Data encryption/decryption and desensitization operation engine and working method thereof
A technology for running engines and working methods, applied in the field of information system security, and can solve problems such as business unavailability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
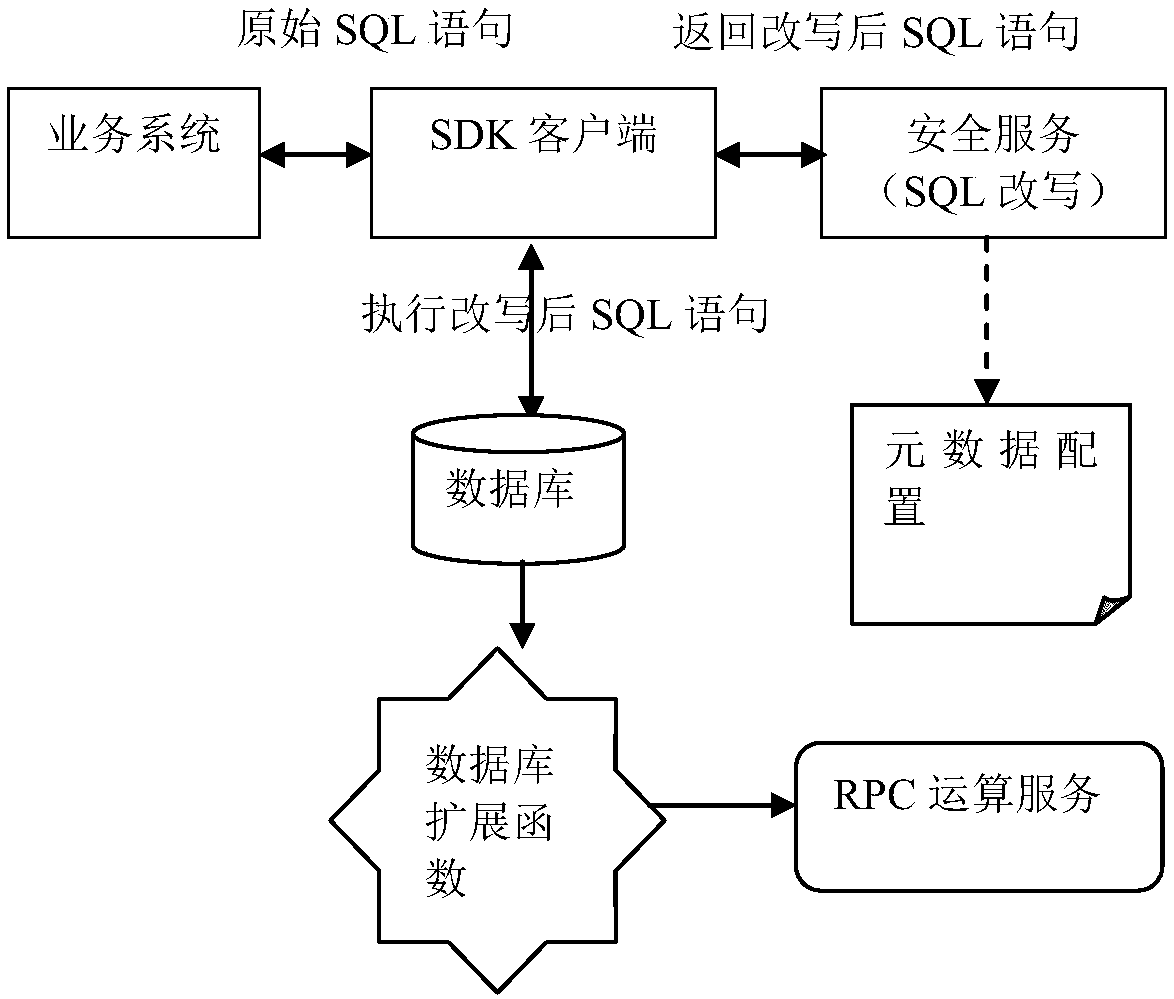
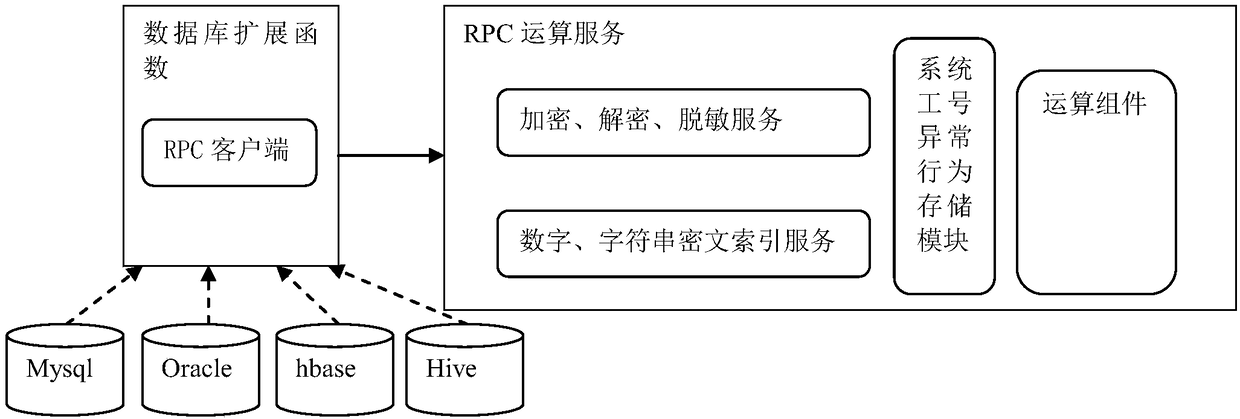
[0043] see figure 1 , which is a schematic diagram of the operating principle of the overall architecture of a preferred embodiment of the data encryption, decryption and desensitization operation engine of the present invention. The data encryption, decryption and desensitization running engine mainly includes: SDK client, security service, and database extension functions.
