Patents
Literature
42results about How to "Selectively accessed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
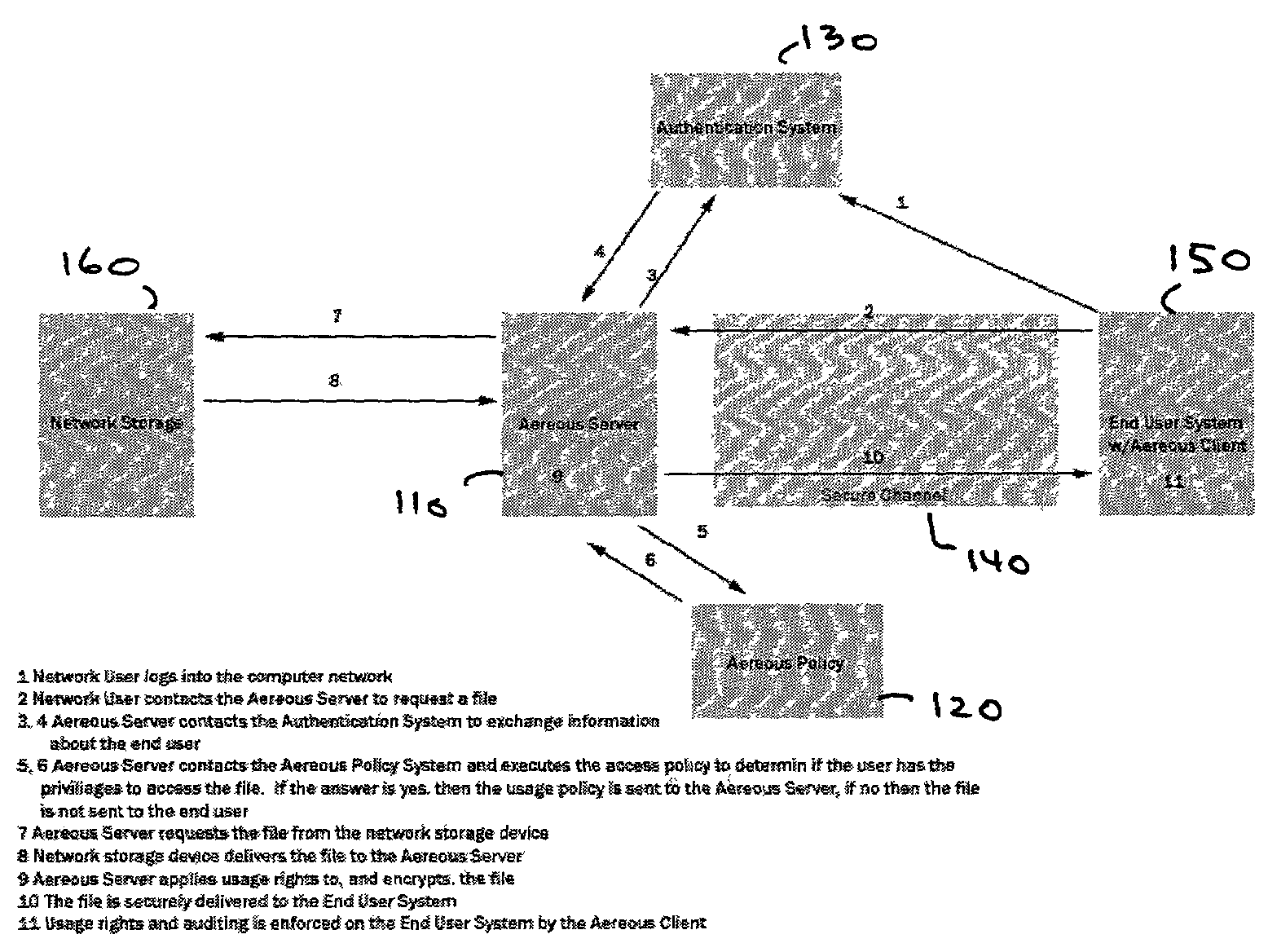
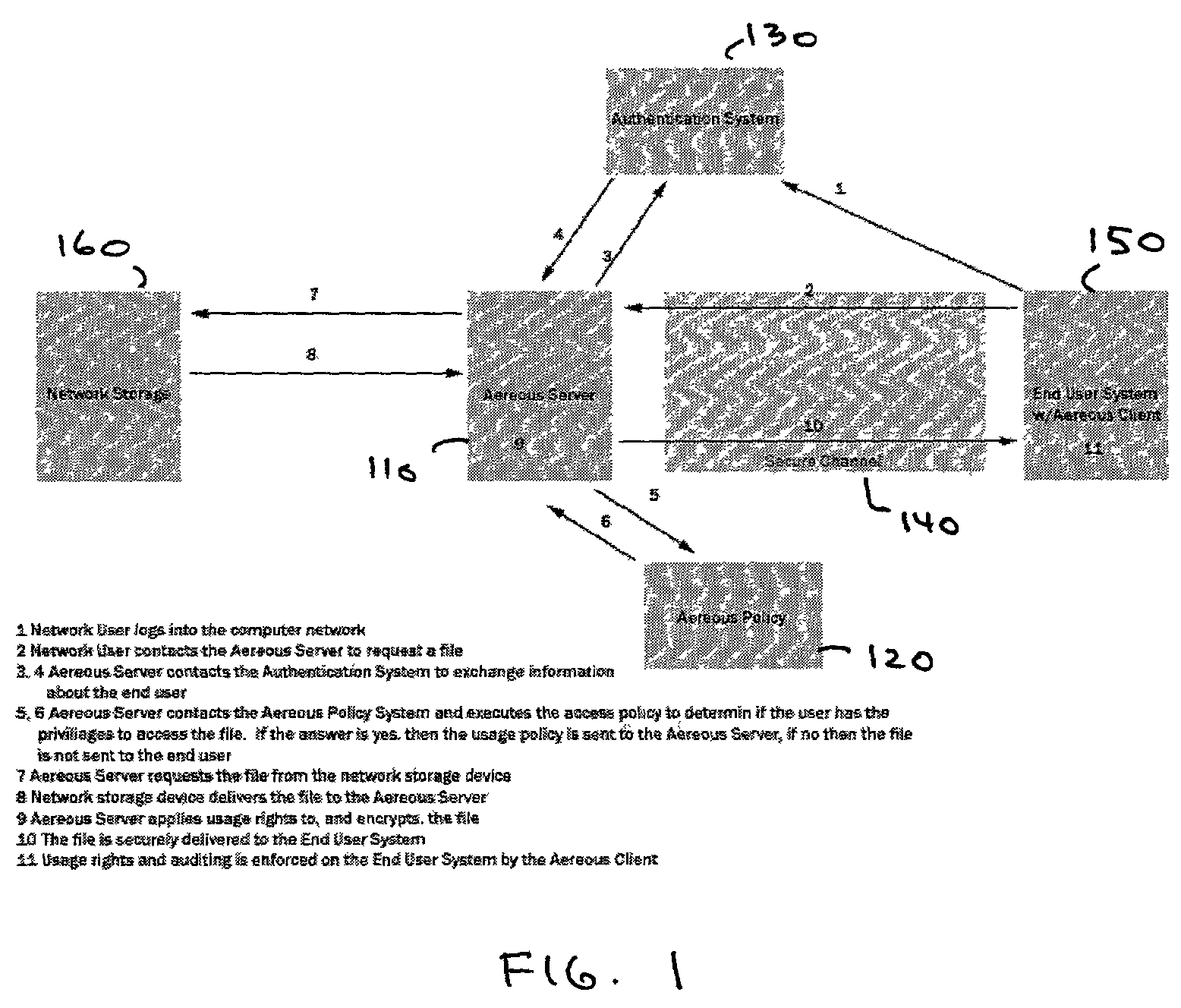
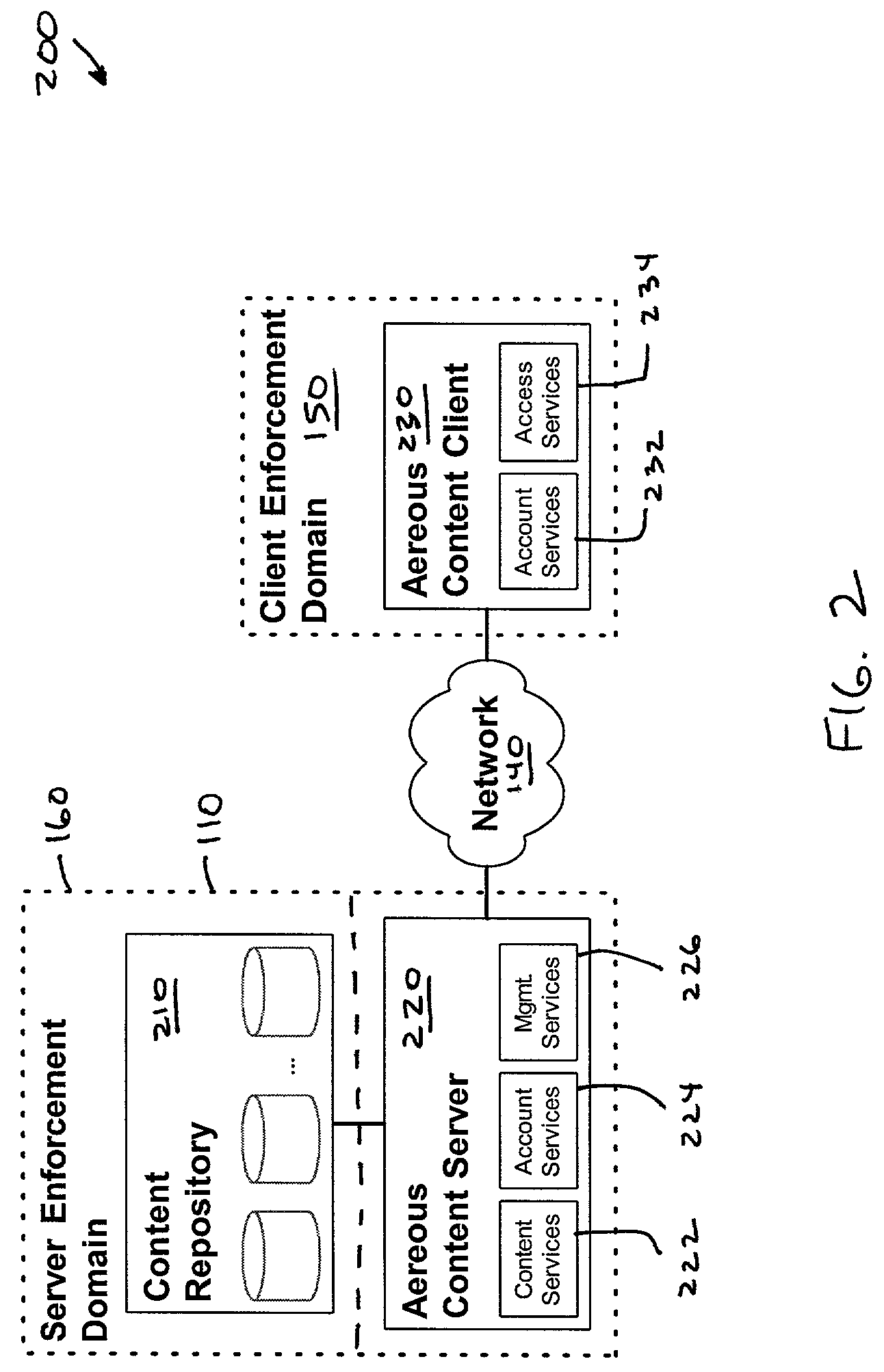
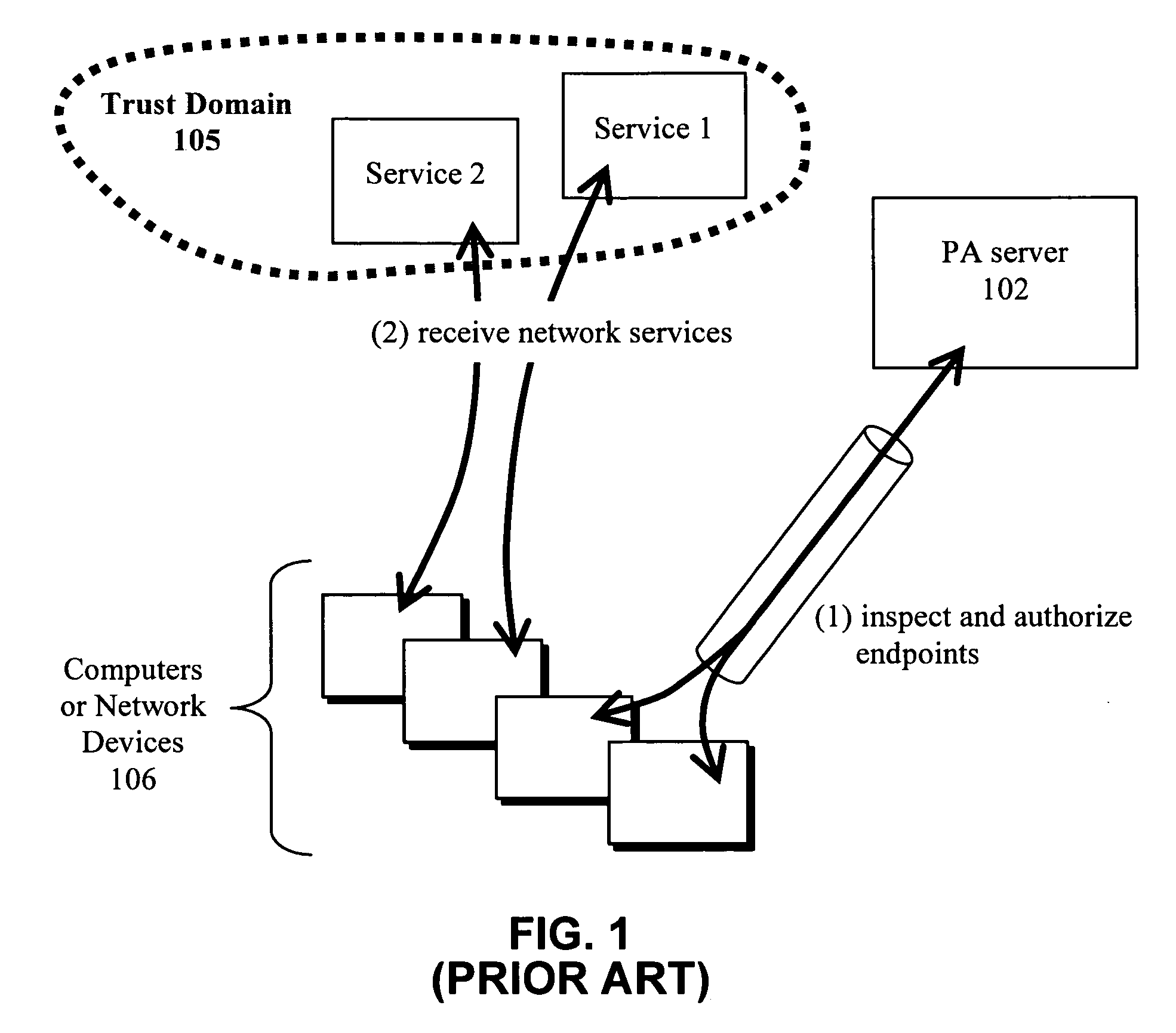
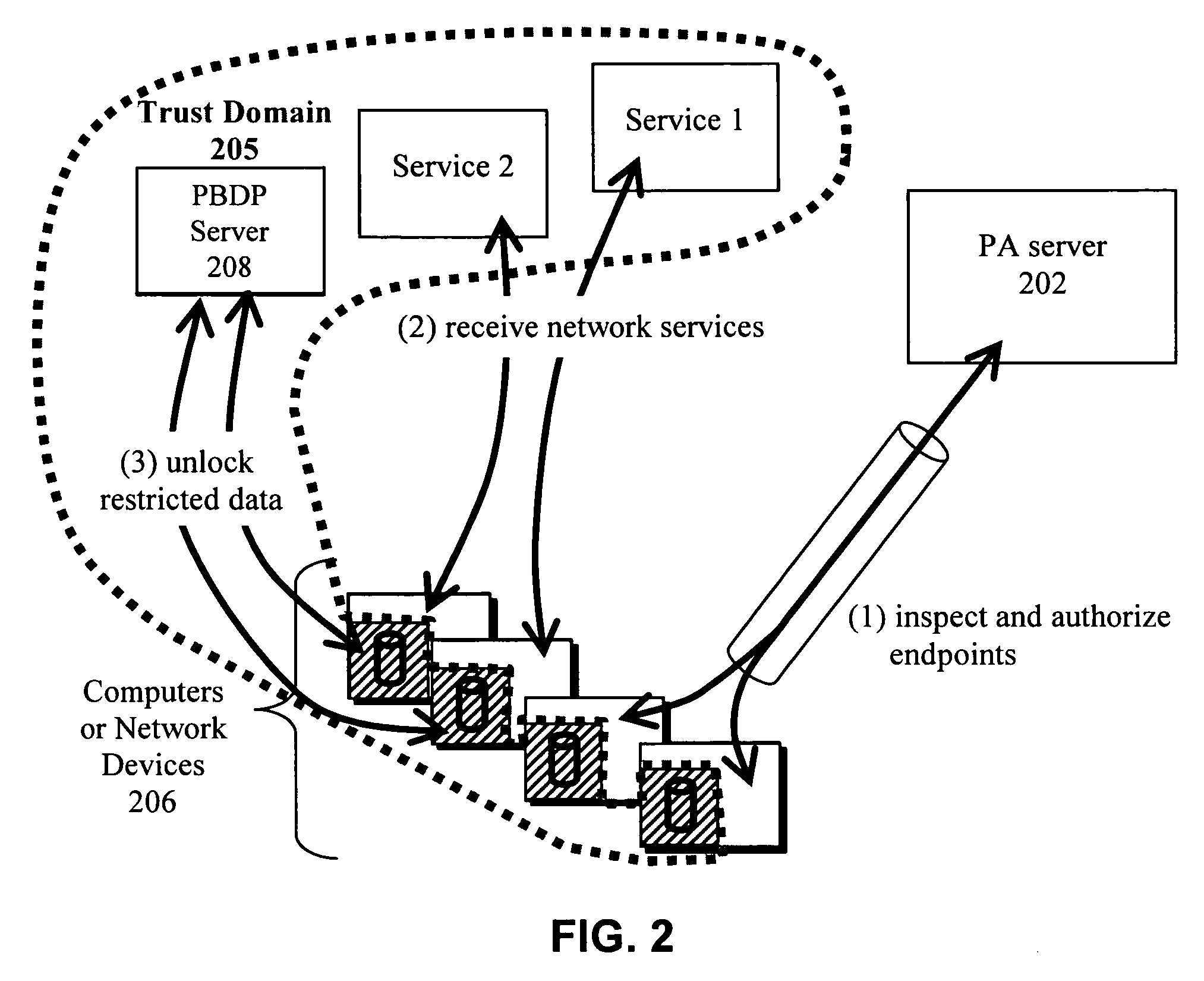
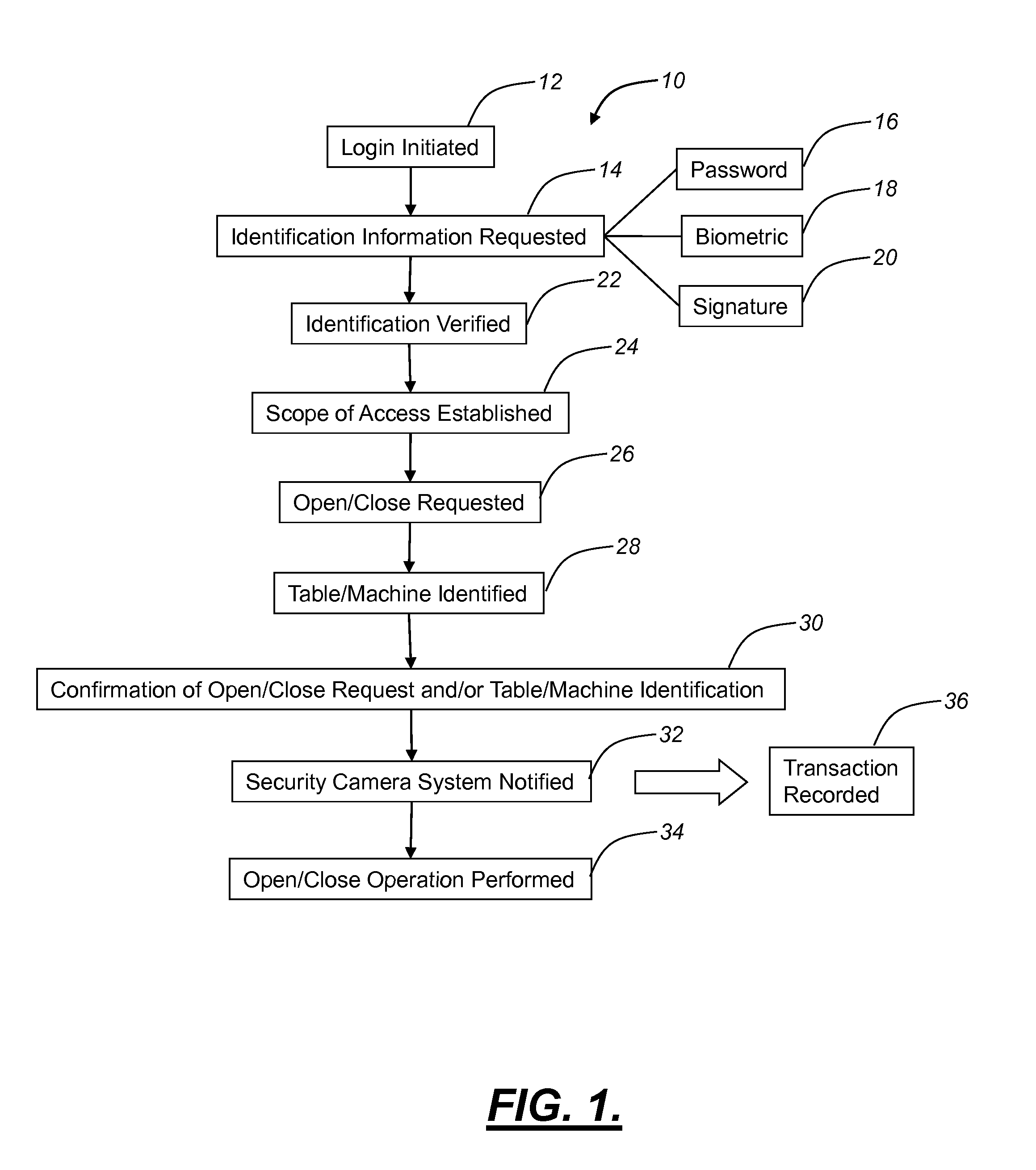
Dynamic file access control and management
InactiveUS7660902B2Improve securitySelectively accessedComputer security arrangementsMultiple digital computer combinationsDistributed File SystemFile system
A dynamic file access control and management system and method in accordance with the present invention may be a proxy file management system that includes one or more file system proxy servers that provide selective access and usage management to files available from one or more file systems or sources. The present invention may embody a secure transport protocol that tunnels distributed file systems, application independent usage controls connected to files on end-user computers, dynamically merging secondary content to a requested file, and applying bandwidth management to any of the foregoing. Embodied in the various implementations of the present invention is enhanced file security. Preferably, the proxy file management system is transparent to an end-user. A dynamic content management system may also be included that selectively adds content to requested files.
Owner:EMC IP HLDG CO LLC
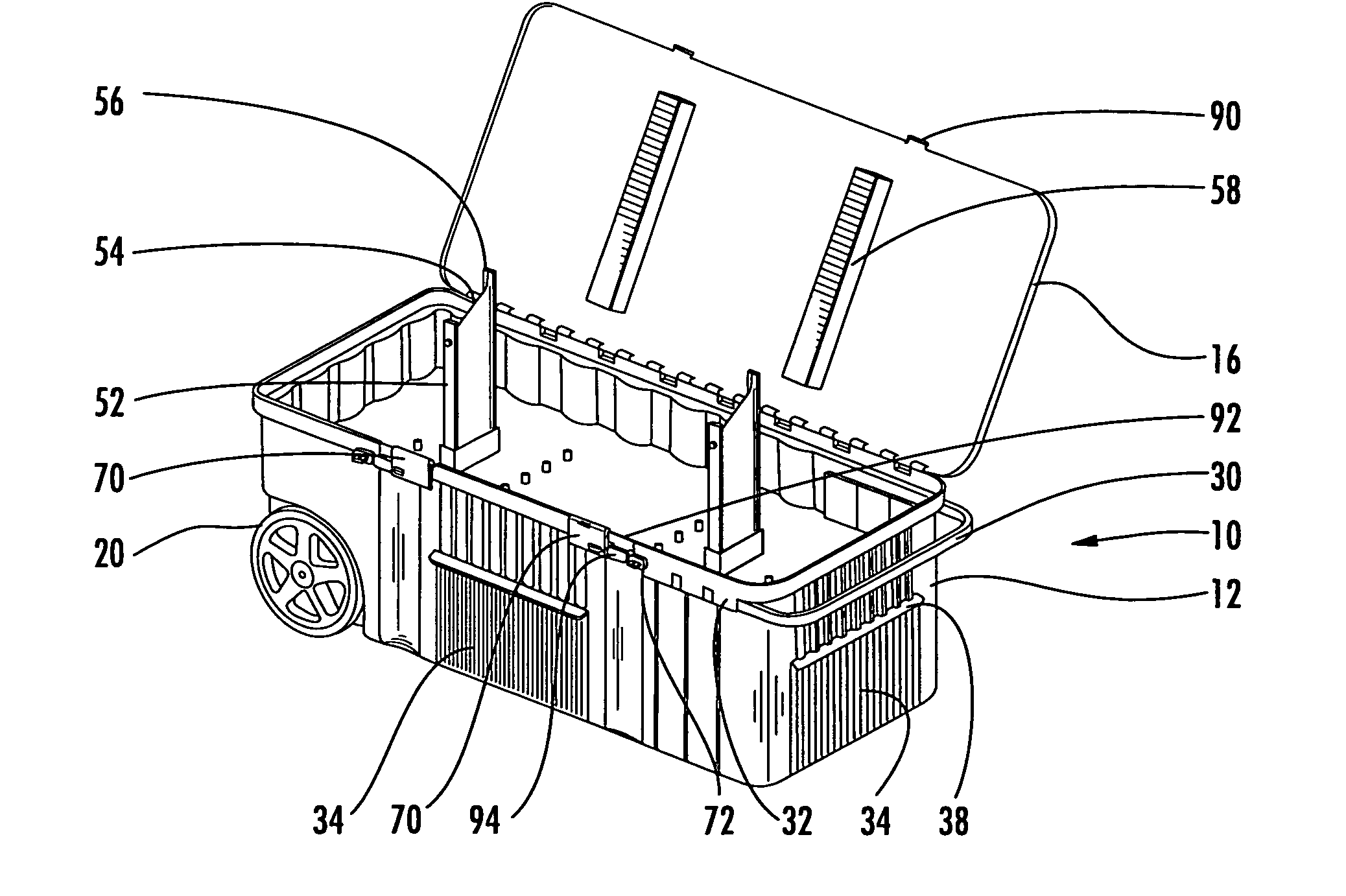
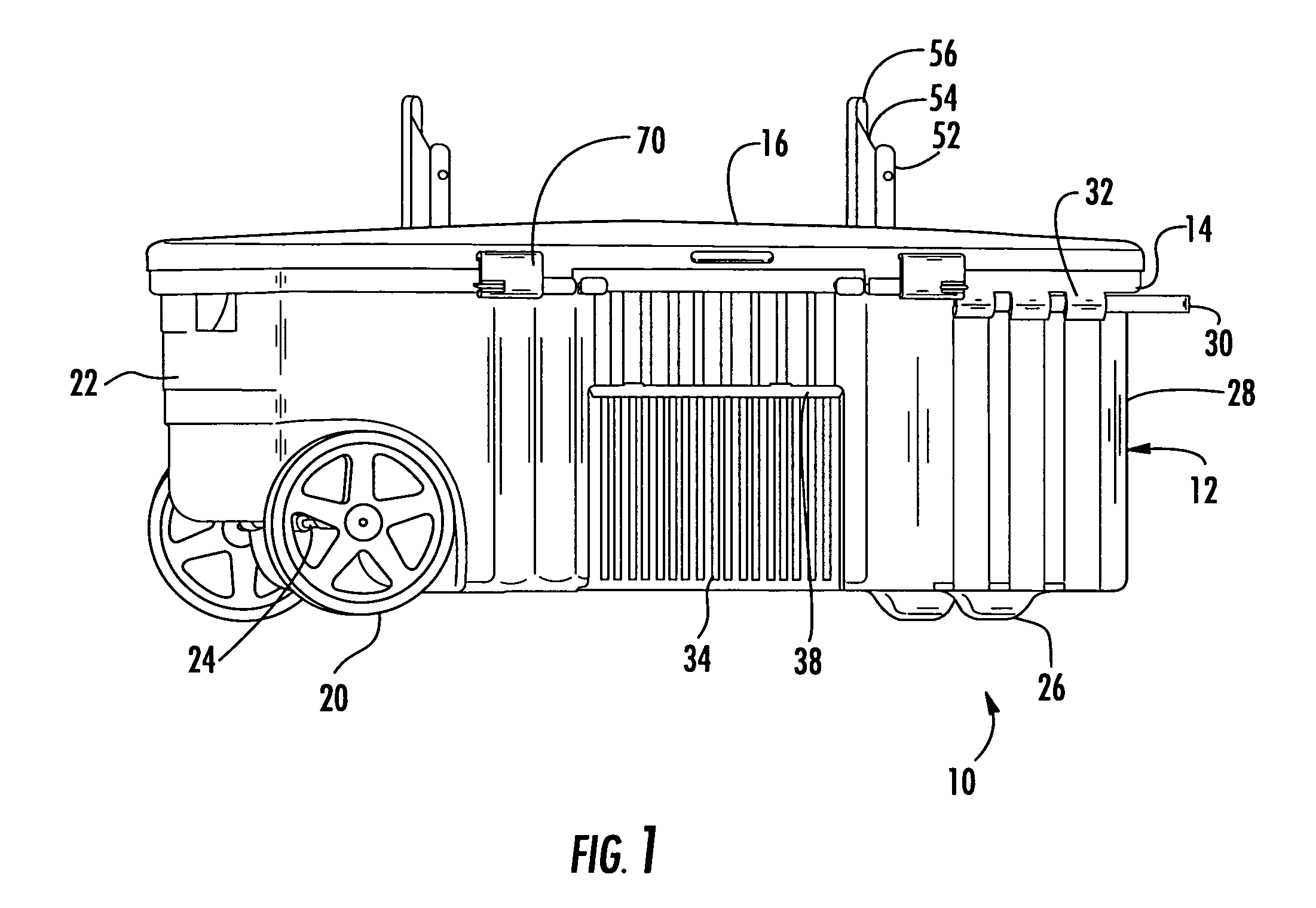
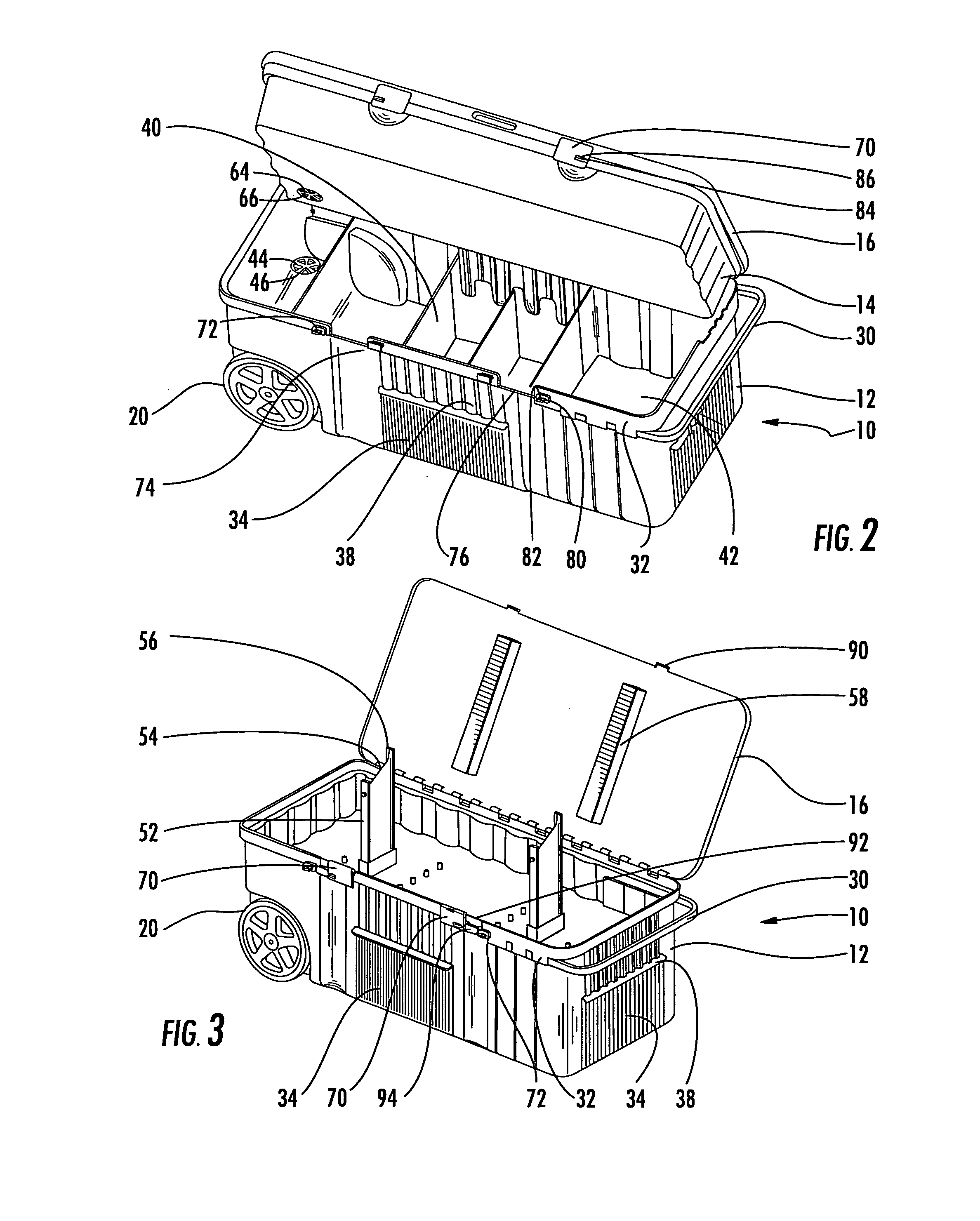
Portable storage container assembly
InactiveUS7284763B1Selectively accessedEasy and economical to manufactureCarriage/perambulator accessoriesCarriage/perambulator with single axisFlangeEngineering
A portable storage container assembly having a bottom container, a top container and a cover, wherein the bottom and top containers may be selectively and individually accessed through the use of a sliding latch member that engages one or more of a series of male members or flanges associated with the bottom container, top container and cover. A locking member may be attached to the latch and a male member to secure the containers in the closed position. Additional storage may be provided through a storage tray accessible from the outside of the bottom container or through a covered recessed area in the cover. The top container may include a pair of stand members for permitting a bow or other elongated devices to be stored.
