Automatic penetration testing method and system
A penetration testing and automatic technology, applied in the information field, can solve problems such as inability to display vulnerability hazards, resentment, repair problems, etc., and achieve the effect of improving inspection efficiency and comprehensiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
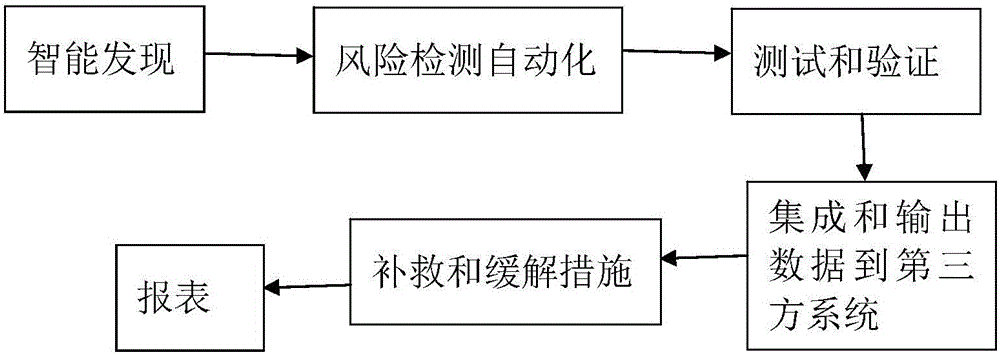
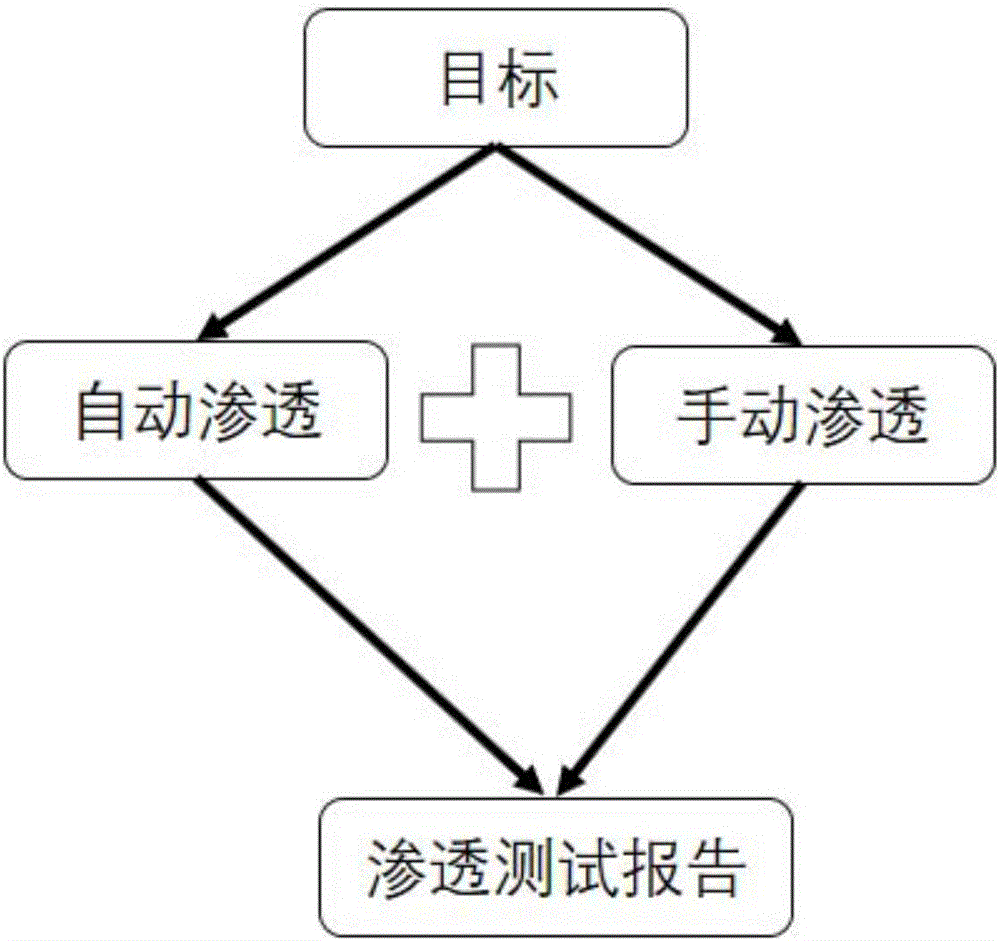
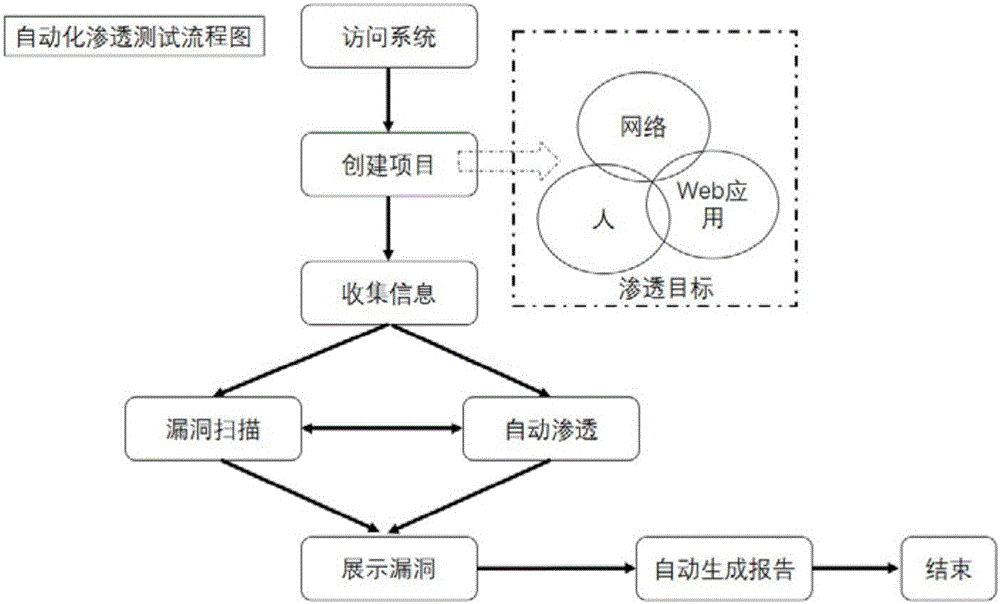
[0081] figure 1 It is a schematic flow chart of the present invention; figure 2 It is a schematic diagram of the permeation mode of the present invention. First of all, the system is developed with the scripting language Ruby. Ruby is a popular computer language and is widely used by security personnel. It has powerful functions and good compatibility. This time the system program is semi-open source (allowing users to review the source code of the program and use it with confidence), users can add their own test scripts, use standard interfaces, can interface with other security systems, and can verify the scanning results of other scanners (WVS, Appscan, Nessus, Nexpose, etc.).
[0082] In order to meet the needs of different groups of people (novice and expert), this system supports two methods of automatic infiltration and manual infiltration. The automatic infiltration can be one-click infiltration; the single-step operation of manual infiltration is more efficient. C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com