System and method to enable PKI- and PMI-based distributed locking of content and distributed unlocking of protected content and/or scoring of users and/or scoring of end-entity access means—added
a distributed locking and content technology, applied in the field of security based communication lines, can solve the problems of security being compromised, the identity of the other party's pubic key being challenged, and the difficulty of authenticating the identity of the other party's pubic key
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
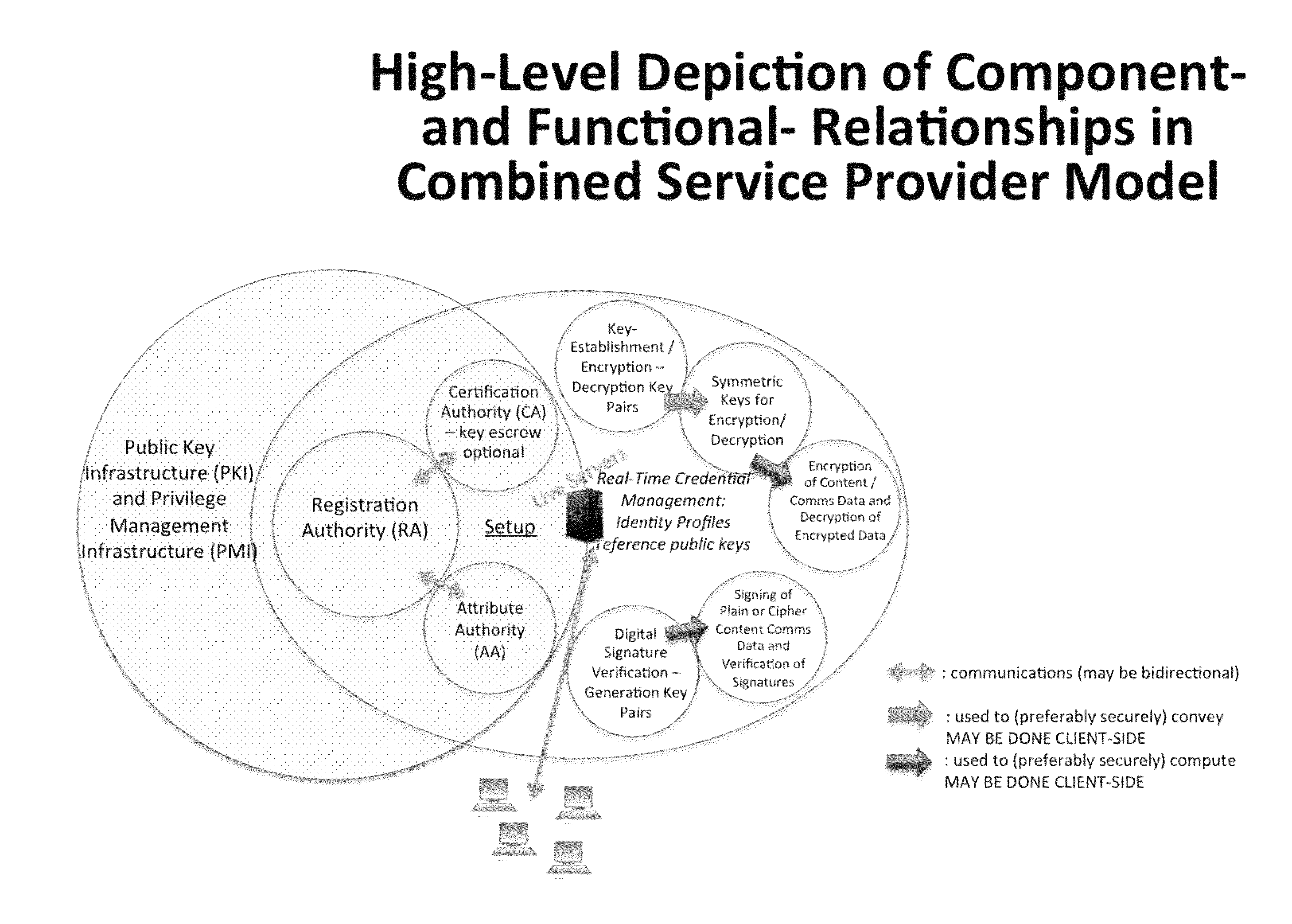
