High-risk asset discovery and network attack tracing method based on TTP
A network attack, high-risk technology, applied in the field of traceability, can solve the problem of not being able to directly see the attacker's purpose and attack technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
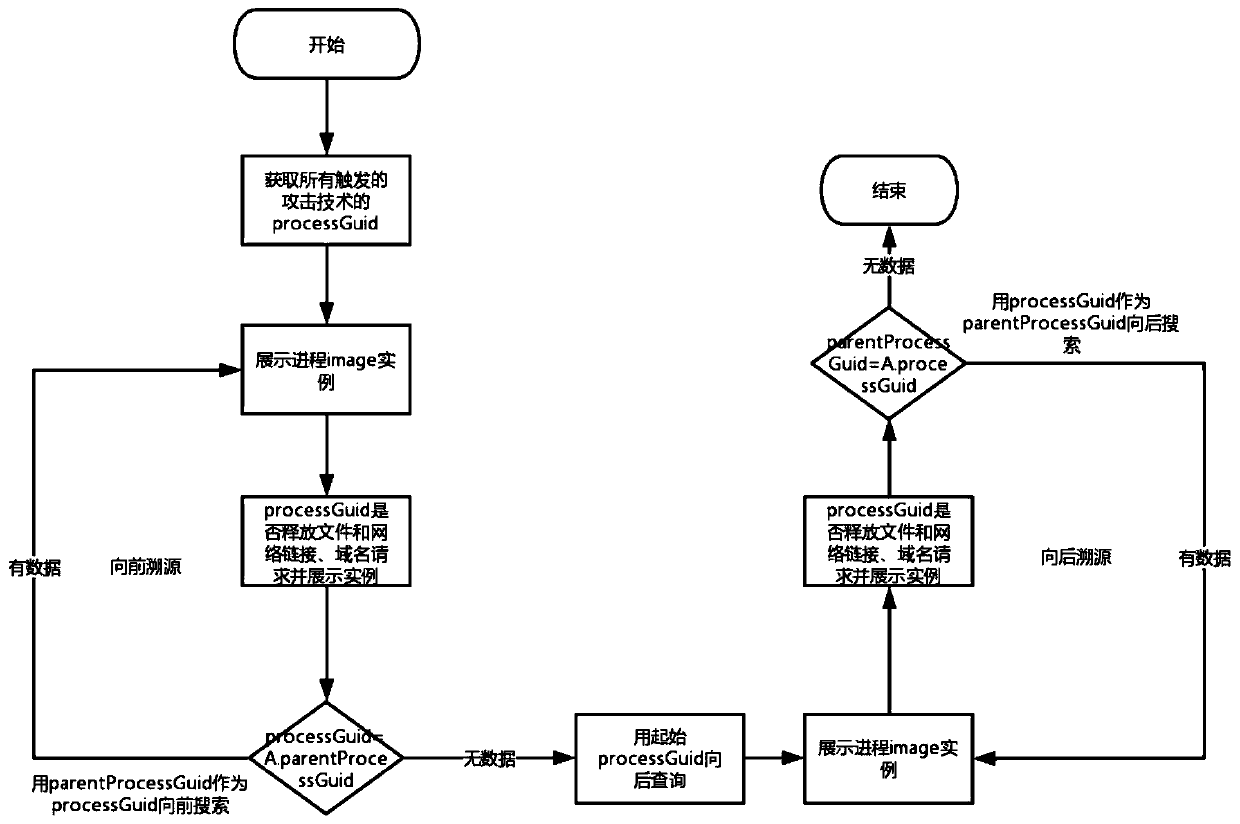
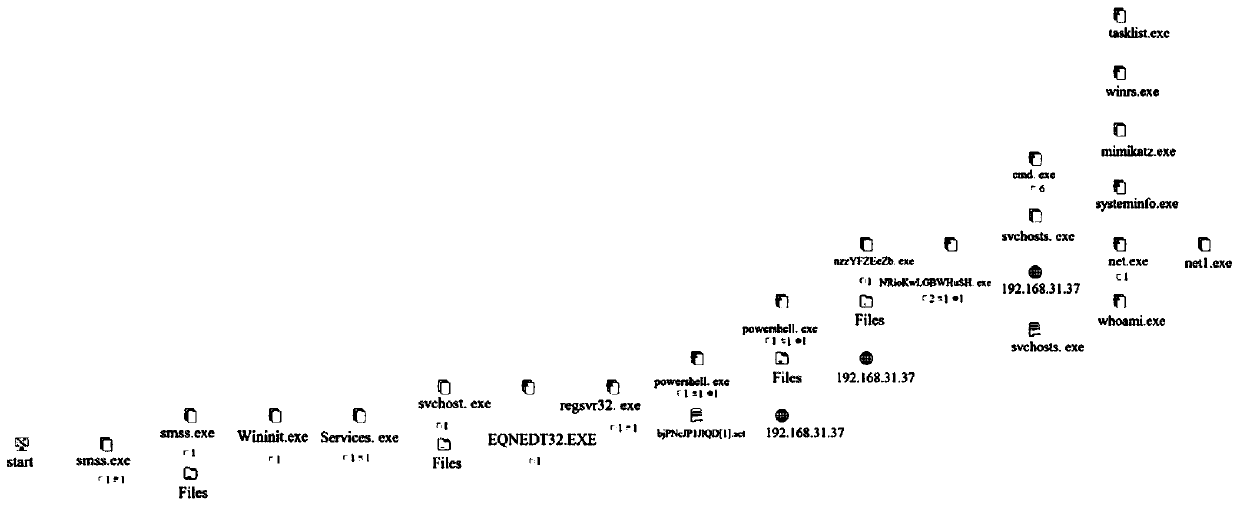
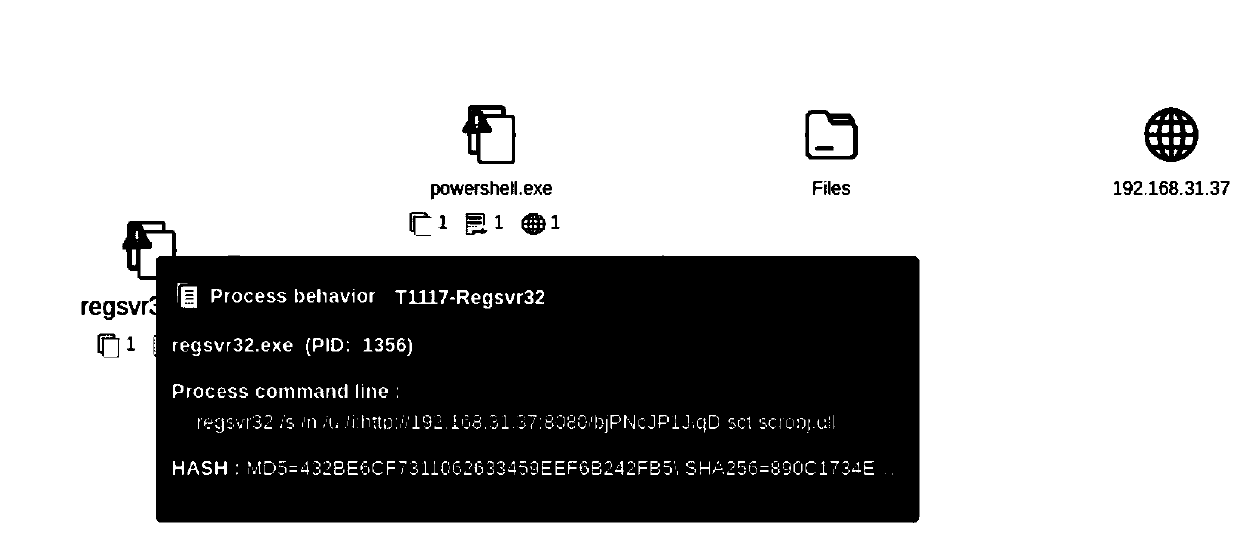
[0048] Embodiment 1, TTP-based high-risk asset discovery and network attack source tracing method, such as Figure 1-5 shown, including the following steps:
[0049] First, trace the source of the process tree for processes that have triggered TTP-related rules, and query whether other processes on the process tree have also detected TTP threats (pre-detection settings), and then display all detected TTP information to the corresponding process tree. process.
[0050] The process of TTP-related rules has been triggered. The detection of attack technology Techniques (TTP-related rules) comes from the Siem platform (security information event management platform, commonly known as the log analysis platform). Through the real-time detection capabilities of the Siem platform, the real-time transmitted Terminal logs, detection attack techniques Techniques. Operations in the original terminal data generally carry process information, which can be output to the alarm.
[0051] Whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com