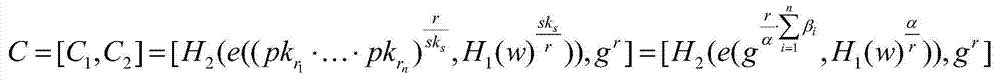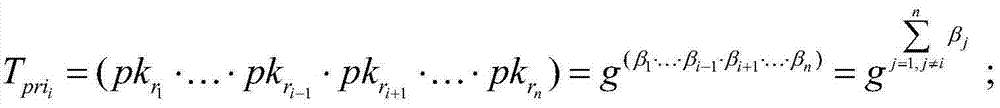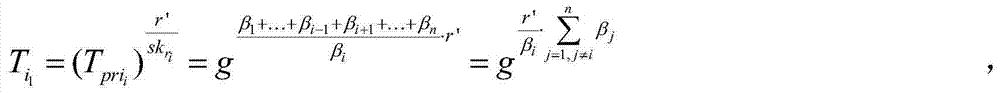Patents
Literature
539results about How to "Satisfy security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
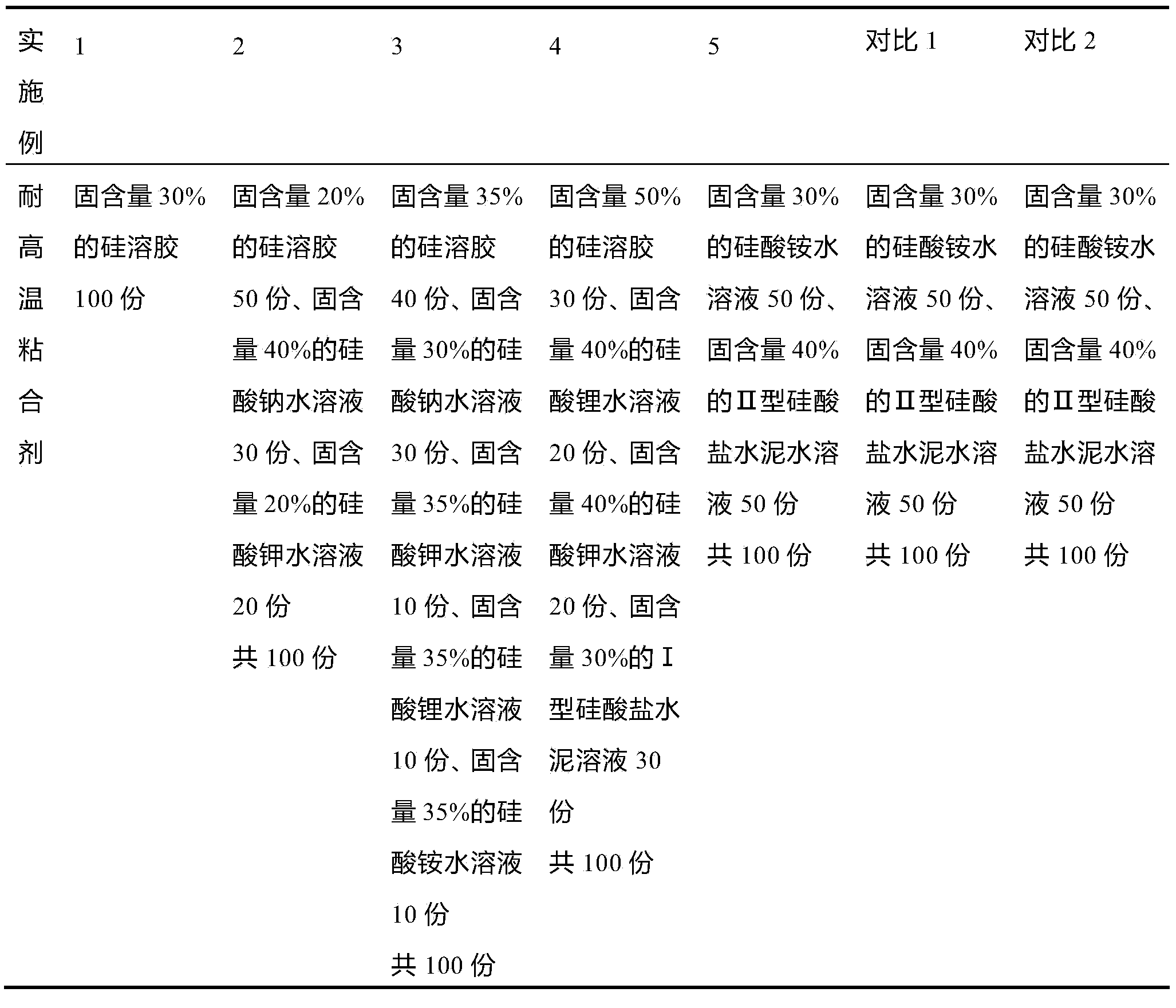
Non-aqueous electrolyte and lithium secondary battery using the same
InactiveUS20060172201A1High conductivityExcellent charge discharge characteristicOrganic electrolyte cellsNegative electrodesSolventCarboxylate
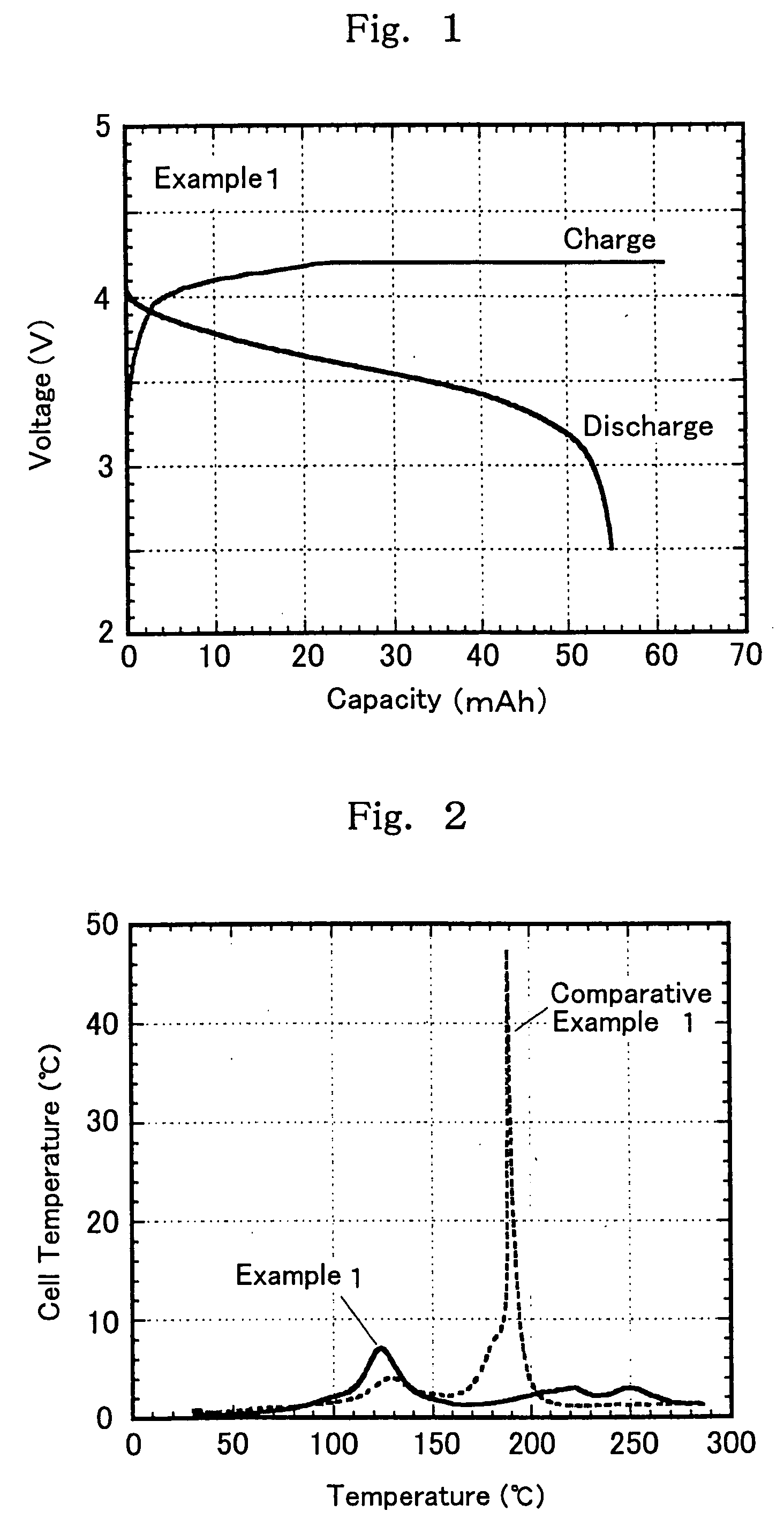
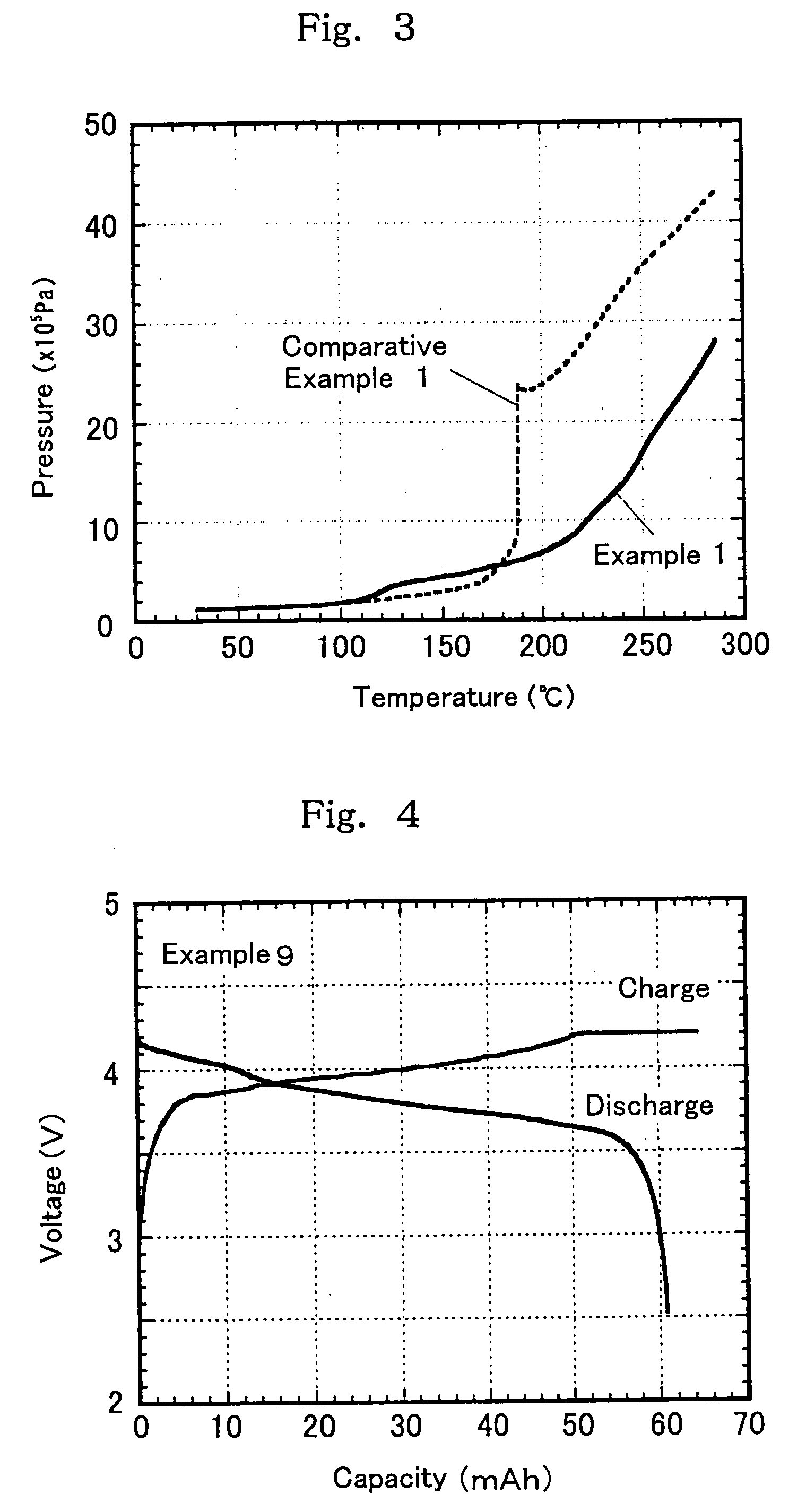
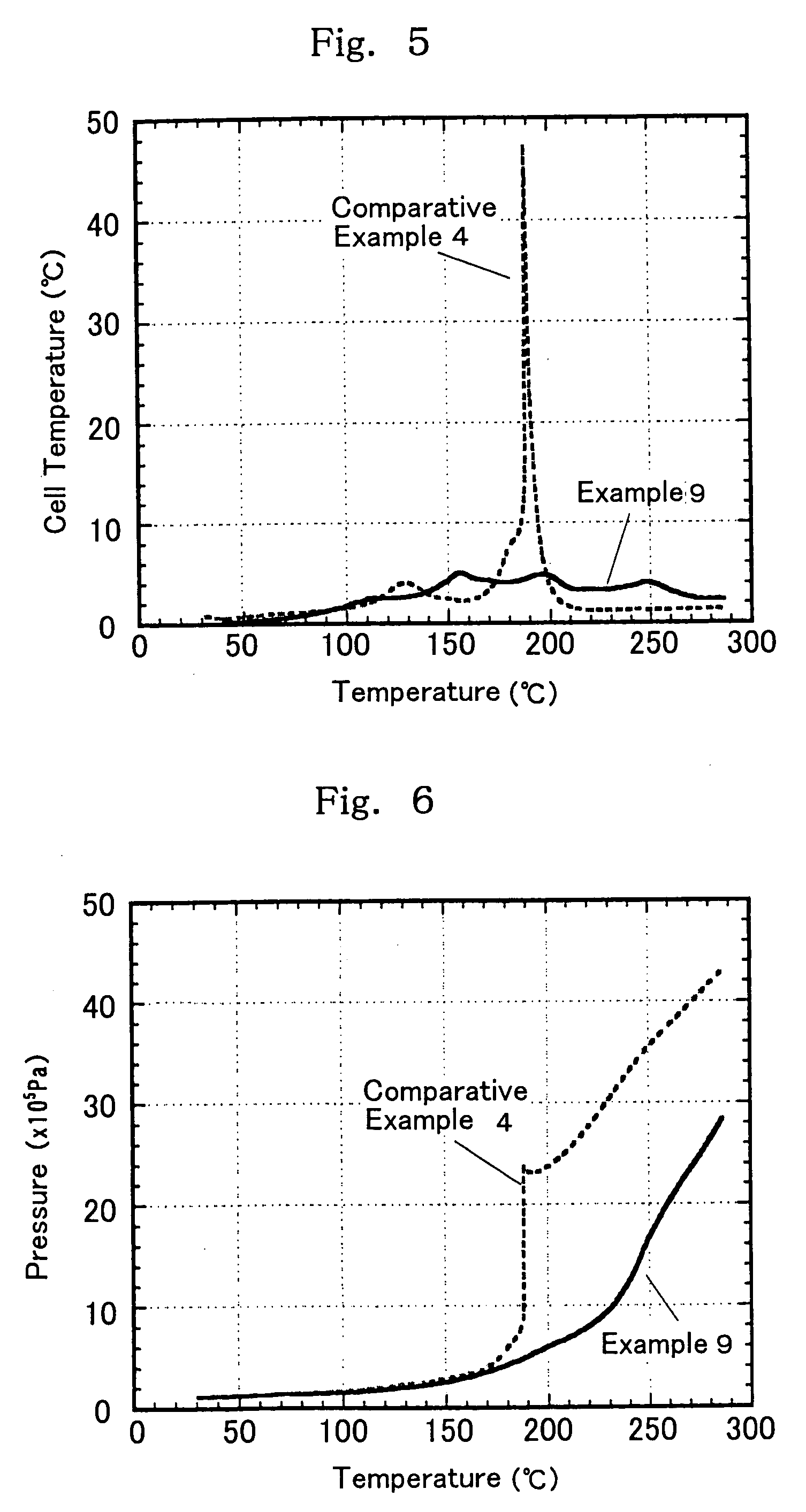
The present invention is directed to a non-aqueous electrolyte for lithium secondary battery, having both flame retardancy (self-extinguishing property) or nonflammability (having no flash point) and high conductivity and being electrochemically stable, and a lithium secondary battery using the non-aqueous electrolyte. Specifically, the non-aqueous electrolyte of the present invention comprises a non-aqueous solvent which comprises (a) at least one phosphate selected from (a1) a chain state phosphate and (a2) a cyclic phosphate as an essential component, and which may contain (b1) a cyclic carboxylate and (b2) a cyclic carbonate. Further, the non-aqueous electrolyte comprises the above non-aqueous solvent which further comprises (c1) a vinylene carbonate compound and / or (c2) a vinylethylene carbonate compound, and at least one compound selected from the group consisting of (d1) a cyclic amide compound, (d2) a cyclic carbamate compound, and (d3) a heterocyclic compound.
Owner:MITSUBISHI CHEM CORP
Fire-proof adhesive and application thereof
ActiveCN104099028AReduce total calorific valueImprove thermal conductivityNon-macromolecular adhesive additivesMacromolecular adhesive additivesCombustionAdhesive
The invention discloses a fire-proof adhesive and application thereof. The fire-proof adhesive comprises the following components by parts: 100 parts of high-temperature bonding agent, 10-70 parts of fire retardant, 0.5-50 parts of flame retardant synergist, 5-50 parts of strength enhancer, 0.05-20.0 parts of water-proof modifying agent and 0.01-2.0 parts of curing modifying agent. By adopting the fire-proof adhesive and a preparation method of a fire-retardant EPS (Expandable Polystyrene) foam heat-insulating plate, the combustion performance and physicochemical performance of the fire-retardant EPS foam heat-insulating plate can be improved remarkably. For example, the heat-conducting coefficient can be lowered below 0.055w / m.k, the specific gravity can be lower than 150Kg / M<3>, the compressive strength is higher than 150KPa, and the heat value is less than 3MJ / kg.
