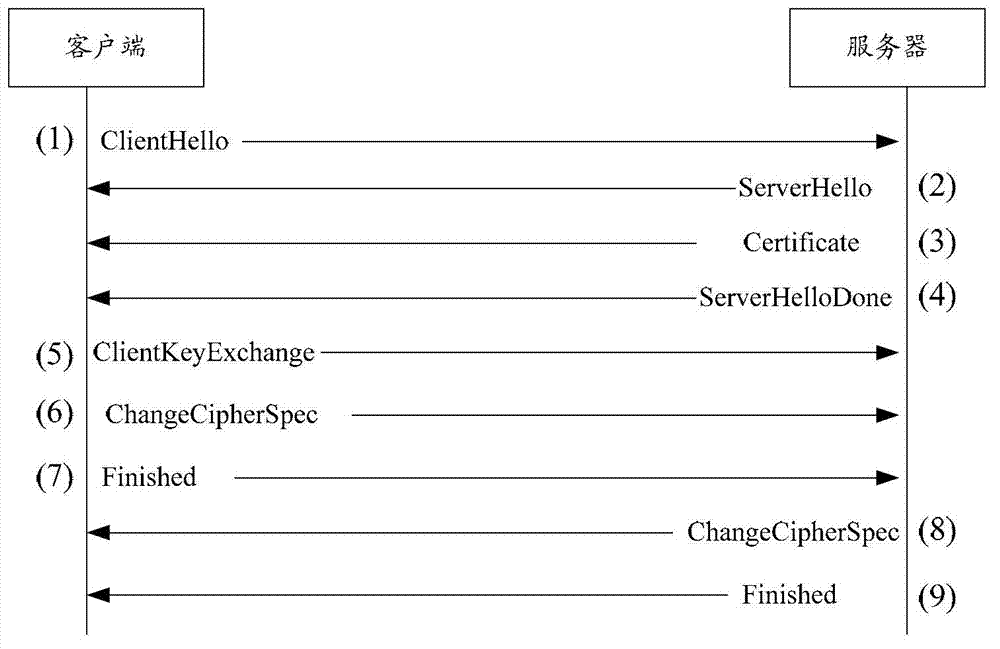
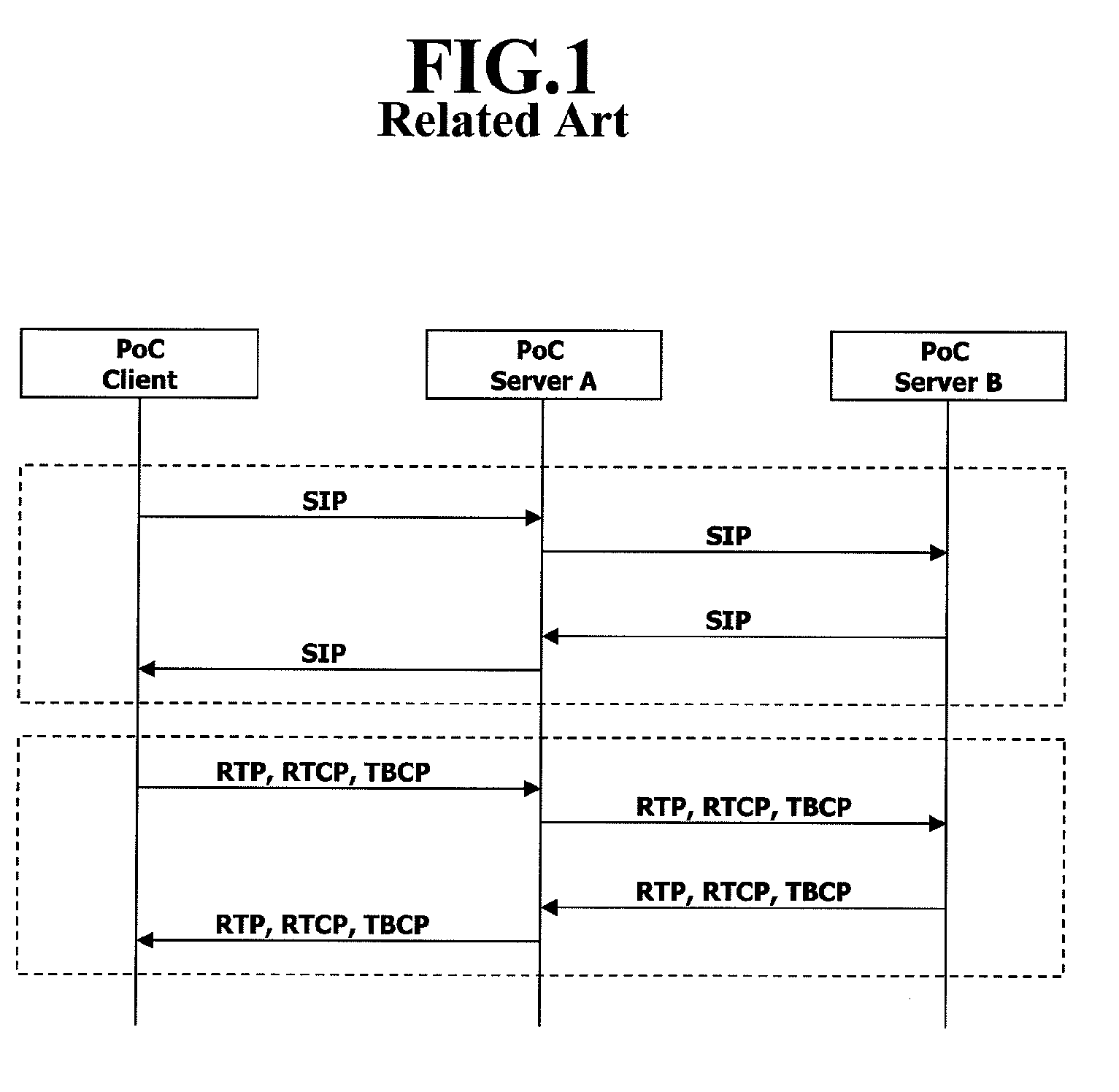
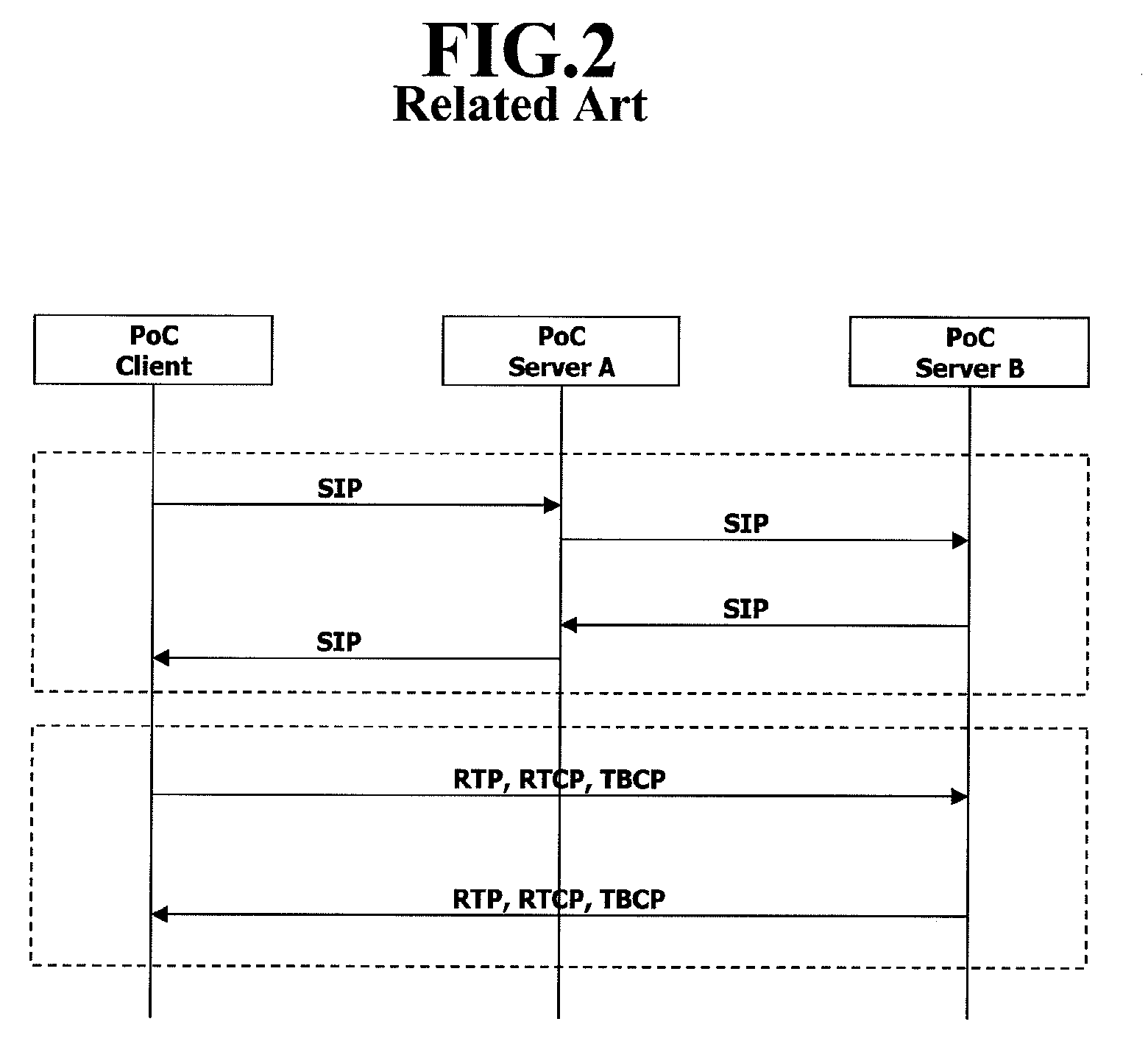
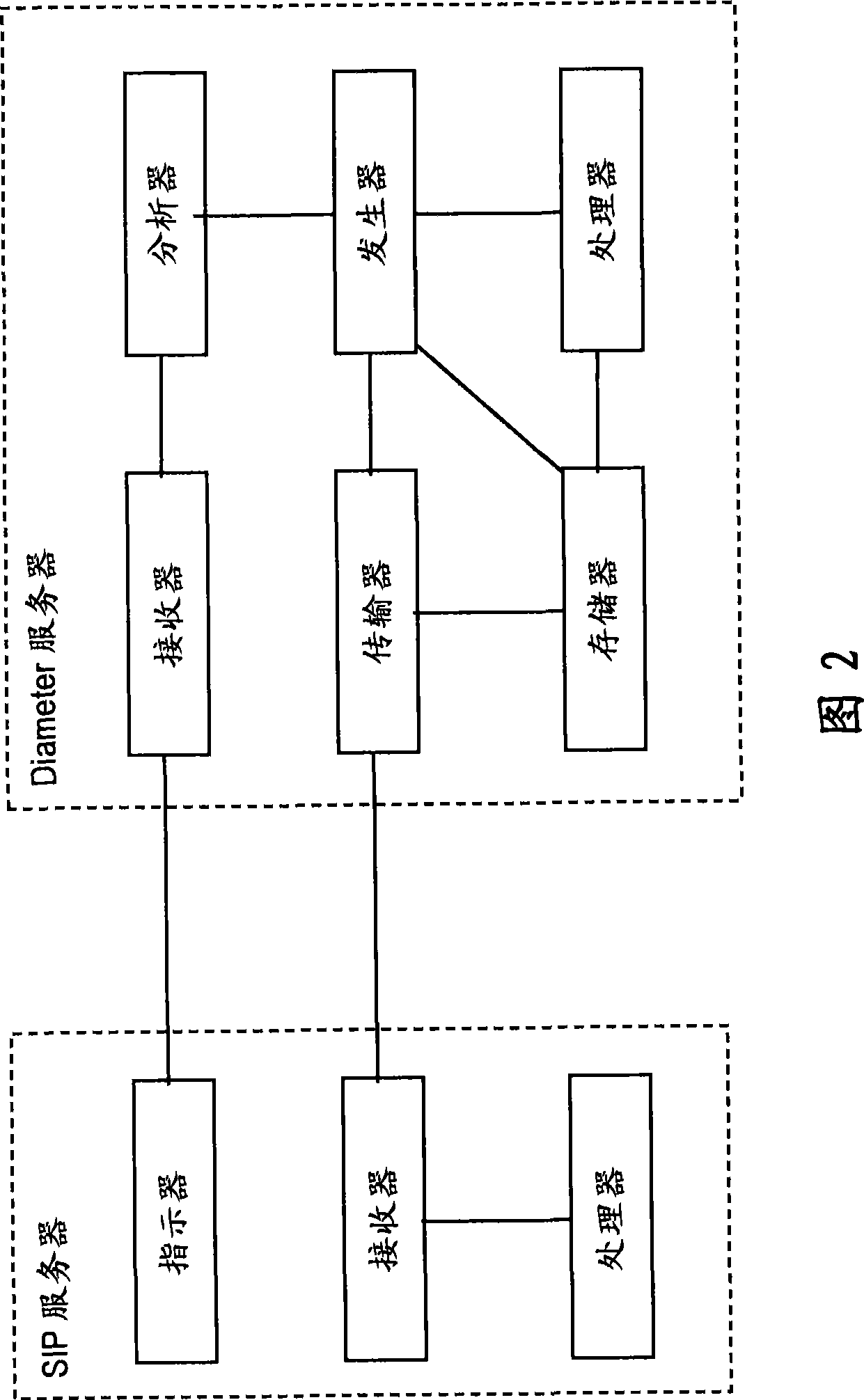
Patents
Literature
51 results about "Proxy pattern" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
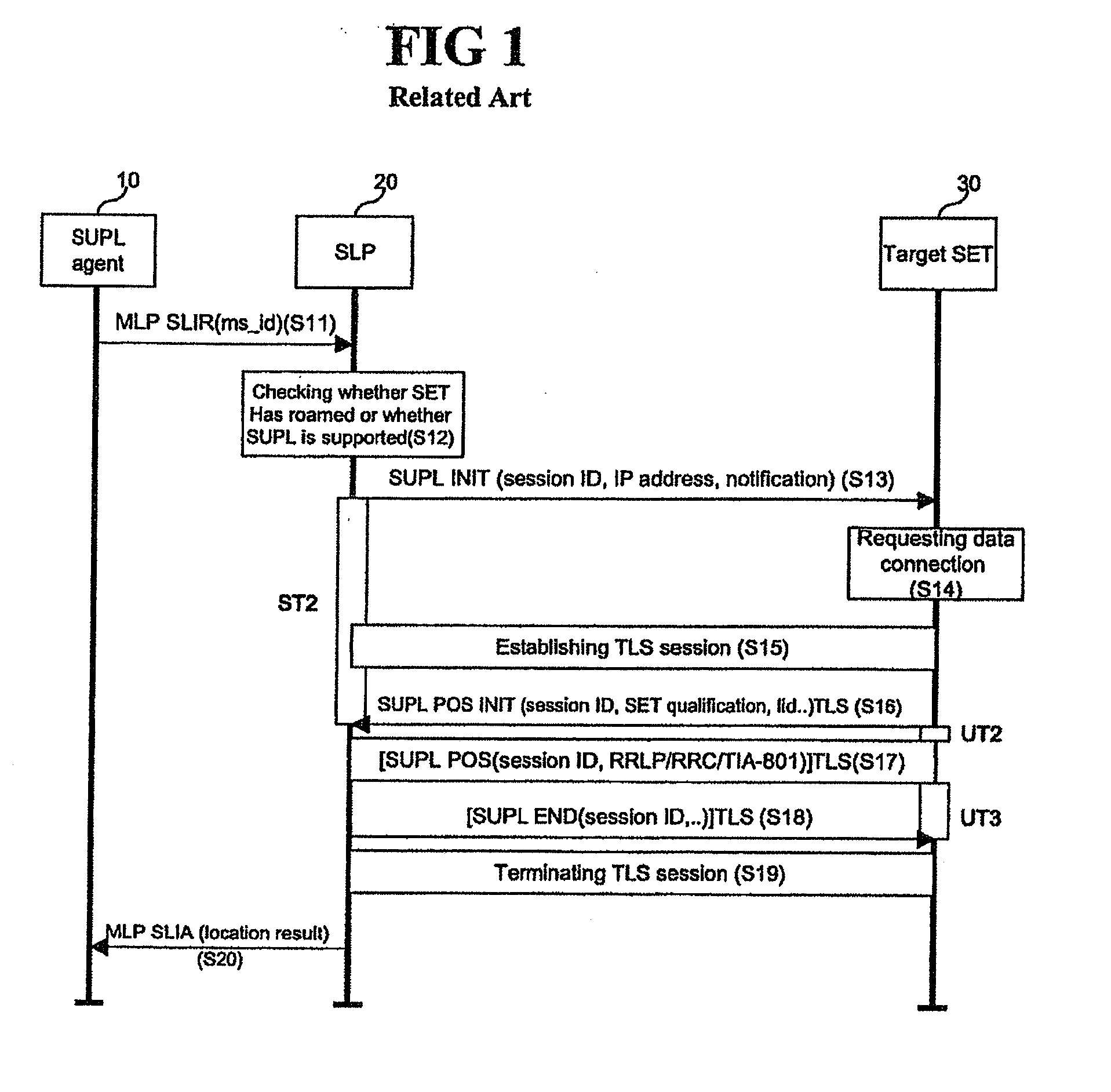
In computer programming, the proxy pattern is a software design pattern. A proxy, in its most general form, is a class functioning as an interface to something else. The proxy could interface to anything: a network connection, a large object in memory, a file, or some other resource that is expensive or impossible to duplicate. In short, a proxy is a wrapper or agent object that is being called by the client to access the real serving object behind the scenes. Use of the proxy can simply be forwarding to the real object, or can provide additional logic. In the proxy, extra functionality can be provided, for example caching when operations on the real object are resource intensive, or checking preconditions before operations on the real object are invoked. For the client, usage of a proxy object is similar to using the real object, because both implement the same interface.
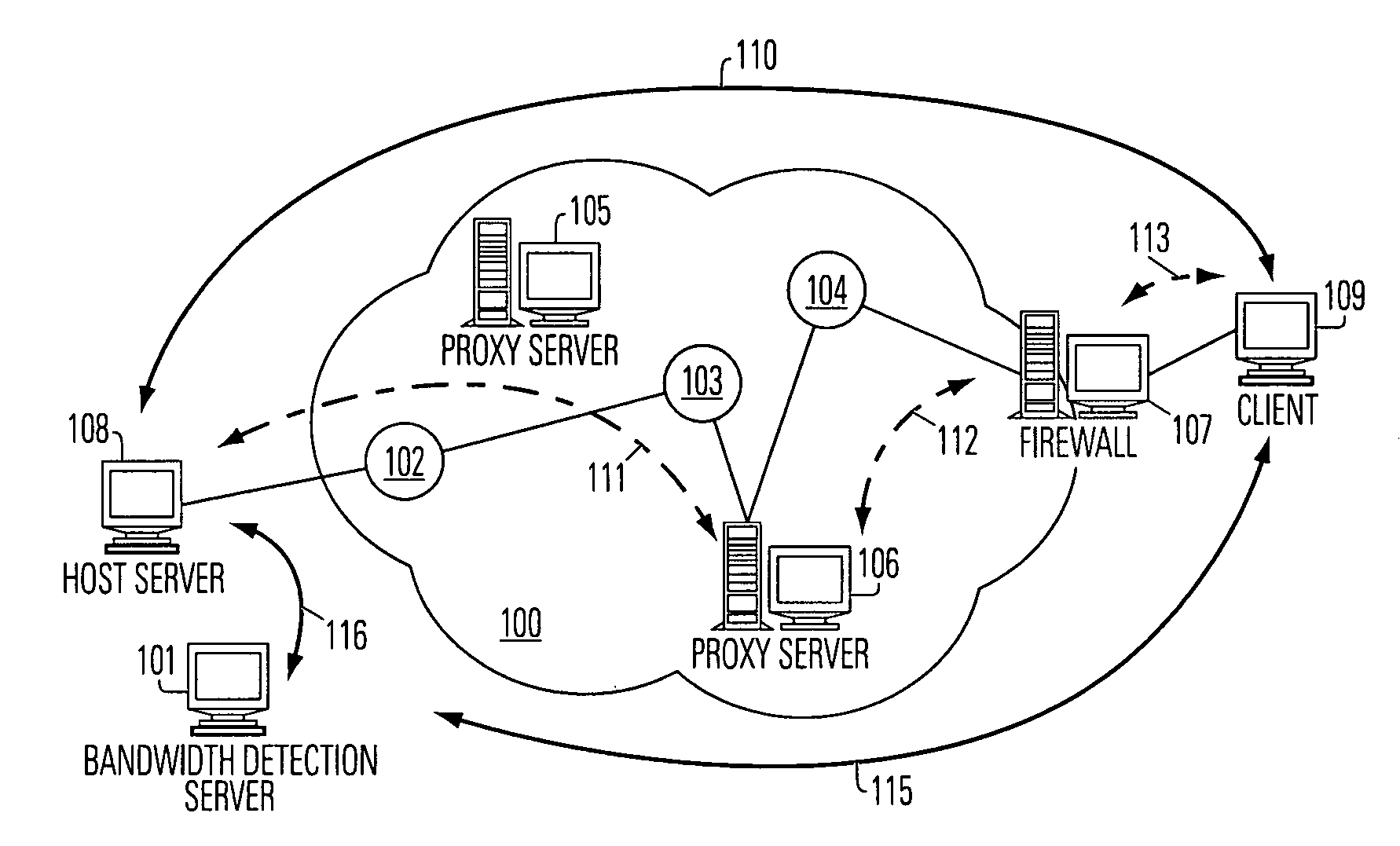
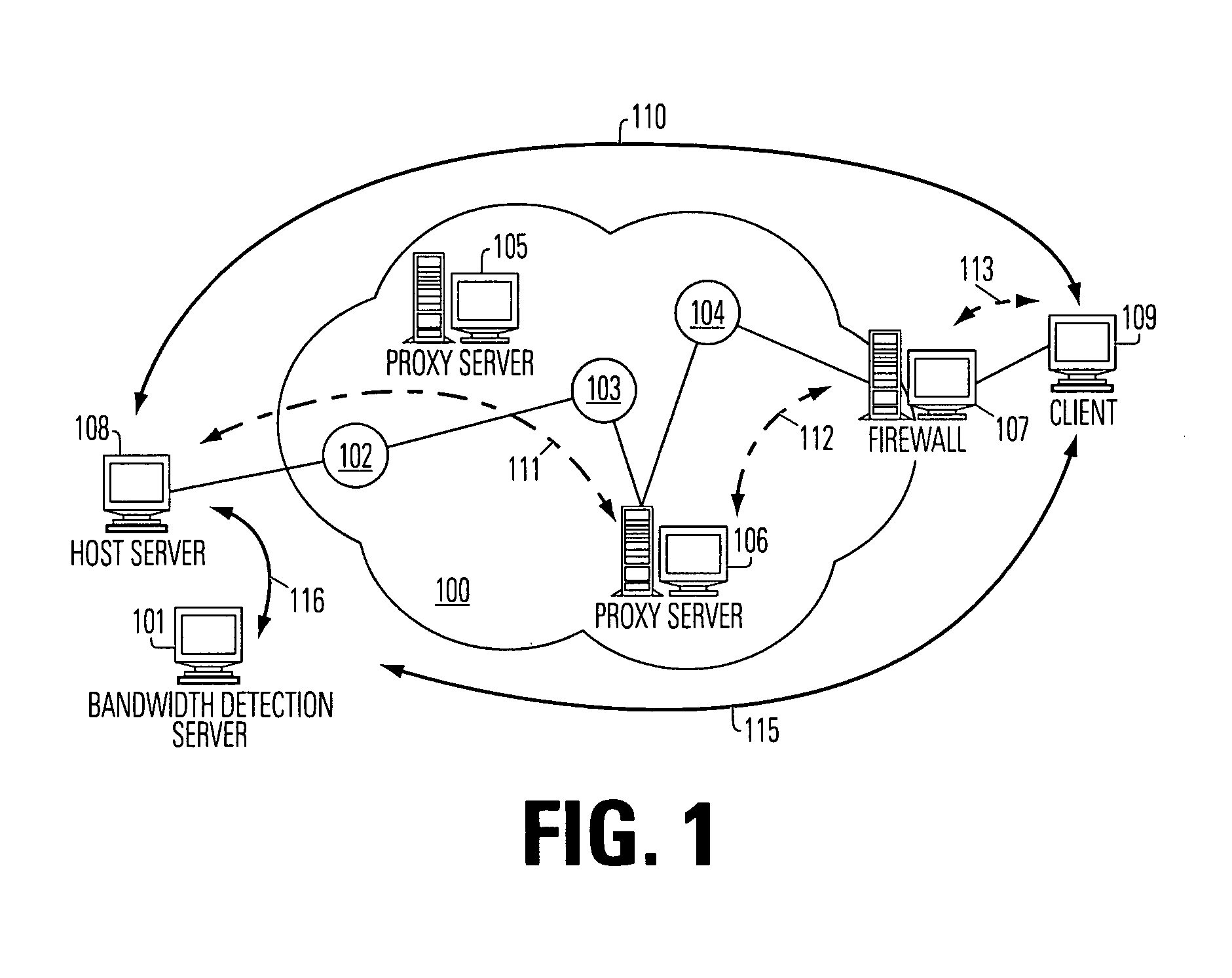
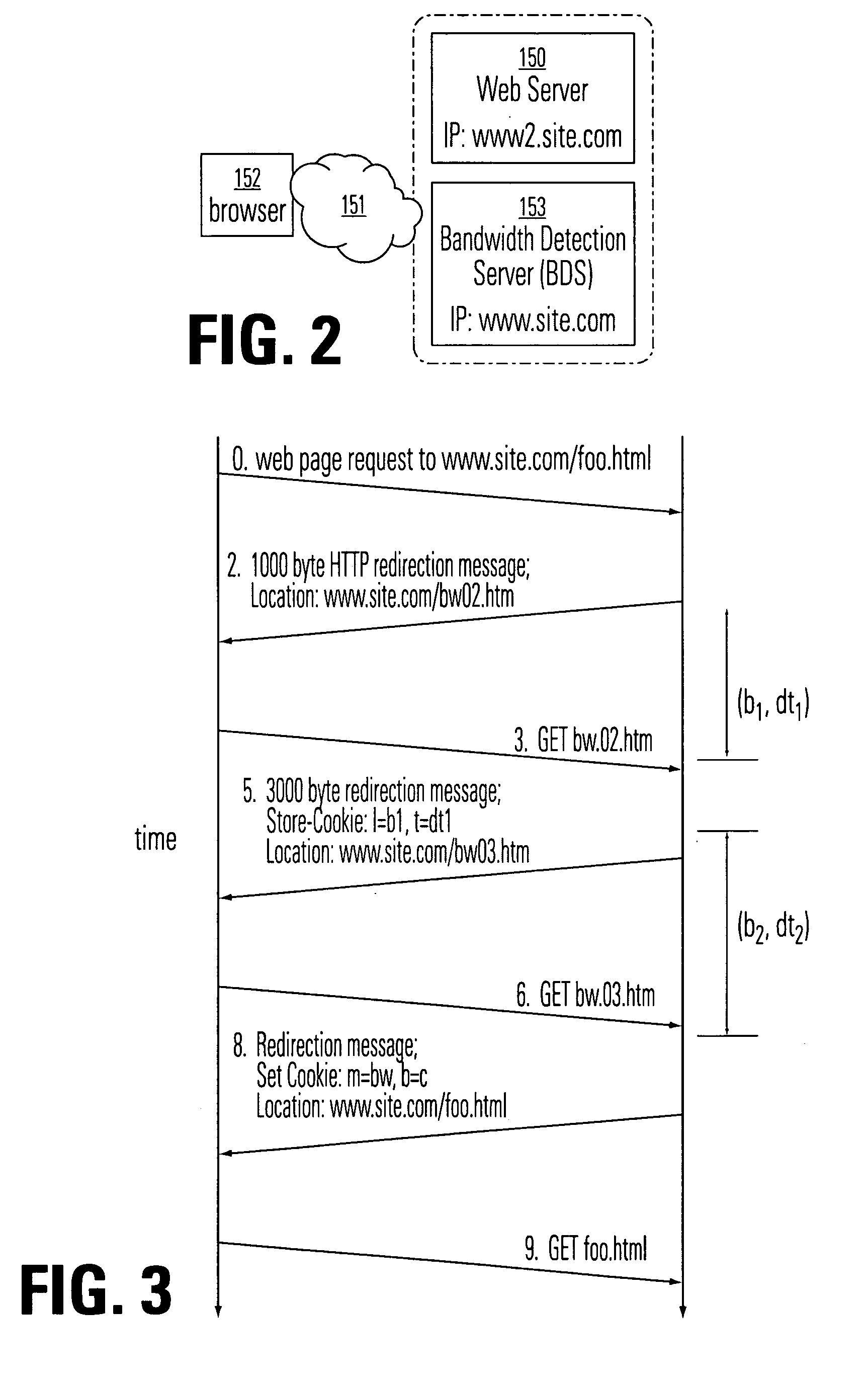
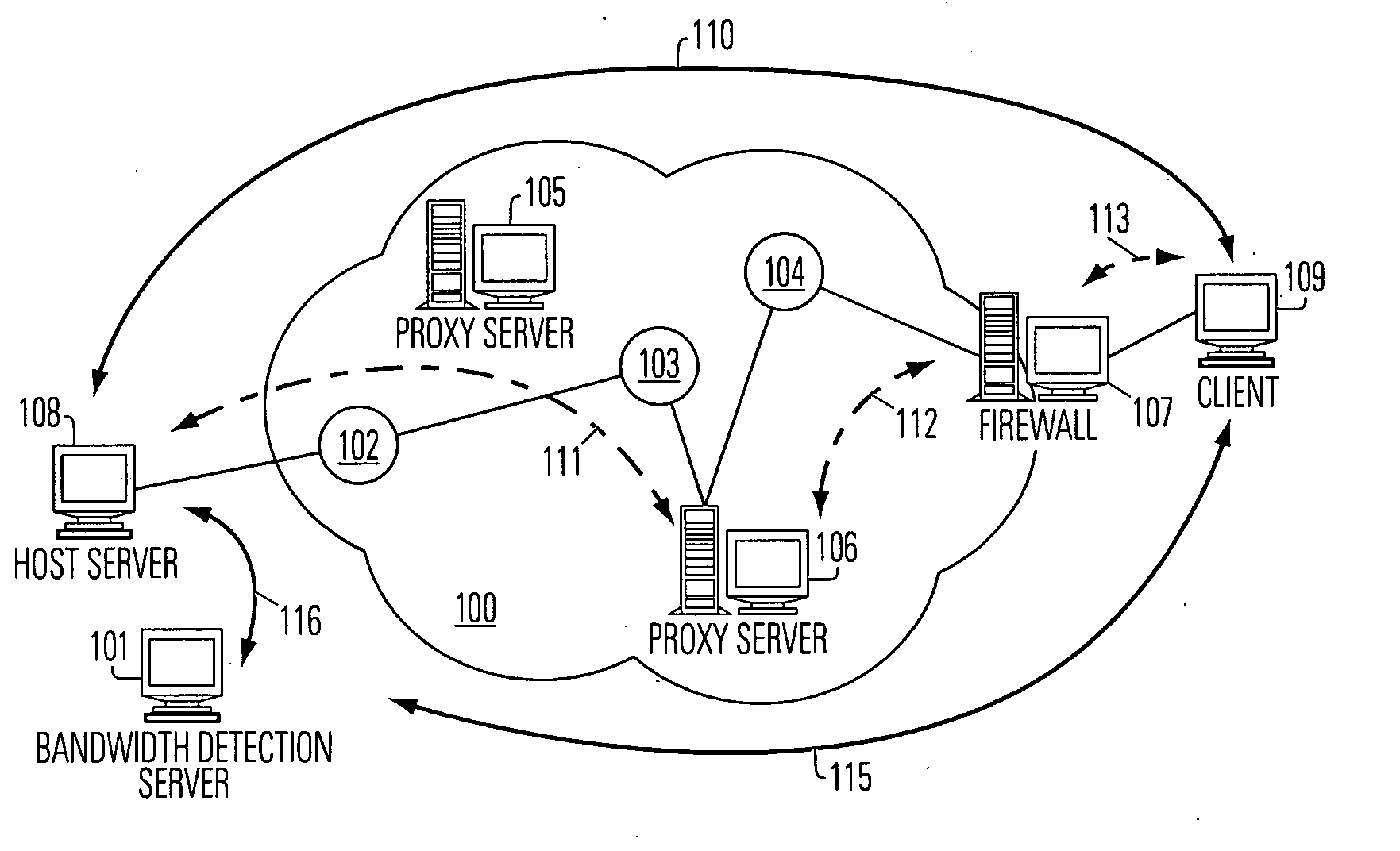
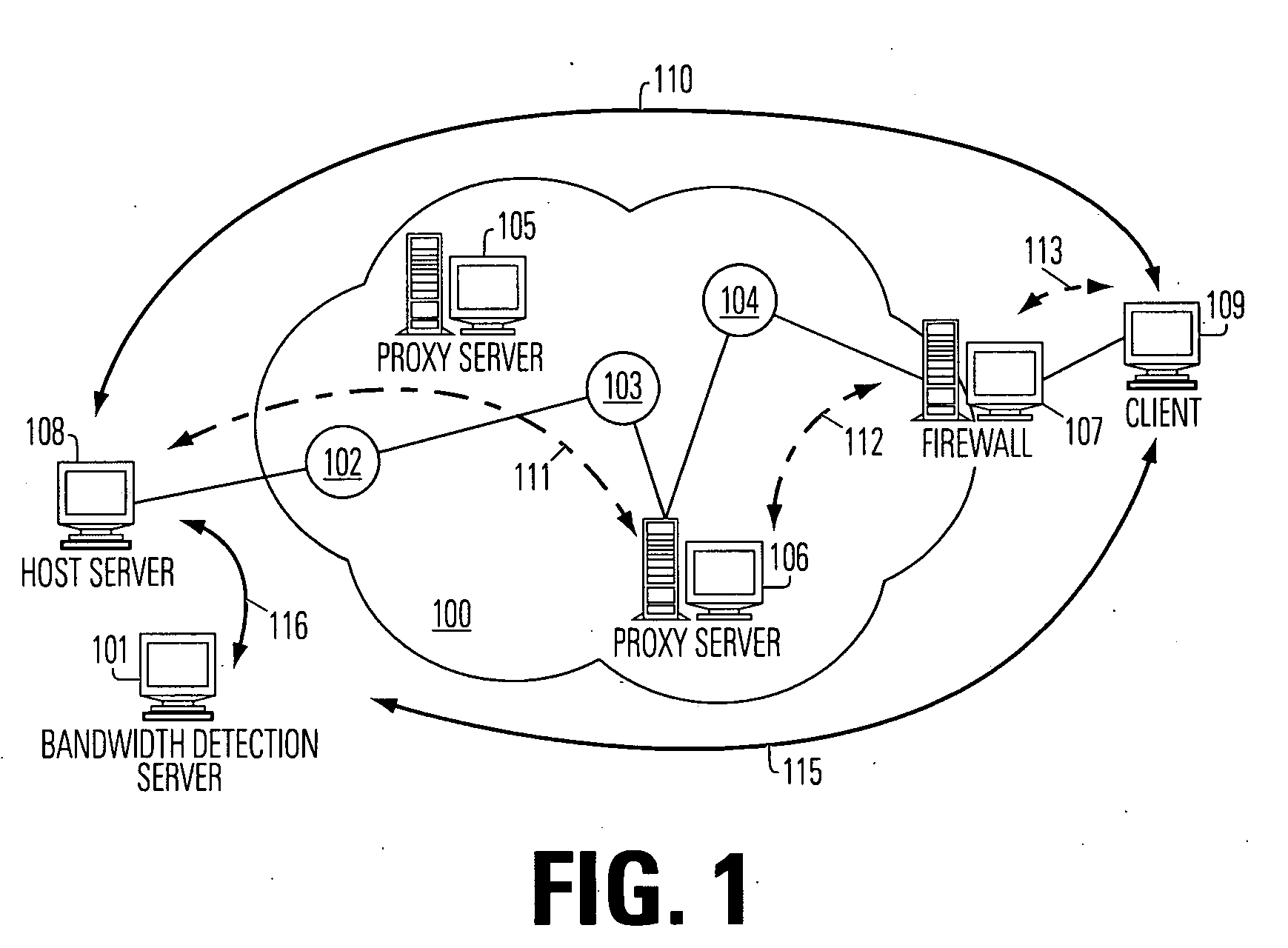
Bandwidth detection in a heterogeneous network with parallel and proxy modes
