Crypto-delta-transfer-based remote sharing backup recovery method
A recovery method and backup technology, which is applied in the field of network information security, can solve problems such as Rsync not working, and achieve the effects of saving bandwidth consumption, ensuring security, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] Encrypted incremental transfer is mainly divided into two operations: backup and restore. It is assumed that the client and the server respectively retain data of different versions of the same file.
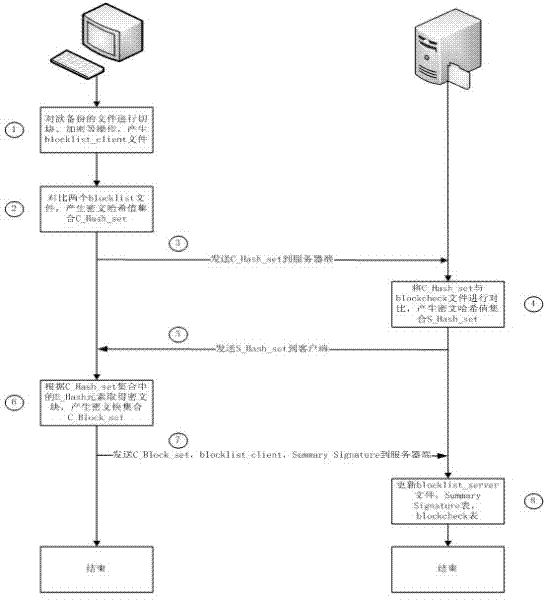
[0064] Such as figure 1 As shown, the backup operation includes the following steps:
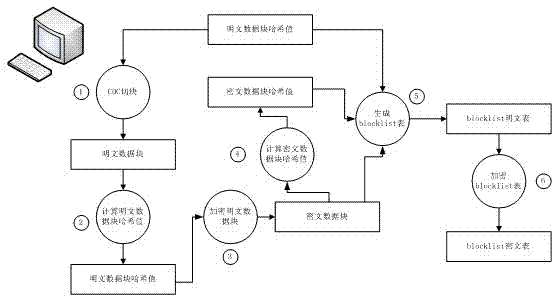
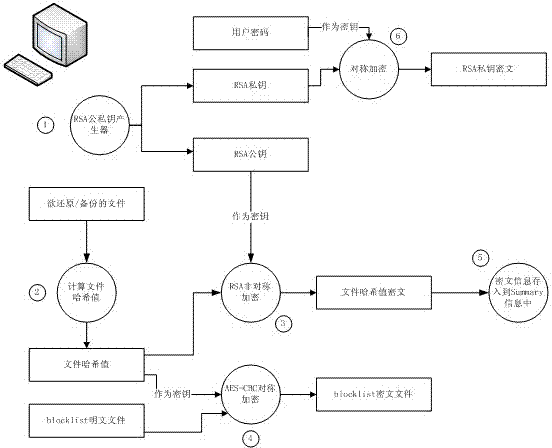
[0065] 1. The client performs a series of operations such as cutting and encrypting the files to be backed up, and generates plaintext blocks, hash values of plaintext blocks, ciphertext blocks, hash values of ciphertext blocks, blocklist_client ciphertext files, and Summary Signature files;
[0066] 2. The client compares the generated blocklist_client file with the locally stored blocklist_server file to generate a ciphertext block hash value set C_Hash_set;
[0067] 3. The client sends the ciphertext block hash value set C_Hash_set to the server;
[0068] 4. After receiving the ciphertext block hash value set C_Hash_set, the server compares it with the blockcheck table to gene...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com