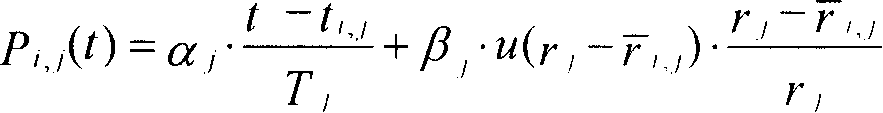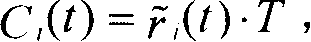Patents
Literature
100 results about "Priority function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
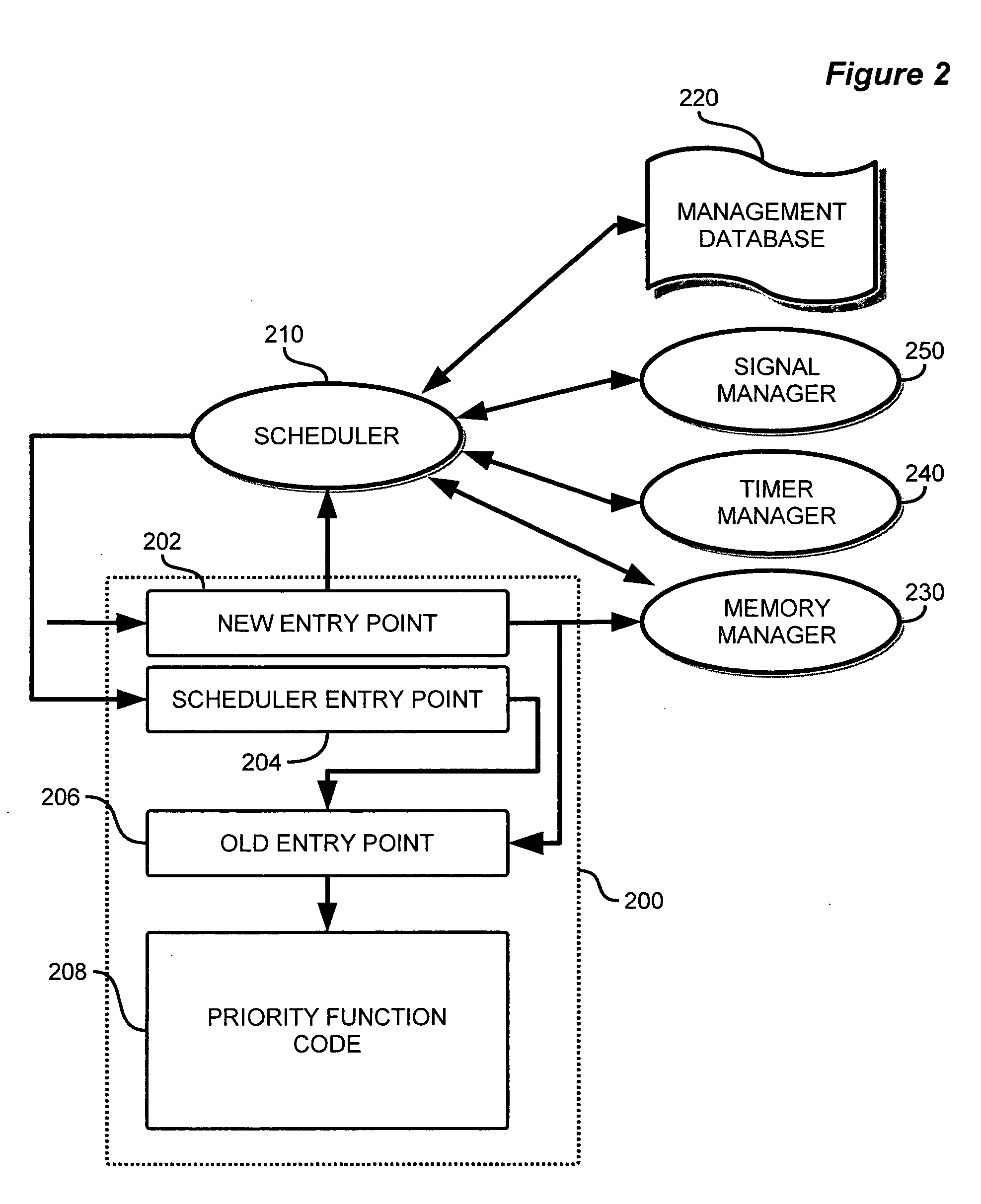
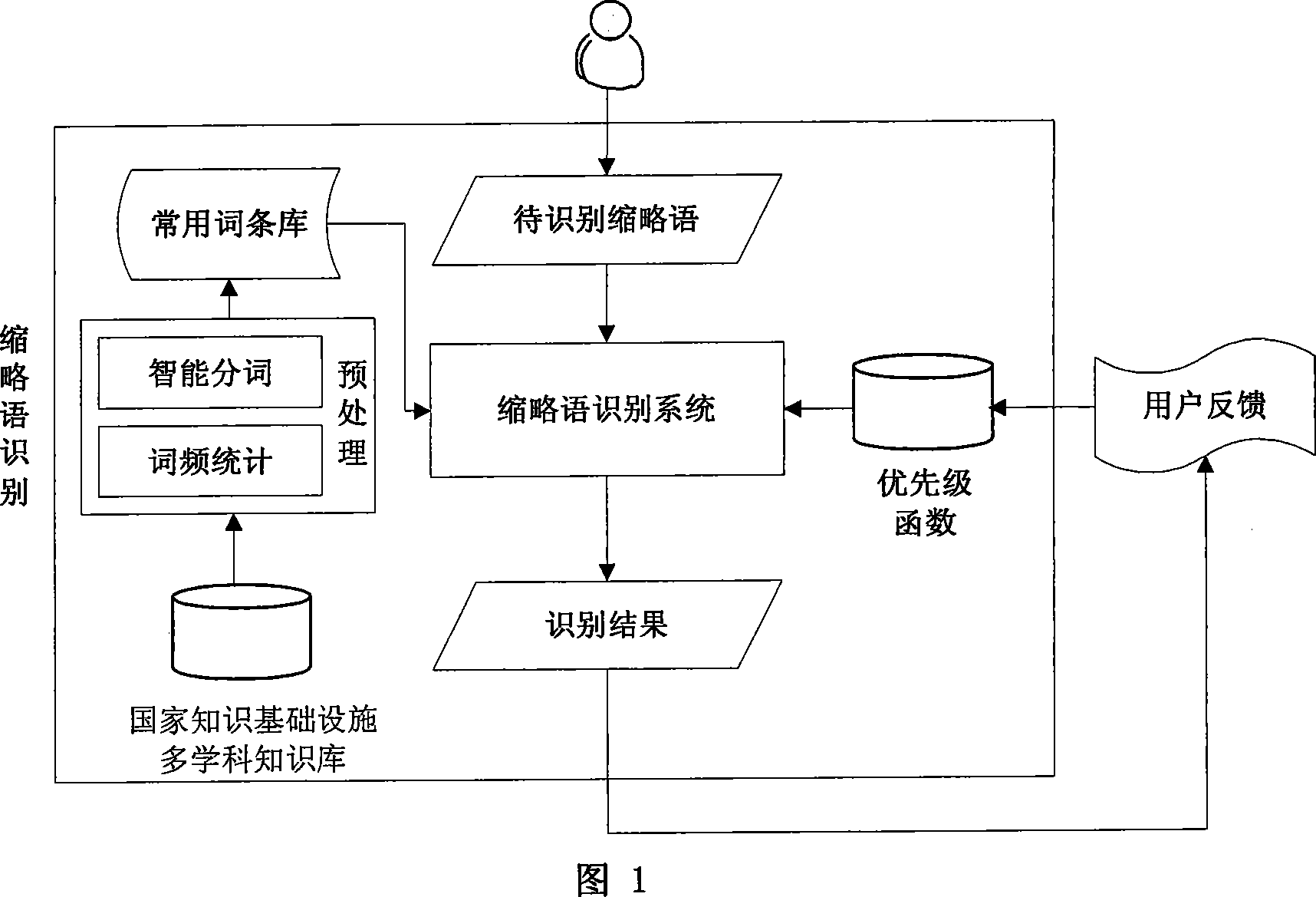
The priority function needs to guide the selection of the consistent collection and then followed by the selection of the tasks within that consistent selection. As more and more of the system is established, the priority function is weighted to choose tasks that are consistent with the already established system.
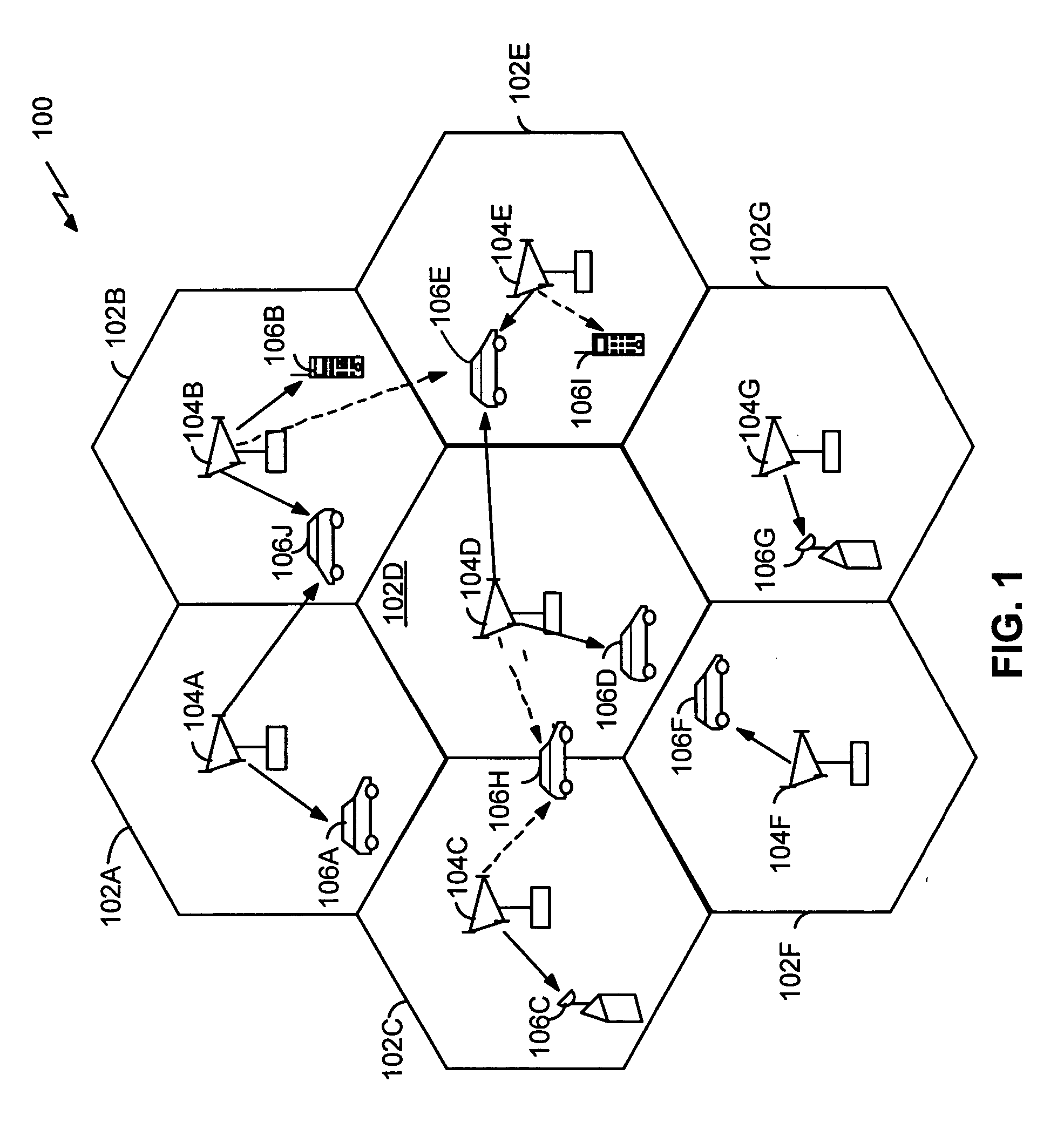
Scheduling of wireless packet data transmissions
InactiveUS20050063389A1Improve throughputChange the balanceError preventionTransmission systemsQuality of serviceInterference ratio
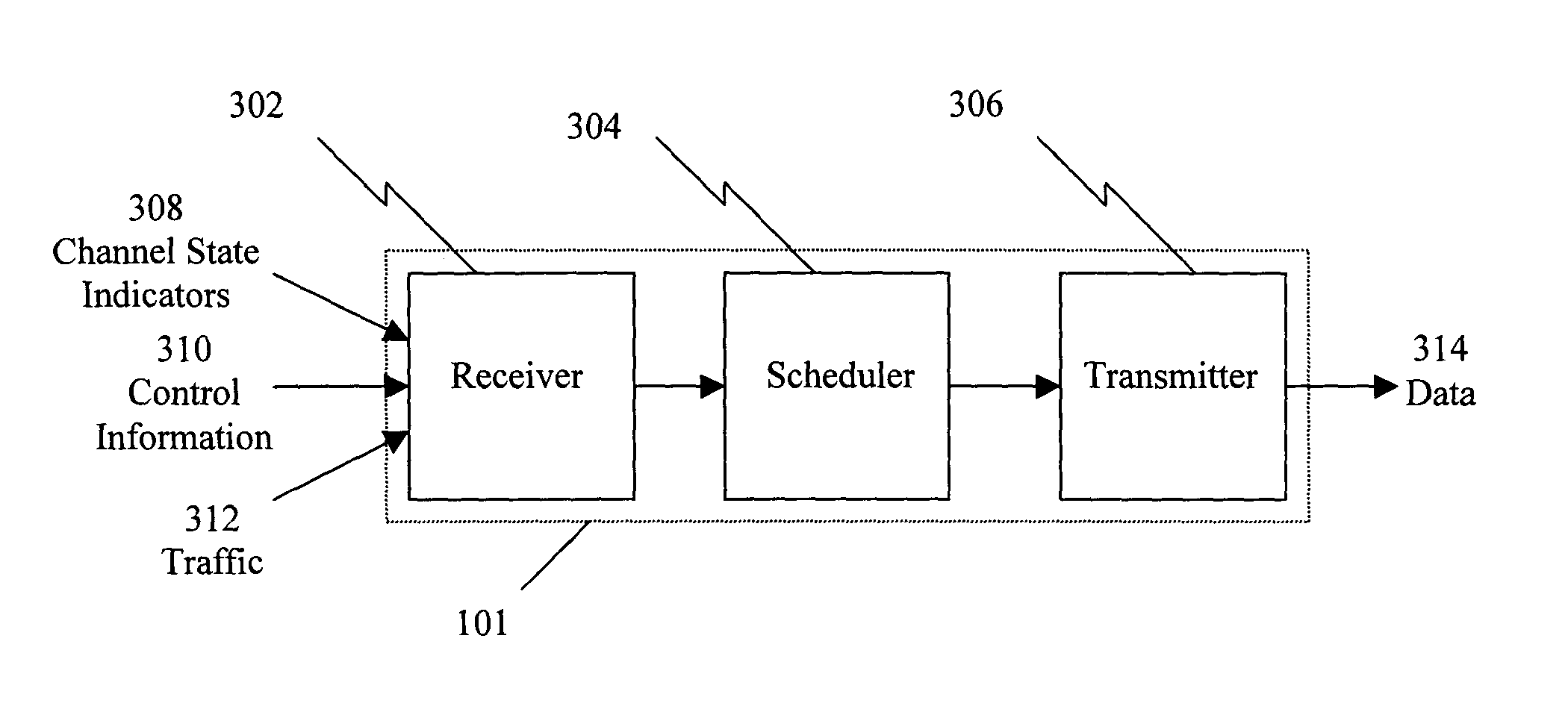
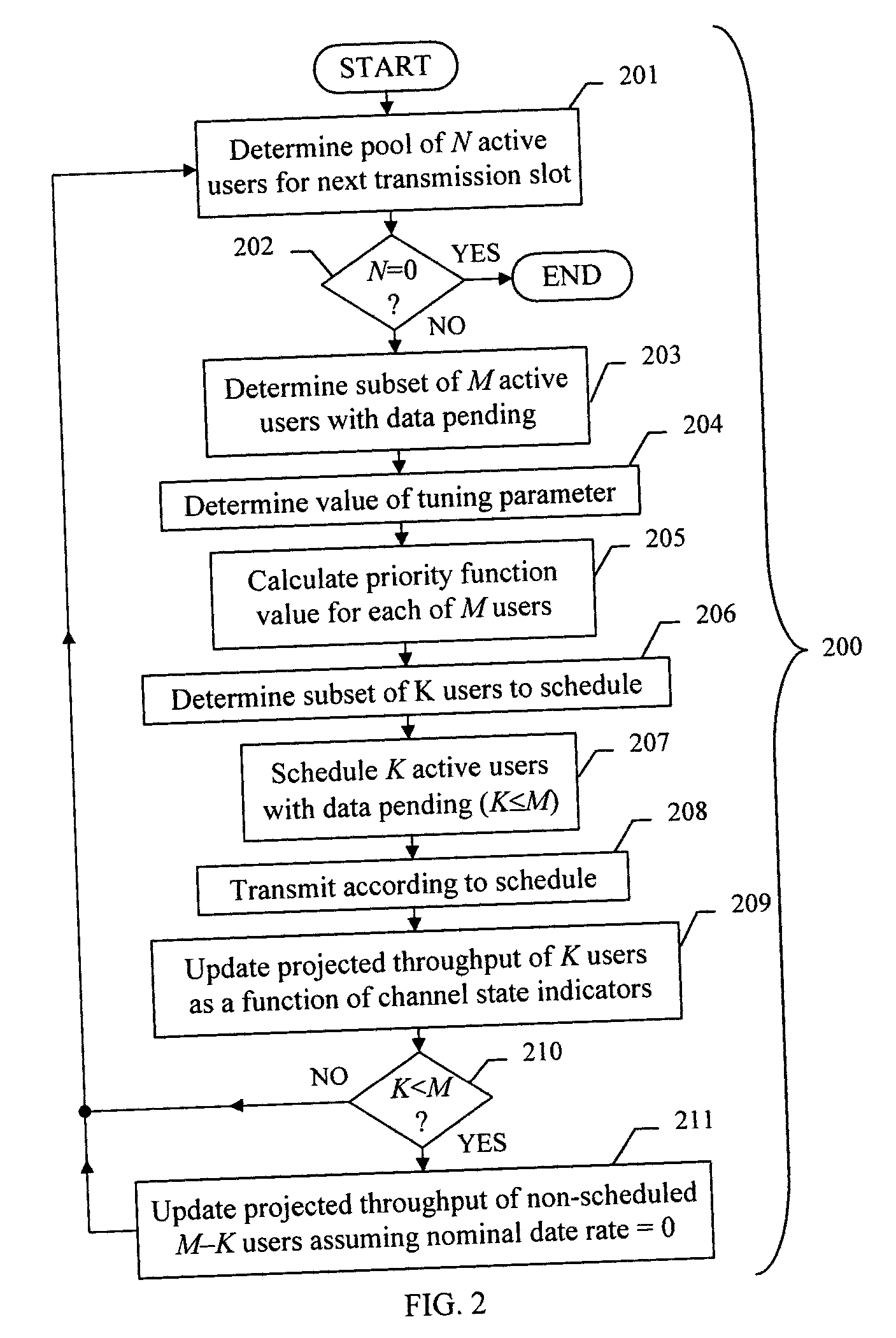
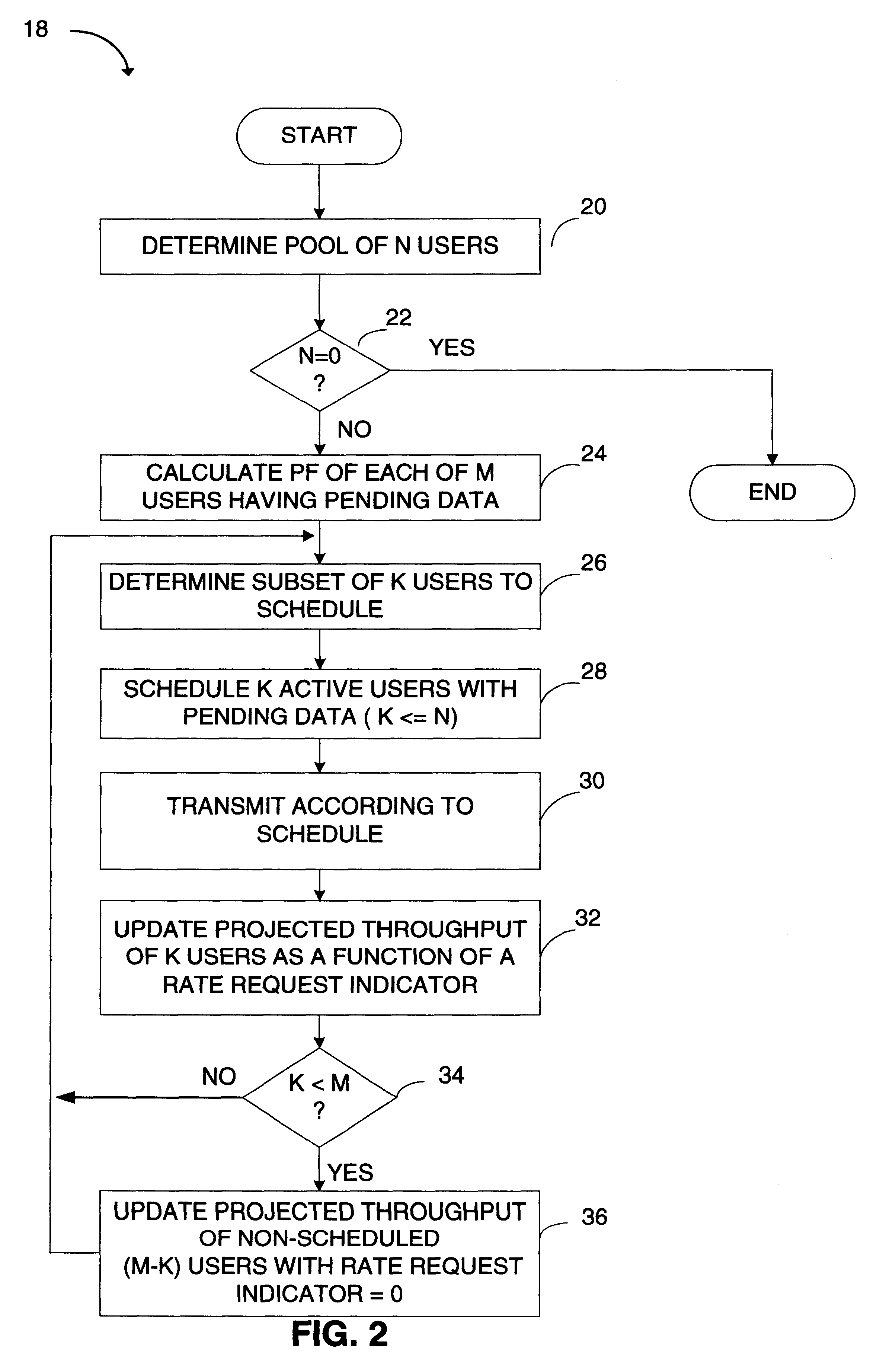
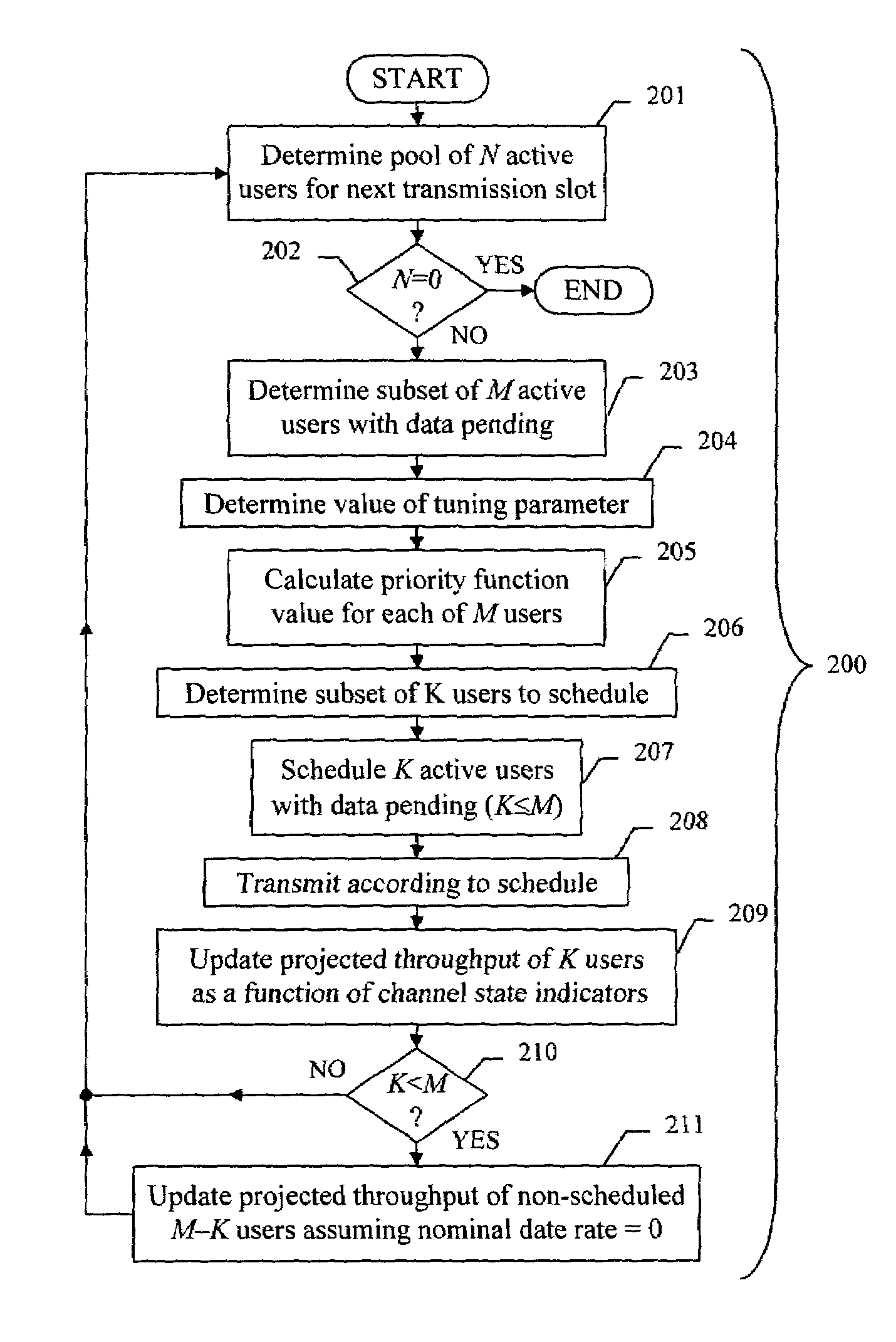
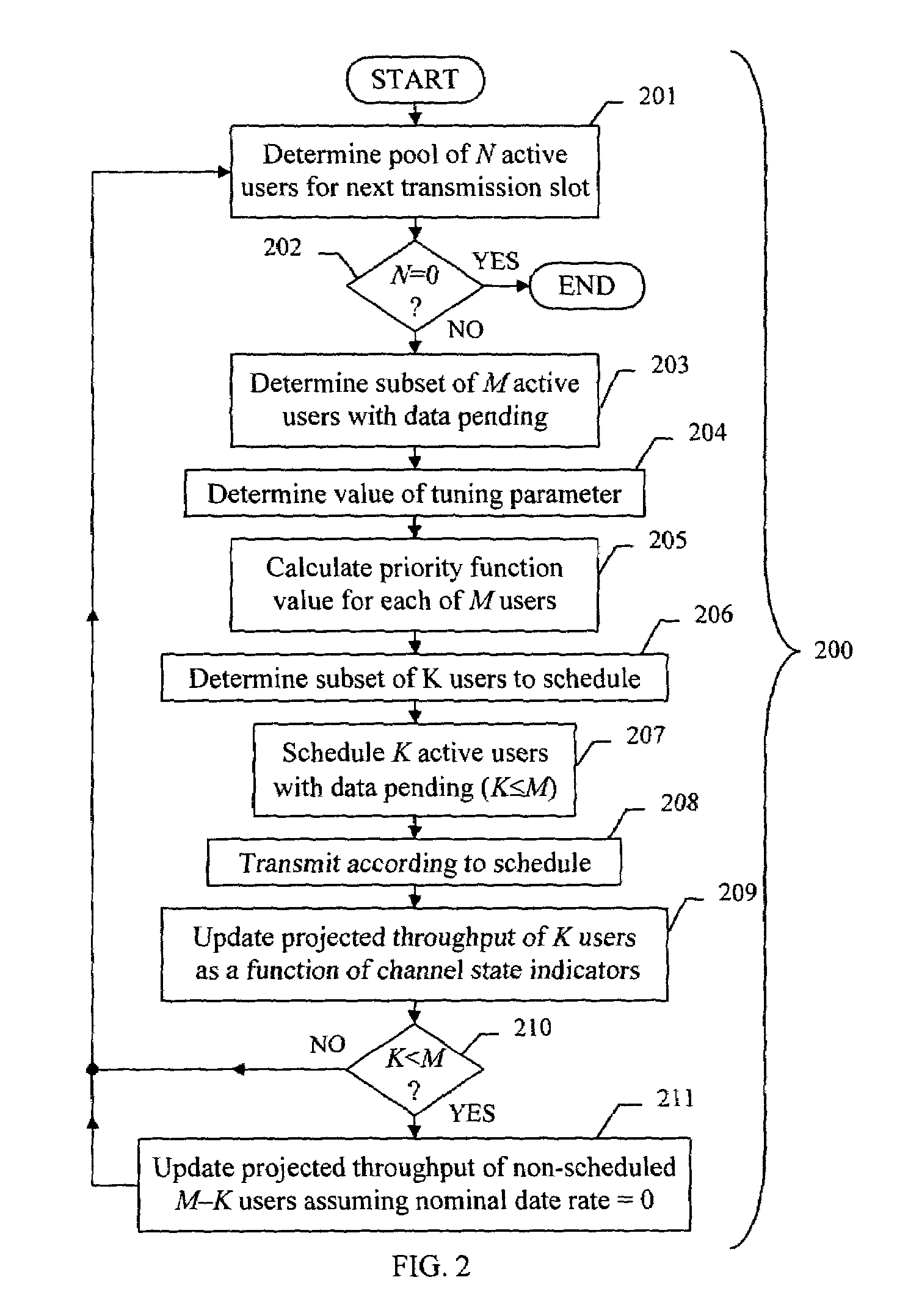
A method for scheduling packet data transmissions in a wireless communication system is described wherein a priority function is based on a channel state indicator (CSI), the projected average throughput of the users, and a tuning parameter designed to control the throughput and fairness characteristics of the scheduling algorithm. The method also considers fairness criteria dictated by predetermined Quality of Service (QoS) requirements. The channel state indicator may be a Requested Data Rate (RDR) or Carrier-to-Interference ratio (C / I) information. The base station calculates a priority function for the multiple mobile users. Each priority function is a function of the CSI, the projected average throughput of a given mobile user, the average projected throughput over a set of users, and the tuning parameter.
