Mining method and system for malicious code hiding behaviors
A malicious code and behavior technology, applied in the field of network security, can solve problems such as the lack of effective and active methods to discover the hidden behavior of malicious code, the inability to implement effective analysis of malicious code, and the inability to analyze the path of hidden malicious behavior, so as to improve hidden behavior. The effect of analysis and mining capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below through specific embodiments and accompanying drawings.
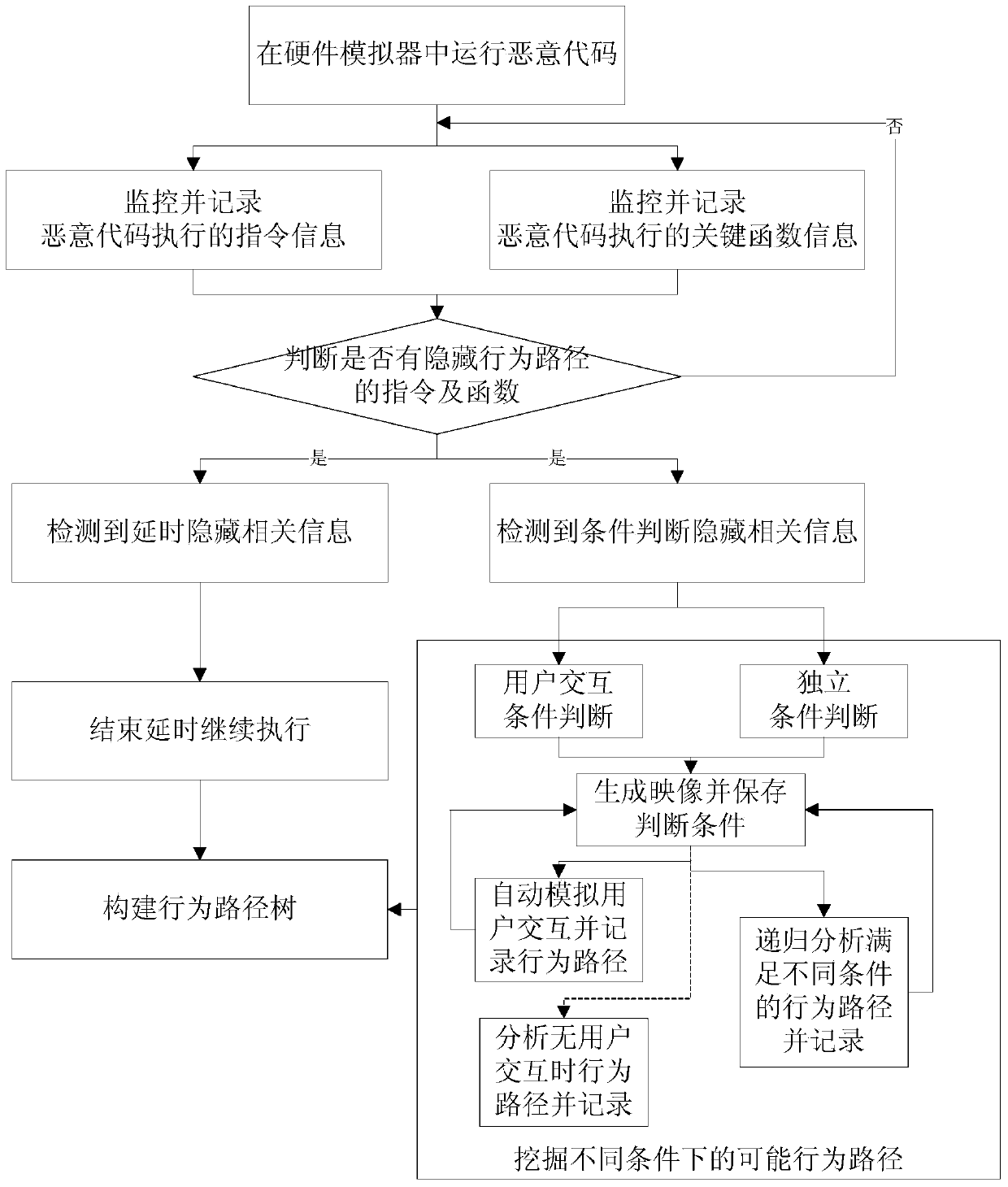
[0036] Such as figure 1 As shown, the malicious code hiding behavior mining method of the present invention comprises the following steps:
[0037] 1. Monitor and record the instruction information and function information of the dynamic execution of malicious code.
