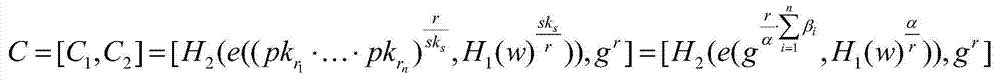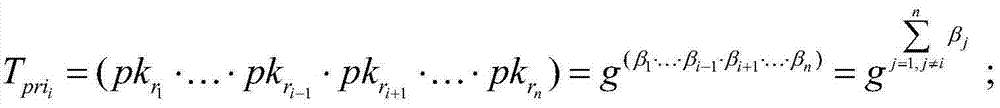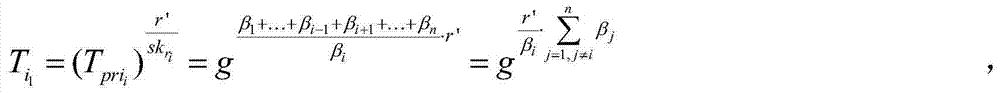Searchable public key encryption method
A public key encryption, public key technology, applied in the field of searchable public key encryption, can solve problems such as the difficulty of circular privacy DLP
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention is described in further detail below by specific embodiment:
[0035] The searchable public key encryption method of the present invention specifically comprises the following steps:
[0036] (1) The data owner, receiver and cloud server initialize the operating environment respectively, specifically:
[0037] The data owner, receiver and cloud server run the initialization algorithm respectively. The initialization algorithm is GlobalSetup(λ), and GlobalSetup(λ) is:
[0038] After inputting the security parameter λ, GlobalSetup(λ) outputs a global parameter GP={G,G 1 ,e,H 1 ,H 2 ,g,q}; among them, e is a bilinear map, G and G 1 is a multiplicative cyclic group whose order is a prime number q; e:G×G→G 1 is an admissible bilinear map; H 1 and H 2 are two hash functions, H 1 and H 2 as two random fable machines, and H 1 :{0,1} * →G,H 2 :G→{0,1} λ (where λ is a security parameter), and g is a generator of the group G.
[0039] (2) The da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com