Patents
Literature
79 results about "Container Object" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
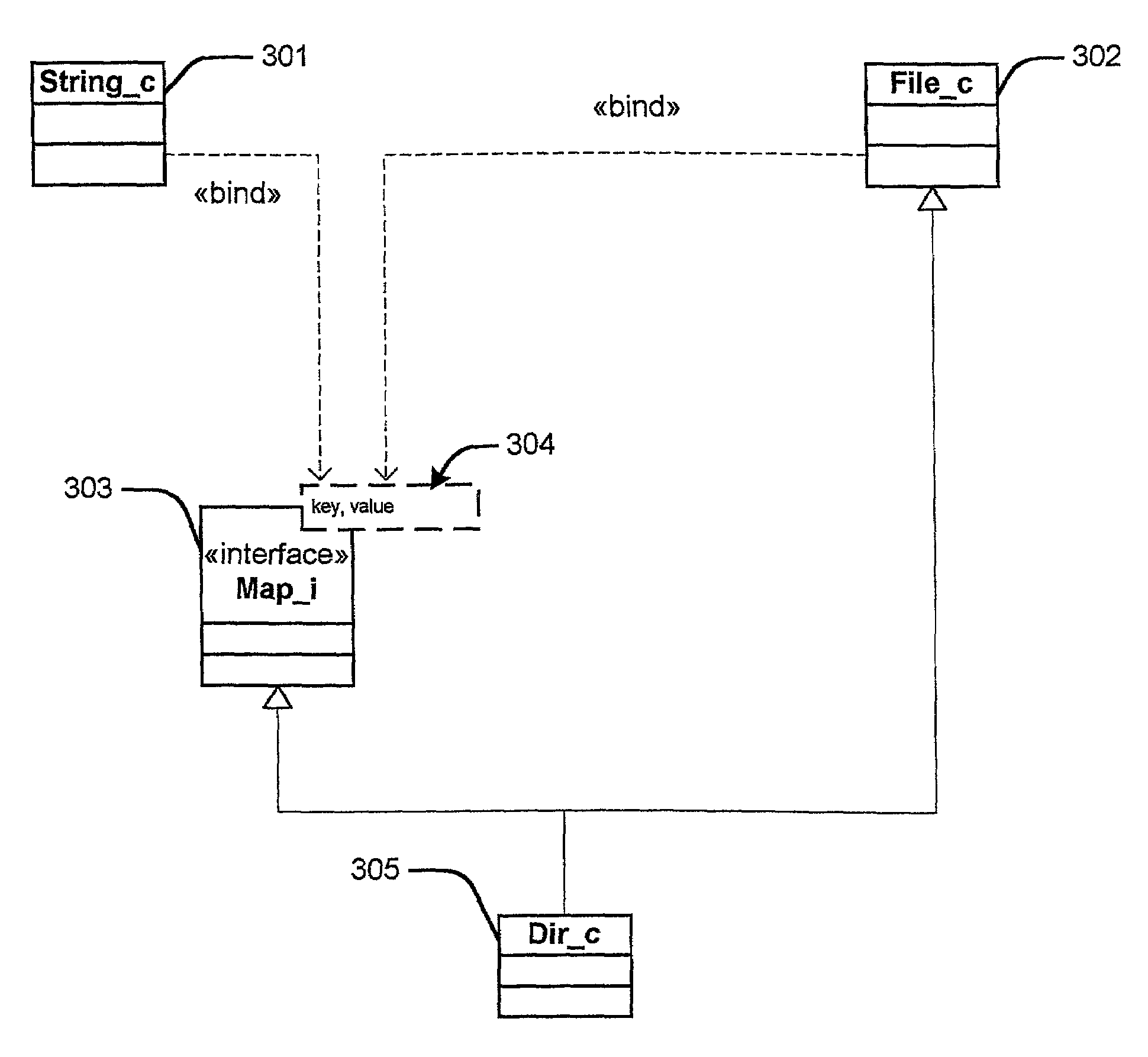
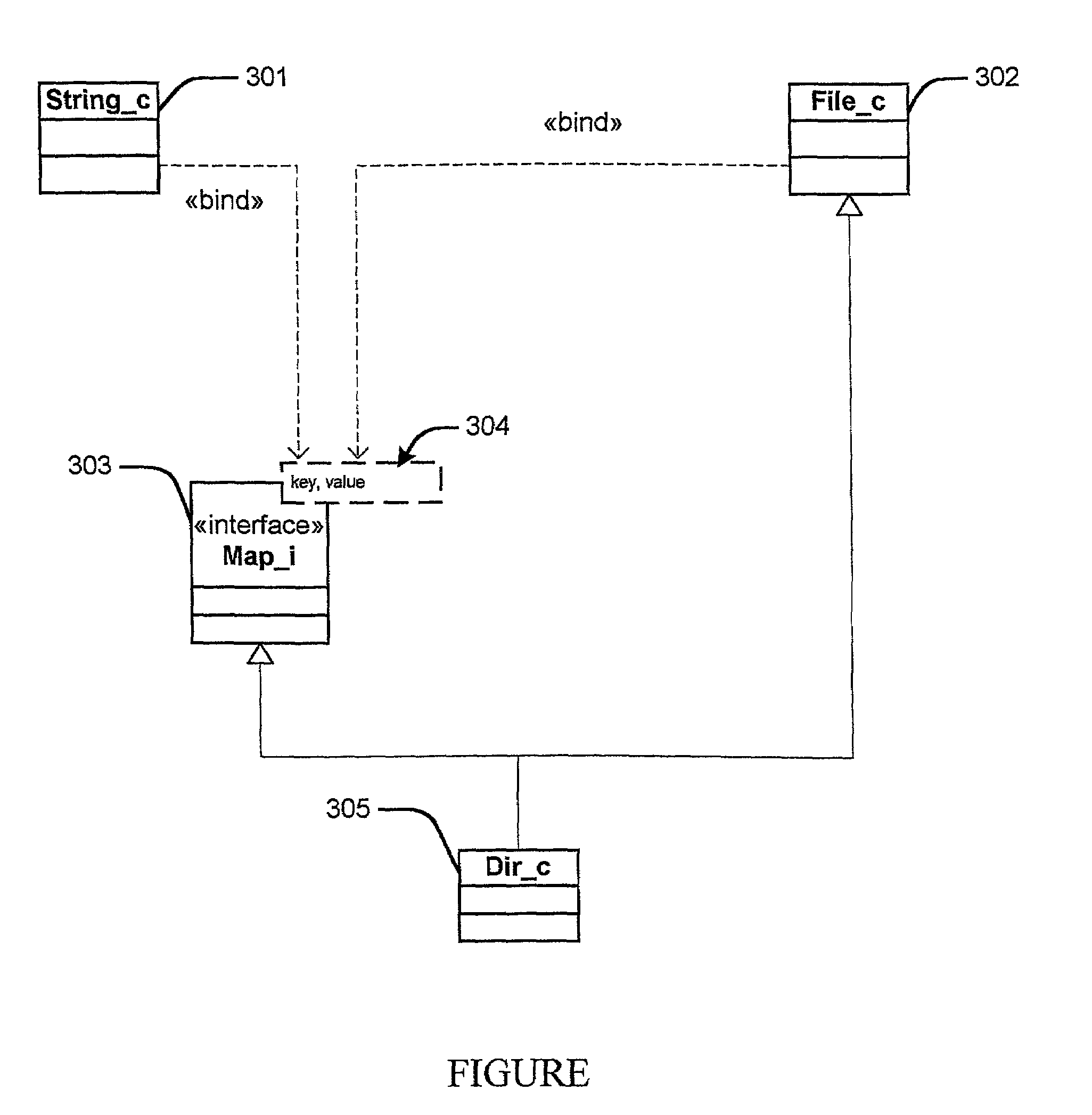
An object that holds the values or locations of other objects.
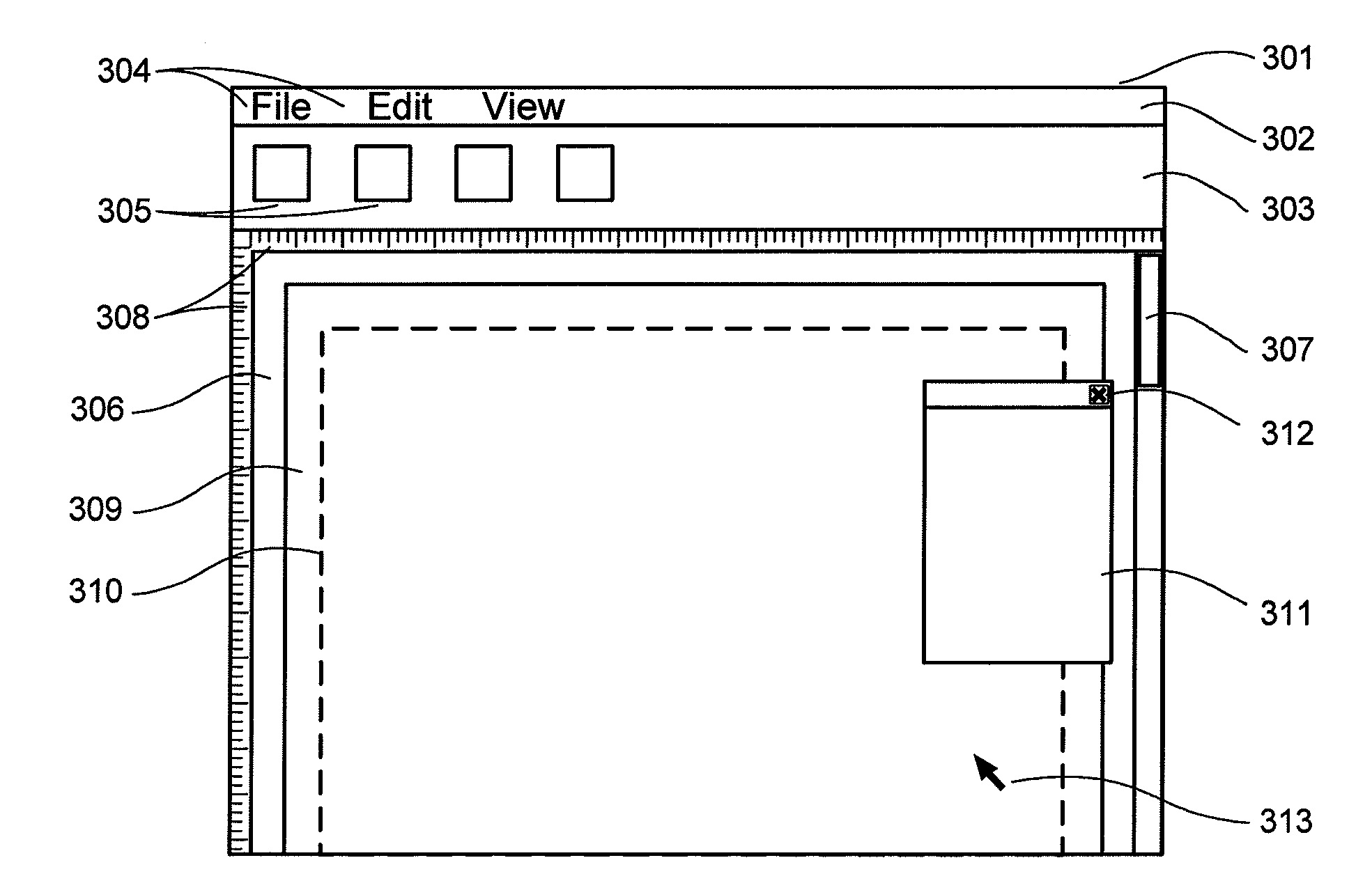
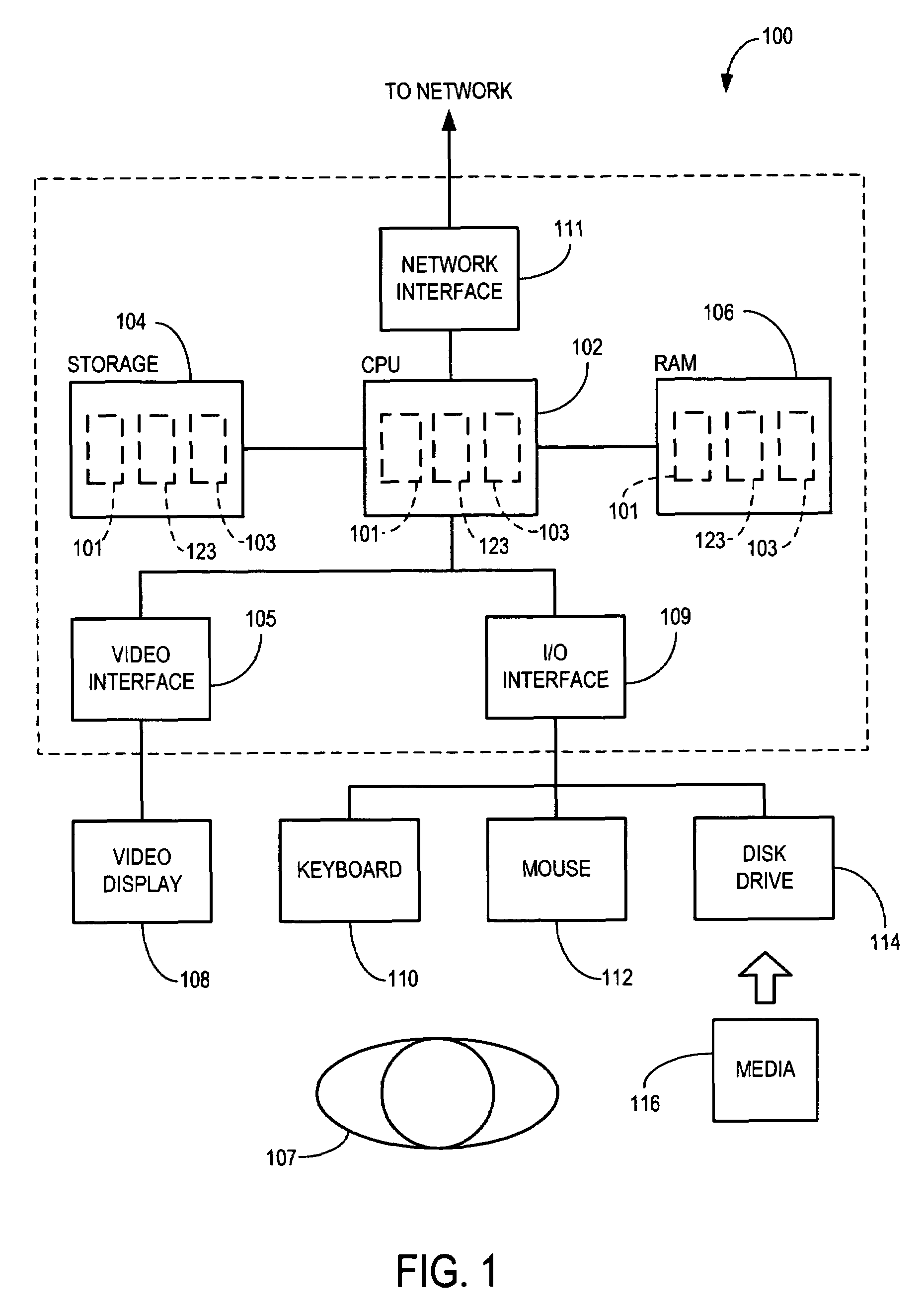
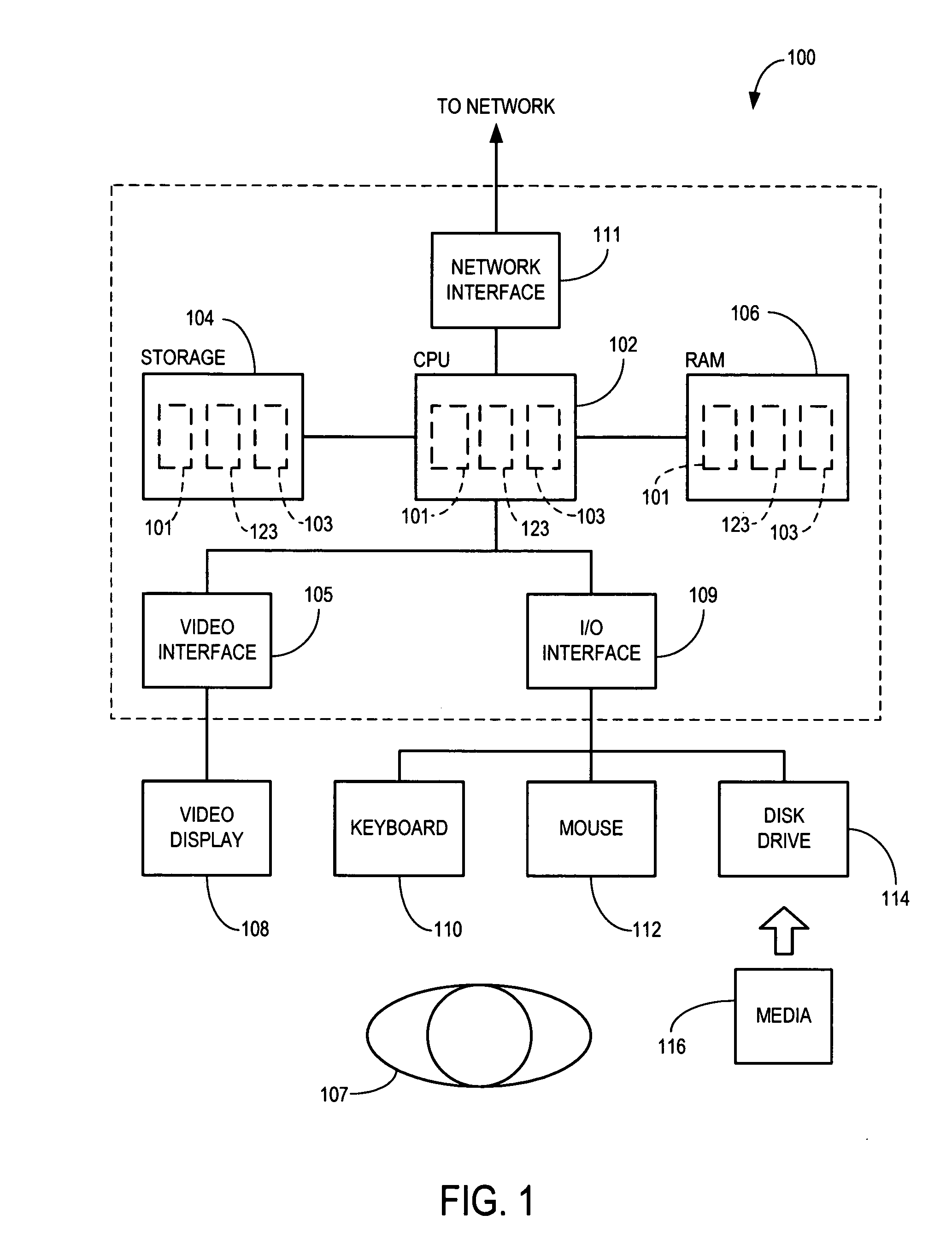
Document layout method
InactiveUS20090307583A1Natural language data processingOther printing apparatusGraphicsGraphical user interface
Methods and apparatus for variable document printing are disclosed in which a graphical user interface is configured to allow user manipulation of layout rules associated with content containers within a template for variable document generation. One method involves laying out (626) container objects (407, 408) forming part of a template (624) intended for a variable data document. The objects each have a rectangular boundary in two-dimensional space, and the method comprises detecting an operation (628, 2800) to modify a position of at least one edge of at least one of the objects. Then, rules of association between edges of the objects having a corresponding orientation to the one edge are identified. A position of at least the one edge is then modified whilst observing the rules of association between all the correspondingly oriented edges. Finally an objective function derived from the rules of association between the correspondingly oriented edges is minimized (3009) to thereby balance a layout of the objects in at least the dimension of modification. Other methods involve maintaining the objective function for a group of edges, the addition and removal of constraints in respect of correspondingly oriented edges, the removal, addition and then removal of constraints in modifying the width of a container, the calculation of text container sizes, and the creation of tables, particularly for text containers.
Owner:CANON KK
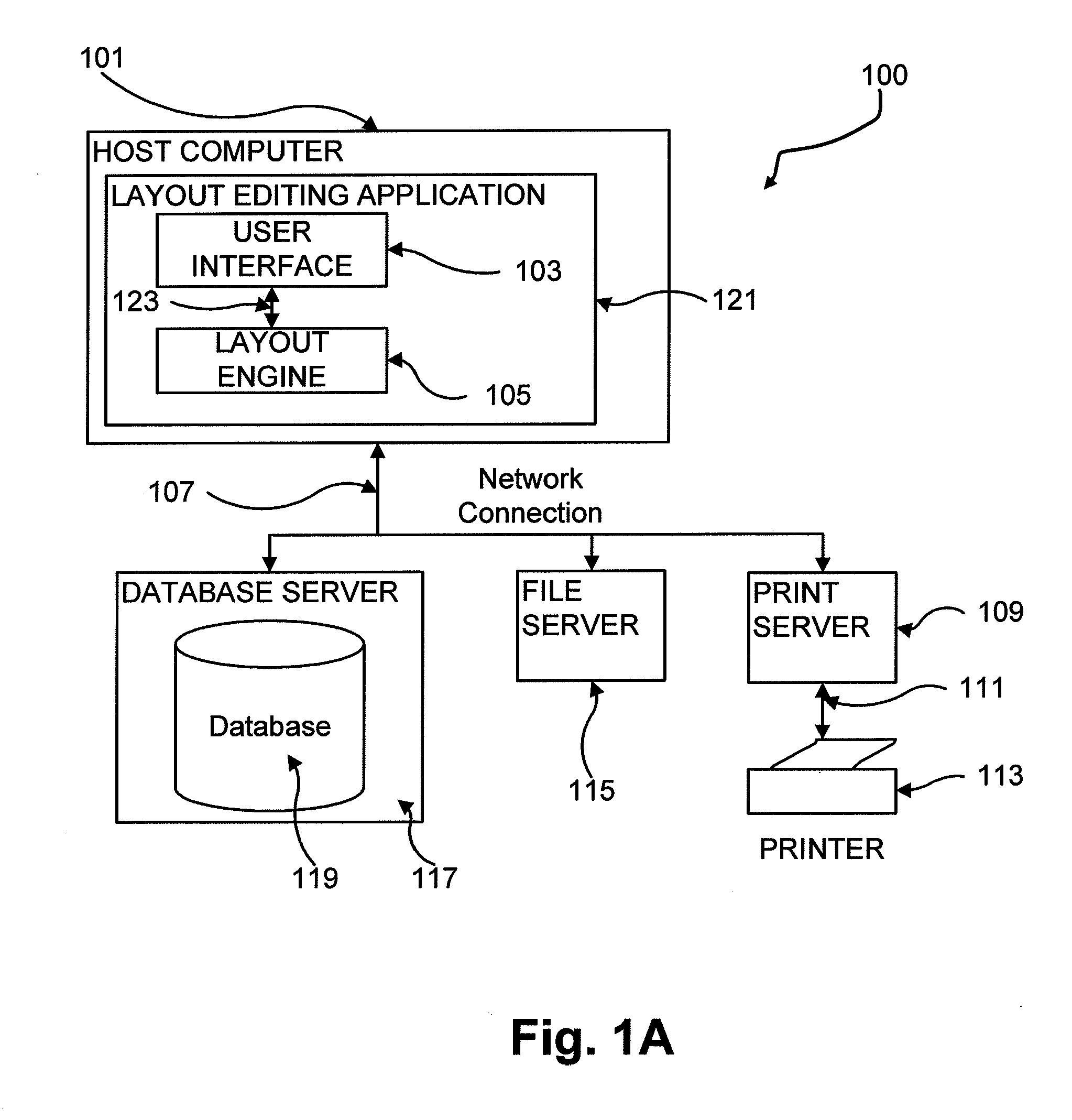
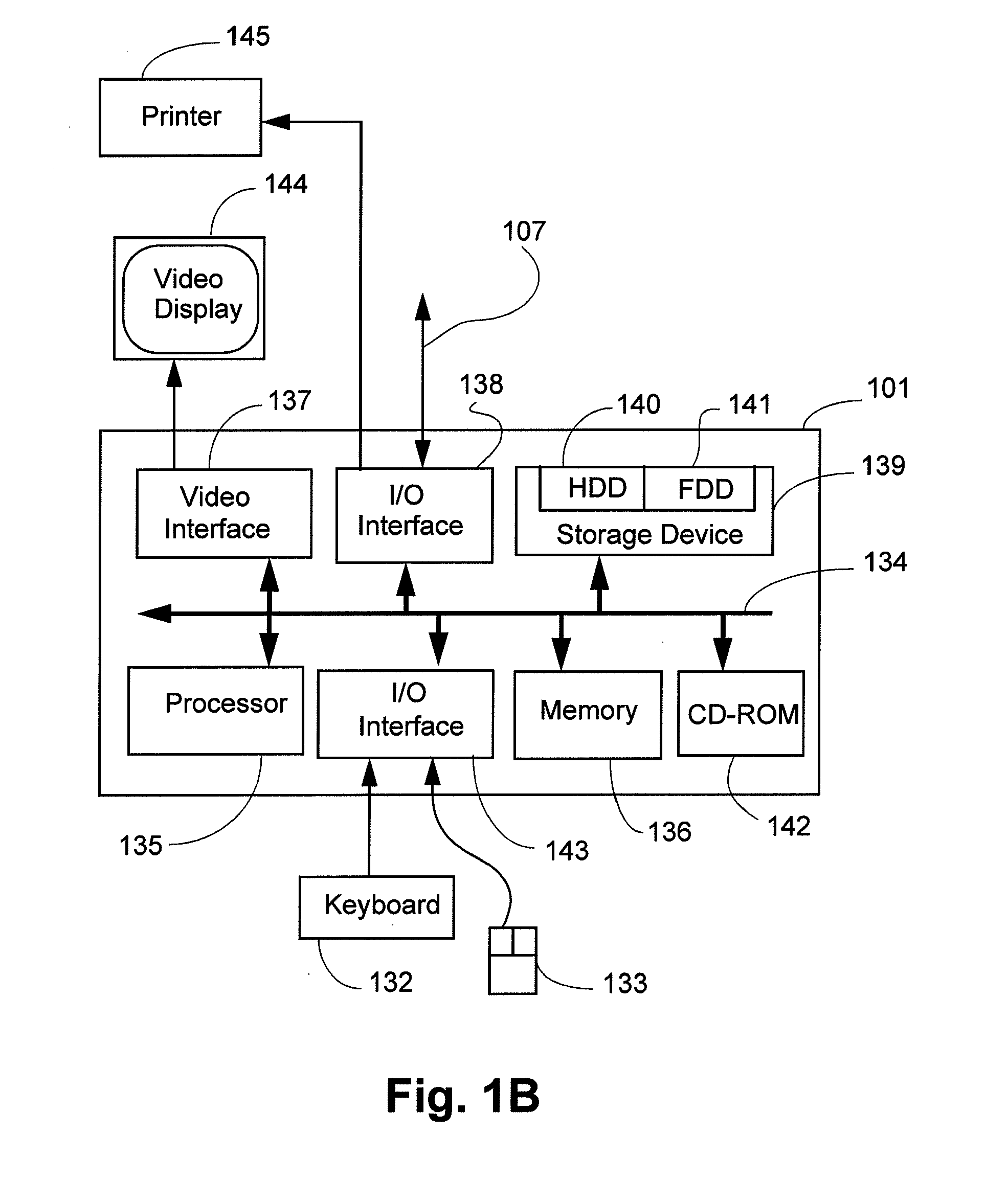
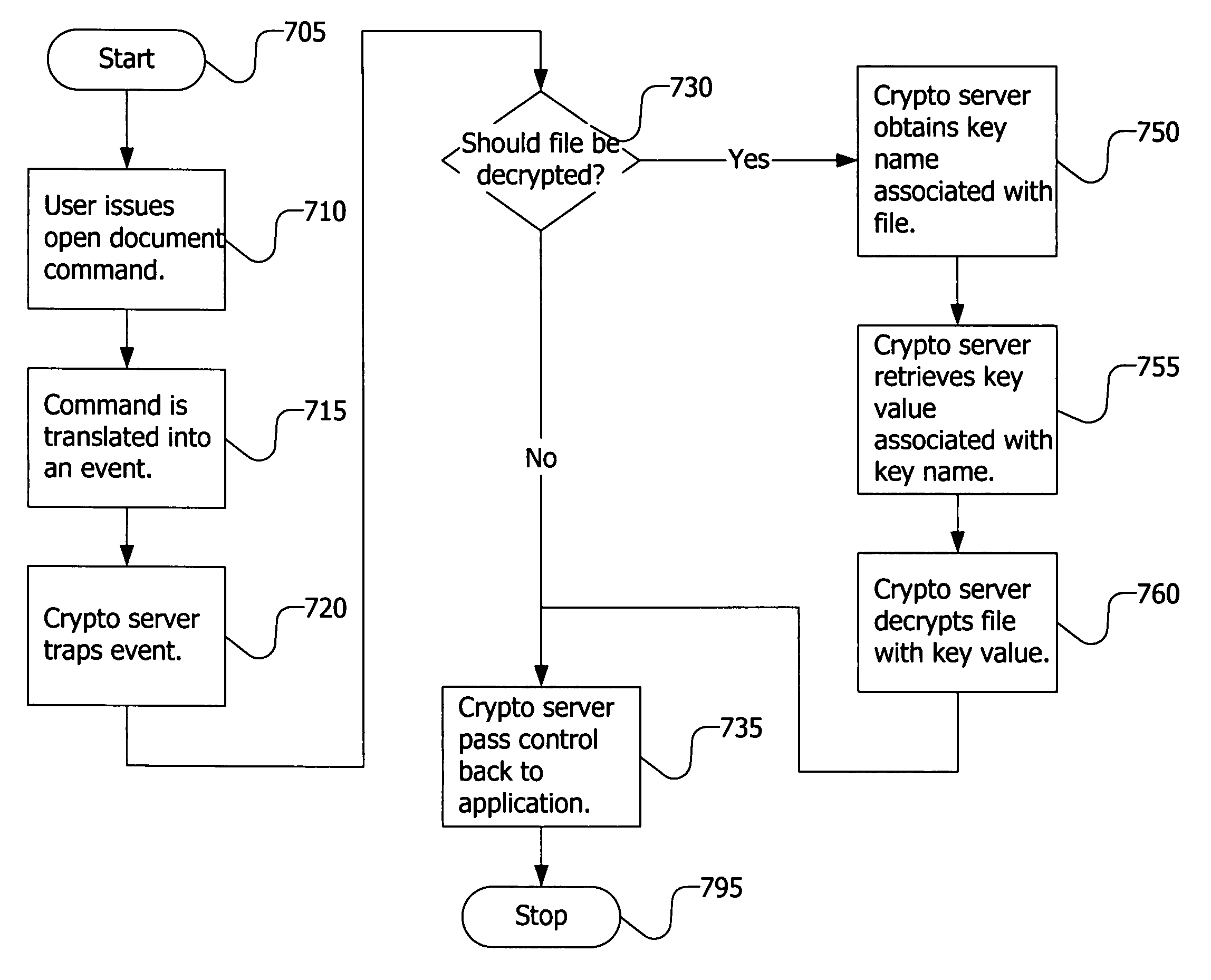
Transparent encryption and decryption with algorithm independent cryptographic engine that allows for containerization of encrypted files
InactiveUS6981141B1Digital data processing detailsInternal/peripheral component protectionComputer hardwareContainerization
An encryption method that is largely transparent to a user is accomplished by intercepting a change document or open document command, carrying out an encryption or decryption process, and then completing the command on an encrypted or decrypted file. The encryption method can be used in a wide variety of environments, such as an individual computer program, a database or electronic messaging over the Internet. The encryption method can select from a plurality of encryption algorithms. The encryption method can also allow just a portion of a document to be encrypted, placed in a container, and then be represented by an object linking and embedding (“OLE”) container object or other representation supported by the file.
