Patents
Literature
189 results about "Local agent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Local agent. An agent who works on behalf of the insurance companies in a small territory in a sales and service capacity. The agent is an independent contractor who earns commission on sales.
System and Method for Distributed Denial of Service Identification and Prevention
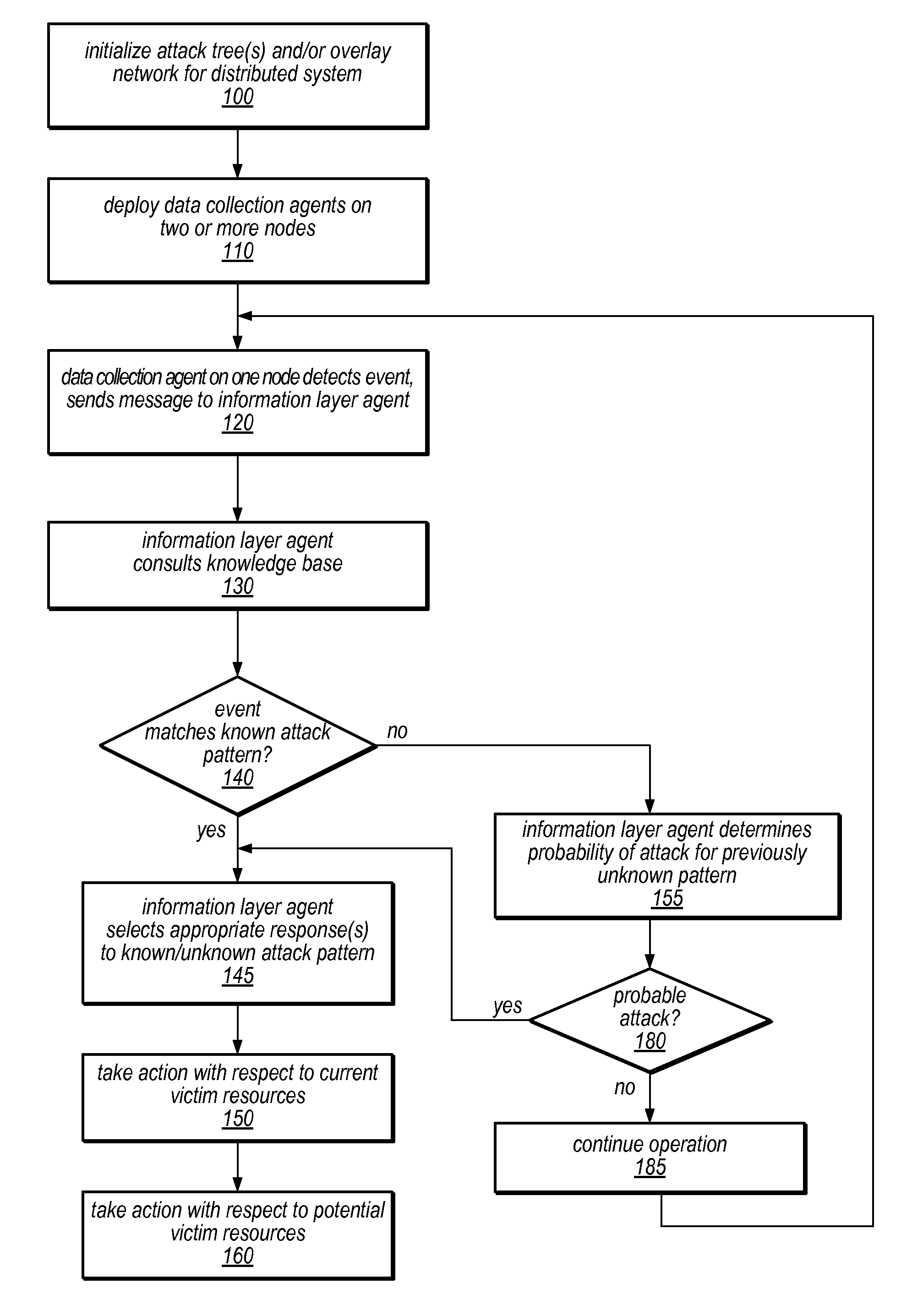
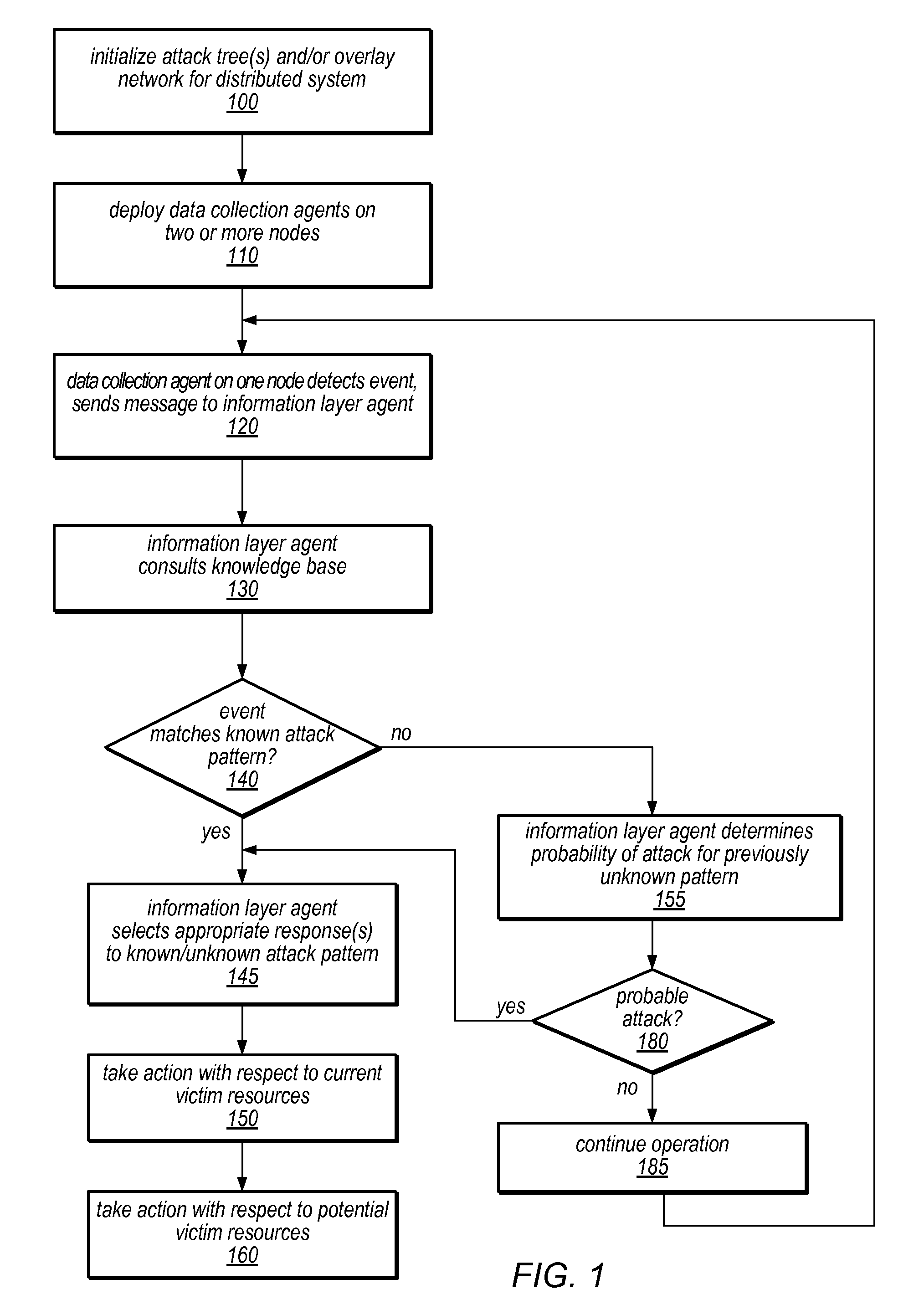
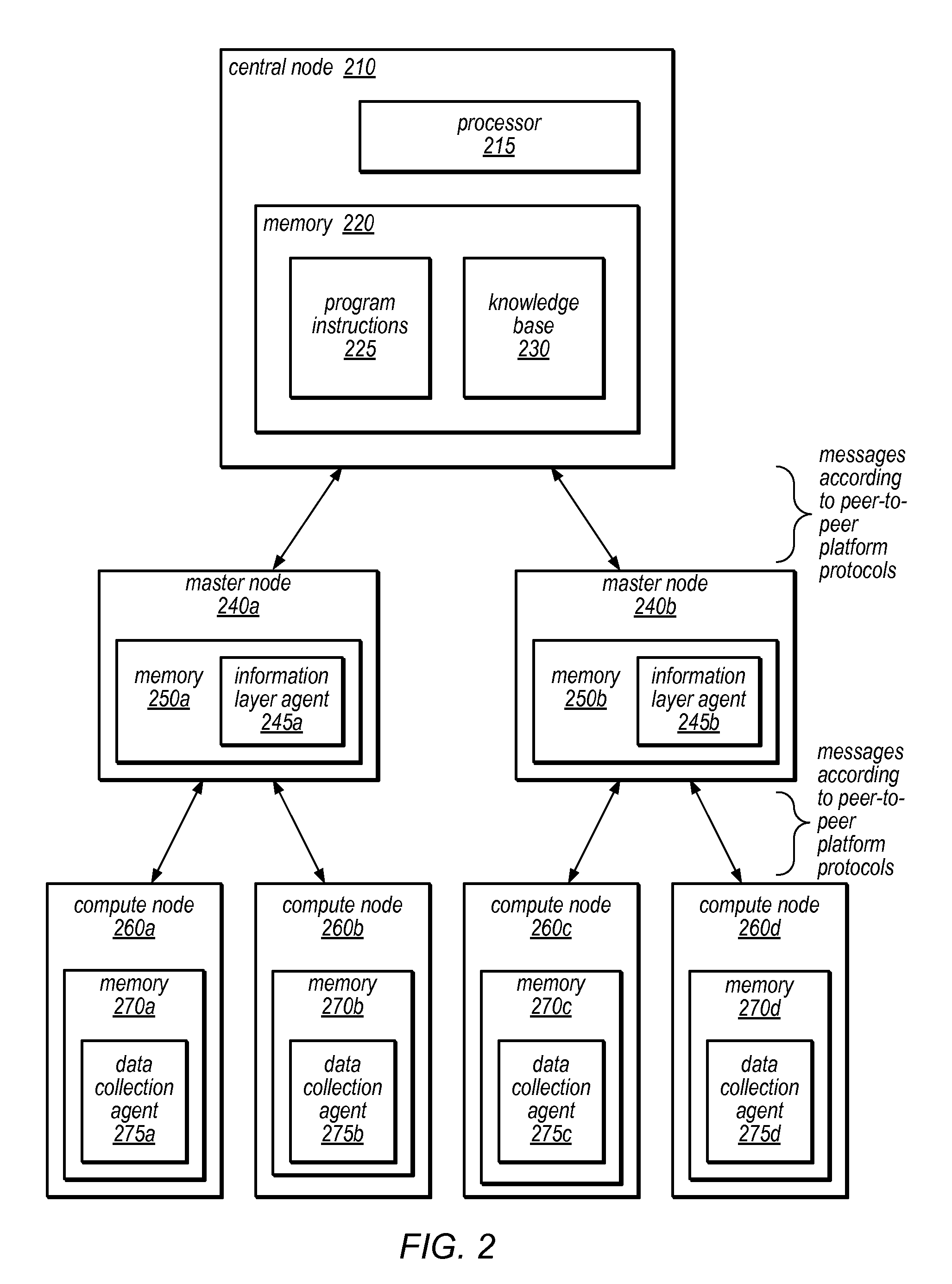
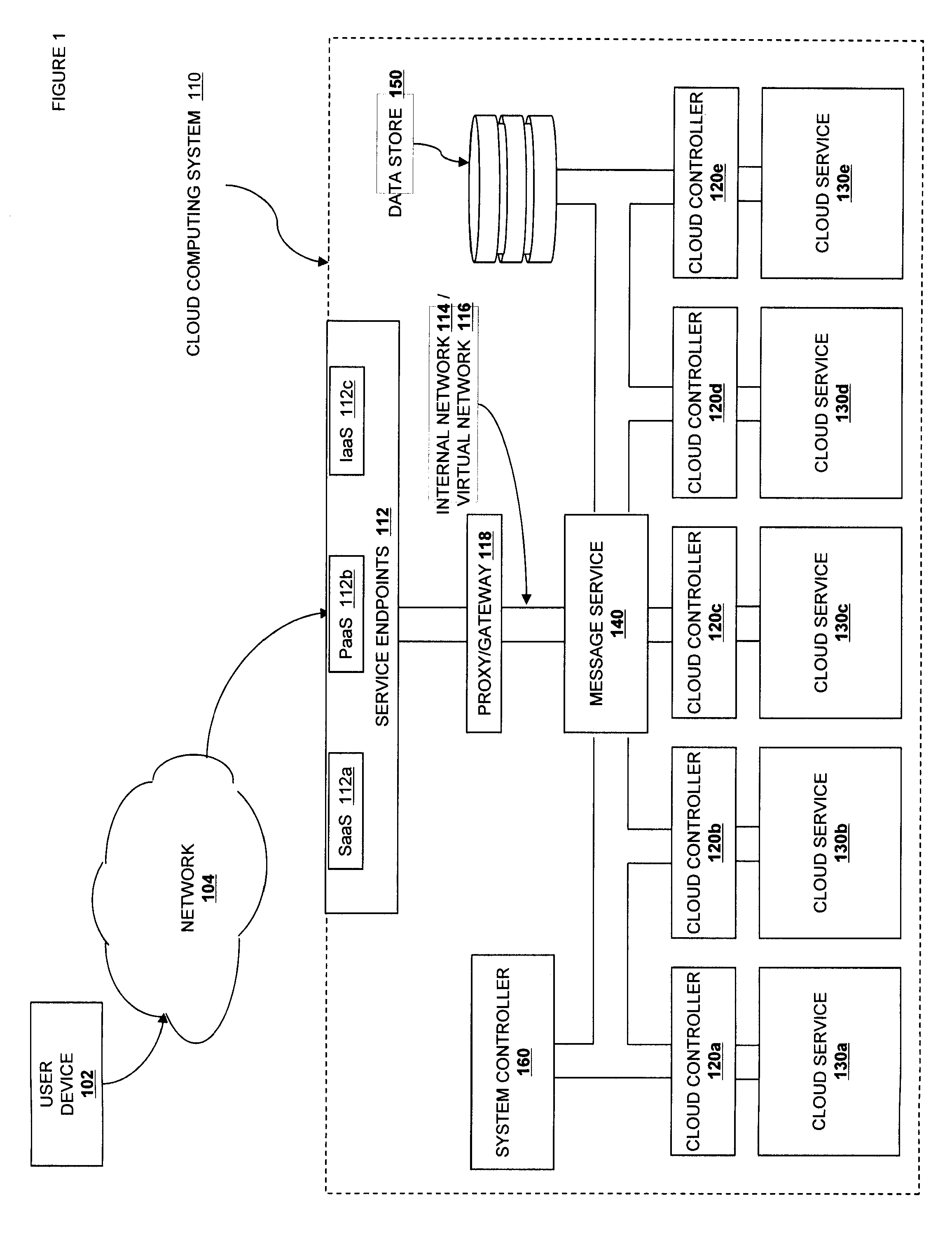
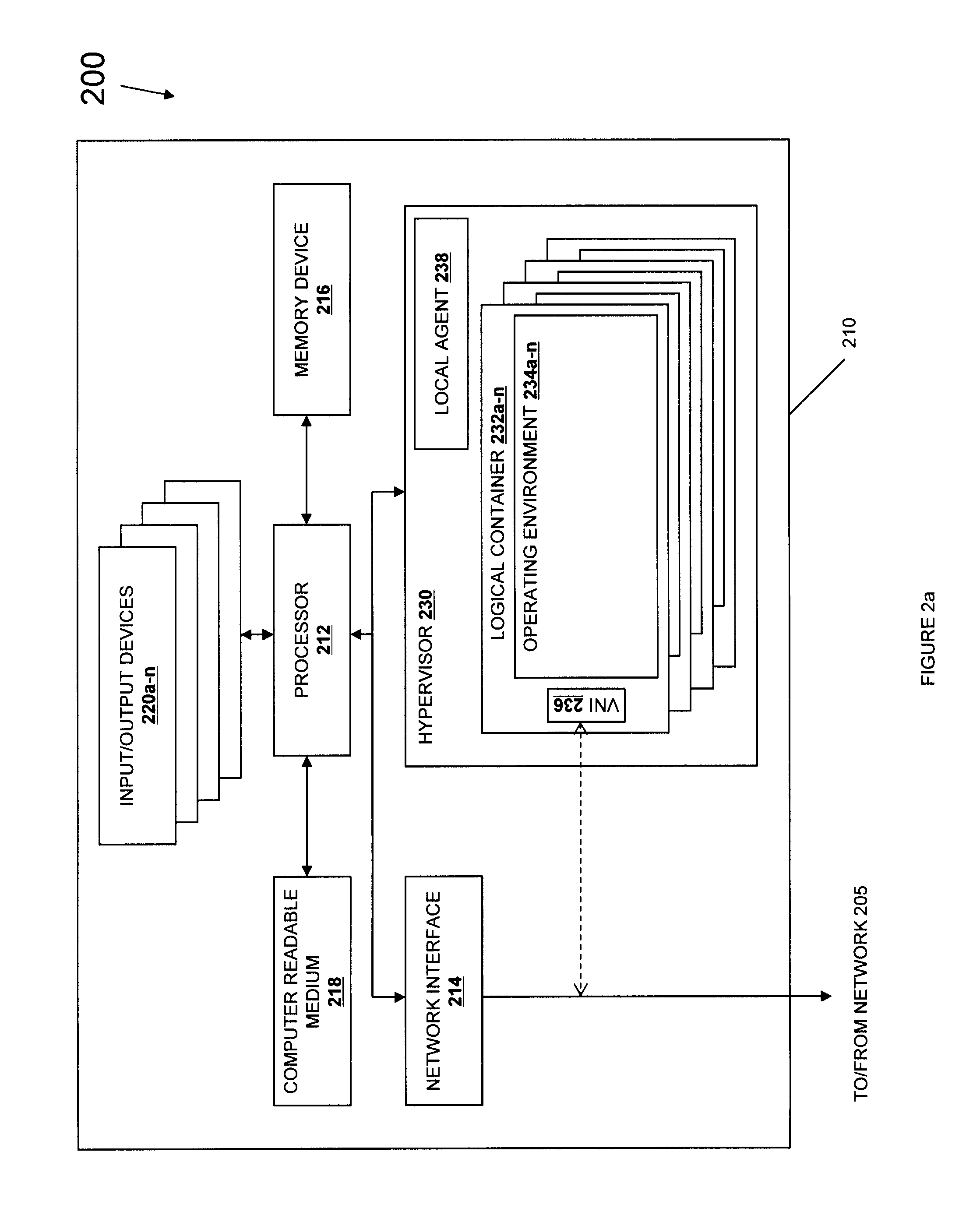
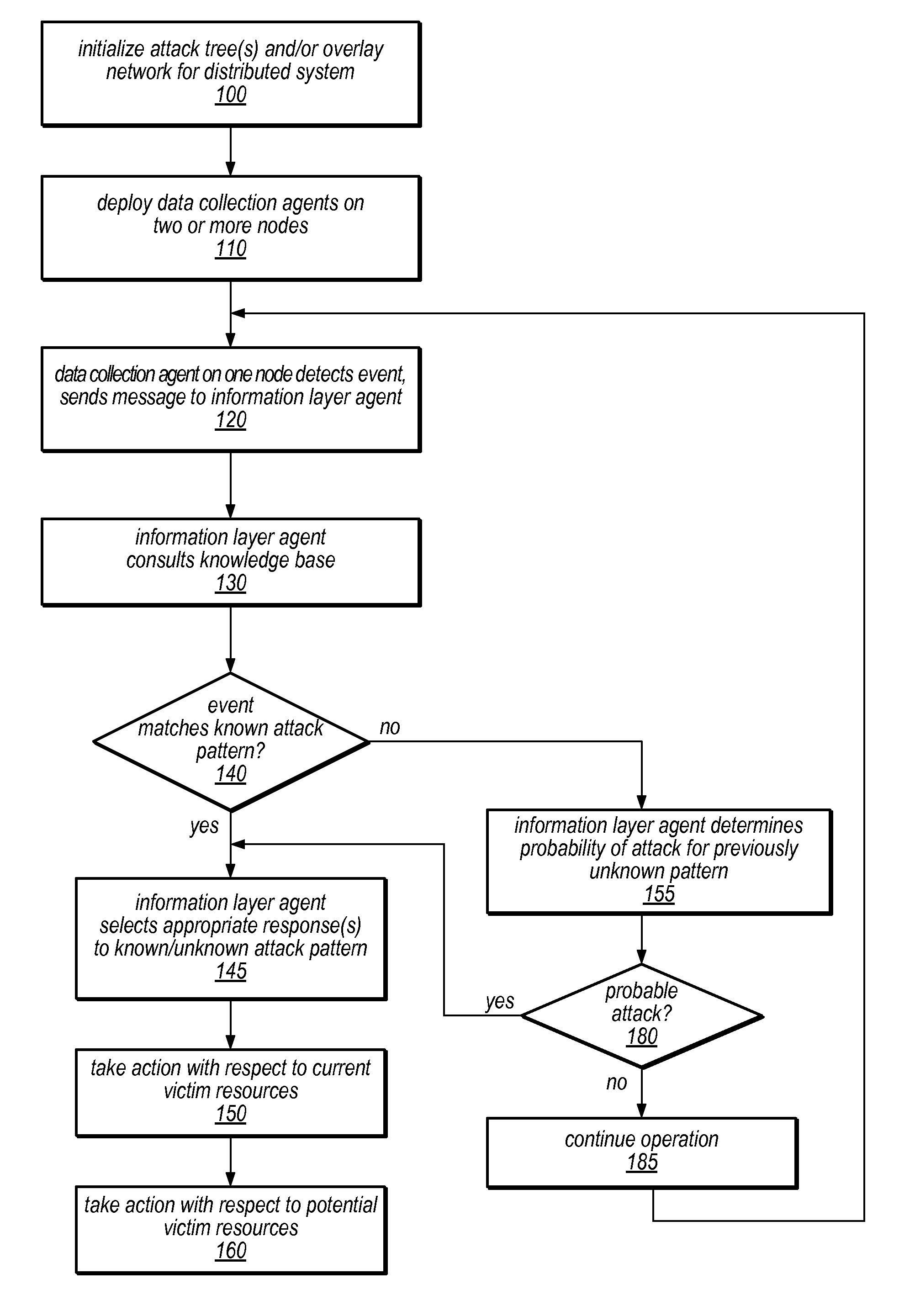
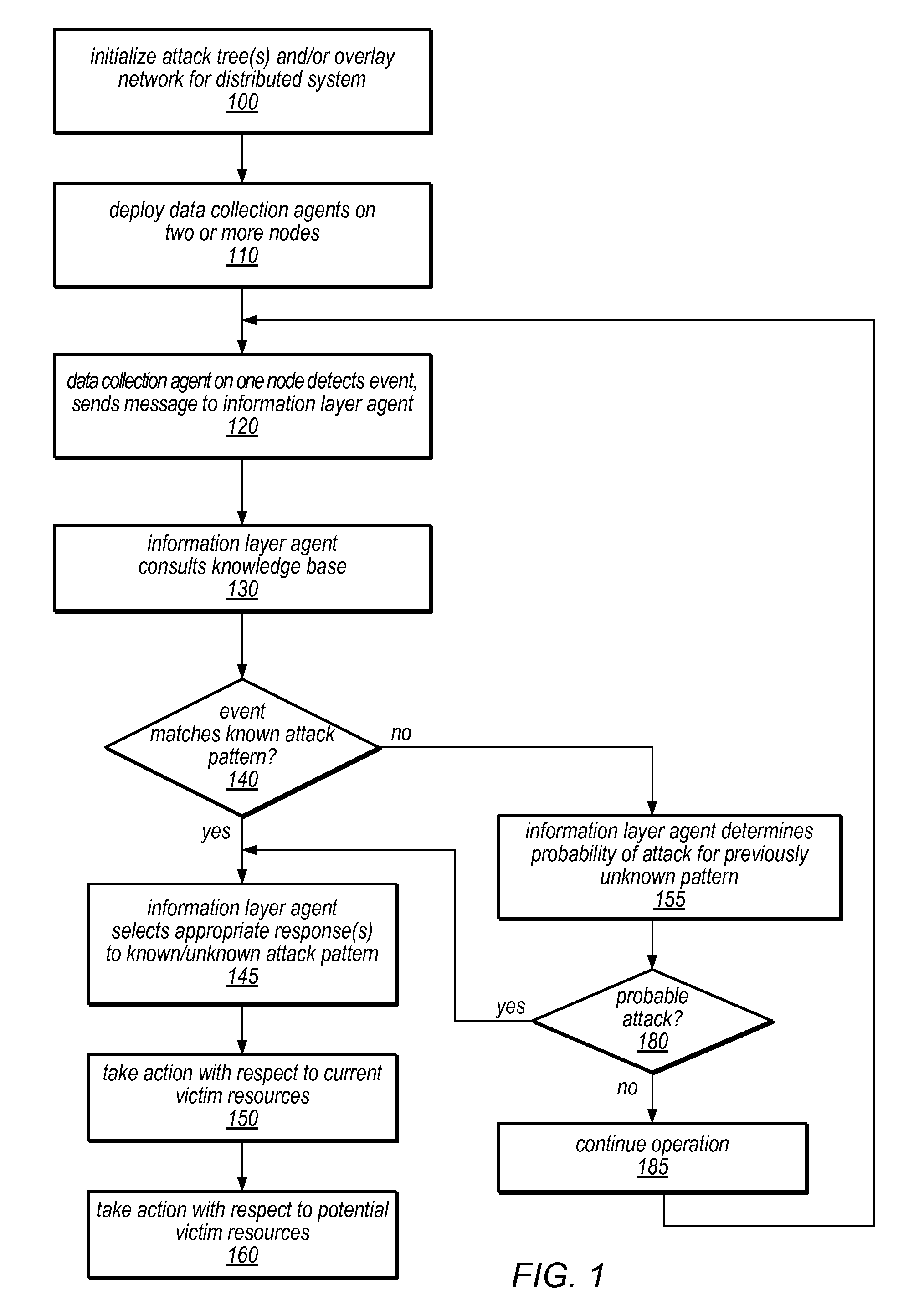
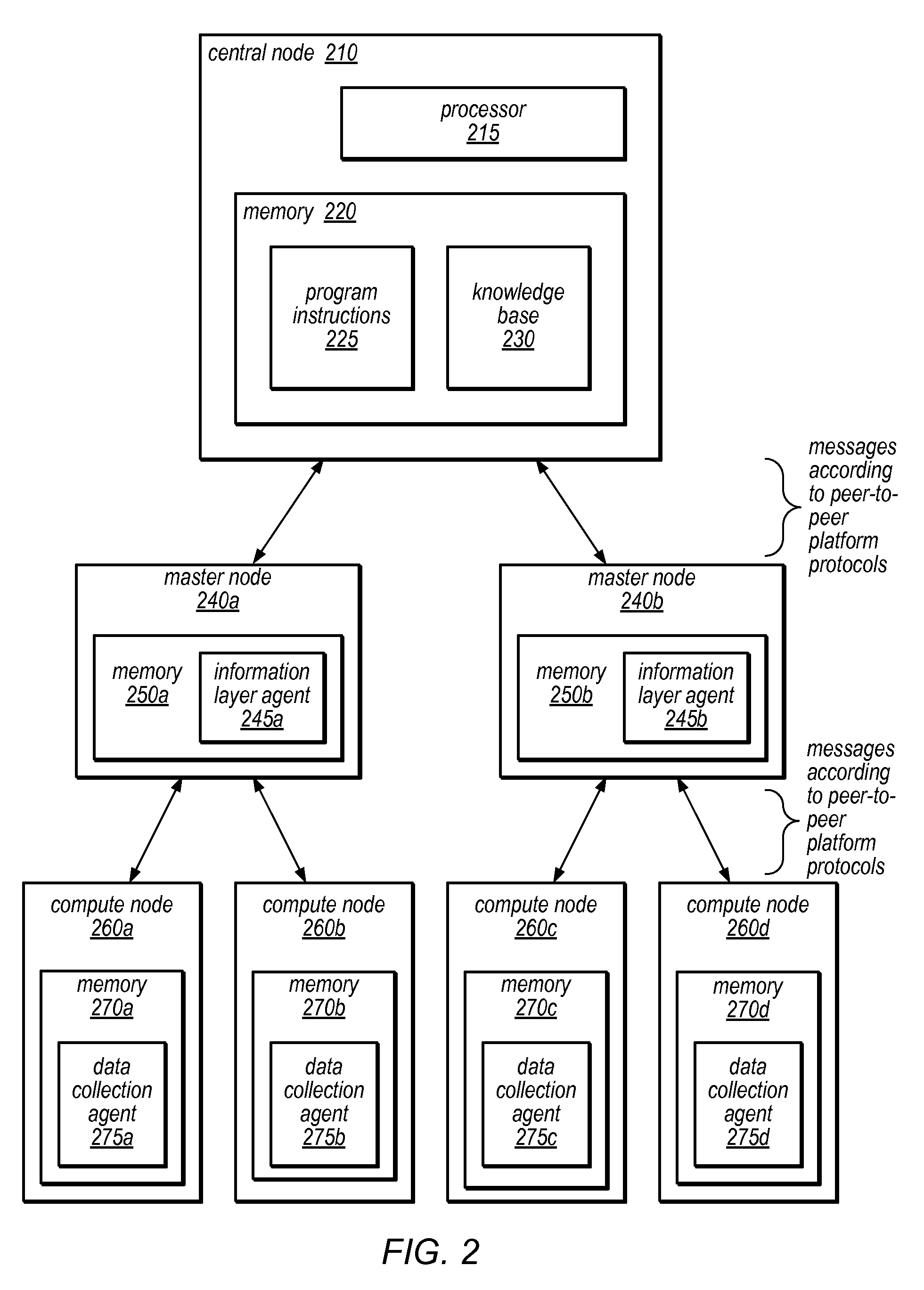
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
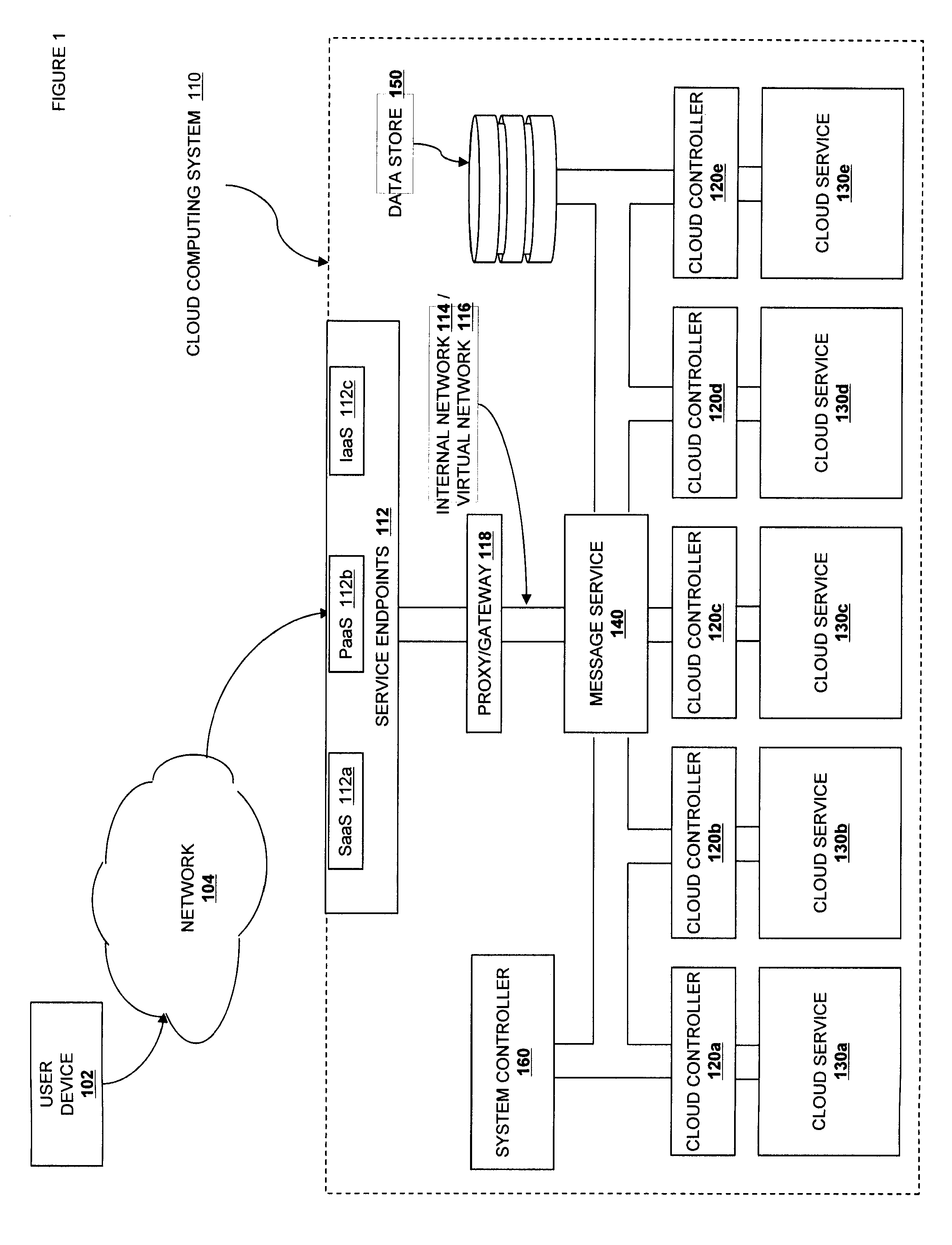
Market-Based Virtual Machine Allocation
InactiveUS20130304903A1Program control using stored programsDigital computer detailsMarket placeMarket based
A cloud computing system management system including a plurality of computing devices configured to host virtual machine instances, each computing device in the plurality of computing devices including a local agent that continuously evaluates the observed load relative to a utility maximization function. If observed load is higher than a calculated optimal level, individual loading processes are offered for “sale” via a market scheduler. If observed load is lower than a calculated optimal level, then available capacity is offered as a bid via the market scheduler. The market scheduler matches bids with available processes and coordinates the transfer of load from the selling device to the buying device. The offered prices and utility maximization functions can be employed to optimize the performance of the cloud system as a whole.
