Threat intelligence analysis system for attack tracing
An analysis system and intelligence technology, applied in the field of threat intelligence analysis system, can solve the problems of insufficient threat intelligence sources, high rate of missed or false positives, and lack of uniform specifications, etc., to achieve wide source methods, less resource use, and high operating efficiency high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific embodiments.
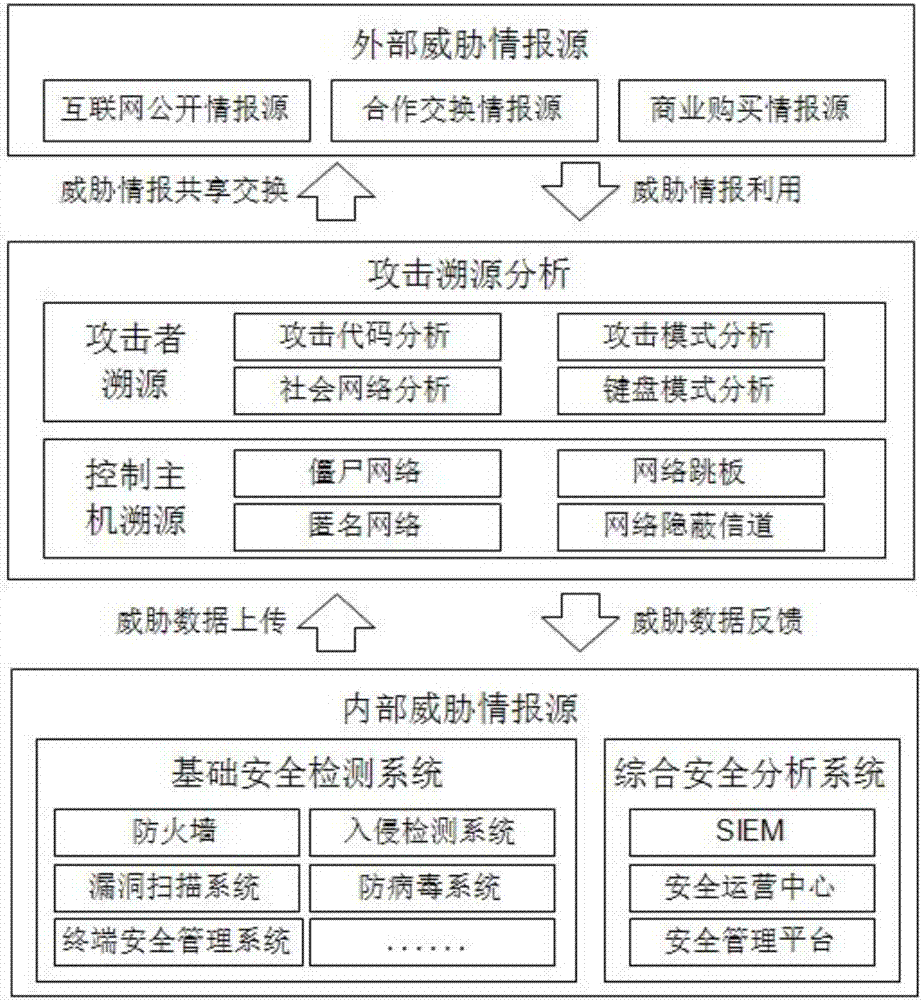
[0026] see figure 1 , the present invention includes an internal threat intelligence source module, an external threat intelligence source module and an attack traceability analysis module.
[0027] Among them, the internal threat intelligence source module mainly refers to the threat intelligence formed by the organization's own security monitoring protection analysis system, including data from the security detection module and the security analysis module. Security detection modules, such as firewalls, intrusion detection systems, vulnerability scanning systems, antivirus systems, and terminal security management systems. Enterprise internal security analysis modules, such as SIME, security operation center and security management platform;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com