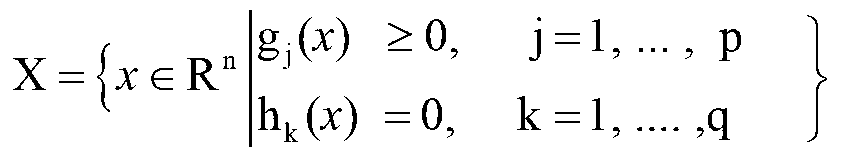Patents
Literature
135results about How to "Improve digging ability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
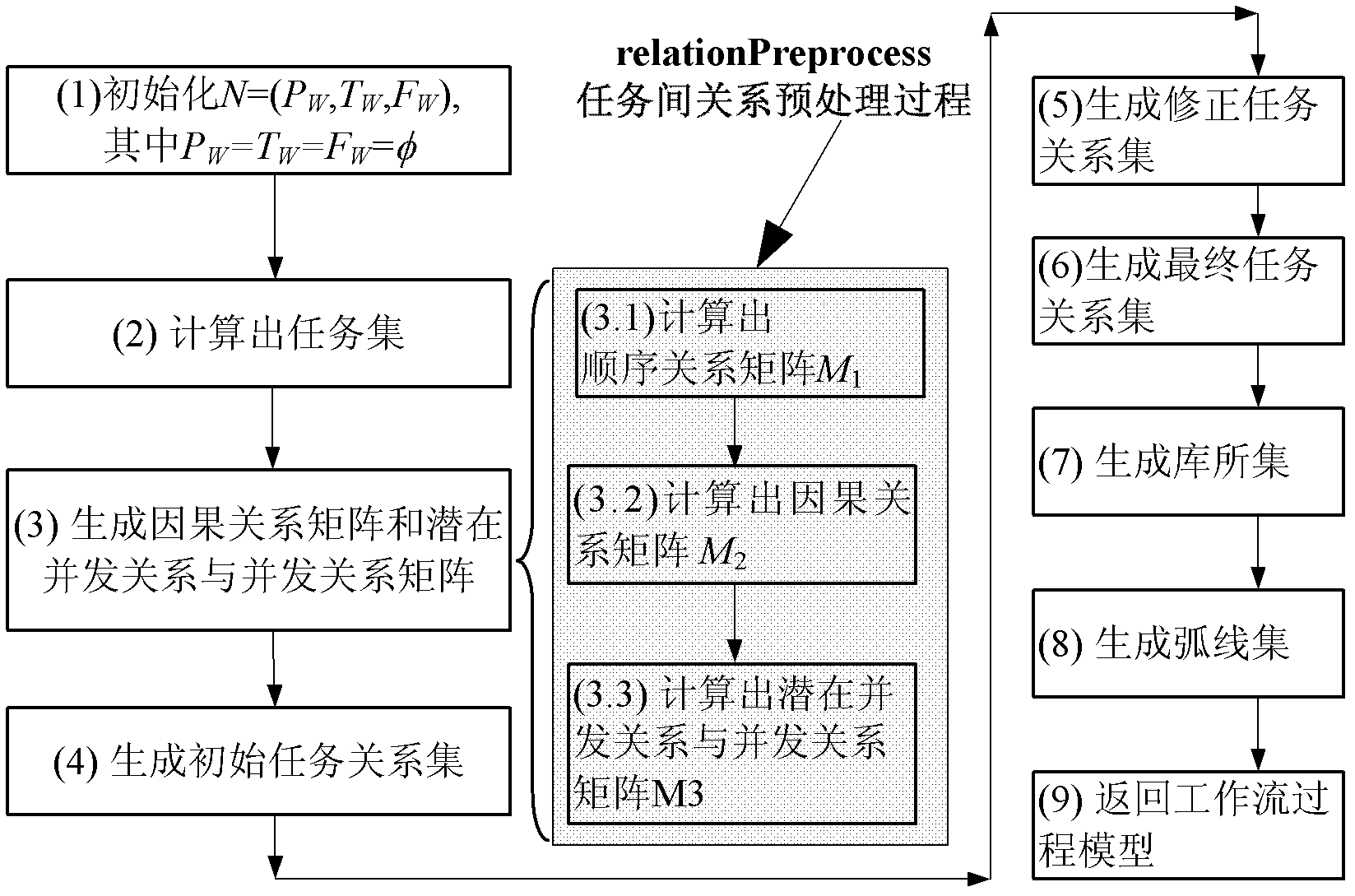
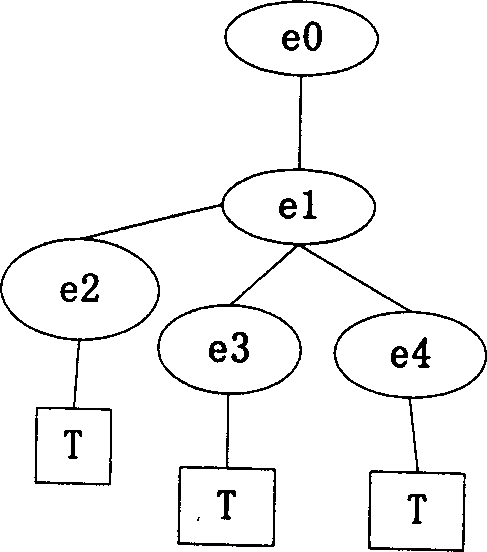
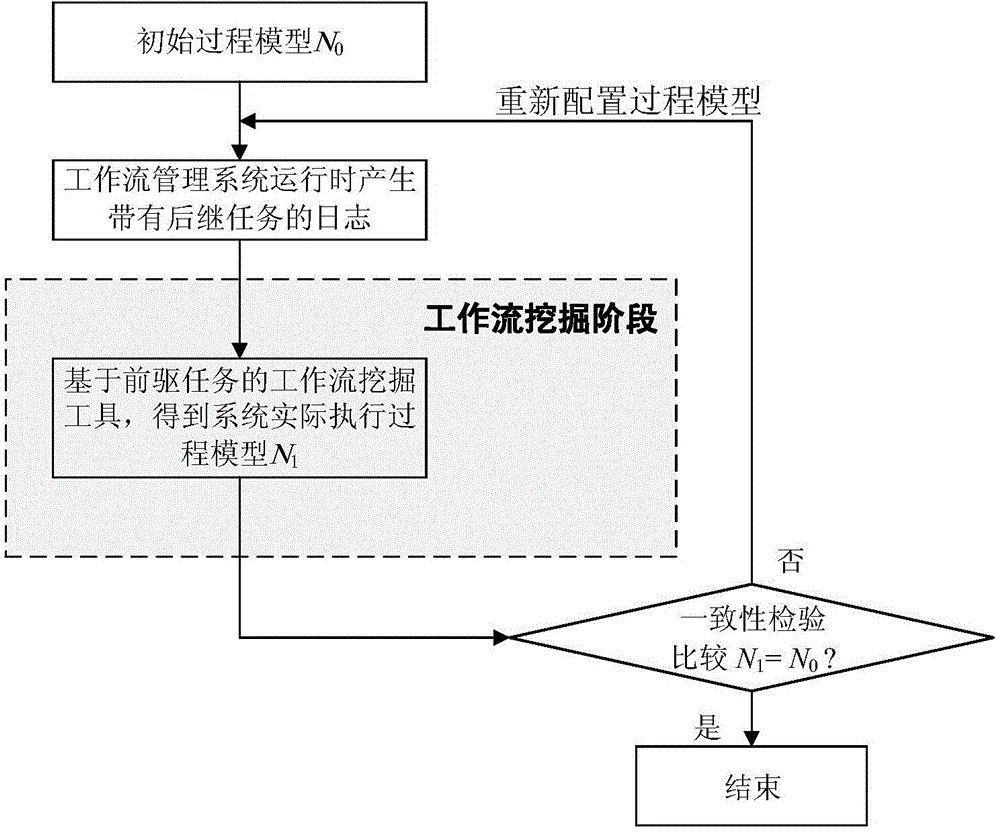
Workflow mining method based on subsequent tasks
InactiveCN102332125AImprove digging abilitySimplify dependenciesInstrumentsEvent typeCausal relations
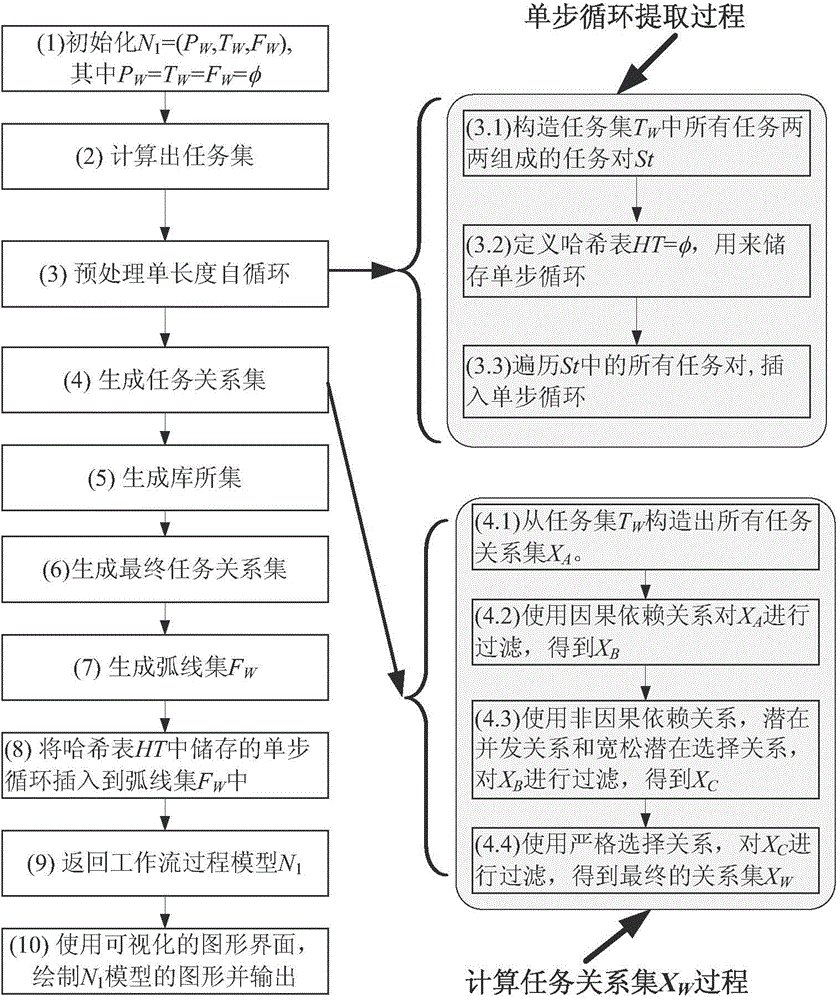
The invention discloses a workflow mining method based on subsequent tasks. The workflow mining based on an event log takes the event log as an input and takes a workflow model described by a Petri network as an output result; by the method, event types are introduced to ensure that the workflow log comprises a subsequent task of the current task, and the subsequent task refers to an aggregate of the tasks to which an execute permission is transferred after the current task is finished; and the method comprises the following steps of: (1) setting an initial value for a workflow process model to be mined; (2) analyzing the event log W, and calculating a task set TW, an initial task and an end task TO; (3) calling a relation Preprocess process to obtain a causal relation matrix M2 and a potential concurrency relation and concurrency relation matrix M3; and (4) calculating an initial task relation set XW according to the matrixes M2 and M3. By the invention, an integrated workflow mining method based on the subsequent tasks is formed.
Owner:NANJING UNIV
Shipborne water bank line overwater and underwater integrated measurement system integrated method
ActiveCN105352476AMeet the requirements of the upper and lower positionsAvoid repeated calibration workProgramme controlComputer controlSystems designData acquisition
The invention provides a shipborne water bank line overwater and underwater integrated measurement system integrated method; integration of hardware of a measurement system is realized through design of a multi-sensor lift platform of an integrated mapping device, and requirements of changing sensor upper and lower positions under different operating conditions of a measurement ship are met. The system designs a data acquisition display control software framework to realize multi-sensor collaborative data acquisition, point cloud real-time display and the like. Through point cloud data preprocessing, data interpolation, spatial registration and other steps, multi-source data are subjected to fusion and resolution, so as to obtain a point cloud product for solving problems of difficult-and-inappropriate-to-reach island topographic measurement and marine unit coastal zone and mud flat topographic survey. The method realizes water bank line overwater and underwater integrated measurement, overcomes limitation of a traditional measurement technology, greatly improves the efficiency of measurement, and provides a bran-new measuring technological means for high-precision three-dimensional measurement problems required by wisdom navigation channels, digital water conservancy, wharfs, bank lines, off-lying sea islands and various engineering construction.
Owner:QINGDAO XIUSHAN MOBILE SURVEYING CO LTD
Subtopic mining method
ActiveCN106844416AImprove digging abilityNatural language data processingSpecial data processing applicationsAlgorithmComputer module
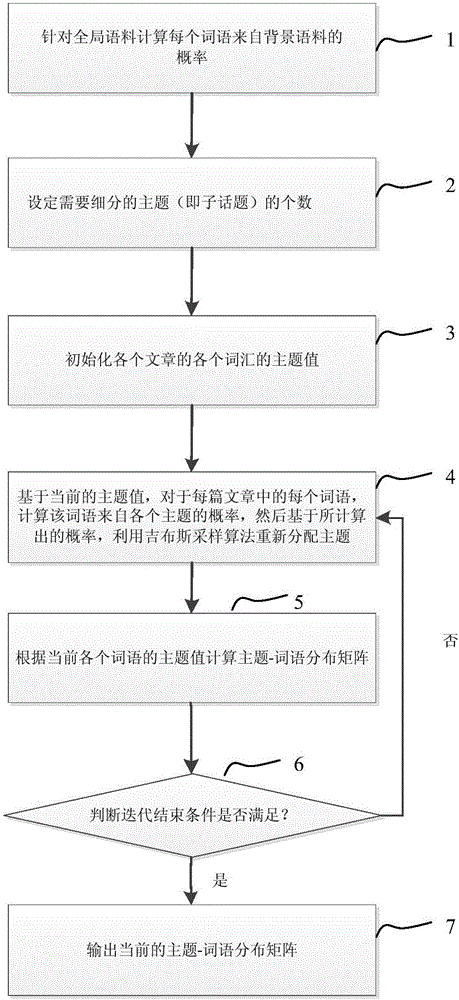
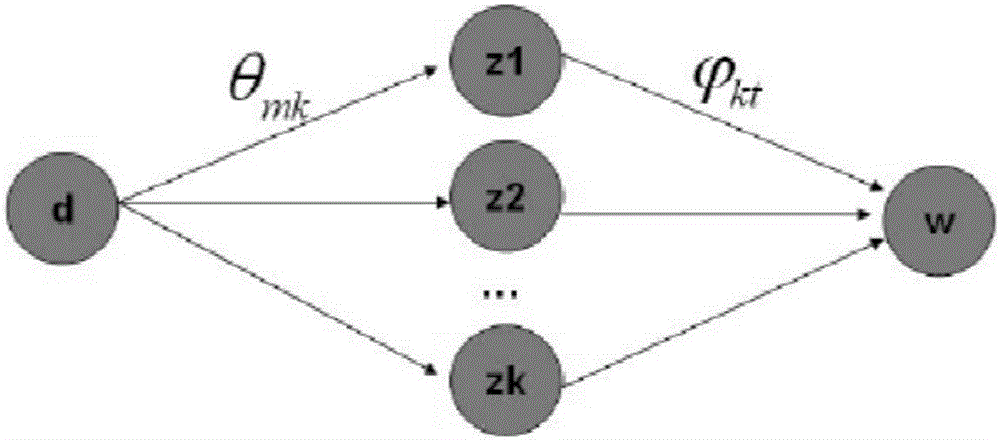
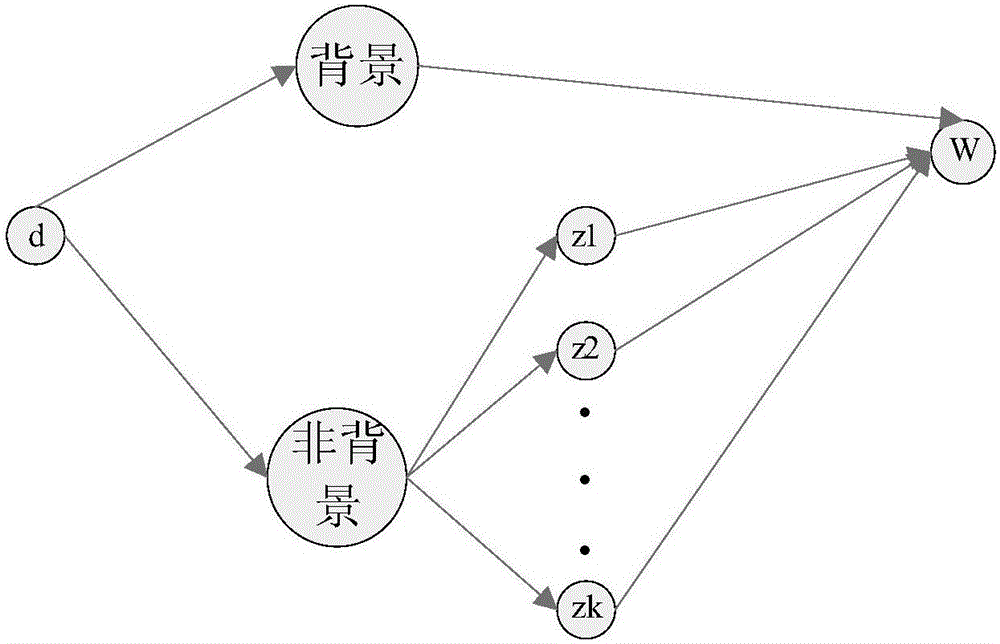
The invention provides a subtopic mining method. The method comprises the steps that (1) a subject value of each term of each document in a corpus is initialized; (2) based on the current subject values of all the terms of all the documents, the probability of each term in each article coming from all subtopics and the probability of each term coming from a background module are calculated, and then a subject value is redistributed for each term in each article through a Gibbs sampling algorithm based on the calculated probabilities, wherein the probability of each term coming from the background module is calculated according to term distribution vectors, subjected to statics in advance, in the background module, and the term distribution vectors in the background module are constant from beginning to end in the iteration process; and (3) if iteration stop conditions are met, LDA subtopics are obtained according to current subject value information, and if not, the step (2) is returned to. Through the method, the topic mining effect targeting a feature article set can be remarkably improved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Lorentz-force-based laser welding pool control method
ActiveCN108247226AAffecting the physical laws of interactionImprove controllabilityLaser beam welding apparatusEngineeringStressed state
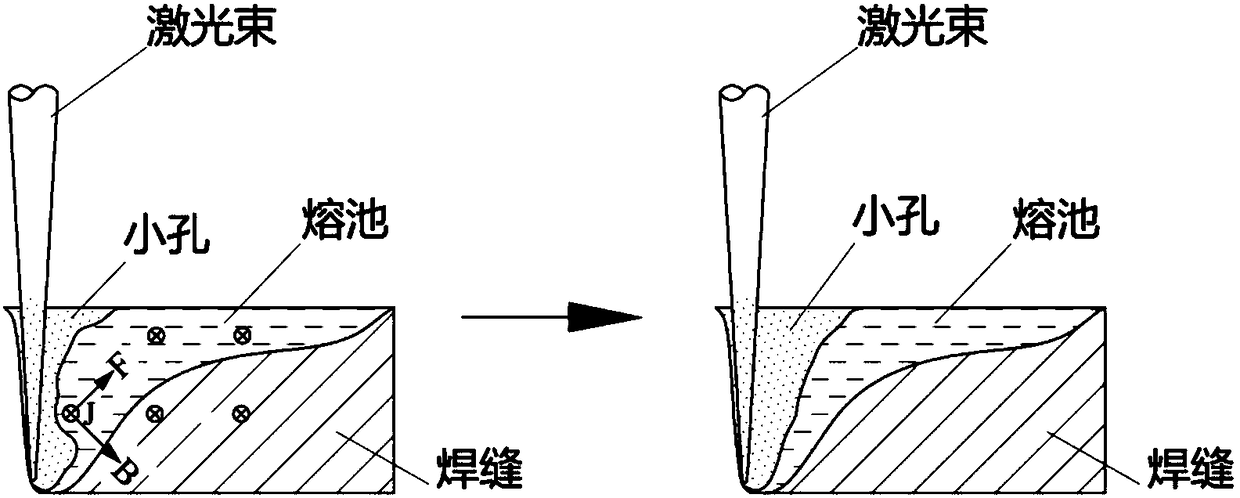
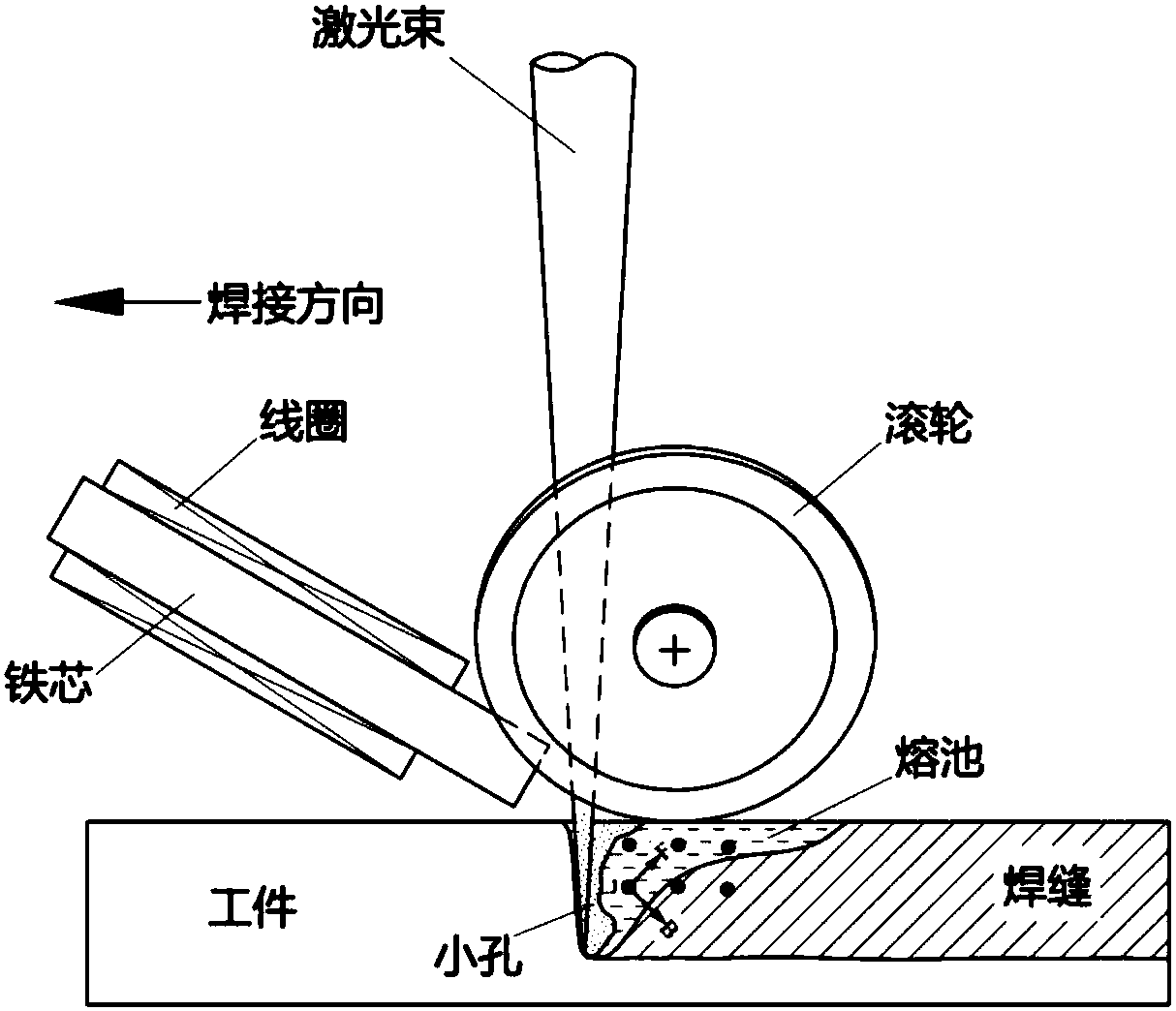
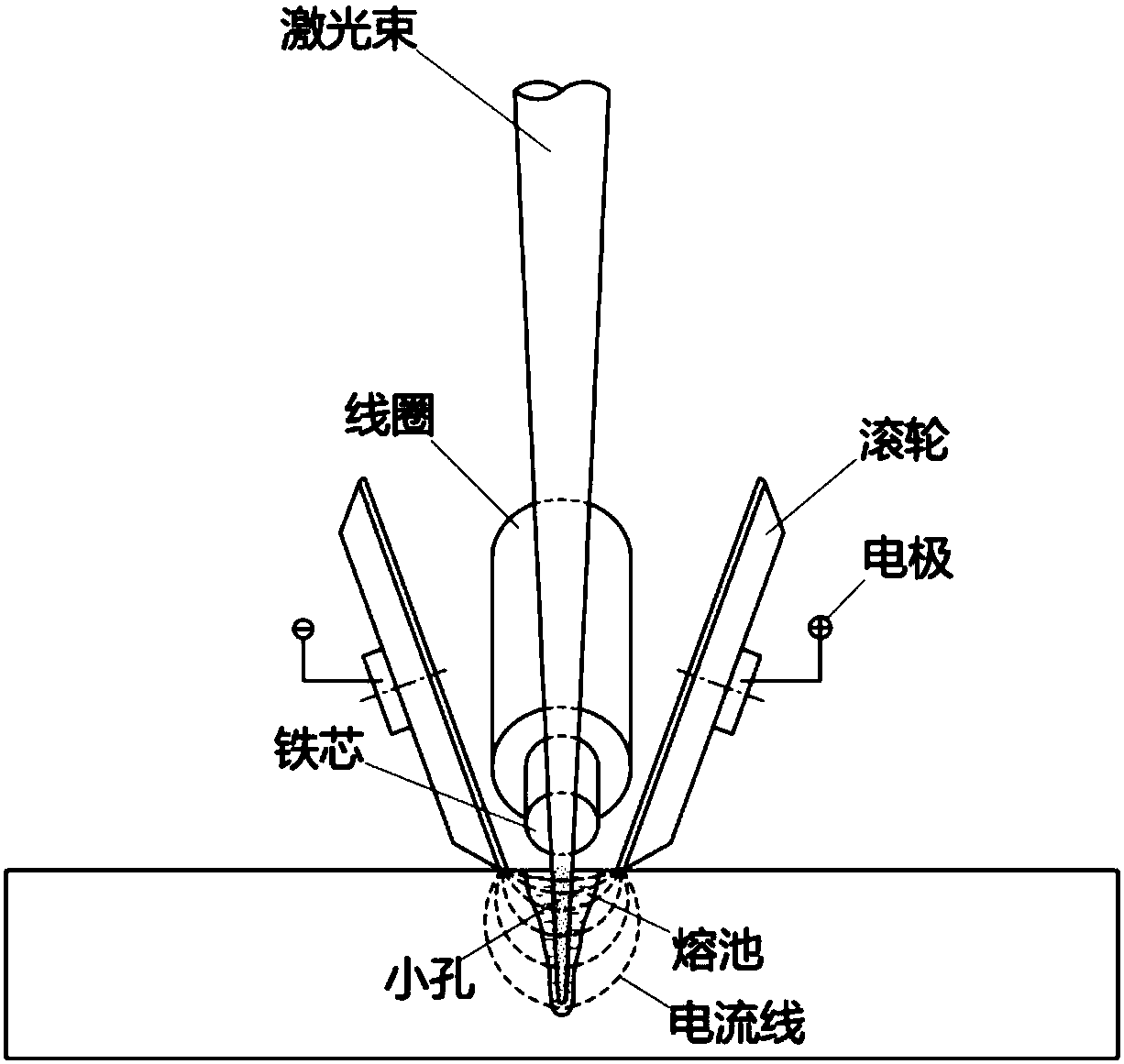
The invention provides a Lorentz-force-based laser welding pool control method and belongs to the technical field of laser processing. According to the method, current and a magnetic field which are perpendicular to each other are applied to a laser welding pool to generate Lorentz force following the ampere left-hand law in the welding pool; the stress state, the flow behavior and the solidification process of a melt are actively controlled through the Lorentz force. The backward Lorentz force is applied to the welding pool to make a welded tiny hole be deepened and stretched, so that metal vapor / plume in the tiny hole escape smoothly. A solution in the welding pool flows smoothly. The effects of increasing the weld penetration depth increase, improving the welding stability and optimizing welding formation are achieved. If AC or pulse wave modulation is conducted on parameters of the applied current and the applied magnetic field, the Lorentz force can have the effects of stirring, vibrating and directionally driving the solution in the welding pool. The adjustment functions of the weld microstructure and performance can be achieved while the welding defects such as pores, cracks, undercut and poor formation are controlled.