Owner:应急管理部四川消防研究所
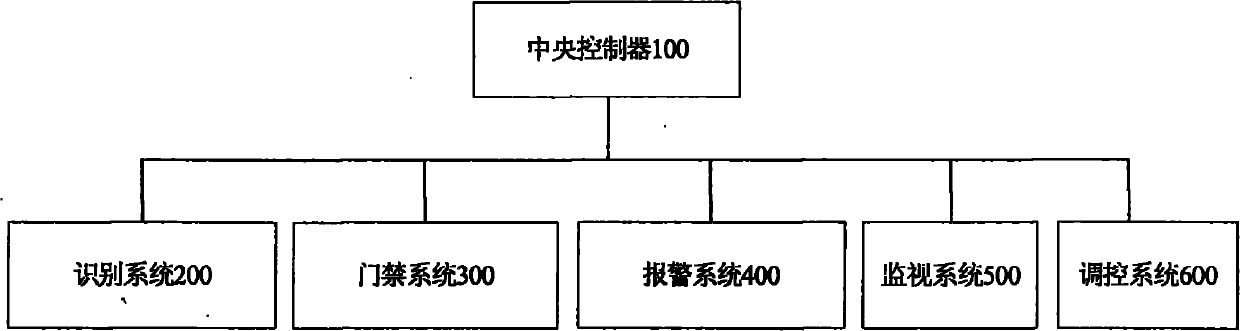
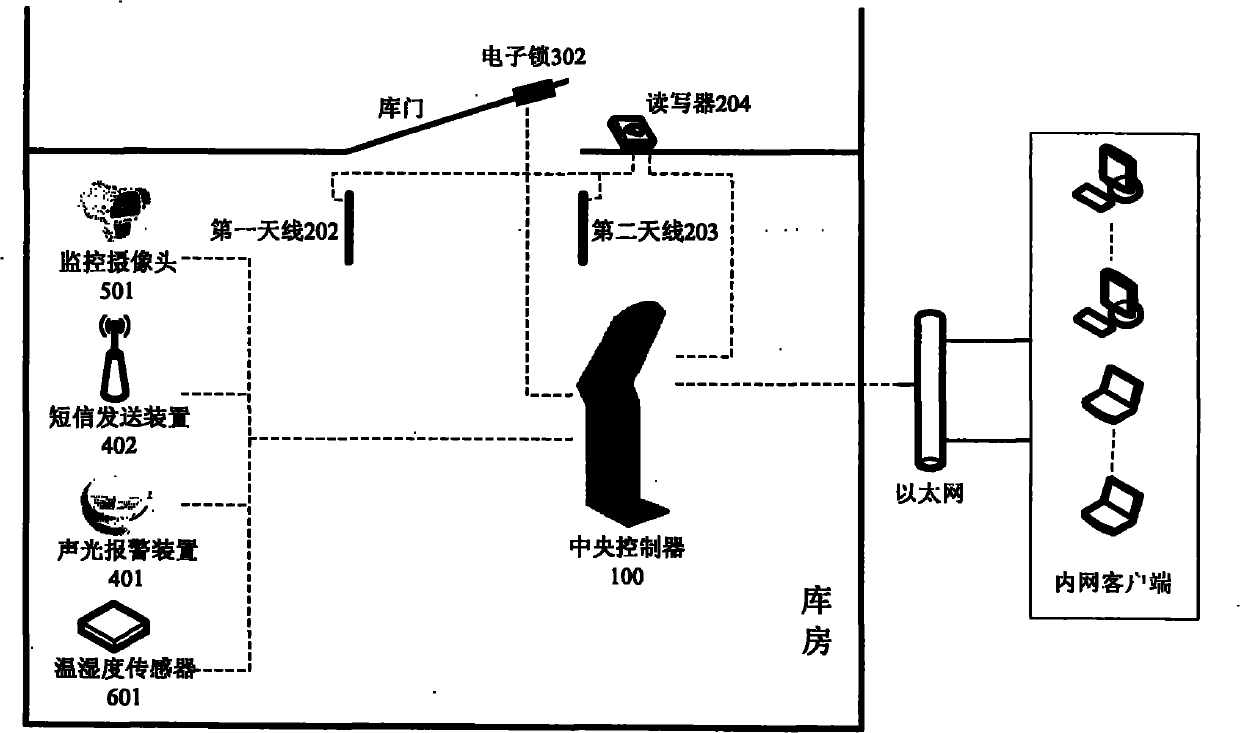
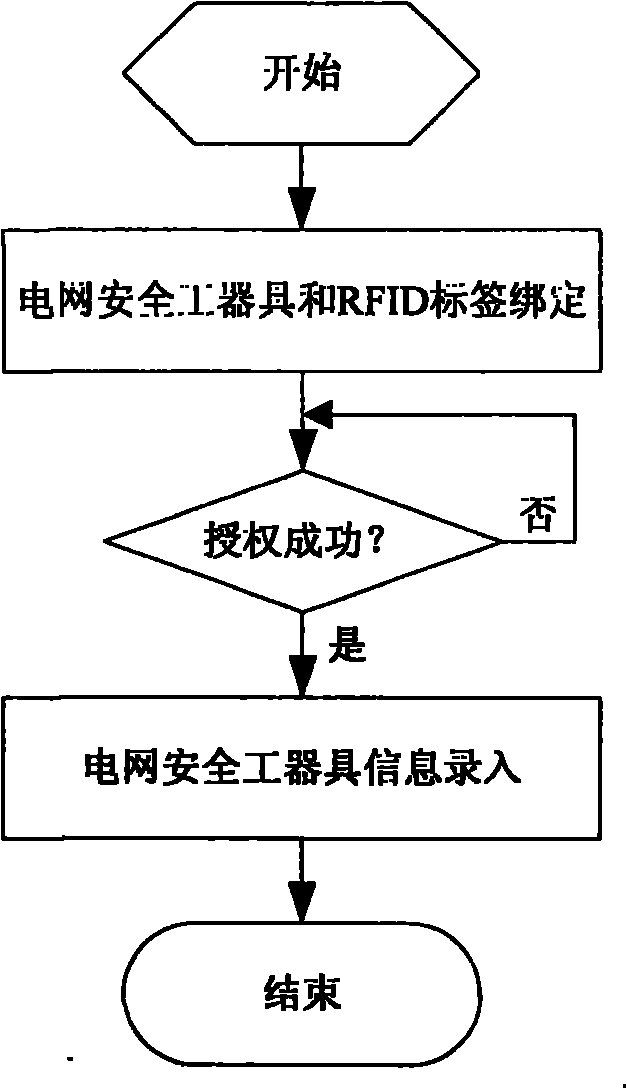
Object intelligent monitoring system based on RFID (Radio Frequency Identification)
InactiveCN102169547ARealize centralized monitoringSatisfy securityCo-operative working arrangementsClosed circuit television systemsData informationData center
The invention discloses an object intelligent monitoring system which comprises a monitoring center, an identification system, an entrance guard system, an alarming system, a monitoring system and a regulation system. The monitoring center is used for concentratedly processing data information submitted by each system and giving a control order. Meanwhile, as a data center of the system of the invention, the monitoring system is used for providing data service for local operation and remote control. The invention also relates to a method for the object intelligent monitoring system. The method adopts a high-efficient and reliable intelligent identification technology of RFID for management of objects in an individual, informationized and intelligent manner, specifically including warehousing, borrowing, returning, examining, discarding, etc. of the objects. Meanwhile, environment factors of an object intelligent warehouse are regulated and an early alarming is conducted to realize an integral monitoring of both the objects and the environment, thereby fully meeting the requirements for security, effectiveness, timeliness and reliability of the object warehouse.
Owner:武汉鹏晔科技有限公司
Electric vehicle energy recovery system and control method thereof
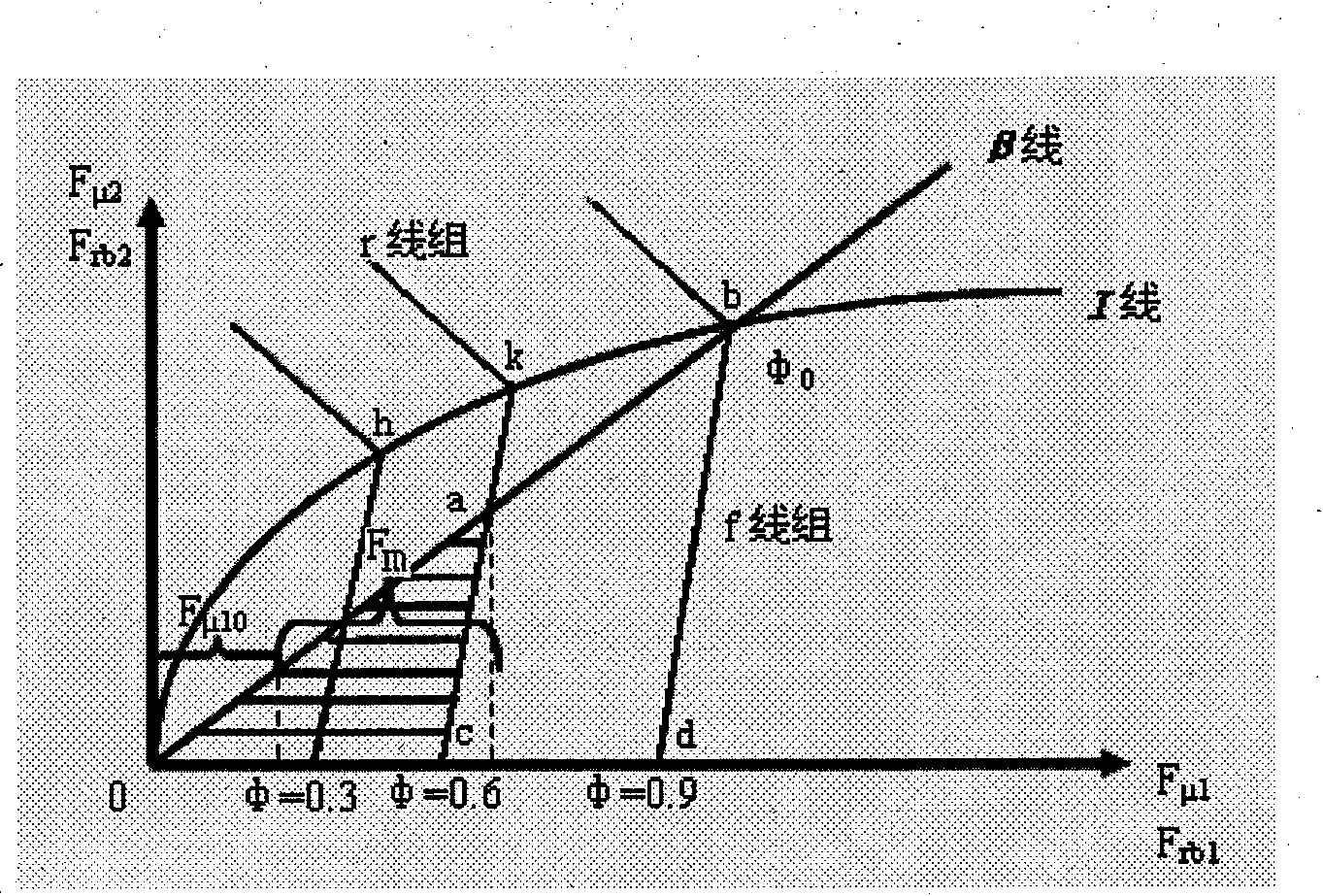
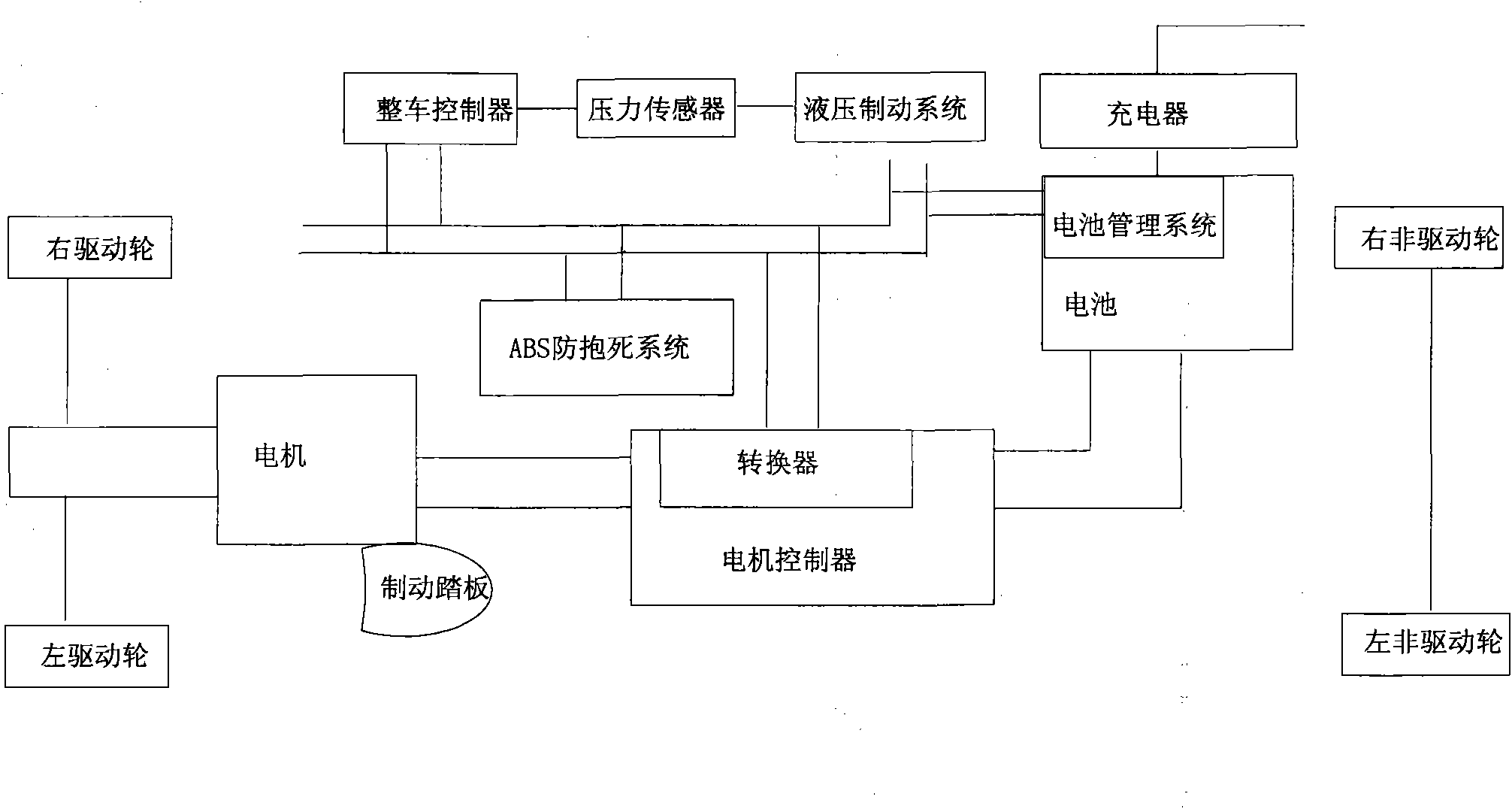
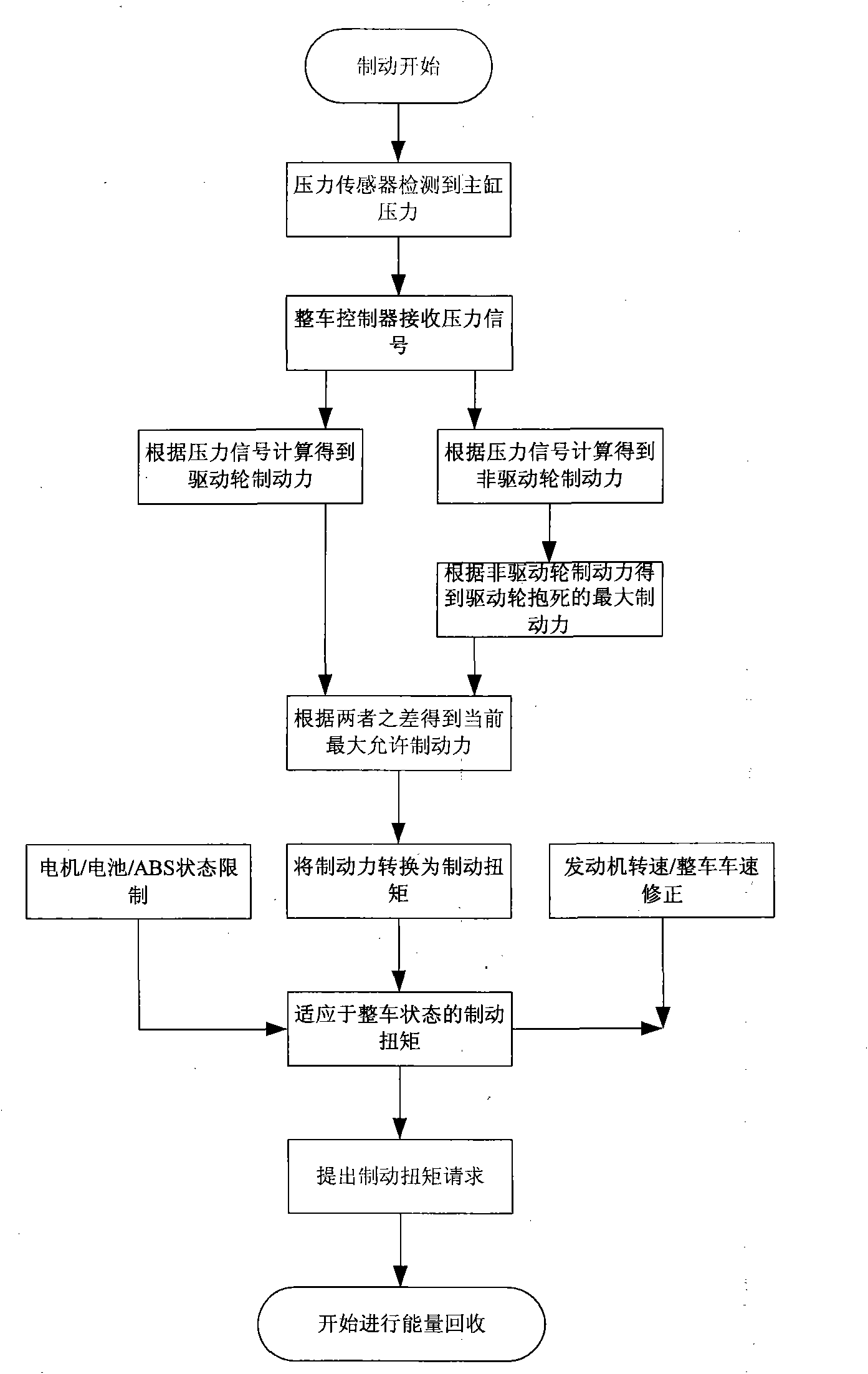
ActiveCN101979259AMaximum recoverySatisfy securitySpeed controllerElectrodynamic brake systemsAdhesion coefficientBrake torque
The invention discloses an electric vehicle energy recovery system and a control method thereof. On the basis of the pressure of a brake master cylinder of an electric vehicle, a maximal brake force Fm which is allowed to be applied to a current driving wheel is obtained by calculating according to a brake force distribution curve in an electric vehicle brake system design and a driving wheel locking curve when the electric vehicle travels on a road surface with an ideal synchronous surface adhesion coefficient; and the Fm is converted into a torque, namely a maximal motor brake torque which can be applied currently so that the overall vehicle energy of the electric vehicle can be recovered to the maximum. Simultaneously, the calculated brake torque is corrected according to the requirements on the drivability and the safety of a vehicle, so that brake energy can be recovered to the maximum on the premise of ensuring the drivability and the safety of the electric vehicle.
Owner:CHERY AUTOMOBILE CO LTD
Master end operator device of master slave minimal invasive blood vessel interventional surgical assistant system
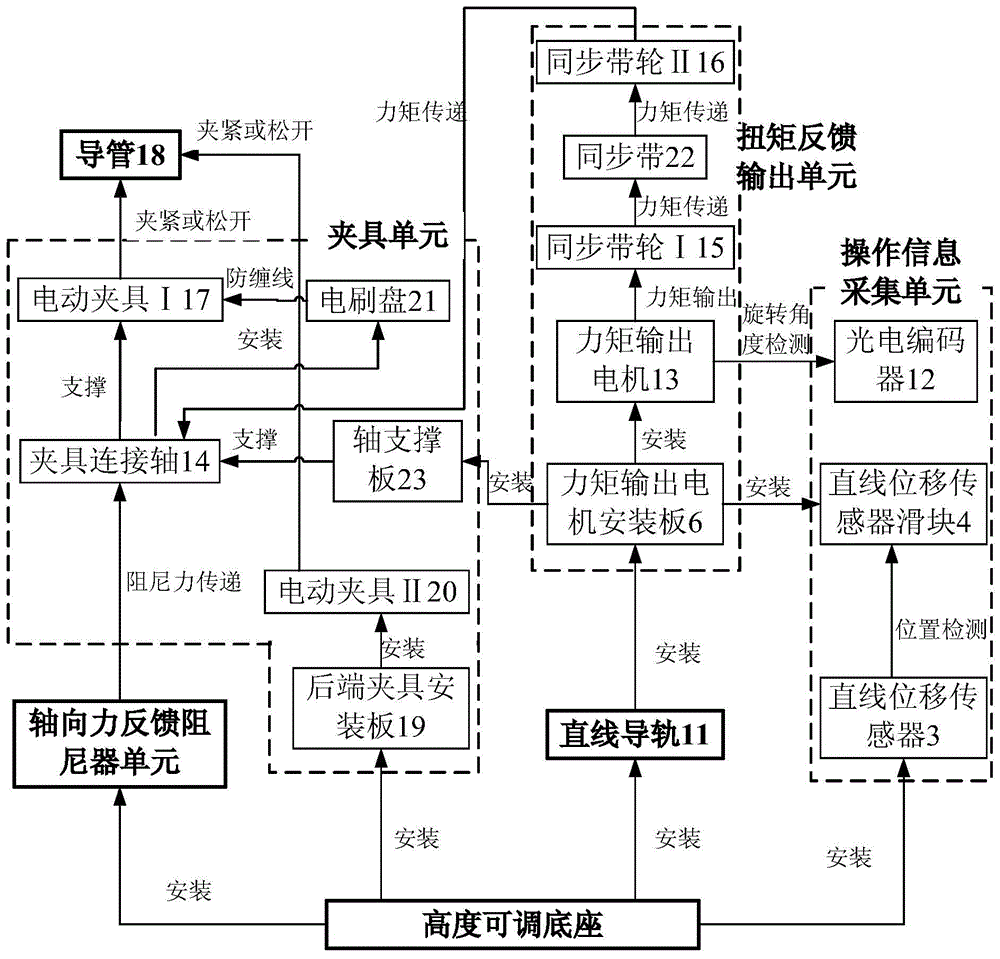
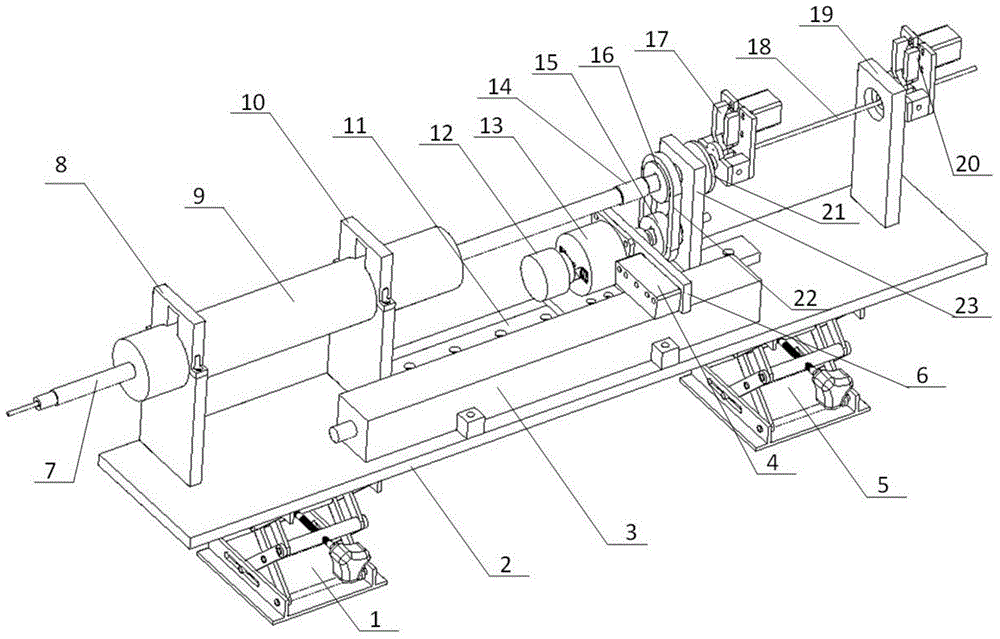
A master end operator device of a master slave minimal invasive blood vessel interventional surgical assistant system is characterized by comprising an axial force feedback damper unit, a torsion feedback output unit, a clamp unit, an operation information unit, a catheter, a linear guide rail and a height-adjustable base; a work method of the device comprises detection, transmission, processing and action of signals; the device has the advantages that the catheter is directly operated, and the ergonomic demands are met; real-time and intuitive feedback is realized, and the surgical safety and operation demands of a doctor are met; axial operation information is obtained by a friction-free magnetic induction mode, and efficiency is realized without adding the load; the height is adjustable.
