Quantum fuzzy machine learning countermeasure attack model method
A technology for attacking models and machine learning, applied in machine learning, quantum computers, computing models, etc., to achieve reliable operation, improve security and robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
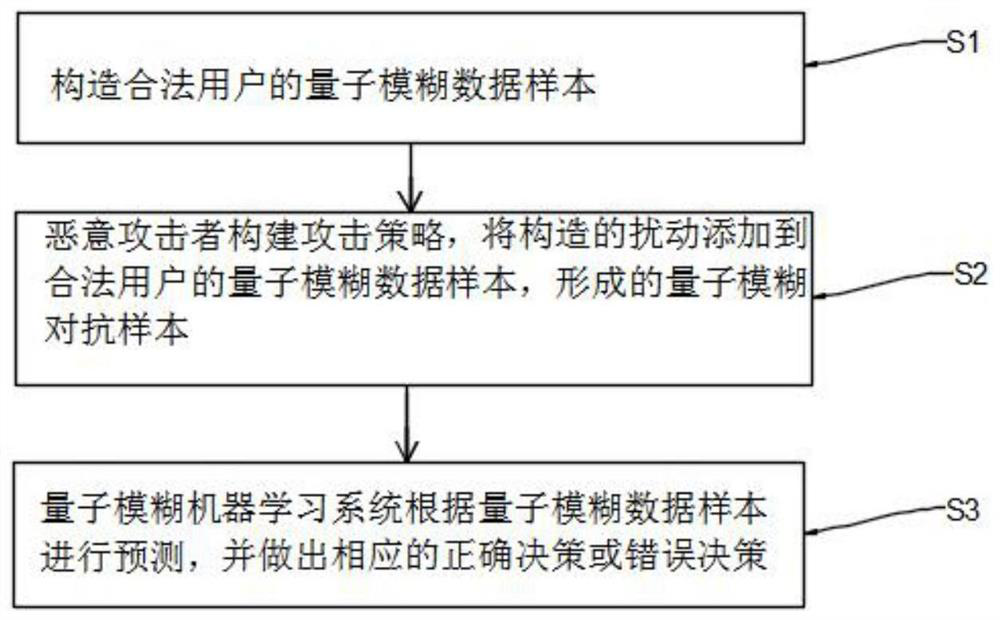
[0045] A quantum fuzzy machine learning confrontation attack model method, its flow chart is as follows figure 1 As shown, the details are as follows:
[0046] S1. Constructing a quantum fuzzy data sample of a legitimate user;
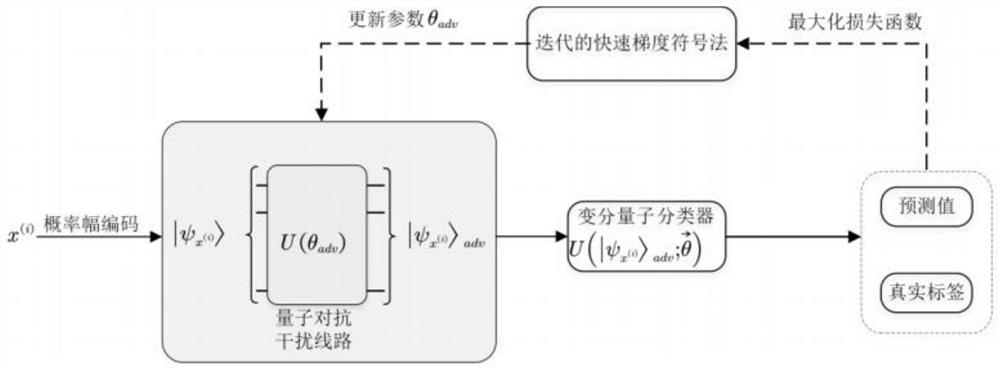
[0047] S2. The malicious attacker builds an attack strategy, and adds the constructed disturbance data to the quantum fuzzy data sample of the legitimate user to form a quantum fuzzy confrontation sample;
[0048] Malicious attackers can choose appropriate attack strategies (such as fast gradient sign method, BIM confrontation attack method, Jacobian-based feature map attack (JSMA), DeepFool, C&W attacks, Universal adversarial perturbations, Houdini, Adversarial Transformation Networks, etc.), the present invention The attack strategy employed is the fast gradient sign method, which is computationally efficient against perturbations.
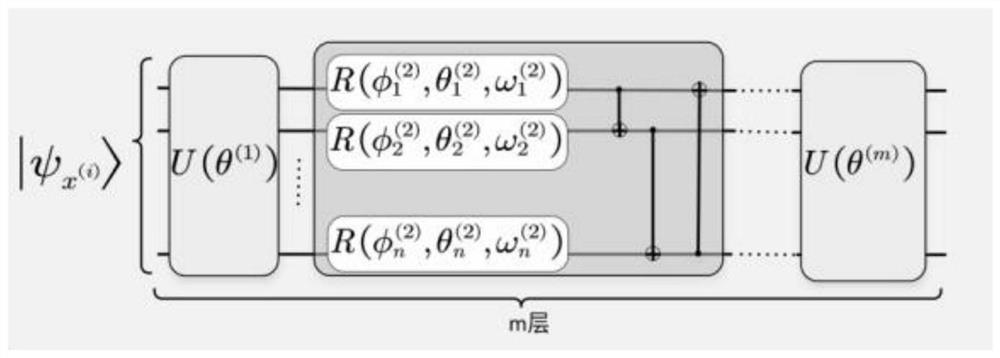
[0049] S3. The quantum fuzzy machine learning system makes predictions based on quantum fuzzy confrontation samples,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com