Digital rights management method based on N RSA (Rivest Shamir Adleman) encryption algorithms based on chaotic algorithm
A technology of digital copyright protection and chaotic algorithm, applied in the field of information security, it can solve the problems of troublesome keys, high calculation cost, factorization is not NPC, etc., and achieves the effect of good openness and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
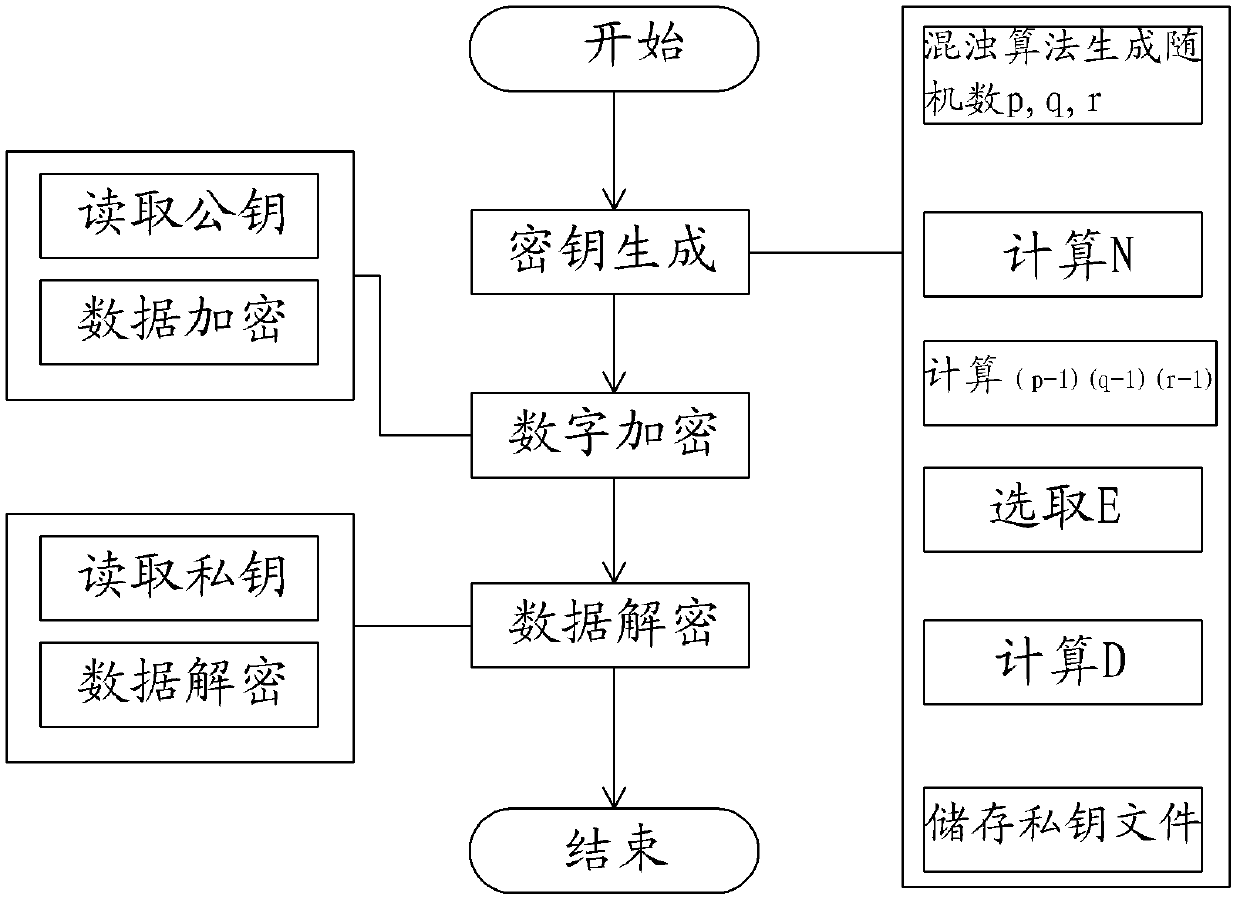
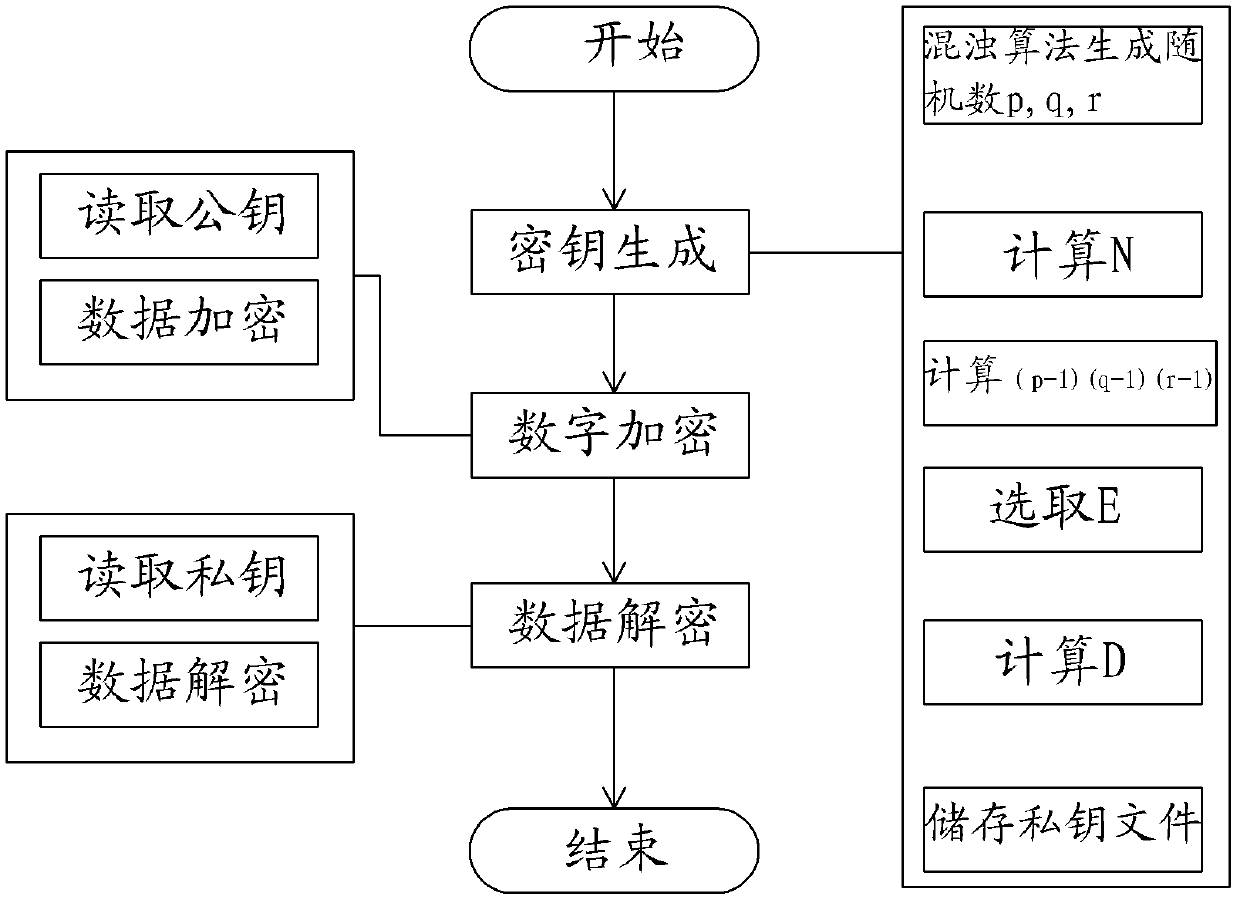
[0045] like figure 1 As shown, a digital copyright protection method based on the N-fold RSA encryption algorithm of the chaotic algorithm of the present invention specifically includes three main steps of private key generation, data encryption and data decryption:
[0046] Step 1. Generate private key parameters, and use this to generate public and private key pairs for encryption and decryption;
[0047] Step 11. First use the chaotic algorithm to randomly generate a random number whose lowest bit is an odd number, because a prime number must be an odd number. If it is an even number, it can be divisible by 2. Then, perform a composite number judgment test on the generated random number. If it passes the test, Then it is a composite number, otherwise when the test of the preset number of times is still not passed, then the random number is regarded as a prime number, and finally, three prime numbers p, q and r are randomly generated by a chaotic algorithm; Miller-Rabin is u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com