Owner:RACKSPACE US
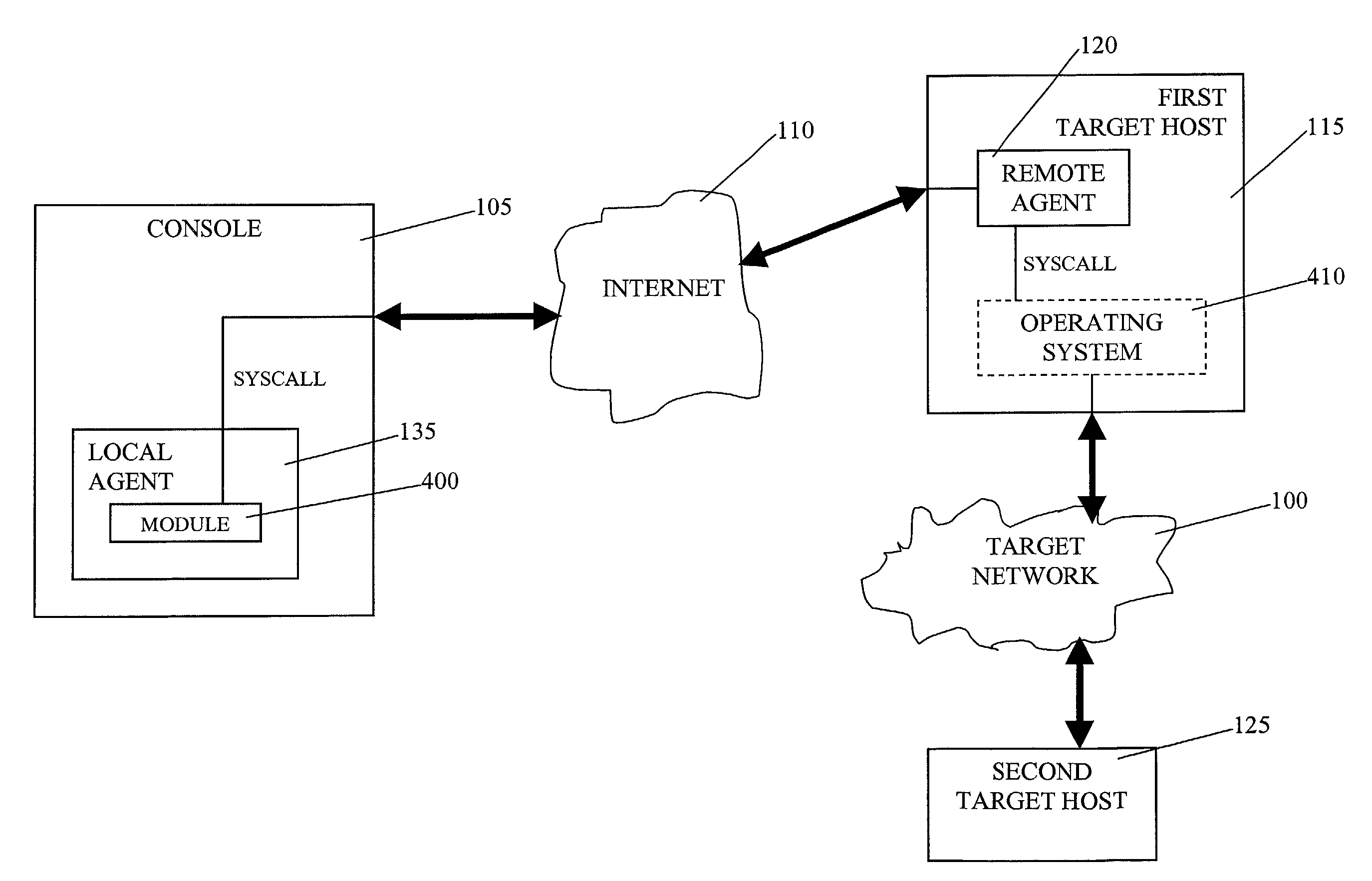
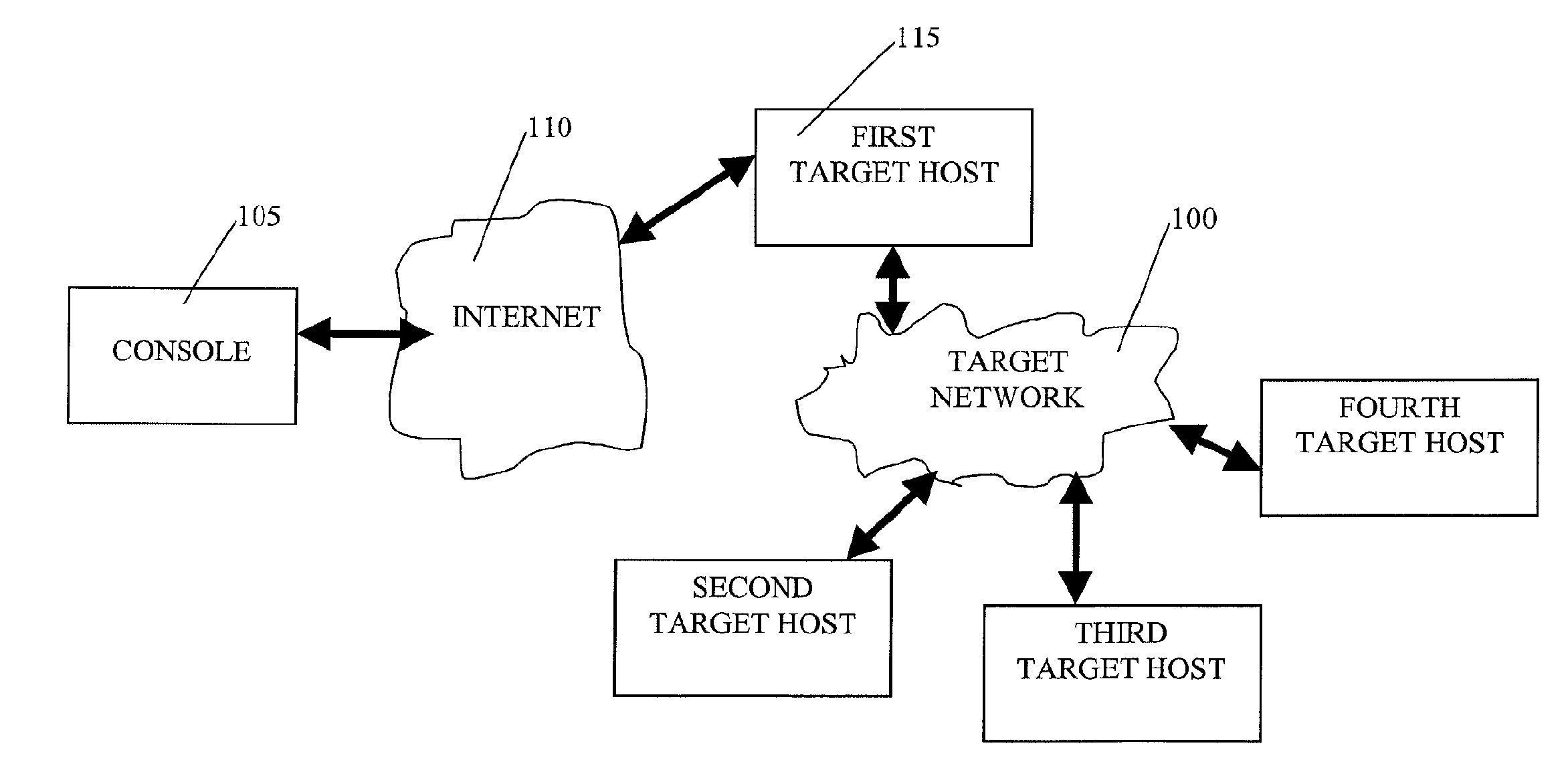
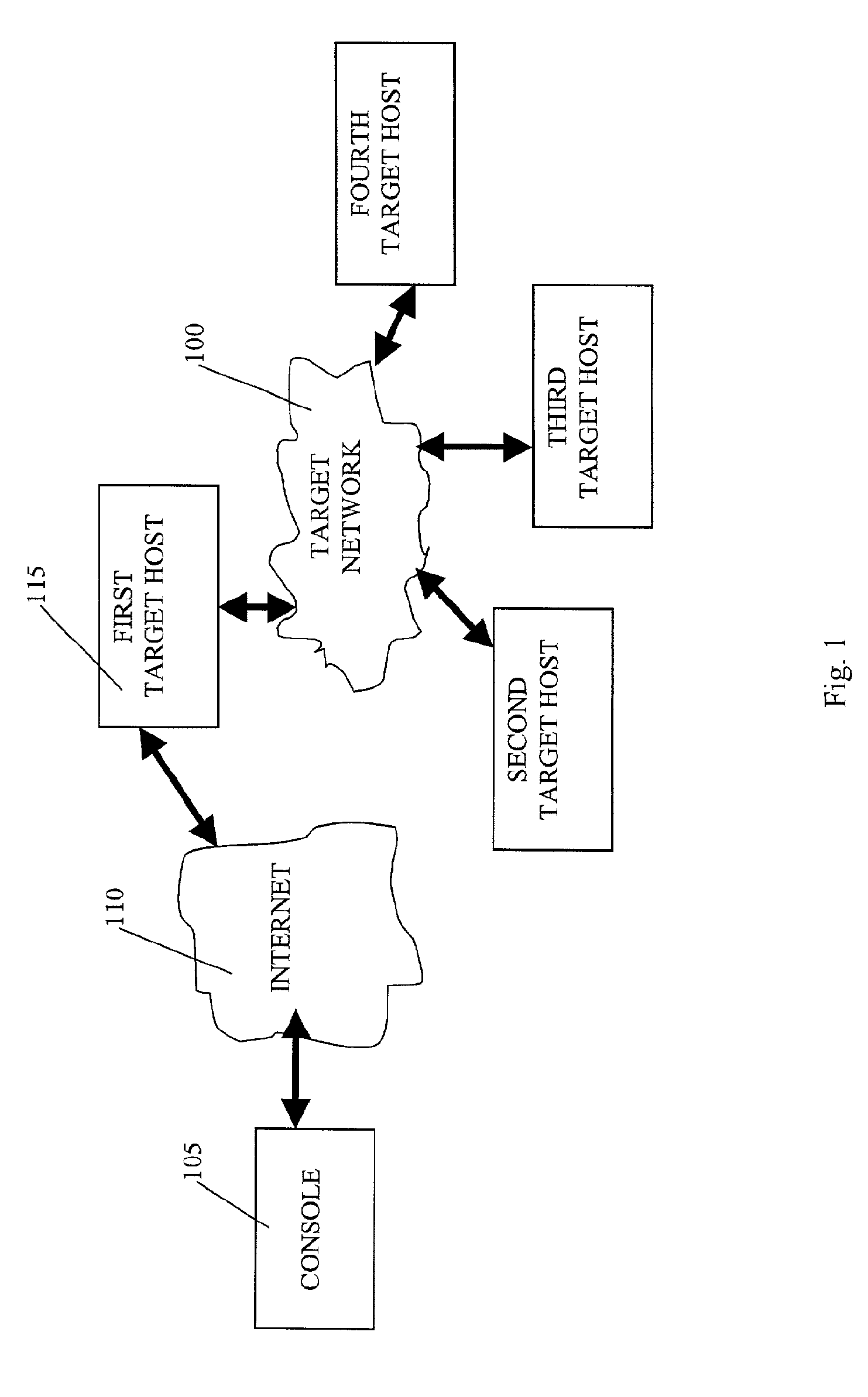
Automated computer system security compromise
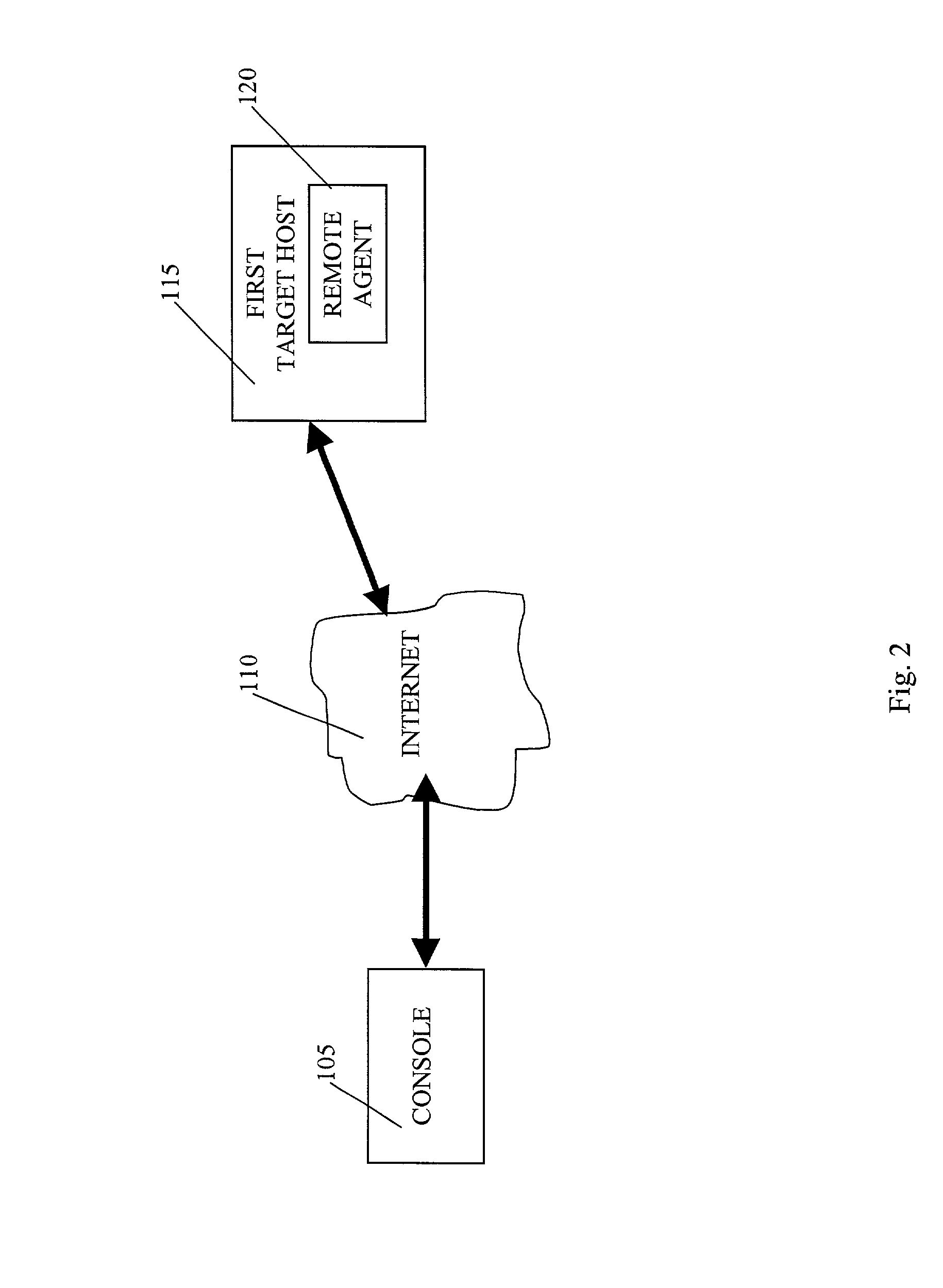
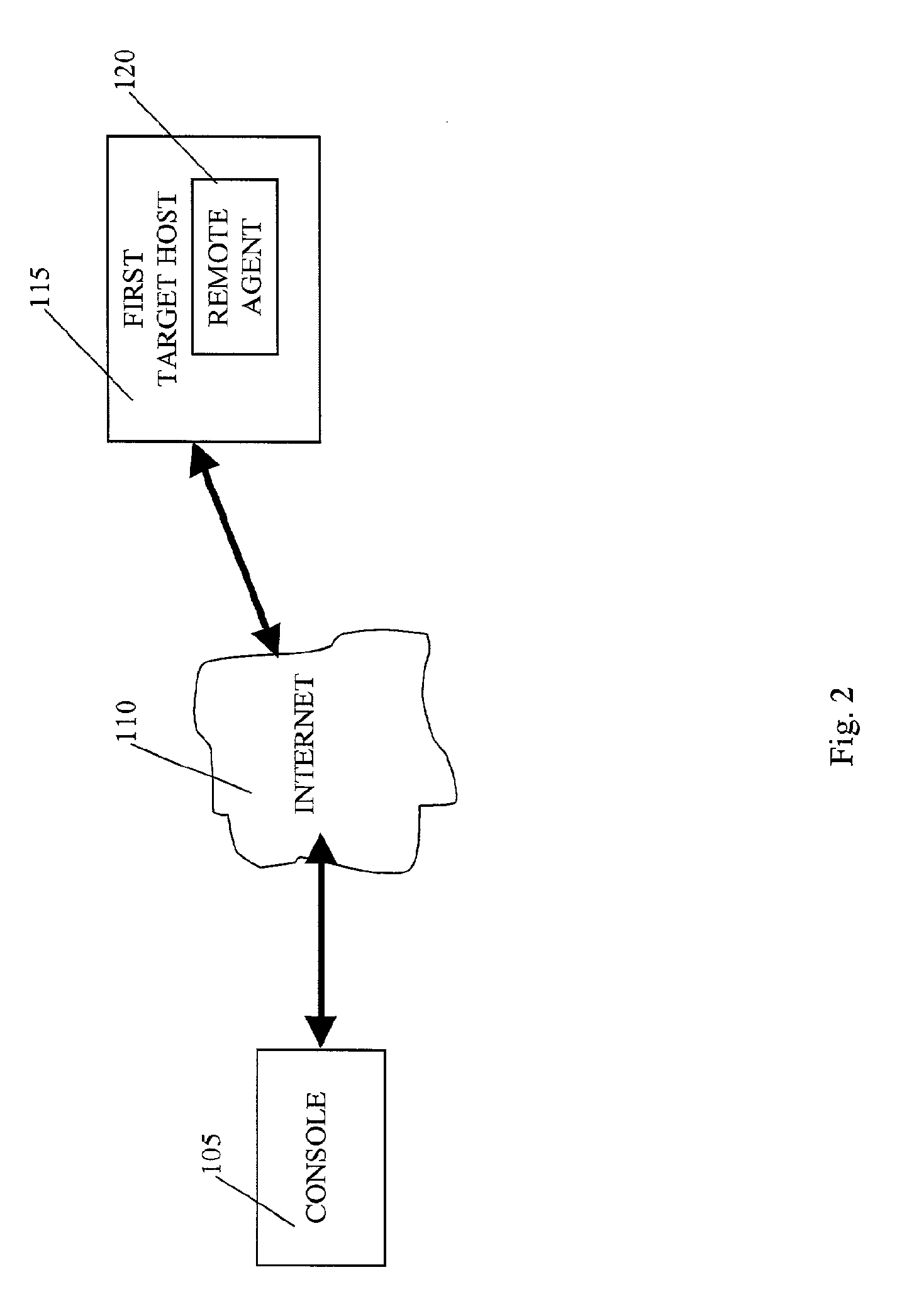
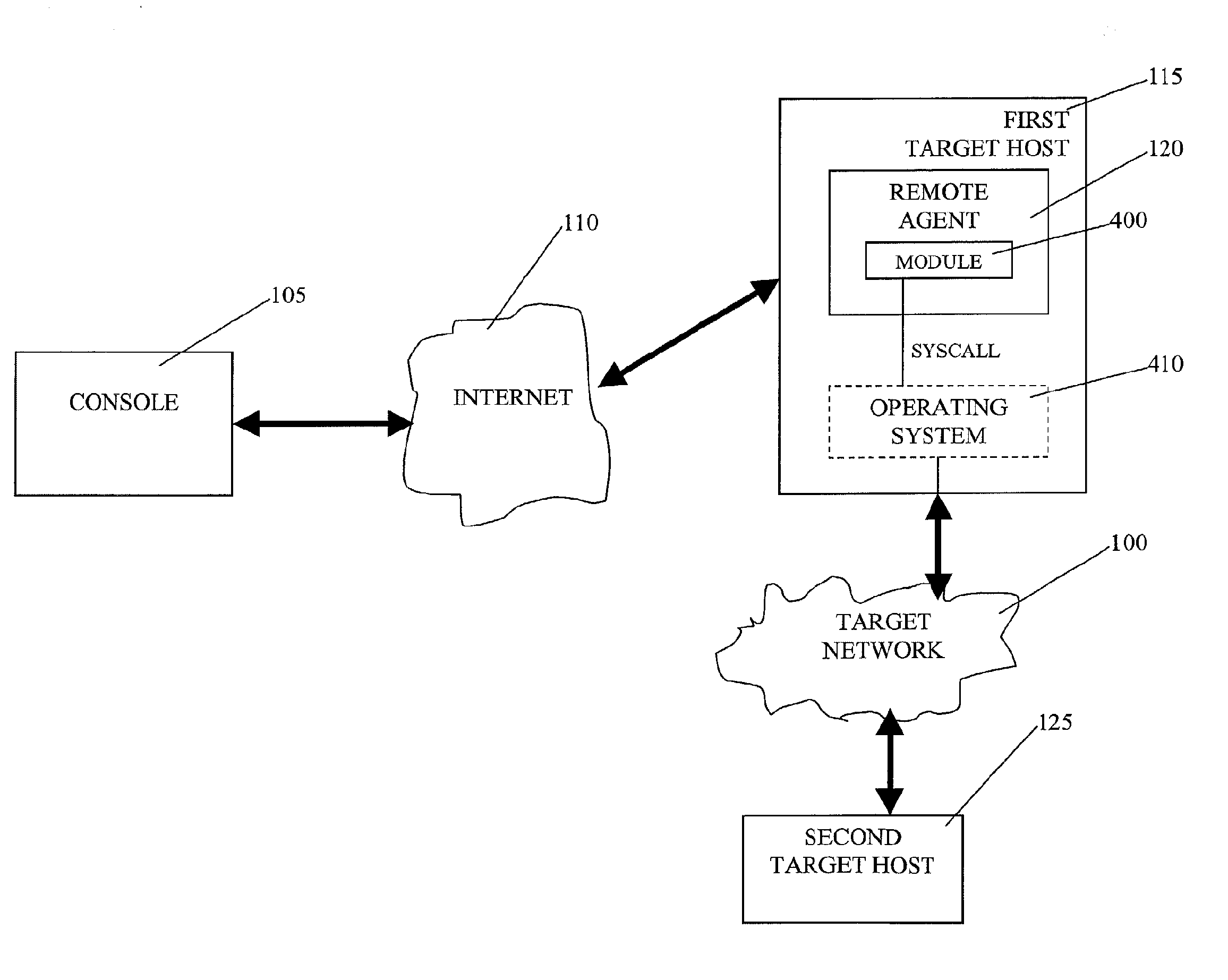
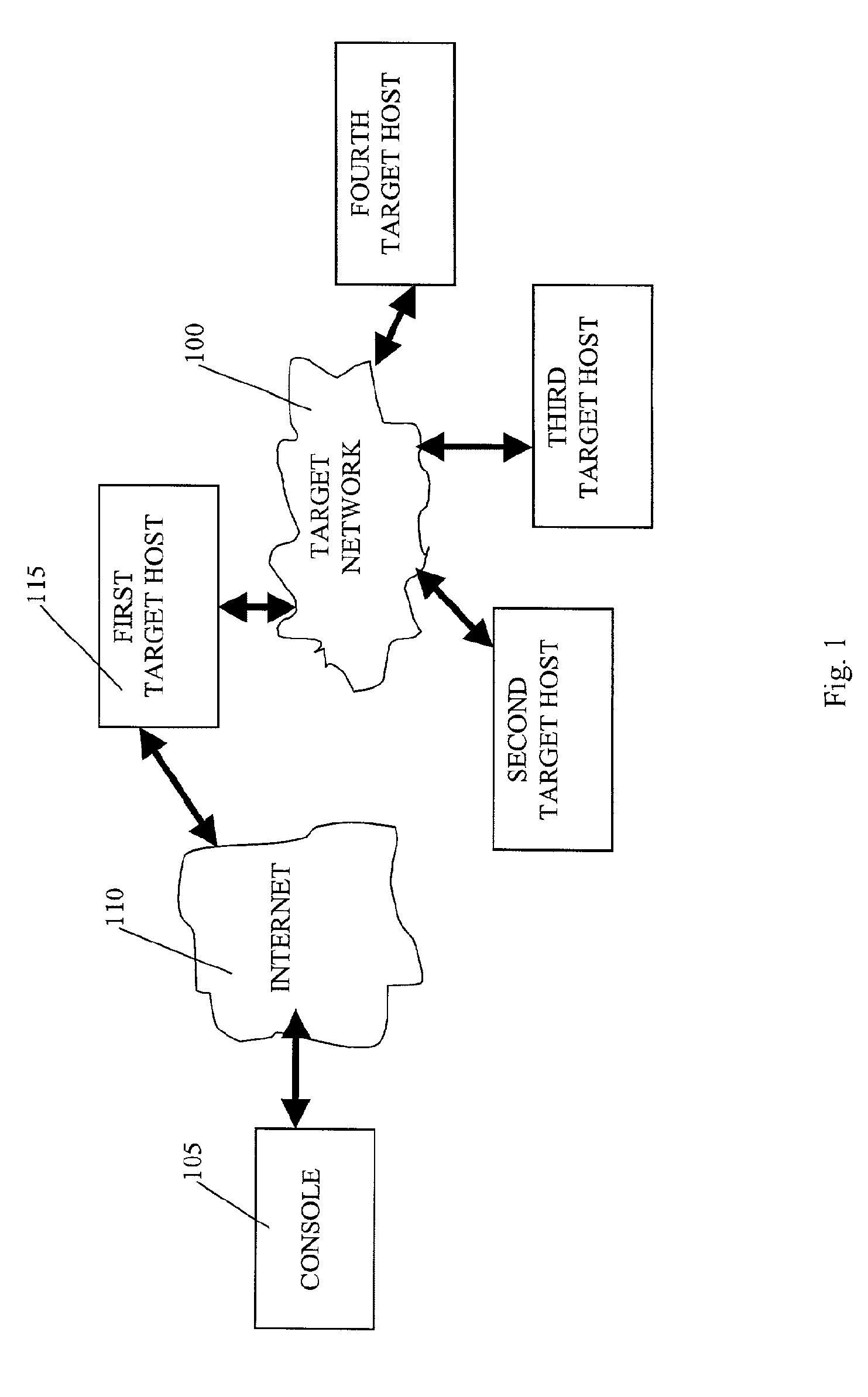
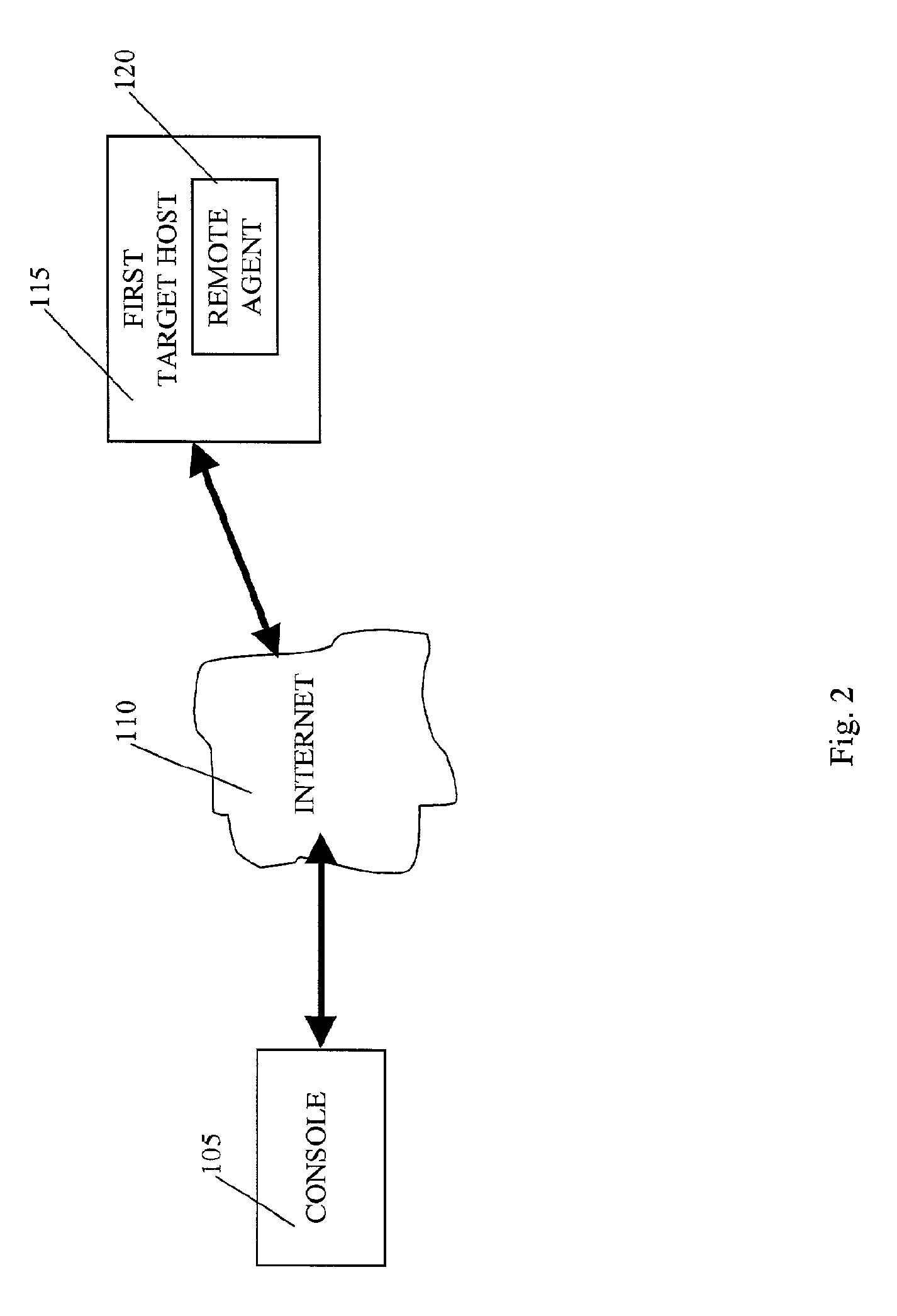
A system is provided for performing penetration testing of a target computer network by installing a remote agent in the target computer network. The system includes a local agent provided in a computer console and configured to receive and execute commands. A user interface is provided in the console and configured to send commands to and receive information from the local agent, process the information, and present the processed information. A database is configured to store the information received from the local agent. A network interface is connected to the local agent and configured to communicate with the remote agent installed in the target computer network via a network. Security vulnerability exploitation modules are provided for execution by the local agent and / or the remote agent.
Owner:FORTRA LLC
Delivering personalized content data via local network
ActiveUS7707271B2Multiplex communicationData switching by path configurationPersonalizationThe Internet
Personalized content is provided over a communications network such as the Internet. Providing personalized content includes both generating content which depends on the recipient of that content and delivering that content in a manner that depends on the recipient. Although methods of providing personalized content are known, none of those methods provide a mechanism for deciding when and how to personalize content. By enabling a content provided to send policy data to local caches and having a local agent computer arrange for content files to be delivered in accordance with those policy files, such a mechanism is provided.