Owner:KING KELLY
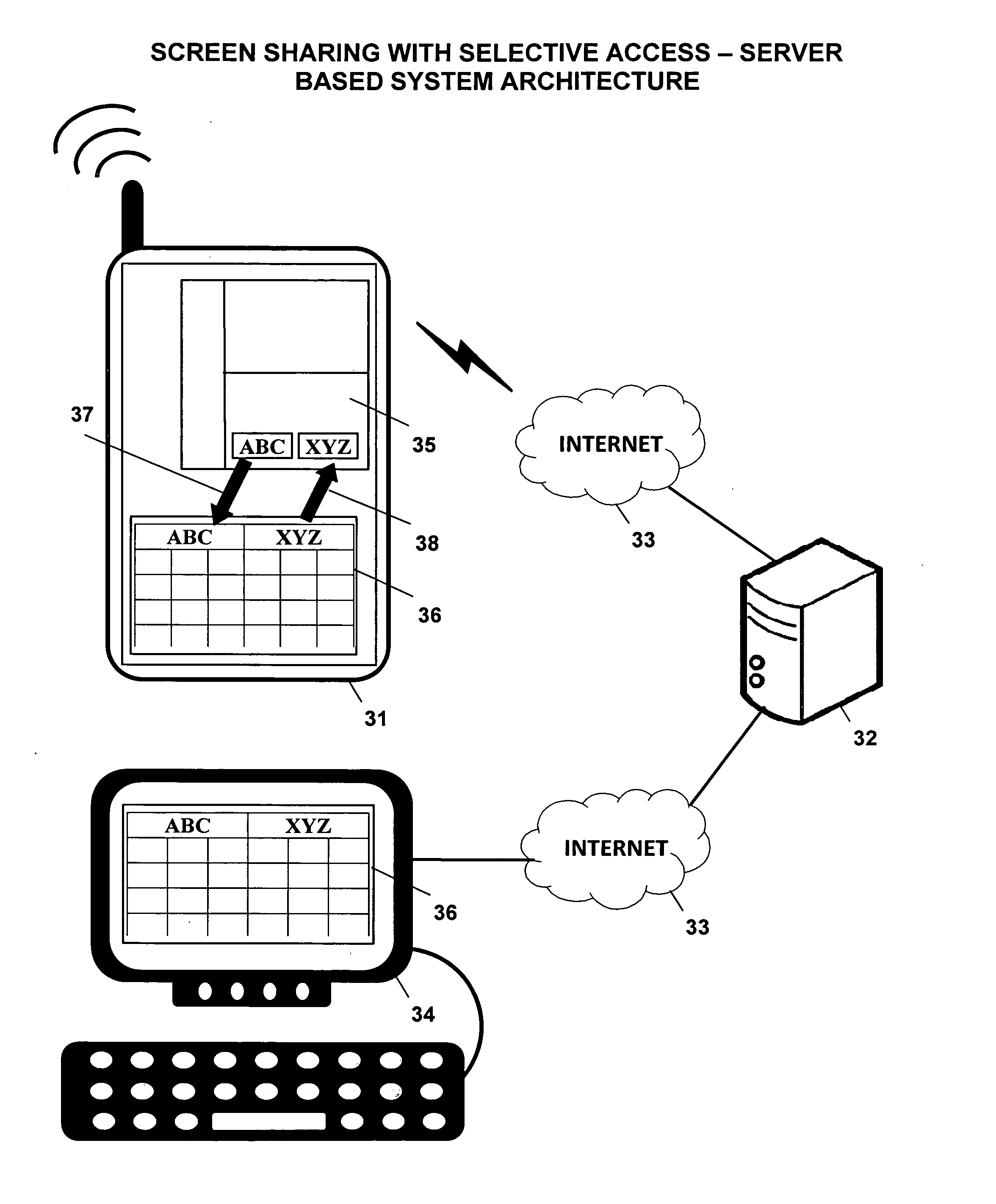
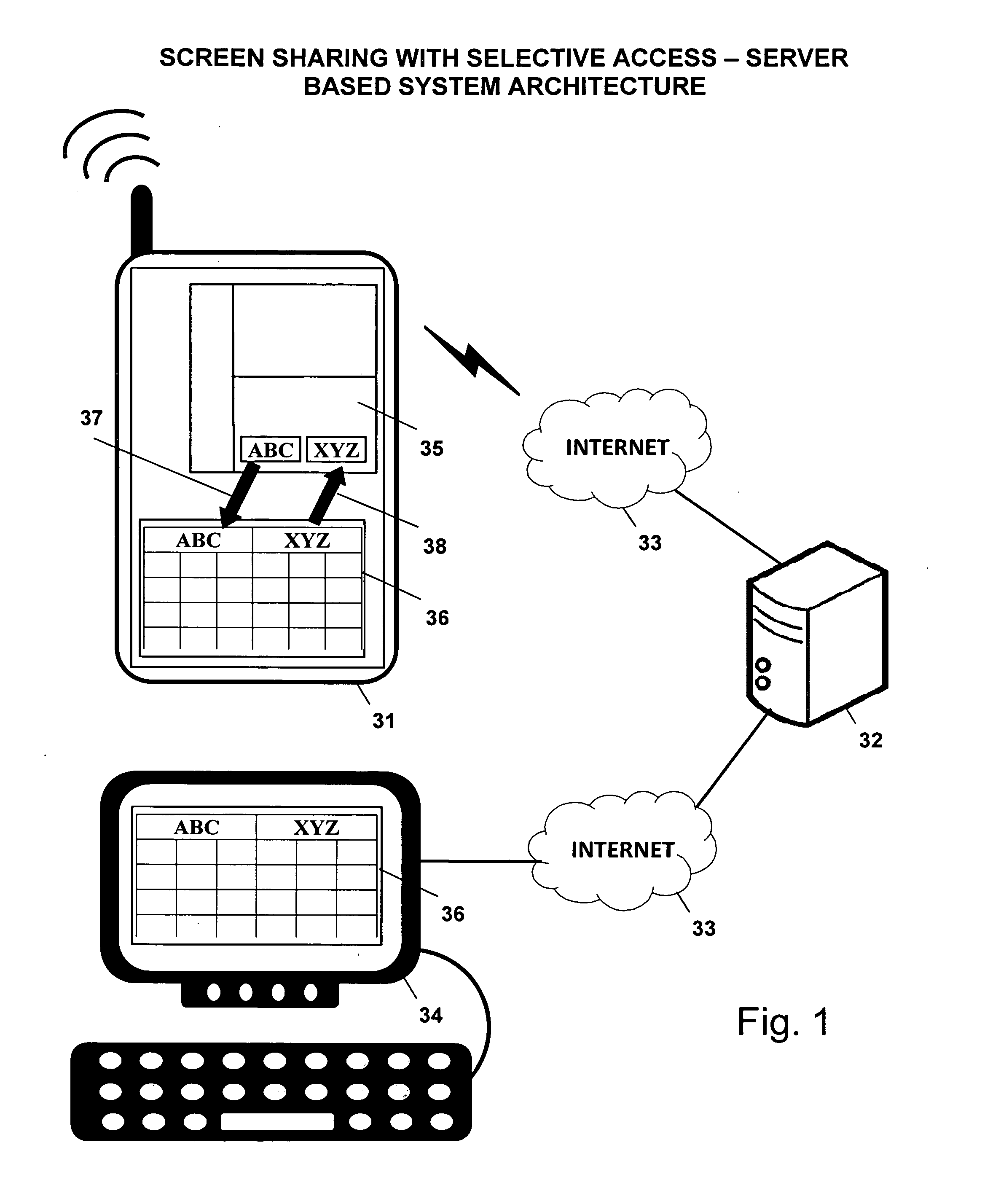
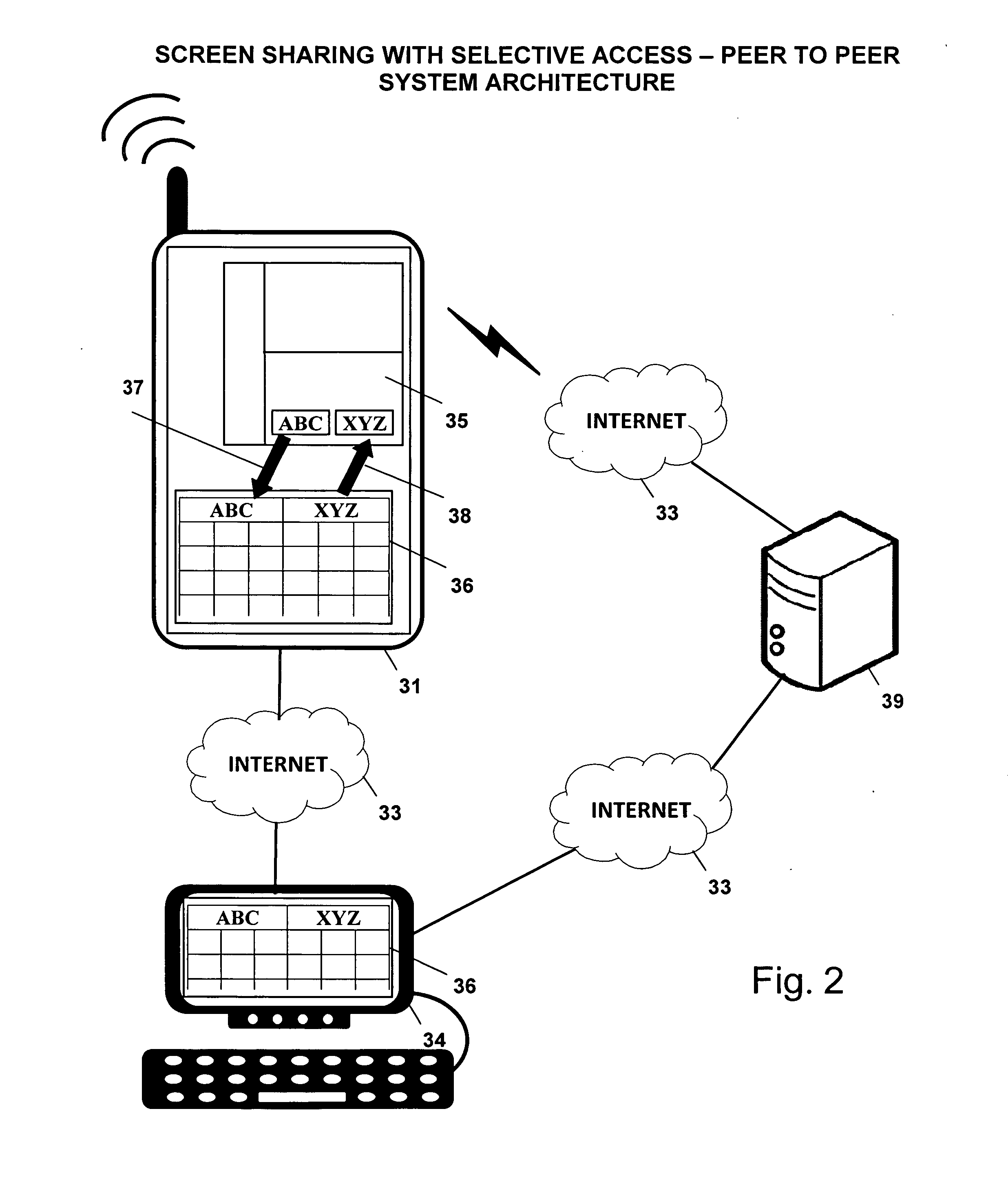
Screen sharing method with selective access to both data and logic of a shared application using a helper application
InactiveUS20110004888A1Guaranteed normal executionSelectively accessedInterprogram communicationExecution for user interfacesGraphicsGraphical user interface
A screen sharing system that enables selective access to application data and application logic is described. This screen sharing system is implemented by coupling a helper application (36) to an application that provides content referred to as content application (35).The helper application is an application that has the ability to programmatically access the content application (35) using window system graphical user interface application programming interface. Helper application (36) is used to get and set content application data and interact with the content application using window system input events that simulate user input.This method enables selective access to both application data and application logic that is necessary for use in a screen sharing system used by participants that may be trusted or may not be fully trusted.
Owner:SRINIVASAN SUDHARSHAN +2
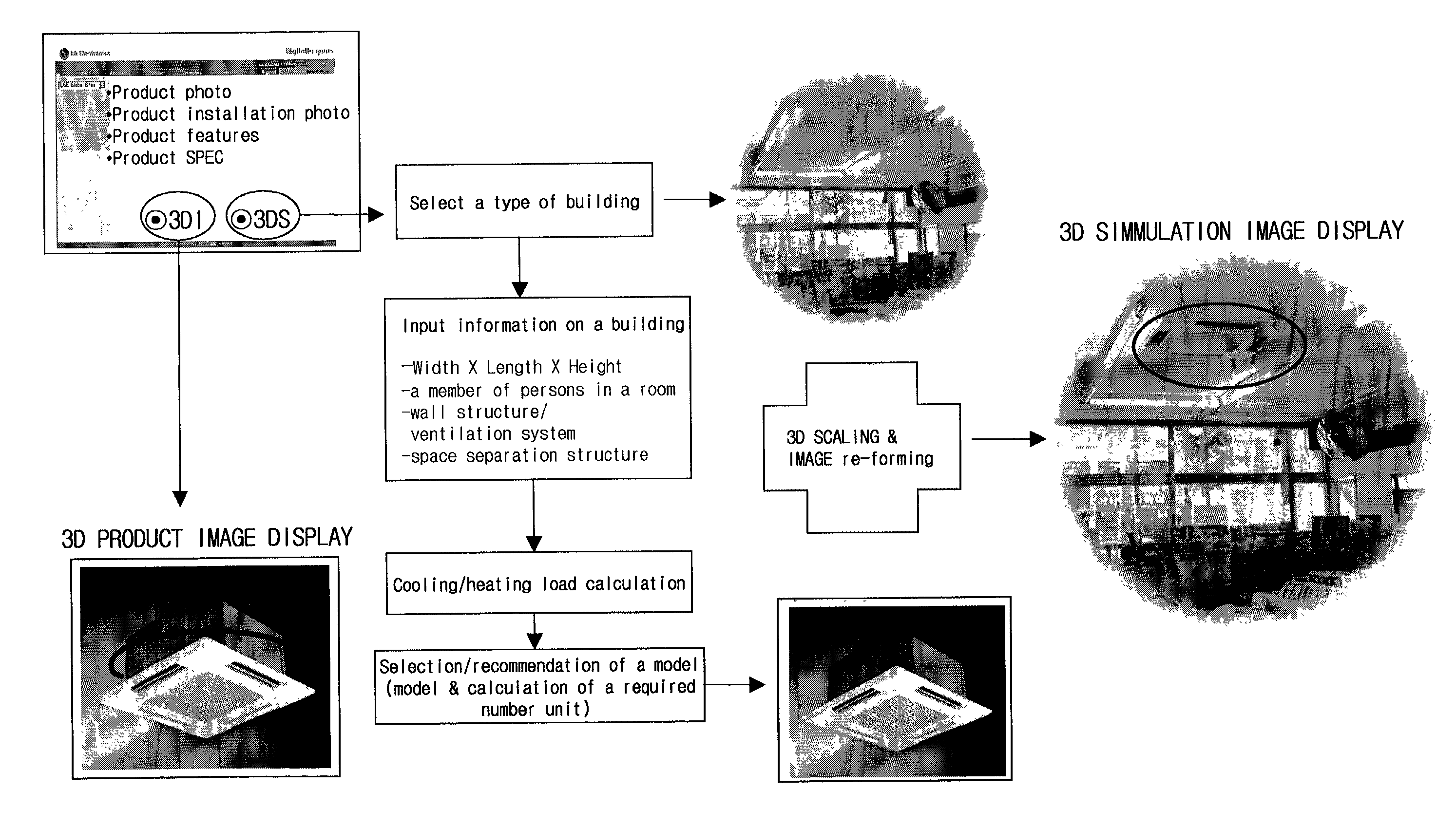
Product selling system and method for operating the same
InactiveUS7353188B2Reduce material handlingImprove satisfactionComplete banking machinesFinance3d imageService provision
A product selling system is provided which allows clients with networks accessible to the Internet to contact a service provider network for purchases. The service provider network includes a database with three dimensional (3D) image data for a variety of its products, and an application which allows a 3D product image to be integrated into a corresponding 3D image of a projected receiving space for the product prior to purchase. A web server which has a program operative with the database facilitates image manipulation to produce a 3D sample image from a product image on the web page if a client desires.
Owner:LG ELECTRONICS INC
Secure data transmission from unsecured input environments
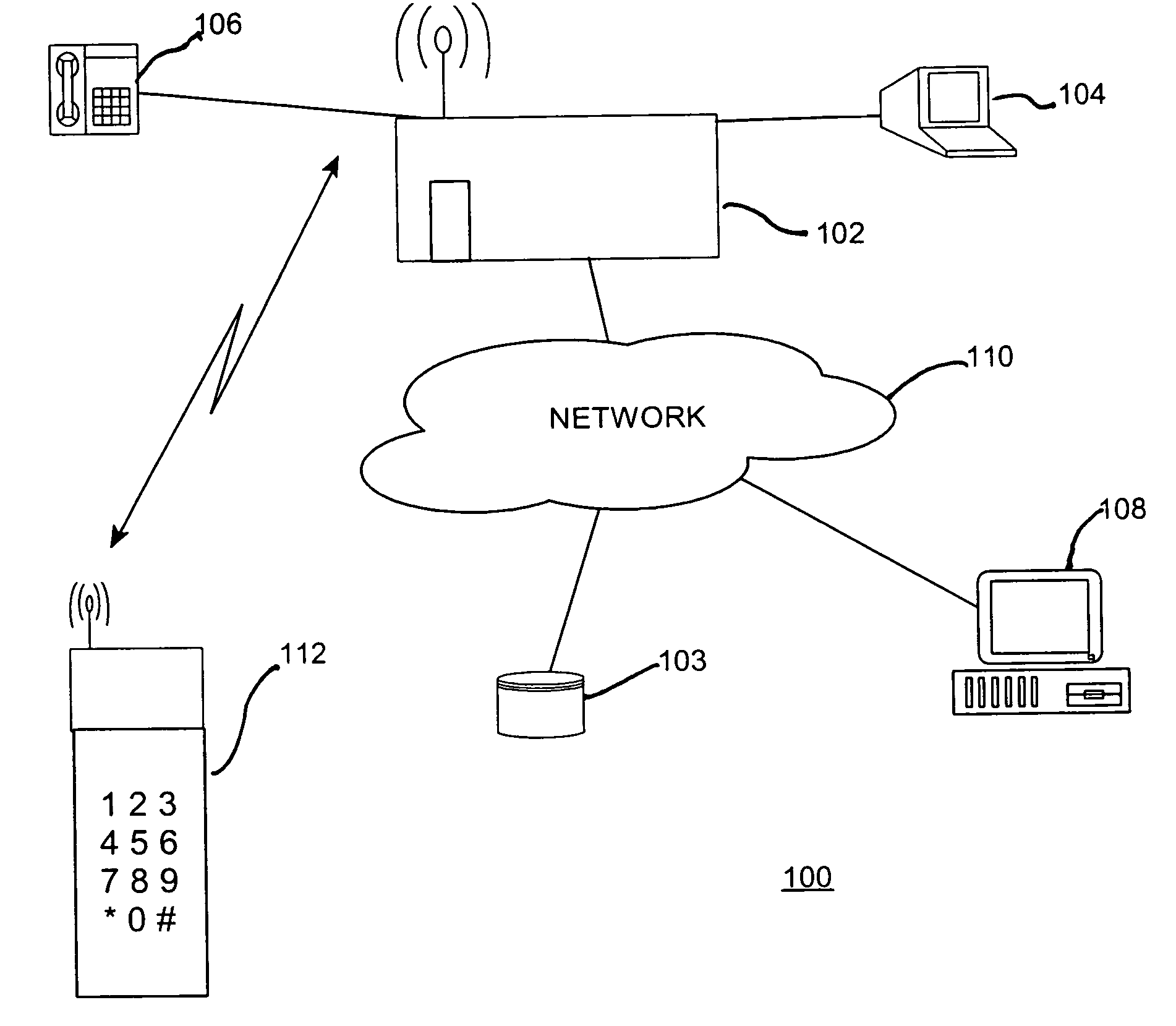
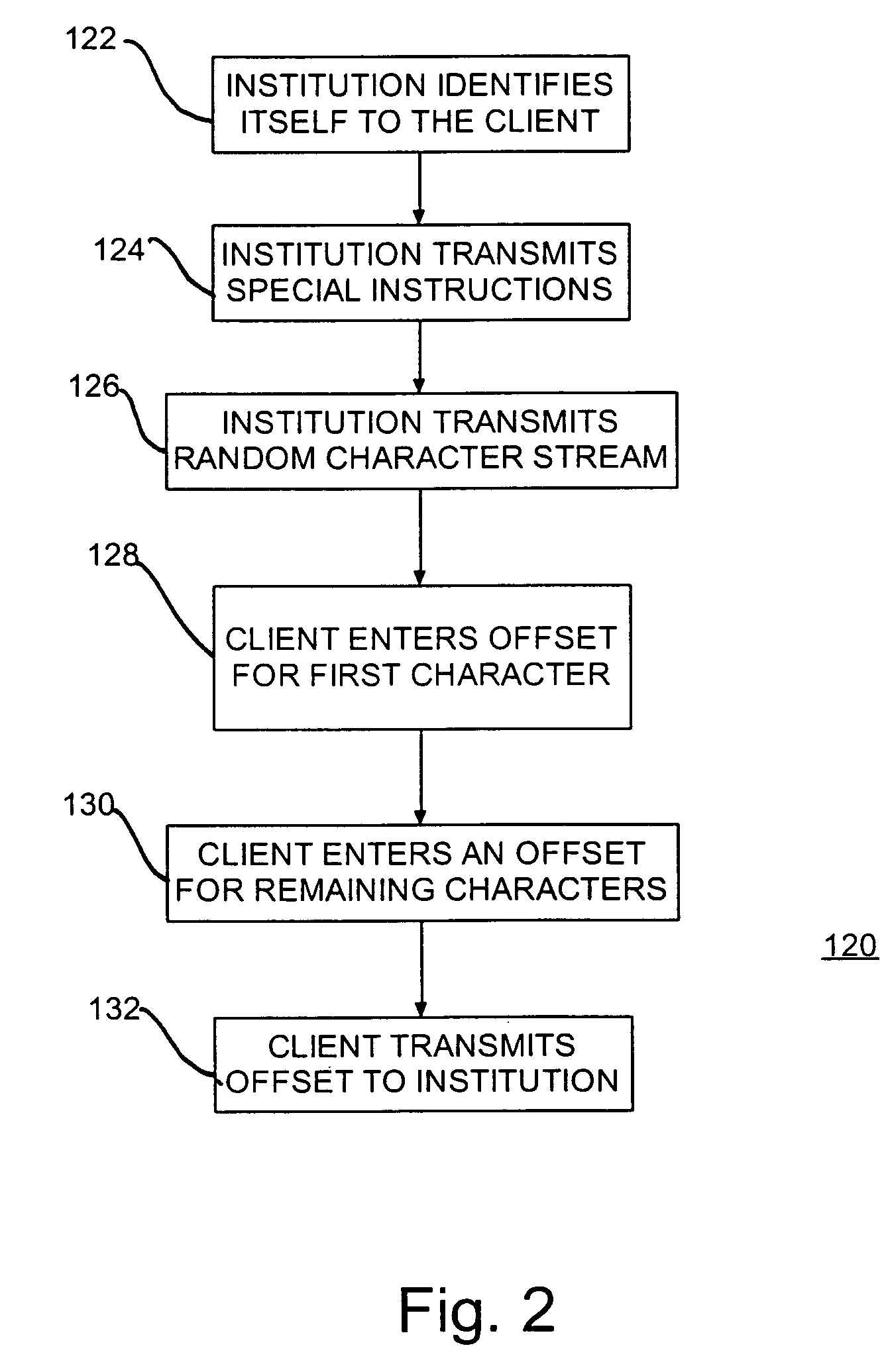
ActiveUS6990586B1Selectively accessedVolume/mass flow measurementUser identity/authority verificationPasswordClient-side
An apparatus, business method and program product for selectively providing access to a service facility such as a financial institution or bank. Client access codes (passwords, PINs) are maintained by the service facility in a database. When a client seeks access to the service facility, e.g., access to the client's account, a random sequence of character is generated and passed to the client. The client responds with an offset that when combined with the random character sequence is the client's access code. The client sends the code to the service facility and is granted access to the client's account. Optionally, the service facility may specify an intended relationship between the offset and the random character sequence, e.g., the offset is added / subtracted from the random character sequence. For additional security, dummy characters may be embedded in the random character sequence.
Owner:IBM CORP
Posture-based data protection
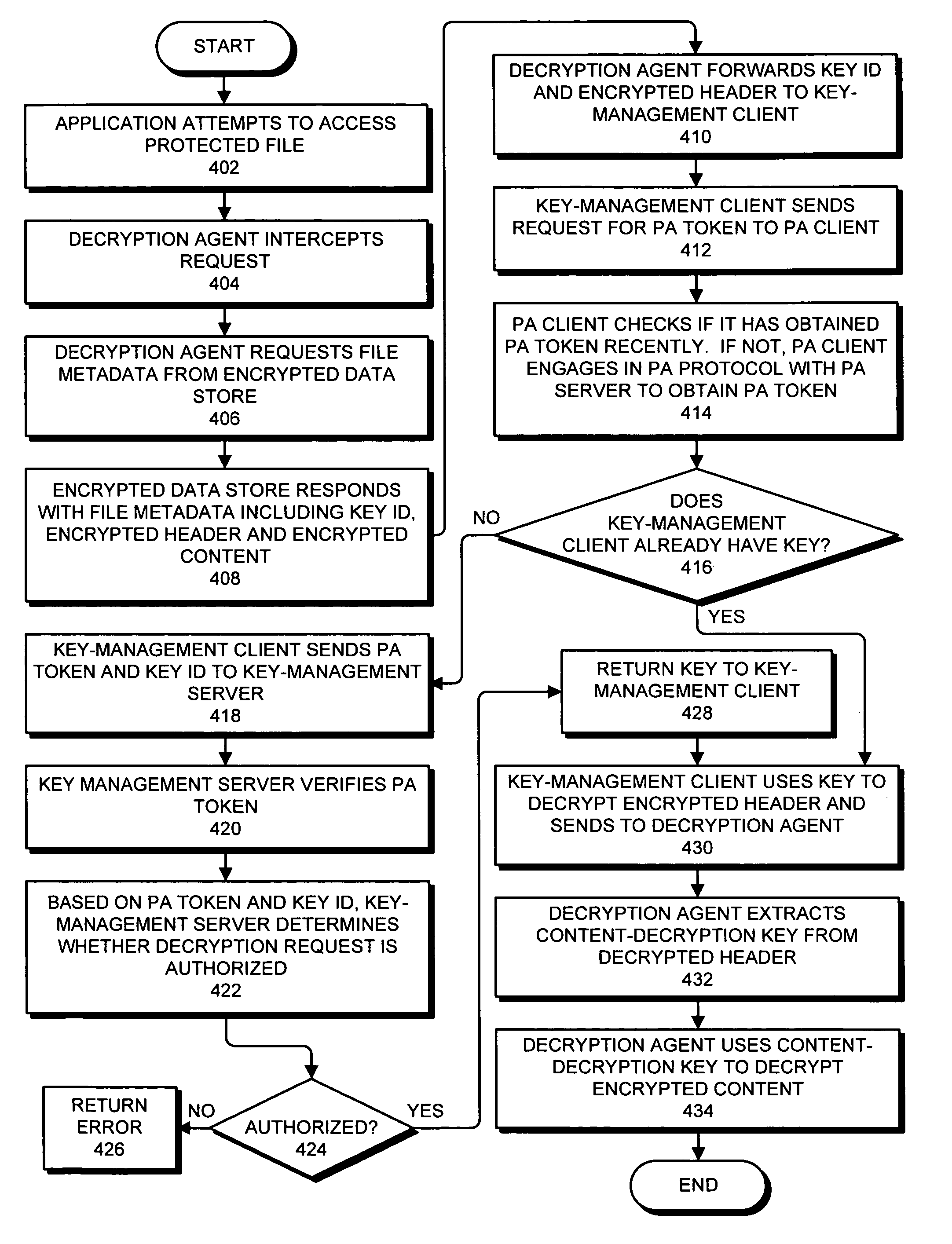
ActiveUS20070277240A1Selectively accessedEasy accessMemory loss protectionError detection/correctionSystem evaluationComputer security
One embodiment of the present invention provides a system that facilitates access to encrypted data on a computing device based on a security-posture of the computing device. During operation, the system assesses the security-posture of the computing device upon which the encrypted data is stored. If the assessed security-posture meets specified criteria, the system provides the computing device with a key which enables the computing device to access the encrypted data.
Owner:PALO ALTO RES CENT INC
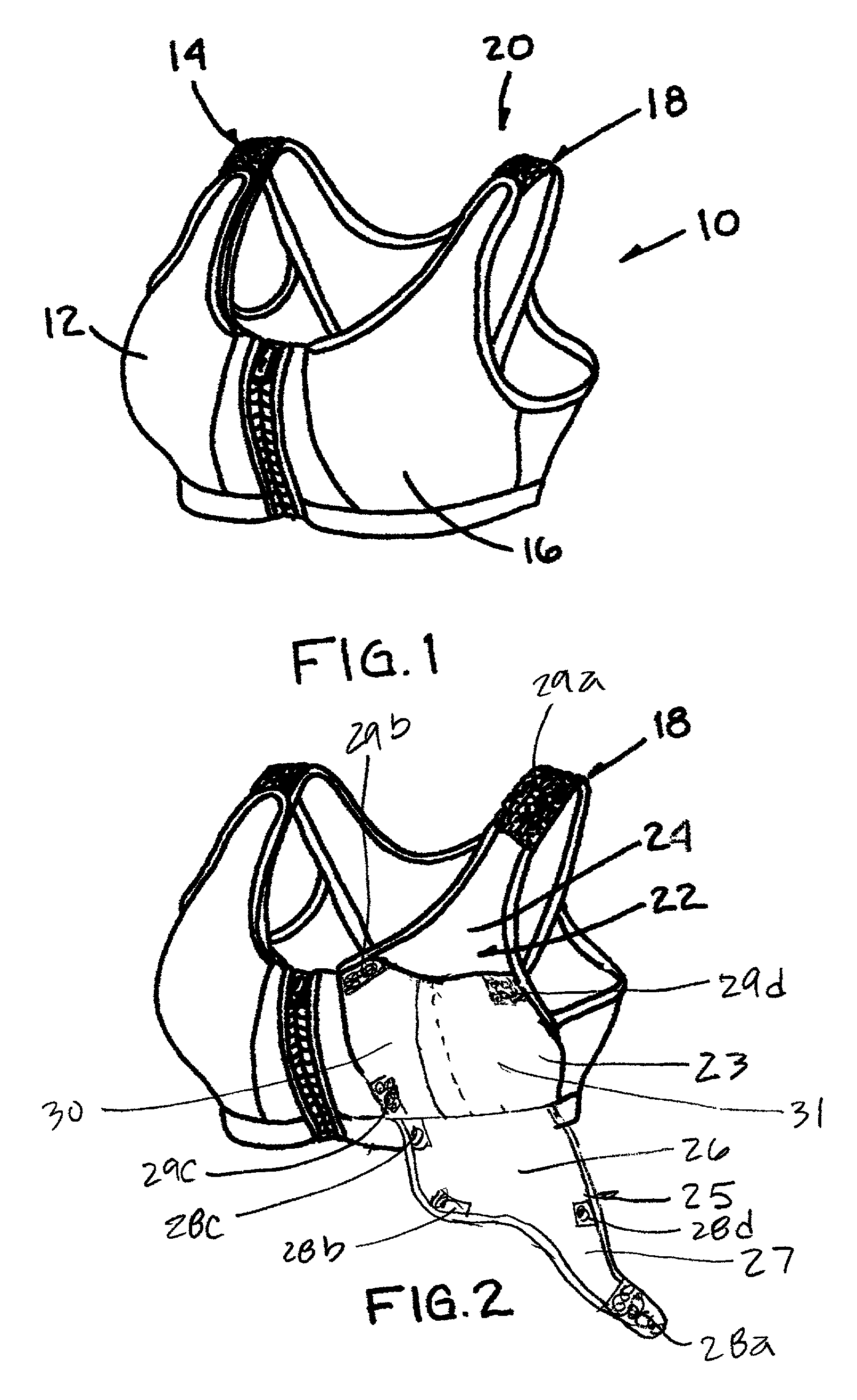
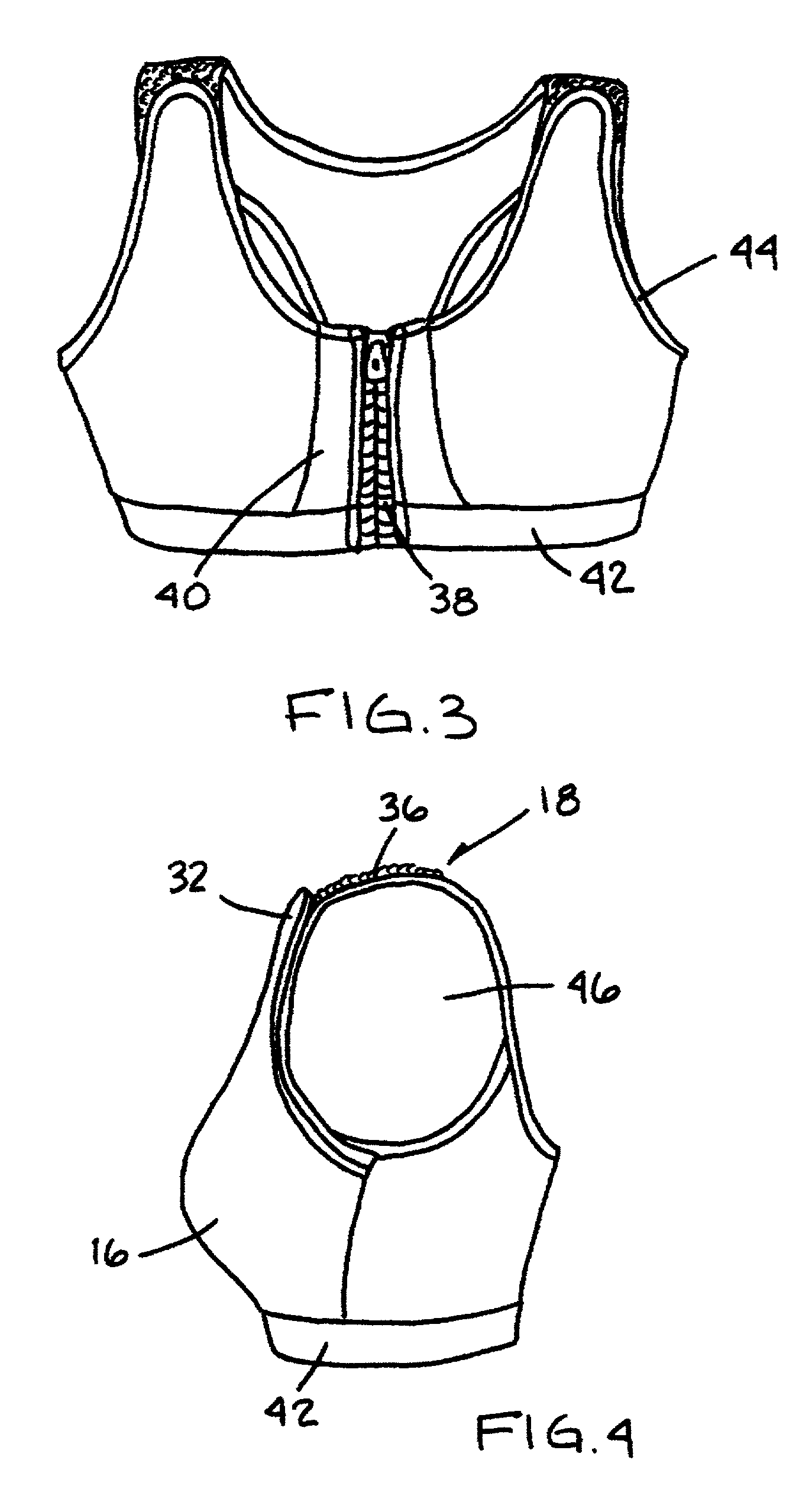
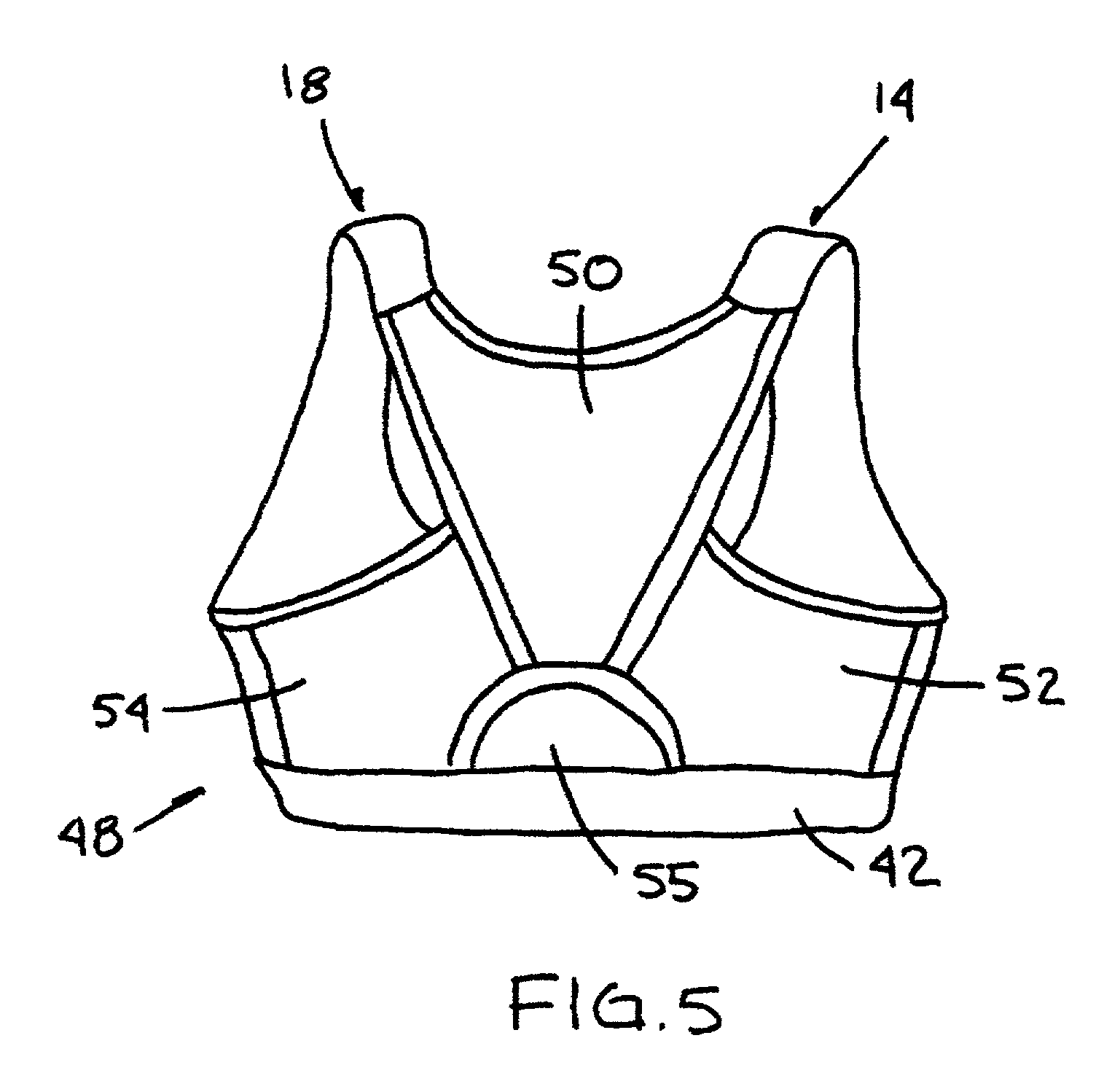
Sports brassiere for nursing
A brassiere includes a pair of shoulder straps and a pair of cup members located generally below the shoulder straps. Each of the cup members includes an inner contact layer substantially completely covering the breast of a wearer, and an outer compression layer slidably disposed in covering relation to the inner contact layer. An adjustment and securing assembly is disposed between each outer compression layer and its corresponding shoulder strap. The adjustment and securing assembly, which may be provided as a hook-and loop fastener system, is adapted and constructed to adjustably secure the outer compression layer to the shoulder strap. Attachment of the outer compression layers to the shoulder straps lifts and compresses the breasts of the wearer to reduce the potential for inertial movement of the breasts both outwardly and downwardly.