InactiveUS6992983B1QuicklyEnabling detectionMultiplex system selection arrangementsError preventionTelecommunications linkData segment
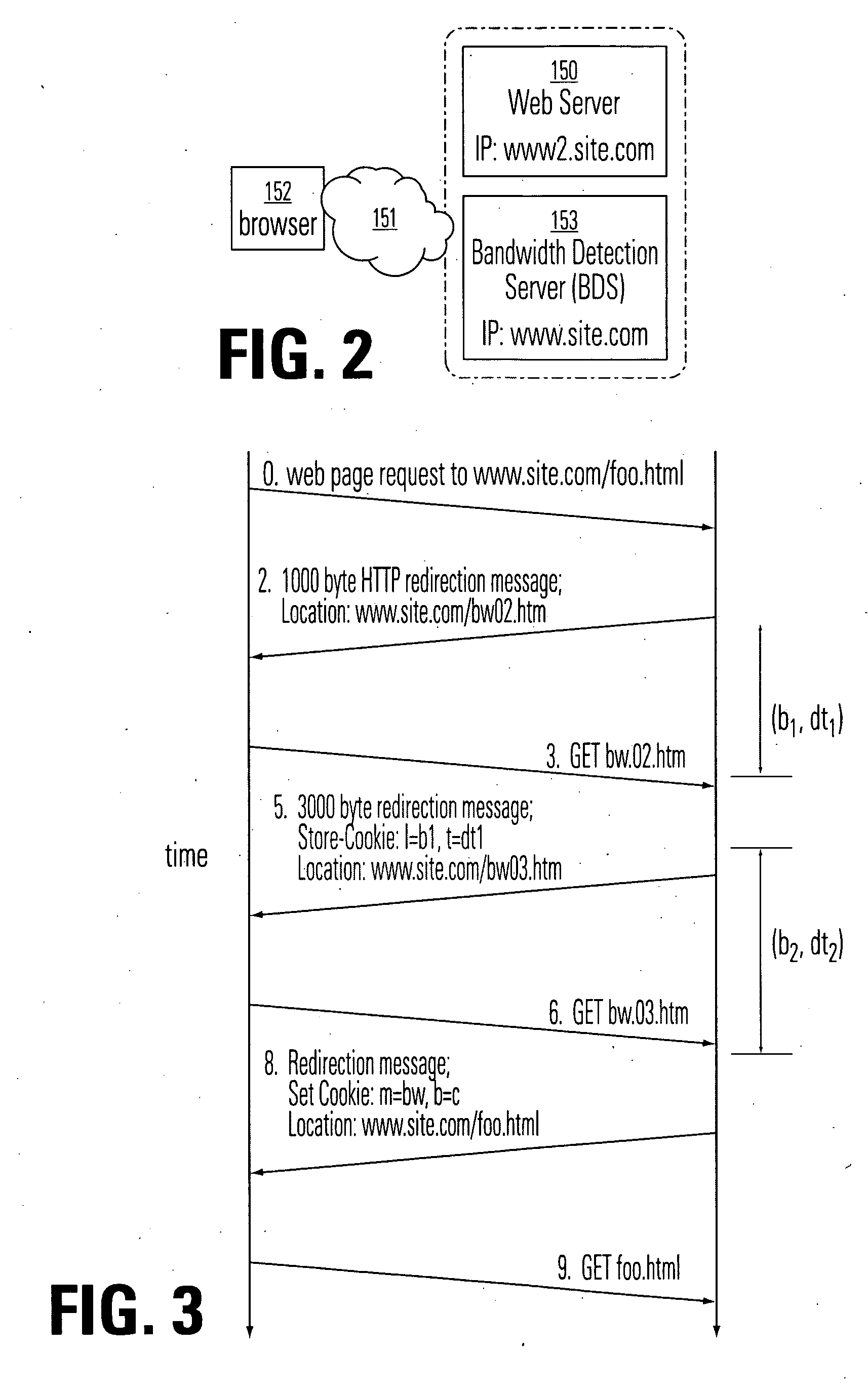
Effective bandwidth of a communication link is determined in a heterogeneous, packet switched network between a source and a destination, where effective bandwidth is defined as the actual available bandwidth between the server and the client, minus the overhead of the various network protocols used to transmit the data. The method includes measuring transmission times between the source and a destination for a plurality data segments having different characteristics, such as different sized files or subfiles of data; processing the transmission times to cancel effects of transmission latencies other than the different characteristics of the data segments; and indicating a bandwidth based on said processing. The processing is done in parallel with the return of user resources to the destination, and using a bandwidth detection engine associated with a proxy server.
Owner:ADOBE INC
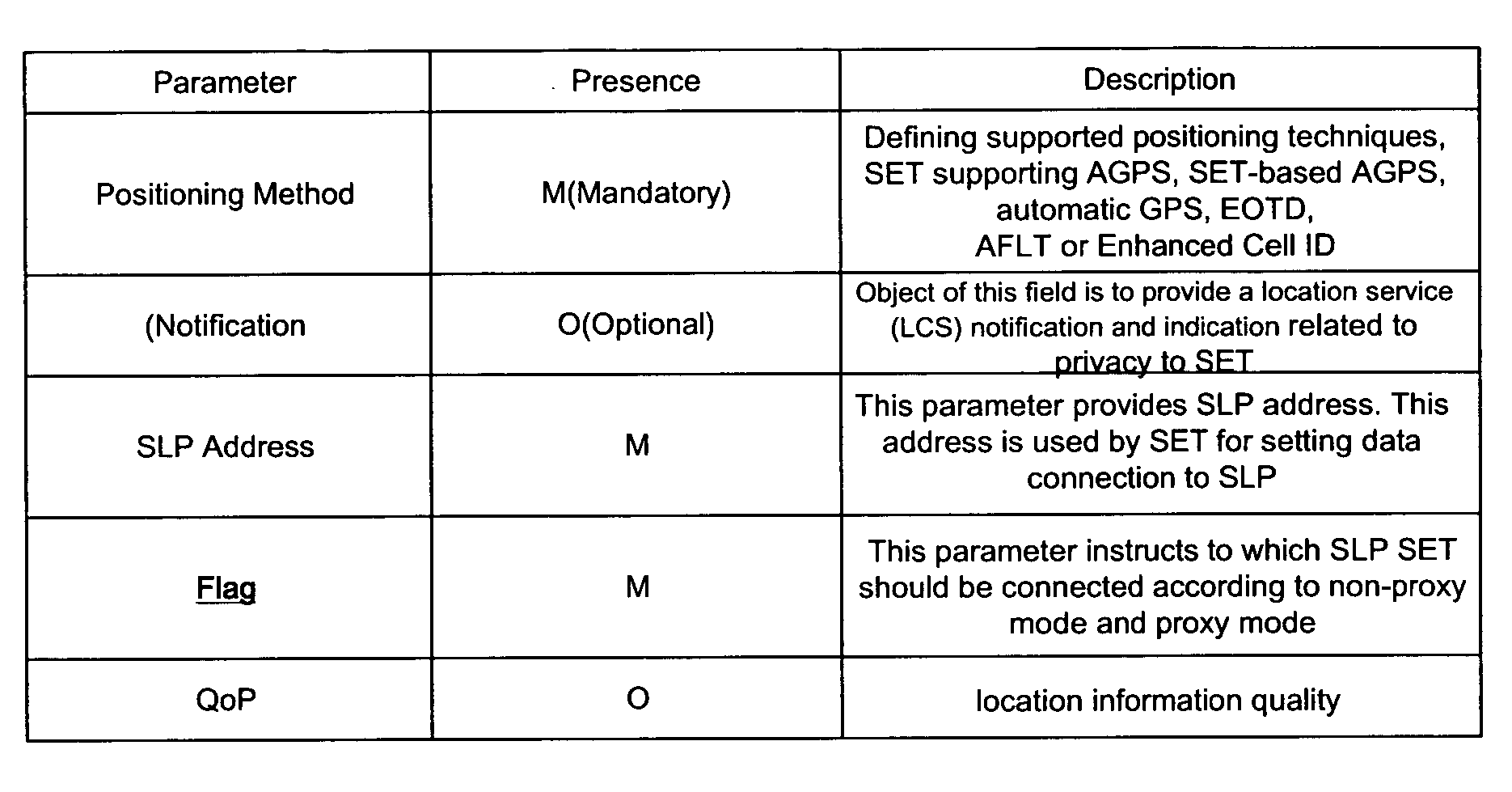
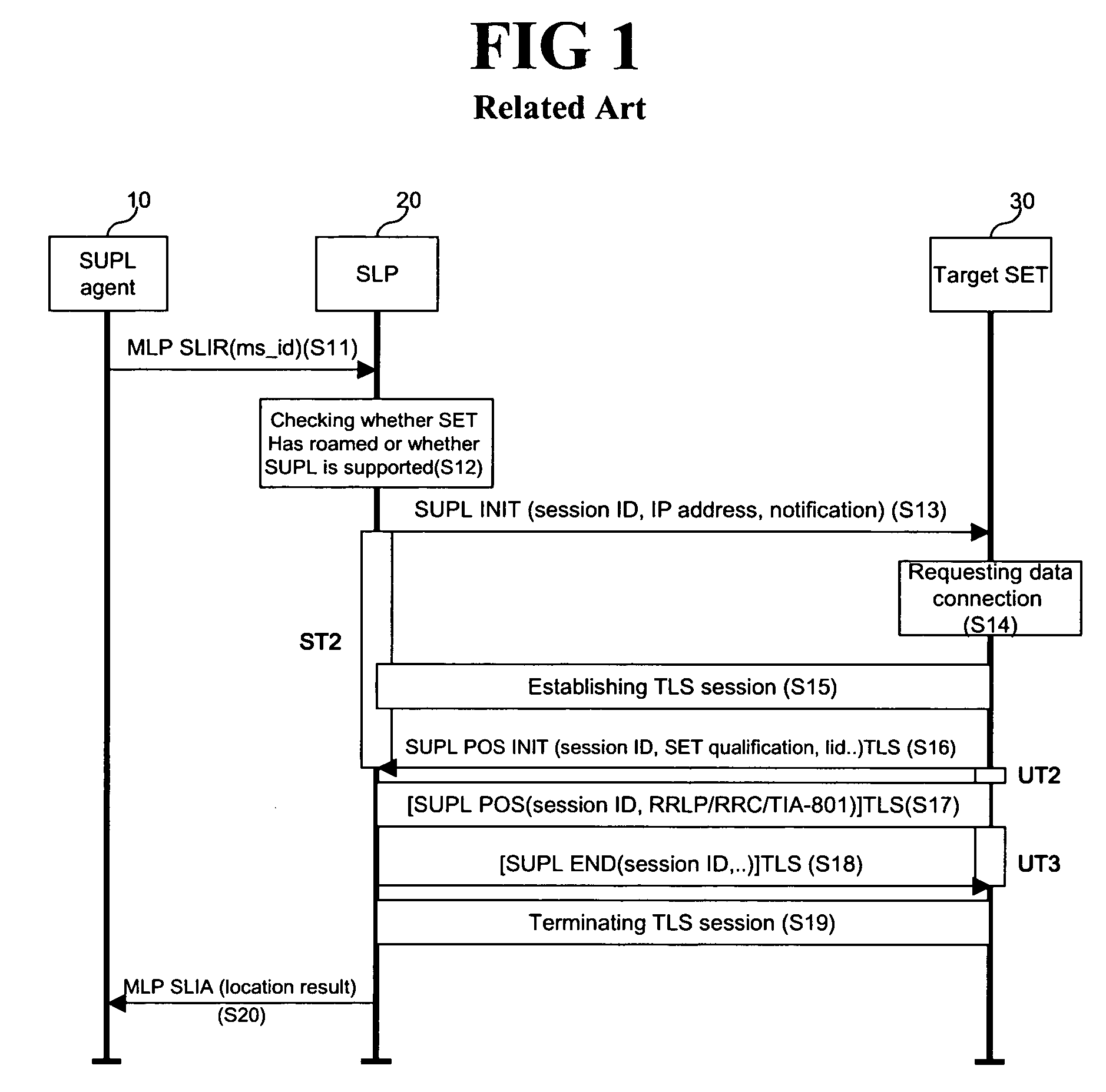
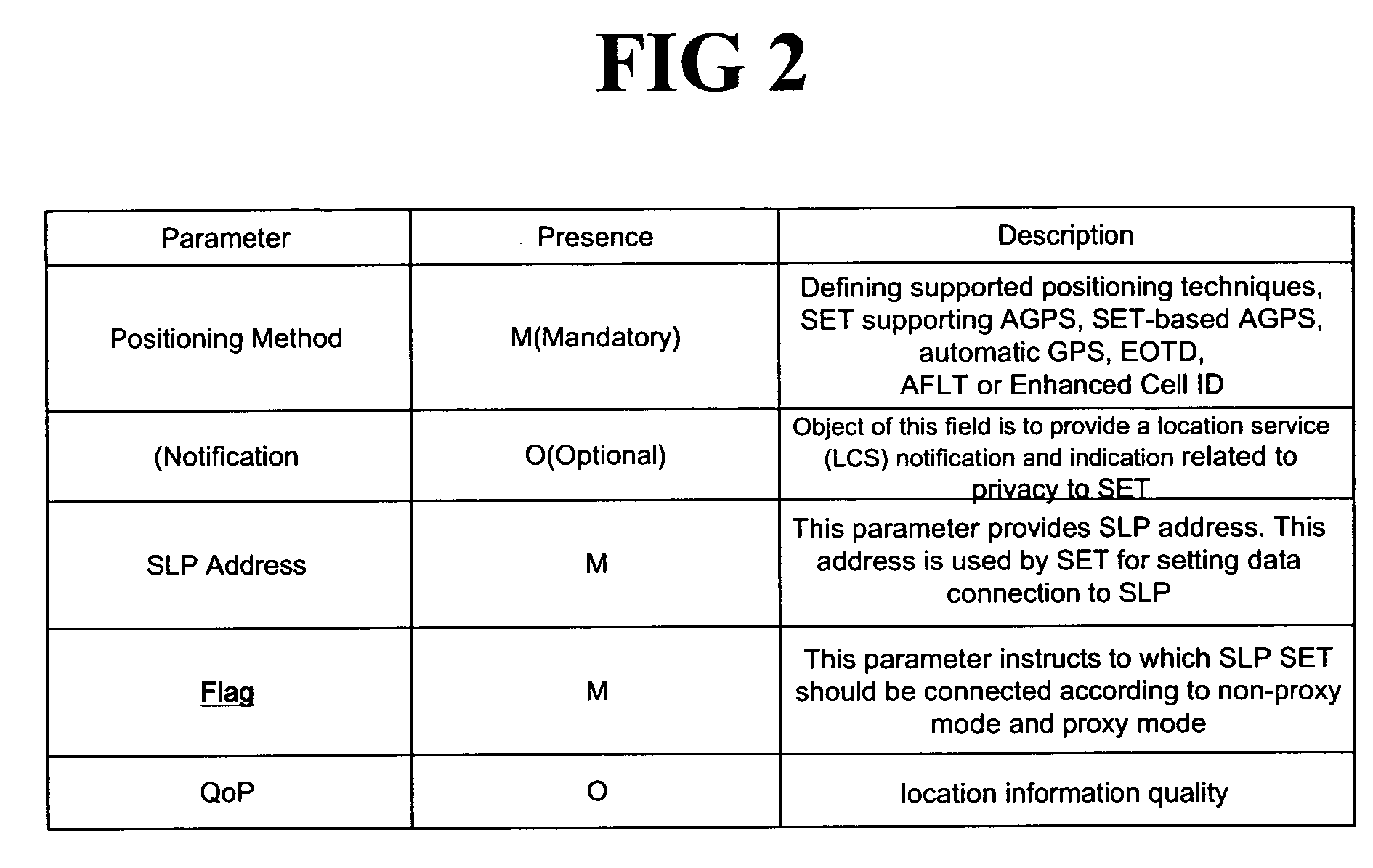
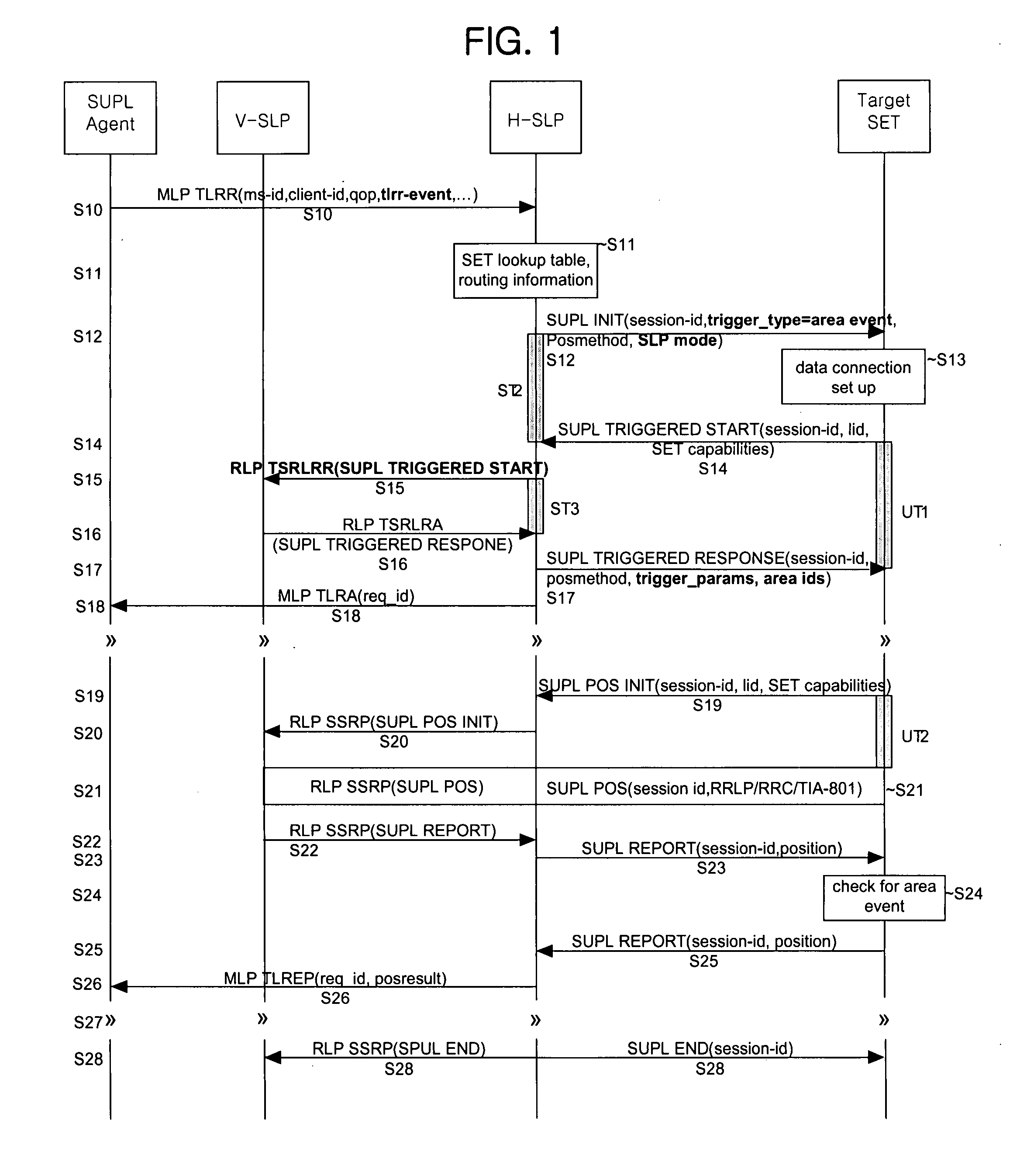
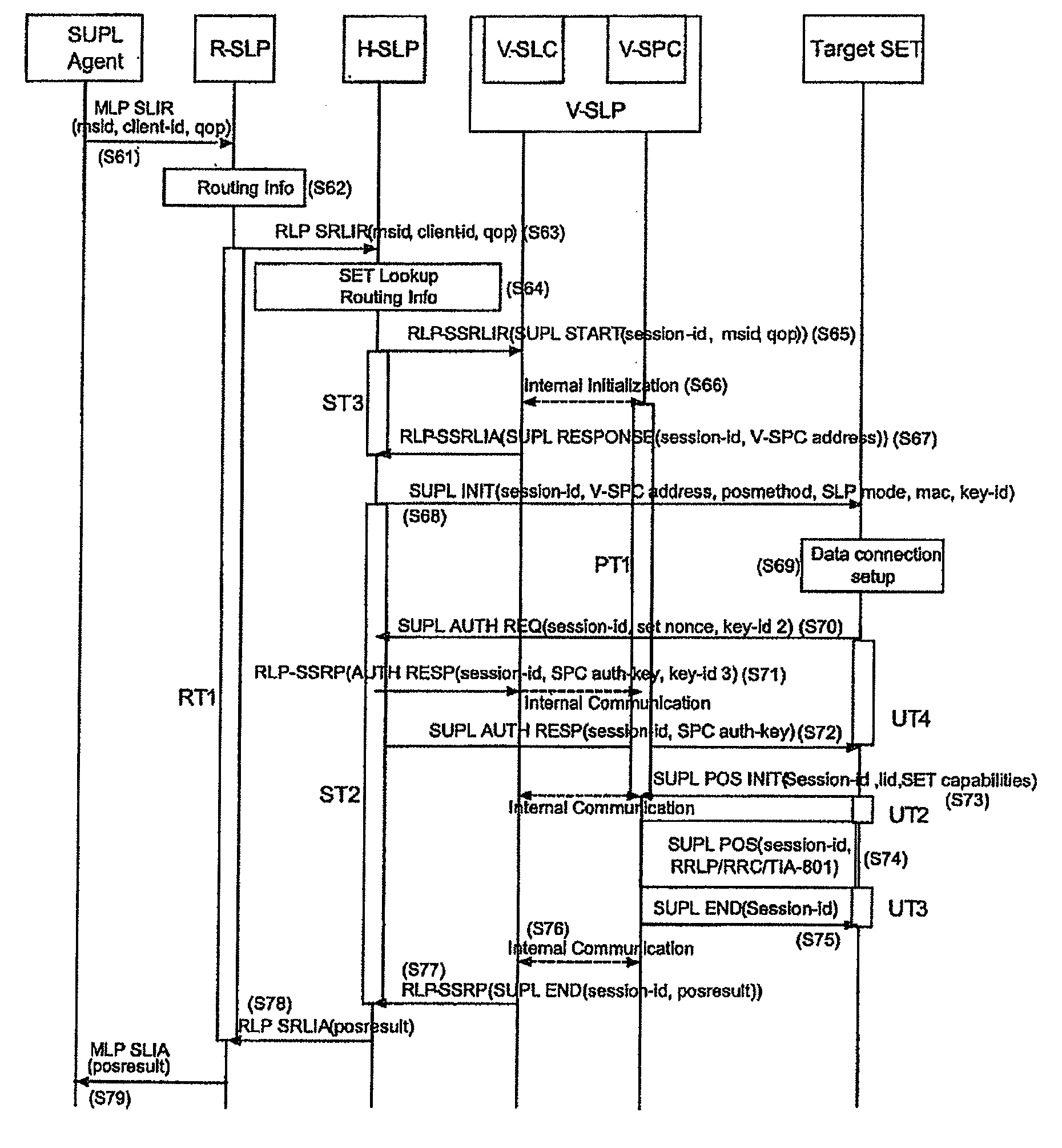
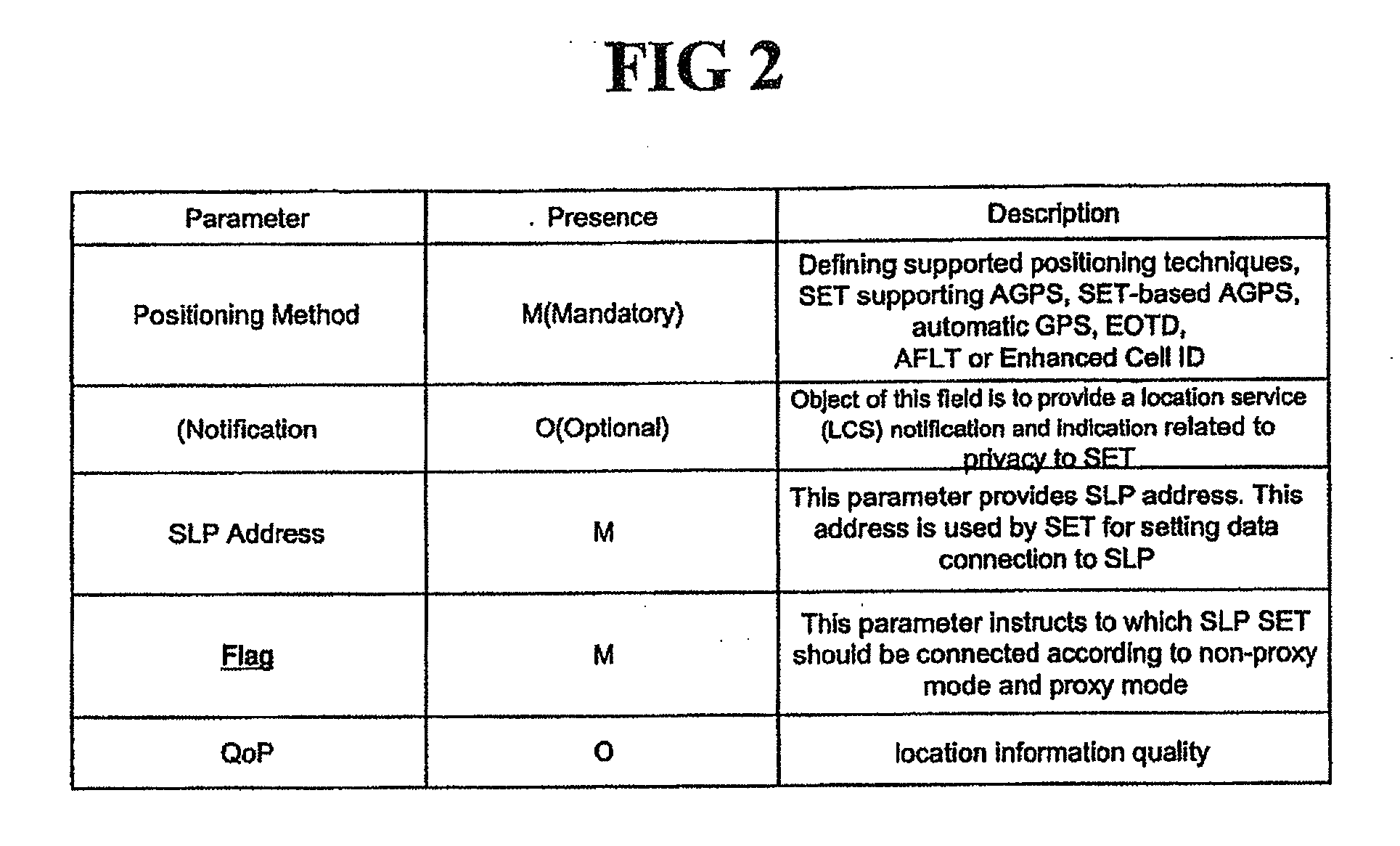
SUPL initialization message in a location information system and method and system for processing SUPL by using the same
ActiveUS20060225090A1Accurate identificationAnalogue secracy/subscription systemsWireless network protocolsInitInformation system