Owner:RPX CORP
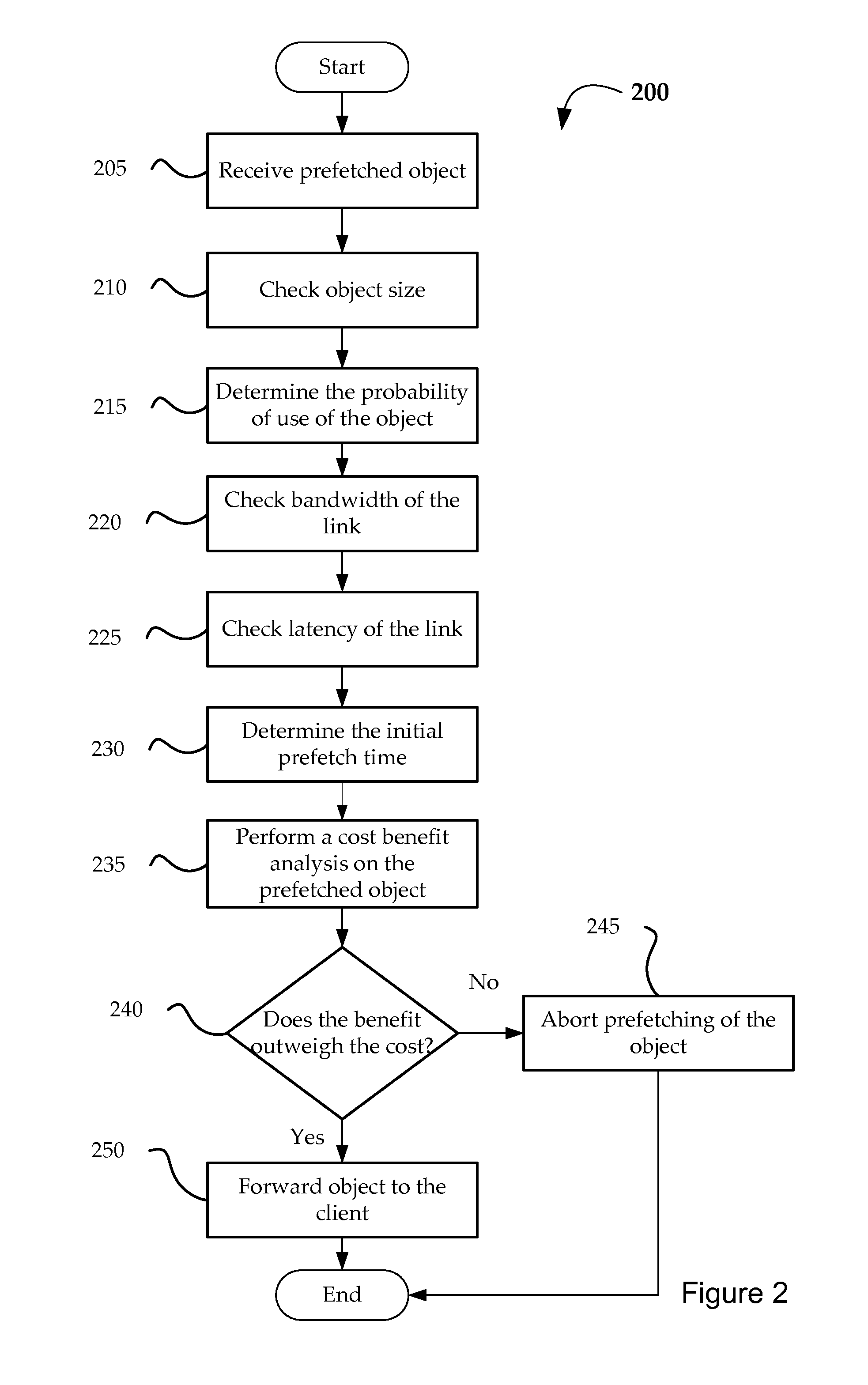
Selective prefetch scanning
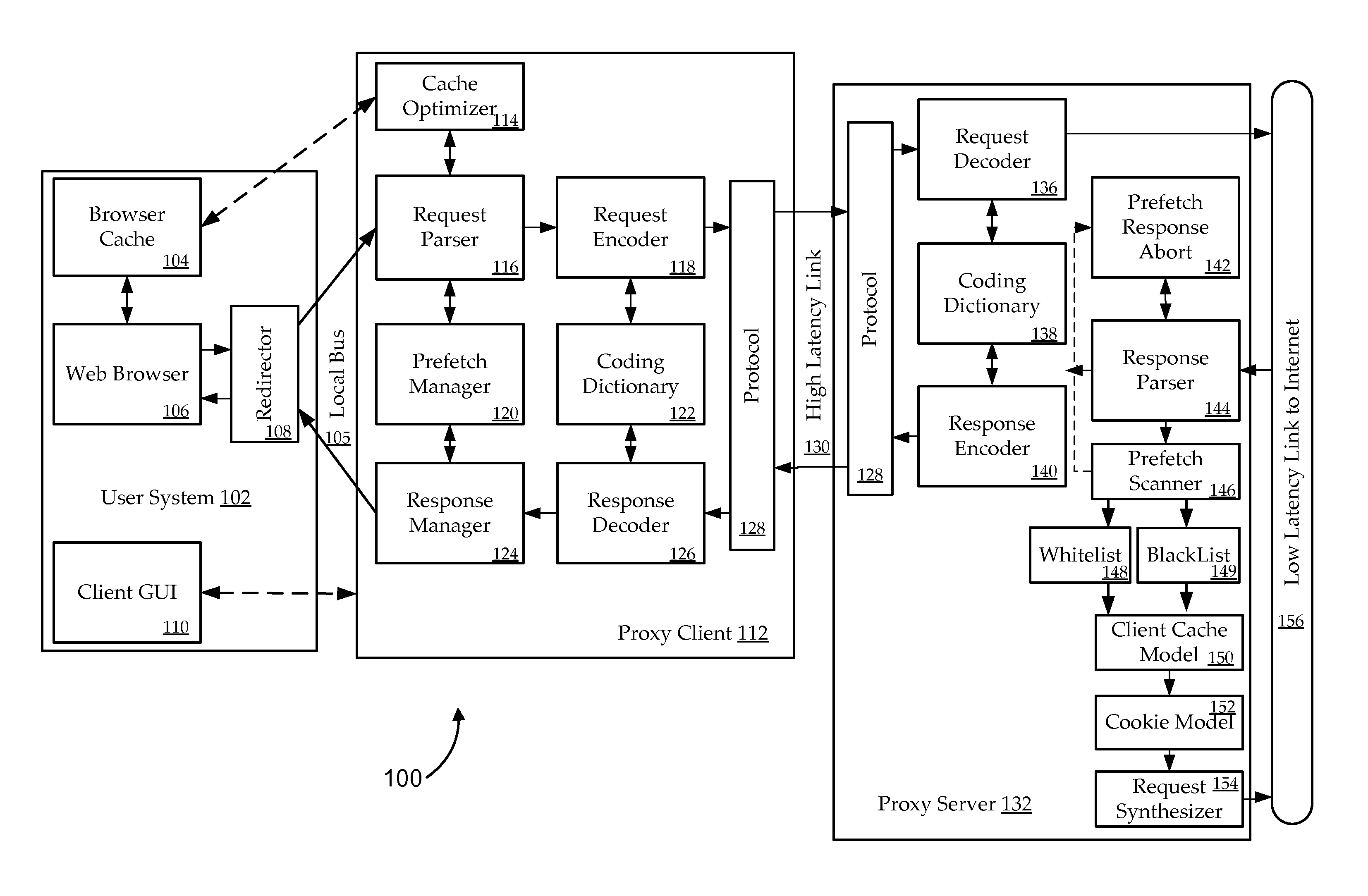
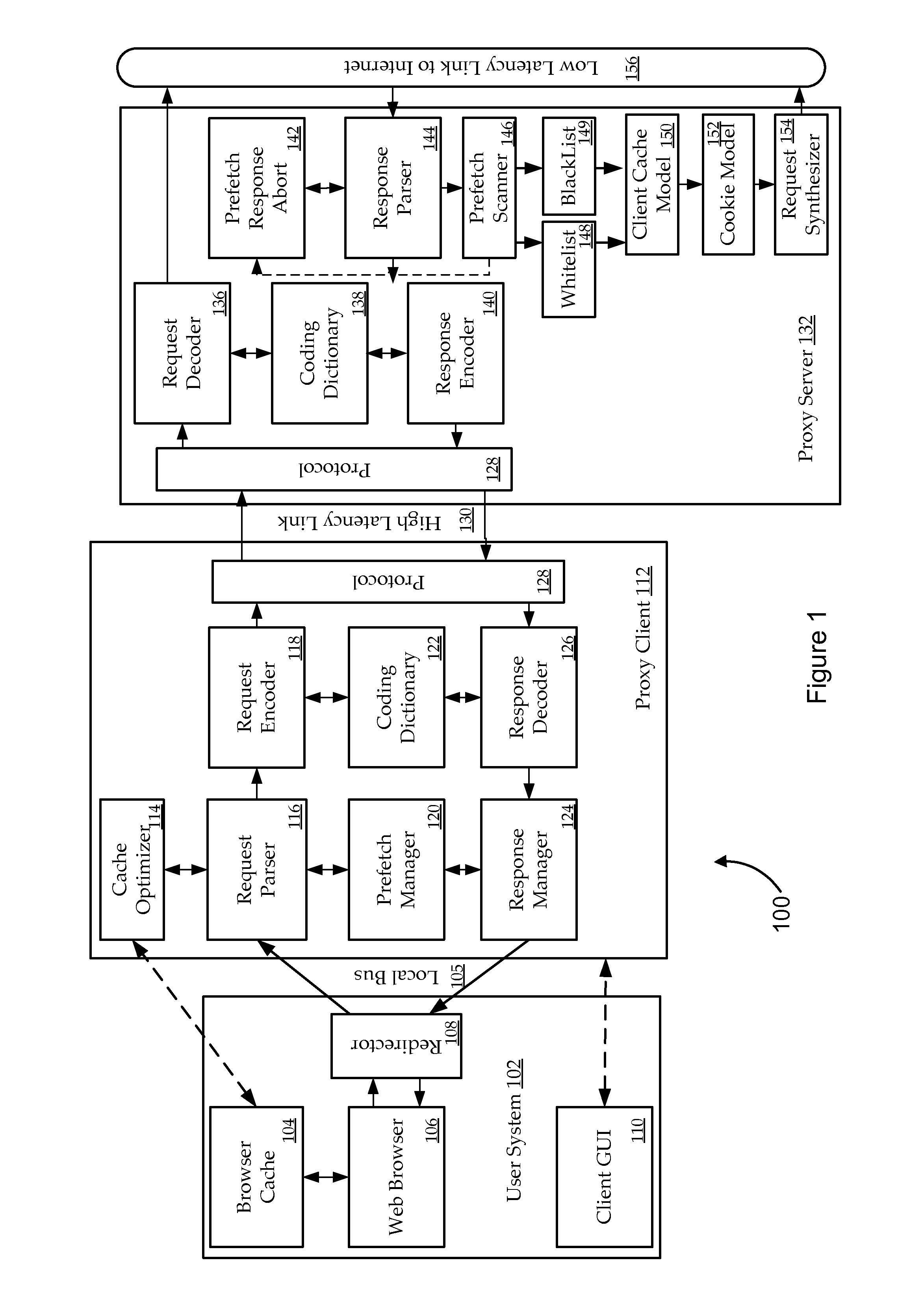
ActiveUS8984048B1Waste of resourceIncrease probabilityWeb data indexingMultiple digital computer combinationsContainer ObjectUniform resource locator
The present invention relates to systems, apparatus, and methods of enhancing prefecher functionality by scanning responses object requests. In certain embodiments, prefetching is improved by identifying references to container objects or sections of container objects at a proxy server. When URLs are identified as part of a container object, a prefetching determination or adjustment to a prefetching decision is made according to the identification of the reference for a subset of URLs identified by the reference to the container object. For example, prefetching of URLs located in cascading style sheet (CSS) files may be restricted to a subset of URLs which are identified by a CSS rule.
Owner:VIASAT INC
Opacity desktop with depth perception
ActiveUS7043701B2Improve depth perceptionDepth variableProgram controlSpecial data processing applicationsContainer ObjectComputer graphics (images)
A method of displaying information within a three-dimensional workspace on a computer display includes partitioning the workspace into a plurality of layers, where each layer corresponds to a display depth relative to a user. At least one substantially opaque container object is displayed at a first display depth. The user is provided with a pointer operative to select objects within the three-dimensional workspace at a plurality of display depths. In response to the user selecting a container object, the opacity level of the selected container object is reduced in order to reveal at least one content object contained therein. The at least one content object contained within the selected container object is displayed at a deeper display depth relative to the first display depth. By combining three-dimensional depth cues with opacity level adjustment the present invention provides a visually pleasing computer workspace with enhanced depth perception and organization features.
Owner:III HLDG 6
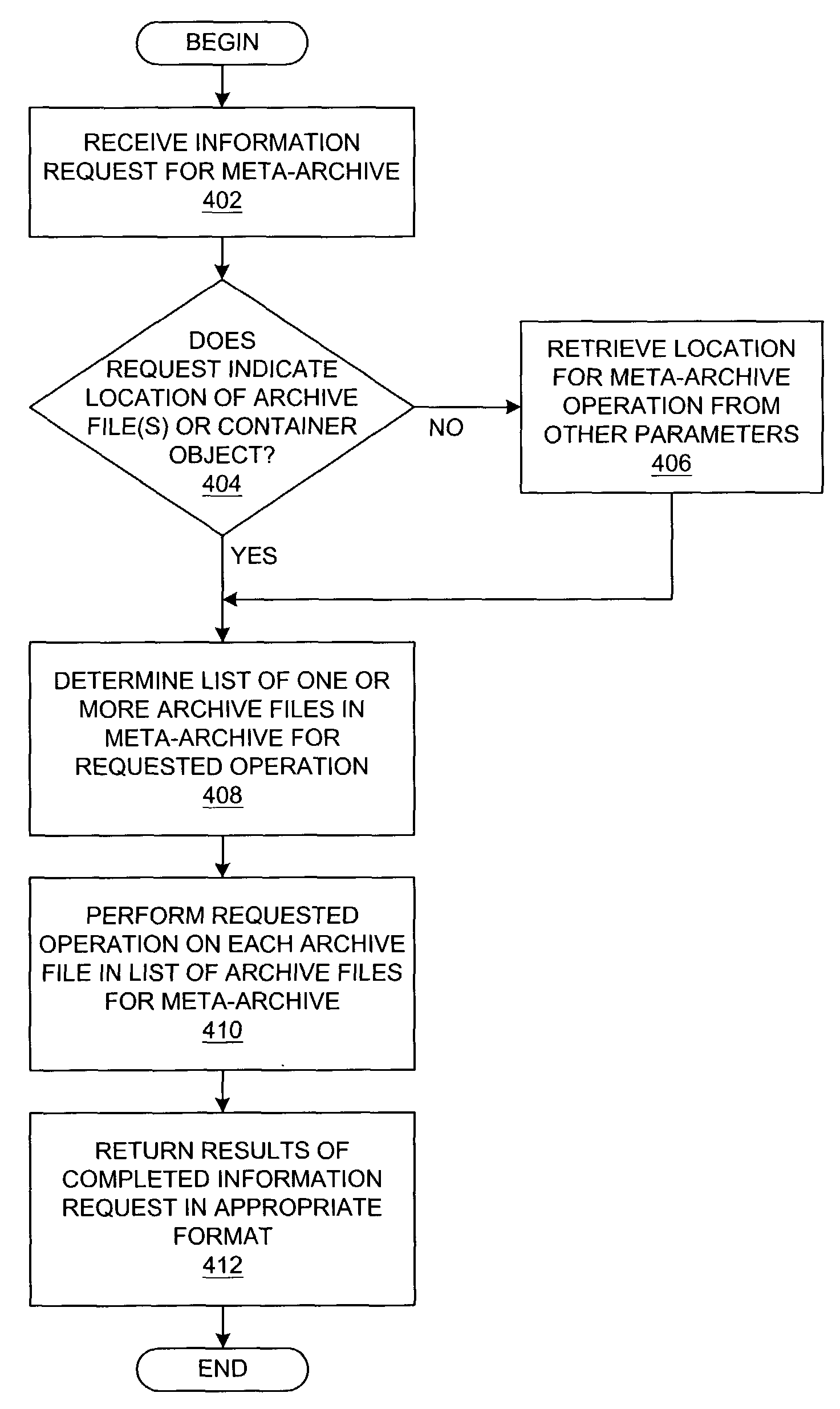
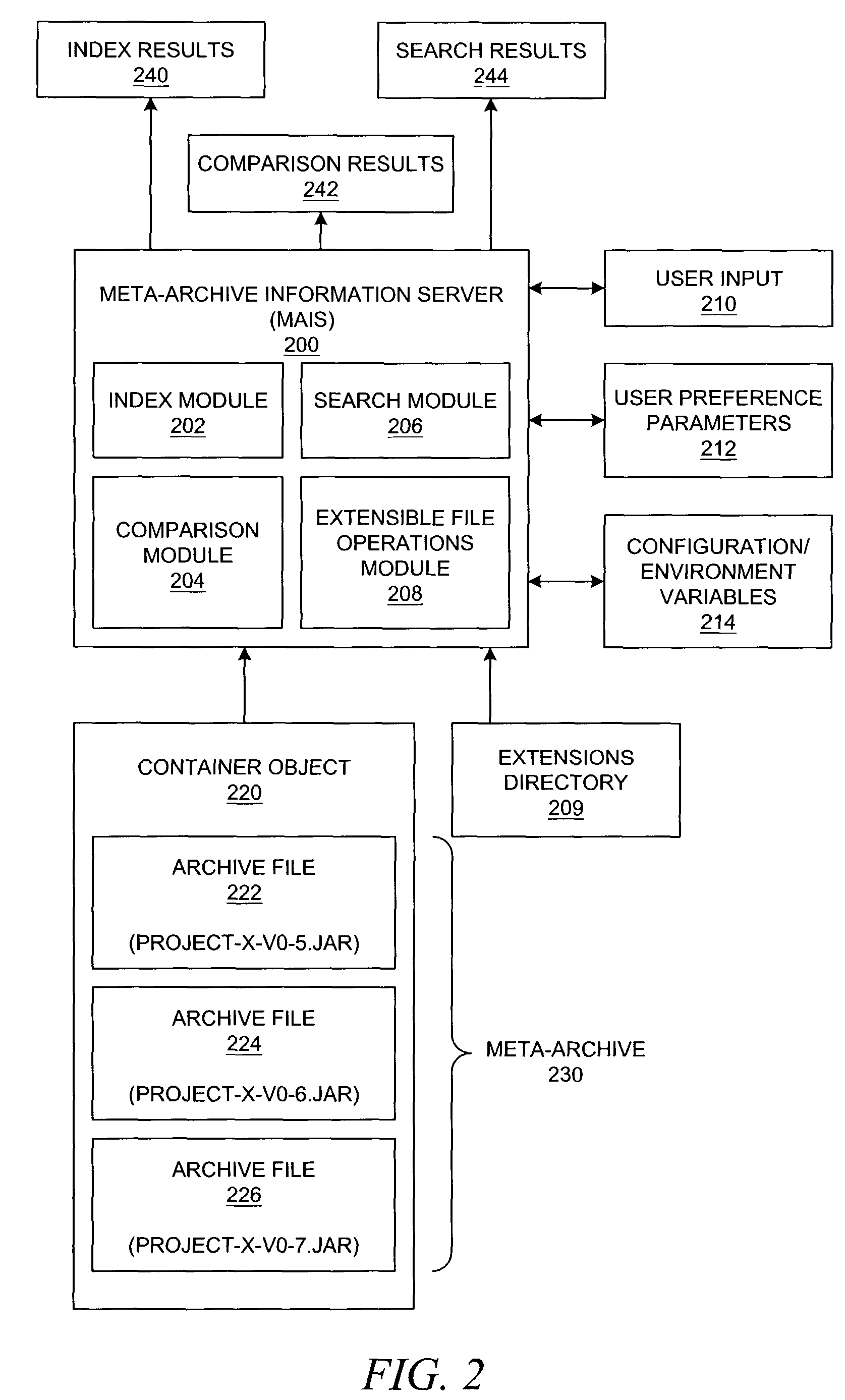
Method and system for information processing using meta-archives
InactiveUS7925661B2Reducing file system disorganizationGuaranteed uptimeWeb data indexingDigital data processing detailsInformation processingContainer Object
A method, system, apparatus, and computer program product are presented for a meta-archive information server that provides a set of operations or services for obtaining information from a meta-archive; these operations may include dynamic indexing, searching, comparing, or other operations. A meta-archive is a set of one or more archive files that are logically grouped in (or otherwise associated with) a container object, e.g., a file system folder, a directory, or another archive file. By allowing a user to derive sets of information from an entire meta-archive, a user can maintain more files within archives, thereby reducing file system disorganization. The meta-archive information server can be easily run over a specific meta-archive when necessary, thereby generating information dynamically, even if the archive files within a meta-archive change over time.