Owner:TELECOMM RES LAB
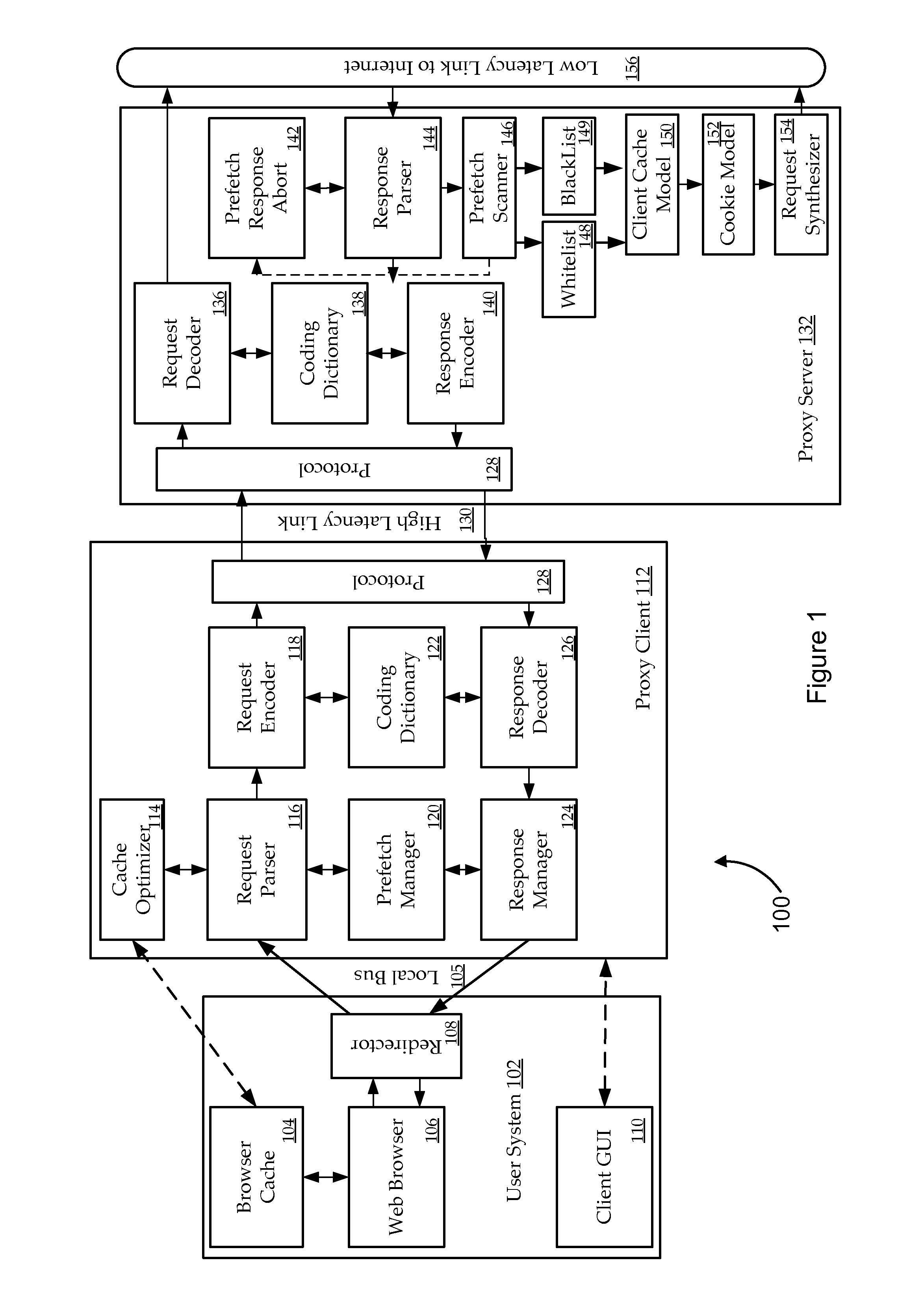
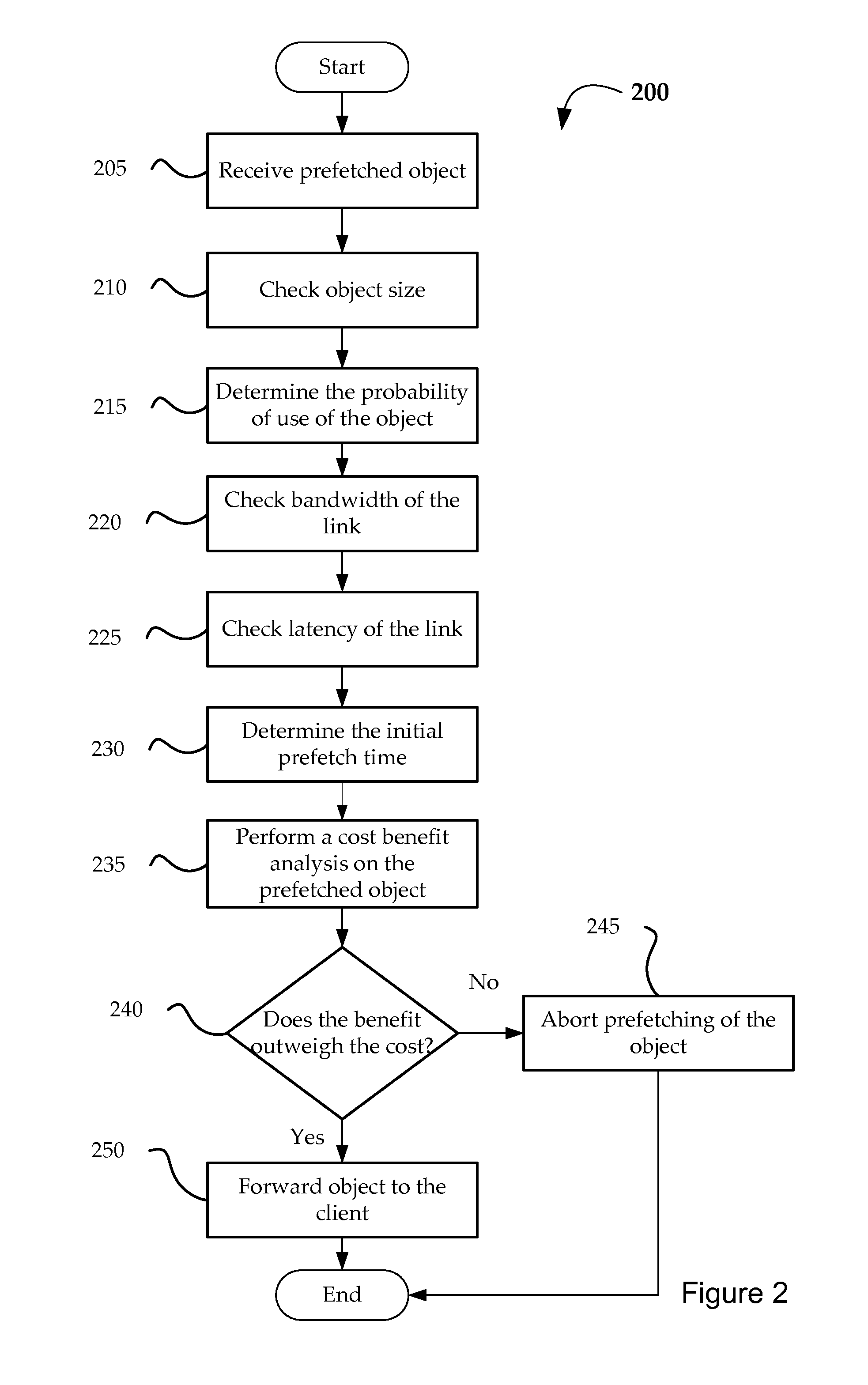
Selective prefetch scanning
ActiveUS8984048B1Waste of resourceIncrease probabilityWeb data indexingMultiple digital computer combinationsContainer ObjectUniform resource locator
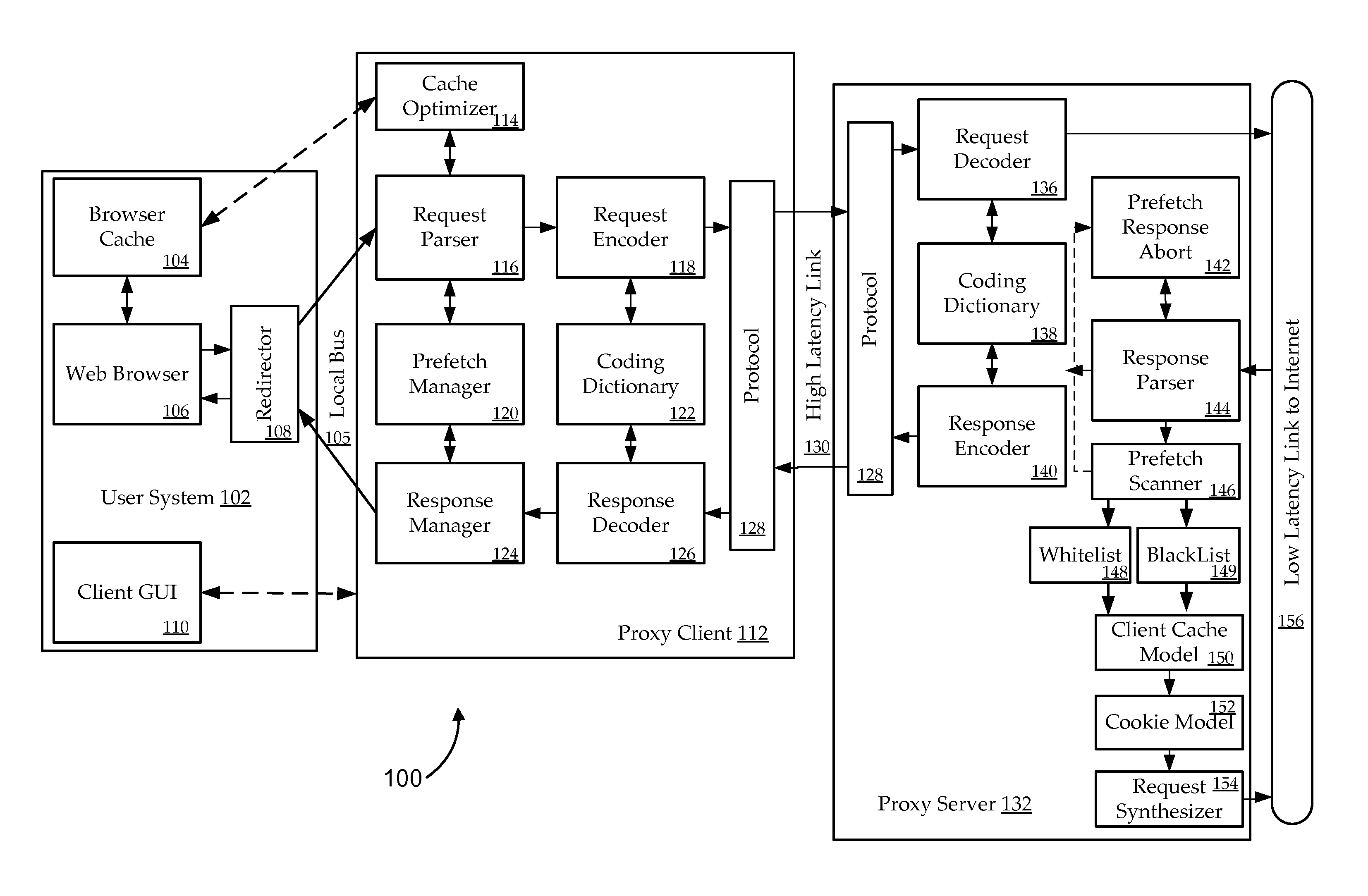
The present invention relates to systems, apparatus, and methods of enhancing prefecher functionality by scanning responses object requests. In certain embodiments, prefetching is improved by identifying references to container objects or sections of container objects at a proxy server. When URLs are identified as part of a container object, a prefetching determination or adjustment to a prefetching decision is made according to the identification of the reference for a subset of URLs identified by the reference to the container object. For example, prefetching of URLs located in cascading style sheet (CSS) files may be restricted to a subset of URLs which are identified by a CSS rule.
Owner:VIASAT INC
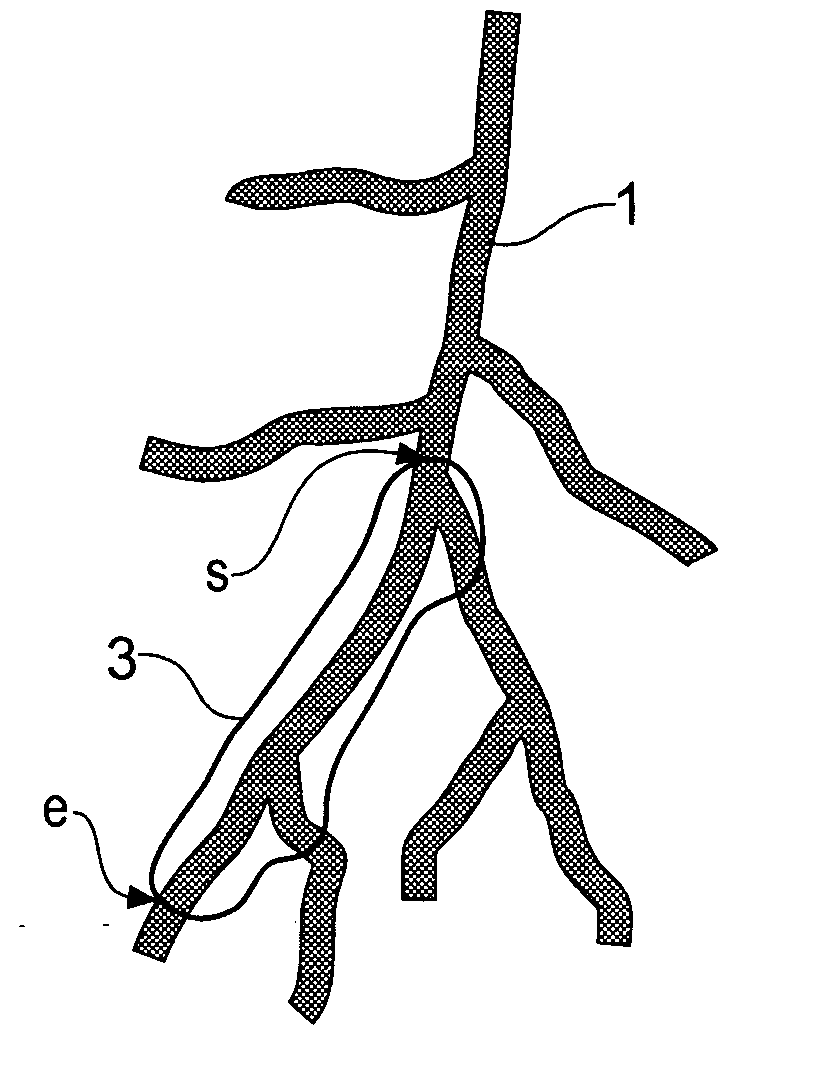
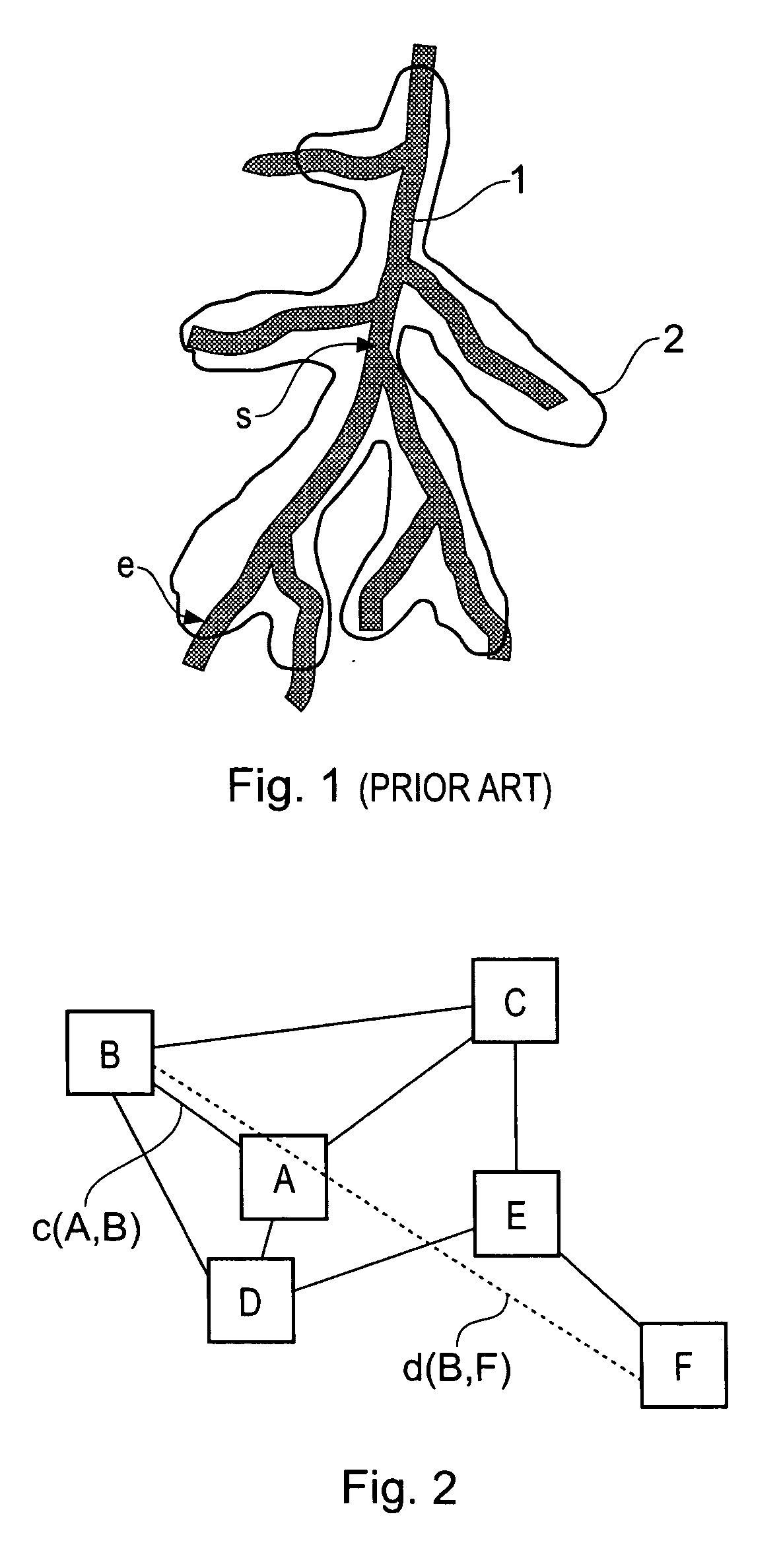
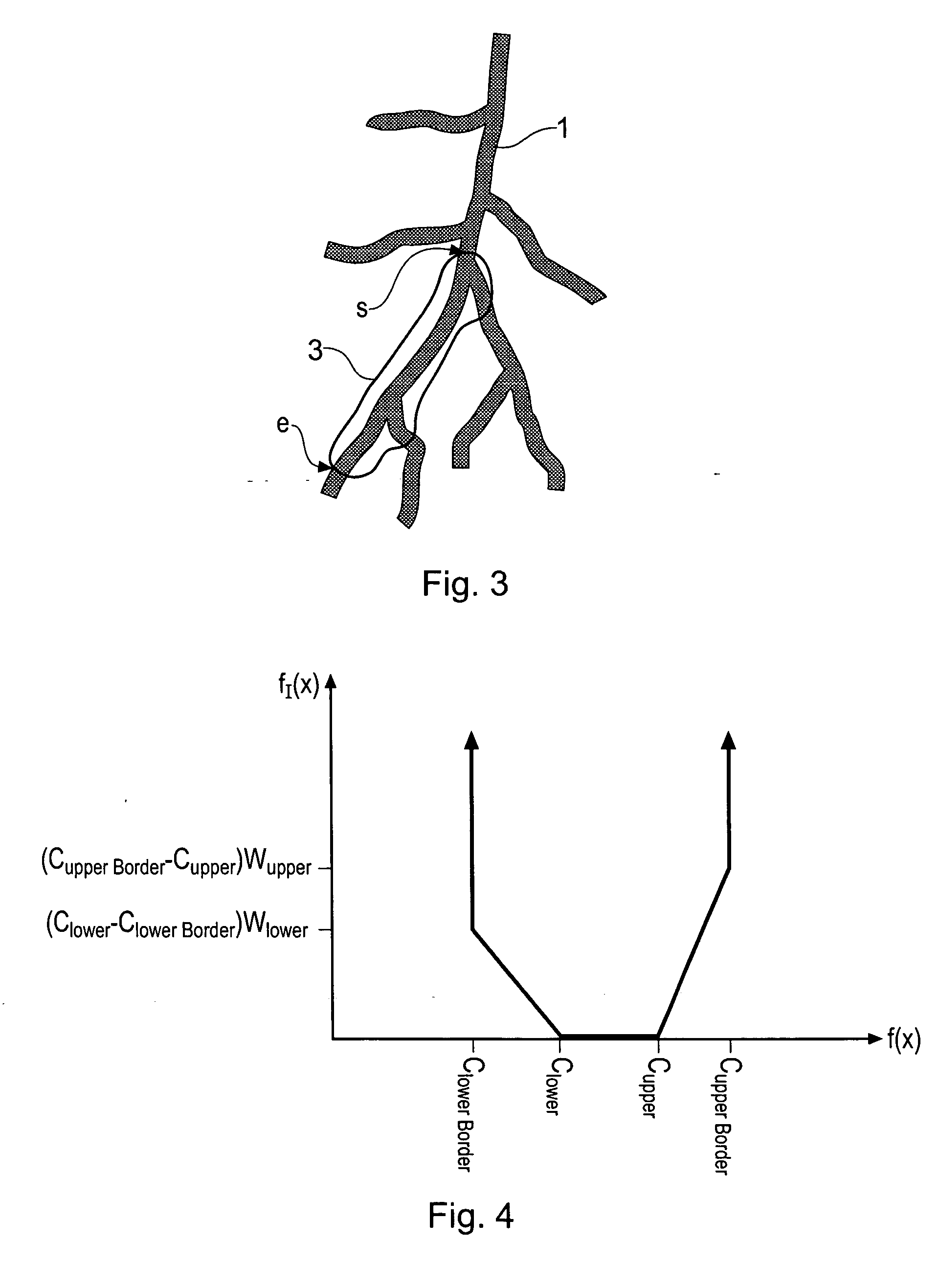
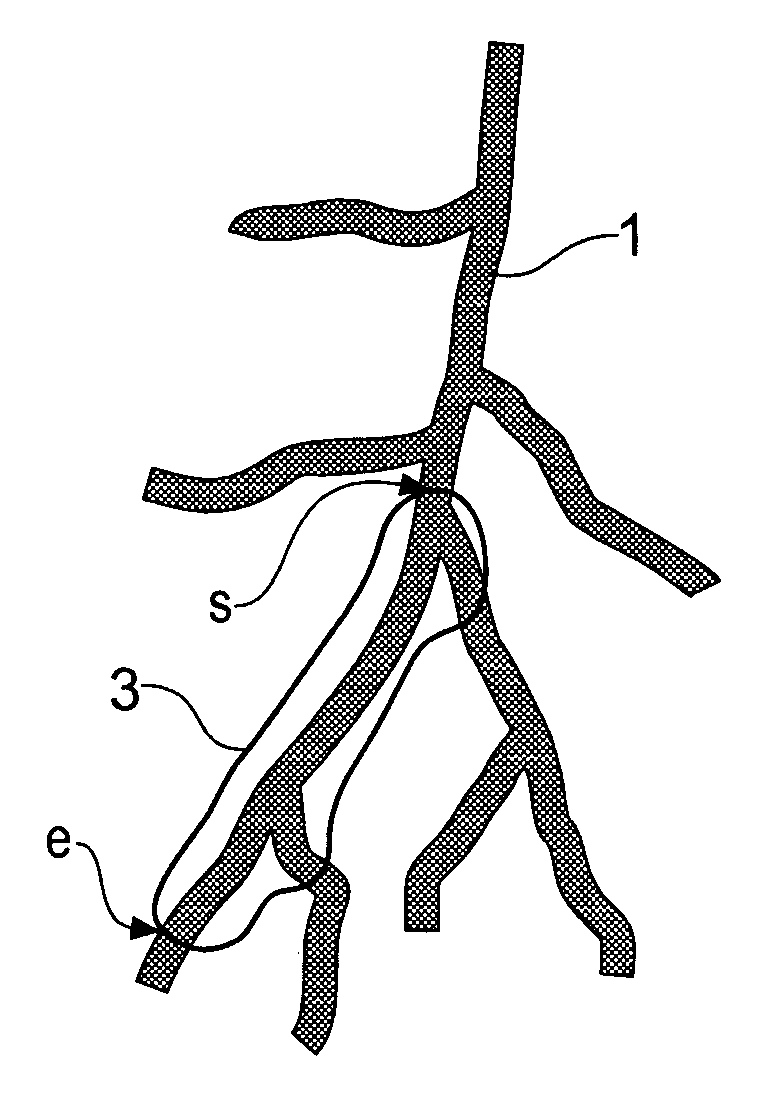
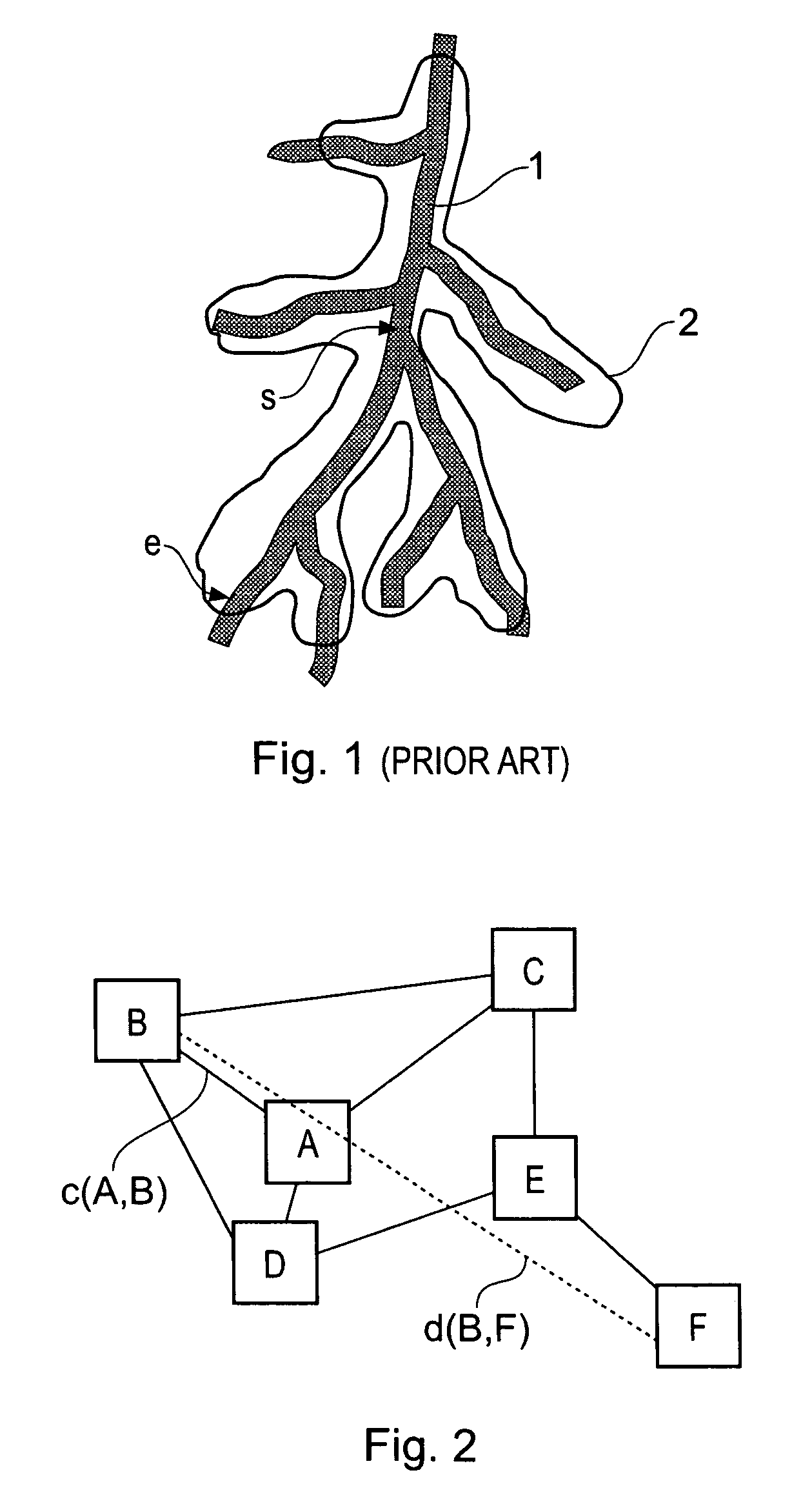
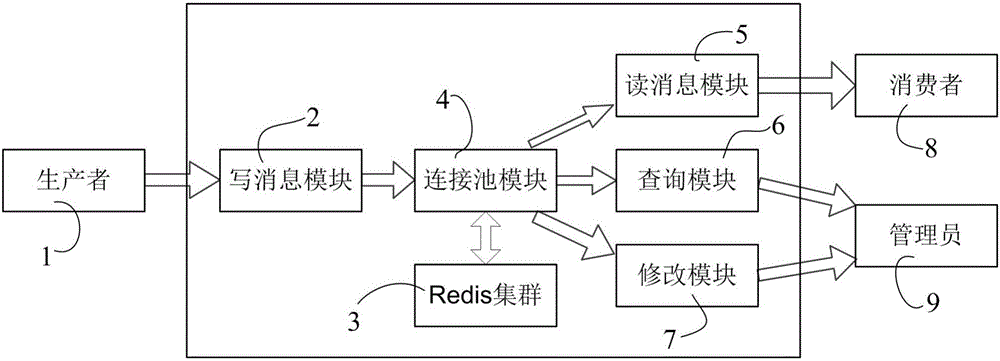
Method for determining a path along a biological object with a lumen
ActiveUS20070024617A1Shorten the timeAvoid excessive computationImage enhancementImage analysisData setVoxel
A path between specified start and end voxels along a biological object with a lumen, such as a vessel, within a patient image three-dimensional volume data set comprising an array of voxels of varying value is identified using an algorithm that works outwards from the start voxel to identify paths of low cost via intermediate voxels. The intermediate voxels are queued for further expansion of the path using a priority function comprising the sum of the cost of the path already found from the start voxel to the intermediate voxel and the Euclidean distance from the intermediate voxel to the end voxel. A cost function that depends on the voxel density is used to bias the algorithm towards paths inside the object. The number of iterations of the voxel required to find a path from the start to the end voxel, and hence the time taken, can be significantly reduced by scaling the Euclidean distance by a constant. Usefully, the constant is greater than 1, such as between 1.5 and 2.
Owner:TOSHIBA MEDICAL VISUALIZATION SYST EURO
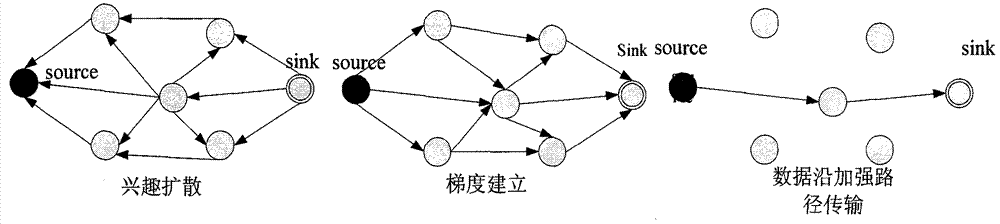
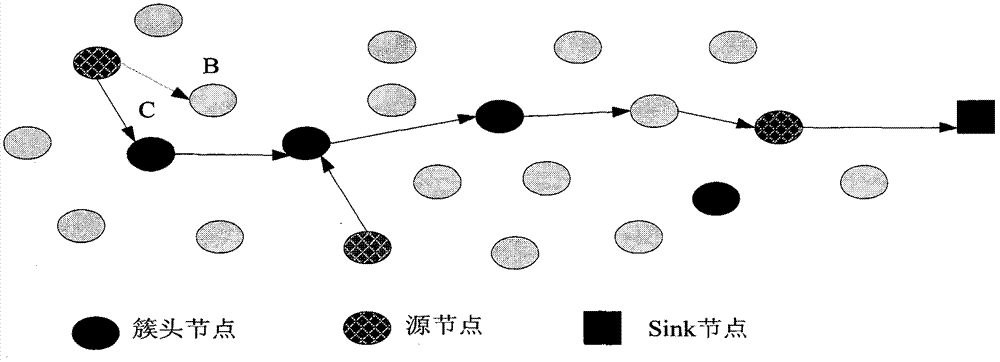
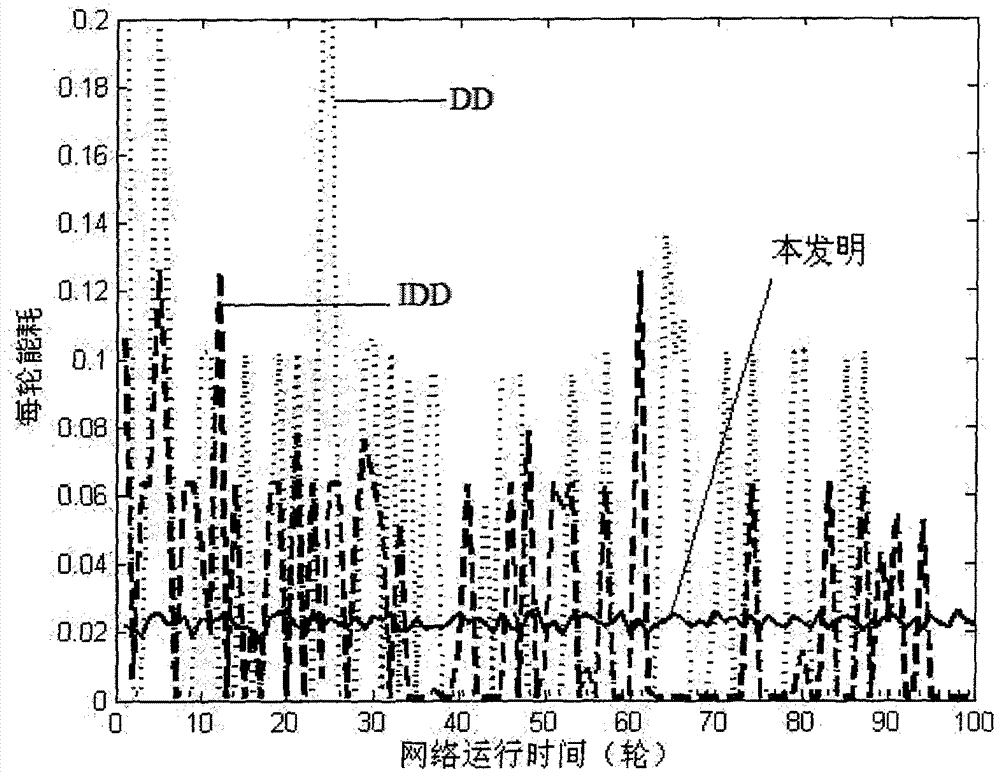
Wireless sensor network multi-source data fusion method based on queries
