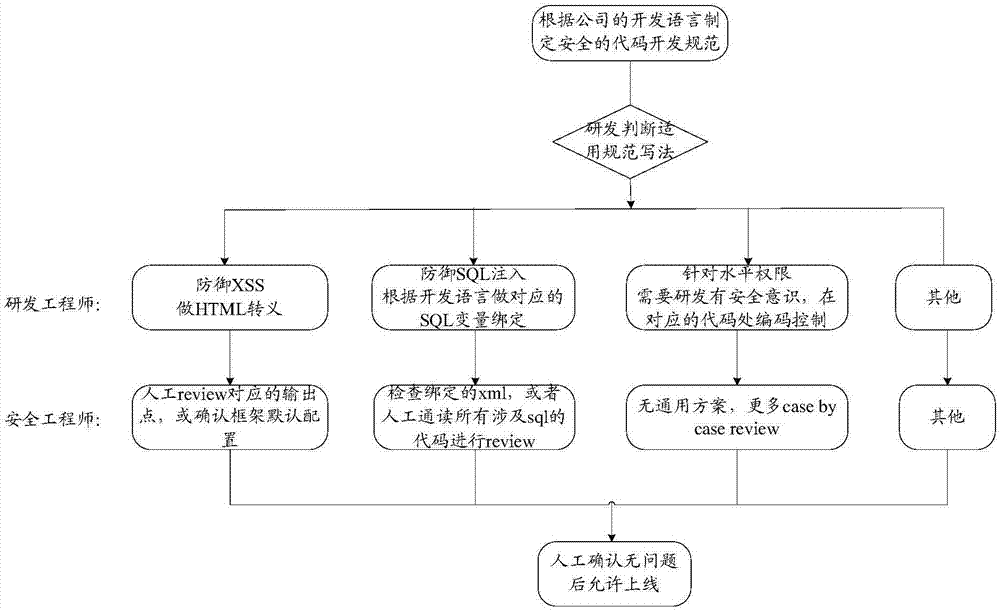
Method and device for processing web-side access
A processing method and access request technology, applied in the field of network information, can solve the problems of not being able to control web risks well, relying on human input and labor level, manual verification by security engineers, etc., to achieve a strict and complete security defense mechanism and reduce human input Cost, effect of improving web security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
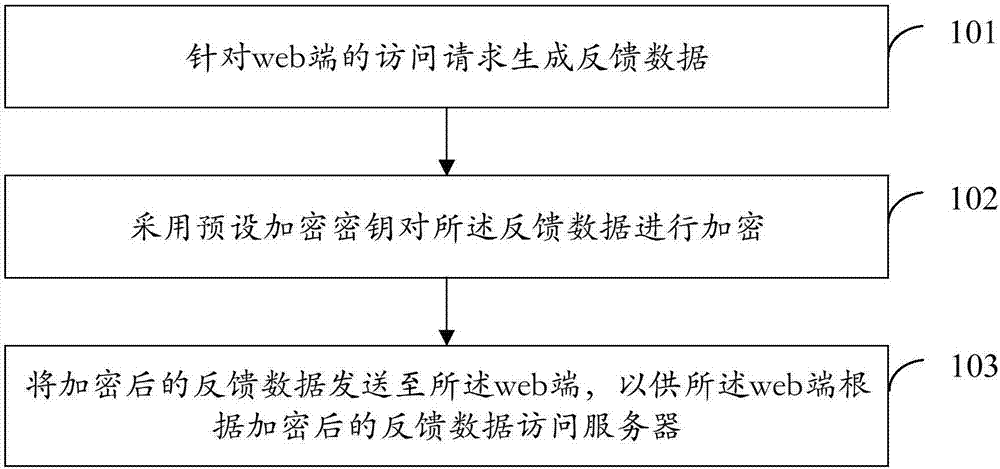
[0079] refer to figure 2 , which shows a flow chart of the steps of Embodiment 1 of a method for processing web-side access of the present application, which may specifically include the following steps:
[0080] Step 101, generating feedback data for the access request on the web side.
[0081] Wherein, the web terminal may be a browser terminal or other clients providing web page access, and may be specifically applied to mobile terminals (such as mobile phones) or other fixed terminals.
[0082] The embodiment of the present application can be implemented on a server corresponding to the web end, and the web end sends an access request to the server, and the access request can be a login request, or an access request triggered by clicking a web page or an access entry (such as a button).
[0083] Feedback data can be provided for the access request on the web side. For example, the feedback data for the login request is the login page that is redirected after successful l...
