Data access control method and system in large-scale cloud storage based on block chain
A technology for data access control and data access, which is applied in digital transmission systems, transmission systems, and key distribution, can solve problems such as lack of scalability, and achieve the effects of protecting user privacy, protecting privacy, and reducing burdens
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
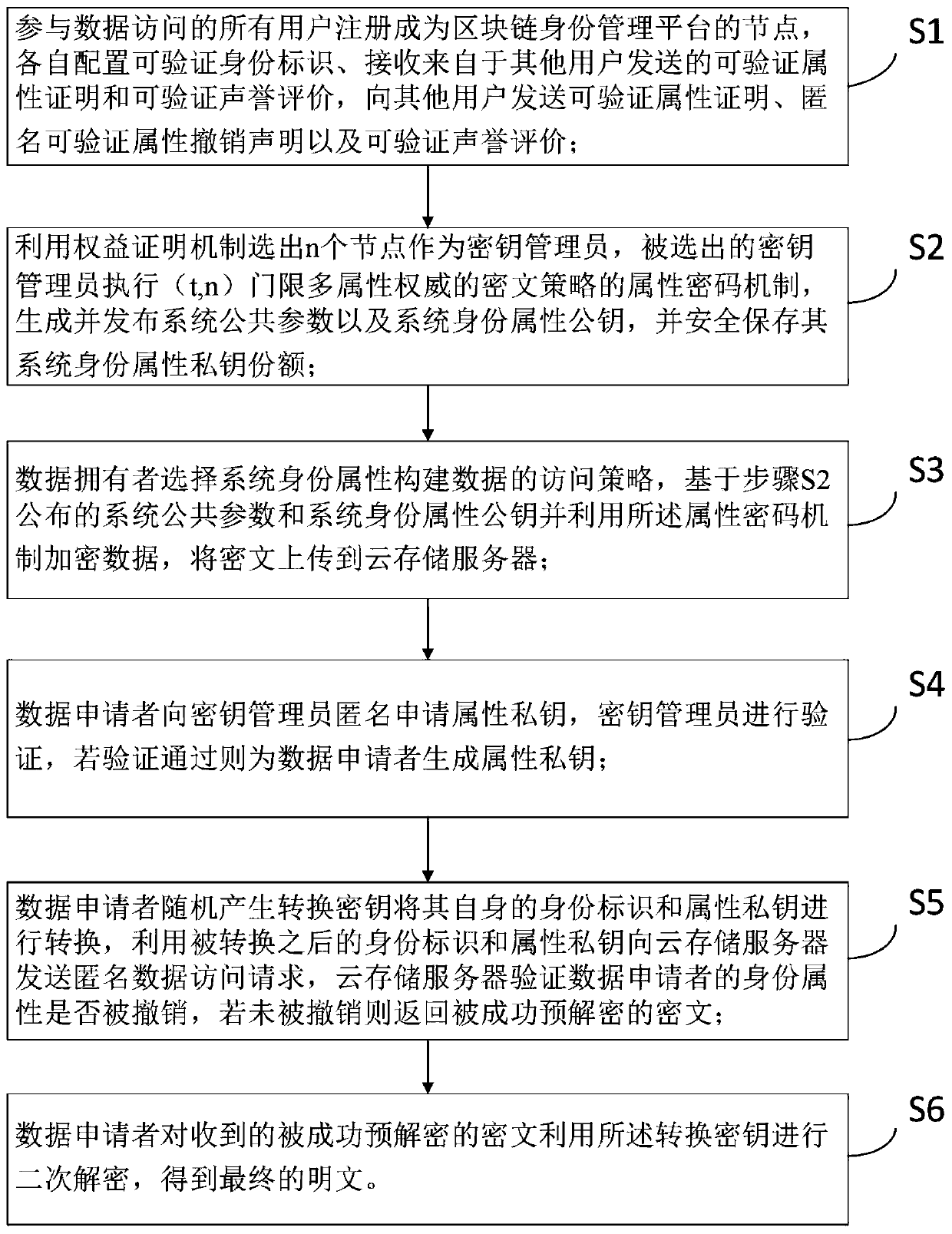
[0111] Such as Figure 8 As shown, the third stage can be implemented in the following way:
[0112] S421. For each attribute in the request, the key administrator generates an attribute private key share for the data applicant by using the corresponding system attribute private key share and the hash value of the data applicant identity identifier in the request;
[0113] S422. The key manager uses the public key locally generated by the applicant in the request to encrypt the generated attribute private key share, and sends it to the data applicant as a response.
[0114] further,
[0115] S5. The data applicant randomly generates a conversion key to convert its own identity and attribute private key, and uses the converted identity and attribute private key to send an anonymous data access request to the cloud storage server, and the cloud storage server verifies the data application Whether the identity attribute of the user has been revoked, if not revoked, the cipherte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com