InactiveCN103139862ABalance scaleReduce energy consumptionEnergy efficient ICTPower managementWireless sensor networkingData transmission
The invention relates to a wireless sensor network multi-source data fusion method based on queries. The wireless sensor network multi-source data fusion method based on the queries comprises clustering, interest spreading and data transmission. In the clustering process, node residual energy to cluster, density of a node placed area and the distance from cluster heads to a base station are utilized. In the interest spreading process, a sink node firstly spread interest news to all cluster heads which then determine whether interest is spread inside clusters according to actual conditions. In the data transmission process, a neighbor node large in priority is chosen as a next jumping node. A priority function enables query data to be transmitted to the sink node along the route which is small in energy consumption, large in residual energy and short in distance according to introducing of neighbor node positions, the fact that whether introduced nodes are source nodes or the cluster heads, residual energy, communication cost of two nodes and the like, and data fusion is performed on the data intersecting position. The wireless sensor network multi-source data fusion method based on the queries can effectively balance node energy consumption in networks, improve energy using efficiency and prolong a network life cycle.
Owner:JIANGNAN UNIV
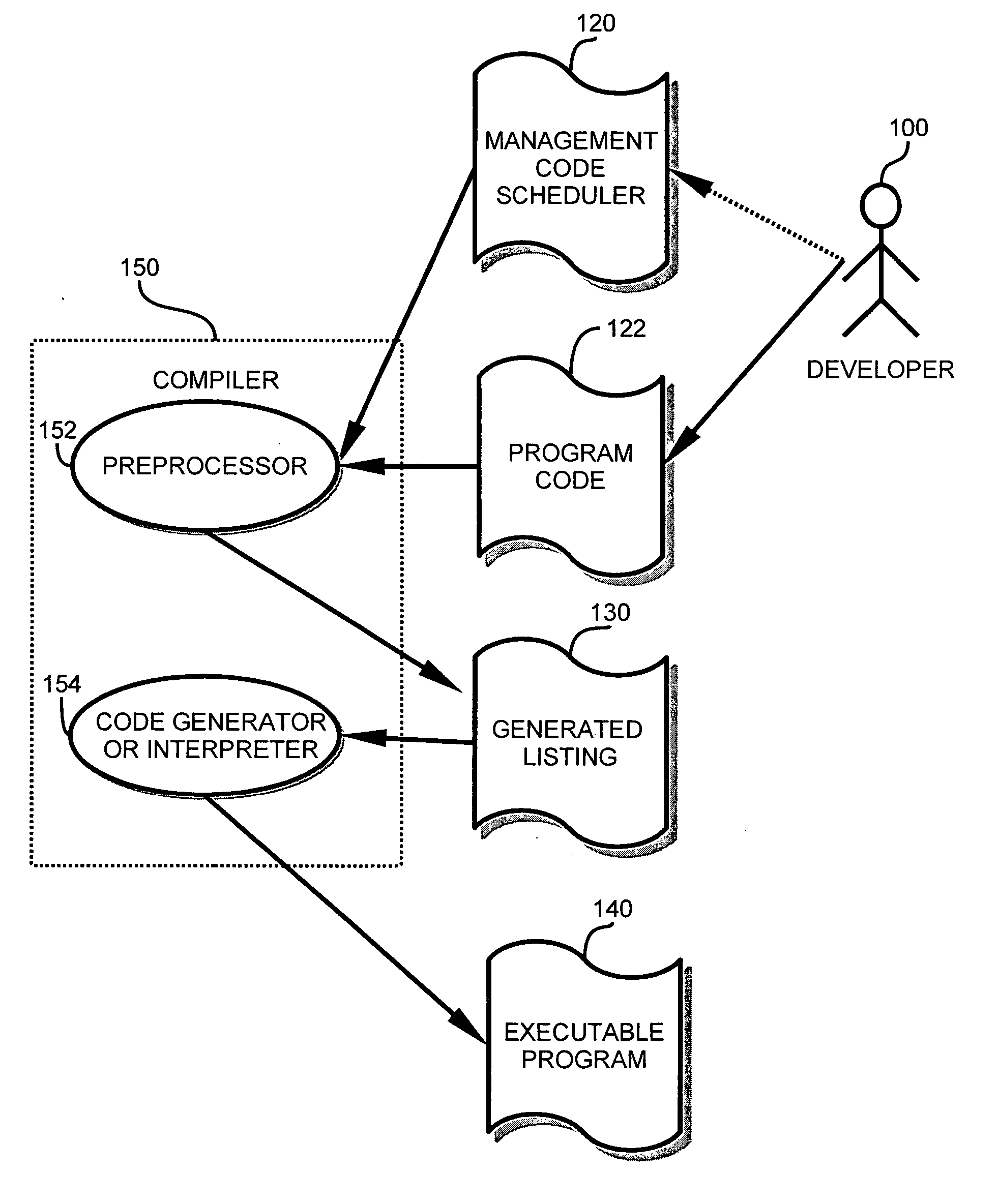
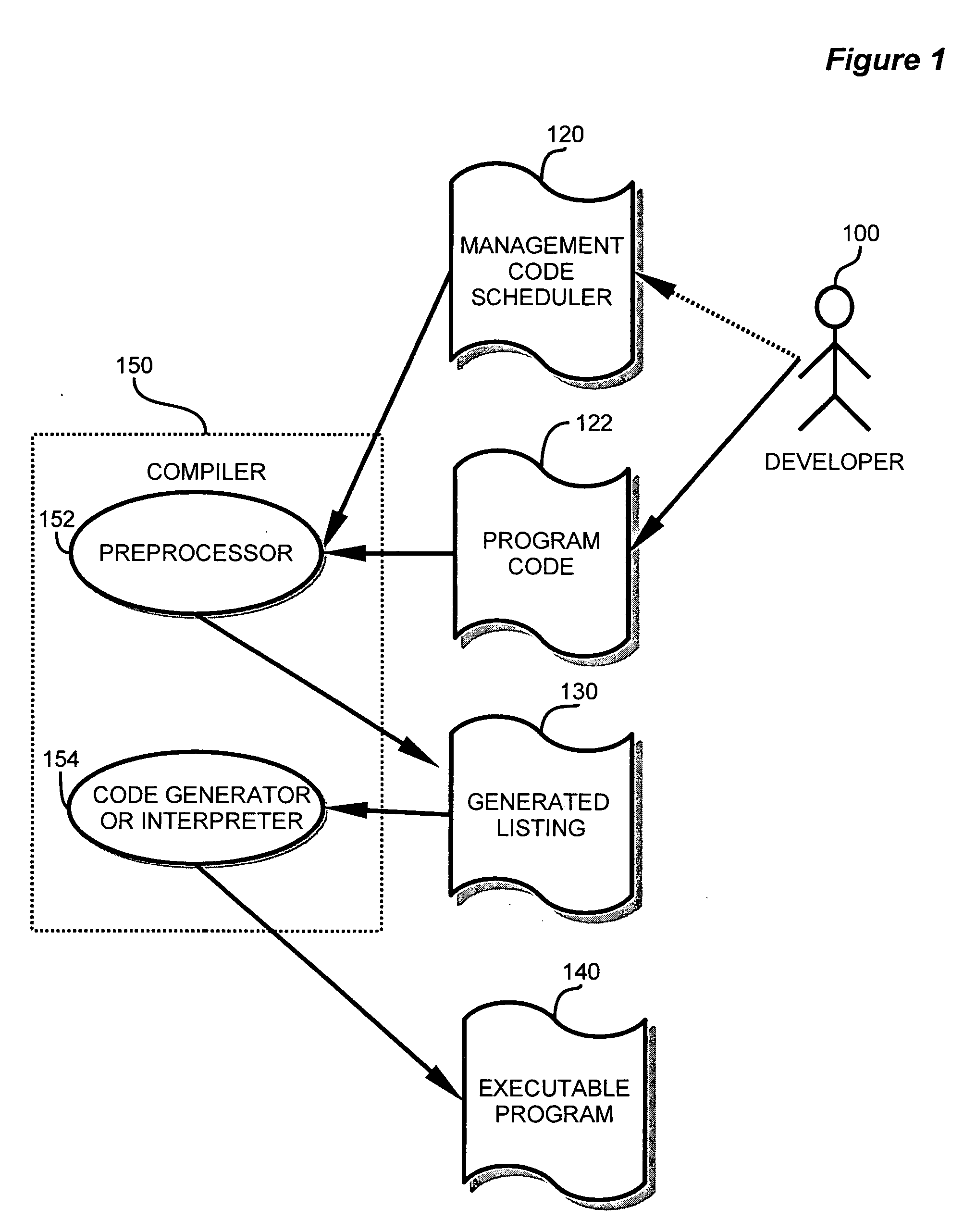
Method and apparatus for implementing task management of computer operations
InactiveUS20060107268A1Easily includedImprove performanceMultiprogramming arrangementsSpecific program execution arrangementsOperational systemPre processor
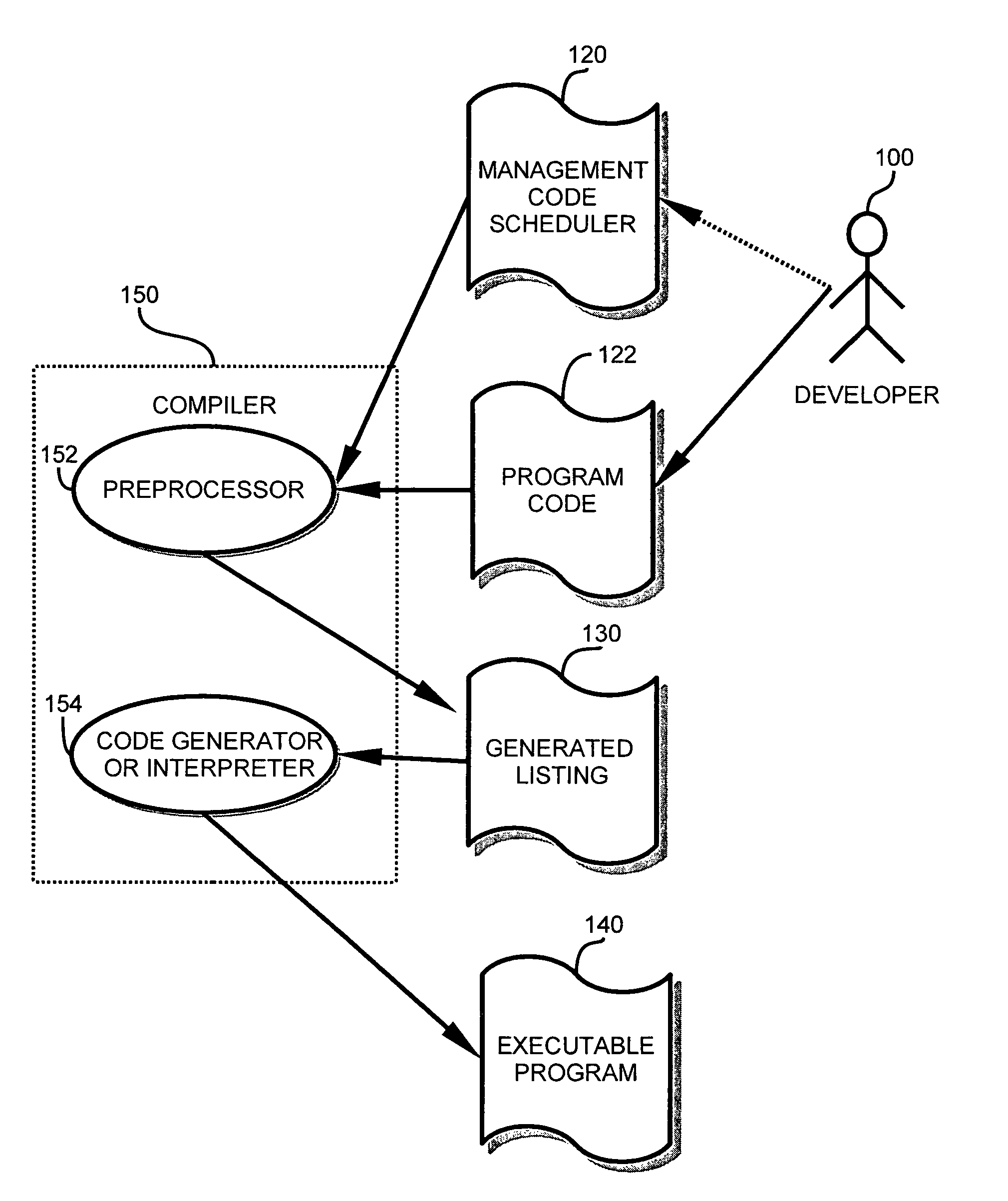
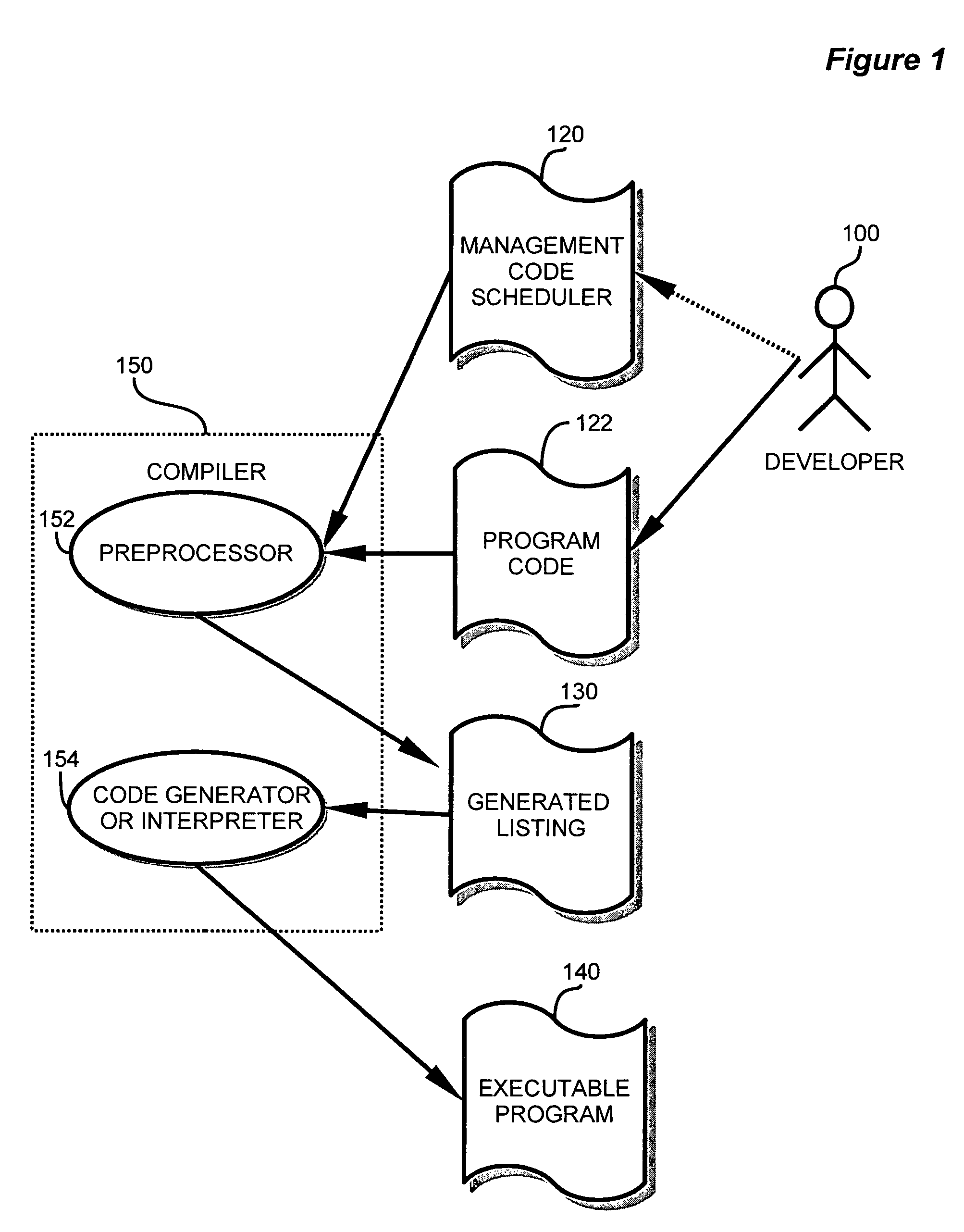
A development and runtime framework for applications that execute in real-time operating systems. Application development is enhanced through simple instructions that allow a programmer to declare functions and sets of functions as tasks and supertasks, respectively, and manage the execution of functions, tasks and supertasks with priorities. A compiler or pre-processor provides tools for generating the code for tasks and supertasks, and the management code for managing execution. Function calls may be made directly to functions within supertasks via respective entrypoints, and the tasks are managed based on the functions being invoked. Within a supertask, a higher priority function may be runnable while a lower priority function of that supertask is suspended. A cookie is used to recognize when a register update for a supertask may be omitted, enabling more efficient context switching.