Owner:IBM CORP
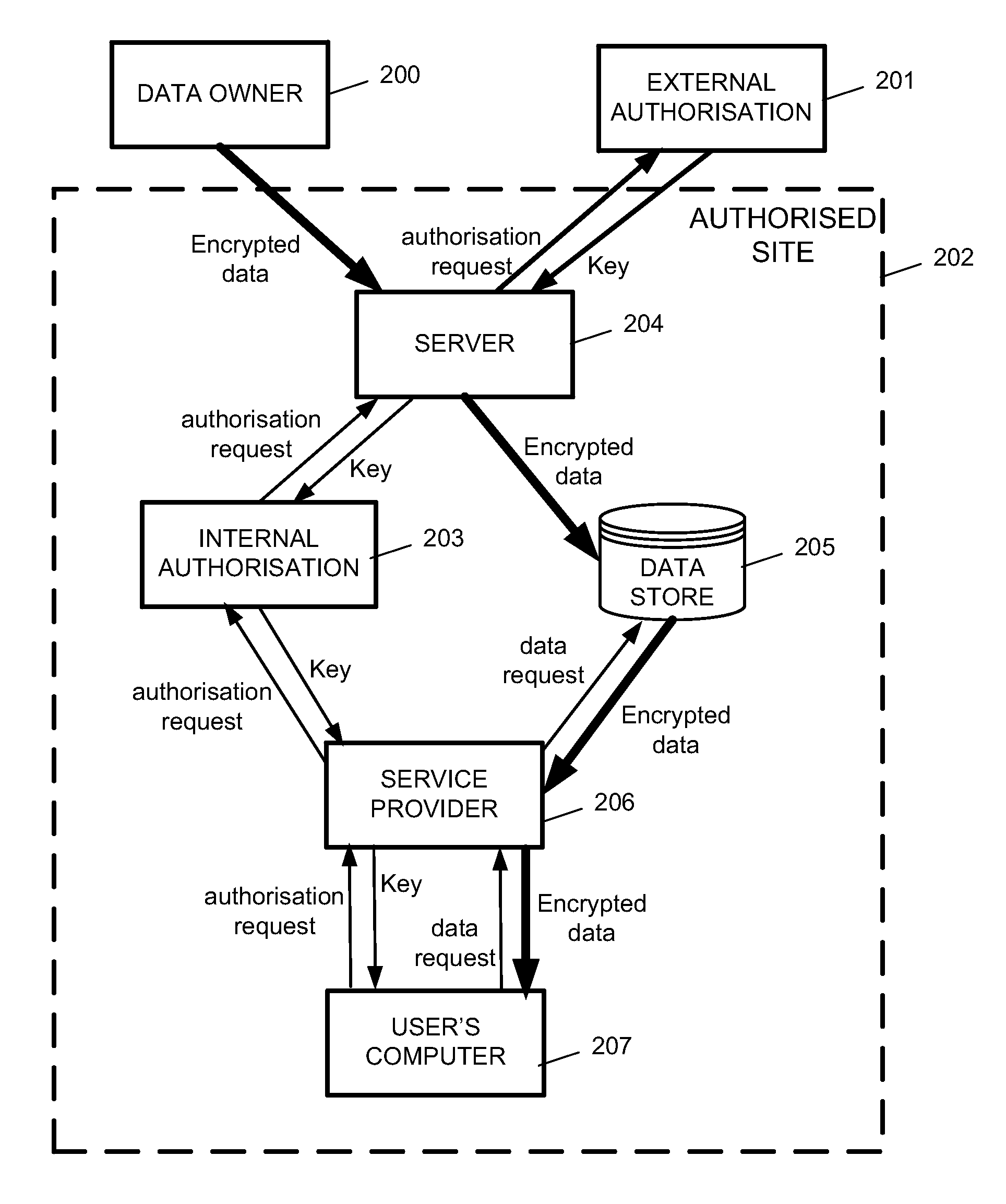
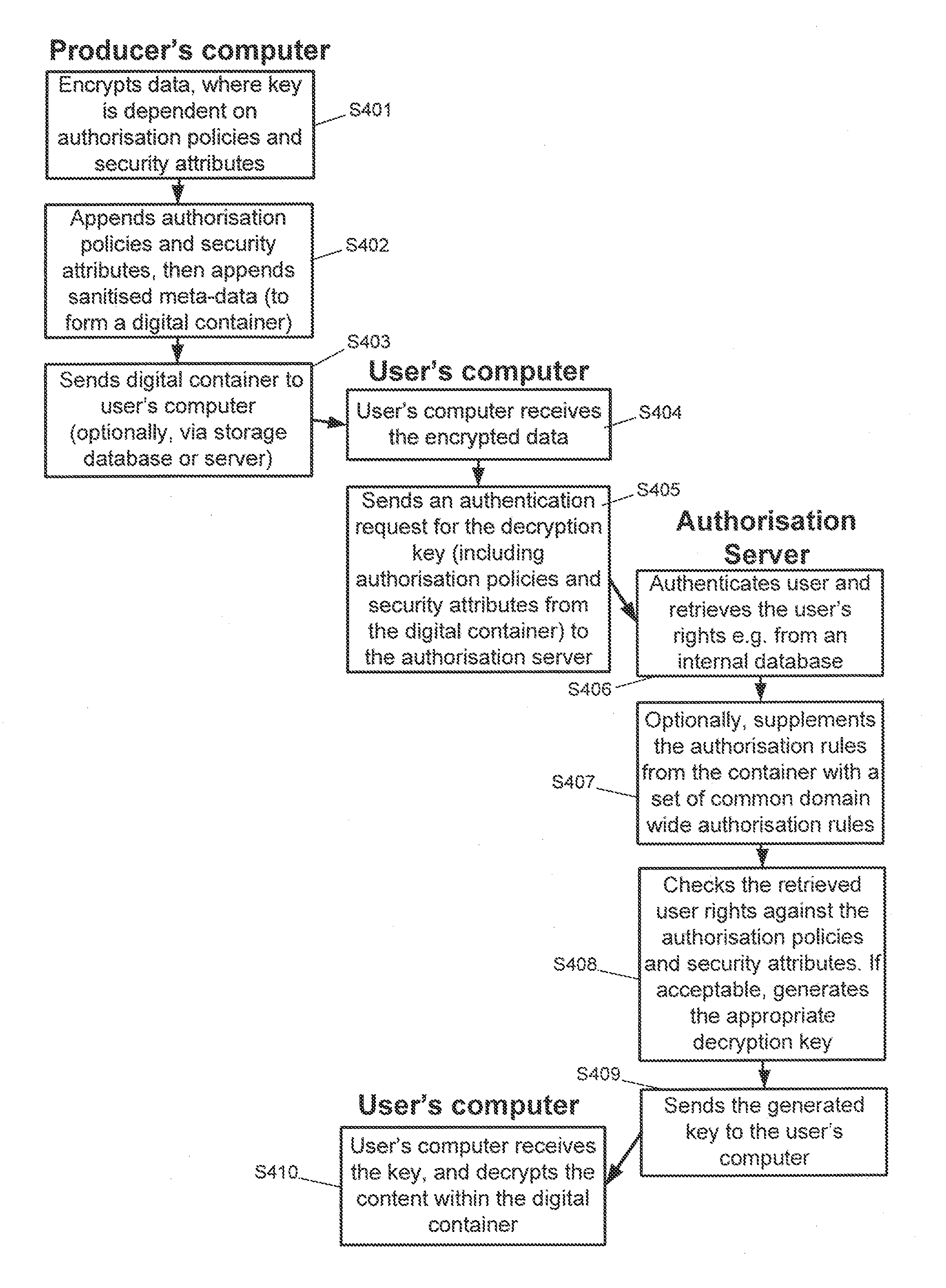
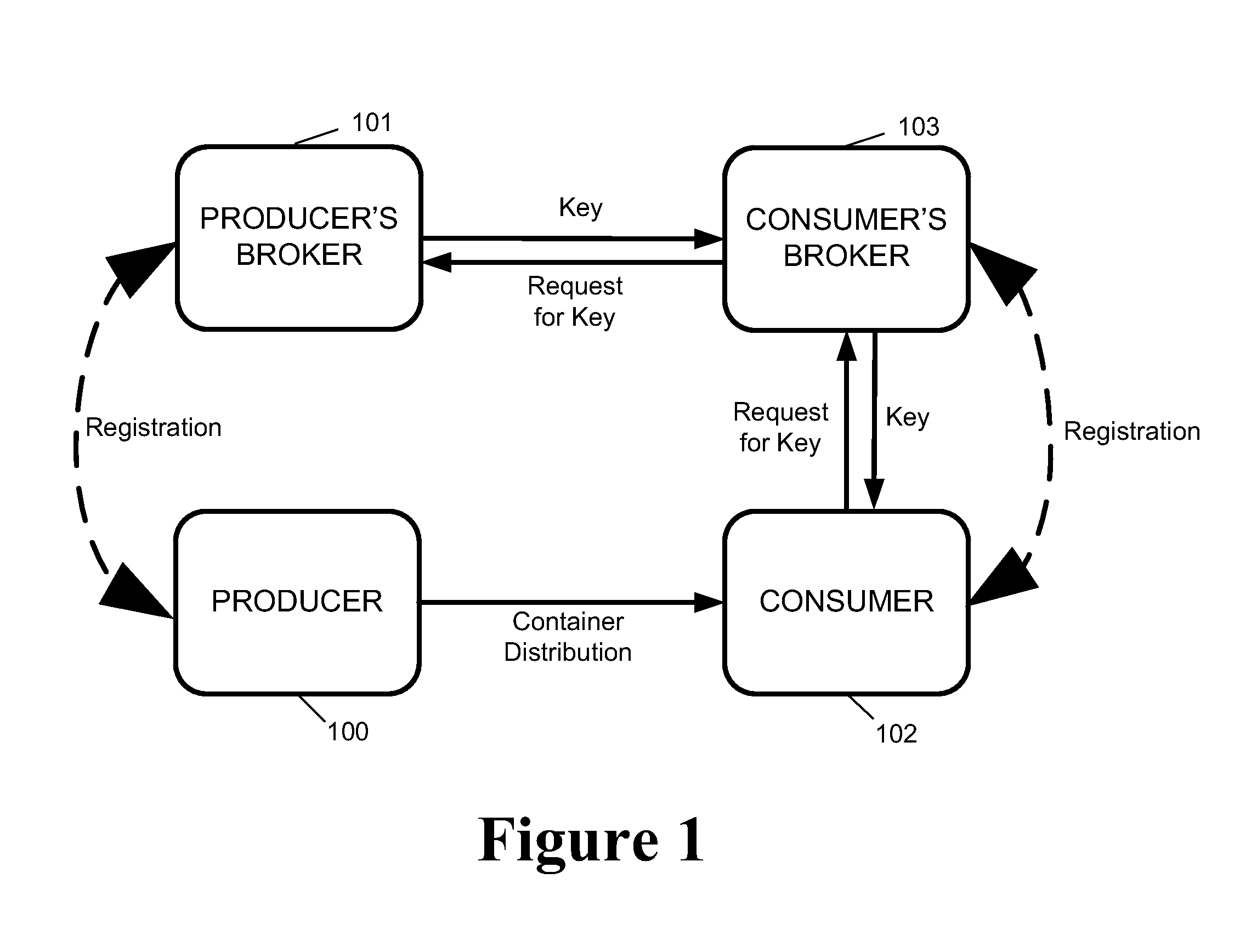
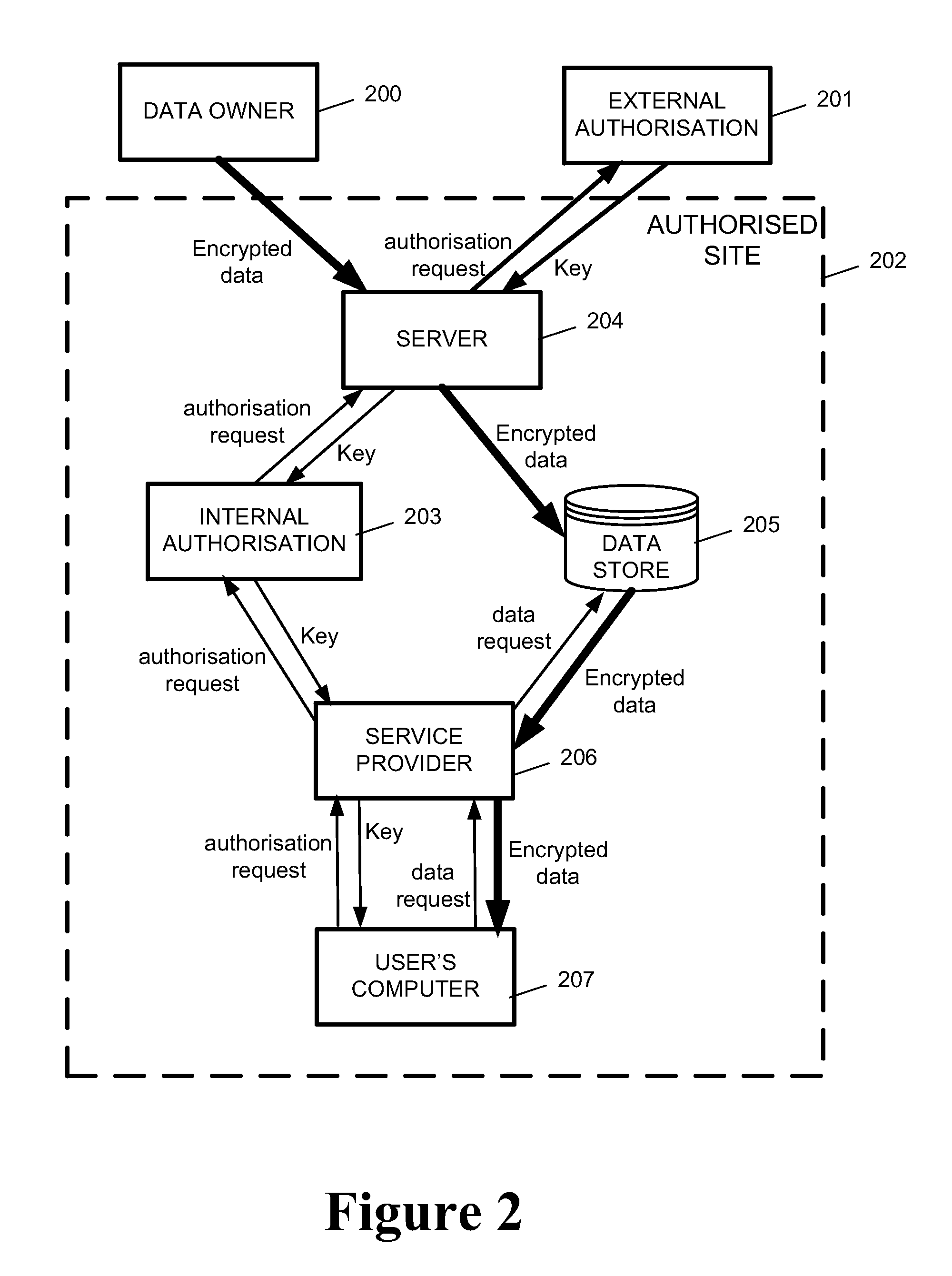
System and Method for Multilevel Secure Object Management
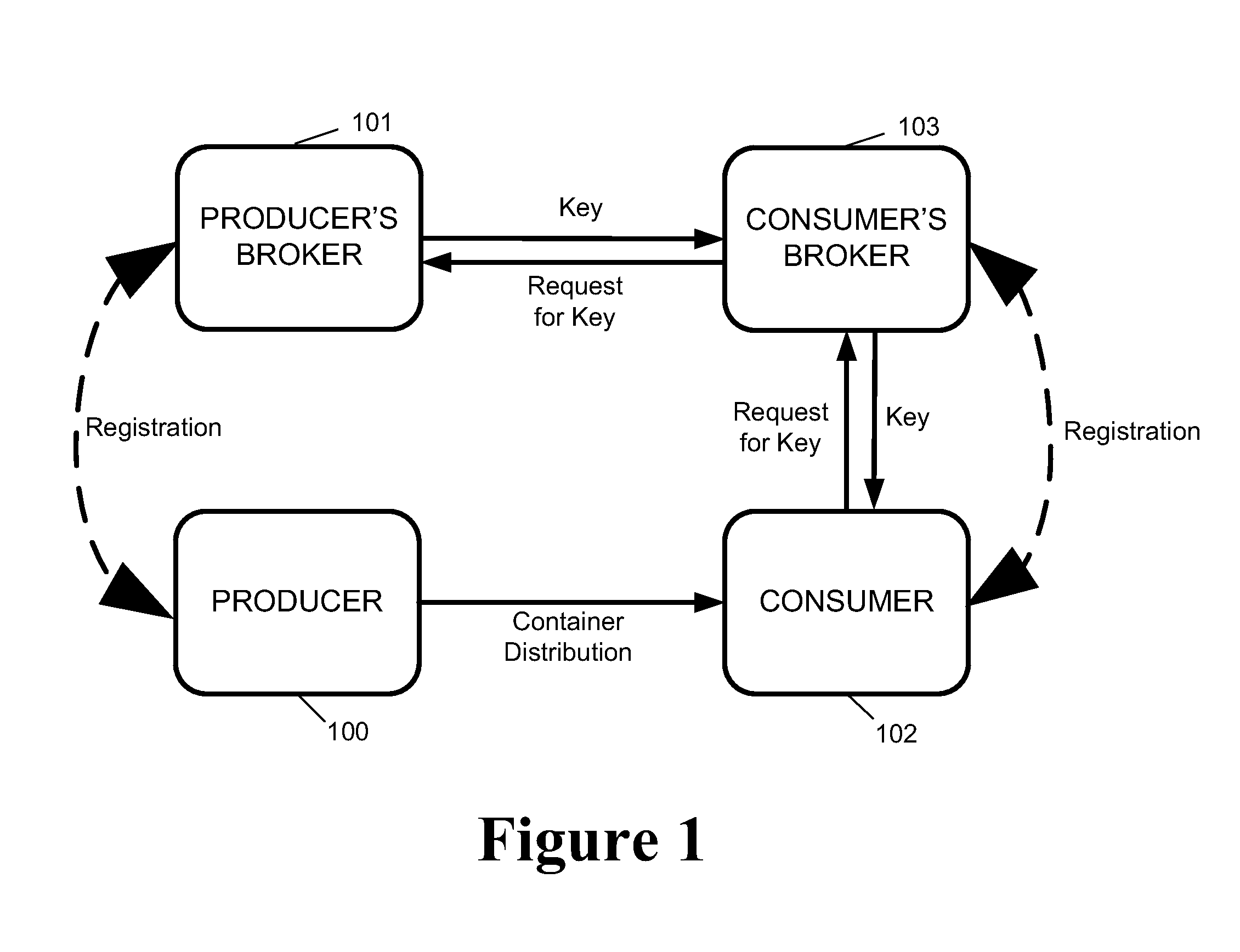
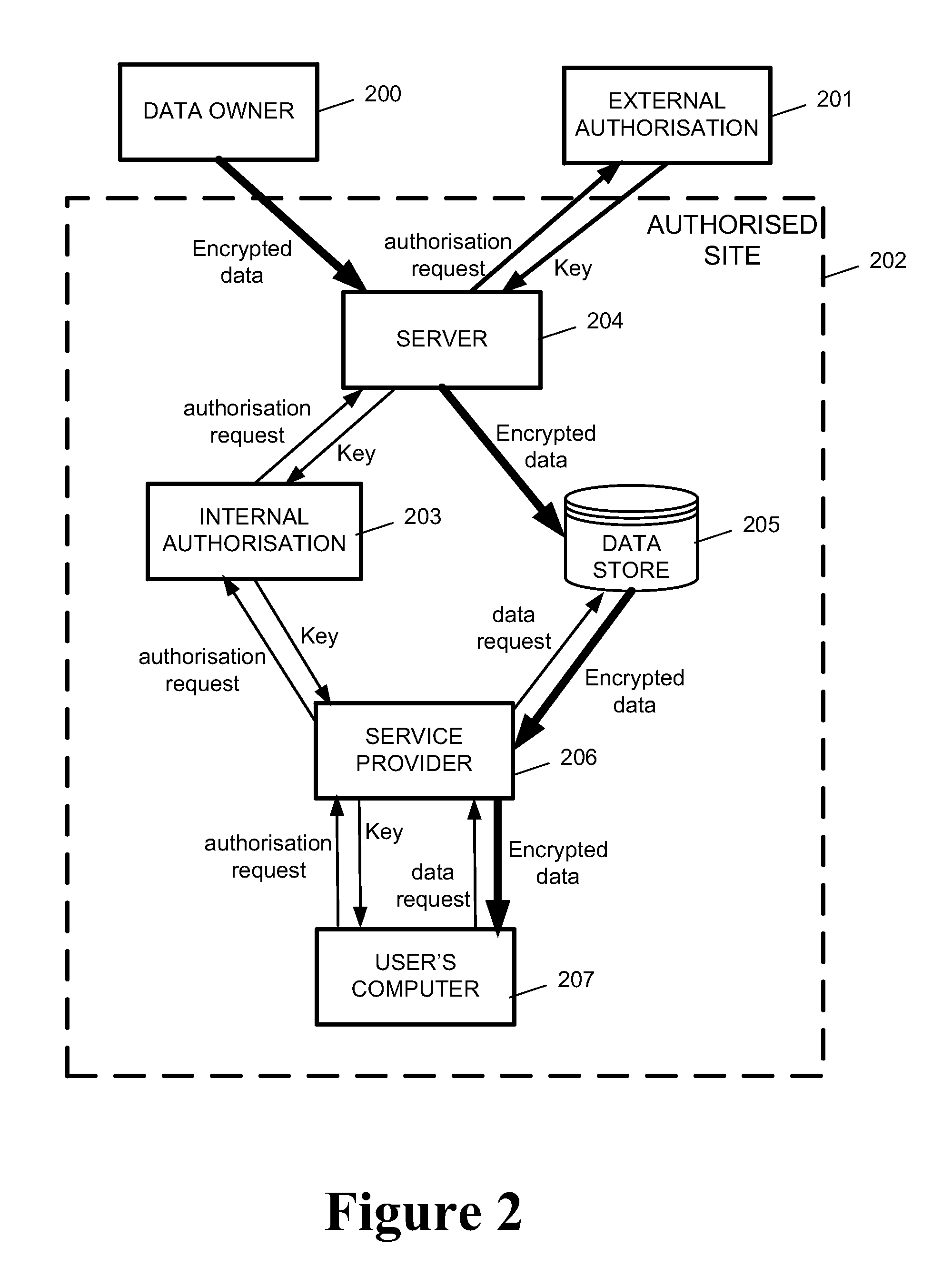
ActiveUS20110040967A1Improve the level ofEasy accessKey distribution for secure communicationSecret communicationContainer ObjectSecure transmission
A system and method for secure transport of data, the method comprising: sharing of key information with a key distributor, wherein the key information is for enabling decryption of first and second encrypted data, the key distributor being for making one or more decryption keys available to an authorised user; creating a container object, the container object comprising: first encrypted data having a first encryption based on at least a part of said key information; second encrypted data having a second encryption based on at least a part of said key information, wherein the first encryption is different to the second encryption; and metadata relating to the first encrypted data and the second encrypted data; and sending the container object to a data store or otherwise making the container object available, to allow user access to said data container object.
Owner:THALES HLDG UK
Dynamic code generation system
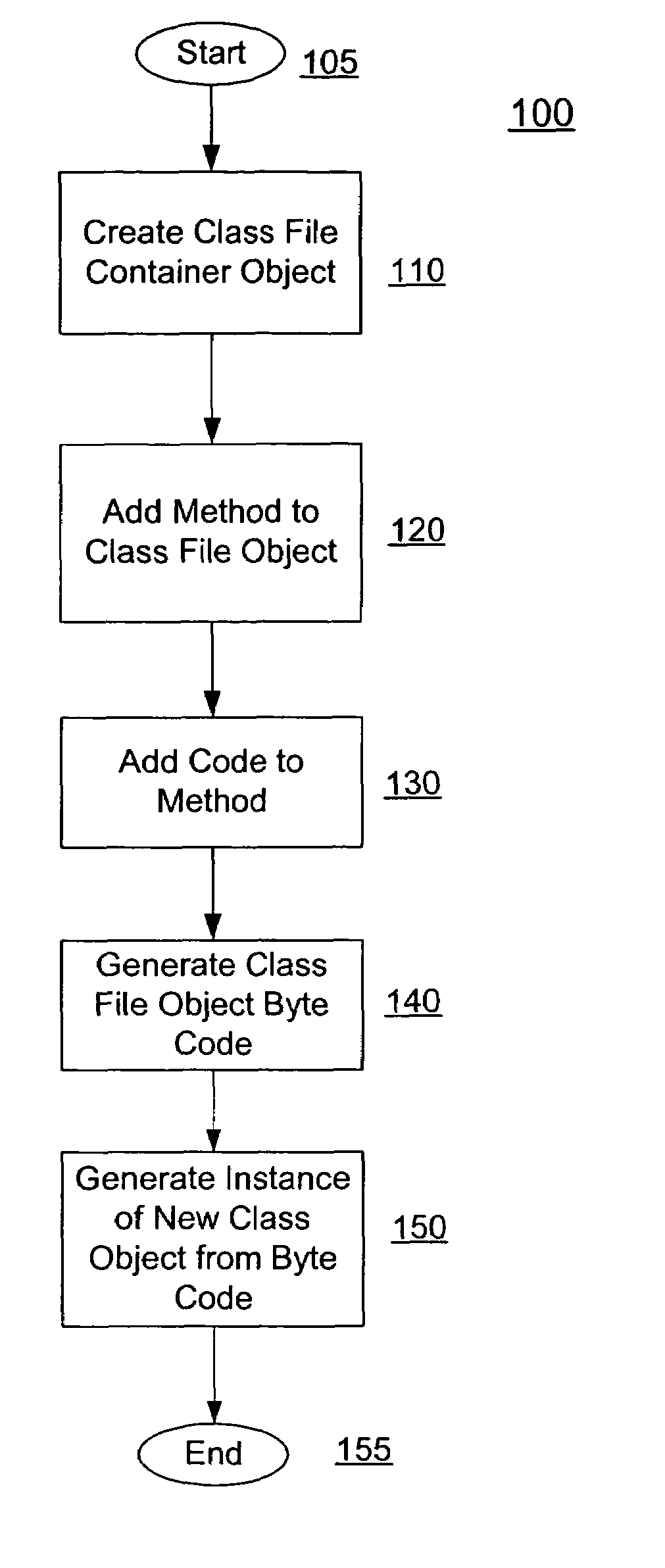
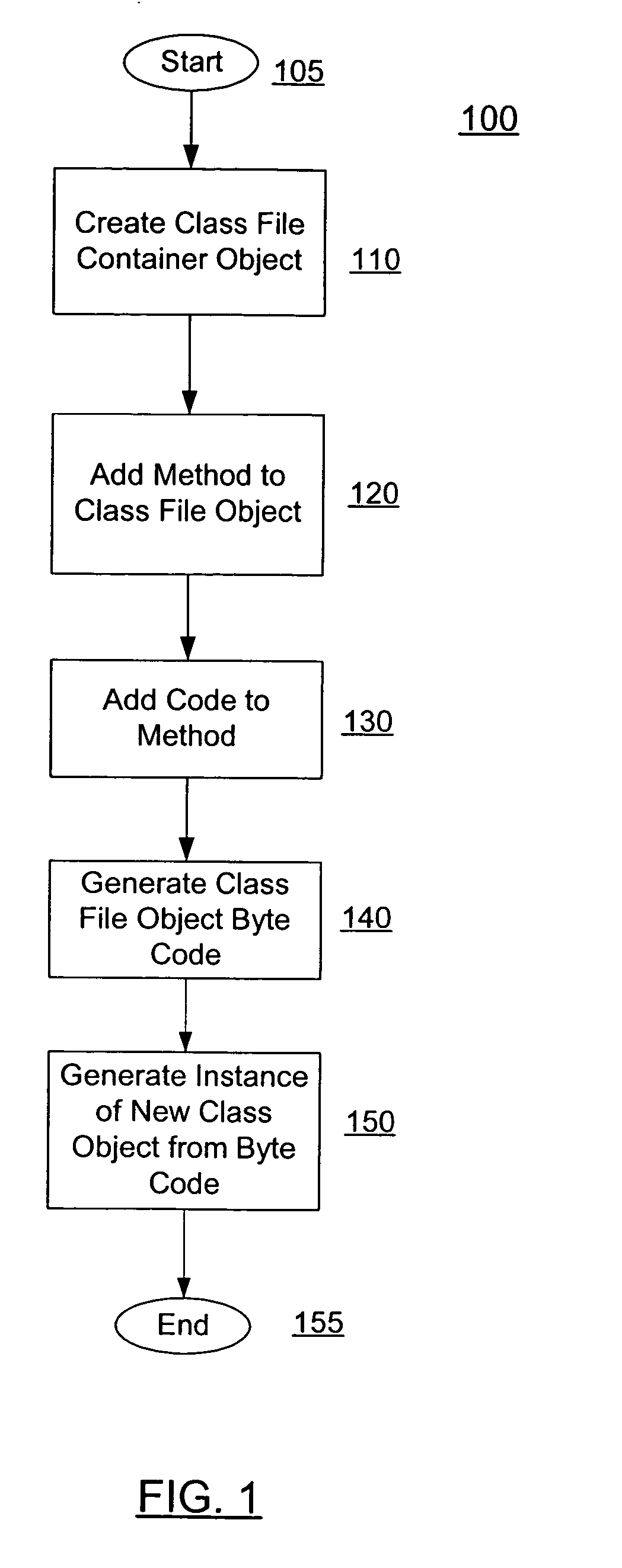
ActiveUS7536675B2Data processing applicationsSpecific program execution arrangementsLanguage constructContainer Object
A system for high level dynamic hot code generation. A class file container object is first created. Methods and code are then added to the class file container object. Byte code is then generated from the populated class file container object. From the byte code, instances of the new class object can by generated. The program code generator is configured to generate code at a programming language construct level, thereby working at a level of program language statements, expressions, variables, and other constructs.
Owner:ORACLE INT CORP
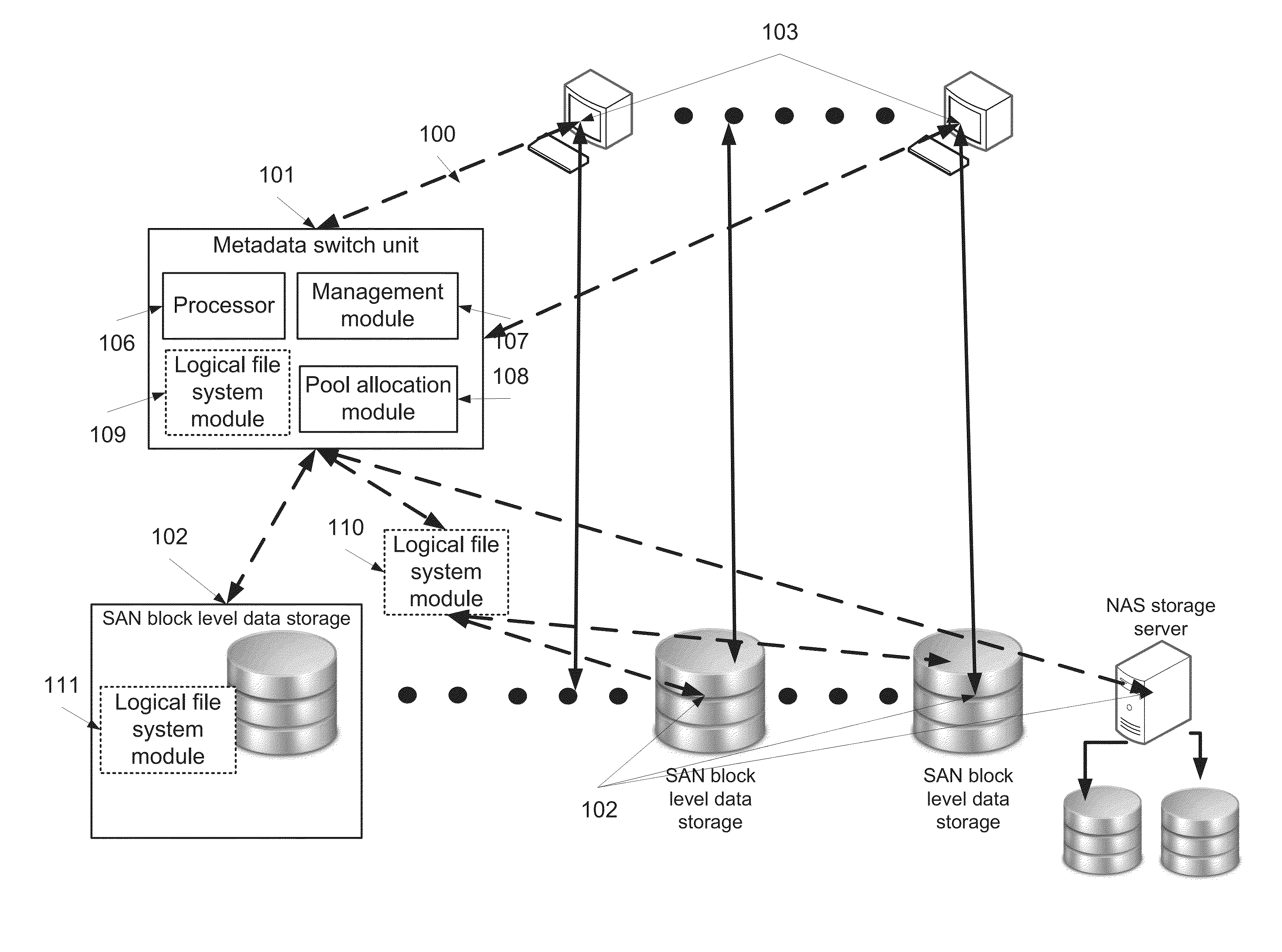
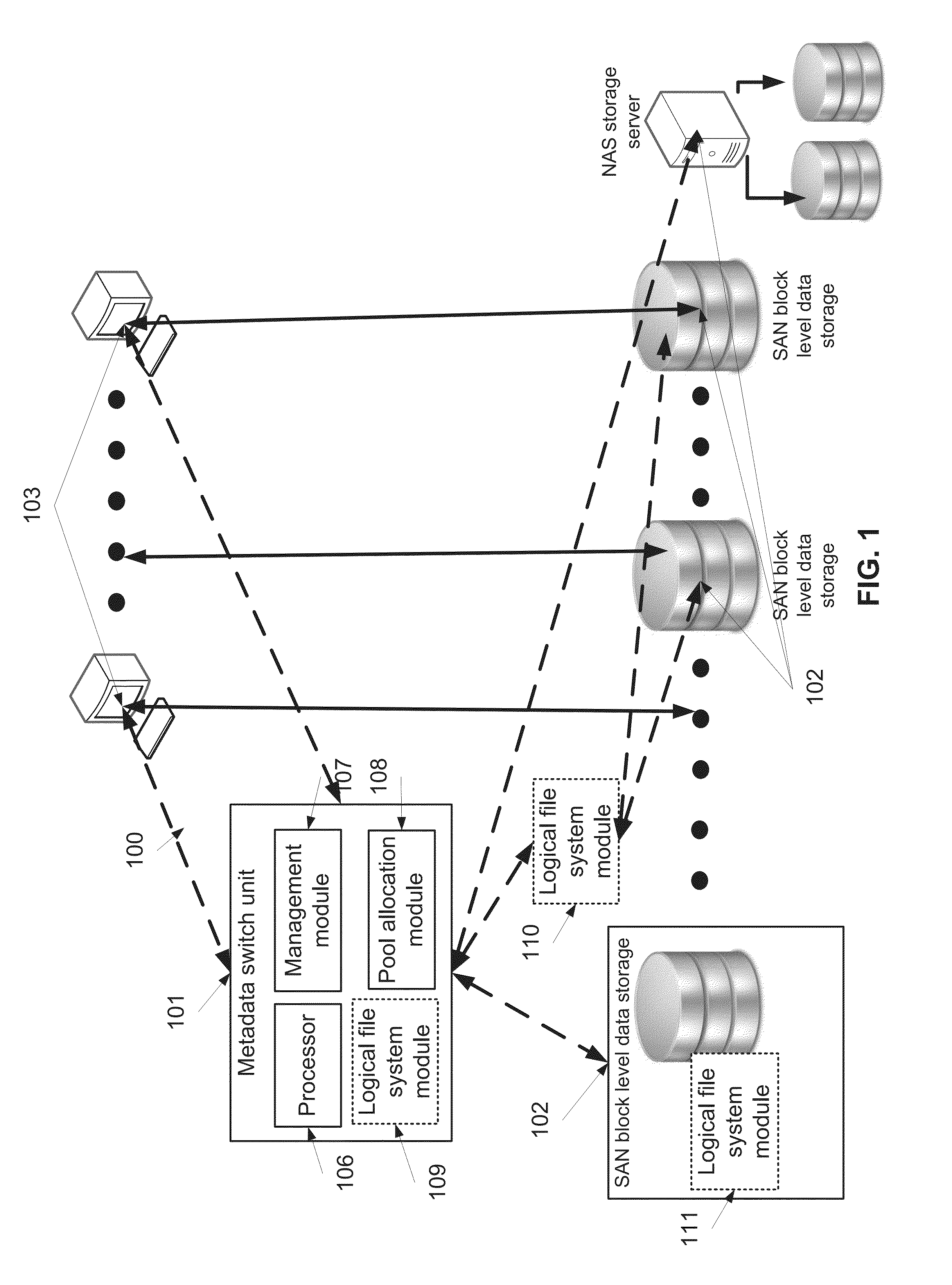
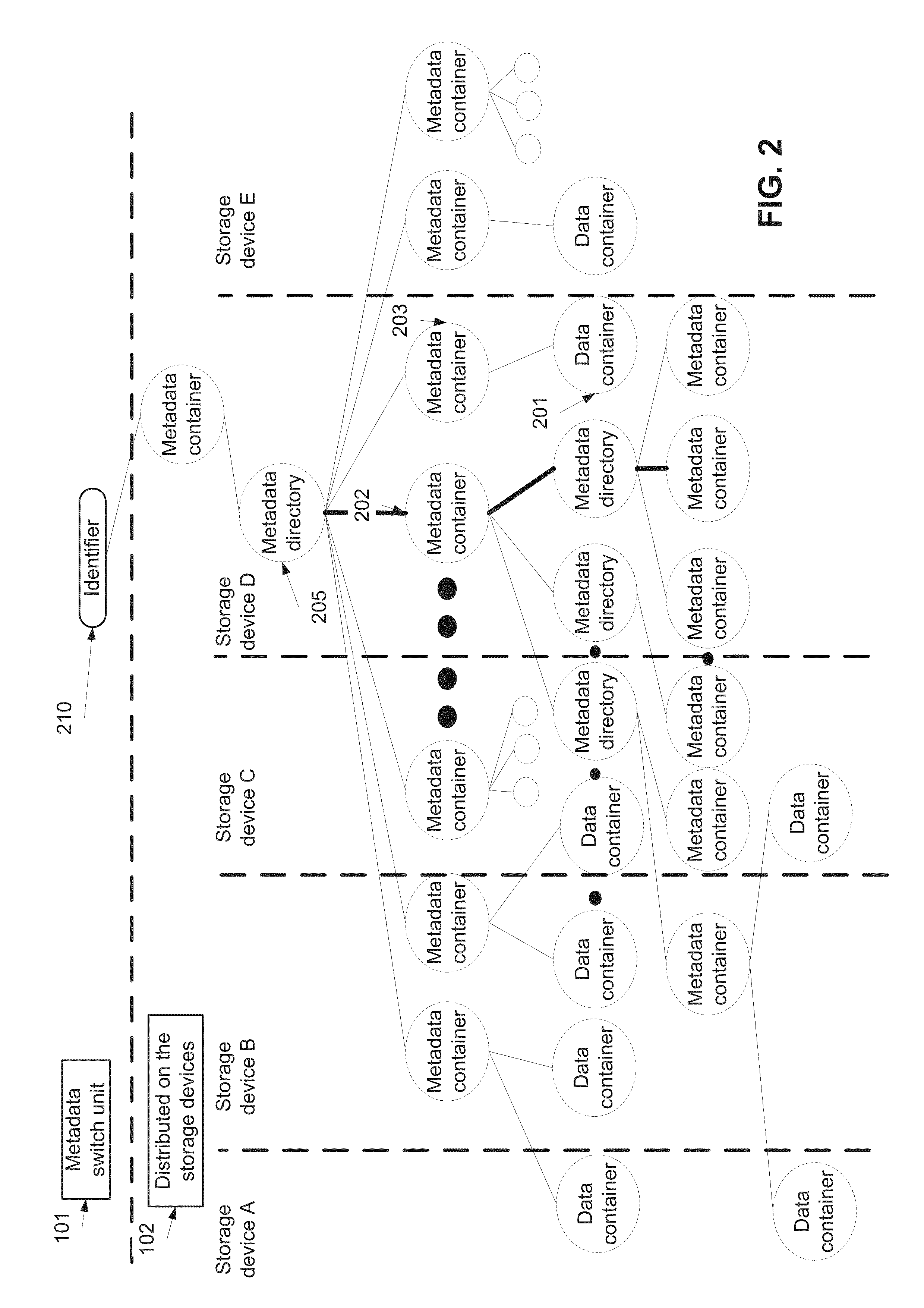
Managing objects stored in storage devices having a concurrent retrieval configuration
InactiveUS20130179481A1Digital data information retrievalSpecial data processing applicationsData controlContainer Object
A data storage method for storing data in a plurality of storage devices having a concurrent retrieval configuration. The data storage method comprises storing data in a plurality of data container objects distributed among in a plurality of storage devices, storing a plurality of metadata container objects and a plurality of metadata directory objects in the plurality of storage devices, wherein each metadata directory object indexes a group of the plurality of metadata container objects and each the metadata container object comprises metadata including storage location data of at least one of the plurality of data container objects and the plurality of metadata directory objects, and managing access to the plurality of data container objects by locally executing a plurality of data control requests by the plurality of storage devices, by a module installed in the plurality of storage devices or in a proxy.
