Access control determination engine optimization system and method based on big data
An access control and big data technology, applied in the field of access control of information security, can solve the problems of low actual performance index, large system resource overhead, and long delay in response to access requests.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
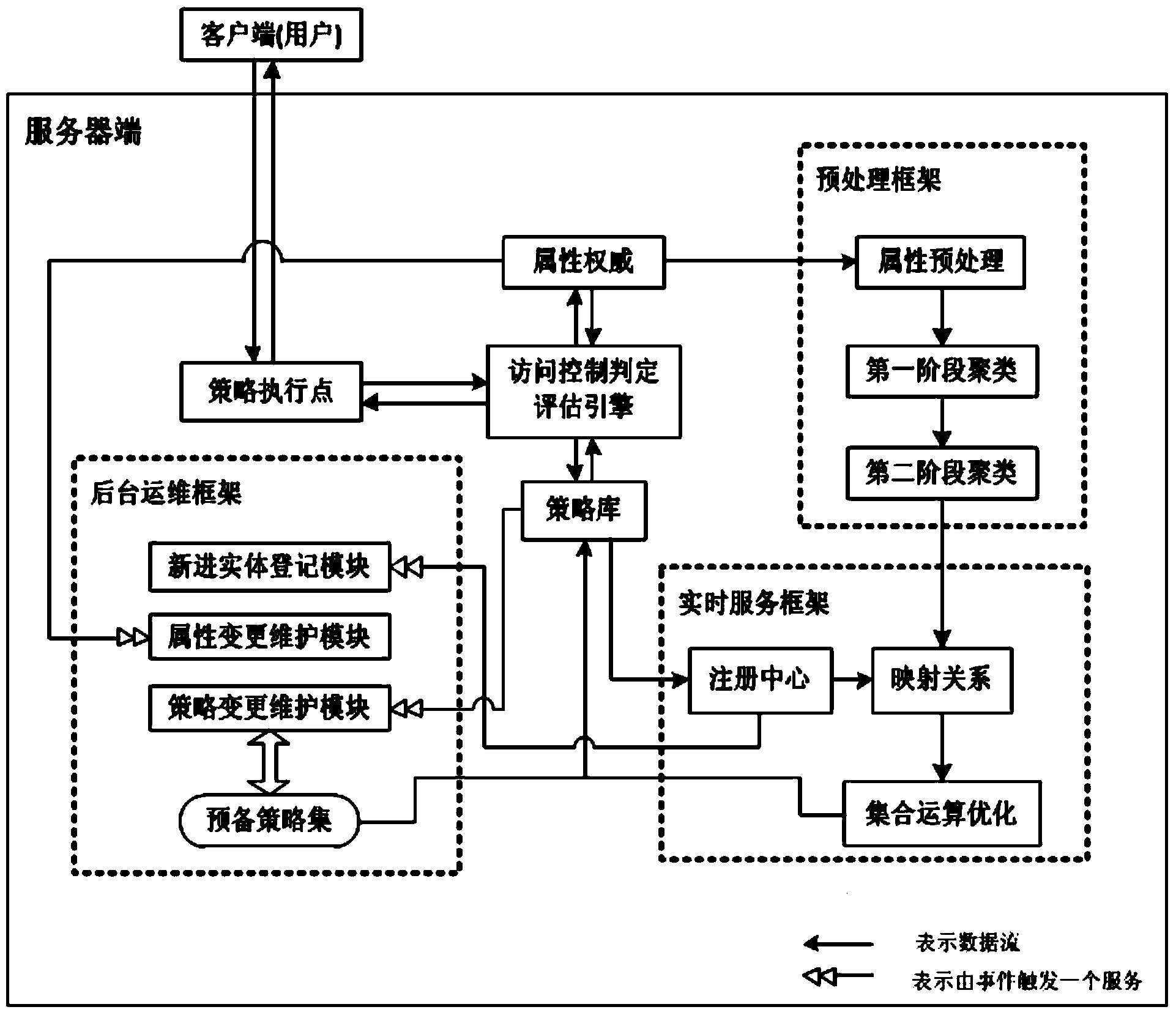
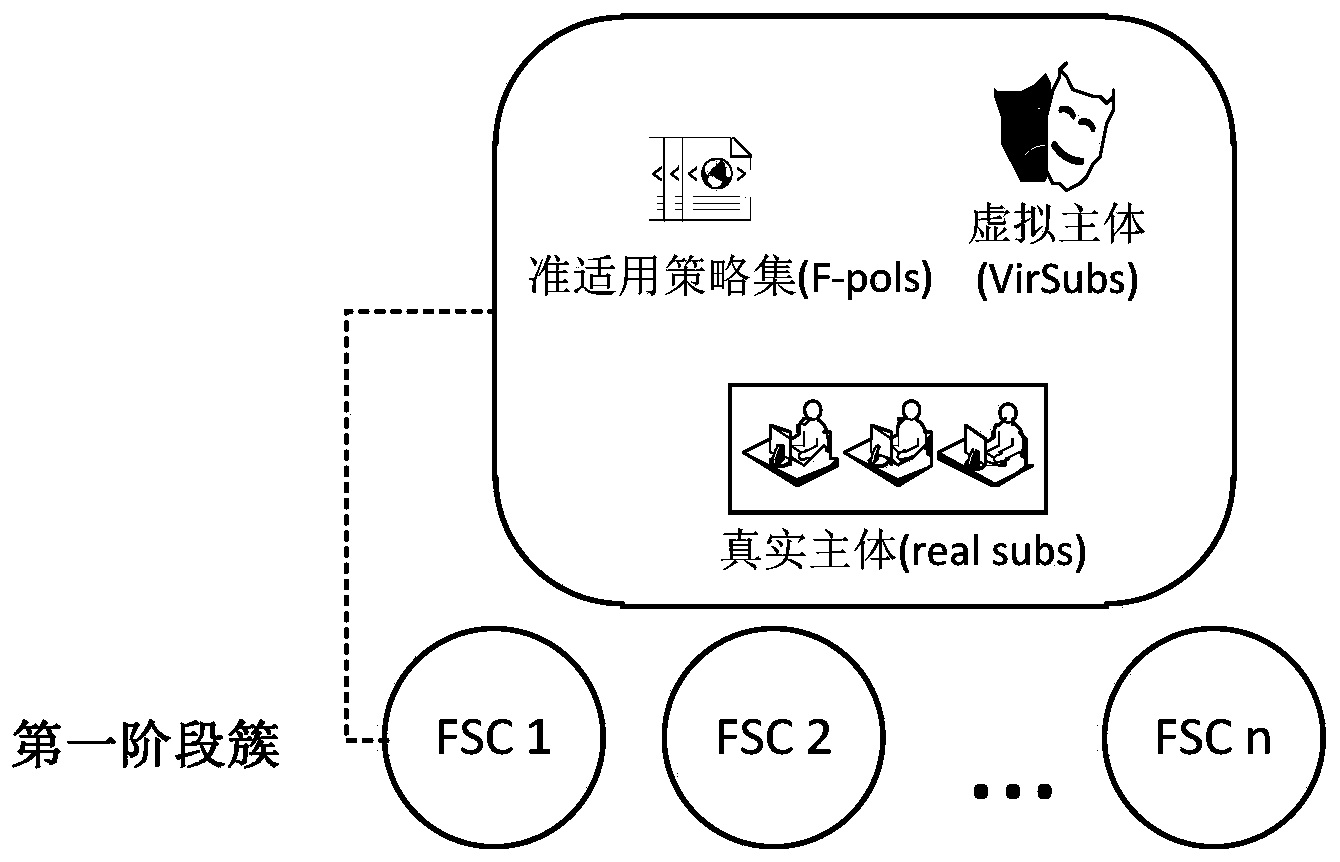
[0057] Such as figure 1 As shown, the present invention is made up of server end and client end, and wherein server end comprises four parts: 1. original access control judgment engine and infrastructure thereof, including: access control judgment evaluation engine module, policy enforcement point, policy library module , Attribute authority module; ② Preprocessing framework: attribute preprocessing module, first-stage clustering module, second-stage clustering module; ③ Real-time service framework: registration center, mapping relationship module, set operation optimization module; ④ Background operation and maintenance Framework: new entity registration module, attribute change maintenance module, policy change maintenance module.
[0058] Among them: ①The original access control system and its infrastructure, here uses Sun’s XACML system as the basic access control engine; ②③④ Parts are developed using Java JDK1.6.0_10-rc2.
[0059] In order to better understand the techni...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com