Owner:WAGNER PENNY JO
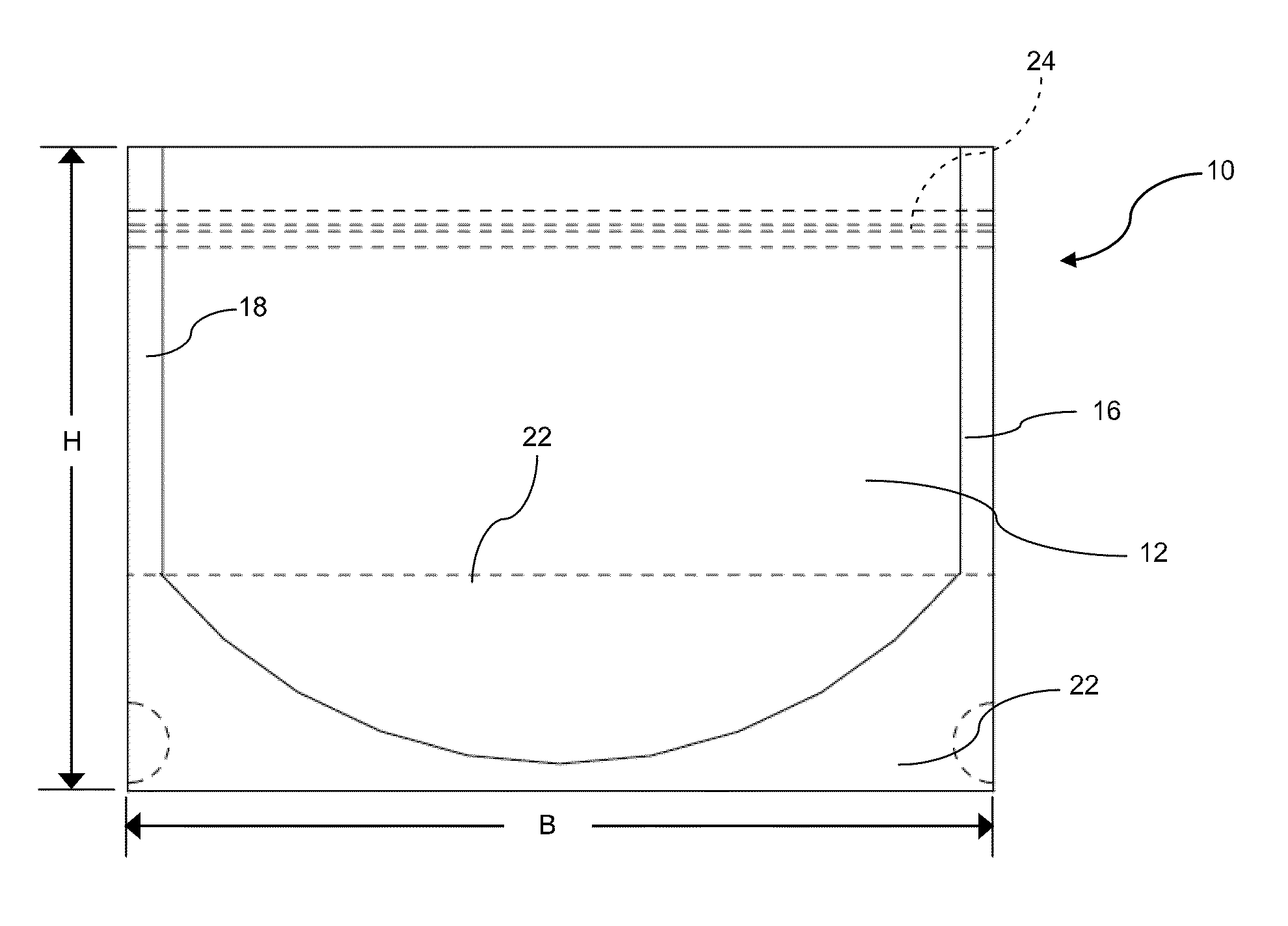
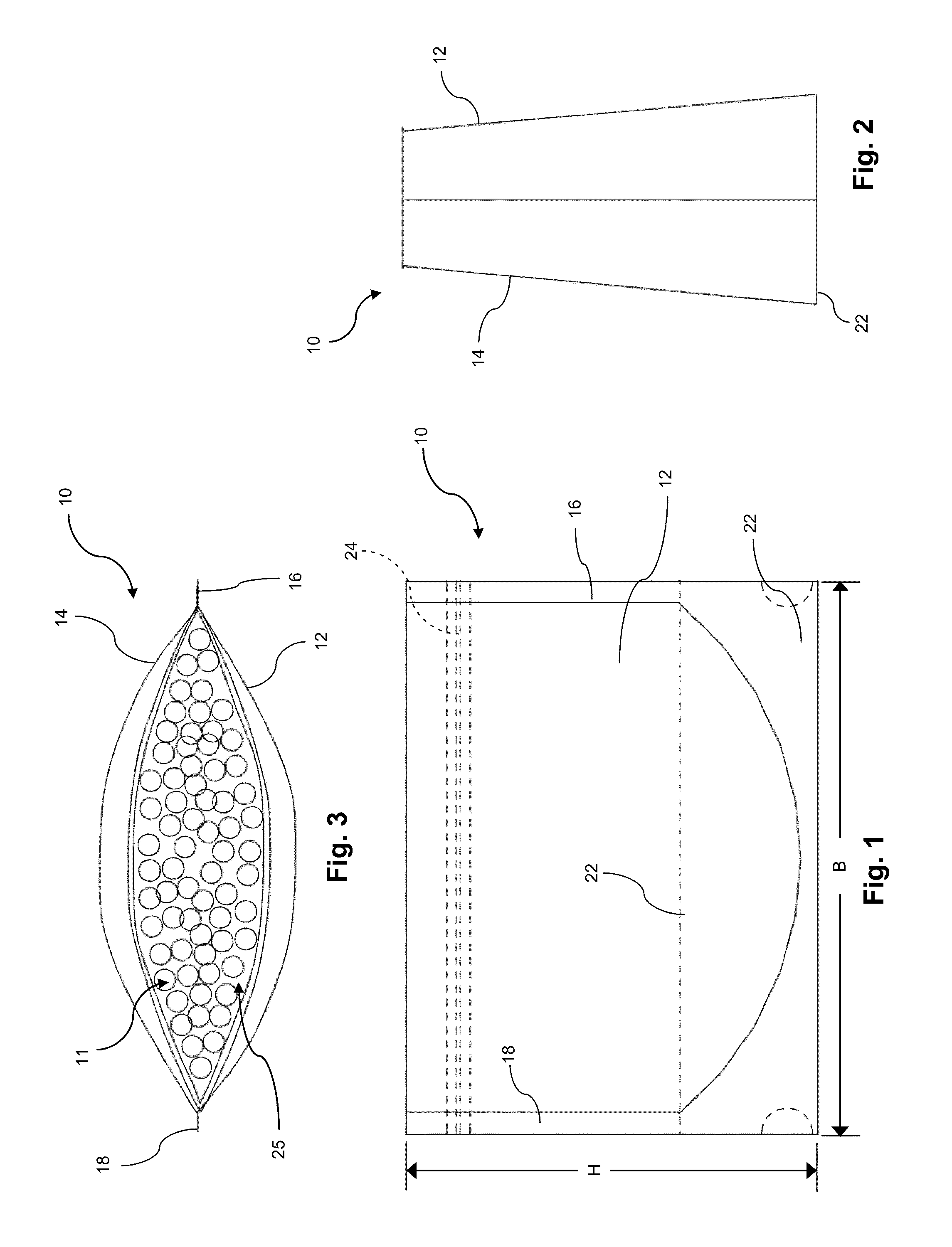
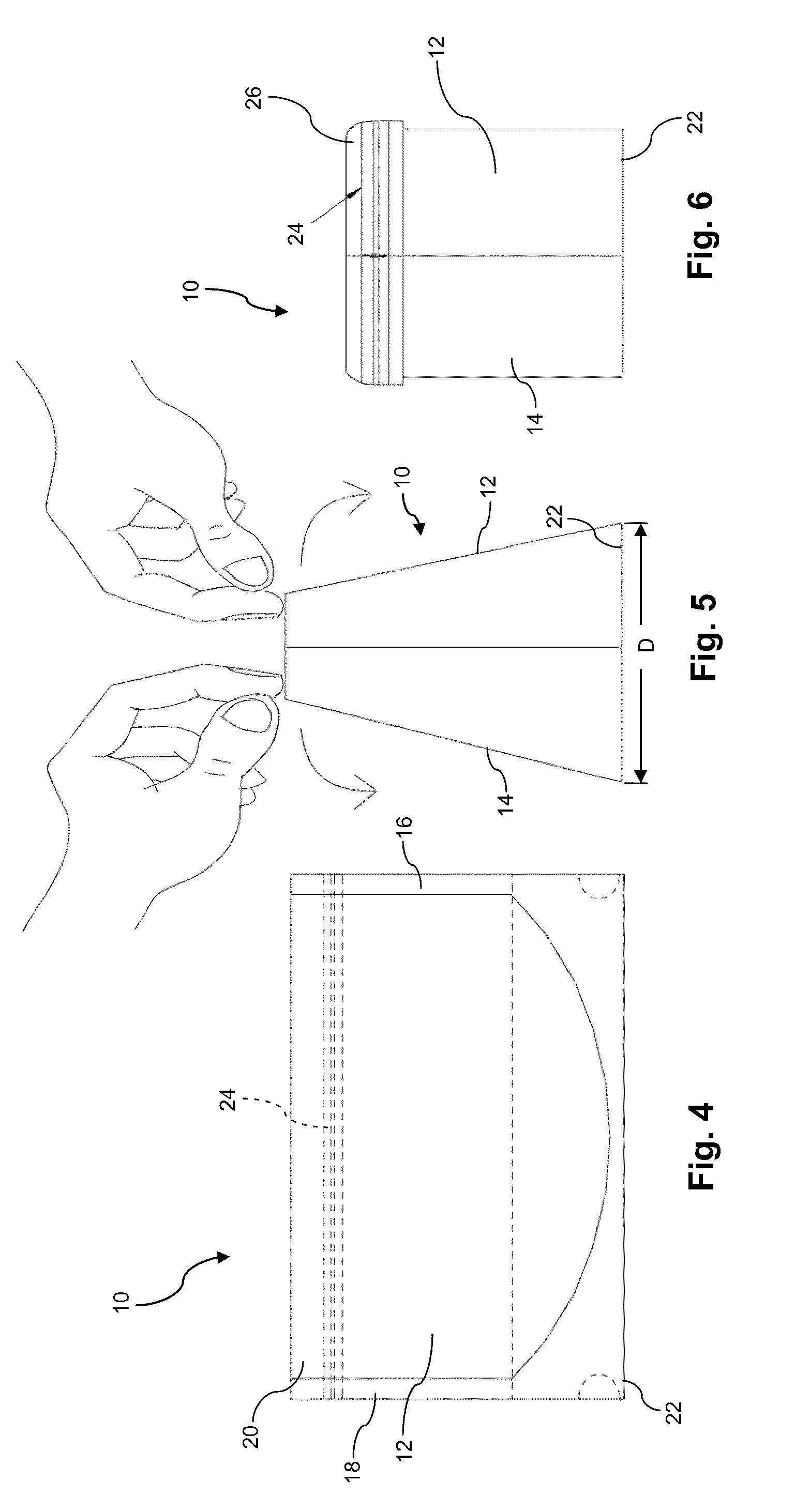
Flexible package and method of forming a cuff
A package having a foldable top region is provided. The package generally includes panel portions that at least partially define an interior cavity therebetween and accessible through an access opening. The top portion can provide a cuff member or cuff region that can be folded and unfolded to facilitate use of the package as a bowl or other cuffed container for material contents. The package can be adapted to hold its shape as a bowl or cuffed container.
Owner:STEELE MARK
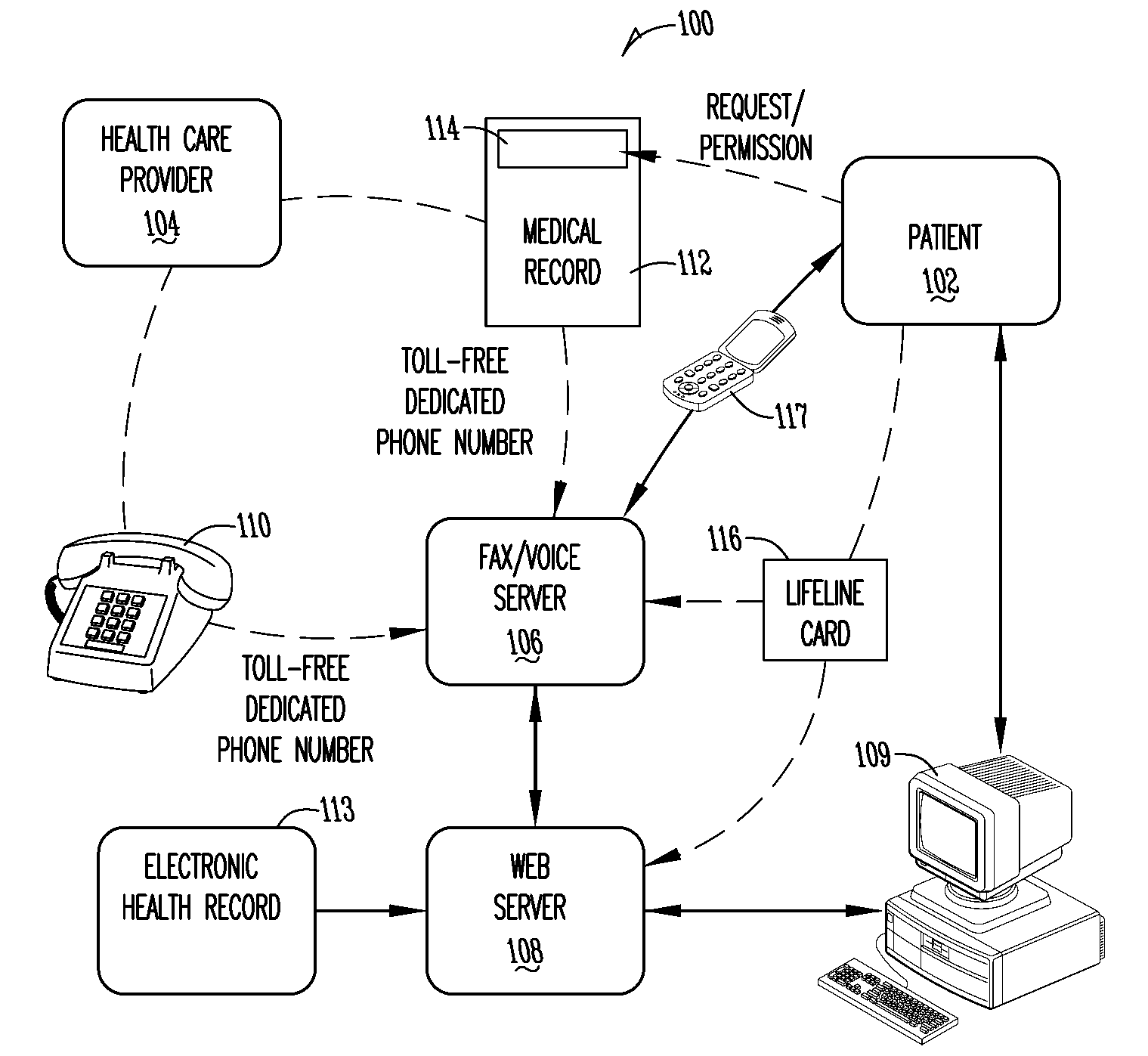
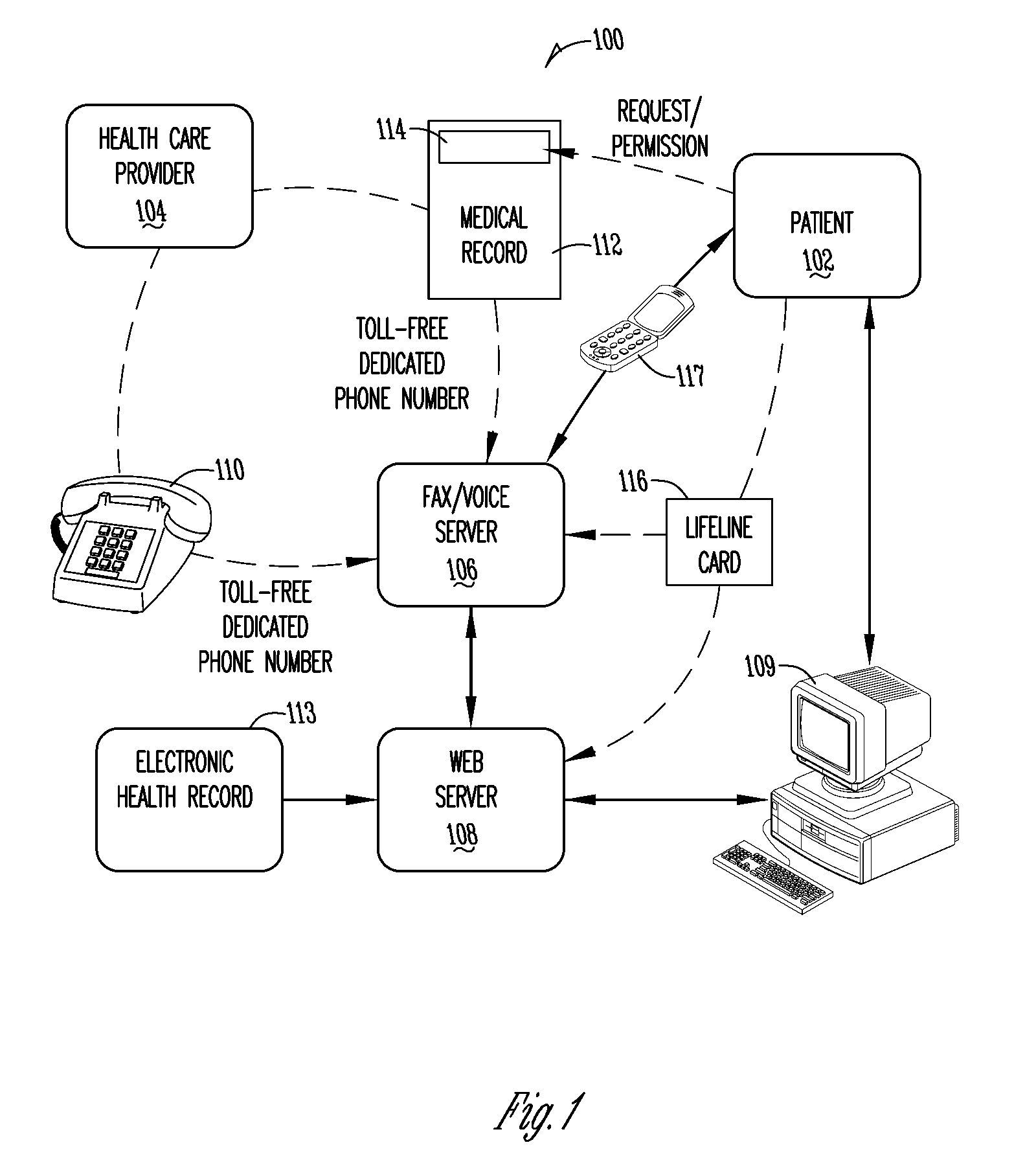
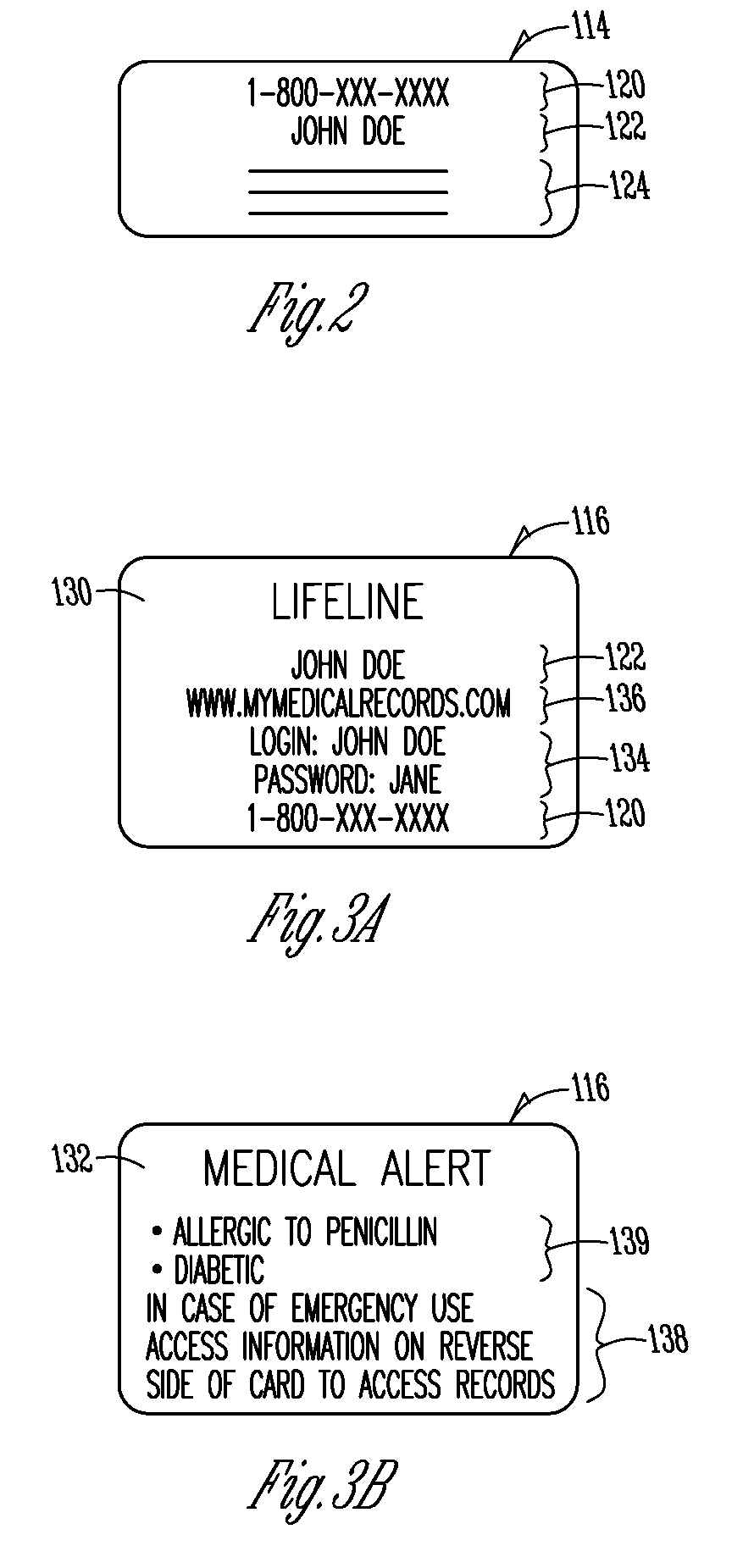
Method and system for providing online medical records with emergency password feature
InactiveUS20090055222A1Selectively accessFacilitate complianceFinanceLocal control/monitoringMedical recordMedical treatment
A method for maintaining personal health records of a user in manner that allows the personal health records to be accessed in an emergency while still allowing the user to control privacy is provided. The method includes providing a web site allowing the user to store a plurality of personal health records associated with the user and accessible through use of a password associated with the user, receiving instructions from the user to allow them to select a subset of the plurality of personal health records, the subset of the plurality of personal health records accessible through use of an emergency password, and making available the subset of the plurality of personal health records on the web site through use of the emergency password. An image of the user and the subset of health records may be displayed upon emergency login.
Owner:MYMEDICALRECORDS
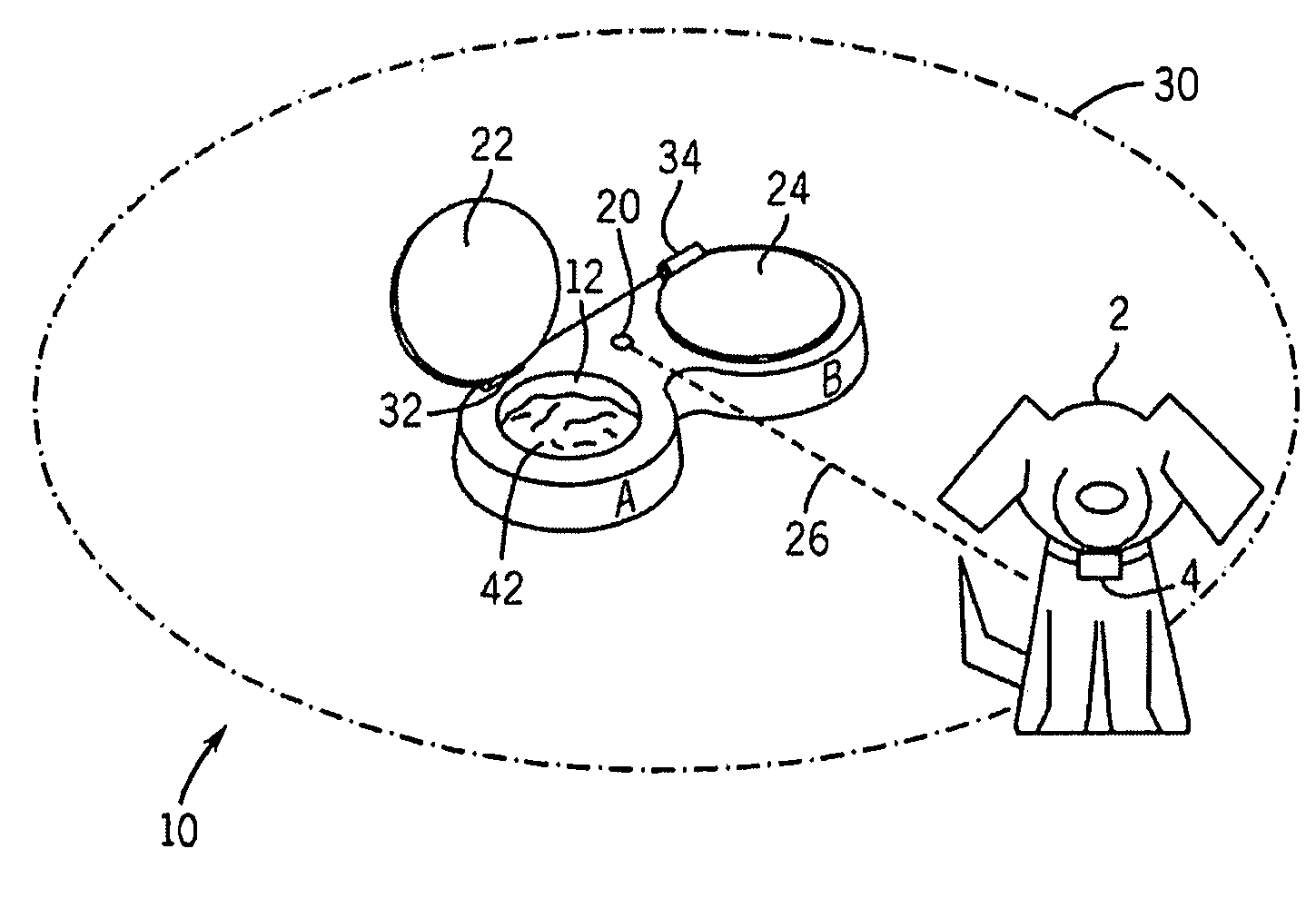
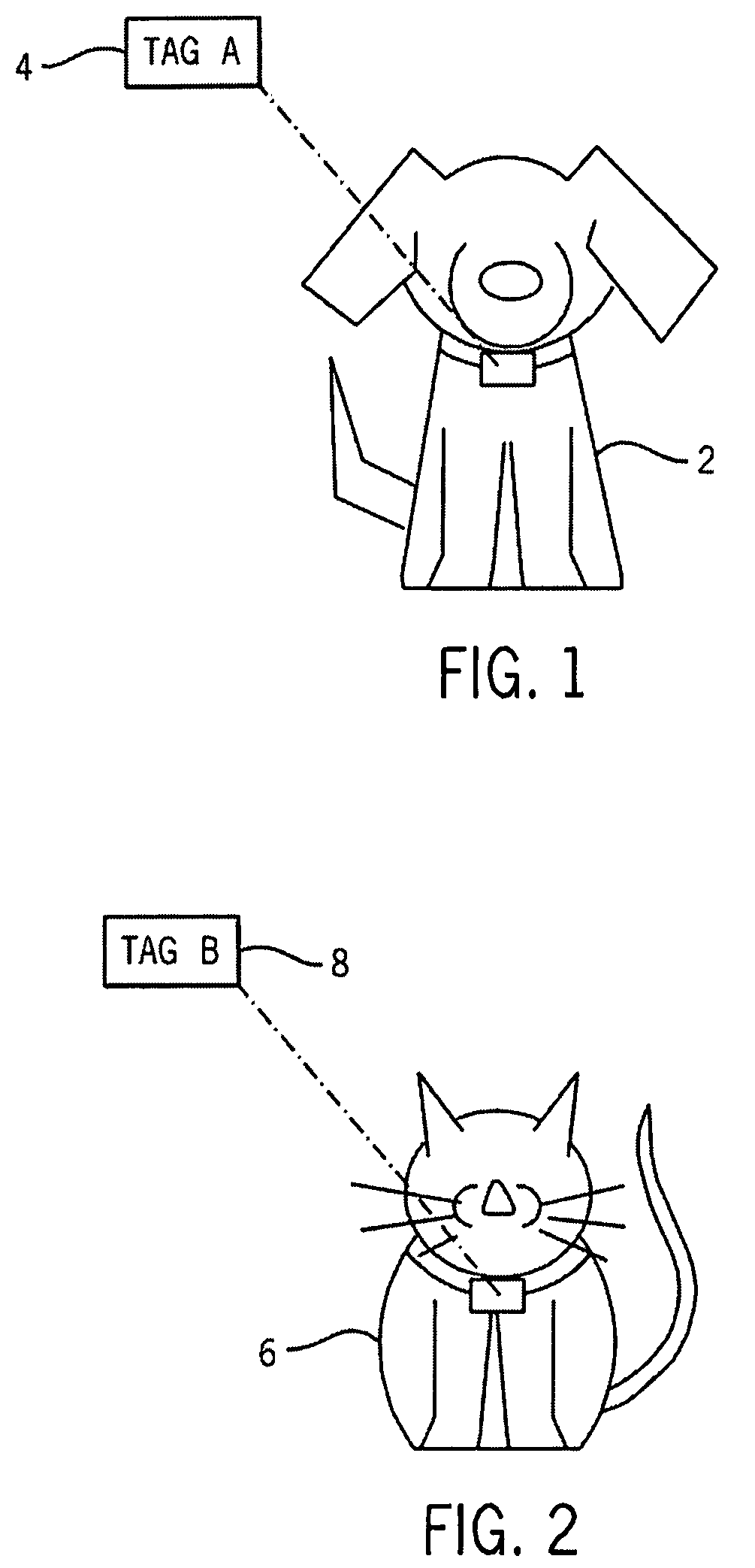
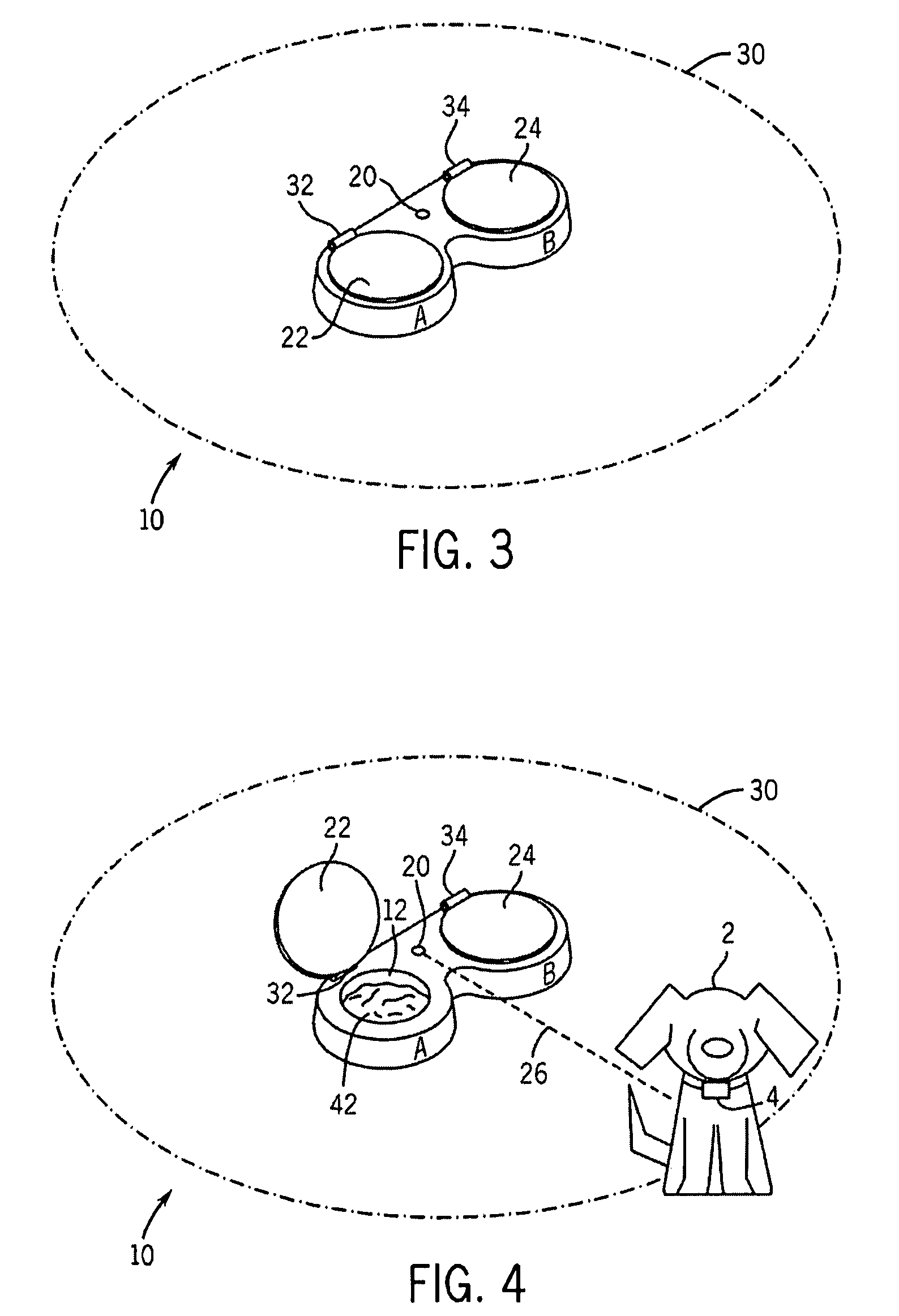
Lidded pet dish
A lidded pet food dish uses wireless technology to independently and selectively open one of a plurality of lidded food compartments for access by a pet. The dish discriminates between pets by means of a tag worn by each pet to allow or prevent access to a given food compartment. Electronic circuitry for this functionality is operable by any wireless technology and provides for manual system override by the pet owner as well as remote control capability.