Owner:PD MANAGEMENT HLDG INC
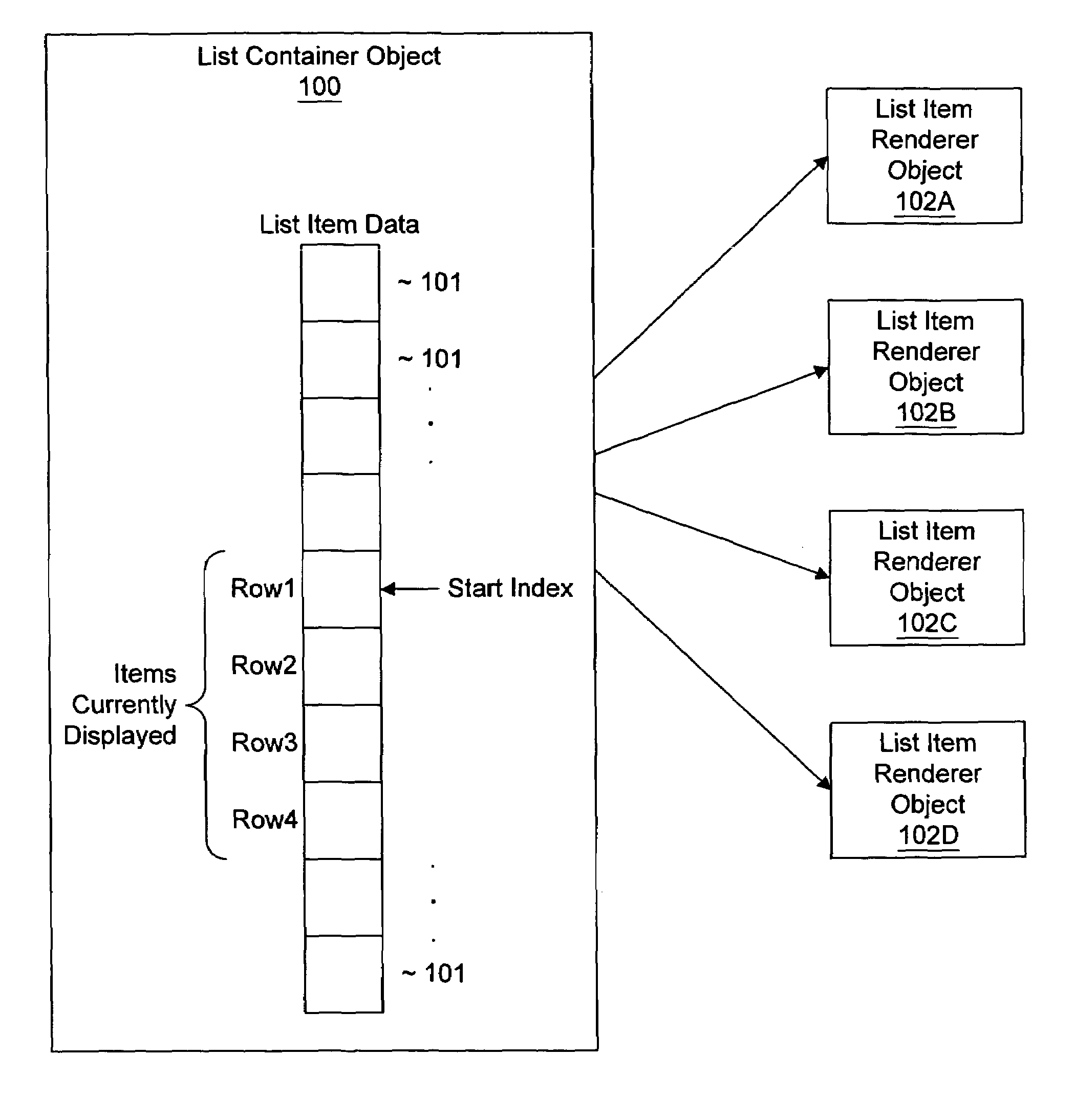
System and method for managing a scalable list of items for display
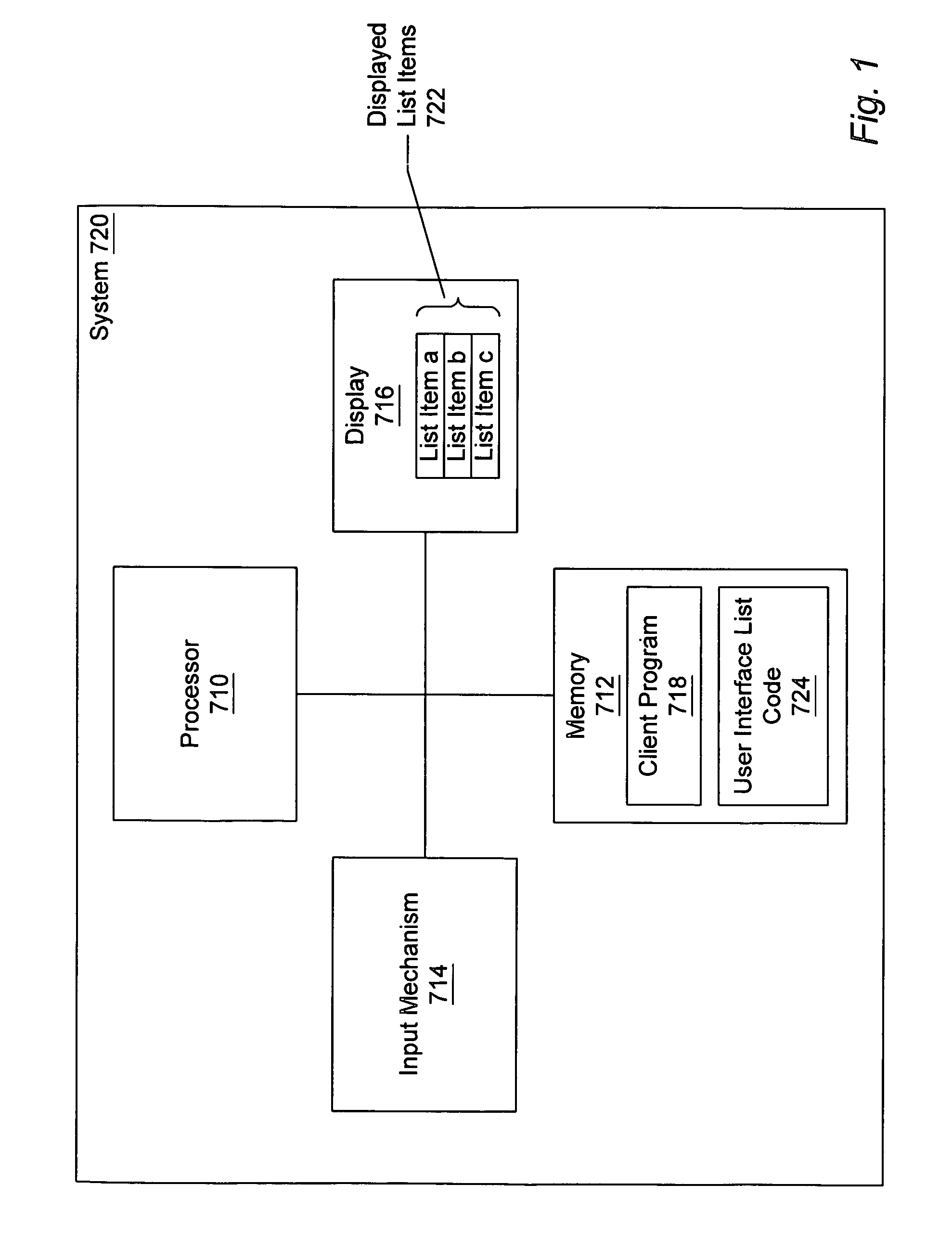
InactiveUS6959425B1Execution for user interfacesDigital output to display deviceContainer ObjectDisplay device
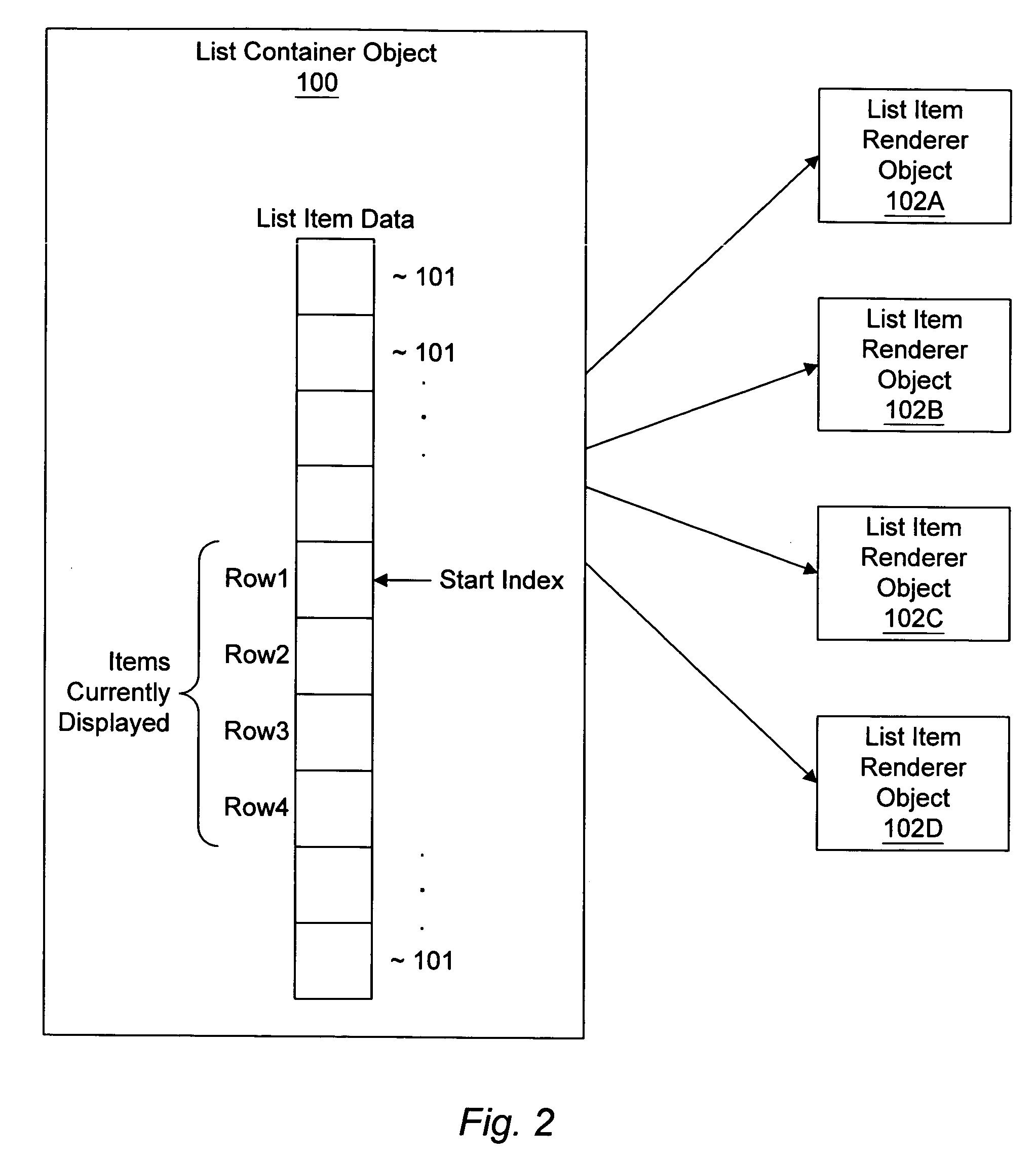
A system and method for managing a scalable list of items for display in a display device of a small footprint device. A client program running in a small footprint device may instantiate a “list container object” and add “list item data objects” to the list container object. The list container object may instantiate a fixed number of “item renderer objects”, which are responsible for appropriately displaying the list item data objects. Each item renderer object may correspond to a row in the displayed list. The list container object interfaces with the set of item renderer objects, in order to manage the display of the list. In one embodiment, the item renderer objects are instances of a class that supports an “item renderer interface” that includes methods for interacting with the item renderer objects. Thus, a general framework is described in which any of various types of objects may be displayed, by implementing the item renderer interface methods appropriately for different item renderer object implementations. The list container object may keep track of the set of list item data objects being displayed at any given time. As a user interacts with the list, e.g., by scrolling up or down, the list container object may receive method calls or user interface events indicating the user's action, may determine the new start index for items to display, and may instruct each item renderer object to redisplay the appropriate list item data object, e.g., by calling an item renderer interface method for each item renderer object, passing the corresponding list item data object as a parameter.
Owner:ORACLE INT CORP
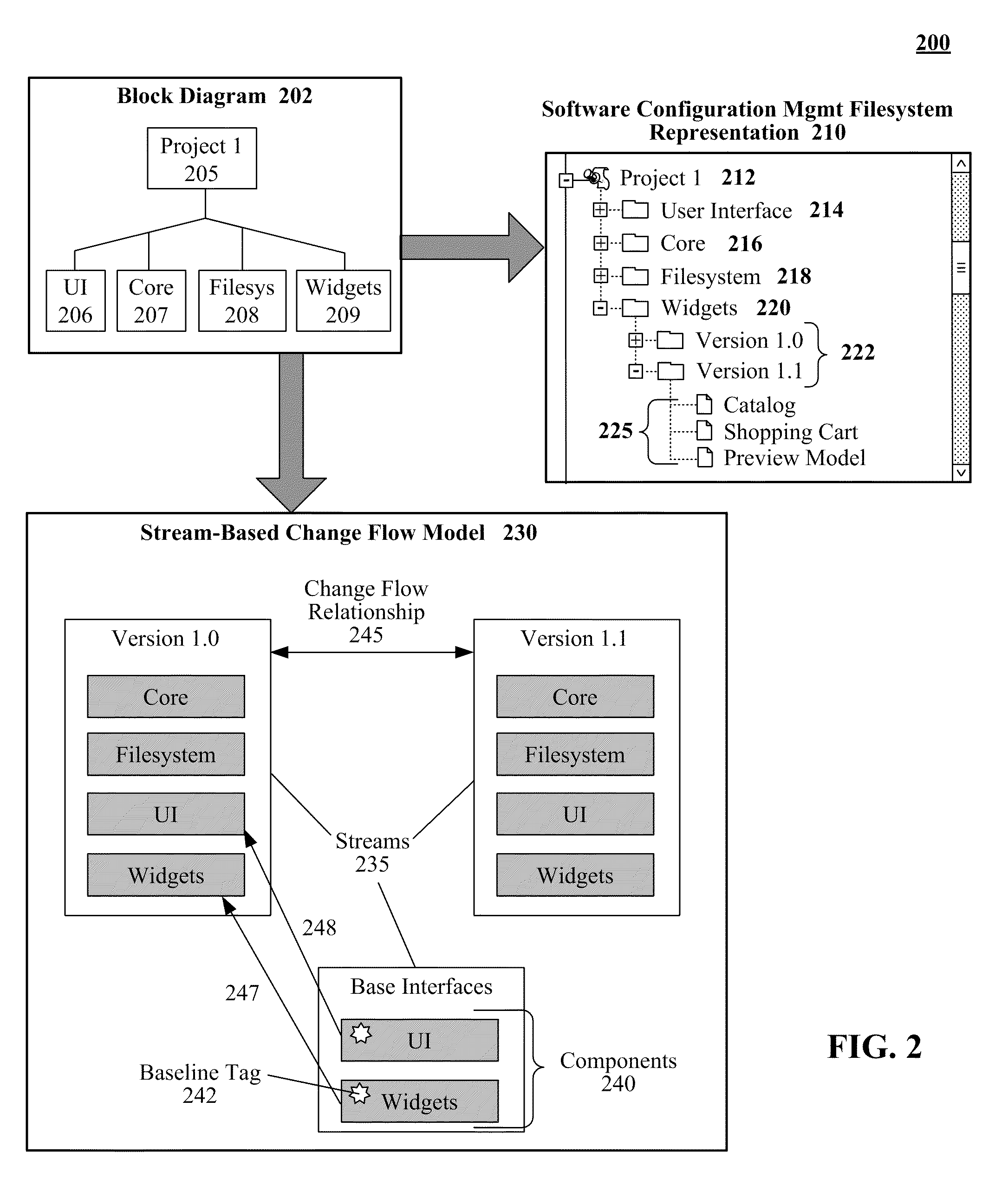
Automated stream-based change flows within a software configuration management system
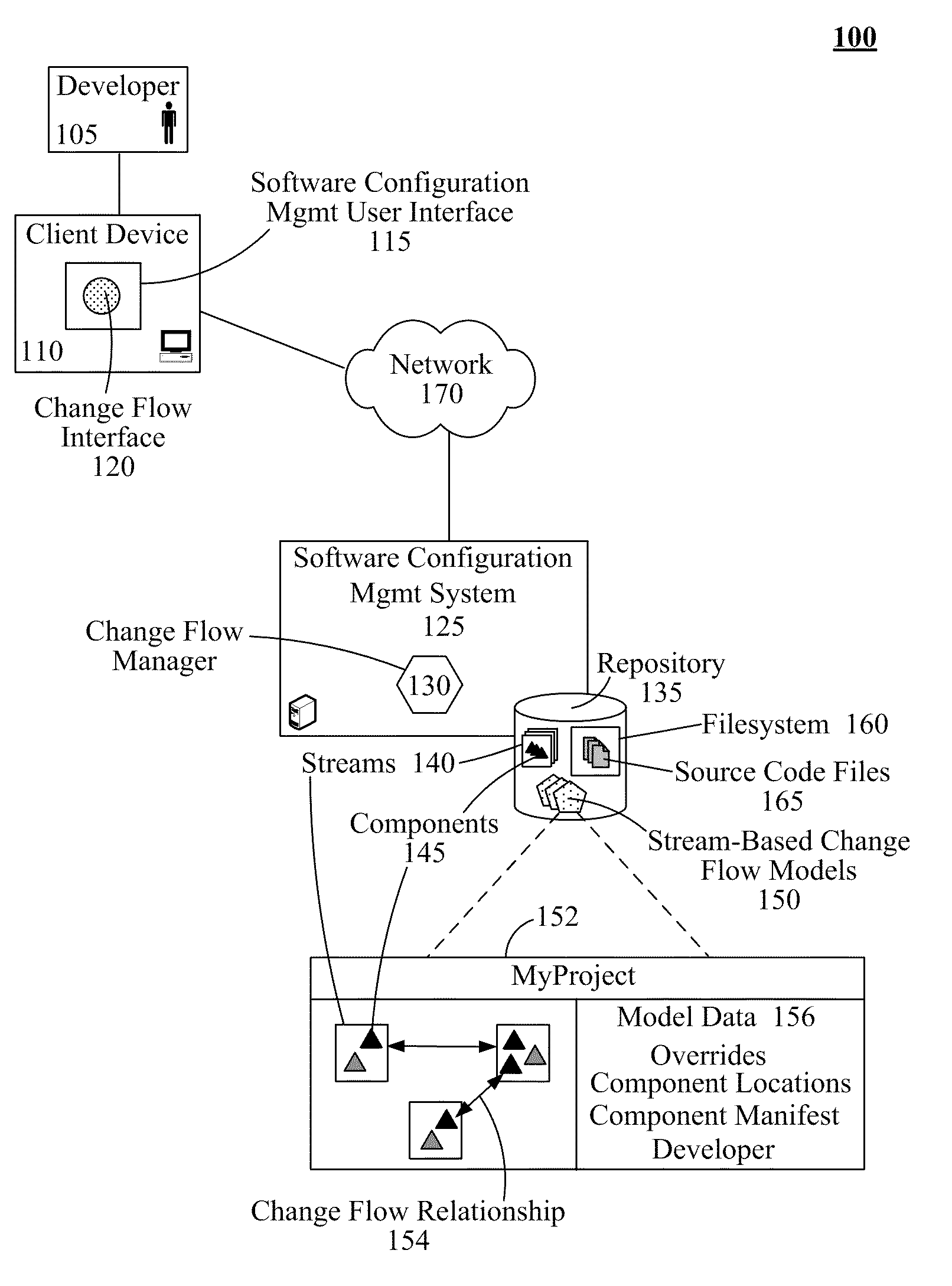
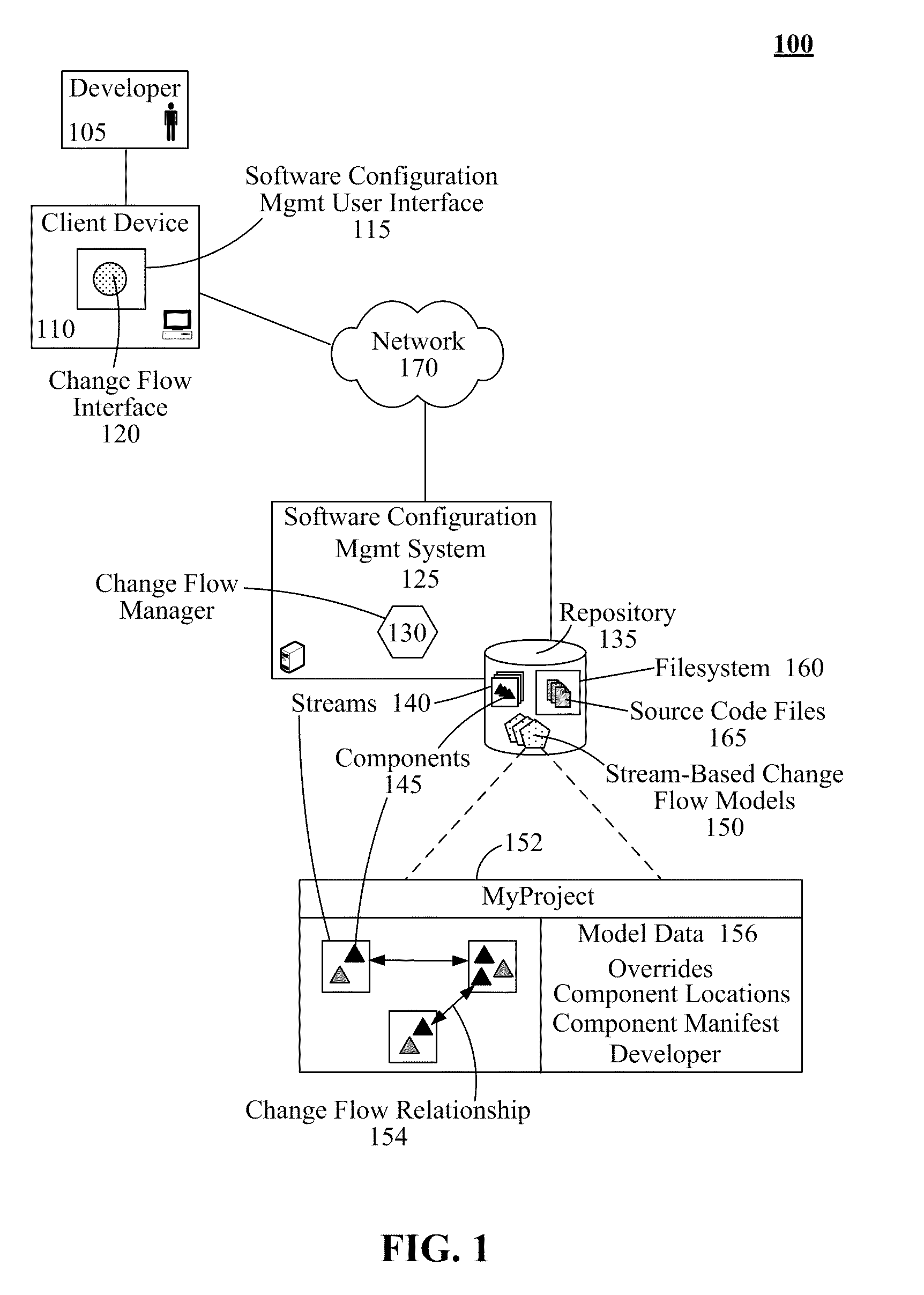
InactiveUS20110161931A1Version controlSpecific program execution arrangementsSource code fileFile system
Using stream-based change flow models to propagate source code file changes within a software configuration management system can begin with the detection of the addition of a source code file, either a new file or new version, to a software configuration management system by a change flow manager. The source code file can then be related to a component based upon the hierarchical placement of the source code file within the filesystem. Stream-based change flow models that contain the component can be identified. Change flow relationships within a stream-based change flow model can define the propagation of changes between streams (an aggregate of components) and / or components. Authorization from a human agent can be requested to initiate propagation of the source code file. Upon receipt of an affirmative response, the source code file can be automatically copied to the container objects that correspond to the identified recipients for changes.
