Programmable security processor
A security processor and program memory technology, applied in the field of programmable security processors, to save time, improve algorithm execution efficiency, reduce time and the number of instructions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
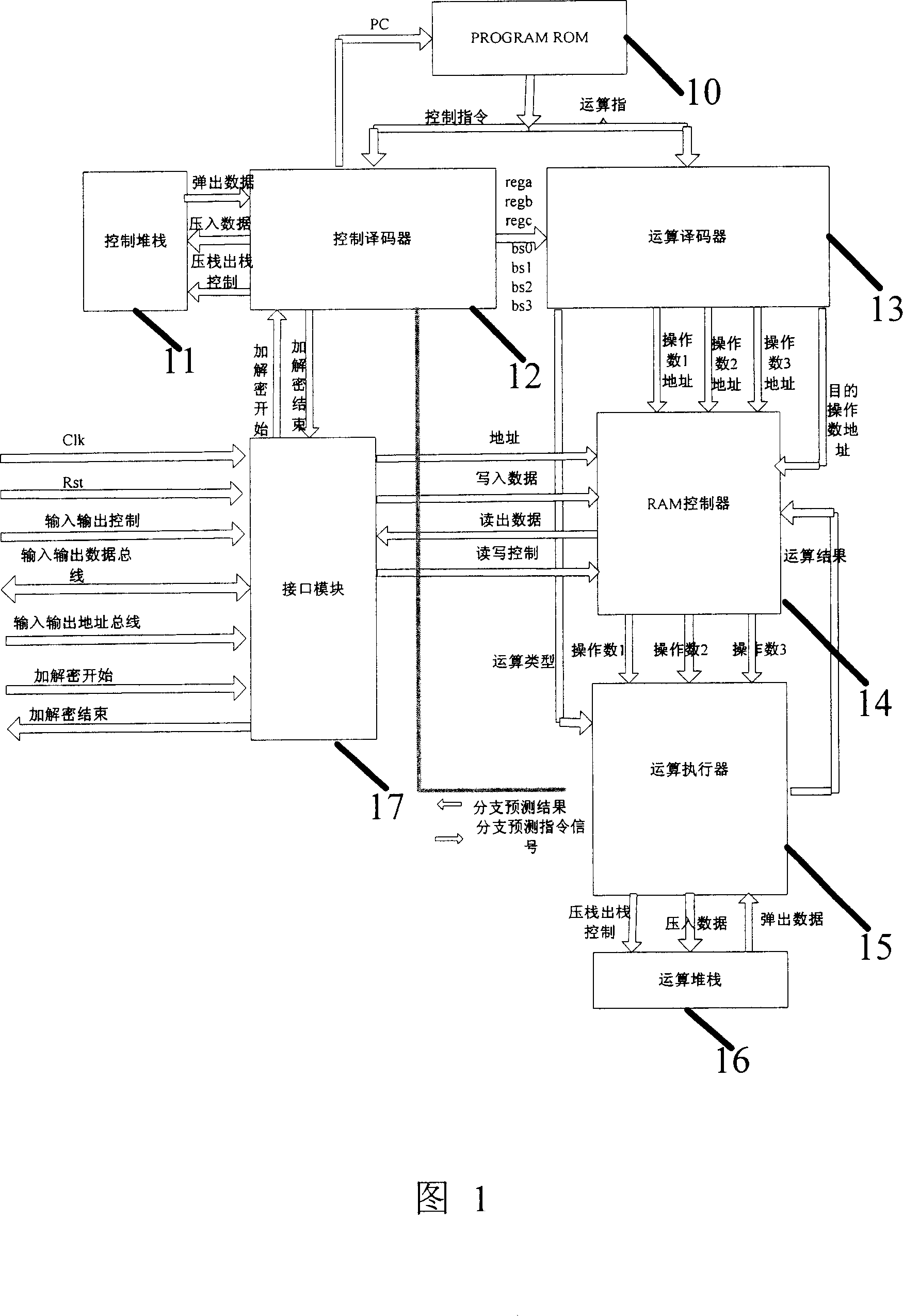
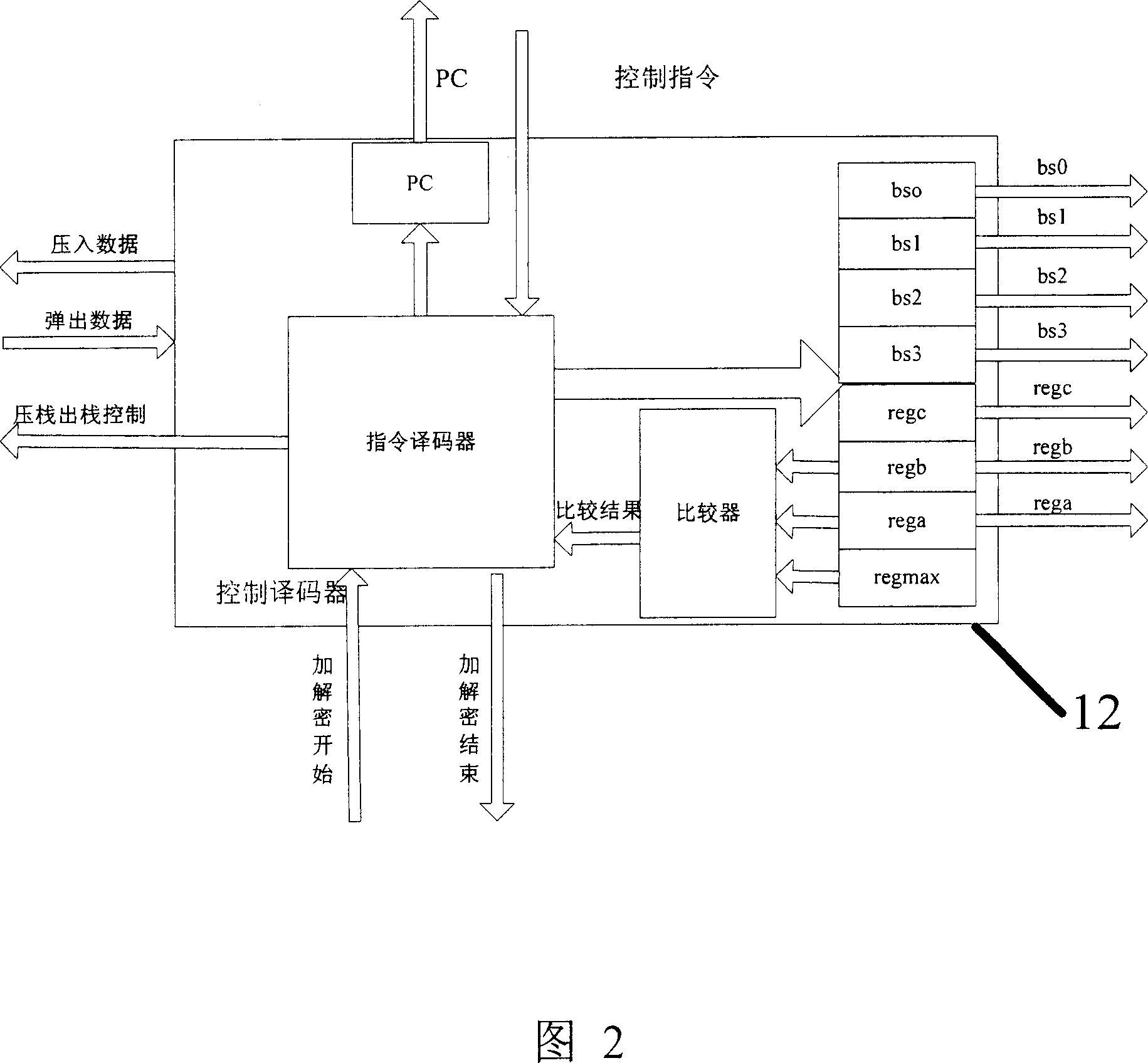
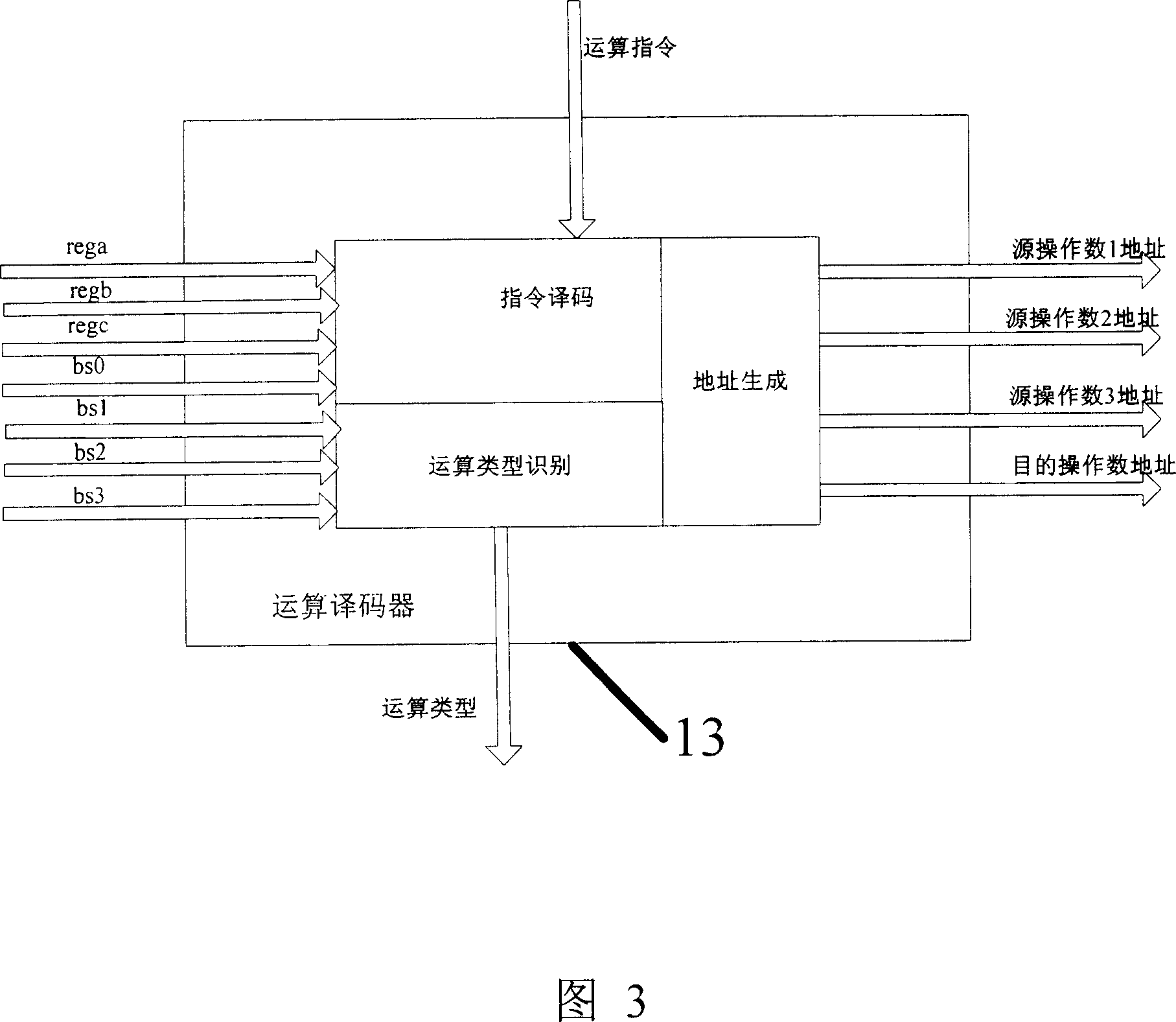
[0051] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
[0052] The processor architecture of the present invention is a structure that can support programming. By analyzing the basic operations of most cryptographic operations, and then setting these basic operation units, various encryption and decryption algorithms can be realized through program control and basic operations.
[0053] Most encryption and decryption algorithms, especially block ciphers, such as RSA, AES, etc., involve a large number of cycles.
[0054] For example, the RSA algorithm, assuming that the key is {d, n}, first divides the encrypted and decrypted data into several groups, and each group is encrypted separately, which is a big cycle; then find the d power modulo n of the grouped data M, the most comm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com