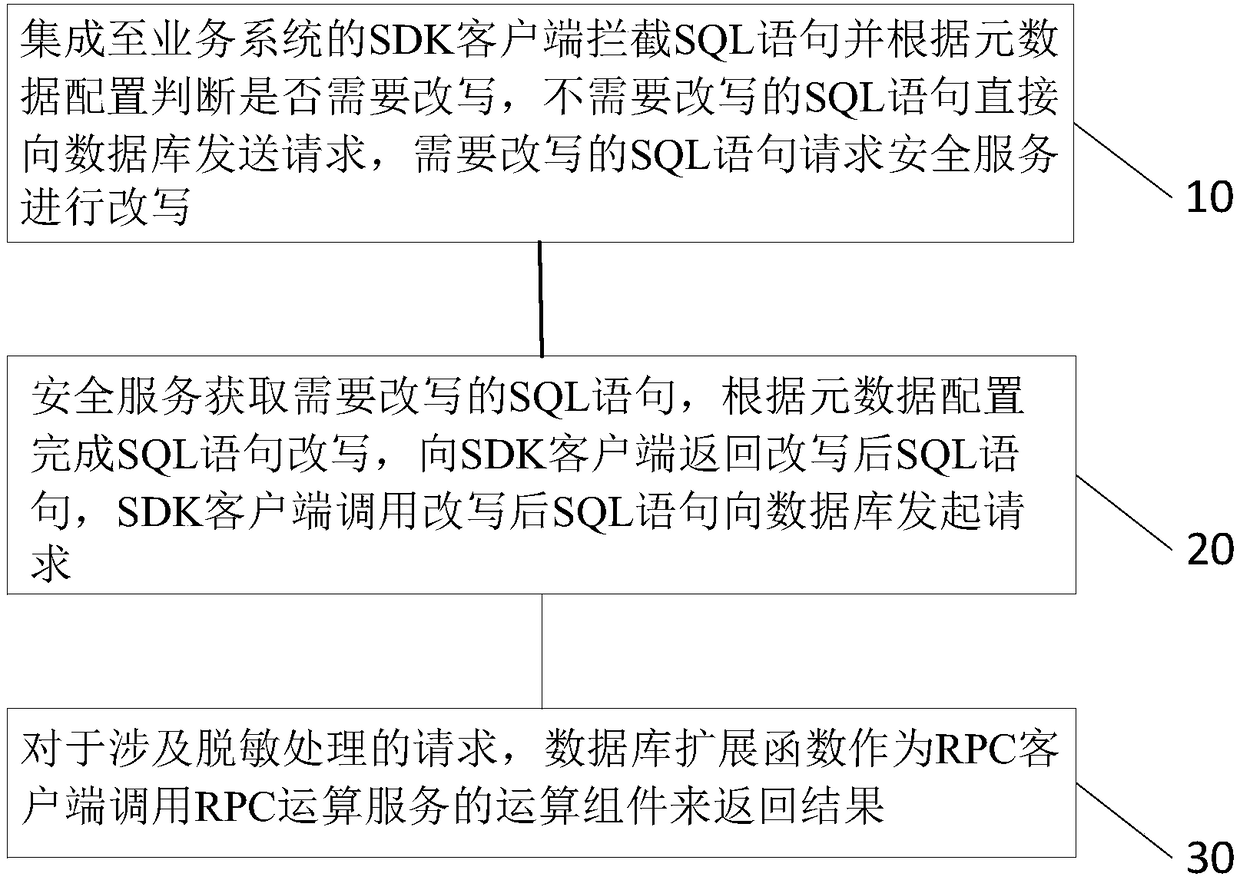
[0044] The SDK client is integrated into the business system, which can intercept SQL statements and determine whether rewriting is required based on the metadata configuration. SQL statements that do not need to be rewritten directly send requests to the database, and SQL statements that need to be rewritten request security services to rewrite; the SDK client can pass The http protocol sends requests to security services.
[0045] The security service is used to obtain the SQL statement that needs to be rewritten, complete the rewriting of the SQL statement according to the metadata configuration, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com