Owner:IBM CORP
Method and system for efficient control of the execution of actions in an object oriented program
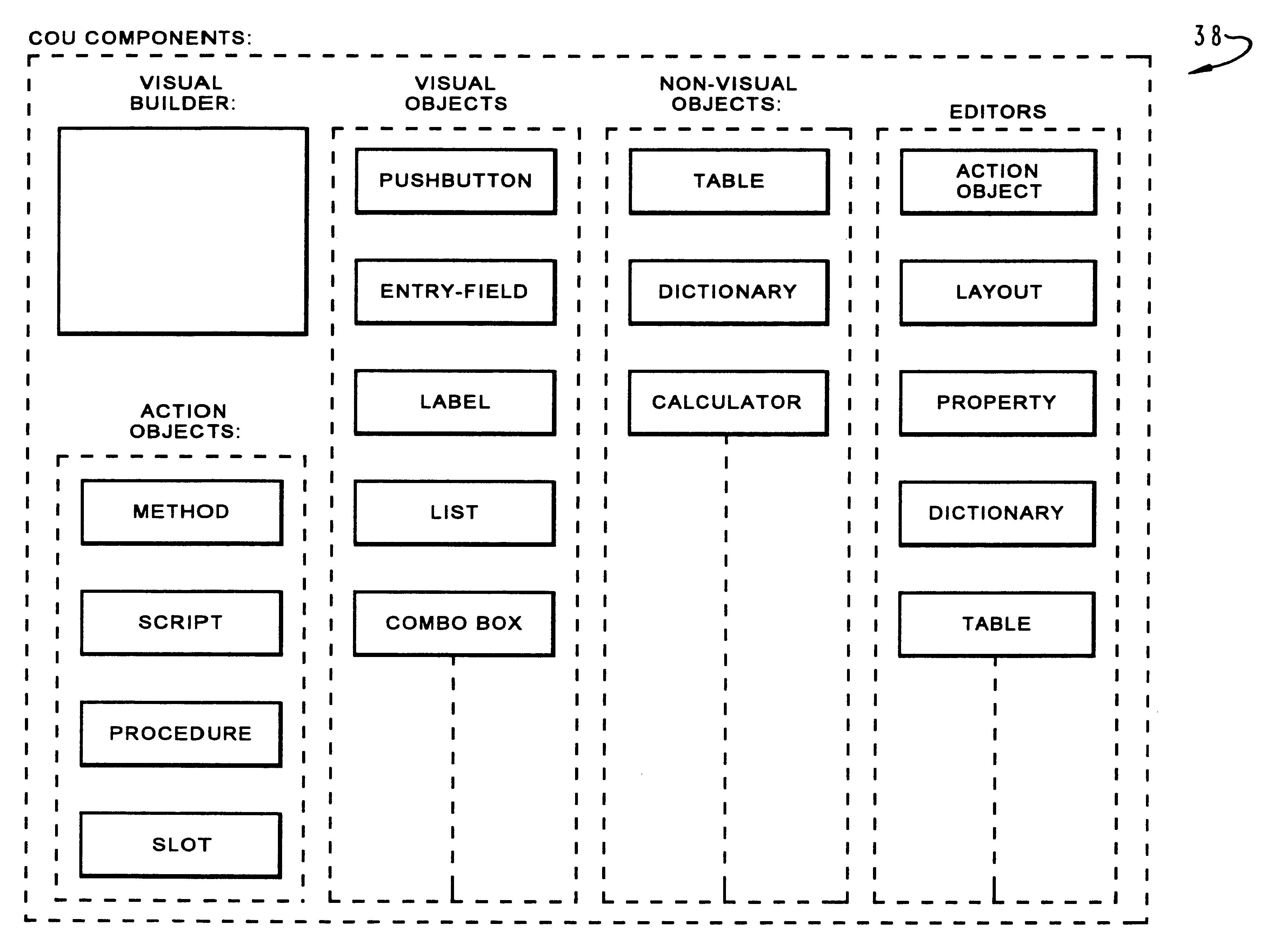
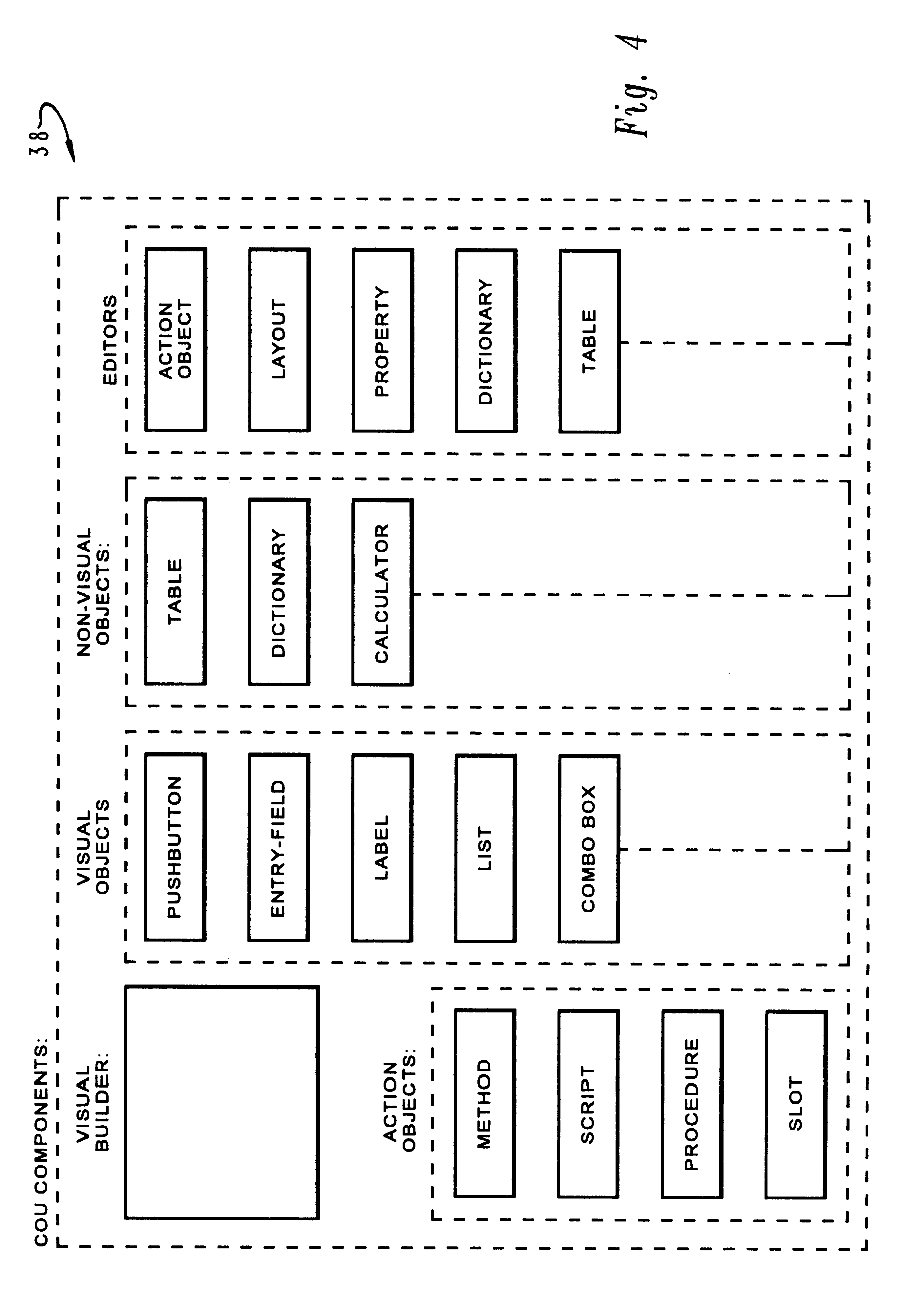
InactiveUS6216149B1Short response timeImprove coordinationMultiprogramming arrangementsSoftware designContainer ObjectComputer science
A method and system for efficiently controlling the execution of actions in an object oriented program. An observable object is defined which responds to a predetermined number of abstract events, each abstract event corresponding to an action slot container object which is associated with the observable object. New abstract events may be defined at execution and a corresponding new action slot container object associated with the observable object at that time. One or more action objects which each specify a unit of behavior are then defined and placed within the action slot container objects such that the occurrence of a corresponding abstract event may initiate the occurrence of multiple units of behavior. Separate subclasses of action objects are also defined, each subclass specifying a manner in which the specified unit of behavior will be implemented. In this manner, methods, scripts, procedures, and other abstract events may be initiated in response to an execution of an action object and a determination of the subclass to which that action object belongs.
Owner:IBM CORP
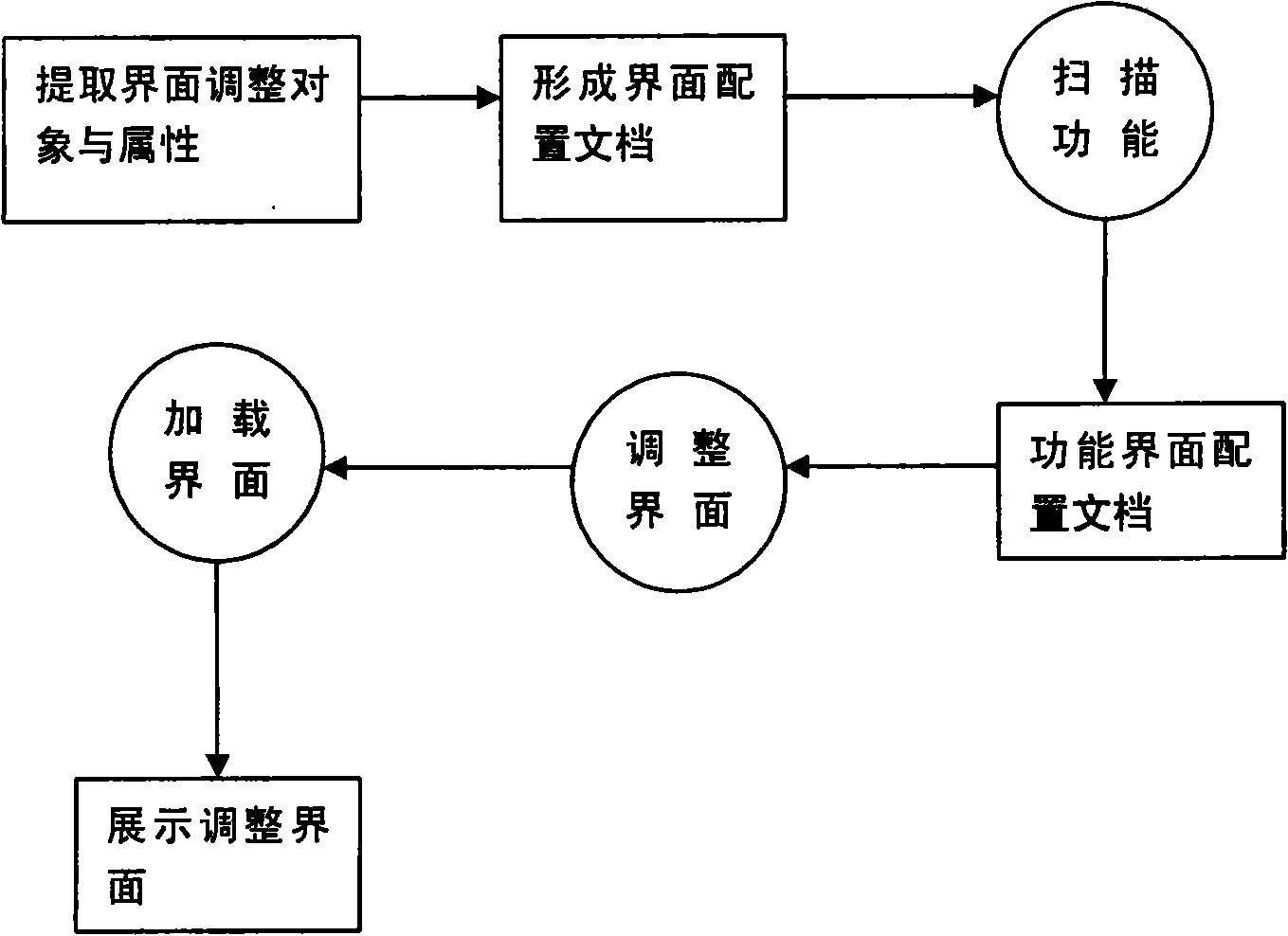
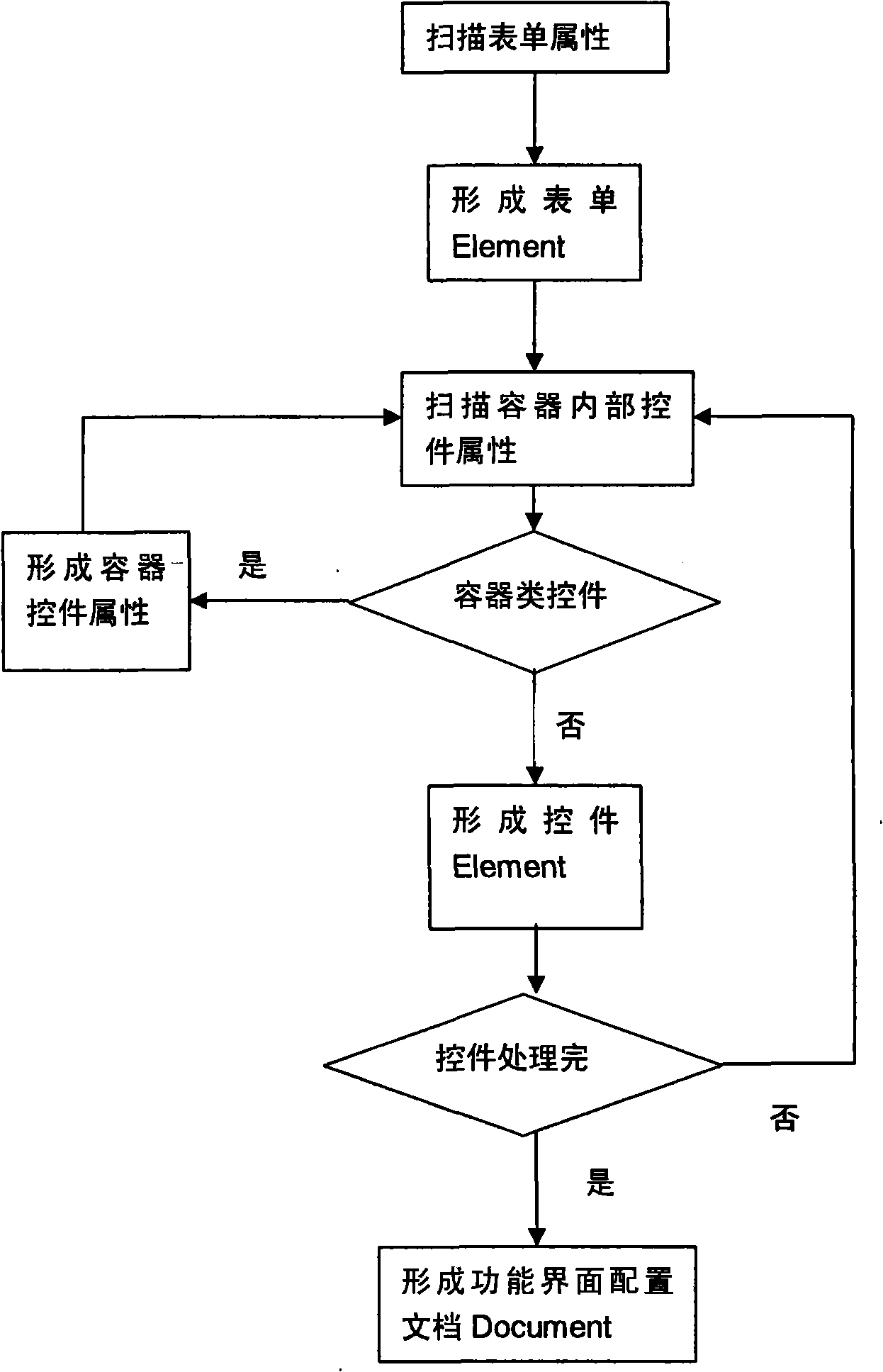
Agile setting human-machine interactive interface accomplishing method
InactiveCN101266544ASolve the problem of dynamic configurationRealize dynamic adjustmentSpecific program execution arrangementsContainer ObjectMan machine
What the invention solves is the method of the man-machine interactive interface dynamic disposition, which resolves the problem of client procedure interface dynamic disposition. The interface appearance attribute is extracted according to the user interface demand to form the an interface disposition document, an initial interface disposition document is stored by a scanning function interface; the simulation display adjustment interface of the man-machine interactive interface is dynamically formed according to the initial interface disposition document, after the user adjusts the simulation interface, a new functional interface disposition document is stored automatically. the appearance display is adjusted in sequence according to the interface properties of an object element, the up and down display relationship of interface multi-object is adjusted according to the level relation, a vessel object which is interdependent showed by a control is decided according to he interdependence relations decision, so that the dynamic adjustment of the client procedure interface is realized.
Owner:INSPUR COMMON SOFTWARE
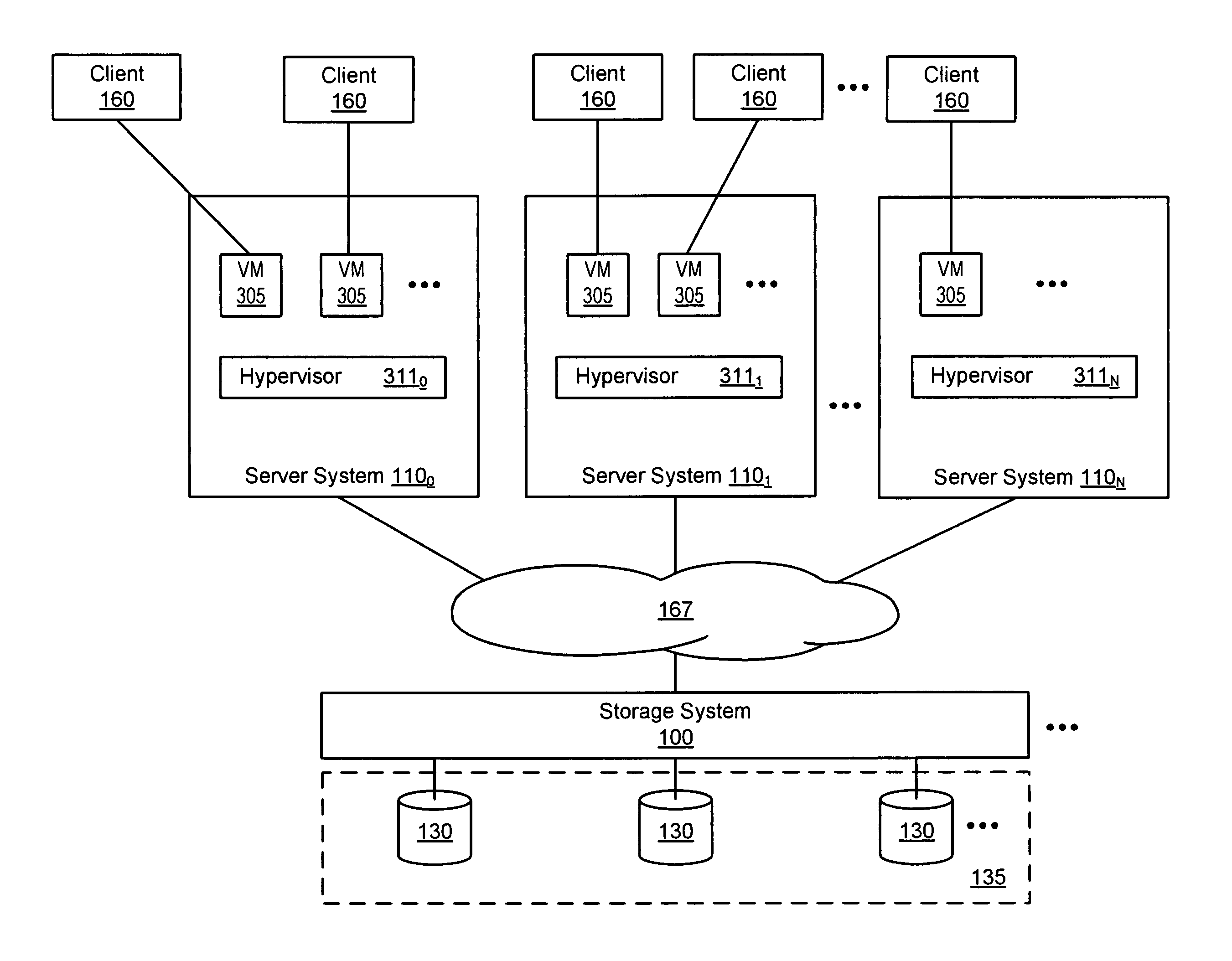
System and method for storage and deployment of virtual machines in a virtual server environment
ActiveUS8943203B1Rapid deploymentMultiple digital computer combinationsProgram controlContainer ObjectComputer module
Described herein are systems and methods for storage and deployment of VMs in a virtual server environment. A VM deployment module executing on a server may produce VM container objects representing VMs, a VM container object comprising VM data describing a VM and vdisk configuration data. The VM deployment module may also later produce VMs on a server using the VM container objects. The VM deployment module may do so by producing a vdisk from a VM container object, the vdisk comprising the VM and vdisk configuration data. Rather than configuring the vdisk as typically done to make the vdisk useable to the server, the vdisk configuration data is used to make the vdisk useable and the VM data on the vdisk immediately accessible to the server. As such, the VM data may be immediately read to produce a VM on the server, thus providing rapid deployment of VMs.
Owner:NETWORK APPLIANCE INC
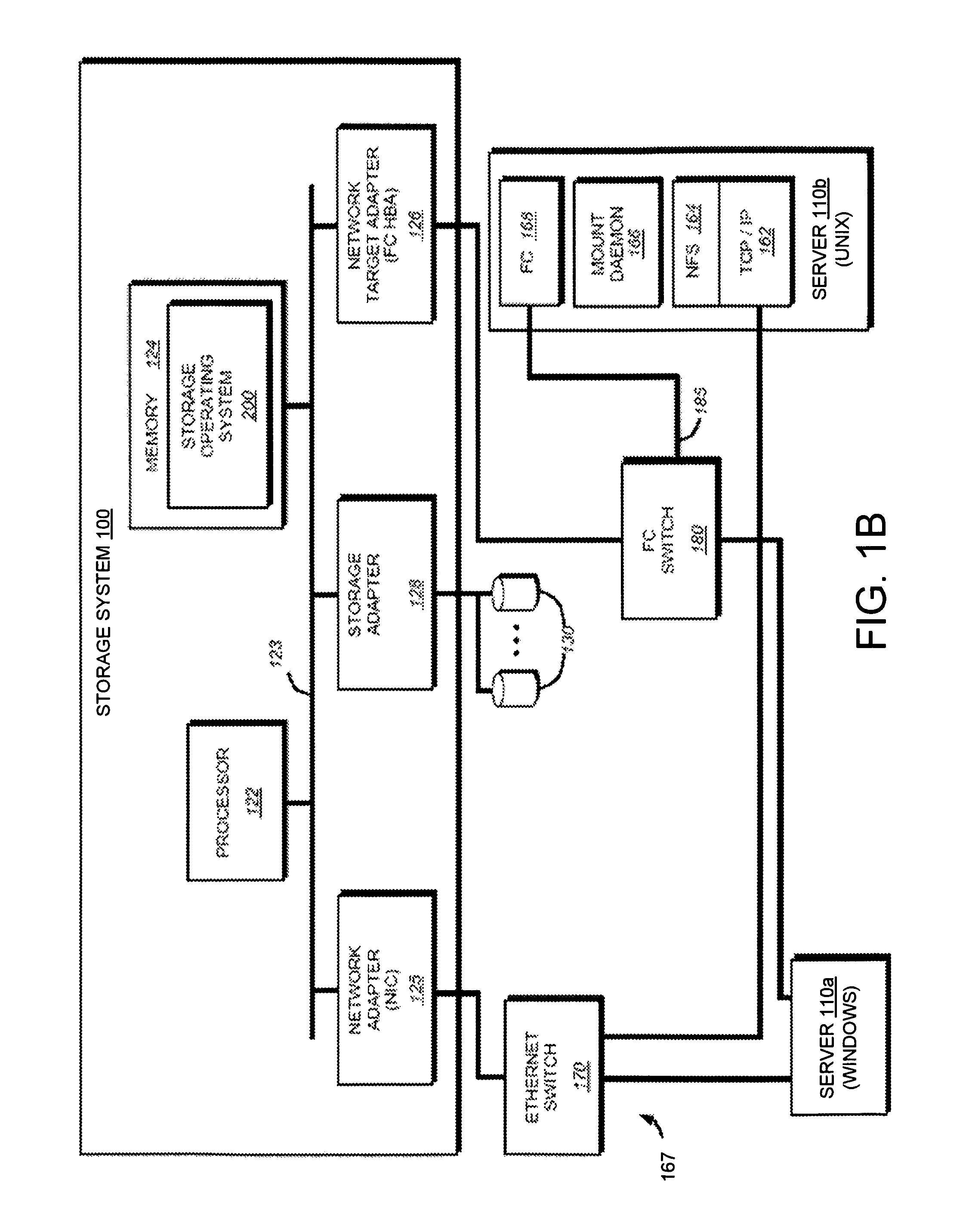
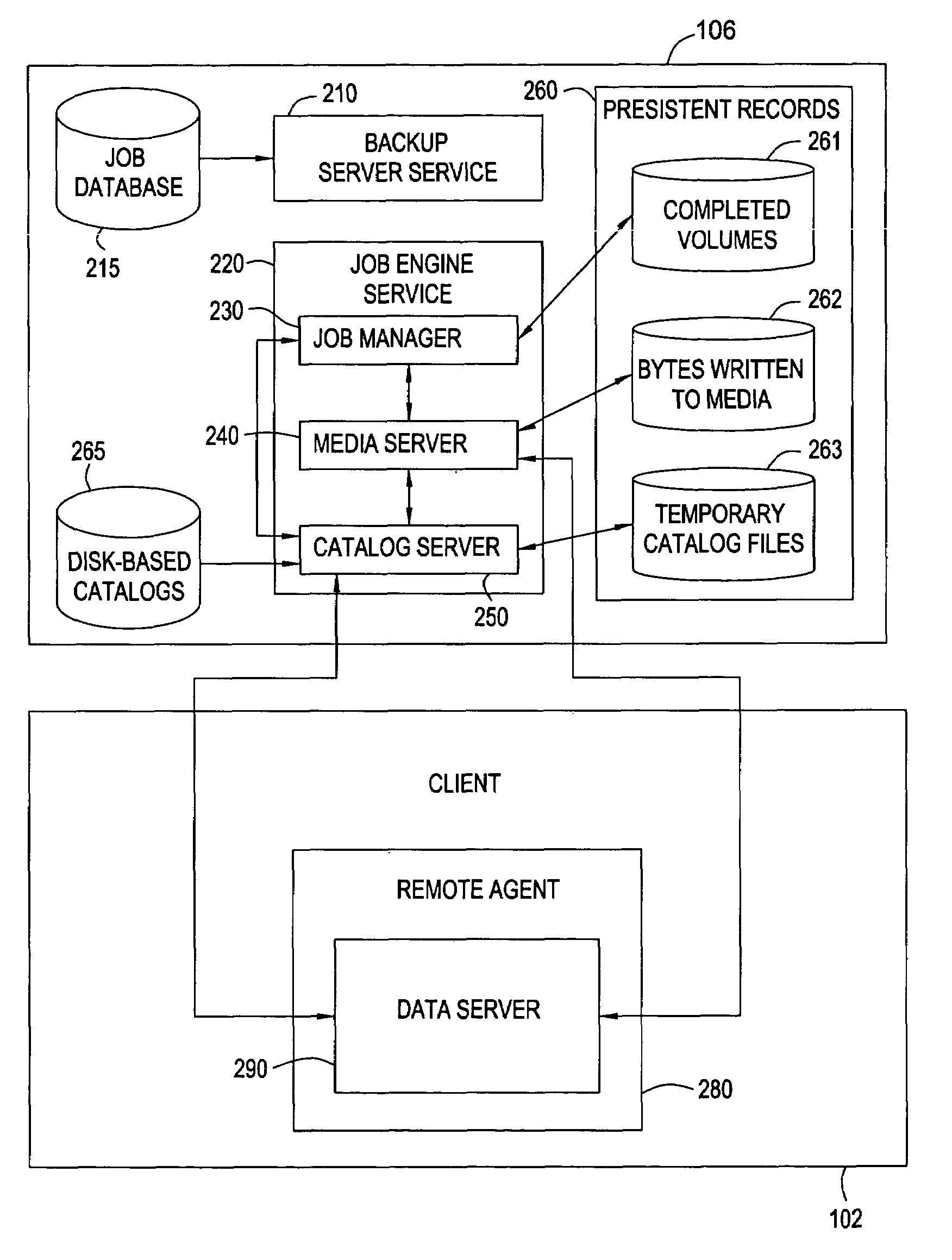
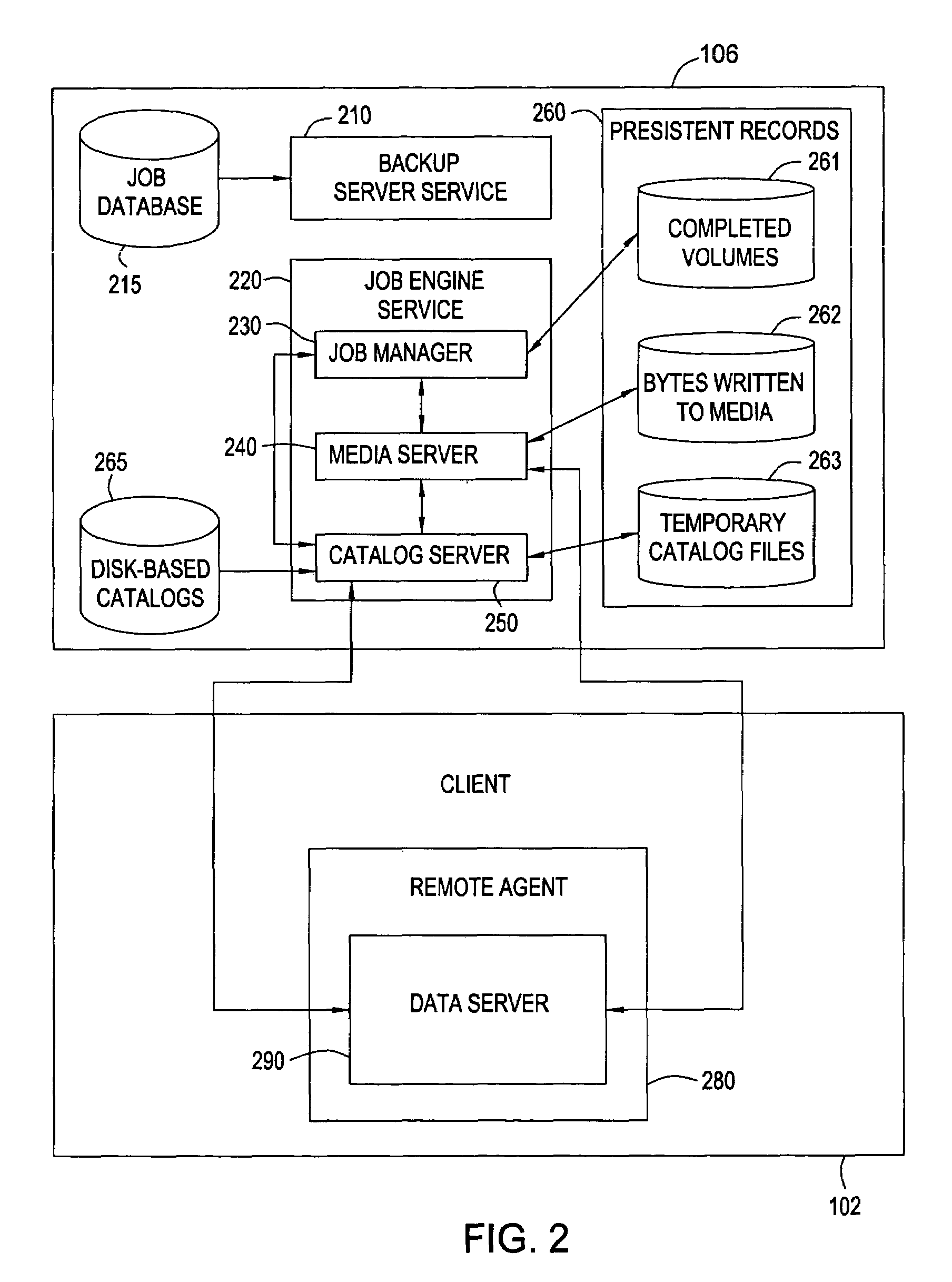
Method and system for completing a backup job that was interrupted during a backup process
ActiveUS7085962B1Memory systemsRedundant hardware error correctionProgramming languageContainer Object
A method and apparatus for completing a backup job that was interrupted during a backup process, including identifying the job that was interrupted during the backup process, using the interrupted job to build a list of one or more volumes that still need to be backed up, generating a disk-based catalog containing a partially backed up volume from the list of volumes that still need to be backed up, retrieving a container object from one or more volumes stored in a client computer, determining whether the container object is listed in the disk-based catalog, determining whether the container object is partially backed up if the container object is listed in the disk based catalog, and writing the data contained in the container object to one or more storage devices if the container object is partially backed up or is not listed in the disk based catalog.
Owner:SYMANTEC OPERATING CORP
Graphical interface method, apparatus and application for opening window of all designated container objects
The invention is carried out in the following environment. The computer system has at least a visual operator interface, an operating system for operating applications within the computer system, and memory for storing at least part, preferably all, of an application. The present invention is of an application, apparatus, and method for selecting multiple container objects whose contents are to be viewed, and displaying in one window the contents of all of the selected container objects, as opposed to displaying one window for objects associated with each selected container object.