Owner:BRITISH TELECOMM PLC
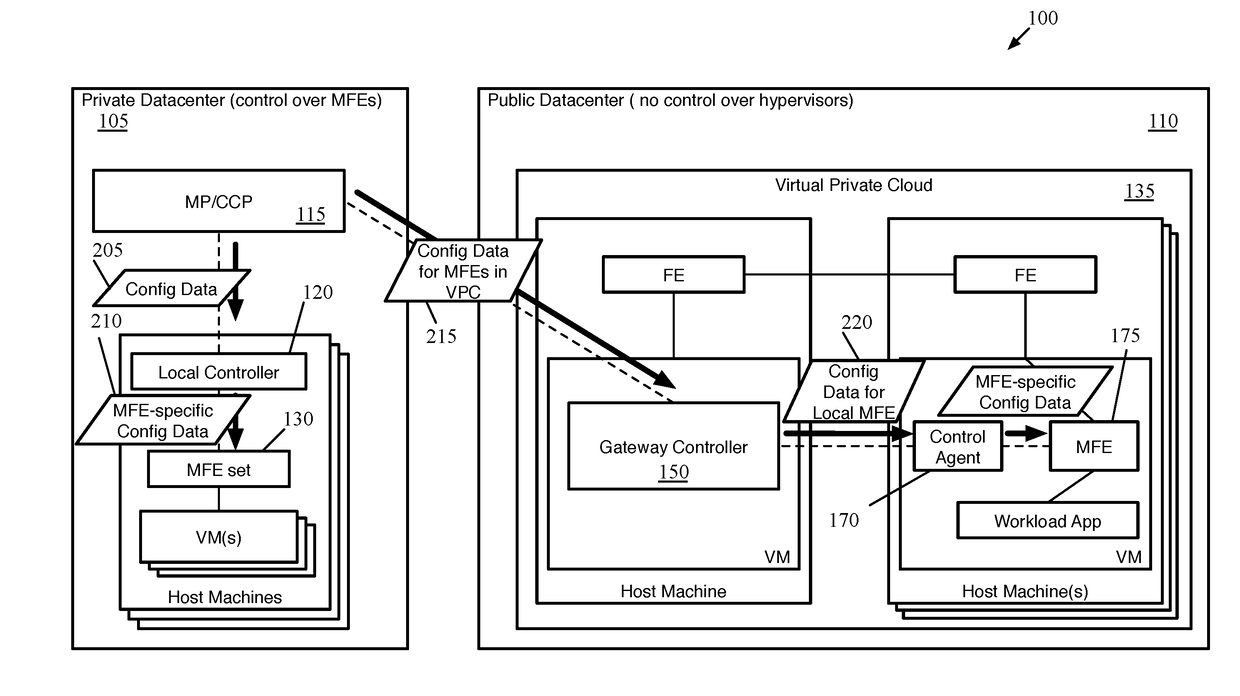
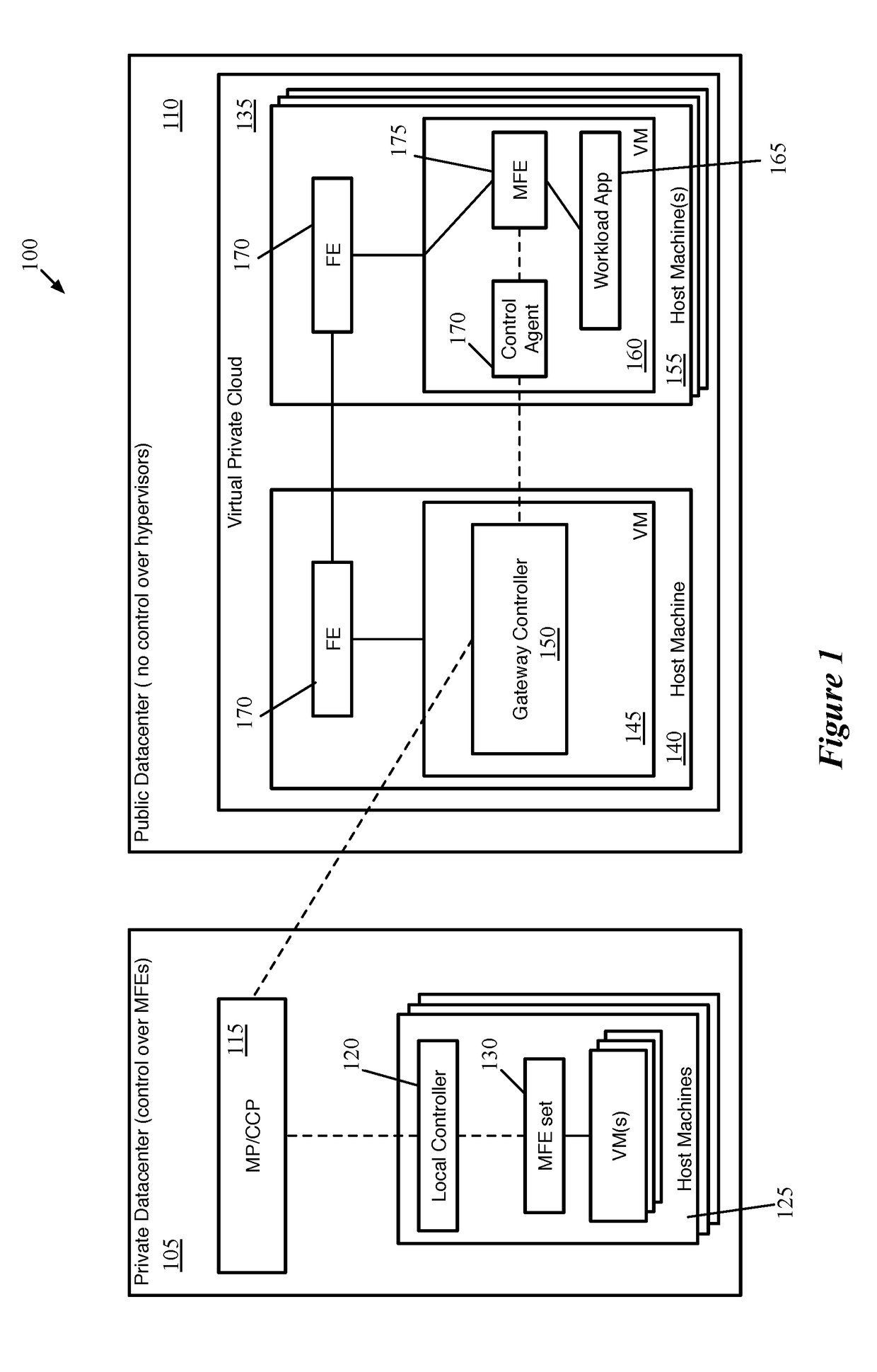
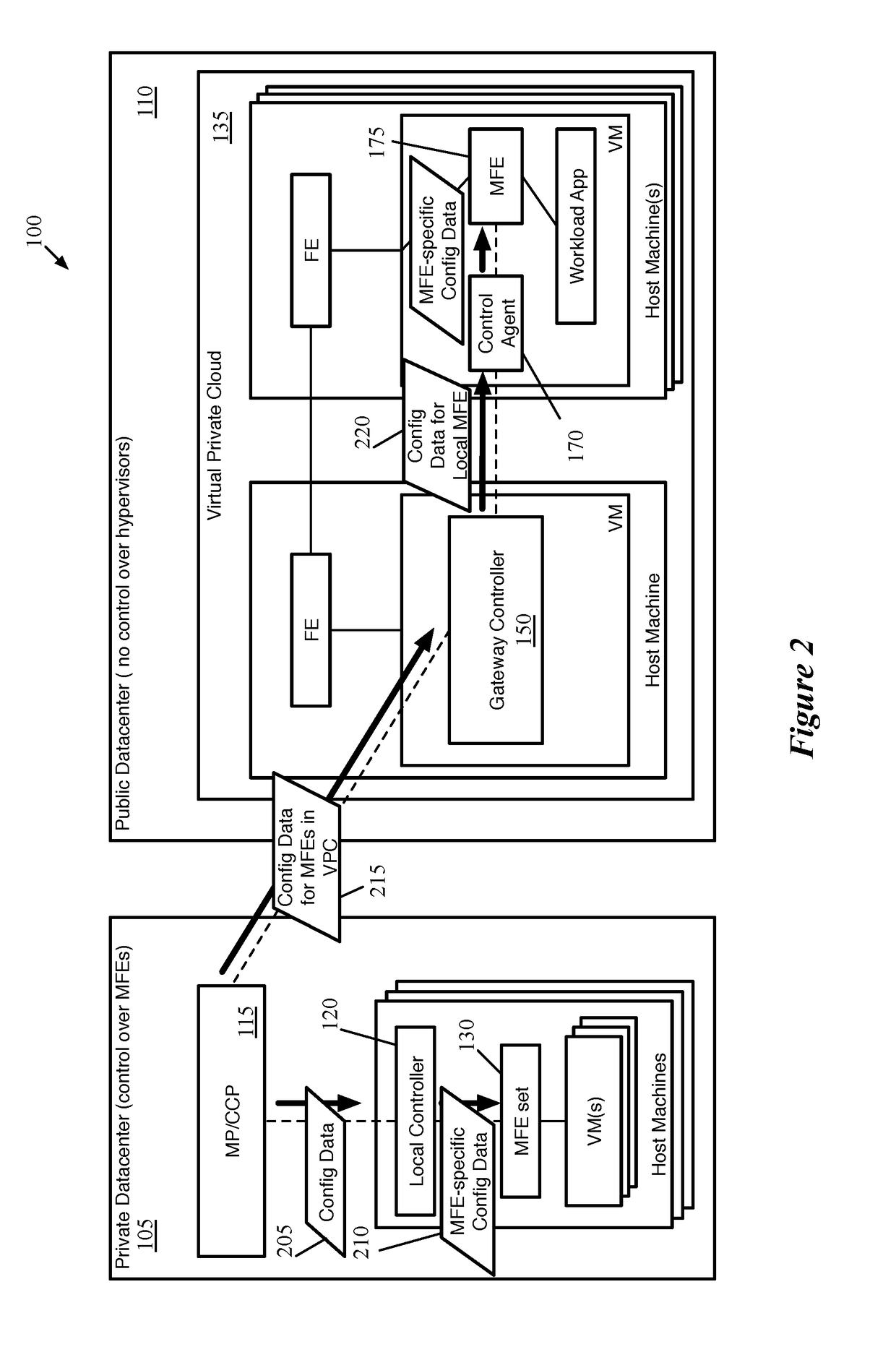
Extension of network control system into public cloud
ActiveUS20180062917A1Digital computer detailsReliability/availability analysisData setControl system
Some embodiments provide a method for a first network controller that manages a logical network implemented in a datacenter including forwarding elements to which the first network controller does not have access. The method identifies a first data compute node (DCN) in the datacenter configured to execute a second network controller. The method distributes configuration data defining the logical network to the first DCN. The second network controller distributes sets of the configuration data to local agents executing on additional DCNs in the datacenter that send and receive messages through the logical network. Both managed forwarding elements and the local agents execute on each of the additional DCNs. Each local agent on a particular DCN is for receiving a set of configuration data from the second network controller and configuring the managed forwarding element on the particular DCN to implement the logical network according to the set of configuration data.
Owner:NICIRA
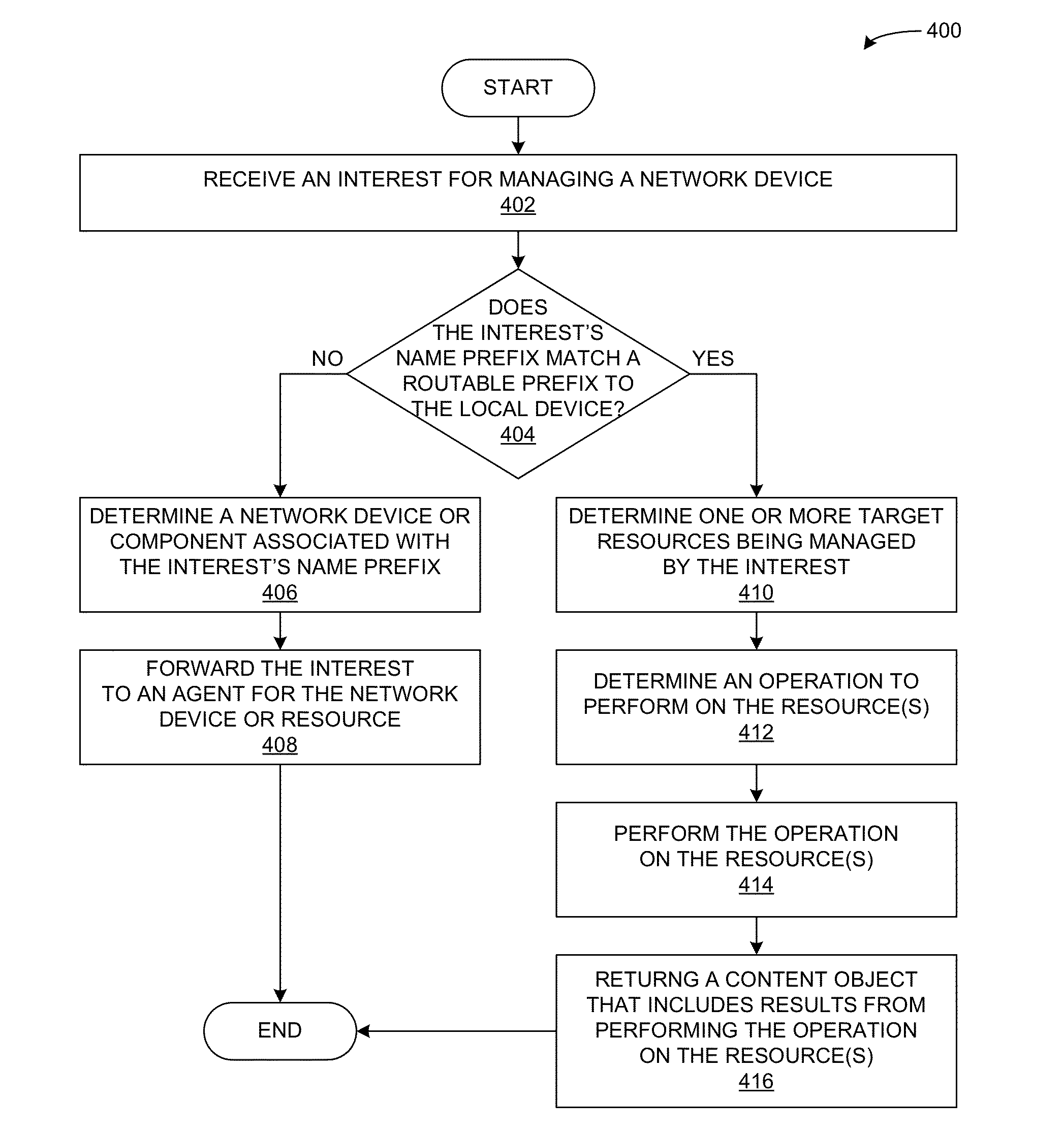
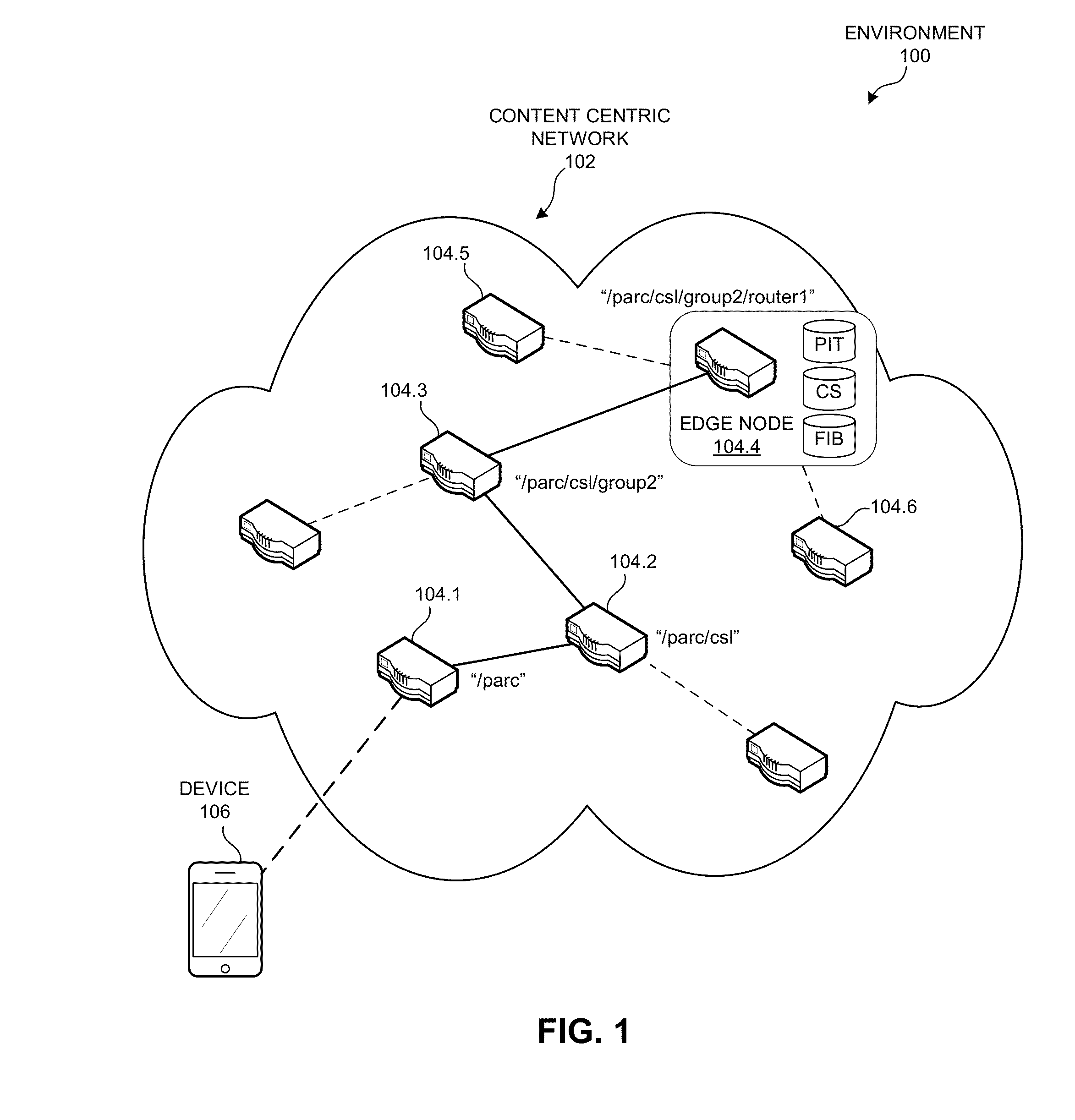
System and method for managing devices over a content centric network
ActiveUS20150381546A1Digital computer detailsData switching networksContent centricLongest prefix match
A device can process commands from a remote device that manages the local device over a content centric network. During operation, the device can receive an Interest for managing a device resource, such that the Interest's name includes a name or a name prefix associated with the device resource, and includes a command for managing the resource. If the device determines that the name prefix corresponds to the local device, the device analyzes the Interest's command to determine a device resource and performs the resource-managing operation on the device resource. If the name prefix does not correspond to the local device, the device performs a longest-prefix-matching lookup using the Interest's name prefix to determine a destination for the Interest. If the Interest's destination corresponds to a component of the local device, the device forwards the Interest to the component or a local agent for the component.
Owner:CISCO TECH INC
Automated computer system security compromise
InactiveUS20070204347A1Memory loss protectionError detection/correctionInformation processingInformation networks
Owner:FORTRA LLC
Automated computer system security compromise
InactiveUS7757293B2Memory loss protectionError detection/correctionComputer moduleComputerized system
A system is provided for performing penetration testing of a target computer network by installing a remote agent in the target computer network. The system includes a local agent provided in a computer console and configured to receive and execute commands. A user interface is provided in the console and configured to send commands to and receive information from the local agent, process the information, and present the processed information. A database is configured to store the information received from the local agent. A network interface is connected to the local agent and configured to communicate with the remote agent installed in the target computer network via a network. Security vulnerability exploitation modules are provided for execution by the local agent and / or the remote agent.
Owner:FORTRA LLC
Method and apparatus for generating automatic greetings in a call center
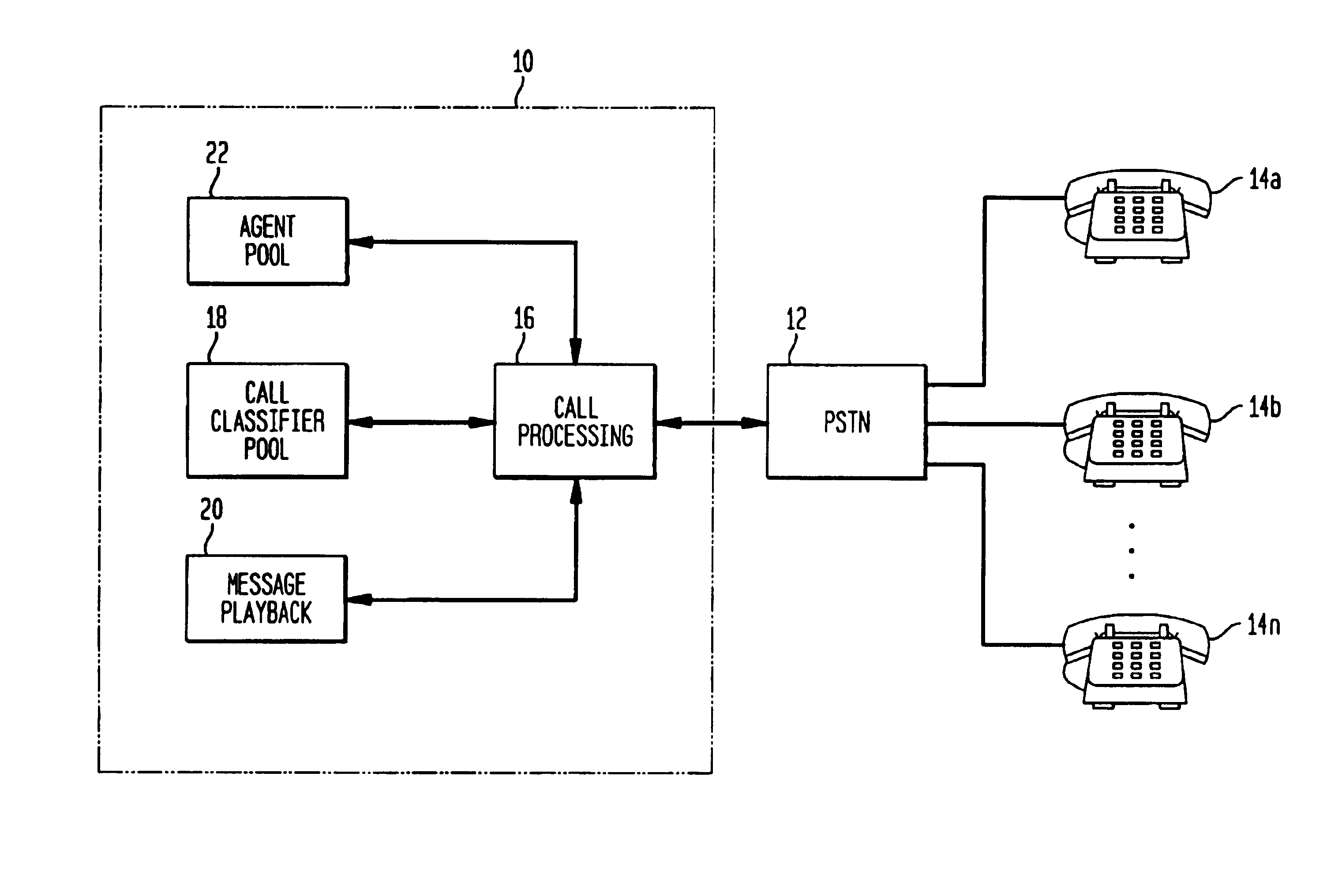
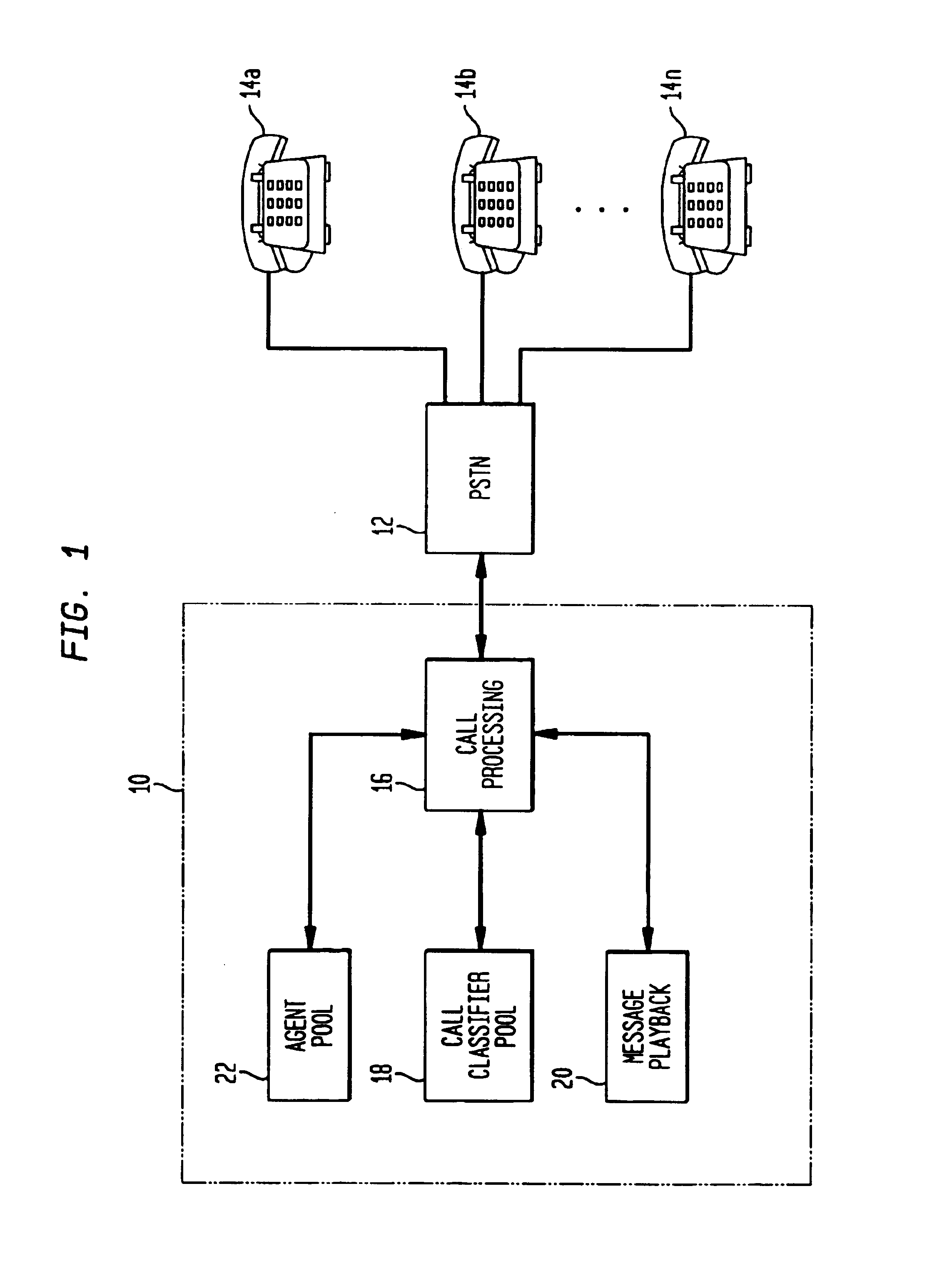
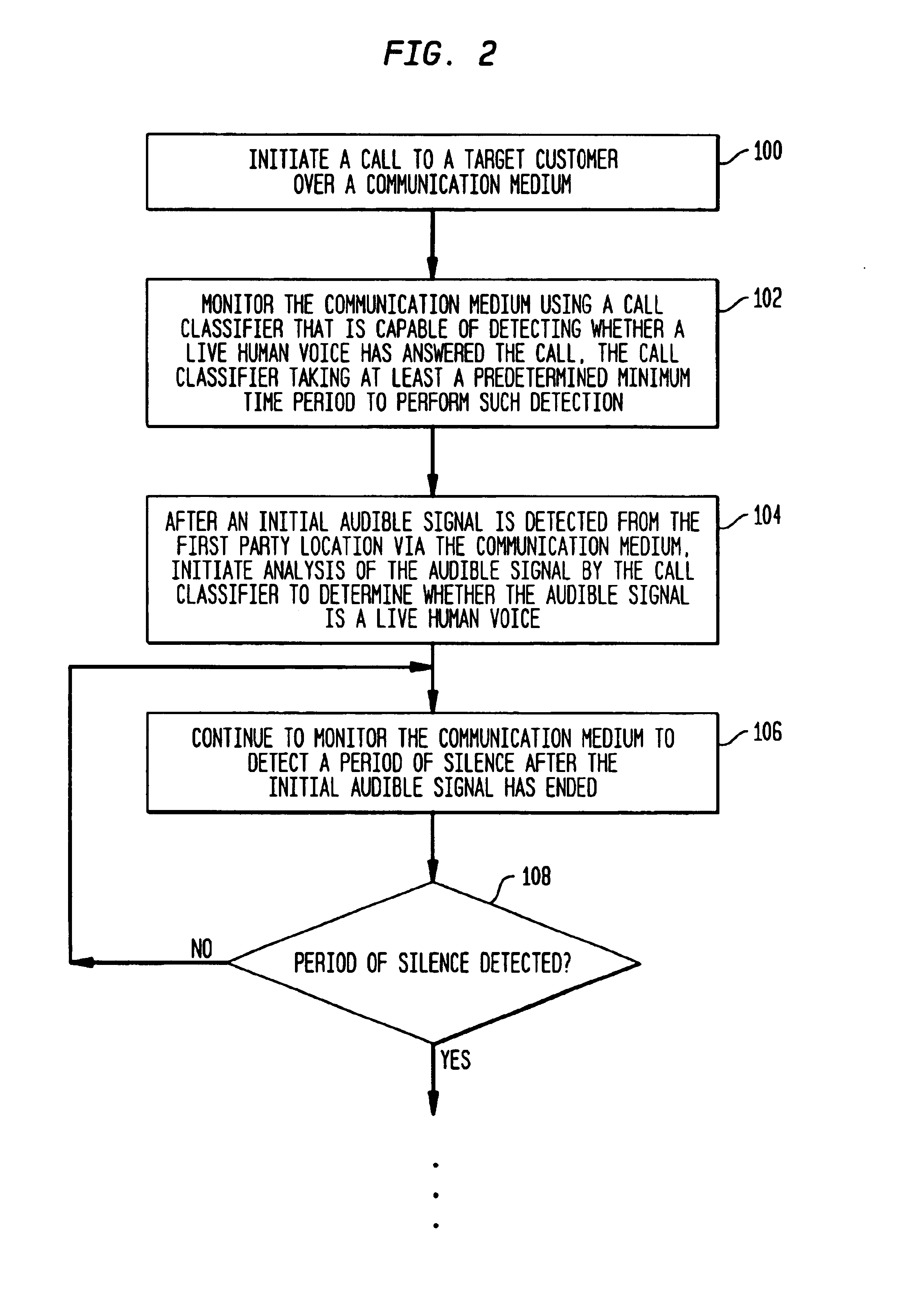
InactiveUS6925166B1Increasing outgoing call success rateReduce the burden onAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersAutomatic testingLocal agent
A call center includes a message playback unit for playing back a prerecorded greeting during an outgoing call while a call classifier unit within the call center processes an audible signal received from a remote party location. A call processing unit places a call to a remote party location via a communication network to attempt to elicit a desired response from the remote party. The call classifier then processes an audible signal received from the remote party location to determine whether or not the call was answered by a live party. The prerecorded greeting is then played while the call classifier is simultaneously processing the audible signal. If the call classifier determines that the call was answered by a live party, the call processing unit completes a talk path between the remote party location and a local agent at the call center who handles the remainder of the call. The call processing unit will normally wait until the greeting has ended to complete the talk path. If the call classifier determines that the call was not answered by a live party, the call processing unit will terminate the call.
Owner:AVAYA INC
Market-based virtual machine allocation
InactiveUS9027024B2Resource allocationProgram control using stored programsMarket basedComputing systems
Owner:RACKSPACE US
System and method for distributed denial of service identification and prevention
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
Current differential protection method for smart distribution network
ActiveCN101938117ARealize acquisitionRealize switch action controlEmergency protective arrangements for automatic disconnectionDifferential protectionPower flow
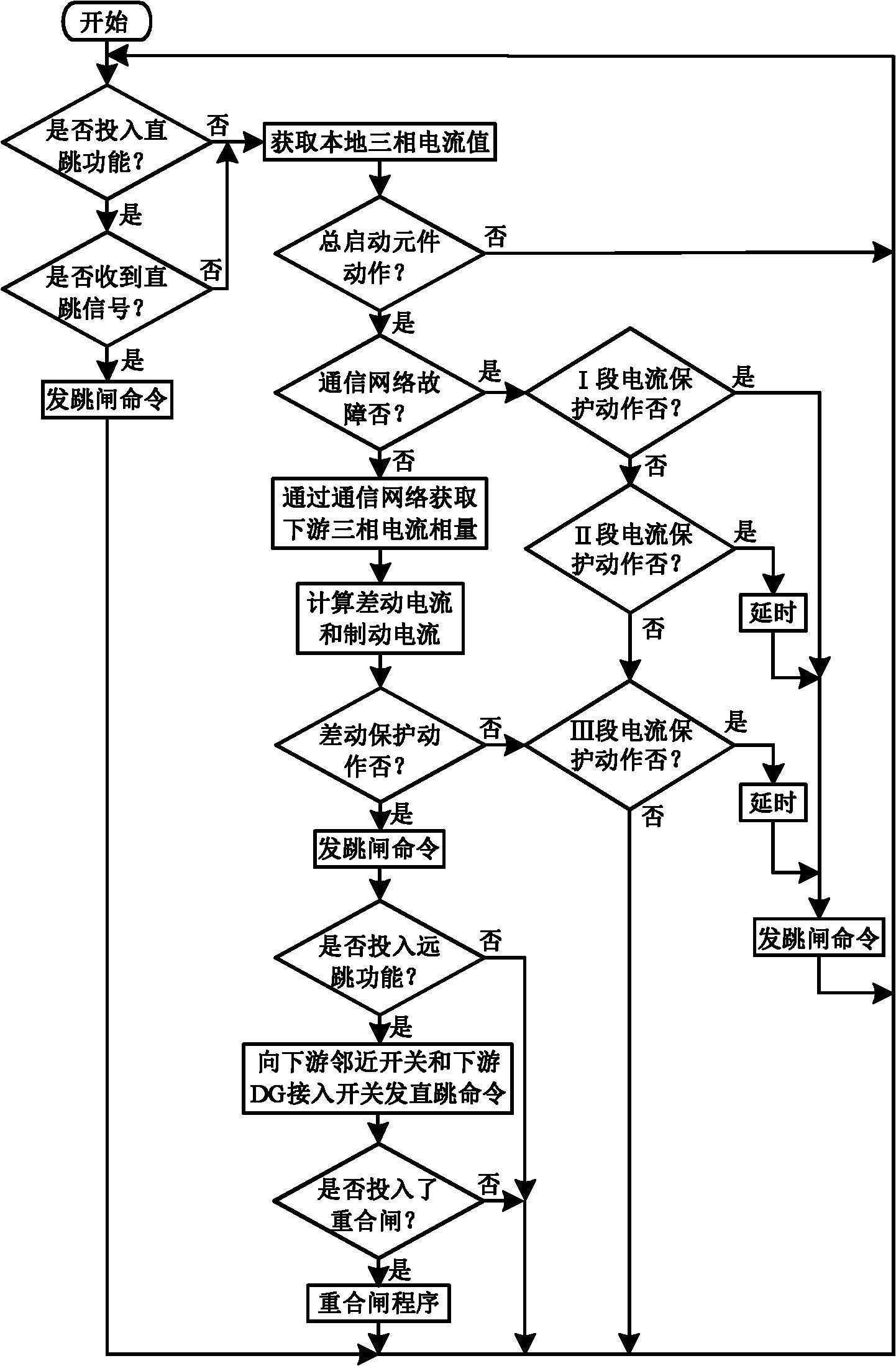
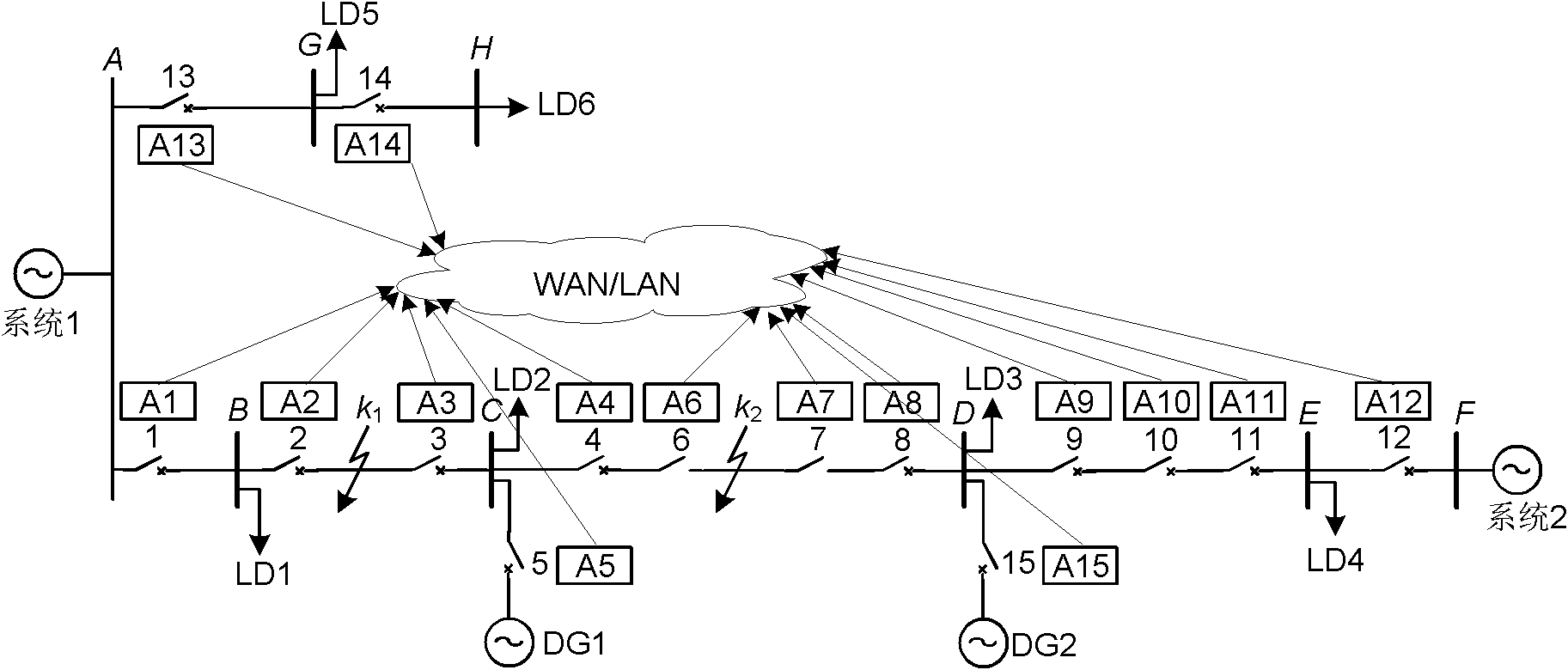
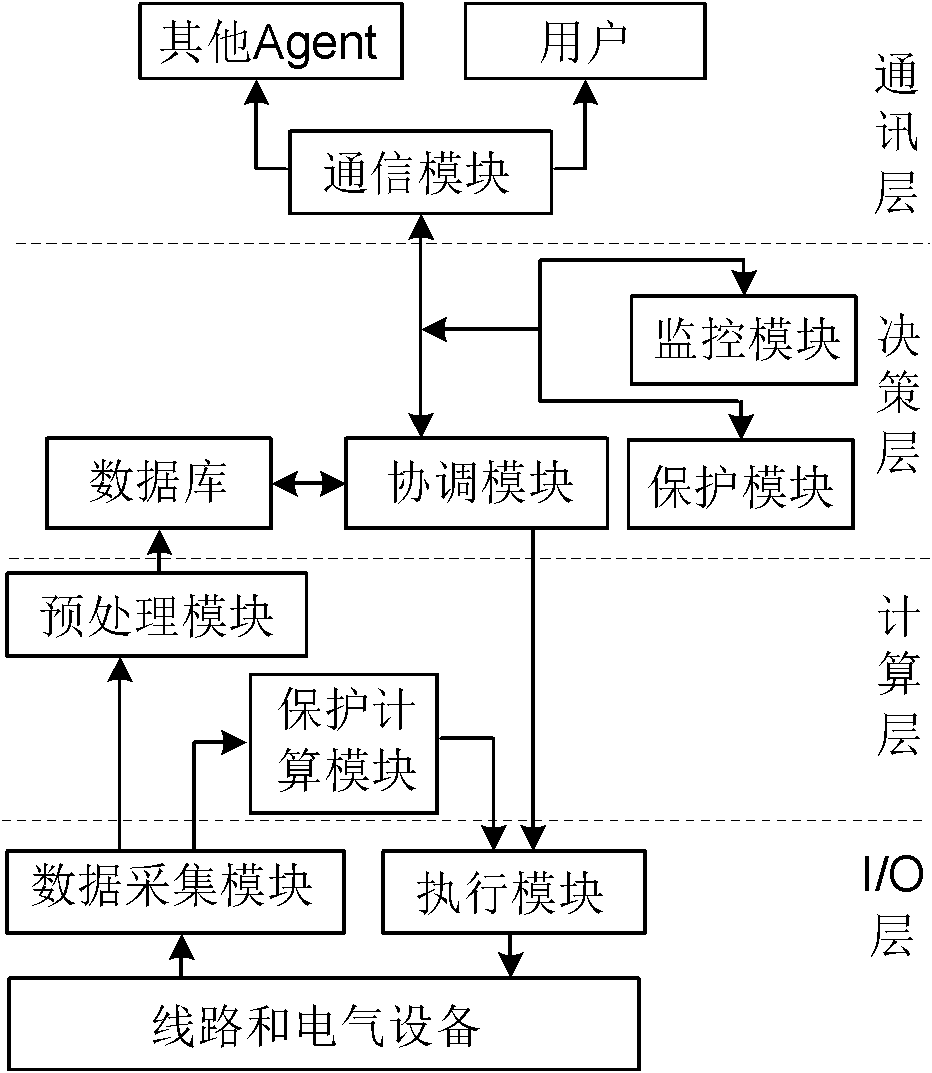
The invention relates to a current differential protection method for a smart distribution network, which comprises: mounting current transformers and smart distribution terminals at the positions of all switches in the smart distribution network, wherein each smart terminal serves as an agent, the agents are connected with one another through an optical fiber Ethernet, and the positive directions of all currents is the direction from a system power supply to the end of a circuit; automatically detecting the working state of a communication network through the agents, and determining if to perform current differential protection; when the communication network fails to work normally, applying the conventional three-stage current protection; when the communication network works normally, applying current differential protection and using the current differential protection as main protection; and allowing a local agent to compute a differential current and a braking current according to the local switching current detected by the local agent and downstream switching current transmitted by a downstream agent and determine if the protection is actuated. The overcurrent protection is local backup protection, and the protection of an upstream agent is local remote backup protection.