Owner:SOFTWARE WIRELESS
Techniques for building a knowledge graph in limited knowledge domains
ActiveUS20200057946A1Reduce in quantityArtificial lifeKnowledge representationTheoretical computer scienceFinite-state machine
Techniques disclosed herein relate generally to constructing a customized knowledge graph. In one embodiment, entities and relations among entities are extracted from a user dataset based on certain rules to generate a seed graph. Large-scale knowledge graphs are then traversed using a finite state machine to identify candidate entities and / or relations to add to the seed graph. A priority function is used to select entities and / or relations from the candidate entities and / or relations. The selected entities and / or relations are then added to the seed graph to generate the customized knowledge graph.
Owner:ORACLE INT CORP
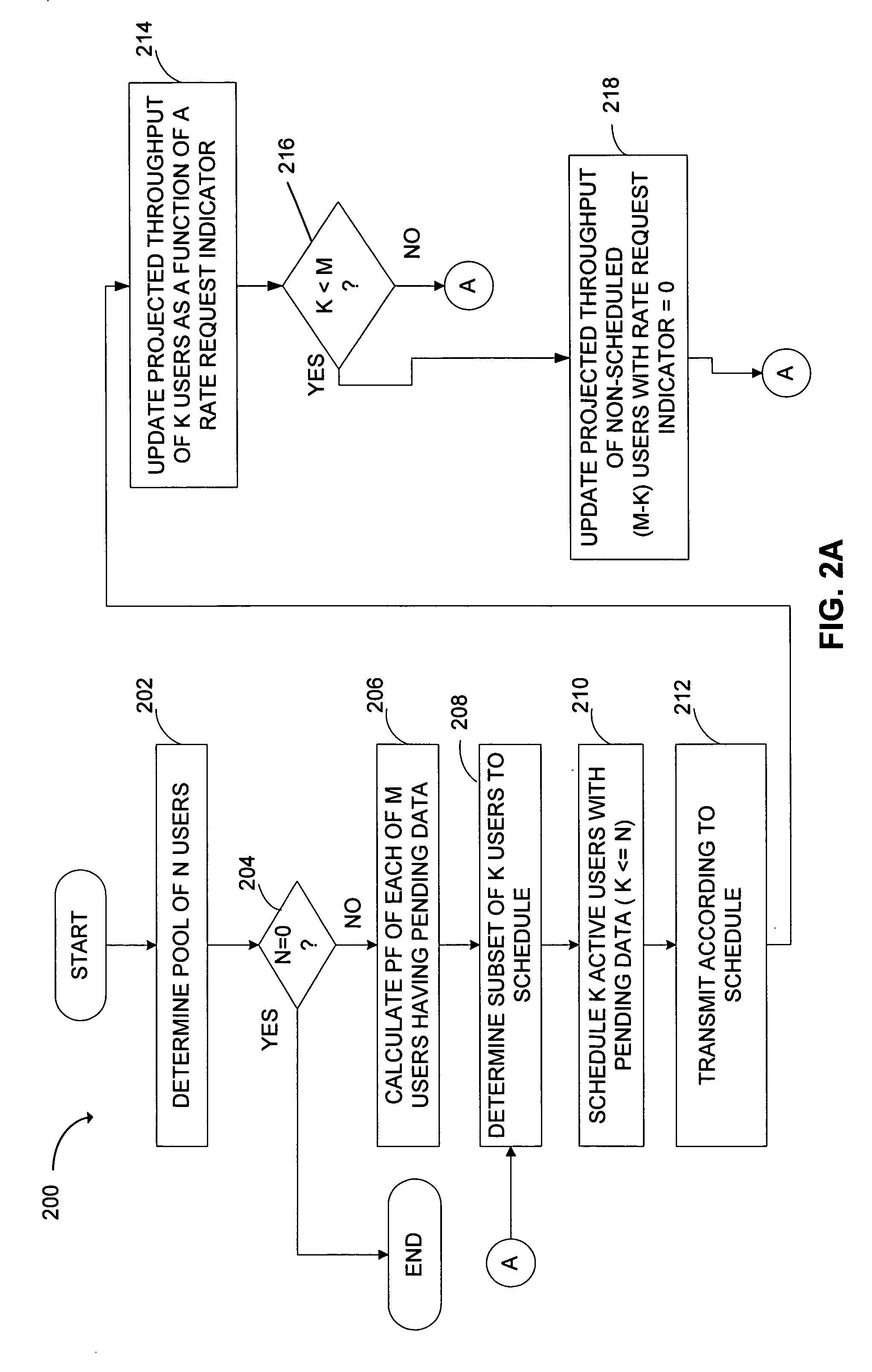
Method and apparatus for scheduling packet data transmissions in a wireless communication system
InactiveUS6847629B2Telephonic communicationTime-division multiplexQuality of serviceCommunications system
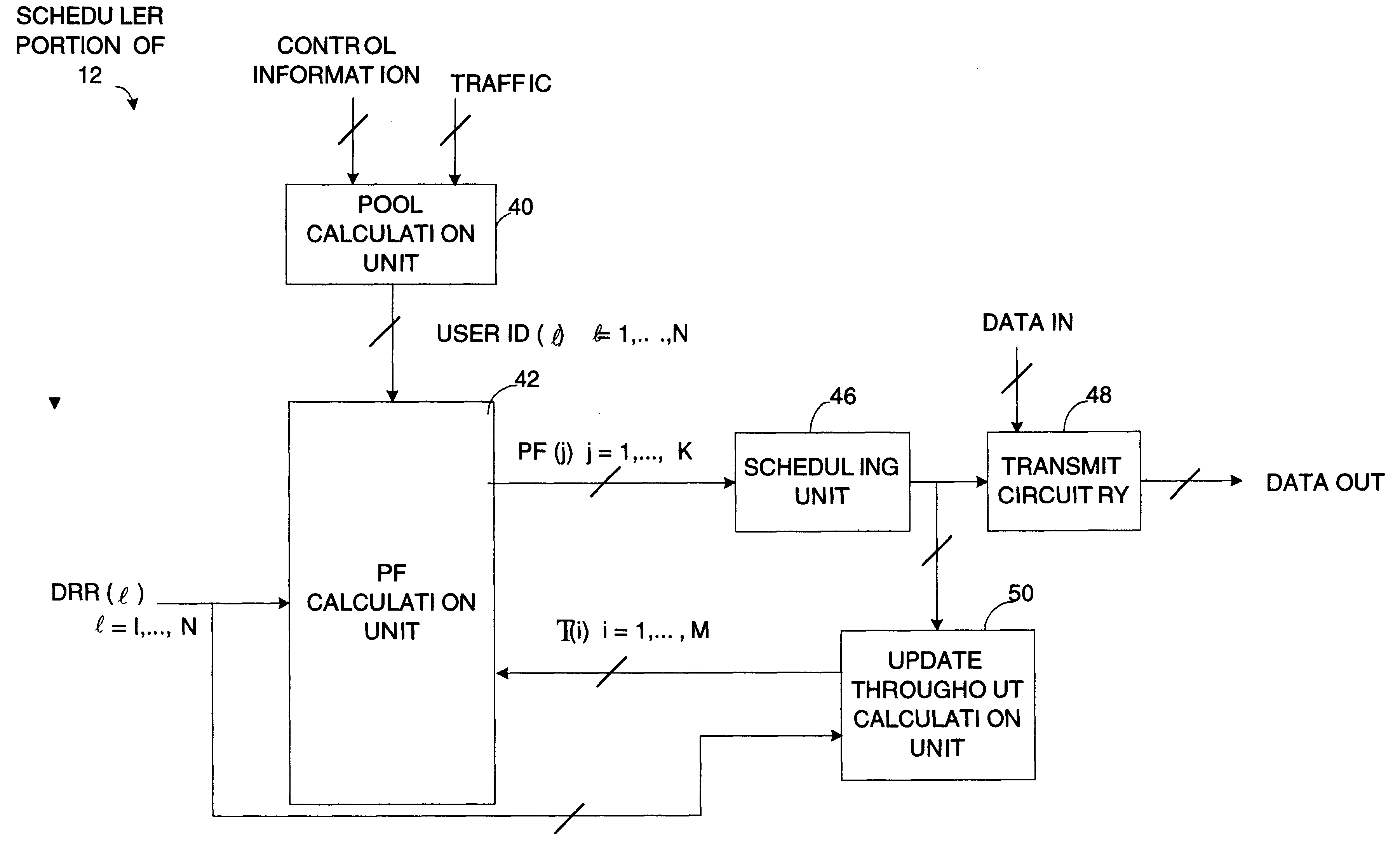
A method (18) for scheduling packet data transmissions in a wireless communication system wherein a per-user Priority Function (PF) (24) is based on a channel condition indicated by a Rate Request Indicator (RRI). The method also considers fairness criteria dictated by predetermined Quality of Service (QOS) requirements. In one embodiment, the rate request indicator is a Data Rate Request (DRR). In another embodiment, the rate request indicator is Carrier-to-Interference (C / I) information. In the exemplary embodiment, the base station calculates a Priority Function (PF) for the multiple mobile users. Each PF is a function of the rate request indicator and the projected throughput of a given mobile user. The PF values allow the base station to schedule active mobile units having pending data. The scheduling produces an approximately equal share of the allocated transmission time to the multiple mobile stations.
Owner:QUALCOMM INC
Business processing method and device based on thread pool
The invention discloses a business processing method and device based on a thread pool. The method and device are used for making a thread pool processing system have the priority function when processing business. The business processing method includes the steps that business to be processed is received and analyzed into N tasks, wherein N is larger than or equal to 1; configuration files of the business to be processed are obtained according to business types of the business to be processed, wherein the configuration files include task queue information of the business to be processed and task priority of the various tasks analyzed by the business to be processed; the N tasks are put into task queues corresponding to the business to be processed according to the task priority of the various tasks, wherein the task queues have priority; the N tasks are sequentially put into the thread pool according to the task queue priority. Due to the task queue priority, business with higher priority is processed first. Besides, the tasks in the task queues also have priority so that the important tasks can be processed first.
Owner:CHINA UNIONPAY
Method and apparatus for scheduling packet data transmissions in a wireless communication system
InactiveUS20050002352A1Error prevention/detection by using return channelDigitally marking record carriersCommunications systemData transmission
A method for scheduling packet data transmissions in a wireless communication system wherein a per-user Priority Function (PF) is calculated based on the channel condition and throughput for each user. In one embodiment, the system supports retransmission of data packets and sub-packets, wherein the retransmission information is used to schedule data transmissions. In another embodiment, at each time interval the system updates the priority factor for the user having the highest priority factor in the previous time interval. The priority factors of the other users remain unchanged.
Owner:QUALCOMM INC
Method and apparatus for implementing priority management of computer operations
InactiveUS20060031838A1Reduce amountReduce overheadMultiprogramming arrangementsSpecific program execution arrangementsOperational systemReal-time operating system
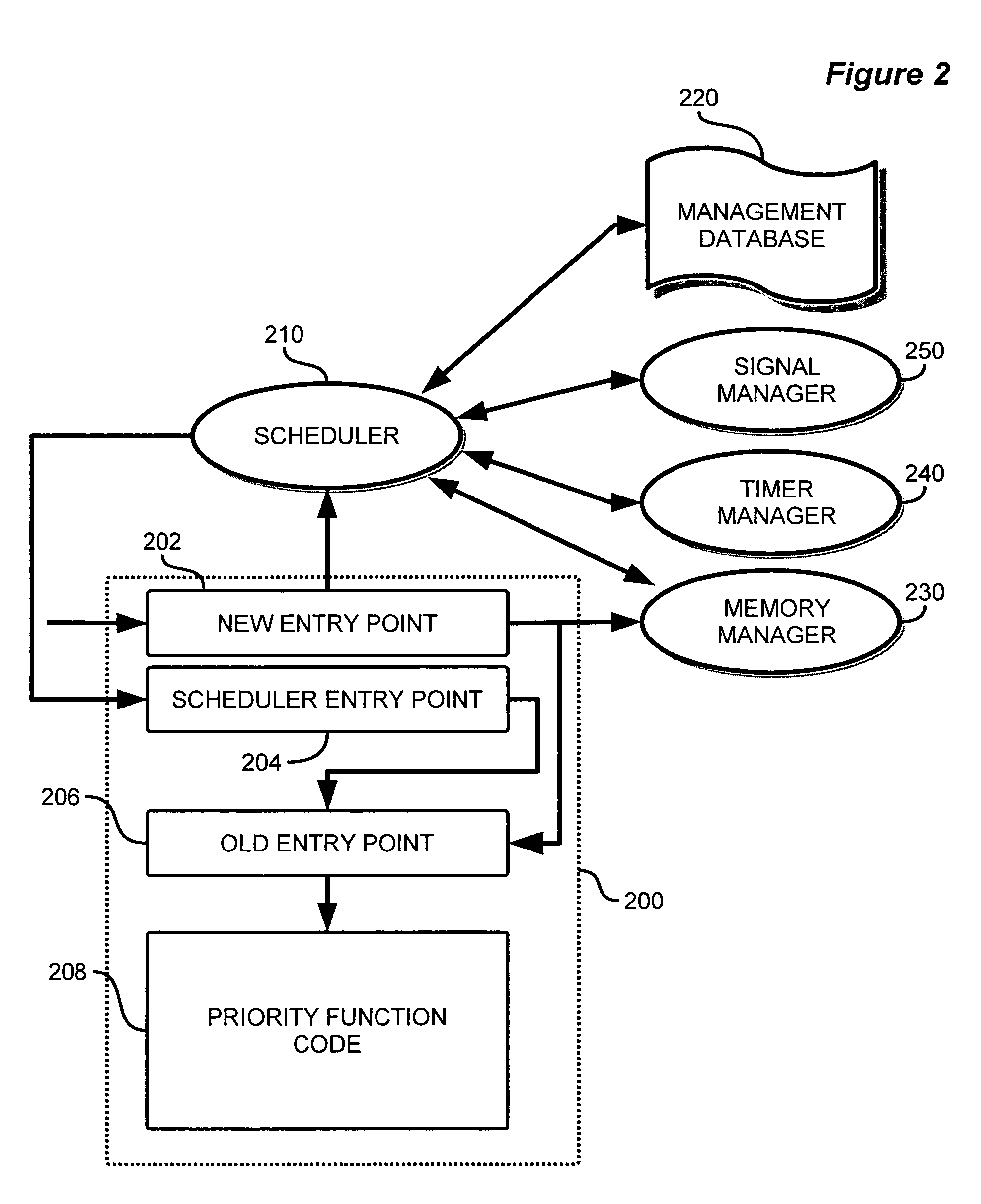
A development framework and runtime environment for applications that execute in real-time operating systems. Application development is enhanced by providing simple instructions that allow a programmer to declare any function as a function managed with priority. Compiler tools implement priority function and the management code for managing execution at runtime. At runtime, priority functions are managed based on their respective priority level. The priority function information is stored when execution is to be delayed.
Owner:CHRABIEH RABIH
Scheduling of wireless packet data transmissions
InactiveUS7295513B2Error preventionFrequency-division multiplex detailsQuality of serviceInterference ratio
A method for scheduling packet data transmissions in a wireless communication system is described wherein a priority function is based on a channel state indicator (CSI), the projected average throughput of the users, and a tuning parameter designed to control the throughput and fairness characteristics of the scheduling algorithm. The method also considers fairness criteria dictated by predetermined Quality of Service (QoS) requirements. The channel state indicator may be a Requested Data Rate (RDR) or Carrier-to-Interference ratio (C / I) information. The base station calculates a priority function for the multiple mobile users. Each priority function is a function of the CSI, the projected average throughput of a given mobile user, the average projected throughput over a set of users, and the tuning parameter.
Owner:TELECOMM RES LAB
Method and system for identifying Chinese full name based on Chinese shortened form of entity
ActiveCN101093478AAchieving identifiabilityAchieve understandingSpecial data processing applicationsNatural language understandingMulti path
A method for identifying Chinese full name according to Chinese short form of entity includes screening out candidate primitive set from normally used entry-bank according to abbreviation sentence to be identified, utilizing multi-path priority function combination to screen said set, calculate priority of candidate primitive, holding candidate primitive with high priority and seeking out one candidate primitive with highest priority as final result. The system used for realizing said method is also disclosed.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method for determining a path along a biological object with a lumen
ActiveUS7379062B2Shorten the timeAvoid excessive computationImage enhancementImage analysisData setVoxel
A path between specified start and end voxels along a biological object with a lumen, such as a vessel, within a patient image three-dimensional volume data set comprising an array of voxels of varying value is identified using an algorithm that works outwards from the start voxel to identify paths of low cost via intermediate voxels. The intermediate voxels are queued for further expansion of the path using a priority function comprising the sum of the cost of the path already found from the start voxel to the intermediate voxel and the Euclidean distance from the intermediate voxel to the end voxel. A cost function that depends on the voxel density is used to bias the algorithm towards paths inside the object. The number of iterations of the voxel required to find a path from the start to the end voxel, and hence the time taken, can be significantly reduced by scaling the Euclidean distance by a constant. Usefully, the constant is greater than 1, such as between 1.5 and 2.
Owner:TOSHIBA MEDICAL VISUALIZATION SYST EURO
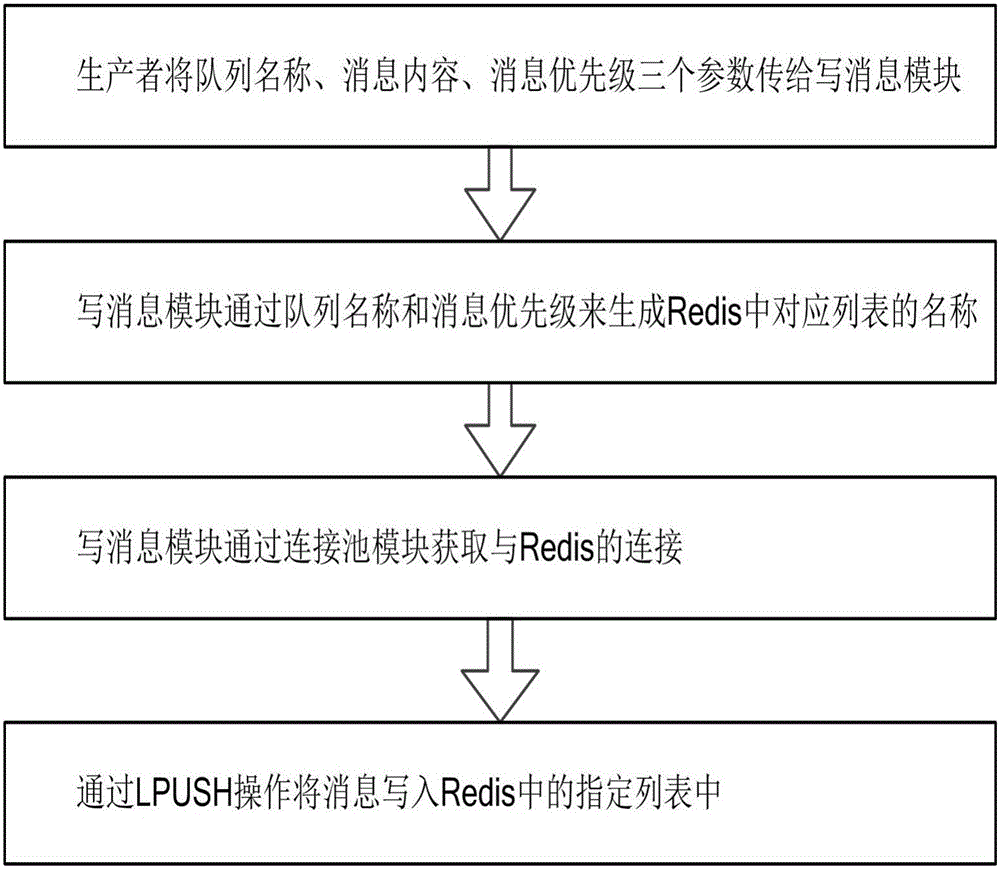
Method and system for achieving priority message queues based on Redis
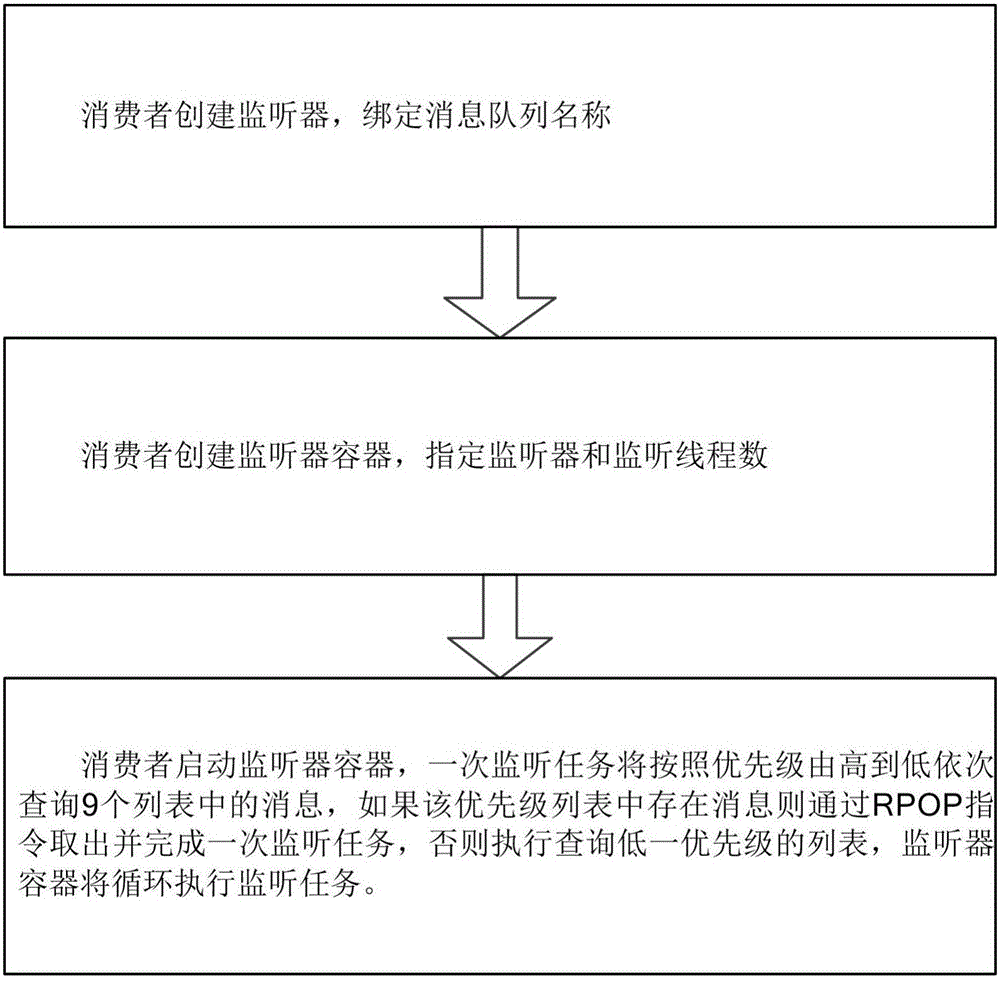
InactiveCN105868033AImplement storageLarge storage capacityInterprogram communicationMessage queueConnection pool
The invention relates to a method and system for achieving priority message queues based on Redis. The system comprises a message write module and a Redis cluster. The message write module is connected with the Redis cluster through a connection pool module. After being connected with the Redis cluster through the connection pool module, the message write module can write message bodies into the Redis cluster, wherein each message body comprises a queue name, message content and a message priority, the Redis cluster stores the message content in the message bodies in message lists of the message queues corresponding to the queue names and the message priorities, and after the Redis cluster stores the message content in the corresponding message lists, connection between the message write module and the Redis cluster is released through the connection pool module. The message queues with the priority function are achieved through the lists of the Redis cluster, the message queues, the number of the message lists in the message queues and the corresponding message content can be checked in real time, and the priorities of the messages can be corrected in real time.