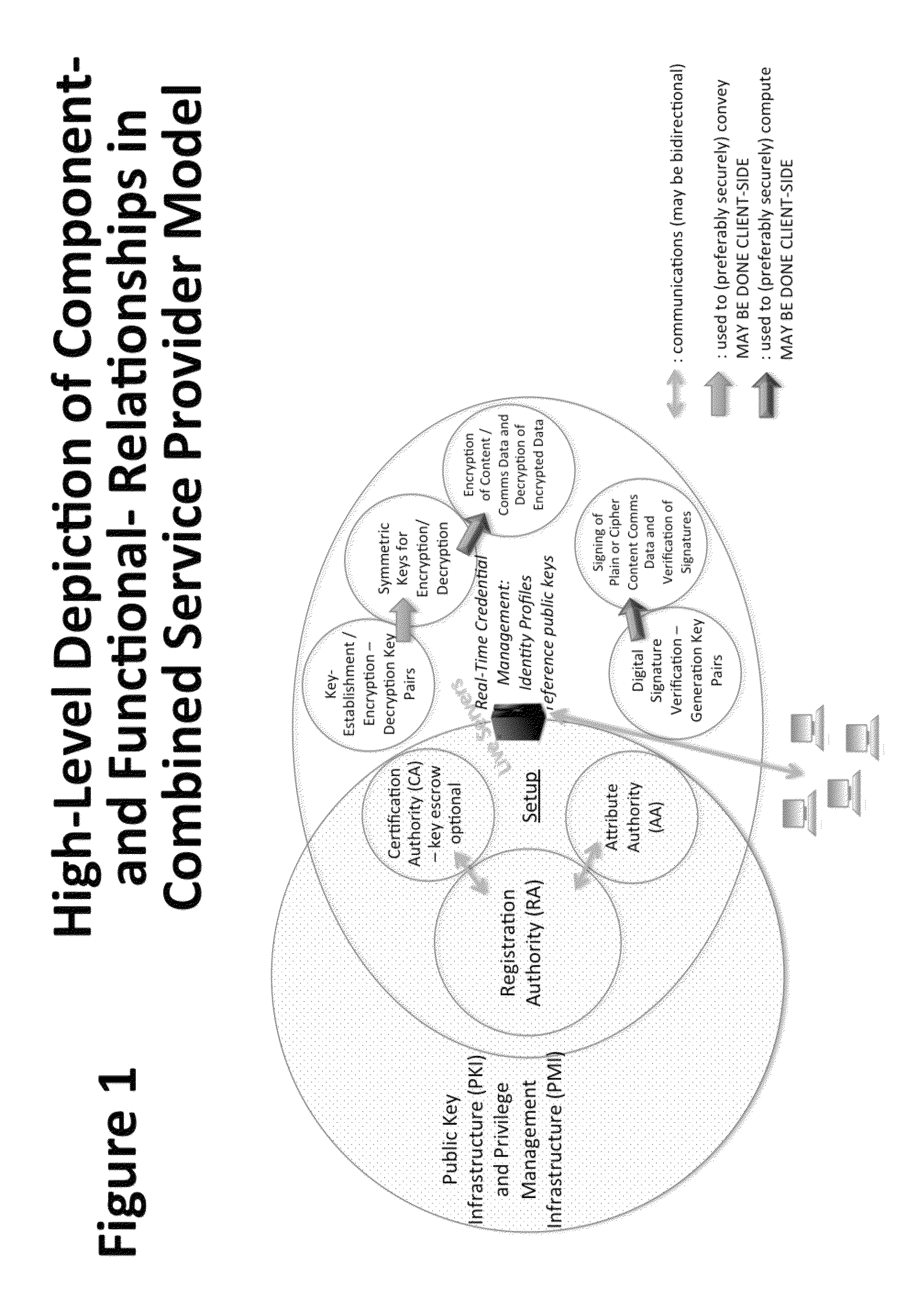
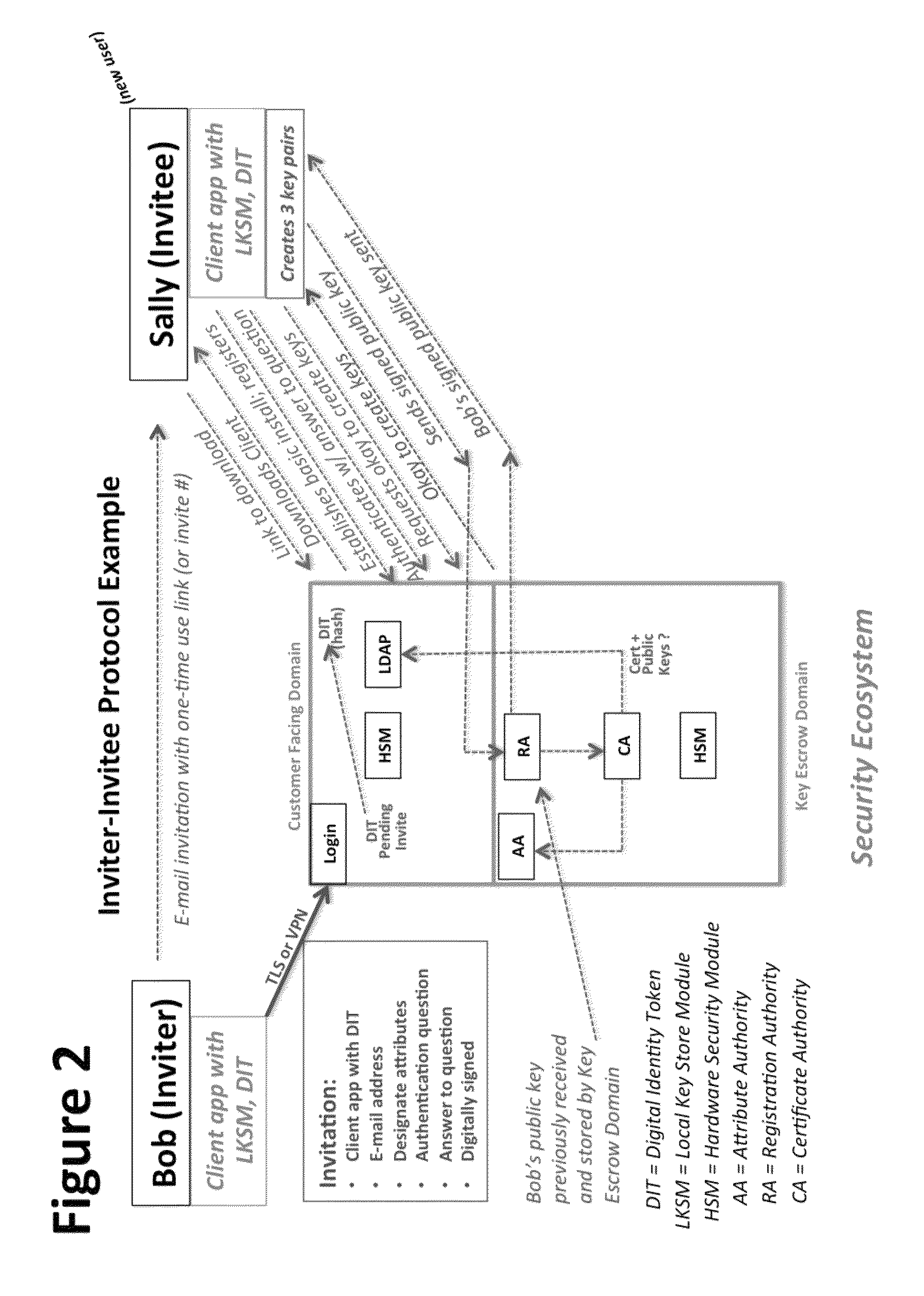
[0004]The present descriptions generally relate to the field of enabling security based communication lines established between users when using X.509-compatible PKI and PMI and related tools (see FIG. 1“High-Level Depiction of Component- and Functional-Relationships in Combined Service Provider Model”). Rather than a centrally managed system of identity and relationship recognition and authorization, these functions are transferred to users through an Inviter-Invitee protocol suite, through which Inviters vouch for the identity of Invitees who successfully complete the protocol establishing communication lines. The Security Ecosystem includes an Attribute Authority which acts as a Trusted Third Party mediating service provider for users that can: securely set up identities, uniquely associate keys to identities and their invitees, thereby securing each communication line. The system delegates authorizations to inviters and invitees for each communication line, and then proceeds to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com