Method for achieving multi-application of intelligent secret key equipment
An intelligent key device, multi-application technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
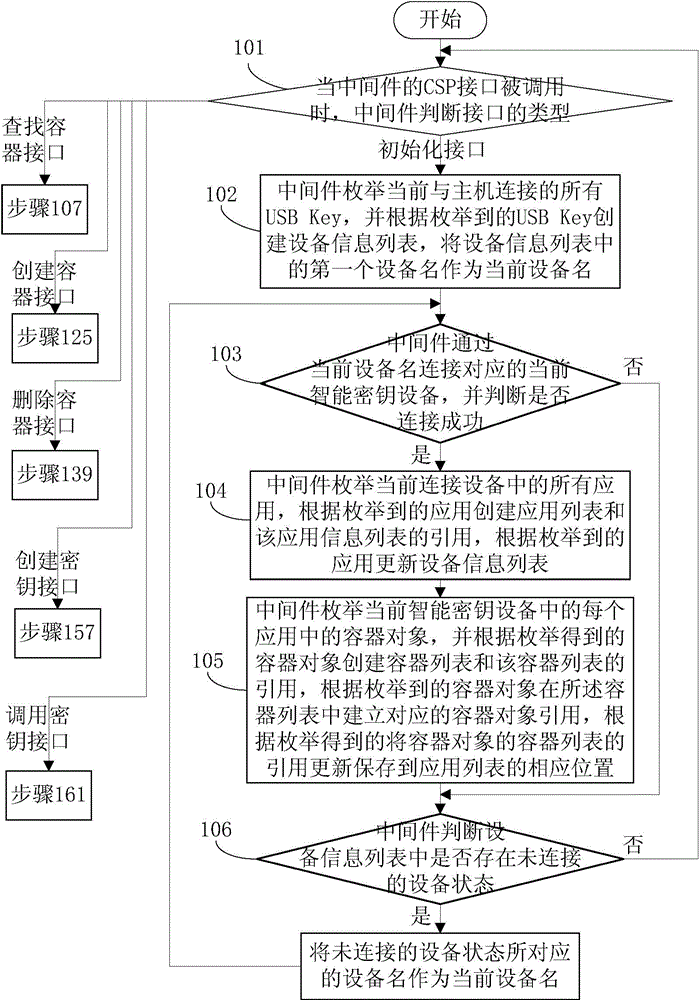
[0150] Embodiment 1 of the present invention provides a method for implementing multiple applications of smart key devices, such as Figure 1-Figure 5 shown, including:
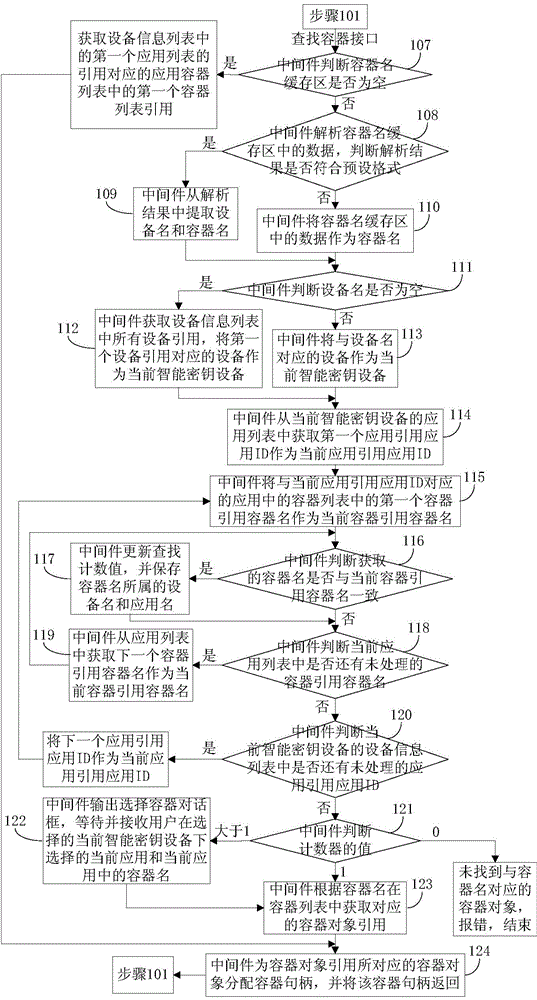
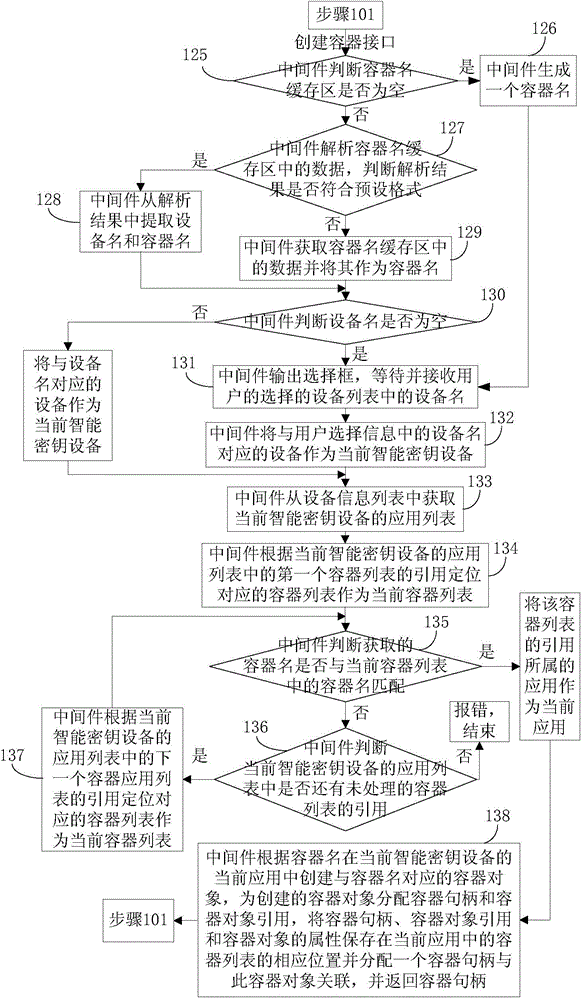
[0151] Step 101: When the CSP interface of the middleware is called, the middleware judges the type of the interface. If it is an initialization interface, then execute step 102. If it is to search for a container interface, then execute step 107. If it is to create a container interface, then execute step 125. To delete the container interface, execute step 139; if to create a key interface, execute step 157; if to call the key interface, execute step 161;
[0152] In this embodiment, the key will be invoked by calling the corresponding interface during encryption, decryption, and signature;
[0153] Step 102: the middleware enumerates all USB Keys connected to the host, and creates a device information list according to the enumerated USB Keys, using the first device name in the device information list as the...
Embodiment 2
[0249] Embodiment 2 of the present invention provides a method for implementing multiple applications of smart key devices, such as Image 6 with Figure 7 shown, including:
[0250] Step 201: When the PKCS#11 interface of the middleware is called, the middleware judges the type of the interface, if it is an initialization interface, then execute step 202, if it is an open session interface, then execute step 207, if it is an object interface, then execute step 209 , if it is to delete the object interface, execute step 216;
[0251] In this embodiment, the initialization interface is specifically:
[0252]
[0253] Open the session interface specifically as follows:
[0254]
[0255] Create an object interface specifically as:
[0256]
[0257] The delete object interface is specifically:
[0258]
[0259] Step 202: the middleware enumerates all USB Keys connected to the host through the initialization interface, and creates a device information list according ...
Embodiment 3
[0298] Embodiment 3 of the present invention provides a method for implementing multiple applications of smart key devices, such as Figure 8 with Figure 9 shown, including:
[0299] Step 300: When the national secret interface of the middleware is called, the middleware detects the type of the called interface. If it is an enumerated device interface, execute step 301. If it is a connection device interface, execute step 302. If it is an enumerated application interface Then perform step 303, if it is to create an application interface, then perform step 305, if it is to open an application interface, then perform step 308, if it is to delete an application interface, then perform step 311, if it is to enumerate container interfaces, then perform step 314, if it is to create a container Step 316 is executed for the interface, step 319 is executed if the container interface is opened, step 322 is executed if the container interface is deleted, step 325 is executed if the key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com