Owner:SHANDONG UNIV +1
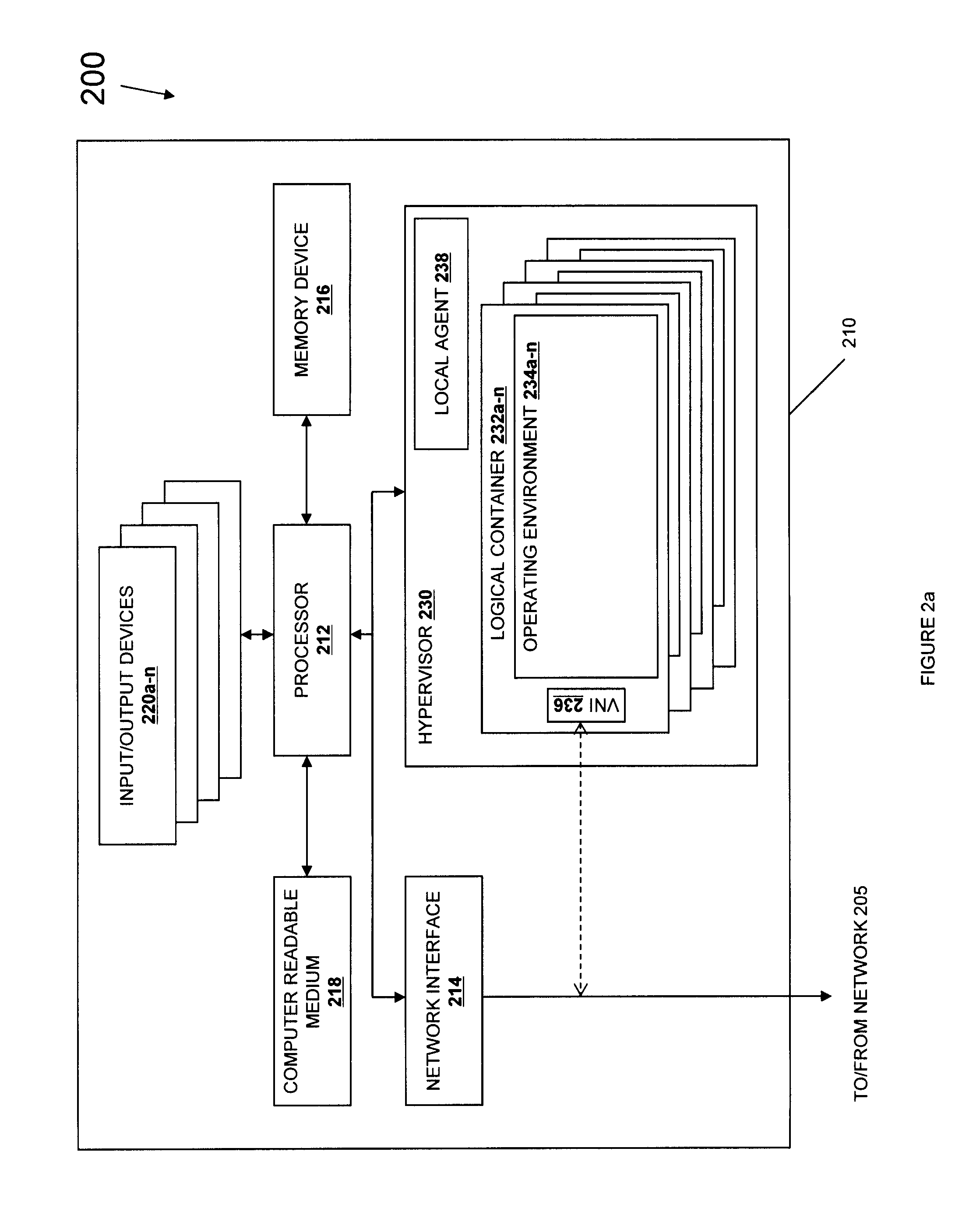
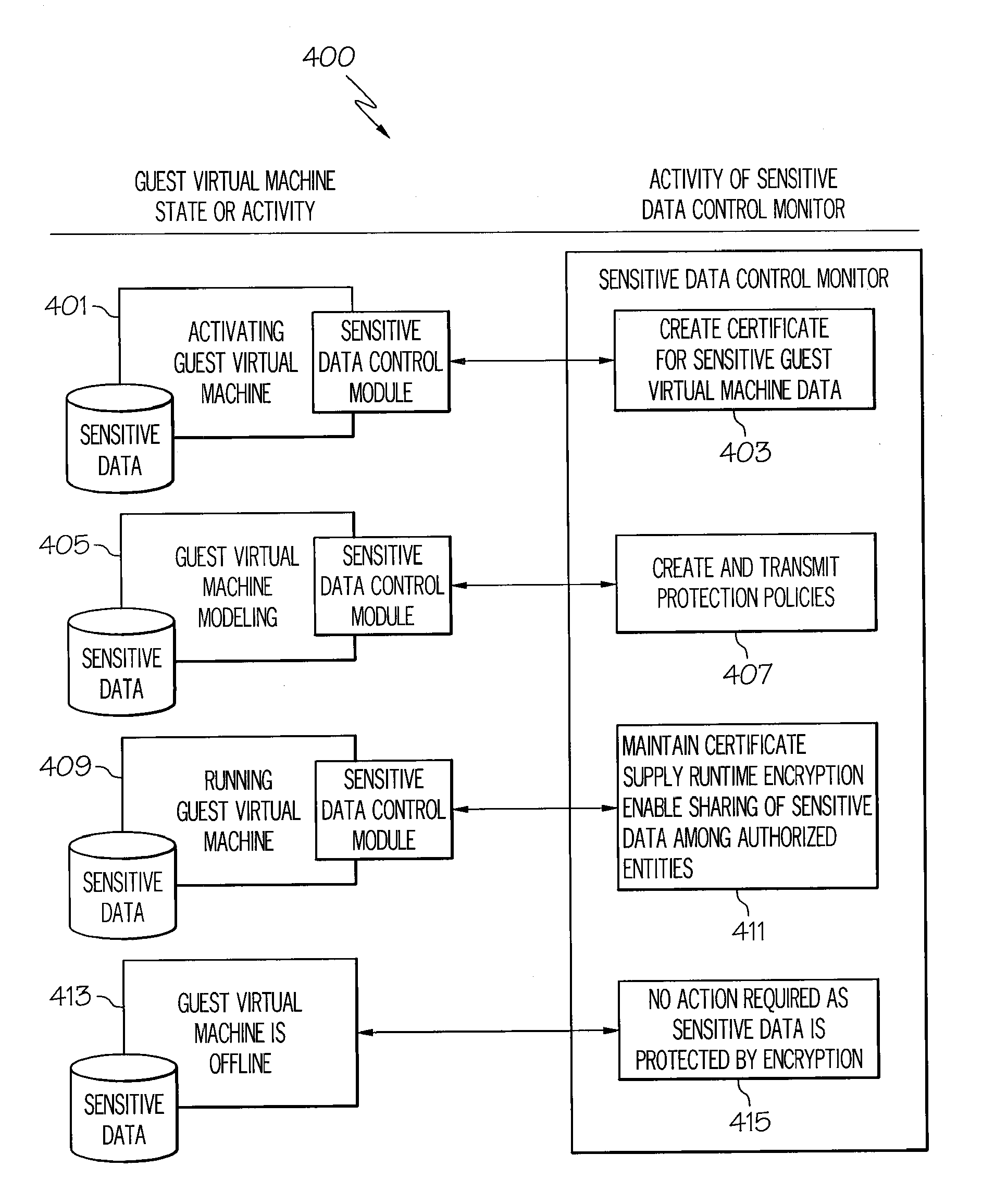
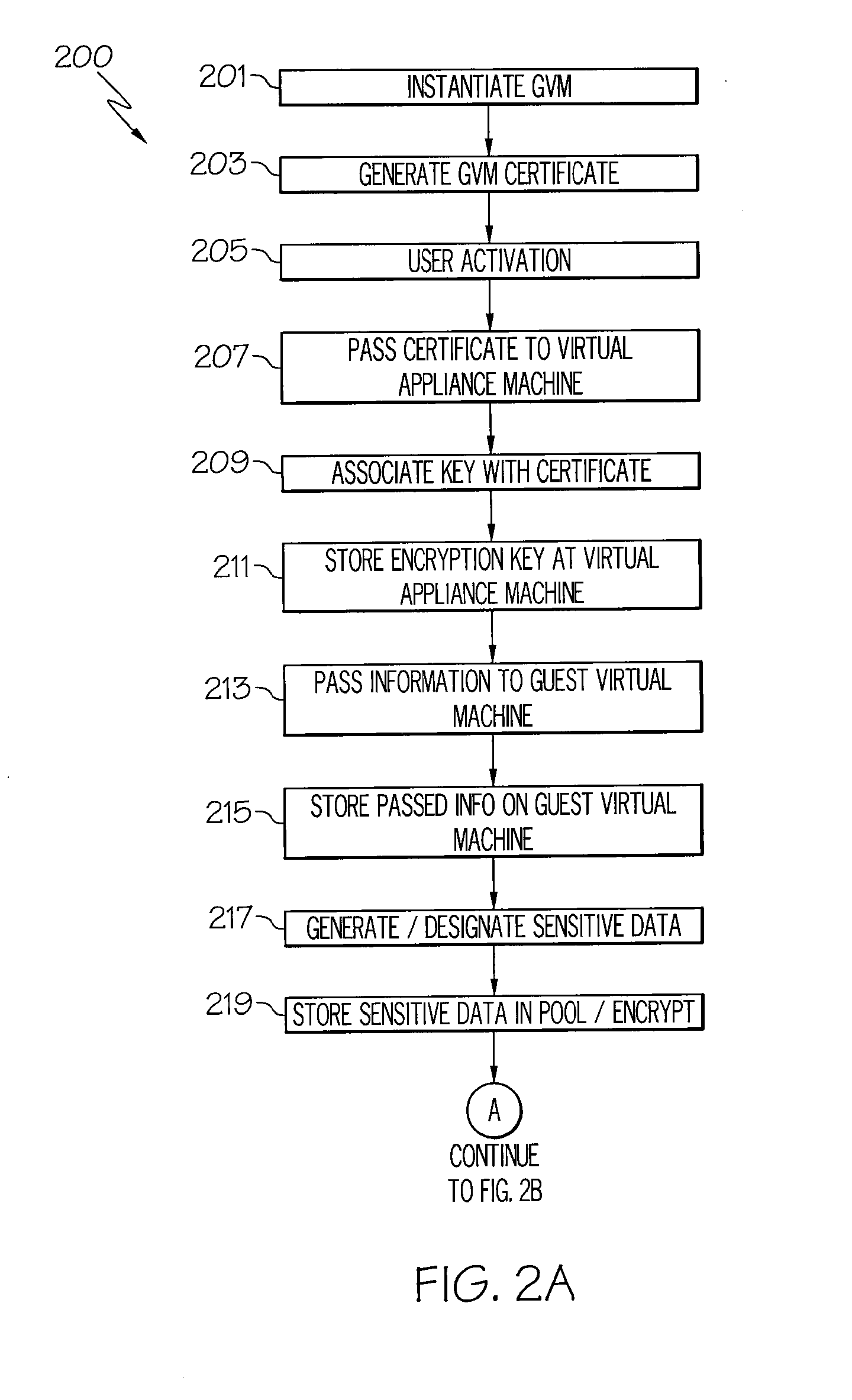
System and method for multi-layered sensitive data protection in a virtual computing environment
ActiveUS20140095868A1Encrypt dataDigital data protectionProgram controlData controlVirtual appliance
Systems and methods for providing sensitive data protection in a virtual computing environment. The systems and methods utilize a sensitive data control monitor on a virtual appliance machine administering guest virtual machines in a virtual computing environment, wherein each of the guest virtual machines may include a local sensitive data control agent. The sensitive data control monitor generates encryption keys for each guest virtual machine which are sent to the local sensitive data control agents and used to encrypt data locally on a protected guest virtual machine. In this manner the data itself on the virtual (or physical) disc associated with the guest virtual machine is encrypted while access attempts are gated by a combination of the local agent and the environment-based monitor, providing for secure yet administrable sensitive data protection.
Owner:CA TECH INC
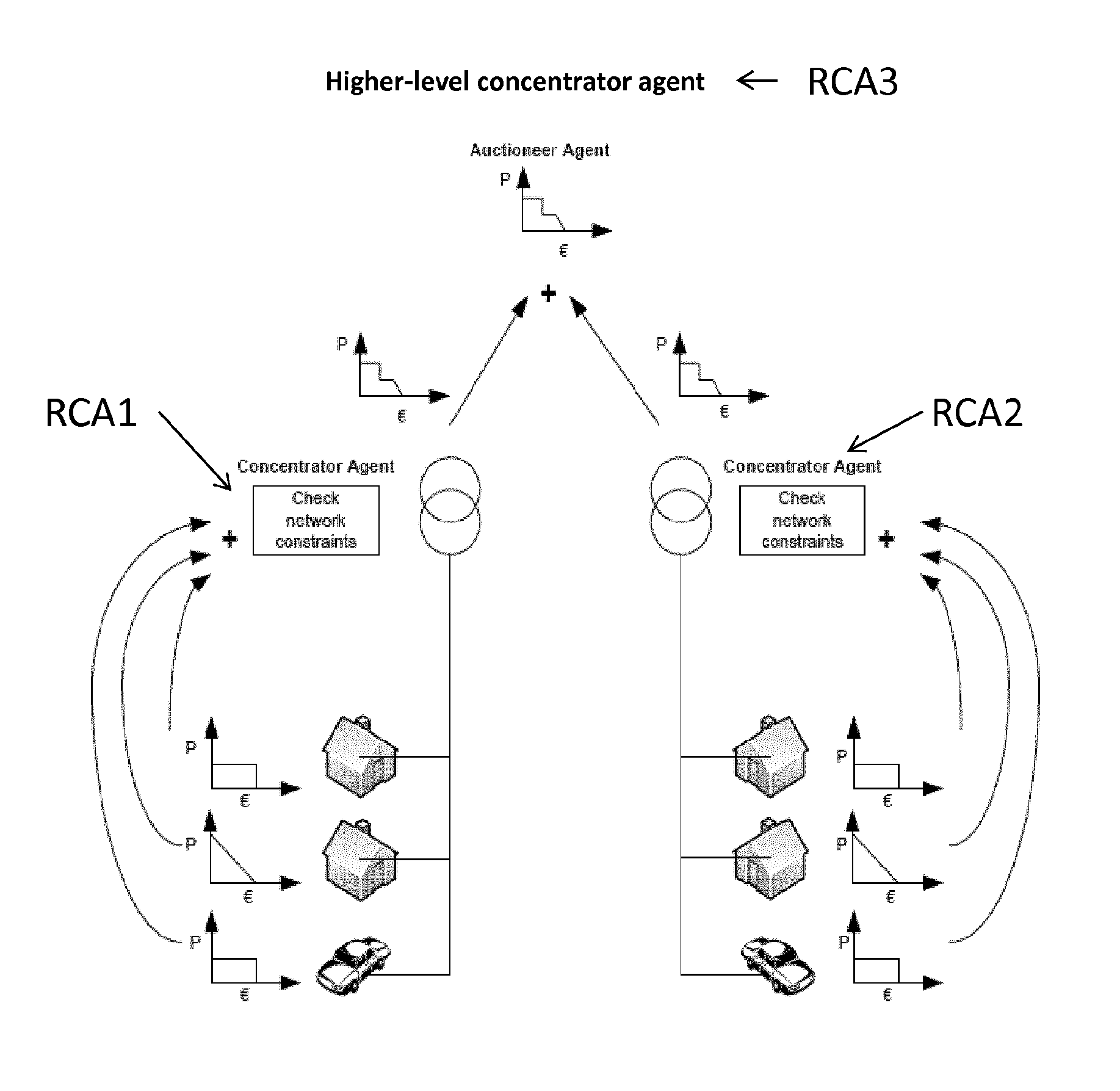
Method and system for distributing and/or controlling an energy flow taking into account constraints relating to the electricity network
ActiveUS20150280436A1Easy to useLess exchangingLevel controlMaterial dimension controlElectricityPower grid
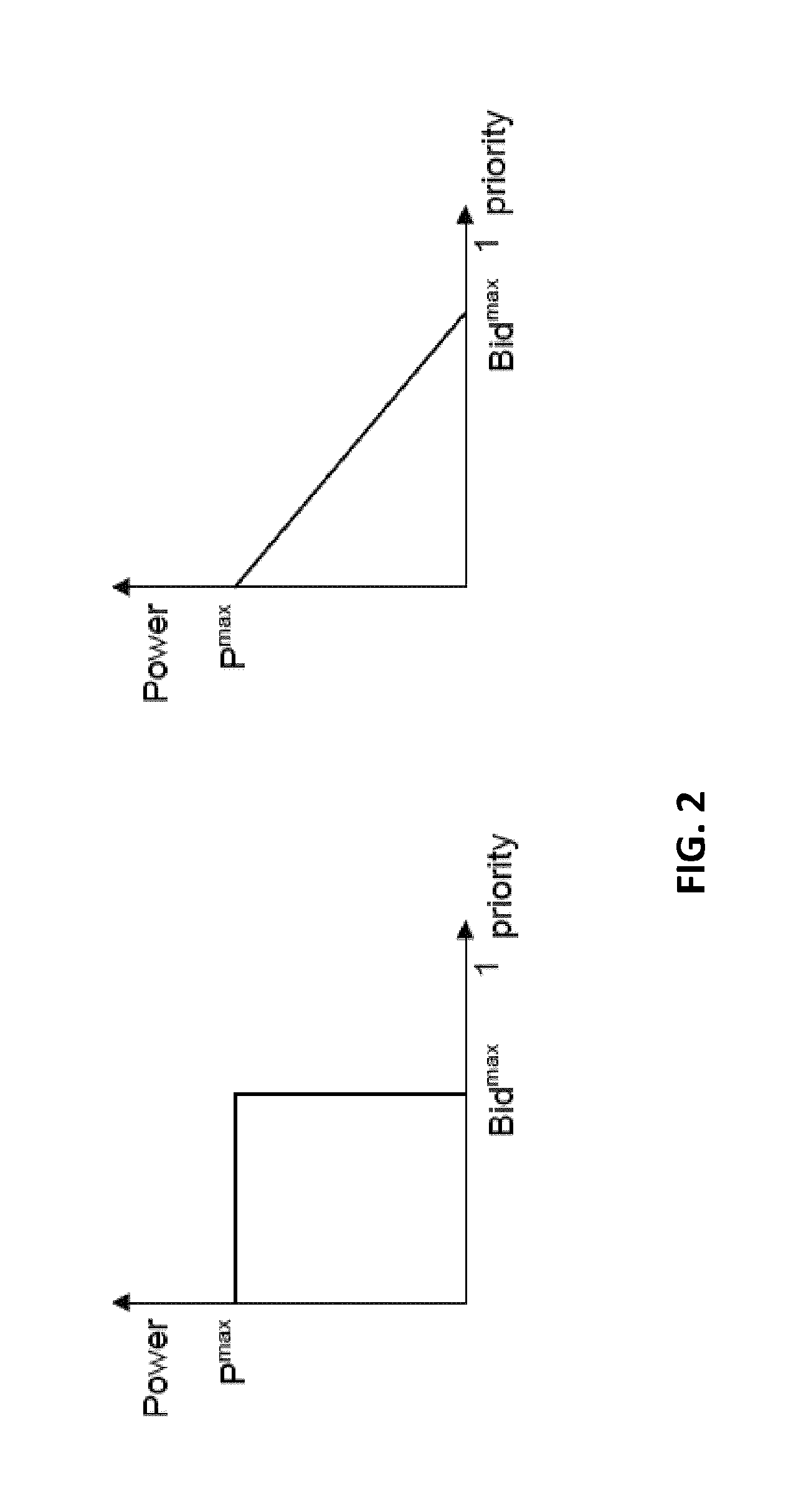
Method and system for distributing and / or controlling an energy flow to a cluster of a plurality of nodes in an electricity network, wherein each node has an associated status, taking into account constraints relating to the energy delivered to the nodes and constraints relating to the electricity network, comprised of:allocating a local agent to each node of the cluster of a plurality of nodes, wherein the local agent receives a priority for energy to be delivered;allocating a regional concentrator agent to the regional network, comprising at least a part of the cluster, wherein a total of the at least one regional network forms the electricity network;receiving by the at least one regional concentrator agent, the priority for energy to be delivered among the nodes and determining an aggregate priority for energy to be delivered to the at least one regional network, depending on voltage limitations.
Owner:KATHOLIEKE UNIV LEUVEN +1
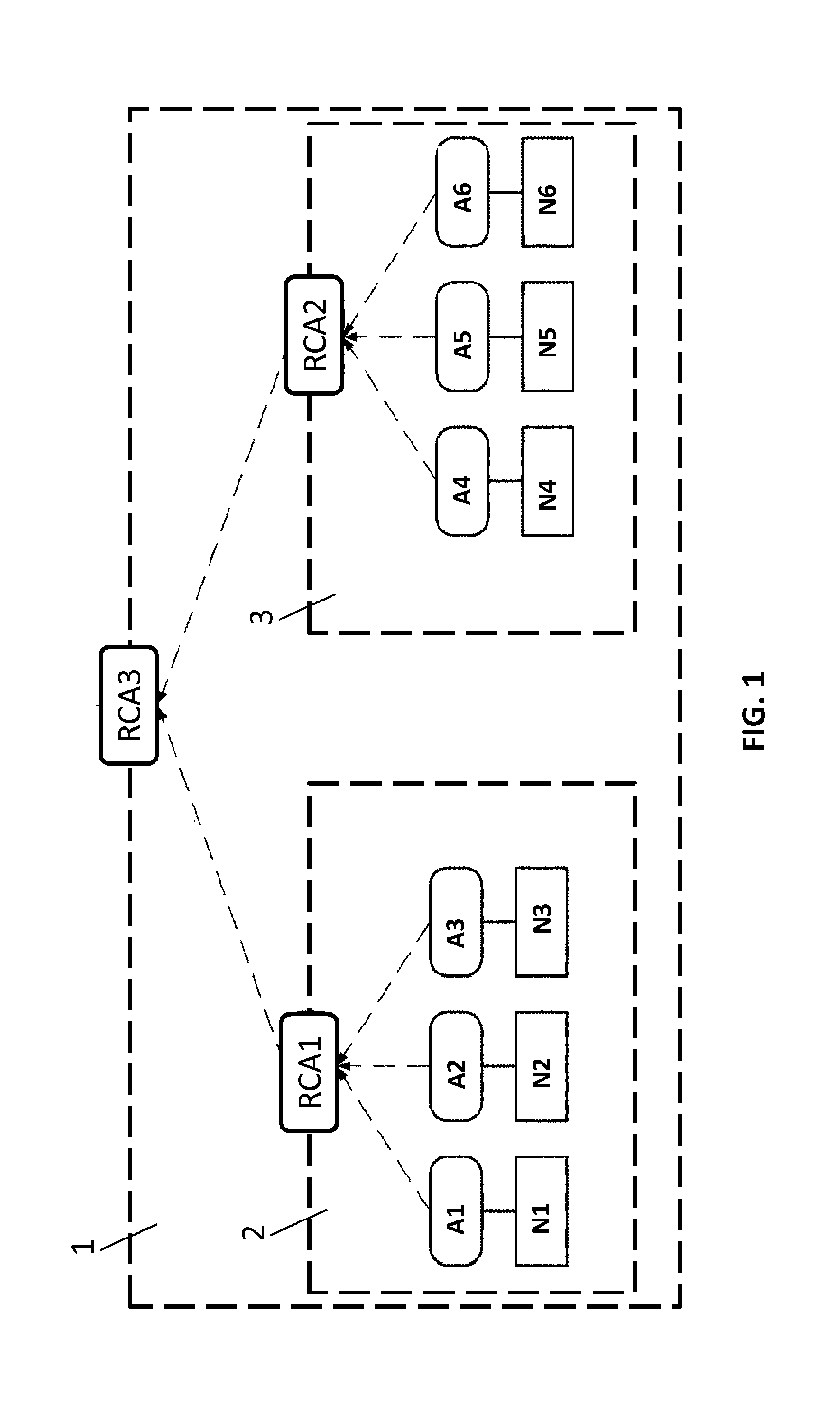
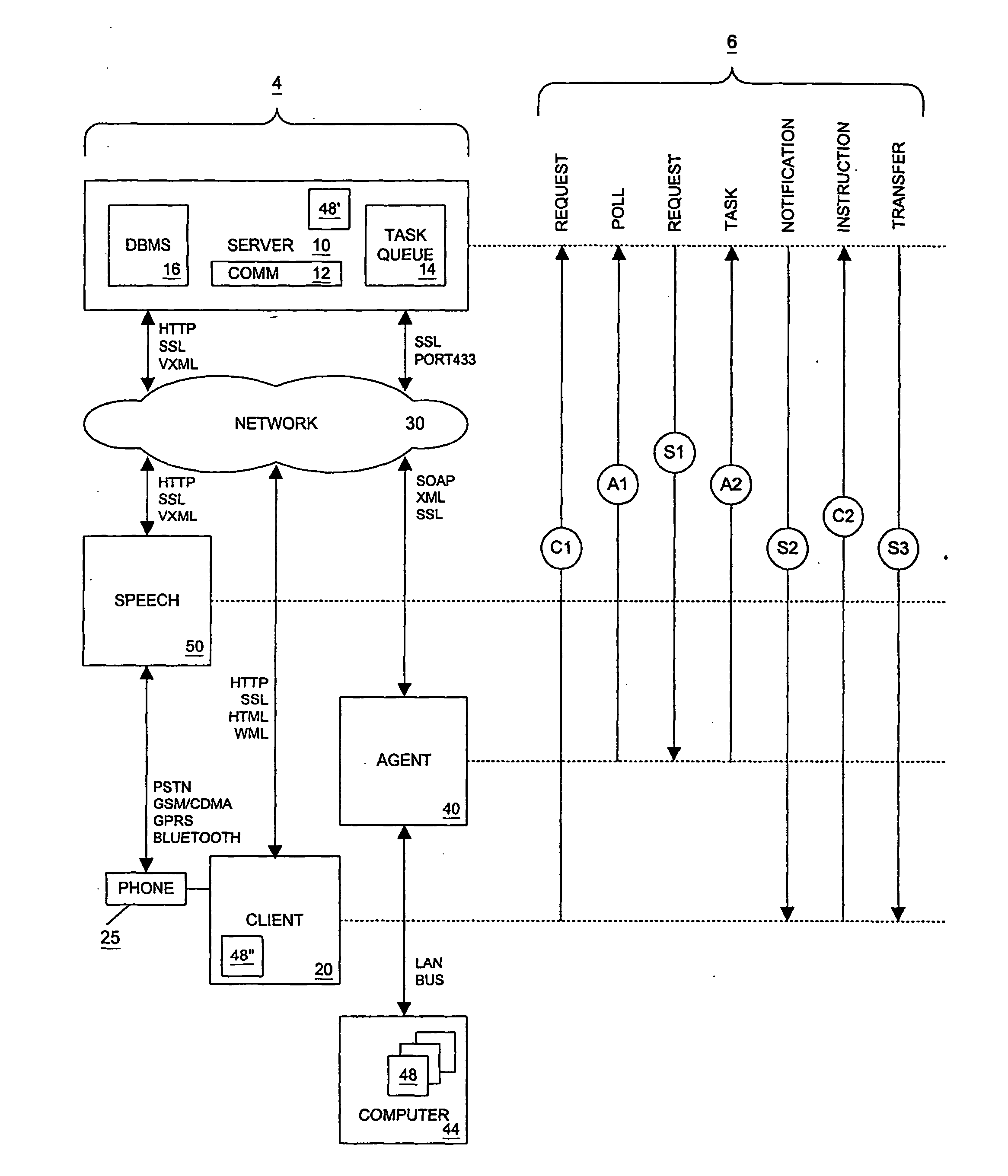
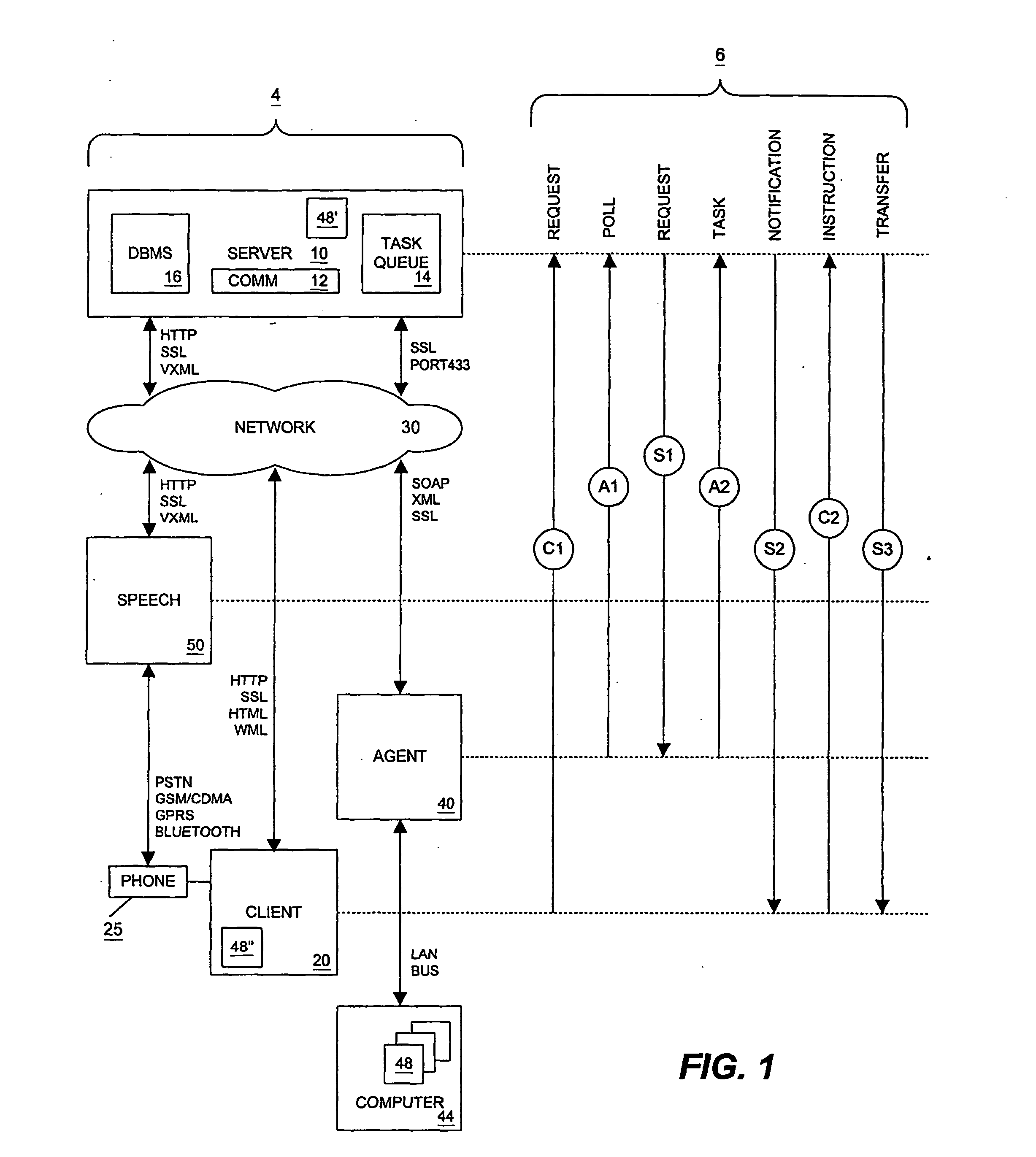
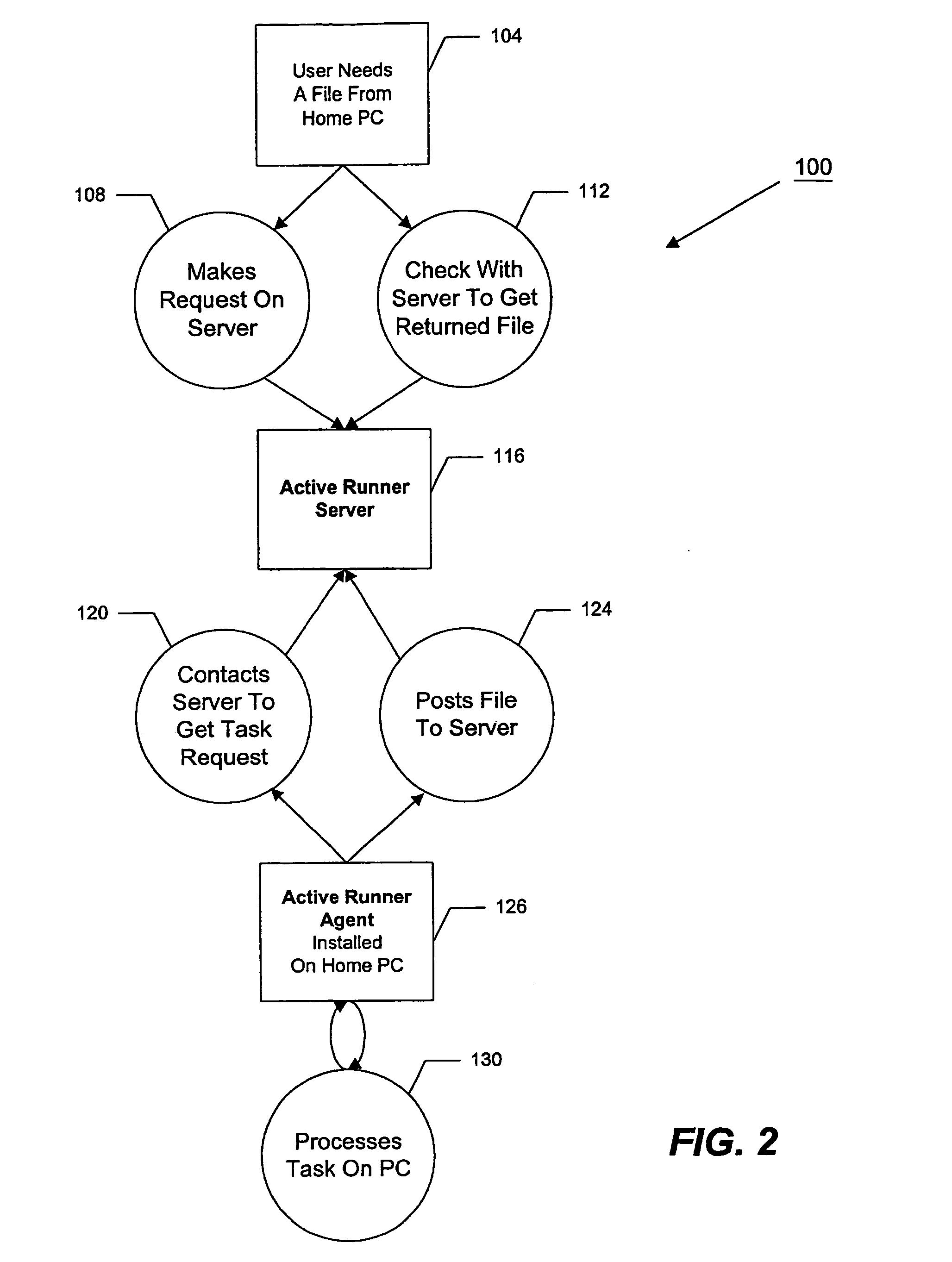
Local agent for remote file access system
ActiveUS20060282521A1Data be brokenDigital computer detailsTransmissionDatabase interfaceMessage delivery
Systems and methods for remote file access are disclosed. According to an embodiment, a local agent polls a server for a task request at a polling interval scheduled by a schedule timer in accordance with a set of local agent and remote client preferences. The local agent is responsible for executing a task from the task request and causing a file to be uploaded to the server. The local agent uses a task processor for polling a server, a schedule timer for controlling polling, and one or more protocol stacks, such as TCP / IP and SOAP, for communicating with the server. The local agent can also interface with a MAPI database for message delivery.