Owner:JIANGSU CAS JUNSHINE TECH +1
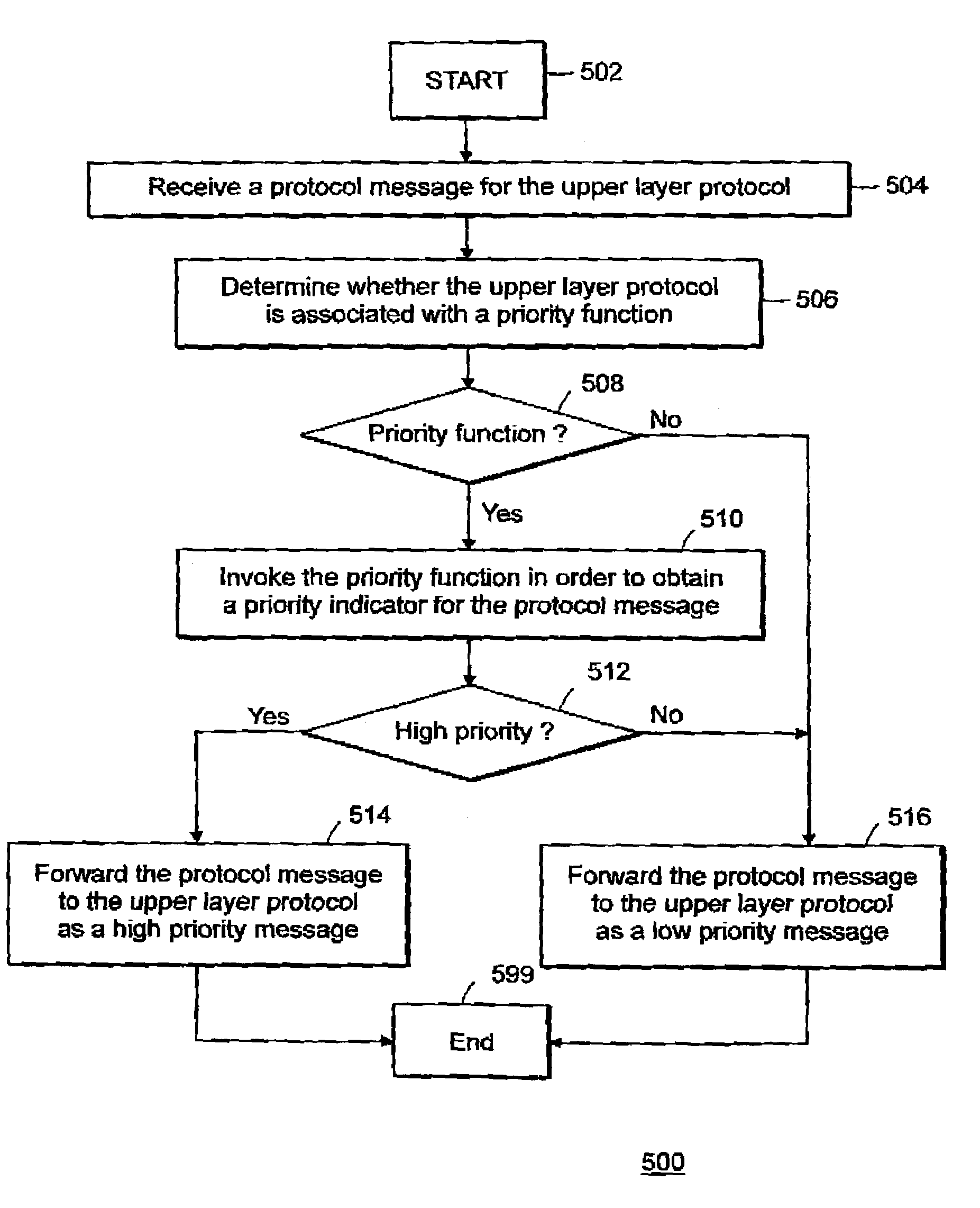
Priority forwarding in a communication system
InactiveUS6987777B1Time-division multiplexData switching by path configurationCommunications systemMessage passing
In a technique for priority forwarding, an upper layer protocol that requires priority forwarding includes a priority function that is invoked by a lower layer protocol in order to obtain the priority for a message. The upper layer protocol provides the priority function to the lower layer protocol when the upper layer protocol is installed in the protocol stack. The lower layer protocol invokes the priority function before passing a message to the upper layer protocol in order to determine a priority for the message. The lower layer protocol places the message in the appropriate queue based upon the priority indicator obtained from the upper layer protocol's priority function.
Owner:RPX CLEARINGHOUSE
A dynamic unloading method of fog computation based on Lyapunov optimization
ActiveCN109343904AImprove performanceOptimum CPU cycle frequencyResource allocationProgram loading/initiatingLyapunov optimizationFog computing
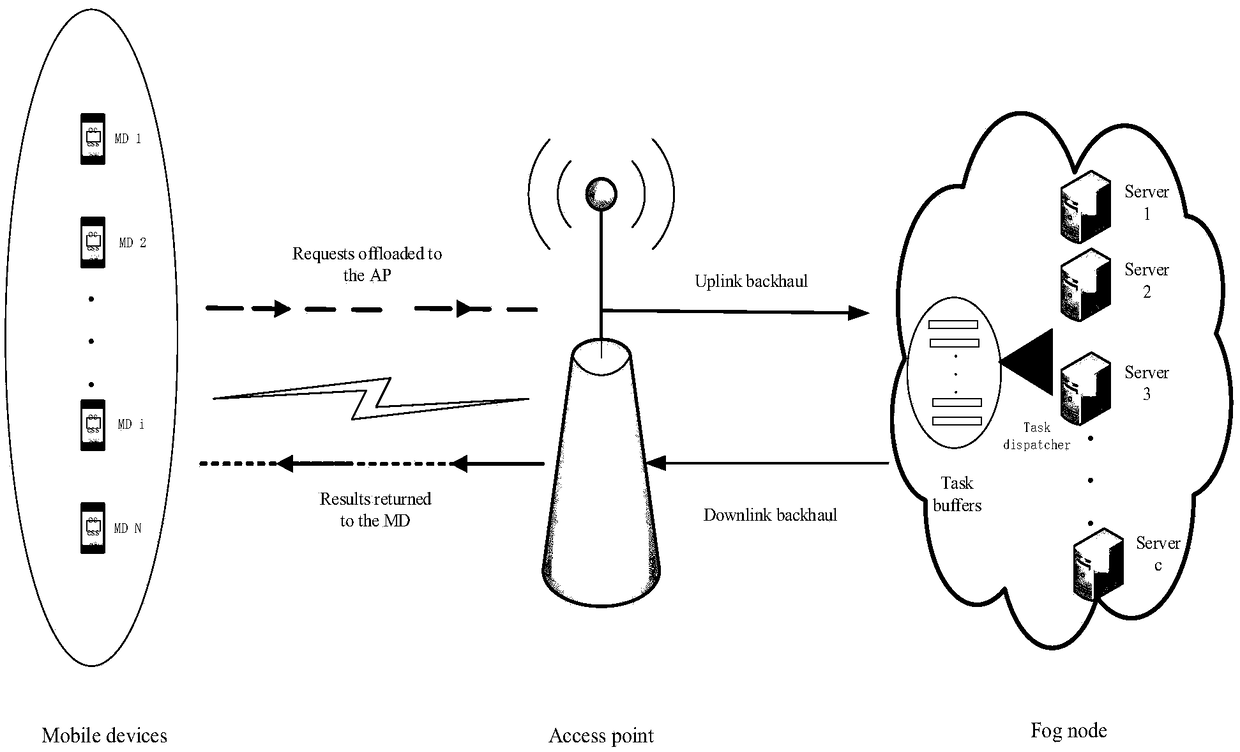
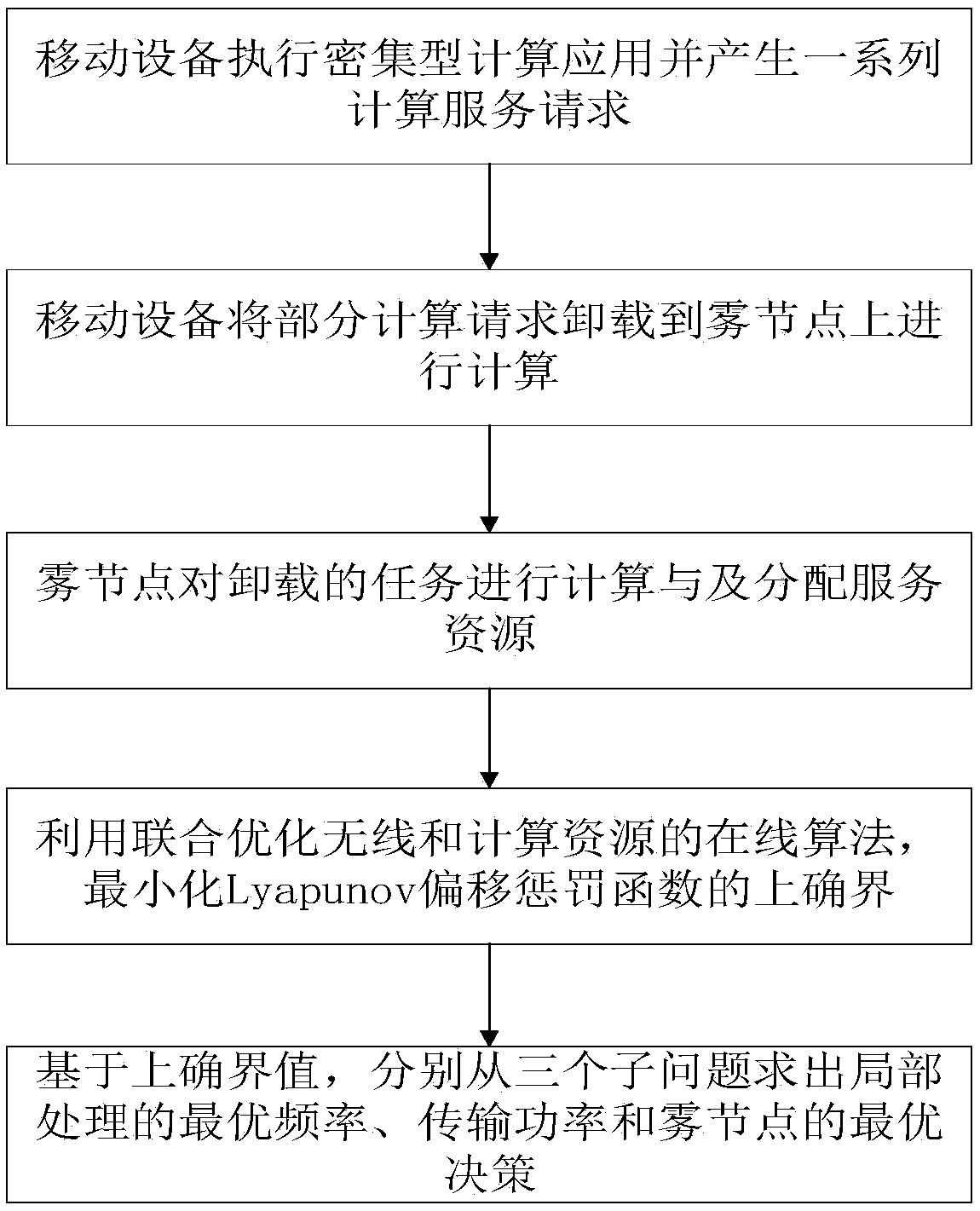
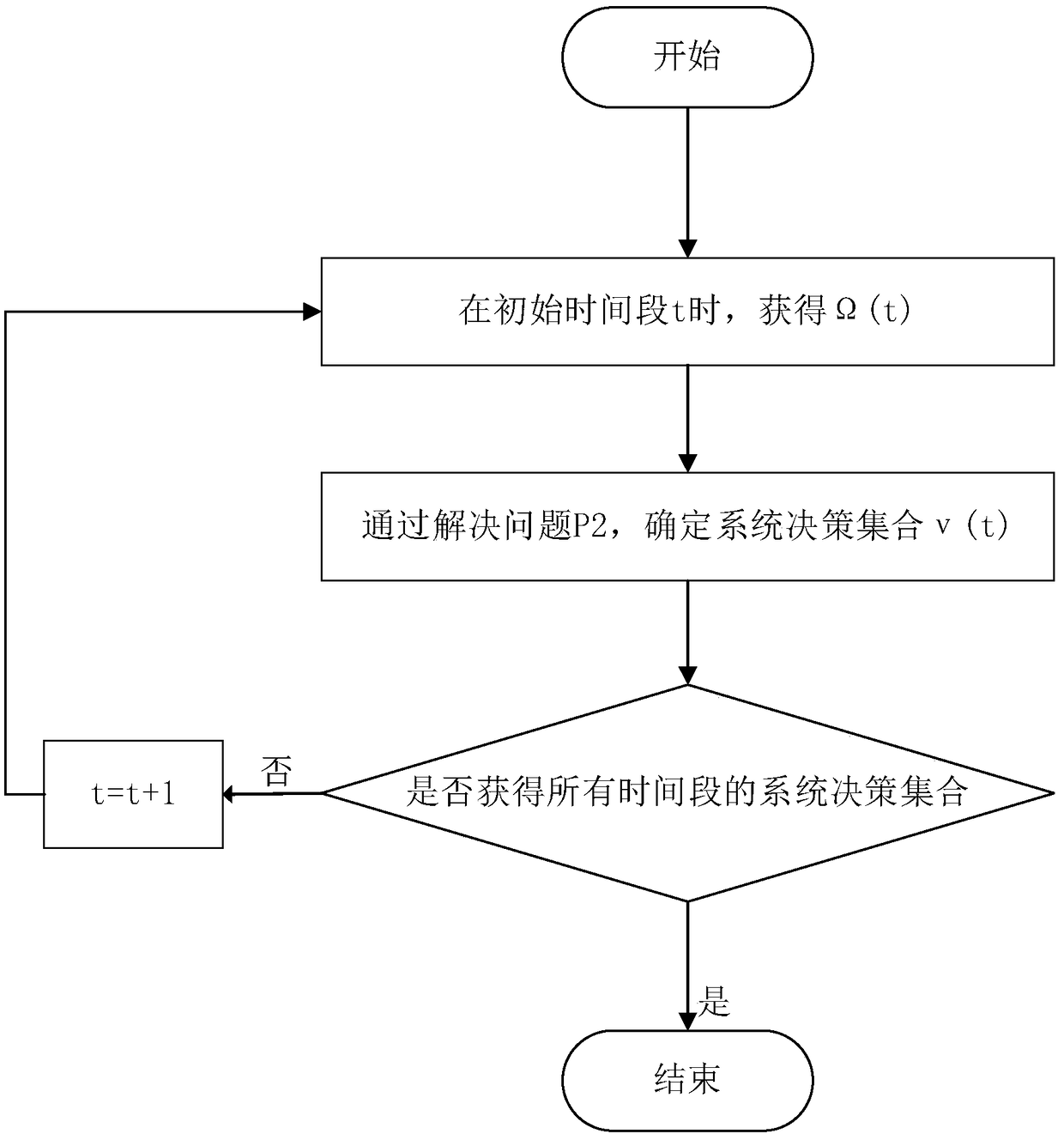
The invention provides a dynamic unloading method of fog calculation based on optimization, belonging to the field of wireless network communication. The present invention divides the calculation request into a local calculation portion and a fog calculation portion. By offloading computationally intensive requests to fog nodes, application performance can be significantly improved. An online joint radio and computational resource algorithm based on Lyapunov optimization is used to derive the upper bound of Lyapunov migration penalty function. By minimizing the upper bound from the perspectiveof different decision variables, , the optimal CPU cycle frequency of local processor is obtained with a convex optimization method. By using the predefined offload priority function, the optimal transmission power of the optimal subchannel is obtained. On the fog node, the optimal request scheduling decision is obtained by absurdity proof.
Owner:YANSHAN UNIV
Method and system for achieving priority of Openflow switchboard chip flow tables
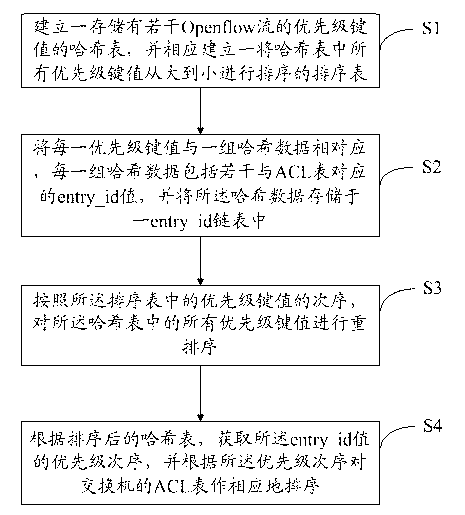
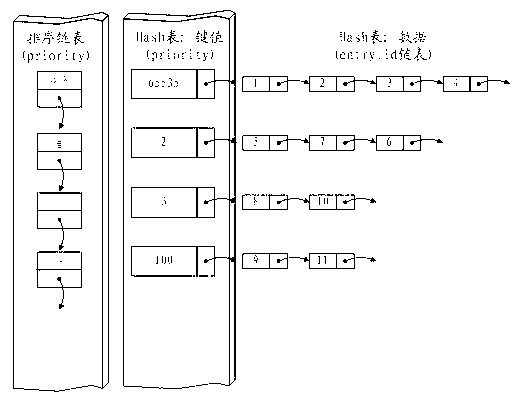
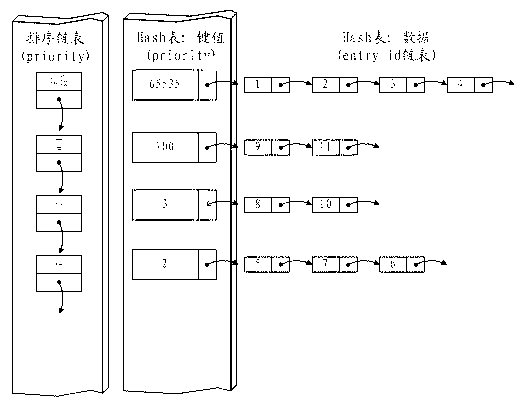
ActiveCN102843298ASatisfy the flow table priority functionEasy to implementData switching networksRe sequencingPriority call
The invention provides a method and a system for achieving priority of Openflow switchboard chip flow tables. The method comprises the following steps of: establishing an Hash table which is stored with a plurality of Openflow priority values and correspondingly establishing a sequencing table for sequencing all priority values in the Hash table from big to small; enabling each priority value to be corresponding to one group of Hash data, wherein each group of Hash data includes a plurality of entry_id values corresponding to an ACL (Access Control List), and the hash data is stored in one entry_id link list; re-sequencing all priority values in the Hash table according to the sequence of the priority values in the sequencing table; acquiring the priority sequence of the entry_id values according to the sequenced Hash stable, and correspondingly sequencing an ACL table of the switchboard according to the priority sequence. According to the invention, an ACL function on the traditional switchboard chip is utilized to achieve a flow table priority function satisfying an Openflow protocol, and moreover, an achieving manner is simple.