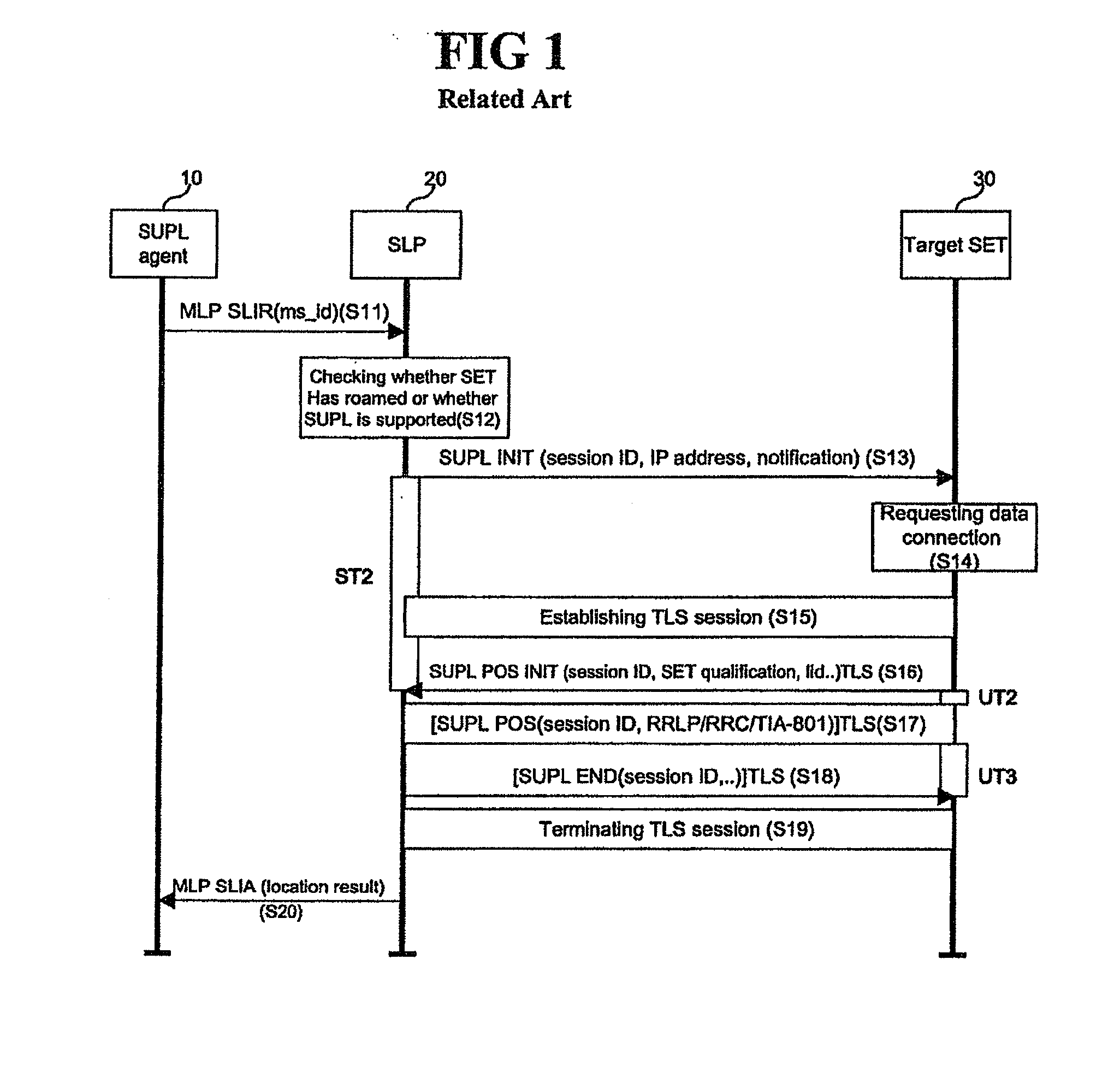
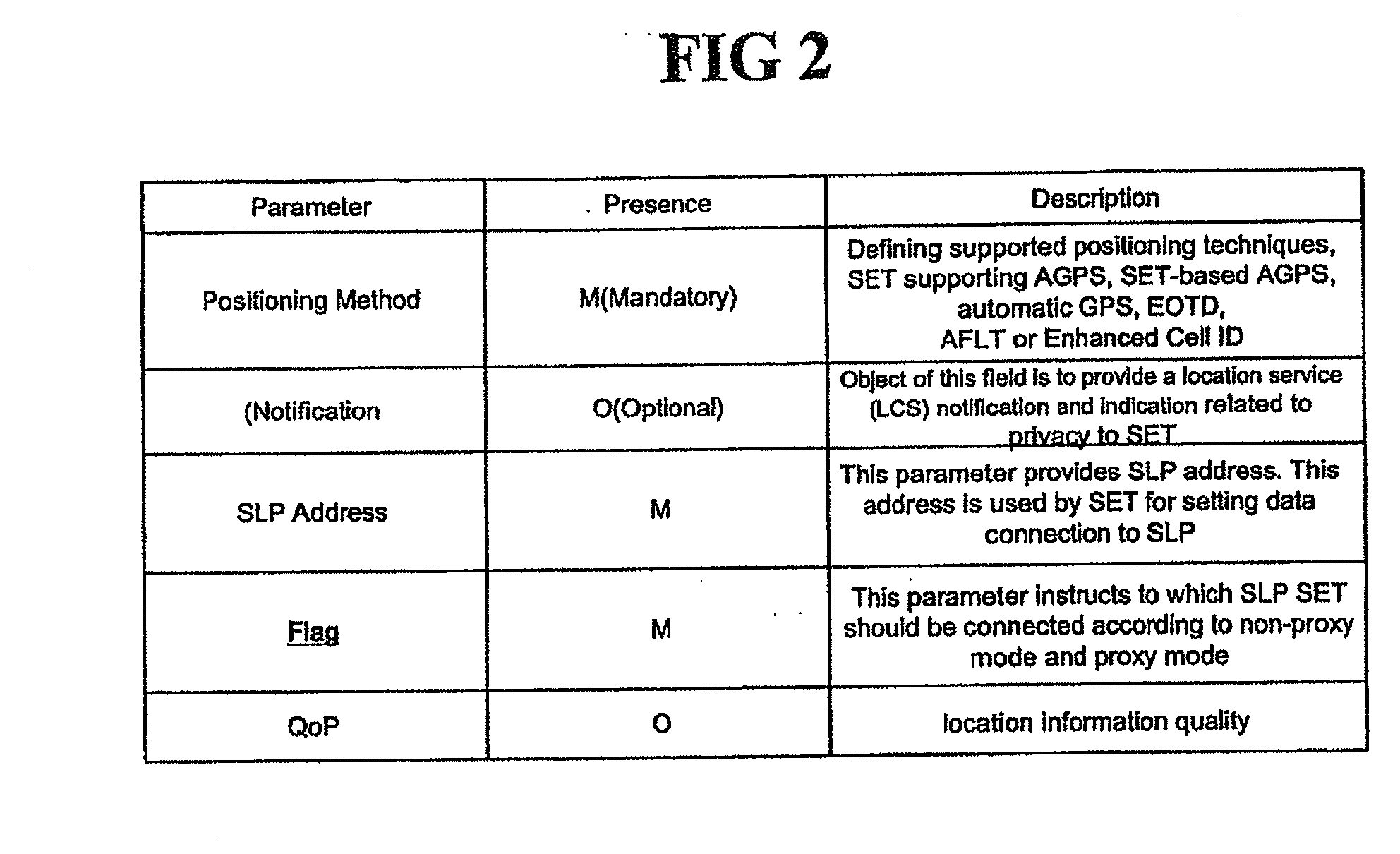
A SUPL enabled terminal, method and system for processing SUPL are discussed. According to one embodiment, the SUPL enabled terminal includes a processor to process a SUPL location platform (SLP) mode indicator received in a SUPL initiation message, the SLP mode indicator indicating whether the terminal is to operate according to a proxy mode or a non-proxy mode.
Owner:LG ELECTRONICS INC
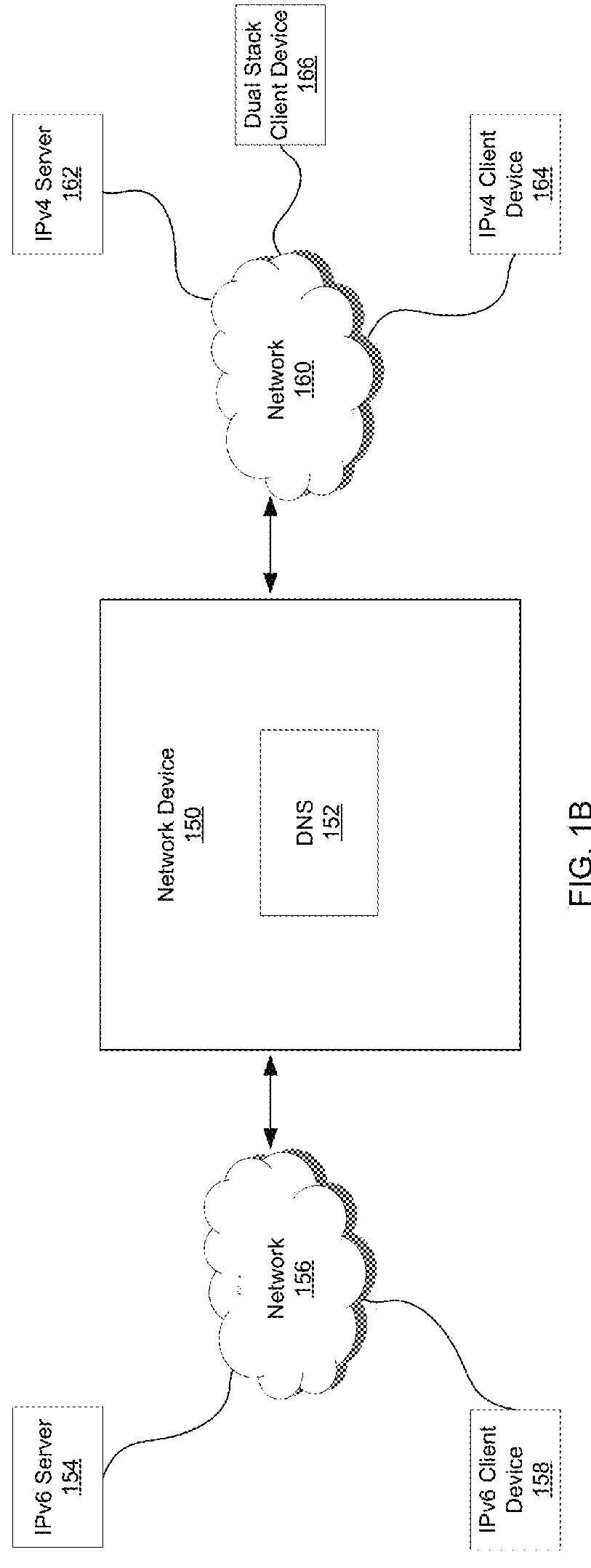
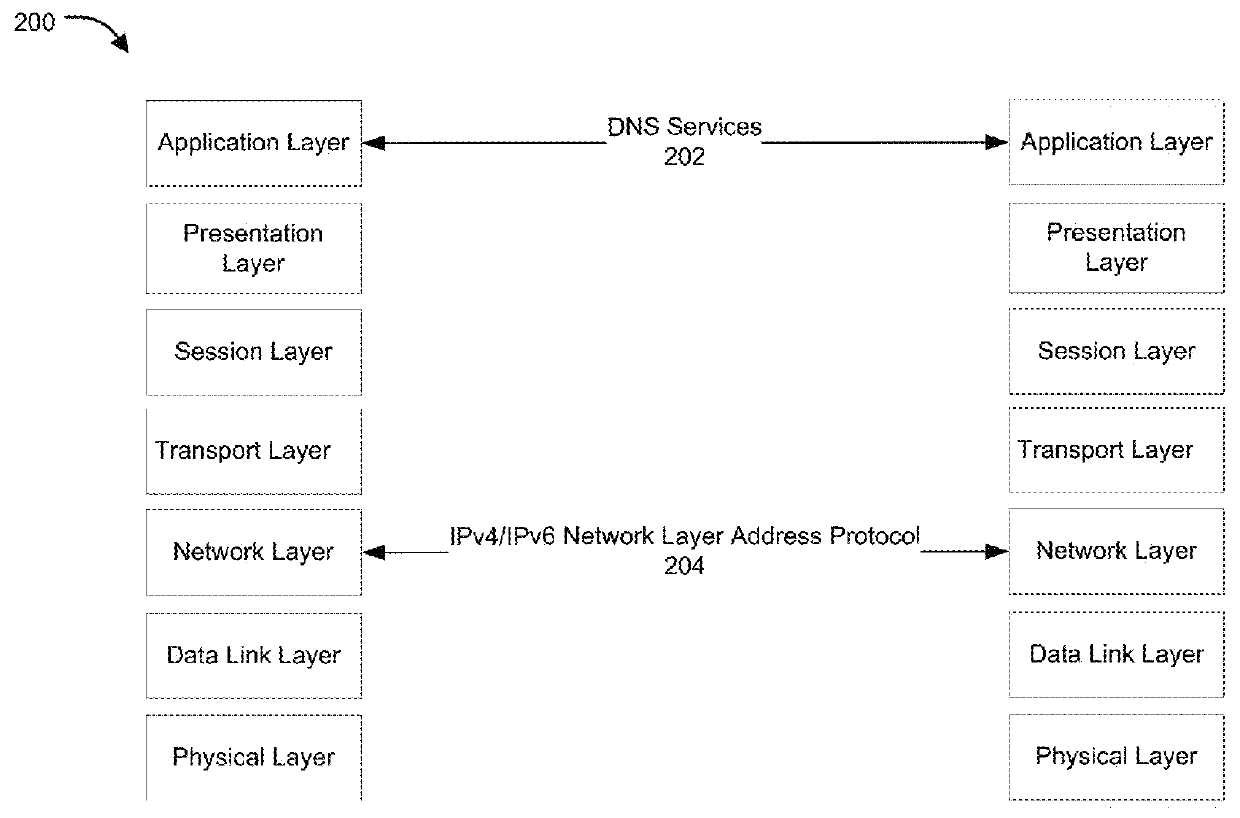
Dns-enabled communication between heterogeneous devices
Methods and systems for an IPv4-IPv6 proxy mode for DNS servers are provided. According to one embodiment, a DNS query is received by a network device from a dual-stack client. A determination is made the network device whether a first record type containing an Internet Protocol (IP) address for a server associated with the query exists within a DNS database of the network device. If the first record type exists for the server, then communication is enabled between the client and the server based on the first record type; otherwise it is automatically determined whether a second record type usable by the client exists for the server. Responsive to a determination that the second record type exists, data associated with the second record type is shared with the client by the network device to enable communication between the client and the server.