Owner:GOEHRING HEIDI L
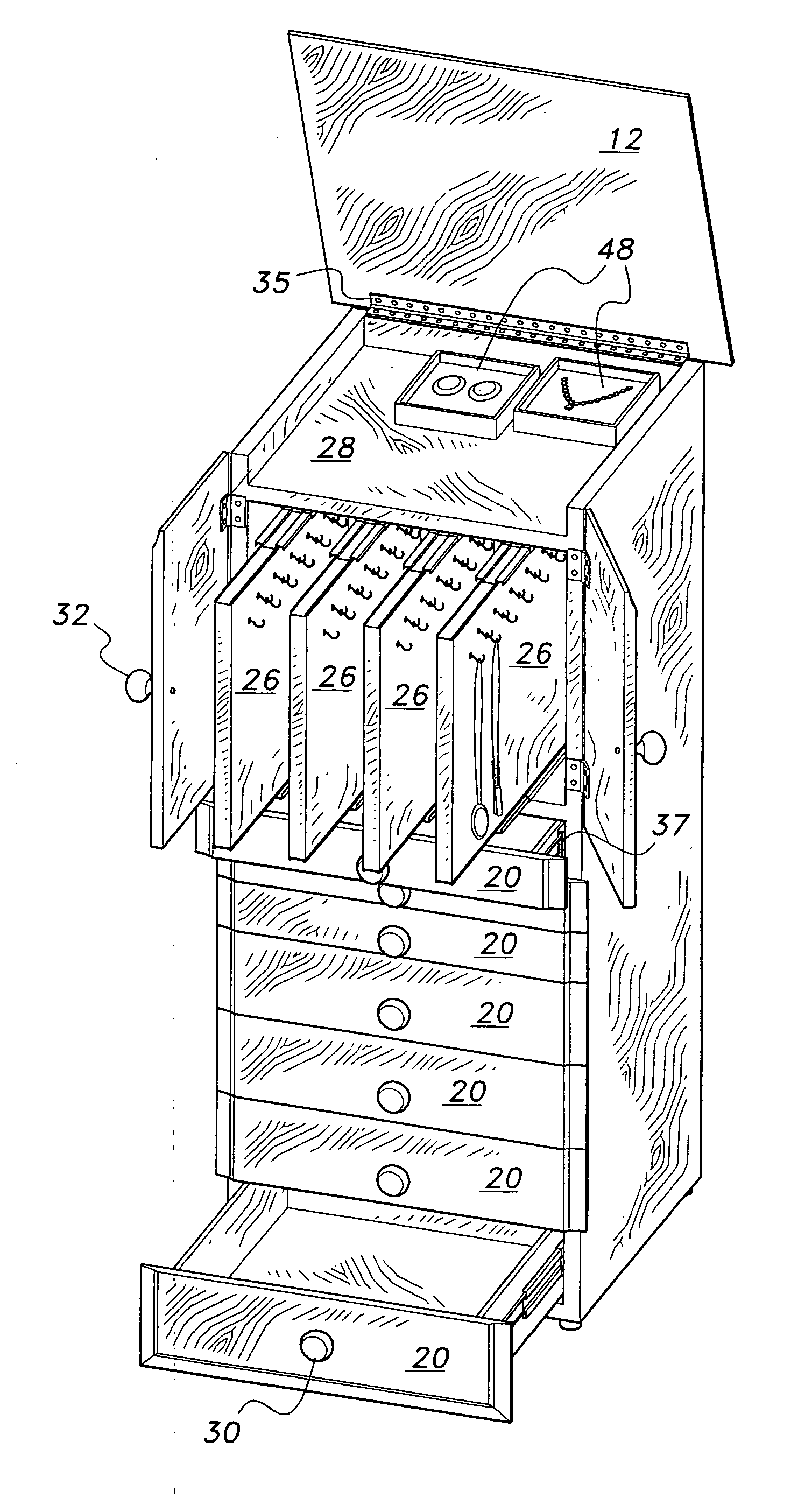
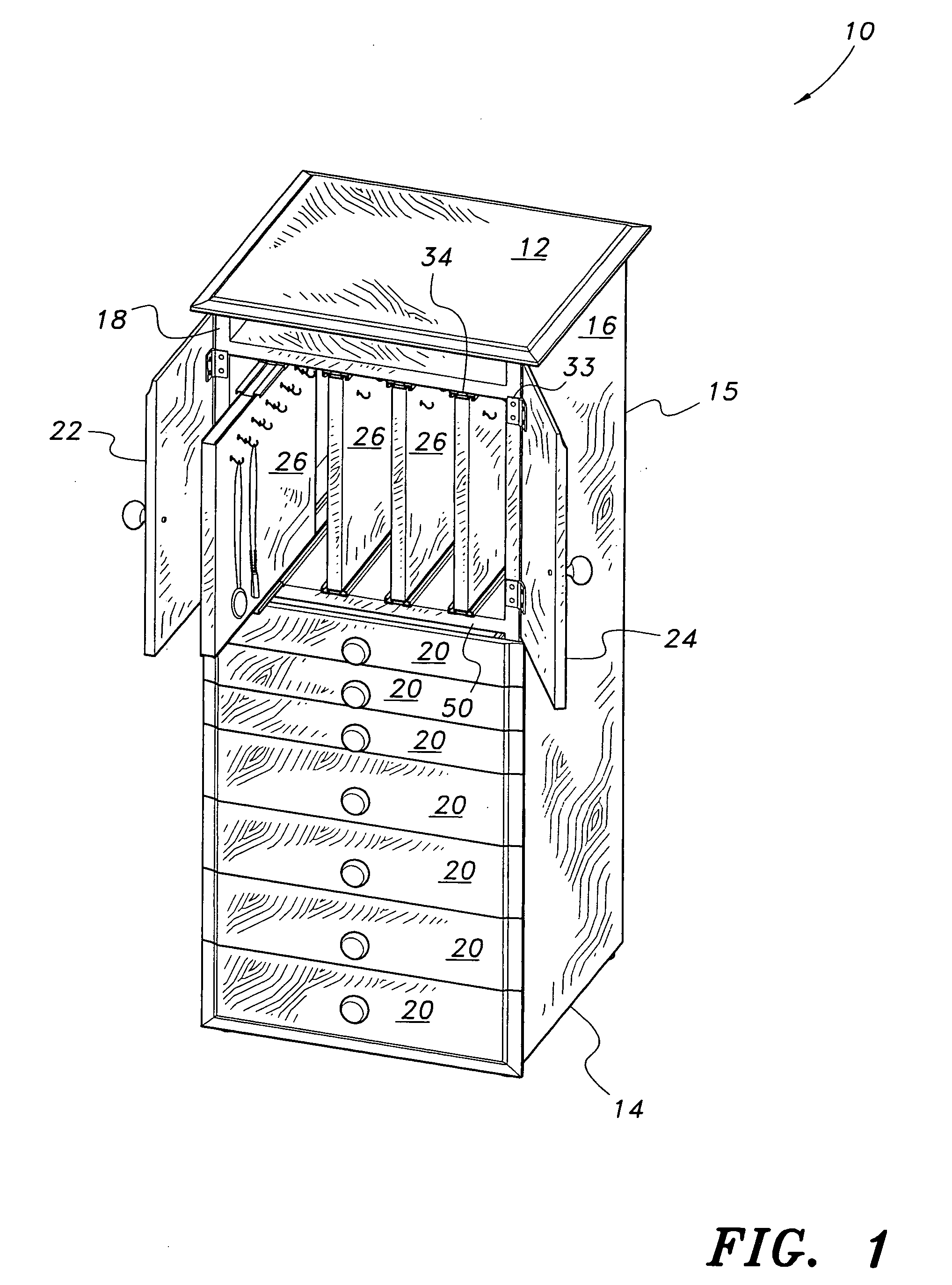
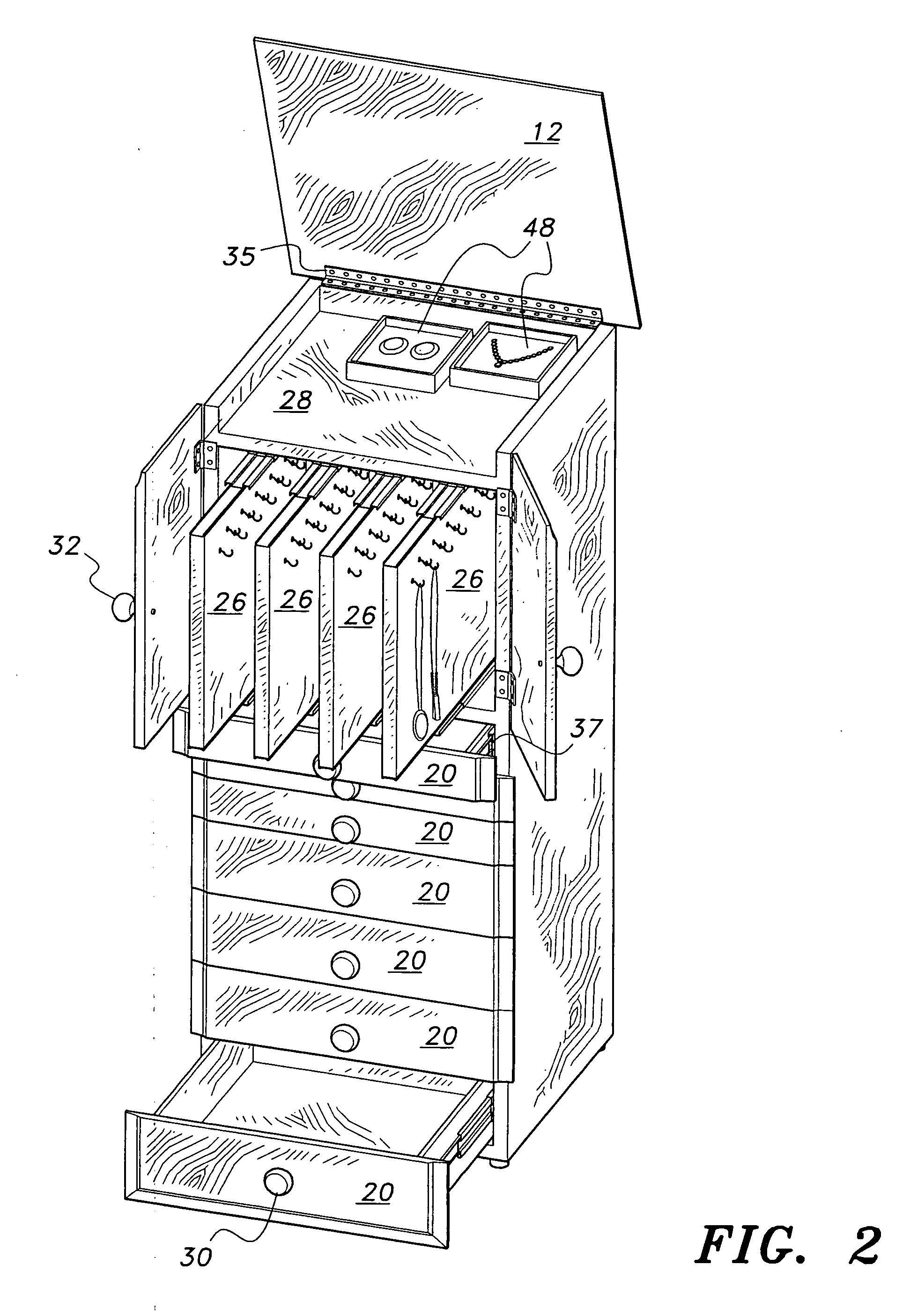
Jewelry storage cabinet
InactiveUS20070262683A1Selectively accessedReadily apparentChestsDressing tablesEngineeringMechanical engineering
Owner:CREED GARY D
Thyristor-based semiconductor memory device with back-gate bias
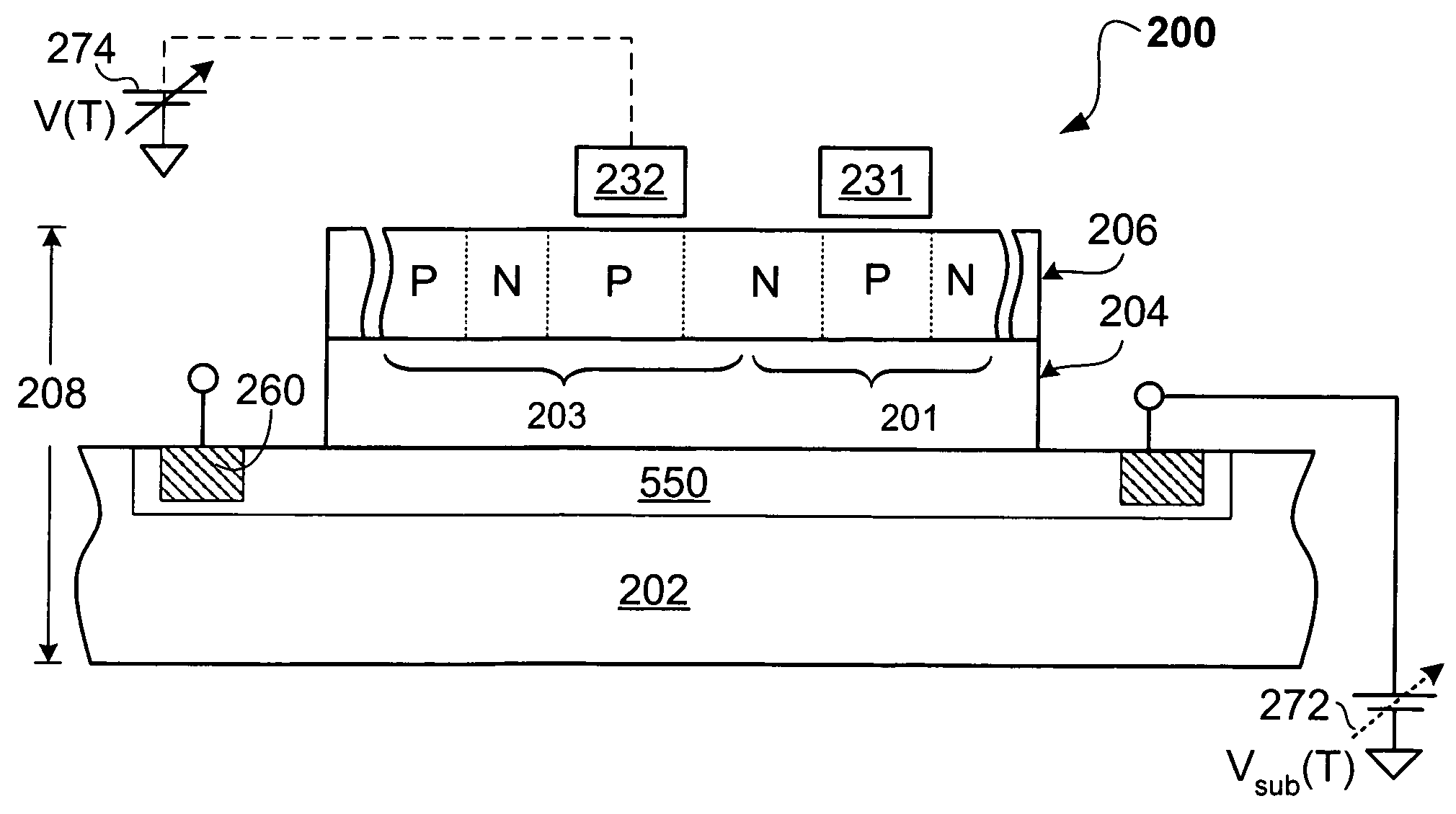
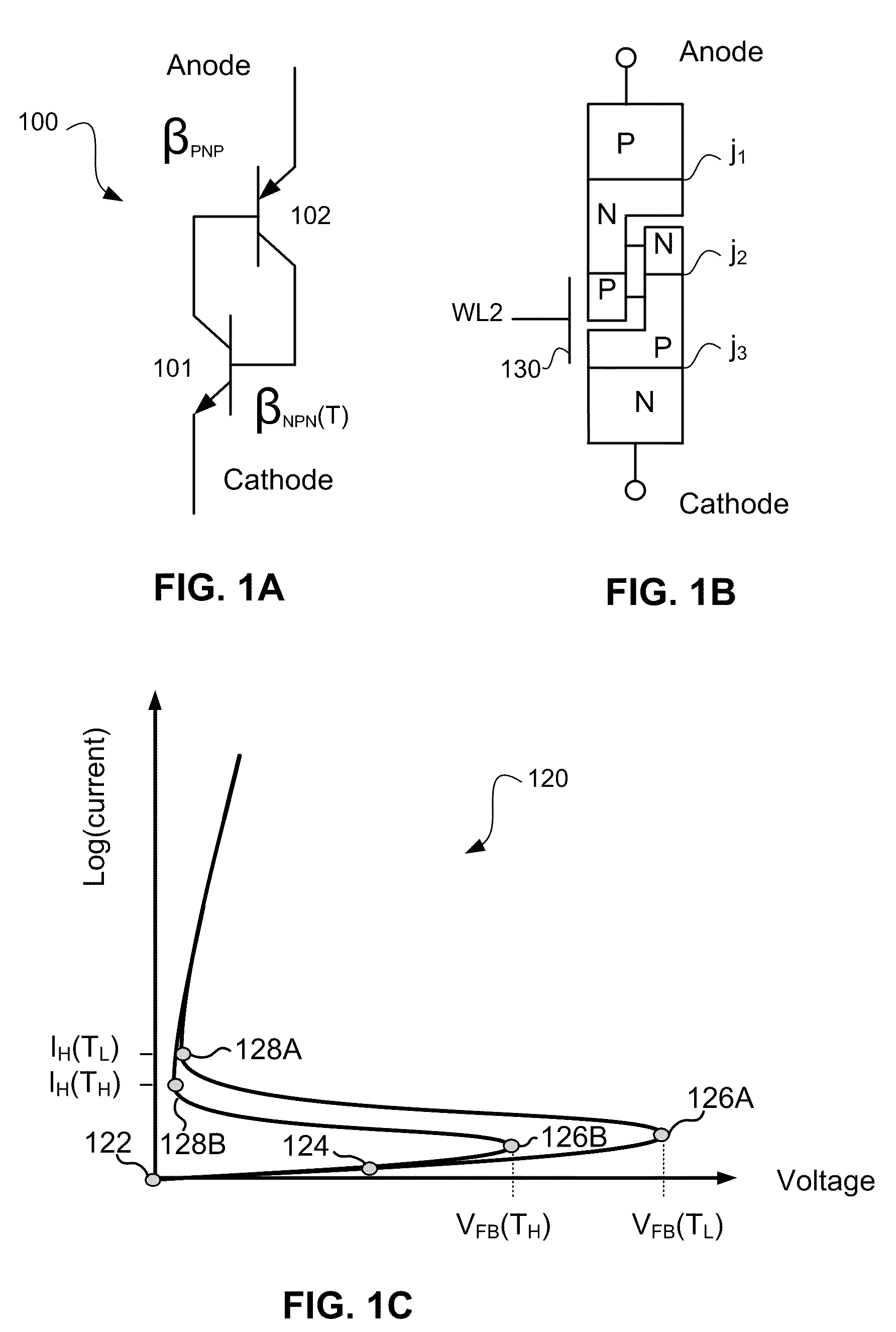
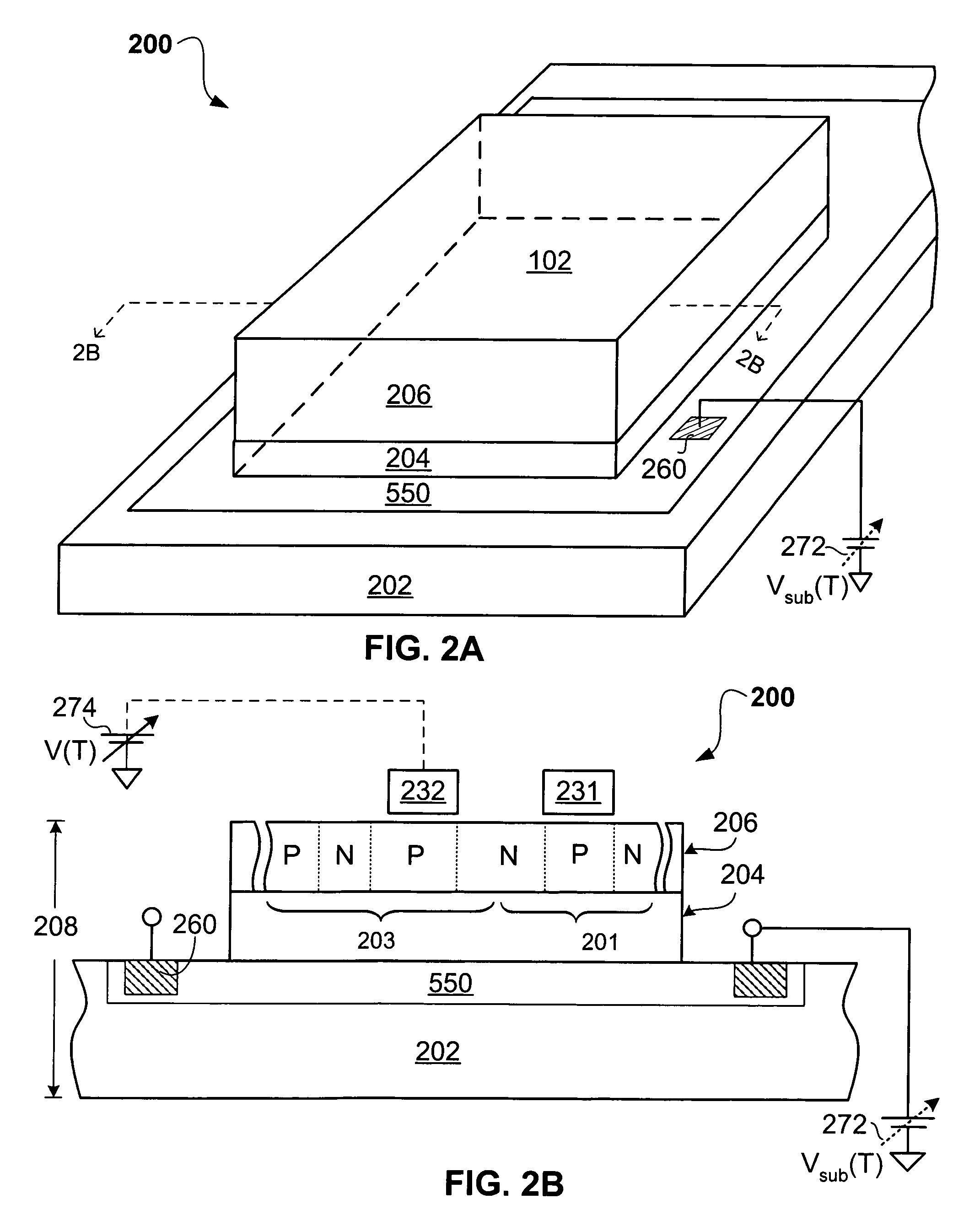
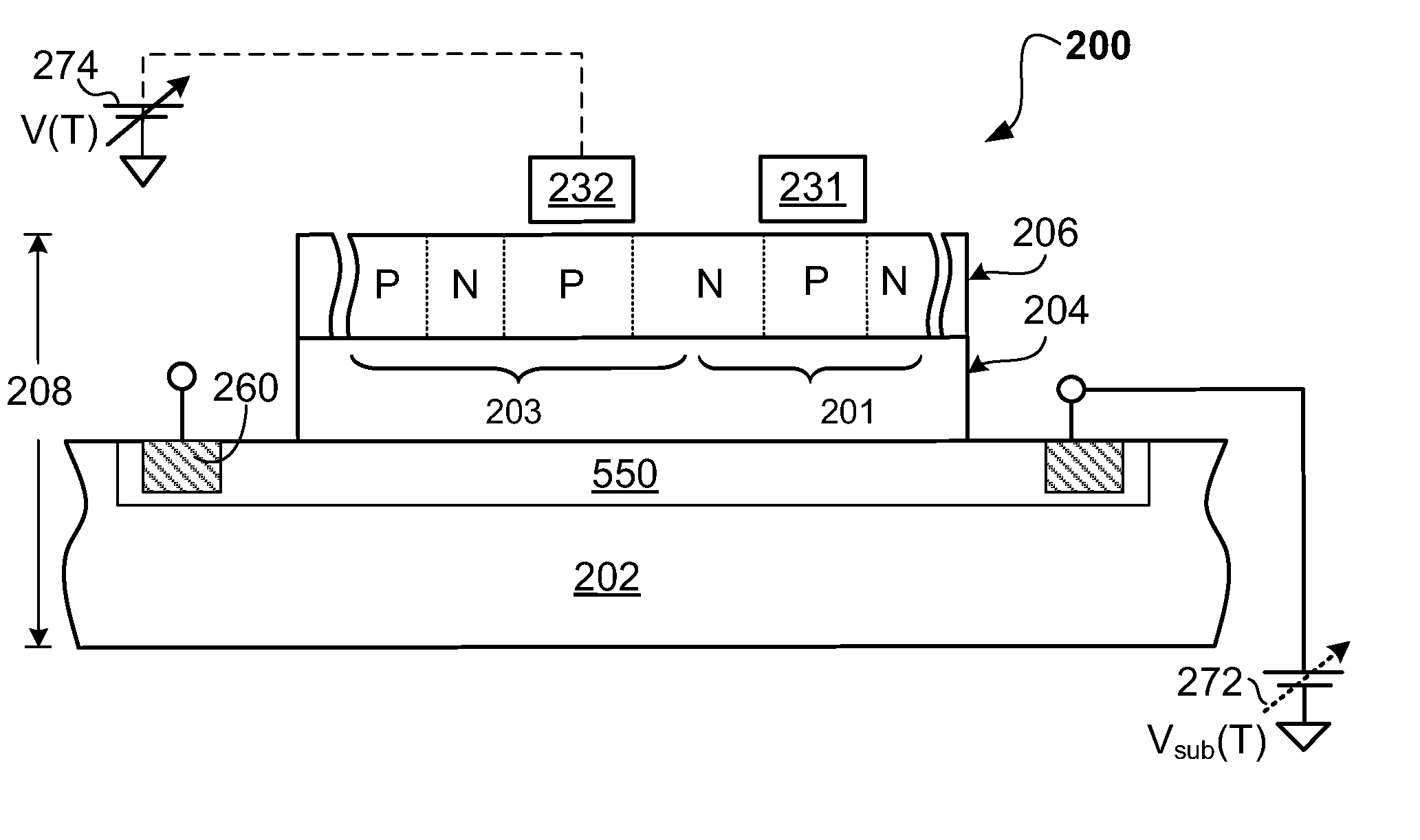
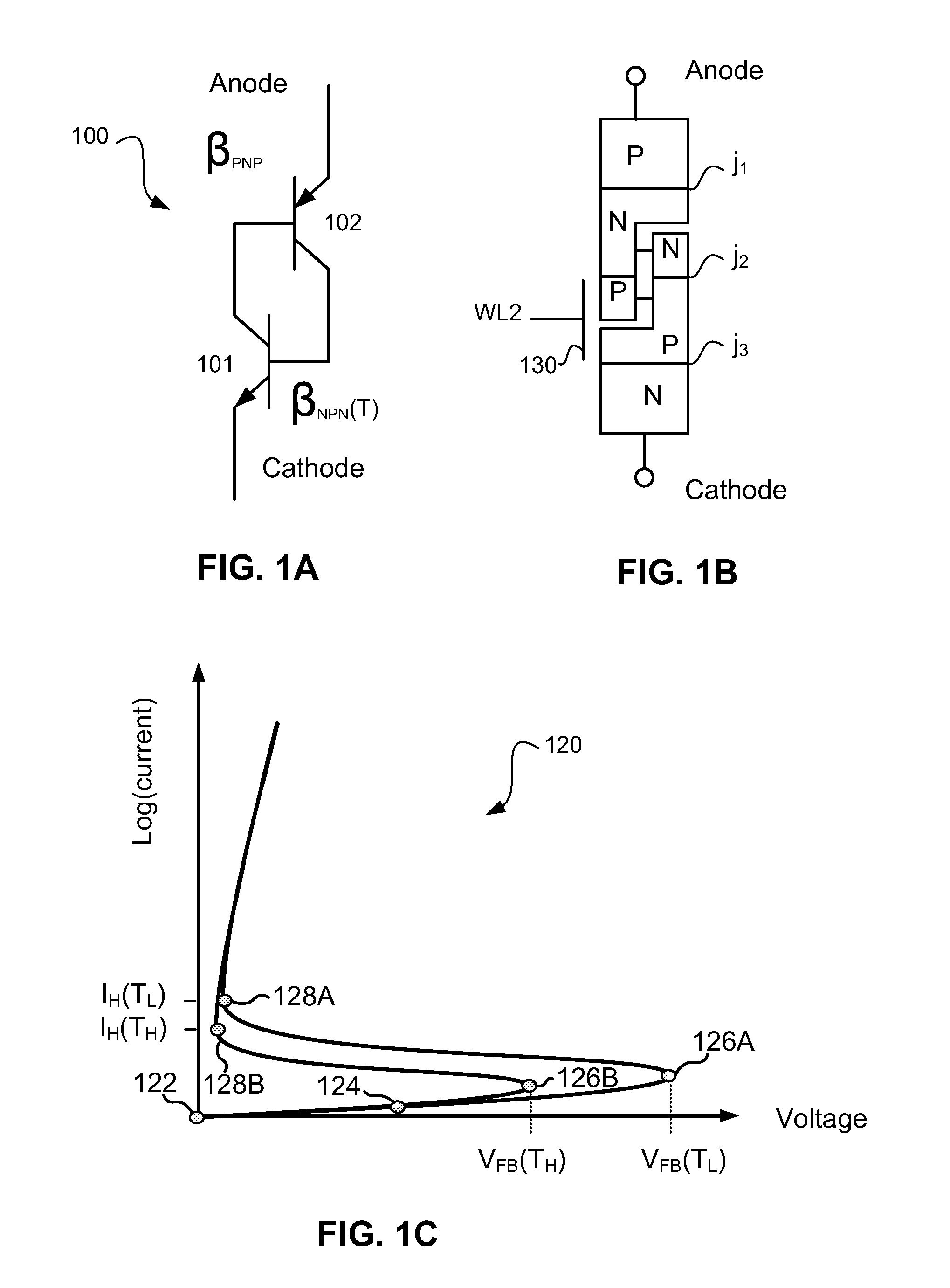
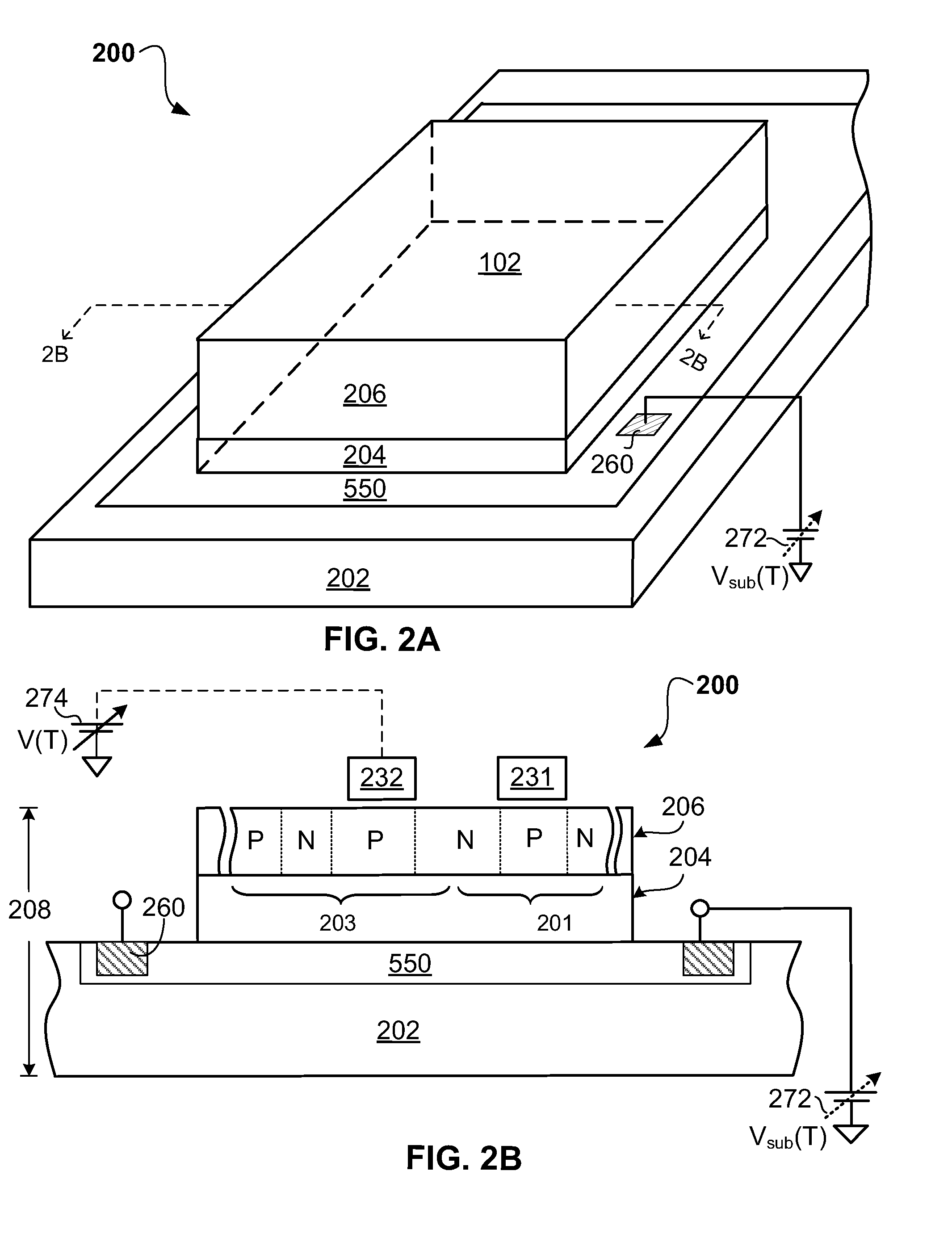
InactiveUS7573077B1High density of impurityAvoid voltage dropThyristorDc-dc conversionThyratronEngineering
In accordance with an embodiment of the present invention, a thyristor-based semiconductor memory device may comprise an array of thyristor-based memory formed in an SOI wafer. A supporting substrate may be formed with a density of dopants sufficient to assist delivery of a bias level to the backside of an insulating layer beneath a thyristor. Such conductivity within the substrate may allow reliable back-gate control for the gain of a component bipolar device of the thyristor.