Owner:SUZHOU CENTEC COMM CO LTD
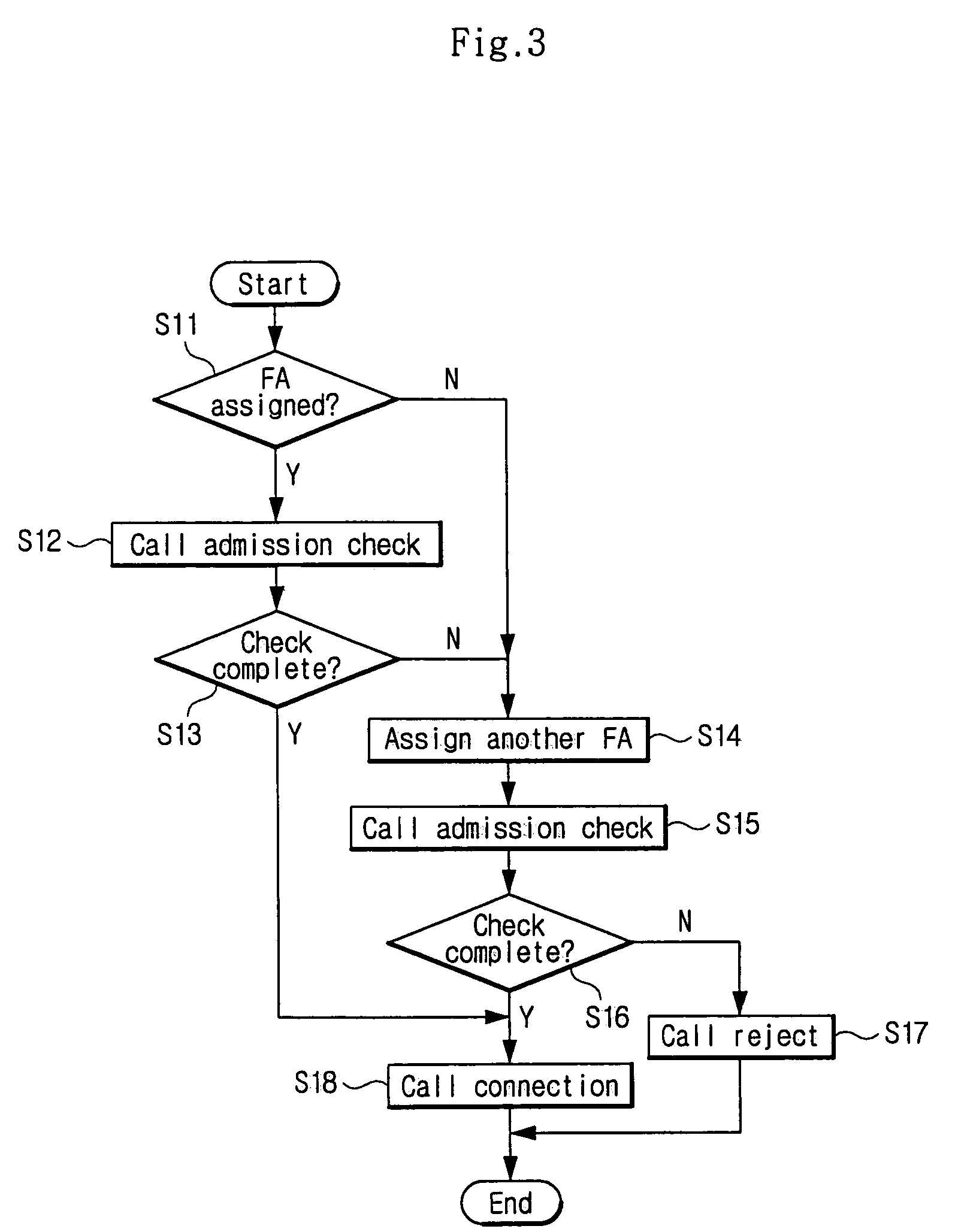
Method of controlling call admission in a mobile communication system
InactiveUS7295514B2Reduce scrap rateGuaranteed QoS levelError preventionFrequency-division multiplex detailsMobile communication systemsSpeech sound
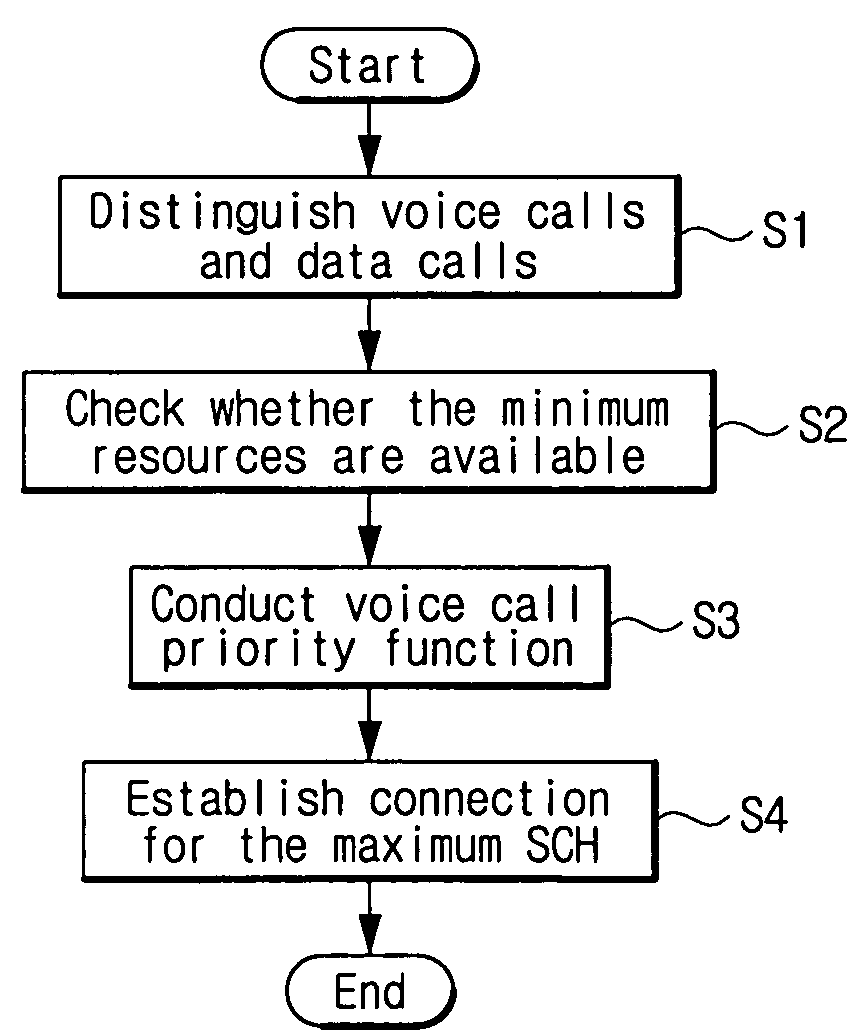
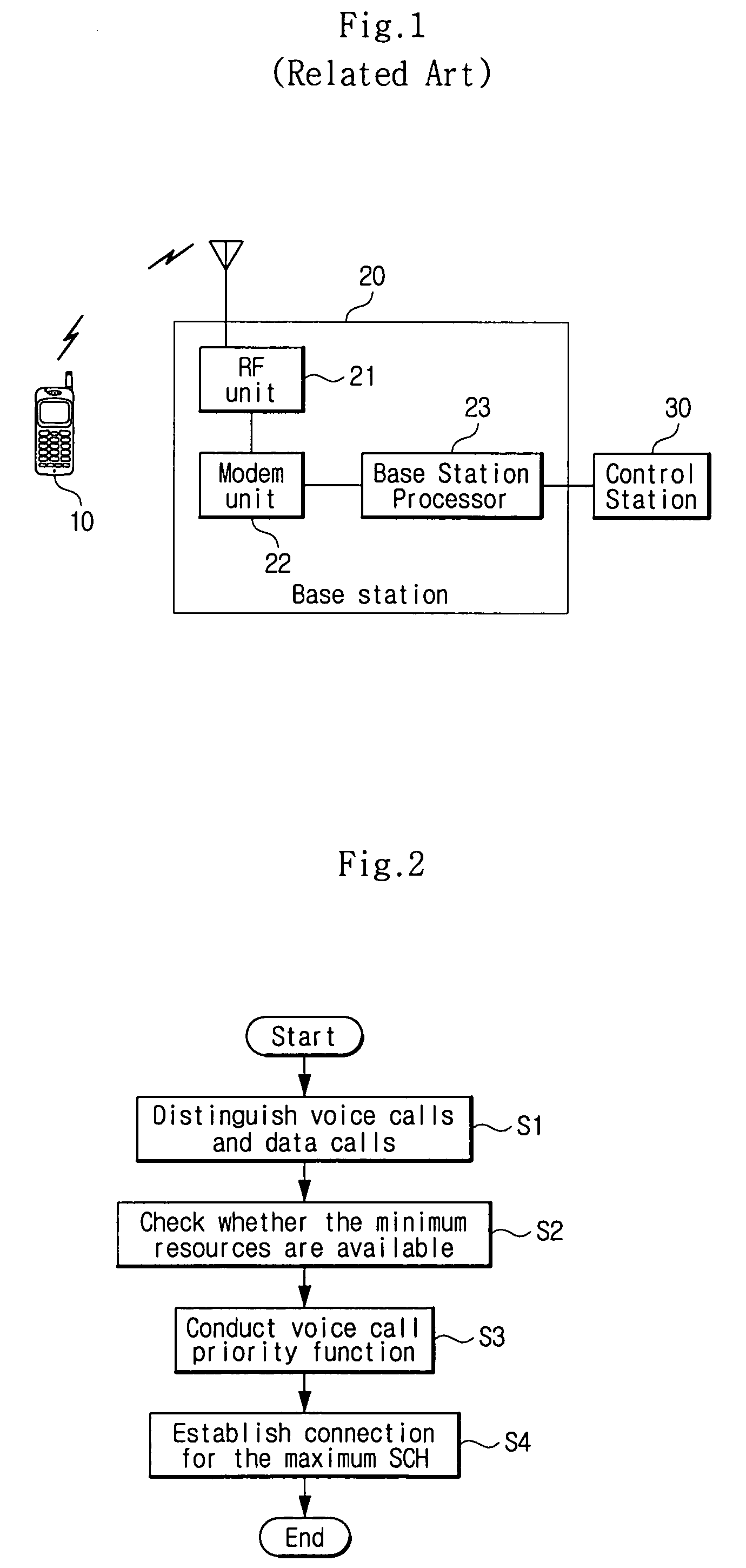
A system and method for controlling call admission control in a mobile communication system enables call admission control function to be conducted in a forward link of the mobile communication system. The call admission control method includes a call admission control process, in which voice calls and data calls are distinguished from each other, minimum resource availability is checked, a voice call priority function is conducted, and a maximum supplemental channel (SCH) for the data call is established. According to this process QoS (Quality of Service) for all users is satisfied to the greatest extent and the occurrence of call reject and call drop of voice calls and data calls are reduced. Further, the voice call priority may be guaranteed and the database related to the call admission control may be adjusted easily by the system operator according to the relevant cell environment.
Owner:LG ERICSSON
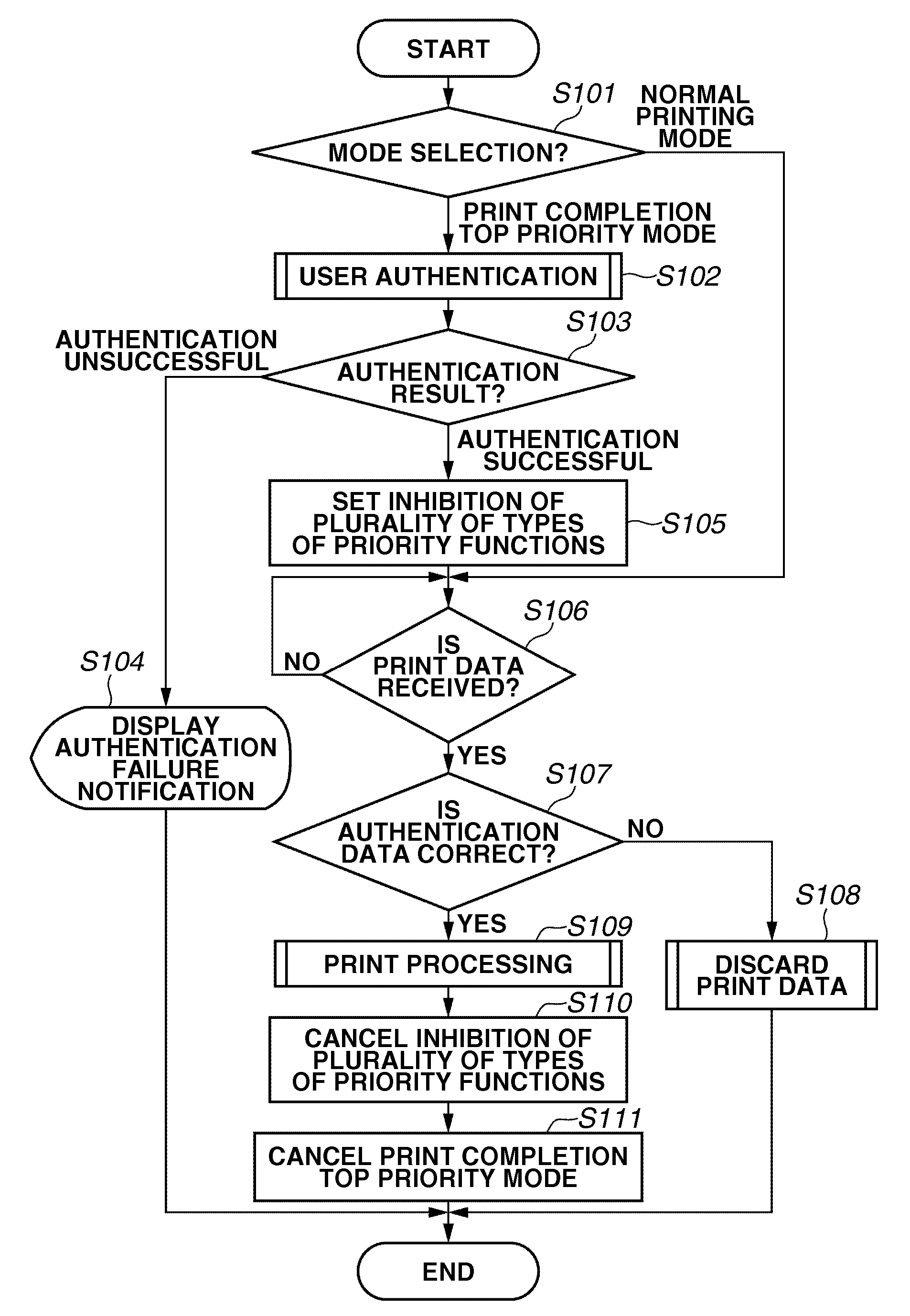
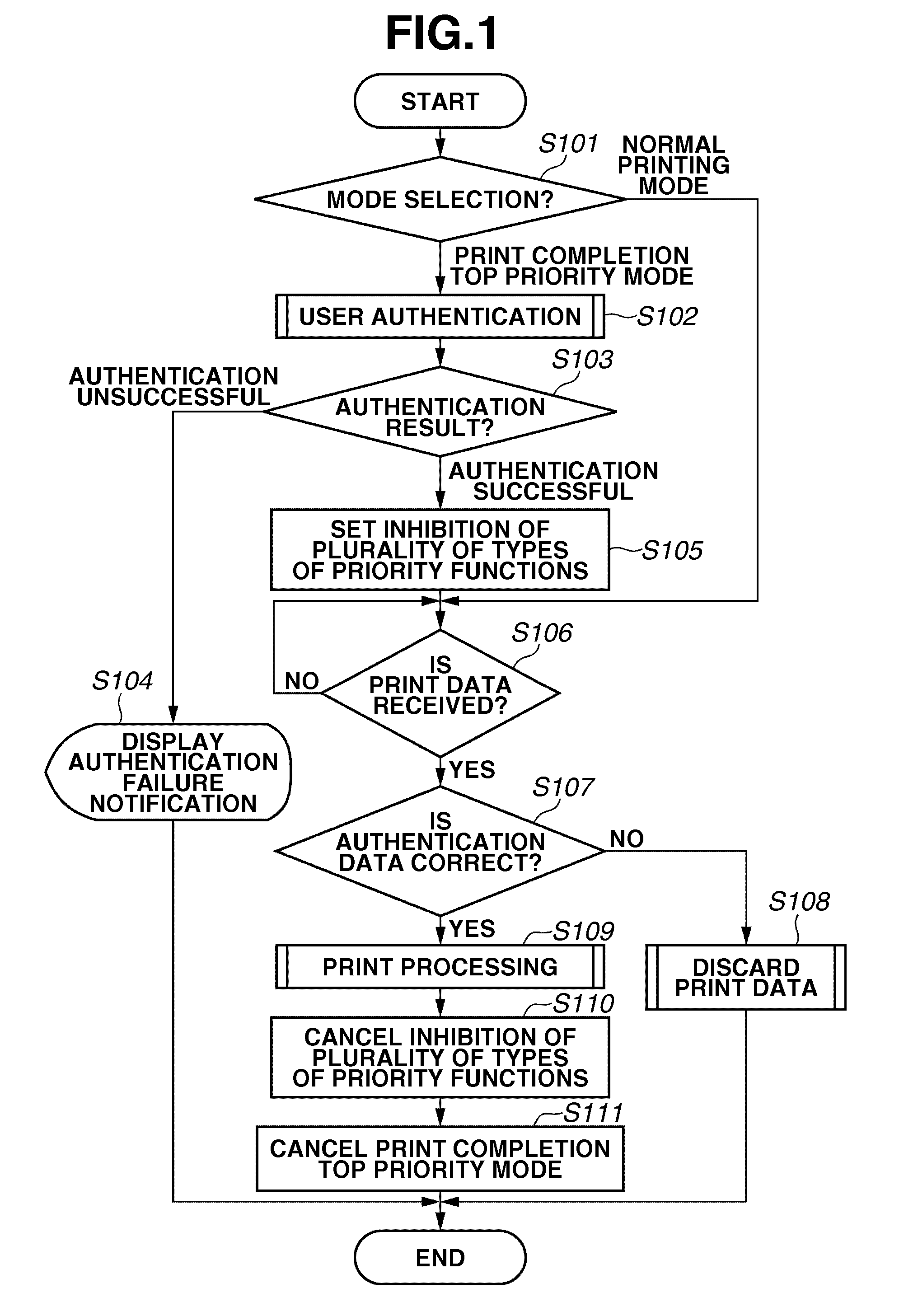
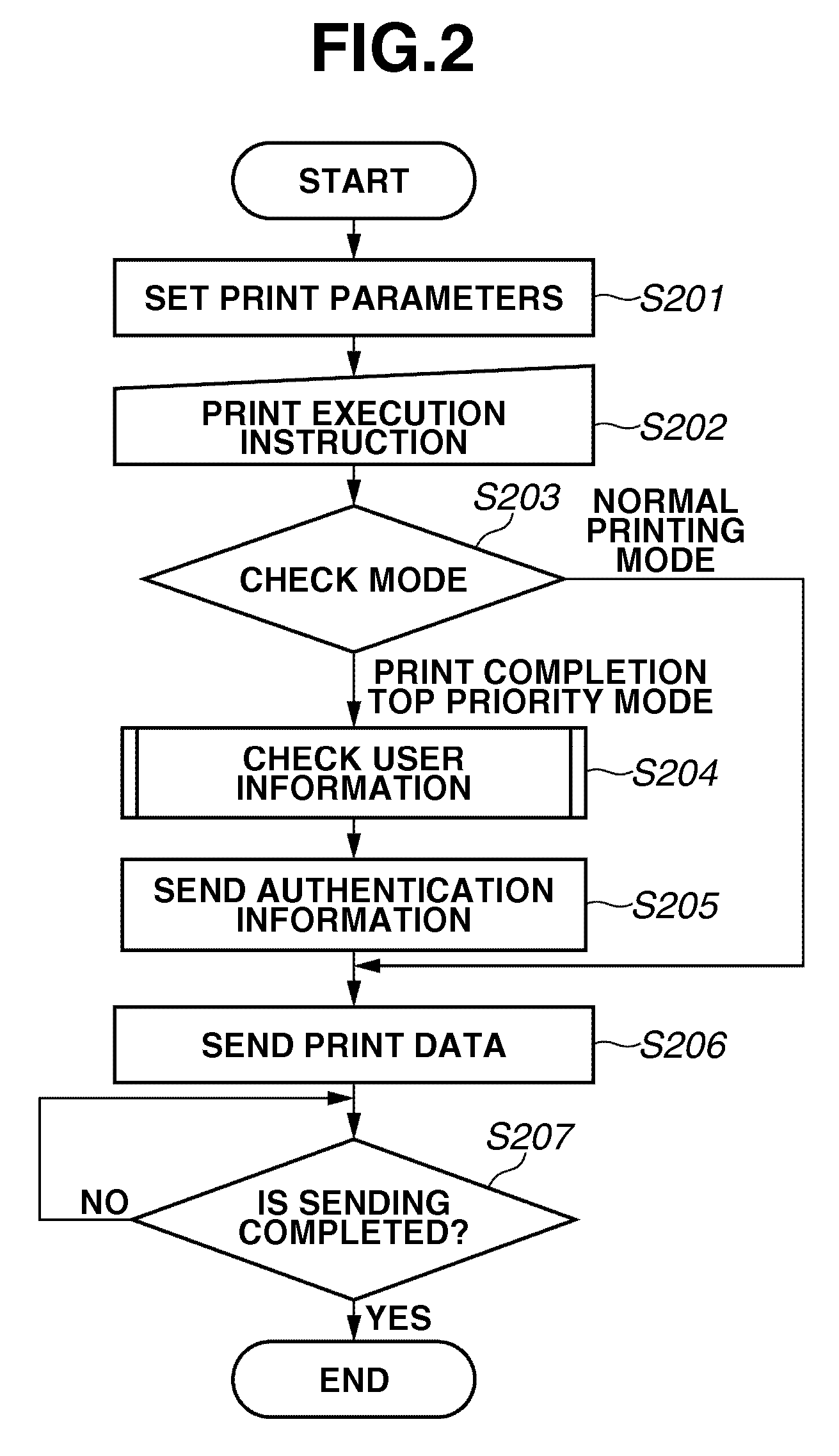
Job processing system, control method and recording medium
A method for controlling a job processing system for causing a job processing unit to execute a job, including performing a plurality of priority functions, which cause the job processing unit to execute a job in priority to a job being executed and / or waiting to be executed, and collectively inhibiting the plurality of priority functions upon receiving a request for collectively inhibiting the plurality of priority functions.