Owner:IBM CORP
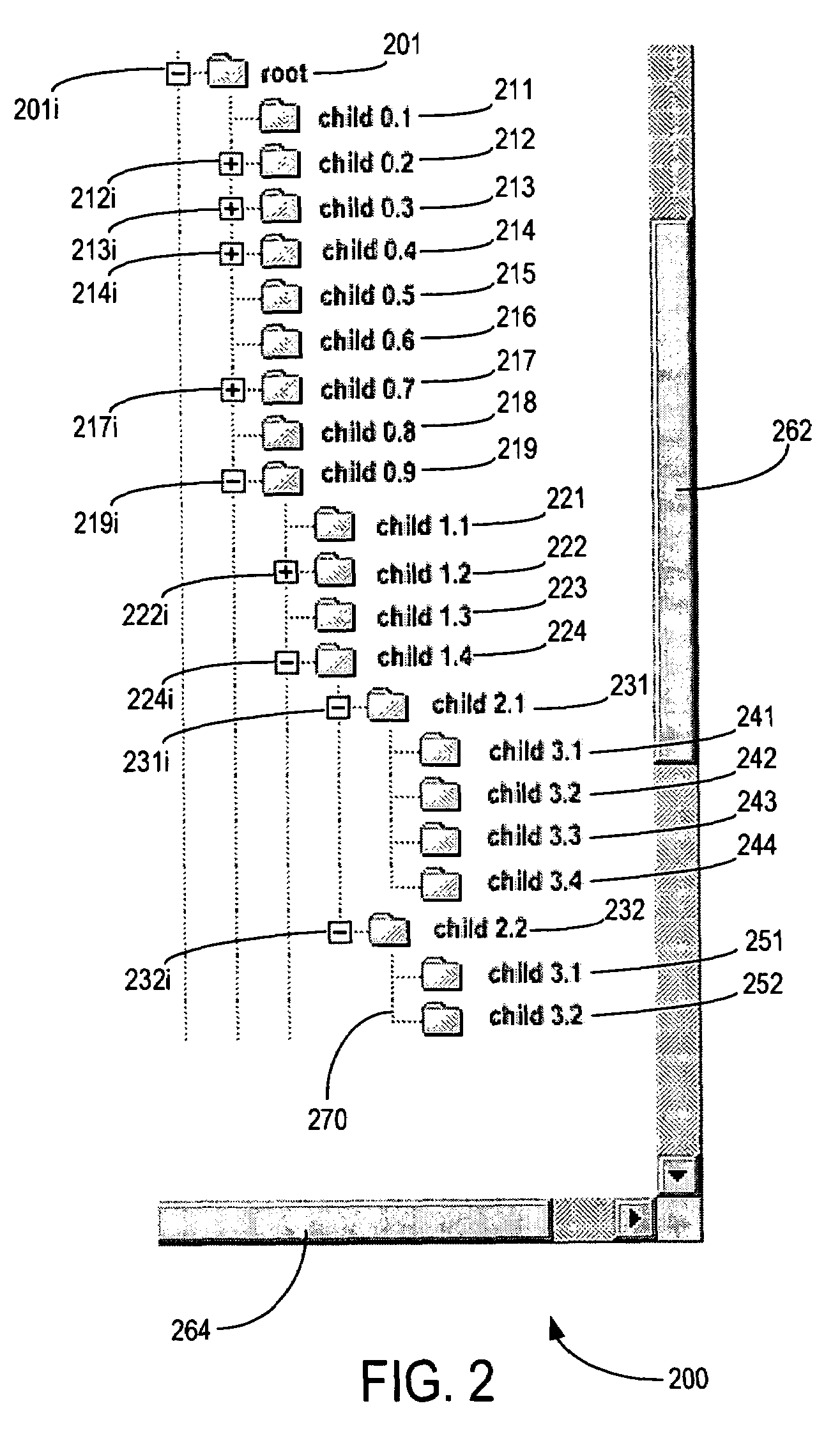
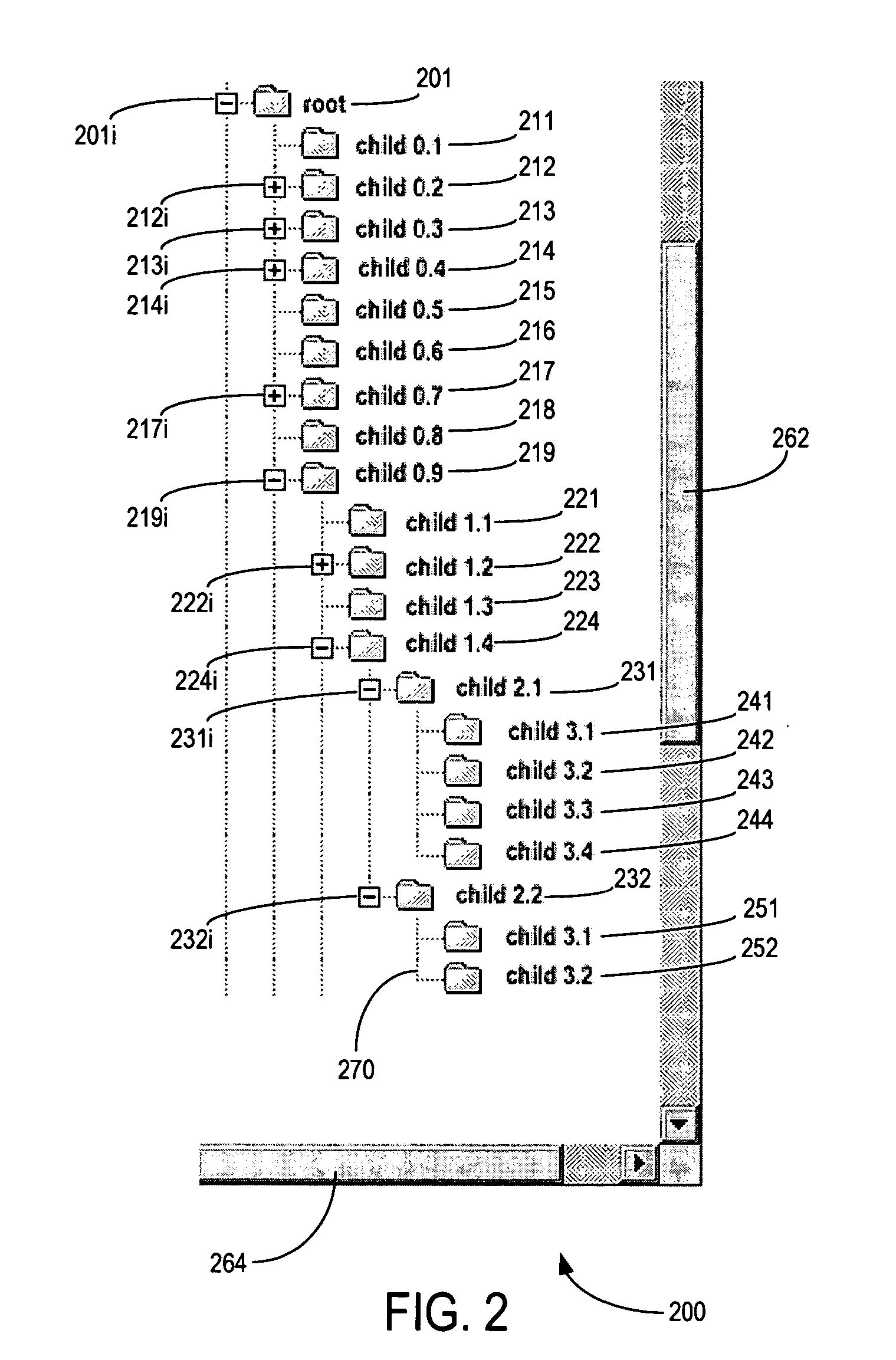
Space-efficient linear hierarchical view and navigation
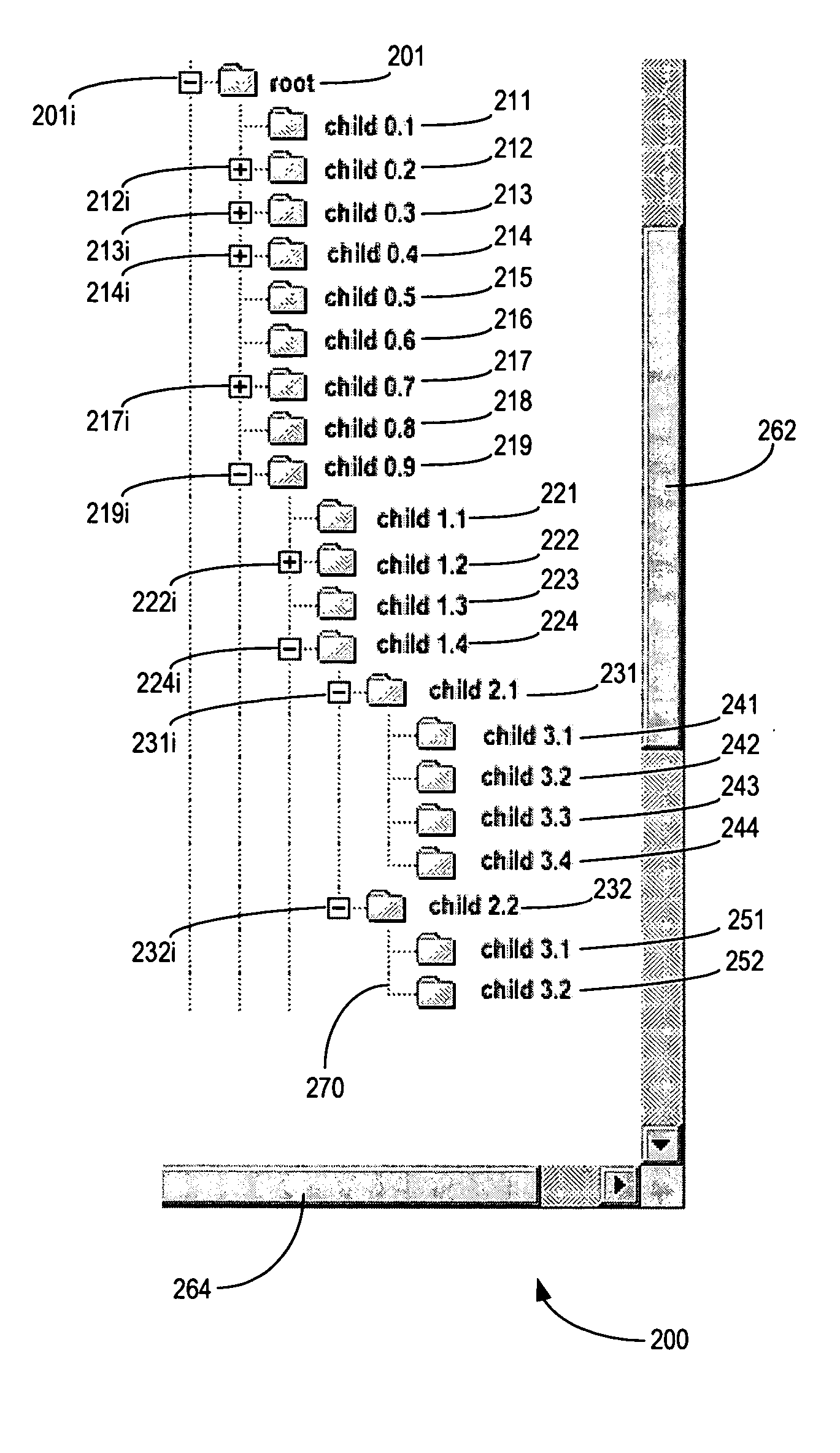
ActiveUS7340690B2Input/output processes for data processingContainer ObjectTheoretical computer science
There is disclosed a method and system for presenting hierarchical objects in a linear view, in which each open container object is split into a pair of bracketing ends, the bracketing ends brackering therebetween any lower level objects contained in the container object. A multi-level hierarchical arrangement of container objects may be represented by multiple pairs of such bracketing ends arranged in a nested configuration. Both bracketing ends of each pair may be configured with a navigation control to close a corresponding container object. The linear hierarchical view may be placed in either a horizontal orientation or a vertical orientation, depending on the nature of the data. A visual characteristic may be used to identify and distinguish between hierarchical levels within the linear hierarchical view. To make more efficient use of available screen space, container objects in the linear hierarchical view may be dynamically collapsible.
Owner:GOOGLE LLC
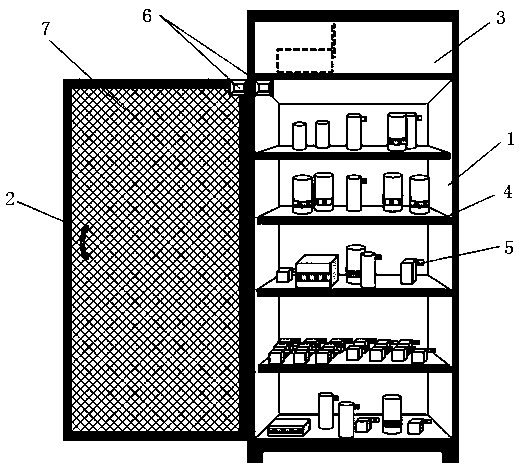
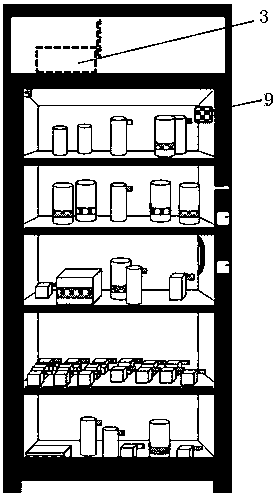
Unmanned retail intelligent container based on RFID (Radio Frequency IDentification) technology, and goods selling method thereof
InactiveCN108510024AWide compatibilityRich varietyCoin-freed apparatus detailsCo-operative working arrangementsContainer ObjectElectromagnetic interference
The invention discloses an unmanned retail intelligent container based on RFID (Radio Frequency IDentification) technology, and a goods selling method thereof. The unmanned retail intelligent container comprises a container body and a mobile phone APP (Application) client side, wherein the container body comprises a container body, a container door, a container terminal control box, a plurality ofcontainer object containing trays and a plurality of RFID electronic tags used for being pasted to commodities; the container door is hinged to the front end of the container body; the top of the container body is provided with the container terminal control box; the plurality of container object containing trays are installed in the container body; the inner wall of the container door is provided with an electromagnetic wave shielding layer; an electromagnetic relay door lock is arranged between the container body and the container door; an RFID antenna and the electromagnetic relay door lock are both connected with the container terminal control box; and the container terminal control box and the mobile phone APP client side are both remotely connected to a data server. By use of the container, the stability of the unmanned retail container is greatly improved, disk reading accuracy is optimized, the compatible range of commodities available for sale is wide, commodity varieties arerich, the limitation of a traditional container that the traditional container only can be compatible with vertical commodities and standardized commodities can be overcome, and electromagnetic interference resistance performance is high.
Owner:JIANGSU JUNYI INTERNET OF THINGS
Methods and apparatus for creating and transforming graphical constructs
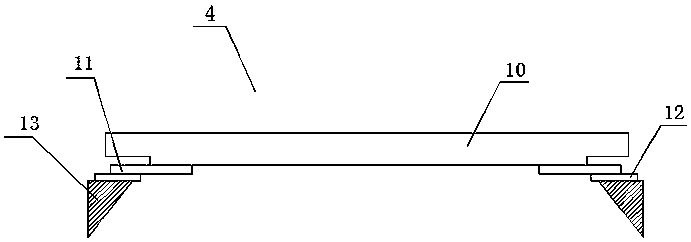
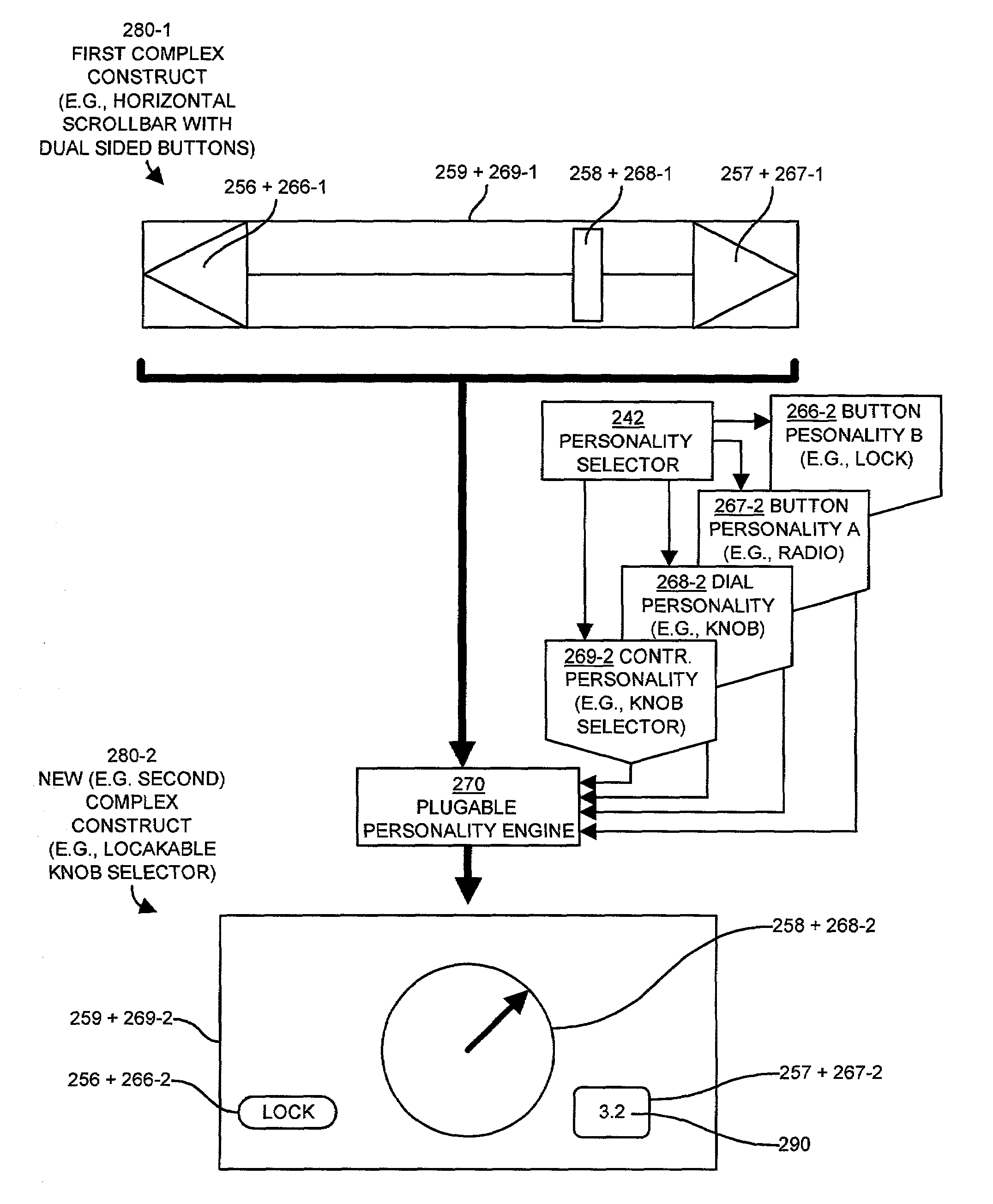
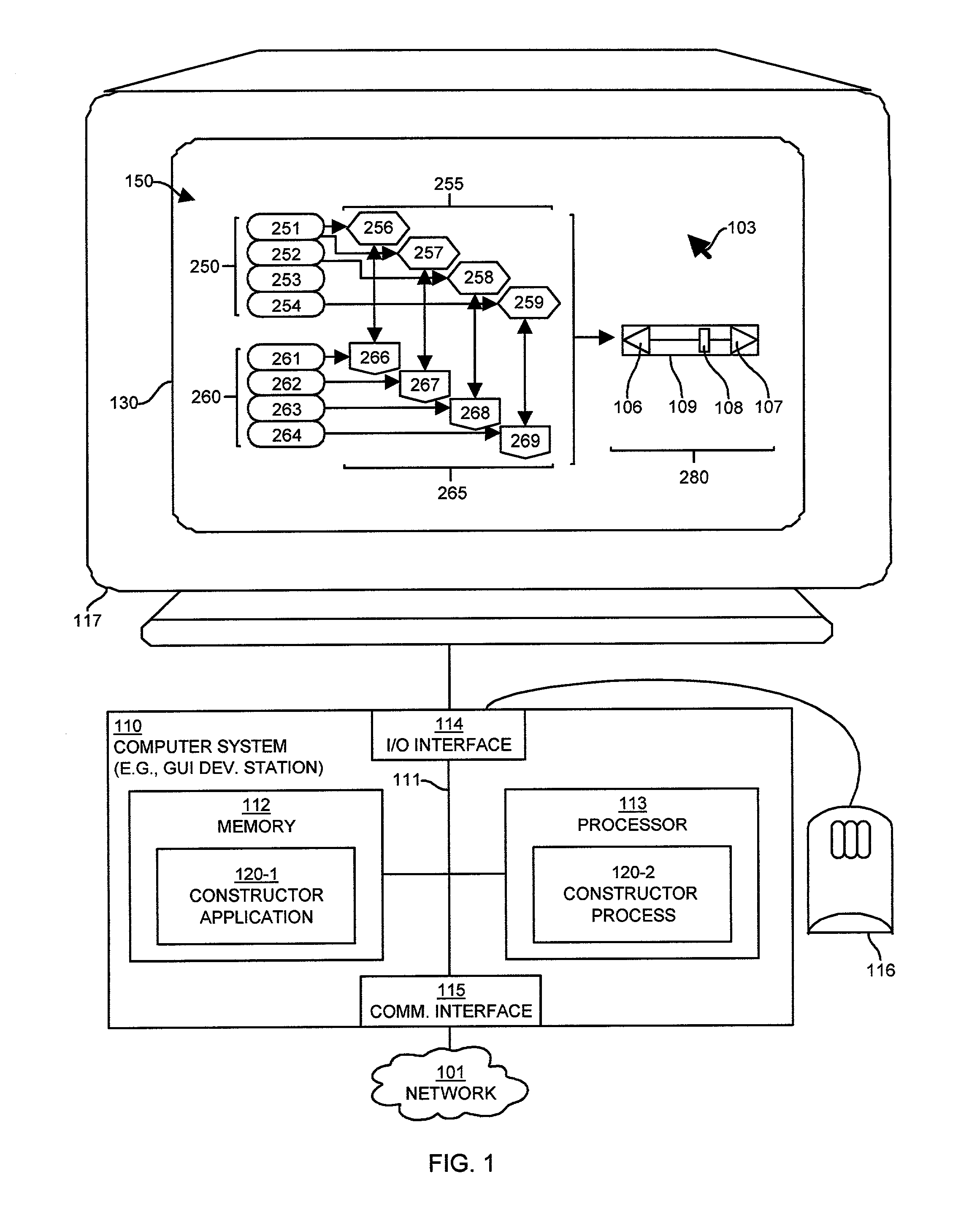
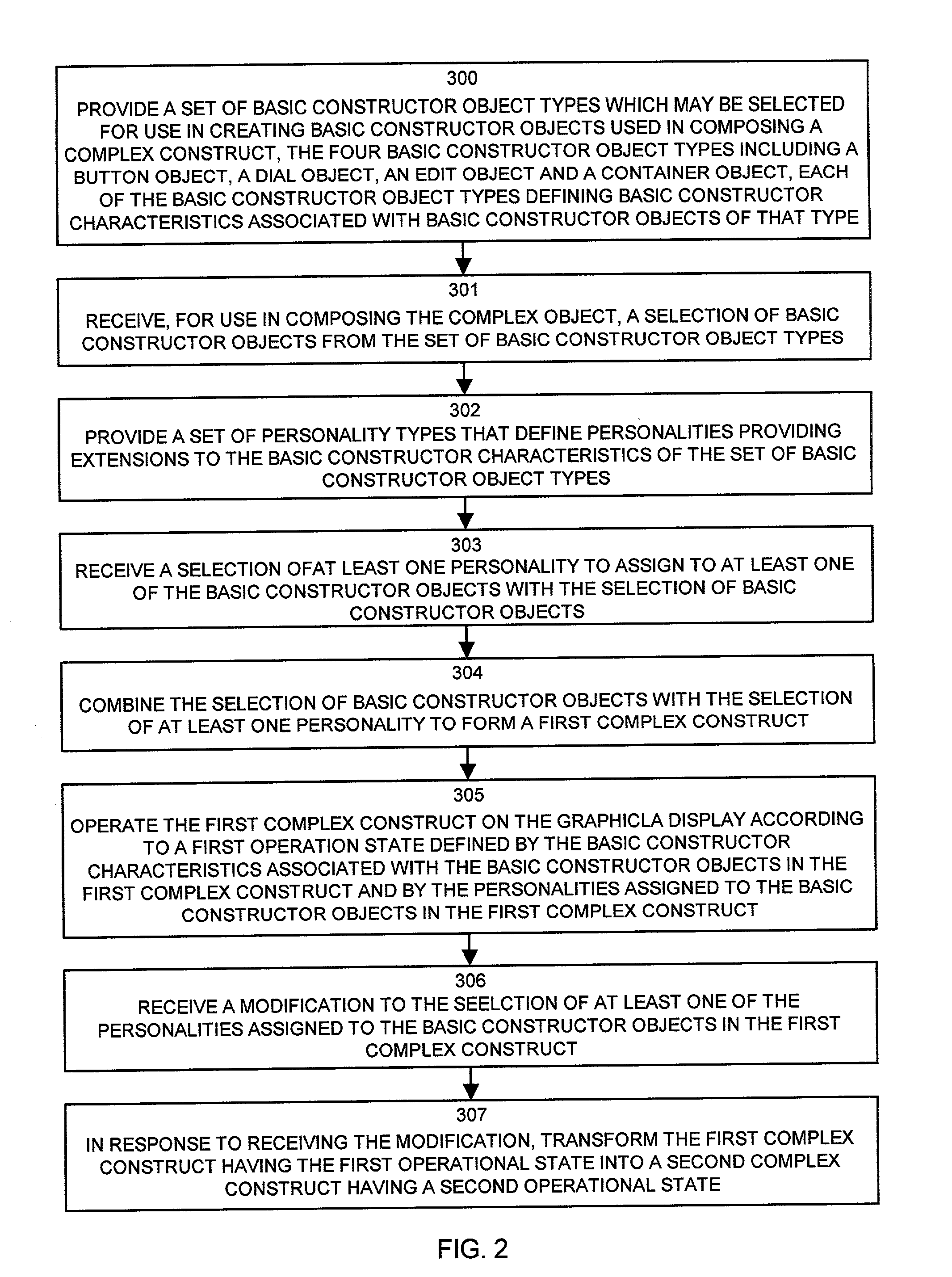
InactiveUS7024633B1Minimal requirementEasy to useVisual/graphical programmingProgram controlGraphicsContainer Object
Mechanisms and techniques provide a system for composing a complex constructs for use on a graphical display of a computerized device. The system receives a selection of basic constructor objects for use in the complex object. The basic constructor objects are chosen from a set of basic constructor object types including a button object type, a dial object type, an edit object type, and a container object type. The systems also receives a selection of one or more personalities to assign to the basic constructor objects. The personalities define extensions to basic constructor object operation and define a view for the object when rendered on an interface. The system combines the personalities and the basic constructor objects to define complex constructs such as menus, a scrollbars and the like. Personalities can be modified to alter the complex construct from one operational state to another.
Owner:ORACLE INT CORP
Method for enabling a compiler or interpreter to use identifiers found at run time in a map container object in a manner similar or identical to identifiers declared at compile time
InactiveUS6993744B2Specific program execution arrangementsMemory systemsContainer ObjectApplication programming interface
A method for enabling a compiler or interpreter to use identifiers found at run time in a map container object in a manner similar or identical to identifiers declared at compile time is presented. More specifically, names defined in a map container object during the execution of a program are treated in a manner similar or identical to names defined in a programming namespace at compilation (or interpretation) time. The map container is applied to encapsulate a non-programming namespace application programming interface (API), so that names defined in a non-programming namespace can be treated in a manner similar or identical to names defined in a programming namespace at compilation (or interpretation) time.