Owner:BEIJING UNIV OF TECH
Excavator cutting head
InactiveCN102277886AMeet excavation needsImprove completenessSoil-shifting machines/dredgersHydraulic motorReduction drive
The invention provides a tunnelling and excavating integrated machine cutting head. The cutting head mainly comprises a hydraulic motor, a hydraulic motor fixing box, a T-shaped gear reducer, rotating brackets and rollers on which a plurality of pick-shaped cutters are distributed. The cutting head has the following beneficial effects: by adopting the hydraulic motor for driving, the explosion-proof requirement in the mine and the convenience of use in the ground engineering are satisfied; by adopting the T-shaped gear reducer, the cutting head has simple and compact whole structure; the cutting head has strong tunnelling and excavating capabilities; a hydraulic motor output shaft is used for transmitting power to a bevel gear set, after primary bevel gears change the direction of rotation through transmission, the power is transferred to an intermediate gear by pinions of a straight gear set to realize primary speed reduction, then the power is transferred to gearwheels, and finally the power is transferred to the bilaterally symmetrical rotating brackets by spline shafts; the rocks are cut and broken by the rollers which are sleeved on the rotating brackets and provided with pick-shaped cutters; and the cutting head can be used for tunnelling, excavating and breaking the rocks with hardness being less than 8, can satisfy the requirement for ditch excavation in the mine and on the ground, saves the labor investment, and improves the degree of mechanization and safety of coal mine and ground engineering development.
Owner:CHINA UNIV OF MINING & TECH
Self-propulsion trailing suction hopper dredger
ActiveCN105507355AStrongImprove digging abilityMechanical machines/dredgersSludgeHigh pressure water
The invention discloses a self-propulsion trailing suction hopper dredger. The self-propulsion trailing suction hopper dredger comprises a dredger body; a movable cover is provided with a driving pressing block; a second driving device is arranged at the top of the driving pressing block; the movable cover is internally provided with a translation mechanism; the translation mechanism is provided with a movable through hole; a rake tooth shell is arranged in the movable cover; the rake tooth shell is internally provided with an engagement block; rake teeth are arranged on an inclined plane of the engagement block; a fixed plate is arranged on the top surface of the engagement block; positioning shafts are arranged on the two sides of the fixed plate; a first high-pressure water spraying device is vertically arranged on the inner side of the movable cover; and a second high-pressure water spraying device is obliquely arranged at the outer end of the movable cover. The first high-pressure water spraying device and the second high-pressure water spraying device are matched with each other and spray water to each other, so that underwater soil blocks are loosened; meanwhile, the rake teeth are driven to move up and down; one section of notch is opened underwater, and hard sludge can be conveniently raked when the rake teeth rake the sludge, so that digging resistance of a rake head is reduced, and the digging capability and dredging efficiency of the rake head are improved; and the self-propulsion trailing suction hopper dredger has the effects of high sludge digging efficiency and low production cost.
Owner:ZHEJIANG UNIV OF WATER RESOURCES & ELECTRIC POWER
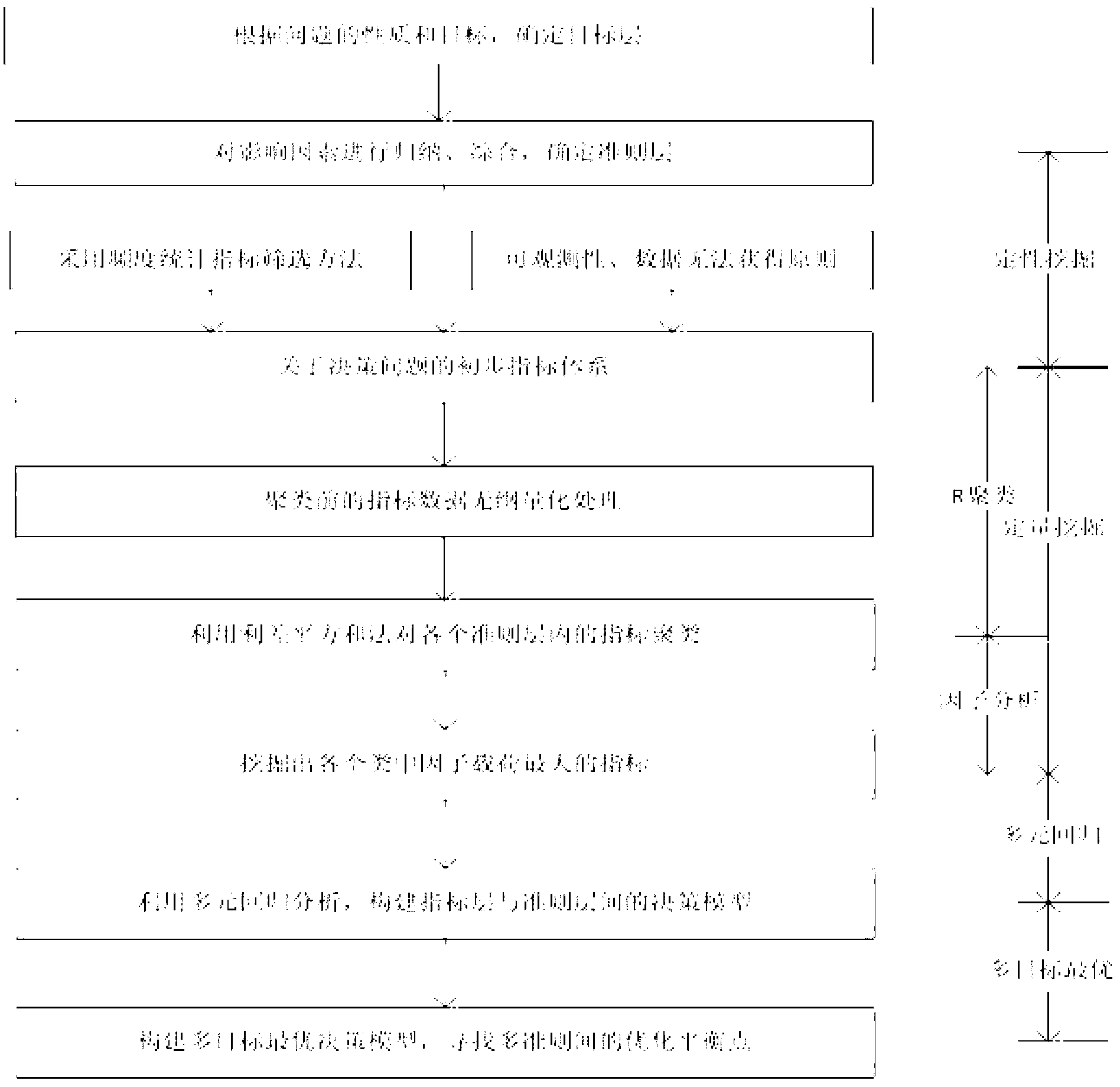
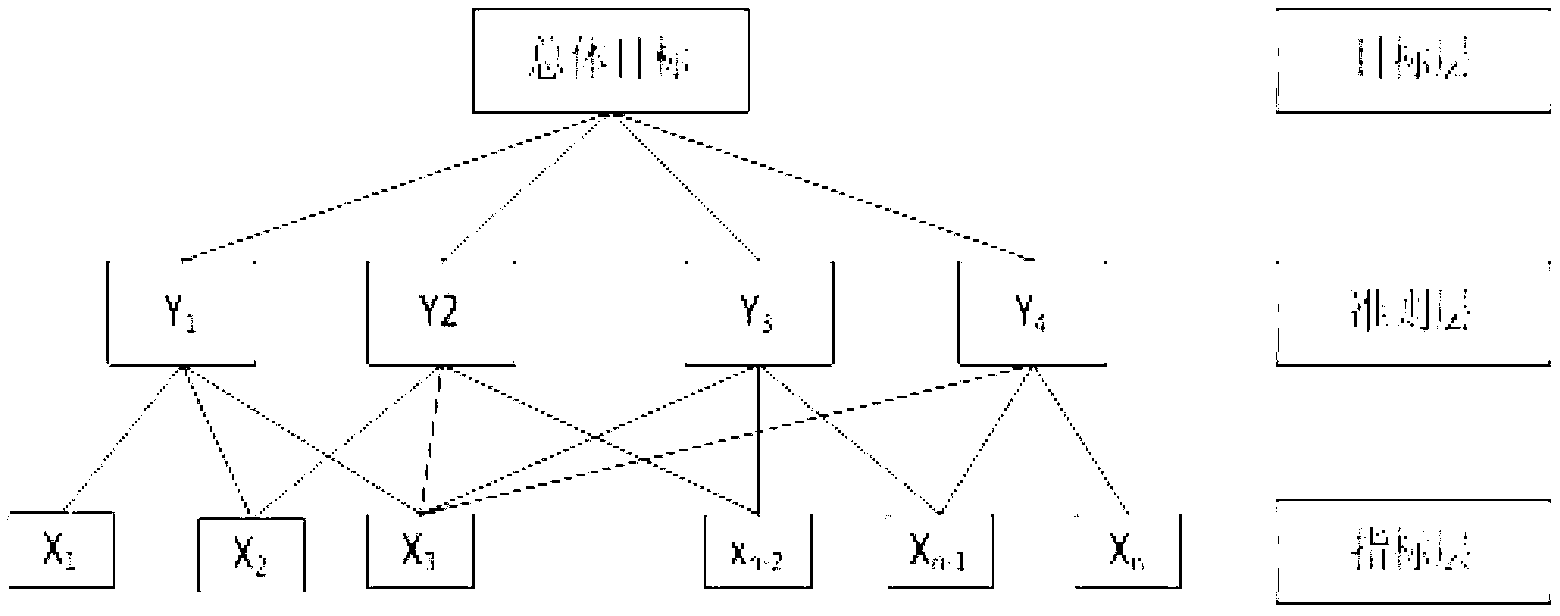
Electric power multi-objective decision support method based on intelligent data mining model
InactiveCN103295079AResolve duplicationAddresses failure to cover all aspects of reviewsForecastingDecision modelRegression analysis
The invention relates to an electric power multi-objective decision support method based on an intelligent data mining model. The method comprises the steps of enabling a decision maker to be clear on decision objectives and determine objective layers according to properties of practical problems; calculating all influence factors needing to be considered to achieve the objectives, performing induction and synthesis on the influence factors, and determining criterion layers; adopting a frequency statistical index screening method to perform mass election on all indexes under every criterion layer, and deleting indexes from which observed data cannot be obtained according to an observability principle; adopting the sum of deviation squares to cluster the indexes in every criterion layer; adopting a factor analysis method to analyze factor loads of every statistical index, reserving indexes with maximum factor loads in every kind of indexes, and screening out co-factor indexes between the multiple criterion layers; establishing decision models between indexes layers and the criterion layers on the basis of a multivariate regression analysis method; searching optimal balancing points between multiple criterions according to decision models of every criterion so as to achieve optimum of a final objective layer.
