Multi-authority attribute-based encryption method based on blockchain
An attribute-based encryption and blockchain technology, applied in user identity/authority verification and key distribution, can solve problems such as inability to dynamically and efficiently manage user attributes, not meeting forward or backward security, and difficulty in realizing user revocation. , to achieve the effect of realizing user attribute revocation, avoiding single point of failure, ensuring forward security and backward security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
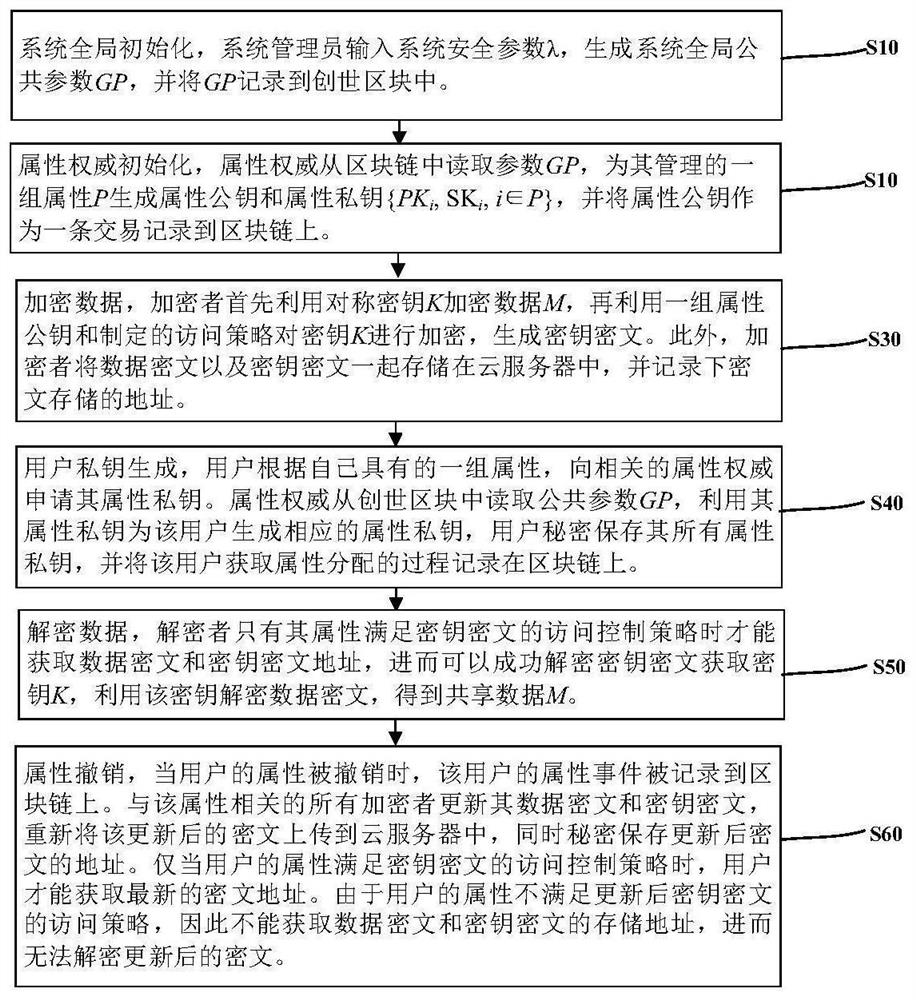
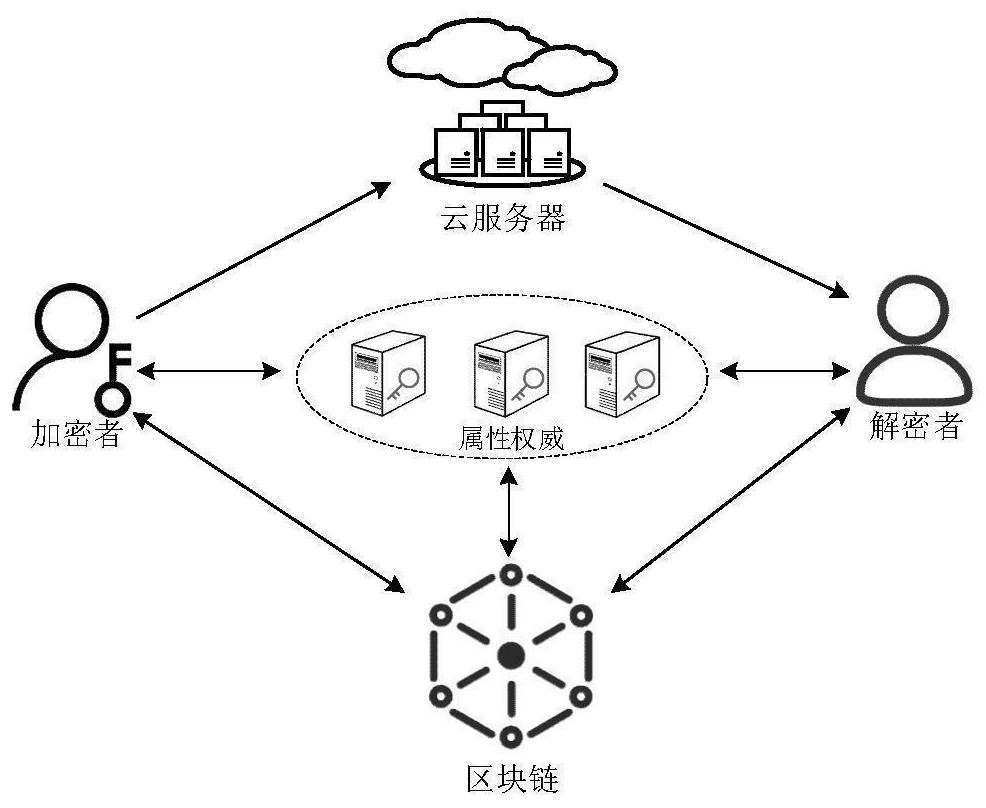
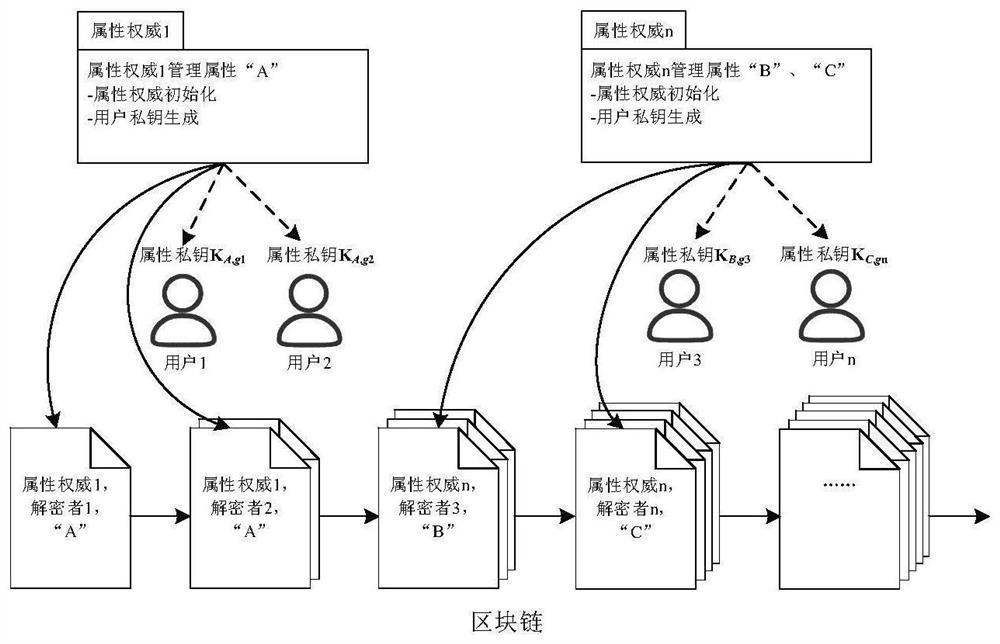
[0064] see Figure 1 to Figure 5 , the technical solution provided by the present invention is that this embodiment provides a blockchain-based multi-authority attribute-based encryption method, such as figure 1 As shown, including: system global initialization, the system administrator enters a system security parameter λ, generates the system global public parameter GP, and records the GP into the genesis block, initializes the attribute authority, and all attribute authority is obtained from the genesis block Read GP, assuming that any attribute authority manages a set of attributes P, for each attribute i∈P, the attribute authority generates a pair of attribute public key and attribute private key Property private keys must be kept secret and attribute the public key recorded on the blockchain.
[0065] Described encryption method specifically comprises the following steps:
[0066] S30. To encrypt data, the encryptor first selects a symmetric key K for the data M...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com