Owner:T RAM ASSIGNMENT FOR THE BENEFIT OF CREDITORS LLC +1
Beverage containers with multiple compartments and independent openings
Owner:DIXON KAHISHA
Refrigerator appliance with features for assisted dispensing
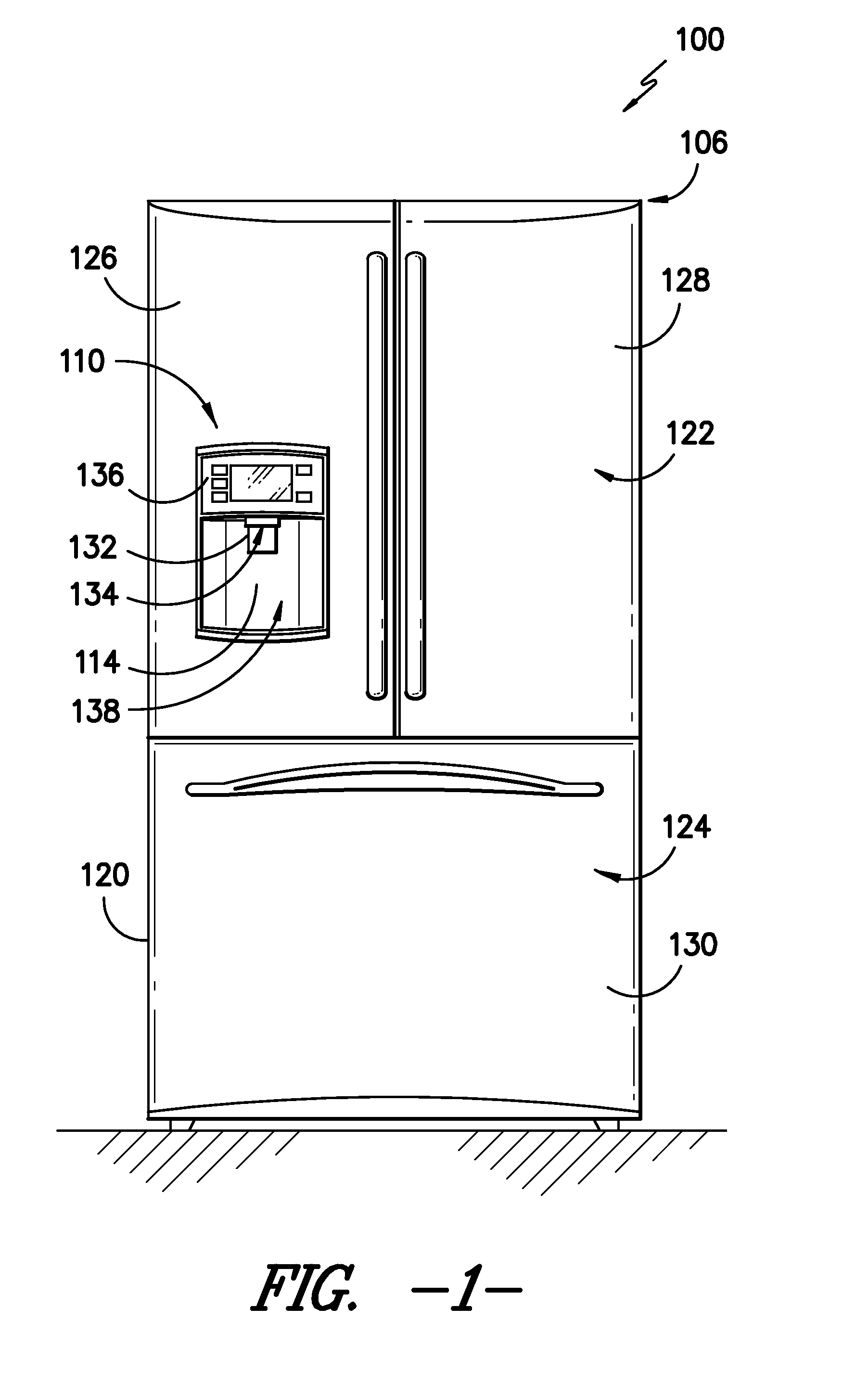
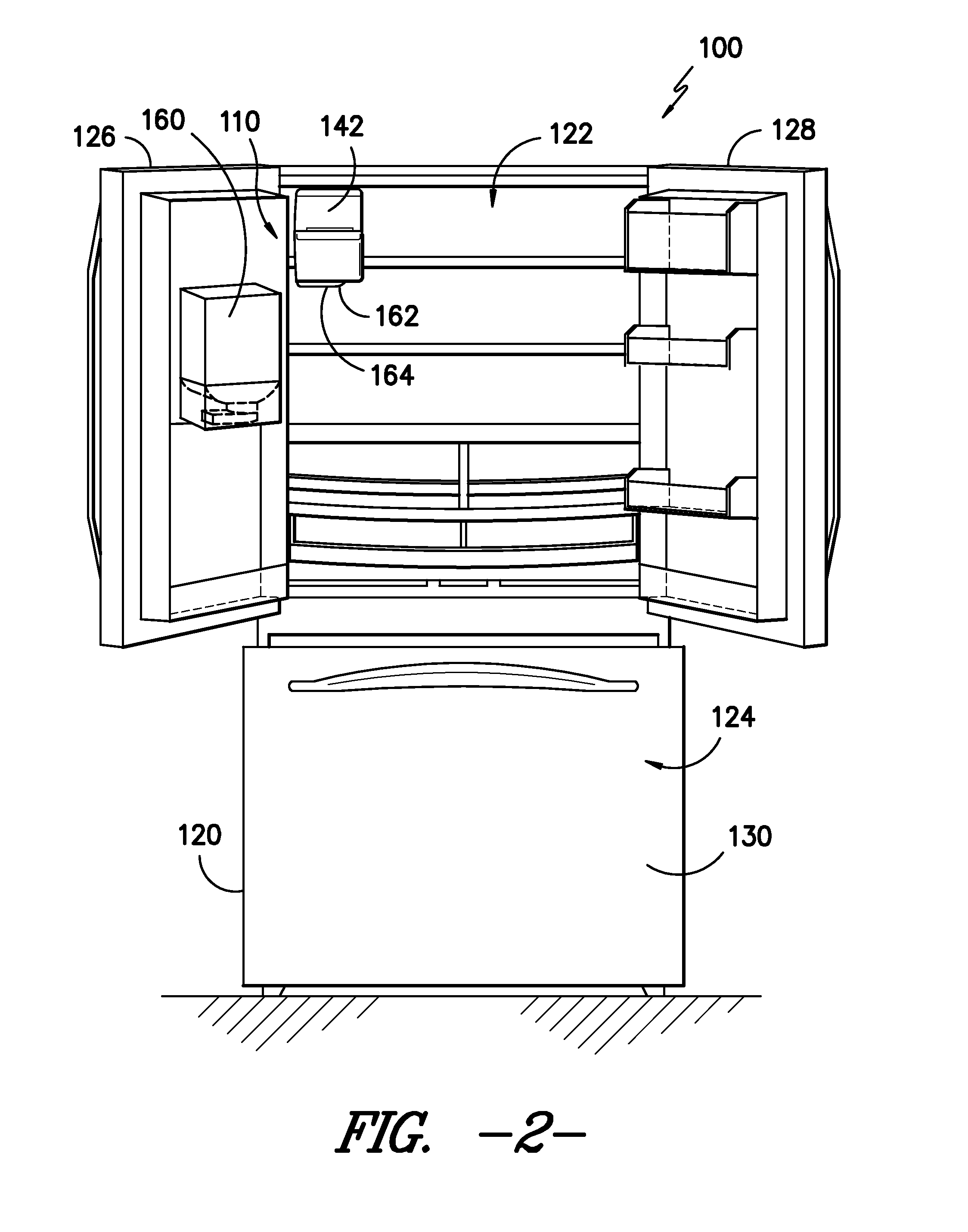
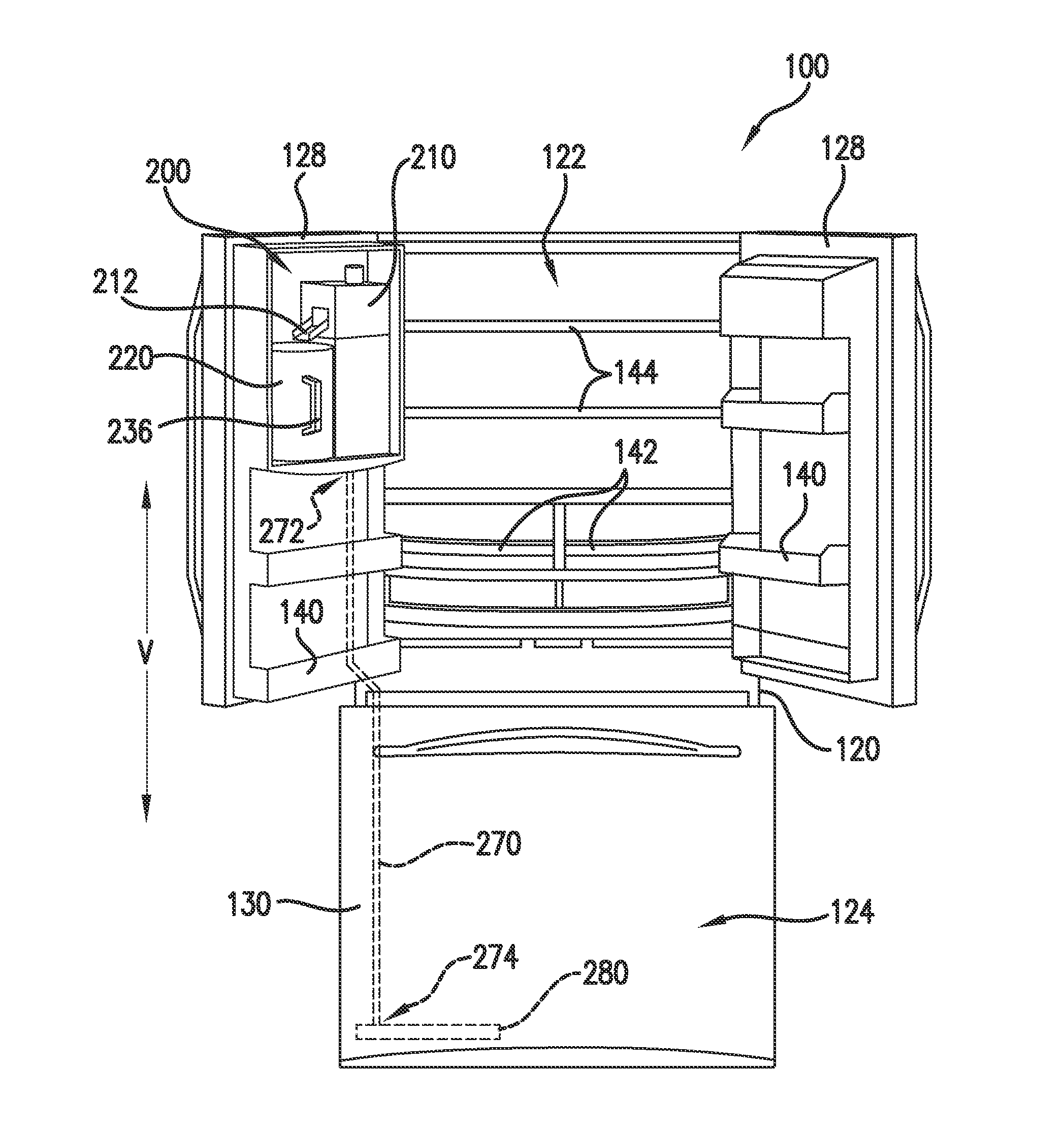
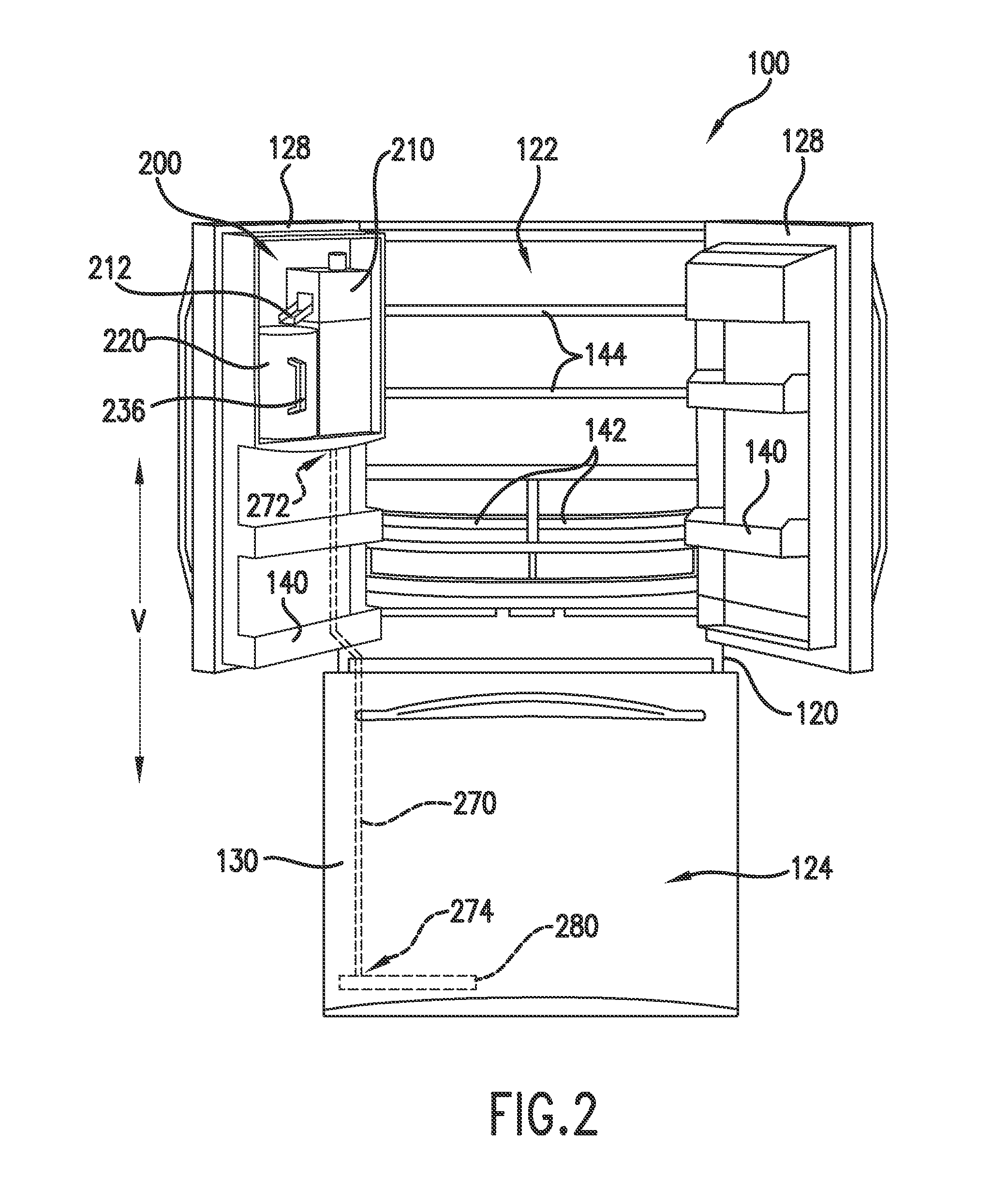
ActiveUS20130312872A1Selectively accessedLiquid fillingDomestic cooling apparatusWater flowDisplay device
Owner:HAIER US APPLIANCE SOLUTIONS INC
Accessible display package and method of use
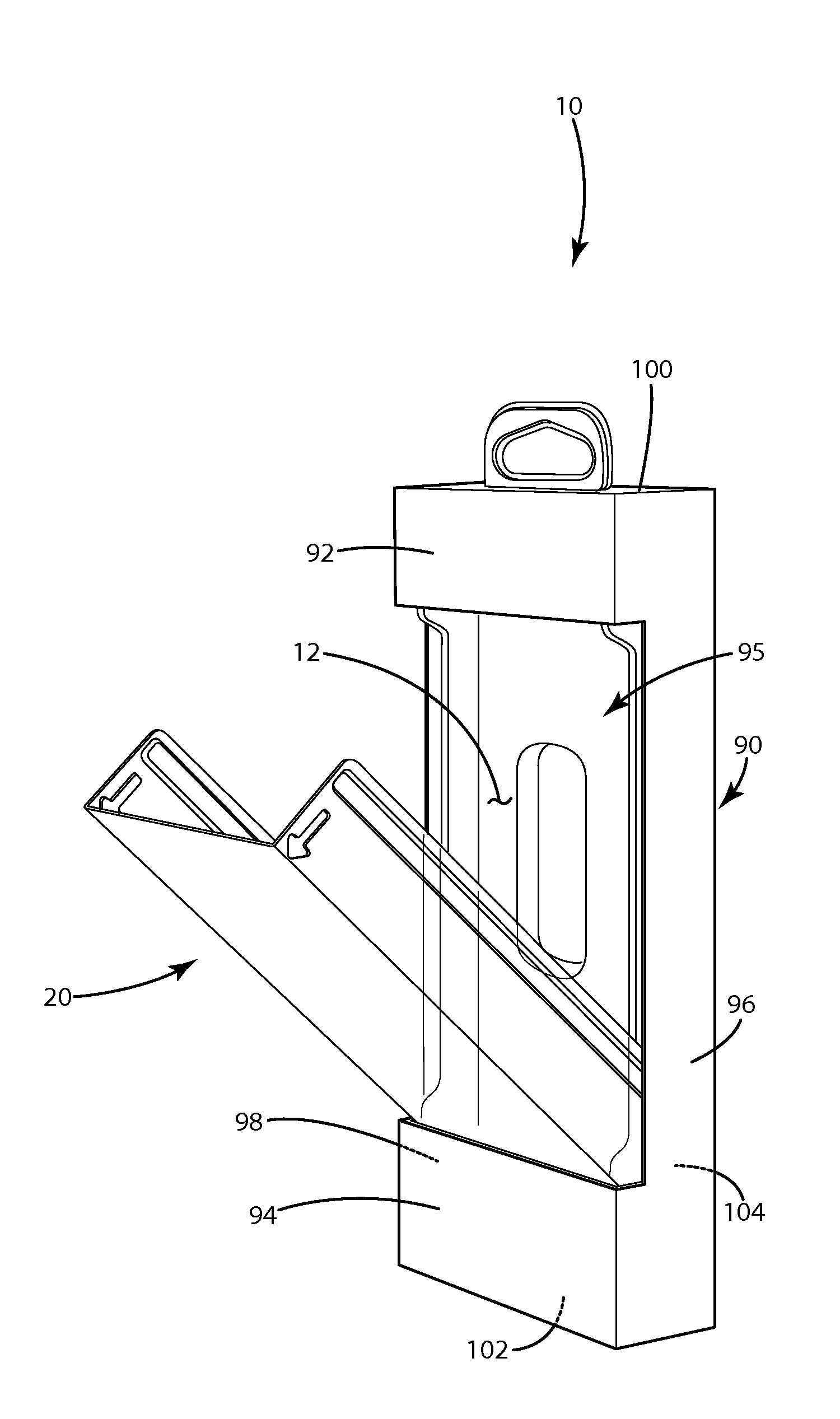
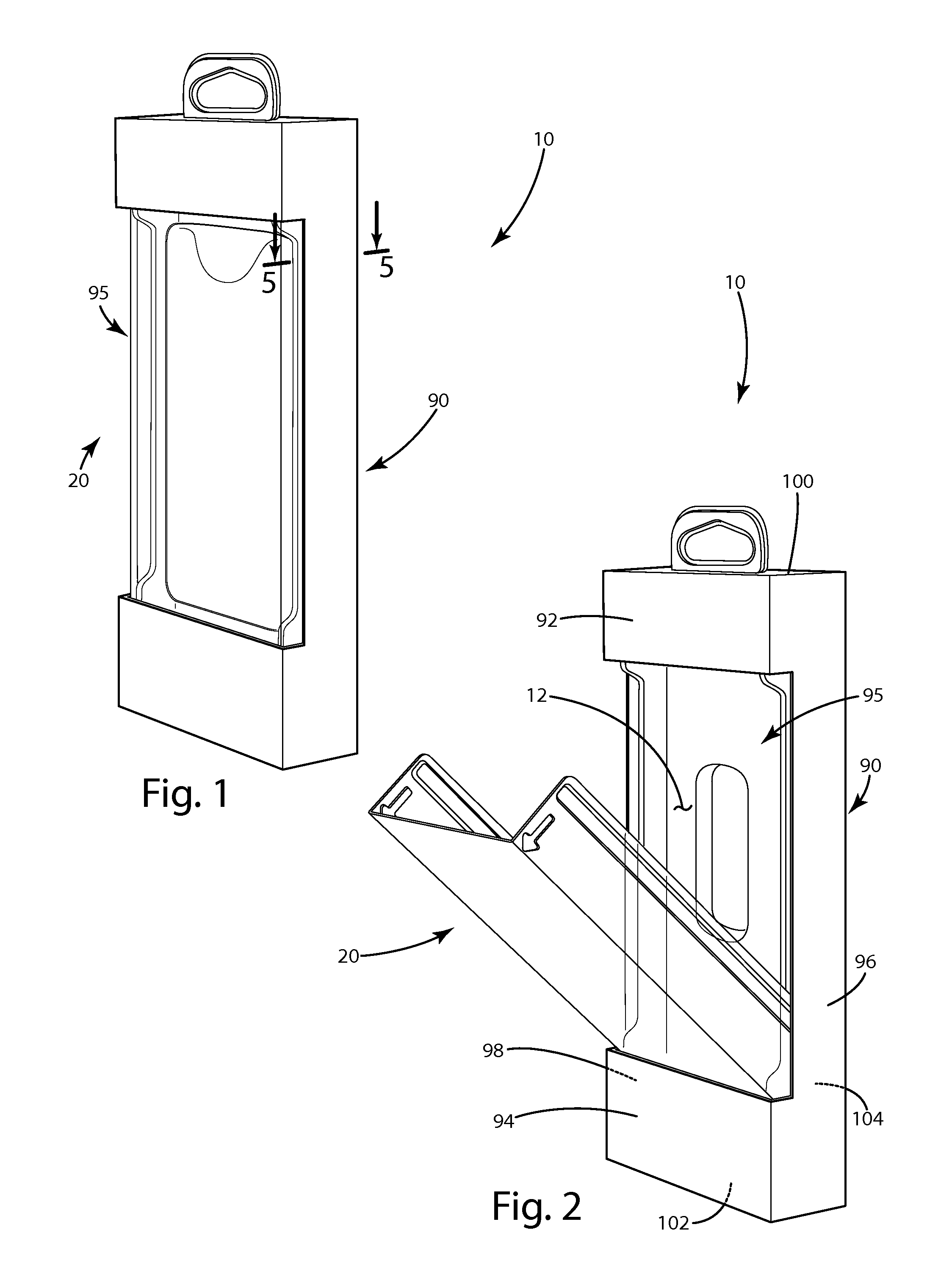
InactiveUS8459460B1Selectively accessedBoxes/cartons making machineryOther accessoriesEngineeringMechanical engineering
The present invention provides a box package having a clamshell with a panel assembly, and a method of manufacturing and using a box package. The clamshell includes a first part and a second part adapted to form a cavity. The first and second parts are movable relative to one another about an operating hinge between an open position and a closed position. A panel assembly covers at least a portion of each of the first and second parts. The clamshell may include more than one manufacturing hinge, and at least one of the manufacturing hinges may divide the first and second parts. The panel assembly may define an access window and at least a portion of the first part may open and close through the access window.
Owner:DISPLAY PACK
Asset security system and associated methods for selectively granting access
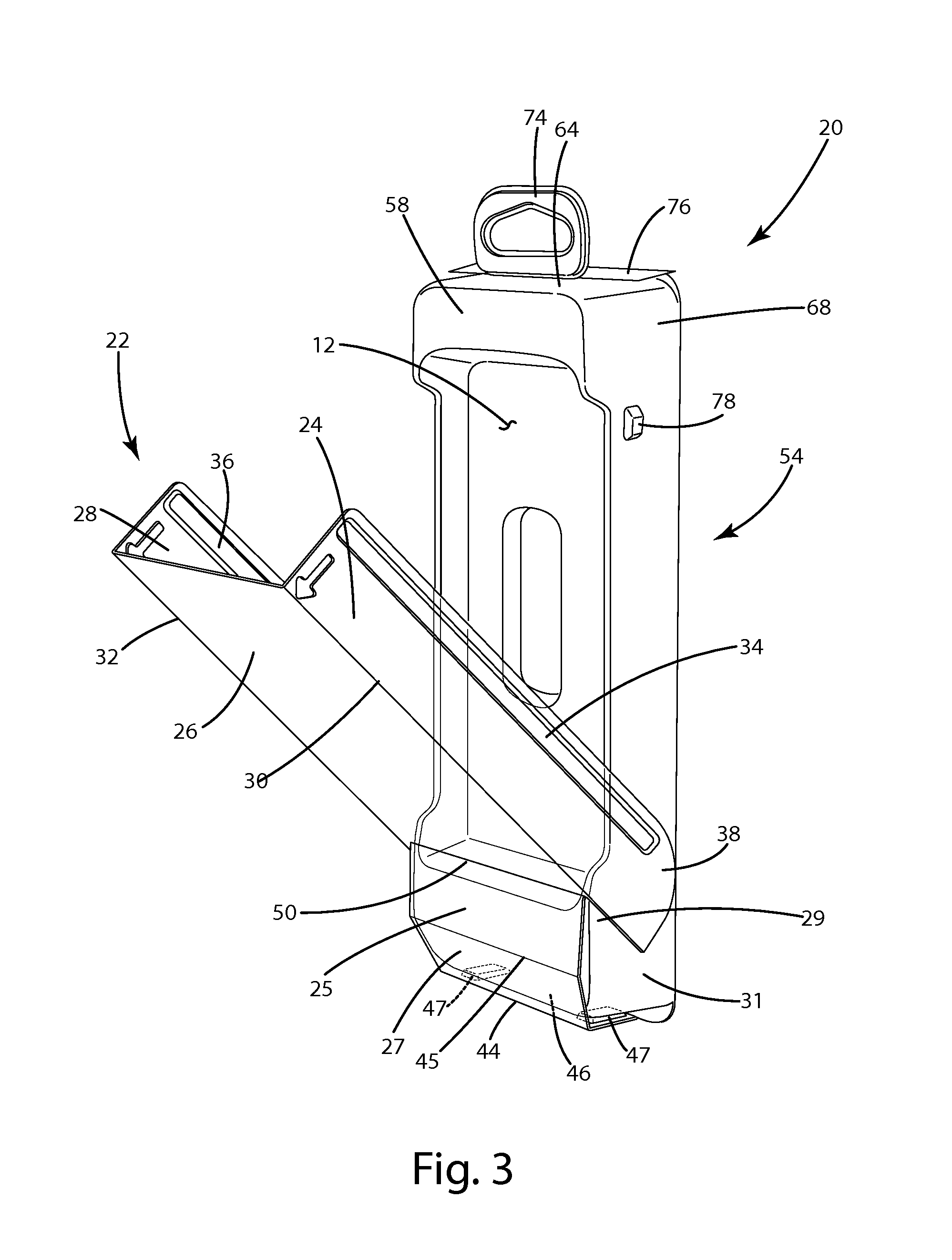
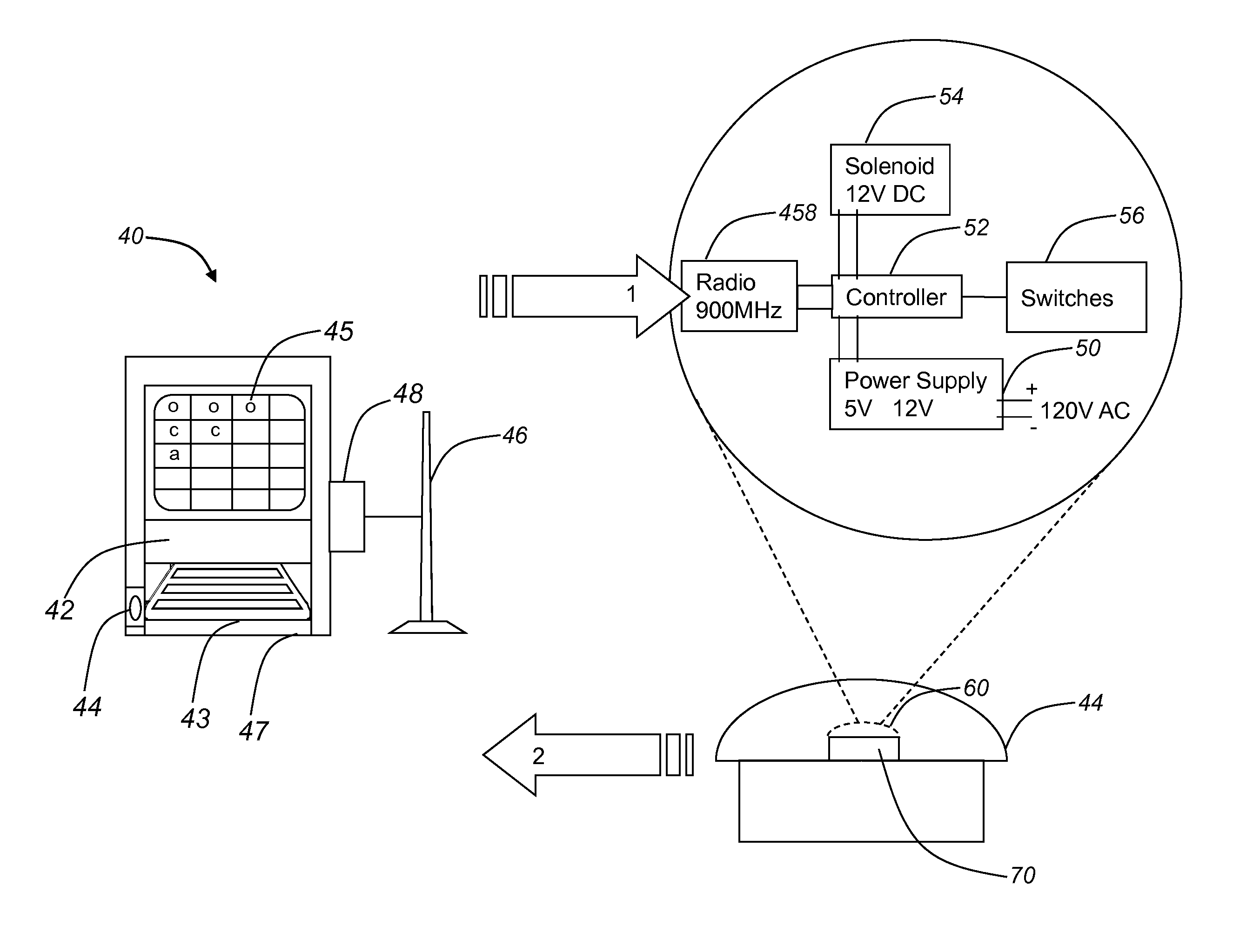
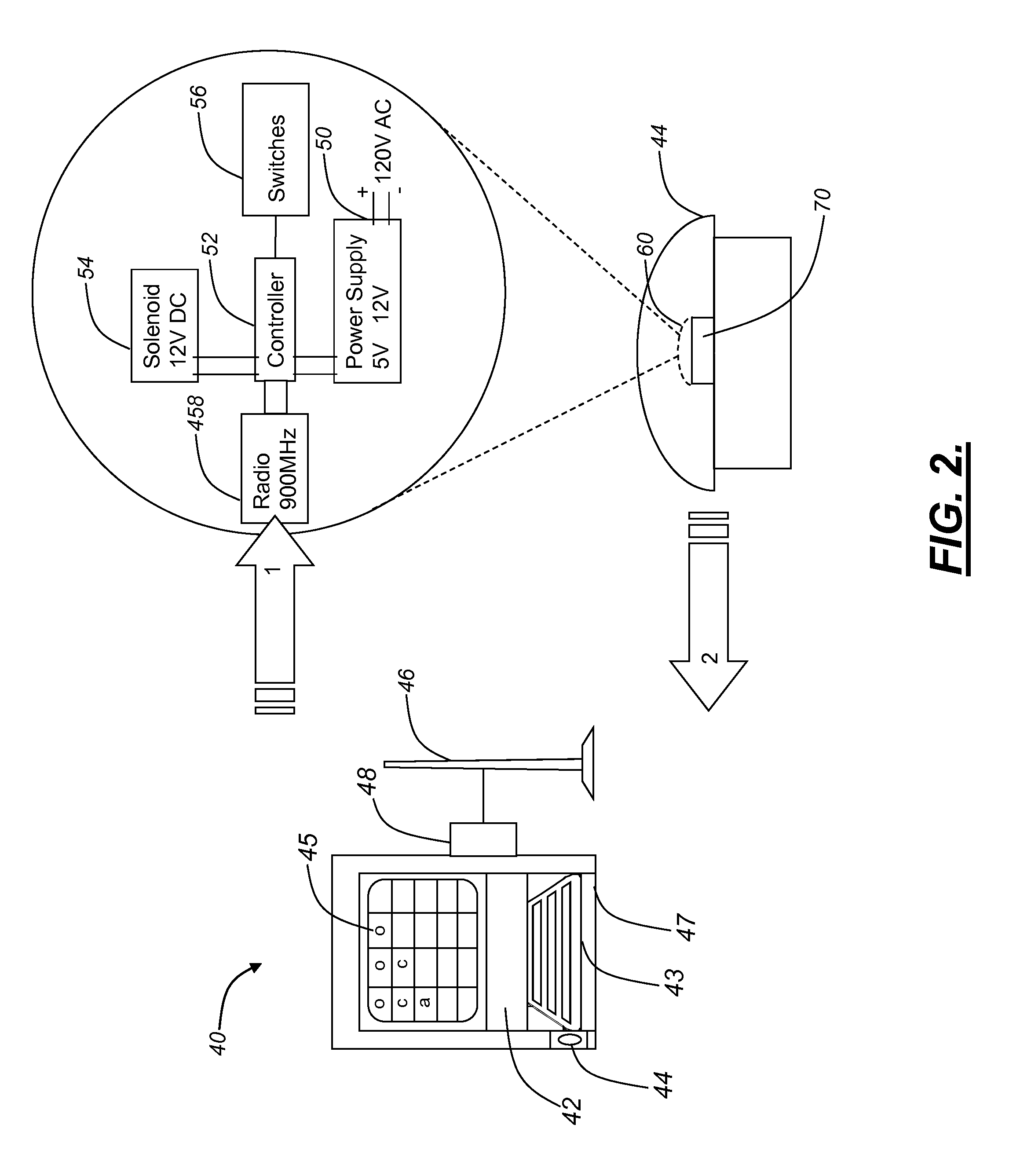
ActiveUS20100176916A1Avoid accessSelectively accessedElectric signal transmission systemsDigital data processing detailsComputer hardwareBiometric data
An automated asset management and security system for providing selective authorized access to an asset disposed within or associated with a remotely located lockable device, including: a control console, including: a processor executing one or more algorithms operable for identifying a user, authorizing a predetermined level of access based upon the identity of the user, receiving a command from the user to provide access to the asset disposed within or associated with the remotely located lockable device, and generating a corresponding command for the lockable device; and a communications channel for delivering the corresponding command to the lockable device; wherein the lockable device includes: a controller having a unique address executing one or more algorithms for implementing the corresponding command and implementing the translated command; and an actuation mechanism operable for selectively providing access to the asset disposed within or associated with the remotely located lockable device responsive to the corresponding command. The processor further executes one or more algorithms operable for identifying the user based on acquired biometric data. The processor further executes one or more algorithms operable for recording the identity of the user and the time and nature of the received command. Optionally, the communications channel is a wireless communications channel. Preferably, the lockable device further includes one or more switches operable for detecting the status of the lockable device in terms of whether or not the lockable device is in an access granted, access denied, or alert status. The processor further executes one or more algorithms operable for recording the detected status of the lockable device.
Owner:MARCON INT
Loss prevention merchandiser
A merchandise dispensing apparatus for providing theft deterrence includes a housing defining an interior space adapted to hold a plurality of associated products. A vending door is mounted to the housing for selectively allowing access to the interior space. A bar is provided on which the associated products are supported, the bar extending in the interior space of the housing. An advancing assembly is disposed in the housing for urging product supported on the bar in a direction towards the vending door.
Owner:FASTENERS FOR RETAIL
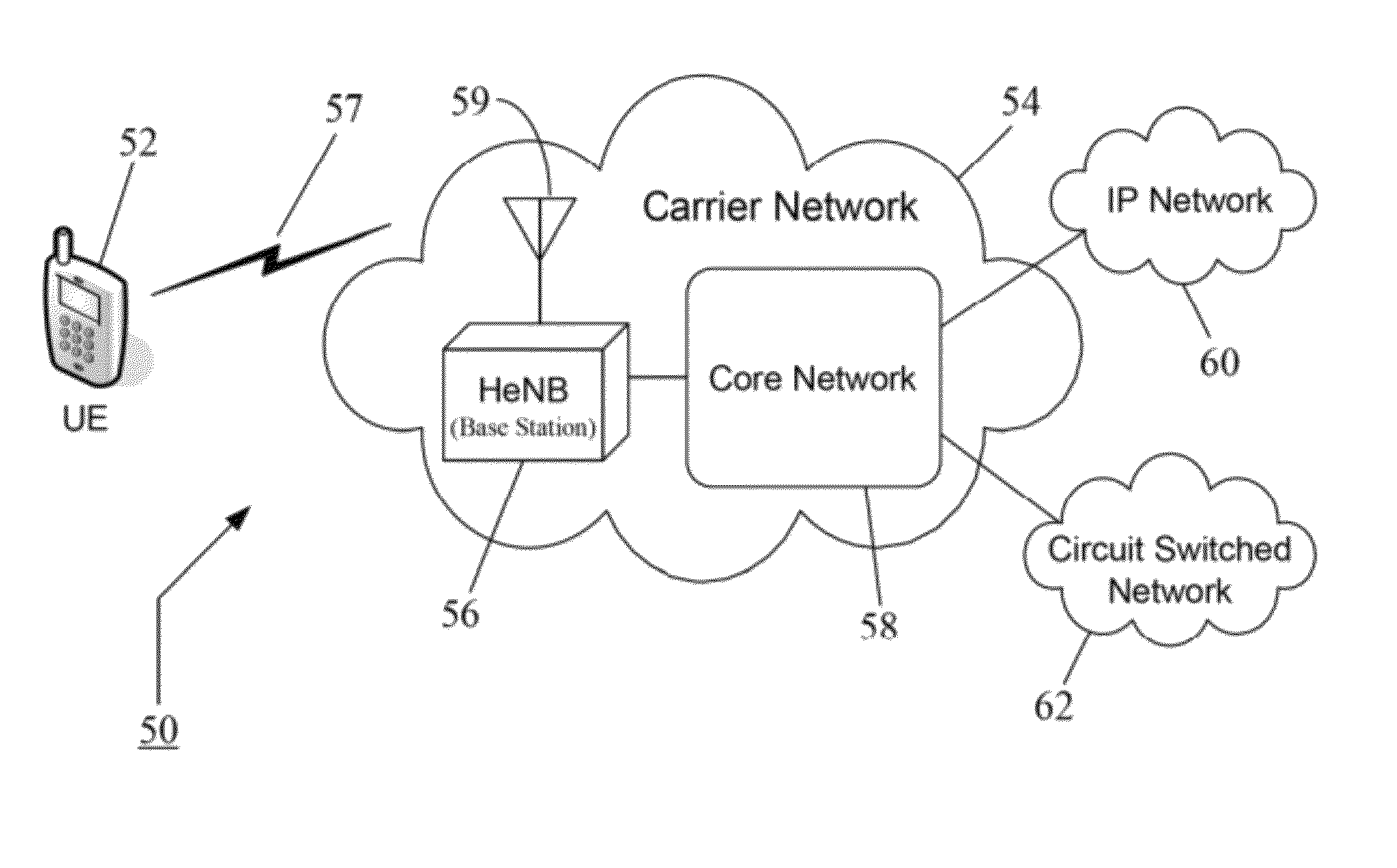
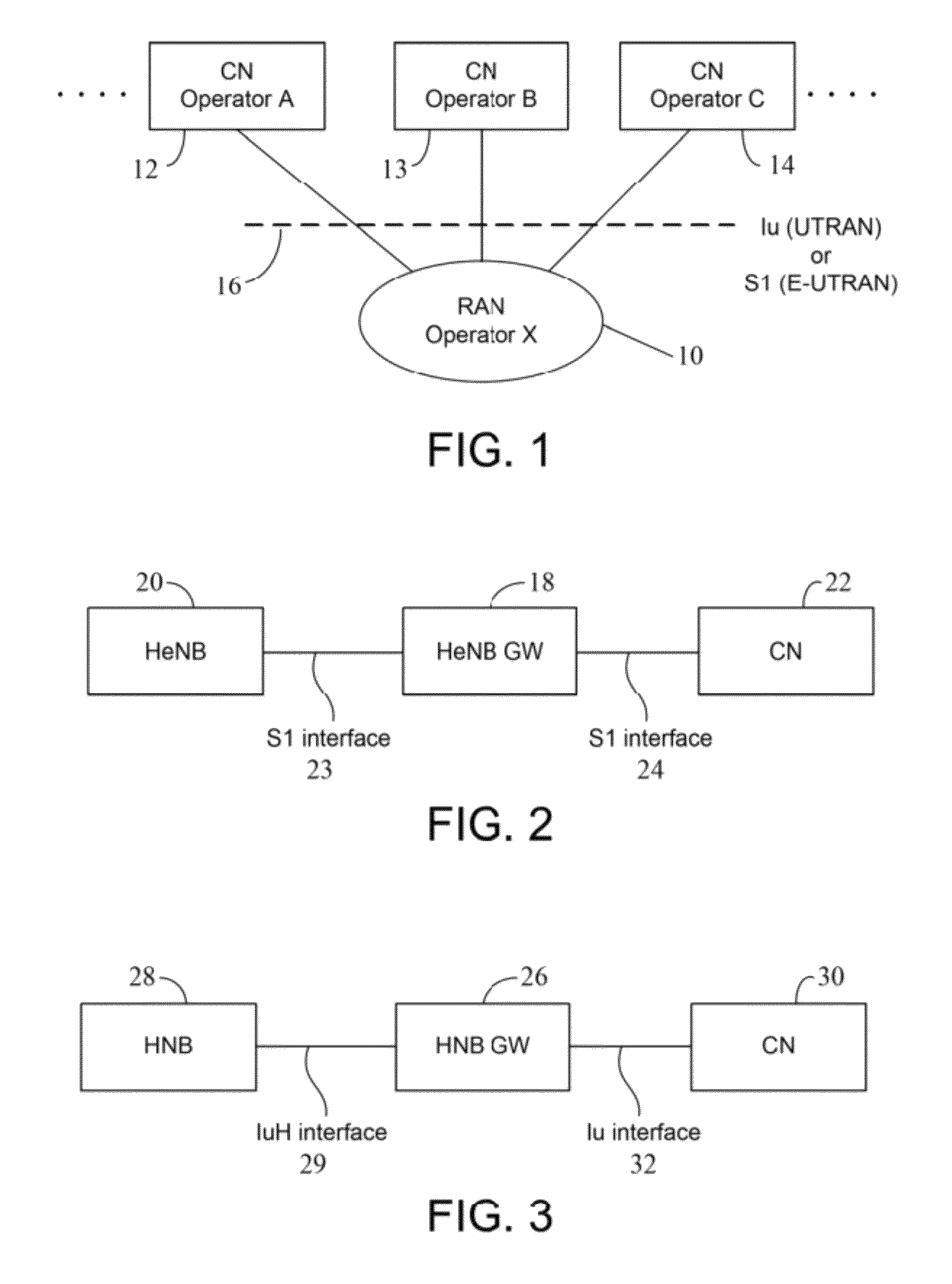
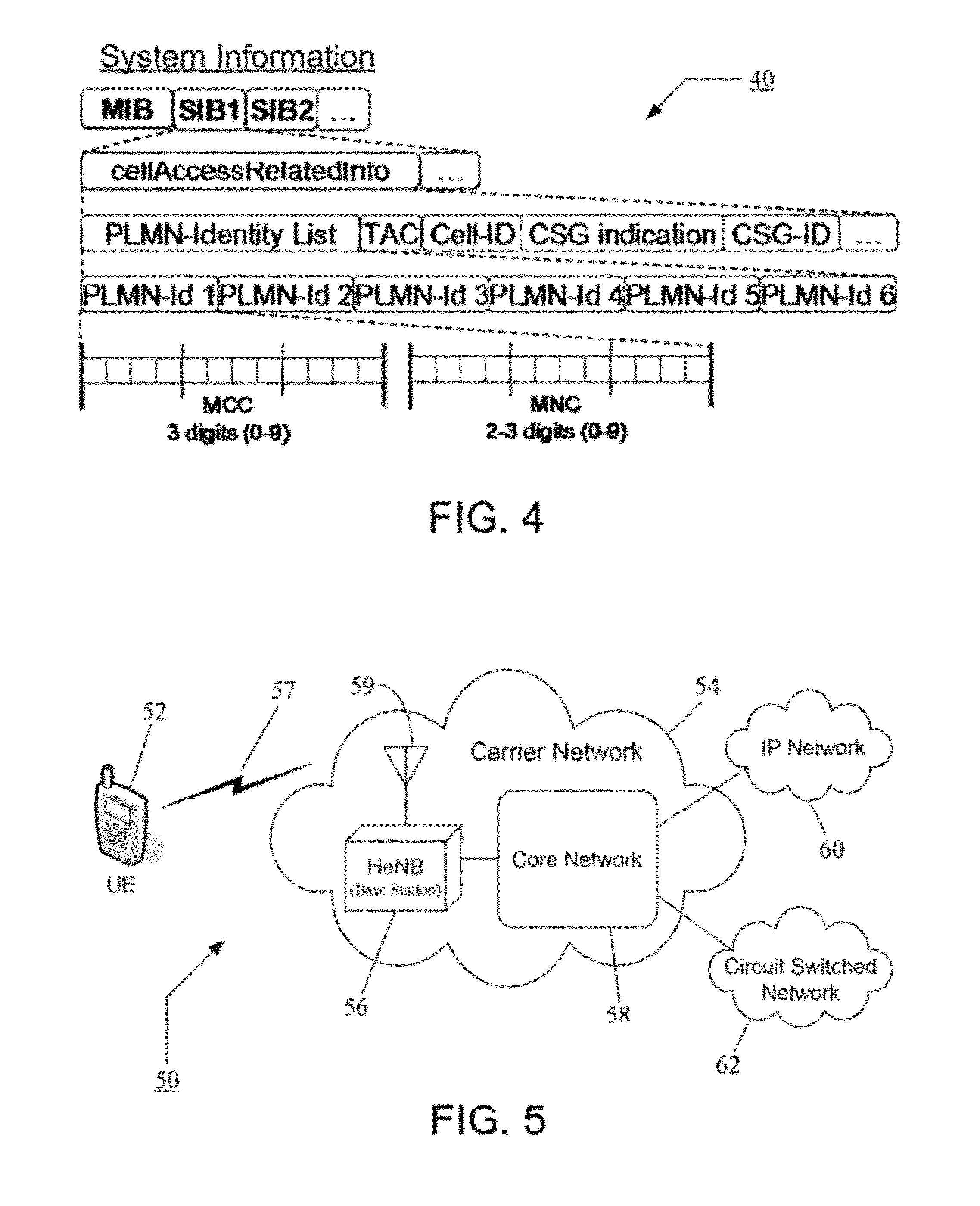
Closed subscriber group (CSG) handling for supporting network sharing of home base stations
InactiveUS9392420B2Good cellular coverageGood peak rateBroadcast service distributionWireless commuication servicesPublic land mobile networkRadio access network
A system and method for enhanced support for handling of Closed Subscriber Groups (CSGs) and sharing of Radio Access Network (RAN) for home base stations and other small cells. An enhanced System Information (SI) structure indicates multiple CSG IDs and CSG Indications, thereby making it possible to support different CSG IDs and CSG Indications for every Public Land Mobile Network Identity (PLMN-ID) and also to support a PLMN-ID with multiple associated CSG IDs and CSG Indications. The enhanced SI makes it possible to have different CSG IDs for different operators, to have multiple CSG IDs for one operator (i.e., a single PLMN), and to selectively use the CSG concept for some PLMNs (as given by their respective CSG Indications), but not for all. A network of base stations (e.g., a RAN) thus can be effectively shared by multiple operators, leading to better cellular coverage, peak rates, and capacity.