Owner:SHENZHEN INST OF ADVANCED BIOMEDICAL ROBOT CO LTD
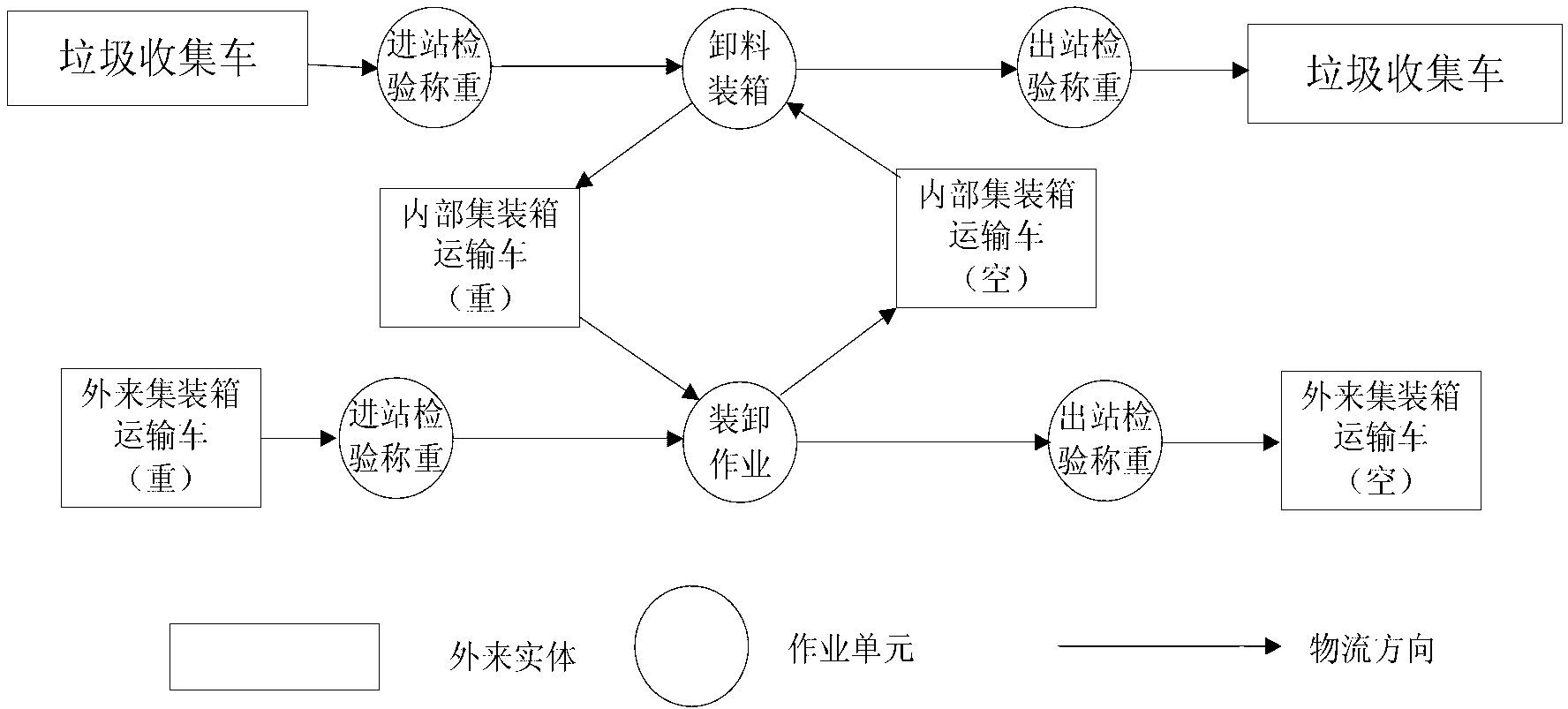
IoT (Internet of Things)-technology-based refuse collection management system
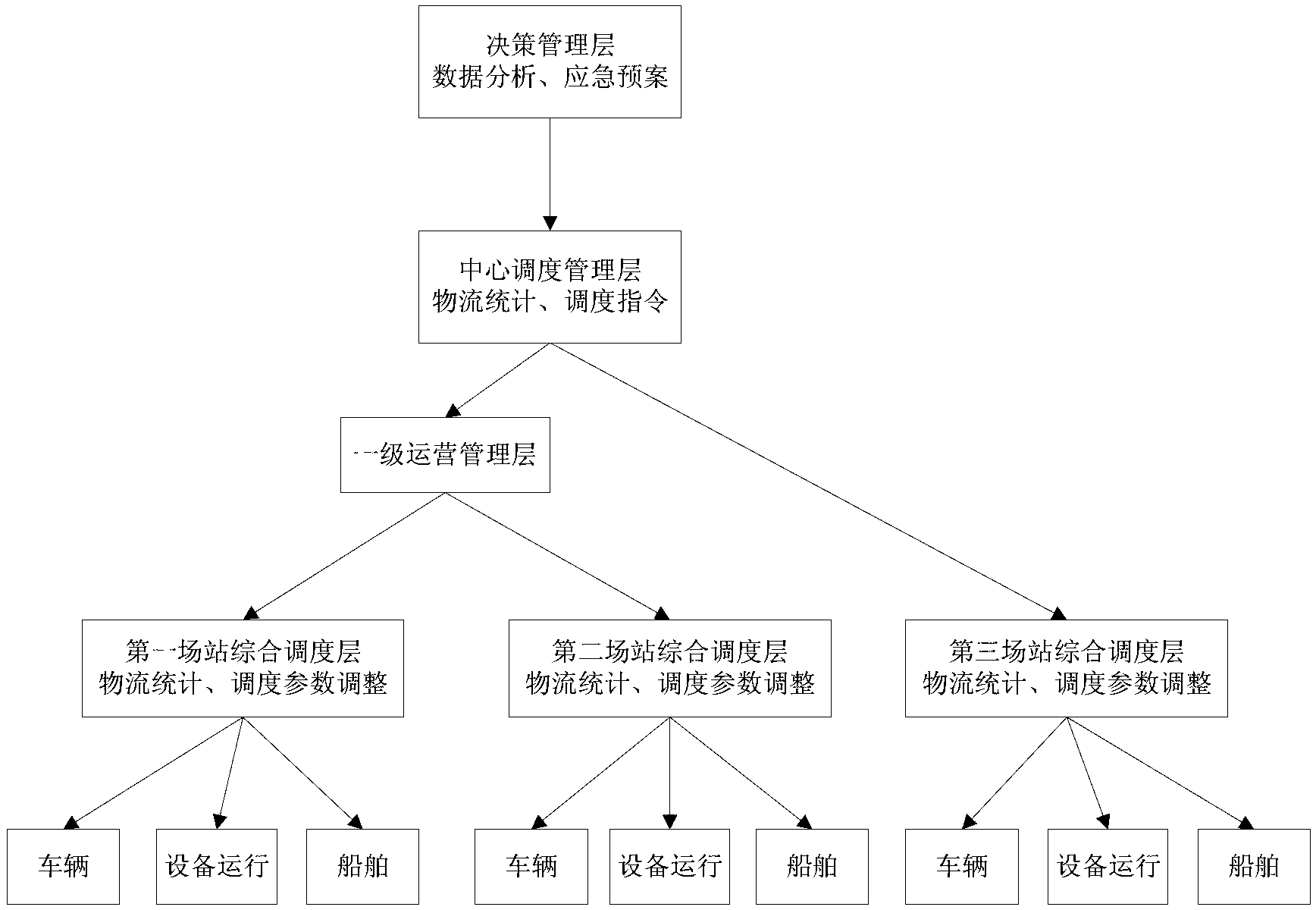
InactiveCN102708476AMeet extension requirementsSatisfy securityLogisticsRefuse collectionDecision management
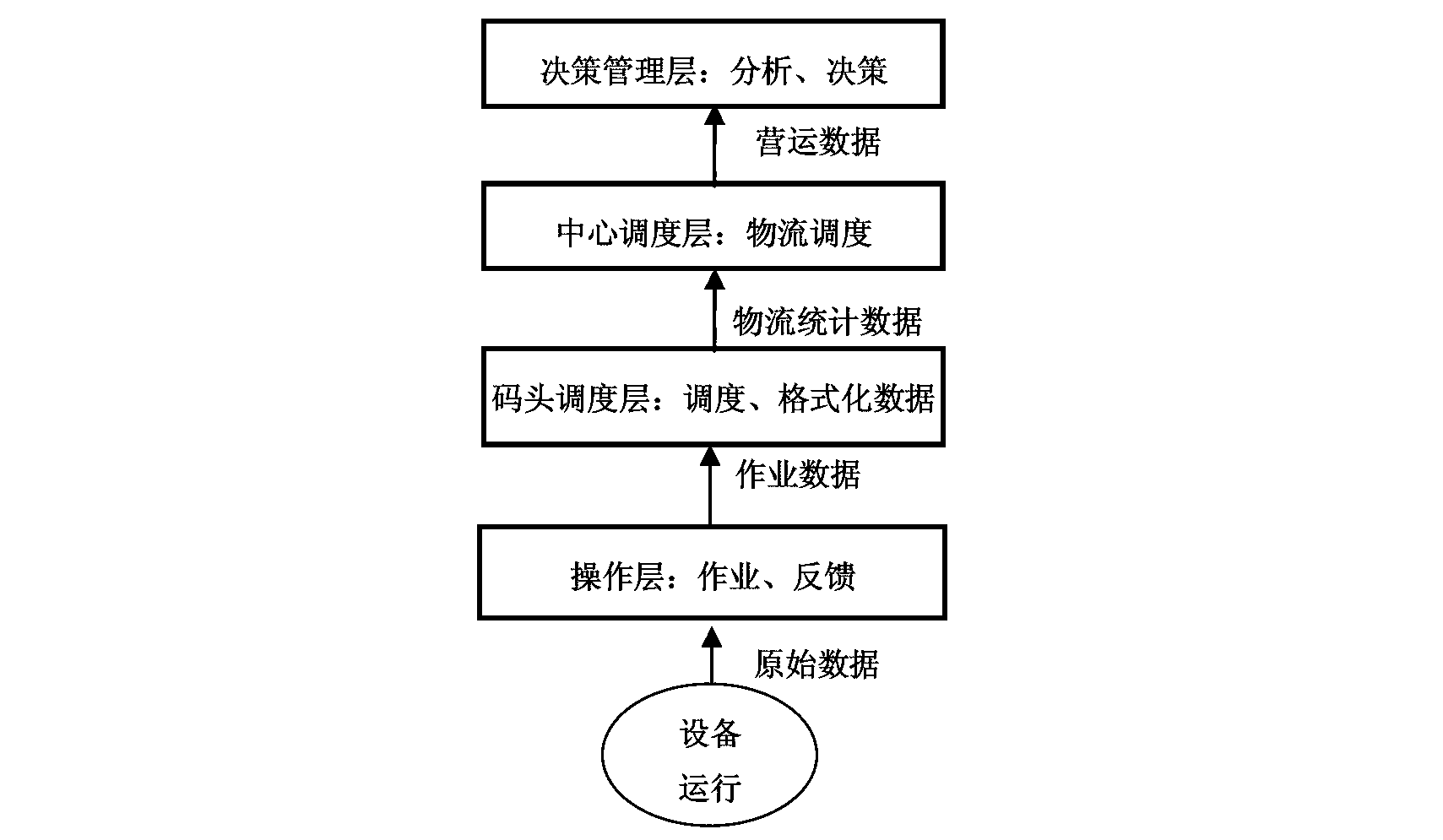
The invention provides an IoT (Internet of Things)-technology-based refuse collection management system which comprises a decision management layer, a center dispatching management layer and a dock comprehensively-dispatching management layer from top to bottom. A data processing flow of the refuse collection management system is implemented in a logistics mode, and the refuse collection management system comprises an operating layer, a wharf dispatching layer, a center dispatching management layer and a decision management layer, wherein the operating layer generates operation information and then feeds back or transfer the operating information to the wharf dispatching layer through the system and each hardware device interface, and after the operating information is formatted, final statements and final reports are formed and uploaded to the center dispatching layer, and then the center dispatching layer organizes the final statements and the final reports and then transfers operating data to the decision management layer. The refuse collection management system comprises an operation monitoring command center (as an upper dispatching center) and an operation management subsystem comprising a transfer station operation management system, a wharf and storage-yard operation management system, a ship dispatching management system, a refuse wharf short-barge operation management system, an emergency dispatching command system and a data statistical analysis and statement management system.
Owner:上海中海龙高新技术研究院
Searchable public key encryption method
InactiveCN104852801ASatisfy securityProtect member privacyPublic key for secure communicationSpecial data processing applicationsData fileKeyword cipher
The invention discloses a searchable public key encryption method. Firstly, a receiver set is defined, a data owner selects keywords, a file is encrypted by the adoption of an encryption algorithm, the keywords are encrypted by the adoption of a searchable public key encryption scheme, the data owner employs information of the to-be-assigned receiver to generate keyword ciphertext, and the keyword ciphertext and the encrypted data file are stored in a cloud server. If the data owner can confirm that those users can access their own data, a special trap door is sent to each confirmed receiver. As long as the receiver obtains his own trap door, the receiver can generate the correct keyword trap door, and the server can find out the searched file. According to the method, the searchable public key encryption scheme for supporting a plurality of receivers is designed in a public key encryption environment, the security of the keyword ciphertext and the keyword trap door can both be satisfied, and the membership privacy of the assigned receivers can be protected by the scheme.
Owner:SHAANXI NORMAL UNIV
Construction method for high artesian area ultra-deep foundation pit
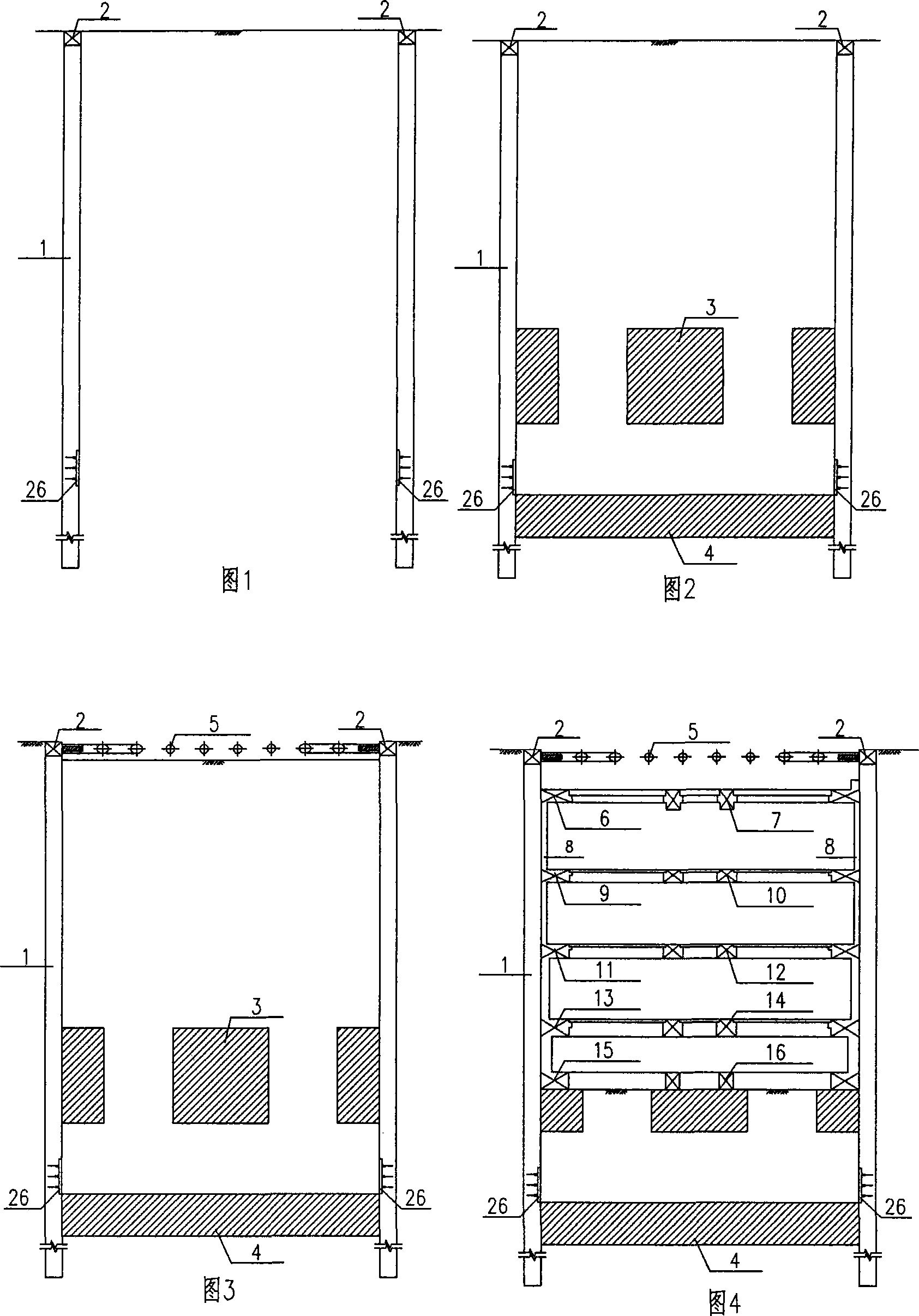
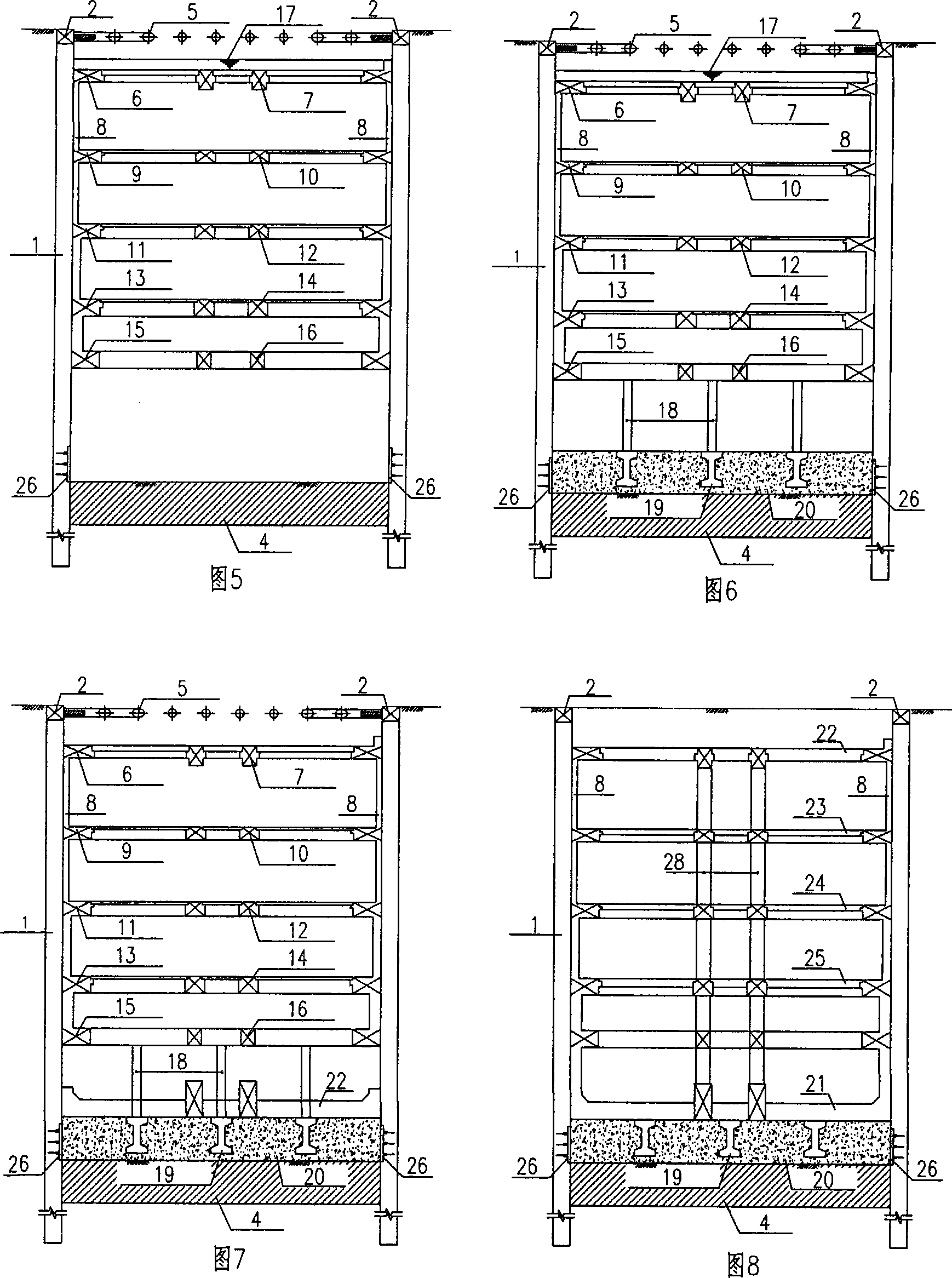
InactiveCN101139838AProtect the surrounding environmentReduce project costExcavationsPurlinSafety coefficient
The invention relates to track traffic and tunnel categories, in specific to a super-deep foundation pit construction method for high pressure water areas. The method adopts underground continuous walls (or drilling piles, drill biting piles and corresponding waterproof curtains) as enclosure structures and inner supports as support structures; in the premises of complying with pressure water safety factor that is required in specifications, perform open excavation down to a certain elevation; during the course of open excavation method, carry out casting for surrounding purlins, supports and upper side walls; then, add water into the foundation pit, and the water injection height should guarantee the excavation to the bottom can resist pressure water and meet certain safety factors; perform underwater excavation down to the baseplate elevation and overbreak a certain depth for underwater bottom closing concrete cast; then, pump water out of the foundation pit before casting baseplate and back-casting remaining internal structures.
