System and method for multi-layered sensitive data protection in a virtual computing environment
a virtual computing environment and multi-layered technology, applied in computing, instruments, electric digital data processing, etc., can solve the problem of heightened security risks of sensitive data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
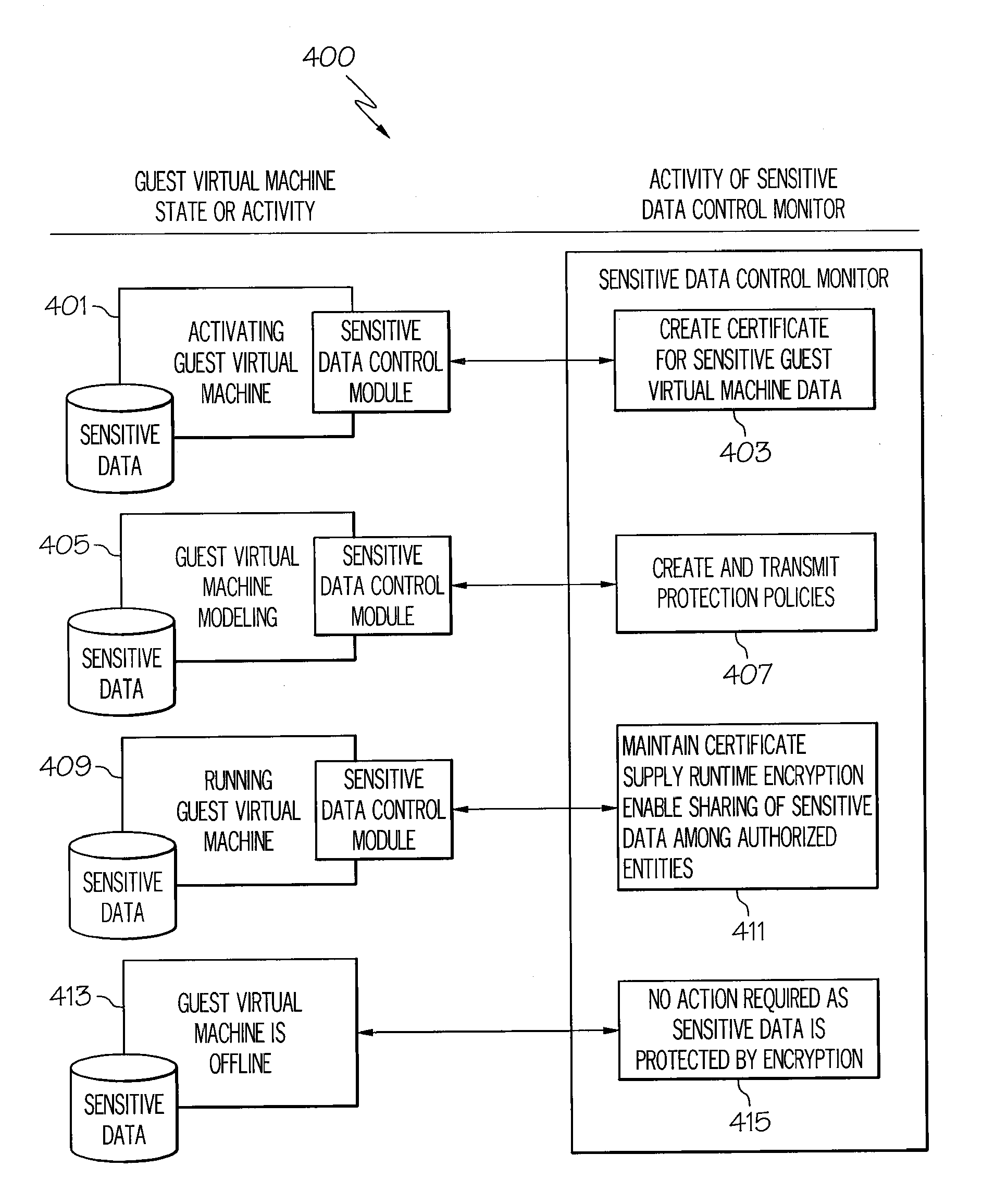
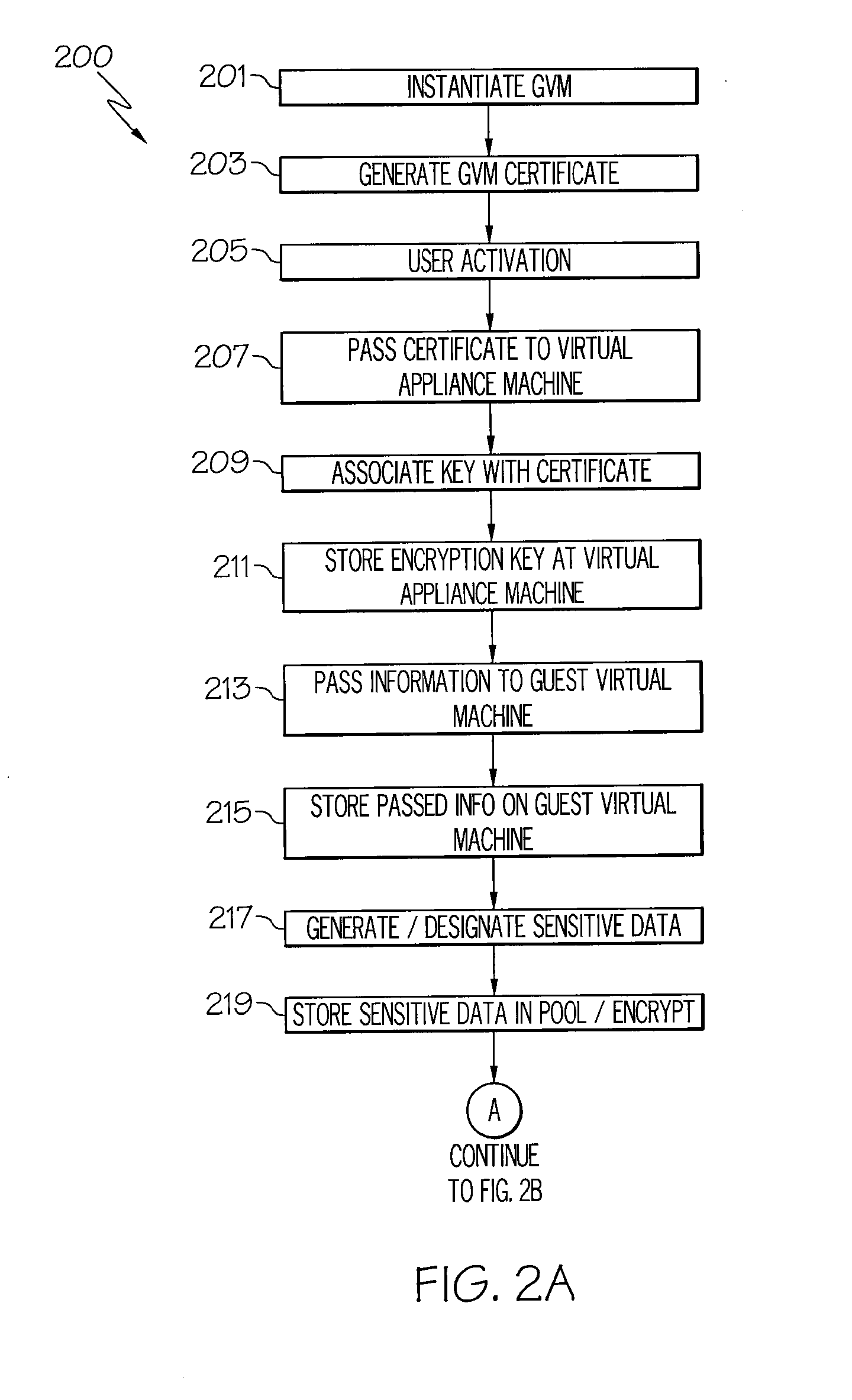
[0011]The systems and methods provided herein utilize multiple security layers to protect sensitive information stored within virtual machines from unauthorized access. Not only is protection from within running virtual machines used, but sensitive data is protected outside of the virtual machine environment (i.e., offline protection) for instances wherein, for example, data is copied or moved from one virtual machine to another. Furthermore, traditional sensitive data protection is non-transparent, and in some instances, users need to be aware of protection schemes and specific user associated data for enforcement to occur. Accordingly, the sensitive data protection provided herein combines internal data protection with transparent protection from unauthorized access attempts originating outside an original virtual machine. Additionally, methods for sharing sensitive data on virtual discs with other trusted virtual machines are enabled.
[0012]Accordingly, the systems and methods pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com