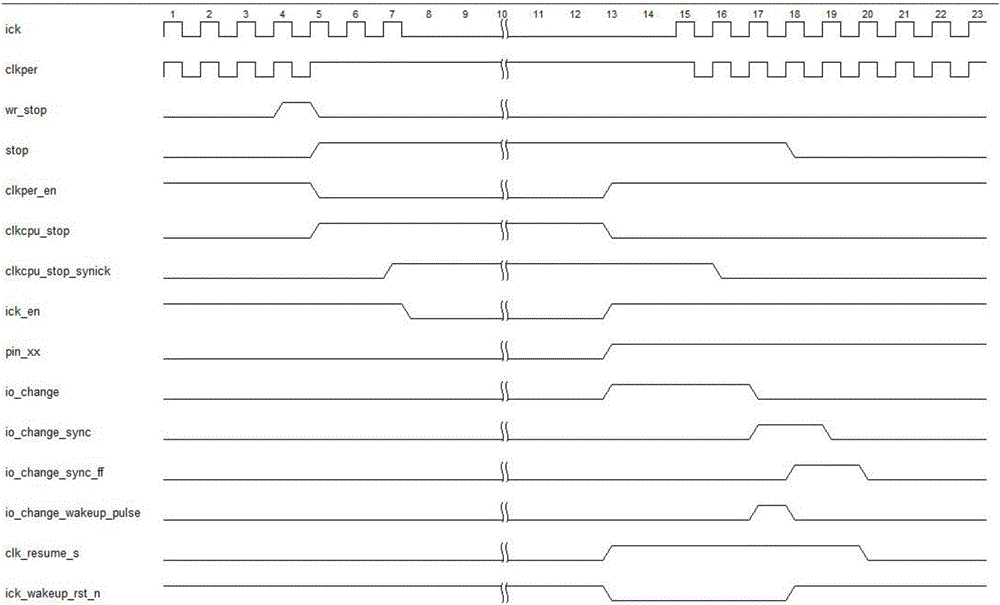
Ultra-low power consumption clock control method applied to MCU (Micro-programmed Control Unit) system
PendingCN106371549AExtended service lifeReduce power consumptionPower supply for data processingElectrical batteryEngineering
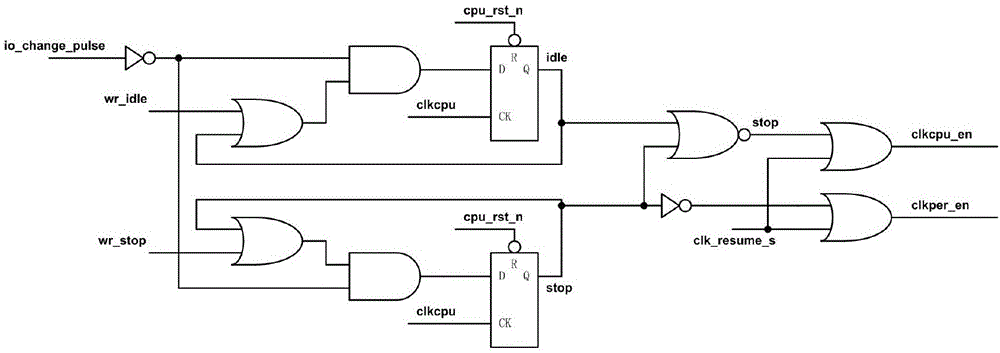
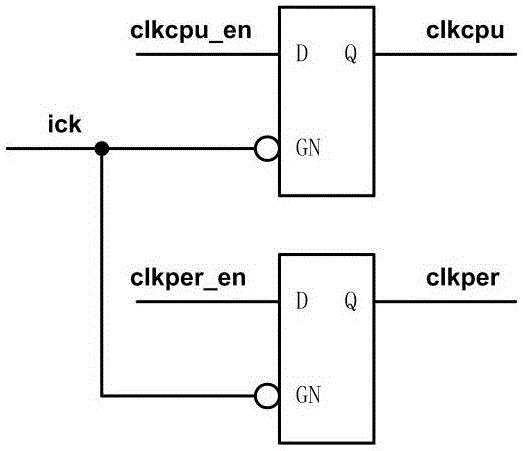
The invention discloses an ultra-low power consumption clock control method applied to an MCU (Micro-programmed Control Unit) system. In the ultra-low power consumption clock control method, the MCU system is adopted; the whole MCU system includes two clocks of clkcpu and clkper; a low power consumption mode of the system includes an IDLE mode and a STOP mode; when the system enters the IDLE mode, the clock clkcpu is closed and the clock clkper is opened, a CPU (Central Processing Unit) enters a dormant state, only external equipment is working at the moment; when the system enters the STOP mode, the clocks of clkcpu and clkper are simultaneously closed, the CPU enters a deep sleep state, the CPU and the external equipment stop working at the moment. Through the gated clocks and the deep sleep mode, the power consumption of the system is reduced, the overall stability is improved and the service life of a battery is prolonged. In the design of a microprocessor, most of the power consumption comes from the clocks, the clocks cause uninterrupted charging and discharging, thus the power consumption of the whole system is greatly influenced through reduction of the clock activity; the clock gating is conducted from the clock source of the system, the work clocks of the whole MCU are closed, and meanwhile the system is enabled to enter the deep sleep state.
Owner:SHENZHEN BOJUXING IND DEV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com