Owner:SHANGHAI TUNNEL ENGINEERING RAILWAY TRANSPORTATION DESIGN INSTITUTE
Flame-retarding light-diffusing polycarbonate resin composite for LED lamp and preparation method thereof
The invention discloses a flame-retarding light-diffusing polycarbonate resin composite for an LED (light emitting diode) lamp and a preparation method thereof, and the flame-retarding light-diffusing polycarbonate resin composite for the LED lamp comprises the following components by weight percent: 75-90% of polycarbonate resin, 5-10% of brominated polycarbonate, 2-5% of an organic-silicon flame retardant, 0.5-8% of a light-diffusing agent, 0.1-0.5% of a heat stabilizer, 0.1-0.5% of a light stabilizer and 0-1% of a processing aid. The invention adopts organic and inorganic light diffusion compound to overcome the defect that haze and light transmittance are difficult to balance by using a single diffusing agent, and the environmentally-friendly brominated polycarbonate serving as a flame retardant and the organic-silicon flame retardant are compounded to achieve minimal influence on light transmittance under the condition of high-efficiency flame retarding and broaden the application scope of LED lampshades made of light-diffusing polycarbonate resin. The LED lampshade made of the composite disclosed by the invention has the outstanding advantages of high flame retarding performance of and balanced haze and light transmittance, and ensures the security while being used in harsh environmental conditions.
Owner:GUANGZHOU SUPER DRAGON ENG PLASTICS
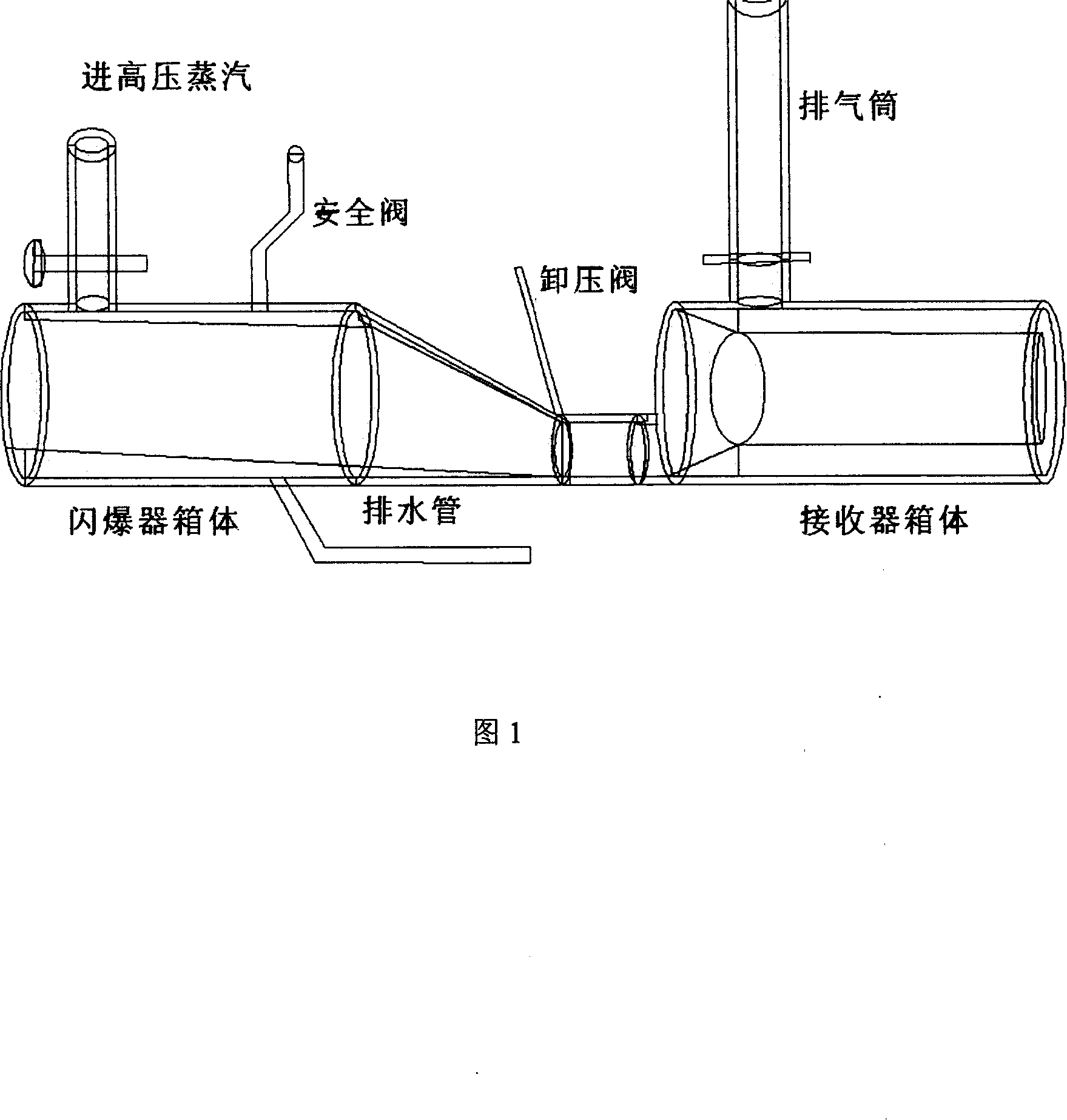
Hemp-like bast fibre flash explosion-high temperature boiling combination degumming technique
The flash bursting and high temperature digesting process for degumming hemp bast fiber includes pre-treatment, flash bursting and high temperature digesting to eliminate residual pectin, hemicellulose and lignin from hemp bast fiber, and raise the fiber fracturing degree and softness. The flash bursting and high temperature digesting process has ideal degumming effect, obvious non-fiber component eliminating effect and less pollution, and the degummed hemp bast fiber has high cellulose rate, high fiber fracturing degree and high fiber flexibility.
Owner:THE QUARTERMASTER EQUIPMENT RESEARCH INSTITUTE OF THE GENERAL LOGISITIC DEPARTME
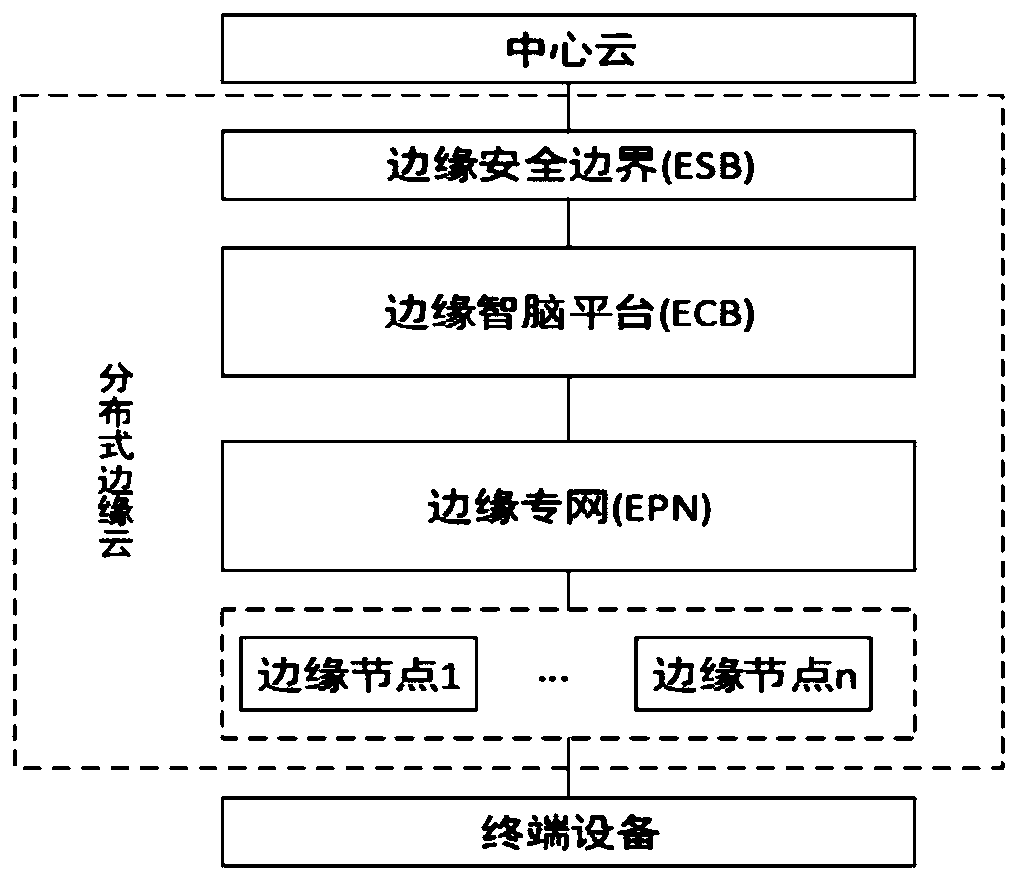
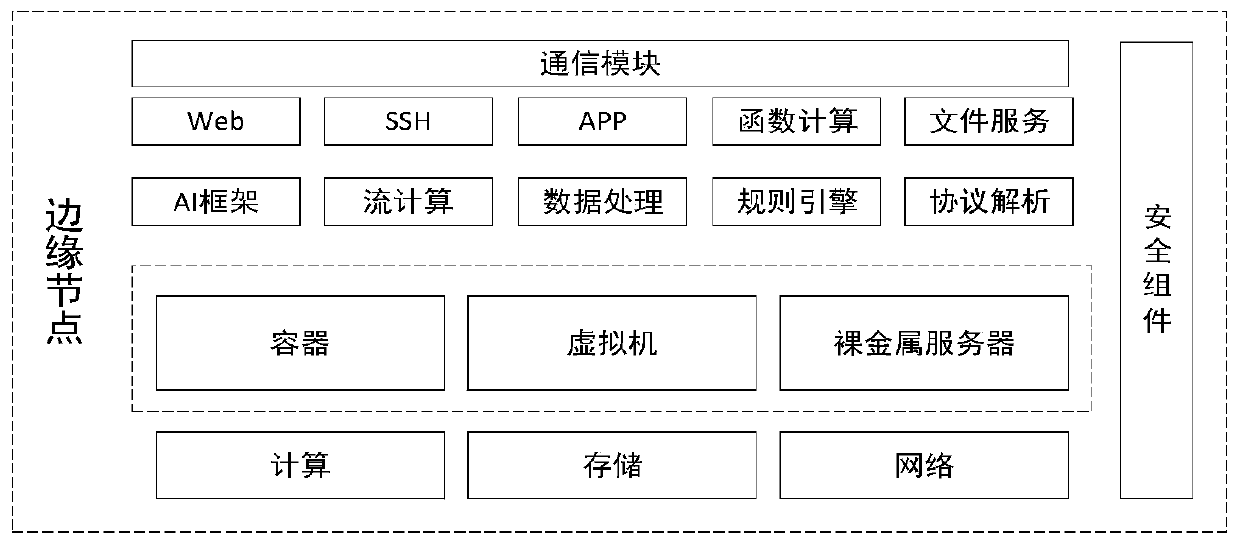
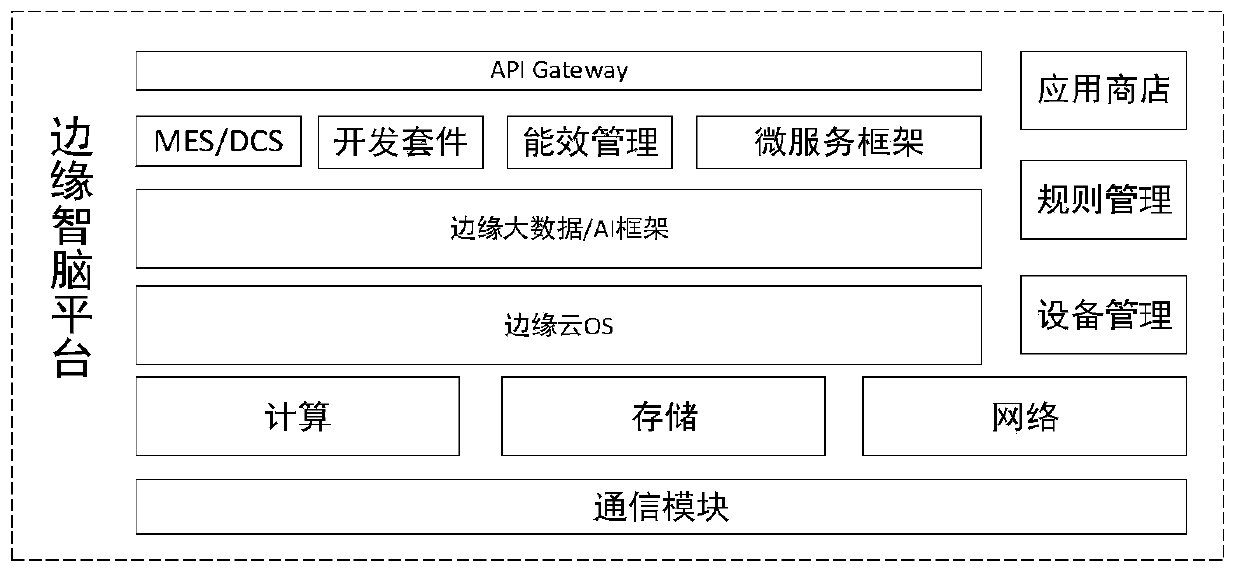
A distributed edge cloud system architecture
ActiveCN110572448AReduce interactionAchieve decouplingTransmissionCommunications securityTime delays
The invention belongs to the technical field of edge cloud computing systems, and discloses a distributed edge cloud system architecture. The architecture comprises an edge node, an edge computing intelligent brain platform layer and an edge security boundary layer, wherein the edge node communicates with the edge computing intelligent brain platform layer through an edge private network; an intelligent brain platform of the edge computing intelligent brain platform layer is in butt joint with a plurality of different edge nodes to realize distributed deployment; data are acquired through external terminal equipment accessed by the edge node and uploading the data to the edge node for processing; the edge computing intelligent brain platform layer communicates with the center cloud or theindustry cloud through the edge security boundary layer; the edge security boundary layer serves as an interface for communication between the edge cloud system and the center cloud or the industry cloud and is used for guaranteeing the communication security between the edge cloud and the center cloud or the industry cloud; the system architecture has the characteristics of low time delay and high security, and meets the requirements of agile connection, real-time service, data optimization, intelligent application, security and privacy protection.
Owner:FENGHUO COMM SCI & TECH CO LTD
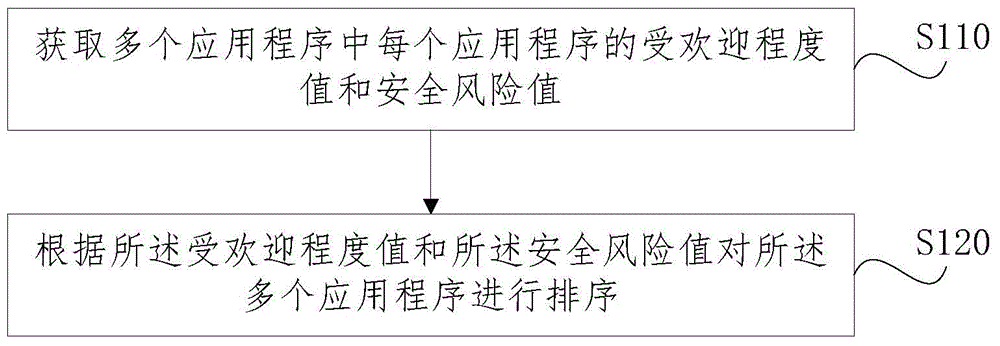
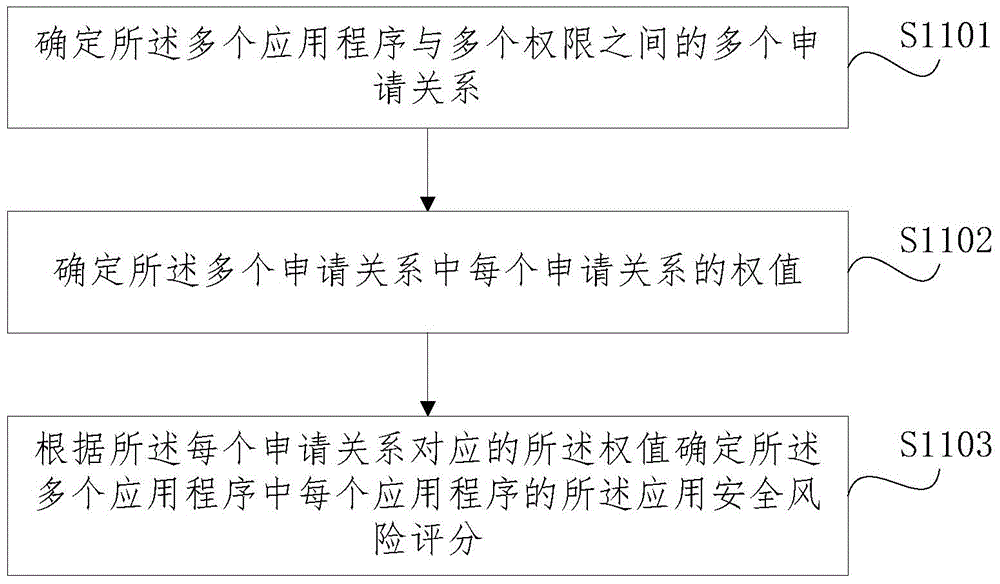
Application program recommending method and device
ActiveCN104090967AMeet popSatisfy securityPlatform integrity maintainanceCommerceSecurity privacyMultiple applications
The embodiment of the invention discloses an application program recommending method and device. The method comprises the steps that the popularity degree value and the safety risk value of each application program in a plurality of application programs are obtained; the application programs are sorted according to the popularity degree values and the safety risk values. According to the technical scheme, the application programs are sorted according to the popularity degree values and the safety risk values of the application programs, therefore, the application program which can better meet the popularity preference and the safety preference of a user can be recommended to the user preferentially, and safety privacy can be guaranteed while the user enjoys the application program with abundant functions.
Owner:BEIJING ZHIGU RUI TUO TECH
Method for inhibiting acrylamide formation and use thereof
InactiveUS20060194743A1Suppressing formation of acrylamideSatisfy securityBiocideCosmetic preparationsIngested foodOrganic matter
An object of the present invention is to establish a method for actively suppressing the formation of acrylamide, which is formed by heating edible materials at a relatively high temperature, and uses thereof, and to provide more safe compositions such as foods, beverages, cosmetics, pharmaceuticals, and intermediates thereof. The present invention solves the above object by providing: a method for suppressing the formation of acrylamide, comprising the steps of incorporating an organic substance having an ability of suppressing the formation of acrylamide into an edible material having a possibility of forming acrylamide by heating and heating the resulting mixture, when heating the edible material; compositions such as foods, beverages, cosmetics, pharmaceuticals, and intermediates thereof, produced by the method, whose possibility of forming acrylamide is suppressed; and compositions such as foods, beverages, cosmetics, pharmaceuticals, and intermediates thereof, having an ability of suppressing the formation of acrylamide, comprising an organic substance having an amino group(s) and / or saccharides having an ability of forming acrylamide and organic substance having an ability of suppressing the formation of acrylamide.