Owner:STATE GRID CORP OF CHINA +1
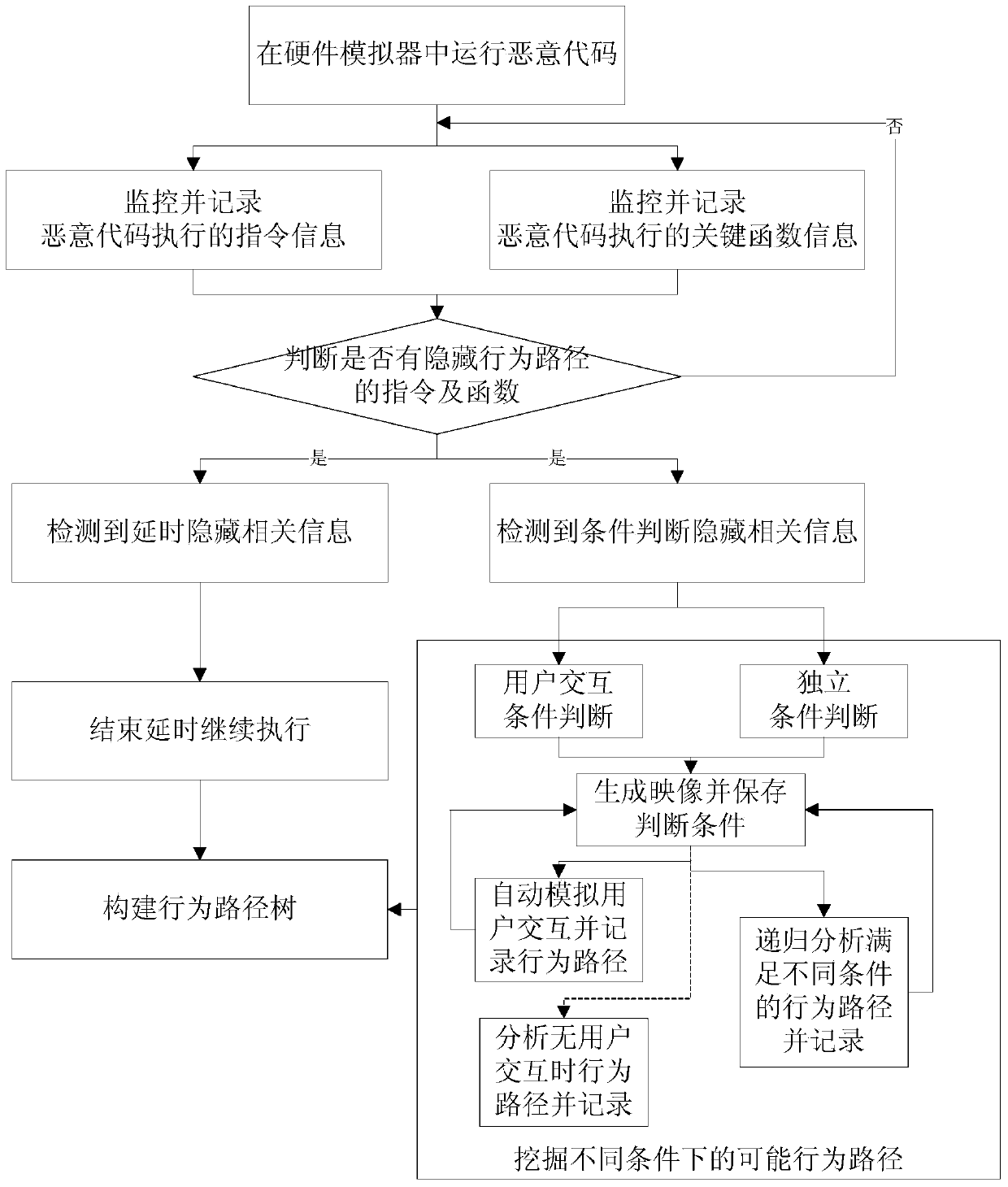
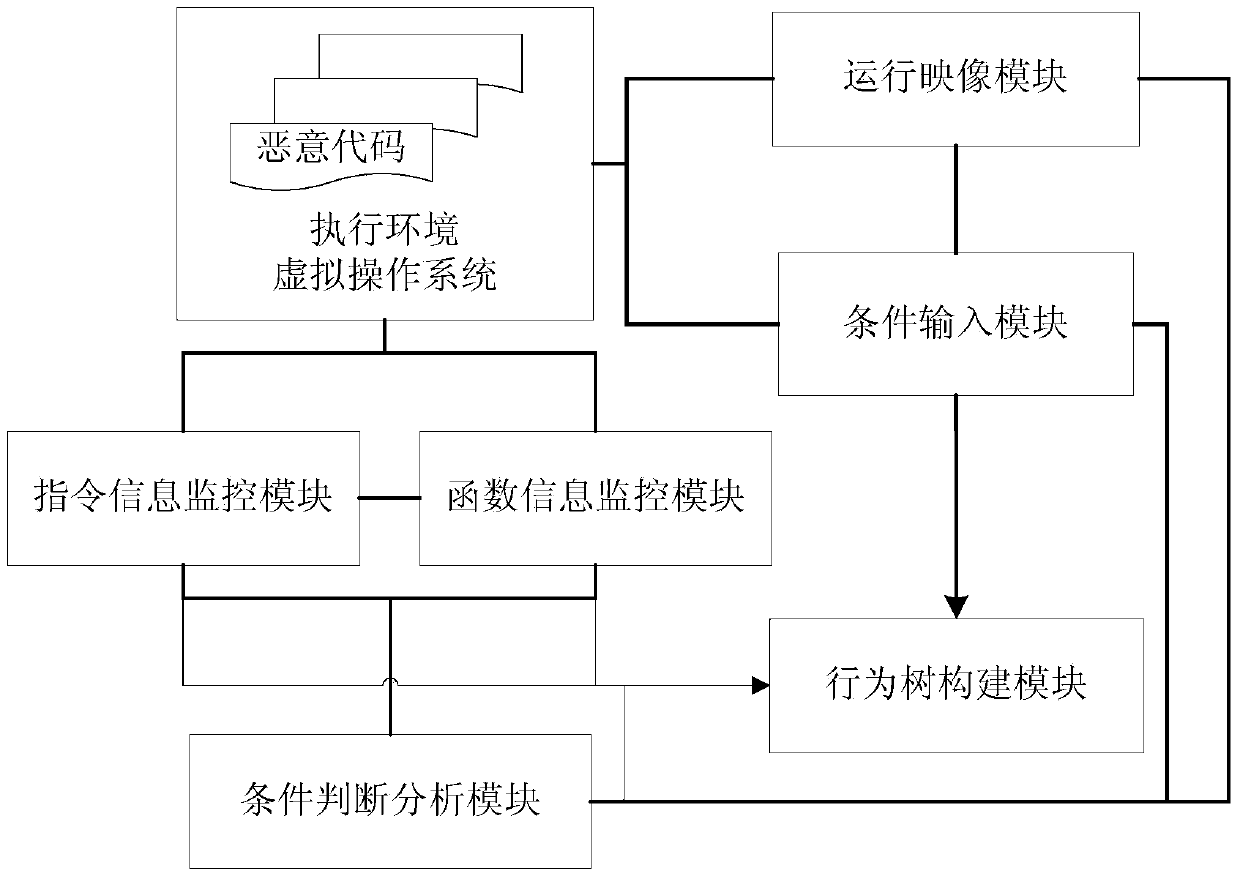
Mining method and system for malicious code hiding behaviors
ActiveCN103810427AImprove digging abilityPlatform integrity maintainanceBehavioral analyticsTime delays
The invention relates to a mining method and system for malicious code hiding behaviors. The method includes the steps that malicious codes are operated in a virtual environment; whether related instructions and functions related with hiding behavior routes are included in instruction information and function information executed by the malicious codes or not is judged; if execution information related with time delay hiding is detected, the malicious codes are made to continuously execute follow-up instructions and functions through ending corresponding time delay behaviors; if execution information related with conditional judgment hiding is detected, the execution information is classified according to conditional judgment, and possible execution routes of the malicious codes are mined through meeting execution conditions of different routes; analyzed various behavior route information executed by the malicious codes is used for generating a malicious code behavior route tree. The malicious code hiding behaviors avoiding analyzing in the modes of time delay hiding and conditional judgment hiding can be effectively mined, the various hiding behavior routes possibly existing are effectively found out, and the capacity for analyzing and mining the malicious code hiding behaviors is improved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
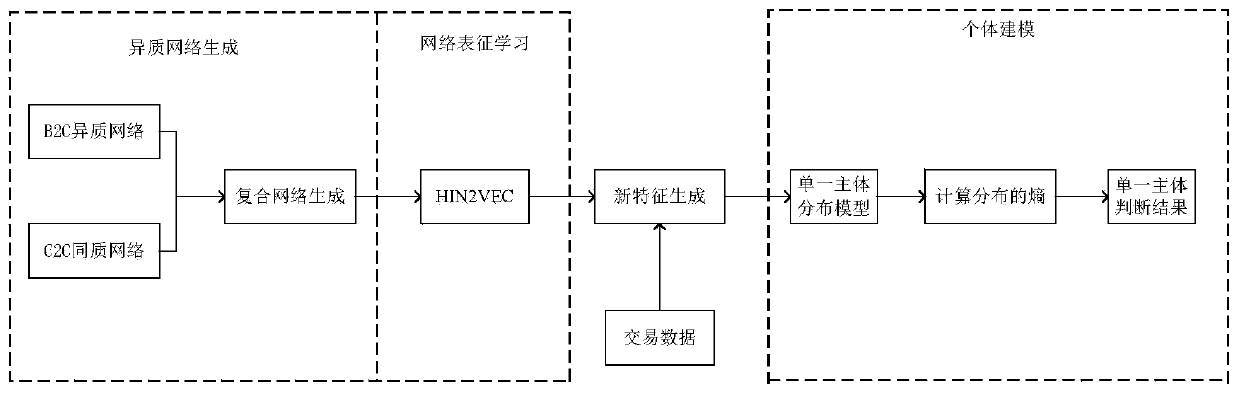
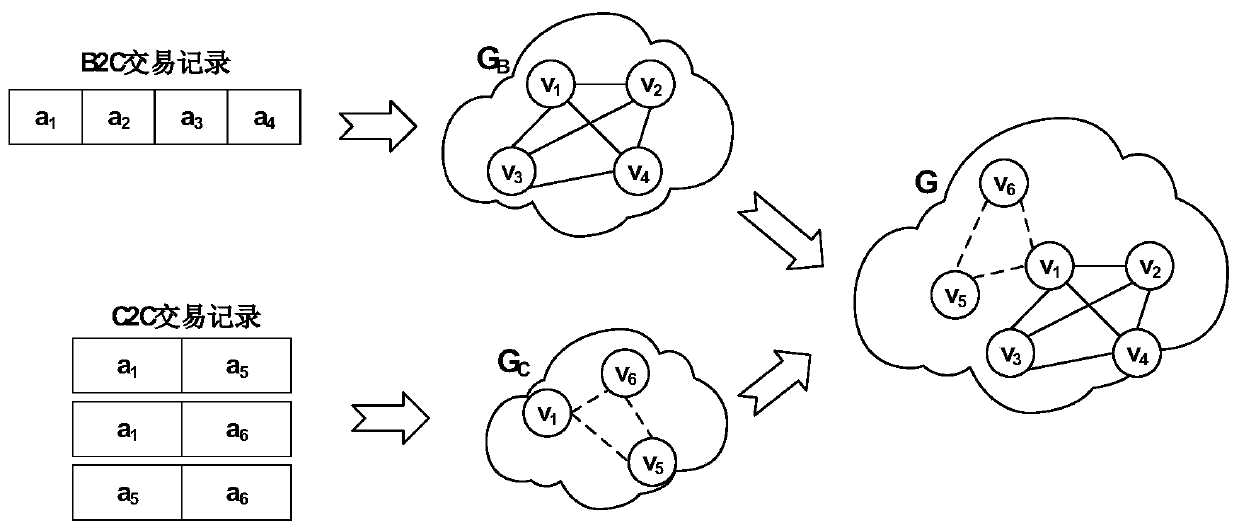
Online transaction-oriented fraud detection method based on individual behavior modeling
ActiveCN109754258AImprove digging abilityDetect Fraudulent Transactions GuaranteeProtocol authorisationSemantic tool creationData connectionRelational graph
The invention discloses an online transaction-oriented fraud detection method based on individual behavior modeling, and relates to anti-fraud detection of Internet financial network transactions. Themethod is divided into two parts: a first part, generating a heterogeneous information network by using a relational graph and obtaining a vector representation capable of mining a connection betweentransaction attributes by using heterogeneous network representation learning; And in the second part, under the condition that the vector representation of the node is learned, an individual behavior model is established, and the transaction abnormity possibility is predicted. The defects of a traditional fraud detection method are overcome, the mining capacity of the method for potential data connection is improved, and better guarantees are provided for detecting fraud transactions, intercepting the fraud transactions and protecting the fund safety of users and enterprises.
Owner:TONGJI UNIV
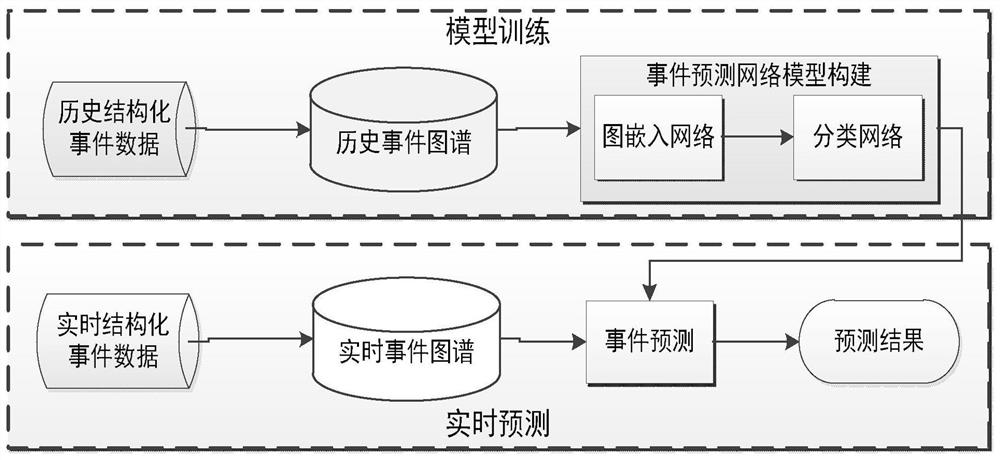
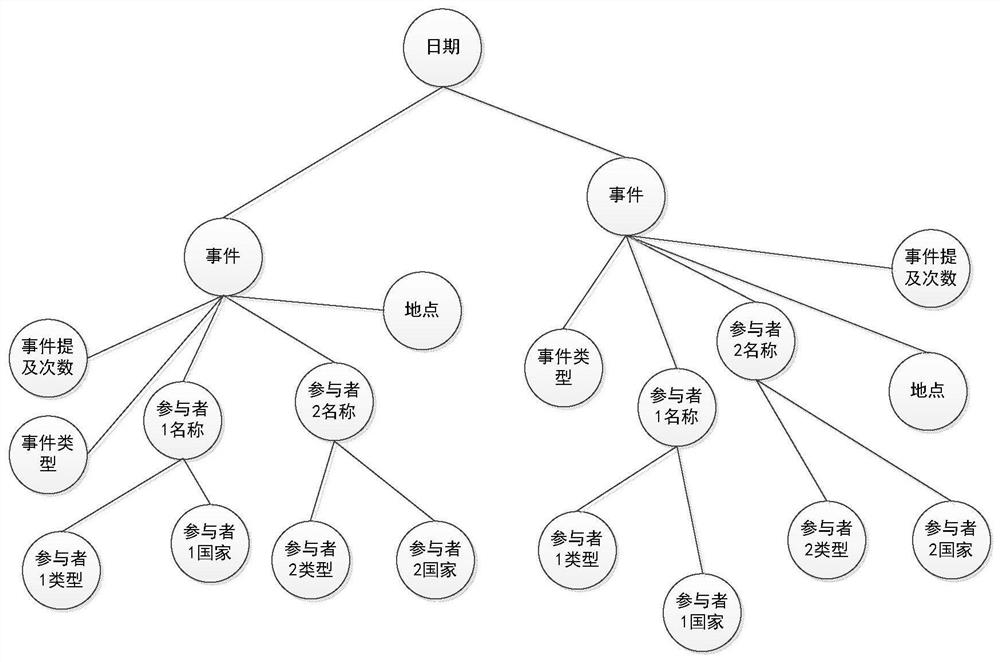
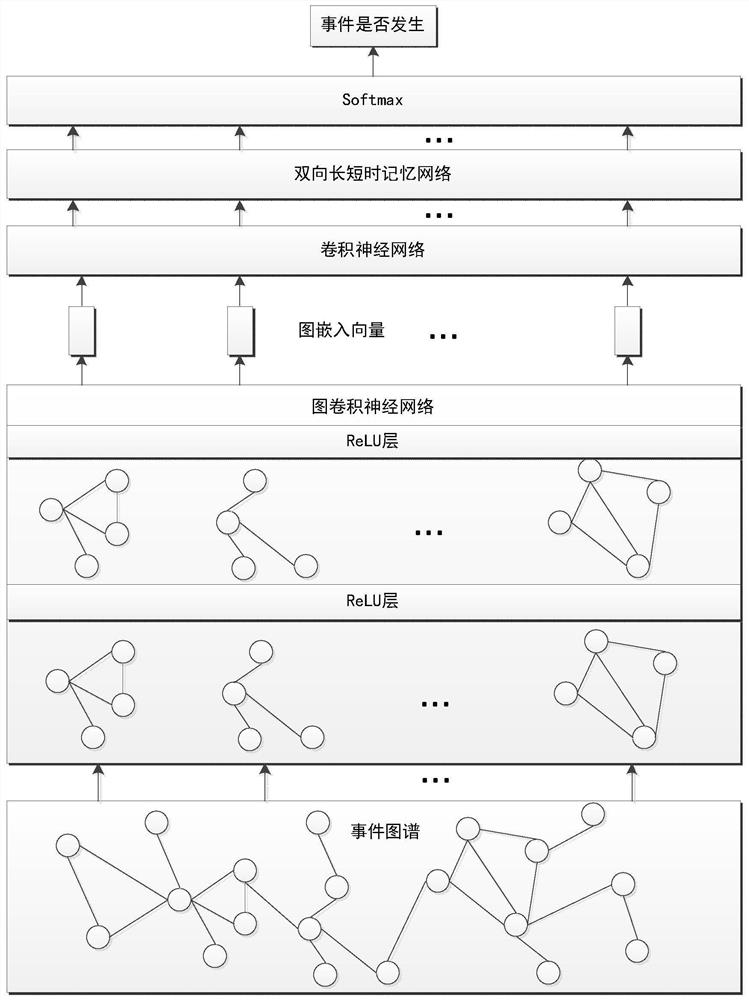
Method for predicting group events through event knowledge graph
The invention discloses a method for predicting group events through an event knowledge graph, and relates to the technology of event knowledge graph mining and application. The method is implementedthrough the following technical scheme: the method comprises two stages of prediction model training and real-time prediction; in the prediction model training stage, historical structured event dataare used as input data to construct a historical event graph, a graph embedding network is adopted to learn vectorized representation of the event graph, and then whether an event occurs or not is predicted based on a classification network model established by a deep neural network. In the real-time prediction stage, real-time structured event data are used as input data to construct a real-timeevent graph, the real-time event graph is used as input data of a trained event prediction model, the event graph constructed by the real-time event data is input into the event prediction model, vectorized representation of the event graph is obtained, and then deep semantic information of the event data is mined and is converted into a dichotomy problem that an event occurs or does not occur, and a result with the maximum probability is taken as a prediction result of whether the event occurs or not.
Owner:10TH RES INST OF CETC
Digging machine matched with tractor
The invention discloses a digging machine matched with a tractor. The digging machine comprises a drill spindle, wherein a spiral cutting blade is arranged on the drill spindle, a drill point is connected at the lower part of the drill spindle, a ground breaking blade which extends onto the drill spindle is arranged on the periphery of the drill point longitudinally, an earth and stone splashing prevention device covers the drill spindle. The digging machine can be matched with tractors with different models, so that persons can be liberated from heavy manual work, the labor intensity is reduced, and the digging machine can be widely applied to forest planting, fruit tree fence planting, and fertilizer applying to fruit trees in autumn; the digging machine has high digging ability, and is powerful, artistic in appearance and comfortable to operate, and is suitable for various terrains; and furthermore, the digging machine can prevent earth and stone from splashing when digging, so as to prevent the dug stones from splashing to shoes or bodies of workers and prevent splashed earth and stone from injuring persons.
Owner:昌邑市兴源铸造有限公司
Submerged arc welding process
The invention discloses a process for carrying out submerged arc welding on two plates with thicknesses of no more than 14 mm. The process comprises the following steps: after one part to be welded forms a groove, checking an assembling clearance between the two plates and making the assembling clearance satisfy requirements, fixing a gasket on the back face of an abutted part; enabling a variable speed submerged arc welding trolley to move along a welding joint at a constant speed; controlling a welding wire to swing backwards relative to the trolley in a reciprocating way at a constant speed in the direction of the welding joint when the welding wire on the trolley moves at the constant speed with the trolley; controlling the swinging amplitude of the welding wire, so that the swinging arc of the welding wire always falls within a range of a molten pool; and adjusting the height of the welding wire so as to guarantee that an electric arc can directly act upon the root of the groove when the welding wire is positioned at a swinging arc front point. According to the invention, the desired welding current is reduced, linear energy is also reduced, the expansion stress of the welding joint is reduced and cracks are uneasy to generate on a welding joint terminal; moreover, as the two sides of the side wall of the groove can be continuously heated by the electric arc, the deposition rate is increased, the production efficiency is increased, the electric quantity and the consumption of the welding material are reduced and the production cost is reduced.