Owner:FORTINET
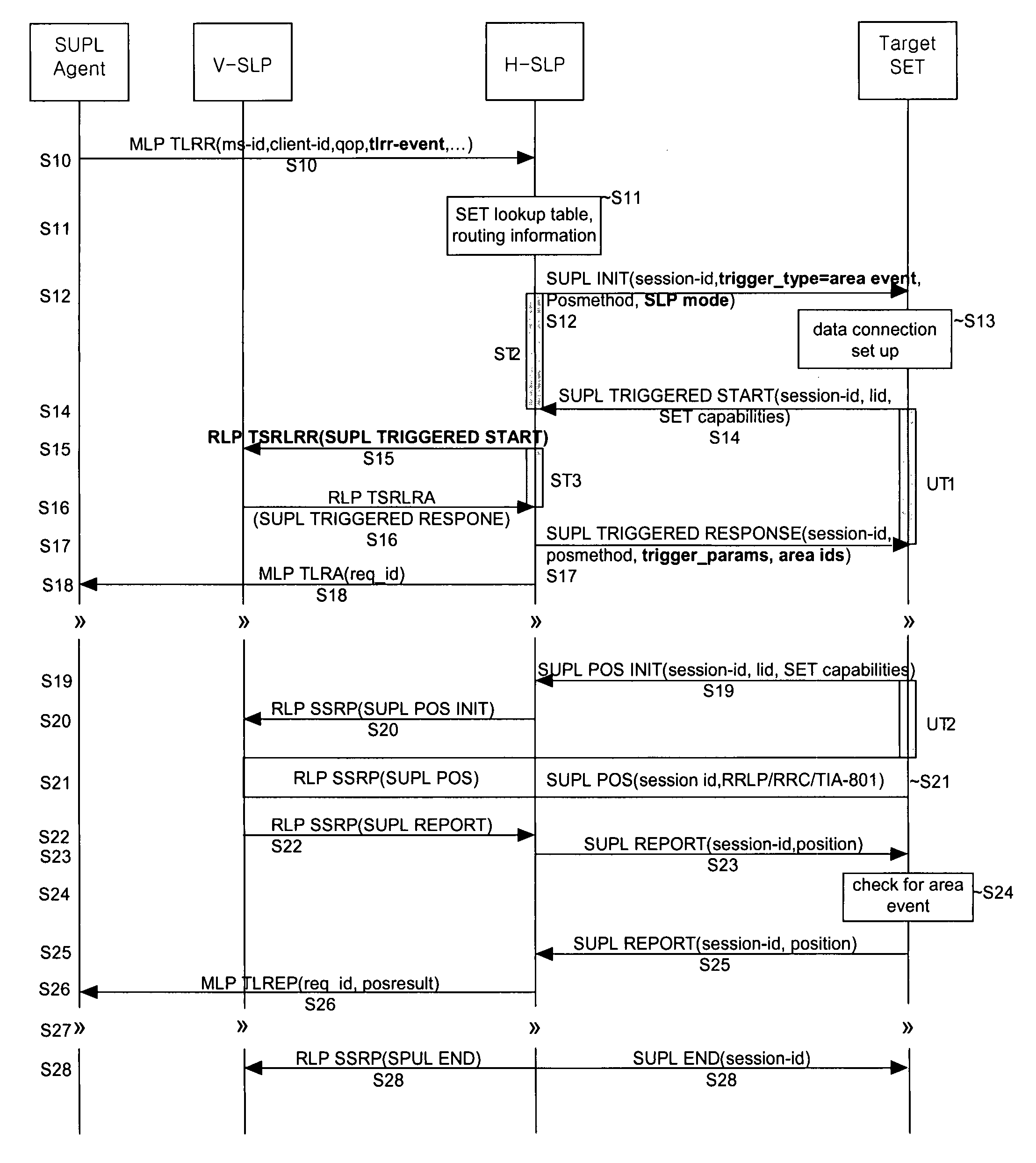
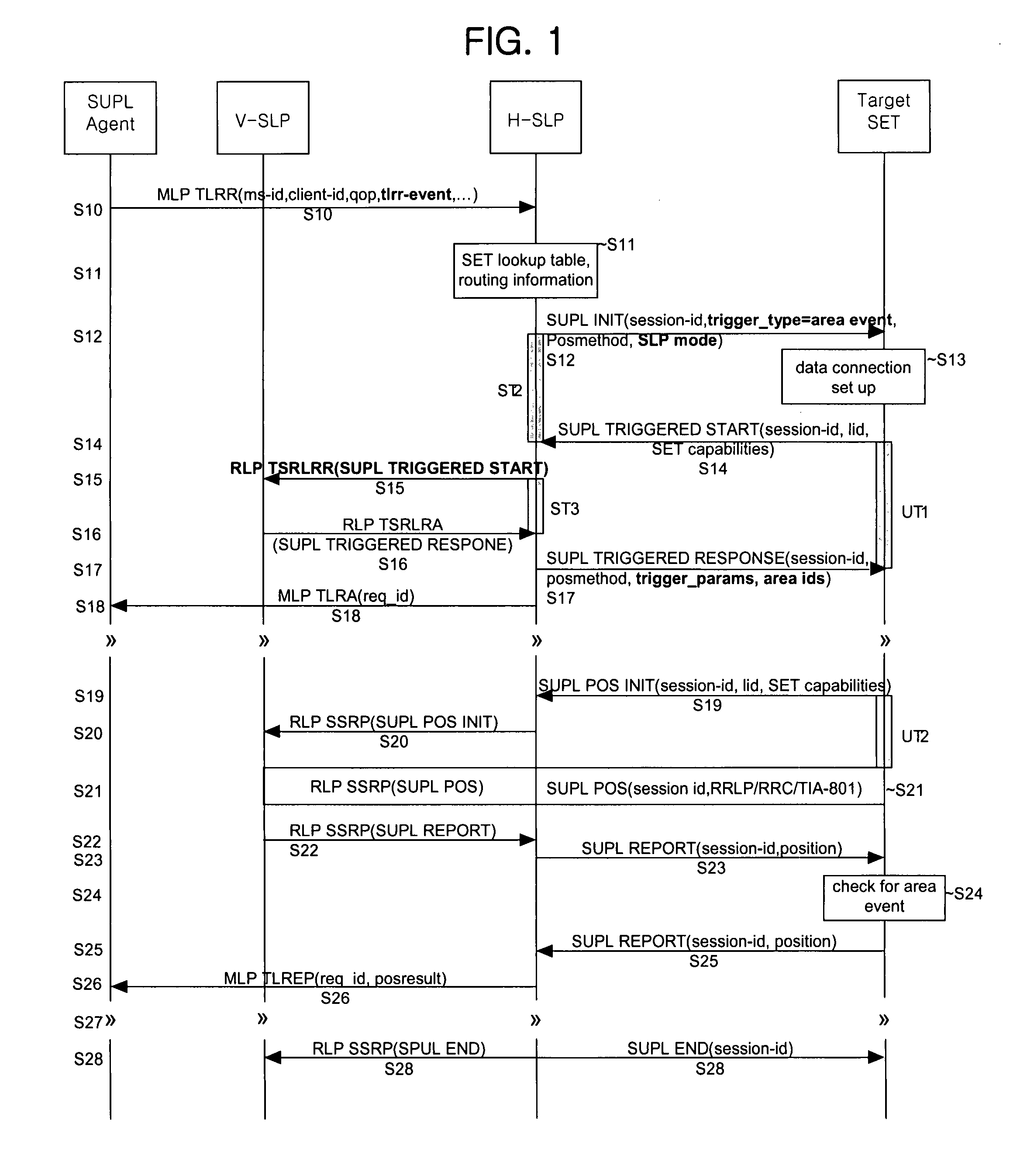
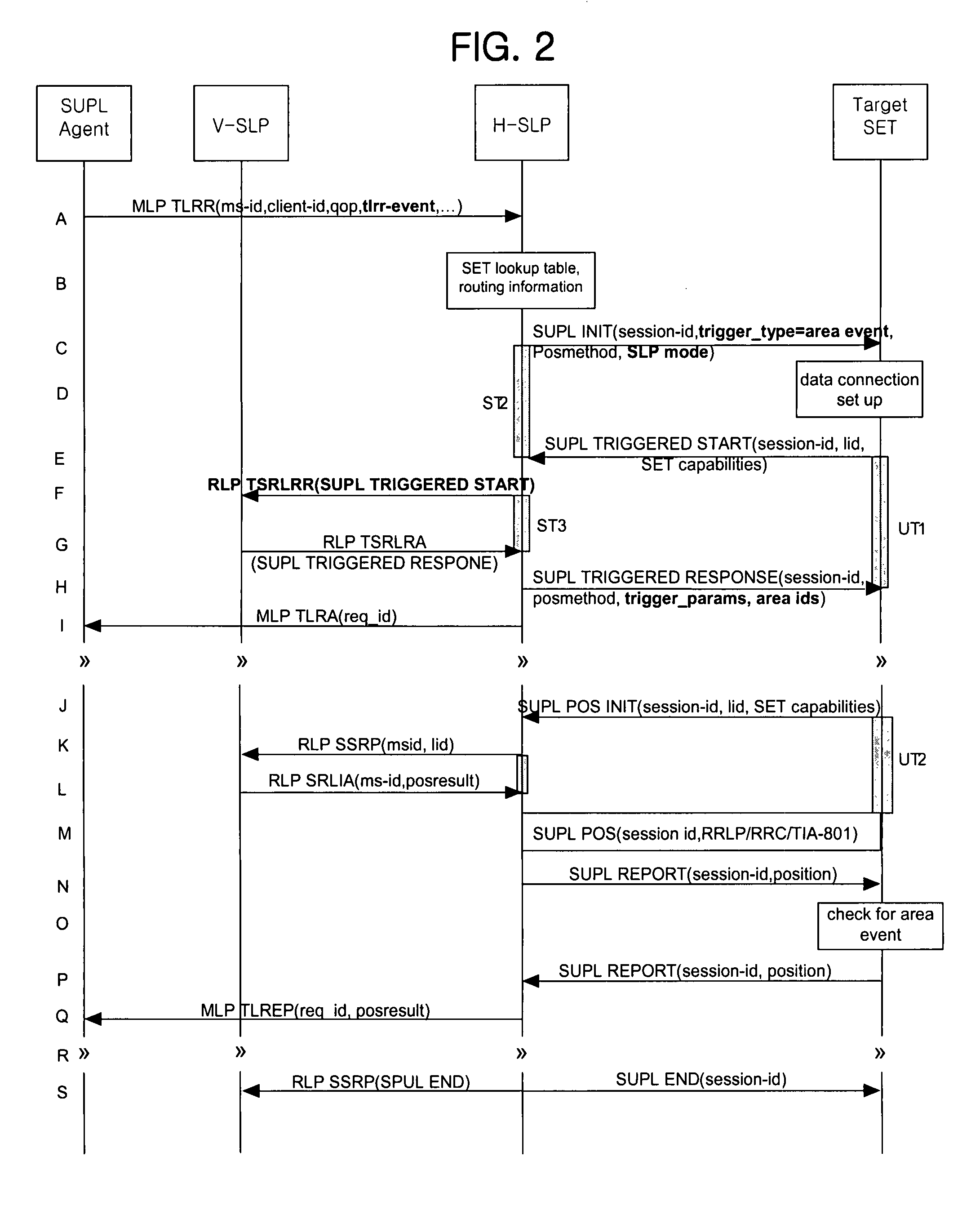
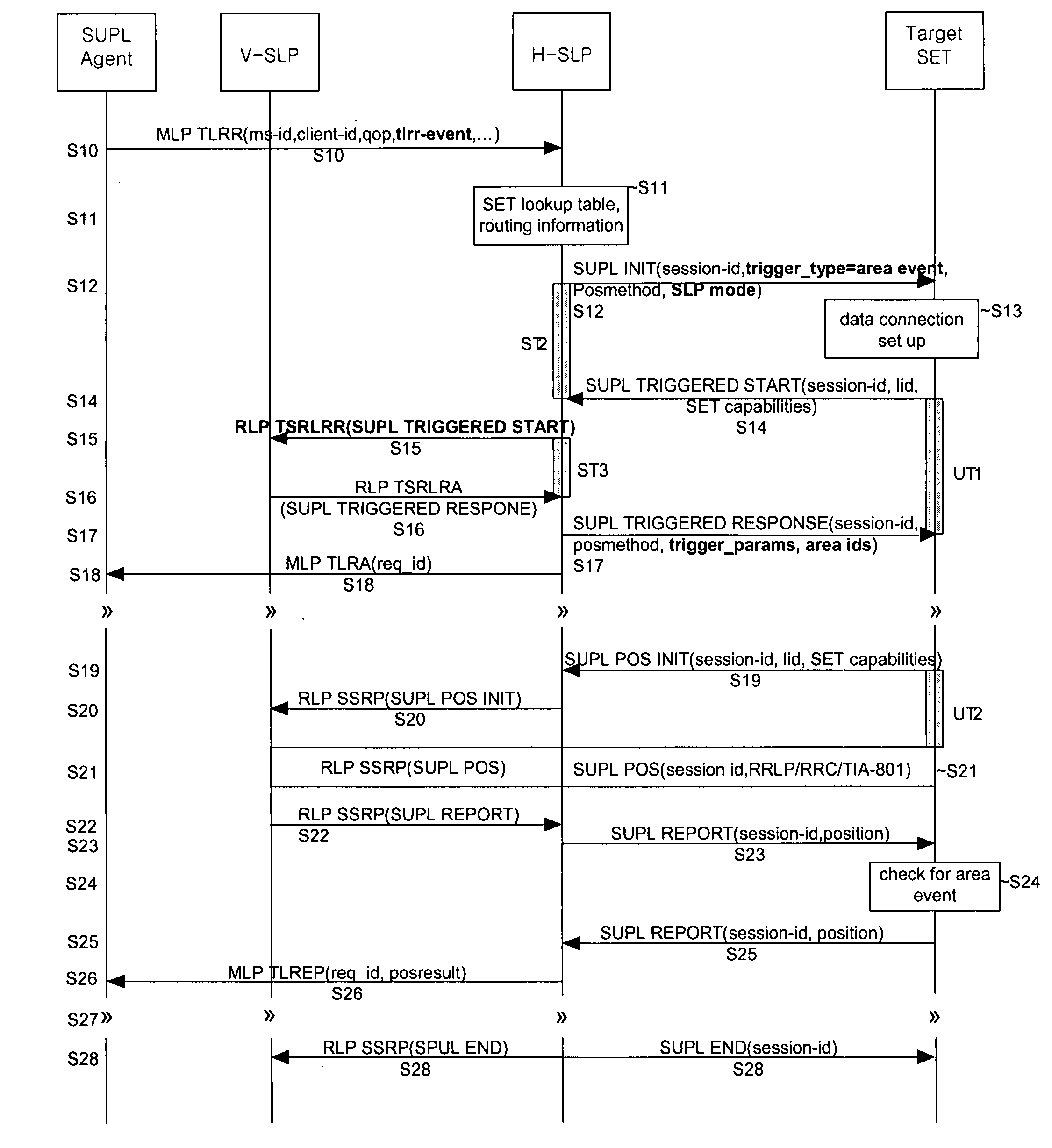
Network-initiated area event triggered positioning method for roaming terminal in mobile communication system
ActiveUS7778639B2Effective positioningPosition fixationServices signallingTelecommunicationsEvent triggered
A network-initiated area event triggered positioning method for a roaming terminal in a session-based position information system is disclosed. Network-initiation of area-based positioning of a roaming terminal is discriminated according to a proxy mode and a non-proxy mode, and area-based positioning for the roaming terminal is performed in various manners according to whether an SLP for performing the positioning procedure with respect to the discriminated modes is a V-SLP or an H-SLP.
Owner:LG ELECTRONICS INC
Live-agent-enabled teis systems
Systems for providing live-agent and hybrid live-agent access to transaction-enabled information systems are disclosed. In various embodiments, a live agent can include a person who using one or more communications devices can hear the utterances of a caller to the transaction-enabled information system and in response may respond verbally to the caller (e.g., by asking the caller for added information that the transaction-enabled information system would otherwise ask for by automated means), and / or may respond by making an input to the transaction-enabled information system (by keyboard, touch screen, verbally, or some other means) based upon the live agent's understanding of the caller's intention. In some embodiments, the transaction-enabled information system may be designed to switch to the live agent mode either automatically, when a specified requirement has been fulfilled and / or when a caller expresses an intention to proceed with the assistance of a live agent.
Owner:SPEAKSOFT
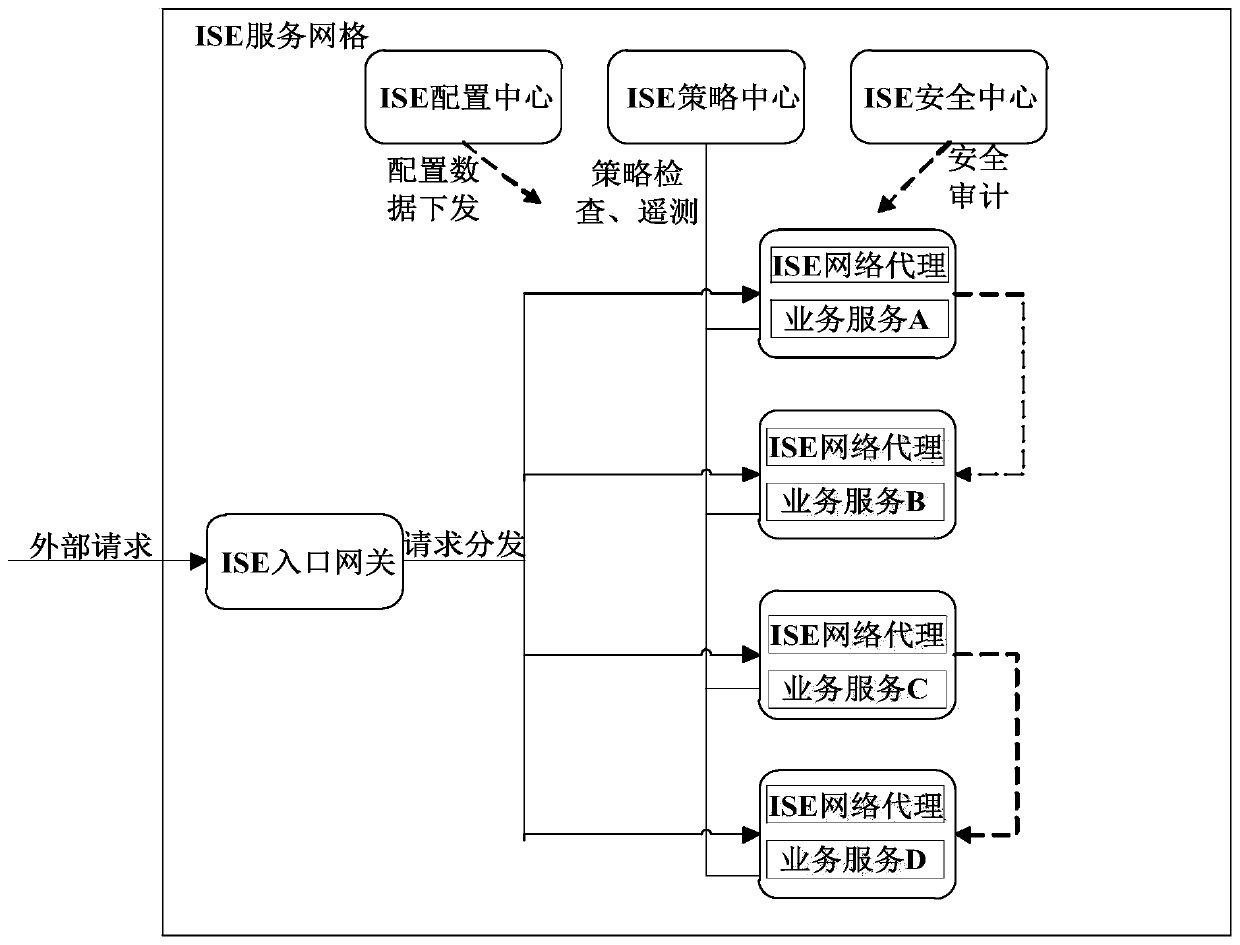
Micro-service engine based on proxy mode
ActiveCN109981789AImprove development efficiencyReduce operation and maintenance costsData switching networksNetwork agentDistributed computing
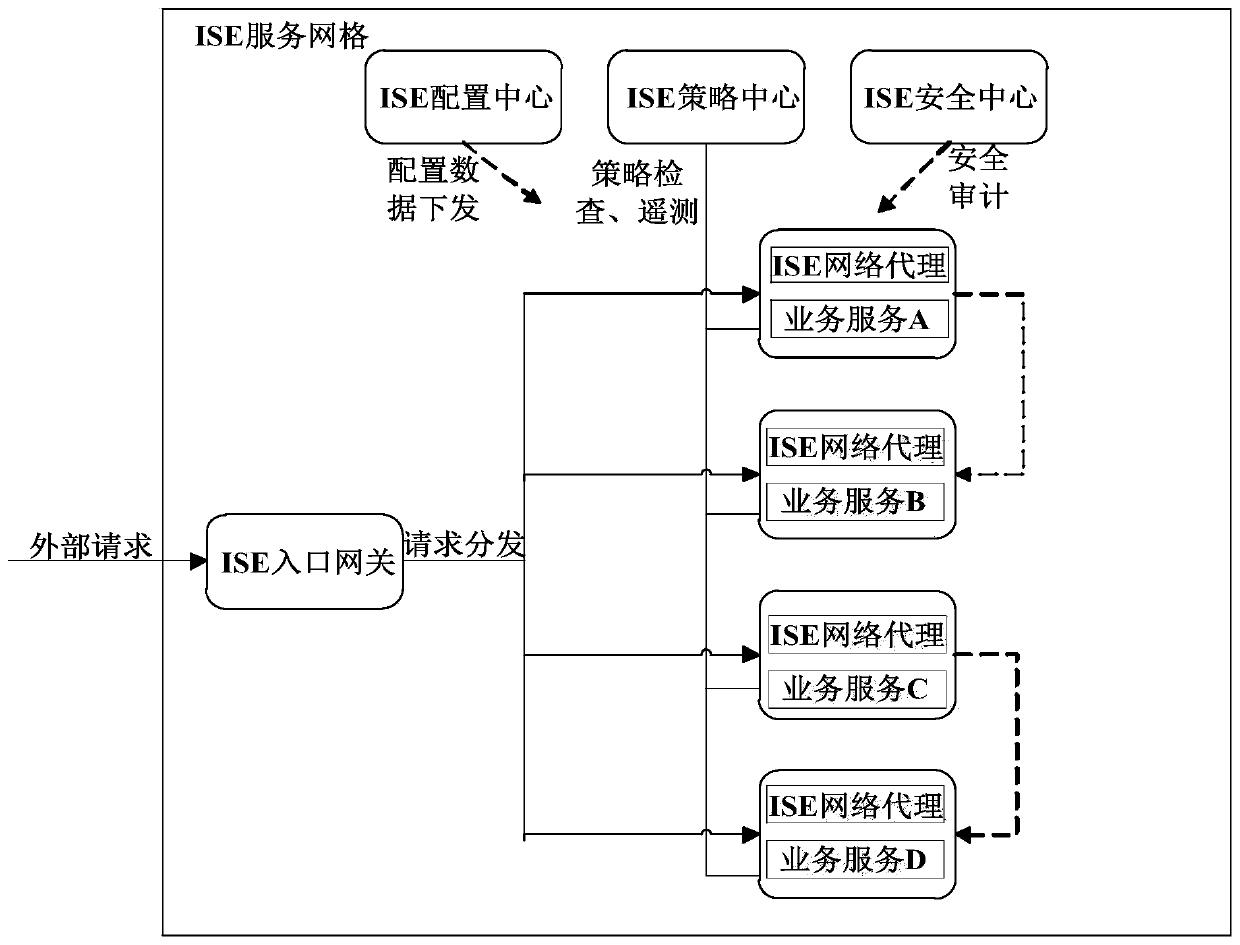
The invention particularly relates to a micro-service engine based on a proxy mode. The micro-service engine based on an proxy mode establishes an ISE service grid for deployed business services, andthe ISE service grid comprises an ISE entrance gateway, an ISE network agent, an ISE strategy center, an ISE configuration center and an ISE security center; and an external request is received through the ISE entrance gateway, and the external request is issued to the business service through the ISE network agent. According to the micro-service engine based on the proxy mode, the ISE network proxy is used for uniformly forwarding the communication flow of the micro-service application in a proxy manner, so that the problems of communication routing, flow control, fusing, safety, performancedata collection and the like among the micro-service applications are well solved, the development efficiency of the applications is improved, and the operation and maintenance cost is reduced.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Data encryption/decryption and desensitization operation engine and working method thereof
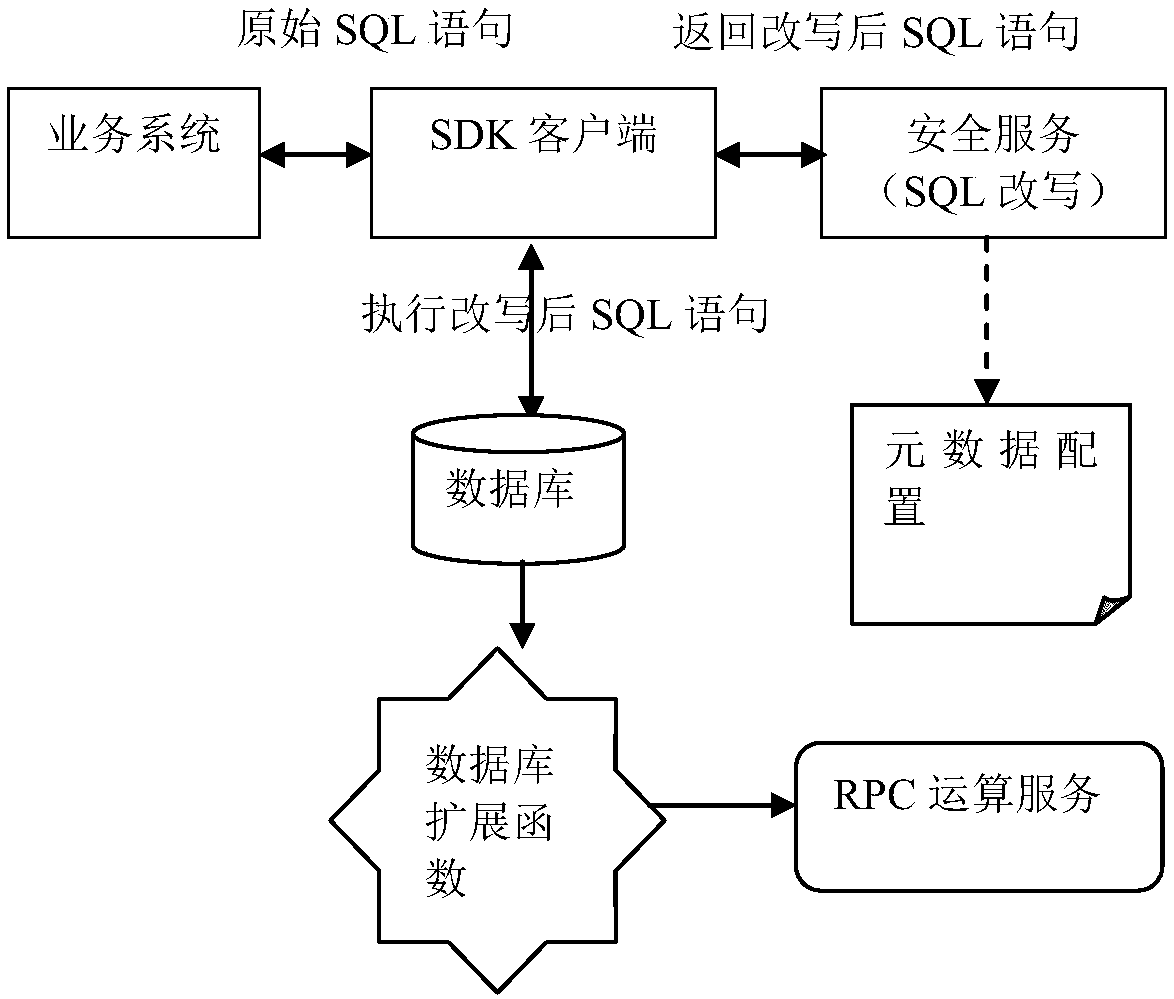
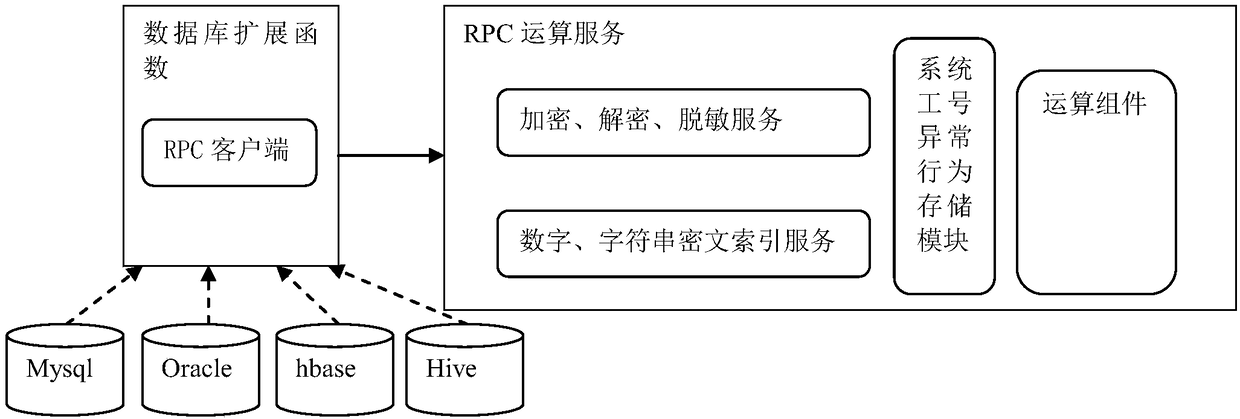
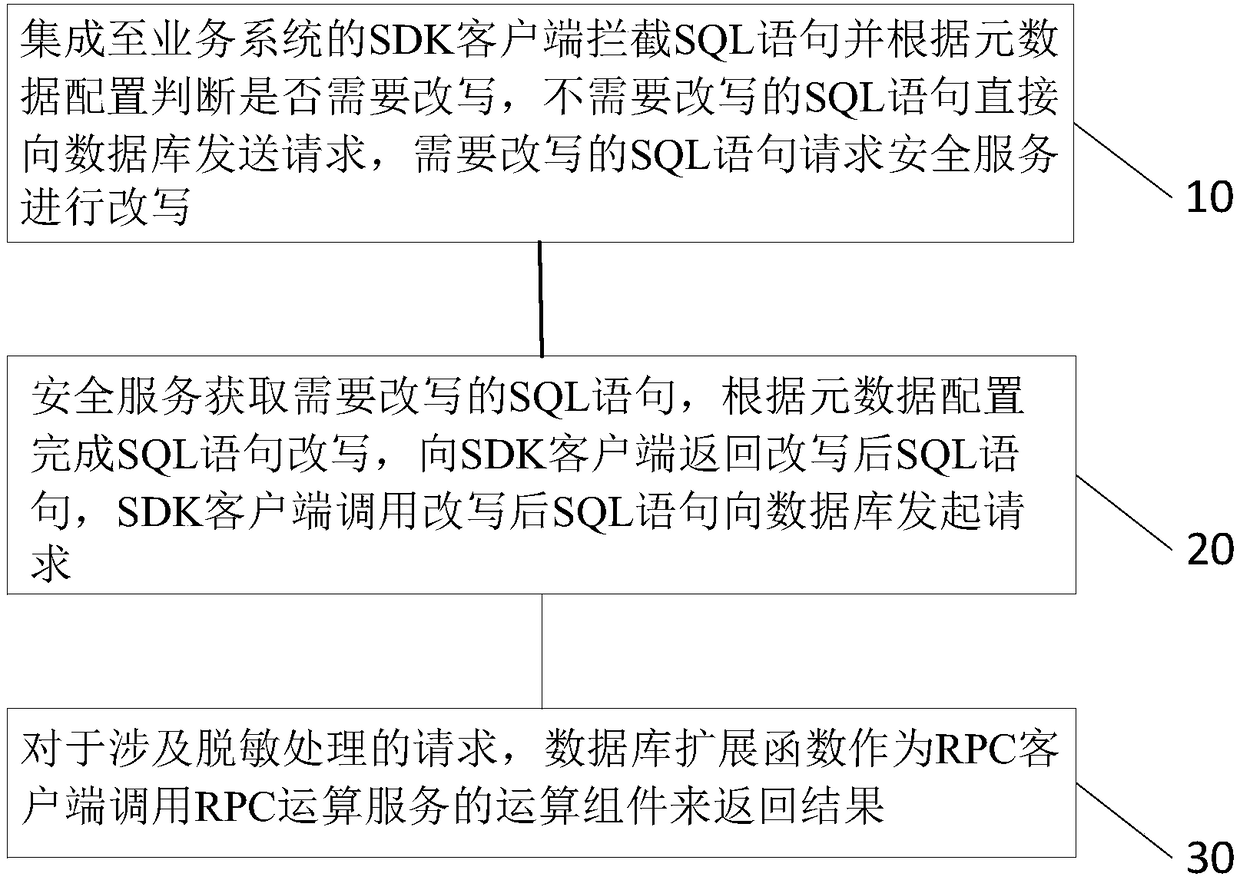
The invention relates to a data encryption / decryption and desensitization operation engine, a working method thereof and a computer readable storage medium. The working method of the data encryption / decryption and desensitization operation engine comprises the following steps of: 10, intercepting SQL statements by an SDK client integrated to a business system, judging whether the SQL statements need to be rewritten or not according to a metadata configuration, directly sending requests to a database by the SQL statements not needing to be rewritten, and requesting a security service by the SQLstatements needing to be rewritten so as to be rewritten; 20, obtaining the SQL statements needing to be rewritten by the security service, completing SQL statement rewriting according to the metadata configuration, returning the rewritten SQL statements to the SDK client, and calling the rewritten SQL statements to initiate a request to the database by the SDK client; and 30, for the request involved in desensitization processing, taking a database expansion function as an RPC client to call an operation component of an RPC operation service so as to return a result. By using a client SDK mode, the business unavailability risk, caused by stability, of transparent data encryption gateway agency mode is avoided.
