Fine-grained data access control method based on fragmenting of secret keys
An access control and fine-grained technology, applied in the field of information security, can solve security risks and other problems, and achieve the effect of high security, strong security, and less calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0082] Embodiments of the present invention will be further described below with reference to the drawings and specific embodiments.
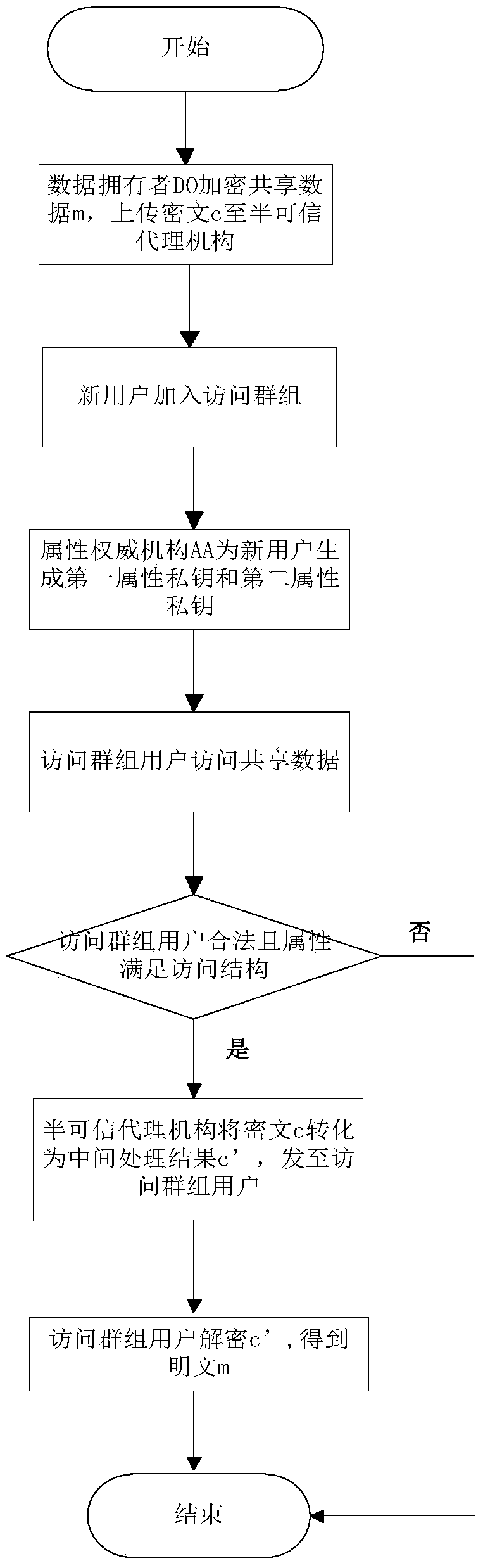
[0083] refer to figure 1 , the implementation steps of the present invention are as follows:
[0084] Step 1, the data owner DO encrypts the shared data.
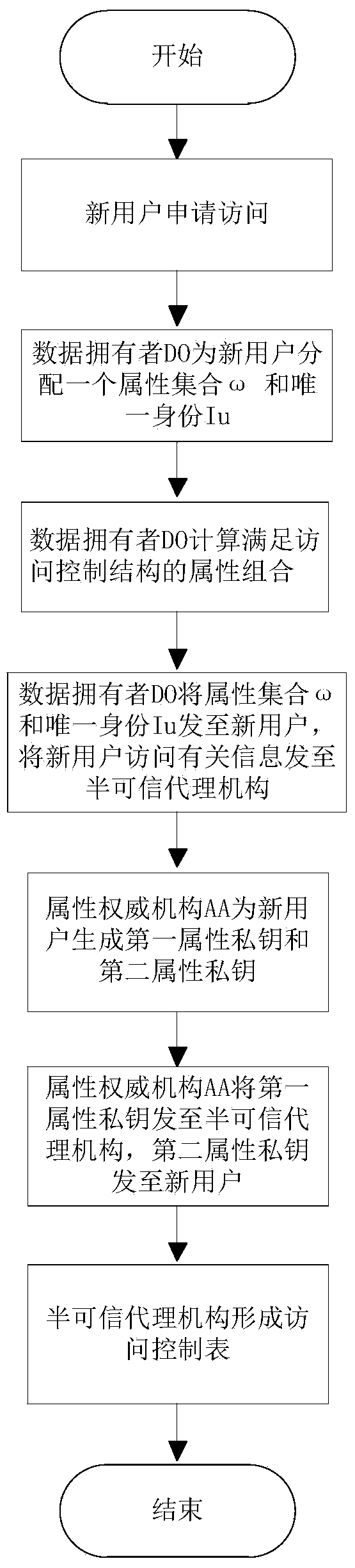
[0085] refer to figure 2 , the specific implementation of this step is as follows:
[0086] 1a) The attribute authority AA generates a master key mk and a public key pk, expressed as follows;
[0087] mk = ( α , { t j } j = 1 n ) ,
[0088] pk = ( g , y = e (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com