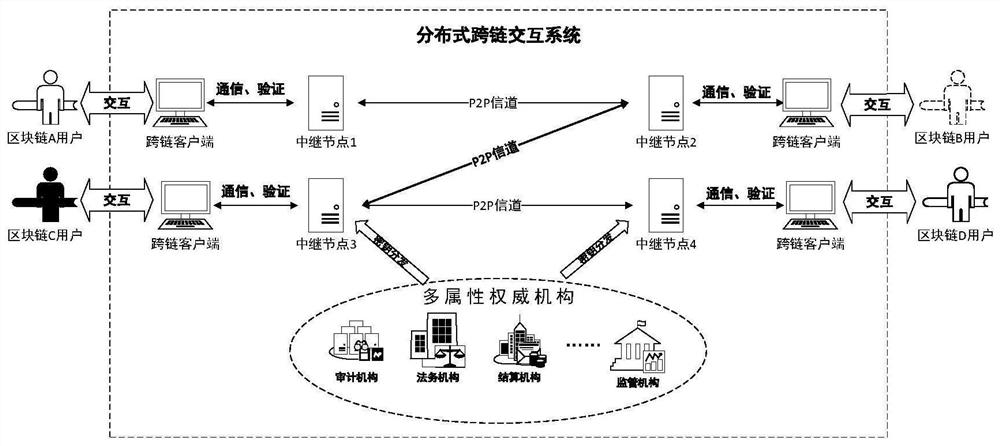
Distributed cross-chain system and cross-chain information interaction and system access control mechanism
An access control and information interaction technology, applied in the blockchain field, can solve problems such as business security impact, blockchain data communication and value transfer difficulties, and achieve strong flexibility and scalability, and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
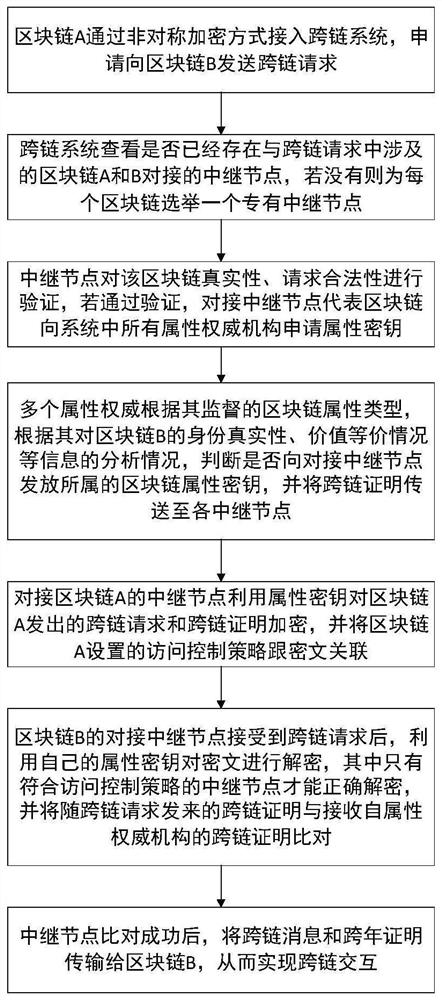
[0033] image 3 It is a one-to-one blockchain cross-chain data interaction and transaction processing method. As shown in the figure, blockchain A users can log in to the cross-chain system client through PC or mobile terminals, and bind blockchain A account, when the user sends a cross-chain message M with private data, the message data will be added with the relevant tags of blockchain A, further indicating that it comes from blockchain A.
[0034] Step 1: Before sending a cross-chain message M, the user of blockchain A needs to fill in the user address of the target blockchain B, design an access control strategy to specify which attributes users in the system can view the specific information requested, and upload the user's Identity certification information, etc., in which the client signs and encrypts the cross-chain message M through digital signature technology and elliptic curve encryption technology.
[0035] When the distributed cross-chain system receives a cross...
Embodiment 2
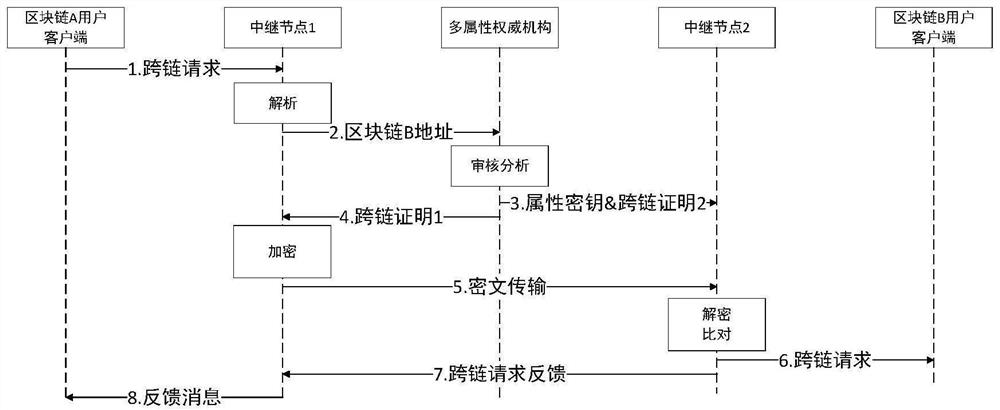
[0043] Figure 4 It shows a one-to-many blockchain cross-chain data interaction and transaction processing method. As shown in the figure, step 1, step 2 and step 4 are related to image 3 The methods shown are the same, while the other steps are executed independently by the relay node 2 and the relay node 4 . Since the setting of the access structure in the attribute cryptosystem has strong flexibility, it can better support the one-to-many secret sharing scheme, so the relay node 3 only needs to set up a set of access structures to construct The receiver's fine-grained access control policy can greatly reduce the workload of the sender's relay node.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com