Owner:SHENZHEN TIANYUAN DIC INFORMATION TECH CO LTD
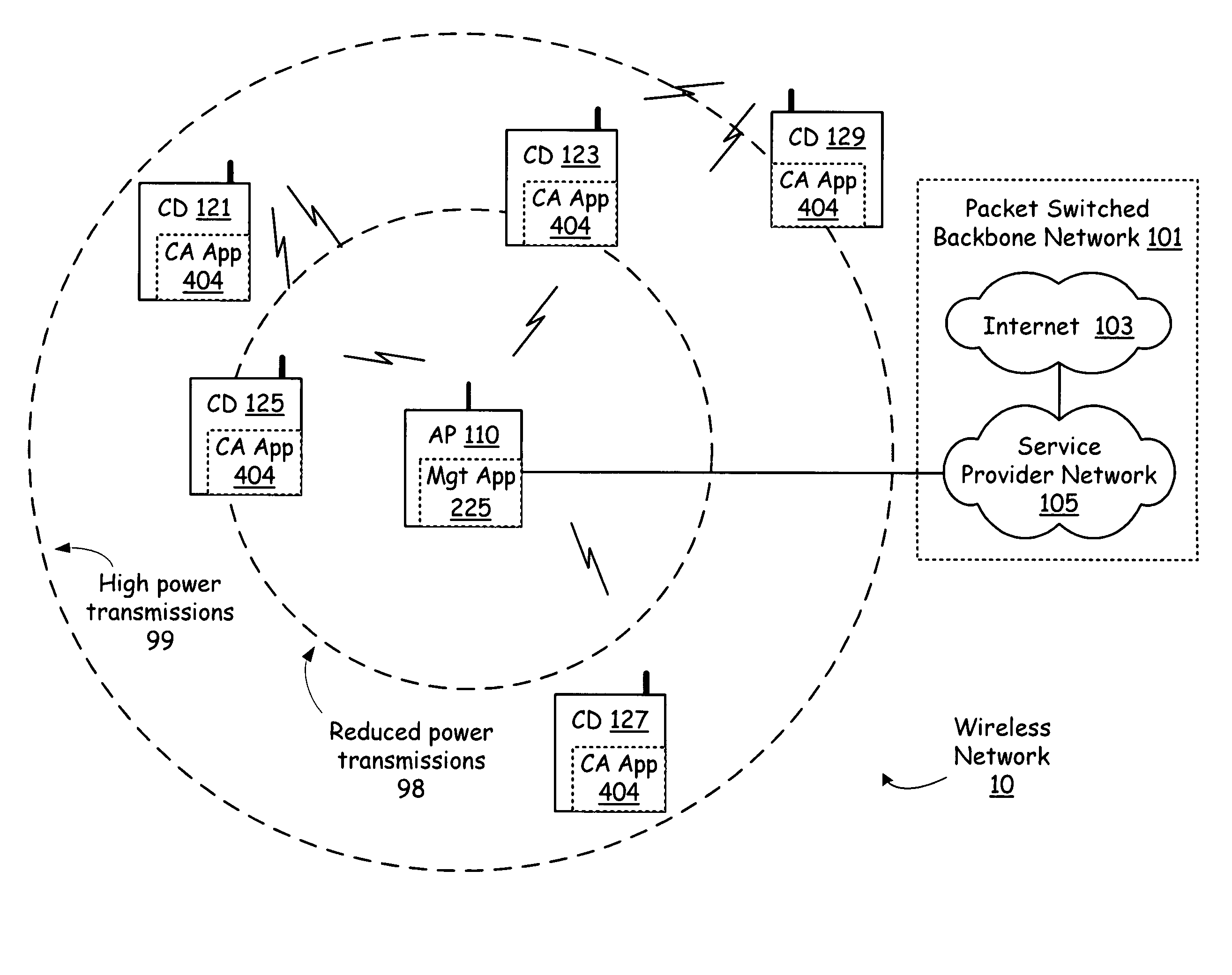
Cell network selectively applying proxy mode to minimize power
A wireless access point and multiple wireless terminals exchange utilization, status, mobility and reception characteristics. Each wireless terminal generates reception characteristics based on transmissions received from the wireless access point and from other devices in the network. In one operating mode, the characteristics gathered by the wireless devices are forwarded to the wireless access point, and, based on all received characteristics, the wireless access point selects a client device for the relay of communications between itself and another client device. In another mode of operation, the access point selects a relay proxy on a transmission by transmission basis. In response to a request, a servicing client device repeats intercepted transmissions sent by a client device and intended for the access point.
Owner:AVAGO TECH INT SALES PTE LTD
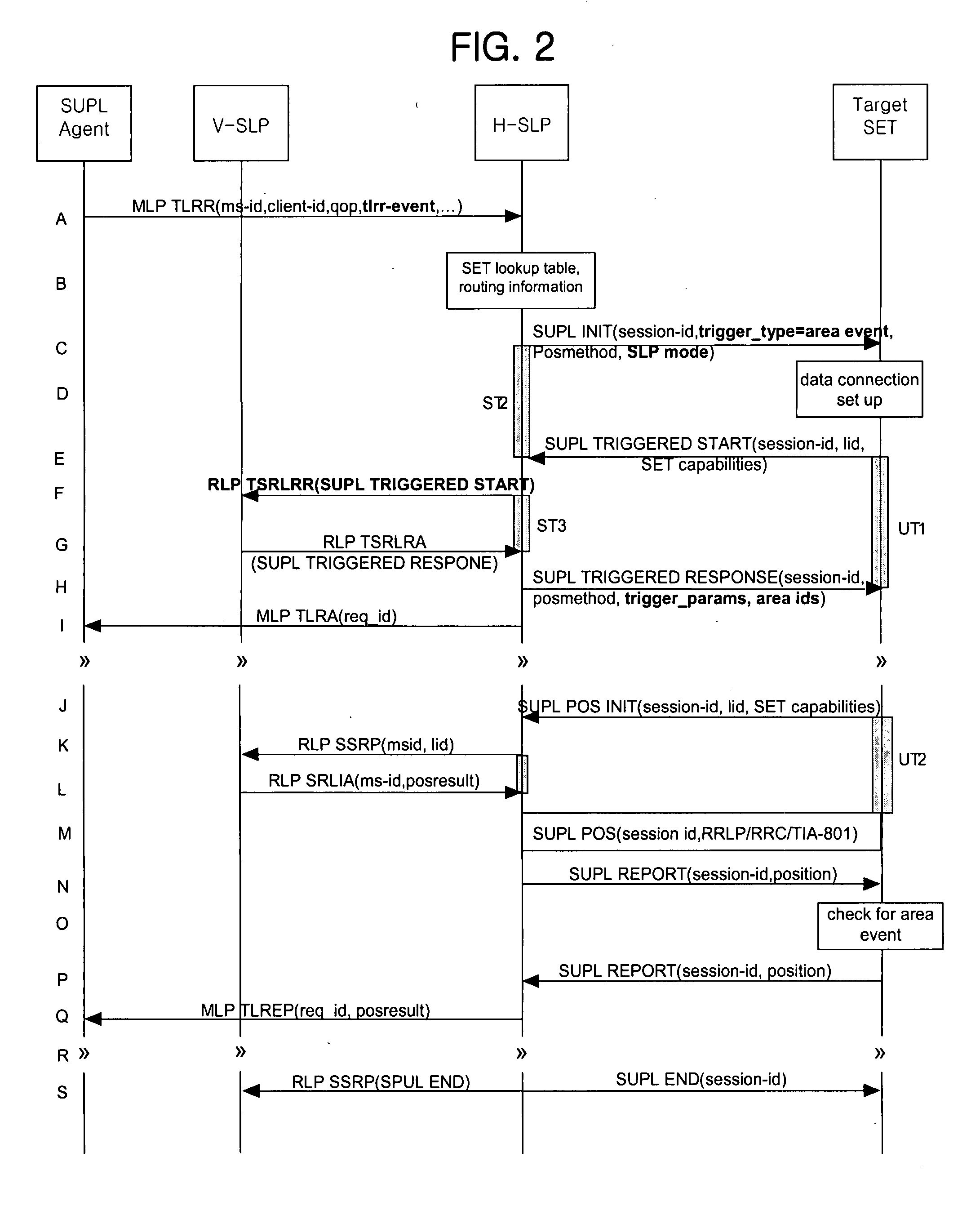
Network-initiated area event triggered positionning method for roaming terminal in mobile communication system
ActiveUS20070238458A1Effective positioningPosition fixationServices signallingTelecommunicationsEvent triggered
A network-initiated area event triggered positioning method for a roaming terminal in a session-based position information system is disclosed. Network-initiation of area-based positioning of a roaming terminal is discriminated according to a proxy mode and a non-proxy mode, and area-based positioning for the roaming terminal is performed in various manners according to whether an SLP for performing the positioning procedure with respect to the discriminated modes is a V-SLP or an H-SLP.
Owner:LG ELECTRONICS INC
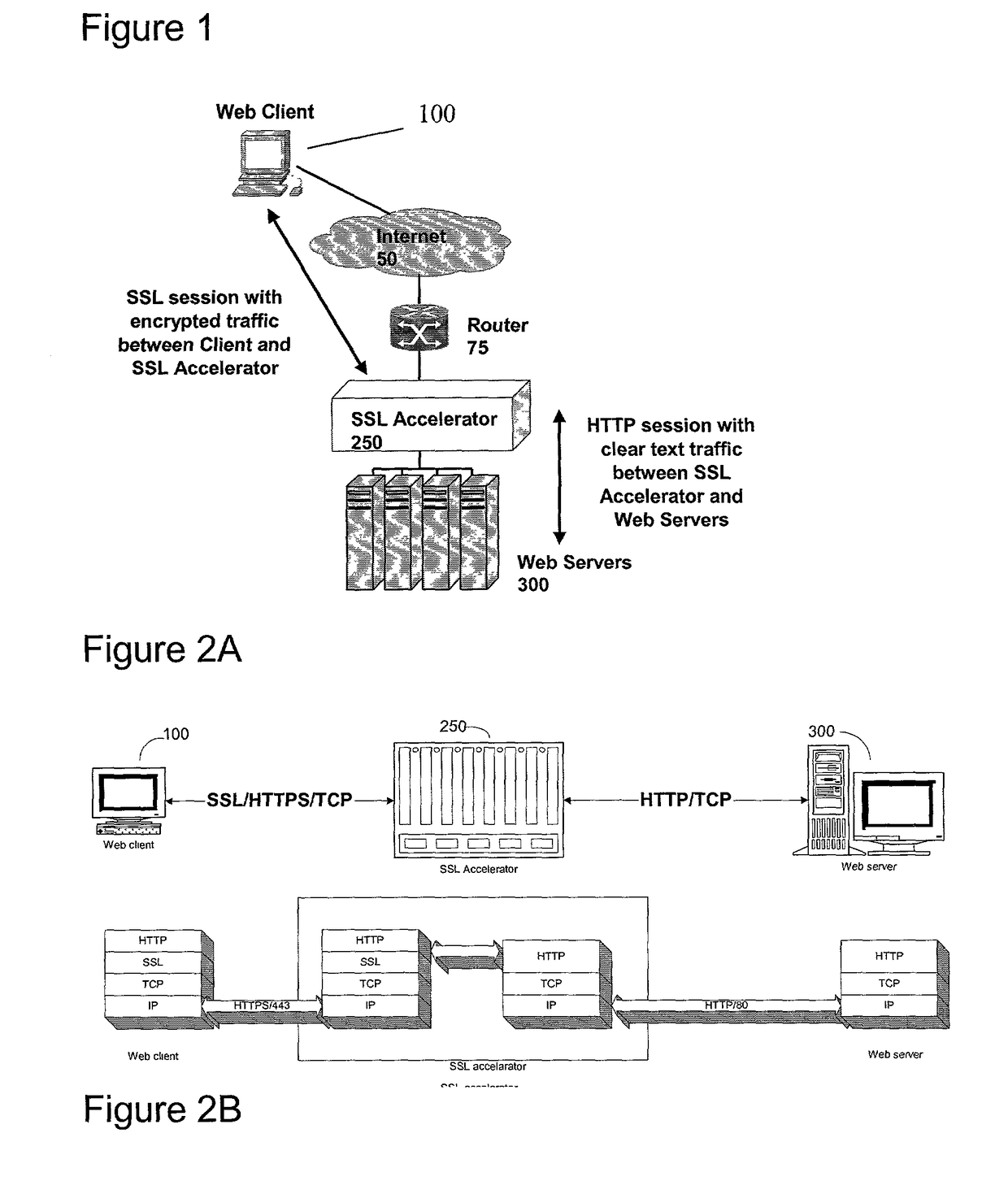
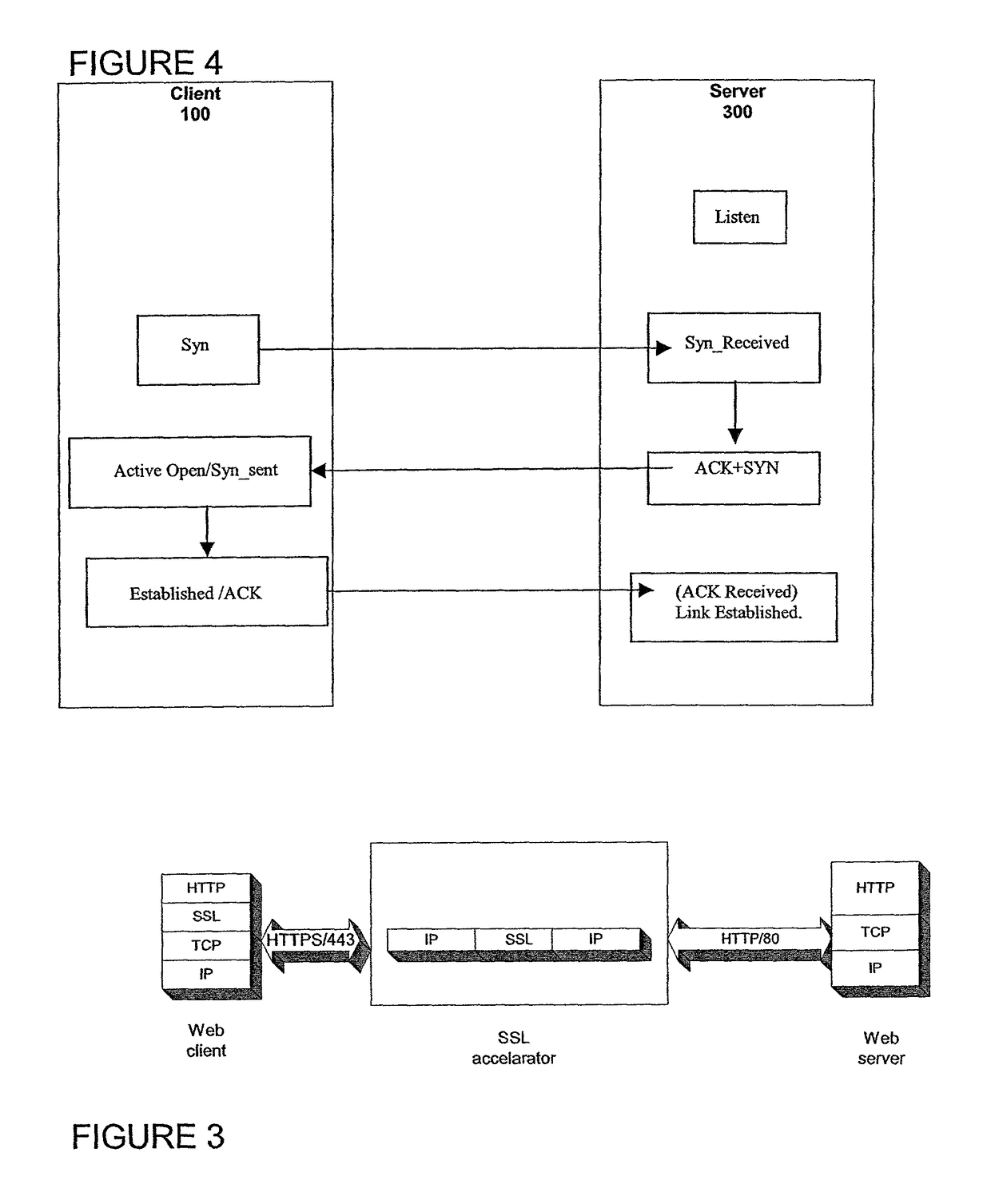
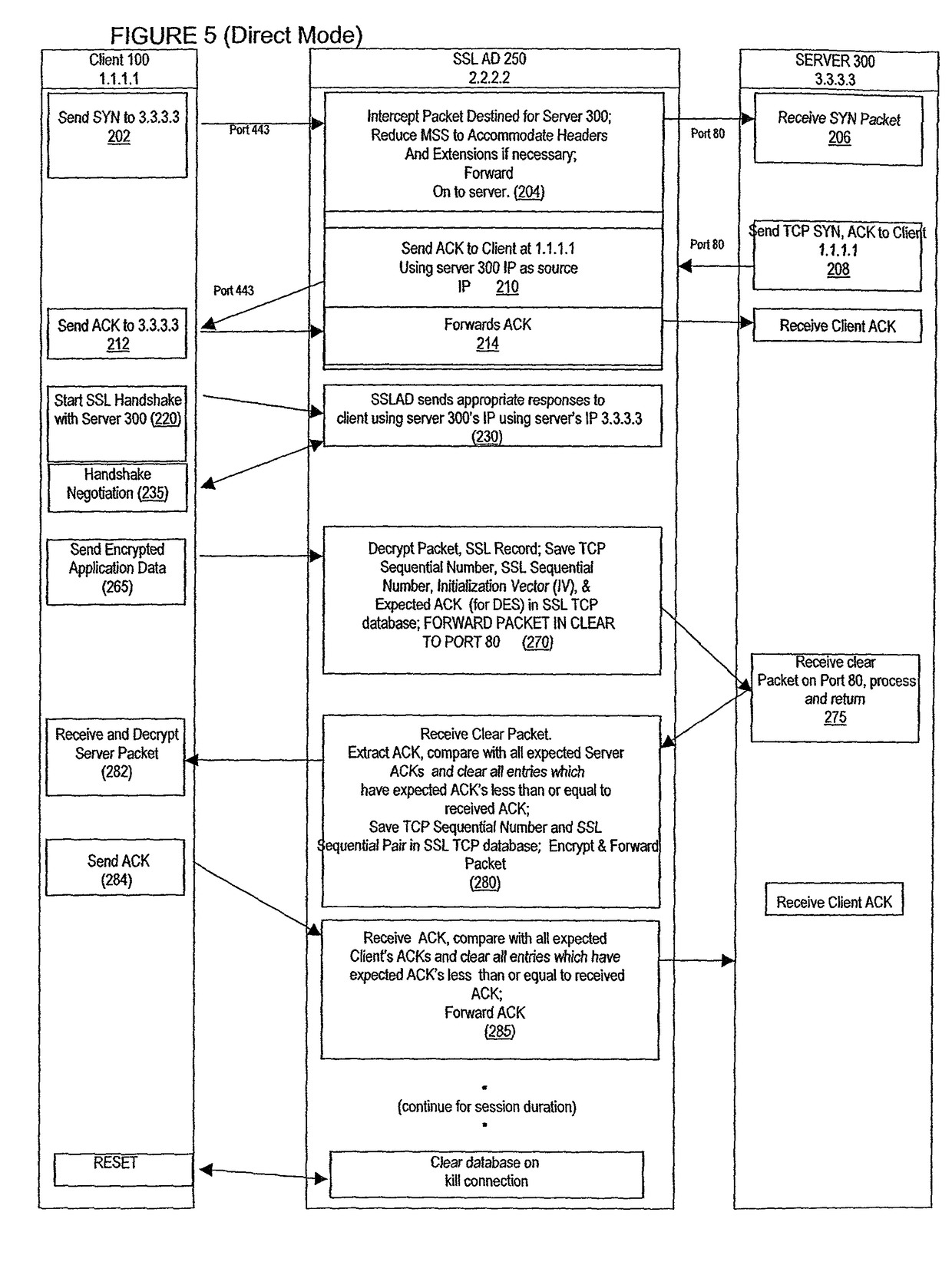
Secure sockets layer cut through architecture
ActiveUS7908472B2Reduce workloadEnhance layeringDigital data processing detailsUser identity/authority verificationData packEngineering
An acceleration apparatus is adapted to operate in a direct mode and a proxy mode. In the direct mode, the acceleration apparatus decrypts data packets received from a client and forwards the decrypted data packets to a server using a communication session negotiated by the client and the server. In the proxy mode, the acceleration apparatus responds to the client on behalf of the server and forwards the decrypted data packets to the server using a communication session negotiated by the acceleration device and the server. The acceleration apparatus automatically switches from the direct mode to the proxy mode upon detection of a communication error associated with the communication session negotiated by the client and the server.
