Security analysis framework based on network traffic meta data
A technology for security analysis and network traffic, applied in the field of security analysis framework based on network traffic metadata, can solve problems such as network attack detection point lag, lack of unknown threat perception capabilities, lack of intelligent backtracking and correlation analysis capabilities for security events, etc. Achieve the effect of improving accuracy and emergency response time and ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
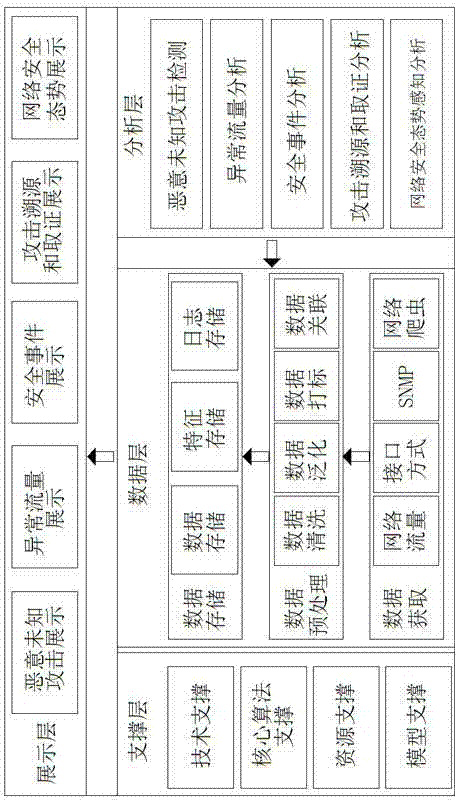
[0025] The security analysis framework consists of a data layer, an analysis layer, a support layer, and a display layer. Through the acquisition, preprocessing, and storage of metadata related to users, applications, locations, operations, and time in network traffic, key technologies, With the support of core algorithms, auxiliary resources and model libraries, the security analysis and display of network metadata can be realized.
[0026] The data layer includes three parts: data acquisition, data preprocessing and data storage, wherein data acquisition obtains data through network traffic, application program interface API, non-API, SNMP and other methods, from DNS, HTTP, FTP , SMTP protocol analyzes and extracts metadata related to networks, personnel, applications, sessions, locations, operations, and time; data preprocessing includes data cleaning, generalization, marking, and association to provide standardized guarantees for subsequent storage and analysis; Data stora...
Embodiment 2
[0040] Taking the detection of malicious and unknown attacks through HTTP traffic as an example to illustrate a security analysis framework based on network traffic metadata, including:
[0041] Data layer: includes three parts: data acquisition, data preprocessing and data storage; use network flow technology (NetFlow, sFlow) to obtain metadata of HTTP GET, POST and server return type, respectively:
[0042] a) HTTP GET metadata: including timestamp, domain name, URL (remove domain name), Referer, user IP, user port, server IP, server port, User-Agent;
[0043] b) HTTP POST metadata: including timestamp, domain name, URL (remove domain name), sending type, sending bytes, Referer, user IP, user port, server IP, server port, User-Agent;
[0044] c) Server return type: including timestamp, HTTP status code, file type, file size, server IP, server port, user IP, user port;
[0045] For the massive HTTP traffic metadata obtained by analysis, it is regularly imported to the HDFS f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com