Owner:GUANGZHOU SHIPYARD INTERNATIONAL LTD
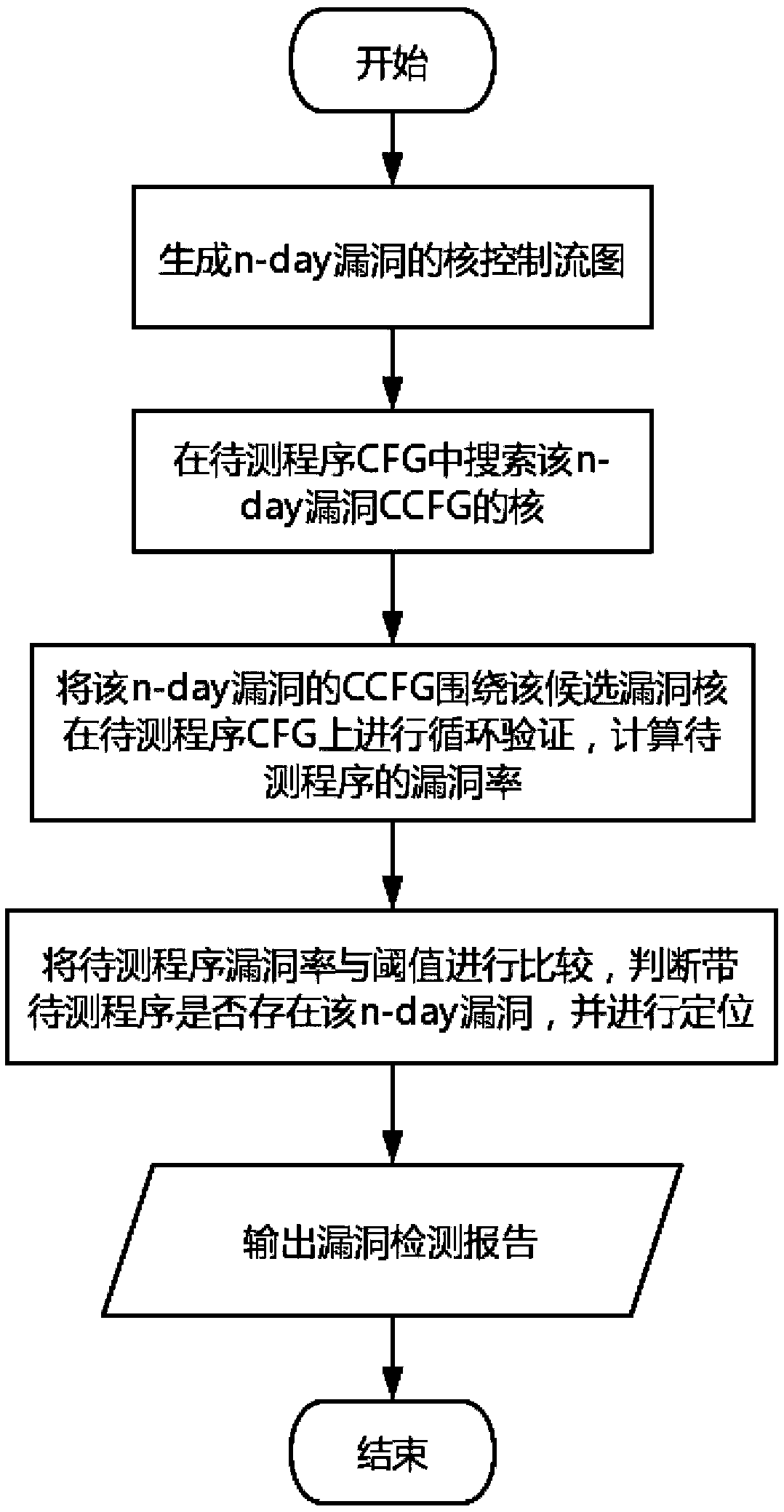
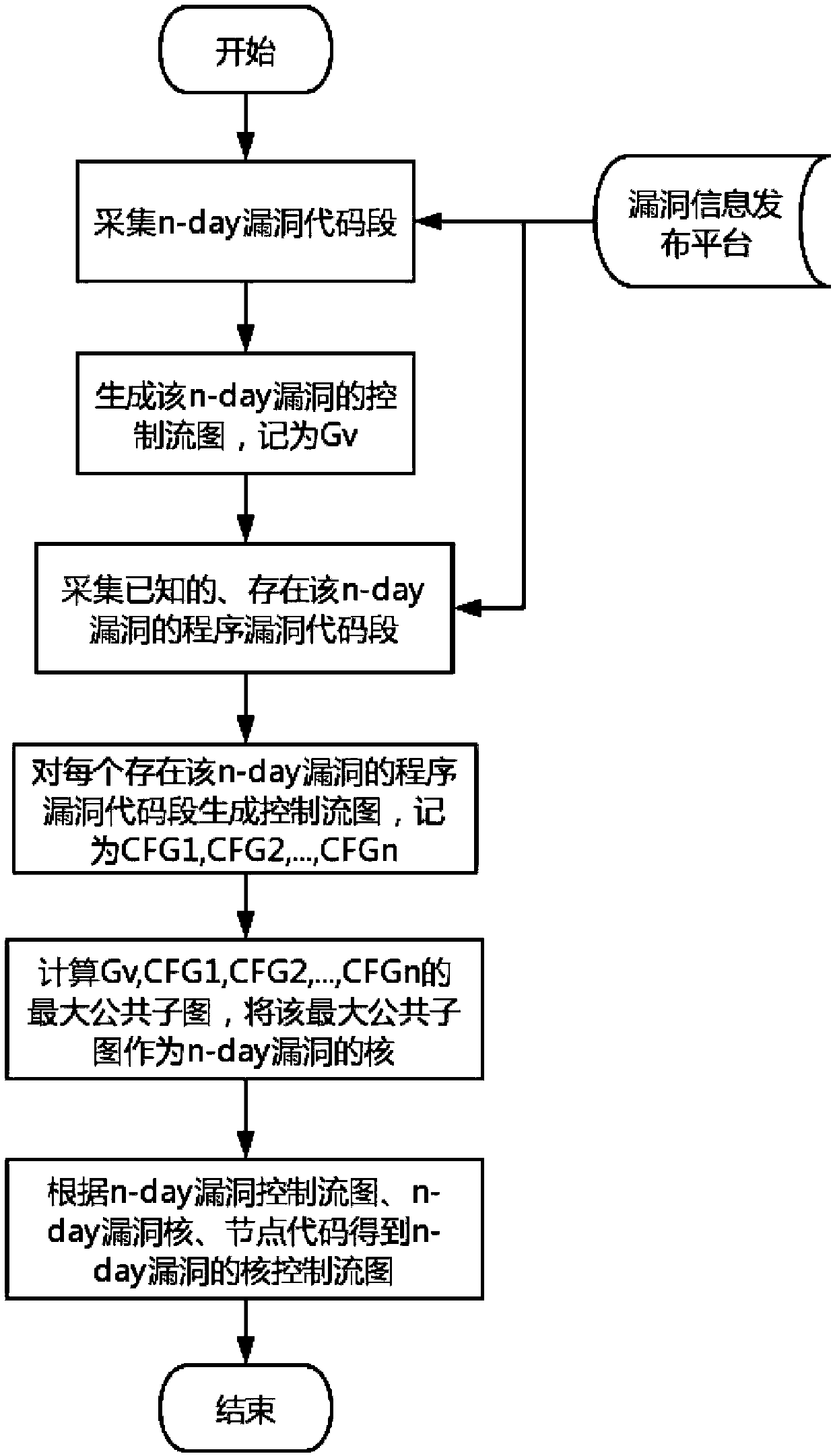
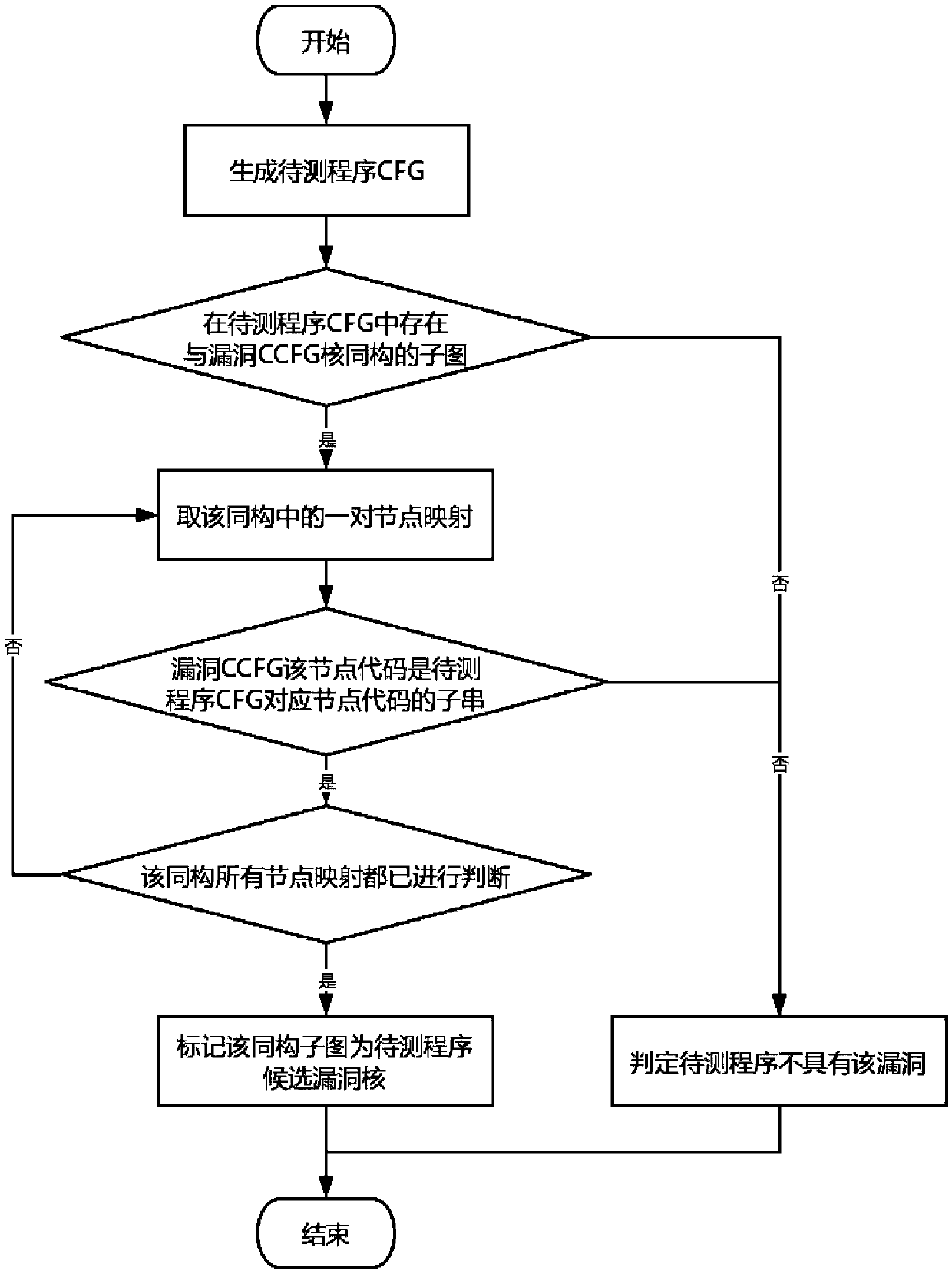
A vulnerability detection method based on kernel control flow graph cyclic verification
ActiveCN109670318AImprove accuracyImprove digging abilityPlatform integrity maintainanceComputer scienceSecurity bug
The invention relates to a vulnerability detection method based on kernel control flow graph cyclic verification. The method comprises the steps of 1) generating the CCFG of a n-day vulnerability; 2)generating a to-be-tested program CFG, and searching a core of the vulnerability CCFG in the to-be-tested program CFG; 3) circularly verifying the vulnerability CCFG around the core on the CFG of theprogram to be tested, and calculating the vulnerability rate of the program to be tested; and 4) comparing the vulnerability rate of the to-be-tested program with a threshold value, judging whether the vulnerability exists in the to-be-tested program, positioning the vulnerability according to the position of the candidate vulnerability core, and outputting a vulnerability retrieval report. The invention aims to solve the problem that the n-day vulnerability detection accuracy based on a control flow graph-based vulnerability detection method is not enough, and provides the concept and the technology of kernel control flow graph and cyclic verification and the complete vulnerability detection method based on kernel control flow graph cyclic verification. According to the present invention,the accuracy of the vulnerability mining personnel at the n-day vulnerability is improved, and further the security vulnerability mining capability is improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Trajectory data processing method and device, storage medium and equipment
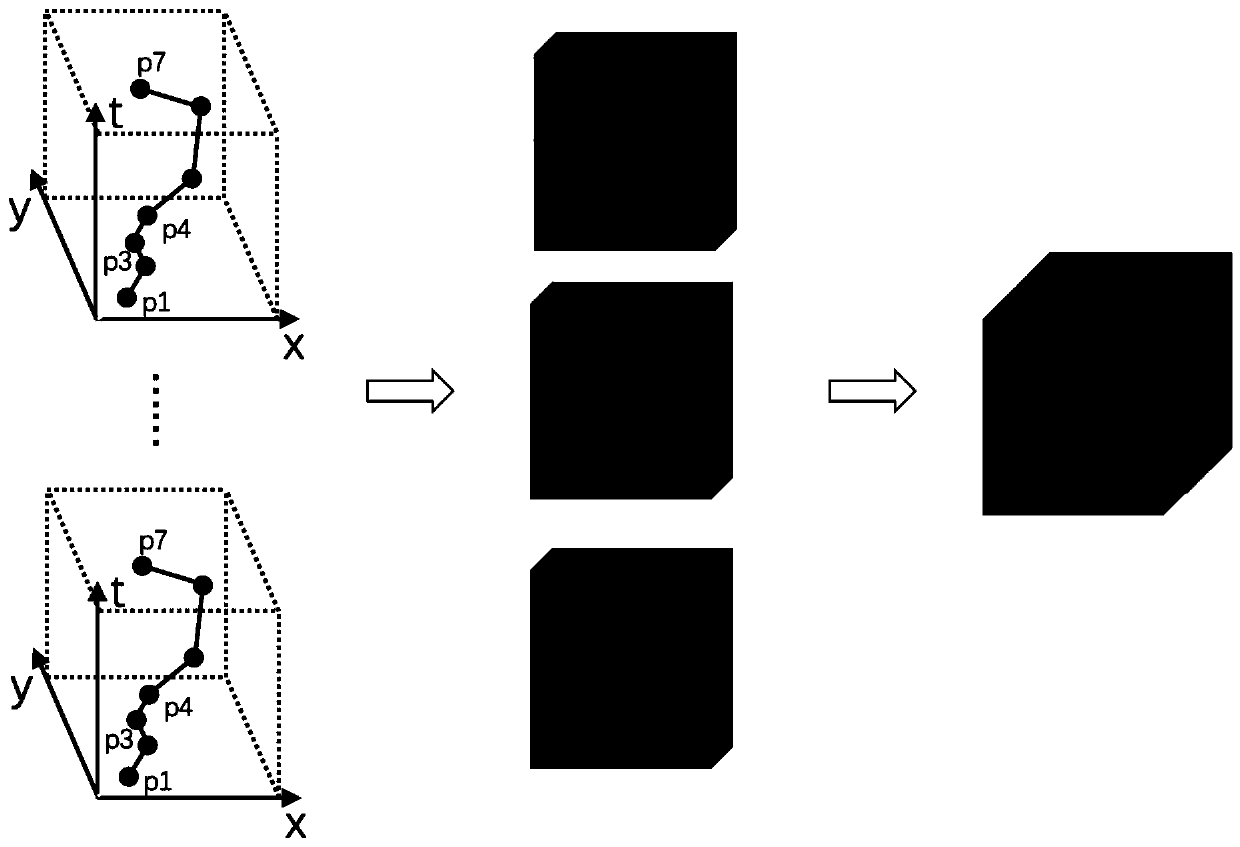
ActiveCN110428500AImprove digging abilityPreserve important feature informationImage enhancementImage analysisTraffic volumeMultiple dimension
The invention discloses a trajectory data processing method and device, a storage medium and equipment, and belongs to the technical field of networks. The trajectory data processing method comprisesthe following steps: acquiring trajectory data in a target geographic range, wherein the trajectory data comprises moving trajectories of a plurality of moving objects; generating a feature map layerof the trajectory data, wherein the feature map layer at least comprises a trajectory flow map layer, a moving speed map layer and a traffic direction map layer; performing fusion processing on each image layer included in the feature image layer, and displaying a fused feature image layer; and when a selection instruction for any pixel position on the fusion feature layer is obtained, displayingthe track flow at the pixel position, and the moving speed and the passing direction of the moving object. According to the trajectory data processing method, attribute information of multiple dimensions such as flow, speed and direction, is comprehensively considered in the trajectory modeling stage, and the motion mode of the moving object in the real world can be accurately mined, and the subsequent trajectory mining effect can be improved, and in addition, visual analysis can be carried out on the fused feature map.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Text excavating method of semi-structural document set
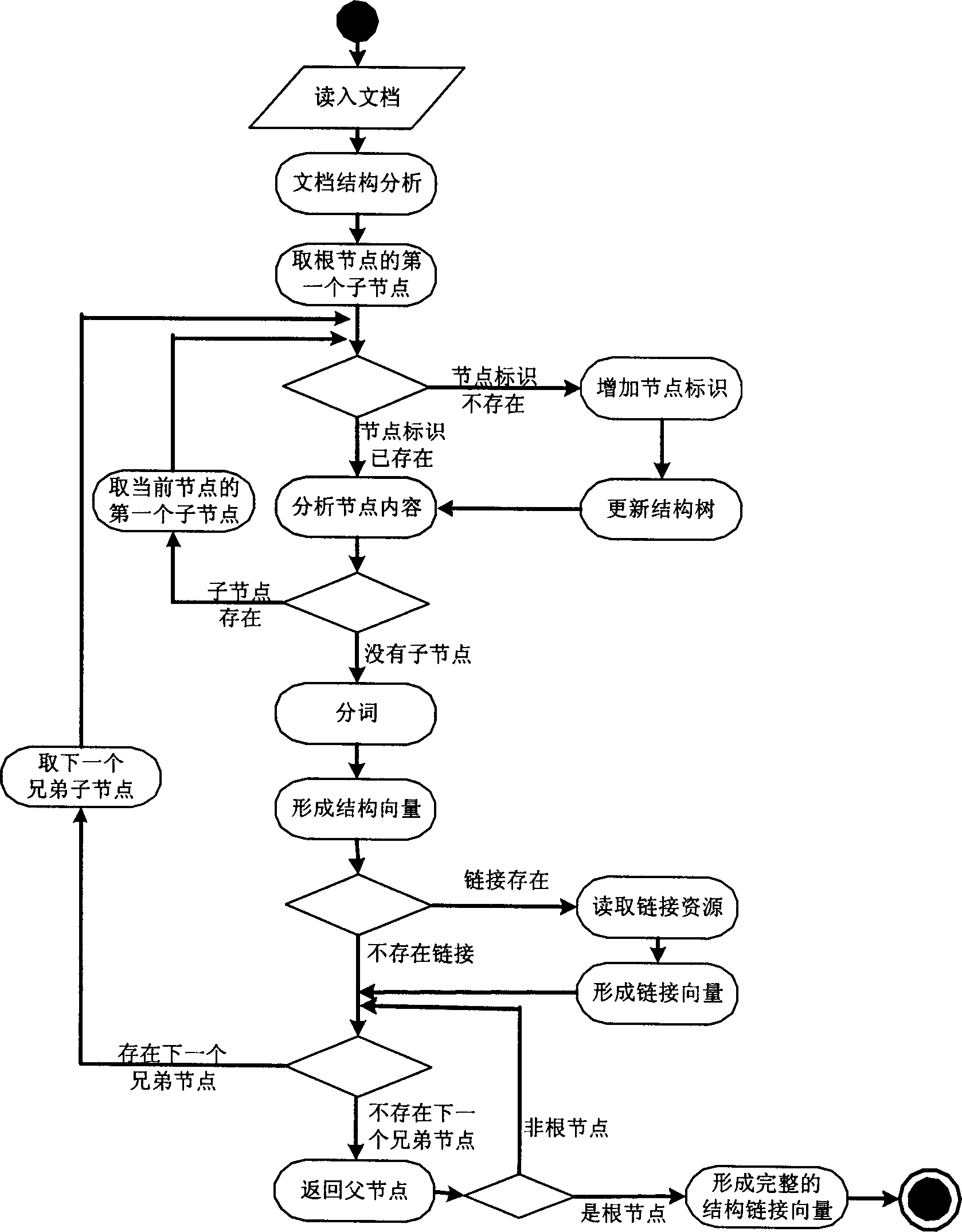
InactiveCN1399228AImprove digging abilityMathematical modelsSpecial data processing applicationsInformation processingText mining
The present invention belongs to intelligent information processing technology and especially relates to text excavating method of semi-structural document set. One excavating method to structural link vector model of semi-structural document is proposed. The said method can utilize comprehensively the word information, structure information and link information and express them in united mathematical model. The text excavating of semi-structural document set with the model can utilize the structure information and link information in semi-structural document, and thus has greatly improved excavating effect. The said method can be used widely in intelligent information processing.