Owner:NEXSI SYST
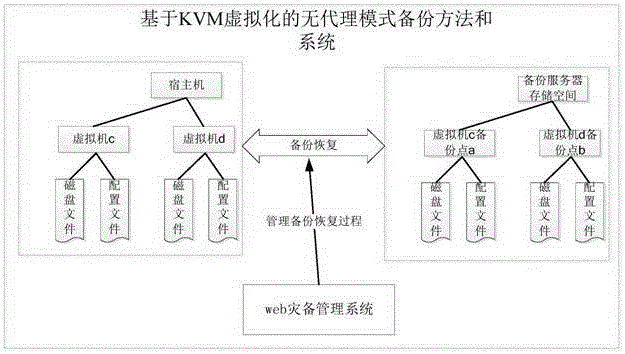
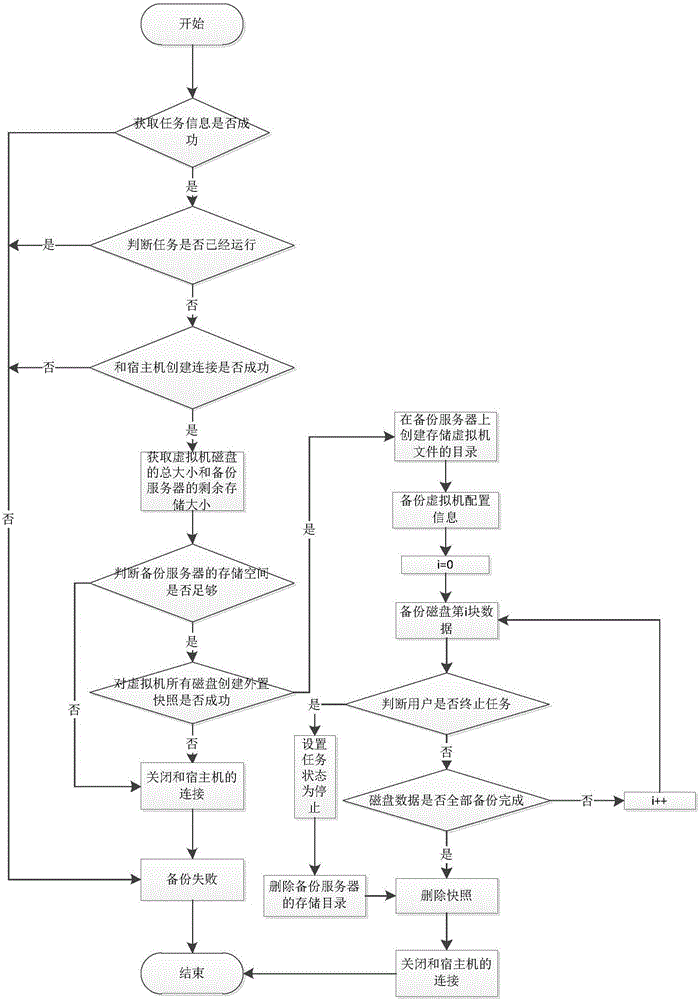
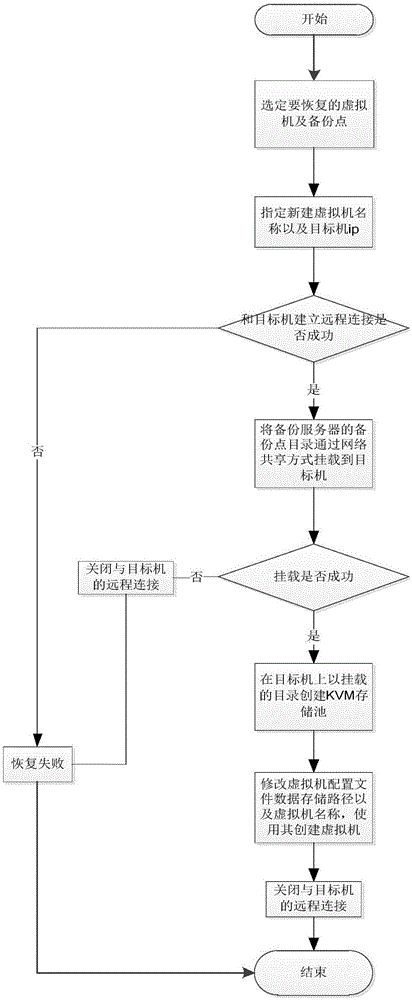
KVM virtualization-based agency mode-free backup method and system
ActiveCN106445733AReduce maintenance costsShorten the timeRedundant operation error correctionDatabase backupStop time
The invention relates to the technical field of database backup and recovery, in particular to a KVM virtualization-based agency mode-free backup method. The method comprises the steps of registering a host, in which a virtual machine needed to be backed up is located, in a web disaster recovery backup management system; creating a backup task; starting the backup task; creating a quick recovery task; and starting the quick recovery task, thereby realizing data backup and quick recovery. The invention furthermore provides a KVM virtualization-based agency mode-free backup system. The system comprises the web disaster recovery management system for managing the whole backup recovery process, the host comprising two or more virtual machines, and a backup server for backing up disk files and configuration files of the virtual machines. According to the method and the system, agency mode-free backup is adopted, so that system deployment and personnel maintenance costs are greatly reduced; and second-level quick recovery of the virtual machines is supported, so that enterprise application stop time is shortened and enterprise loss is reduced.
Owner:广州鼎甲计算机科技有限公司
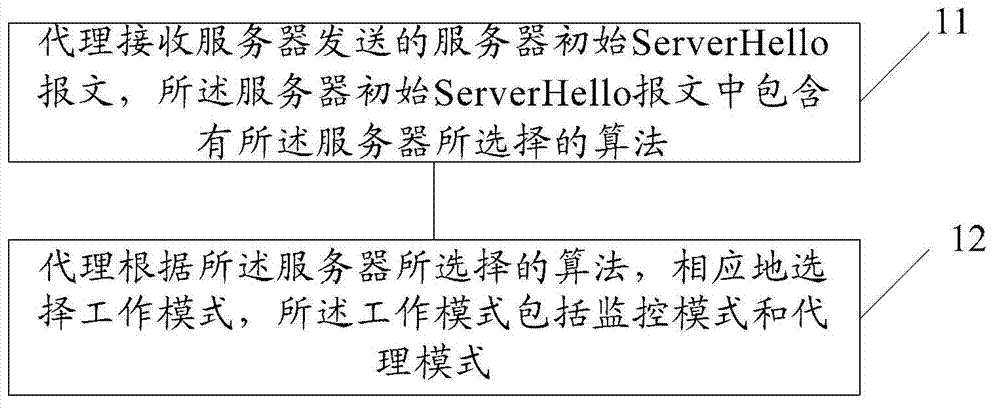
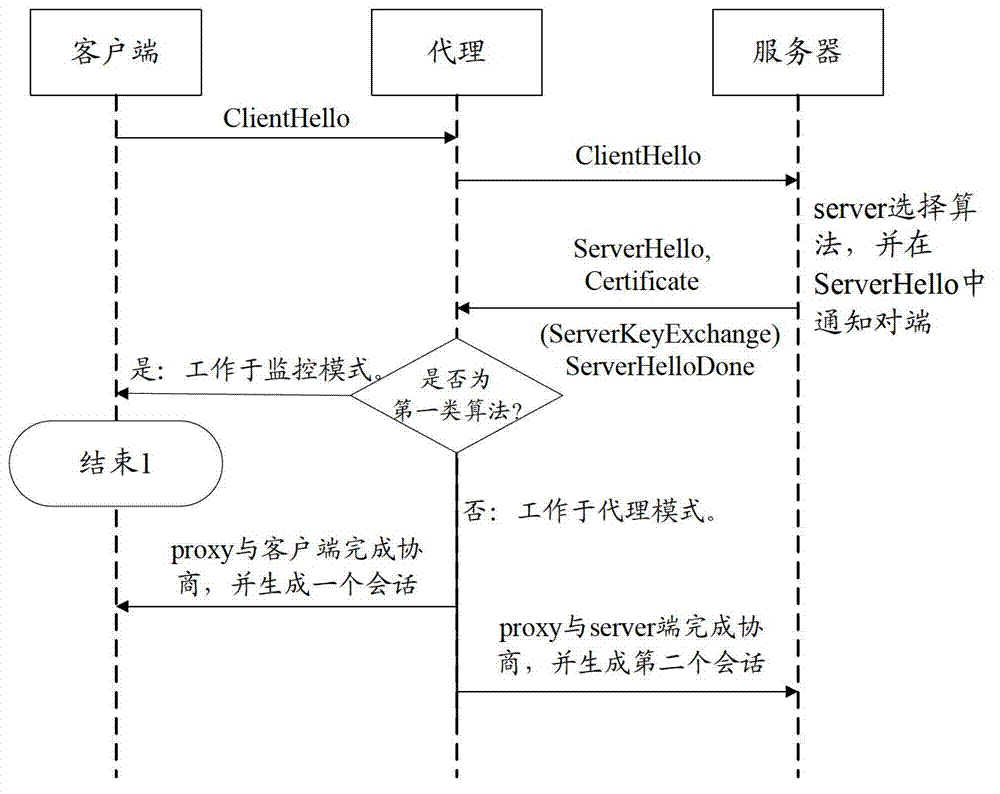
TLS (Transport Layer Security) scanning method and device
The embodiments of the invention provide a TLS (Transport Layer Security) scanning method, relating to the field of enciphered communication. During server-side scanning, the method can efficiently support the certification of various algorithms and / or clients. The method comprises the following steps that: a proxy receives a server initial message sent by a server, wherein the server initial message comprises algorithms selected by the server; and the proxy selects working modes correspondingly according to the algorithms selected by the server, wherein the working modes comprise a monitor mode and a proxy mode so as to support the certification of the algorithms and / or clients selected by the server, and the proxy does not change any message in the monitor mode and changes the message in the proxy mode. The embodiments of the invention further provide a corresponding network device.
Owner:HUAWEI TECH CO LTD
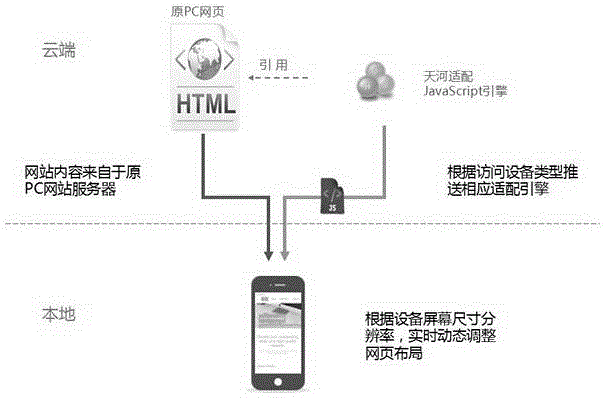
Method for converting PC terminal WEB webpage into mobile terminal WEB webpage
ActiveCN105138542AShorten the timeReduce labor costsWebsite content managementSpecial data processing applicationsTerminal webPersonal computer
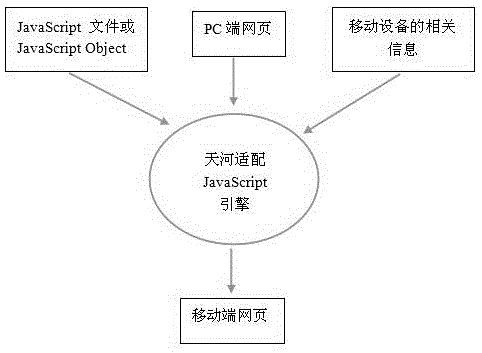
The invention discloses a method for converting a PC (Personal Computer) terminal WEB (the World Wide Web) webpage into a mobile terminal WEB webpage. According to the method, original webpage information is subjected to information configuration; a Tianhe adaptation JavaScript engine is used for modifying the attribute of a specified label, so that the specified label can adapt to a mobile terminal browser; the goal of direct logging-in from a mobile terminal for PC terminal webpage browsing is achieved; the single development of mobile terminal WEB versions is not needed; the development cost and the maintenance cost can be effectively reduced on the premise of sufficiently using the contents of an original website and maintaining the original interface appearance; the development can be completed only through little time and little labor cost, so that the mobile terminal and the PC terminal maintain the same website; and a proxy pattern can also be selected, and different websites are used.
Owner:BEIJING TIANHESHI TECH CO LTD
Supl initialization message in a location information system and method and system for processing supl by using the same
ActiveUS20090209269A1Accurate identificationWireless network protocolsMessaging/mailboxes/announcementsInitMessage processing
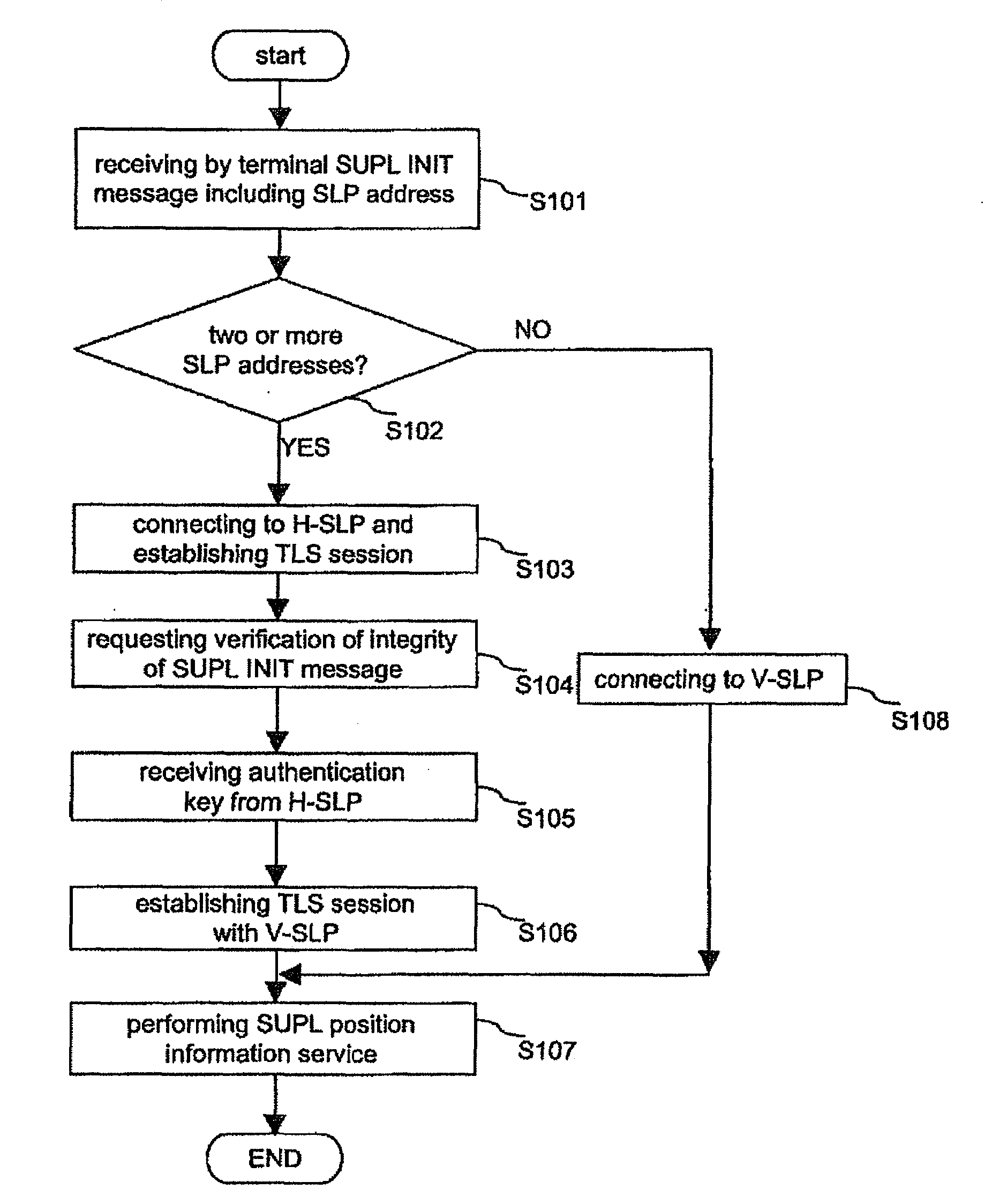
A terminal and method and system for processing SUPL are discussed. According to one embodiment, the invention provides a method of processing a SUPL request for a terminal that has performed roaming, the method comprising: receiving a SUPL INIT message from a home SLP entity, the SUPL INIT message including an indicator that indicates whether a home SLP entity uses a proxy mode or a non-proxy mode; checking the indicator to determine whether a first message or a second message should be transmitted to the home SLP entity; and transmitting the first message or the second message to the home SLP entity according to a result of the checking step.
Owner:LG ELECTRONICS INC
IP address reduction method under transparent reverse proxy mode
ActiveCN106453272ADeployment transparencyImprove the protective effectTransmissionNetwork deploymentReverse proxy
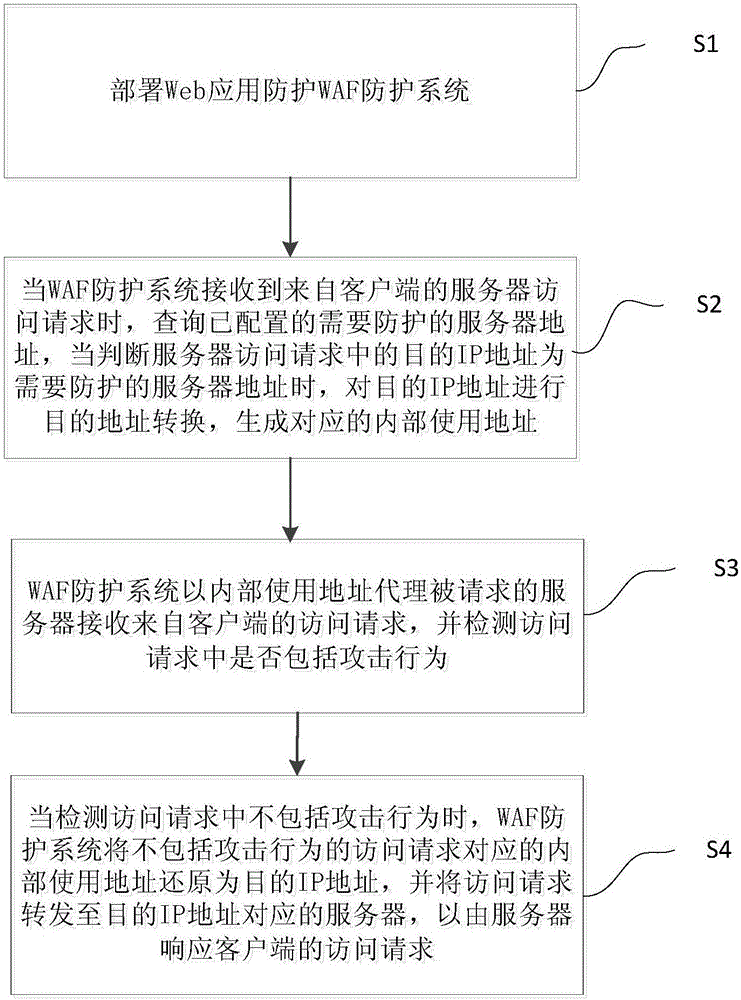
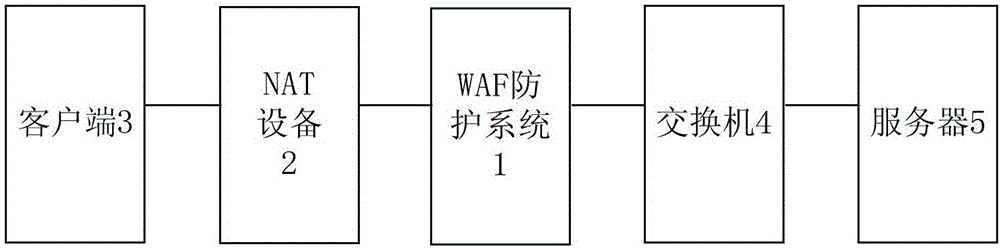
The invention provides an IP address reduction method and system under a transparent reverse proxy mode. The method comprises the following steps: deploying a WAF protection system; when the WAF protection system receives a server access request from a client, performing target address conversion on a target IP address to generate a corresponding internal use address; using the internal use address to act for a requested server by the WAF protection system to receive the access request from the client, and detecting whether the access request comprises an attack behavior; restoring the internal use address corresponding to the access request excluding the attack behavior as the target IP address by the WAF protection system, and forwarding the access request to a server corresponding to the target IP address. The transparence of the WAF proxy mode to the network environment and the business server is realized, the proxy address is unnecessary to be configured in the network deployment, the deployment is transparent through the tracking conversion on a source IP on the basis of the connection tracking technology.
Owner:WEBRAY TECH BEIJING CO LTD
User equipment, method and system for simultaneous session control
ActiveUS20090124246A1Network traffic/resource managementWireless network protocolsSession controlData transmission
A user equipment (UE), method and system for processing session based communications, are discussed. According to an embodiment, the method includes receiving a message from a terminal that informs whether the terminal supports simultaneous PT (push-to) sessions; recognizing that the terminal supports simultaneous PT sessions according to the received message; and transporting data to one or more terminals through the server operating in B2BUA (Back-to-Back User Agent) mode, wherein a simultaneous PT session refers to a session where the server performs a PT session priority function or a PT session locking function.
Owner:LG ELECTRONICS INC
Bandwidth detection in a heterogeneous network with parallel and proxy modes
InactiveUS20060072620A1QuicklyEnabling detectionResonant long antennasTime-division multiplexNetworking protocolTelecommunications link
Effective bandwidth of a communication link is determined in a heterogeneous, packet switched network between a source and a destination, where effective bandwidth is defined as the actual available bandwidth between the server and the client, minus the overhead of the various network protocols used to transmit the data. The method includes maintaining a database of bandwidth parameters indexed by destination address, and using the database when setting a communication channel.