Owner:CANON KK
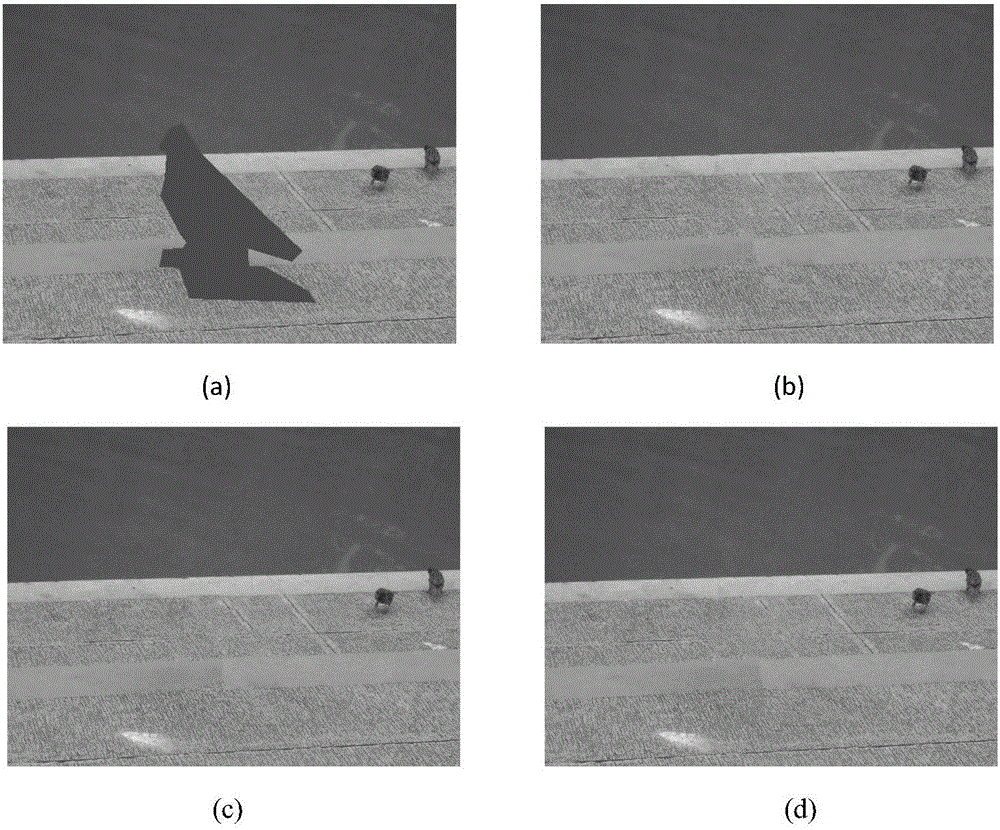
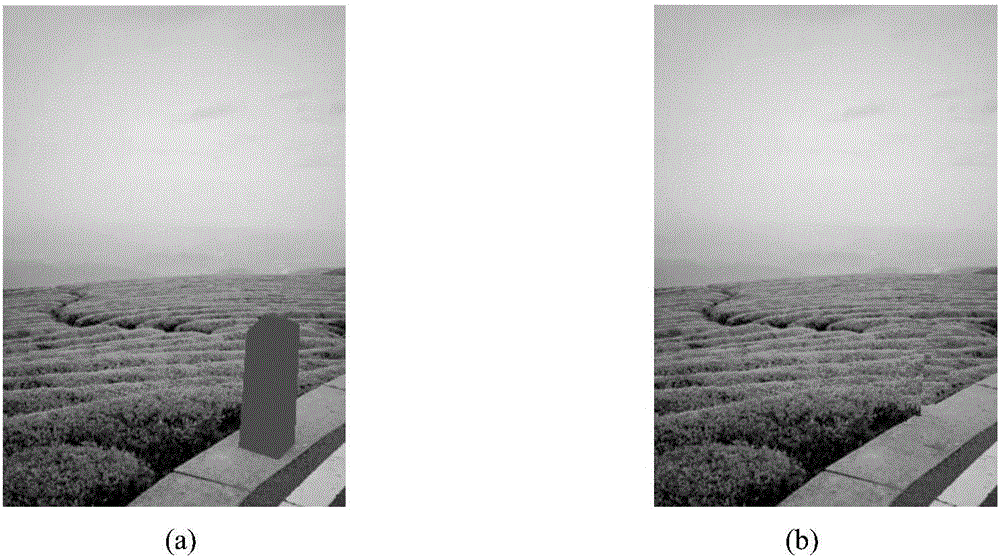
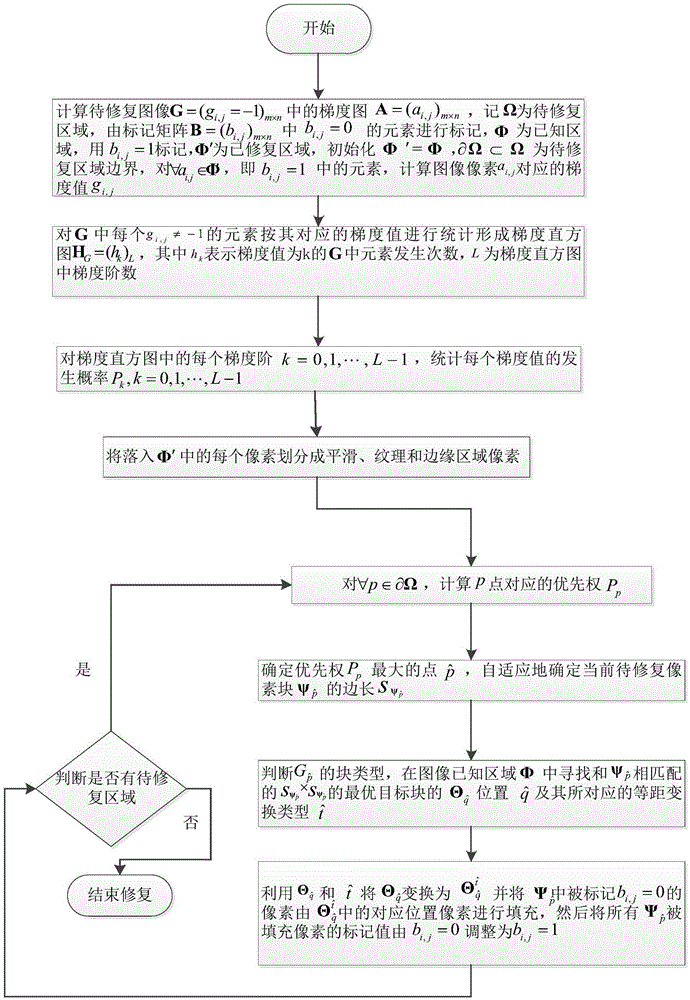
Image repairing method based on sample structure consistency
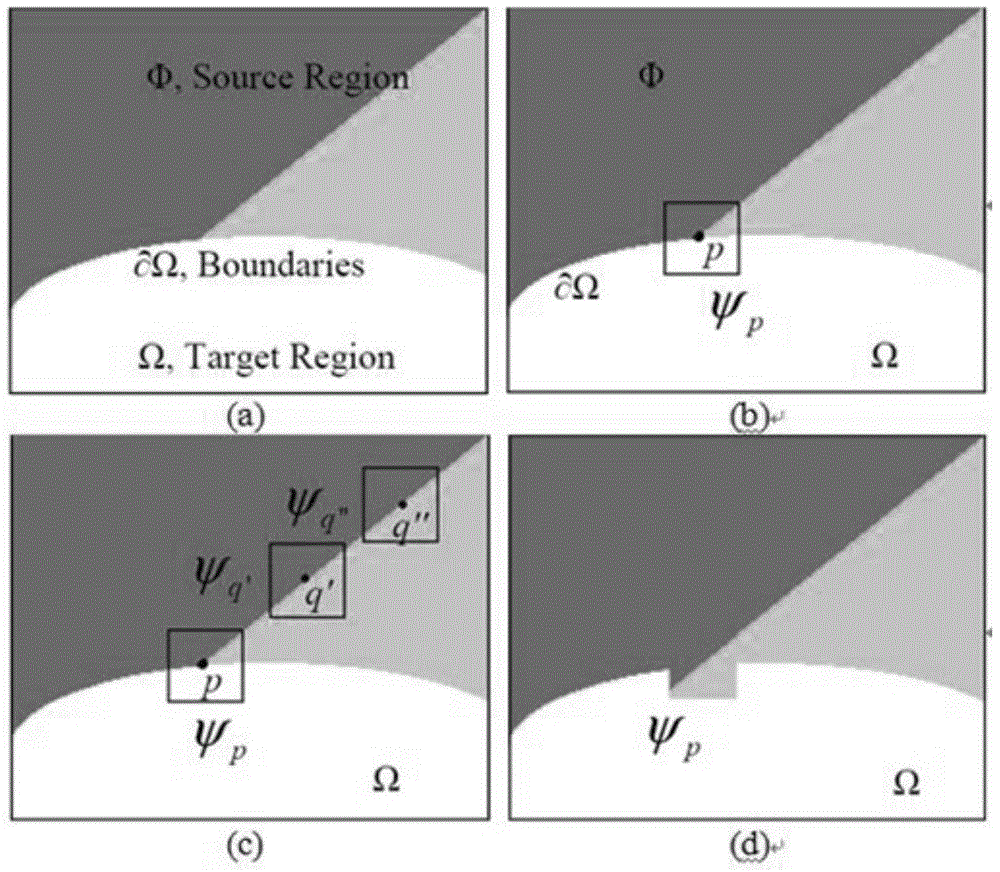
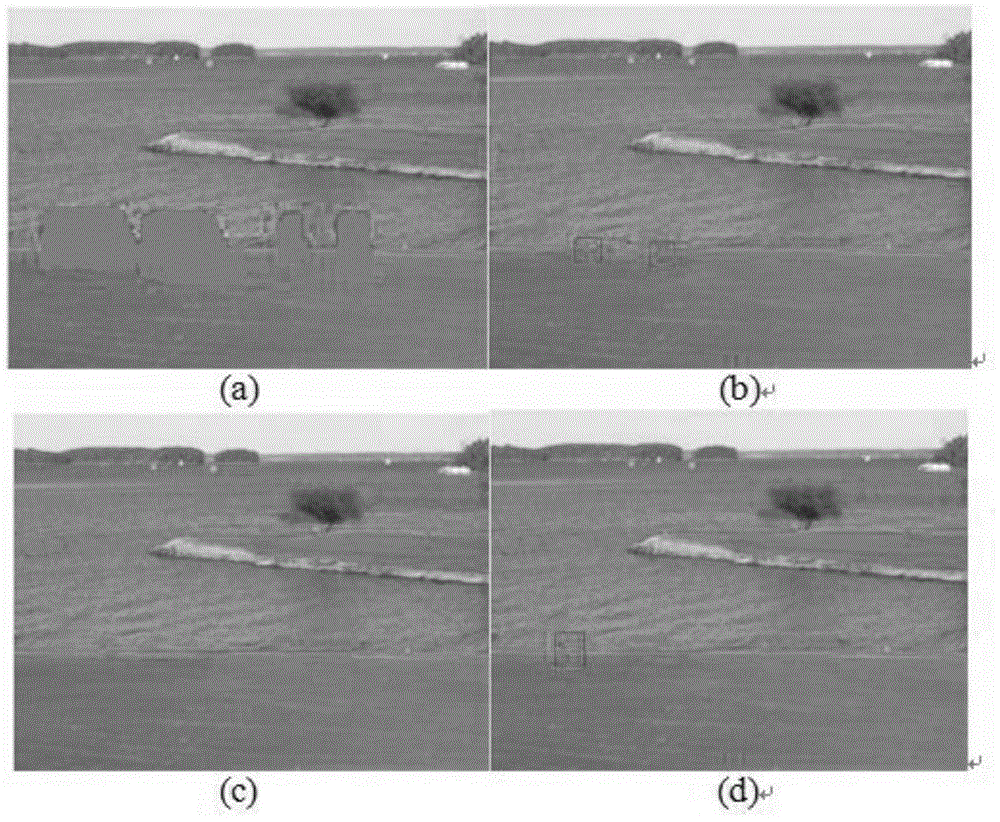
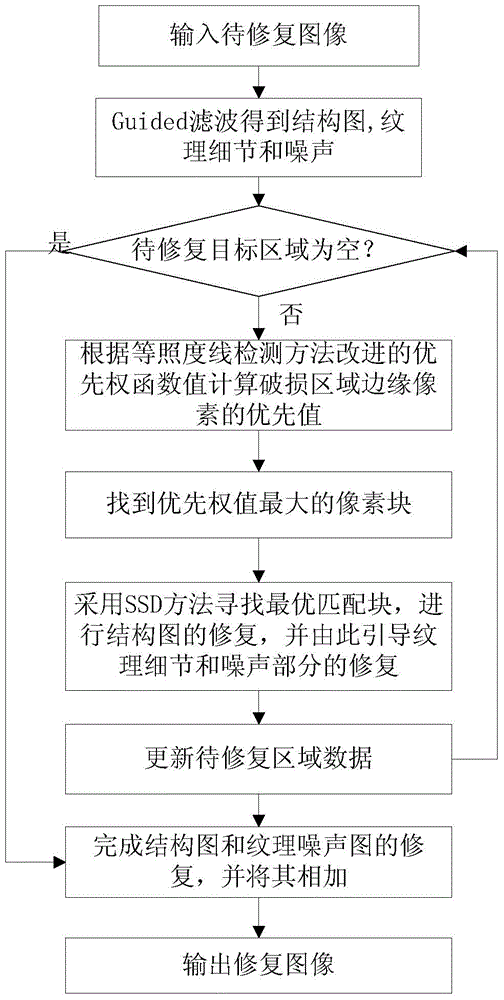
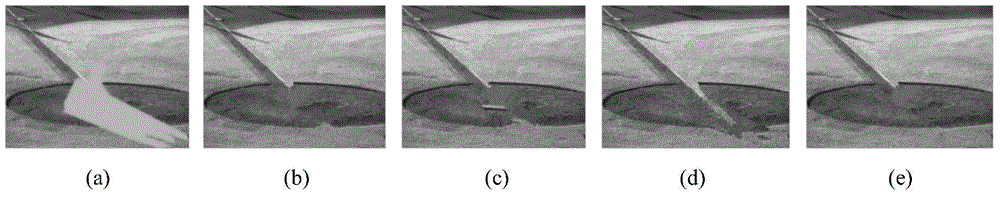
The invention relates to an image repairing method based on sample structure consistency. The image repairing method comprises the following steps: determining an image defect area boundary (the symbol of which is shown in the description) and calculating a priority function value of each pixel point p on the image defect area boundary; selecting the pixel point (p') with a maximum priority value P(p) from the pixel points on the image defect area boundary and then finding matching blocks which is the most similar to a target block (psi p') in a known image area; finding the optimal matching block (psi q') and then enabling unknown pixel points in the target block (psi p') to be filled with corresponding pixel values in the optimal matching block (psi q'); updating the confidence of the filled pixel points; repeating the above steps till the defect area is completely filled.
Owner:ZHEJIANG UNIV OF TECH
Method and apparatus for implementing priority management of computer operations
InactiveUS8166483B2Reduce amountReduce overheadMultiprogramming arrangementsSpecific program execution arrangementsOperational systemApplication software
A development framework and runtime environment for applications that execute in real-time operating systems. Application development is enhanced by providing simple instructions that allow a programmer to declare any function as a function managed with priority. Compiler tools implement priority function and the management code for managing execution at runtime. At runtime, priority functions are managed based on their respective priority level. The priority function information is stored when execution is to be delayed.
Owner:CHRABIEH RABIH
Image inpainting method based on isoluxline
ActiveCN104574317AImprove reliabilityImprove repair effectImage enhancementImage structurePriority function
The invention discloses an image inpainting method based on isoluxline. The image inpainting method based on the isoluxline comprises the following steps of improving a traditional isoluxline function through an edge-stopping function of an anisotropic propogation arithmetic and combining the improved isoluxline function with a traditional image inpainting priority function to obtain a stable priority calculation function; obtaining a priority value of a broken pixel block in a structural image through the priority calculation function; seeking a sample block with the highest similarity, namely the best-match domain block, within the scope of a whole image and completing the inpainting of the broken area in the structural image and completing the inpainting of the broken are in the structural image; inpainting a broken texture detail image by a texture detail sample block, corresponding to the best-match domain block in the structural image, in a texture detail image; superimposing the structural image completed the inpainting and the texture detail image to complete an image inpainting process. The image inpainting method based on the isoluxline effectively maintains the structural information of an image need the inpainting and obtains relatively ideal inpainting effect of a texture with illumination changes simultaneously.
Owner:天津渤化讯创科技有限公司
Combined content addressable memories
InactiveUS6957299B2To overcome the large delayReduce in quantityMemory adressing/allocation/relocationDigital storageMemory chipComputer module
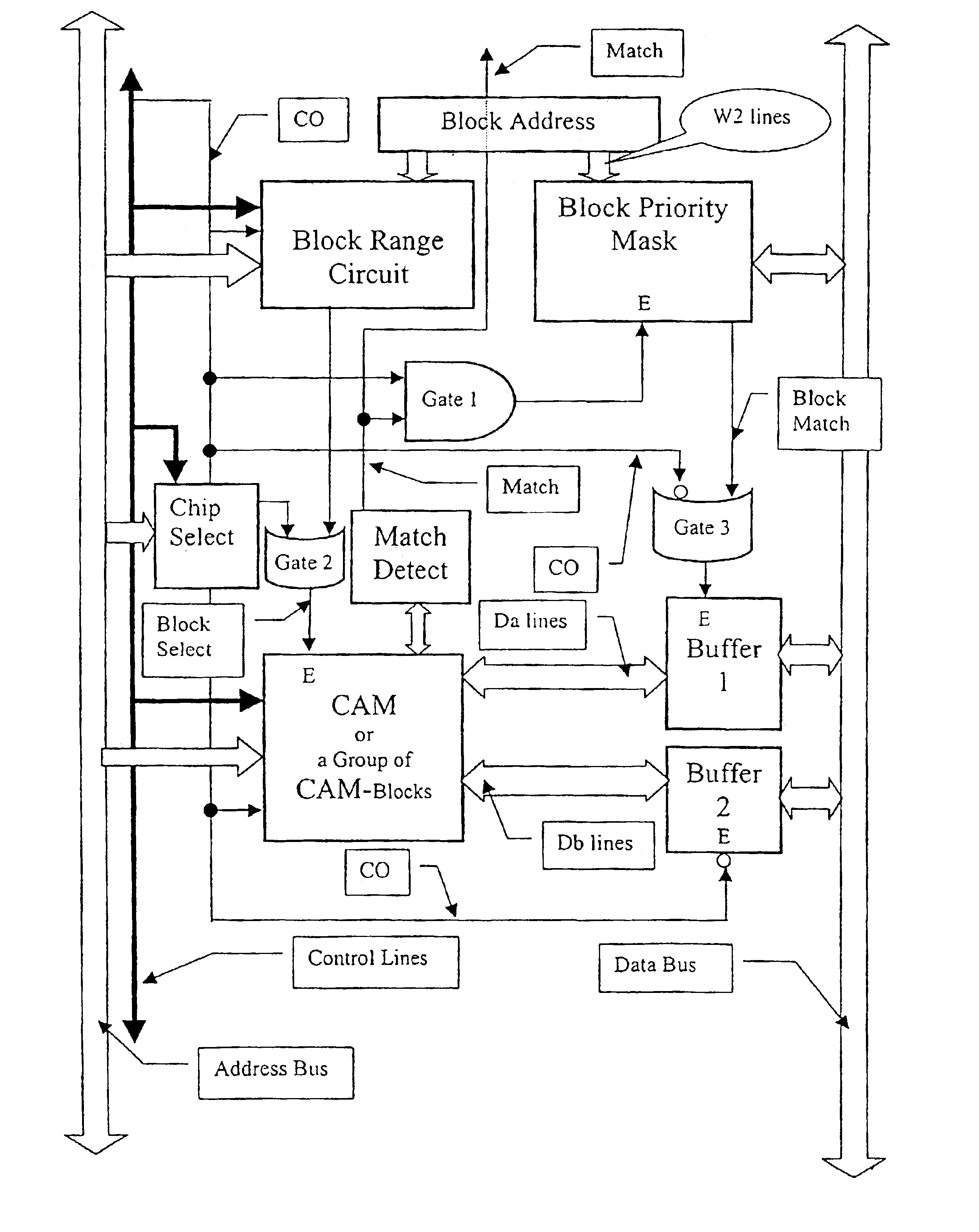
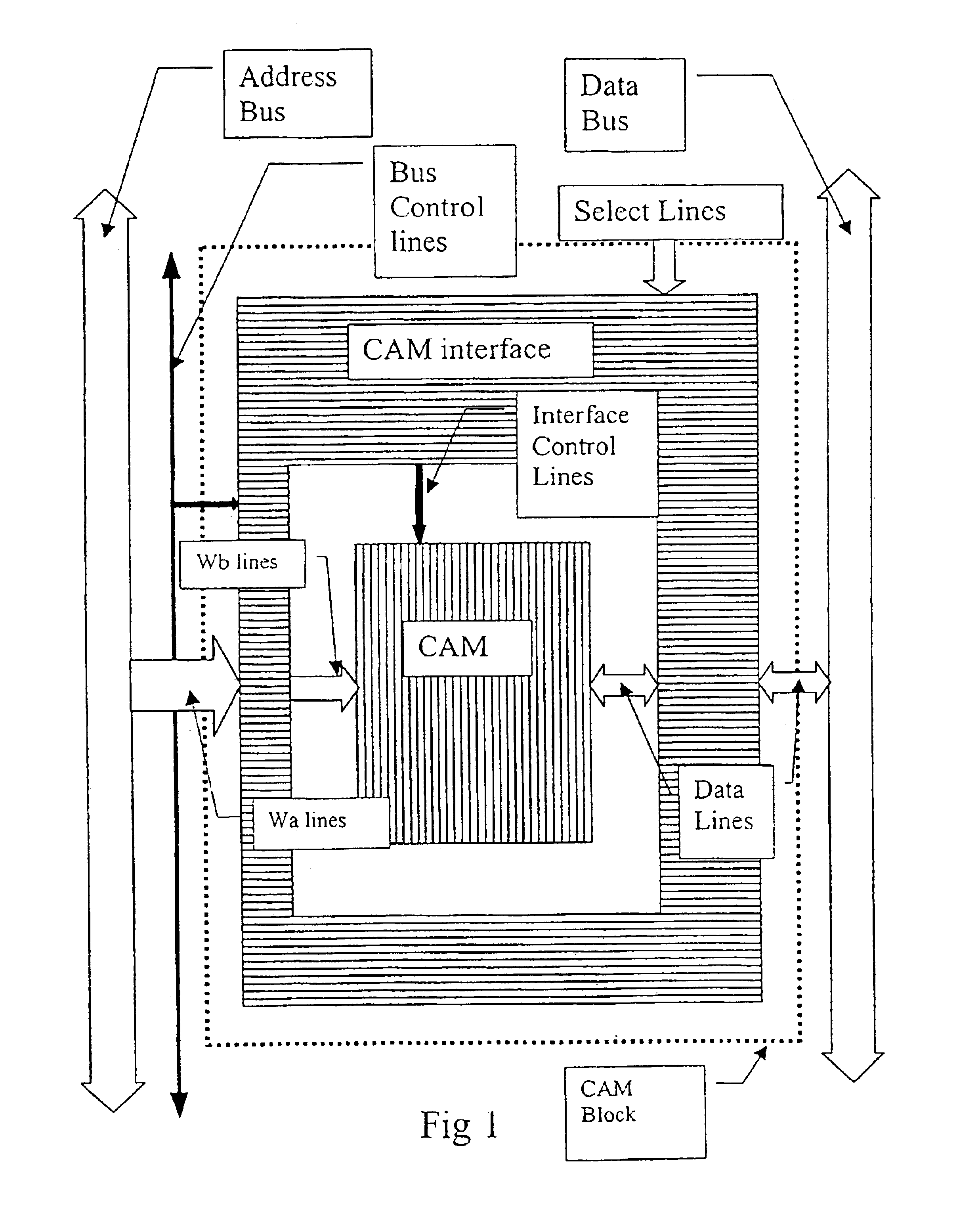
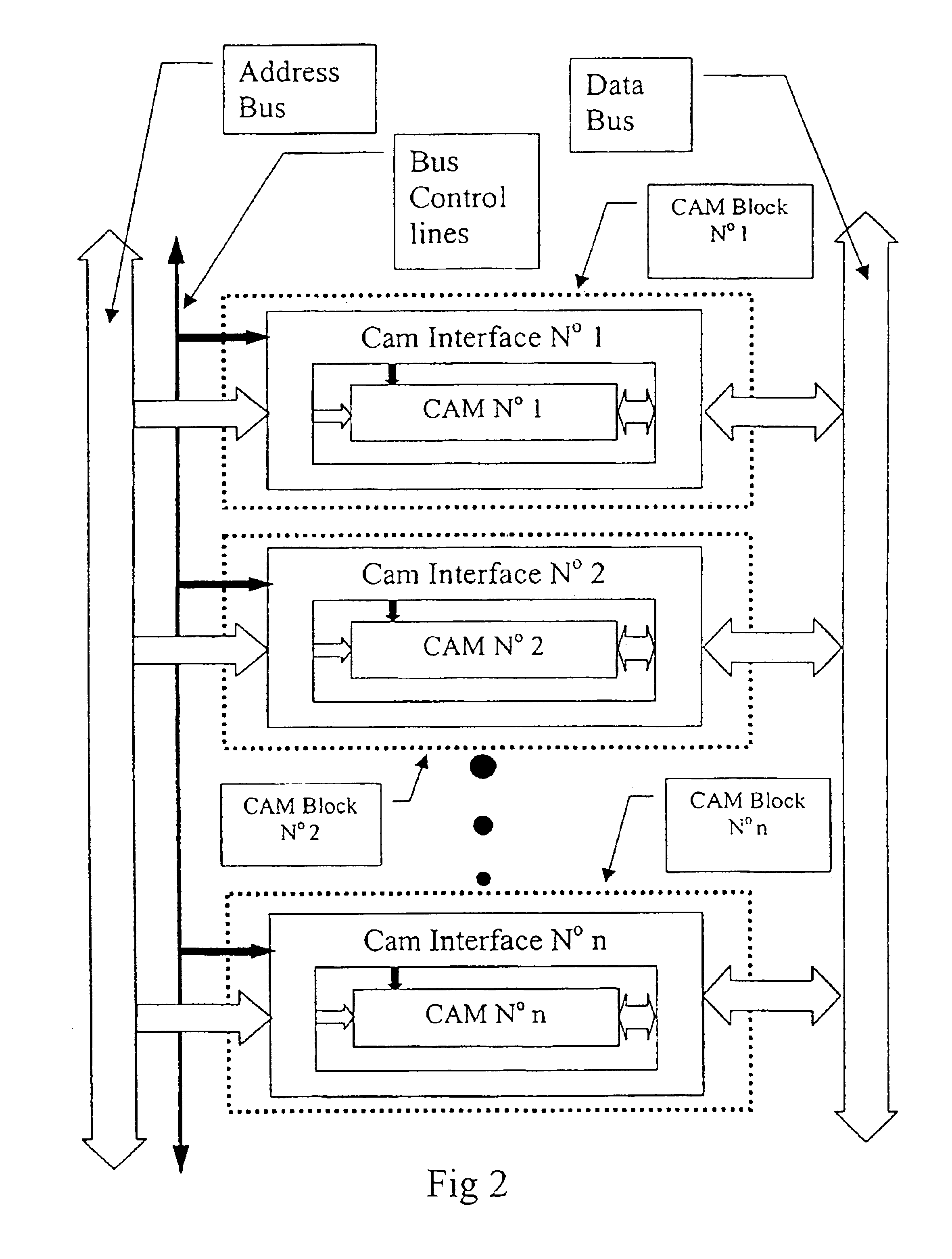
A method and circuit for a high speed interface that enables the integration of several Content Addressable memories into a larger, Combined Content Addressable Memory with only an insignificant delay in the original response time of the individual memories. The interface provides connections to the Bus system only and no connection between different CAM devices of the system is needed, whereby the combination of one CAM and one CAM interface in a single device, such as a chip is enabled. Such chips may be used as modules for increasing the CAM Memory by directly attaching them to the Bus System without any additional interface, as known for standard memory chips such as RAM. The inventive interface may also be used for creating a hierarchical structure within a CAM device by dividing the memory cells in groups, each group being interfaced to the larger combined CAM device via an interface according to the invention. In such a structure the priority function in each group operates on a smaller number of cells and due to the relatively small number of gates necessary for making the interface the implementation of a CAM device with a reduced number of gates is facilitated. In a combined CAM device several CAMs are connected to an Address Bus and to a Data Bus via their respective interfaces. In the Read and Write mode, the interface will connect the two sets of lines and thus be transparent for the Read or Write operation. In the search mode (Content Addressing mode), the Interface will select and set a number of lines of the Data Bus according to the CAM response so as to output the address of one matching cell that is the highest in a predefined direction. The interface circuit adds the logic functions and lines necessary to expand the Content addressable functions of the CAM module to a larger range of addresses, sets an additional number of bus lines in order to write the address of the cell within that larger range and checks that no other cell with a higher address responds throughout the system by masking the bits of the CAM address if they would change the address of a cell with a higher address. In this way the whole ensemble of CAMs is capable of functioning as a single CAM of larger size.
Owner:ROBOGROUP TEK
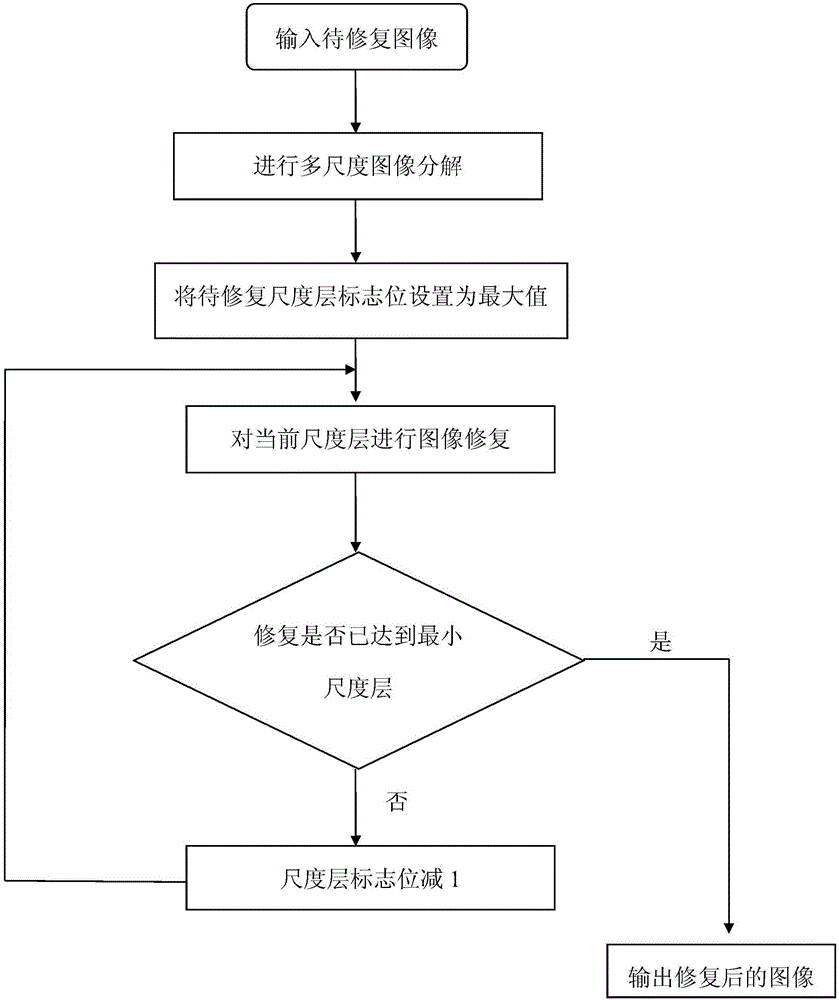
Multi-scale image restoring algorithm based on structure information
The invention discloses a multi-scale image restoring algorithm based on structure information. The multi-scale image restoring algorithm comprises the steps of performing multi-scale decomposition on a to-be-restored image I, and obtaining a series of different scale layer images; from a largest scale layer image, calculating priority of a damaged area of a current k-th scale layer image Ik by means of a priority function calculation method based on the structure information, searching an optimal matching block according to a priority sequence by means of a similarity measuring rule which is composed of corresponding matching rules, performing image restoration of the current k-th scale layer, obtaining a corresponding restoring effect graph and performing up-sampling reconstruction on the restoring effect graph for obtaining a restored comparison reference graph of a (k-1)th scale layer, restoring the image of the (k-1)th scale layer for obtaining a preliminary restoring result in this scale; performing comparison between the preliminarily restoring result in the previous step and the comparison reference graph, and obtaining a new (k-1)-th scale layer damaged image; and obtaining a final restoring effect graph of the (k-1)th scale layer. The multi-scale image restoring algorithm realizes high restoring sequence accuracy, and furthermore realizes more natural and reasonable image structure texture after restoring.
