Attribute-based multi-mechanism hierarchical ciphertext-policy weight encryption method under cloud environment
A technology of ciphertext strategy and encryption method, which is applied in the field of network and information security, and can solve problems that do not involve the hierarchy of multi-authorization institutions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
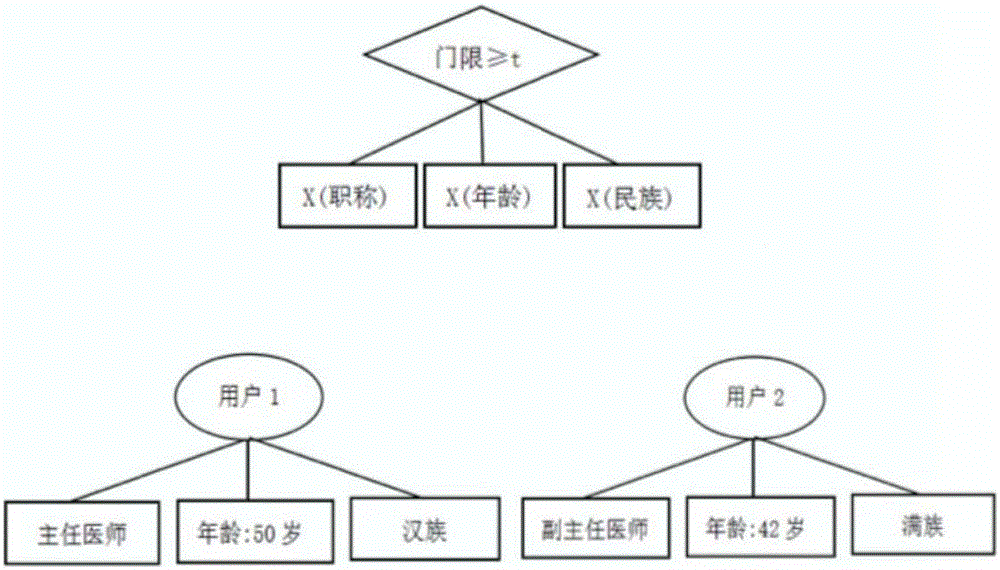
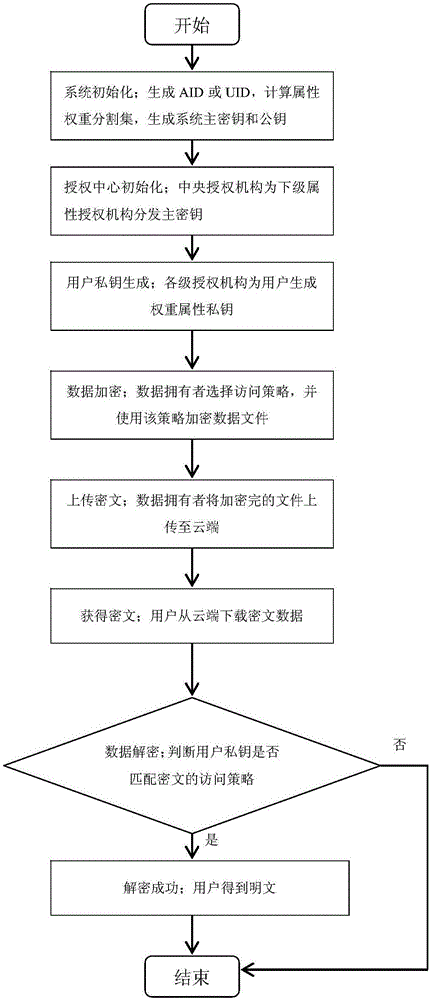
[0021] The specific embodiment of the present invention will be further described in detail in conjunction with the accompanying drawings. The present invention proposes a weighted attribute-based encryption scheme of a hierarchical authorization center, which not only introduces attribute weights into the encryption scheme, but also adopts a multi-level authorization center mechanism, and utilizes the difference in the size of attribute weights that can be distributed by authorization agencies at different levels. Implemented finer-grained access control. This method is proved to be safe under the standard model, and the performance analysis shows that this scheme is more suitable for cloud environment than existing schemes.
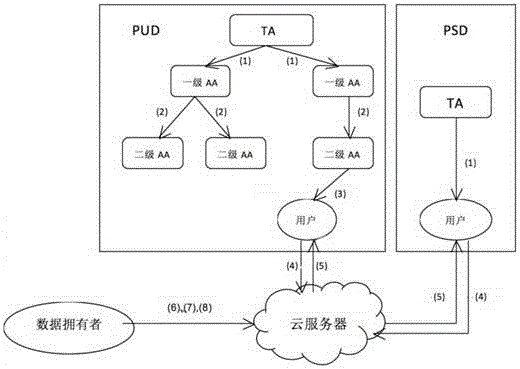
[0022] Such as figure 1 As shown, it is divided into two different management areas, namely the public domain (Public Domain, PUD) and the personal domain (Personal Domain, PSD). Among them, (1) is to generate AID or UID, and distribute master key or ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com