Owner:TELEFON AB LM ERICSSON (PUBL)
Loss prevention merchandiser
A merchandise dispensing apparatus for providing theft deterrence includes a housing defining an interior space adapted to hold a plurality of associated products. A vending door is mounted to the housing for selectively allowing access to the interior space. A bar is provided on which the associated products are supported, the bar extending in the interior space of the housing. An advancing assembly is disposed in the housing for urging product supported on the bar in a direction towards the vending door.
Owner:FASTENERS FOR RETAIL
Pillbox
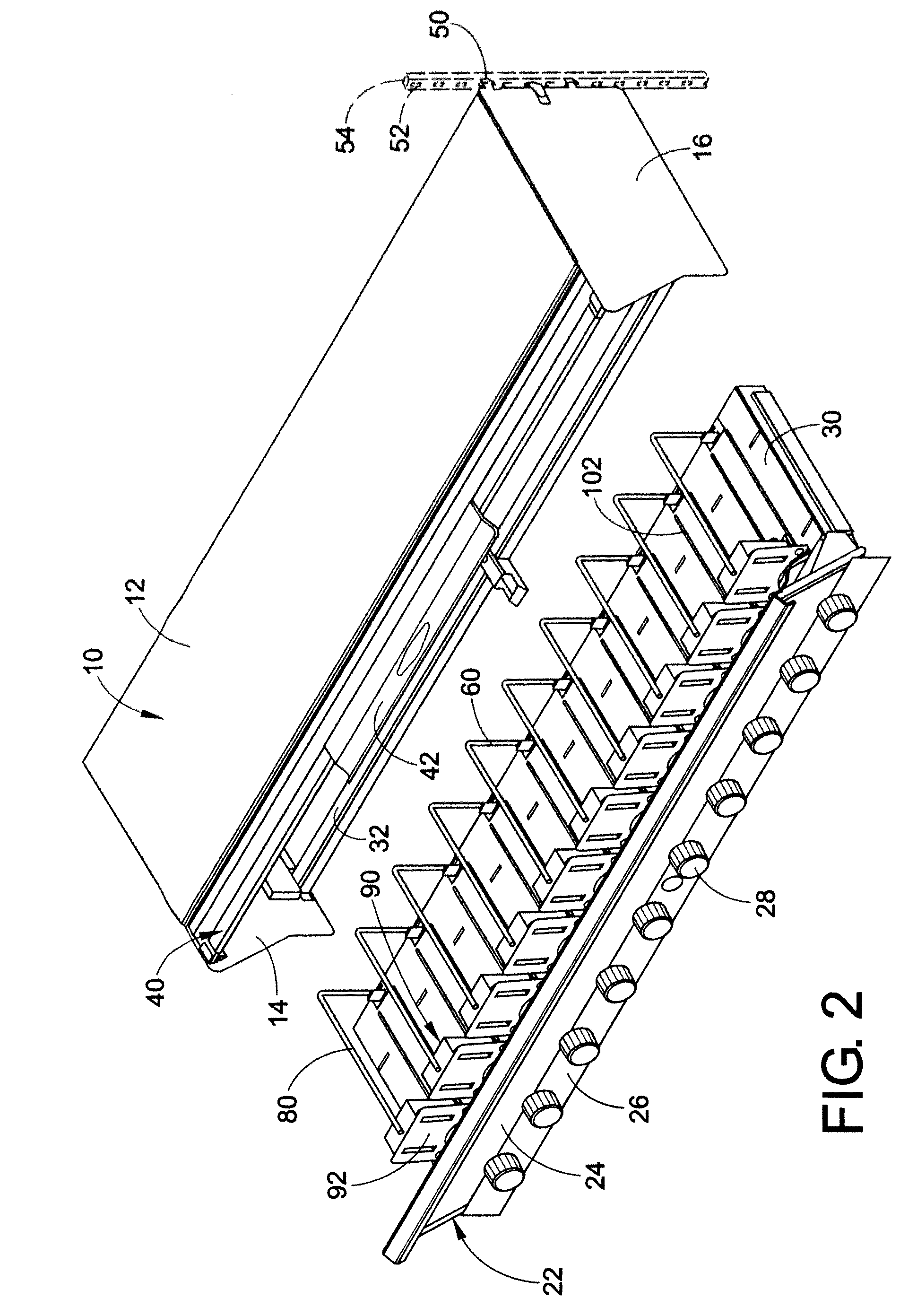
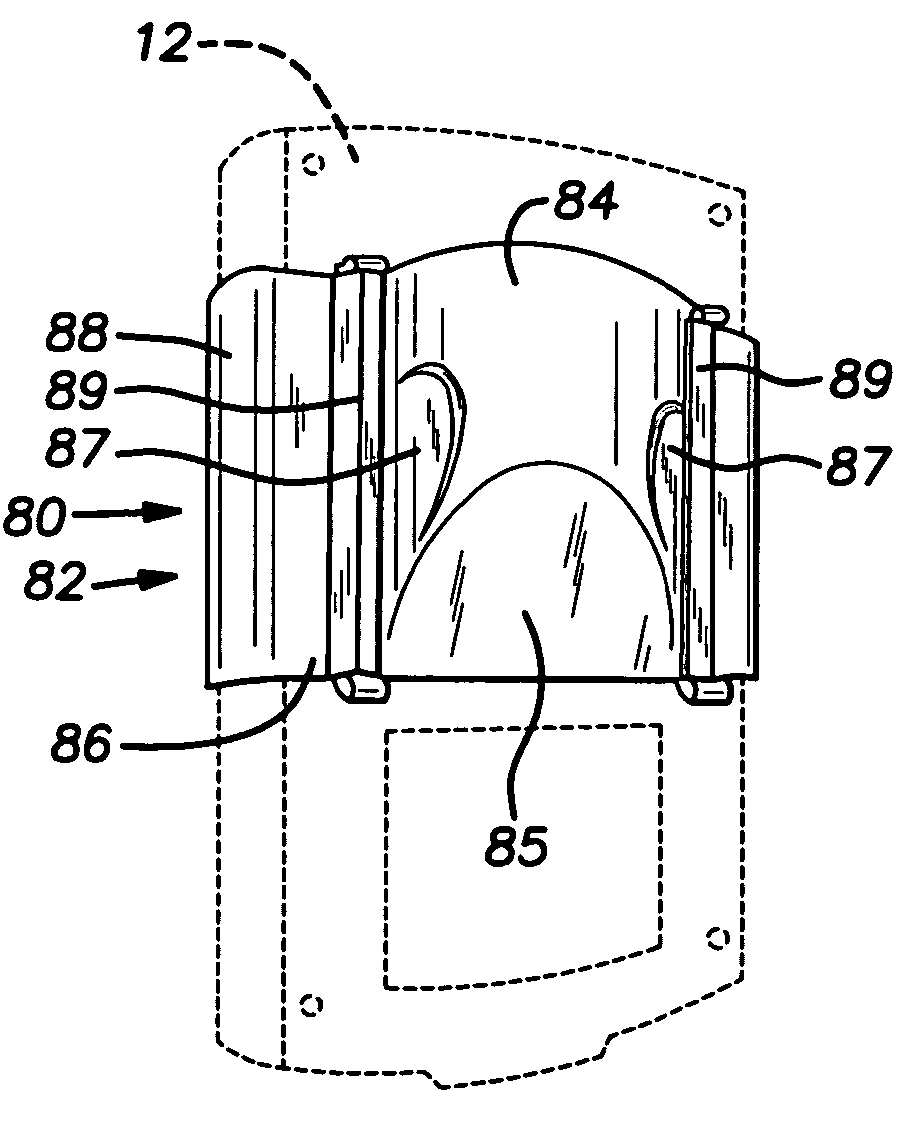
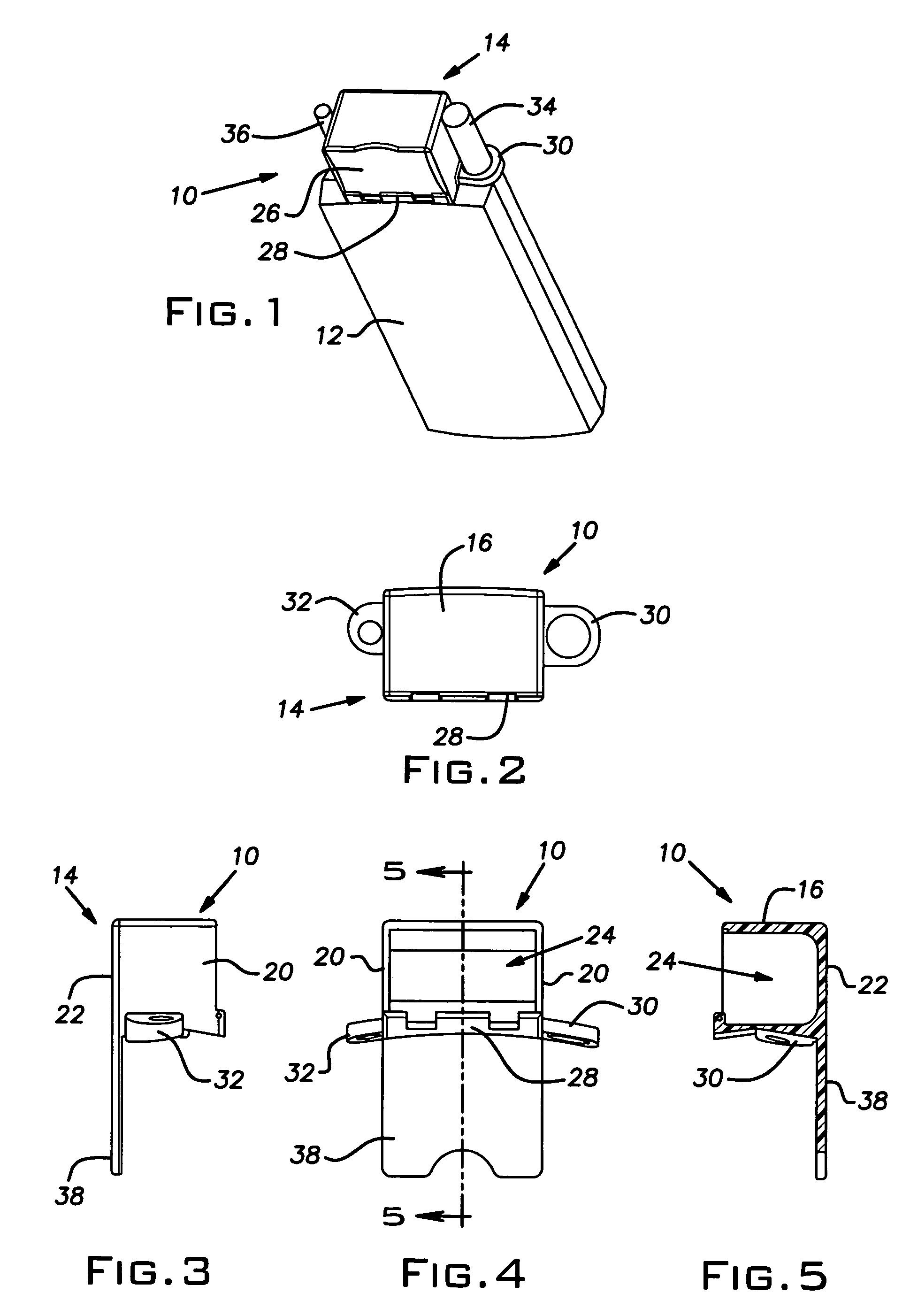
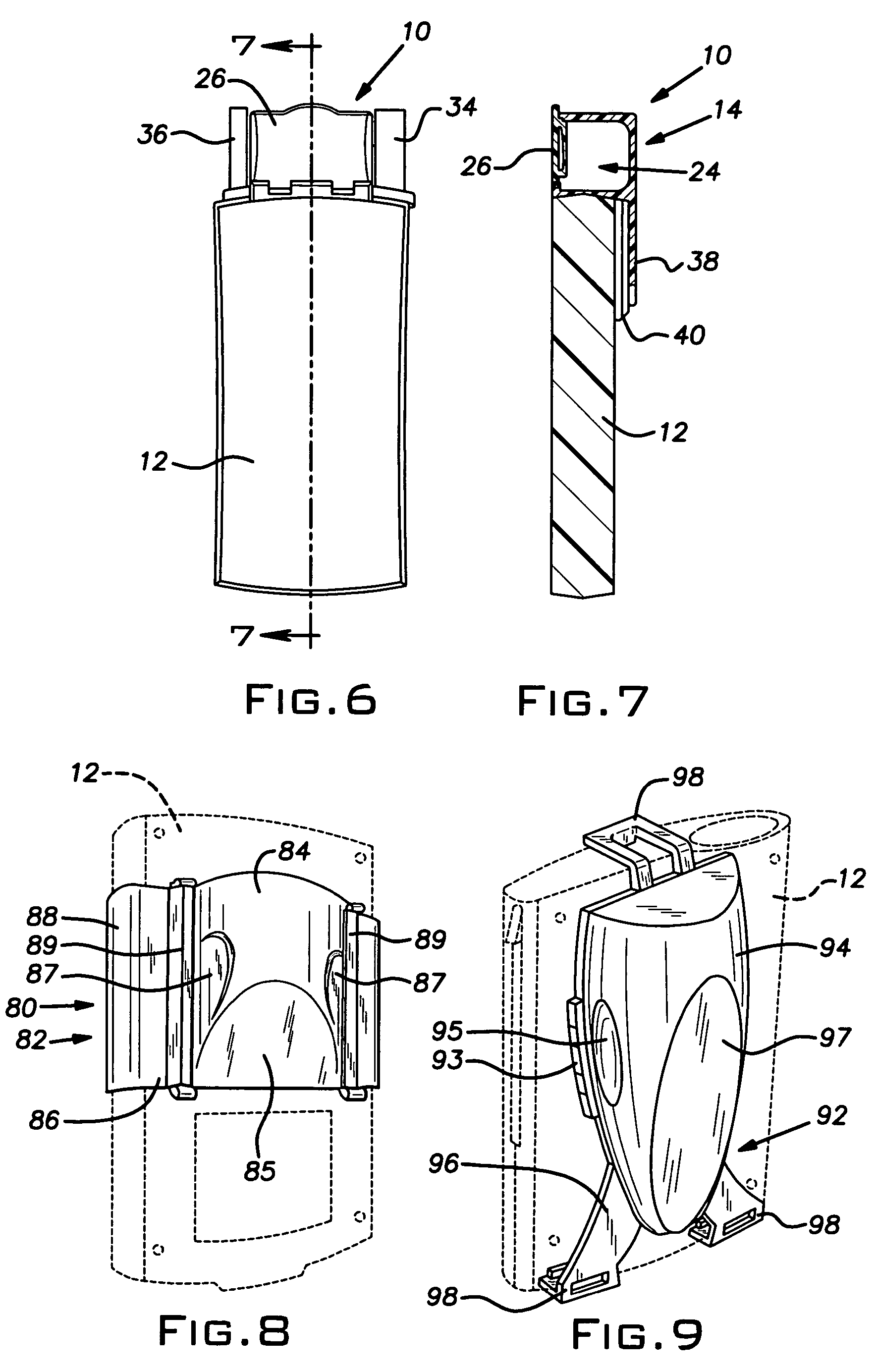
InactiveUS7337899B2Easy to disassembleSelectively accessedSmall article dispensingPursesCellular telephoneBiomedical engineering
A pillbox that can be used with a portable electronic device (“PED”) such as a cellular telephone or personal digital assistant includes a generally cubic body portion that is attached to one end of a PED. The body portion defines a compartment within which medication can be placed. Preferably, an extension projects from one wall of the body portion and the extension is connected to the PED. The body portion preferably conforms generally to the contour of the PED. A door is connected to the body portion to permit selective access to the compartment. Other embodiments of the invention include a holster within which the PED can be inserted. In some of the embodiments, the door defines the medication-storage compartment.
Owner:CREATIVE ACTION
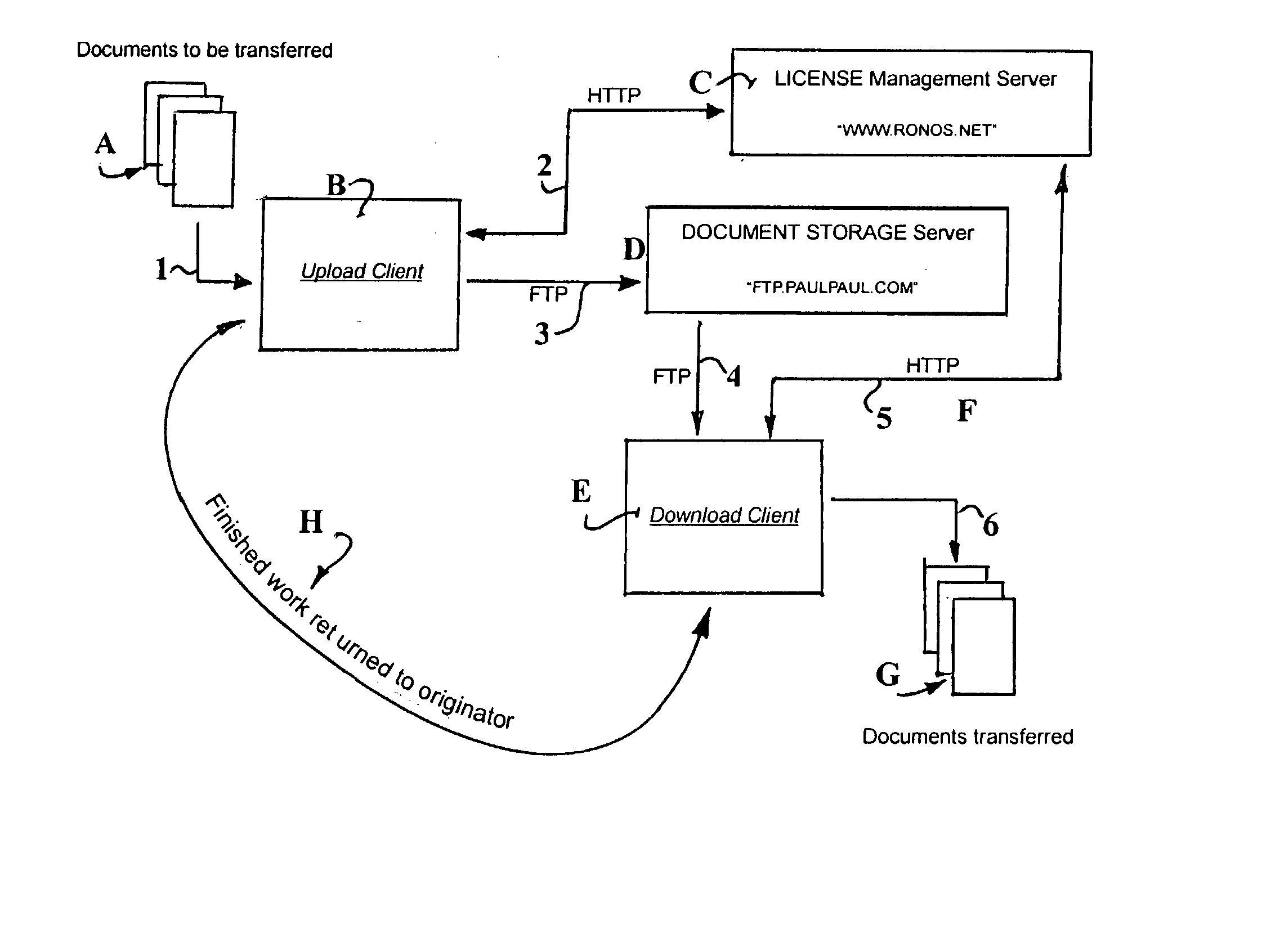
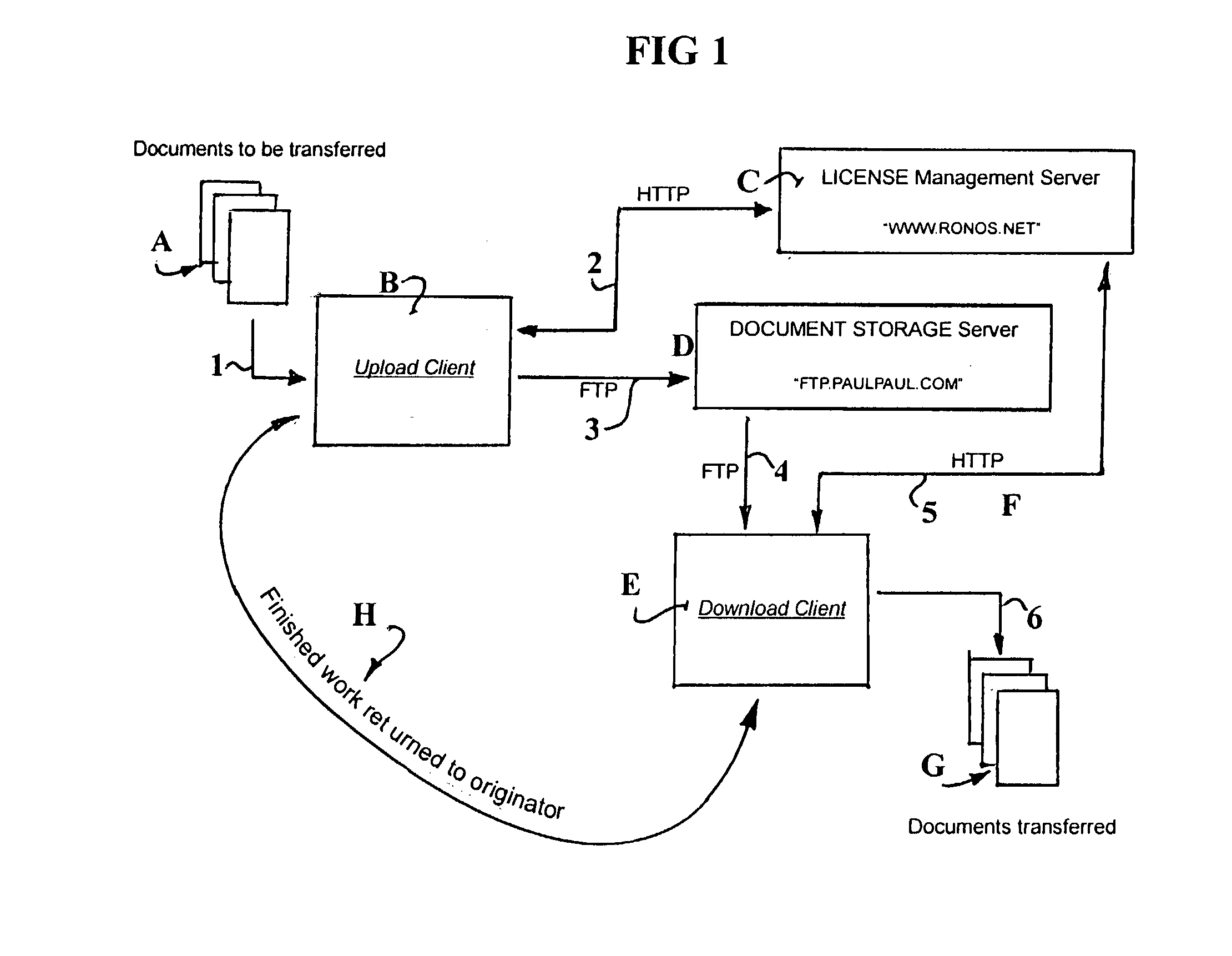
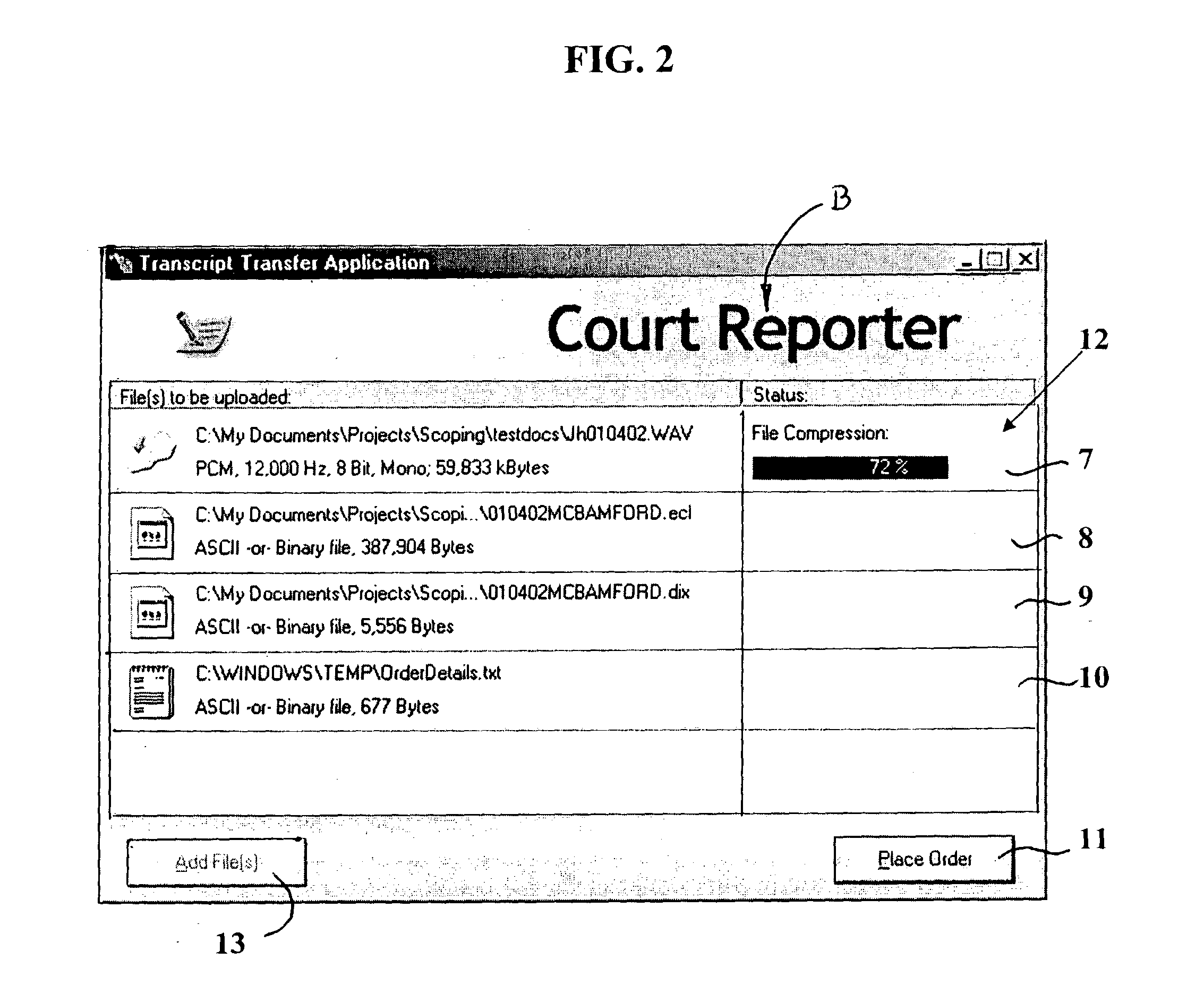
Data conversion secure transfer method and software system for court reporters and scopists
InactiveUS20030163429A1Fast secure transferEasy to useMultimedia data retrievalComputer security arrangementsData transformationSoftware system
A single application program and system process whereby digital media or sound files, typically those derived from a court hearing, are converted, compressed, encrypted, and sent electronically to an FTP site by a court reporter. The converted files are then retrieved electronically via FTP from said site by a scopist whereby the files are decompressed, decrypted, and displayed on the scopist's computer. Such functions are conducted in a secure manner so as to produce secure data file format which allows users to effectively transfer the files across the Internet. The inventive application program provides executable code providing computer instructions and operation functionality of providing for files to be stored on an FTP Internet site, and includes means for verification of user's serial numbers for authentication of valid users, and prevention of unauthorized access to the secure data. Converted and completed files from the scopist are either uploaded to a final destination via electronic email or replacing them on an FTP Internet site as designated by the inventive method.