Owner:F POSZAT HU
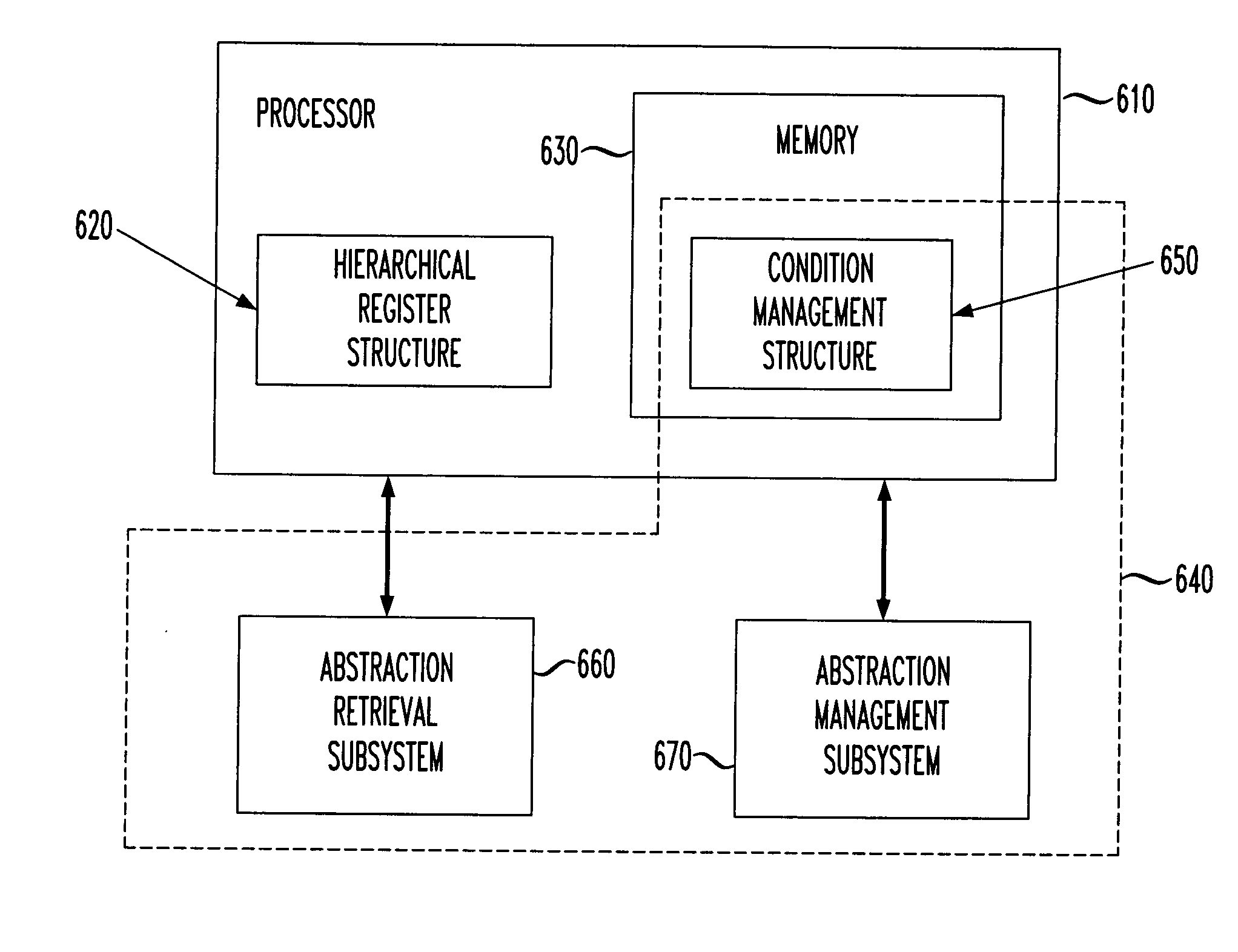
Condition management system and a method of operation thereof
InactiveUS7389496B2Reduce developmentReduce maintenanceProgram initiation/switchingDigital computer detailsContainer ObjectDatabase
For use with a processor employing a hierarchical register consolidation structure (HRCS), a condition management system and method of operation thereof. In one embodiment, the system includes a condition management structure (CMS) that abstracts groups of status indicators associated with the HRCS into a tree of hierarchical container objects and element objects. Each of the container objects is associated with at least one of the element objects and linked to a single parent object, and each of the element objects configured to represent at least one of the status indicators and linked to a single child object. The system further includes an abstraction retrieval subsystem that employs the CMS to traverse the HRCS to determine a condition of at least one of the status indicators, and an abstraction management subsystem that employs the CMS to control a propagation of selected ones of the status indicators through the HRCS.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Method used for generating CIM model describing power grid change in designated time slot and system thereof
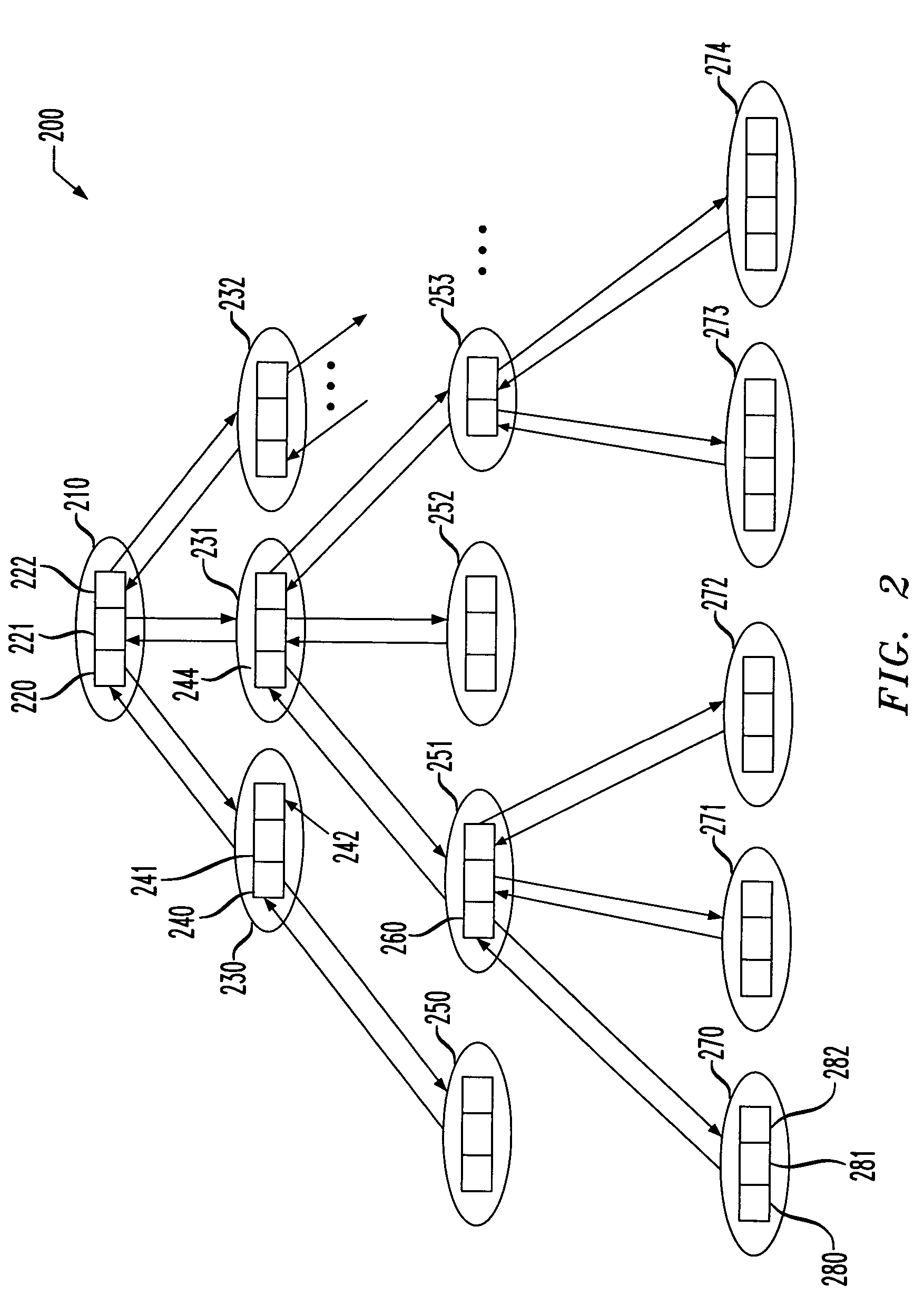
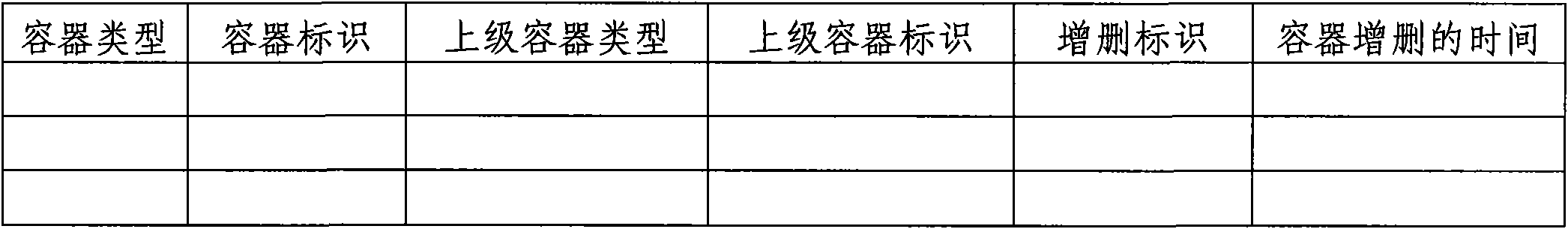
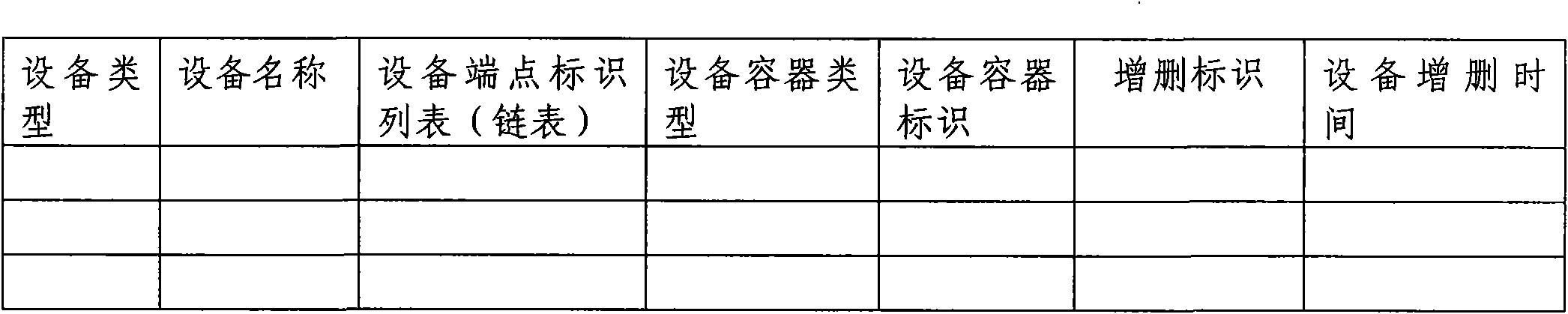
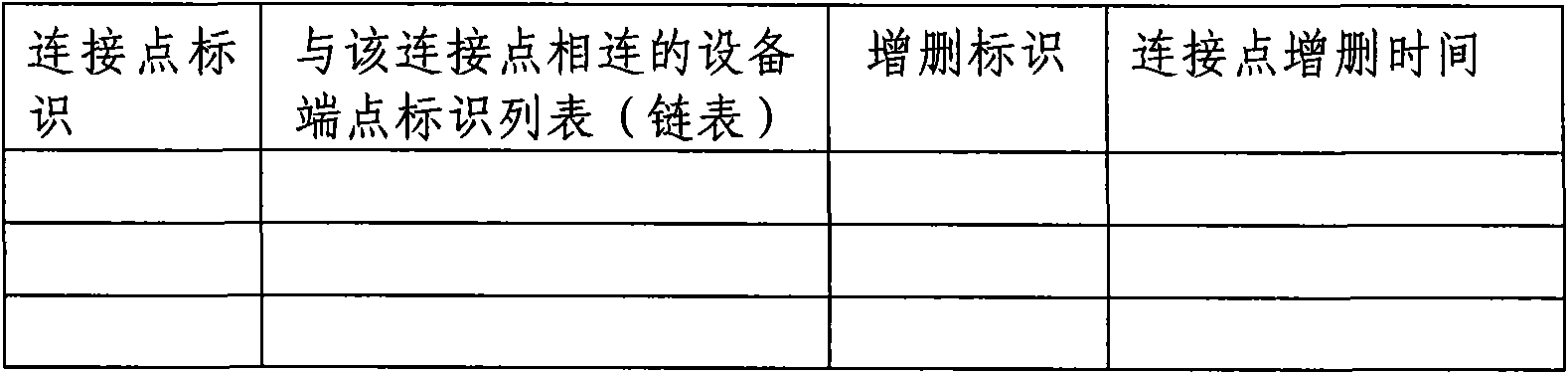
ActiveCN101930481ASpecial data processing applicationsAc network circuit arrangementsContainer ObjectPoint object
The invention relates to a method used for generating CIM model describing power grid model change in designated time slot. The invention belongs to the power system technical field. The method includes the following steps: an initial CIM model is imported, and a hierarchical relationship structure library and a topology connection relationship structure library are established in a buffer area; change conditions of power grid model objects (container object, equipment object and topology connection point object) in designated time slot are input; all the record sorts in an object information list are subject to addition and deletion and sequencing is carried out, thus forming an addition deletion object index table; the power grid model objects (the container object, equipment object and topology connection point object) in the buffer area are sequentially updated according to the addition deletion object index table; and a CIM model XML file describing power grid model change in the designated time slot is generated by the CIM XML grammatical rule according to the hierarchical relationship structure library and topology connection relationship structure library which have time property in the buffer area.
Owner:EAST CHINA GRID
Condition management system and a method of operation thereof
InactiveUS20050005089A1Simple interfaceReduce developmentProgram initiation/switchingDigital computer detailsContainer ObjectDatabase
For use with a processor employing a hierarchical register consolidation structure (HRCS), a condition management system and method of operation thereof. In one embodiment, the system includes a condition management structure (CMS) that abstracts groups of status indicators associated with the HRCS into a tree of hierarchical container objects and element objects. Each of the container objects is associated with at least one of the element objects and linked to a single parent object, and each of the element objects configured to represent at least one of the status indicators and linked to a single child object. The system further includes an abstraction retrieval subsystem that employs the CMS to traverse the HRCS to determine a condition of at least one of the status indicators, and an abstraction management subsystem that employs the CMS to control a propagation of selected ones of the status indicators through the HRCS.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Space-efficient linear hierarchical view and navigation
ActiveUS20060010399A1Digital computer detailsInput/output processes for data processingContainer ObjectTheoretical computer science
There is disclosed a method and system for presenting hierarchical objects in a linear view, in which each open container object is split into a pair of bracketing ends, the bracketing ends brackering therebetween any lower level objects contained in the container object. A multi-level hierarchical arrangement of container objects may be represented by multiple pairs of such bracketing ends arranged in a nested configuration. Both bracketing ends of each pair may be configured with a navigation control to close a corresponding container object. The linear hierarchical view may be placed in either a horizontal orientation or a vertical orientation, depending on the nature of the data. A visual characteristic may be used to identify and distinguish between hierarchical levels within the linear hierarchical view. To make more efficient use of available screen space, container objects in the linear hierarchical view may be dynamically collapsible.
Owner:GOOGLE LLC
System and method for multilevel secure object management
ActiveUS8683602B2Improve the level ofEasy accessKey distribution for secure communicationDigital data processing detailsContainer ObjectSecure transmission
A system and method for secure transport of data, the method comprising: sharing of key information with a key distributor, wherein the key information is for enabling decryption of first and second encrypted data, the key distributor being for making one or more decryption keys available to an authorized user; creating a container object, the container object comprising: first encrypted data having a first encryption based on at least a part of said key information; second encrypted data having a second encryption based on at least a part of said key information, wherein the first encryption is different to the second encryption; and metadata relating to the first encrypted data and the second encrypted data; and sending the container object to a data store or otherwise making the container object available, to allow user access to said data container object.
Owner:THALES HLDG UK
Device driver for use in a data storage system
ActiveUS9256383B2Simple and efficient componentSimple and robust and efficient implementationMemory architecture accessing/allocationInput/output to record carriersContainer ObjectObject store
A device driver includes an aggregator aggregating data blocks into one or more container objects suited for storage in an object store; and a logger for maintaining in at least one log file for each data block an identification of a container object wherein the data block is stored with an identification of the location of the data block in the container object.
Owner:WESTERN DIGITAL TECH INC
Method for achieving multi-application of intelligent secret key equipment
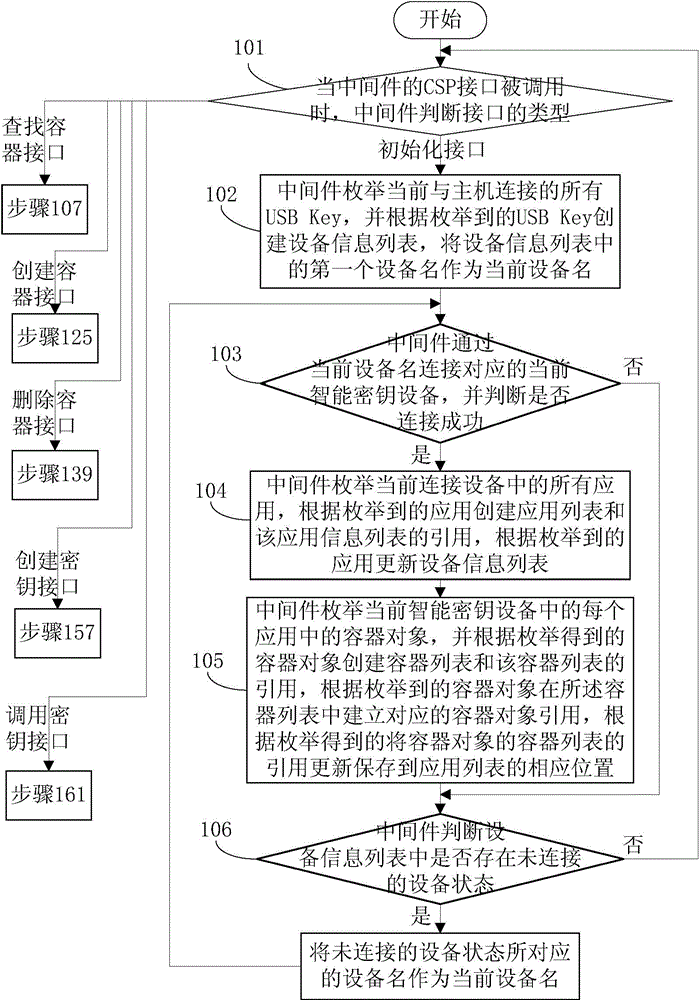
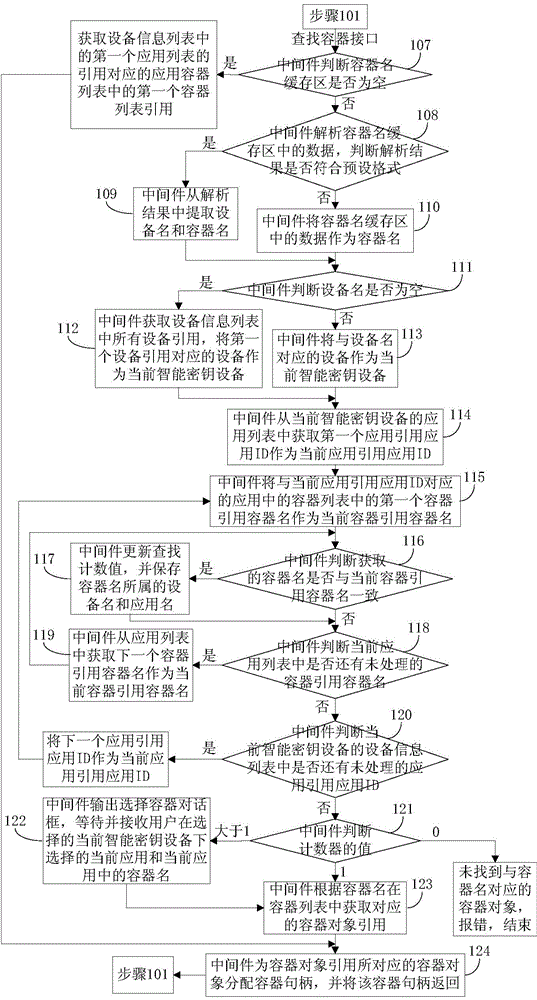
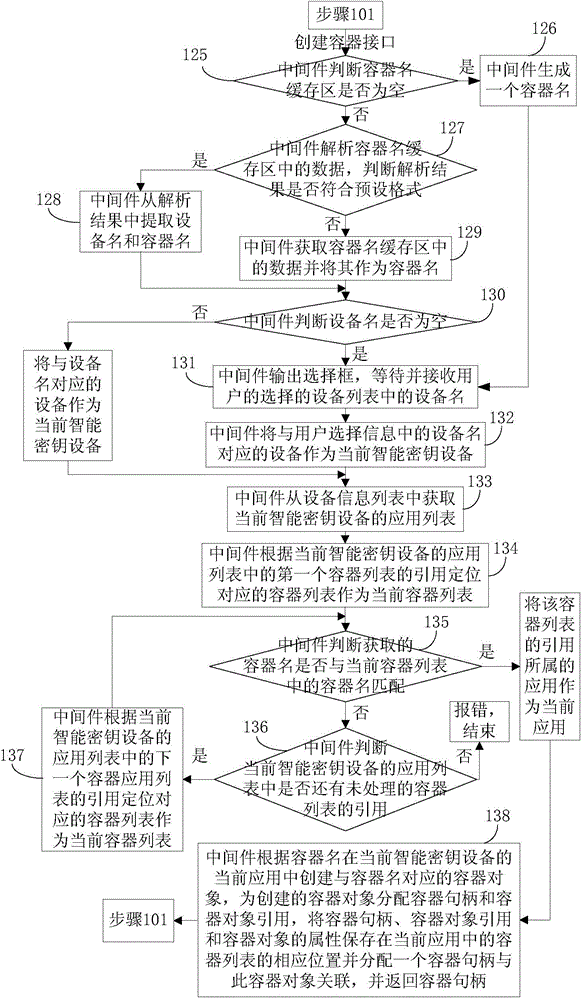
ActiveCN104468116AKey distribution for secure communicationUser identity/authority verificationContainer ObjectMiddleware
The invention discloses a method for achieving multi-application of intelligent secret key equipment. the method includes the steps that when an initialized interface of a middleware is called, an equipment information list, an application list and a container list are built; if a built container interface is called, the middleware builds container objects, distributes container sentence handles and correspondingly stores the container sentence handles to the corresponding positions of the container list, and the container sentence handles are returned; if a built secret key interface is called, the middleware builds secret key objects, distributes corresponding secret key IDs, stores the secret key IDs and secret key functions to the secret key objects, stores the secret key IDs to the container objects, and distributes one secret key handle and stores the secret key handle, and the secret key handle is returned; if a deleting container interface is called, the middleware obtains corresponding container object quotations according to equipment names and container names, deleting commands are generated according to the container object quotations and sent to the corresponding intelligent secret key equipment, after the intelligent secret key equipment successfully deletes the corresponding container objects according to the deleting commands, the middleware removes the corresponding container information from the container list.
Owner:FEITIAN TECHNOLOGIES
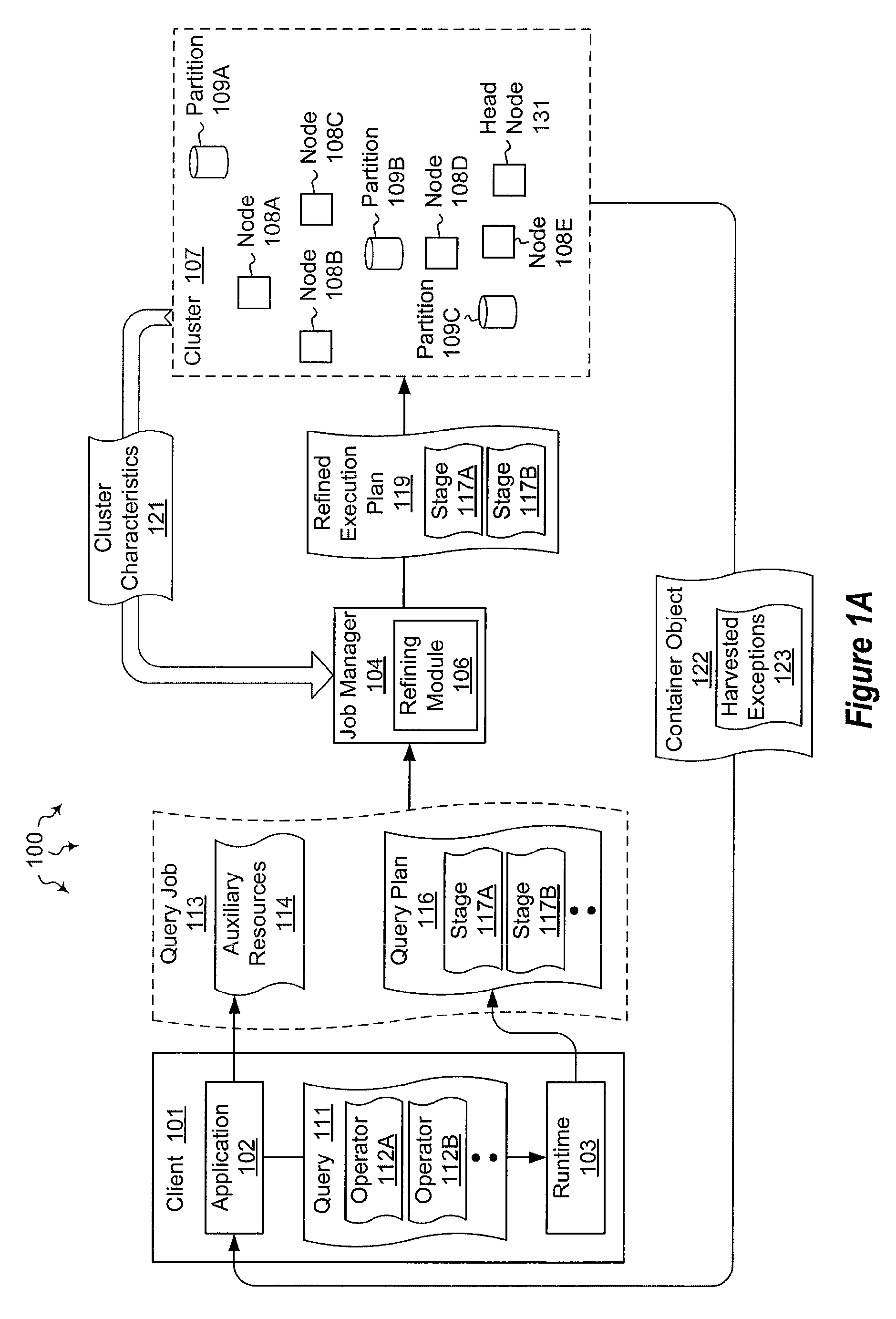
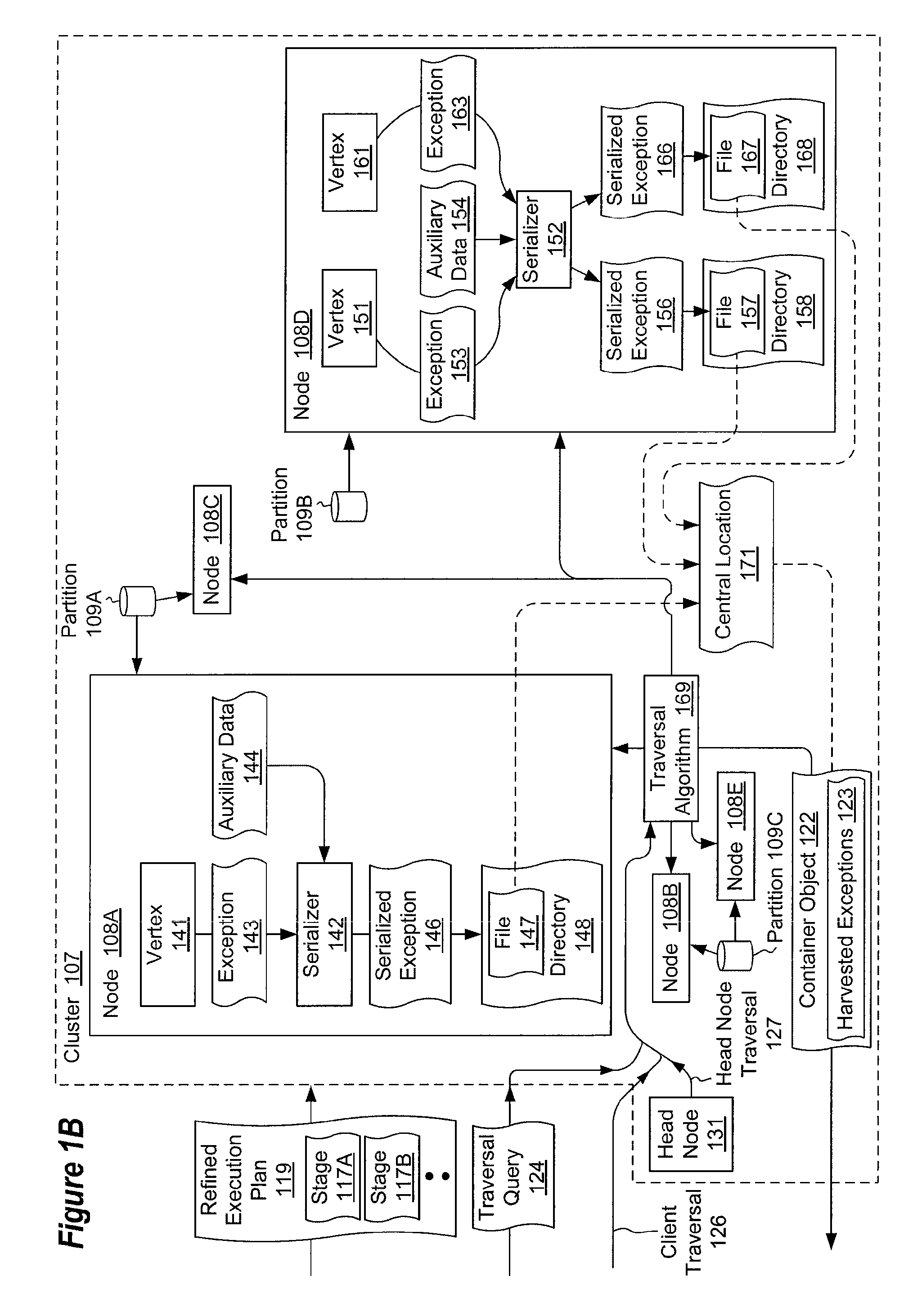
Propagating unobserved exceptions in distributed execution environments
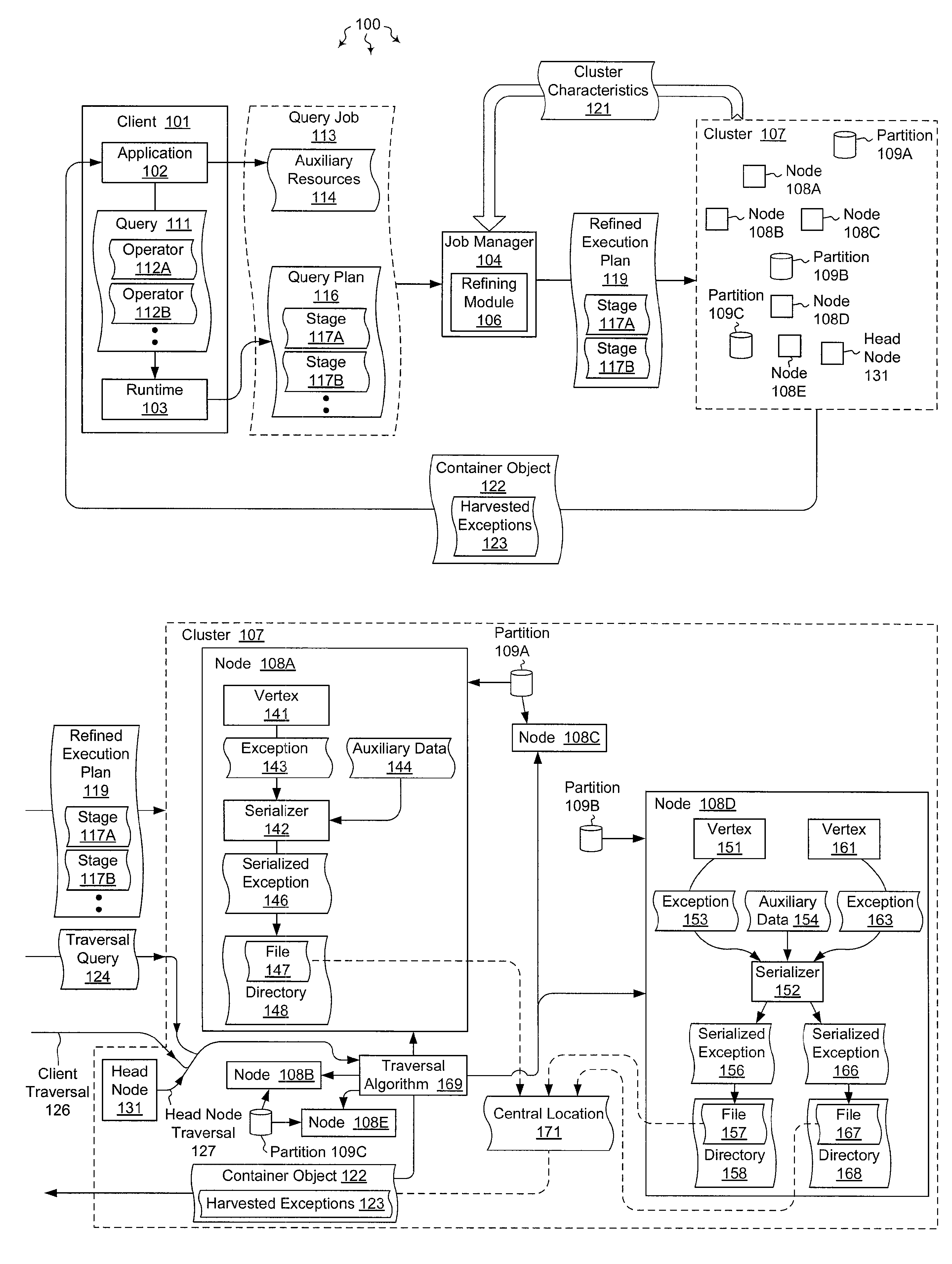
The present invention extends to methods, systems, and computer program products for propagating unhandled exceptions in distributed execution environments, such as clusters. A job (e.g., a query) can include a series of computation steps that are executed on multiple compute nodes each processing parts of a distributed data set. Unhandled exceptions can be caught while computations are running on data partitions of different compute nodes. Unhandled exception objects can be stored in a serialized format in a compute node's local storage (or an alternate central location) along with auxiliary details such as the data partition being processed at the time. Stored serialized exception objects for a job can be harvested and aggregated in a single container object. The single container object can be passed back to the client.
