Double-core parallel RSA password processing method and coprocessor
A processing method and processor technology, which is applied to the public key of secure communication, countermeasures against encryption mechanism, digital transmission system, etc., can solve the problem that cannot meet the increasingly stringent requirements of encryption chip speed and area, and limit the calculation speed of RSA algorithm , chip area increase and other issues, to achieve the effect of resisting time attacks and simple power consumption attacks, saving modular exponentiation time, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
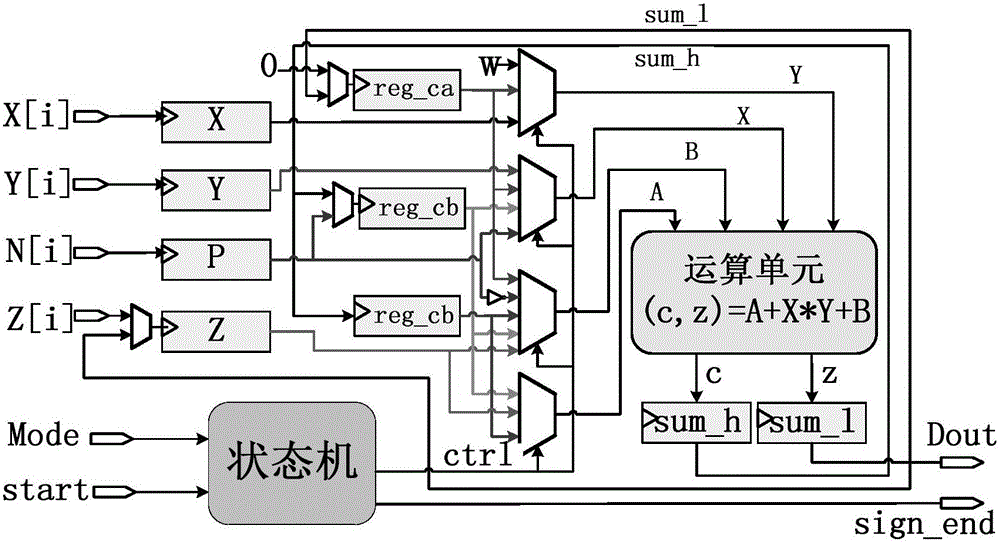
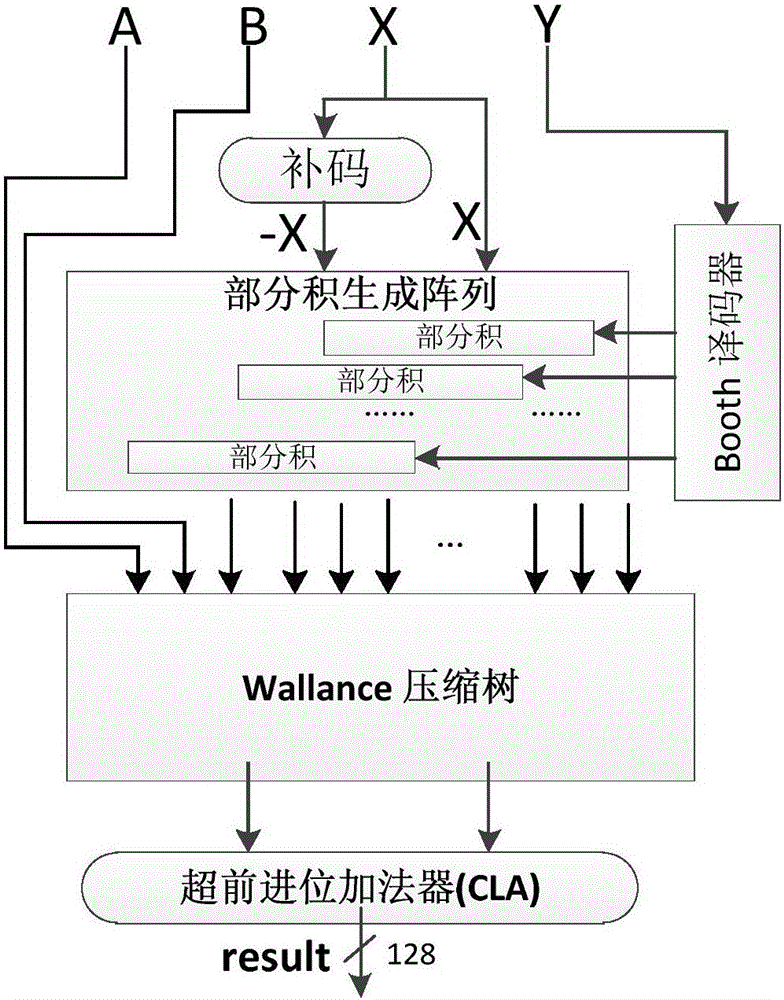
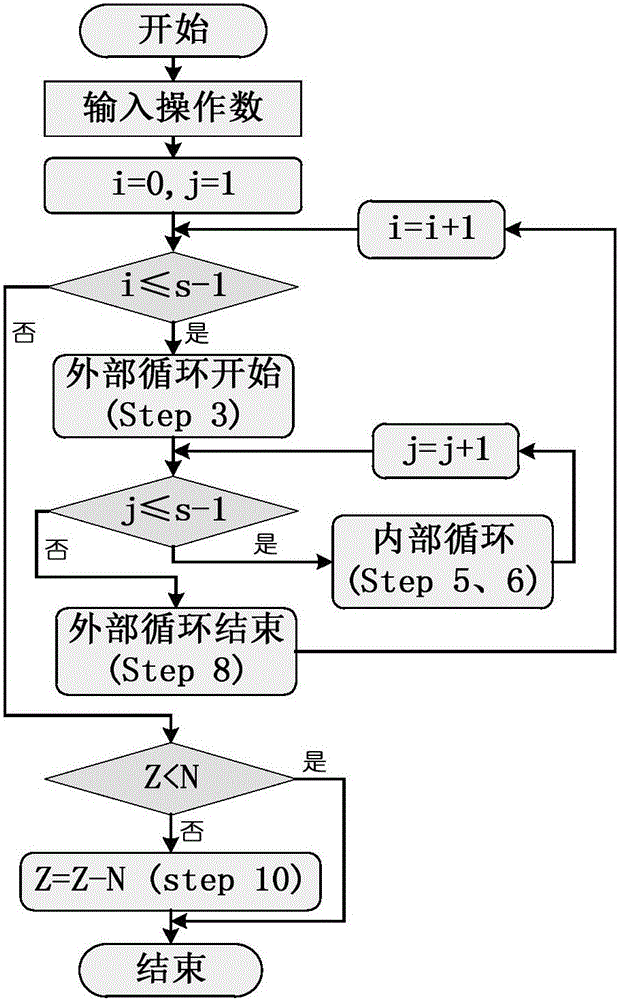
[0031] The design of the invention is a dual-core parallel RSA encryption coprocessor. The design uses the FIOS modular multiplication algorithm based on 64bit words as the execution algorithm of a single operation core, so that the system can fully improve the parallelism of the hardware in the hardware structure and fully reduce the area of the chip. At the same time, the characteristic of no data dependence between the modular multiplication and the modular square in the Powering Ladder modular exponentiation algorithm is used to ensure that the operations of the two cores run independently, which greatly improves the execution efficiency of the RSA encryption operation.
[0032] In order to design an efficient and safe dual-core parallel RAS cryptographic coprocessor, the present invention selects the Powering Ladder modular exponentiation algorithm as the RAS encryption and decryption execution algorithm. The algorithm transforms the modular exponentiation operation int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com