Owner:ADOBE SYST INC
Usage of nonce-based authentication scheme in a session-based authentication application
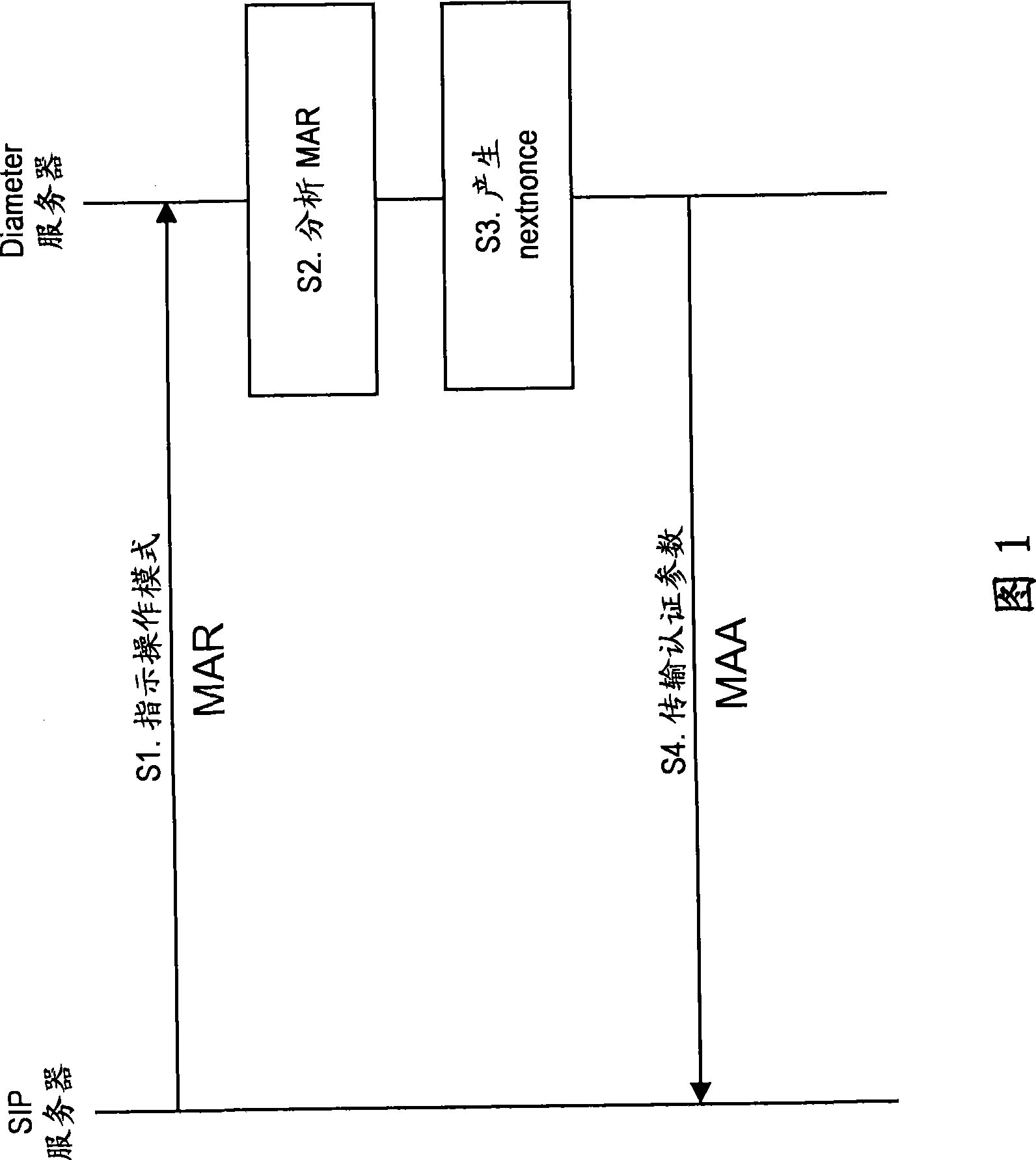
InactiveUS20080005785A1Improve cooperationDigital data processing detailsUser identity/authority verificationCommunications systemSession control
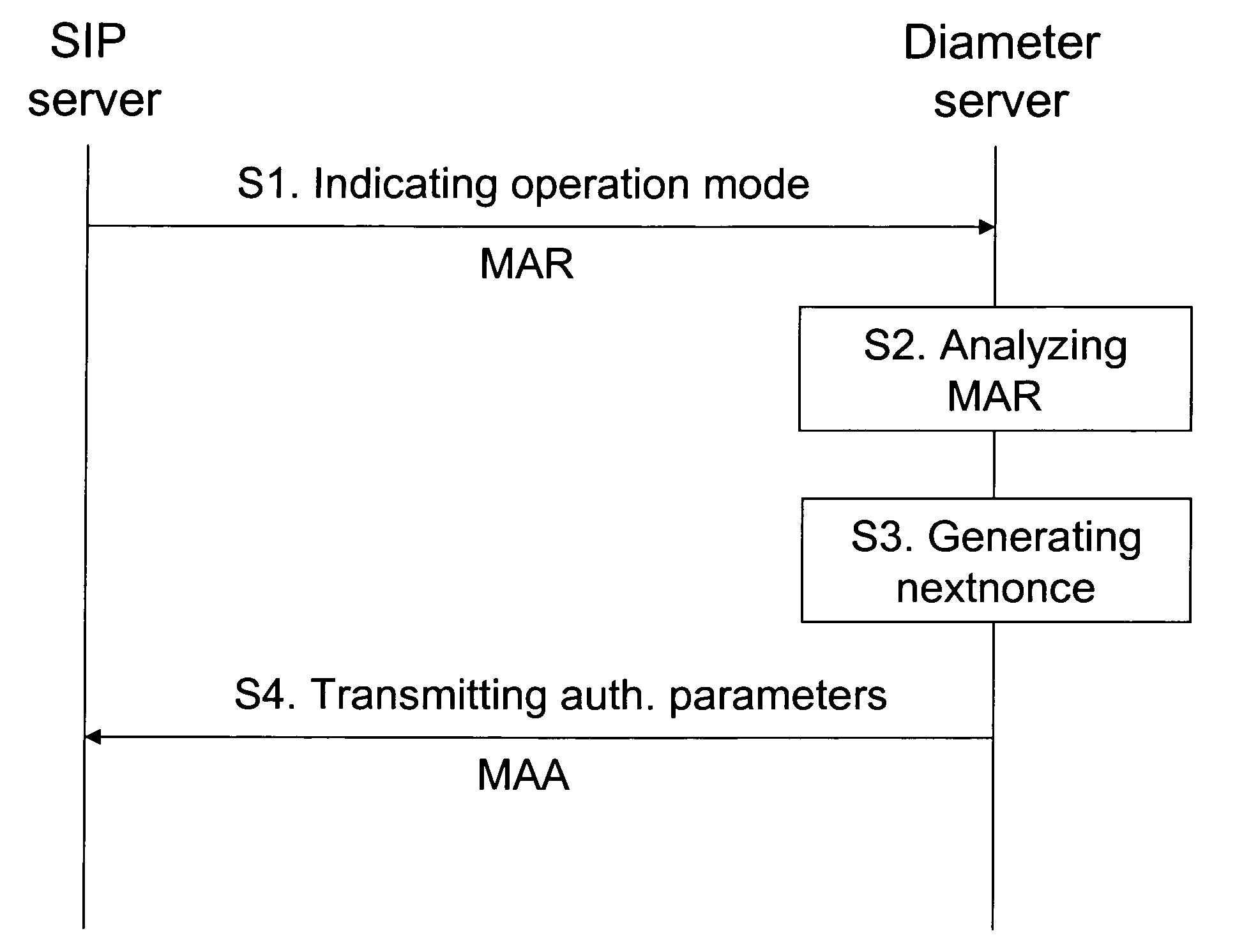
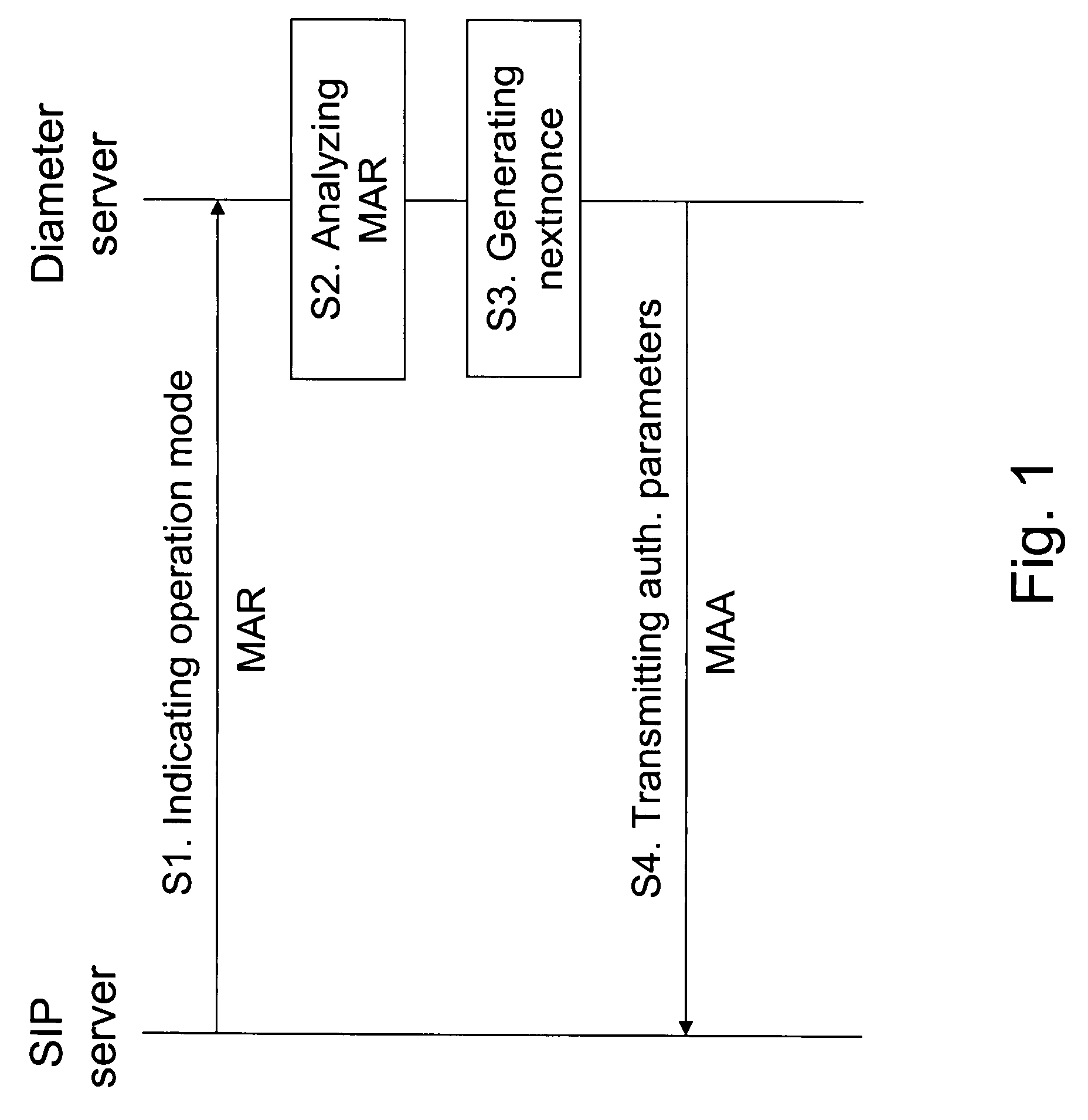
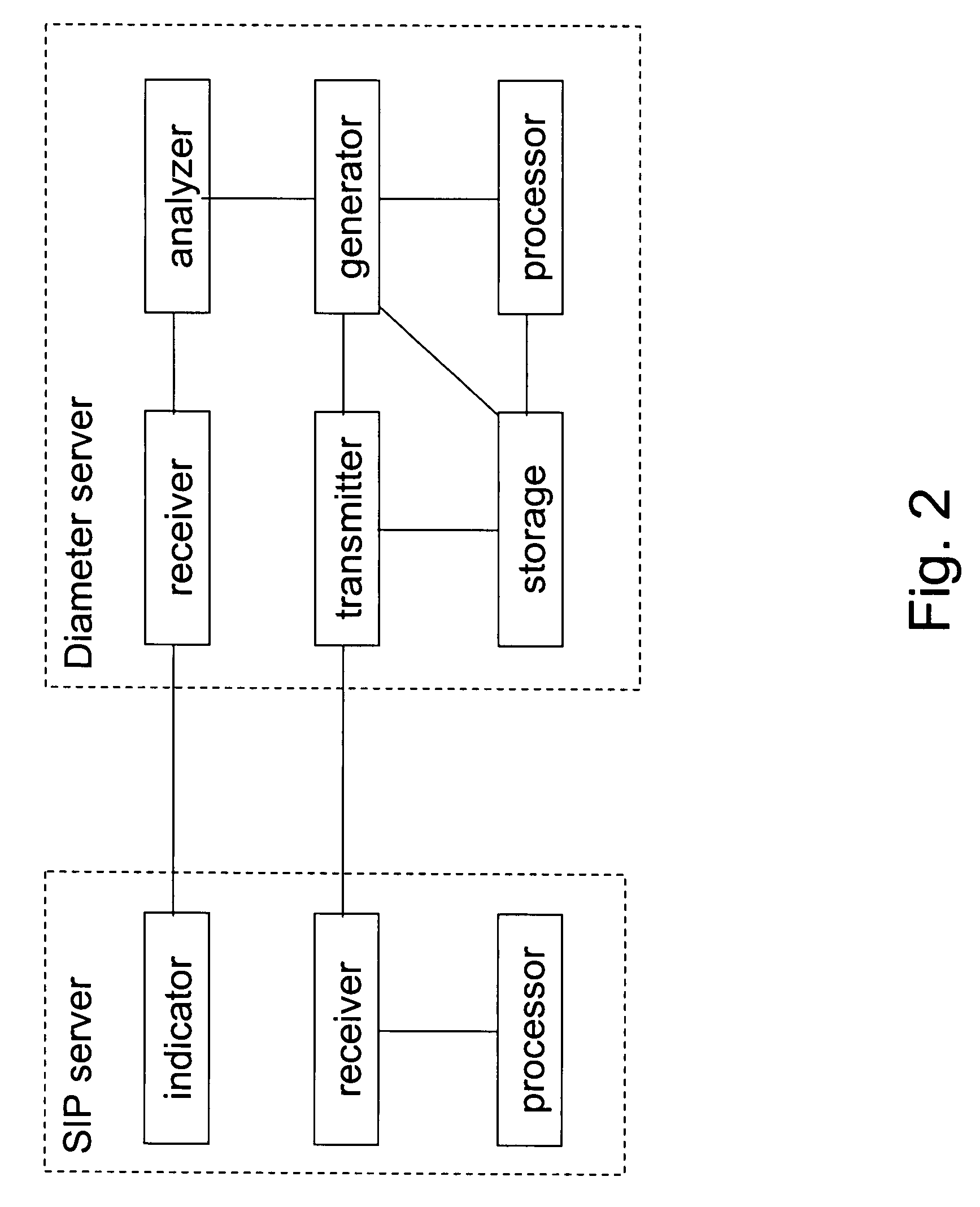
Usage of nonce-based authentication scheme in a session-based authentication application, usable in a communication system comprising a session control server and an authentication server, which are configured to provide for a session-based authentication application, wherein authentication is based on a nonce-based authentication scheme, comprising an indication of an operation mode of the session control server from the session control server to the authentication server in an authentication request, wherein the operation mode included proxy mode and user agent mode.
Owner:NOKIA CORP
Supl initialization message in a location information system and method and system for processing supl by using the same
ActiveUS20090215467A1Accurate identificationWireless network protocolsMessaging/mailboxes/announcementsInitData mining
A terminal and method and system for processing SUPL are discussed. According to one embodiment, the invention provides a method of processing a SUPL request for a terminal that has performed roaming, the method comprising: receiving a SUPL INIT message from a home SLP entity, the SUPL INIT message including an indicator that indicates whether a home SLP entity uses a proxy mode or a non-proxy mode; checking the indicator to determine whether the home SLP operates in the proxy mode or the non-proxy mode; and selectively performing authentication with the home SLP entity based on the checking result indicating whether the home SLP entity operates in the proxy mode or the non-proxy mode.
Owner:LG ELECTRONICS INC
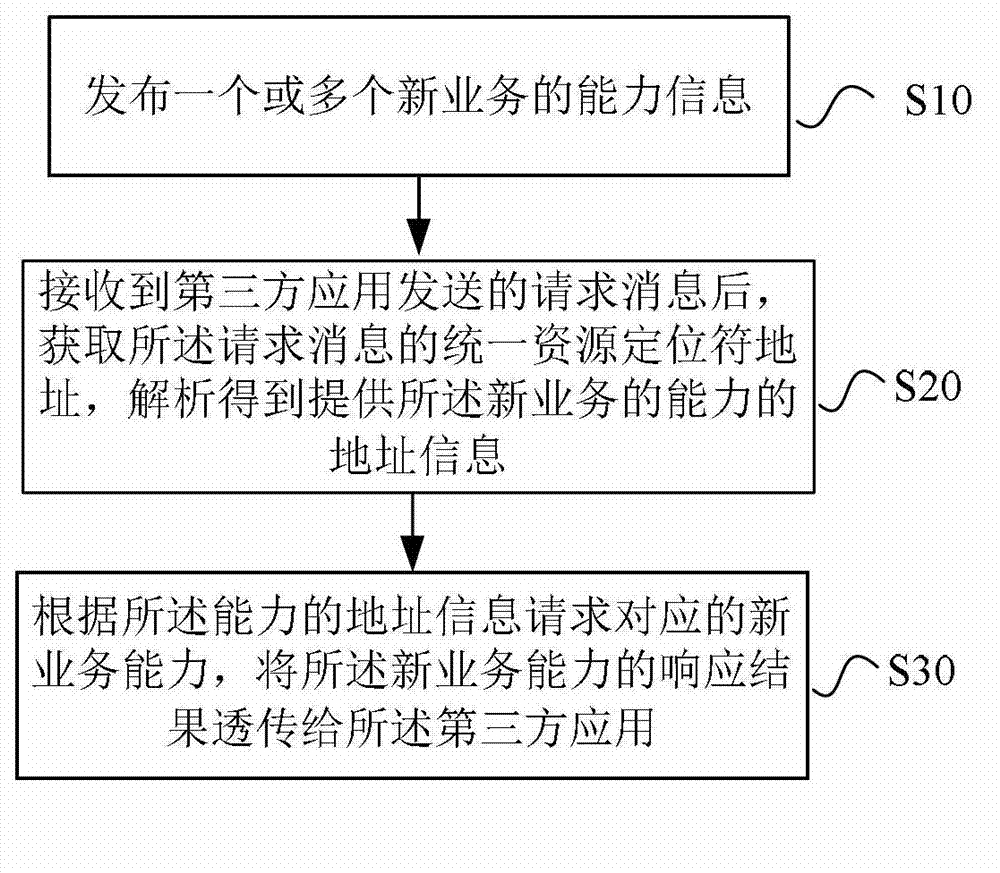
Method for processing new business and business server
InactiveCN103945572AQuick to useReduce usageService provisioningWireless network protocolsThird partyUniform resource locator
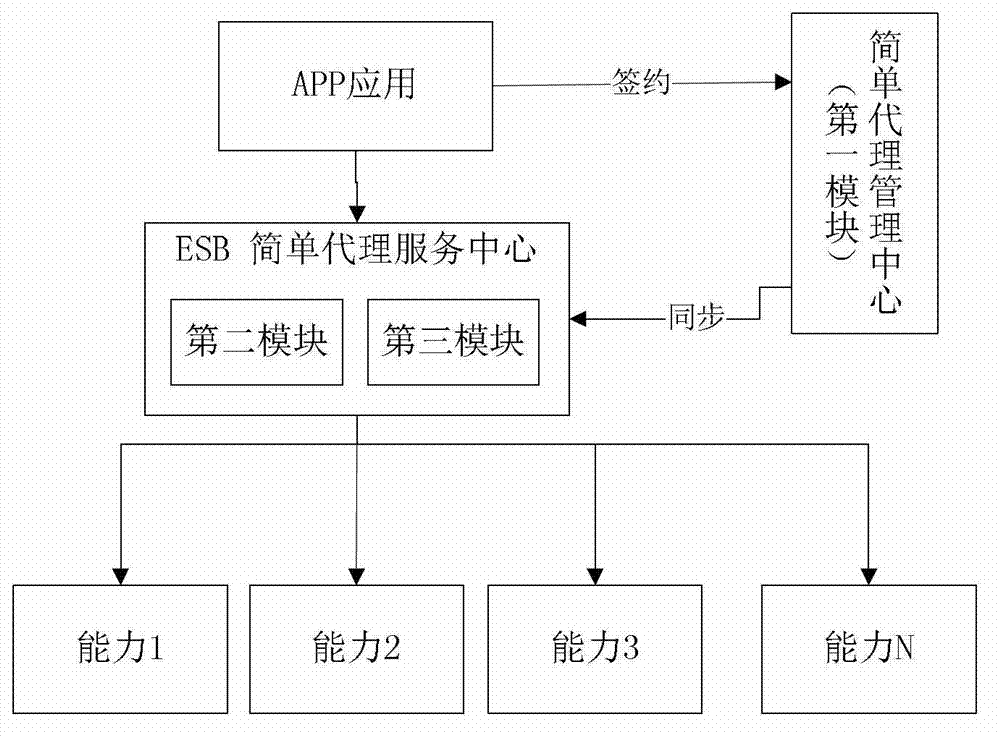
The invention provides a method for processing new business and a business server. The method comprises the steps of releasing one or more messages about the capability of the new business; after receiving a request message from a third party application, acquiring and analyzing the uniform resource locator address of the request message, and obtaining a message of the address offering the capability of the new business; and requesting corresponding capability of the new business according to the address message of the capability, and directly transmitting the response result of the capability of the new business to the third party application. According to the method, the capability of the new business is accessed and managed based on a simple agency mode, so that an operator is capable of quickly responding to the new business in the mobile internet and providing an access to the capability of the new business, thereby forming own mobile internet value-added business.
Owner:ZTE CORP
Android database lazy loading method based on proxy mode
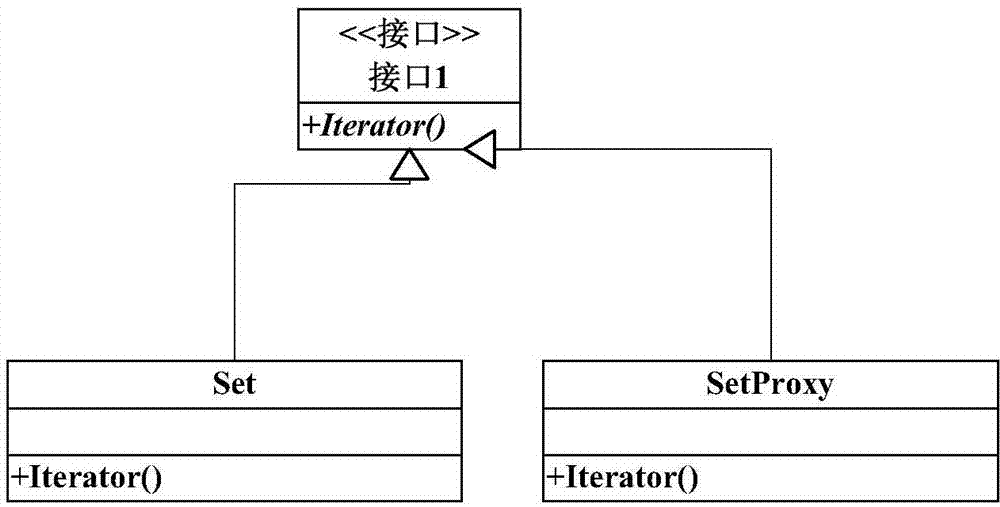
ActiveCN104714813AImprove efficiencyReduce memory overheadProgram loading/initiatingSpecial data processing applicationsData libraryProxy pattern
The invention discloses an android database lazy loading method based on a proxy mode. The method includes the following steps that S100, proxy of a collection class is realized in the proxy mode, and a DAO layer in ORM visits a proxy object of the collection class; S200, a proxy class acts for an Iterator method of the collection class, and only when specific data are taken from a collection to call the Iterator method, does the proxy object fills up the collection by searching for a database. The utilization efficiency of the database is effectively improved, and the memory overhead of a system is effectively lowered.
Owner:AEROSPACE INFORMATION
Order fee deduction processing method in multi-stage proxy mode
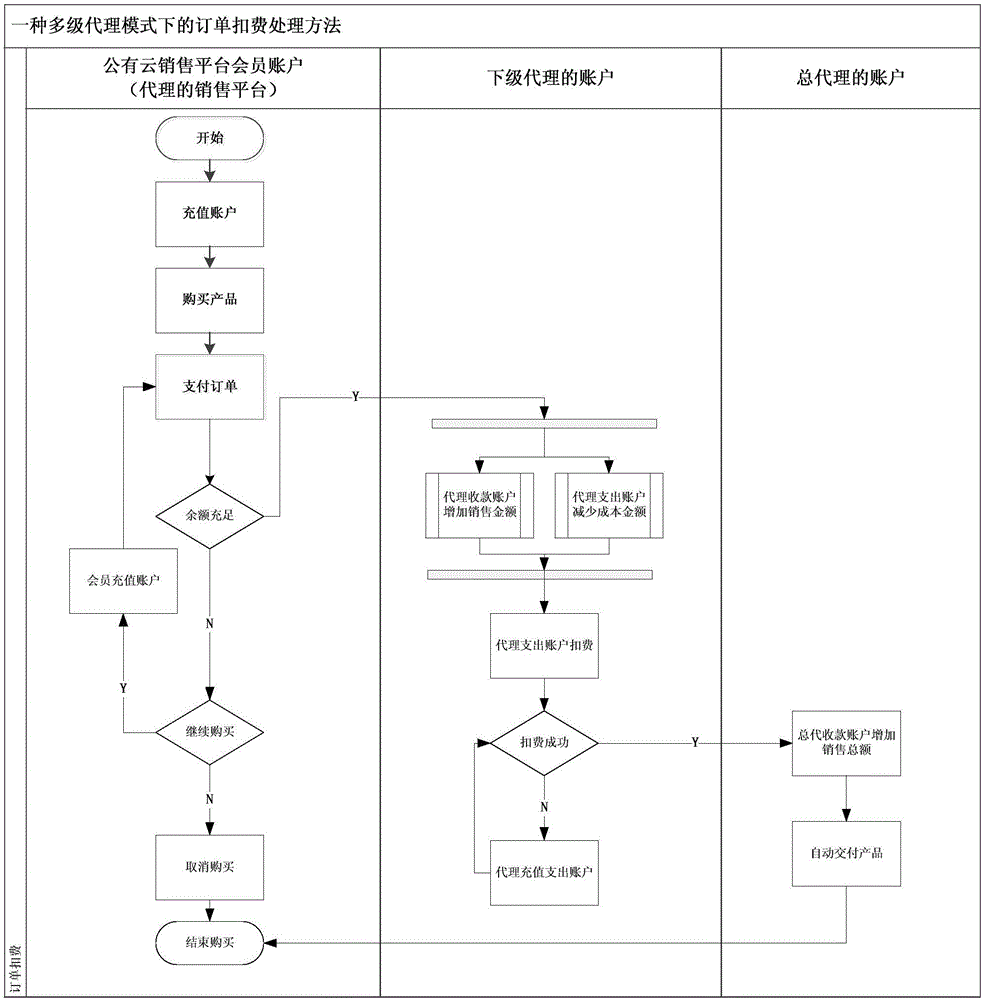
InactiveCN106779913AExpand the agency marketAccelerate the pace of business expansionBuying/selling/leasing transactionsSpecific program execution arrangementsData miningIntegrated processing
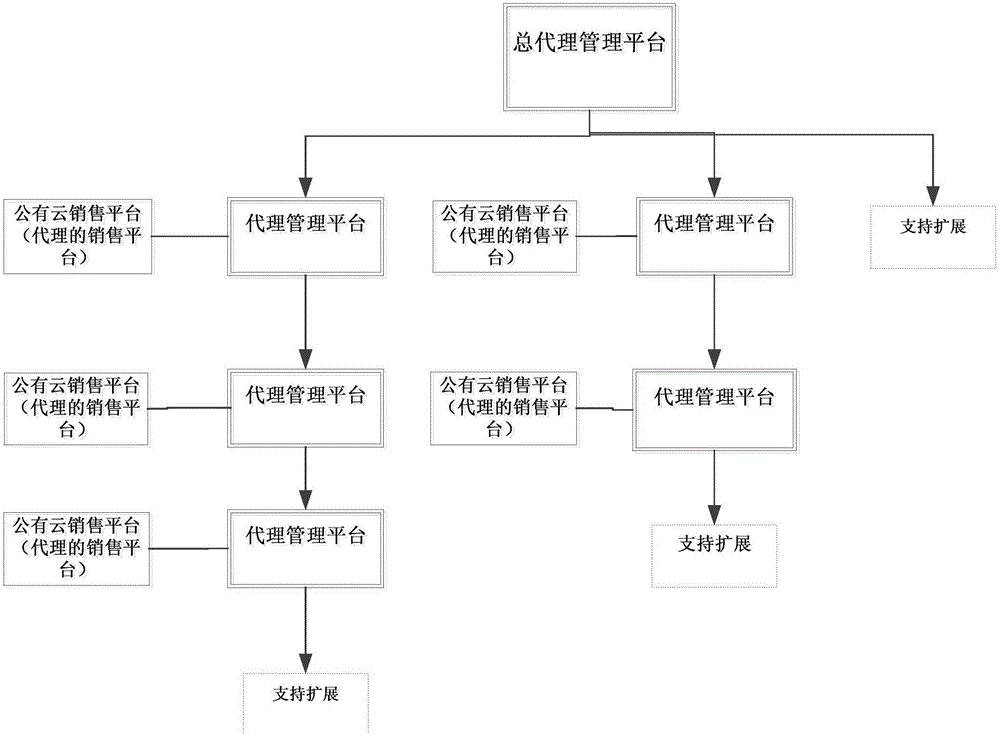
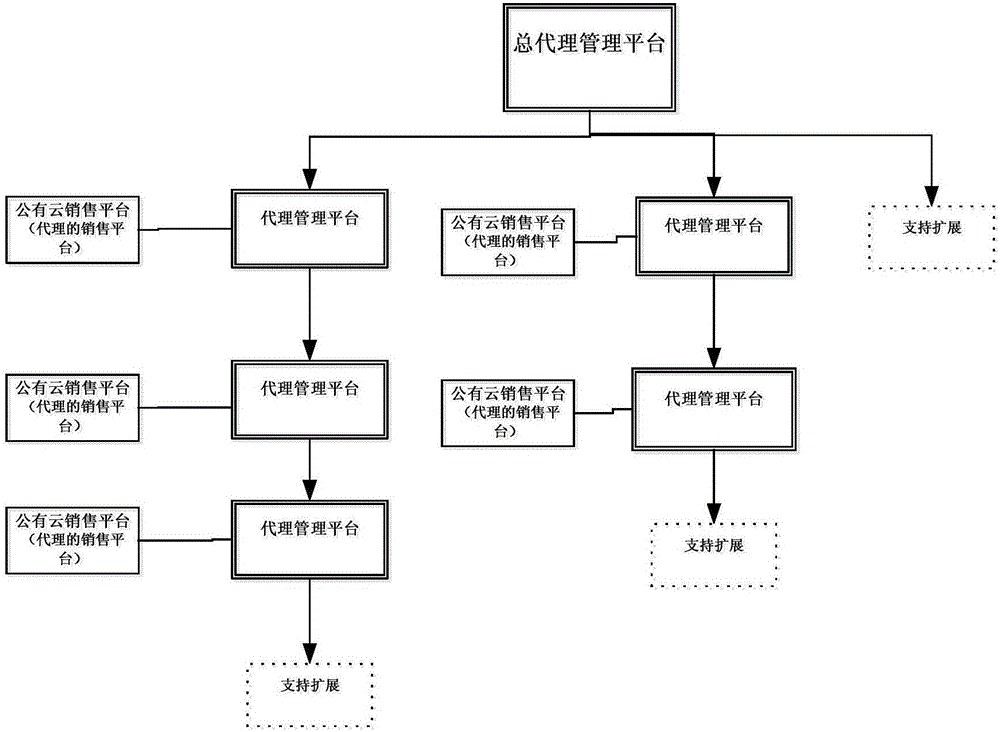
The invention relates to the field of public cloud, and specifically relates to an order fee deduction method in a multi-stage proxy mode. The method includes: members purchase and pay products at a public cloud sales platform, belonged proxy accounts collect charges, proxy in each stage performs fee deduction according to the regulations, and the system delivers the products after completion of fee deduction. According to the method, problems of integrated processing of portal order fee deduction, fee deduction of multi-stage proxy cost, and entry of multi-stage proxy total sales in the cloud sales mode of multi-stage proxy sales are solved, and a systematic and automatic fee deduction processing process is provided.