Owner:PEKING UNIV +1
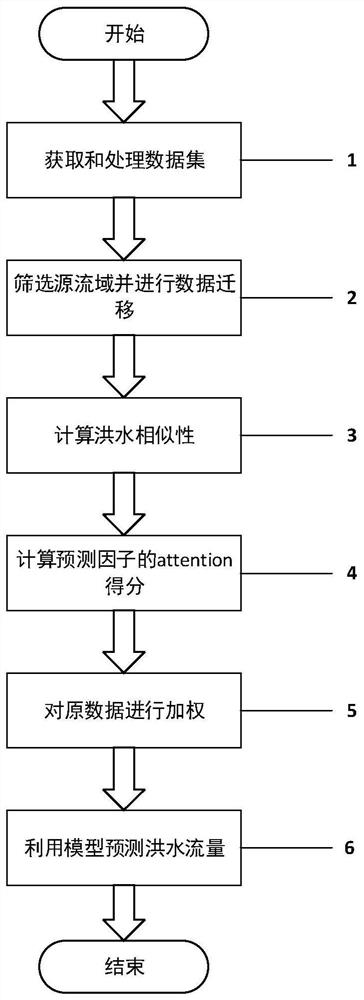
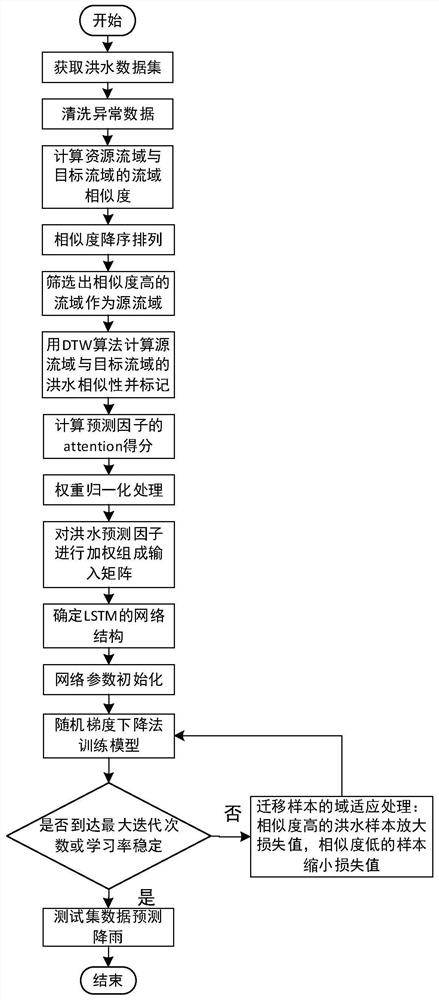
Flood prediction method and device based on long-short-term memory network and transfer learning
ActiveCN111915058AImprove abilitiesImprove forecast accuracyClimate change adaptationForecastingData migrationStream flow
The invention provides a flood prediction method and device based on a long-short-term memory network and transfer learning, and the method comprises the steps: screening a watershed with high similarity as a source watershed for data transfer through the cosine similarity calculation of the natural environment of the watershed after flood data information of a resource watershed is collected; calculating the flood similarity between a source watershed and a target watershed by using a DTW algorithm, forming an input matrix by using the calculated flood similarity and hydrological data as theinput of the model, and calculating weighted data by using an Attention mechanism, so that the model can better mine the information of important characteristic factors; and finally, inputting the weighted data matrix into an LSTM network to establish a flood prediction model, and predicting the future flood flow of the target watershed. According to the method, the characteristic of data shortagein a flood prediction problem of a specific watershed is overcome, the superior performance of the LSTM network for processing the time sequence problem is fully utilized, and flood prediction is more accurate.
Owner:HOHAI UNIV
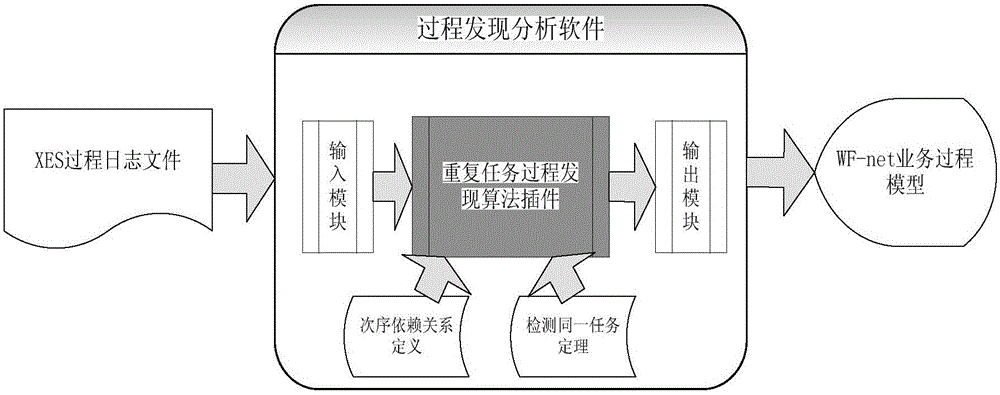
Repetitive task process discovery method based on equivalence class
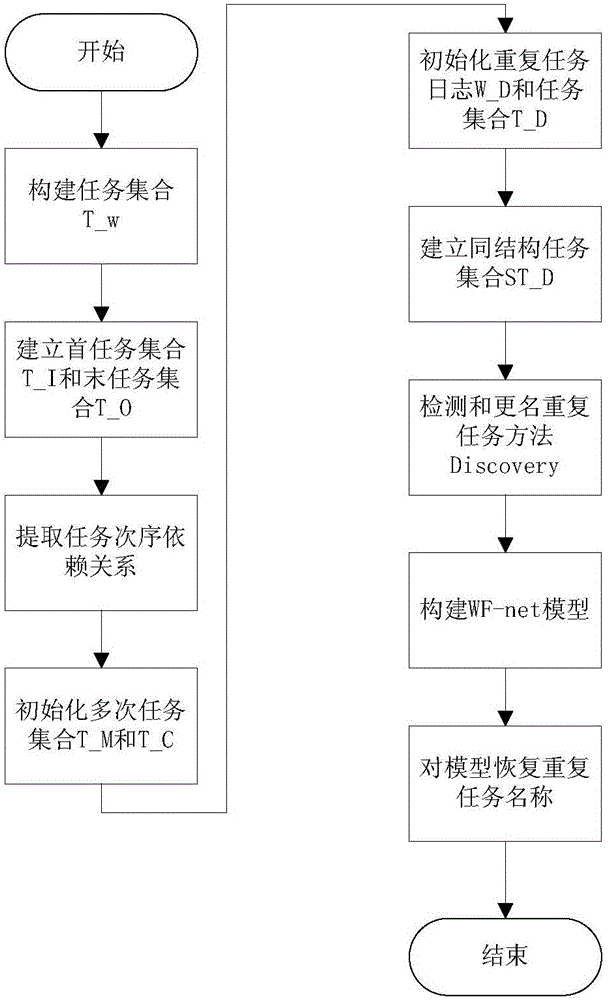
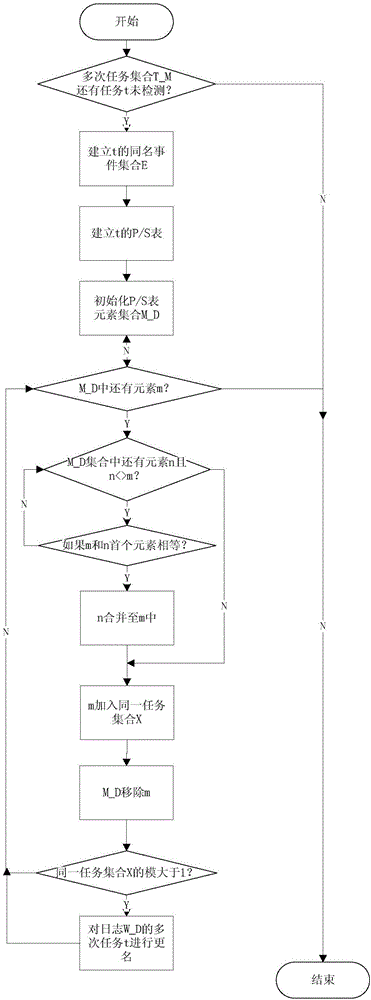
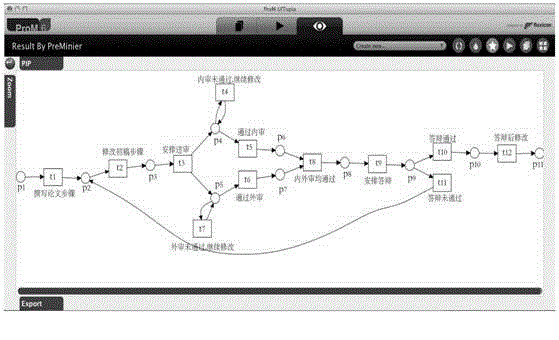
InactiveCN105117430AGuaranteed reasonablenessImprove digging abilitySpecial data processing applicationsRepetitive taskSoftware engineering
The present invention discloses a repetitive task process discovery method based on an equivalence class. The method comprises: by extending an event order relation definition, proposing a determination rule for the equivalence class to divide a same task subset; in a pre-processing stage, dividing events with the same names with a correct dependence order relation into a same task equivalence class subset; in a processing stage, discovering an algorithm to generate a WF-net (Workflow Petri net) model by using a short cycling process; and in a post-processing stage, renaming different same task subsets to eliminate repetitive tasks. According to the method, a standard service process XES file is first read, the dependence order relation definition and the determination rule are adopted to detect the repetitive tasks, and a service process model represented by adopting WF-net is output. The method has relatively good capability to solve the problem in discovery of multi-predecessor-successor repetitive task process with the short cycling structure, and can ensure a correct and reasonable mining result.
Owner:SUN YAT SEN UNIV
Predecessor task-based workflow mining method
ActiveCN104835015AImprove digging abilityResourcesSpecial data processing applicationsWorkflow modelData mining
The invention discloses a predecessor task-based workflow mining method. Tasks in an event log are analyzed, and a predecessor task in the event log of workflow is analyzed; the event log is taken as an input, and a workflow model described by a Petri network is taken as an output result; the method uses the predecessor task-based event log as an input of a current task, i.e., the event log contains information of the predecessor task, and the predecessor task refers to a set of tasks that need to be completed before execution of the current task; the formalized definition of the event log of the predecessor task is that T is a task set, T* is a task sequence containing n tasks, and E=[theta]T is an event set on the bases of the task set T; and the predecessor task sequence ix expressed as sigma is an element of a set E*, and the event log of the predecessor task is expressed as WE*. The invention provides a novel mining method in theory, and realizes practical tools both on an Activiti platform and a ProM platform.
Owner:NANJING UNIV
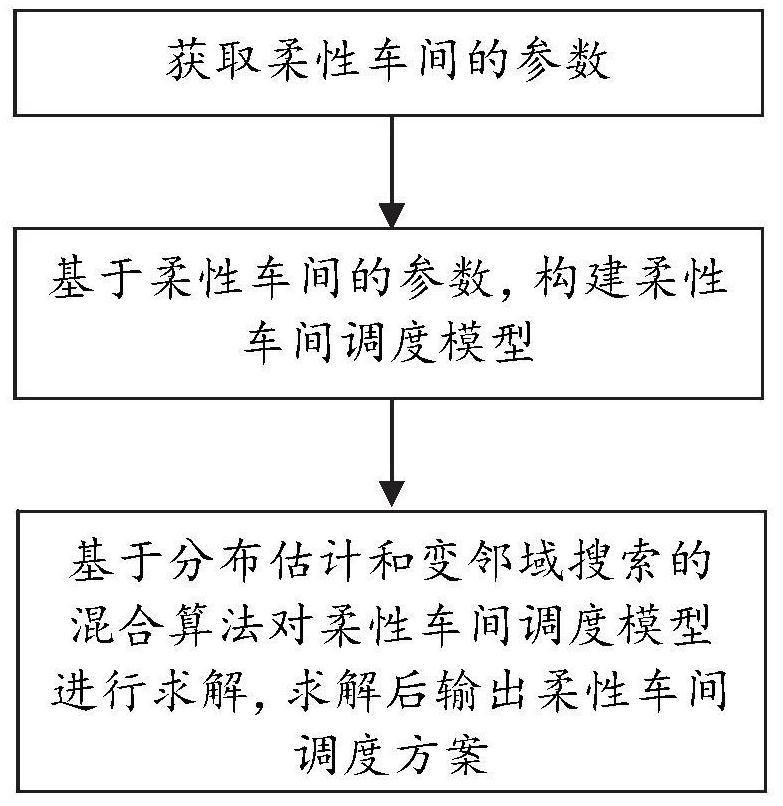
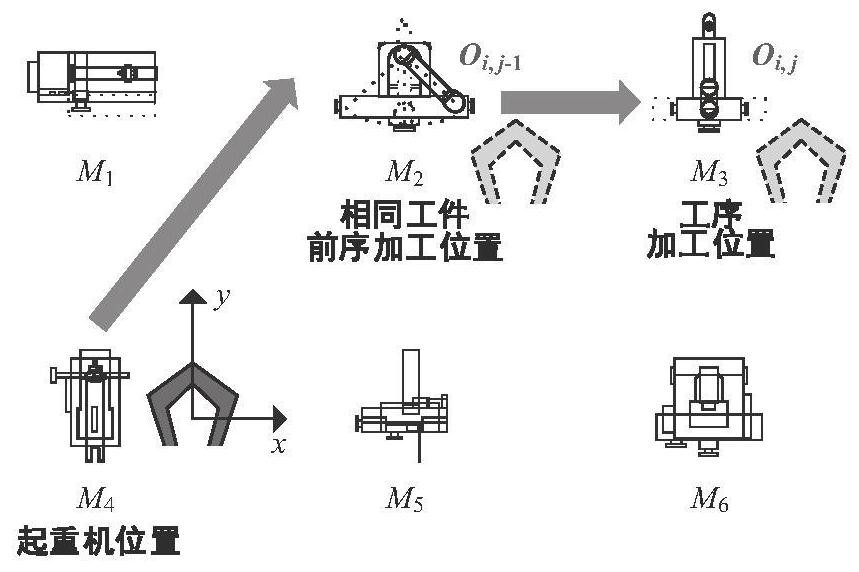
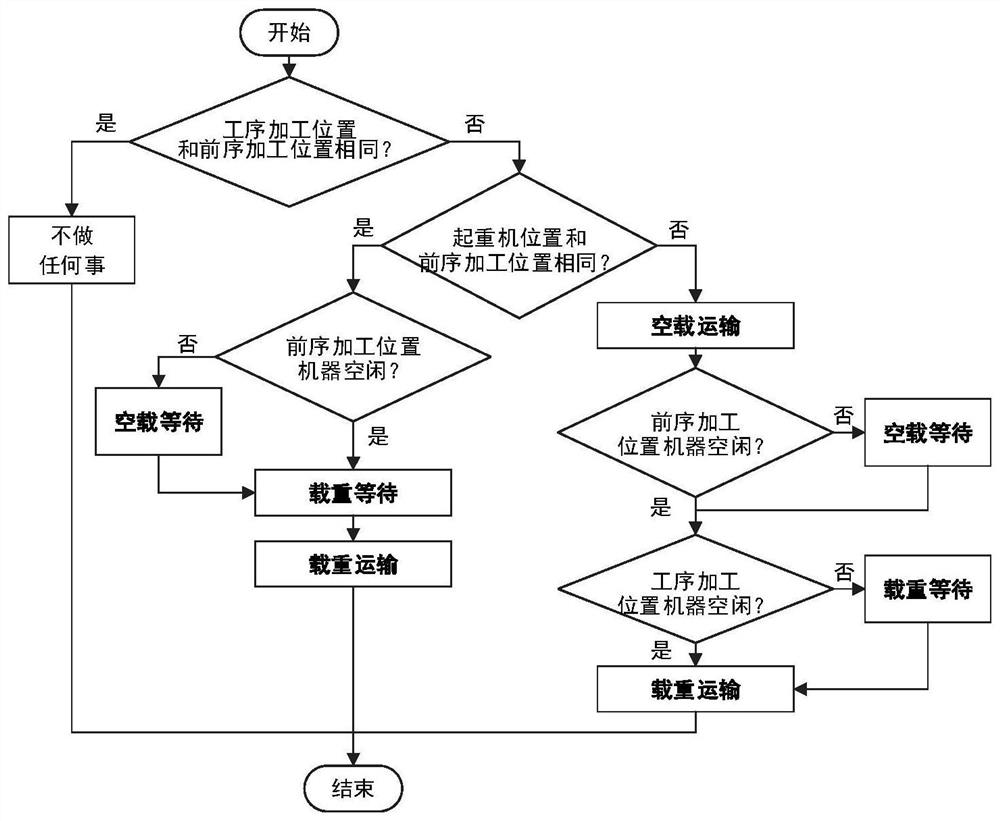
Flexible workshop scheduling optimization method and system considering crane transportation process
PendingCN112286149ASmall maximum completion time and total energy consumptionImprove the efficiency of processing and transportationTotal factory controlProgramme total factory controlHybrid algorithmMachining process
The invention discloses a flexible workshop scheduling optimization method and system considering a crane transportation process. The method comprises the following steps: obtaining the parameters ofa flexible workshop, wherein the parameters comprise the number of machines in the target factory, the number of workpieces, the machining process corresponding to each workpiece, the machining machine corresponding to each process, the machining time of the workpieces and the position coordinates of the crane; constructing a flexible workshop scheduling model based on the parameters of the flexible workshop, wherein the flexible workshop scheduling model aims at minimizing the maximum completion time and the total energy consumption; and solving the flexible workshop scheduling model based ona mixed algorithm of distribution estimation and variable neighborhood search, and outputting a flexible workshop scheduling scheme after solving, wherein all individual solutions in the output solutions of the flexible workshop scheduling model are arranged according to the increasing sequence of fitness values. According to the invention, a hybrid algorithm of distribution estimation and variable neighborhood search is provided to solve the flexible workshop scheduling problem, so that the factory production efficiency is improved.
Owner:SHANDONG NORMAL UNIV
Quantum fuzzy machine learning countermeasure attack model method
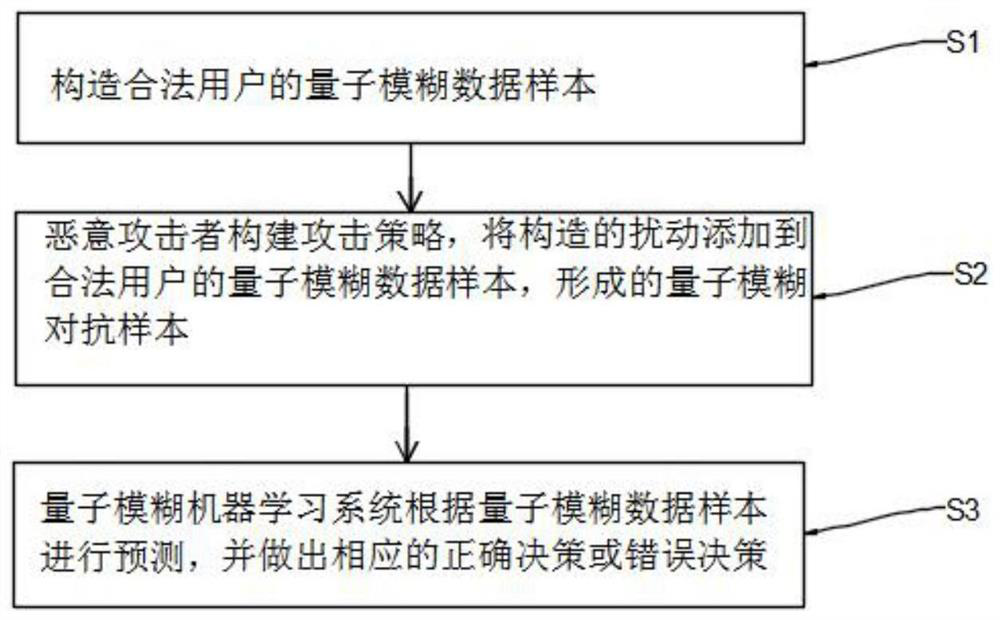
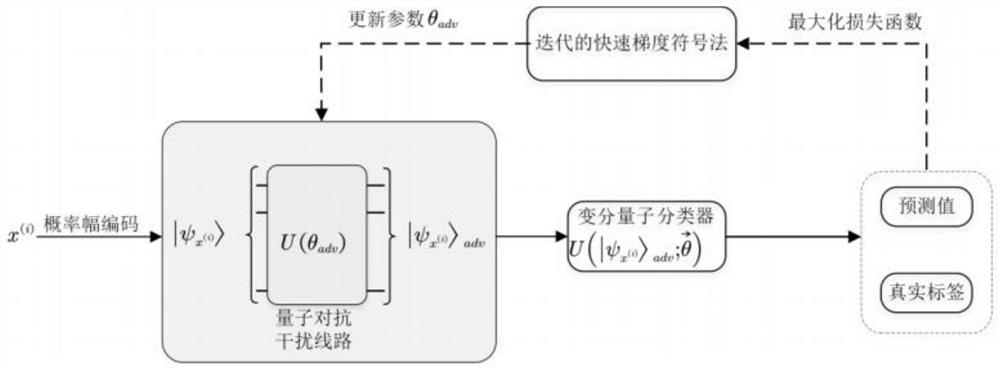
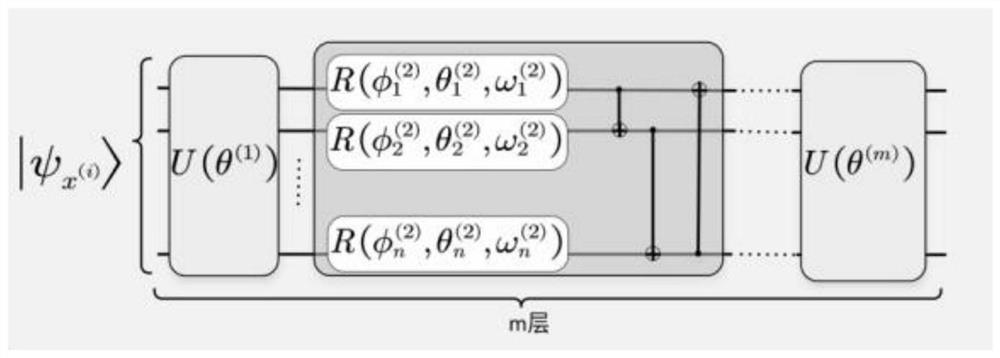
PendingCN112381232AGuaranteed uptimeImprove securityQuantum computersMachine learningAttack modelAlgorithm
The invention relates to the technical field of quantum machine learning, fuzzy set theories and network confrontation, and provides a quantum fuzzy machine learning confrontation attack model method.The method comprises the steps: S1, constructing a quantum fuzzy data sample of a legal user; S2, constructing an attack strategy by a malicious attacker, and adding the constructed disturbance intoa quantum fuzzy data sample of a legal user to form a quantum fuzzy confrontation sample; S3, enabling the quantum fuzzy machine learning system to perform classification according to the quantum fuzzy adversarial samples and make corresponding correct decisions or error decisions; wherein when the quantum fuzzy adversarial sample is a quantum fuzzy data sample of a legal user, a correct decisionis made; when the quantum fuzzy adversarial sample is a sample constructed by a malicious attacker, an error decision is made, the attack purpose is achieved, the defects of vulnerability and many defects of a quantum fuzzy machine learning algorithm are overcome, and safety and robustness are improved.