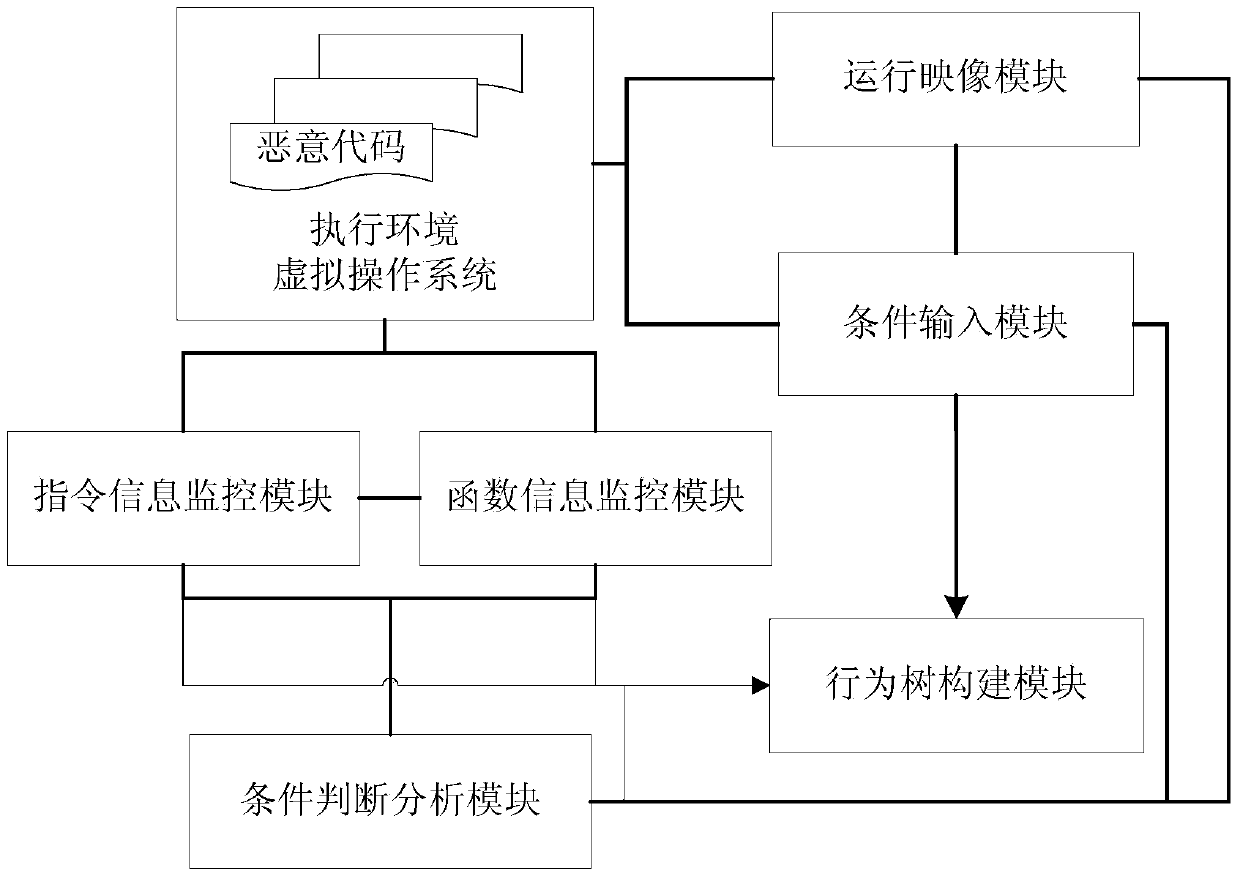
[0038] The invention uses a hardware simulator to dynamically run malicious codes to be analyzed in a virtual operating system, and monitors and records the instructions and function information executed by the malicious codes in the hardware simulator. Instruction monitoring uses the method of disassembly in the intermediate translation module of the hardware simulator to extract instruction by instruction and record the corresponding instruction information. Function information monitoring calculates the corresponding function call address by identifying the system data structure in the virtu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com