Owner:PJH SCOPISTS
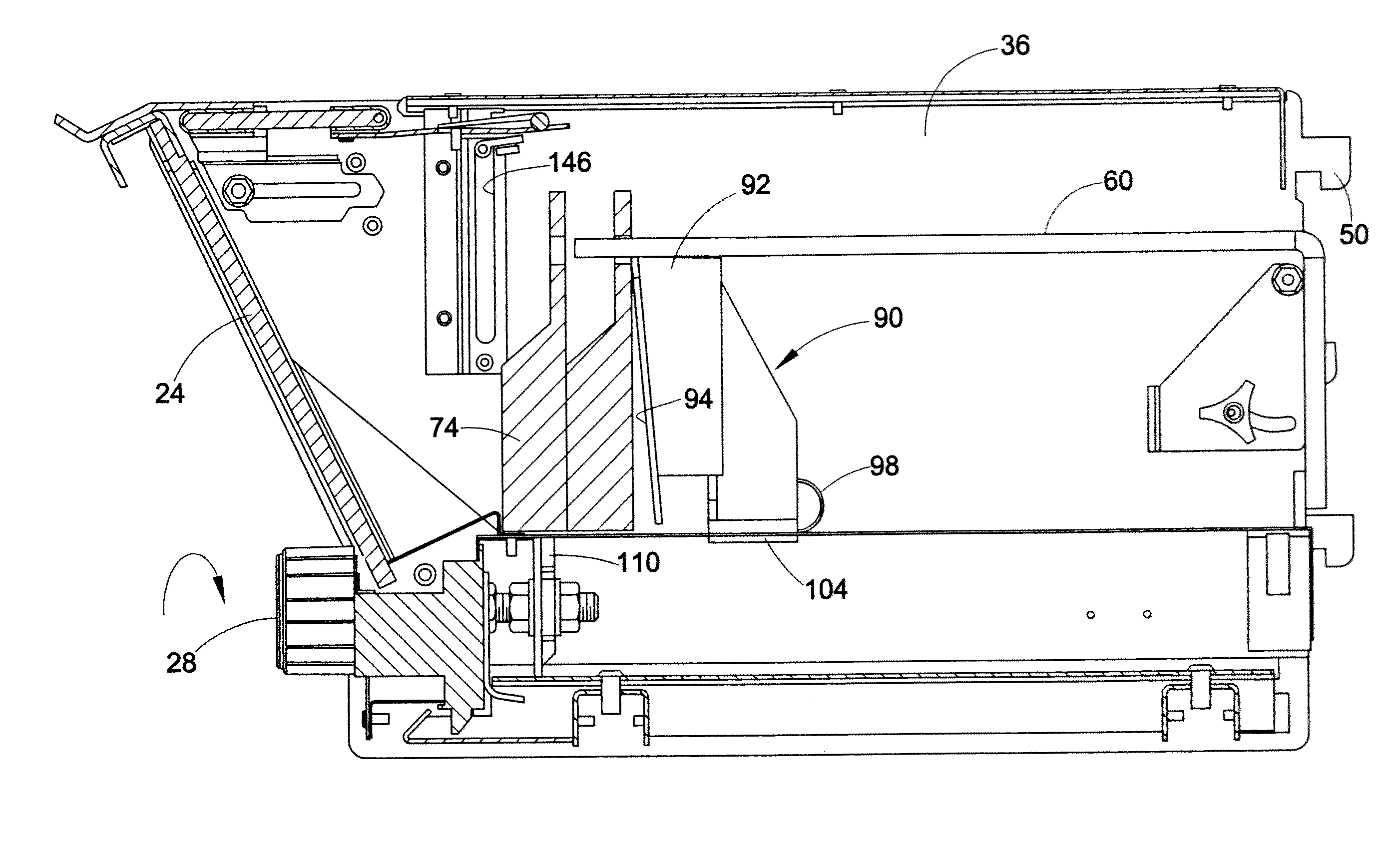
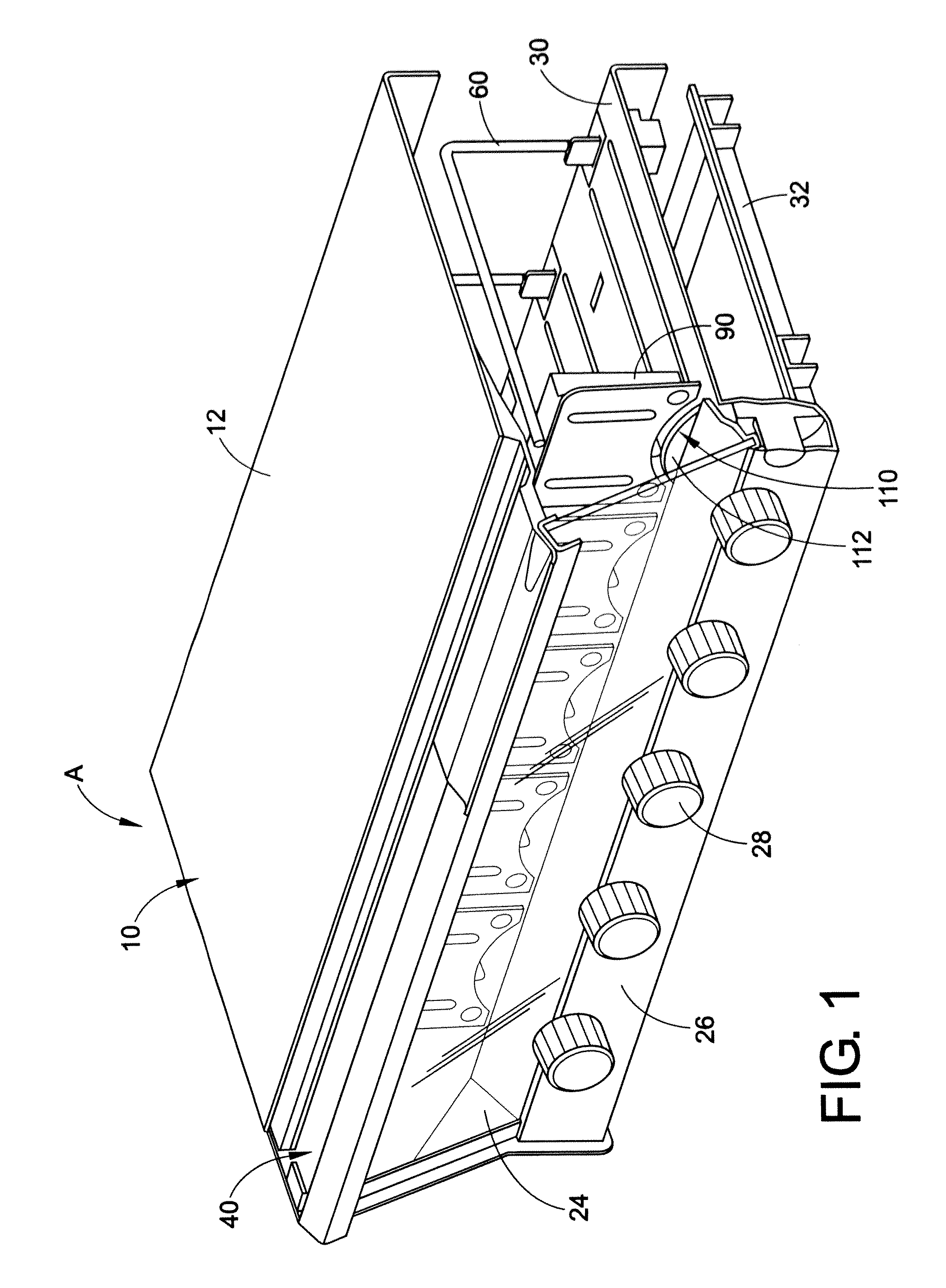
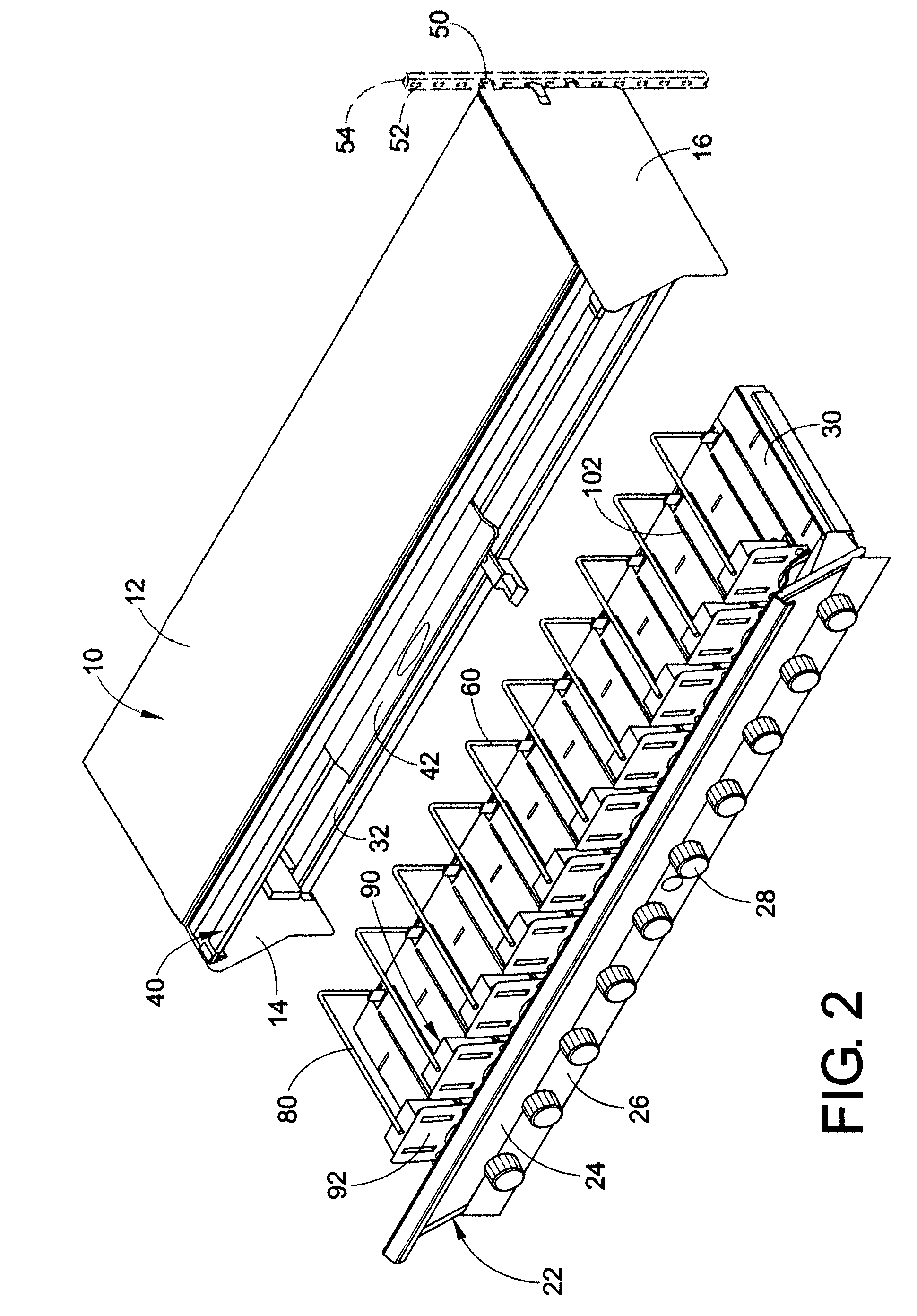
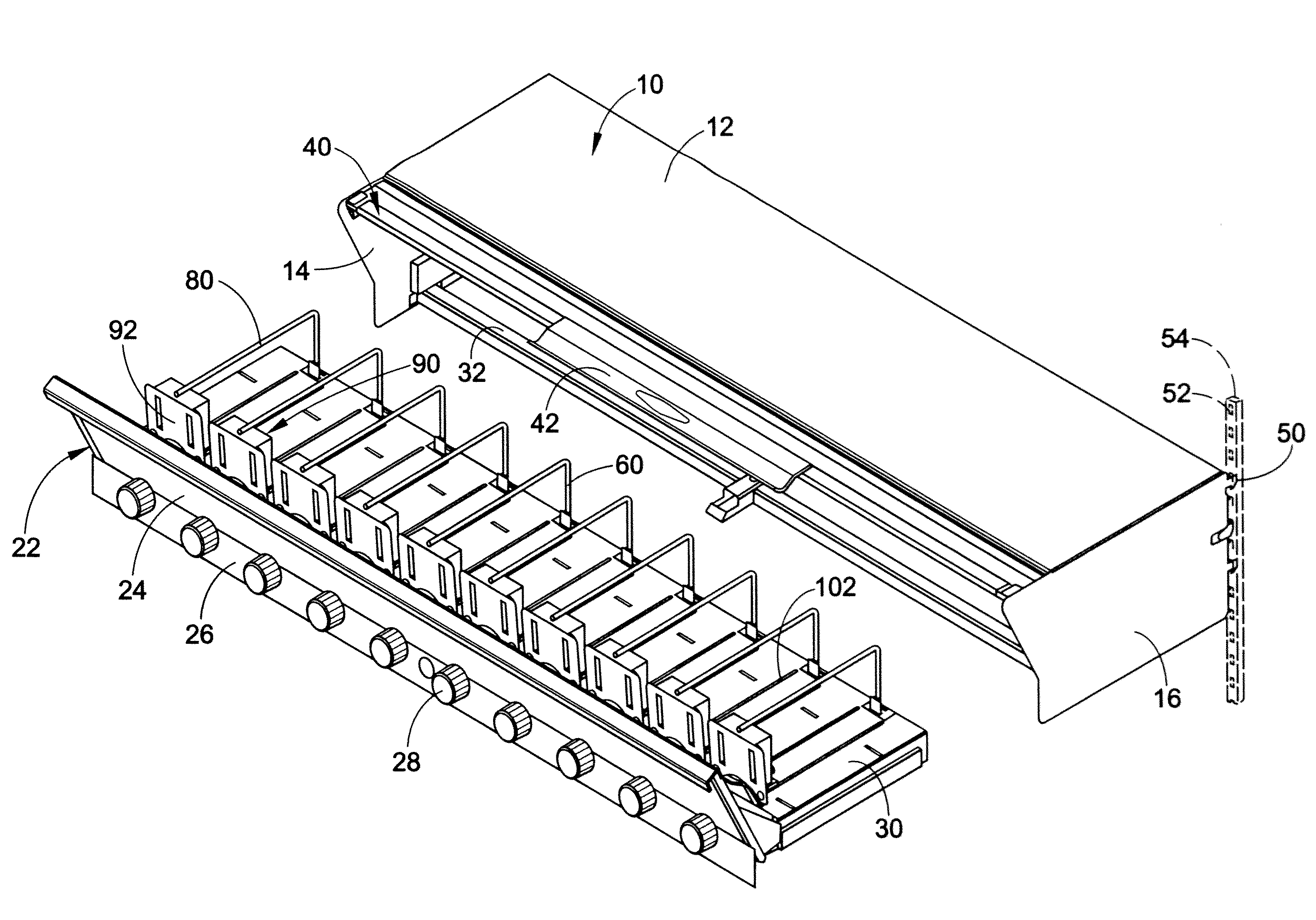
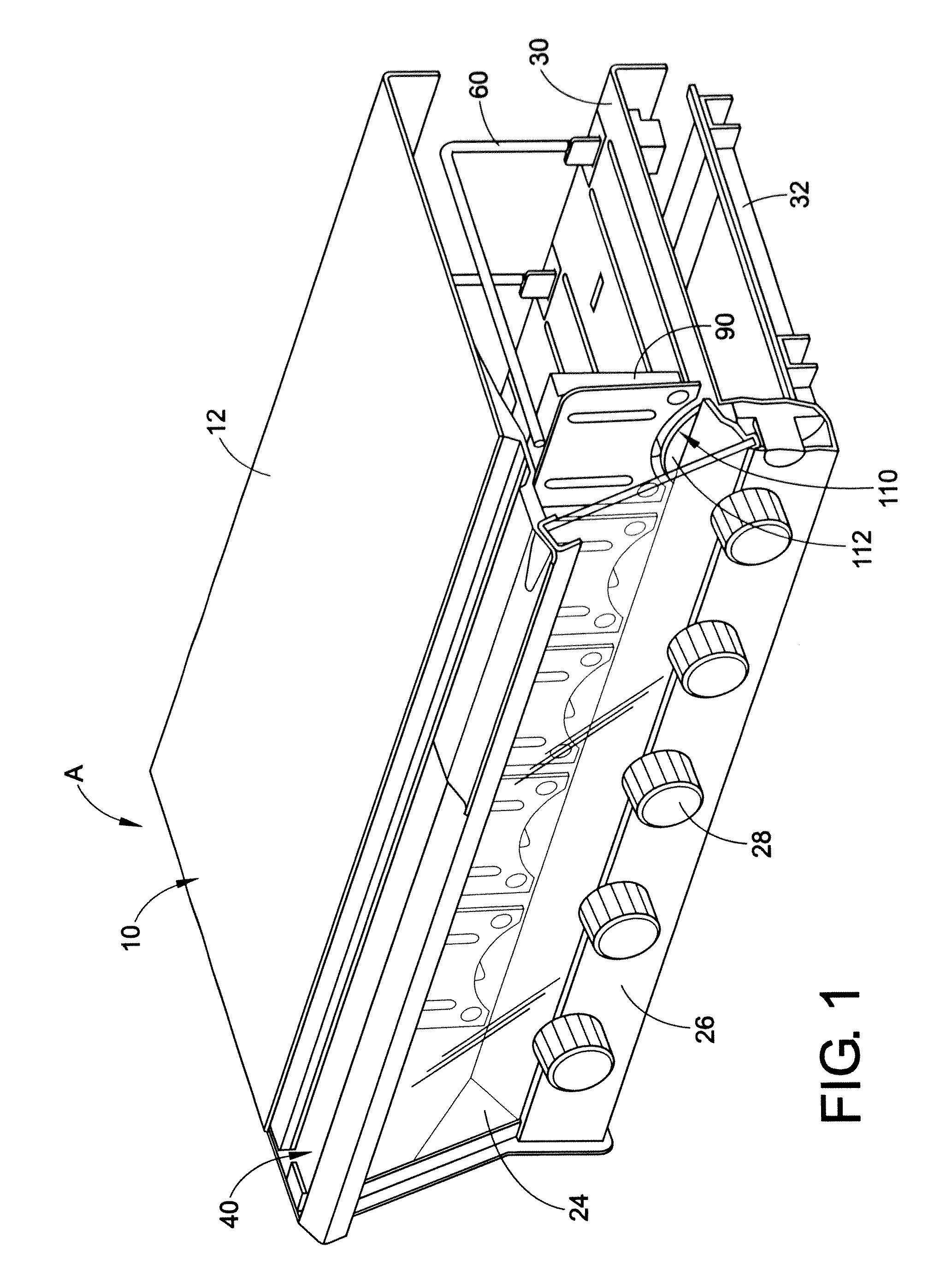
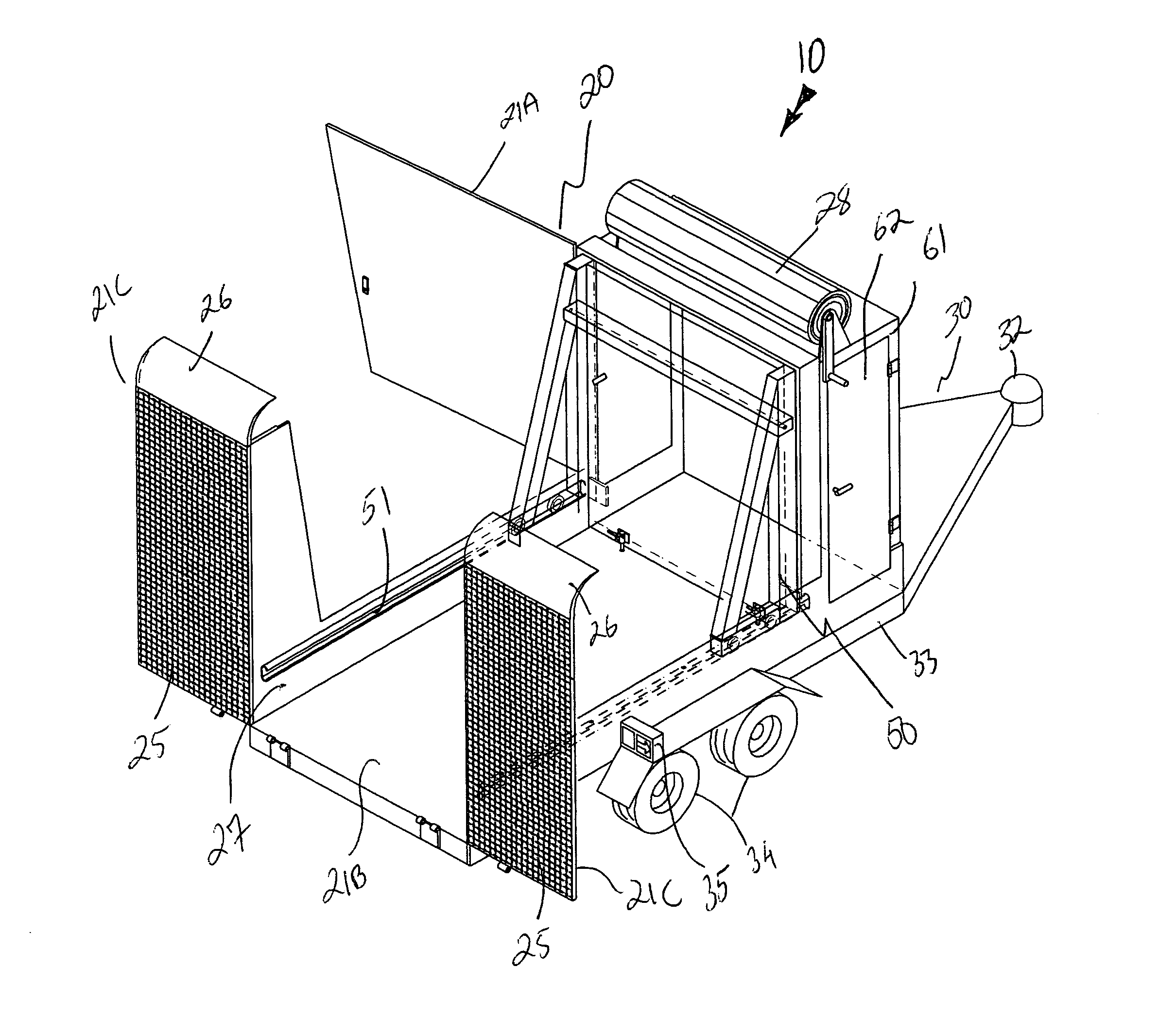
Material/equipment handling assembly
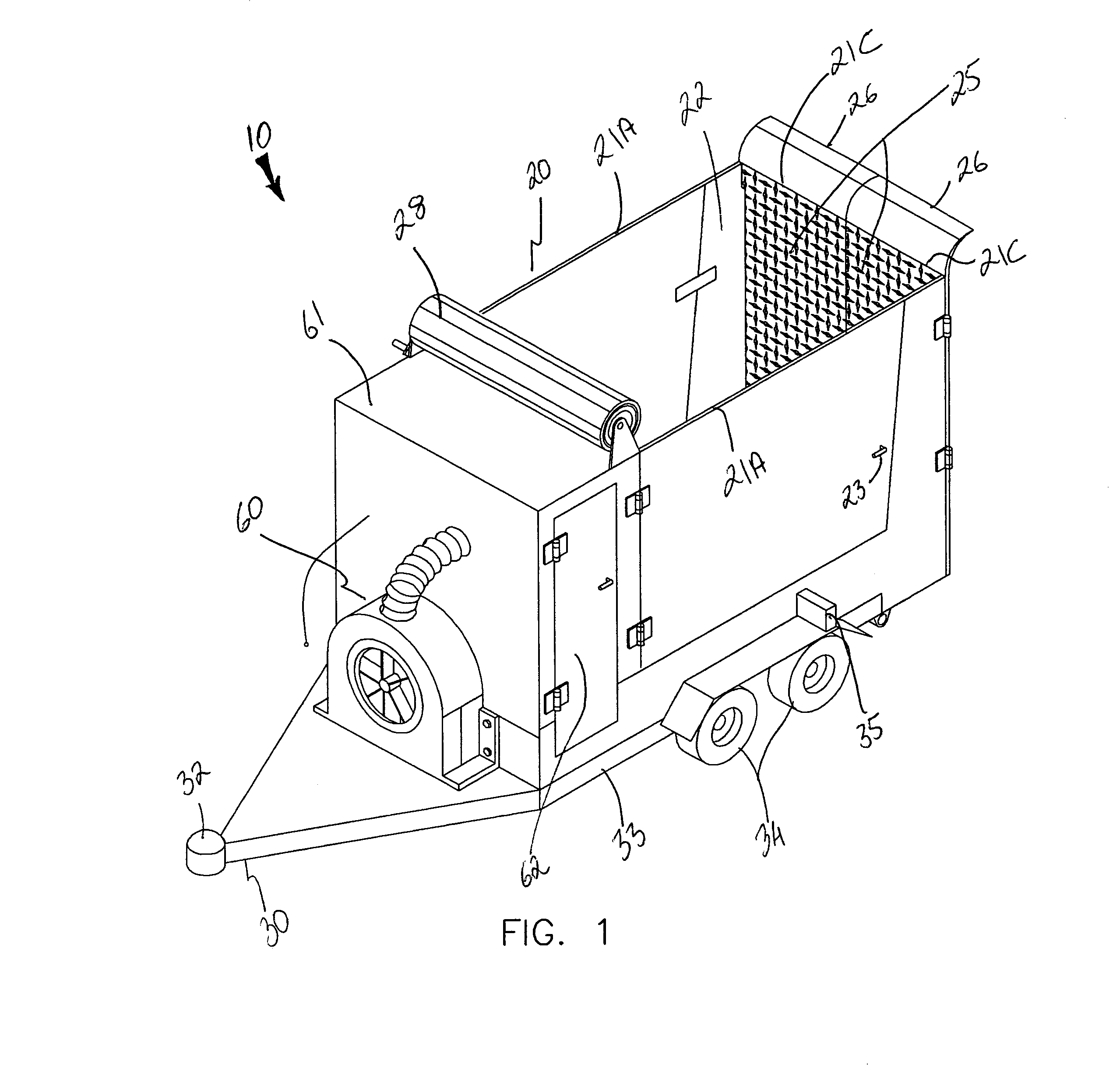
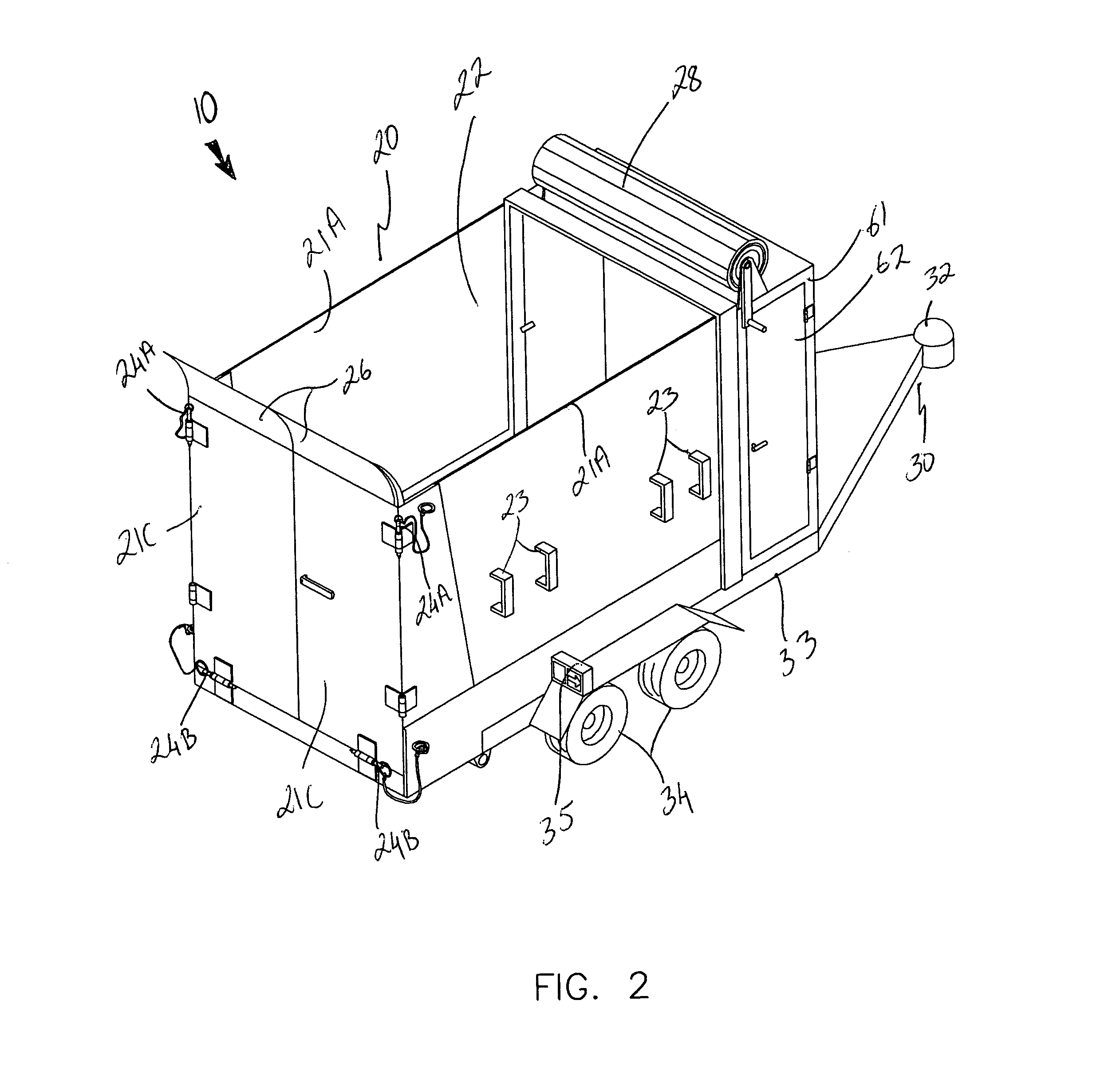
InactiveUS7111908B1Effective supportSelectively accessedSuperstructure subunitsLoad coveringEngineeringMechanical engineering
A trailer assembly includes a body having a plurality of sidewalls for defining a cavity therebetween. Selected sidewalls are pivotally coupled to the body and selectively adaptable between loading and unloading positions and another sidewall defines a substantially planar bottom surface of the body. The body further includes a hitch section protruding forwardly therefrom. The assembly includes a rigid platform including a plurality of wheels connected thereto. Mechanisms are included for pivoting the body between sloped and horizontal positions and for separating a plurality of loads stored within the cavity respectively. The separating mechanism is removably positional within the cavity and slidably adjustable along a longitudinal length of the body. A manually retractable tarpaulin is laterally registered along a width of the body and adjoins a front end portion of the body for protecting exposed material and equipment during transit.
Owner:MILLS FRANK O
Collapsible Package and Method
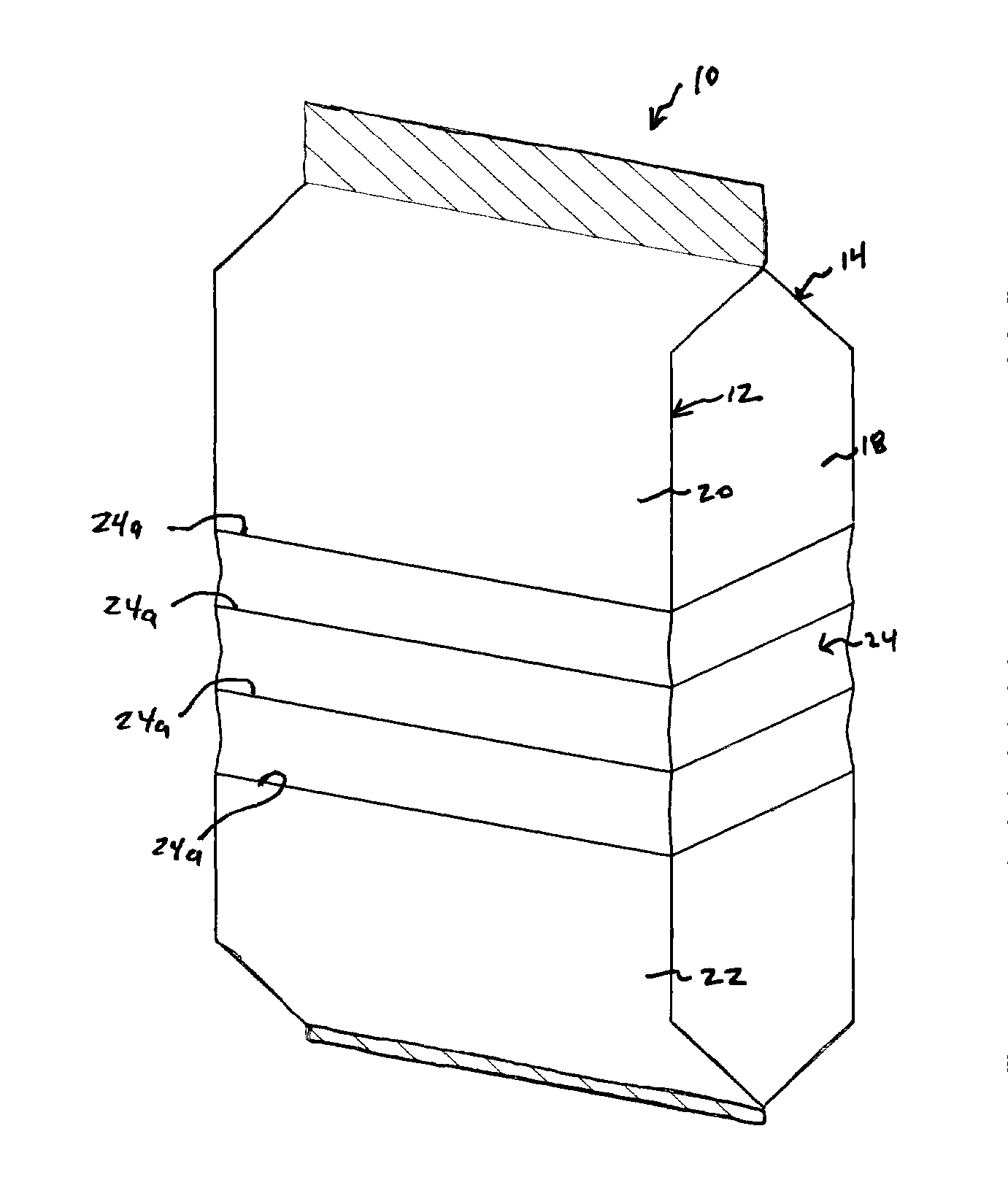
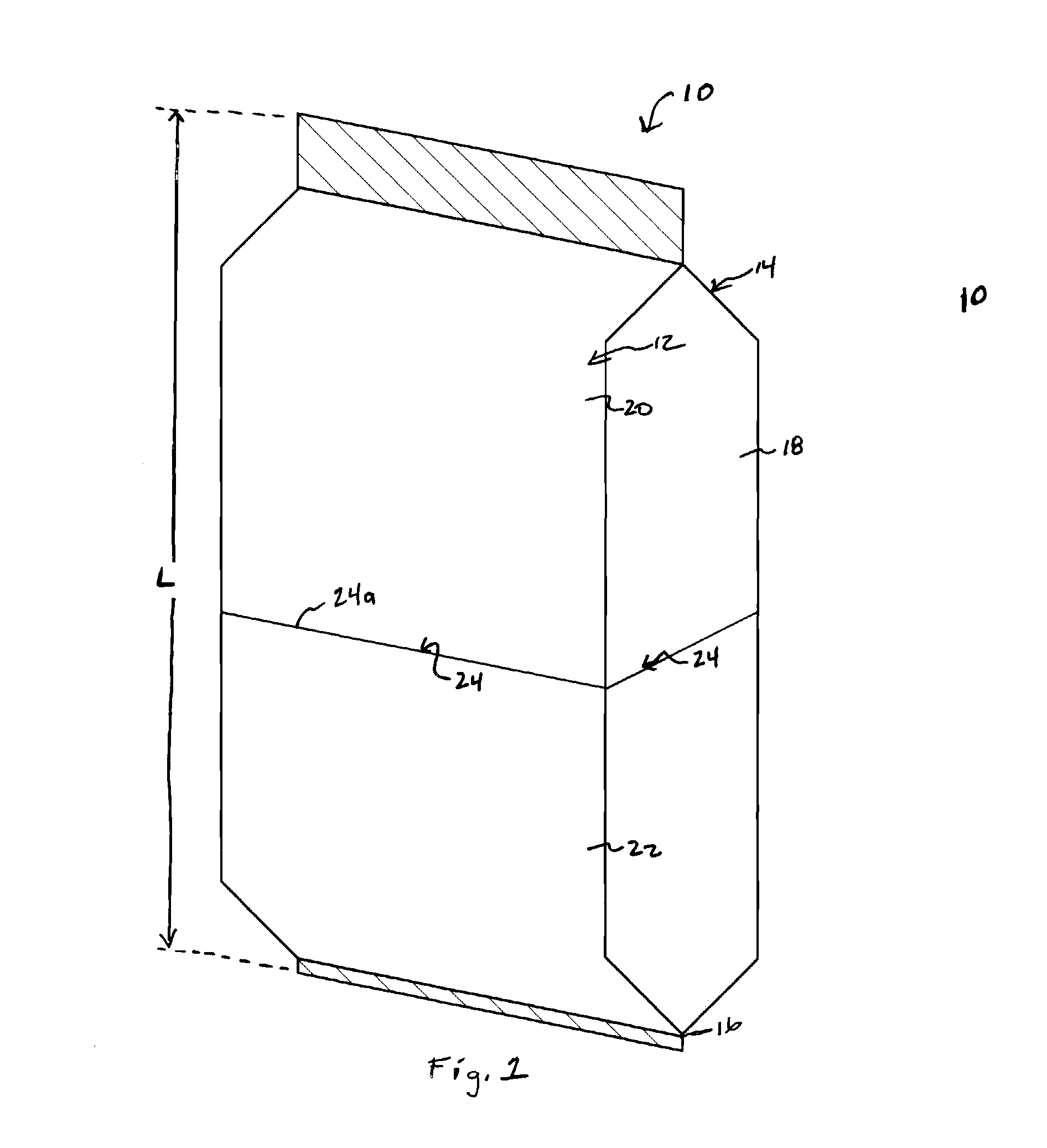
InactiveUS20110253728A1Increased variable telescoping and collapsibilityReduce length dimensionLarge containersRigid containersEngineeringMechanical engineering
A package having one or more collapsible regions or portions is provided. A distinct crease, fold line, material section or separate material can be included with a portion of the package to facilitate collapsibility of a portion of a relatively large package onto or over itself to permit easier access to the interior contents while still allowing for operable use of any access device (e.g., zipper device) provided with the package.
Owner:STEELE MARK
Systems and methods for verifying patient immunity
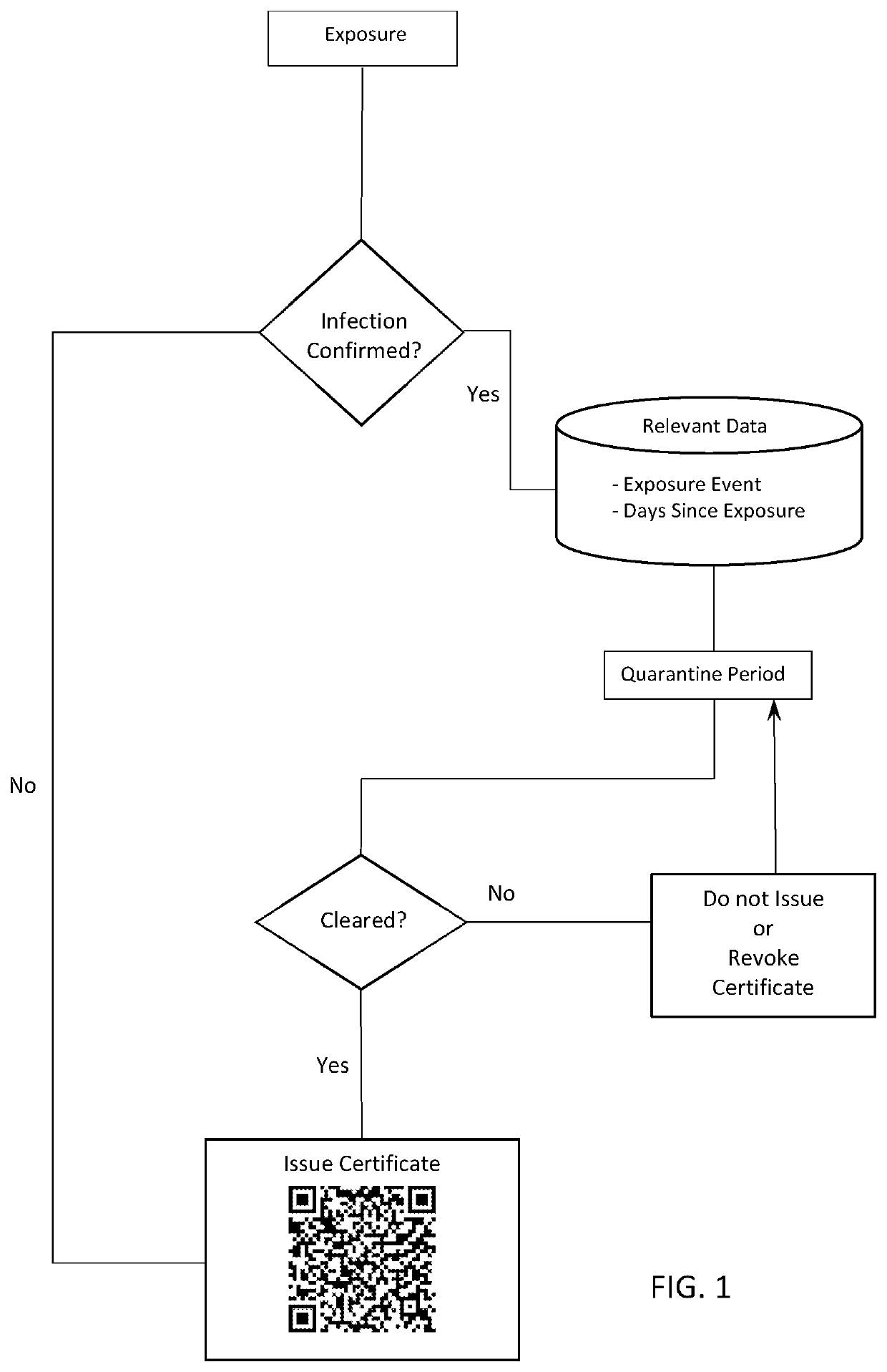
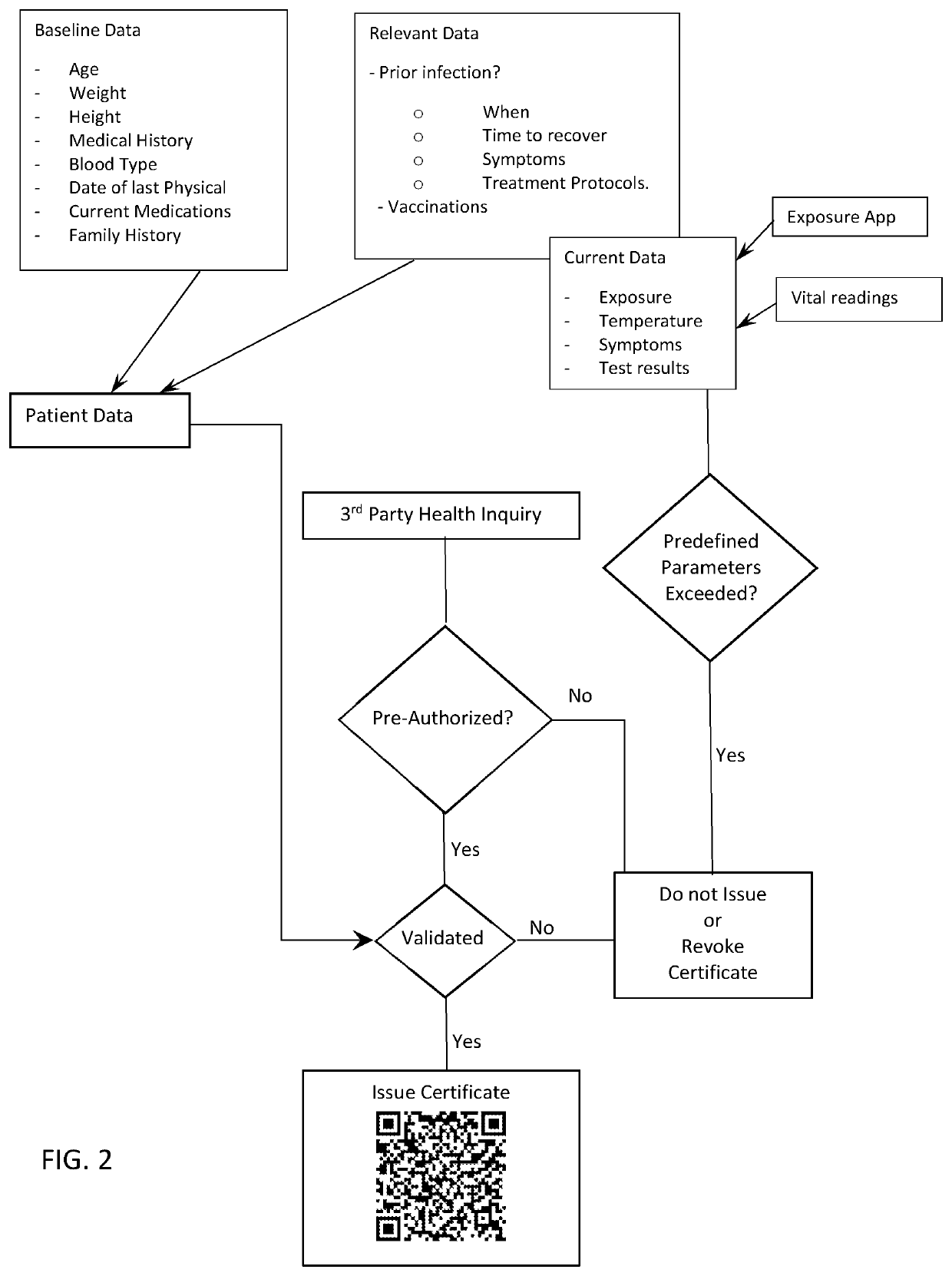
InactiveUS20210319863A1Proven can be very fastReduce chanceHealth-index calculationDrug and medicationsImmunopotencyVaccination
A system and method for verifying a patient's immunity to a predetermined pathogen are provided. The contemplated system relies on at least one of patient-specific and exposure data, which could include immunization or vaccination data, to assess the patient's immunity to a predetermined pathogen. If immunity is verified, the patient is selectively issued a digital certificate real-time and / or on-demand used to allow access to a building, gain authorization to conduct predetermined activities, work, travel freely, etc. The immunity certificate may be renewed or revoked if predetermined events occur, such as a rise in body temperature over a predetermined level.