Owner:OKU KAZUYUKI +3
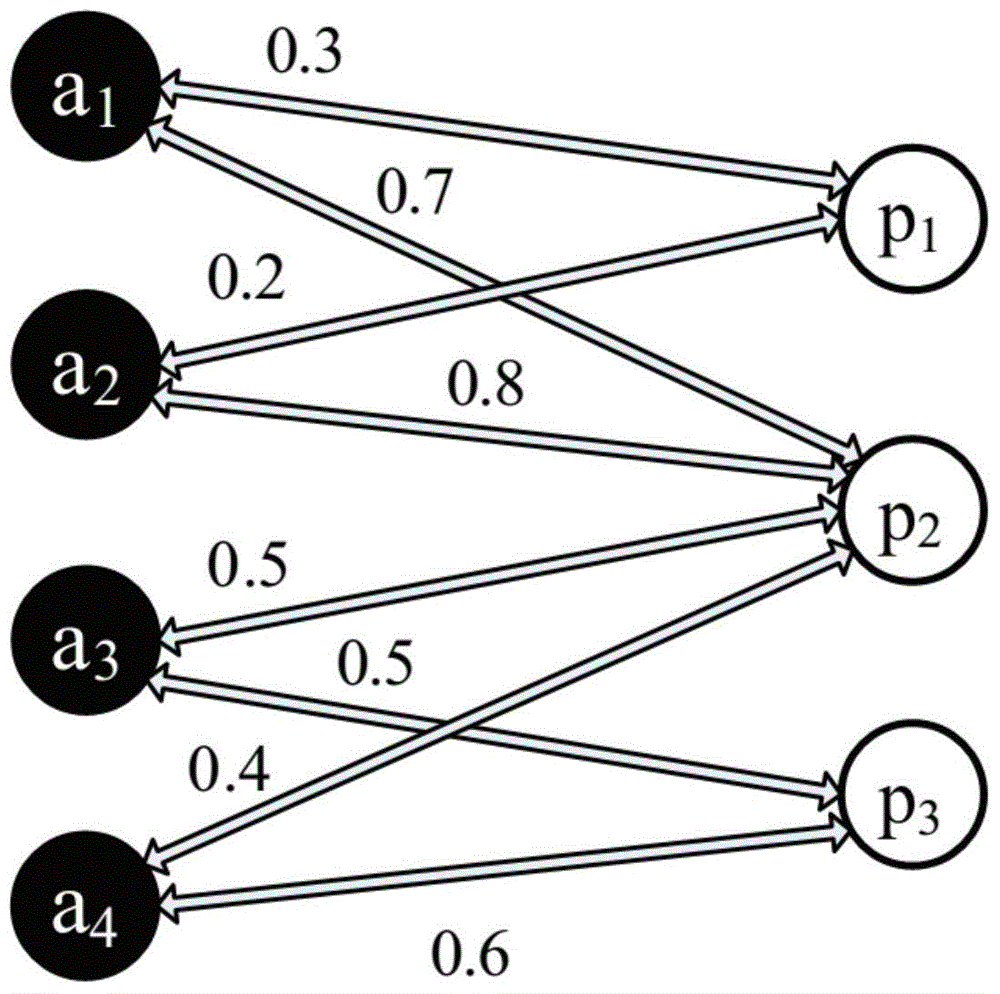
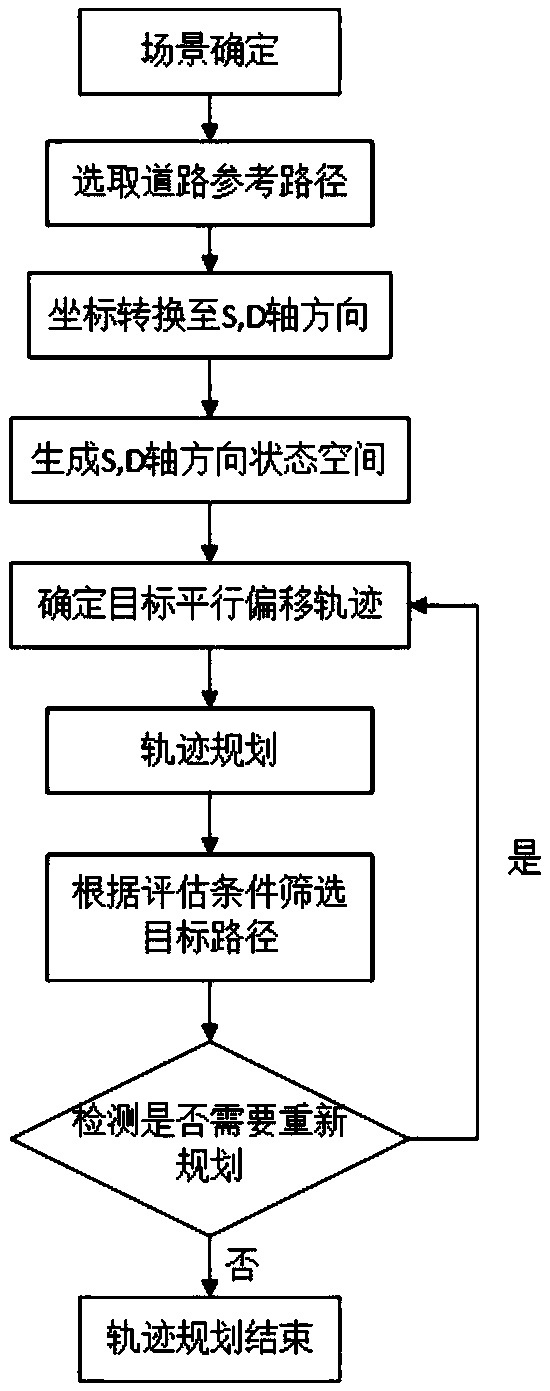
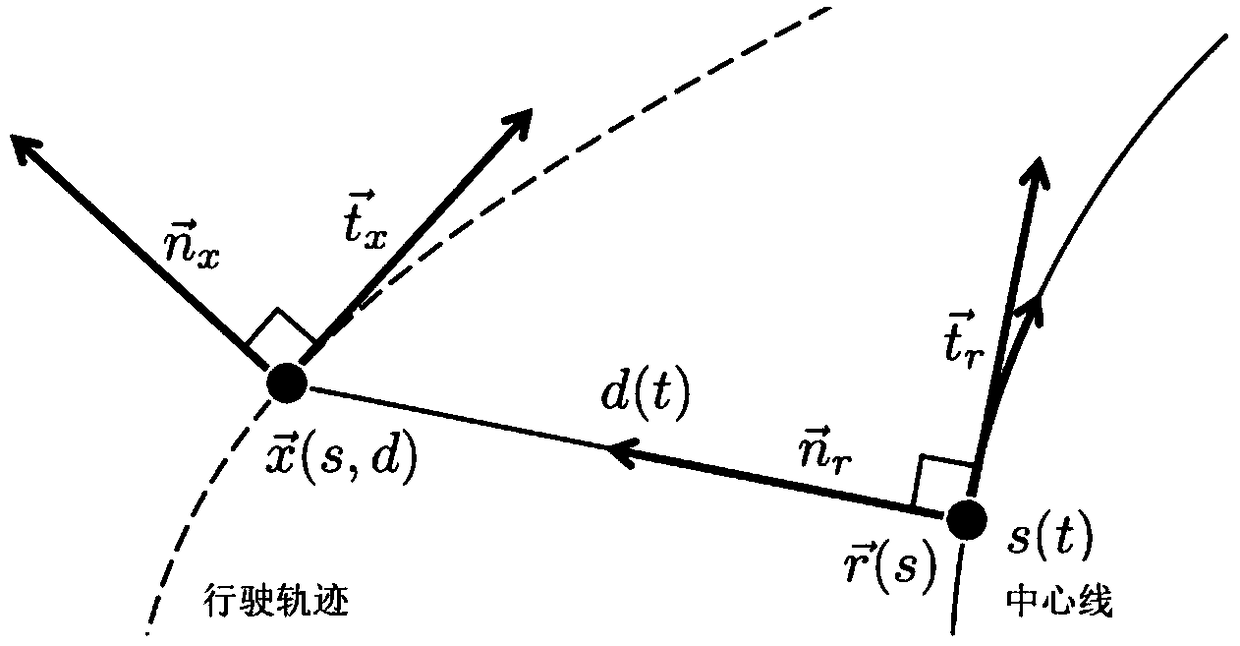
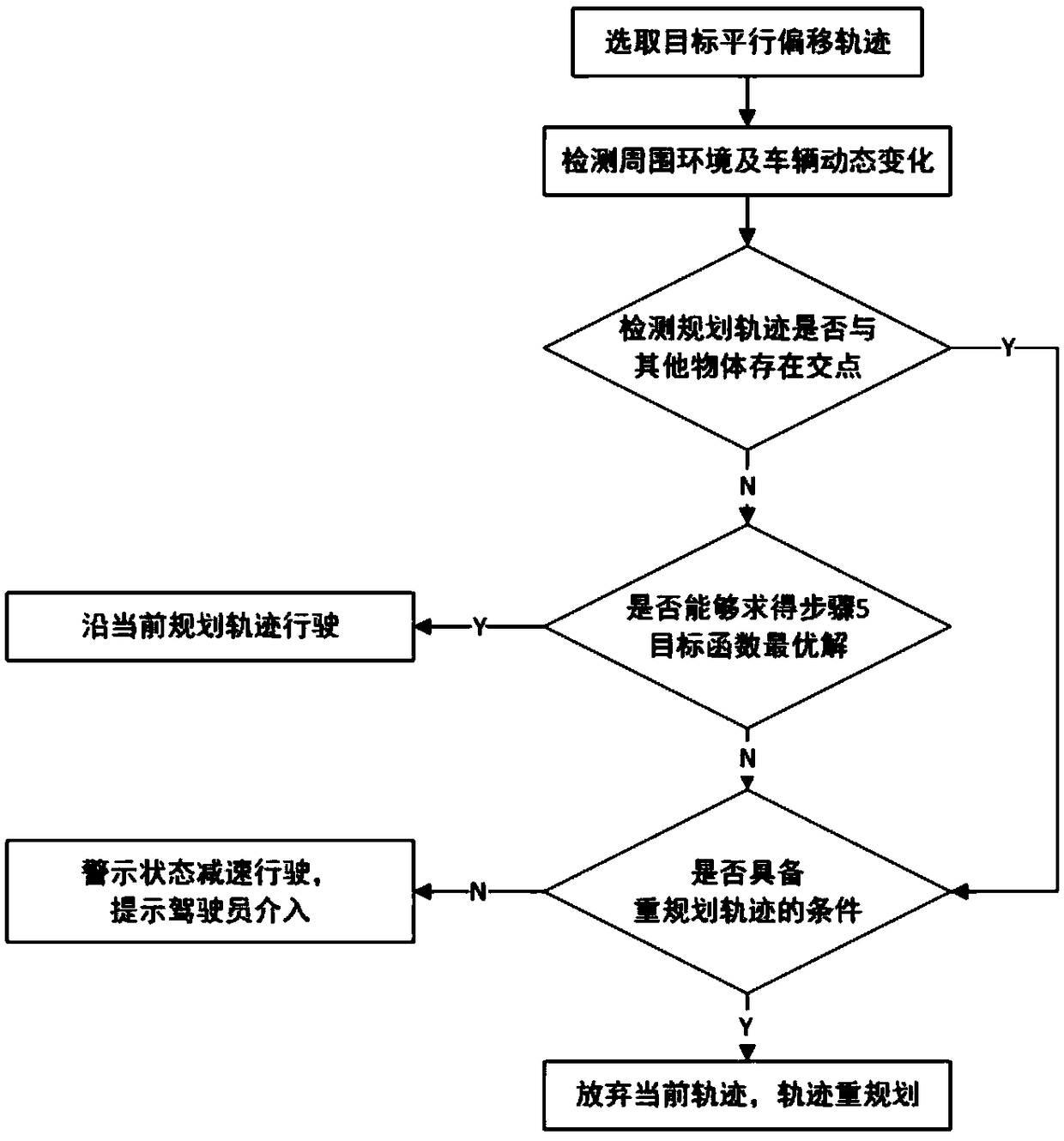
Dynamic trajectory planning method for performing obstacle avoidance and overtaking based on lane line parallel shift
InactiveCN109324620AImprove efficiencySatisfy securityPosition/course control in two dimensionsVehiclesState spacePlanning approach
The invention relates to a dynamic trajectory planning method for performing obstacle avoidance and overtaking based on lane line parallel shift. Different state spaces are established for different road scenes, so that trajectory planning under different working conditions is achieved; and a more accurate subsequent real-time trajectory is planned through coordinate conversion and decoupling. Themethod has the beneficial effects that the different state spaces are established for the different road scenes, so that the effective and accurate trajectory planning under the different working conditions is achieved; through the coordinate conversion and decoupling, the more accurate real-time trajectory planning is achieved for a subsequent trajectory planning party; a planned trajectory screening objective function and constraint conditions are set, so that the trajectory planning efficiency is improved, and the safety, comfort and stability requirements of trajectory planning are met; and evaluation conditions for ensuring the path consistency are set, so that the situation that unsafe factors are generated for a planned path due to environmental changes during vehicle running is avoided, and a dangerous warning of the planned path can be found in time to carry out trajectory re-planning or a driver can be reminded to carry out intervention operation when an optimal path cannotbe selected.
Owner:北京主线科技有限公司
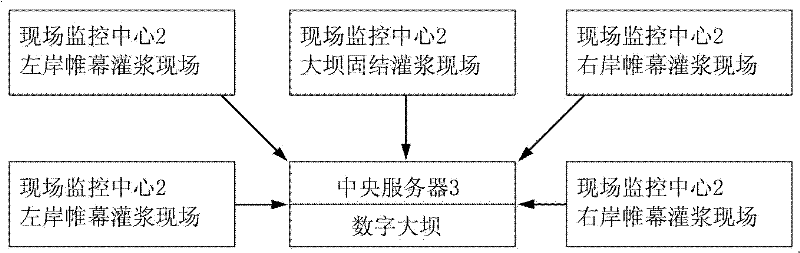
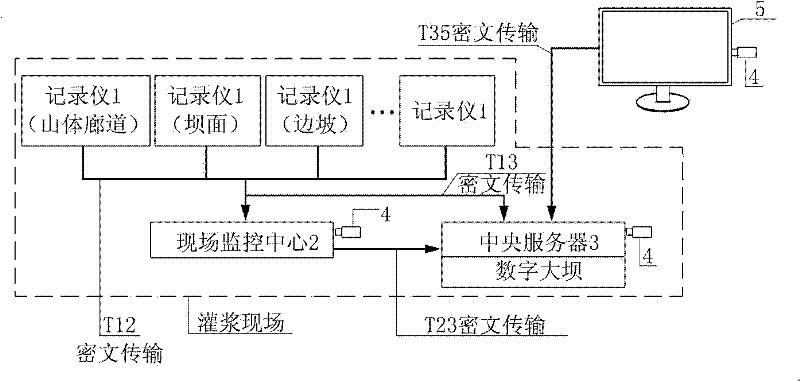
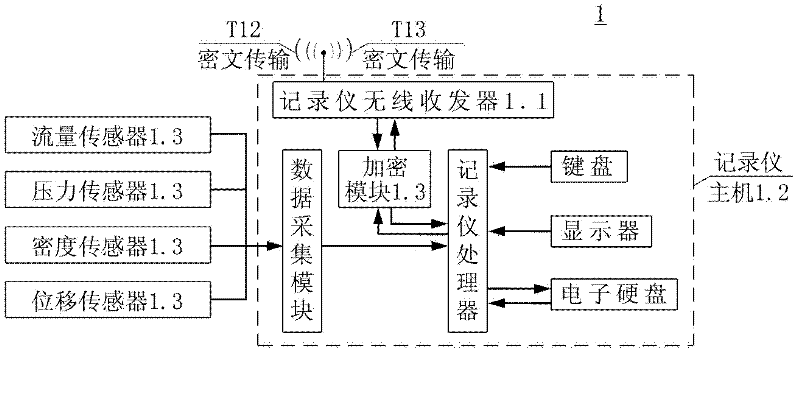
Method and system for monitoring grouting process on site
InactiveCN102393711ASolve the problem of few and cannot monitor the scattered construction surfaces at the same timeAvoid getting out of controlTotal factory controlProgramme total factory controlSite monitoringRemote control
The invention discloses a method and a system for monitoring grouting process on site. The method comprises the steps as follows: firstly, a site monitoring center is arranged among a plurality of grouting recorders, a central server is arranged in a digital dam behind, and the three transmit grouting data in a wired or wireless coded way; secondly, a system device is started by codes and a softdog; thirdly, in the measuring, recording and transmitting of the recorders, the monitoring center controls the recorders remotely by a network so as to discover suspicious data, interrupt logging, andrequire to upload data and process on site, and when a value exceeds a set value, an alarm is used for shutting down automatically and recording data, thereby preventing project quantities from beingout of control; fourthly, programs for checking the on-line state of the recorder and the like are arranged in a host machine of the monitoring center, thereby avoiding cheating; fifthly, the monitoring center can fix the position of the recorder, thereby being beneficial to managing equipment on site; and sixthly, after ensuring that the data is reliable, the data can be uploaded on a server to be stored. By the method and the system, the problem of dispersive monitoring due to few supervisors can be solved, and the data safety and project quality are ensured; the 3G (the third generation telecommunication) transportation has a low cost and is reliable; by adopting the wireless network, rewiring is avoided when a construction surface is changed; and a manager can realize the remote control without being on site.
