Asymmetric double-image encryption and decryption method based on chaos and cascade DFrRT
An encryption method and asymmetric technology, applied in the field of virtual optical information encryption and decryption, can solve the problems of low security of symmetric cryptosystem, easy to attack linear system, etc., to enhance nonlinearity and disorder, resist conventional attacks, The effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
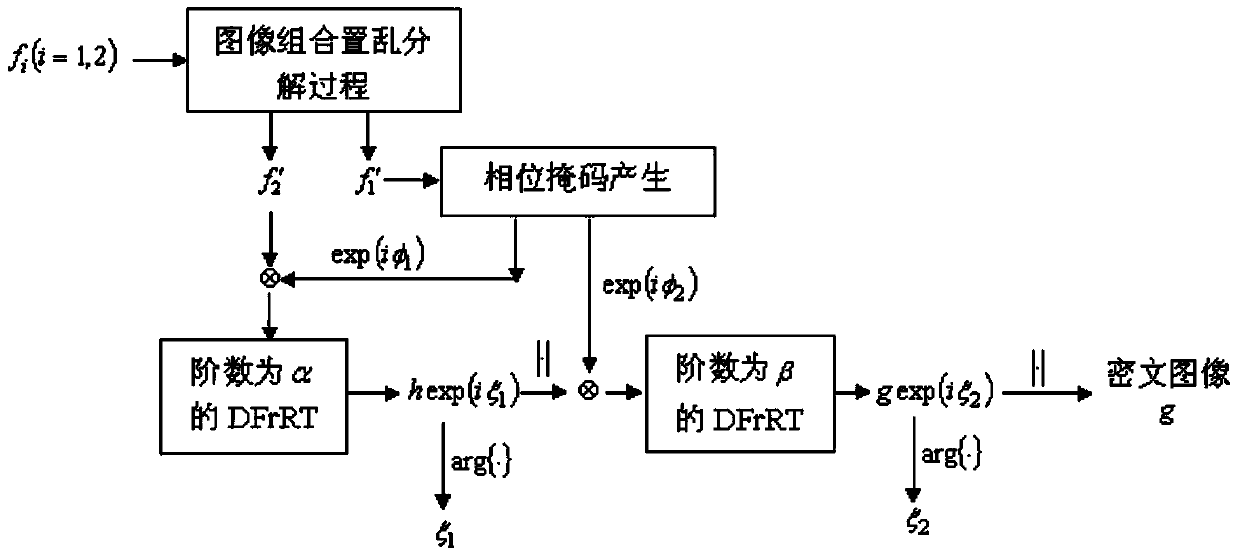
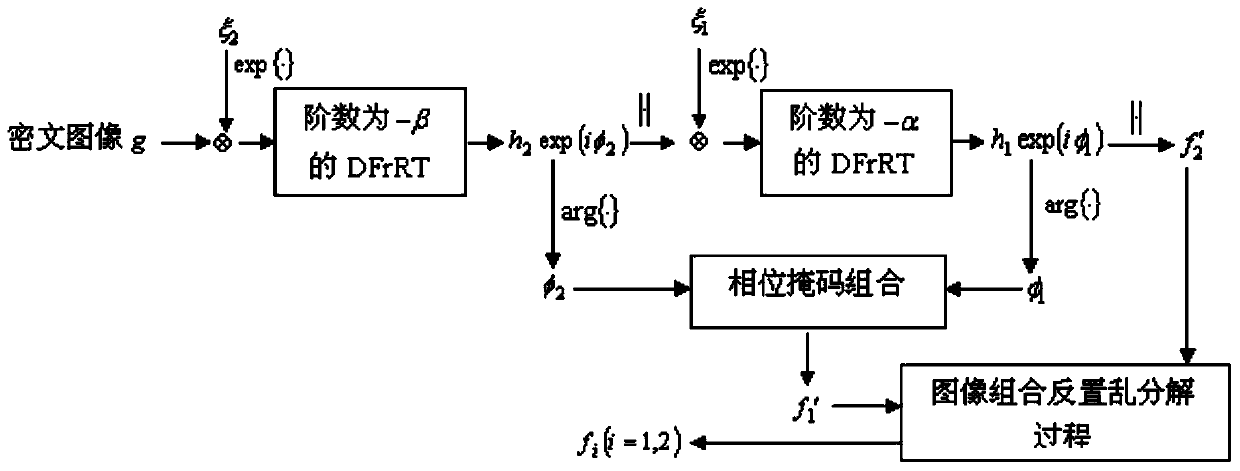
[0103] see figure 1 , with two 256×256 grayscale original grayscale images f 1 and f 2 , first put f i (i=1,2) normalized, and then concatenate the two images horizontally into an expanded image f of size 256×512 e . Scrambling the expanded image f using i times of cat map mapping e , where, by two initial values χ 01 , χ 02 ,y 0 (K represents the number of chaotic numbers to be discarded) The chaotic sequence s generated by the logistic mapping 1 and s 2 As the initial value p of the cat map map i and q i , get the scrambled image f′ e , the scrambled image f′ e Use the inverse operation of step 1 to decompose to get two new images f′ i (i=1,2). Generate two phase masks by generating a phase mask procedure and Based on the image f' 1 . put f' 2 with phase mask Convolution is performed on the obtained complex matrix based on Logistic mapping, and the random transformation of discrete fractions with order α is obtained to obtain the transformed result h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com