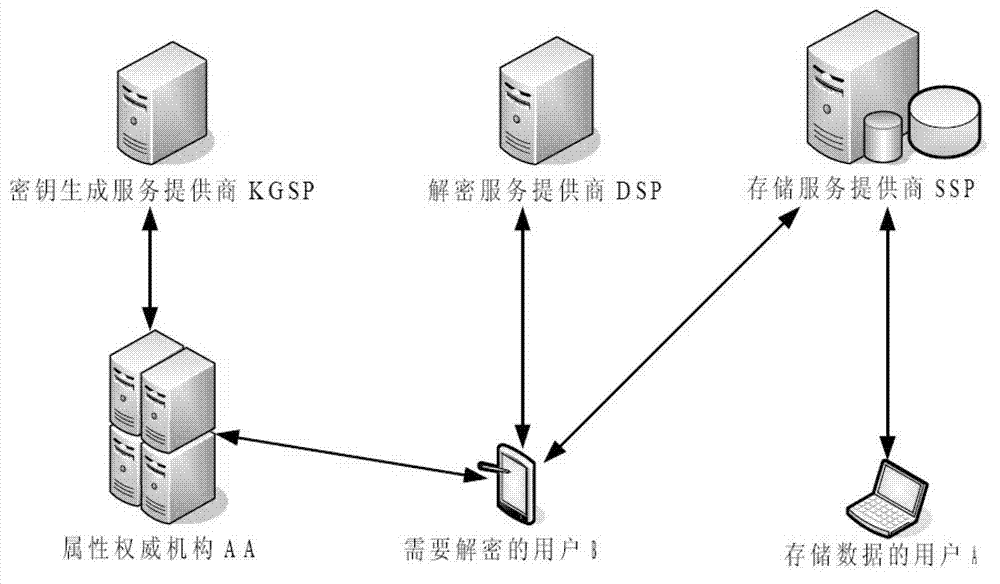
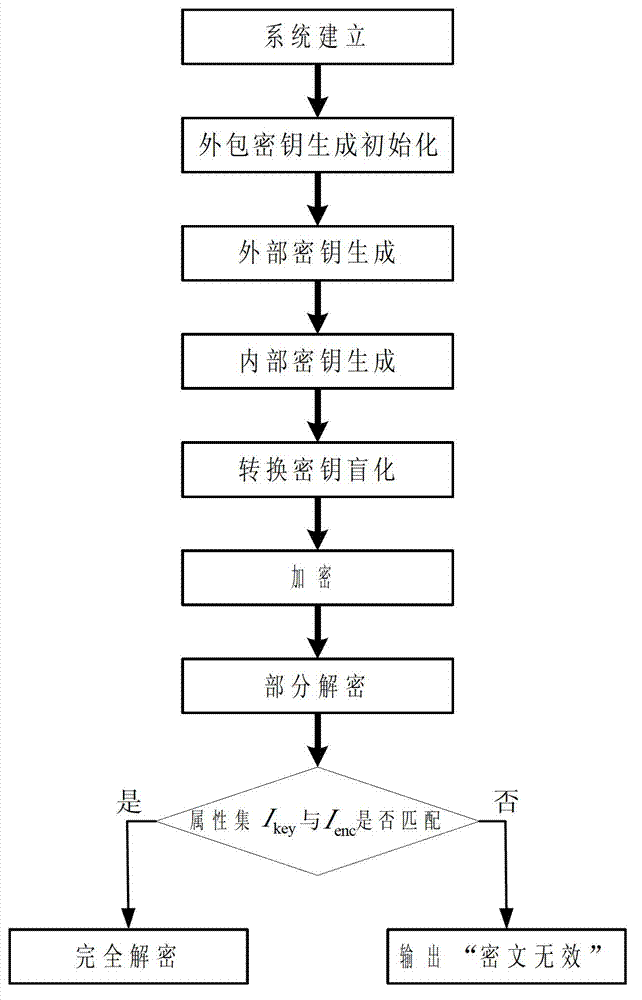
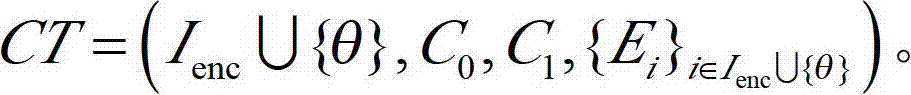Safely outsourced attribute-based encryption method
An encryption method and security outsourcing technology, applied in the field of attribute-based encryption, can solve problems such as complex efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] One, the applied mathematical theory of the present invention explains:
[0067] 1. Bilinear pairing
[0068] In the present invention, the bilinear pair e: G×G→G T is a mapping that satisfies bilinearity, non-degenerateness, and computability, and it maps two elements in the prime order group G to the prime order group G T an element in . For example, a Tate pair defined on a supersingular elliptic curve is a bilinear pair that satisfies the condition.
[0069] 2. Lagrange coefficient
[0070] For d-1 degree polynomial f(x) and set S={x 1 ,x 2 ,...,x d}, with element x i The Lagrangian coefficient corresponding to the set S is From the Lagrangian coefficients, the polynomial f(x) can be calculated as follows:
[0071] f(x)=∑ i∈S Δ i,S f(x i ),
[0072] Here, the Lagrange coefficient is Δ i,S is a polynomial in the independent variable x, so
[0073] f(0)=∑ i∈S Δ i,S (0)f(x i ).
[0074] Two, the realization process of the present invention
[0075]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com