Owner:MICROSOFT TECH LICENSING LLC
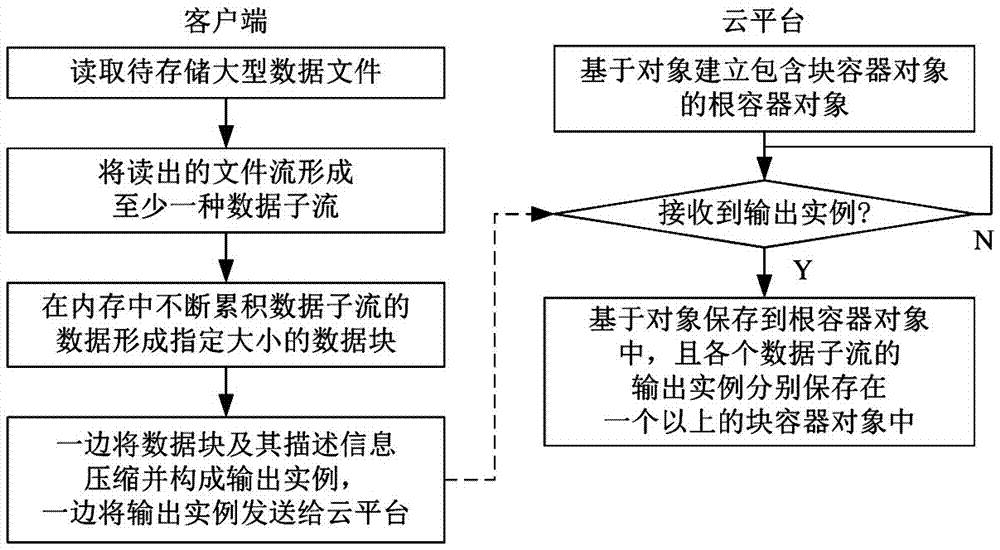
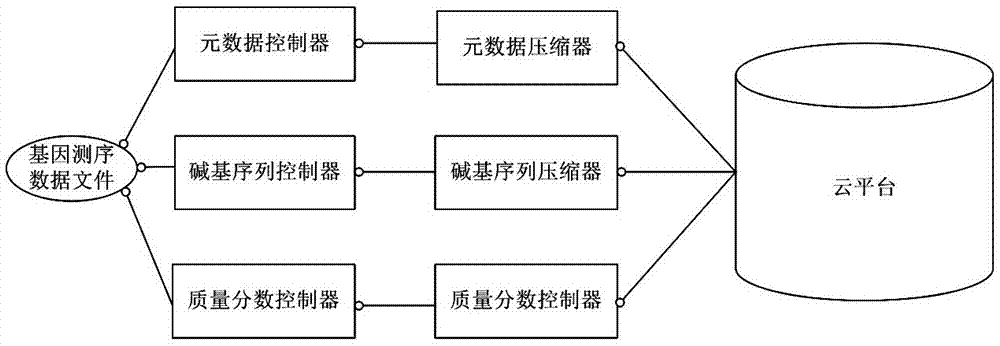
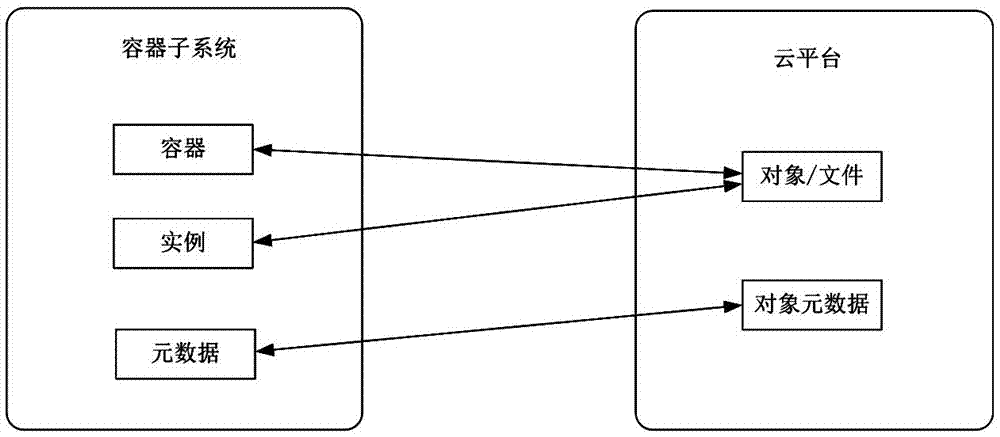
An object storage-based large-scale data cloud storage method
ActiveCN106991134ASave time and costReduce economic costsFile access structuresTransmissionData compressionObject based
The invention provides an object storage-based large-scale data cloud storage method. The method comprises the steps that a client reads to-be stored large-scale data files and forms at least one kind of data sub-stream, forms data blocks with a fixed size through continuous accumulation in memory, compresses the data blocks and description information thereof to form output examples, and sends the output examples to a cloud platform; the cloud platform establishes root container objects containing block container objects, receives the output examples sent by the client for the to-be stored large-scale data files and stores the received output examples into the corresponding root container objects as objects, wherein output examples of each data sub-flow are stored in more than one block container object. The method is based on data streams, data blocks and concurrent compression, supports synchronization of data compression and transmission to cloud and supports targeted compression schemes for data blocks of different data sub-streams; the method can greatly save time cost of data uploading and economic cost of data storage.
Owner:GENETALKS BIO TECH CHANGSHA CO LTD
Signing method
ActiveCN103368746AImprove interoperabilityUser identity/authority verificationContainer ObjectInterconnection
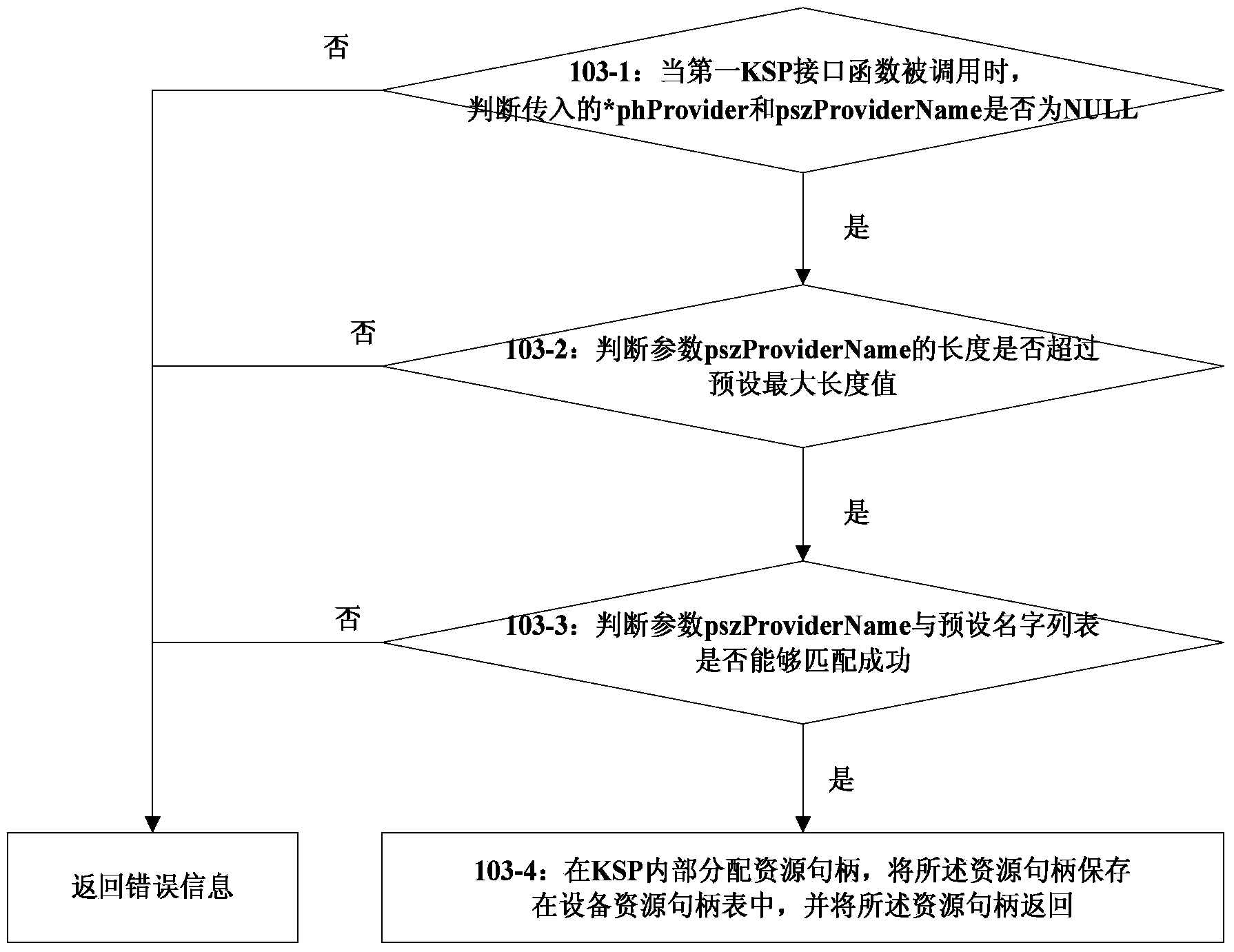
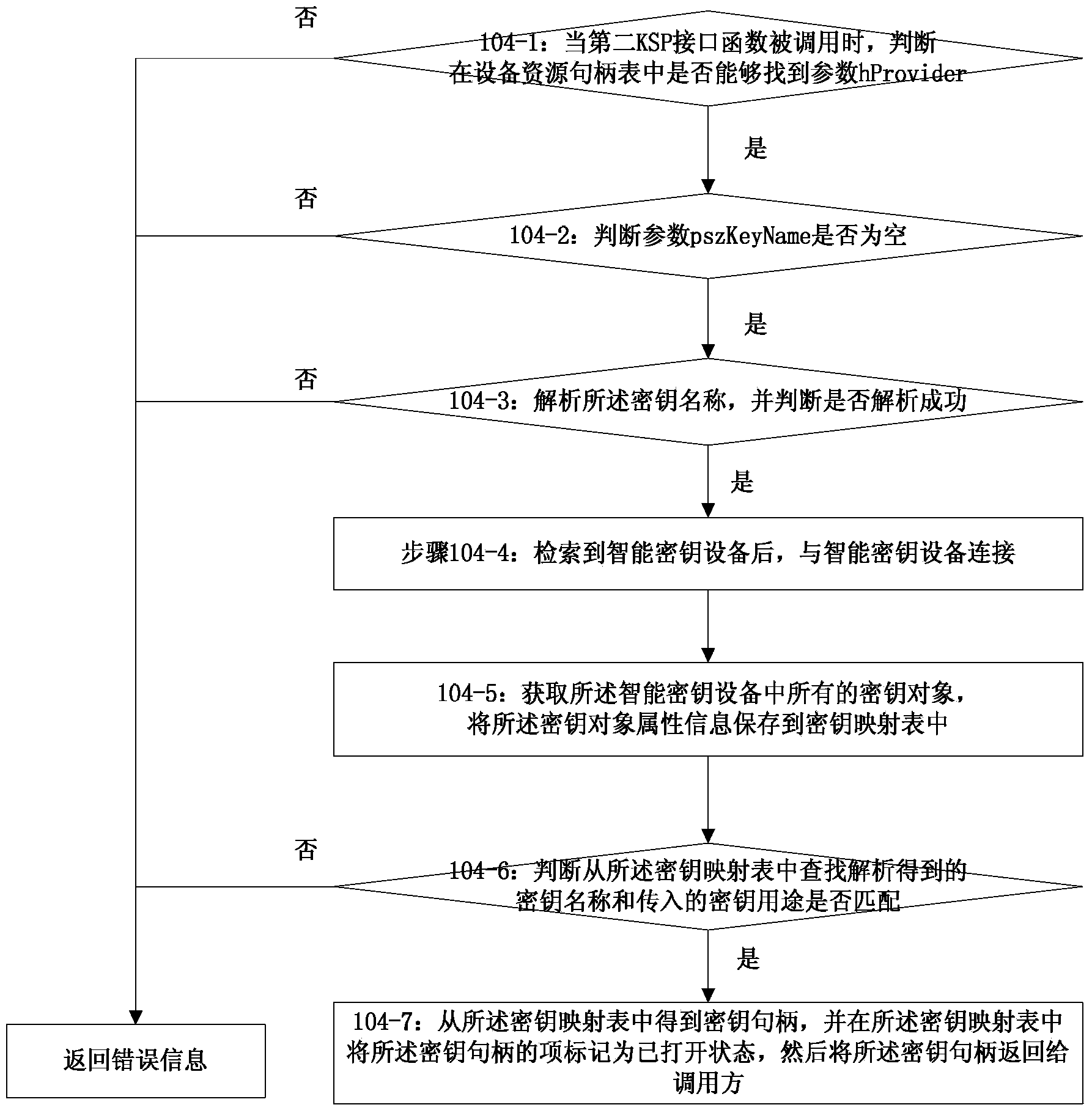
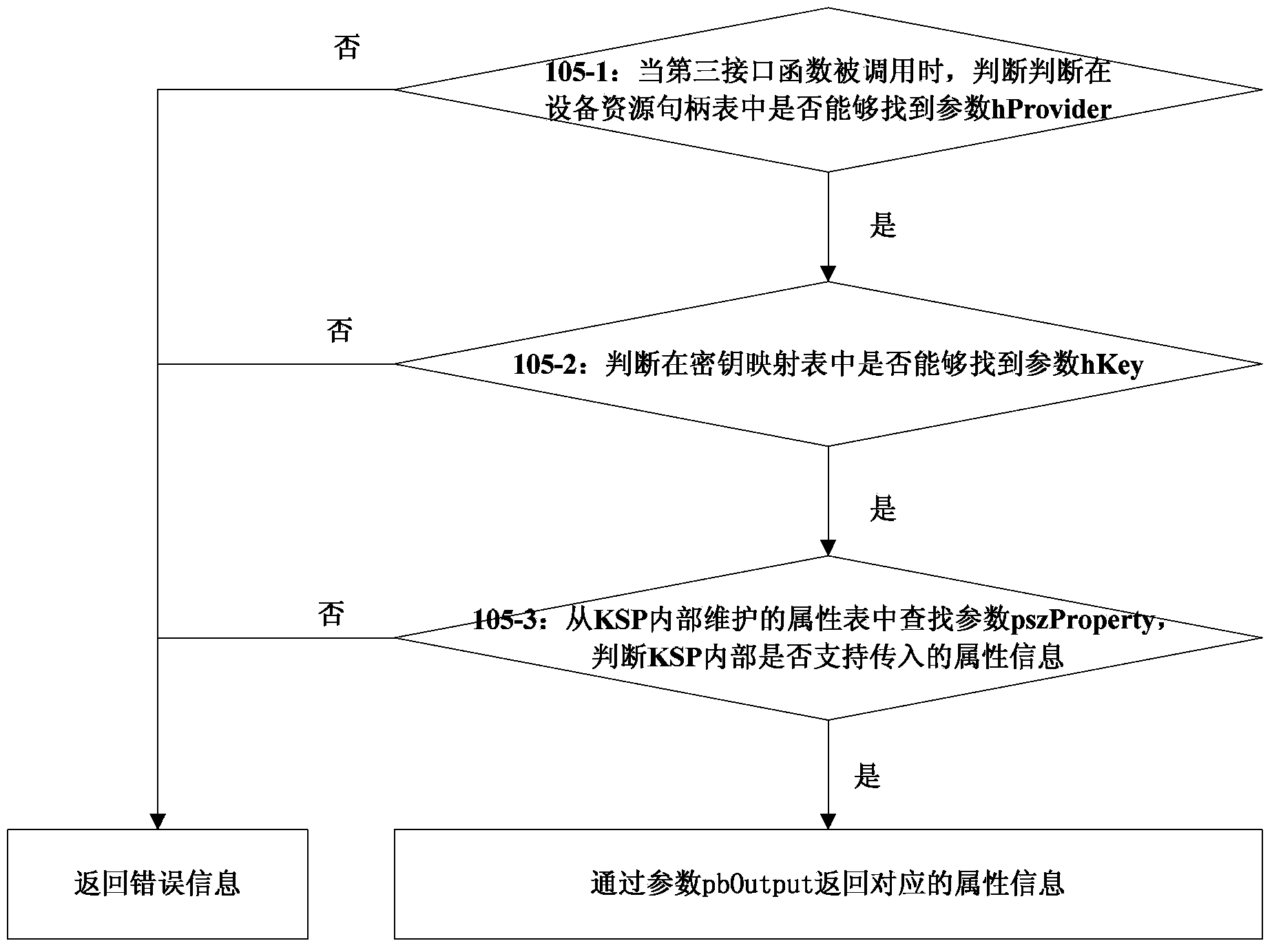
The invention discloses a signing method, and belongs to the information security field. The method comprises the following steps of: when a first CSP (Cryptography Service Provider) interface function is called, returning back a container object handle; when a second CSP interface function is called, generating a key in an intelligent key device, creating a key object according to the attribute of the container object and the introduced key parameter; when a first KSP (Key Storage Provider) interface function is called, returning back a resource handle; when a second KSP interface function is called, returning back a key handle; when a third KSP interface function is called, returning back the needed key attribute; when a fourth KSP interface function is called, executing the signing operation by the key appointed by the key handle. By the technical scheme of the invention, interconnection of the KSP and the CSP can be realized, thus, the KSP can execute the signing operation by the key generated in the CSP.
Owner:FEITIAN TECHNOLOGIES
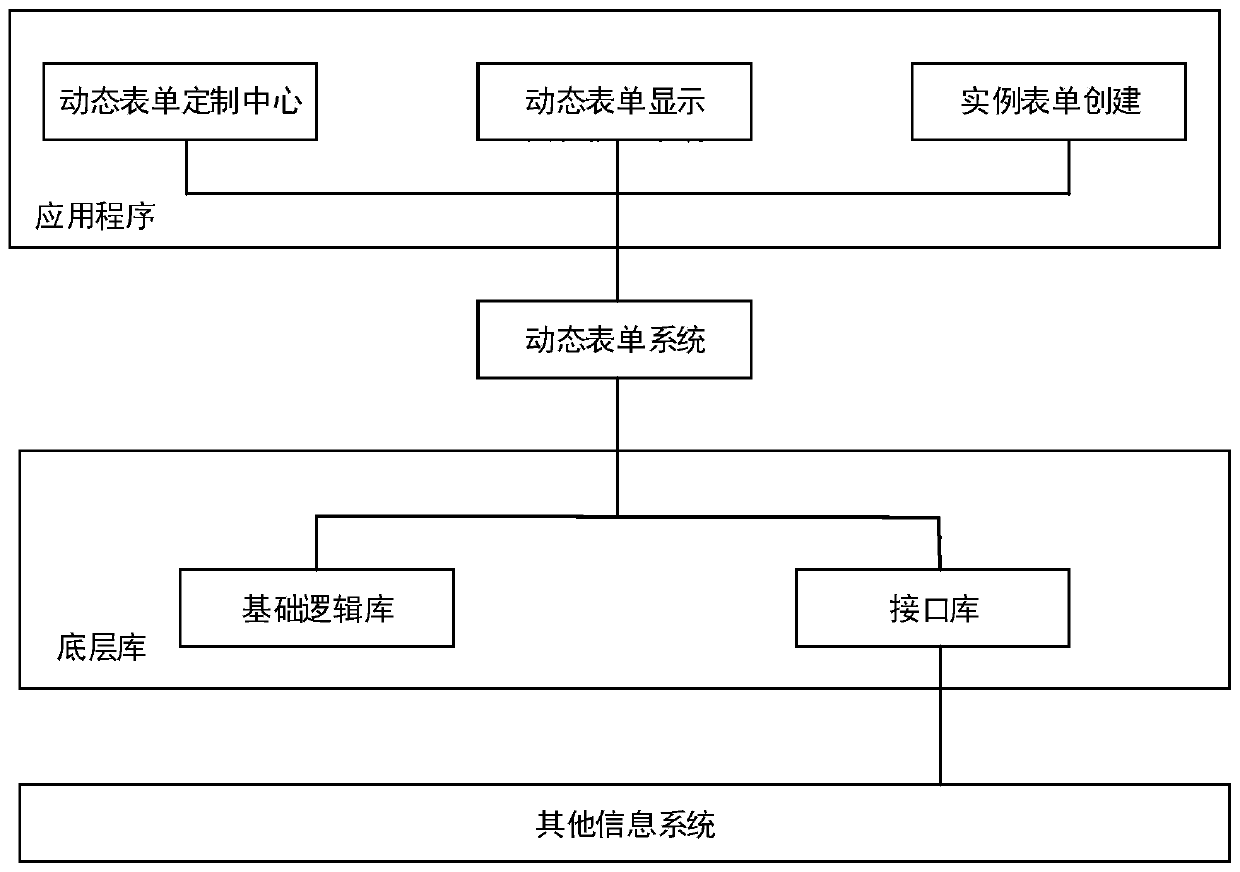
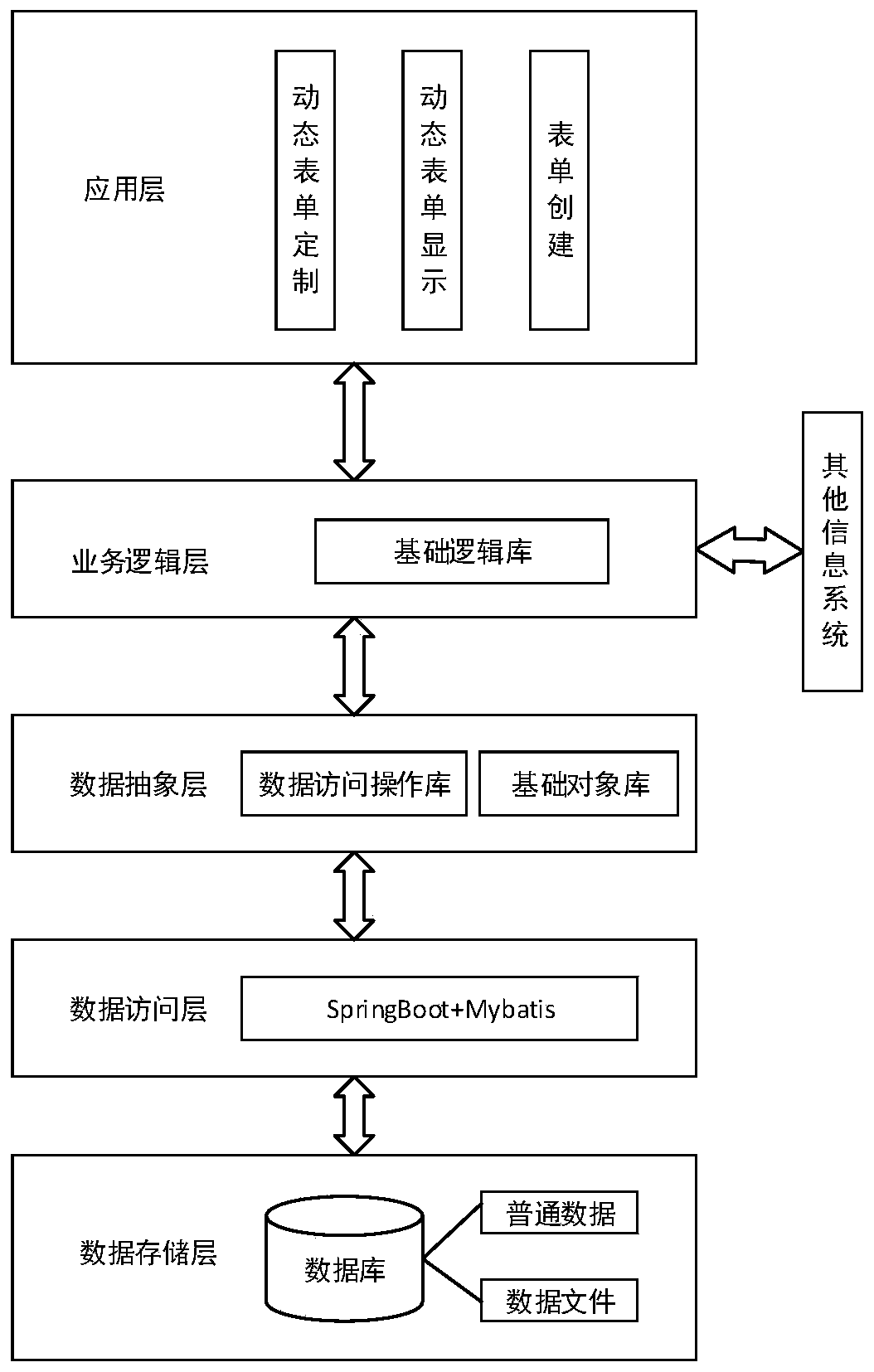
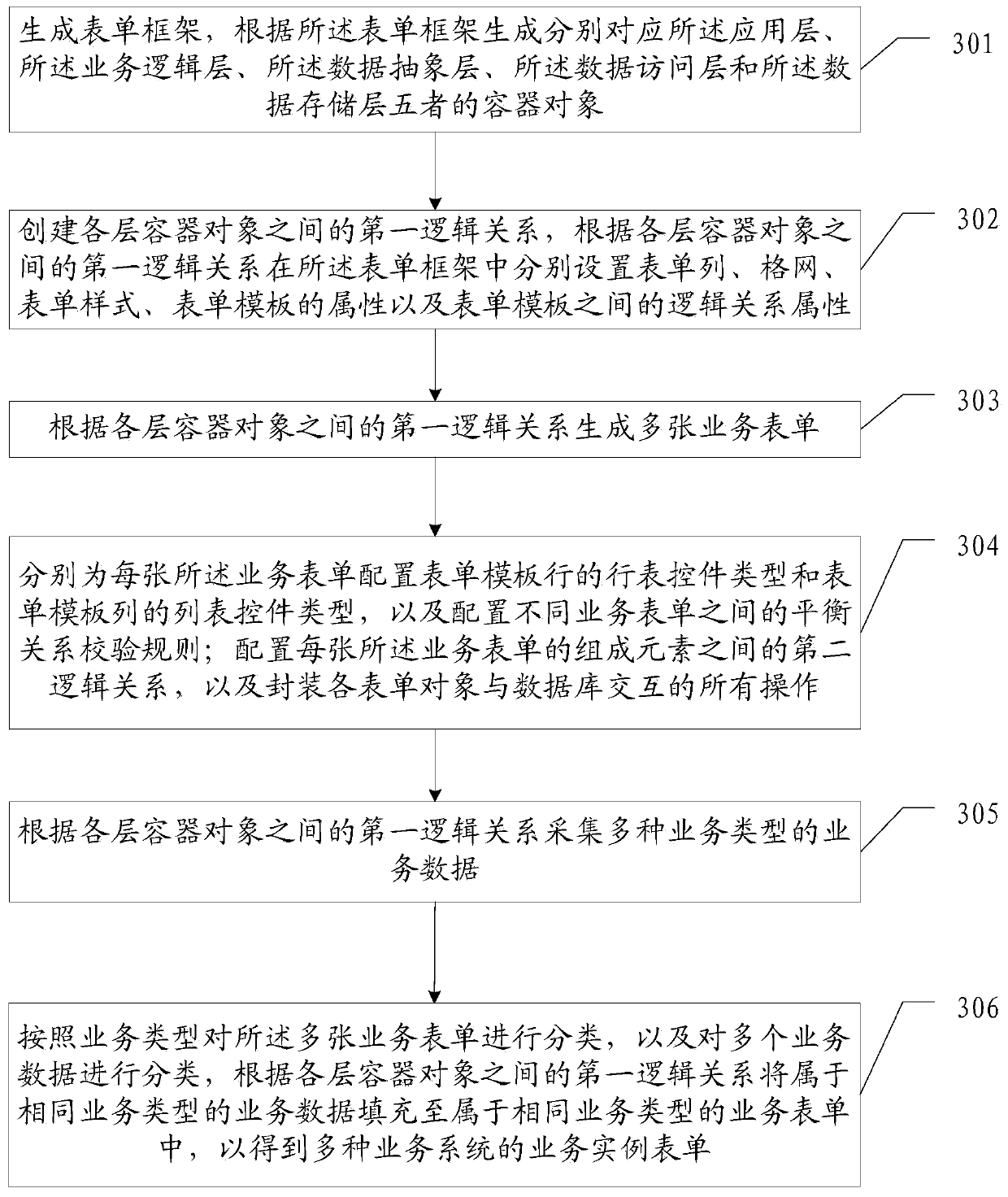
Business form generation method and device and storage medium
The invention discloses a business form generation method and device and a storage medium. The business form generation method comprises the steps: generating a form frame, and generating five layersof container objects according to the form frame; respectively setting dynamic form columns, dynamic form rows, dynamic form styles, attributes of form templates and logic relationship attributes in the form framework according to the first logic relationship among the container objects of each layer; generating a plurality of service forms according to the first logic relationship; configuring each cell control type for each business form, and configuring a balance relationship verification rule between different business forms; configuring a second logic relationship among the constituent elements of the business form, and encapsulating an operation of interaction between the form object and the database; acquiring service data of various service types according to the first logic relationship; and classifying the service forms and the service data according to the service types, and filling the service forms belonging to the same service type with the service data belonging to the same service type according to the first logic relationship to obtain service instance forms of multiple service systems.
Owner:中电万维信息技术有限责任公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com