Owner:CHENGDU UNIV OF INFORMATION TECH
Vibration nipper for heavy machinery
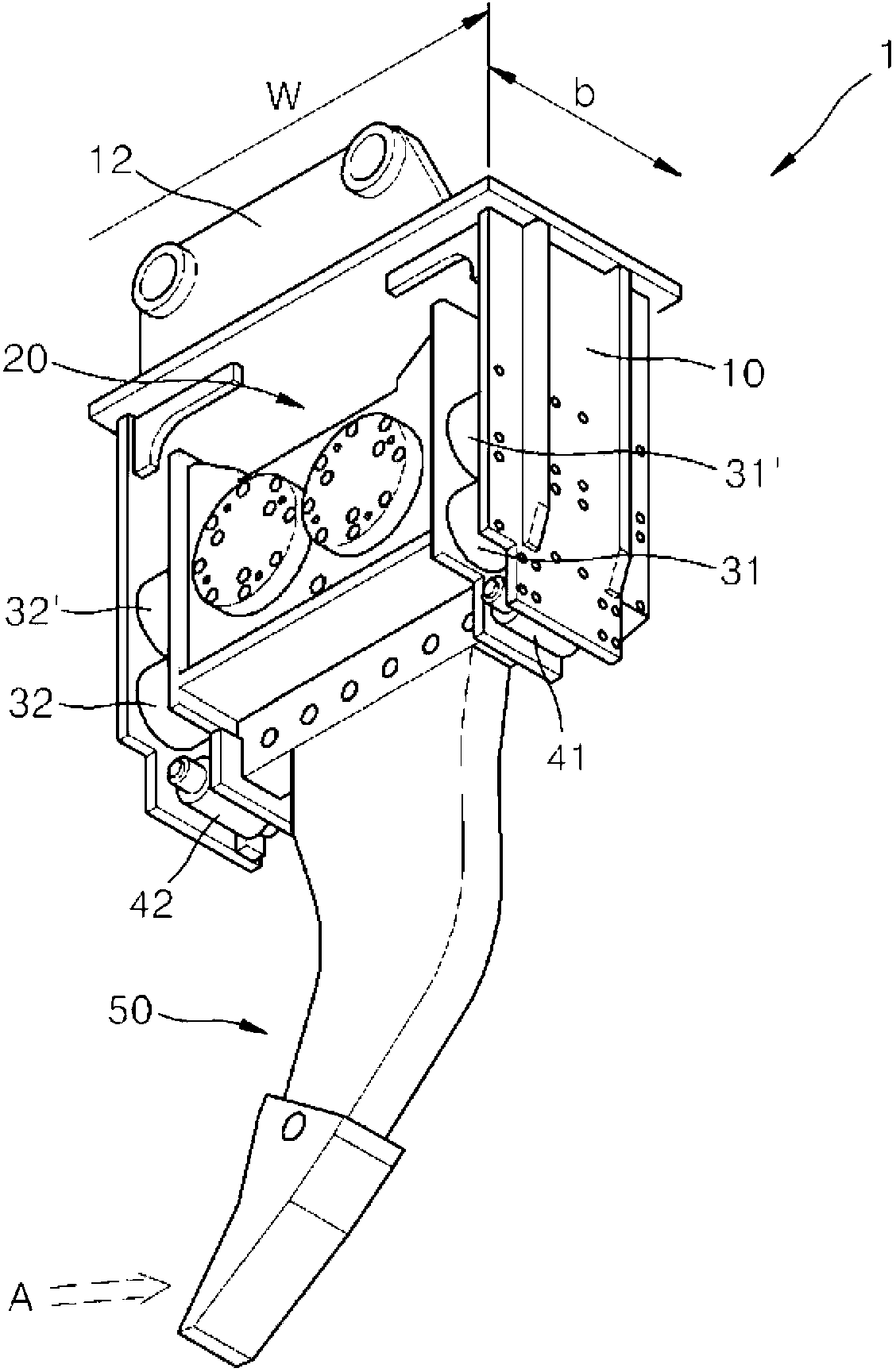
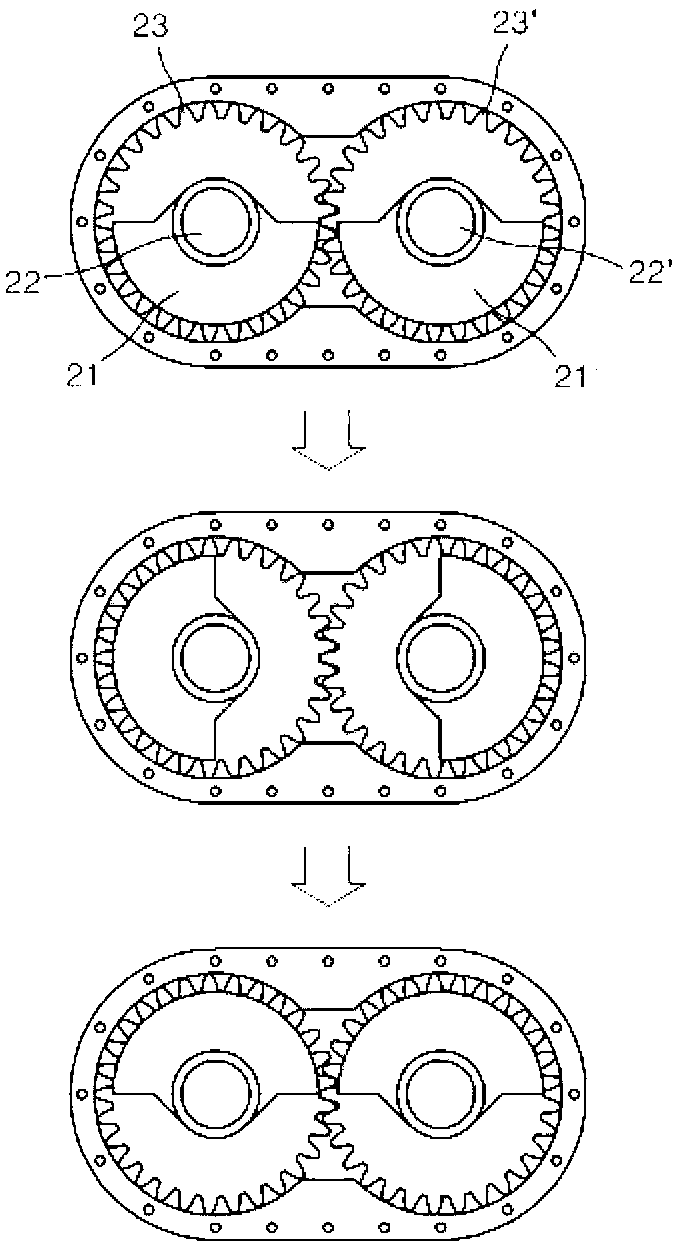
InactiveCN102844500AIncreased durabilityNarrow widthMechanical machines/dredgersElectric machineryHydraulic motor
The present invention relates to a vibration nipper for heavy machinery, wherein a plurality of gears incorporated in a vibration main body and having eccentric weights are aligned in the vertical direction and generate vertical vibration while rotating. Provided is a vibration nipper for heavy machinery, comprising a vibration main body, which gears inside for rotating by a hydraulic motor are aligned in the vertical direction and disposed to be rotatable. The respective gears are mounted with eccentric weights for generating vertical vibration during the rotation of the gears. The vibration main body is mounted with a nipper blade at the lower portion thereof in the longitudinal direction of the vibration main body, so that the vibration main body may be inserted deep into the ground along with the nipper blade at the time of underground excavation. According to the present invention, it is possible to produce the vibration main body in narrower width than existing ones, so that a frame may be produced with reduced width. Therefore, even though the nipper blade is inserted into the ground, the vibration main body may be inserted deep into the ground along with the nipper blade, so that the depth of excavation may be deepen and the performance of excavation may be largely improved. In addition, according to the present invention, even though the nipper blade is applied with excavation resistance in the lateral direction from the ground when the nipper blade excavates the ground, the supporting structure of the nipper blade is improved in the lateral direction by connecting the nipper blade and the vibration main body via a link structure which is displaceable in the vertical direction with respect to the frame. Therefore, the operation of the nipper blade is free and a buffering member for supporting the vibration main body is protected from being damaged, exhibiting much improved durability.
Owner:赵在龙 +1
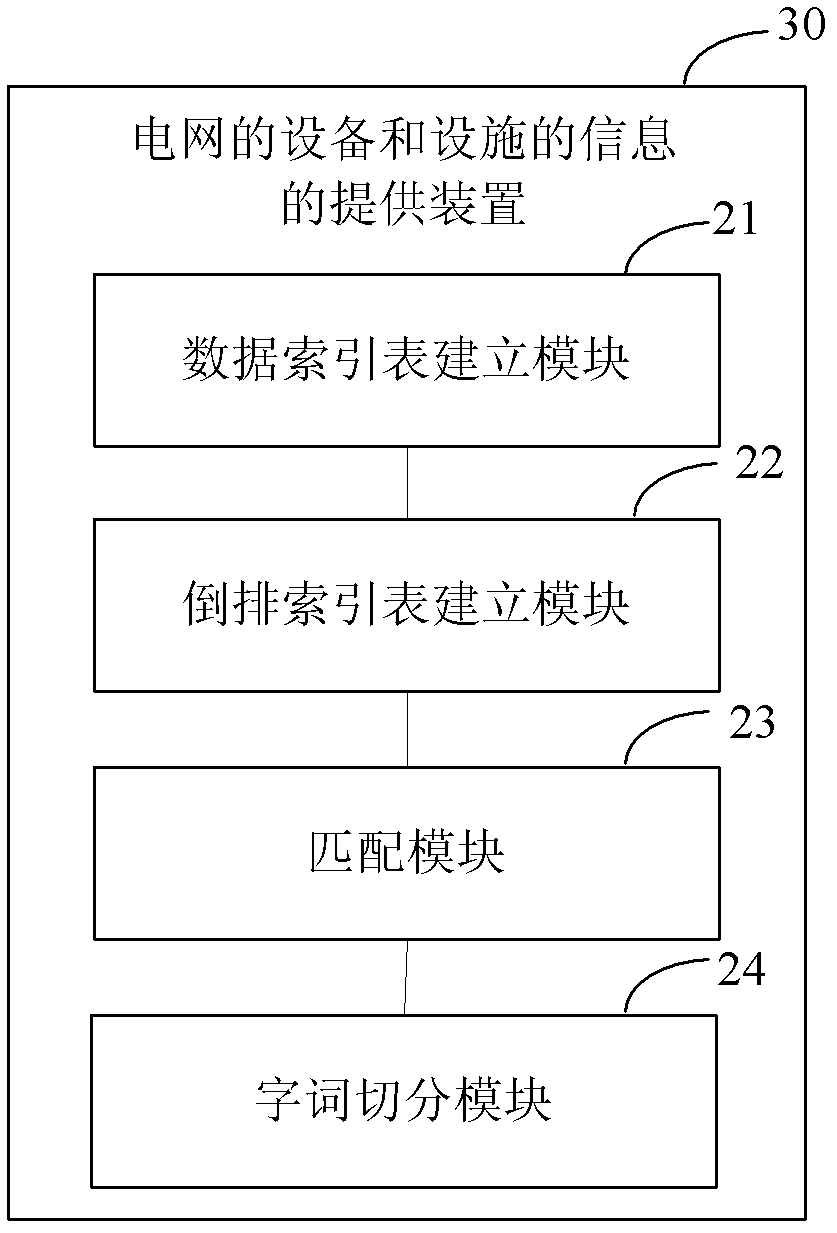
Power grid device and facility information providing method and device
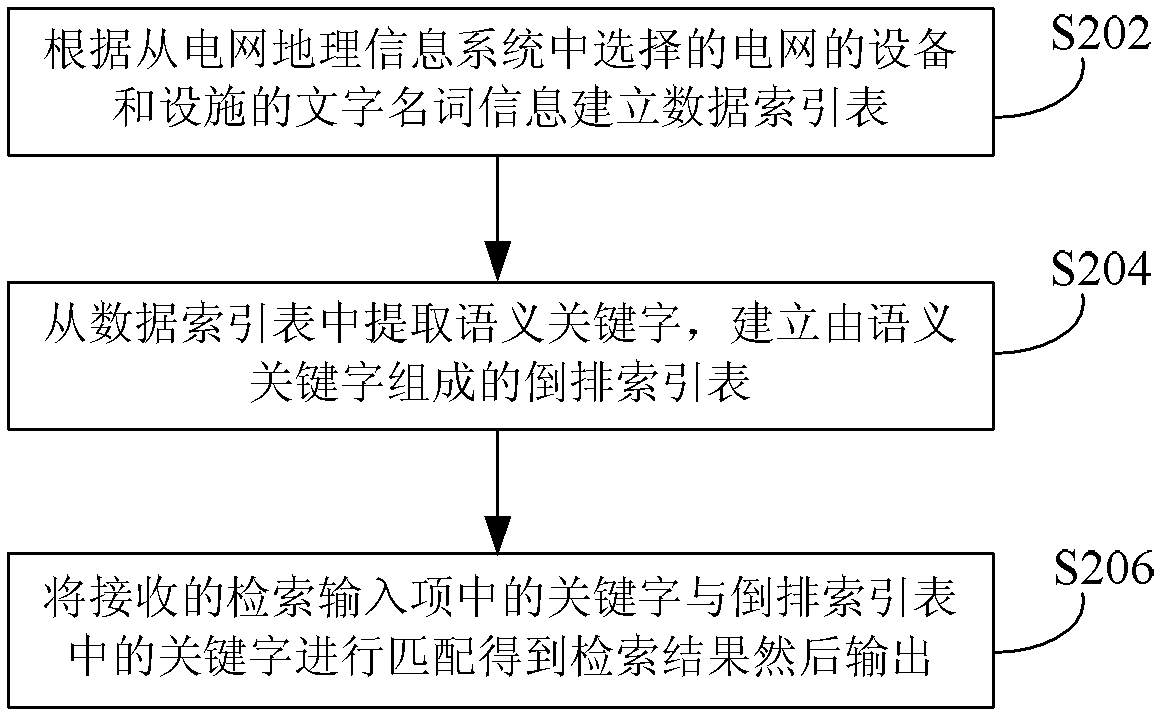
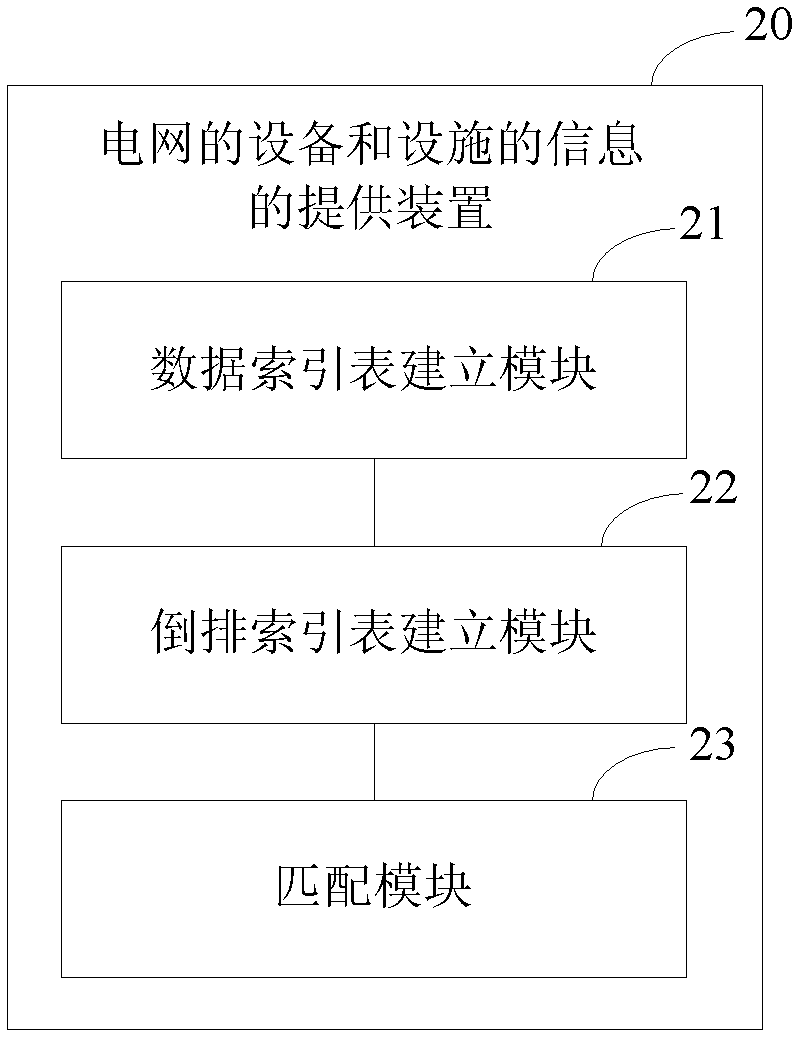
ActiveCN103377229AImprove digging abilitySolve the problem of low operating efficiencySpecial data processing applicationsFuzzy queryPower grid
The invention provides a power grid device and facility information providing method and device to solve the problem of low information retrieval operation efficiency in fuzzy query in a power grid geographic information system (GIS). The method includes building a data index table according to word noun information of a power grid device and facility selected from the power grid GIS, extracting semantic key words from the data index table, building a reverse index table composed of the semantic key words, matching received key words in a retrieval input item and the key words in the reverse index table to obtain a retrieval result, and outputting the retrieval result. By means of the method, retrieval efficiency can be improved, and intelligent searching of power grid resources is further achieved.
Owner:STATE GRID CORP OF CHINA +1
Automatic digging device for tree transplantation
InactiveCN109673464AImprove digging efficiencySave human effortForestryRemote controlElectric machinery
The invention provides an automatic digging device for tree transplantation. The automatic digging device comprises a tree ring, fixed pin plates, chutes, side chutes, a nozzle, a built-in telescopicrod, a digging motor, a digging gear disc, a storage battery, a remote control device, a triangular earth collector, a rack lever, a triangular groove and a side groove hole, wherein two groups of fixed pin plates are integrally arranged at the bottom of the outer end of the tree ring; through holes are formed in two sides of the fixed pin plates; the chutes are formed in the middle of the top ofthe tree ring, and the side chutes are formed in two sides of the chutes; a connecting groove and a connecting block are respectively arranged at two ends of the tree ring; two groups of screw holes are formed in the connecting groove; and two groups of through holes are formed in the middle of the connecting block. Due to the arrangement of the chutes, slide blocks and moving wheels, rotary moving ability is provided for the digging device, the moving position of the digging device is limited, the digging device is ensured to move according to a desired track, the digging efficiency is effectively improved, and the manual labor is greatly saved.