Owner:CHINA THREE GORGES CORPORATION +1
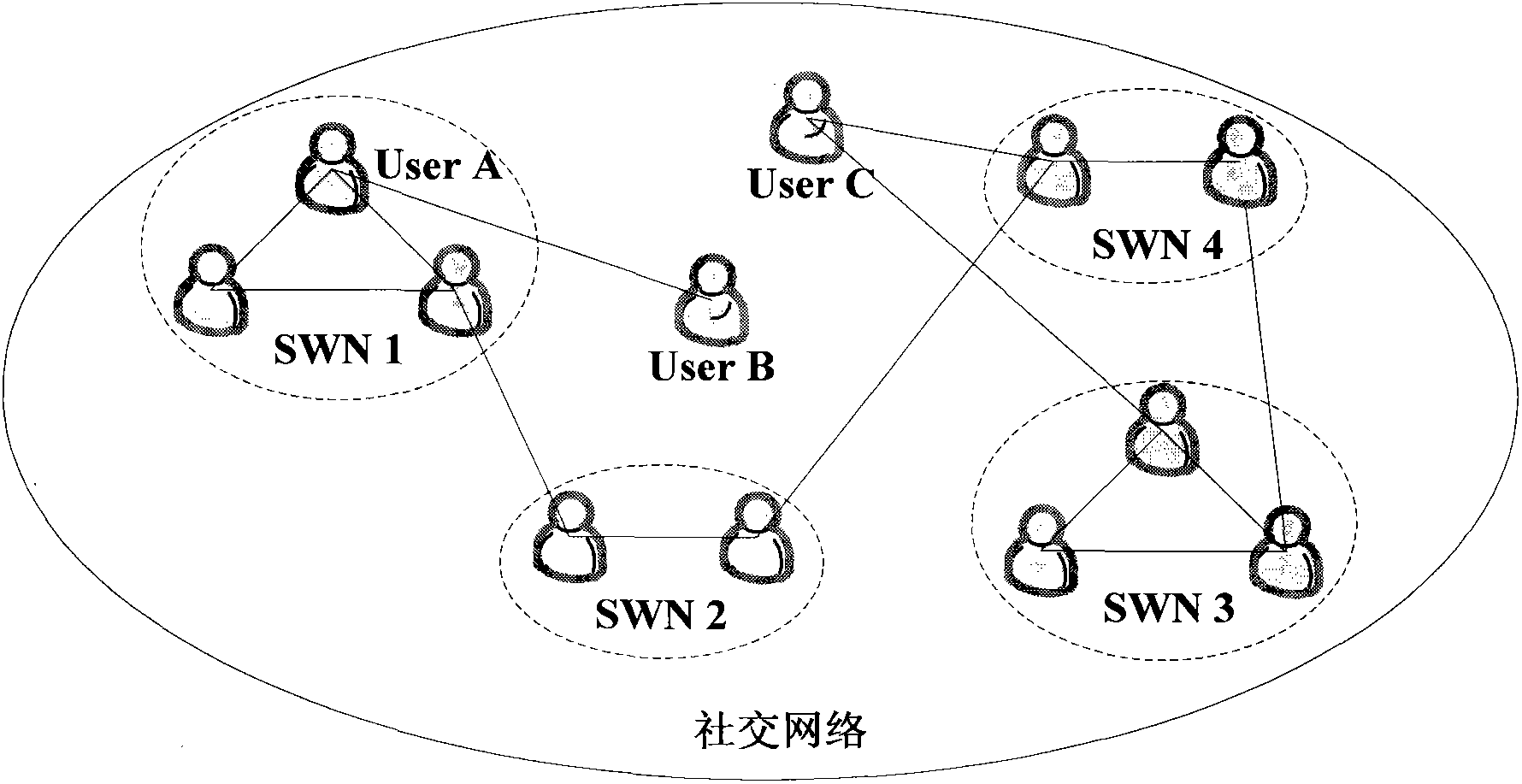
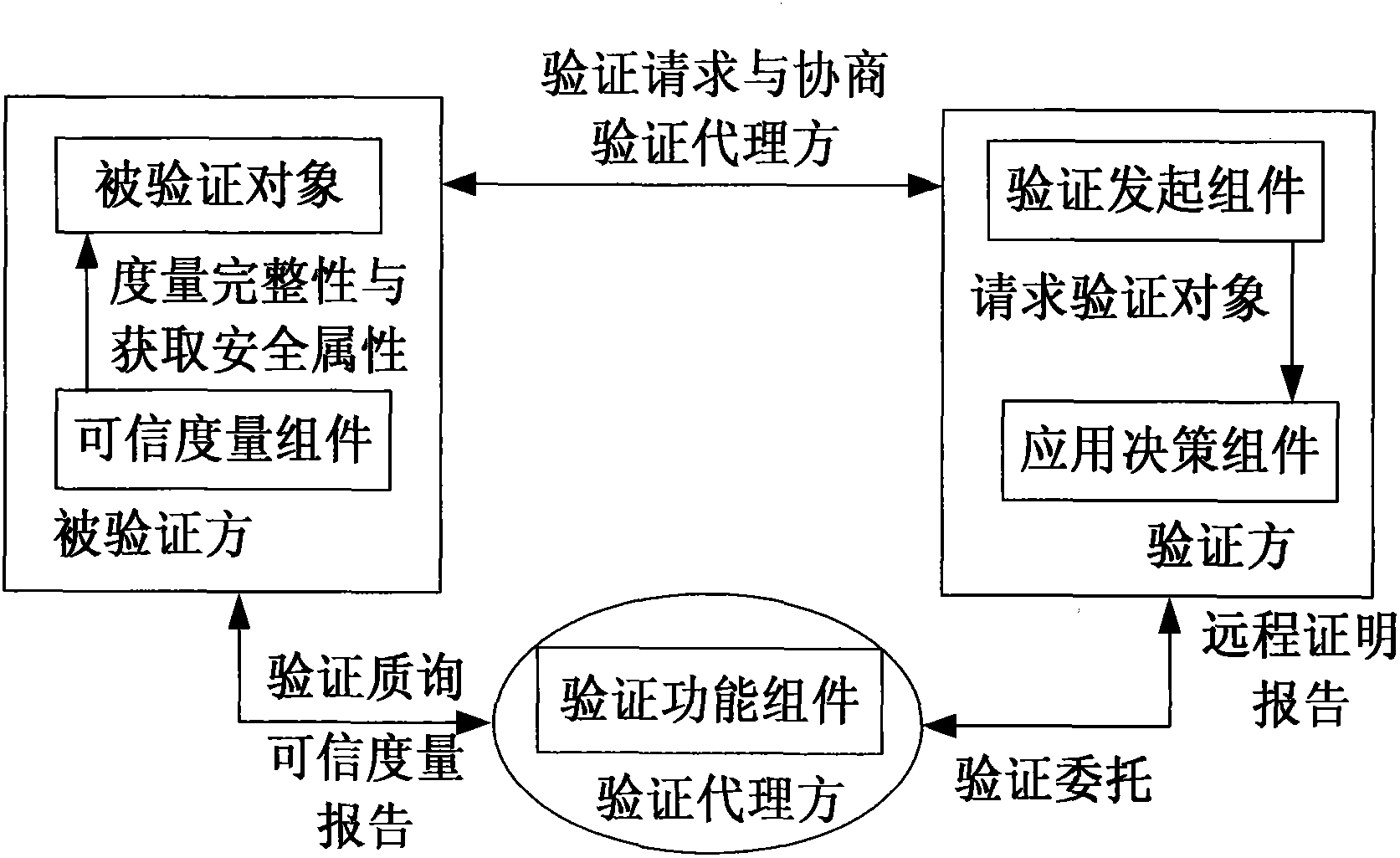
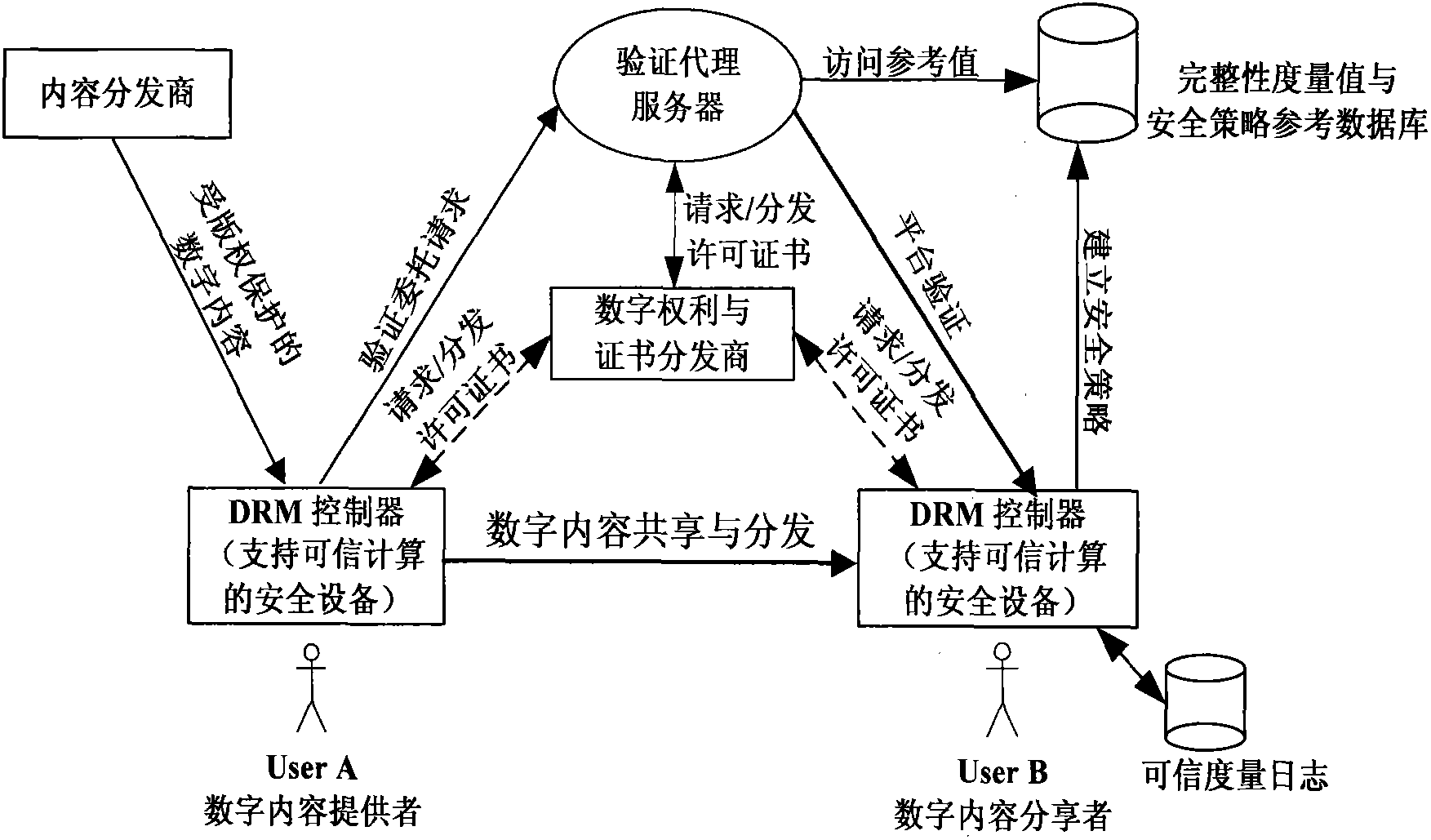
Digital content distribution method for multimedia social network
The invention relates to the technical field of internet, in particular to a digital content distribution method for a multimedia social network. A digital content safety credible distribution system frame and a specific distribution protocol flow are provided; through the certification by a third trusted party of equipment safety attribute and basic configuration before the digital contents are distributed to user terminal equipment from a server terminal, invaluable digital asset safety and controllable transmission are ensured; and a remote certification model which supports the third trusted party is introduced and applied to digital copyright protection of the multimedia social network. By the method, safe sharing and transmission of the digital contents in the multimedia social network are ensured, and the requirements of a user terminal equipment platform for privacy protection such as the safety attribute, basic configuration and the like are simultaneously met.
Owner:HENAN UNIV OF SCI & TECH
Method for extracting tea seed oil by using enzymatic hydrolysis method
ActiveCN102061217AHigh purityLight colorFatty-oils/fats productionOil and greaseEnzymatic hydrolysis
The invention discloses a method for extracting tea seed oil by using an enzymatic hydrolysis method, which comprises the following steps of: airing, unshelling, husking and pulverizing tea seeds; carrying out enzymolysis on the tea seeds in the material-liquid ratios of 1:3 to 1:5 at the extraction temperature of 40-60 DEG C for 1-5h with the enzyme quantity of 40-600U under the pH natural condition; centrifugally layering; adding an organic solvent into centrifugal liquid and extracting; and rotating and evaporating to obtain an oil sample. By adopting the scheme, the method has the advantages of low temperature for equipment operation, low energy consumption, high purity of extracted oil, low content of phospholipid, low acid value and low peroxide value, shallow color, low BOD (Biochemical Oxygen Demand) and COD (Chemical Oxygen Demand) values, easiness of treatment and less pollution, and the oil yield ratio is up to 23.1 percent.
Owner:HUAQIAO UNIVERSITY
Constant temperature and humidity storage box of gingers
InactiveCN102344019AKeep it brightLow costLiving organism packagingDomestic cooling apparatusElectricityEngineering
The invention discloses a constant temperature and humidity storage box of gingers, which belongs to article storage boxes. The structure of the constant temperature and humidity storage box of the gingers comprises a box body, a box door, a refrigerating unit, a control panel, a microcomputer control circuit, an ultraviolet sterilizing lamp, an electric heating pipe and an evaporator, wherein the back part and bottom of the box body are respectively provided with a back part partition board and a bottom partition board; an air inlet fan and an air exhaust fan are respectively arranged at the top of the back part partition board; a ventilating hole is formed on the bottom partition board; a water tank is formed at the lower part of the evaporator; a water tank outer cover is arranged on the outer wall of the box body corresponding to the water tank; a ventilating cover is arranged in the middle of the top of the box body; the ultraviolet sterilizing lamp is arranged on the box top in the interior of the box body; a temperature and humidity sensor is arranged on the side wall of the middle part of the box body; and the microcomputer control circuit is electrically connected with the control panel, the temperature and humidity sensor, the refrigerating unit, the air inlet fan, the electric heating pipe, the air exhaust fan, the ultraviolet sterilizing lamp and the evaporator respectively. The constant temperature and humidity storage box of the gingers has the characteristics of good ventilating and heat radiation condition and no generation of stuffiness and decayed gingers; and the temperature and humidity as well as plant diseases and insect pests can be effectively controlled.
Owner:VEGETABLE RES INST OF SHANDONG ACADEMY OF AGRI SCI
Universal erection load simulation device
InactiveCN106372355ASatisfy the stationarityMeet reliabilityGeometric CADDesign optimisation/simulationLevel shiftingElectricity
The invention provides a universal erection load simulation device which comprises an erection load simulation device, a lower fulcrum moving device, an upper fulcrum moving device and a safety protection device; the universal erection load simulation device is mainly used in a vertical erection simulation test under the practical working conditions of idle load, full load and unbalance load to test and verify the erection time, the erection angle and the erection position accuracy, to test and verify the power matching of a power supply, an erection controller and an erection electric cylinder, to test and verify the performances of the pushing force, the operation speed, the level shifting stability and the gear shifting stability of the erection electric cylinder, and to verify the normal and abnormal power-loss brake performances in the erecting and leveling processes; the motion process of an erection mechanism is simulated, a motion parameter equation of each member is deduced, the overall process of change of the motion parameter is accurately reflected, the stress and the displacement of main stress parts of a launching vehicle are intuitively truly known and predicated, a weak link of a system is found out and improved, so that the requirements of rapidity, stability, reliability, safety and the like in the erection process of a guided missile are met.
Owner:BEIHANG UNIV
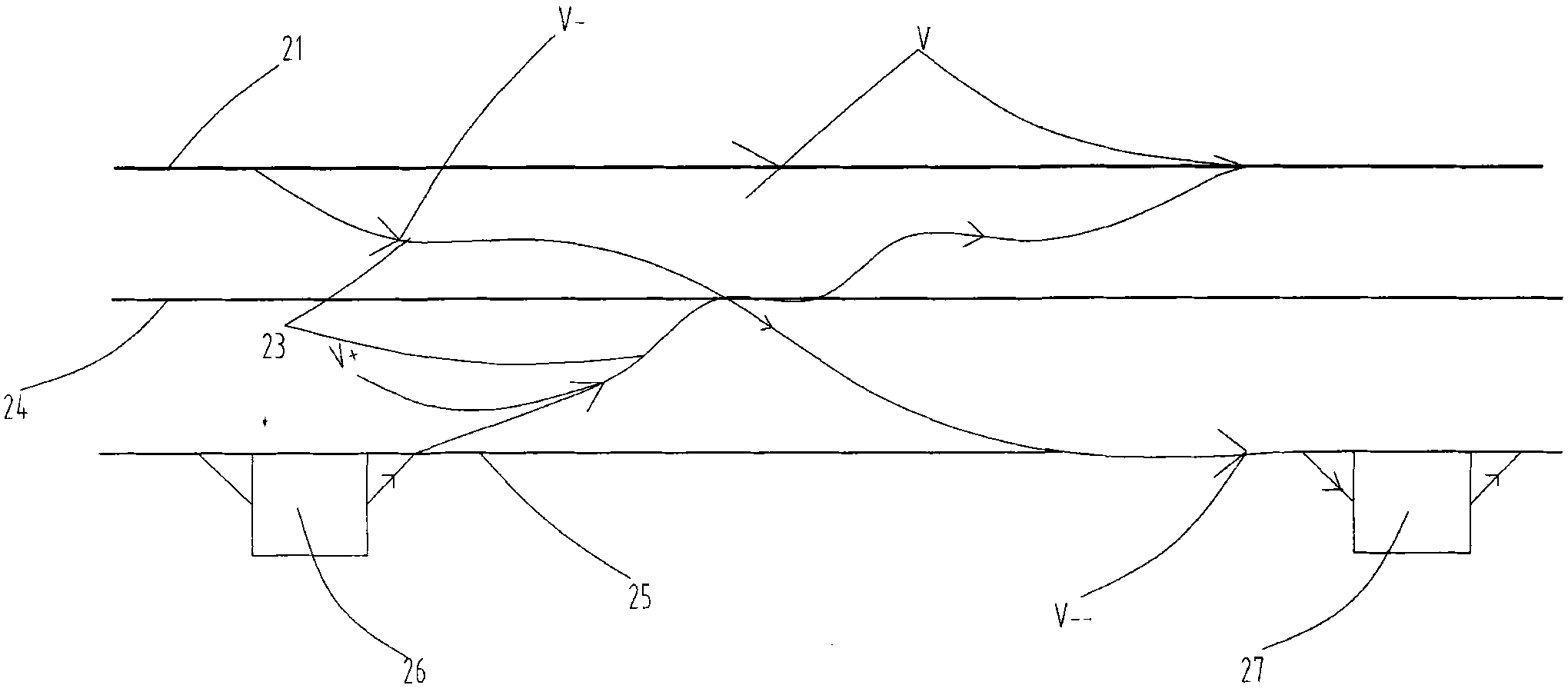
Urban unmanned electronic railcar taxi traffic system
InactiveCN101992782AFast processSatisfy securityRailway componentsRailway tracksInteraction systemsLow speed
The invention discloses an urban unmanned electronic railcar taxi traffic system. The traffic system comprises a combined rail, an unmanned electronic railcar taxi running on the combined rail and a central control computer of the traffic system, wherein the central control computer of the traffic system controls the running state of the unmanned electronic railcar tax on the combined rail. The technical scheme of the invention is as follows: the system consists of a high-speed rail, a speed-changing rail, a low-speed rail, an on-off rail, stations, a driving system, the central control computer of the system, a charge system, a detection system, a human-computer interaction system and a special vehicle. The urban unmanned electronic railcar taxi traffic system is integrated with the advantages of the subway, cars, buses and elevators, meets the requirement of rapidness, safety, economy, convenience and environmental protection of modern urban traffics, and the problem of urban traffic jam is solved fundamentally.
Owner:张婧
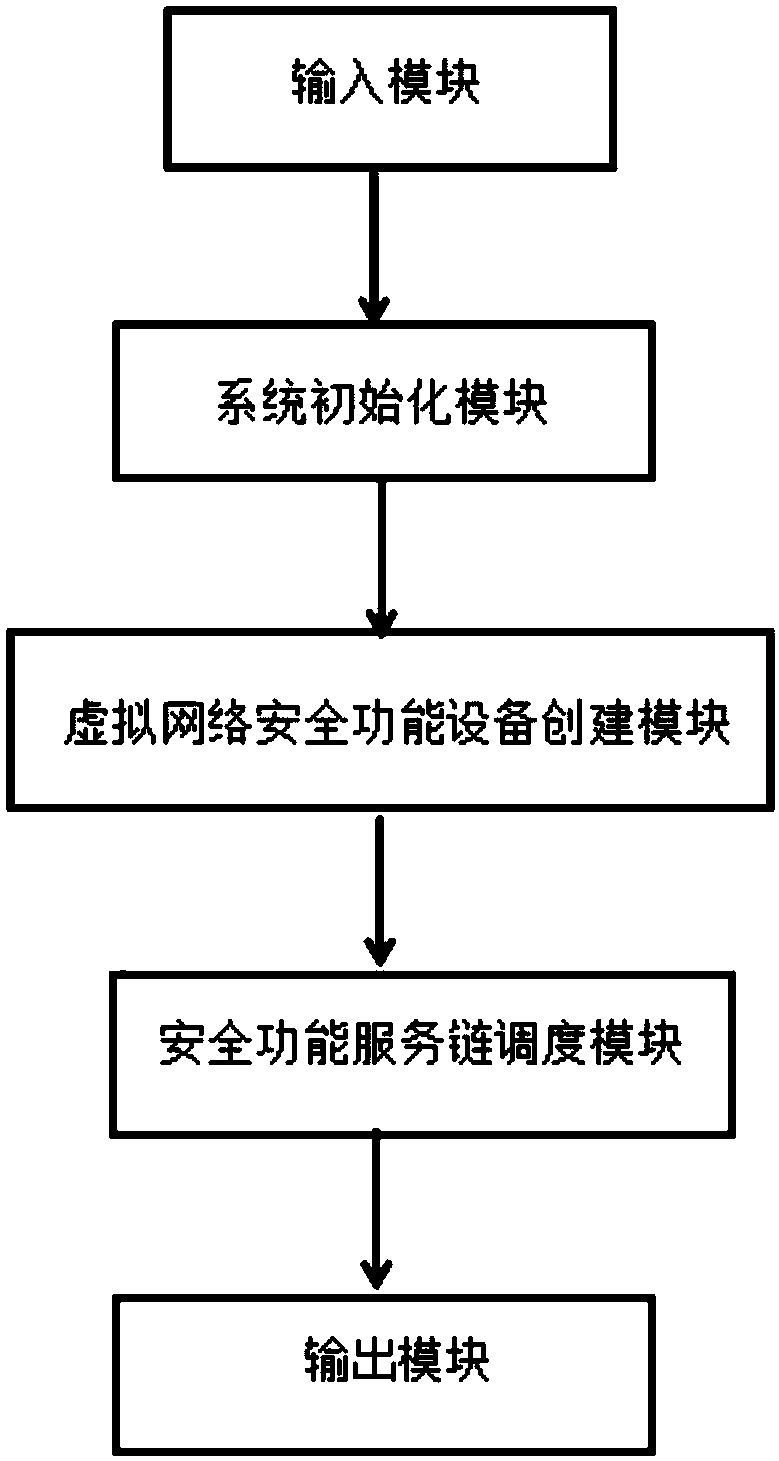
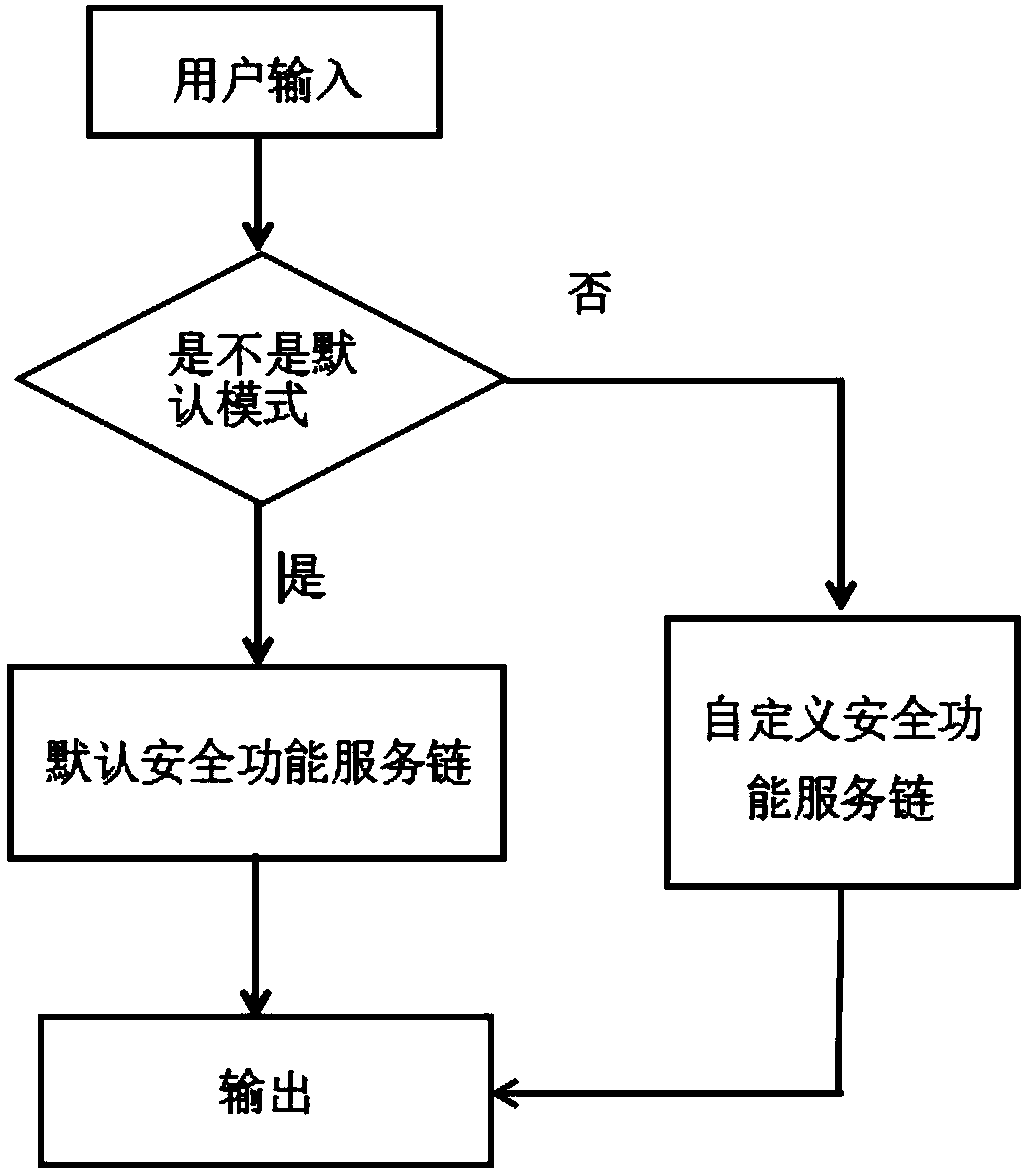
Network safety function service chain system based on cloud computing management platform Openstack
InactiveCN108833335ASolve complexityFix security issuesTransmissionTraffic capacityResource virtualization
The present invention relates to the technical field of network management and network safety, especially to a network safety function service chain system based on the cloud computing management platform Openstack. The system comprises an input module, a system initialization module, a virtual network safety device creation module, a safety function service chain dispatching module and an outputmodule which are in communication connection in order. The system solves the problem that the flow direction is complex and has no clear safe boundary in the cloud environment, meets the demands of different businesses for different safety levels and processing processes, is high in timeliness and flexible to be deployed, is not limited by geographic restrictions, can self-define the network safety function service chain, and can be applied to the various resource virtualized cloud environment networks.