Owner:CITRIX SYST INC
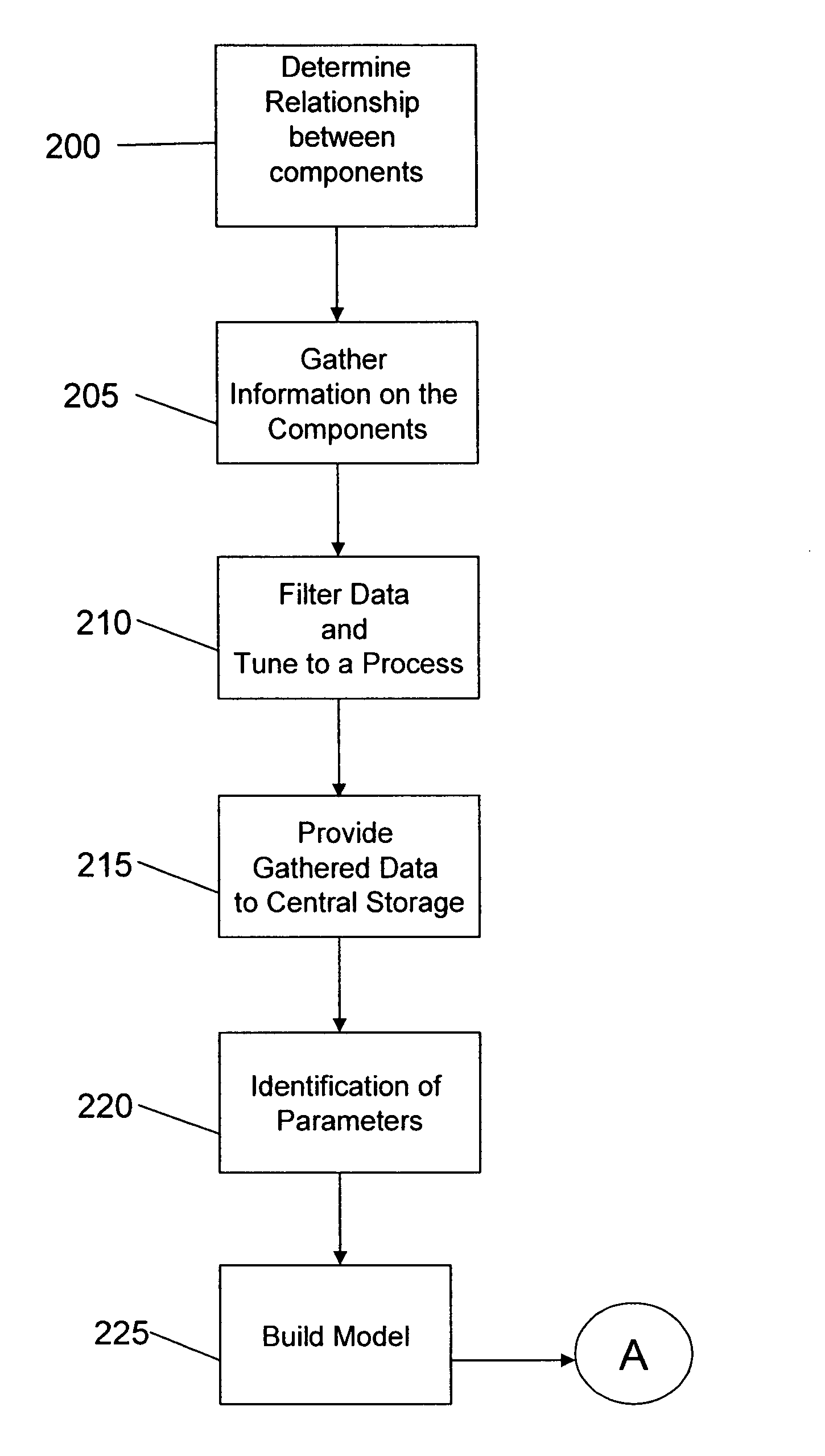
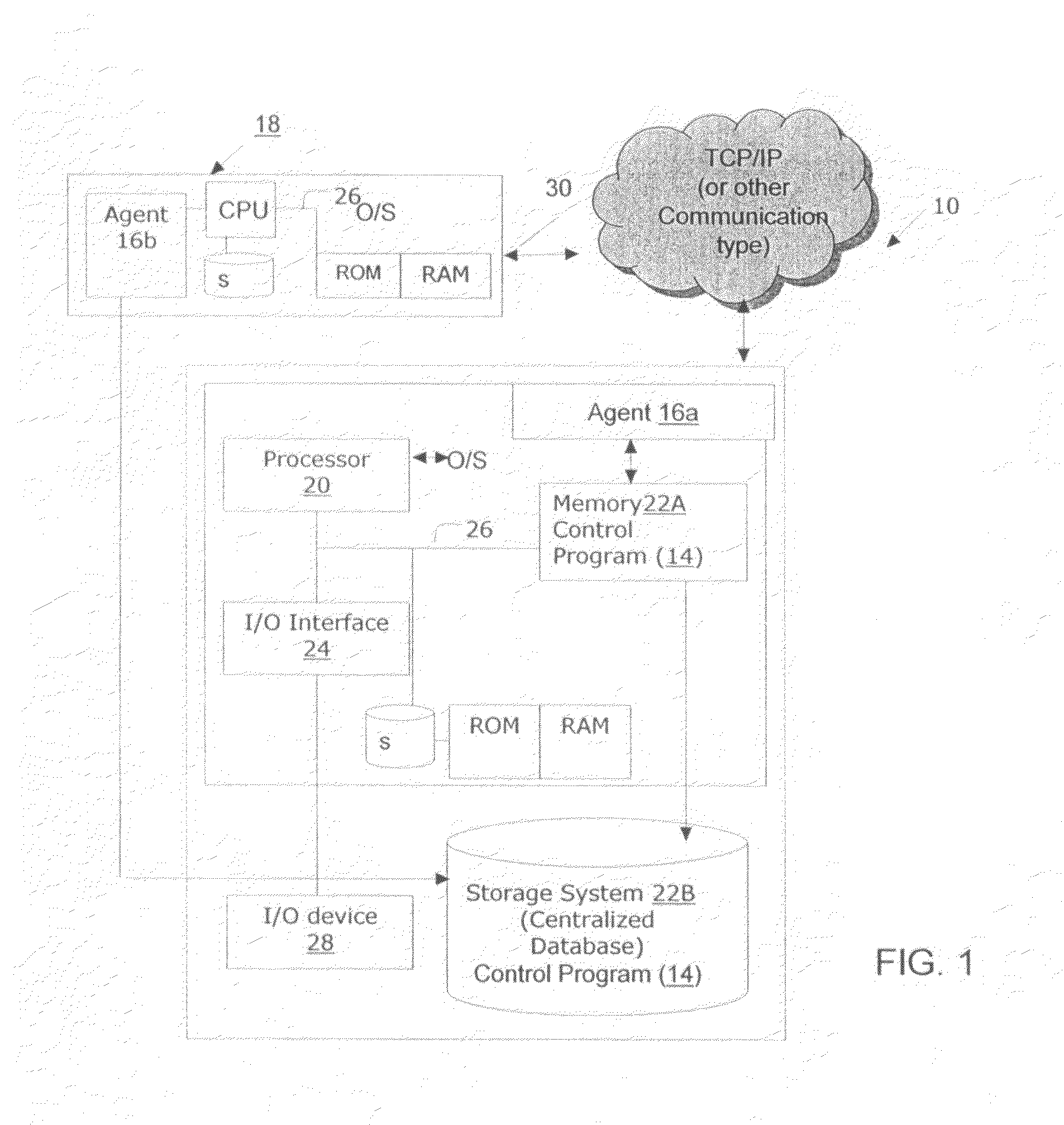
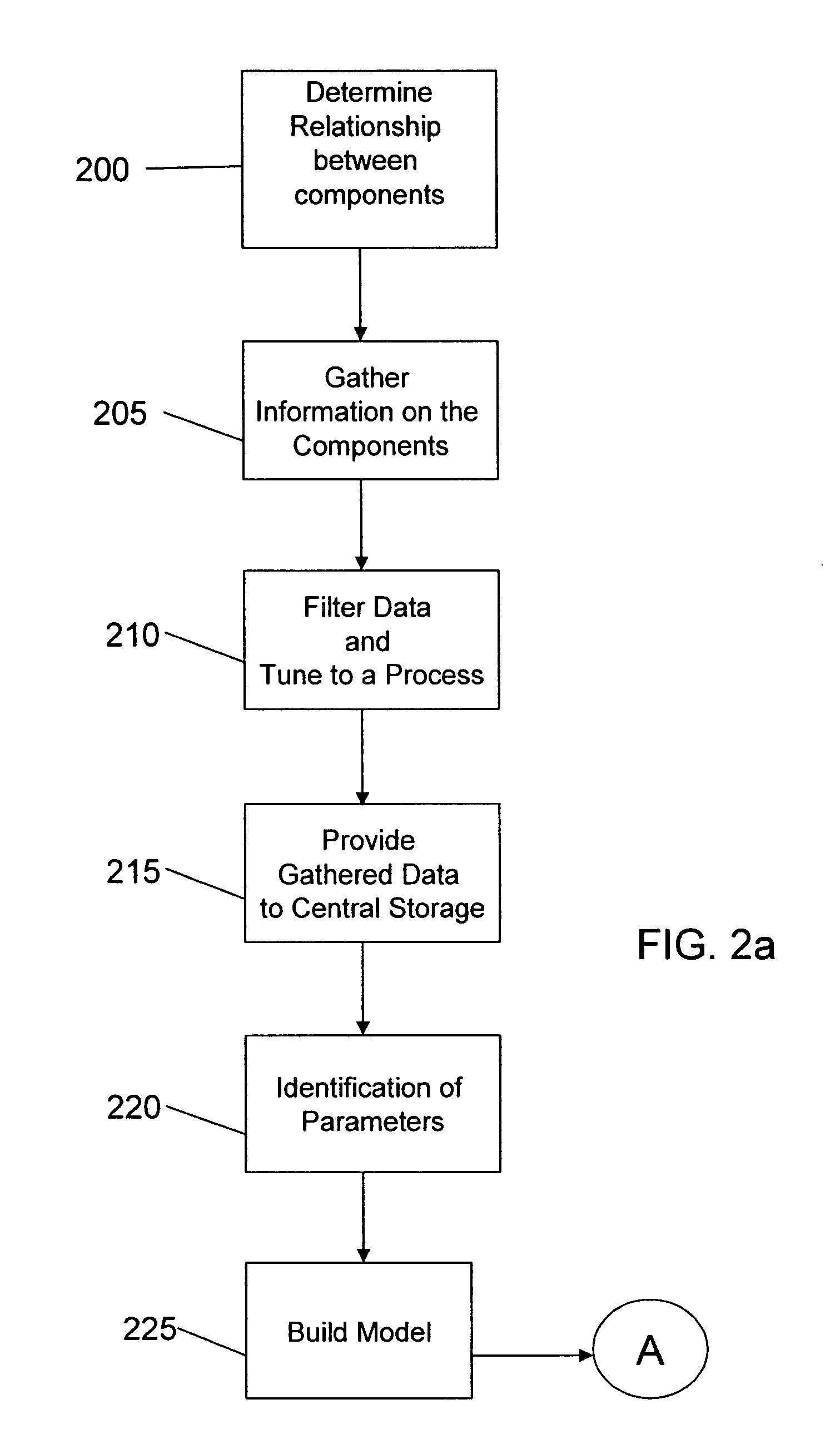
Real-time performance modeling of application in distributed environment and method of use
InactiveUS20090006069A1Improve component performanceImprove performanceError detection/correctionSpecific program execution arrangementsCurrent loadDistributed Computing Environment
A system and method of managing computing systems and, more particularly, to a system and method for modeling applications in a network. The method includes determining dependency of components in a shared distributed computing environment and measuring consumption of the dependent components. The method further includes building a model to compare component behavior with a current load of the dependent components to optimize component performance or to find a deviation and hence a “troubled spot”. The system includes a local agent configured to perform the method and to provide data to a centralized storage.
Owner:IBM CORP
System and methods for tracking local database access
InactiveUS7426512B1Reduce resource overheadReduce overheadDigital data information retrievalData processing applicationsAnalysis dataData access
Owner:IBM CORP
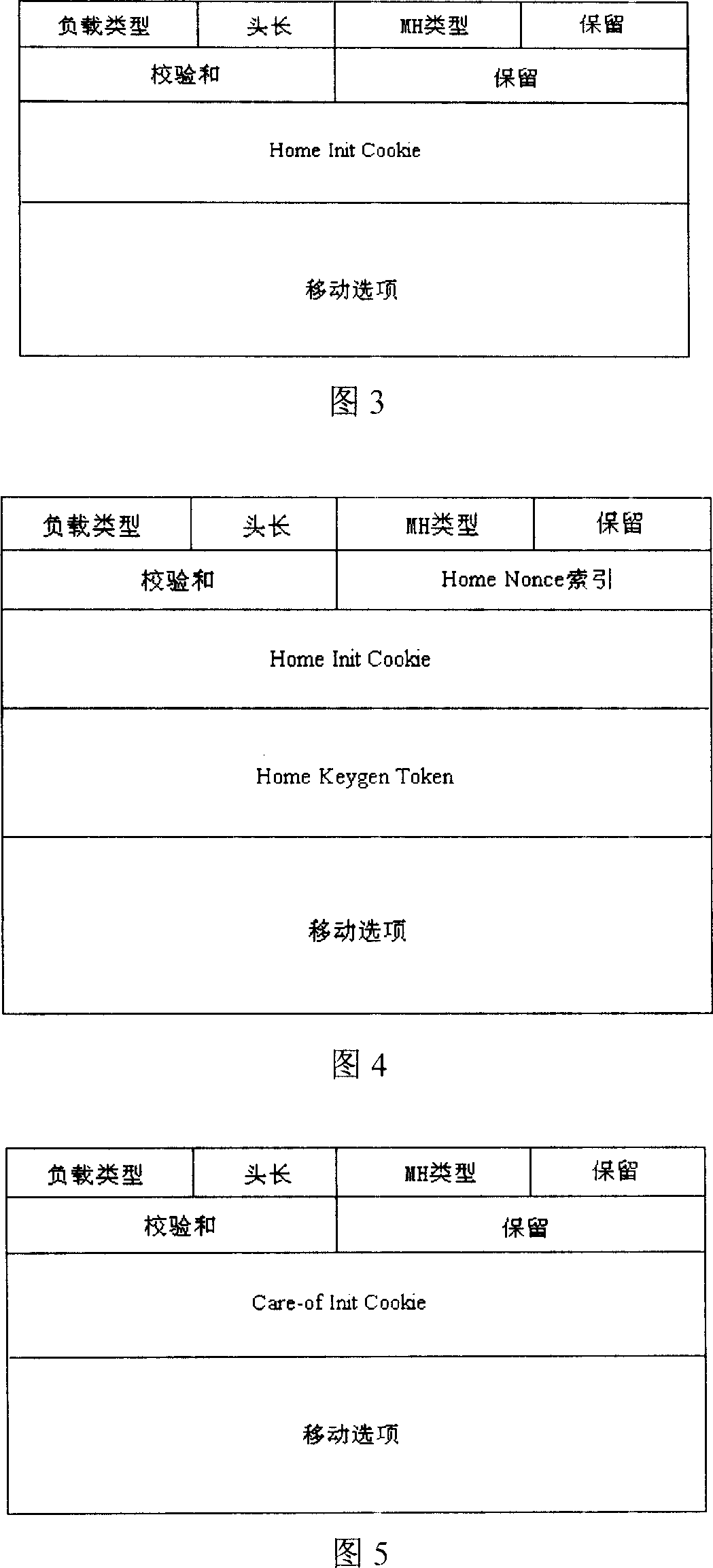
A communication method for switching the mobile node from IPv6 network to IPv4 network
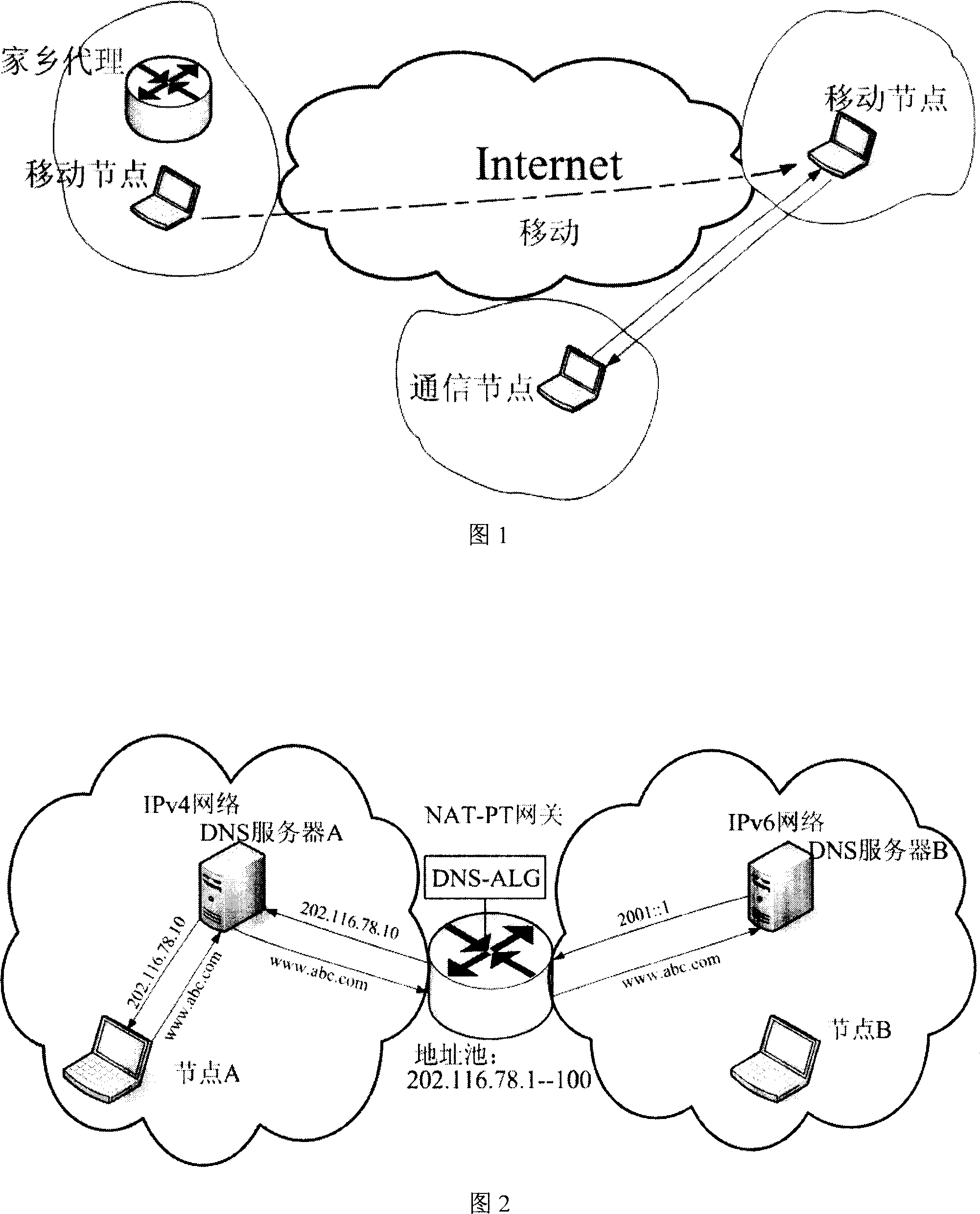
InactiveCN101018412AEnsure application transparencyWireless network protocolsRadio/inductive link selection arrangementsDomain nameComputer science
The related continual communication switch method from IPv6 to IPv4 network comprises: as both the local agent and communication node on IPv6 network, setting a NAT-PT gateway with DNS-ALG between the IPv6 and IPv4 network; when moving from IPv6 to IPv4 network, the node queries the IPv4 addresses of local agent and node distributed by NAT-PT gateway for next register and communication. Besides, this invention applies mobile option of Care-of Test message for convenient data calculation.
Owner:SUN YAT SEN UNIV
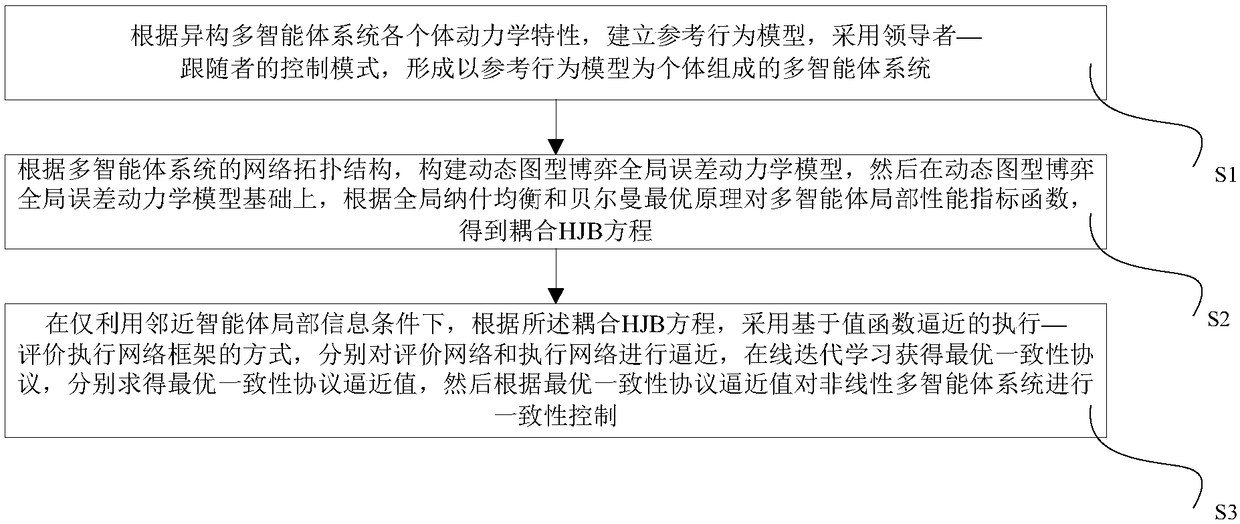
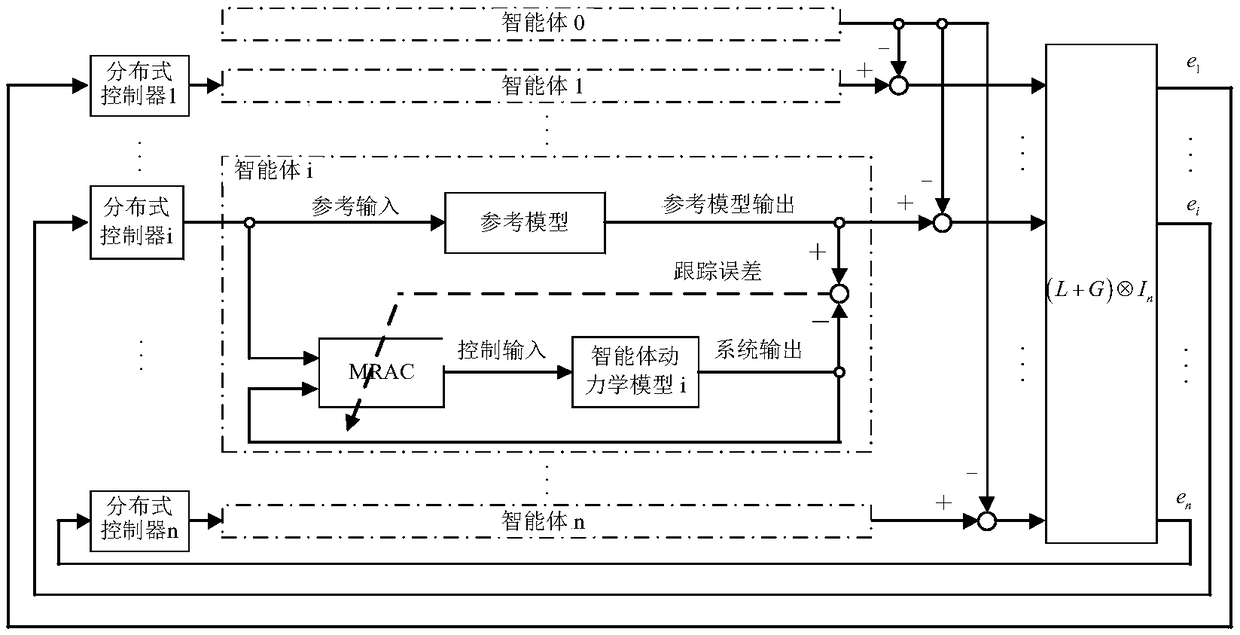
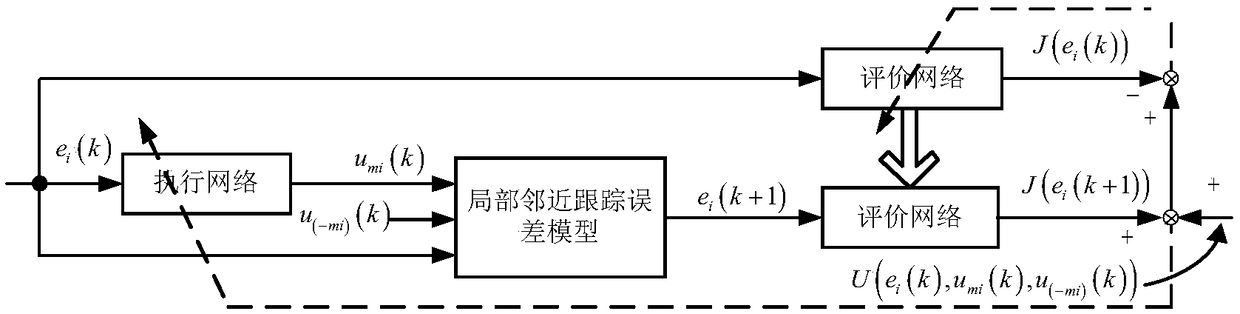
Optimal consistency control method and system of nonlinear multi-agent system
ActiveCN108803349AClose to realizationGuaranteed reliabilityAdaptive controlOptimal controlPerformance index
The invention discloses the optimal consistency control method and system of a nonlinear multi-agent system. The method is characterized by establishing a reference behavior model according to the individual dynamic characteristic of a heterogeneous multi-agent system, and using a leader-follower control model to form a multi-agent system formed by reference behavior models; then, constructing a dynamic graph game global error dynamical model according to the network topology structure of multiple agents, defining a multi-agent local performance index function, and according to the global Nashequilibrium, acquiring a Bellman optimal equation; and then, under the condition of only using local agent information, using an execution-evaluation execution network framework mode based on value function approximation to carry out online iterative learning, and acquiring an optimal consistency protocol to achieve the consistency of each reference model behavior. Compared with the prior art, byusing the method and the system of the invention, under the condition of guaranteeing optimal control performance, the consistency problem of the complex multi-agent system can be high-efficiently solved, and an actual application value and high scalability are achieved.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
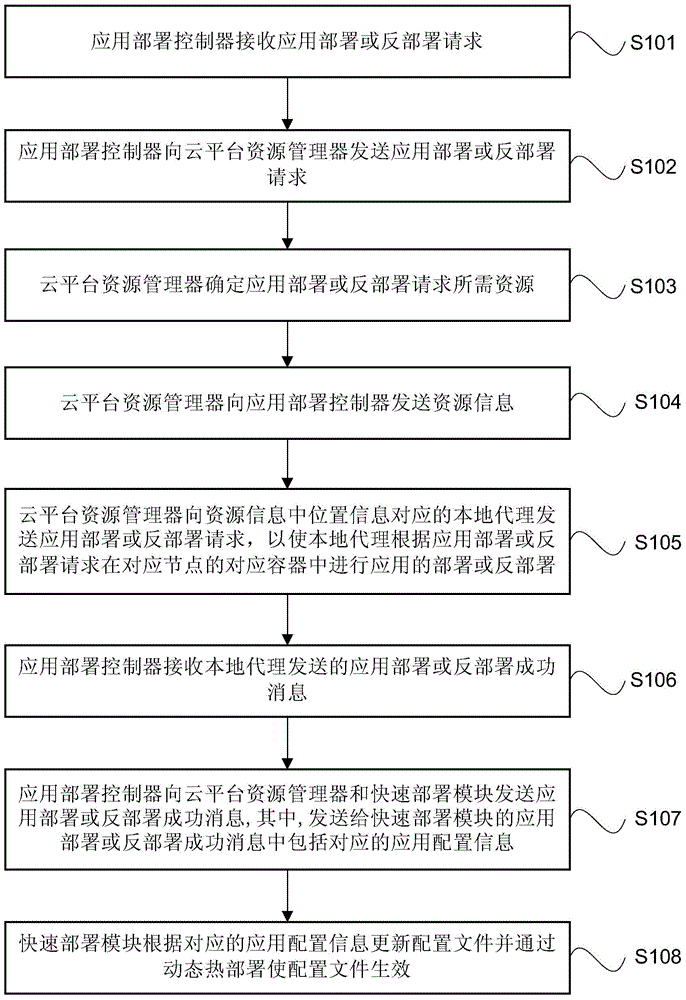
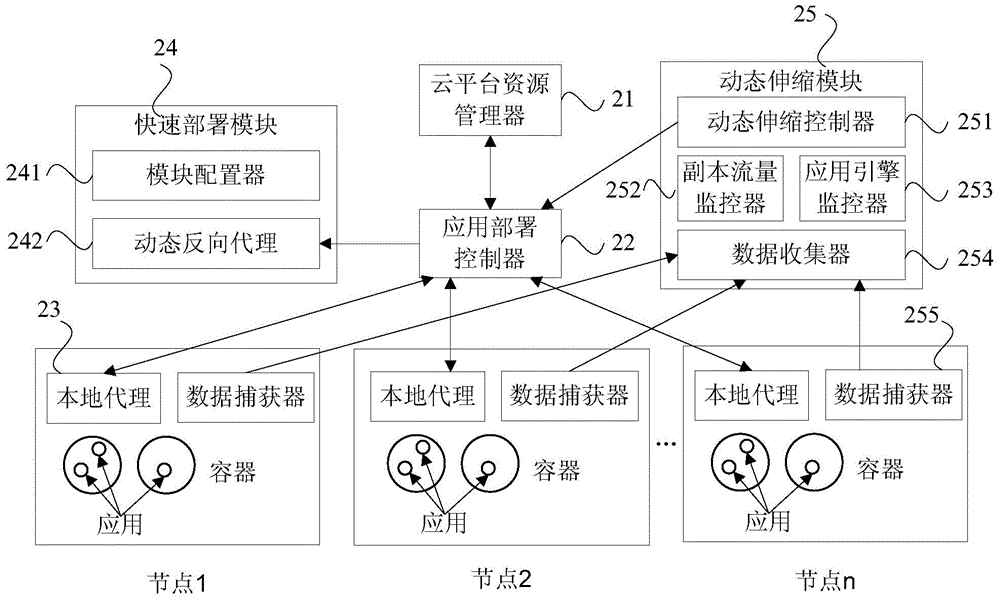
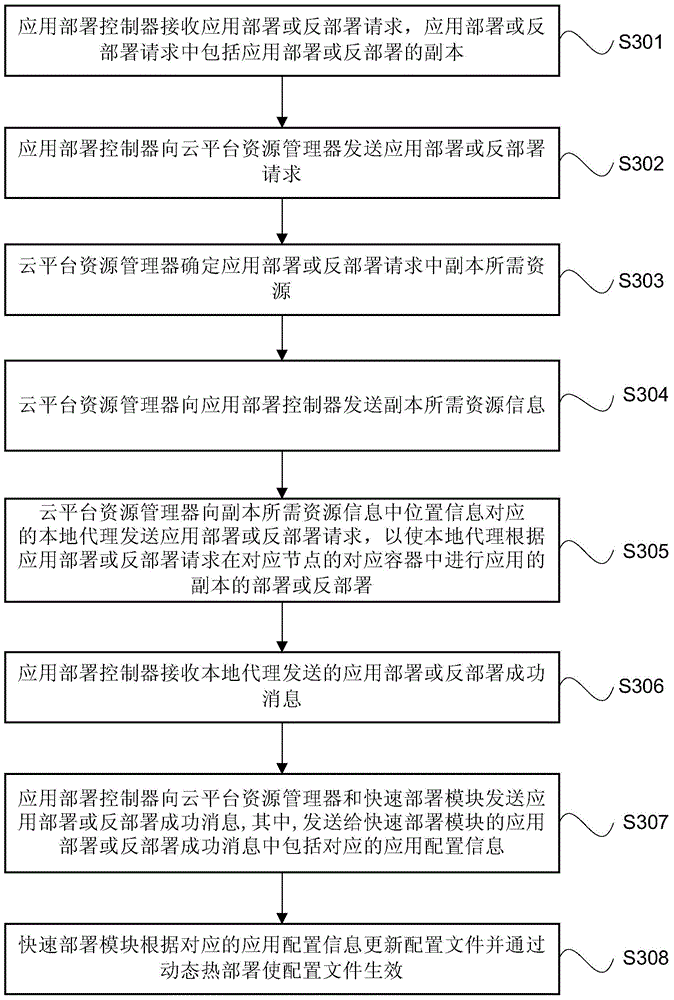
Management method for rapid cloud computing platform application deployment
The invention provides a management method for rapid cloud computing platform application deployment. The method includes the steps that an application deployment controller receives an application deployment or undeployment request and sends the application deployment or undeployment request to a cloud platform resource manager; the cloud platform resource manager determines resources required by the application deployment or undeployment request and sends resource information to an application deployment controller; the application deployment or undeployment request is sent to a local agent corresponding to position information in the resource information so that the local agent can conduct application deployment or undeployment in a corresponding container of the application deployment or undeployment request at a corresponding node; an application deployment controller receives an application deployment or undeployment success message sent by the local agent, and the application deployment or undeployment success message is sent to the cloud platform resource manager and a rapid deployment module; the rapid deployment module renews a configuration file according to corresponding application deployment information in the application deployment or undeployment message, and brings the configuration file into effect through dynamic hot deployment.