Embodiment 2
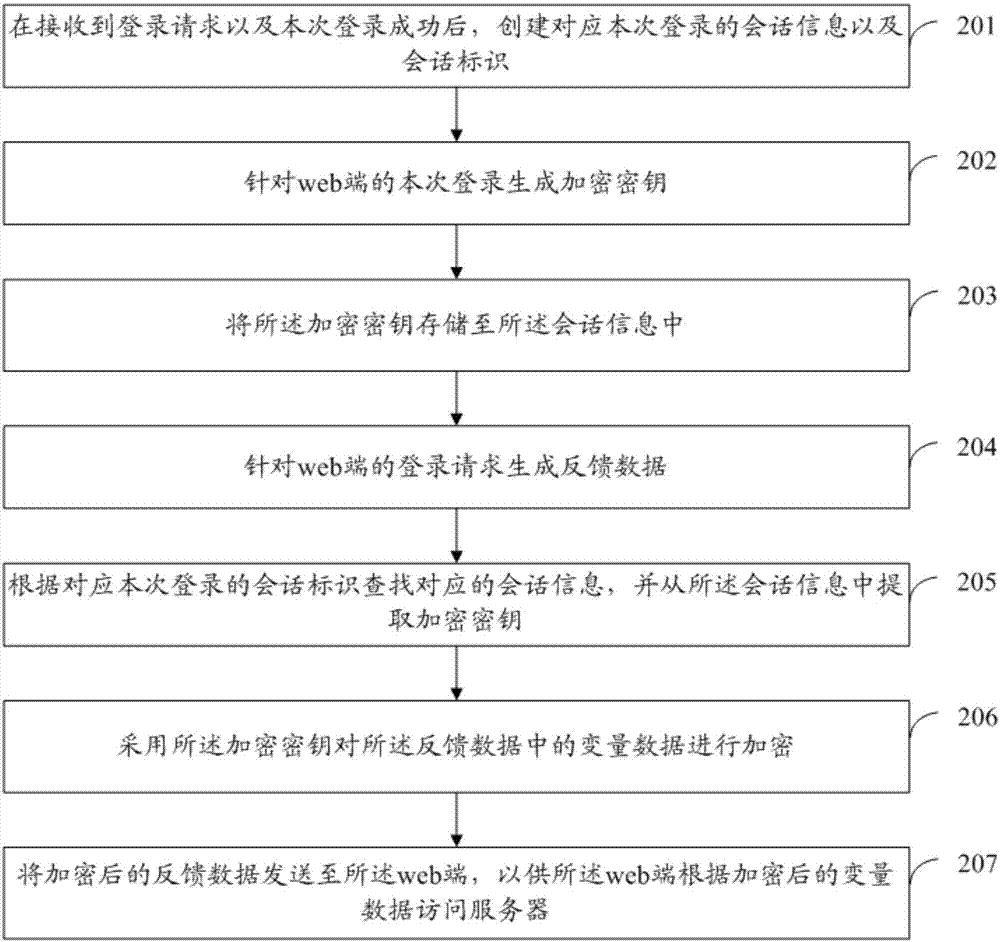
[0097] refer to image 3 , which shows a flow chart of the steps of Embodiment 2 of a method for processing web-side access of the present application. This embodiment can be specifically executed during the web-side login process, and can specifically include the following steps:
[0098] Step 201, after receiving a login request and the current login is successful, creating session information and a session identifier corresponding to the current login.
[0099] In this embodiment, the web terminal initiates a login request to the server, and successfully logs in after the server authenticates the web terminal, and the server can further create a corresponding session information session for this login, and the session information corresponds to a unique session identifier sessionid .
[0100] Step 202, generate an encryption key for this login on the web side.
[0101] After successful web login, you can further create an encryption key only for this login.
[0102] Th...
Embodiment 3
[0122] refer to Figure 4 , which shows a flow chart of the steps of Embodiment 3 of a processing method for web-side access of the present application. This embodiment can be specifically executed after logging in at the web-side, and can specifically include the following steps:
[0123] Step 301: Receive an access request from the web, the access request carries encrypted data that triggers this access, and the encrypted data is encrypted with a preset encryption key.
[0124] The encrypted data can be encrypted variable data. The web end accesses the server through the page provided by the server. Since the variable data has been encrypted with an encryption key, when the web end accesses based on the variable data, the access request carried It is also encrypted data, so that attackers cannot construct new access parameters by modifying system variable data, which improves web security and eliminates various security attacks including horizontal permission vulnerabilities...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com