Owner:SUN YAT SEN UNIV
Low-temperature-resistance polypropylene composition and preparation method thereof
The invention discloses a low-temperature-resistance polypropylene composition, which comprises the following components in percentage by weight: 40 to 75 percent of polypropylene resin, 15 to 45 percent of toughening system and 10 to 30 percent of mineral filler. The polypropylene resin is a propylene polymer of which the comonomers include ethylene, 1-butene and 1-hexylene, and the content of the comonomers is 5 to 20 percent. The toughening system comprises an elastomer and a toughening synergistic agent. The preparation method comprises the following steps: (1) adding a mineral filler anda polypropylene resin into a high-temperature mixer according to a certain ratio, pre-mixing at 170 to 250 DEG C, granulating, and cooling to obtain coarse material; and (2) uniformly mixing the coarse material with the left polypropylene resin, the elastomer and the toughening synergistic agent, adding the mixture to a double-screw extruder, melting and mixing at 180 to 230 DEG C, granulating, cooling, drying and packaging. The invention has the advantage that the low-temperature-resistance polypropylene composition can meet the safety and appearance use requirements of automobile industry and has high low-temperature impact resistance.
Owner:KINGFA SCI & TECH CO LTD +2
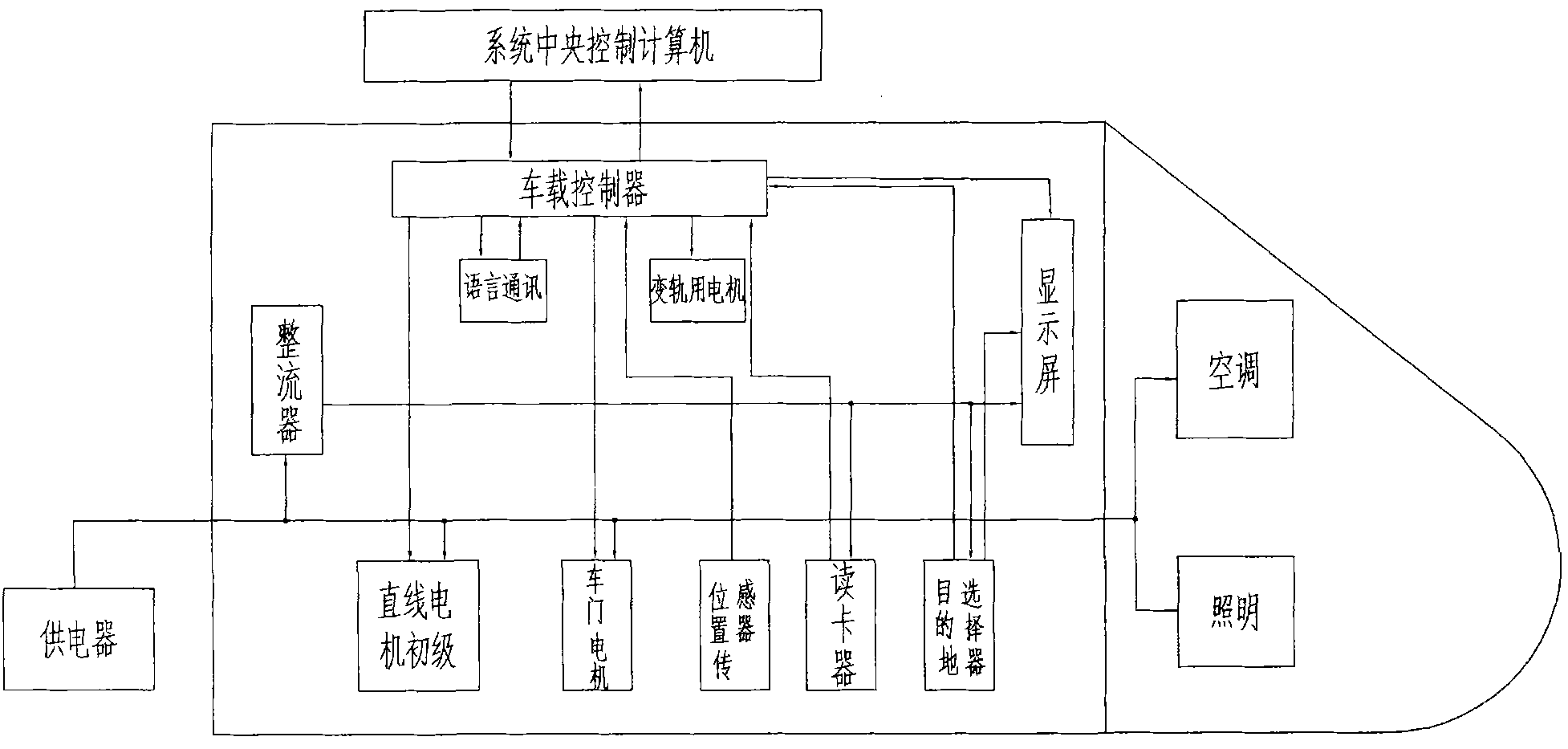
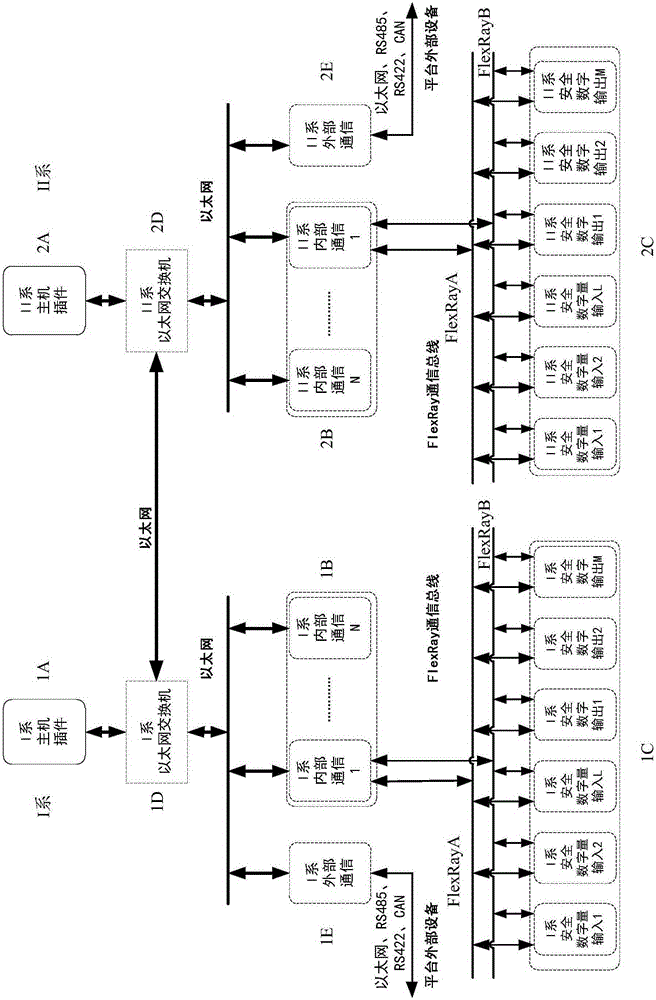
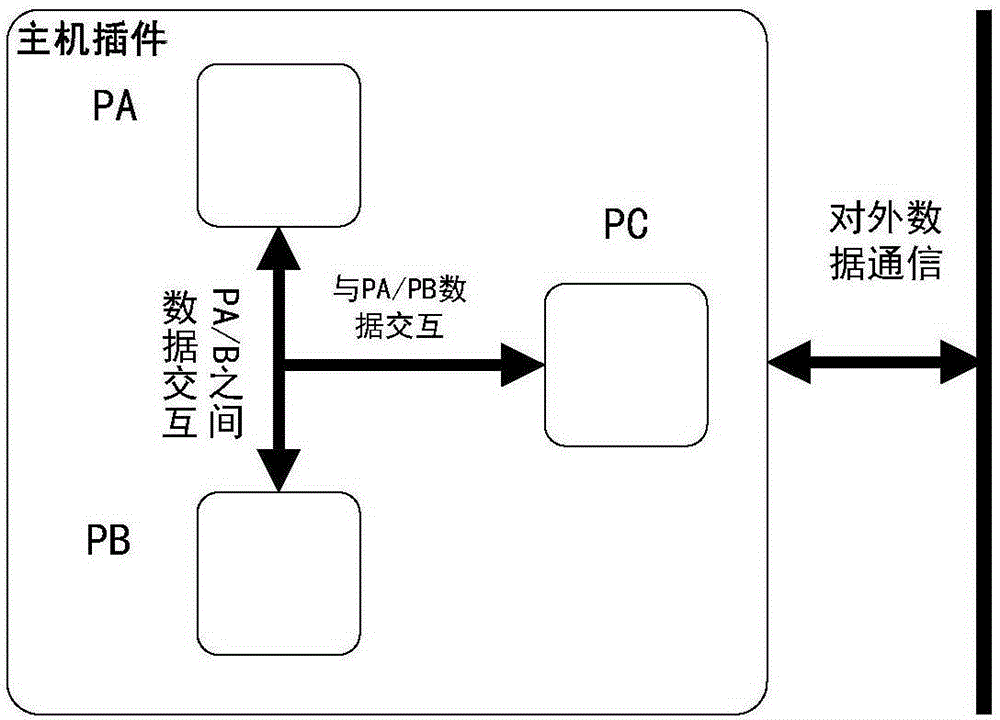
Secure computer platform used for rail transit
InactiveCN105159863AHeavy trafficSatisfy securityDigital computer detailsElectric digital data processingNetwork connectionOutput device
The invention provides a secure computer platform used for a rail transit. The secure computer platform used for the rail transit comprises a first host device, at least one second host device, a first communication transfer device, at least one second communication transfer device, a first input / output device, at least one second input / output device, an Ethernet and a FlexRay bus, wherein the first input / output device, the second input / output device, the first network connection end of the first communication transfer device and the third network connection end of the second communication transfer device are connected with the FlexRay bus, the second network connection end of the first communication transfer device and the fourth network connection end of the second communication transfer device are connected with the Ethernet, the first host device and the first input / output device are communicated through the Ethernet, and the second host device and the second input / output device are communicated through the Ethernet.
Owner:HUNAN CRRC TIMES SIGNAL & COMM CO LTD
A smart community property service and community service system based on the Internet of Things
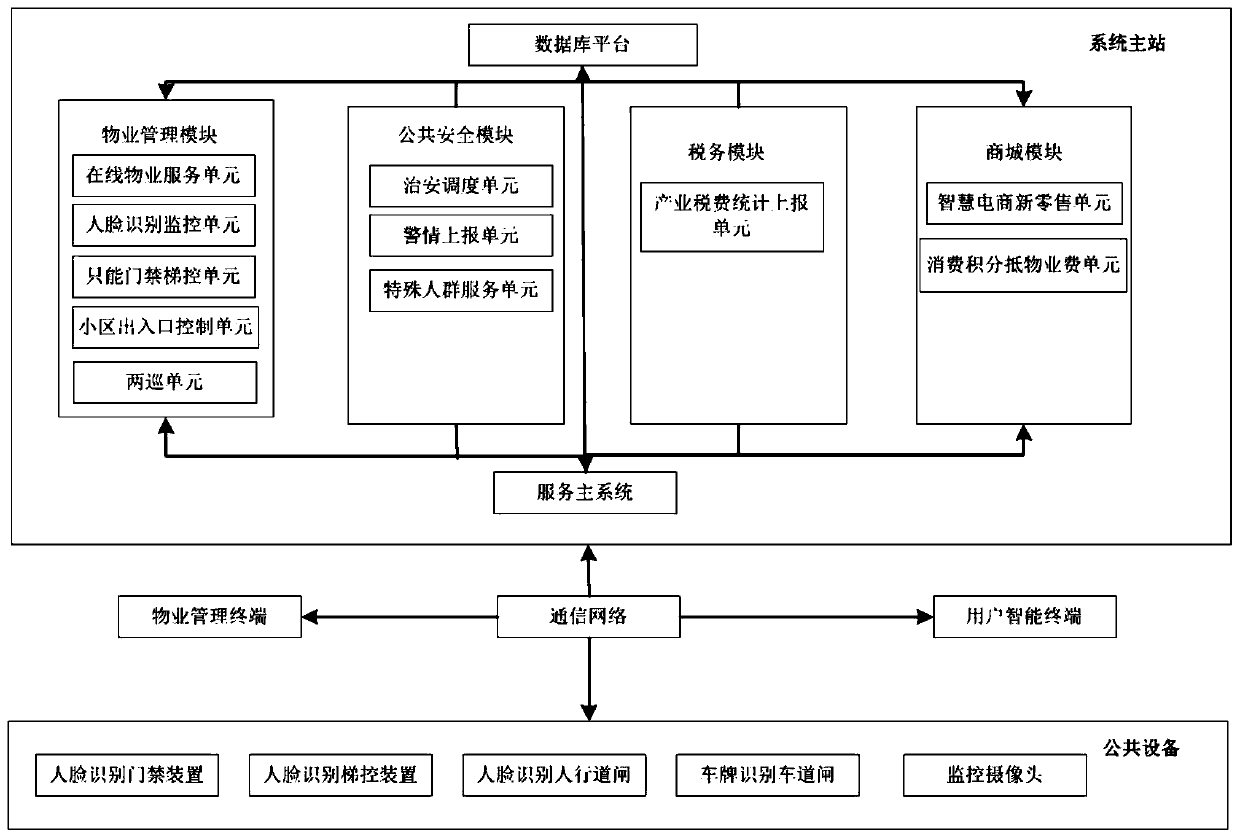
InactiveCN109767357AProcess intelligenceSatisfy securityChecking time patrolsFinanceInternet of ThingsSmart community
The invention provides a smart community property service and community service system based on the Internet of Things, and belongs to the technical field of property management. The system comprisesa system main station, a communication network, a public device, a user intelligent terminal and a property management terminal. The public equipment is connected with the system main station througha communication network, and the user intelligent terminal is connected with the system master station through a communication network. The system master station comprises a service master system connected with the communication network, and a database platform, a property management module, a public security module, a tax module and a shopping mall module which are respectively connected with theservice master system, and the property management module, the public security module, the tax module and the shopping mall module are respectively connected with the database platform. According tothe system, the property companies, public security officers, tax authorities, social residents, natural persons, entity e-commerce, manufacturers and the like are integrated as service objects, and the requirements of intelligent communities for intelligentization, safety, convenience and the like of community properties are met.
Owner:美戴瑜洋(北京)国际商务服务有限公司
User identity authentication system and authentication method thereof
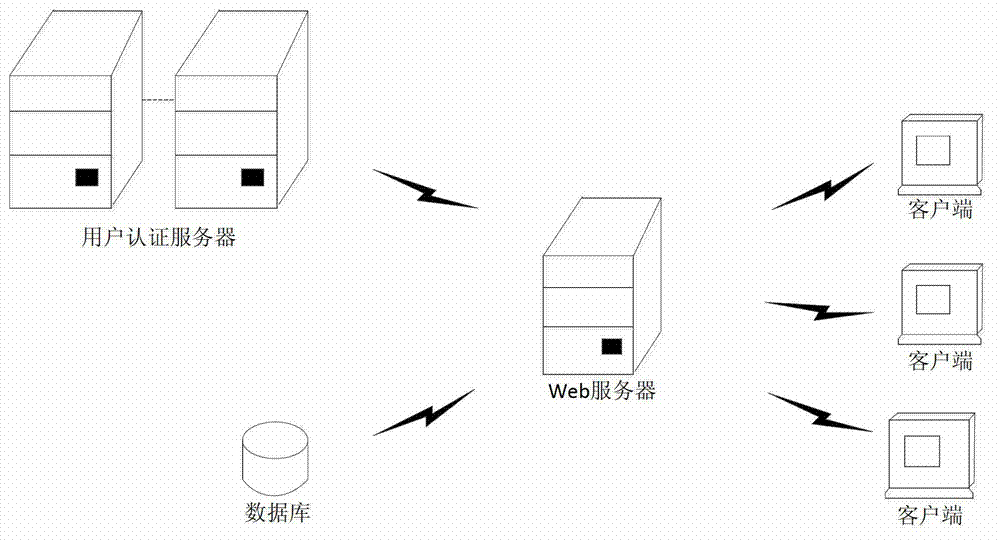
InactiveCN102857501AEasy accessMeet reliabilityUser identity/authority verificationThird partyRelevant information
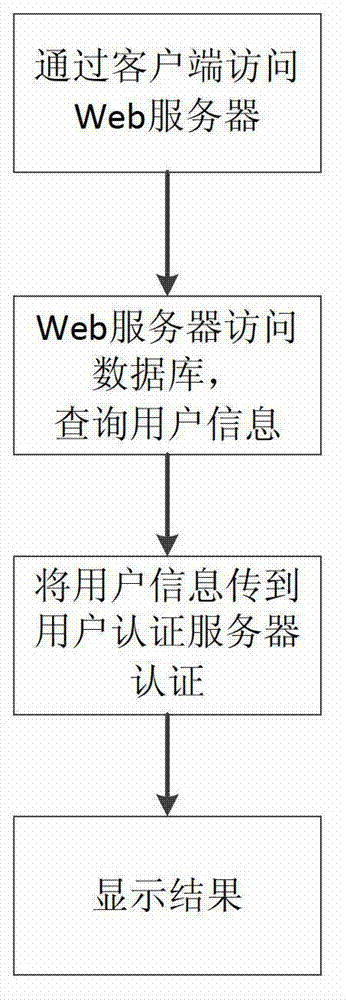
The invention discloses a user identity authentication system, belonging to the field of computers. The system comprises a server, a client and a databank, wherein the server respectively communicates with the client and the databank. Corresponding to the system, the invention discloses an authentication method of the user identity authentication system; the method comprises the following steps: (1) a user accesses to a Web server through the client; (2) the Web server queries user information through the databank; and (3) the user information queried in the databank is transmitted to a user authentication server to be authenticated, if the authentication is correct, the user is allowed to log in, relevant information of the user is displayed, and a unique and unrepeated authentication key is set up; or else input error is displayed. The system supports the lead-in of third-party user information and different authentication modes of the third-party, so that the situation that multiple systems use different user authentication systems is avoided, and thus the use complexity of users is reduced.