Owner:BEIHANG UNIV
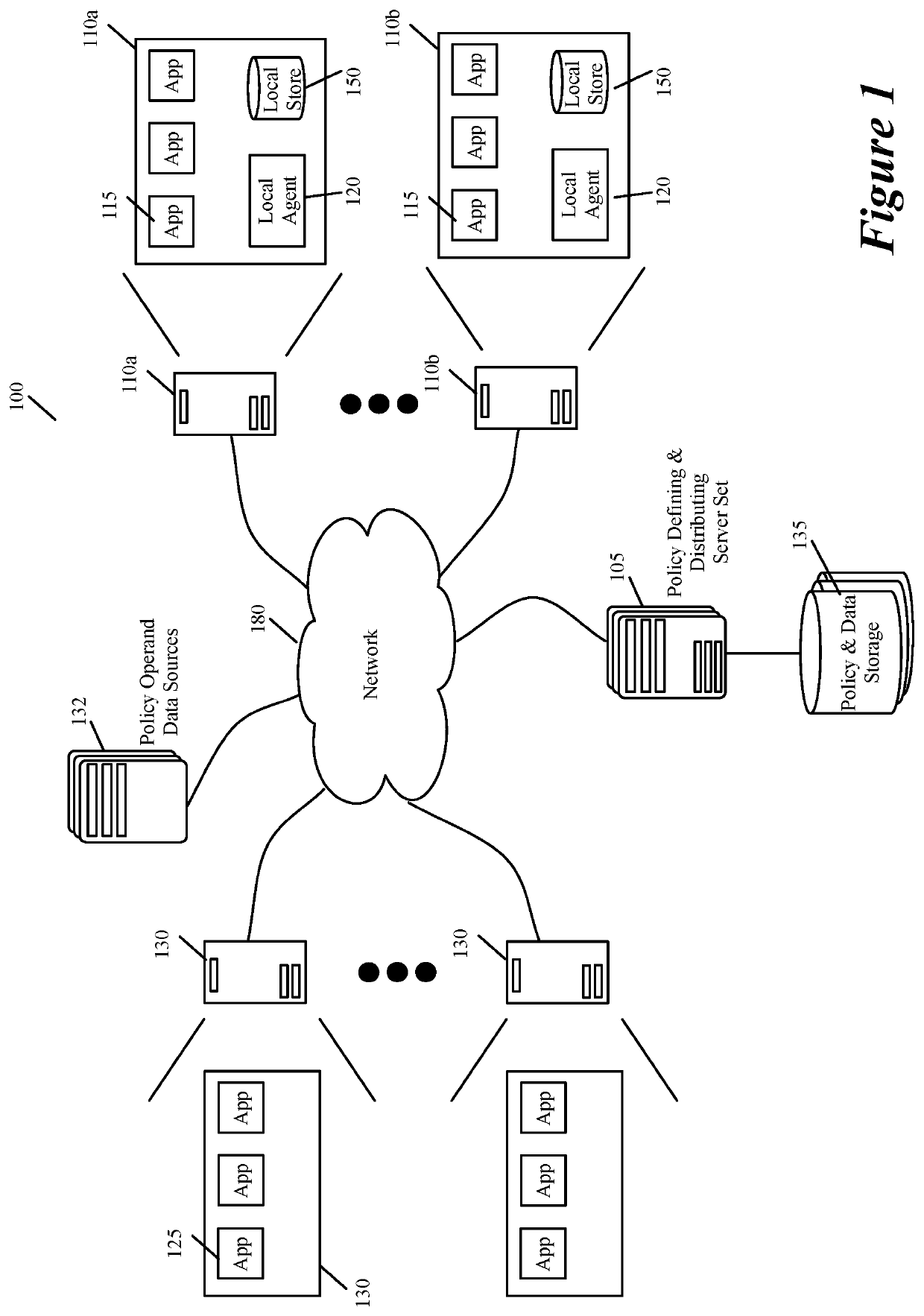
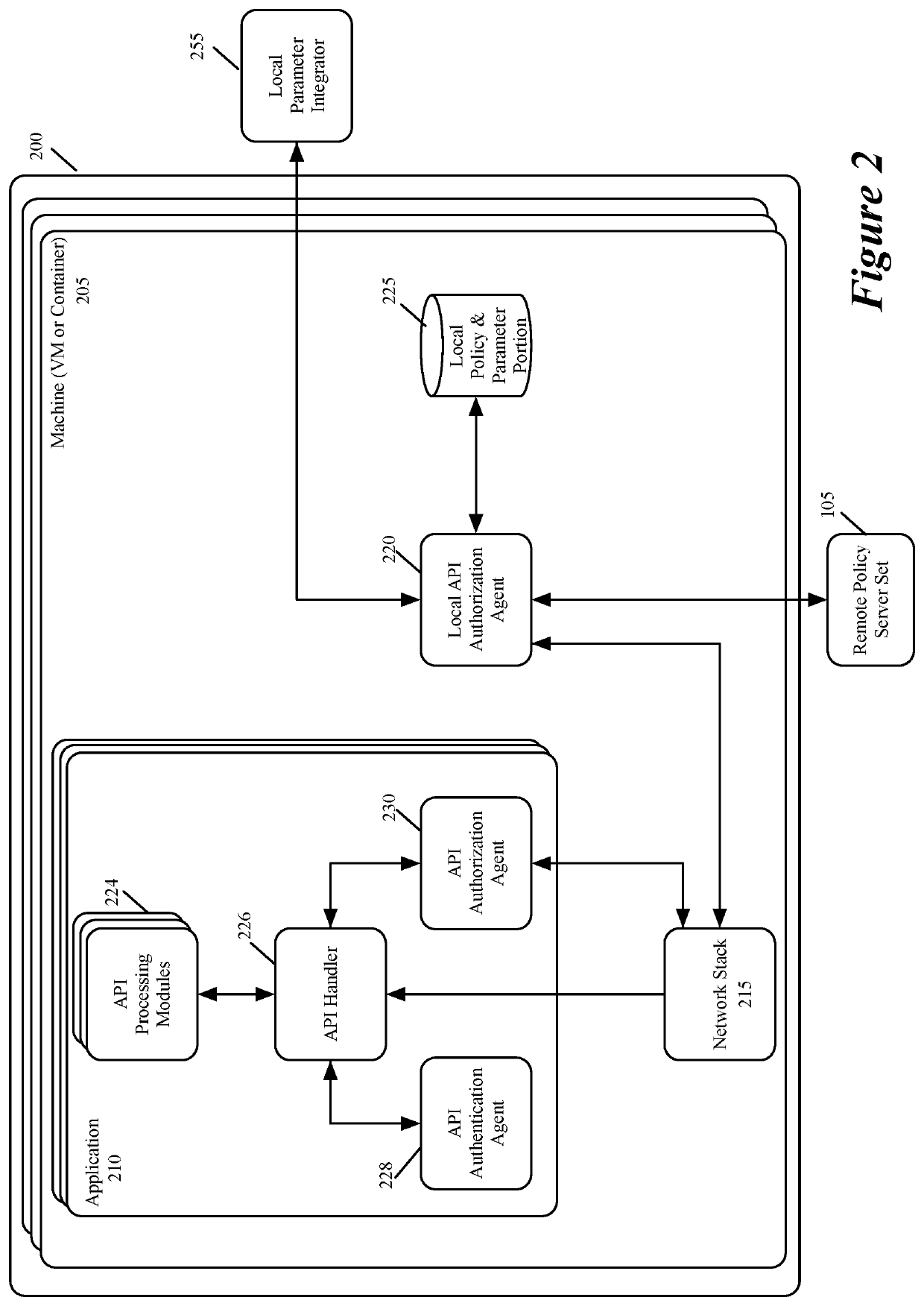
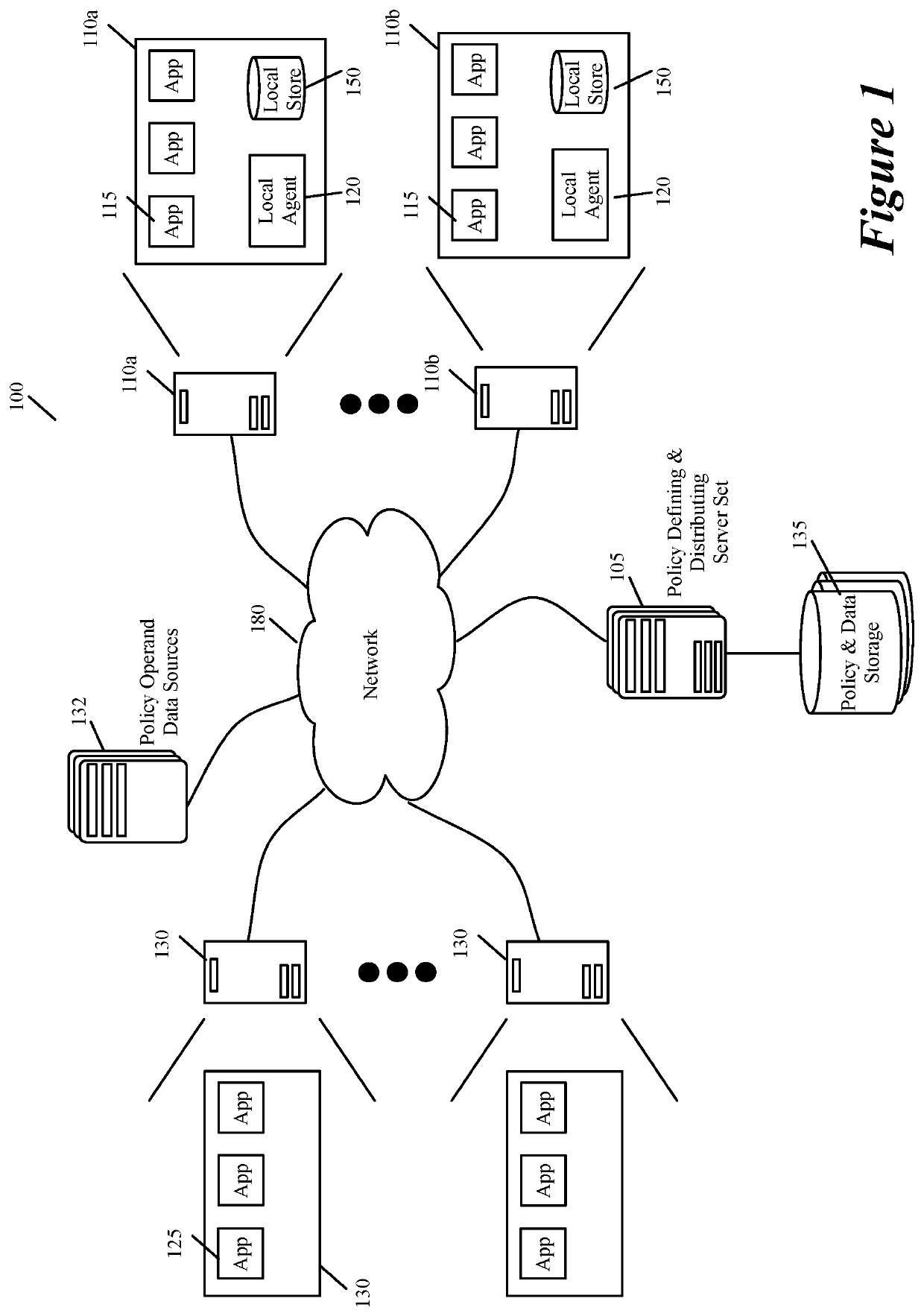
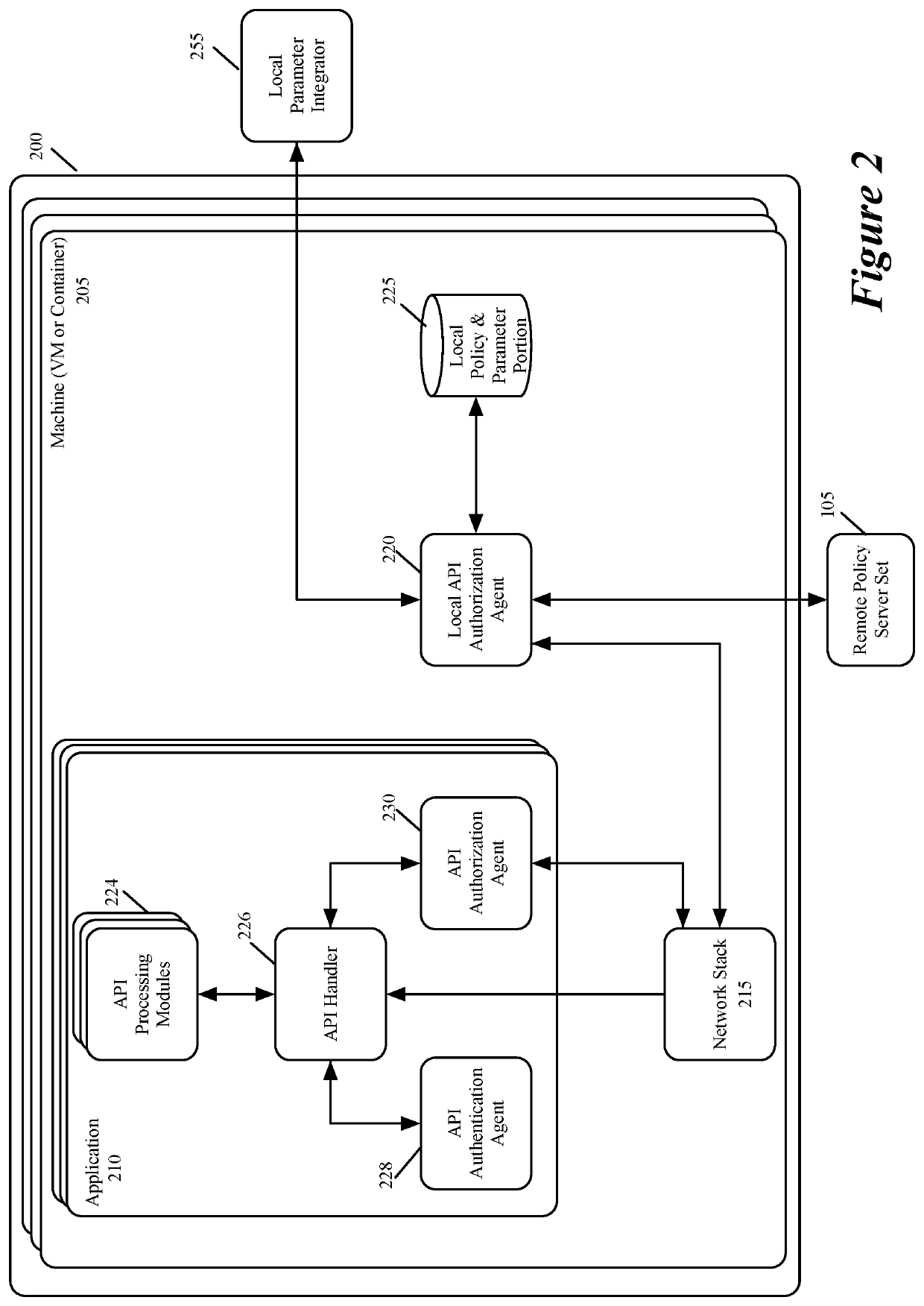
Method and apparatus for specifying API authorization policies and parameters
ActiveUS10592302B1Easy to changeHighly configurableInterprogram communicationDigital data authenticationApplication programming interfaceData center
Some embodiments of the invention provide a system for defining, distributing and enforcing policies for authorizing API (Application Programming Interface) calls to applications executing on one or more sets of associated machines (e.g., virtual machines, containers, computers, etc.) in one or more datacenters. This system has a set of one or more servers that acts as a logically centralized resource for defining and storing policies and parameters for evaluating these policies. The server set in some embodiments also enforces these API-authorizing policies. Conjunctively, or alternatively, the server set in some embodiments distributes the defined policies and parameters to policy-enforcing local agents that execute near the applications that process the API calls. From an associated application, a local agent receives API-authorization requests to determine whether API calls received by the application are authorized. In response to such a request, the local agent uses one or more parameters associated with the API call to identify a policy stored in its local policy storage to evaluate whether the API call should be authorized. To evaluate this policy, the agent might also retrieve one or more parameters from the local policy storage.
Owner:STYRA INC
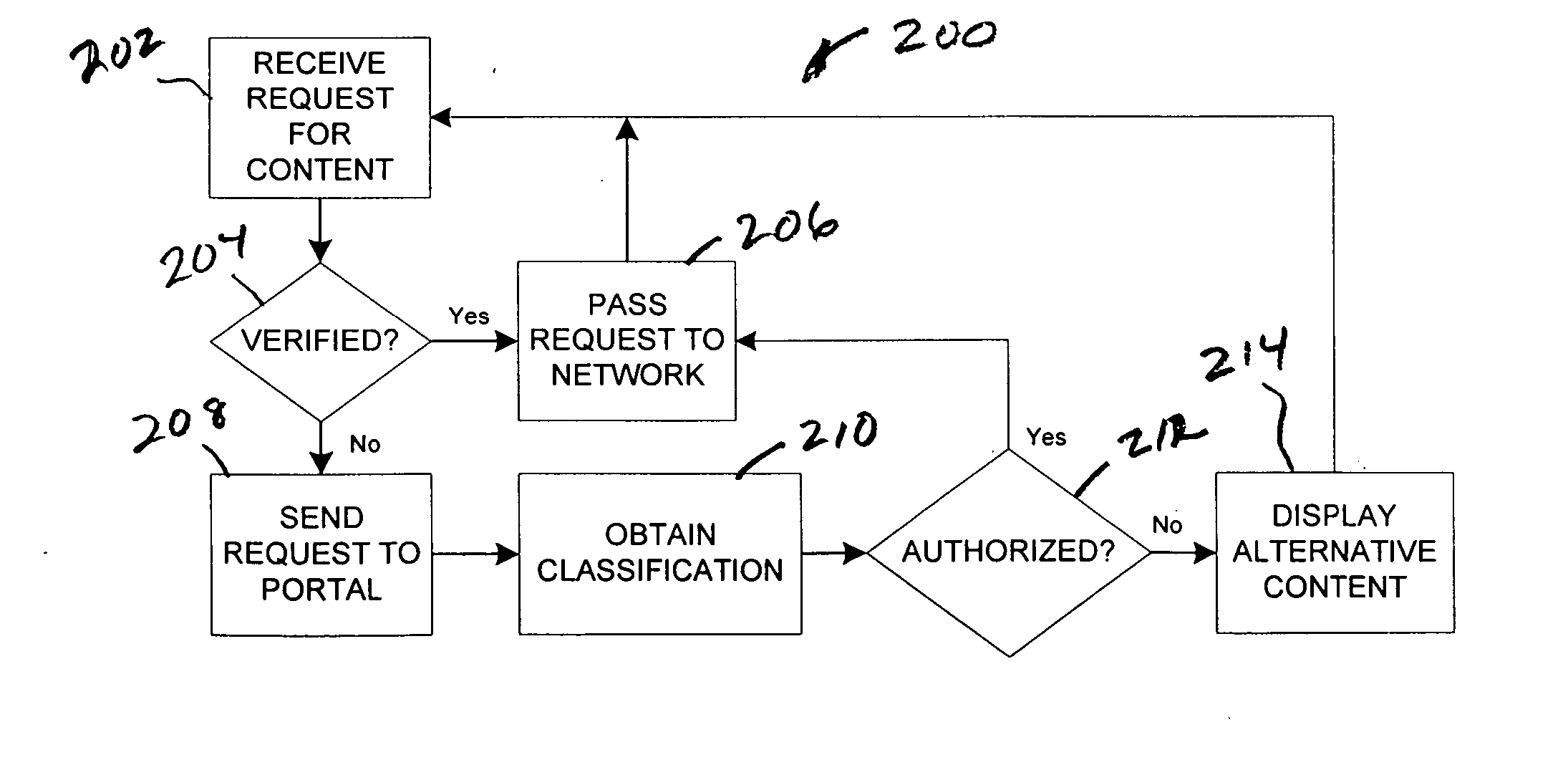
Method and apparatus for content filtering
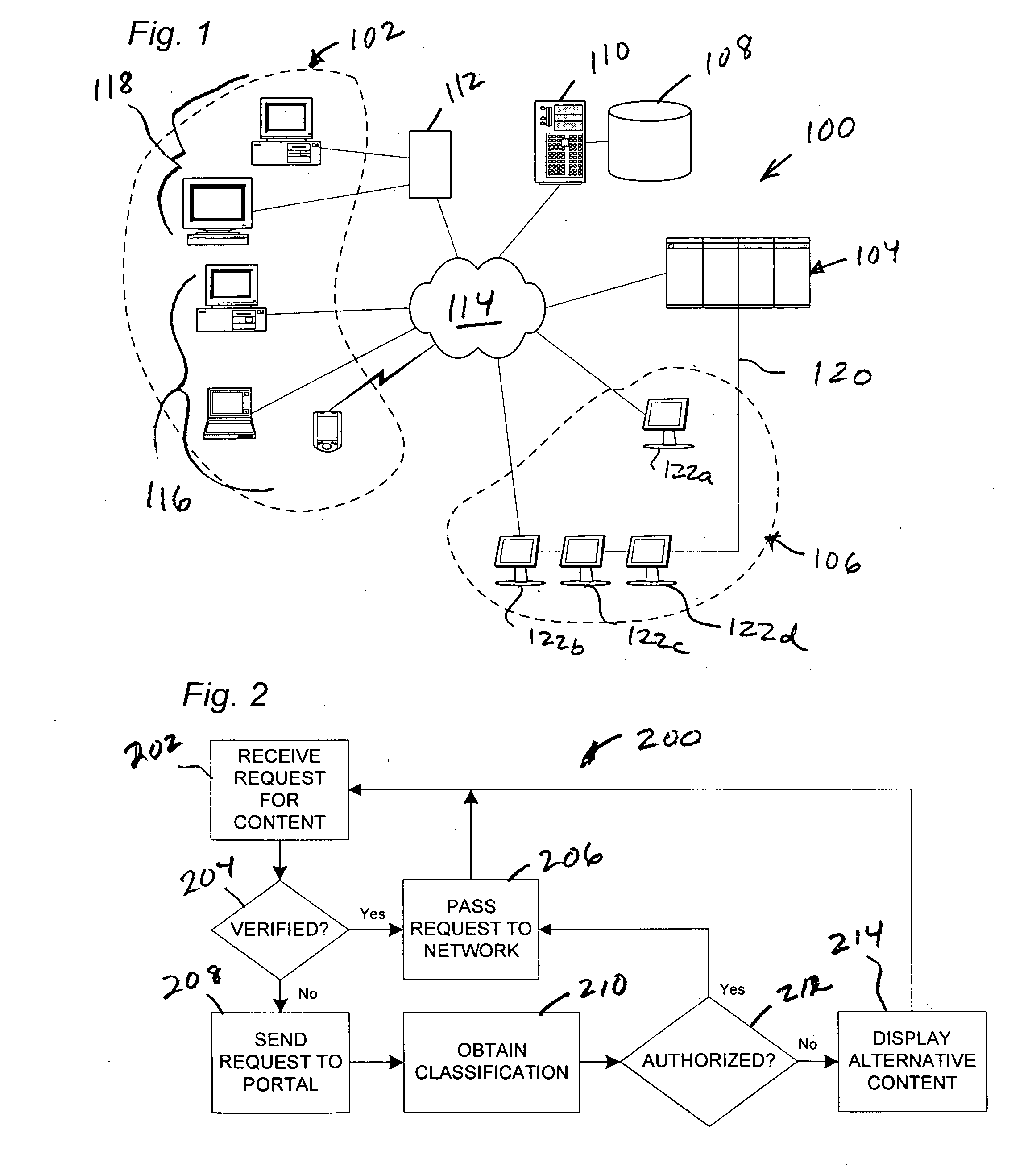
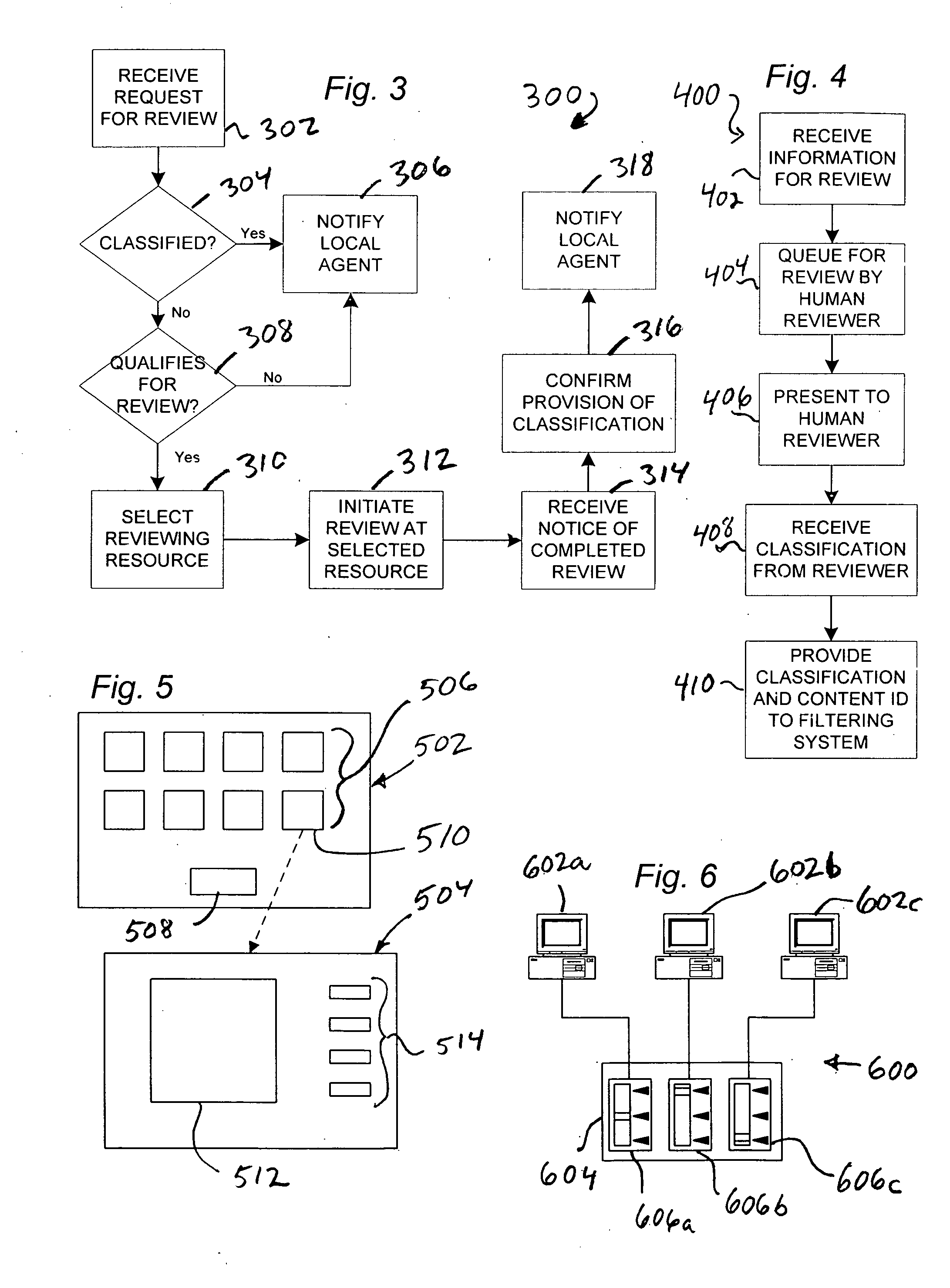
ActiveUS20050120042A1Accurate contentAdjustment of filtering convenientDigital data processing detailsTransmissionContent IdentifierResource network
A method for filtering content makes use of local filtering agents for end users, and a portal to a network of human reviewing resources. Local filtering agents request content classification for unclassified content. The portal routes requests from local agents to available human reviewing resources. A content classification is provided by the reviewing resources, and may be saved in association with a content identifier for future use. The method permits human review of content within a short period after review is requested. In an embodiment of the invention, a centrally-located switch is provided for controlling filtering levels at one or more user terminals.