Owner:商可凡
Method for recommending next position of campus user based on space-time attention network
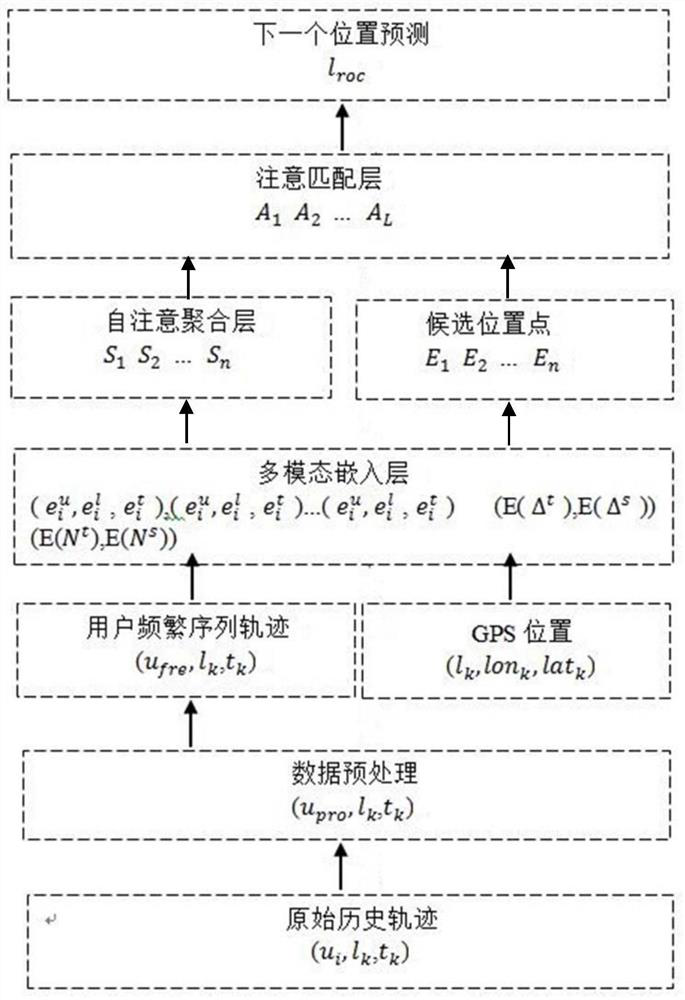
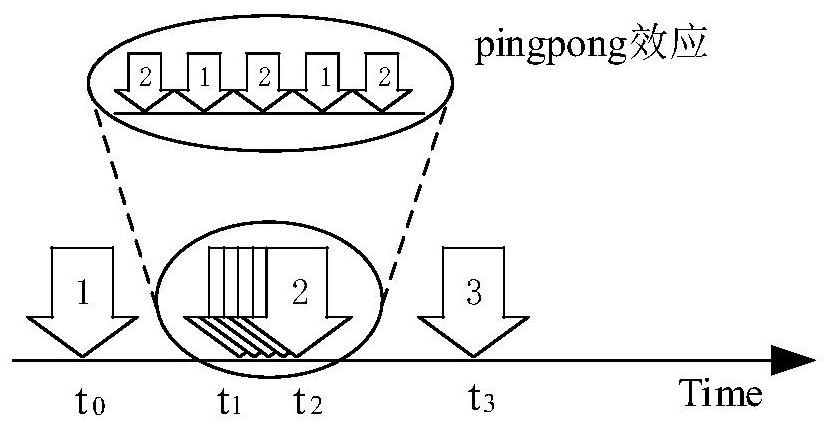
PendingCN113505310ASolving the pingpong effectImprove digging abilityDigital data information retrievalSpecial data processing applicationsPersonalizationReverse order
The invention discloses a method for predicting the next position of a campus user based on a space-time attention network, and the method comprises the steps: employing an SMM algorithm with track data preprocessing according to the distribution characteristics of a time sequence, removing abnormal data through a segmentation merging and adaptive adjustment method, and solving a large number of pinpong effects of track data; mining a sequence mode by adopting a frequent item set in a reverse order, and iteratively removing a redundant item set through the mined sequence mode set to obtain a to-be-mined sequence mode set; dividing the whole historical track of the user into a plurality of time windows, learning the user number, the position number, the sign-in time and the space-time effect of each piece of historical data, and converting into vector representation to construct a multi-modal embedded layer; constructing a self-attention aggregation layer, aggregating important related positions in a user track, and capturing expression of sign-in of each time of long-term dependence updating; and constructing an attention matching layer. According to the method, the database is greatly compressed, the track mode mining performance is improved, and the personalized prediction recall rate is effectively improved.
Owner:LIAONING TECHNICAL UNIVERSITY
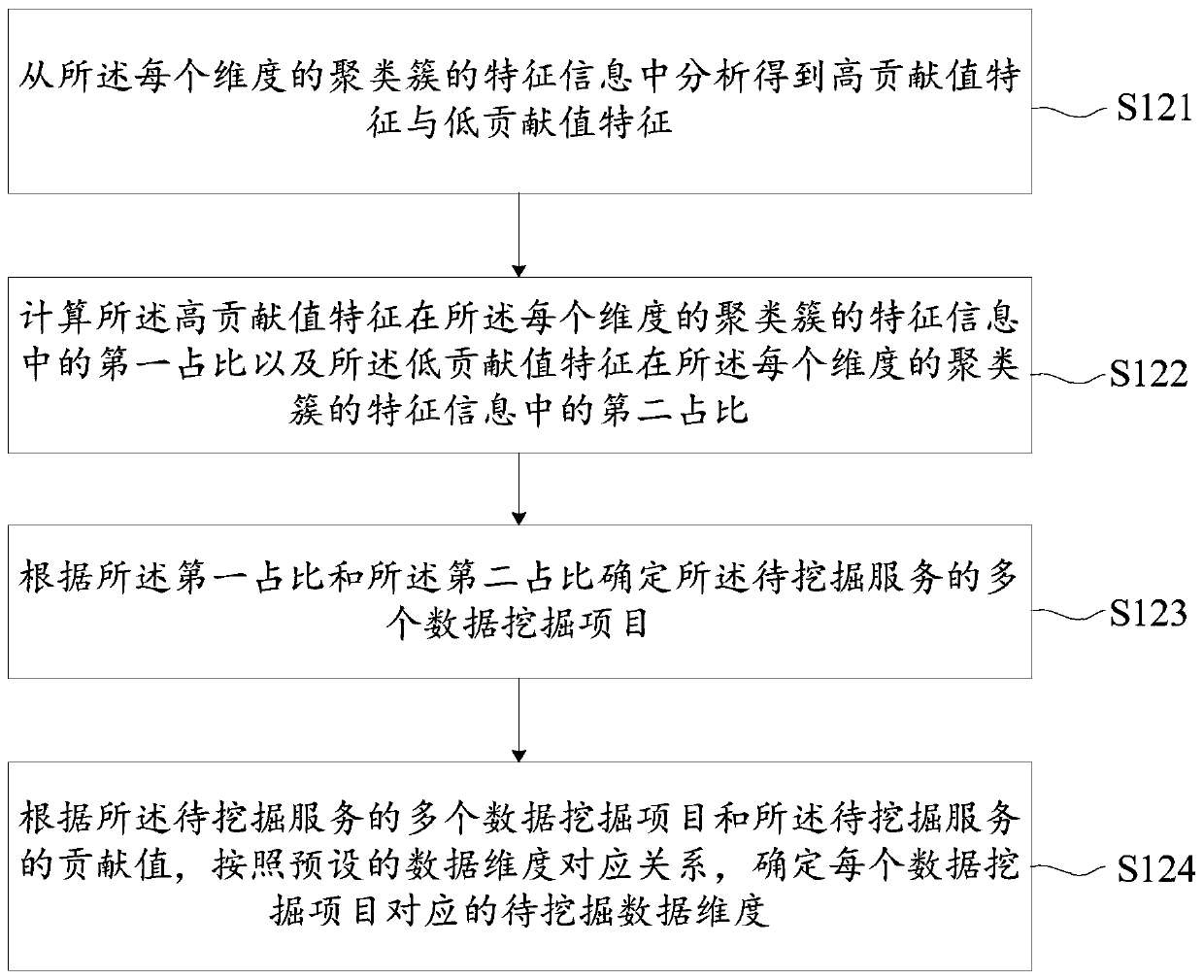
Big data mining method and device and data mining server
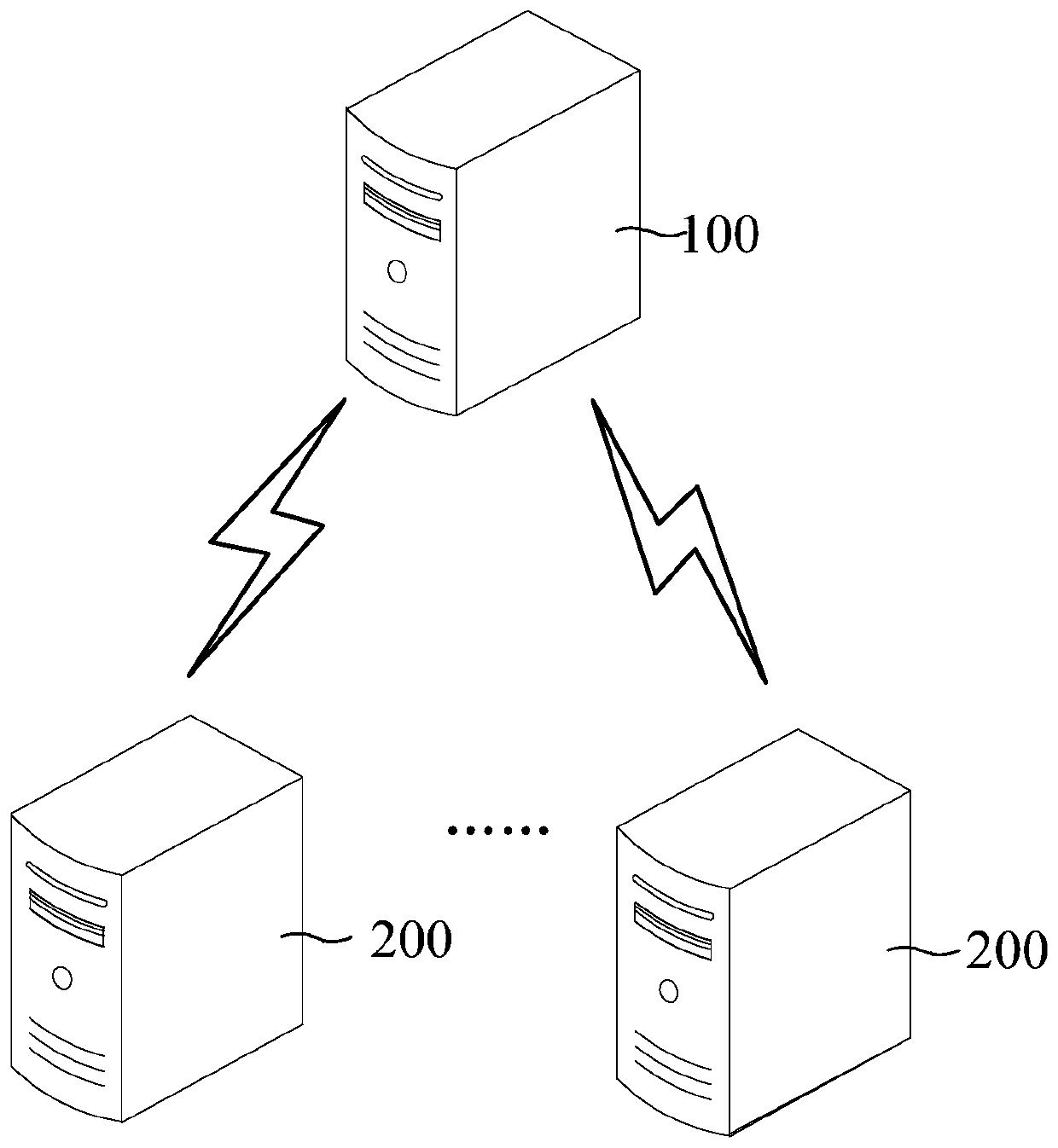
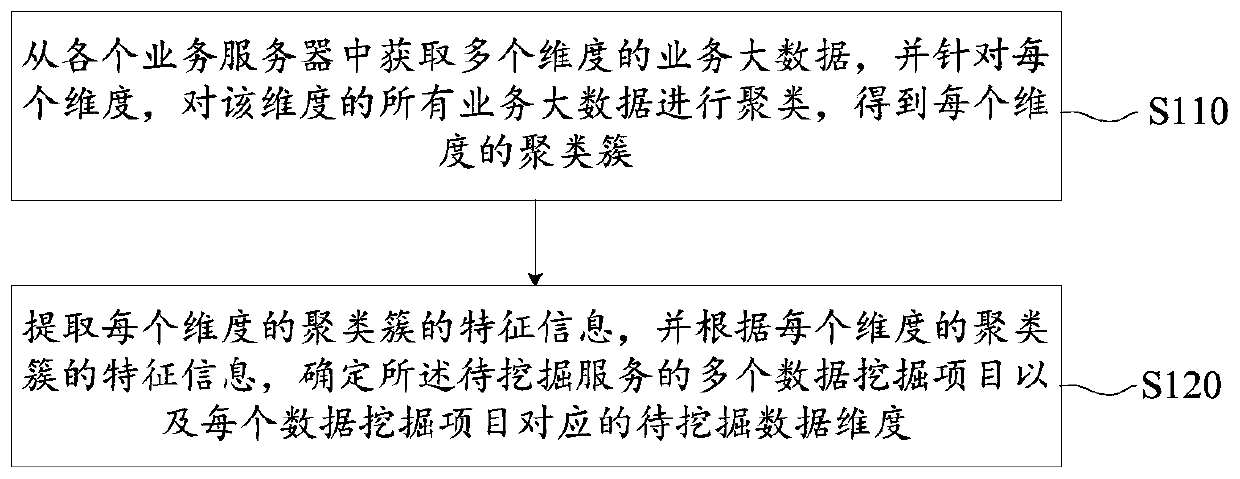
ActiveCN110442623AUnified performanceImprove digging abilityMulti-dimensional databasesSpecial data processing applicationsComputer scienceData dimension
The embodiment of the invention provides a big data mining method and device and a data mining server. Different interestingness measurement dimensions are comprehensively considered, after clusteringall the business big data of each dimension, it can be ensured that the performance of different interestingness measurement dimensions is more unified under different to-be-applied scenes of the data mining project. The big data mining capability is improved. According to the feature information of each clustering cluster, multiple data mining items of the to-be-mined service and the to-be-mined data dimension corresponding to each data mining item are dynamically determined, and subsequent data mining is performed according to the data mining items and the to-be-mined data dimension, so that the problem of relatively poor mining effect or low accuracy of a data mining result possibly caused by adoption of a fixed mining data dimension in the prior art can be avoided.
Owner:厦门久凌创新科技有限公司
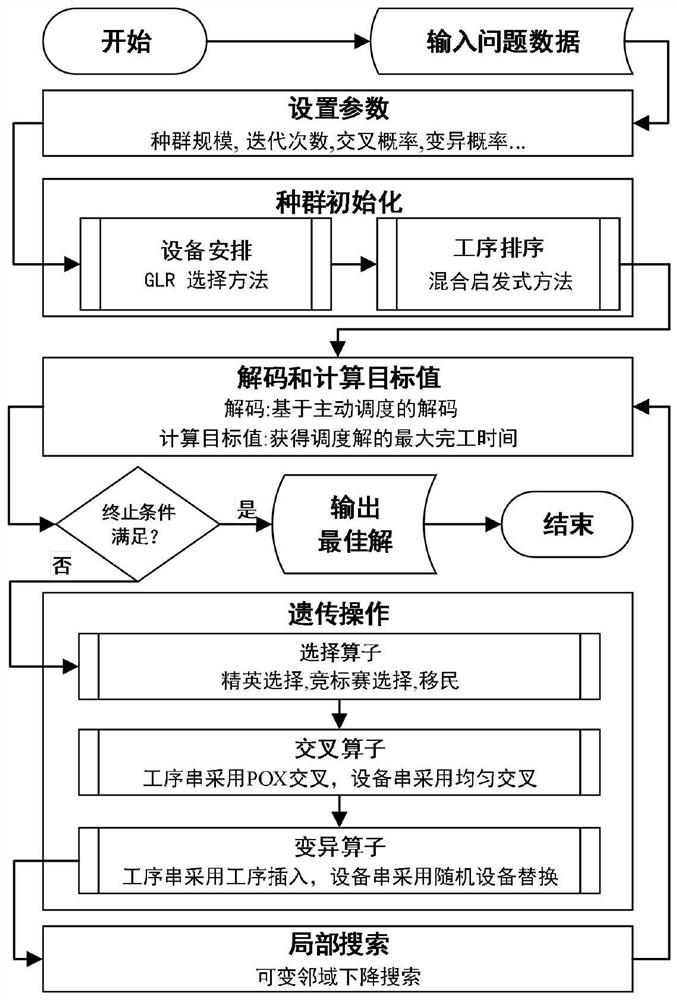
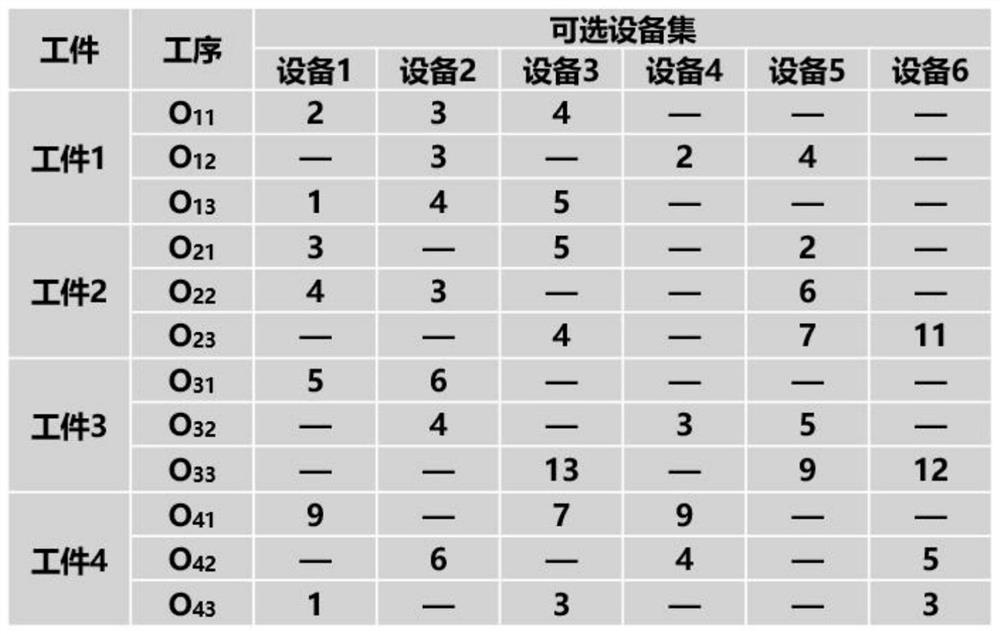
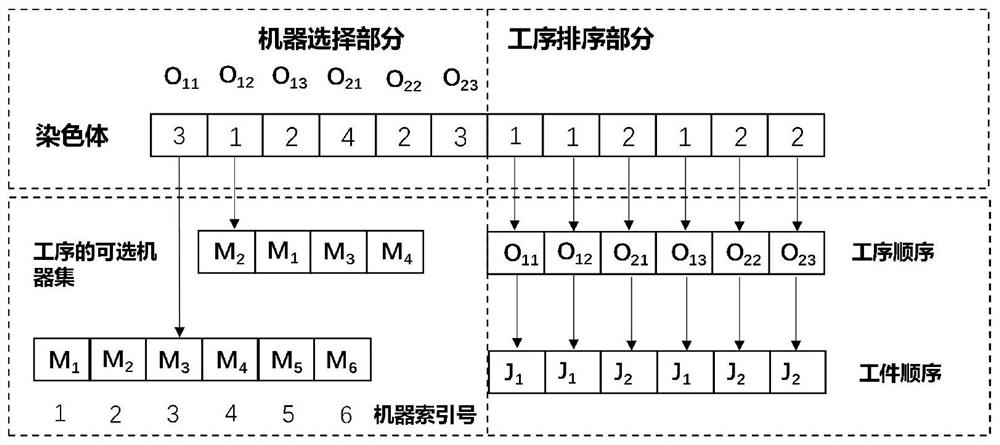
Flexible job shop scheduling method based on multistage neighborhood structure and hybrid genetic algorithm
PendingCN112580922AHigh solution accuracyQuality improvementArtificial lifeResourcesLocal optimumAlgorithm
The invention discloses a flexible job shop scheduling method based on a multistage neighborhood structure and a hybrid genetic algorithm, and the method comprises an initialization strategy of a hybrid heuristic rule, and can effectively improve the quality and diversity of an initial solution. Variable neighborhood descent search is embedded in a universal genetic algorithm framework, a novel multi-level neighborhood structure based on a key process is effectively searched, and the exploration capability of a solution space is greatly improved. The defects of low solving precision, low convergence speed and easiness in falling into local optimum of a general genetic algorithm for a flexible job shop scheduling problem can be overcome, a higher-quality scheduling scheme is obtained, the production efficiency is further improved, and the cost is reduced.