Owner:WUXI CITY CLOUD COMPUTING CENT
3D curve welding seam autonomous demonstration method for welding robot based on linear structure light perception
ActiveCN109514133AReduce complexitySatisfy securityProgramme-controlled manipulatorWelding/cutting auxillary devicesPoint cloudFeature extraction
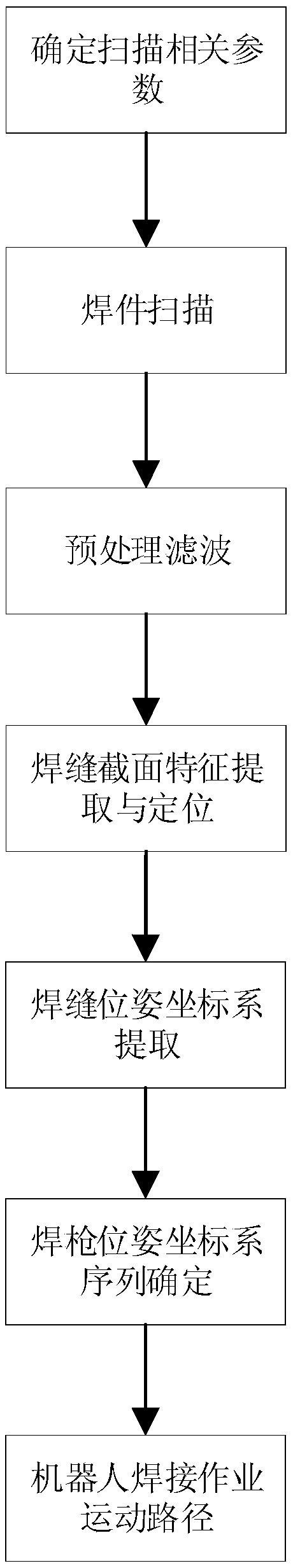
The invention discloses a 3D curve welding seam autonomous demonstration method for a welding robot based on linear structure light perception. The 3D curve welding seam autonomous demonstration method comprises the steps that relevant parameters are determined and scanned, and an orderly point cloud model of a weldment is generated in a scanned mode; the orderly point cloud model of the weldmentis subjected to preprocessing filtering; then, feature extracting and positioning are conducted on the cross section of a welding seam, corresponding welding seam point pose coordinate systems are obtained, and a welding seam point pose coordinate system sequence is formed; the welding seam point pose coordinate system sequence is combined with welding operation technological parameters to form awelding gun pose coordinate system sequence; and a robot welding operation motion path is generated according to the welding gun pose coordinate system sequence. The 3D curve welding seam autonomous demonstration method has the 3D welding seam feature extracting and modeling capabilities, precise 3D positioning of a complex space curve welding seam is achieved, demonstration intelligent programming of welding of small-batch, multi-variety and nonstandard workpieces can be achieved, the welding precision and quality are improved, and the 3D curve welding seam autonomous demonstration method hasquite important economic value and application prospects in the field of application of welding robots.
Owner:SOUTHEAST UNIV
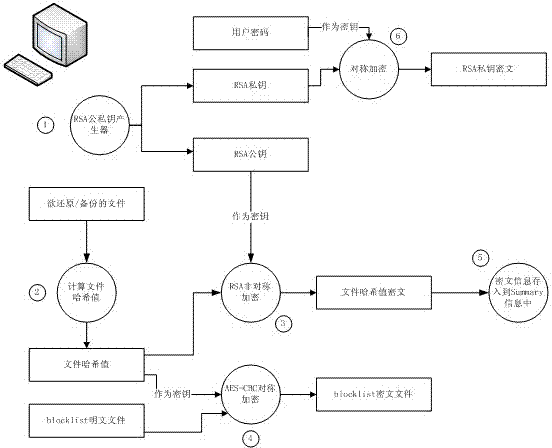
Crypto-delta-transfer-based remote sharing backup recovery method
The invention discloses a crypto-delta-transfer-based remote sharing backup recovery method. In the invention, the bandwidth consumption of data transmission, potential safety hazards of data in transmission and the potential safety hazards of data storage in a data center are comprehensively combined, and a scheme in which a backup client performs data blocking, compression and encryption before the data transmission is provided. Only incremental data is transmitted, thereby improving the transmission efficiency and optimizing transmission bandwidths. The data is transmitted and stored in form of cipher text, so only the cipher text is obtained and clear text data cannot be obtained even though the data is stolen as long as an encryption key is not leaked.
Owner:杭州奕锐电子有限公司
Web reverse proxy method based on preconnect
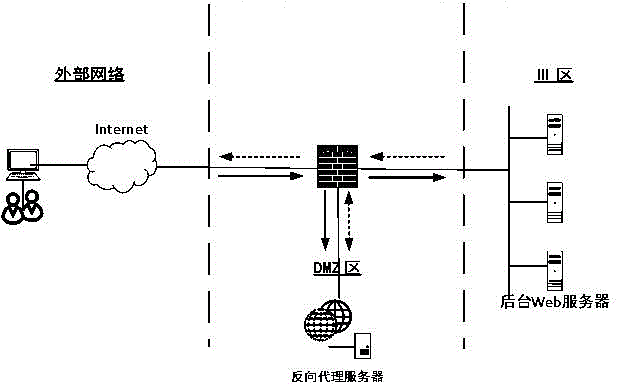
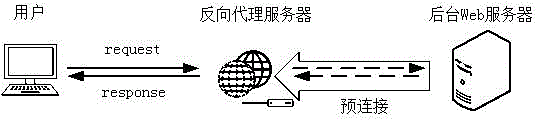
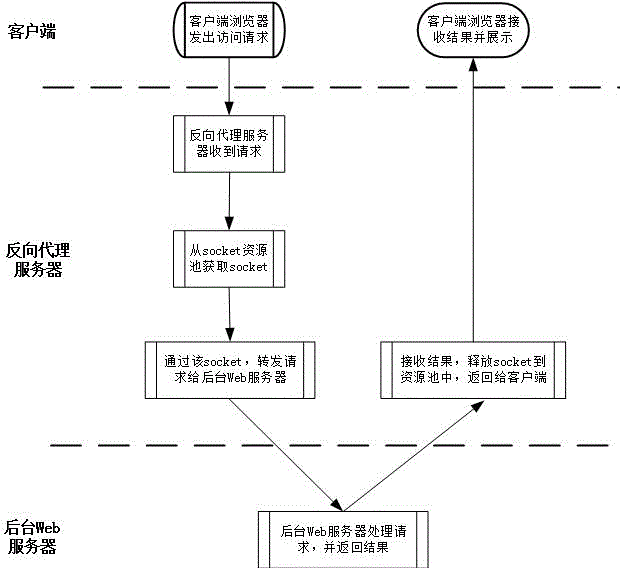
The present invention provides a web reverse proxy method based on preconnect. A background web server actively initiates a request of establishing socket connection to a reverse proxy server, and after the reverse proxy server creates the socket connection, socket is stored into a socket resource pool. When a client browser initiates a web request to the reverse proxy server, the reverse proxy server obtains the socket from the socket resource pool and carries out request forwarding to the background web server by using the socket. The background web server receives the request and processes the request, a result is returned to the reverse proxy server, and finally the reverse proxy server returns the result to the client browser for displaying. The method has the advantages that the method is transparent to a background application system, network security requirements are satisfied in visiting an internal network, the cost of hardware and software is low, and the upgrade operation is simple.
Owner:STATE GRID CORP OF CHINA +2
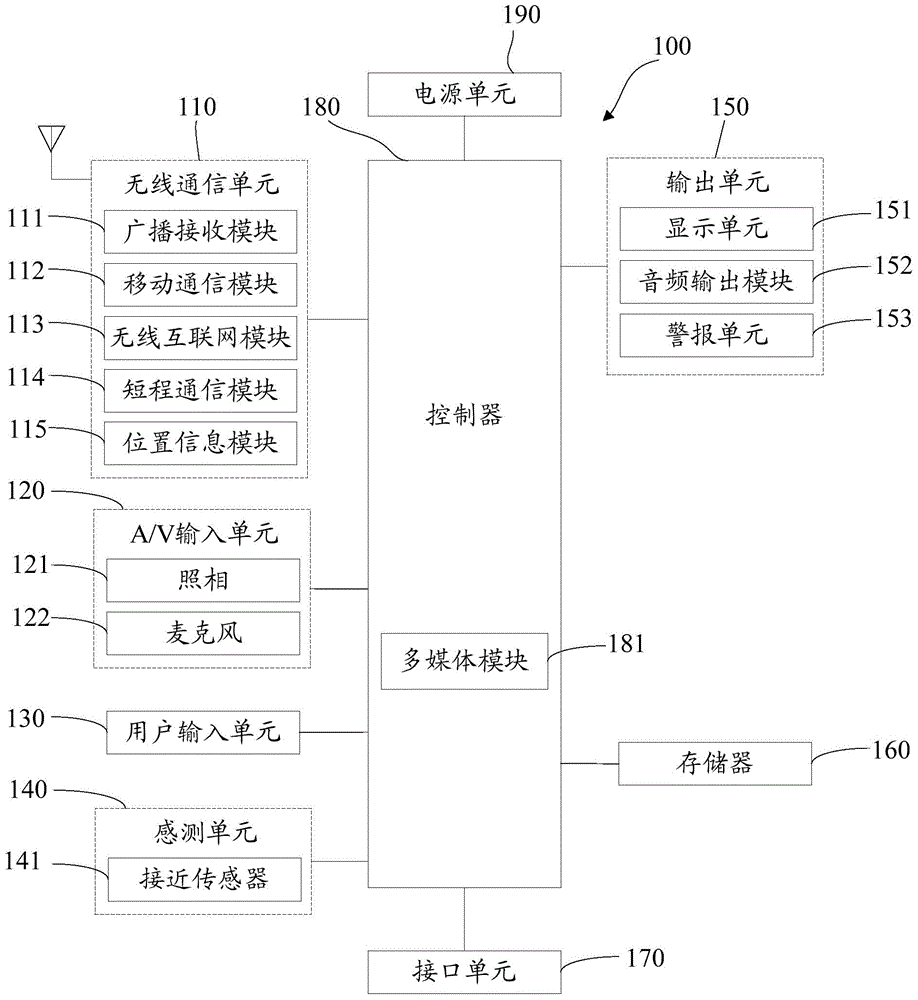
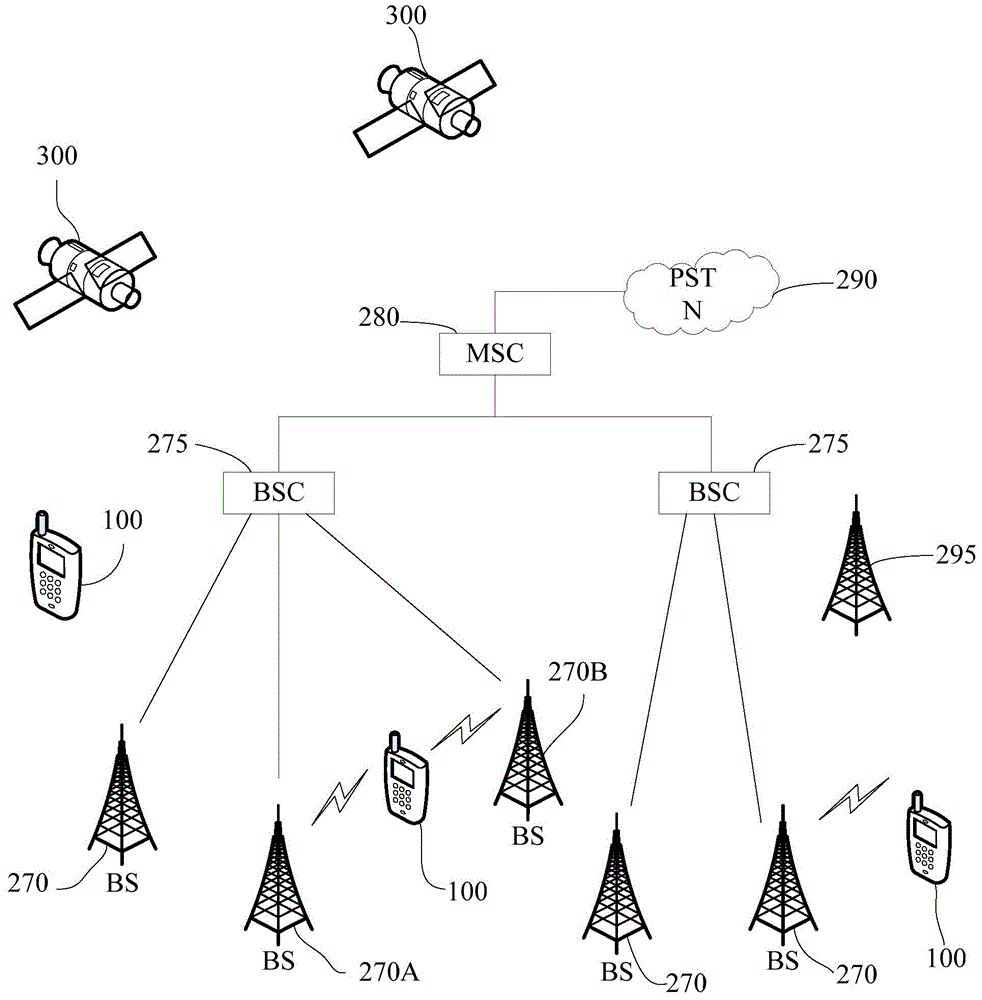
Unlocking method and unlocking device
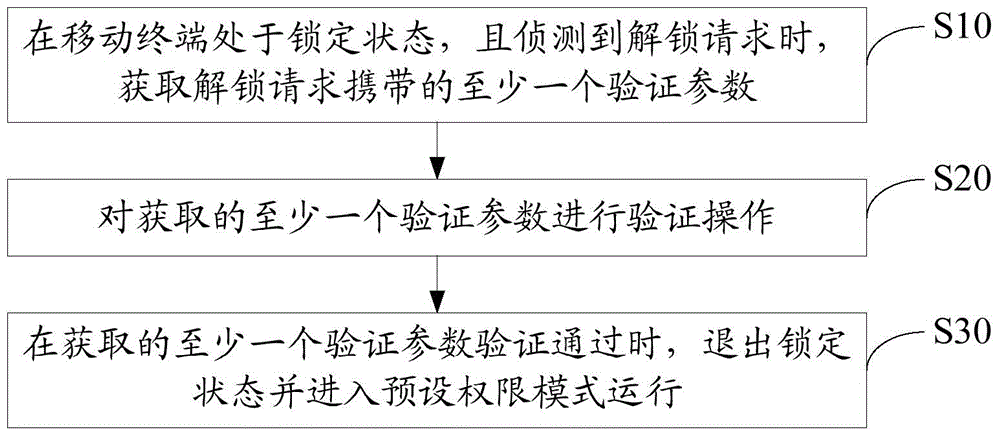
The invention discloses an unlocking method. The unlocking method comprises the following steps: when a mobile terminal is in a locked state and an unlocking request is detected, acquiring at least one verification parameter carried by the unlocking request; performing verification operation on the acquired at least one verification parameter; and when the verification on the at least one verification parameter is successful, exiting from a locked state and operating in a preset permission mode. The invention further discloses an unlocking device. By virtue of the unlocking method and the unlocking terminal, the mobile terminal is capable of improving the privacy on the premise of meeting the safety.
Owner:NUBIA TECHNOLOGY CO LTD
Log management system and operation method thereof
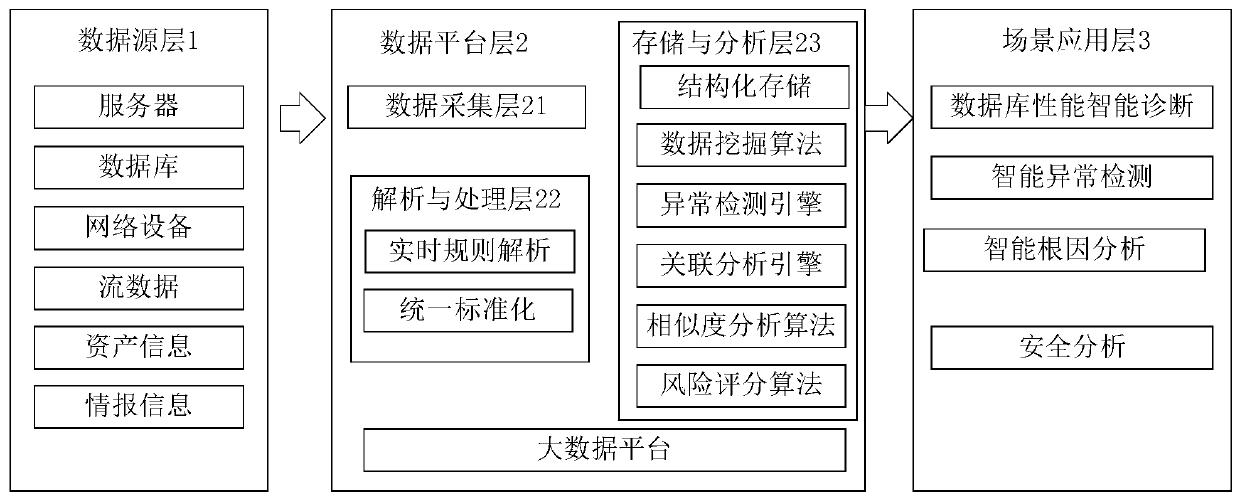
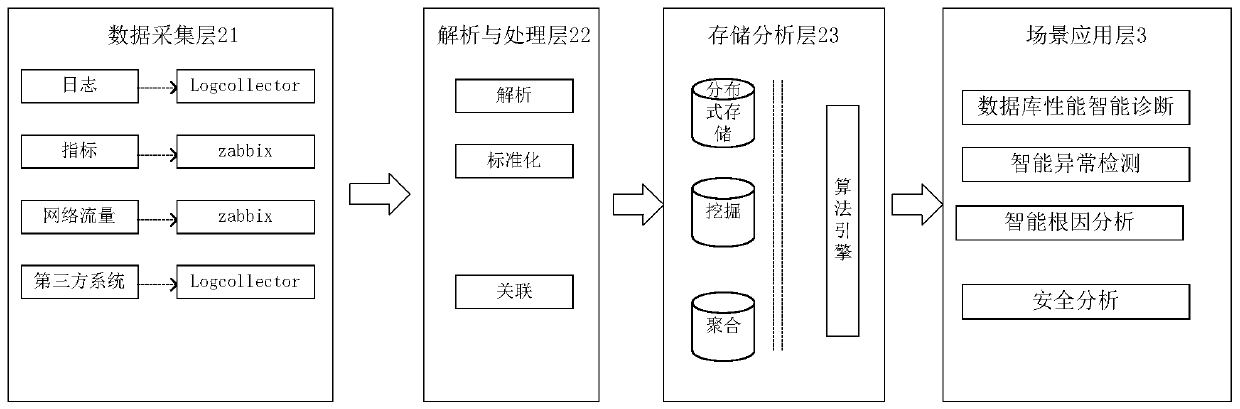
PendingCN111190876AImmediate responseRapid positioningTransmissionSpecial data processing applicationsAnalysis dataData platform
The invention provides a log management system and an operation method thereof. The log management system comprises a data source layer, a data platform layer and a scene application layer. The data acquisition layer is used for acquiring data of the data source layer; the analysis and processing layer is used for processing the data acquired by the data acquisition layer through a queue, enablingthe processed data to enter the data platform layer in real time to be filtered and cleaned, performing real-time rule analysis processing on heterogeneous data sources of different formats through an analysis engine, and then loading the processed data into the storage and analysis layer to be stored and analyzed; after being analyzed by the algorithm engine, the data is called by the scene application layer in real time; the scene application layer is used for carrying out real-time detection on suspicious indexes in combination with in-line requirements, quickly responding to abnormal events and problems, tracing the source and establishing an operation and maintenance knowledge base; a security situation awareness scene is established in combination with various network security equipment events and rules in rows, various security events and potential threats are perceived in real time, and timely response and processing, advanced prediction and risk avoidance capability are achieved.
Owner:天津浪淘科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com