Unlocking method and unlocking device
An unlocking device and unlocking technology, applied in the direction of digital data authentication, etc., can solve the problems of user privacy leakage, mobile terminal security and privacy cannot be taken into account, etc., to achieve the effect of improving privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
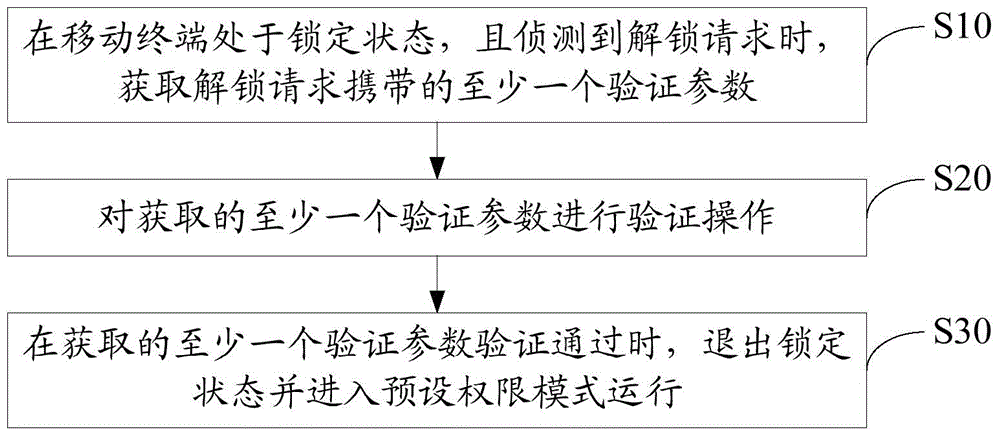
[0043] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
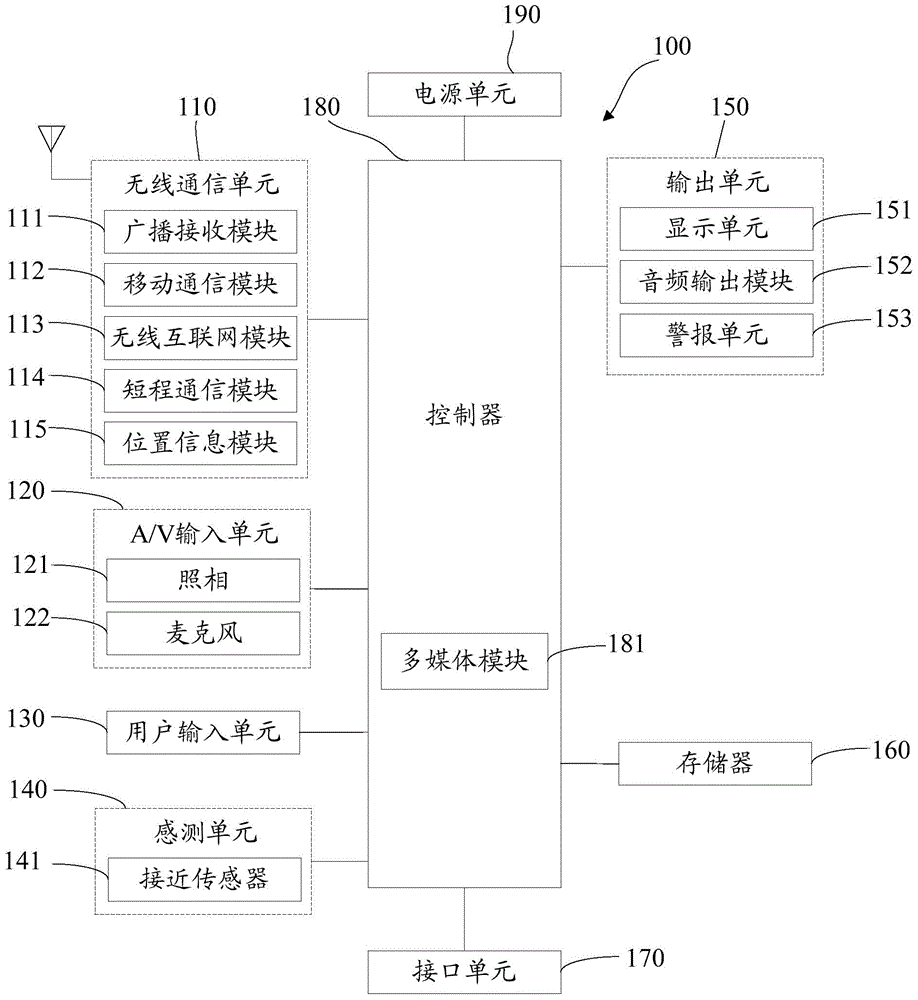
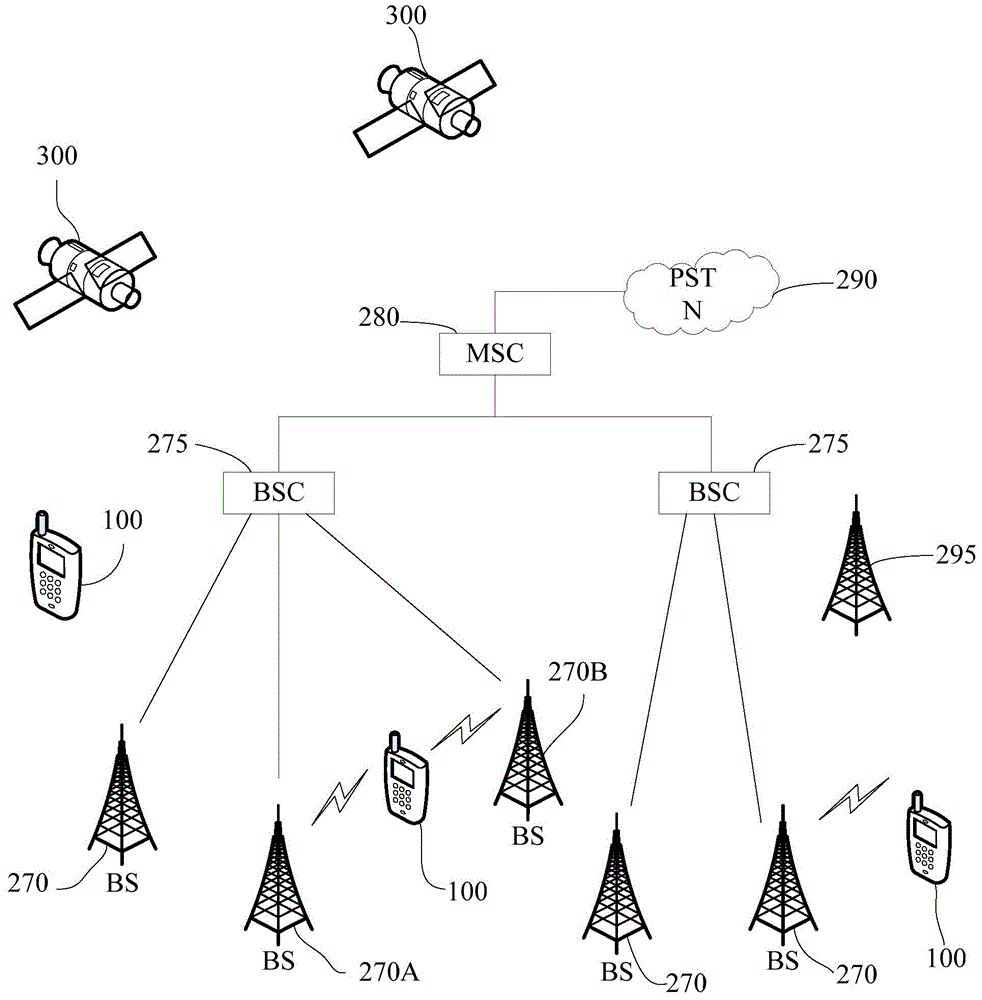
[0044] A mobile terminal implementing various embodiments of the present invention will now be described with reference to the accompanying drawings. In the following description, use of suffixes such as 'module', 'part' or 'unit' for denoting elements is only for facilitating description of the present invention and has no specific meaning by itself. Therefore, "module" and "component" may be used mixedly.
[0045] Mobile terminals may be implemented in various forms. For example, terminals described in the present invention may include devices such as mobile phones, smart phones, notebook computers, digital broadcast receivers, PDAs (Personal Digital Assistants), PADs (Tablet Computers), PMPs (Portable Multimedia Players), navigation devices, etc. mobile terminals and fixed terminals such as digital TVs, desktop c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com