Owner:INTELLECTUAL VENTURES I LLC
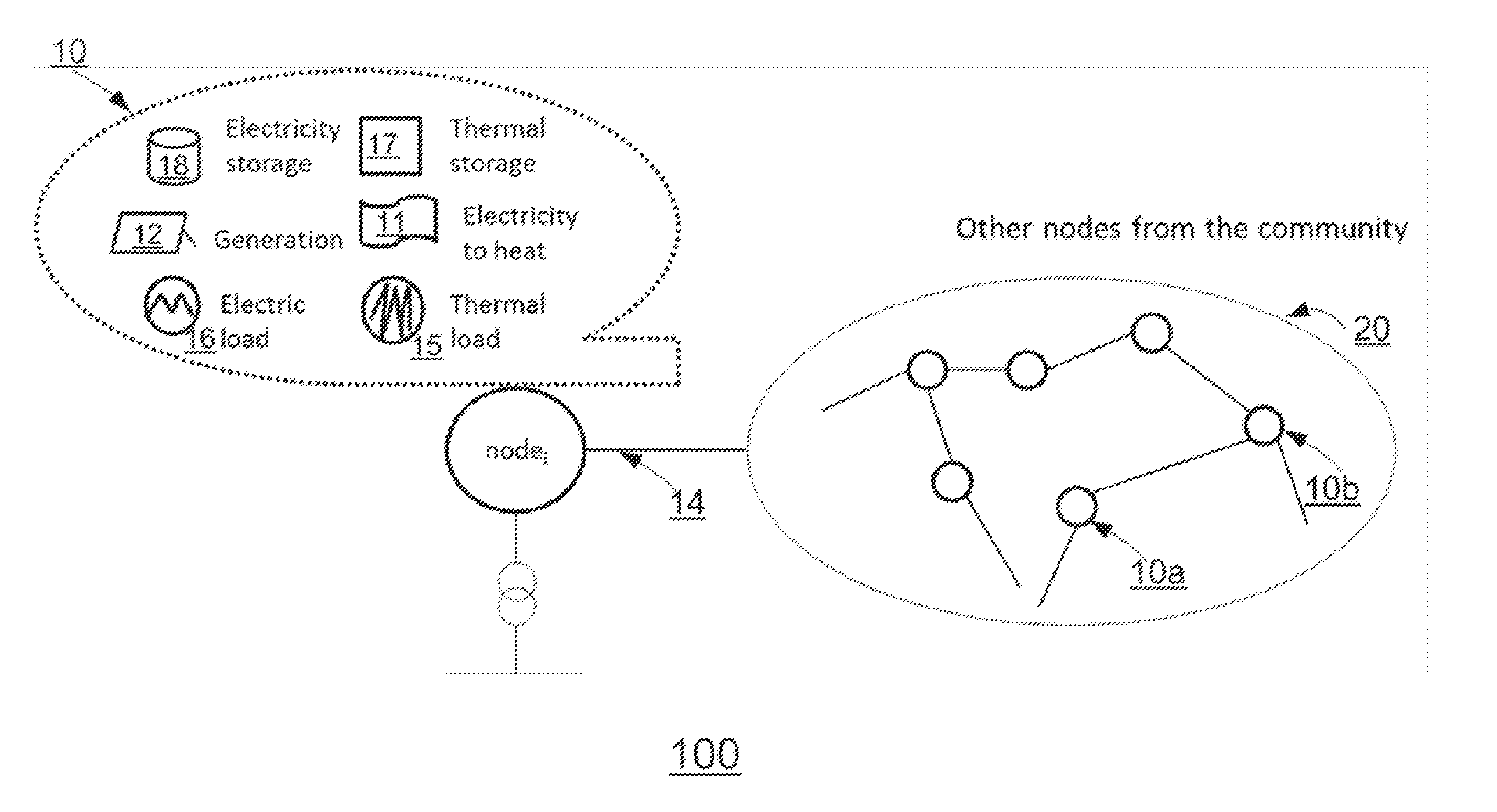
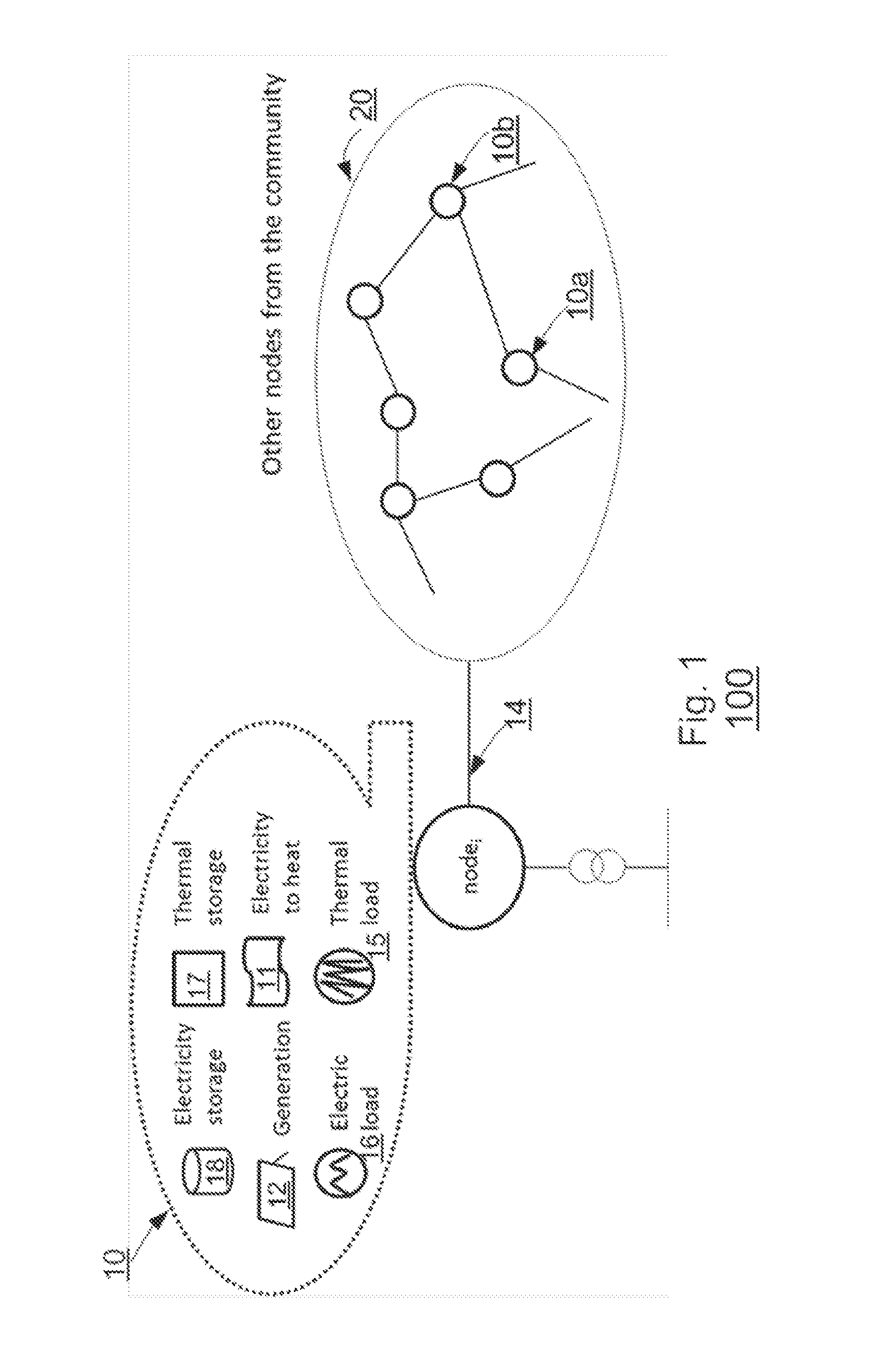
Collaborative balancing of renewable energy overproduction with electricity-heat coupling and electric and thermal storage for prosumer communities
ActiveUS20160011577A1Mechanical power/torque controlData processing applicationsElectric power transmissionHorizon
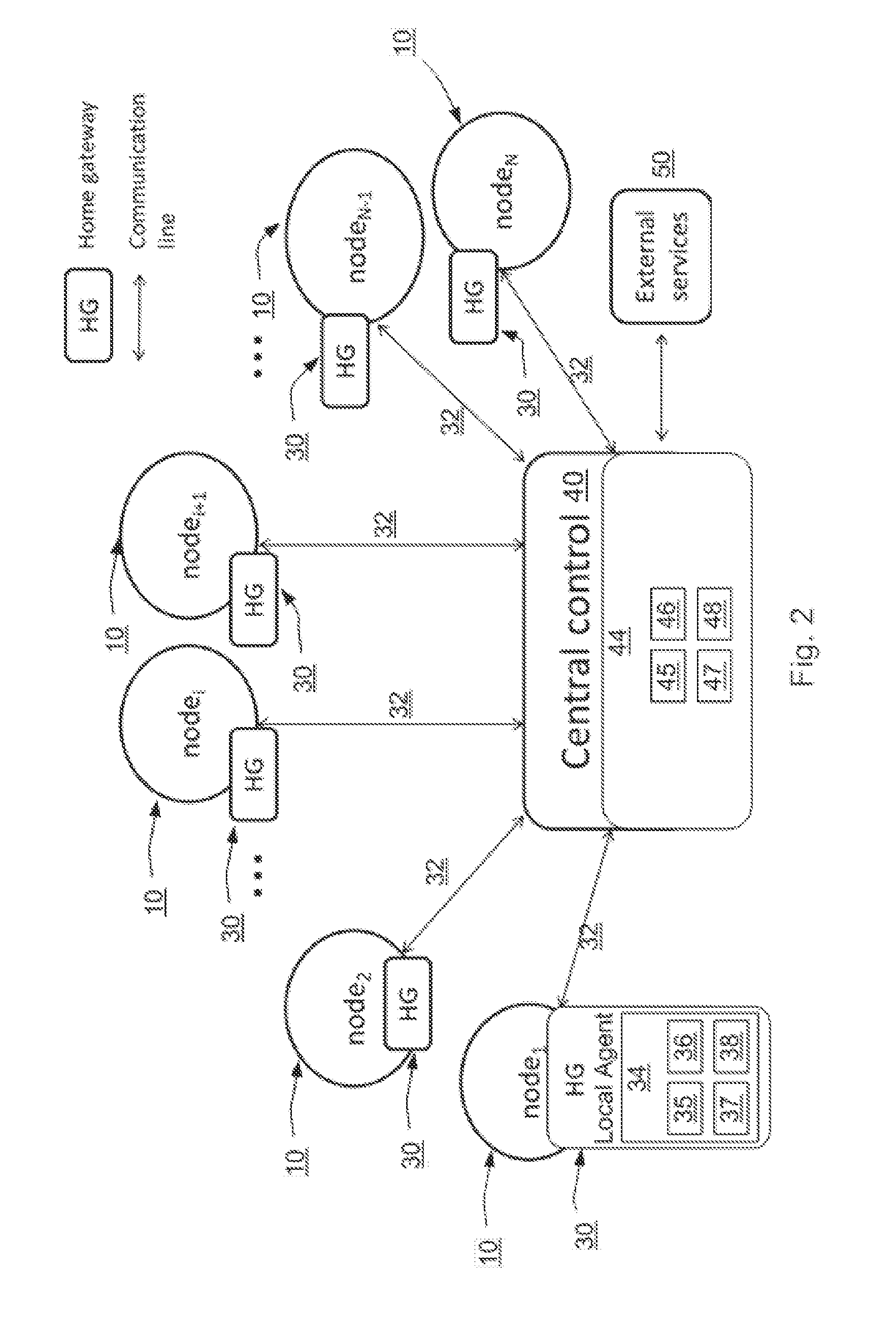
A system and method perform electricity and heat load balancing within a community of energy nodes. The system includes a central control device to solve an optimization problem over a planning horizon and to run an allocation algorithm. Local agent devices communicate with the central control device. Each local agent device receives input parameters from an energy node. Each energy node includes electricity generation equipment, electrical heat-generating equipment, and power transmission equipment, electricity storage equipment and thermal storage equipment. The local agent devices operate the electrical heat-generating equipment based on an allocation instruction received from the central control device. The central control device receives status information from the local agent devices to determine an amount of energy to be converted from electricity to heat by the electrical heat-generating equipment of the energy nodes, to provide the allocation instruction to the energy nodes.
Owner:NEC CORP
Method of encrypting data and files for browser
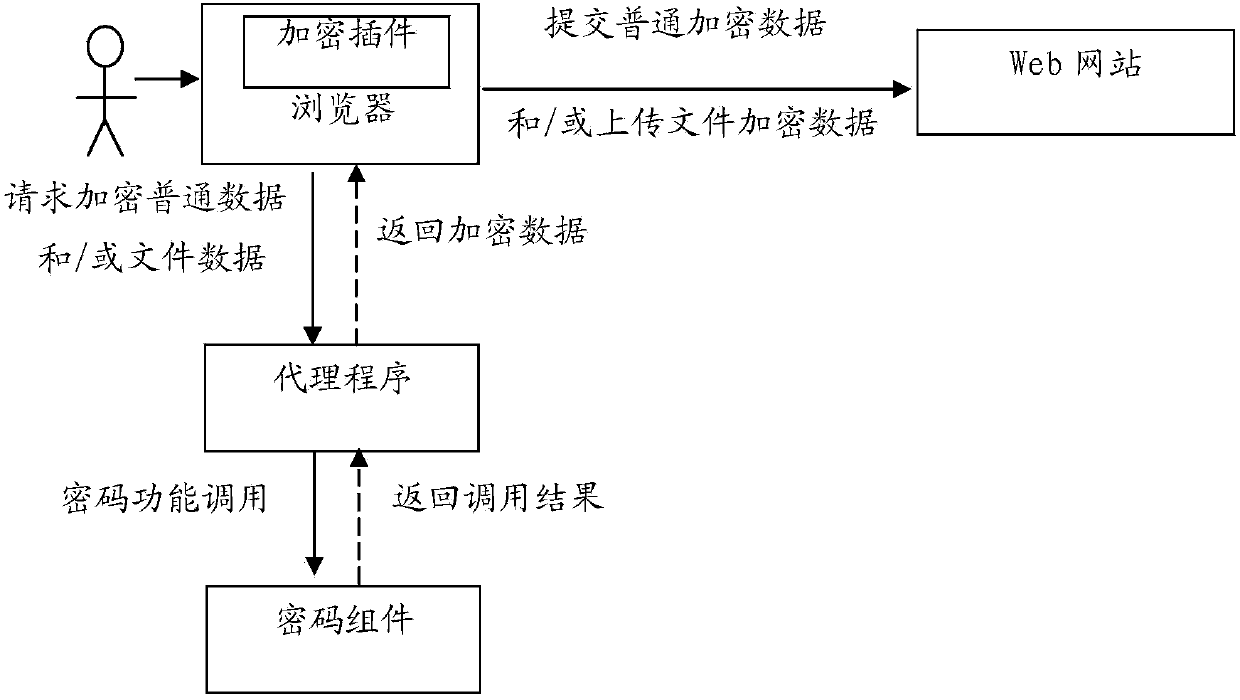
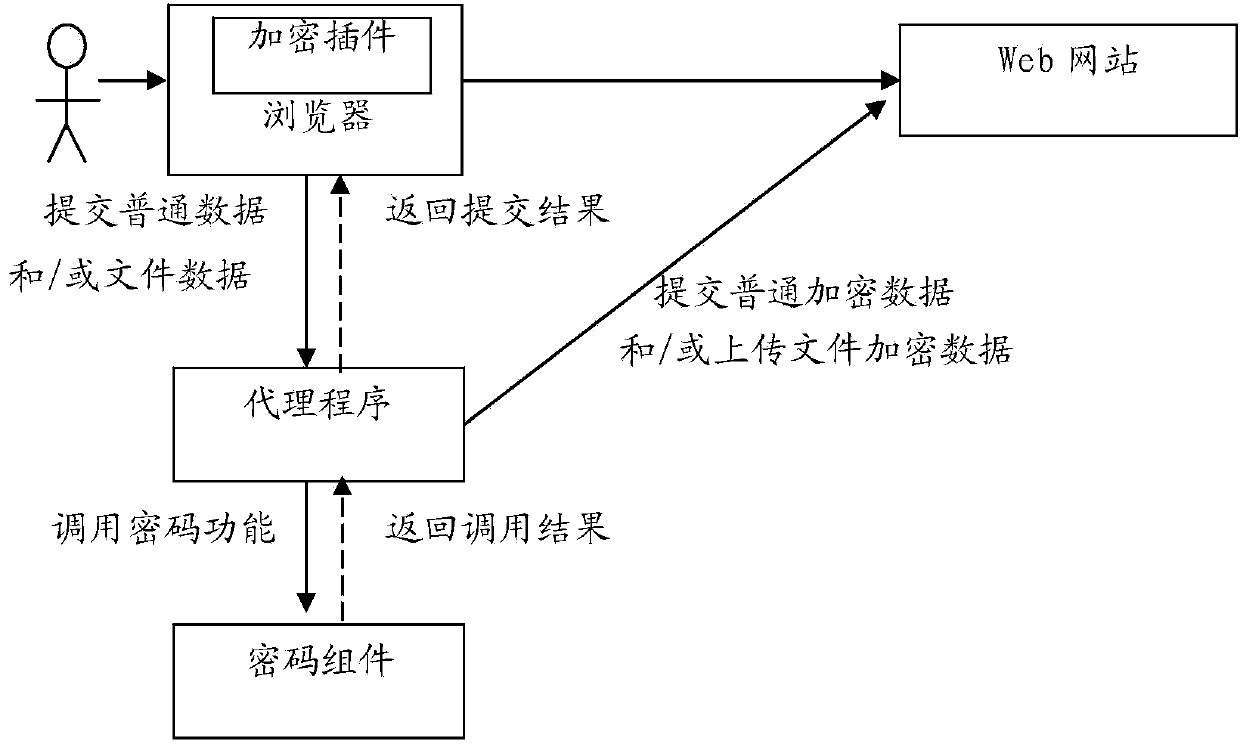
The invention relates to a method of encrypting data and files for a browser. The method comprises the following steps that an encryption plug-in modifies a code for submitting data and / or uploading a file part in a page code, which returns to a user browser, of a Web website; when a user submits the data and / or uploads a file through the browser, the modified page code for submitting the data and / or uploading the file submits data to be submitted or the file data to be uploaded by the user to a local agent program of the user browser, the agent program calls a password module to encrypt the data to be submitted or the file data to be uploaded, and then the browser submits or uploads the encrypted data or the file data to the Web website, or the agent program submits or uploads the encrypted data or the file data to the Web website. According to the method, the submitted data and / or the uploaded file data can be encrypted without modifying the Web website and calling the plug-in of the browser.
Owner:WUHAN UNIV OF TECH
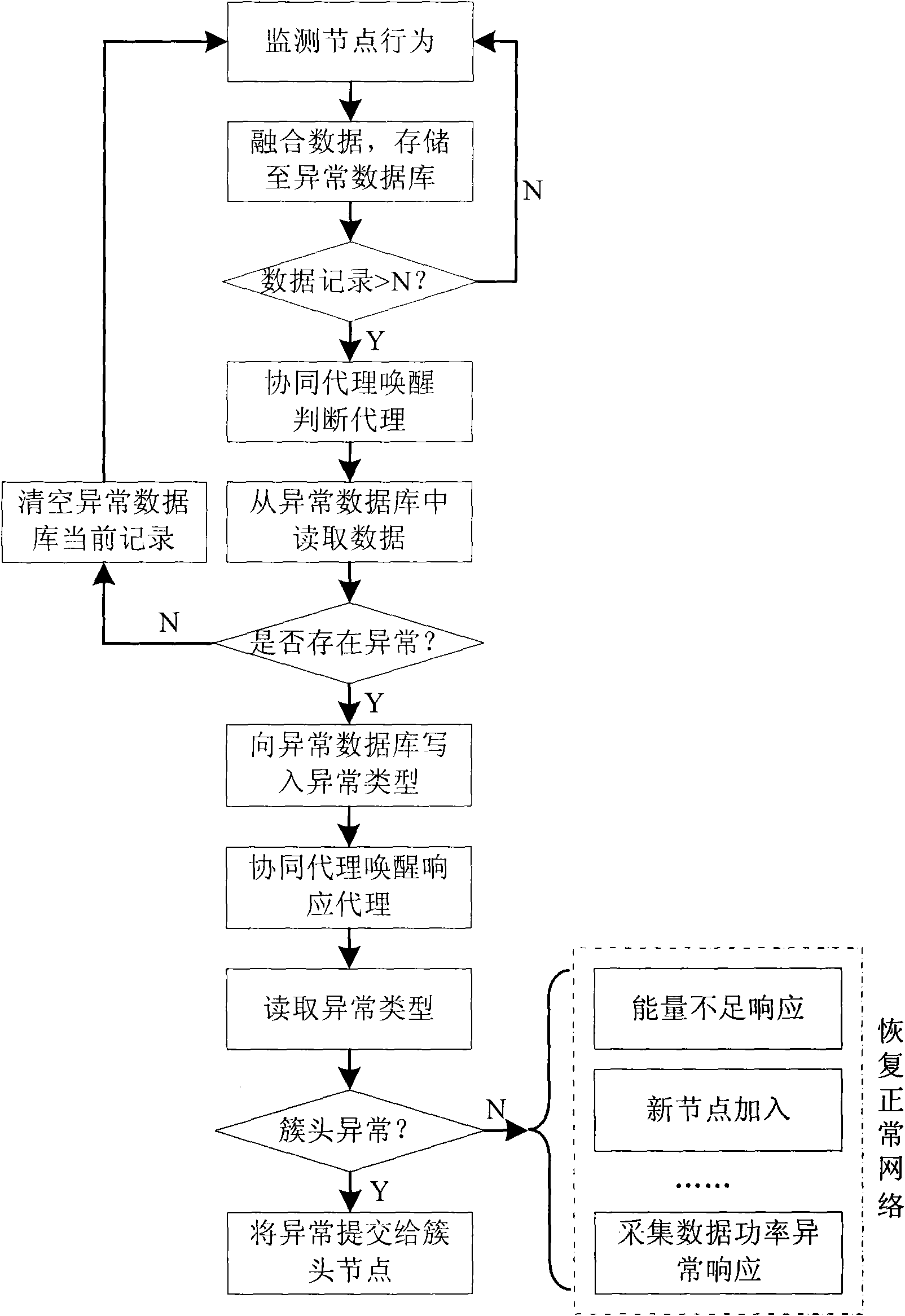
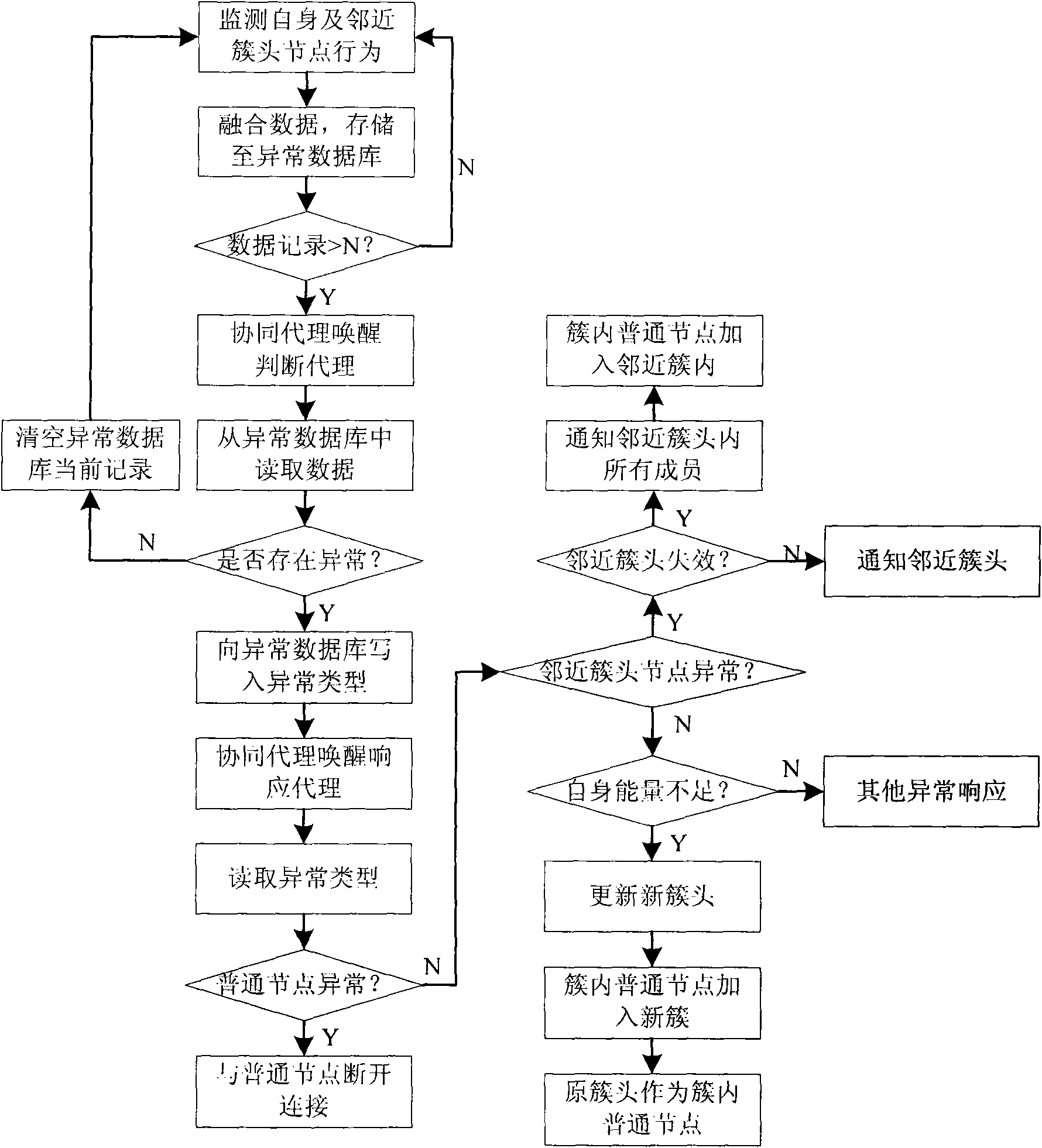
Multi-agent anomaly detection method based on Internet of things
InactiveCN101860883AGet back up and running quicklyImprove the problems caused by failureEnergy efficient ICTNetwork topologiesBalancing networkFault tolerance
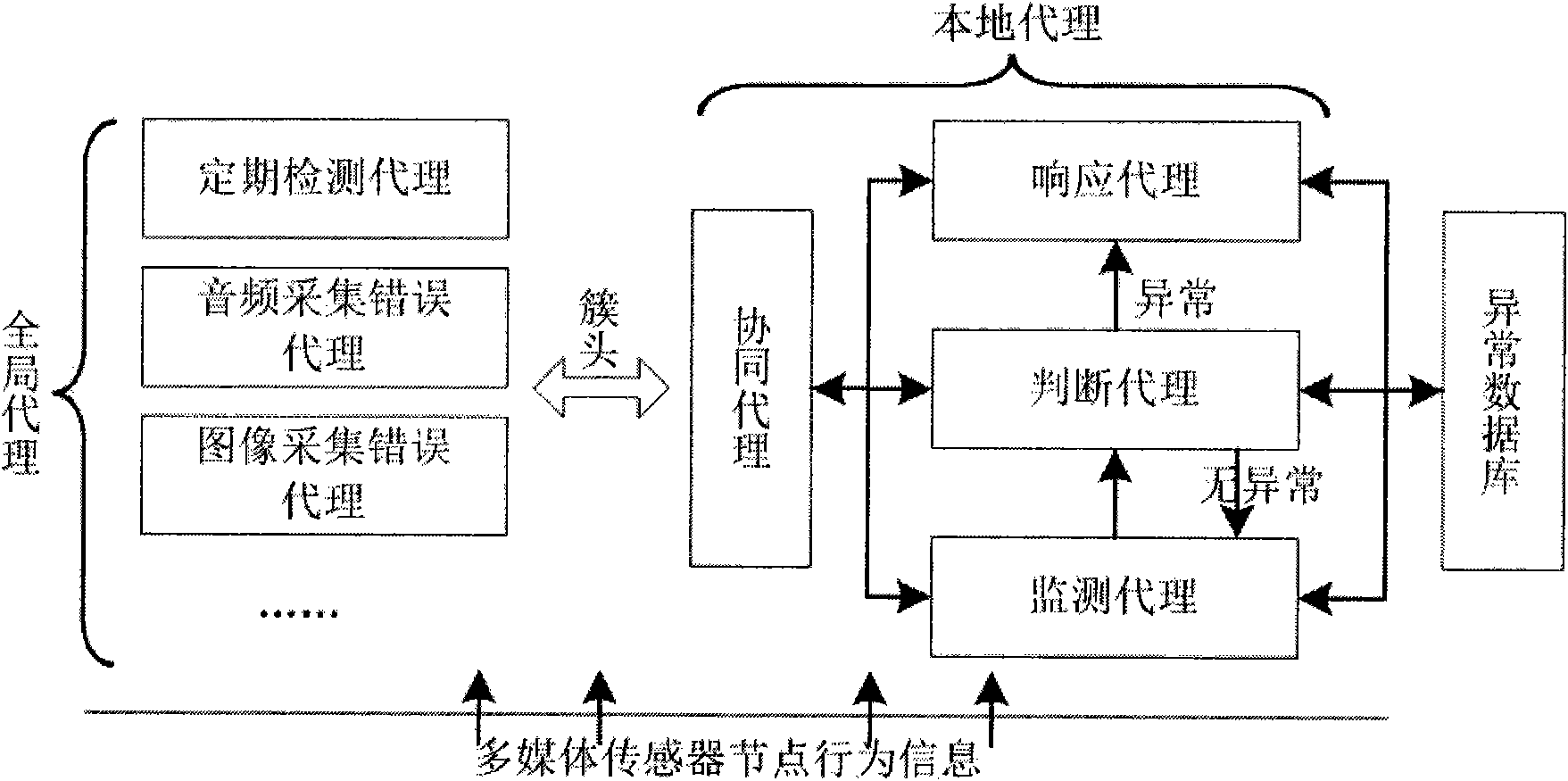
The invention relates to a multi-agent anomaly detection method based on the Internet of things, which is an anomaly detection method for a wireless multimedia sensor network. In the method, the multi-agent technology is introduced mainly to solve the problem of the abnormal situation in the operating process of the wireless multimedia sensor network. The scheme of the multi-agent anomaly detection system is characterized in that: coordinating through a local agent, and monitoring a local sensor network autonomously, independently and promptly; when the terminal finds that the audio / video and other data are abnormal or the network needs regular maintenance, detecting whether the network is abnormal through issuing global agency; and if the abnormal situation occurs to the network, repairing the network dynamically and autonomously to ensure the correct operation of the network. The method of the invention can promptly detect whether the abnormal situation occurs to the network, and repair the network within a limited period to restore the normal operation of the network. Moreover, the invention can reduce the network congestion rate, balance the energy consumption of the network, efficiently utilize resources of the total network, improve the fault tolerance of the network and ultimately prolong the life cycle of the entire network.
Owner:NANJING UNIV OF POSTS & TELECOMM
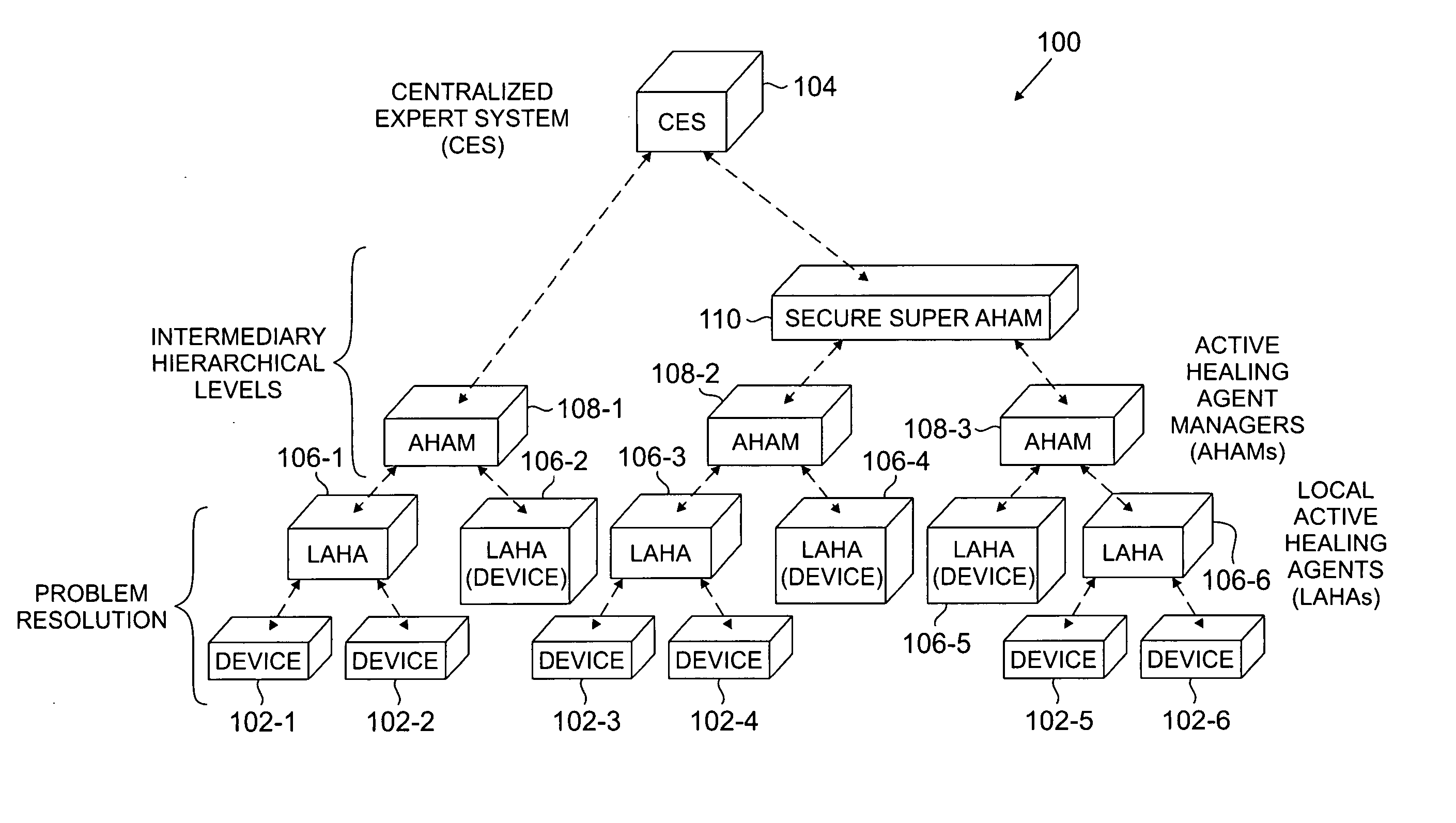
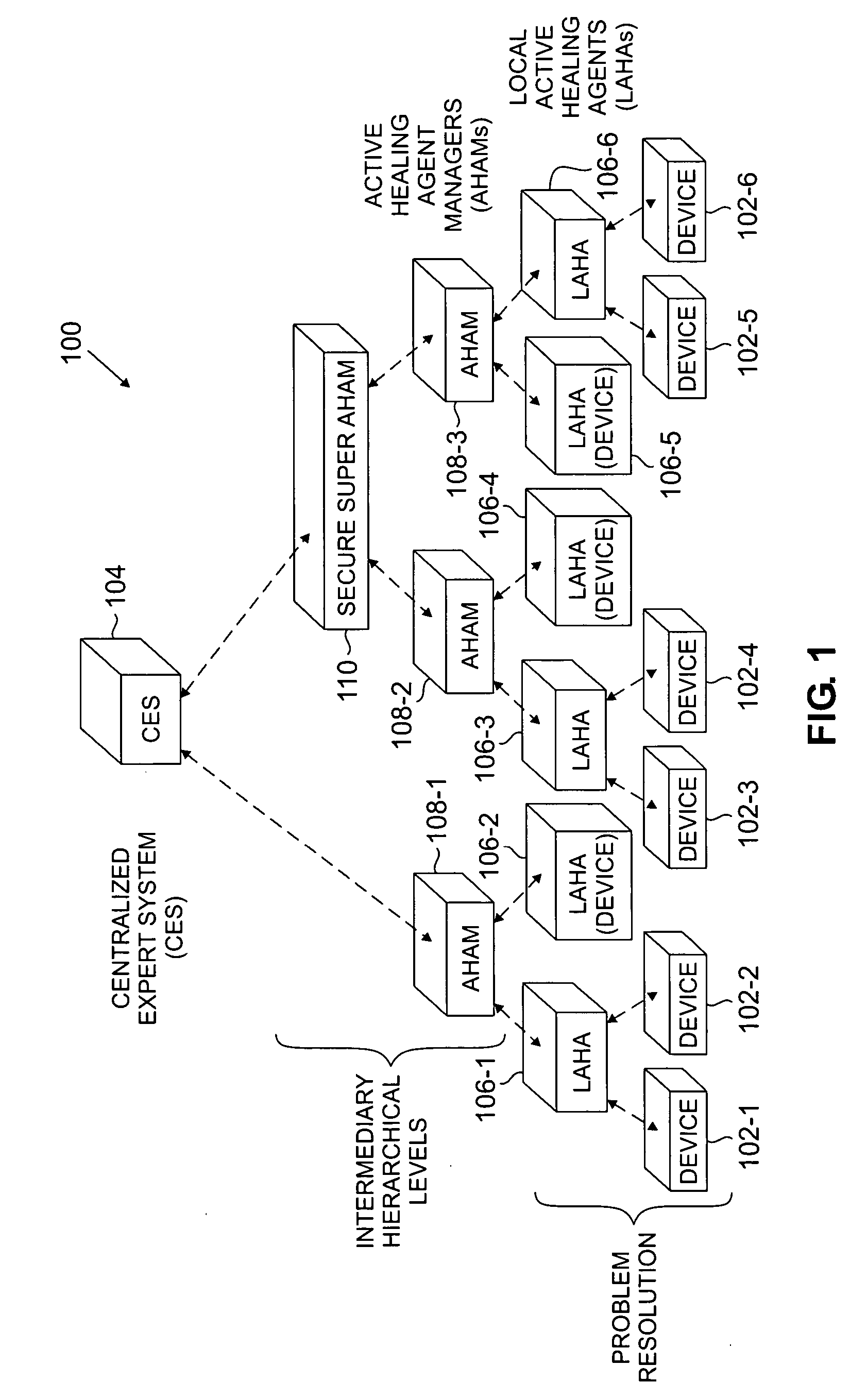
Distributed expert system for automated problem resolution in a communication system
ActiveUS20060069957A1Avoid security issuesAvoiding cost issueNon-redundant fault processingTransmissionCommunications systemProcessing element
A communication system processing element comprises a processor coupled to a memory and implements at least a portion of a distributed expert system. The distributed expert system is arranged in at least two hierarchical levels, including an upper level comprising a central controller, and a lower level comprising a plurality of local agents each associated with one or more communication devices of the system.