Owner:G CLOUD TECH
Method, apparatuses and computer media for nonce-based authentication scheme comprising indication of session control server's operation mode in authentication request
Usage of nonce-based authentication scheme in a session- based authentication application, usable in a communication system comprising a session control server and an authentication server, which are configured to provide for a session-based authentication application, wherein authentication is based on a nonce-based authentication scheme, comprising an indication of an operation mode of the session control server from the session control server to the authentication server in an authentication request, wherein the operation mode included proxy mode and user agent mode.
Owner:NOKIA CORP
Internet of cards intelligent recharging management method
The invention relates to the technical field of communication, and provides an internet of cards intelligent recharging management method which comprises the following steps of S1, creating an Internet of cards recharging management system applied to an Internet of cards centralized management platform, the Internet of cards recharging management system comprising a system setting module, an Internet of cards state detection module, an Internet of cards configuration module and a recharging payment module; S2, setting the state of each Internet of card as a test period, a silencing period, a charging period, a stop period and a termination period; S3, detecting the current state of each Internet of card in real time by an Internet of cards state detection module, recharging the Internet ofcards according to the states, converting the recharging fee into corresponding flow, and recharging the flow into the Internet of cards; and S4, setting a platform recharging fee payment module andan agent recharging fee payment module in the recharging payment module. The internet of cards intelligent recharging management method solves the problems that the existing Internet of cards cannot effectively plan the card recharging data, so that the cost of selling the Internet of cards by a service provider is too high, and the agent modes of all levels and the benefit distribution managementcannot be generated, and the like.
Owner:福建省公田软件股份有限公司
Method for processing product application forms of cloud platform in multi-hierarchy agent mode
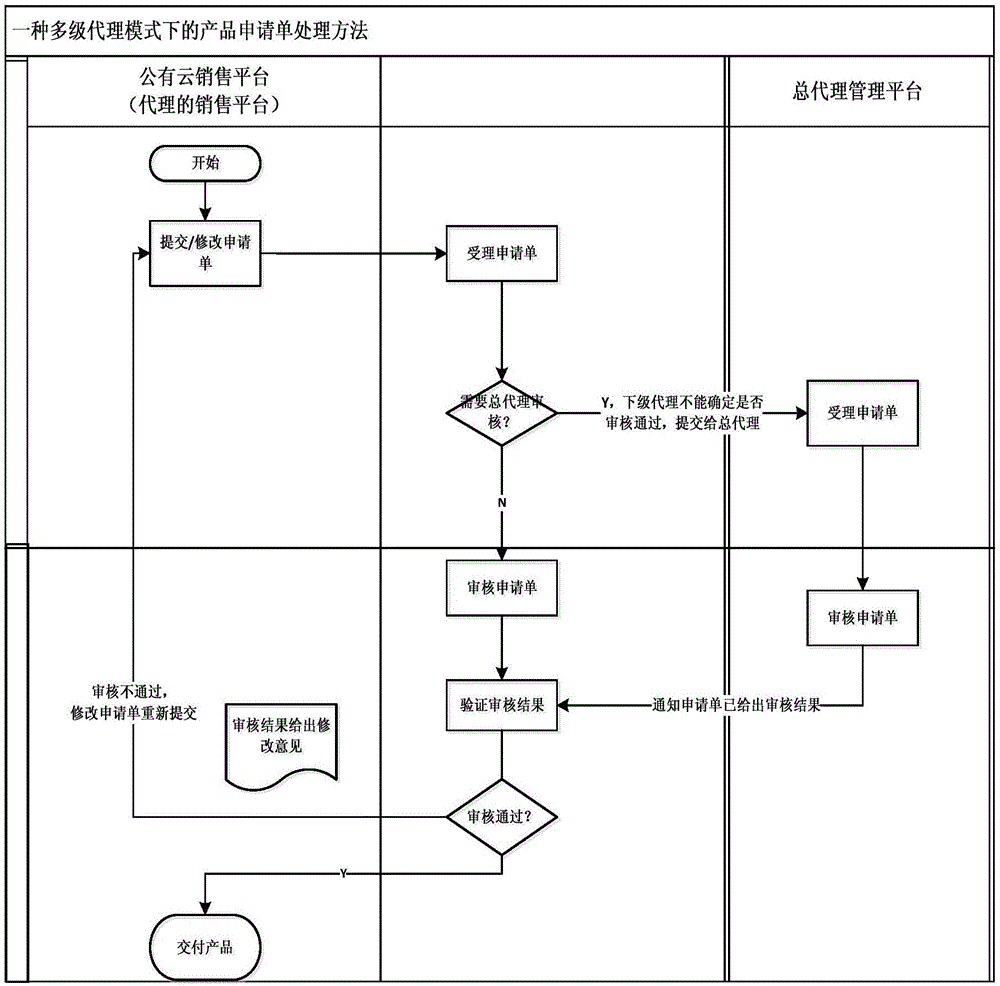
InactiveCN106779924AMeet needsQuick response to demandBuying/selling/leasing transactionsSpecific program execution arrangementsForm processingWorld Wide Web
The invention relates to the technical field of public cloud, in particular to a method for processing product application forms of a cloud platform in a multi-hierarchy agent mode. The method comprises the steps that users submit product application forms in a public cloud sales platform; agents receive the application forms submitted by the users, the application forms agreed to be applied can directly pass audit, and the application forms not meeting the requirements can be refused to be applied and modification suggestions are fed back; if the agents cannot determine whether the application forms can be audited or not, the agents submit the application forms to a general agent, and the general agent determines whether the audit is passed or not; the application forms passing the audit enter a product delivery process; and the application forms not passing the audit are modified by the user and enters an application form process again. According to the method, the problems of application form processing disorder and non-timely response under the condition of relatively large agent scale are solved; and meanwhile, when the sub-agents are insufficiently familiar with G-Cloud platform resource conditions and cannot accurately judge whether the applications are authorized or not, the sub-agents can submit the application forms to the general agent for making a judgment.
Owner:G CLOUD TECH
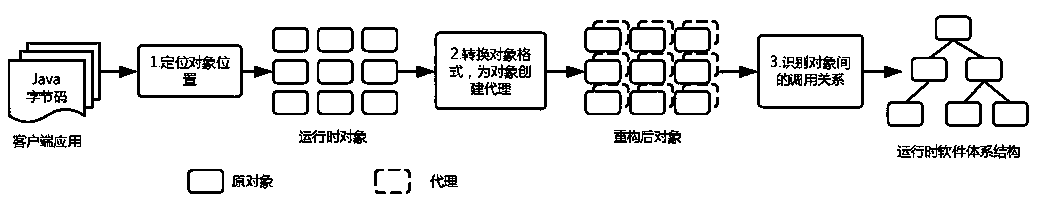
A method for acquiring a run-time software architecture of a client application
ActiveCN109254764AReduce development difficultyReduce the difficulty of upgradingCode compilationCreation/generation of source codeCOLA (software architecture)Software architecture
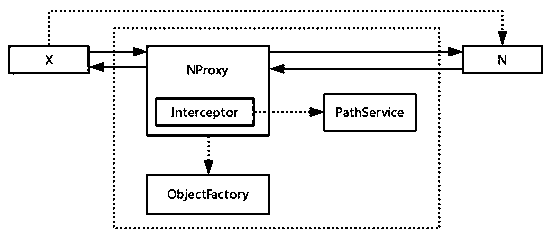
The invention provides a method for acquiring a run-time software architecture of a client application, comprising the following steps: step S1, preprocessing all classes in a source program code of the client application: when an active object is found to be created, recording the object currently created and the position of the created object; Step S2: converting the object: adopting the proxy mode, synchronously constructing a proxy object equivalent to the source object, and accessing the target object through the proxy object; Step S3: acquiring runtime information: creating a proxy classfor all runtime objects through a proxy mode; the interceptor intercepting all classes used at runtime, then recording the function and data structure of the calling path to determine the relationship between objects, and recording the runtime information. The invention obtains the runtime software architecture by reliable means, provides a way for realizing the monitoring and adjustment of the system by the way of the read-write architecture, and provides a basis for the online upgrading and evolution of the system.
Owner:FUZHOU UNIV
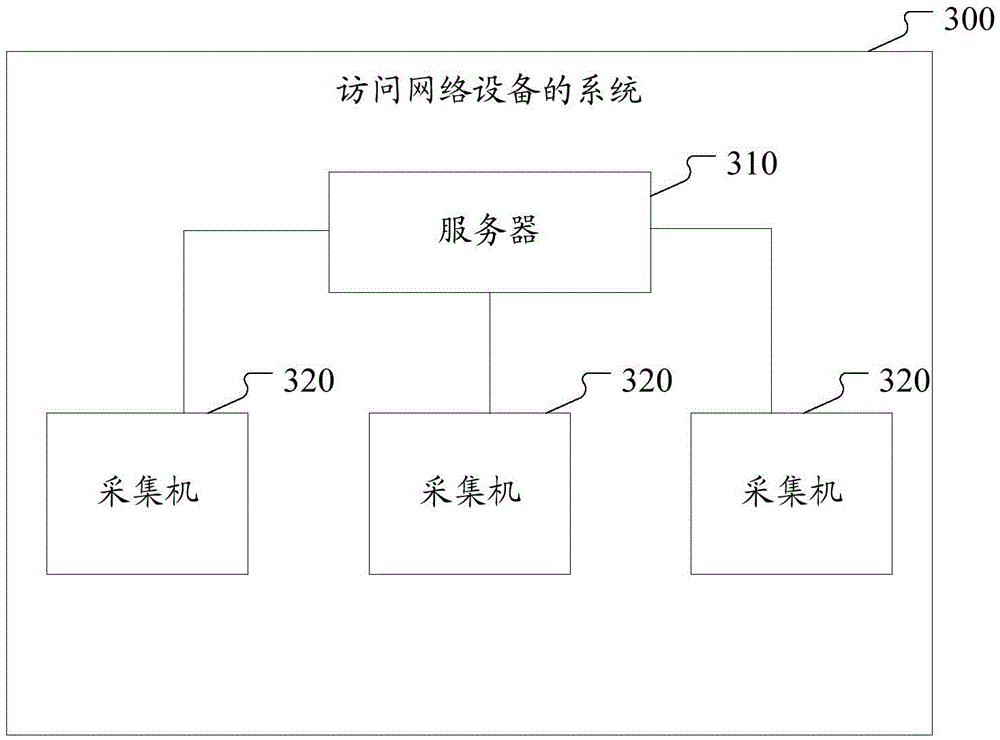
Network device accessing method and system
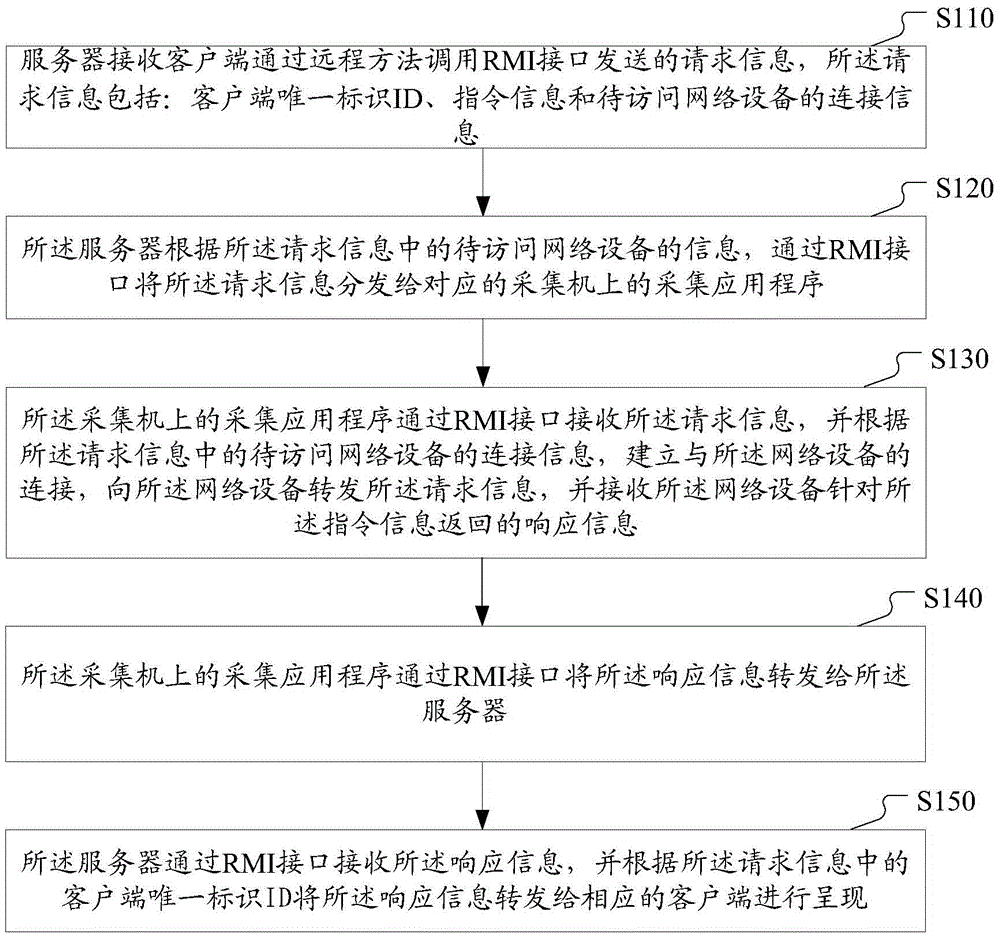
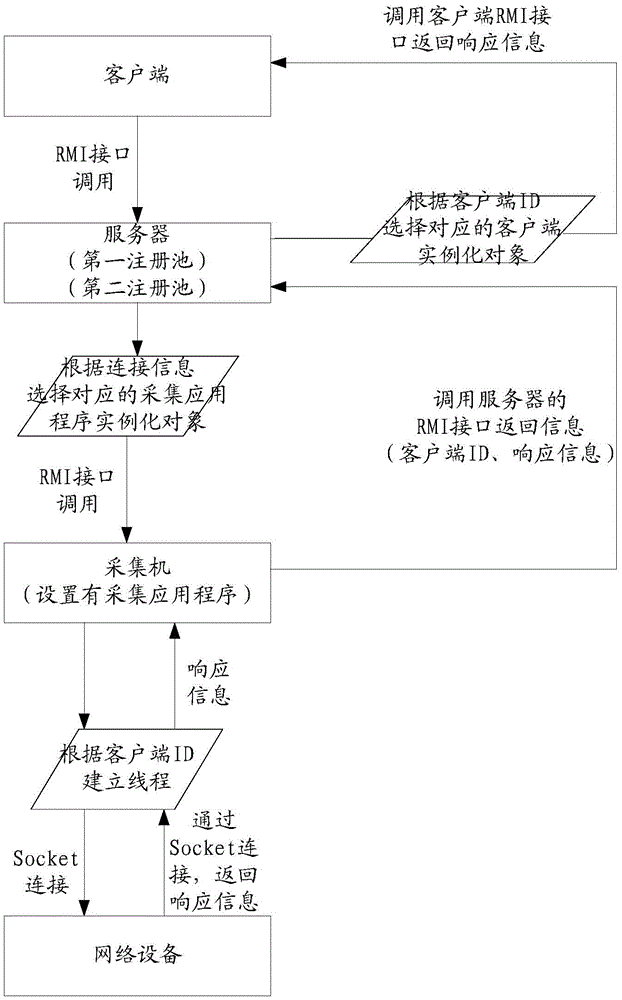
ActiveCN106790325ABreak through limitationsAchieve effectTransmissionClient-sideNetwork block device
The invention discloses network device accessing method and system. The method comprises: a server receives request information transmitted by a client via a remote method invocation (RMI) interface, wherein the request information comprises a unique identification (ID) of the client, command information and connection information of a network device to be accessed; the server distributes the request information to a probe in a corresponding collector via the RMI interface according to the connection information of the network device to be accessed; the probe receives the request information via the RMI interface, establishes a connection with the network device according to the connection information of the network device to be accessed, forwards the request information to the network device, and receives response information returned by the network device; the probe forwards the response information via the RMI interface; and the server receives the response information via the RMI interface and transmits the response information to the client to be displayed. The technical solution of the invention implements remote access of the client to a limited network device based on a remote agent mode, thereby breaking through limitations of networks.
Owner:ULTRAPOWER SOFTWARE
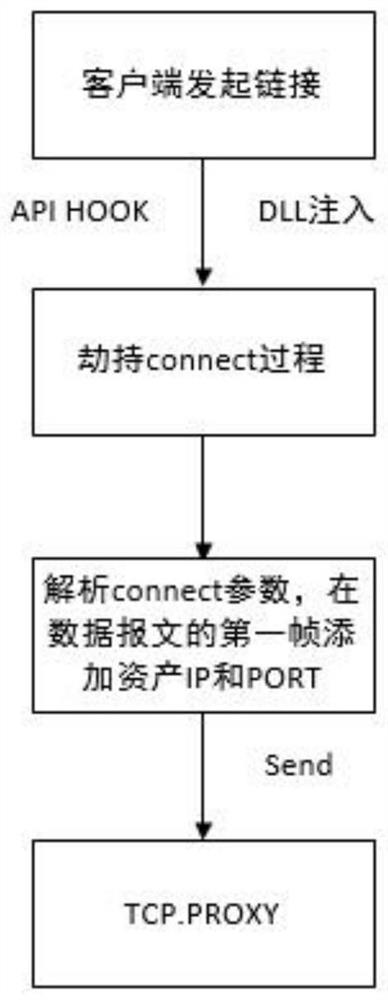
TCP proxy method based on remote desktop protocol
PendingCN114389831AAdapt to special environmentReal-time auditSecuring communicationThird partyRemote desktop
The invention provides a TCP (Transmission Control Protocol) proxy method based on a remote desktop protocol, which comprises the following steps of: 1, carrying out video stream hijacking on a third-party application program, and hijacking a key process of a video stream; step 2, identifying a session parameter when a client initiates connect, inserting the session parameter at an initial position of initiating a first frame data message, and sending the modified message to a TCP proxy; and step 3, the TCP agent analyzes the first frame of message after receiving the first frame of message, establishes a link with the target asset, and performs unvarnished transmission of the TCP stream. According to the method, upper layer protocols are not distinguished and researched any more, and the method is realized by uniformly forwarding TCP layer video streams. The bastion host coexists in an agent mode and a direct connection mode and can be selectively used in a configuration mode, the bastion host adopts a TCP agent, server assets can be audited, operated and maintained in real time, and the bastion host can well adapt to the special environment of a client site.
Owner:山东华软金盾软件股份有限公司
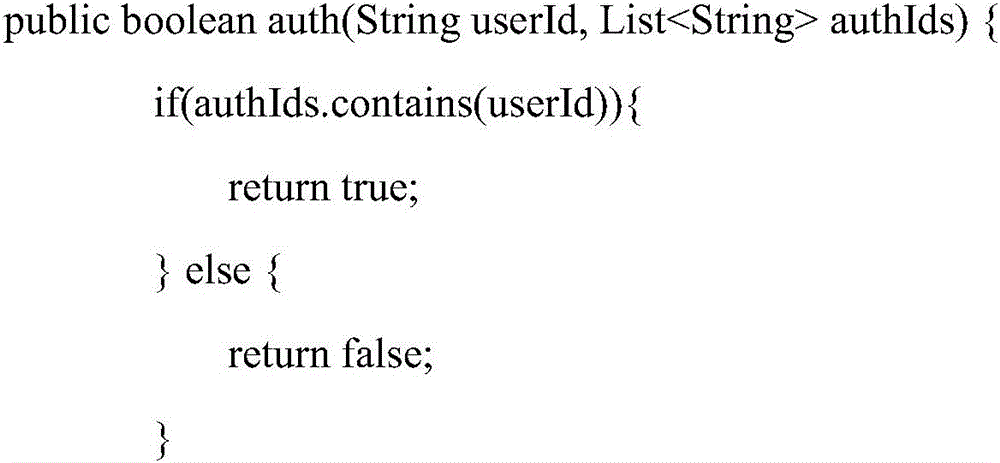
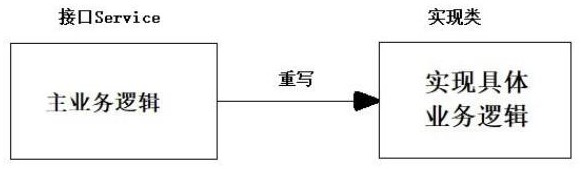
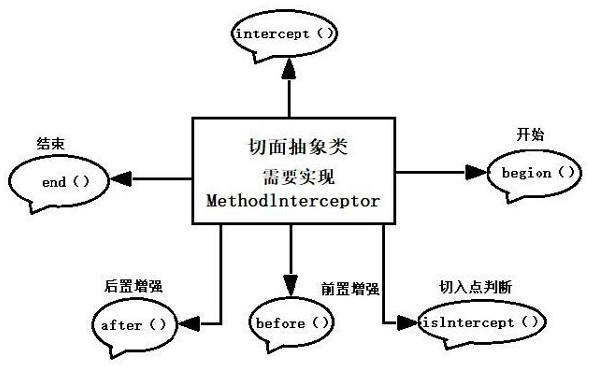
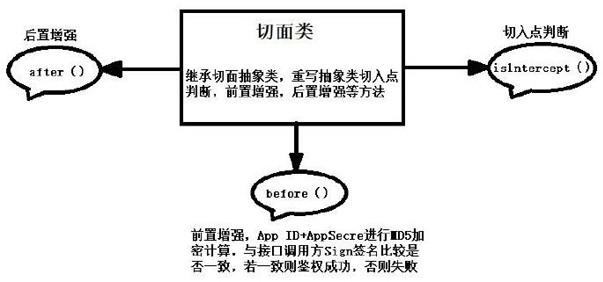
Method and device for realizing authentication of interface calling party in dynamic proxy mode
InactiveCN113779638AImplement extensionsImprove reliabilityInterprogram communicationDigital data protectionHigh availabilityDependability
The invention particularly relates to a method and a device for realizing authentication of an interface calling party in a dynamic proxy mode. According to the method and the device for realizing authentication of the interface calling party in the dynamic proxy mode. The method is characterized by firstly defining a service interface and an implementation class to realize the service interface, and rewriting and realizing a business logic method; then, defining a section abstract class, and rewriting business logic methods of starting, ending, exception, front enhancement and rear enhancement according to needs when the section abstract class is defined; creating a section class, configuring an entry point and enhancement in the section class, and verifying the identity of the caller; and finally, testing and generating a dynamic agent class. According to the method and the device for realizing authentication of the interface calling party in the dynamic proxy mode, non-intrusive code expansion is realized, the method can be enhanced under the condition of not modifying a source code, and meanwhile, proxy logic and business logic are mutually independent and are not coupled so that high reliability and high availability of system use and service provision are ensured.
Owner:INSPUR SOFTWARE CO LTD
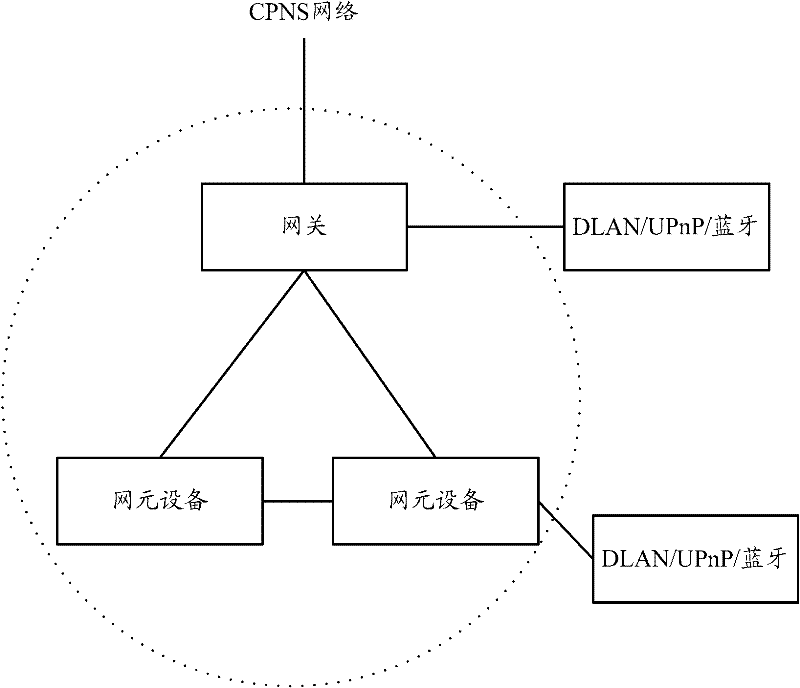
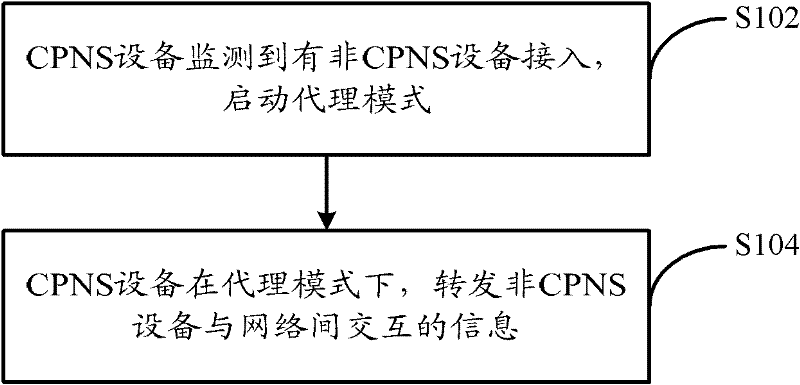
Method for implementing agency mode of personal network equipment, and personal network equipment
InactiveCN102457531ASolve the problem that the CPNS network cannot be accessed through the proxy deviceExpand the ability to use businessServices signallingTransmissionComputer networkPersonal network
The invention discloses a method for implementing an agency mode of personal network equipment, and personal network equipment. The method comprises the following steps that: when monitoring that non-converged personal network service (CPNS) equipment access a network, the CPNS equipment starts the agency mode, wherein the agency mode is that the non-CPNS equipment is allowed to access the network through the CPNS equipment; under the agency mode, the CPNS equipment forwards information interacted between the non-CPNS equipment and the network. By the method, the problem that the non-CPNS equipment cannot access the network through agency equipment is solved, and a CPNS network and the service using capacity of the CPNS equipment and the non-CPNS equipment on the network are expanded.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com