Owner:RAJAGOPAL DHIREN +1
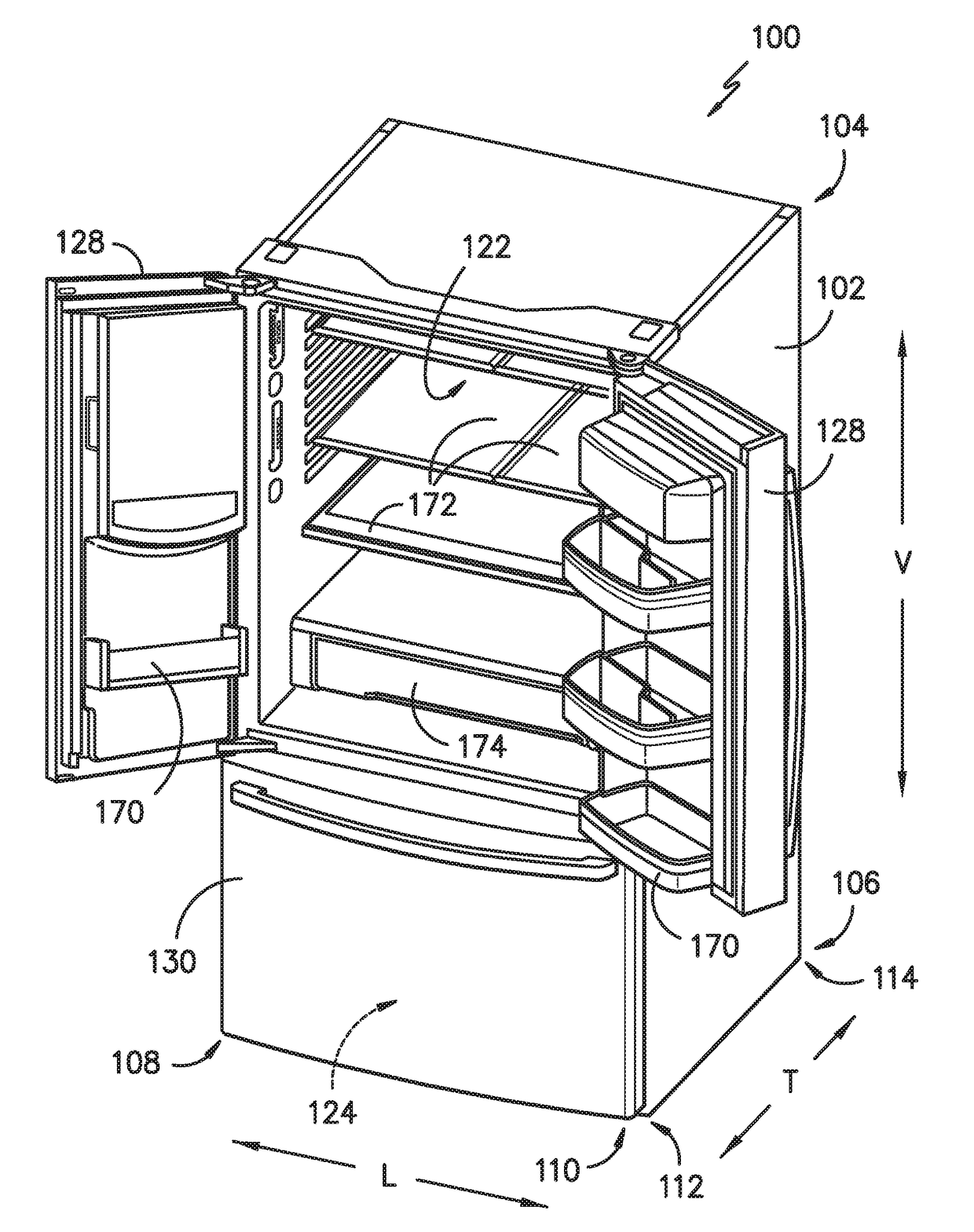
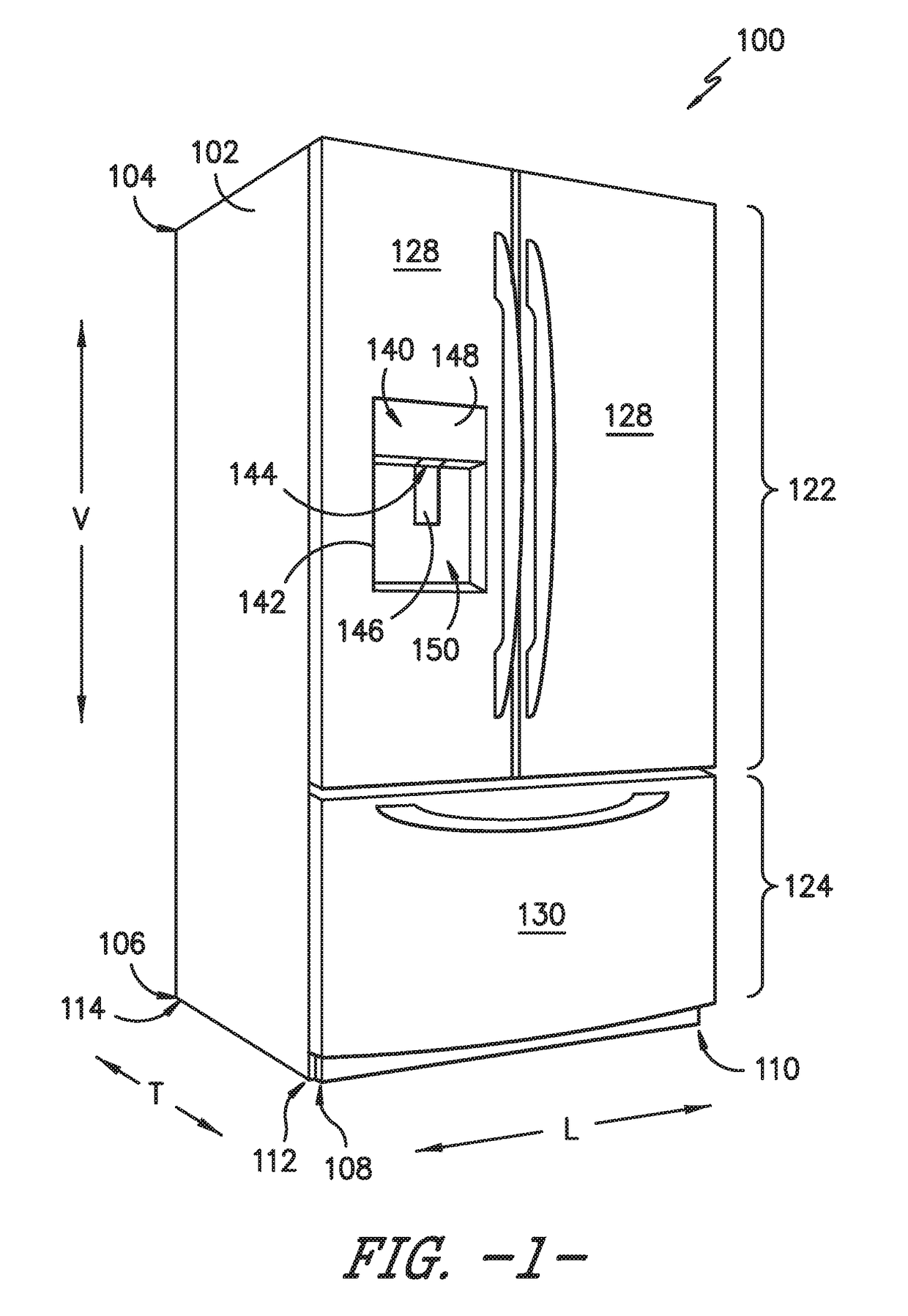
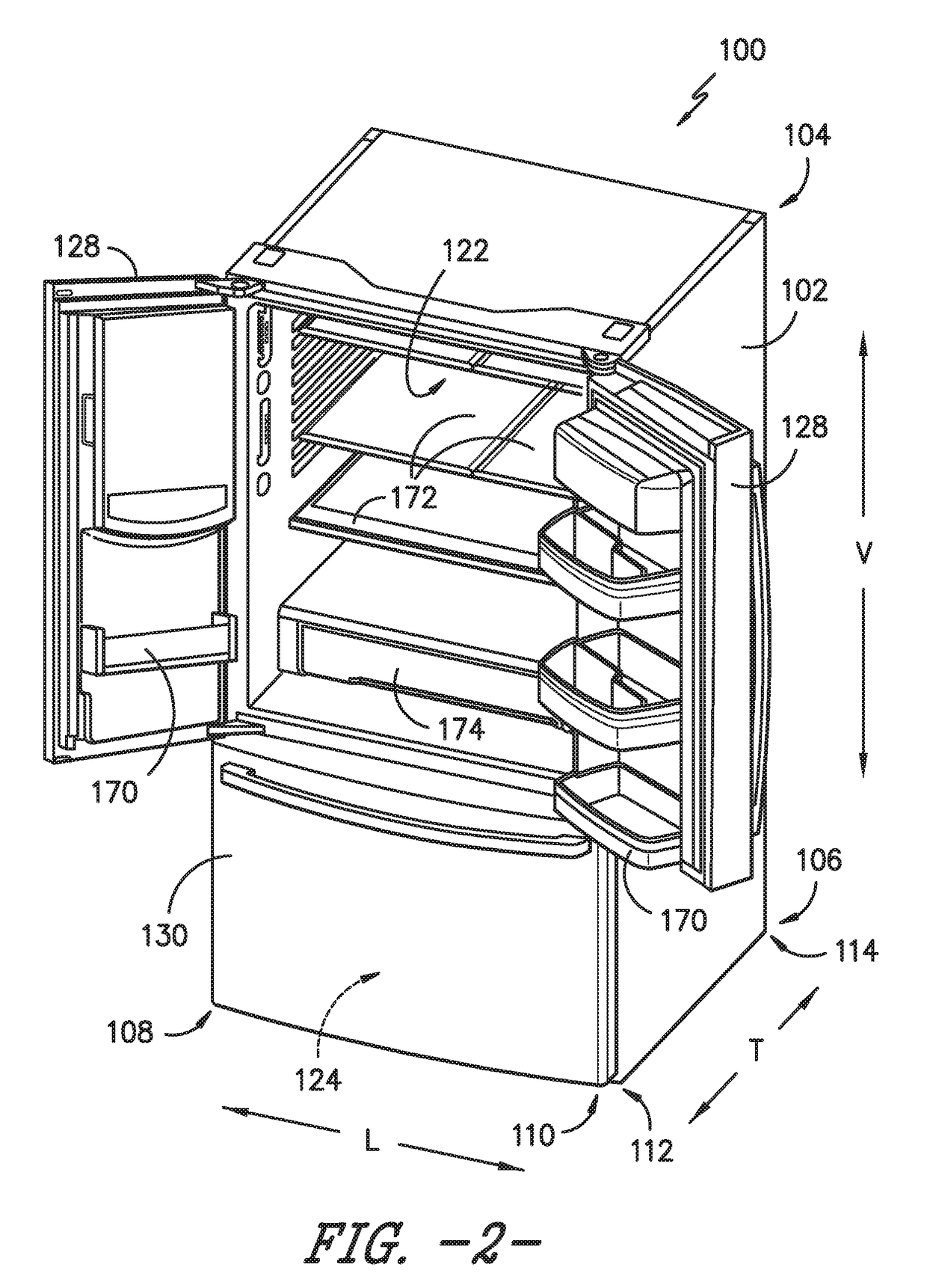
Refrigerator appliance
InactiveUS20140196493A1Selectively accessedDomestic cooling apparatusLighting and heating apparatusFresh foodRefrigerated temperature
A refrigerator appliance is provided. The refrigerator appliance includes an ice maker and a container. The ice maker directs ice into a storage volume of the container. The container is removably positioned within a fresh food chamber of the refrigerator appliance. A valve is mounted to the container and configured for regulating a flow of liquid out of the storage volume of the container.
Owner:HAIER US APPLIANCE SOLUTIONS INC
Tissue Infiltration Device
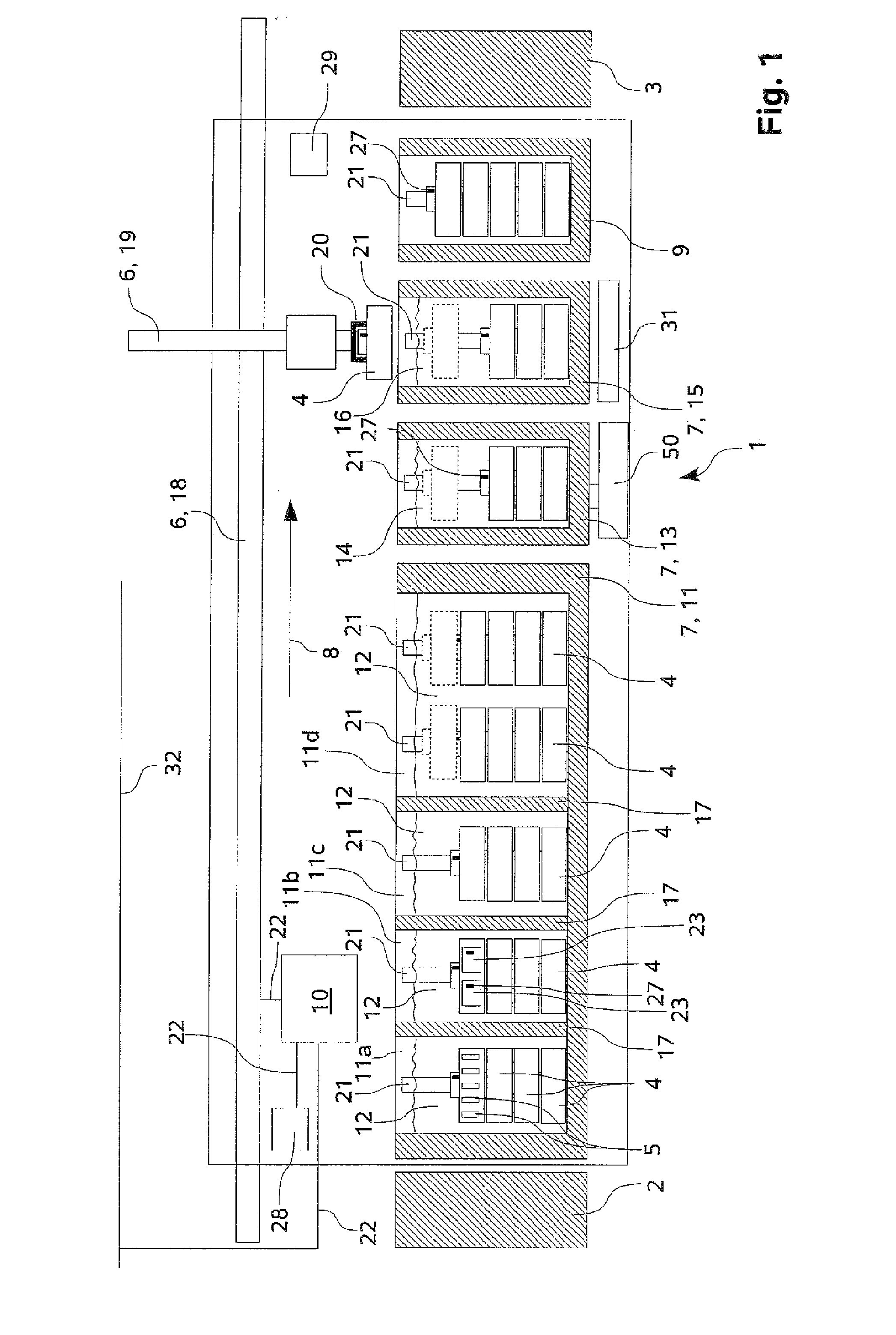
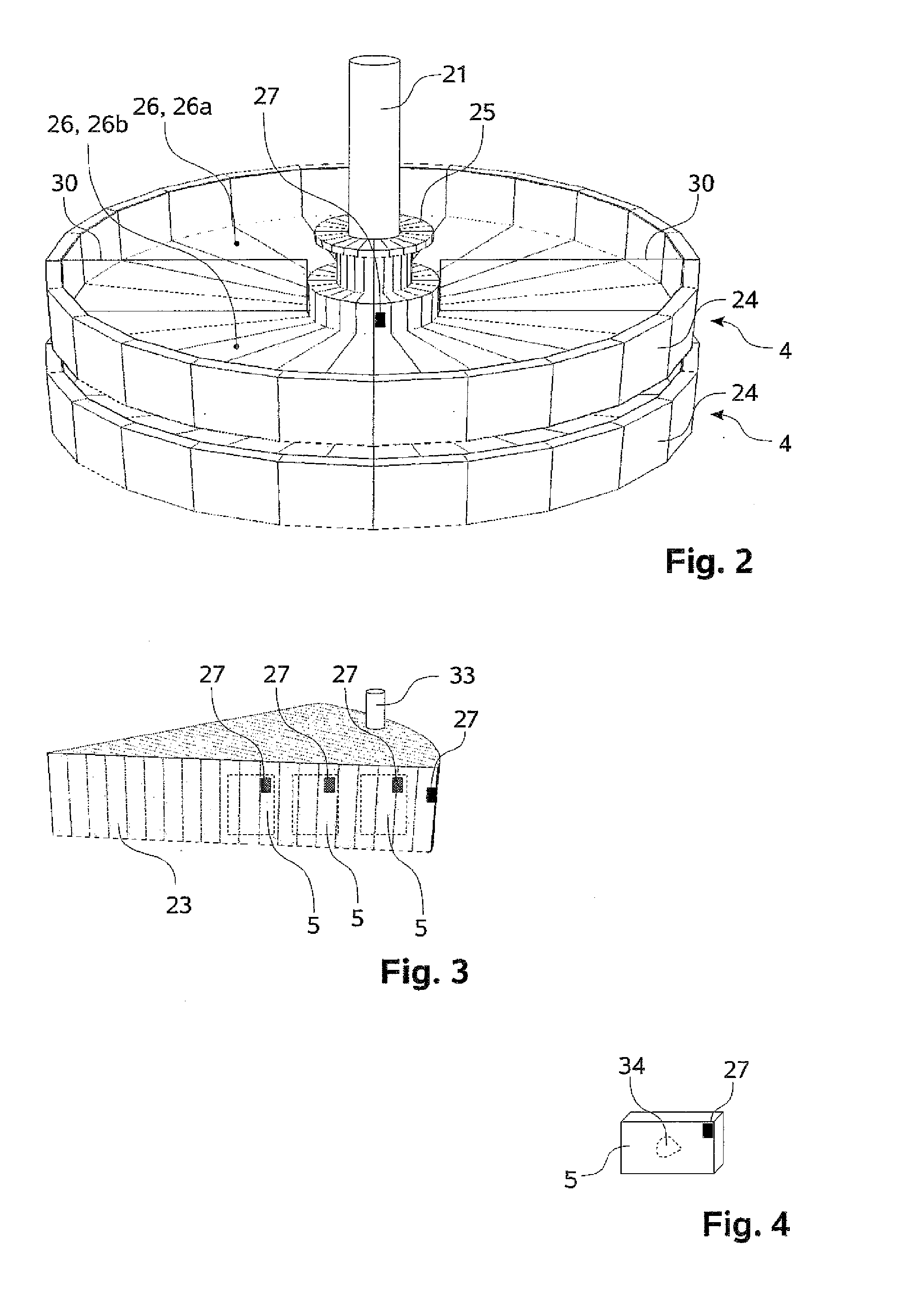
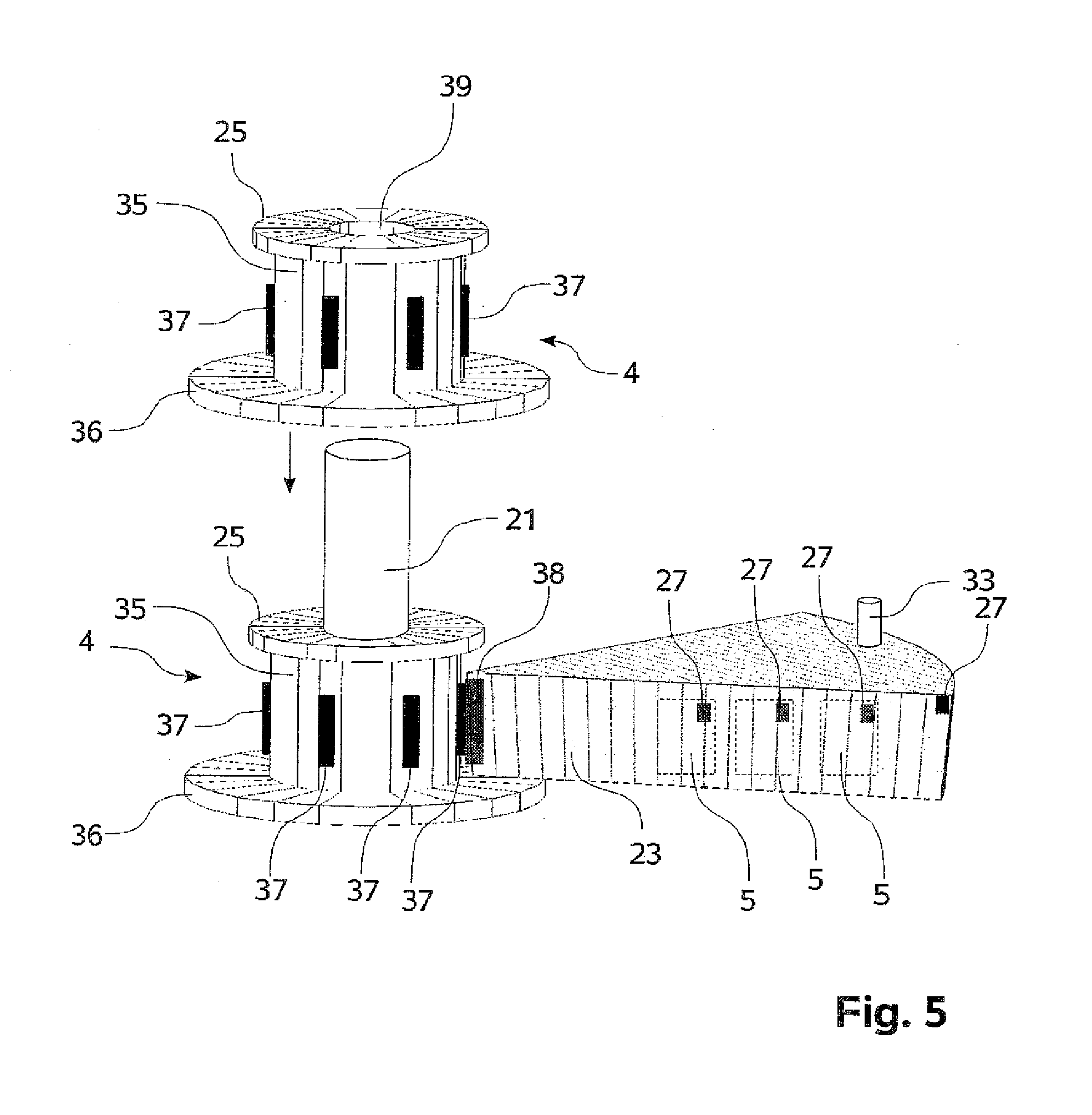
ActiveUS20100216222A1Improve permeabilitySelectively accessedWithdrawing sample devicesPreparing sample for investigationMechanical engineering
The present invention relates to a tissue infiltration device (1) for samples (34) contained in cassettes (5). The tissue infiltration device (1) comprises at least two liquid containers (7, 11a-11d, 13, 15) and a transport apparatus (6). A liquid (12, 14, 16) having a property that can be predetermined can be filled into a liquid container (7, 11a-11d, 13, 15). A plurality of cassettes (5) can be held by a transport device (4). Using the transport apparatus (6), a transport device (4) can be brought to a liquid container (7, 11a-11d, 13, 15) and / or moved away from a liquid container (7, 11a-11d, 13, 15). A sequence of operations (8) can be prescribed in which a transport device (4) runs through the liquid containers (7, 11a-11d, 13, 15) of the tissue infiltration device (1). So that an accelerated or priority processing of a transport device (4) is possible using the tissue infiltration device (1), but without using an additional liquid container (7, 11a-11d, 13, 15) provided only for this purpose, it is provided that at least two transport devices (4) can be brought into a liquid container (7, 11a-11d, 13, 15) above and / or next to one another, wherein said transport devices can have different dwell times in the liquid container (7, 11a-11d, 13, 15).
Owner:LEICA BIOSYST NUSSLOCH
Adjustable opening for a hunting blind
Owner:PD2F INC
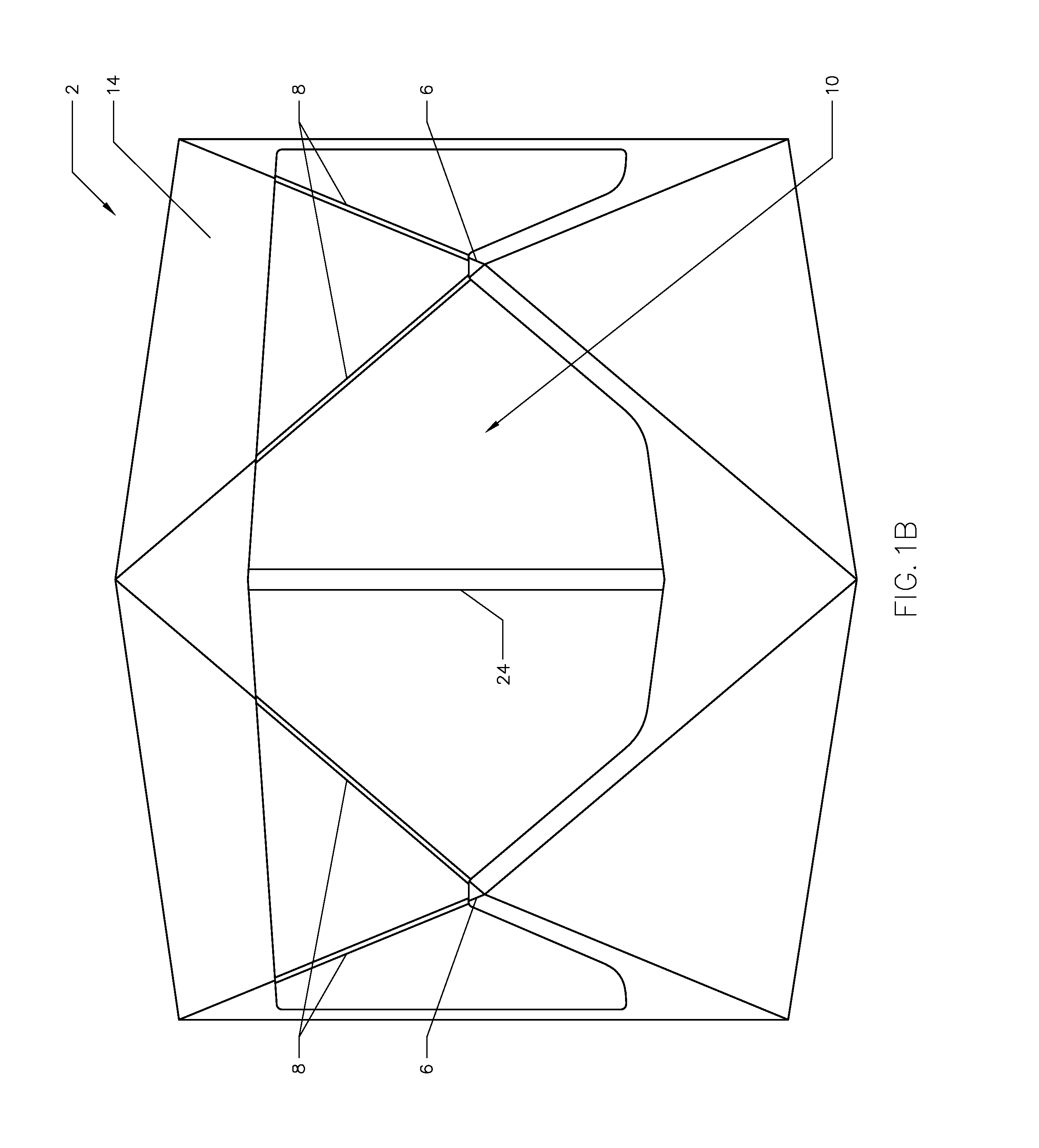
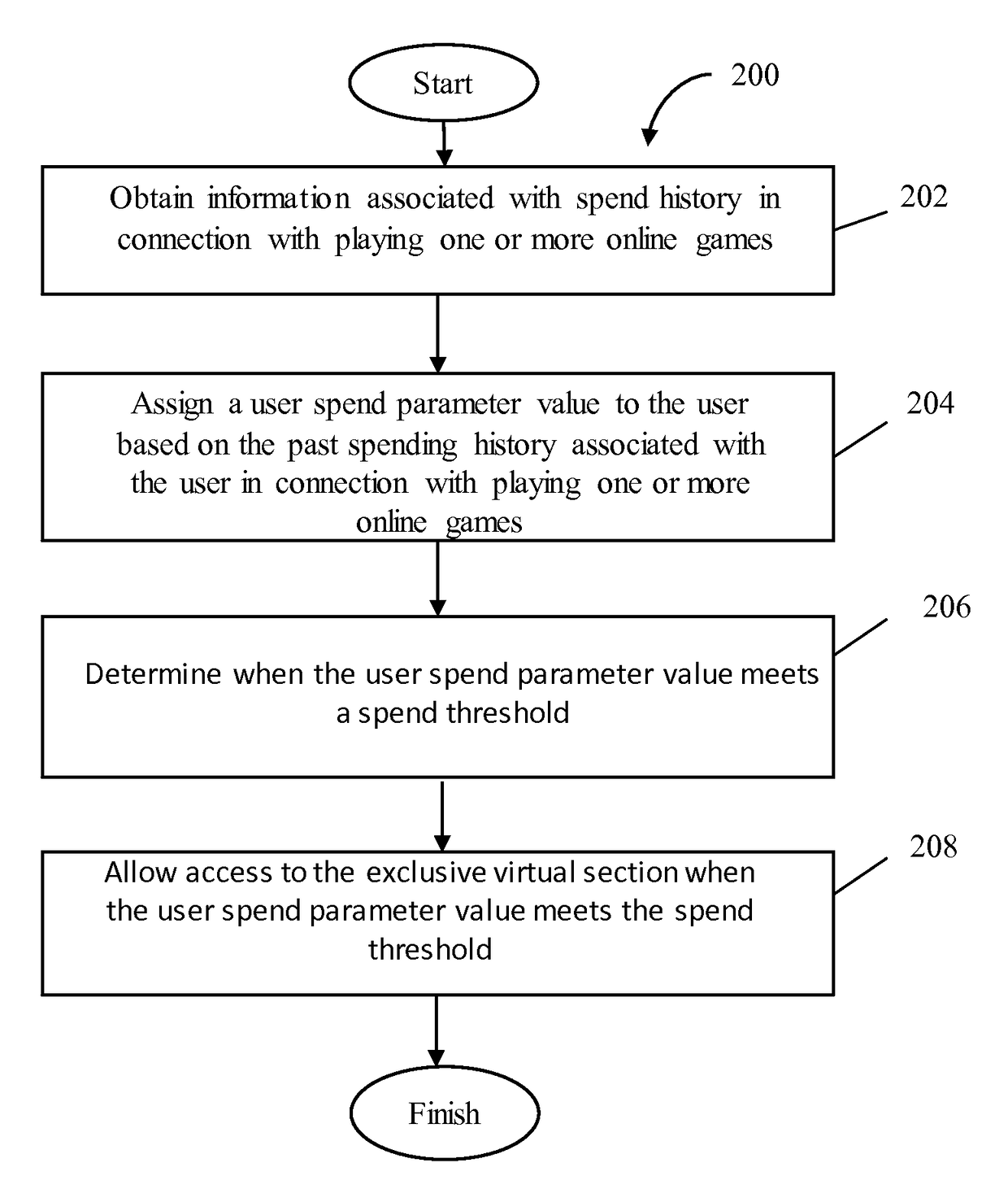
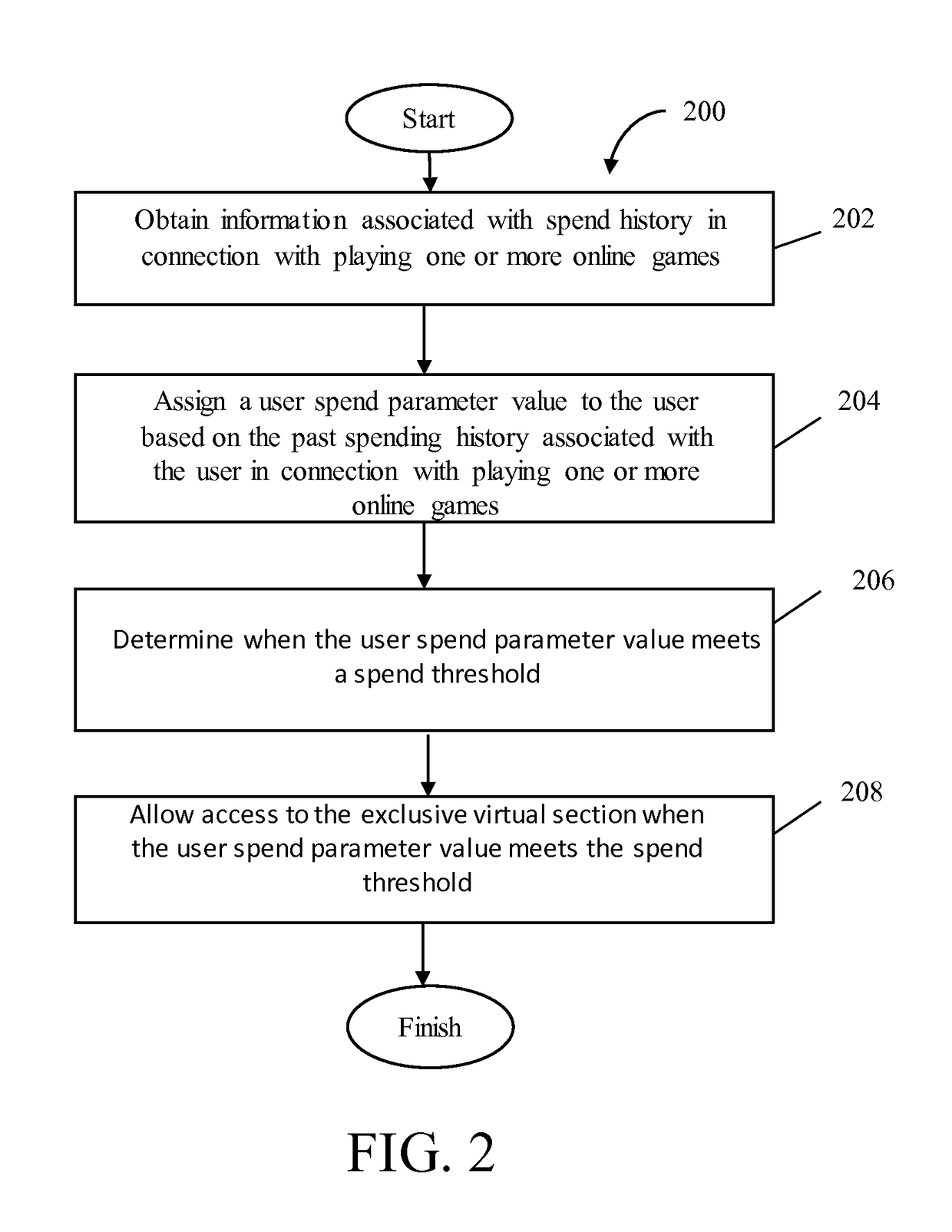
Access to an exclusive virtual section of an online game based on past spending behavior
ActiveUS9623335B1Easy to demonstrateImprove gaming experienceDiscounts/incentivesPayment architectureGame basedMultimedia
This disclosure relates to a system and methodology for obtaining information associated with spend history of a first user in connection with playing an online game and processing the information associated with the spend history to assign the user spend parameter value to the first user which may be further used to provide selective access to an exclusive virtual section associated with an online game when the user spend parameter value meets the spend threshold.
Owner:KABAM
System and Method For Controlling The Temperature of A Temperature Controlled Drawer
ActiveUS20170191731A1Easy temperature controlSelectively accessedLighting and heating apparatusDomestic refrigeratorsTemperature controlFresh food
A refrigerator appliance having a temperature controlled drawer with improved temperature control is provided. A sealed system including a compressor, an evaporator, and an evaporator fan may be configured for cooling the fresh food chamber. A controller is configured to operate the evaporator fan when the compressor is off in order to increase the temperature of the temperature controlled drawer. Additionally, or alternatively, a secondary fan may be attached to the temperature controlled drawer and may be selectively operated by the controller to circulate air from the chilled chamber through the temperature controlled drawer. In this manner, the temperature of the temperature controlled drawer may be more precisely controlled regardless of whether the compressor is running.
Owner:HAIER US APPLIANCE SOLUTIONS INC
Thyristor-based semiconductor memory device with back-gate bias
InactiveUS7859012B1Impurities increasePrevent depletion and inversionThyristorSolid-state devicesDopantThyratron
Owner:T RAM ASSIGNMENT FOR THE BENEFIT OF CREDITORS LLC +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com