Owner:AVAYA INC
Media positioning, searching method and system
InactiveCN101394423AImprove efficiencyHigh speedTelevision systemsSelective content distributionInformation repositoryNetwork topology
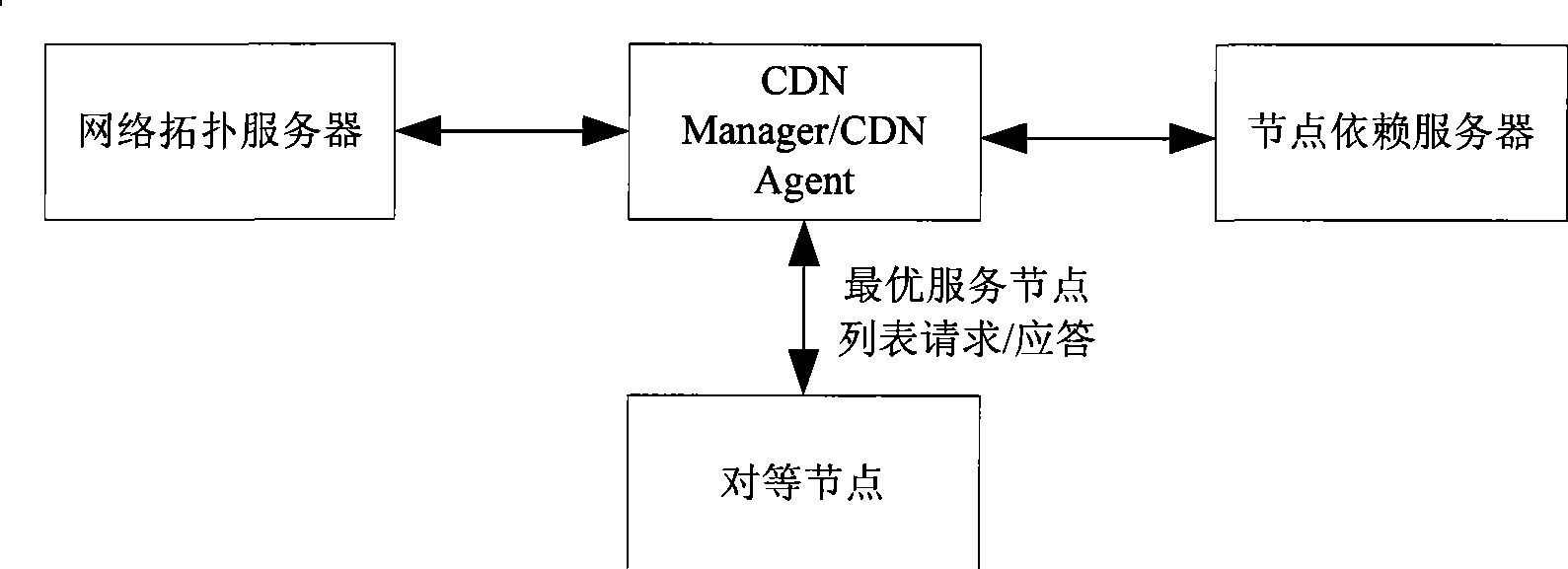
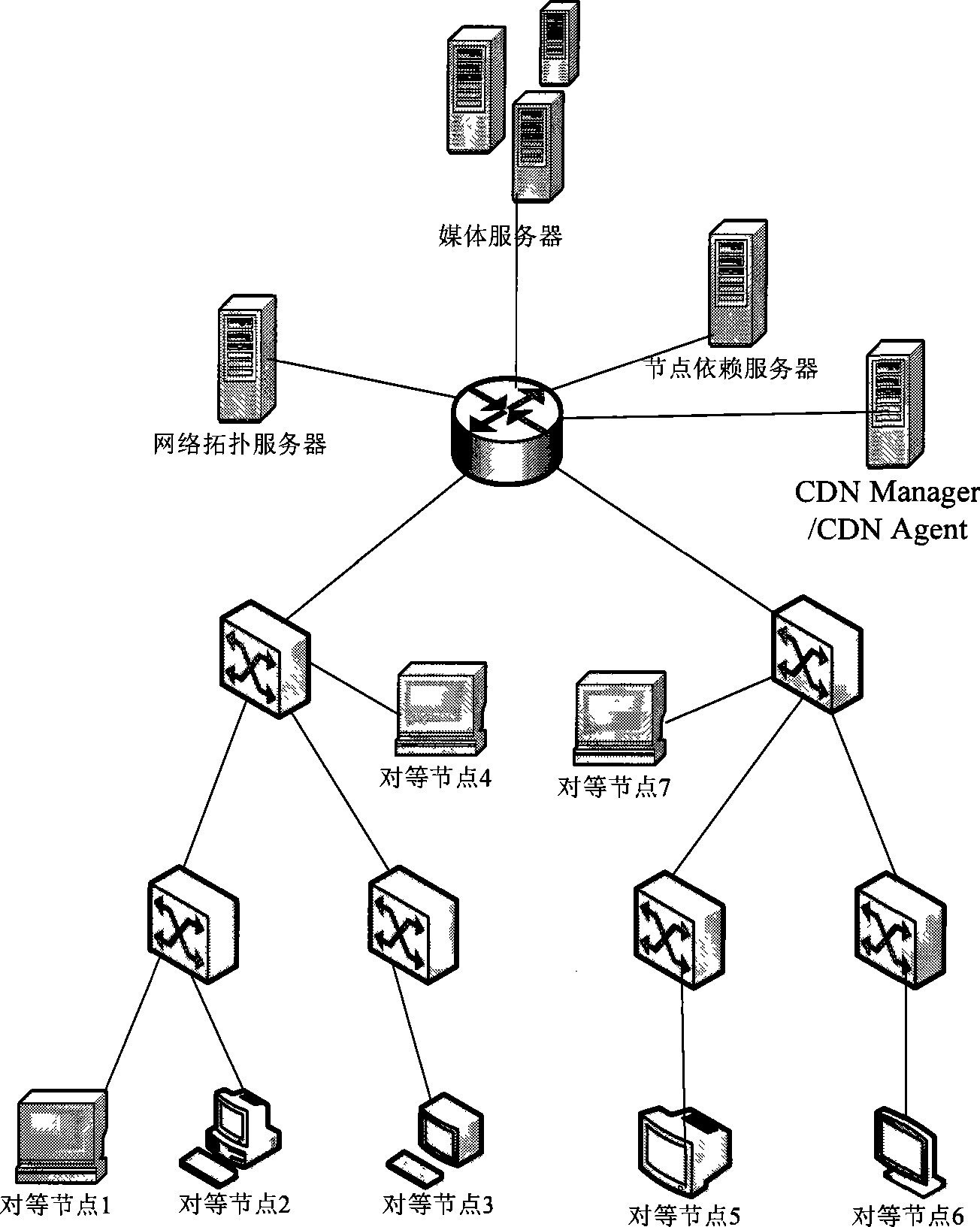
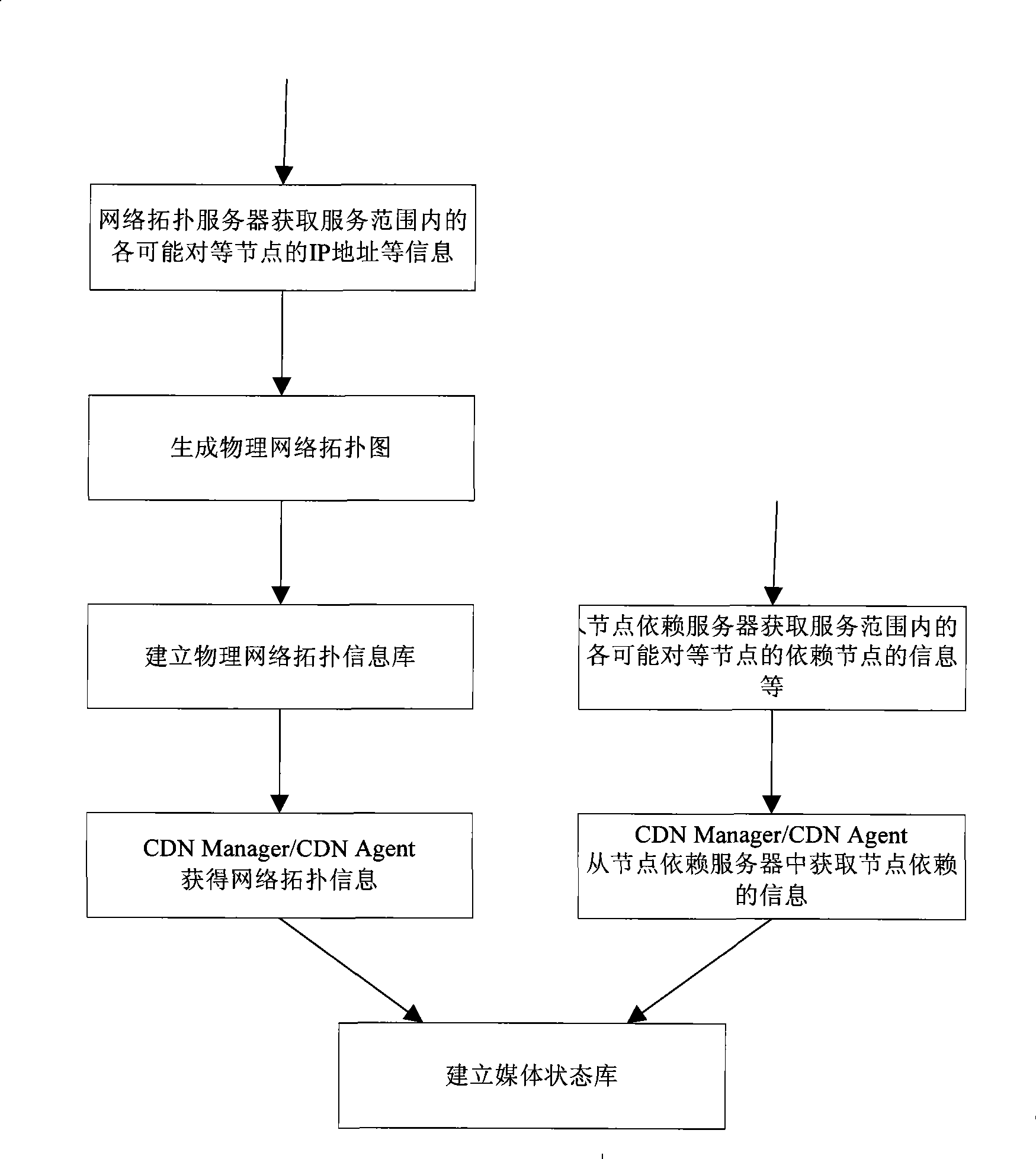
The invention provides a media location and searching method and a system. Based on node dependence and network topologic information, the method relates to a CDN Manager / CDN Agent and peer nodes. The CDN Manager / CDN Agent at least comprises node dependence information, network topologic information and media location information, and a global manager and a local agent CDN Manager / CDN Agent acquire the node dependence information and the network topologic information of each peer node in a service range to generate a physical network topologic graph. A physical network topologic information library is constructed in the network topologic server, and a media state library is established in the global manager and the local agent CDN Manager / CDN Agent. The method can fully exert the advantages of P2P technology, and can improve the delivery efficiency and speed of IPTV media.
Owner:ZTE CORP
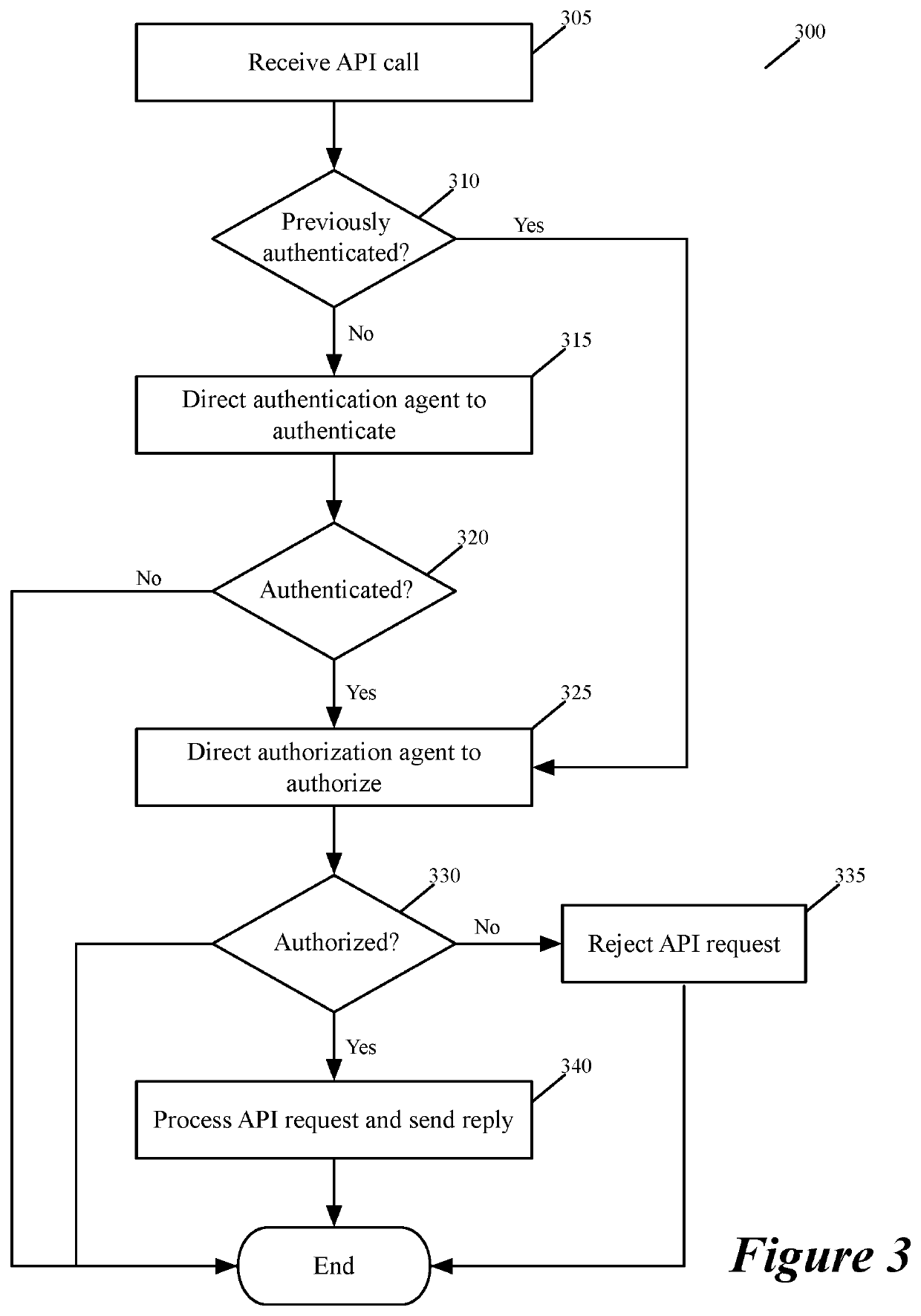
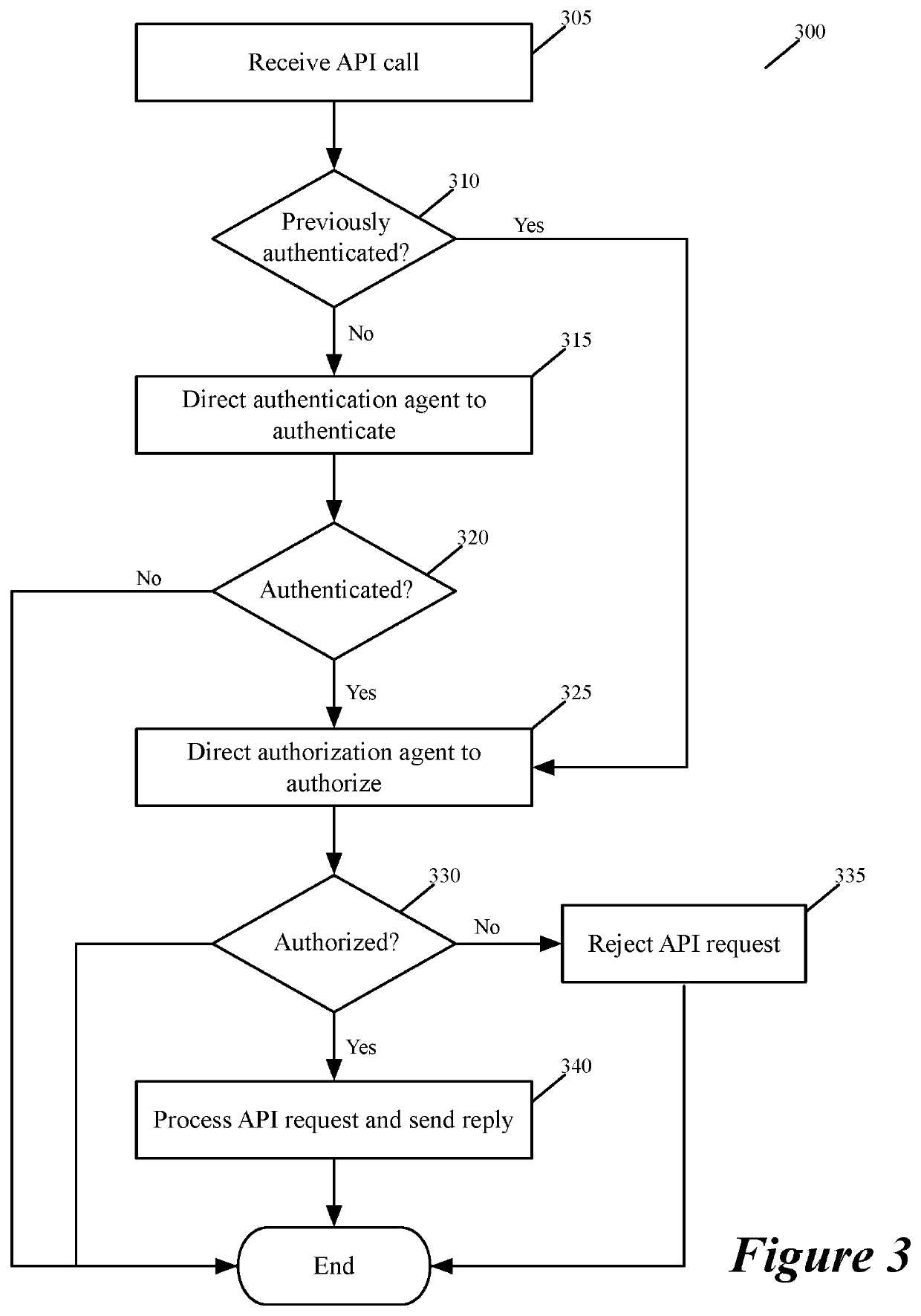
Method and apparatus for authorizing API calls
ActiveUS10990702B1Highly configurableInterprogram communicationDigital data protectionApplication programming interfaceApplication procedure
Some embodiments of the invention provide a system for defining, distributing and enforcing policies for authorizing API (Application Programming Interface) calls to applications executing on one or more sets of associated machines (e.g., virtual machines, containers, computers, etc.) in one or more datacenters. This system has servers that act as a logically centralized resource for defining and storing policies and parameters for evaluating these policies. The servers enforce these policies and distribute the policies and parameters to policy-enforcing local agents that execute near the applications that process the API calls. From an associated application, a local agent receives API-authorization requests to determine whether API calls received by the application are authorized. In response to such a request, the local agent uses one or more parameters associated with the API call to identify a policy stored in its local policy storage to evaluate whether the API call should be authorized. To evaluate this policy, the agent also retrieves one or more parameters from the local policy storage.
Owner:STYRA INC
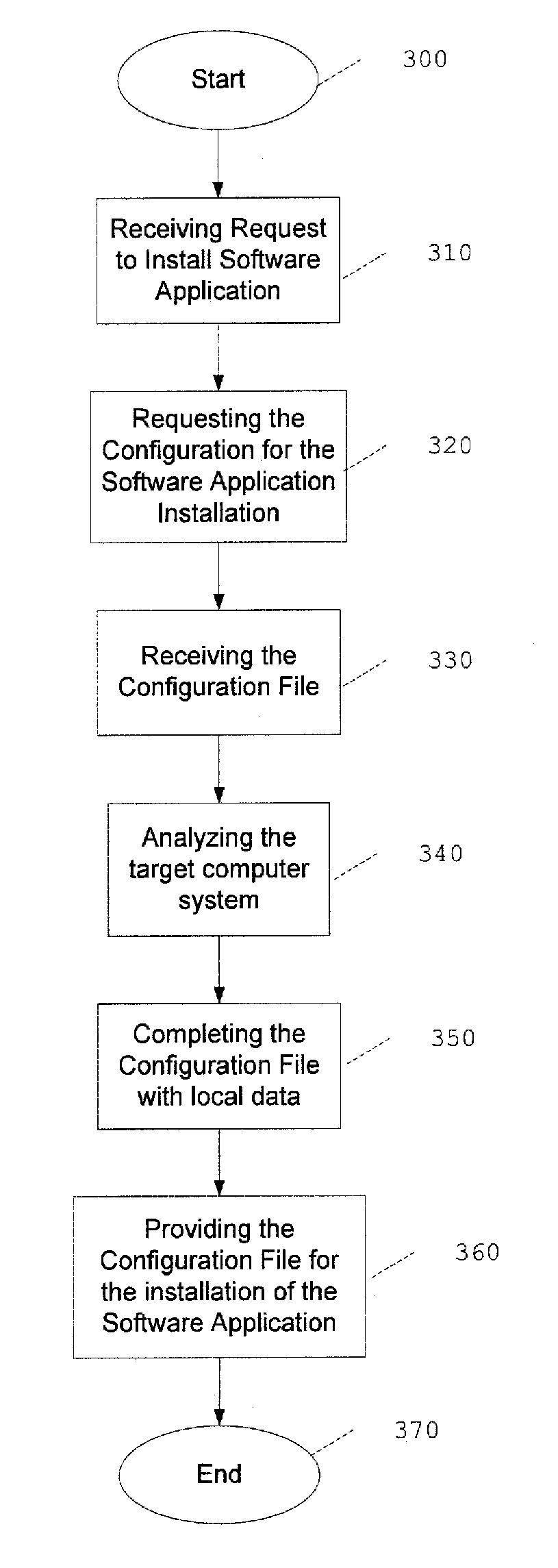
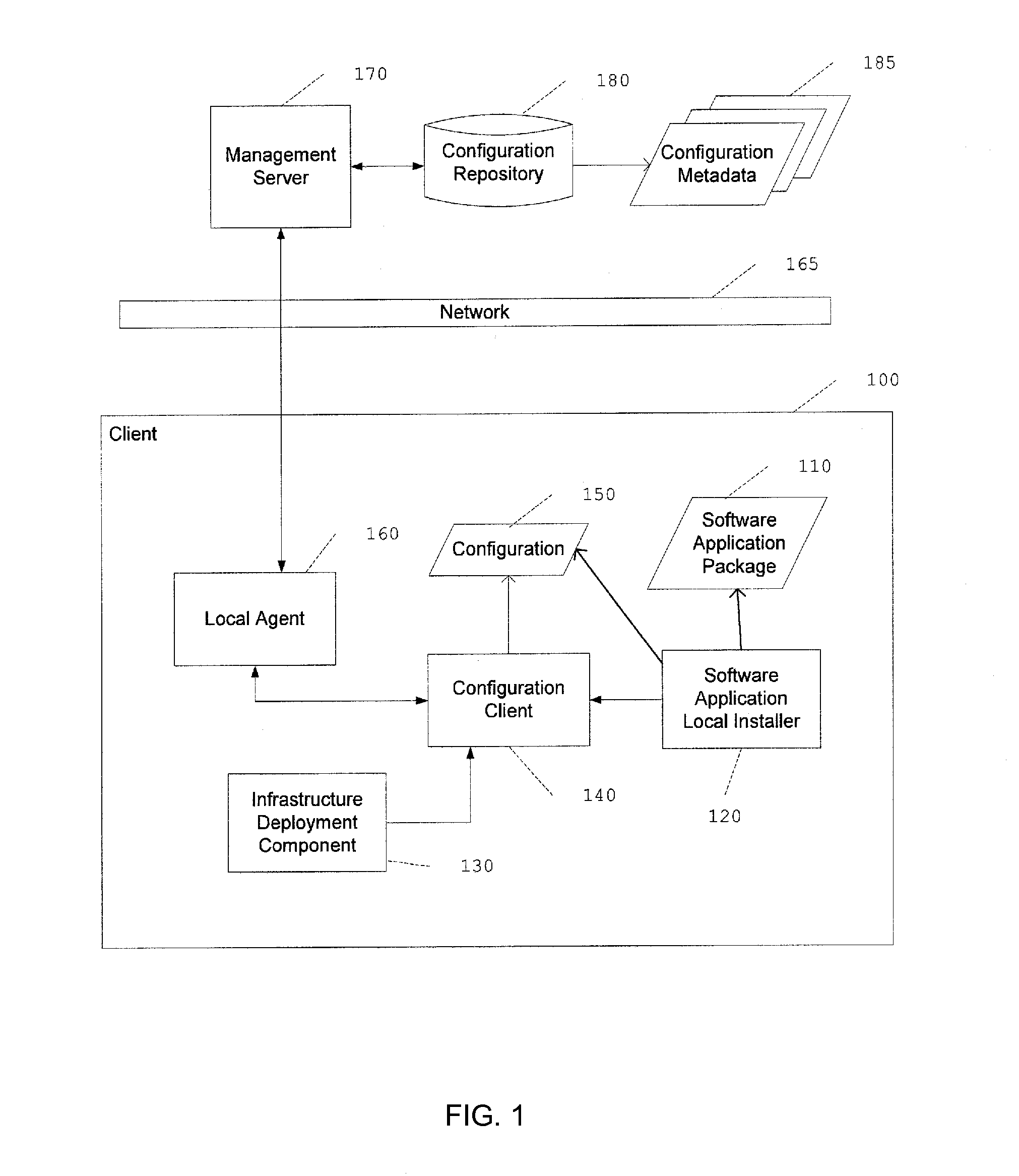
System and method for configuring a computer system for a software package installation
InactiveUS20120005465A1Configure the software applicationEasy and consistentDigital computer detailsProgram loading/initiatingClient-sideSoftware package
A request from an installer of a software application to configure the computer system for installation of the software application is received at a configuration client. Upon receiving the request, a message is sent to a local agent of the computer system to request a configuration for the installation of the software application. The message includes an identifier of the software application used by a configuration management server to identify the configuration corresponding to the software application. A configuration element is received from the local agent in response to the message. The configuration element includes a variable for holding a value that represents a characteristic of the computer system. The value of the variable is configured as a function of the computer system. The configuration element, including the configured variable value, is provided to the installer of the software application and is used for the installation of the software application.
Owner:IBM CORP
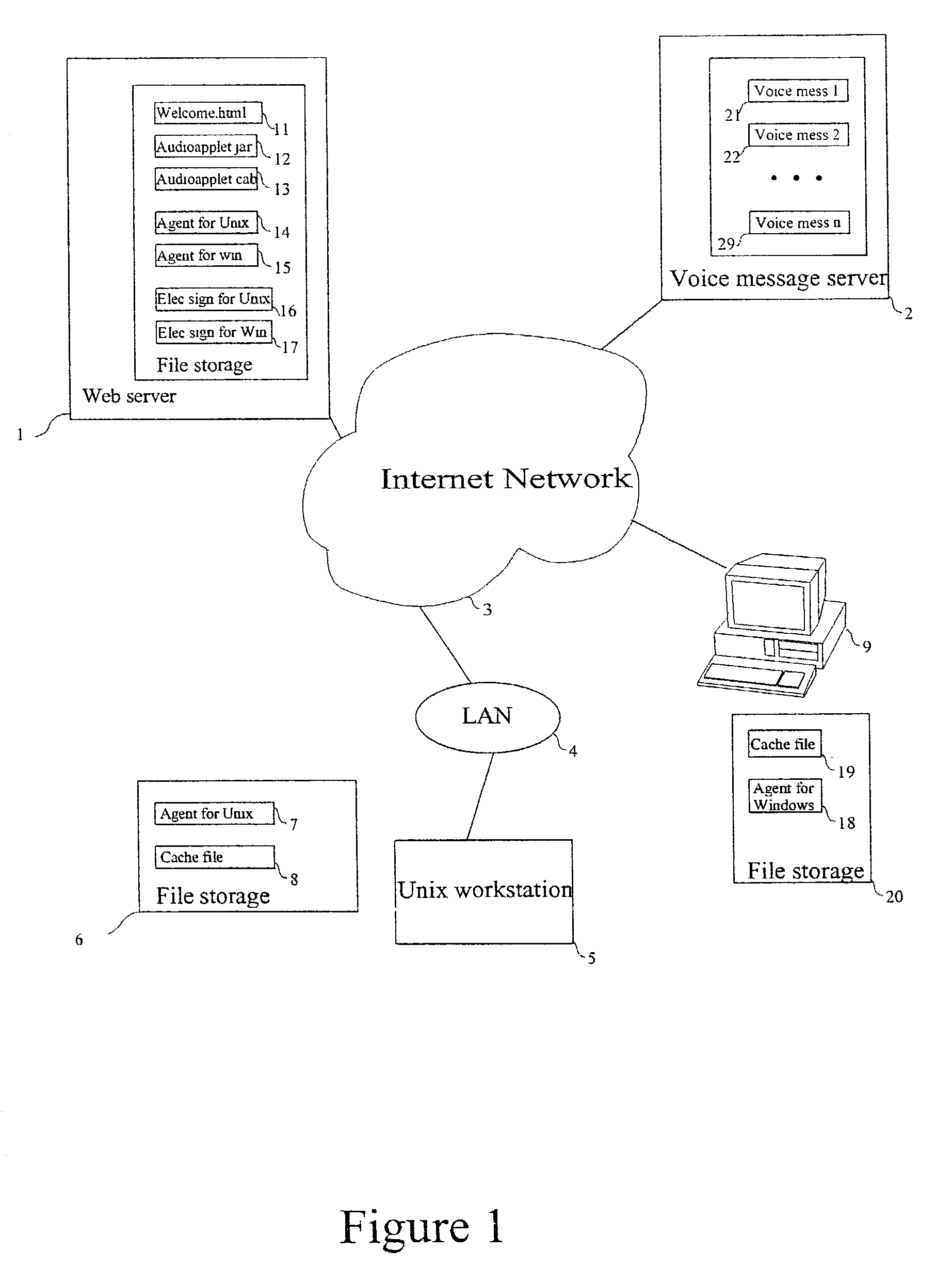
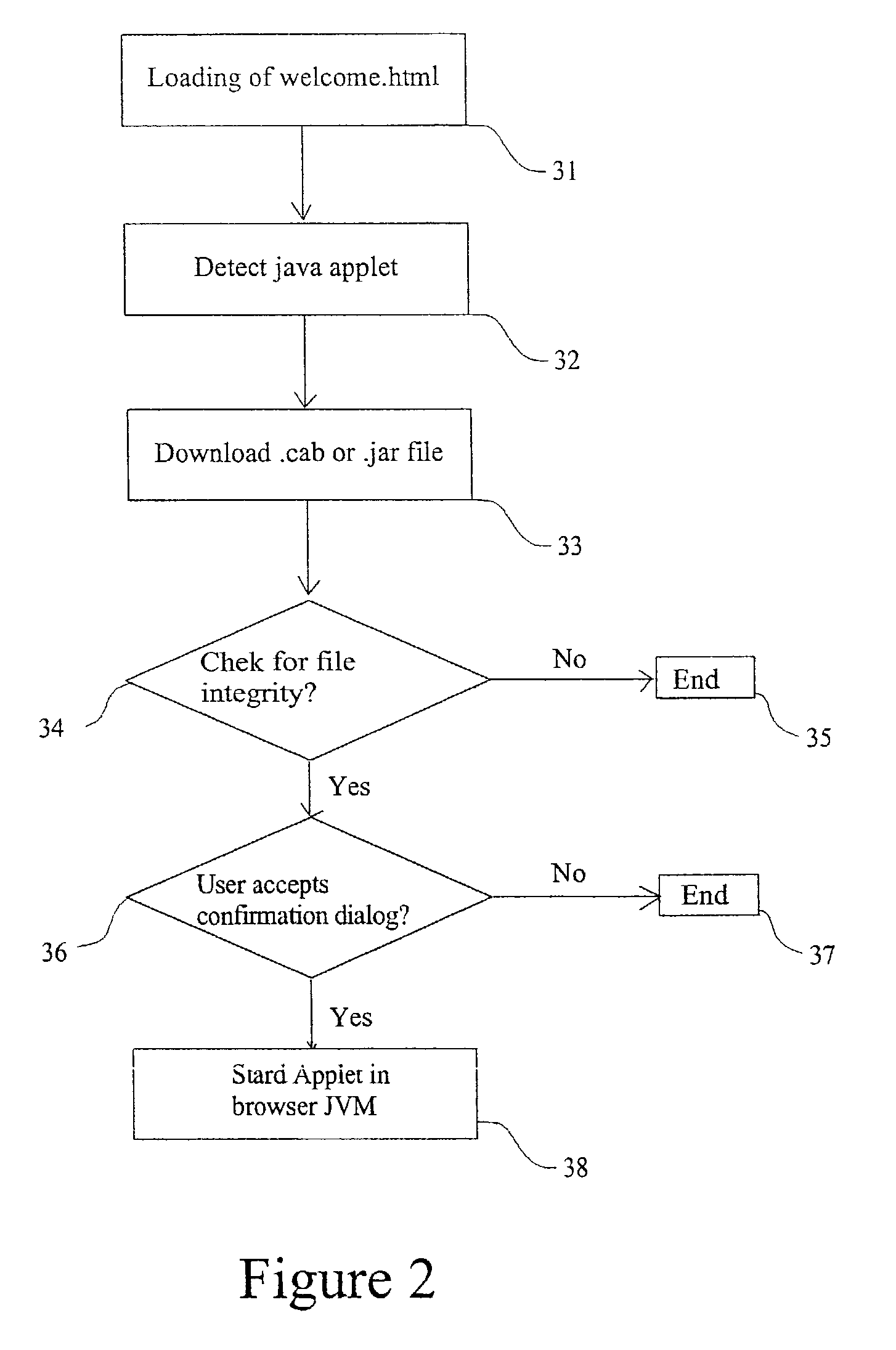
Process of communication between an applet and a local Agent using a Socket communication channel
InactiveUS7428570B2Improve developmentImprove cooperationDigital data processing detailsInterprogram communicationApplication softwareClient-side
A process allowing communication between a java code and an executable software file which permits the java code to receive an access to the internal system resources of the user's computer. The java code is arranged to be configured as a server in the client's configuration, by means of the establishment of a server socket communication channel. Once established, that socket communication channel is used for allowing a full ordered, error-free communication between the java code and the local executable file, thereby allowing the java code to take profit of the internal system resources of the user's computer. Preferably, the java code is received by the user through an Internet / Intranet network as an applet which thus receives an effective and powerful access to the system resources of the user's machine.
Owner:BLACKBOARD CORP INC +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com