Owner:BEIJING UNIV OF TECH +1
Burying plough and working method thereof
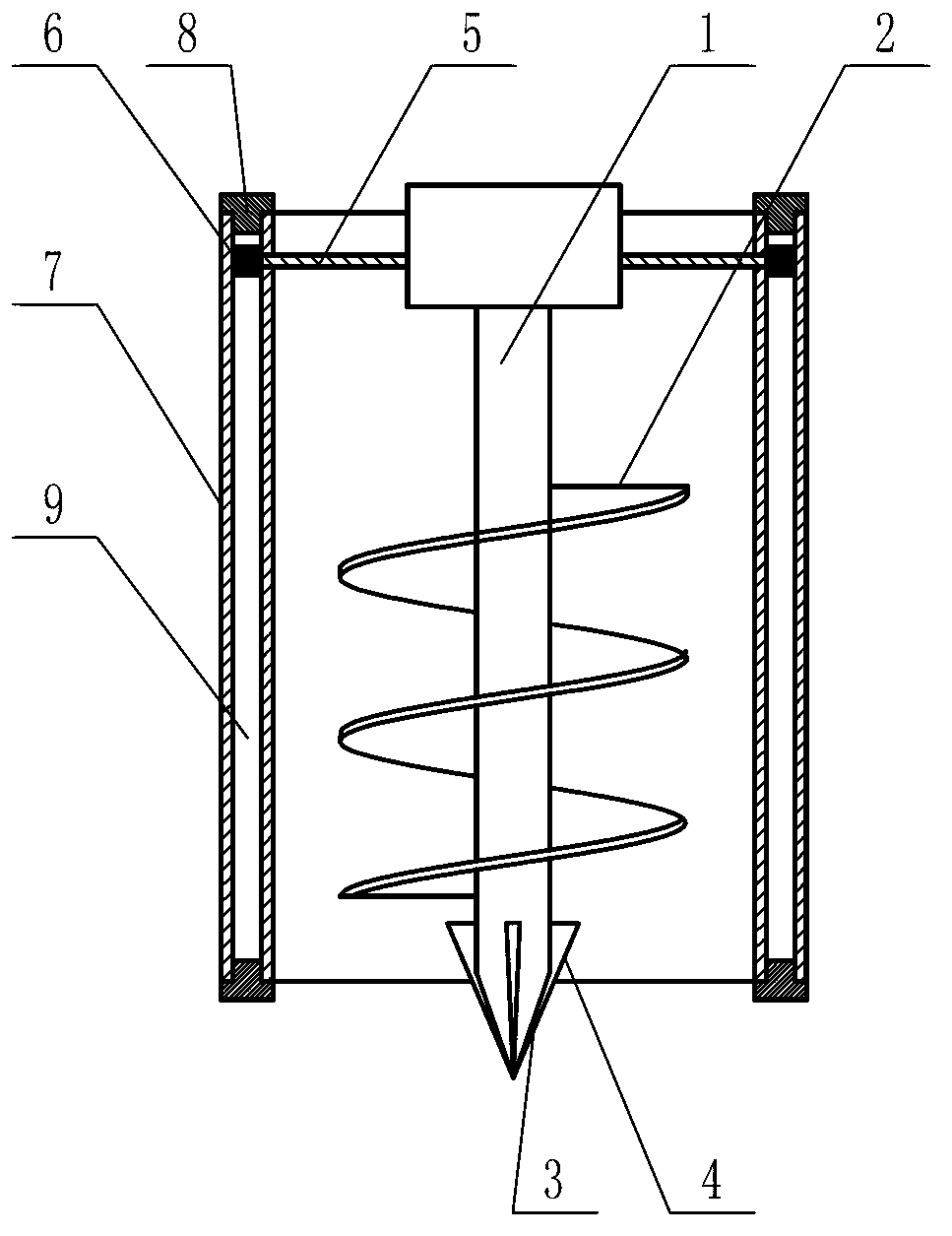
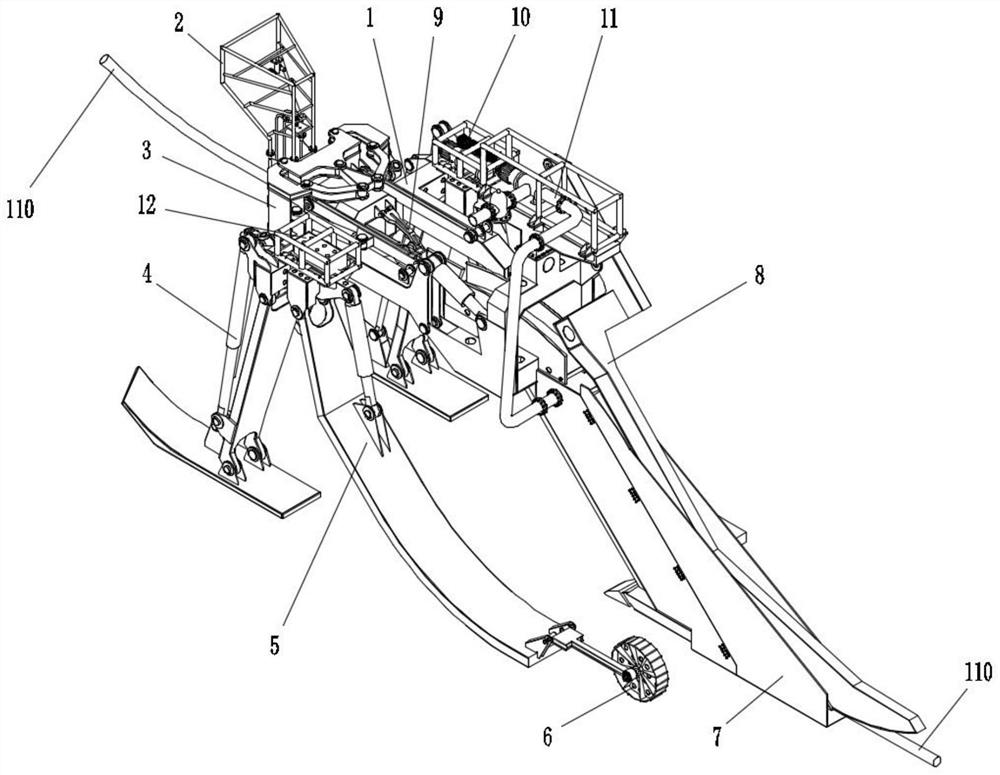
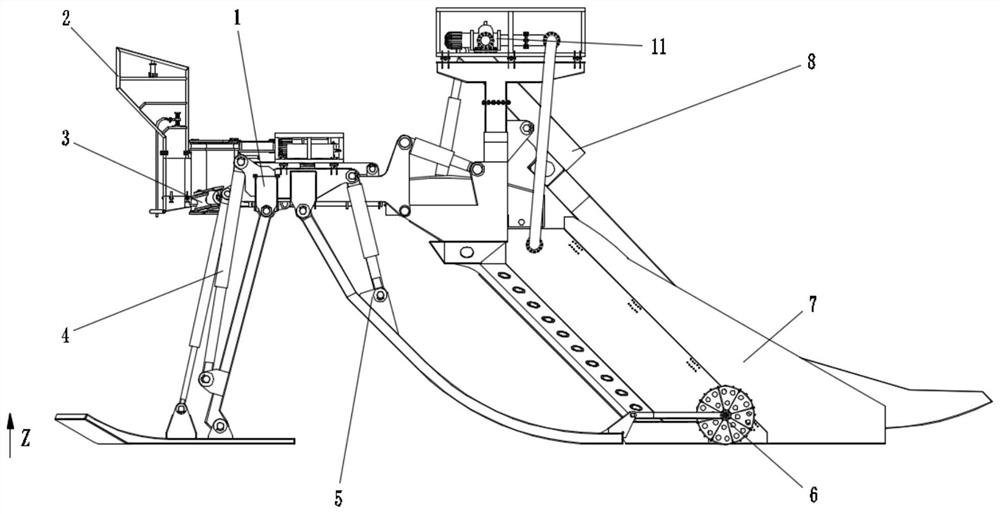
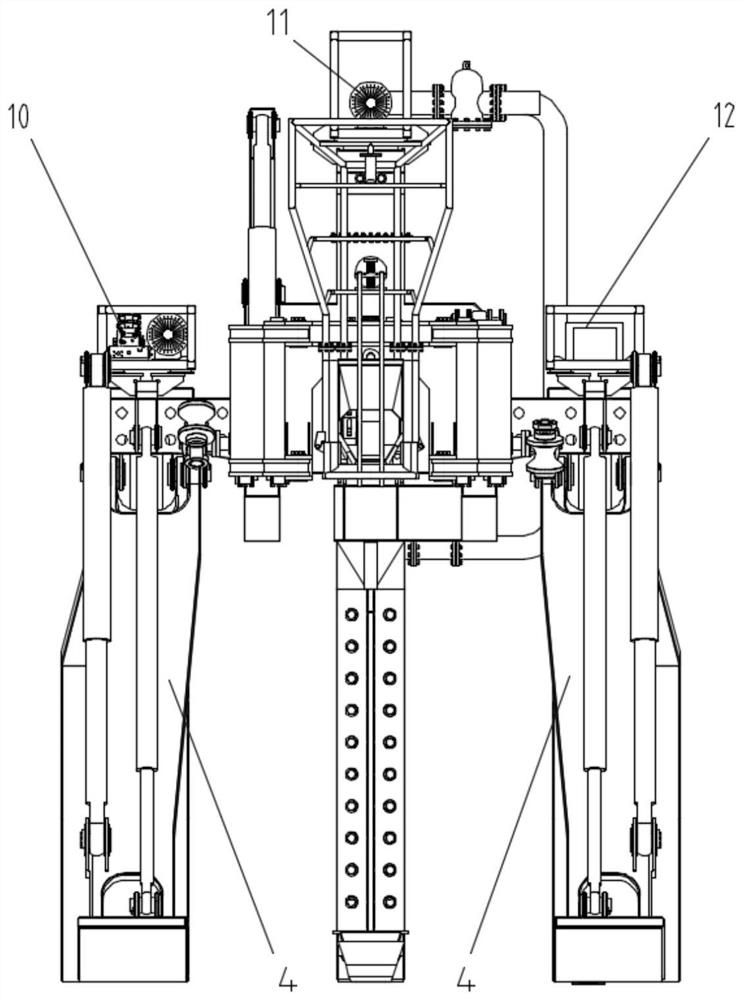
PendingCN112627267AImprove digging abilityImprove digging efficiencySoil-shifting machines/dredgersSoil scienceHigh pressure water
The invention discloses a burying plough and a working method thereof. The burying plough is used for laying submarine cables, and comprises a rack; a coulter system arranged on the rear side of the rack and used for excavating seabed soil; a high-pressure water spraying system arranged on the coulter system or the rack and used for providing high-pressure water for the coulter system in the digging process so as to scour the soil; and a control system used for controlling the burying plough to operate. High-pressure water can be provided for the coulter system in the process of excavating the hard seabed soil so as to scour the soil, so that the excavating capacity and excavating efficiency of the burying plough are improved, and the burying plough is not only suitable for muddy soil, but also suitable for hard sandy soil.
Owner:SHANGHAI ZHENHUA HEAVY IND
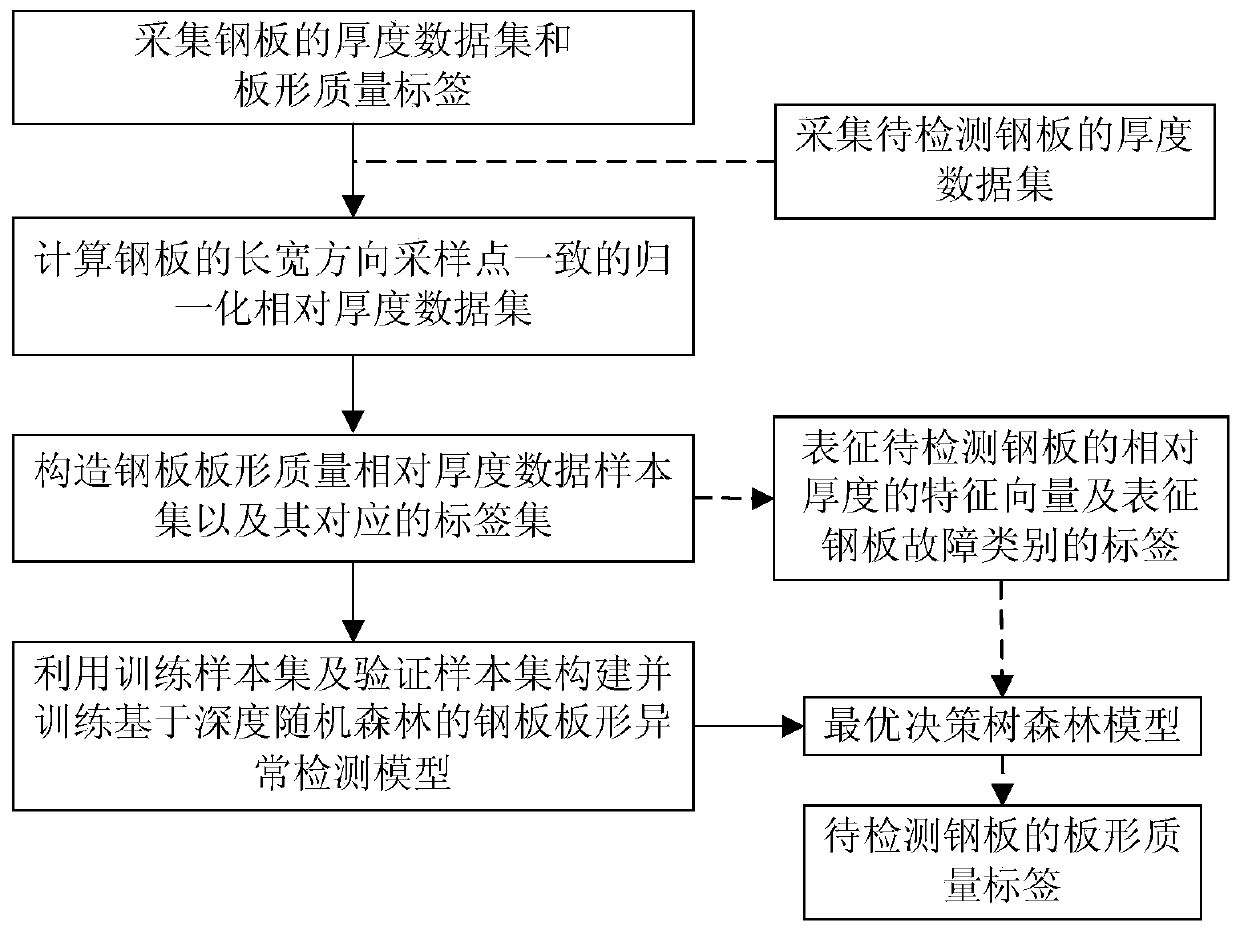
Steel plate shape abnormity identification method based on depth random forest
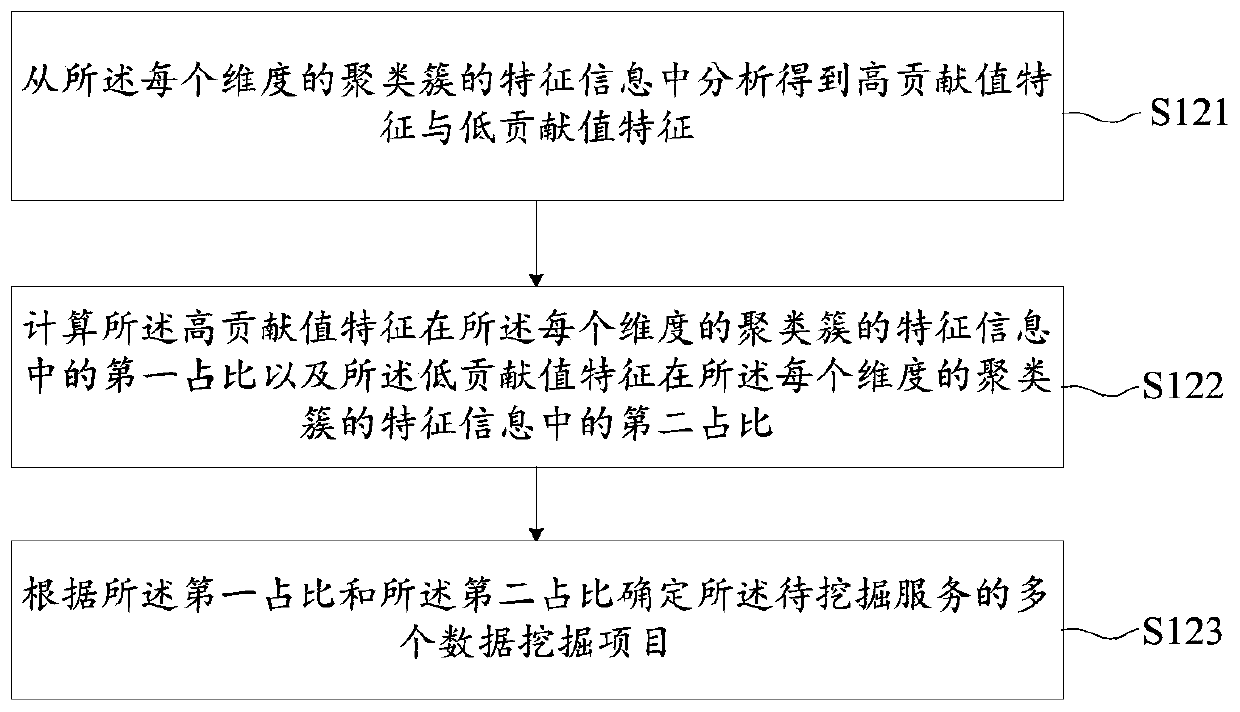
PendingCN111126490AStrong data mining abilityLittle data mining abilityCharacter and pattern recognitionNeural architecturesPhysicsSteel plates
The invention provides a steel plate shape abnormity identification method based on a depth random forest and relates to the technical field of steel plate shape abnormity identification. The method comprises the following steps that: the thickness data set and plate shape quality labels of steel plates are acquired, the relative thickness data set of the steel plates are calculated, up-sampling or down-sampling are performed on the relative thickness data set, so that steel plates with consistent sampling points in a length direction and a width direction can be obtained, normalization processing is performed on the relative thickness data set; a steel plate shape anomaly recognition model based on the depth random forest is constructed and trained by using a training sample set and a verification sample set with feature vectors representing the relative thickness of the steel plates adopted as input and the plate shape quality labels of the steel plates as output, so that an optimaldepth random forest model can be obtained; and the thickness data set of to-be-detected steel plates can be collected, feature vectors representing the relative thickness of the to-be-detected steel plates are calculated and inputted into an optimal depth random forest model, so that the plate shape quality labels of the to-be-detected steel plates can be obtained.
Owner:NORTHEASTERN UNIV
Graph data processing method and device, computer equipment and storage medium
ActiveCN112214499AAvoid wastingReduce memory usageRelational databasesPayment architectureAlgorithmMemory footprint
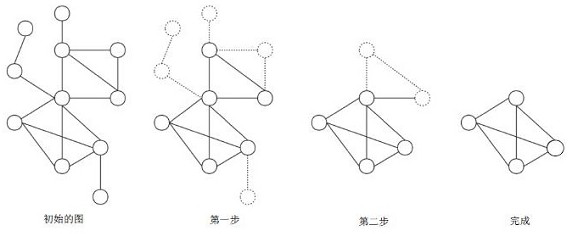
The invention relates to a graph data processing method and device, computer equipment and a storage medium. The method relates to a data mining technology, and comprises the following steps: obtaining the association degree of each node in a network graph; splitting a dense sub-graph from the network graph according to the association degree of each node; based on the dense subgraph, determiningstable nodes in the network graph and the kernel number of the stable nodes; obtaining a sparse sub-graph in the network graph according to the nodes except the stable nodes in the network graph and the connecting edges between the nodes; and determining the kernel number of each node in the sparse subgraph based on the sparse subgraph and the stable nodes. By the adoption of the method, subgraphmining of a super-large-scale network can be supported, memory occupation can be greatly reduced in the mining process, it is avoided that much iteration time and computing resources are wasted on non-important nodes, and mining performance is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Big data analysis method and data analysis server
PendingCN110674182AImprove digging abilityDynamic and Accurate AcquisitionRelational databasesSpecial data processing applicationsEngineeringData profiling
The invention provides a big data analysis method and a data analysis server. Different interestingness measurement dimensions are comprehensively considered, after all business big data of each dimension is clustered, the performance of different interest measurement dimensions in different data mining project to-be-applied scenes can be ensured to be more unified, the big data mining capabilityis improved, and a plurality of data mining projects of the to-be-mined service can be dynamically determined according to the feature information of each clustering cluster.
Owner:厦门久凌创新科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com