Owner:TIANJIN UNIV
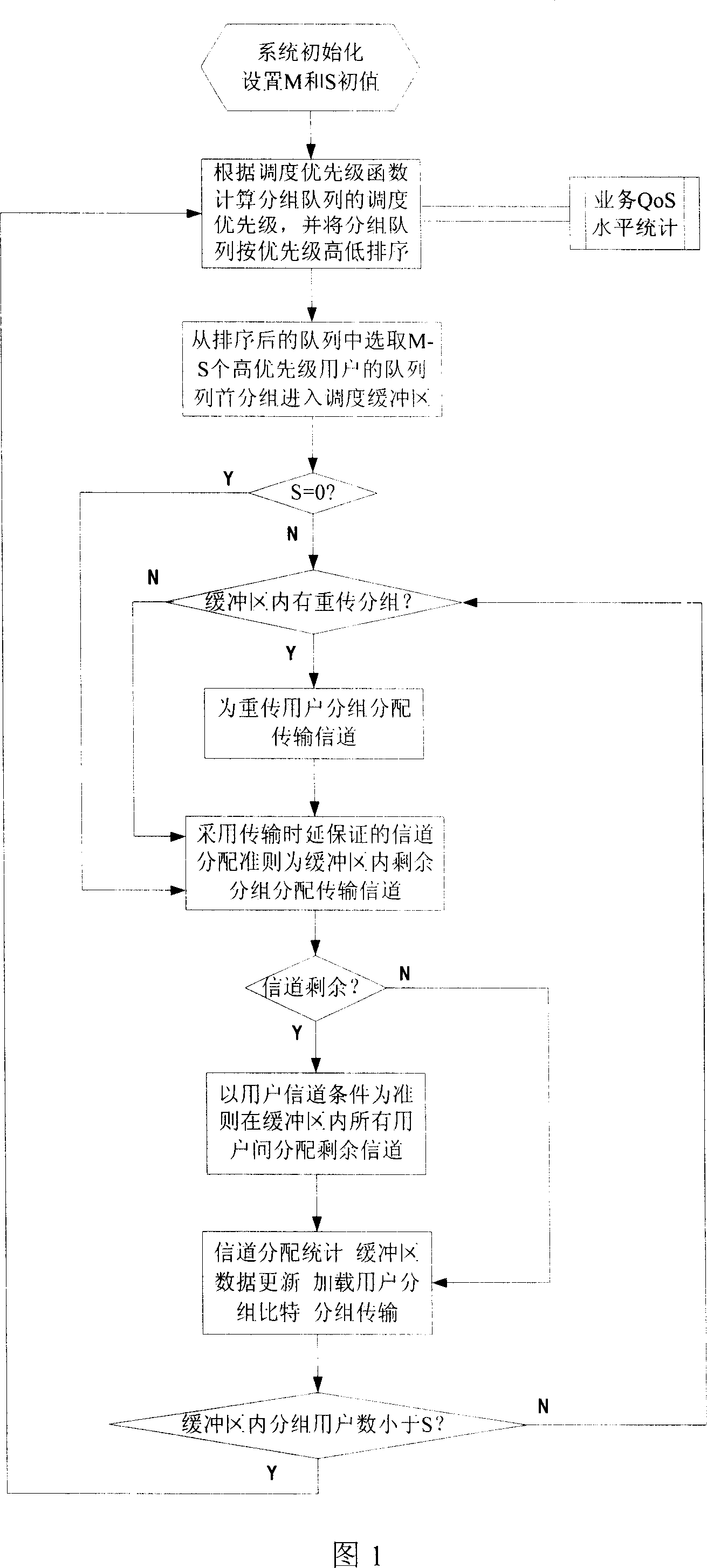
Group dispatching and channel distributing method for HSDPA system
InactiveCN1925460ARealize scheduling needsImprove throughputError preventionRadio/inductive link selection arrangementsDistribution methodMaterial distribution
This invention relates to group and signal channel distribution method of HSDPA system, which belongs to wireless communication field group and materials distribution technique. The system is composed of circle group dispatching process and signal distribution process, wherein, dispatching process designs dispatch priority function according to business QoS demands and business current QoS level for grouping; re-dividing signal channel in distribution process and then adopting transmission to distribute remaining signal channel by use of signal channel and rules.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Criminisi image restoration method based on HSV color space
ActiveCN109493272AGuaranteed certaintyReduce matching errorGeometric image transformationPattern recognitionImaging quality
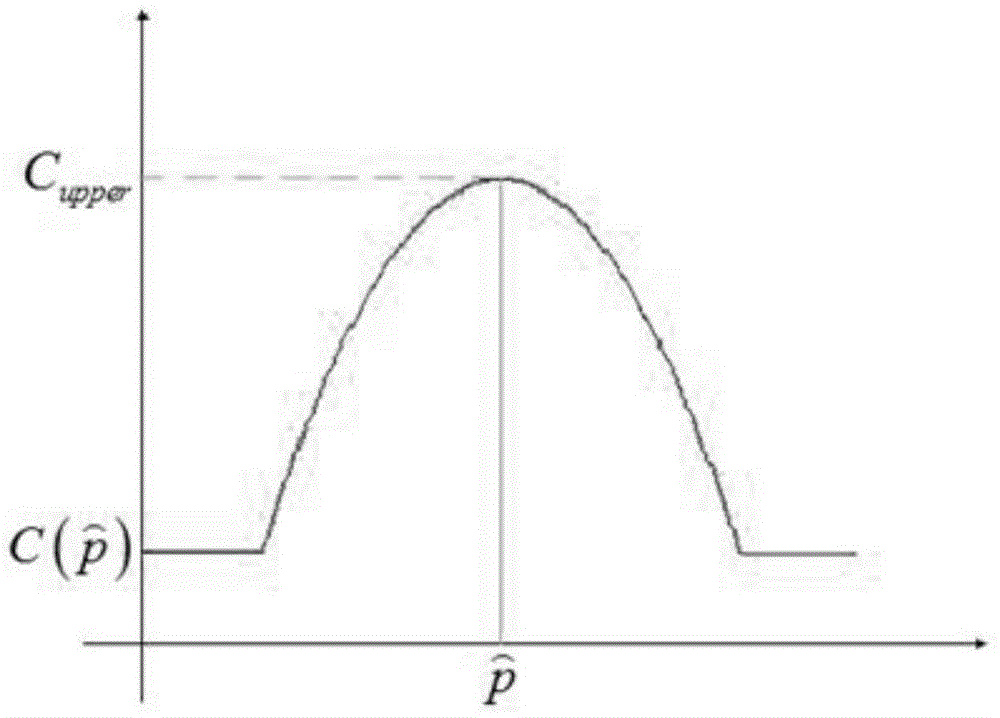
The invention provides a Criminisi image restoration method based on HSV color space, comprising the following steps: 1, judging whether there is an image damaged area to be repaired; 2, taking the pixel point p of the damaged edge, calculating the confidence value C according to the pixel value in the square area of 9*9 centered on the point p, judging the size thereof, and if the confidence value C is great than the threshold value K, calculating the priority value P of the square area block according to the priority function; 3, according to that matching principle, the b matching block inthe undamaged region is searched by comparing the difference value of the hue H and the luminance V in the HSV color space; 4, filling the searched best matching block into the pixel block to be repaired, and making the central pixel points coincide; 5, updating that boundary information of the repair area, and simultaneously updating the confidence value of pixel point of the repair completed area; 6, repeating that above steps until all pixel block are repaired. The invention makes up for the defects of inaccuracy of priority function in Criminisi restoration algorithm and degradation of image quality after restoration, and has excellent performance.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
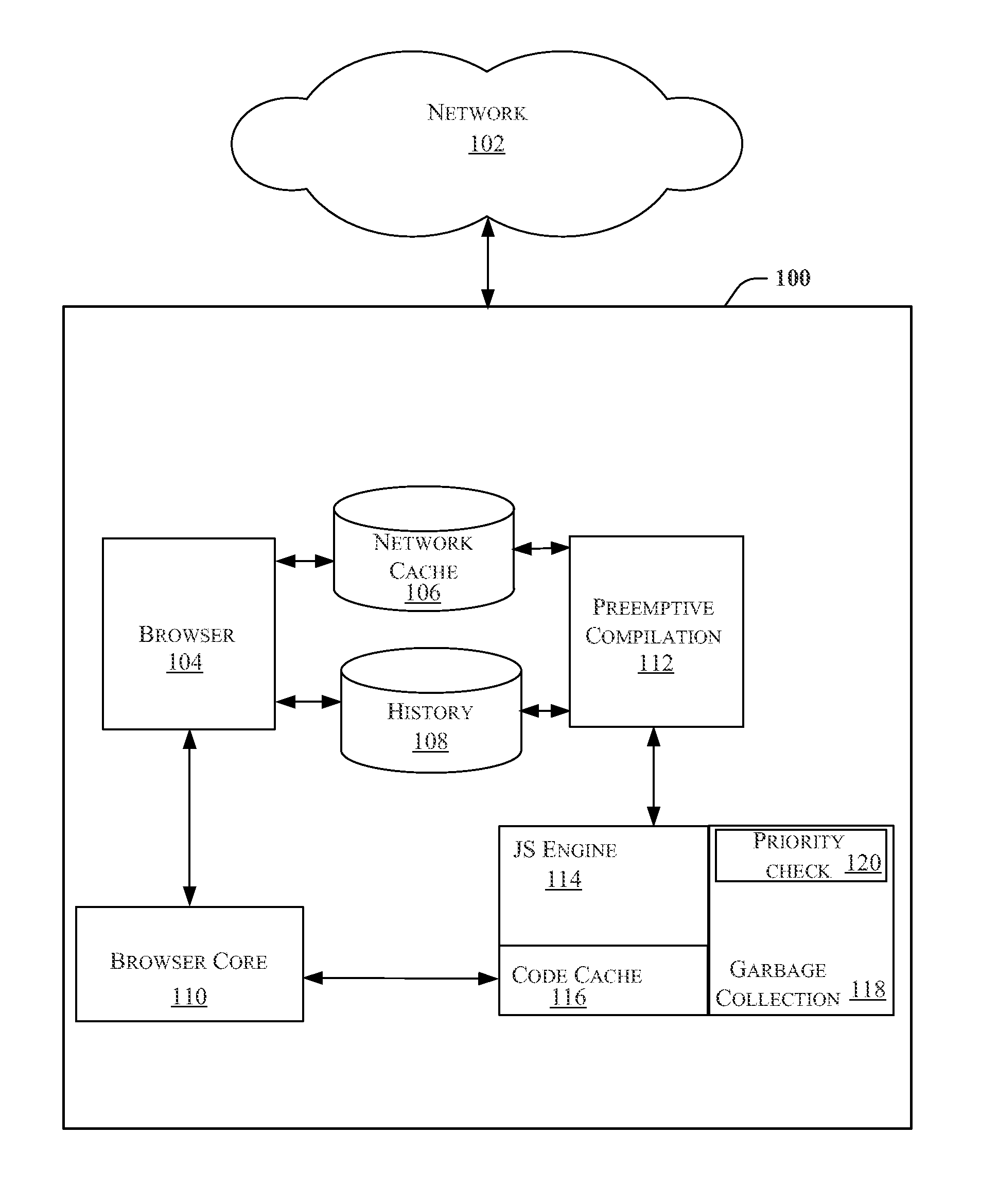
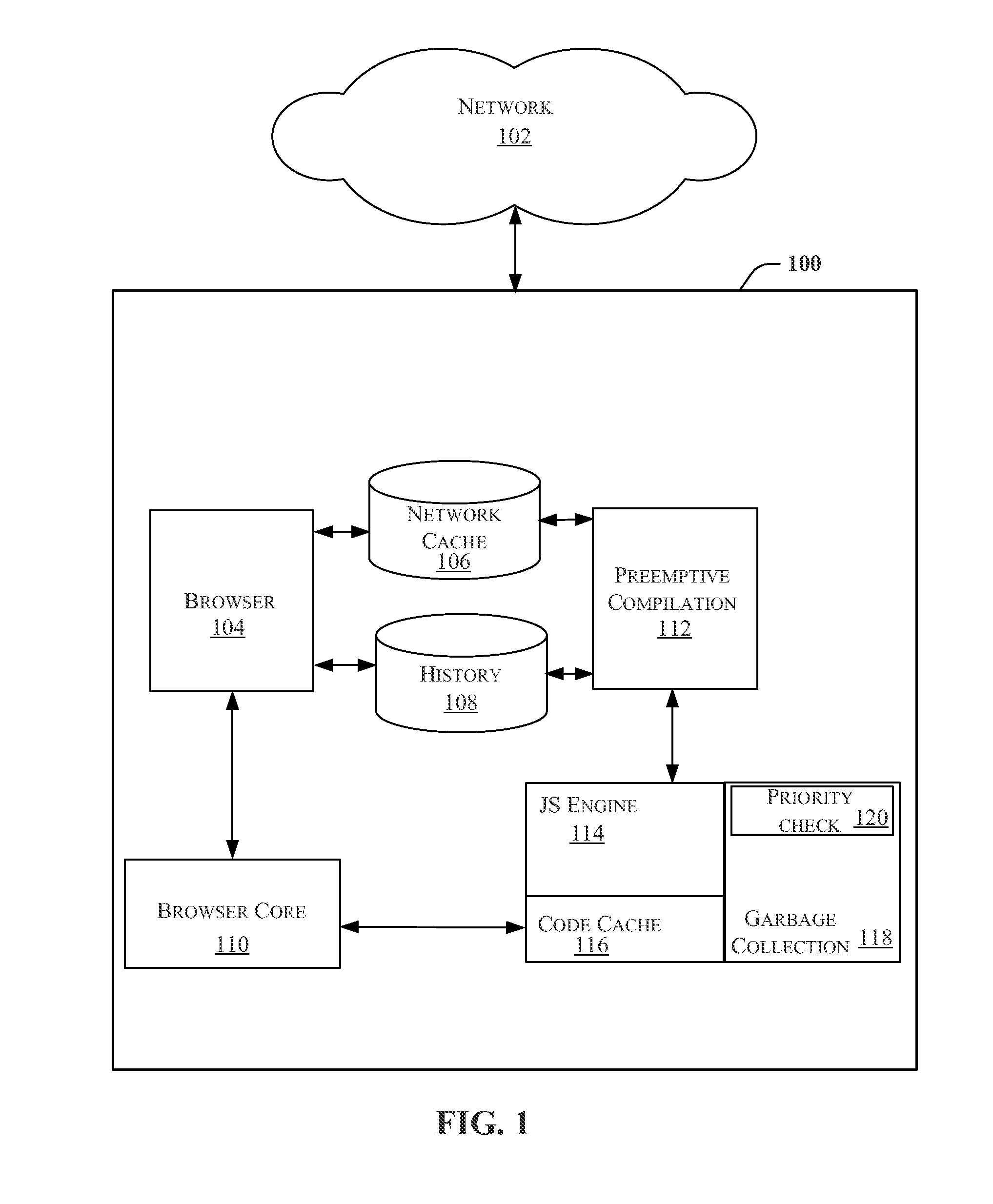
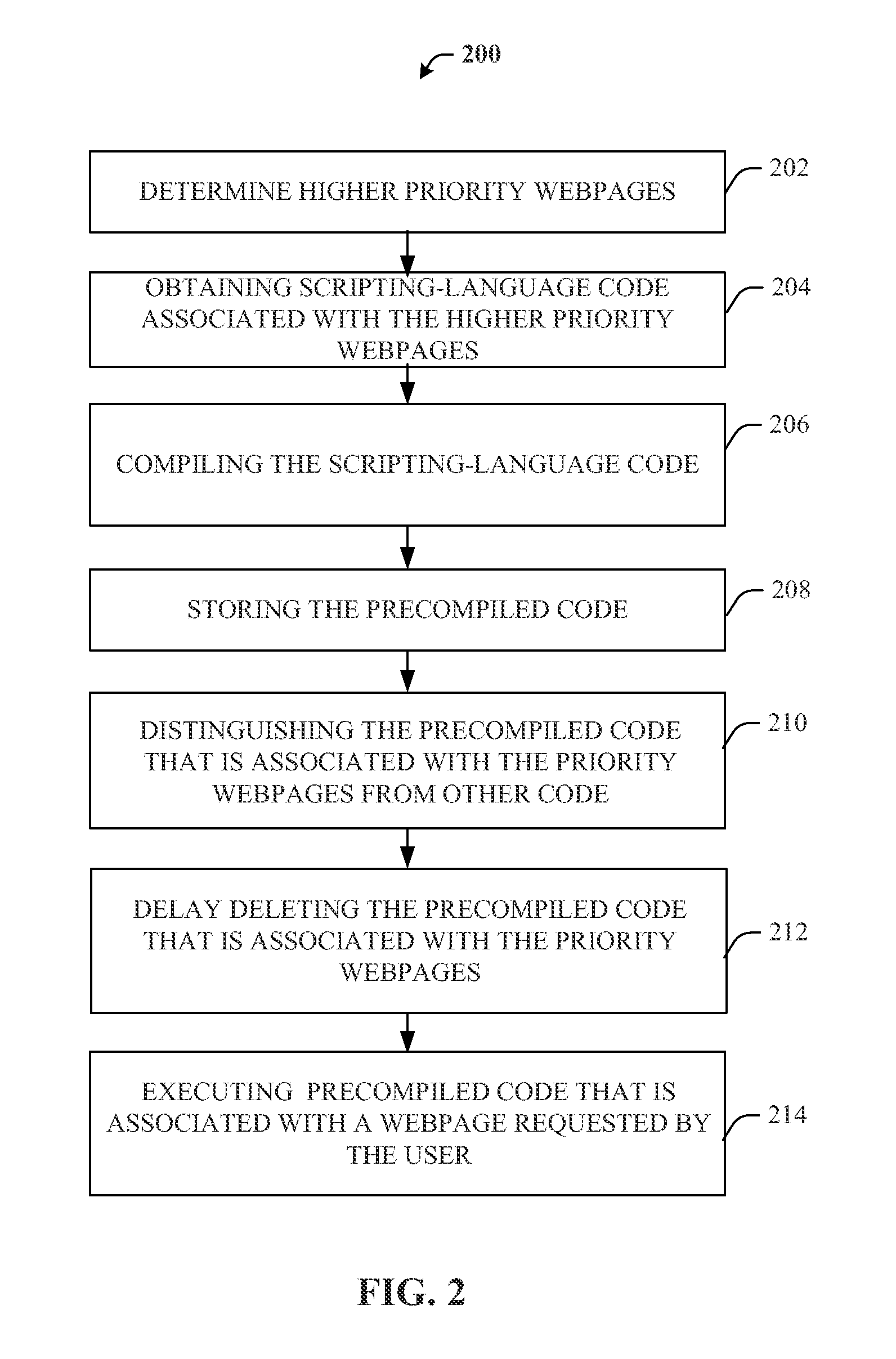
Methods and apparatus for improved browsing performance by precompilation of high-priority JavaScripts in a webpage and delaying the removal of corresponding compiled code
ActiveUS8880991B2Memory adressing/allocation/relocationSpecial data processing applicationsScripting languageParallel computing
Methods and apparatus for processing scripting-language code in webpages are disclosed. The method includes obtaining scripting-language code that is utilized by a higher-priority webpage, compiling the scripting-language code to generate higher-priority compiled code objects, storing the higher-priority compiled code objects on a communication device, distinguishing the higher-priority compiled code objects from other compiled code objects that are stored on the communication device to delay the higher-priority compiled code objects from being removed from the communication device, and executing the higher-priority compiled code objects when the webpage is requested by the user. In many variations, this approach is not applied to all webpages visited, but only on certain webpages and scripts that are considered high priority, either implicitly or explicitly, based on a priority function that computes a multi-level priority from the history and past browser activity.
Owner:QUALCOMM INNOVATION CENT
Improved Criminisi image restoration method with self-adaptive gradient block division and equilong transformation
ActiveCN105678712AReduce misjudgmentReduced cost when matching searchesImage enhancementTime complexityImage restoration
The invention provides an improved Criminisi image restoration method with self-adaptive gradient block division and equilong transformation. The method is characterized by, to begin with, marking known and restoration regions of an image to be restored, calculating a gradient histogram for all pixel points in the known region, and dividing the pixel points in the known region into smooth, texture and edge three types of pixels; then, enhancing discrimination capability for an edge texture portion through a block-classification improved priority function to solve the problem of texture extension caused by a conventional method; next, judging the block type of blocks to be restored by judging known gradient information in the block to be restored, and establishing a self-adaptive block size function to ensure that different types of blocks to be restored are restored by different sizes of blocks respectively, and carrying out matching only in the corresponding types to improve matching efficiency; and finally, introducing the equilong transformation to improve matching precision. Compared with the existing method, the method well overcomes the problems of texture extension and high time complexity and the like, and the restoration quality is improved.
Owner:SHAANXI NORMAL UNIV
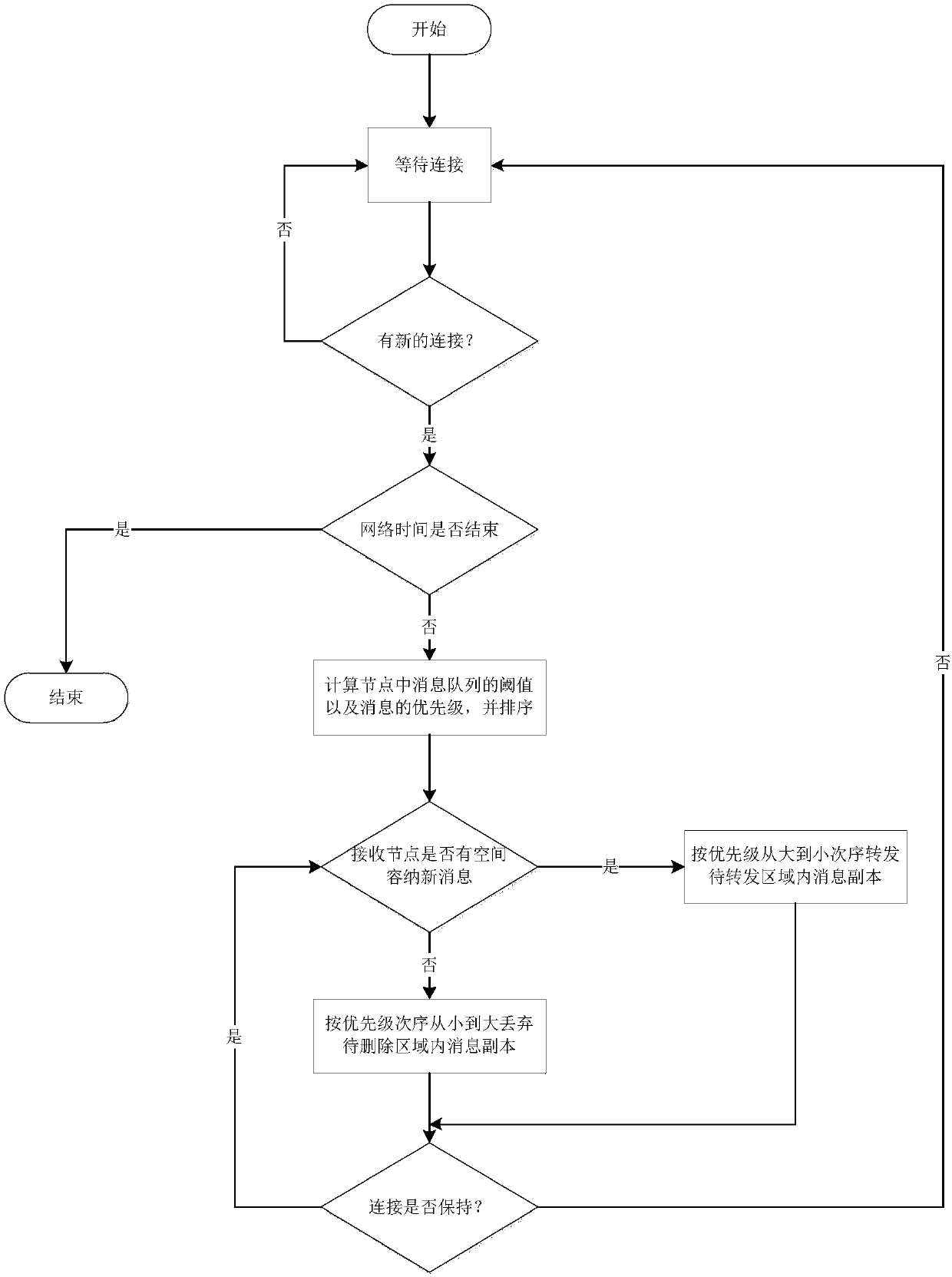
Priority-based cache management method in opportunity network
InactiveCN108449270AGood for forwardingOptimizing the Discard PolicyData switching networksWireless communicationDelayed timeData transmission
Owner:CENT SOUTH UNIV
Resource distribution method in WiMax system
InactiveCN101951683AEnsure fair distributionUnrestricted combinationEnergy efficient ICTWireless communicationResource blockGreedy algorithm
The invention relates to a resource distribution method in a WiMax system. In the method, the hypothesis is that each connected grouping reaches a base station in the mode of Poisson distribution, and each connection only belongs to one service type of five services of UGS, rtPS, ertPS, nrtPS and BE; and the grouping from the same connection is stored in one buffer zone to arrange in one queue; among the queues, a dispatcher in a base station end dispatches the grouping and distributes a subchannel according to a dispatching priority factor. The method specifically comprises the following steps: firstly, a base station end is divided into different resource blocks, and an equipment end feeds back channel information according to a dividing result; secondly, the dispatcher of the base station end calculates the value of the dispatching utility function of different service types; thirdly, the dispatcher dispatches in an MAC layer according to the obtained dispatching priority function;and finally, a power distribution module in the base station end distributes power on a corresponding subcarrier by a Greedy algorithm according to the result of the dispatcher so as to finish the resource distribution of all services in the WiMax system.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com