Attack source IP portrait generation method and device based on network attack behavior
A network attack and attack source technology, applied in the field of network security, can solve problems such as limited access to attack source information and inability to understand attack source IP
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
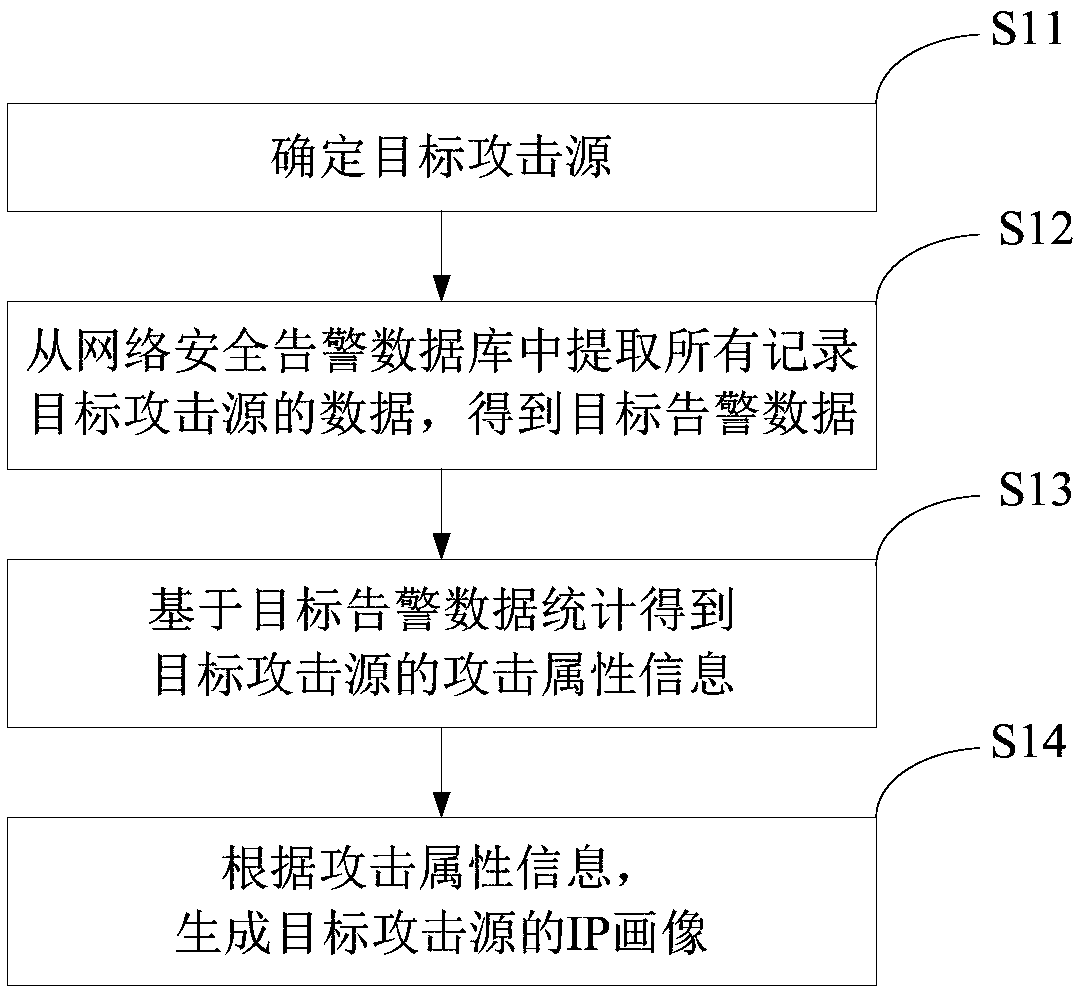
[0051] An embodiment of the present invention provides a method for generating an attack source IP portrait based on network attack behavior, such asfigure 1 As shown, the method includes:
[0052] S11: Determine the target attack source.
[0053] S12: Extract all data recording target attack sources from the network security alarm database to obtain target alarm data.
[0054] In this step, the network security alarm database includes alarm data of multiple attack sources. The alarm data may be an alarm log and / or an alarm record.
[0055] S13: Obtain the attack attribute information of the target attack source based on the target alarm data statistics.
[0056] S14: Generate an IP profile of the target attack source according to the attack attribute information.
[0057] In this embodiment, the "image" of malicious IP addresses in the network space can be realized by using the network security alarm database to count the attack attribute information of the target attack s...
Embodiment 2
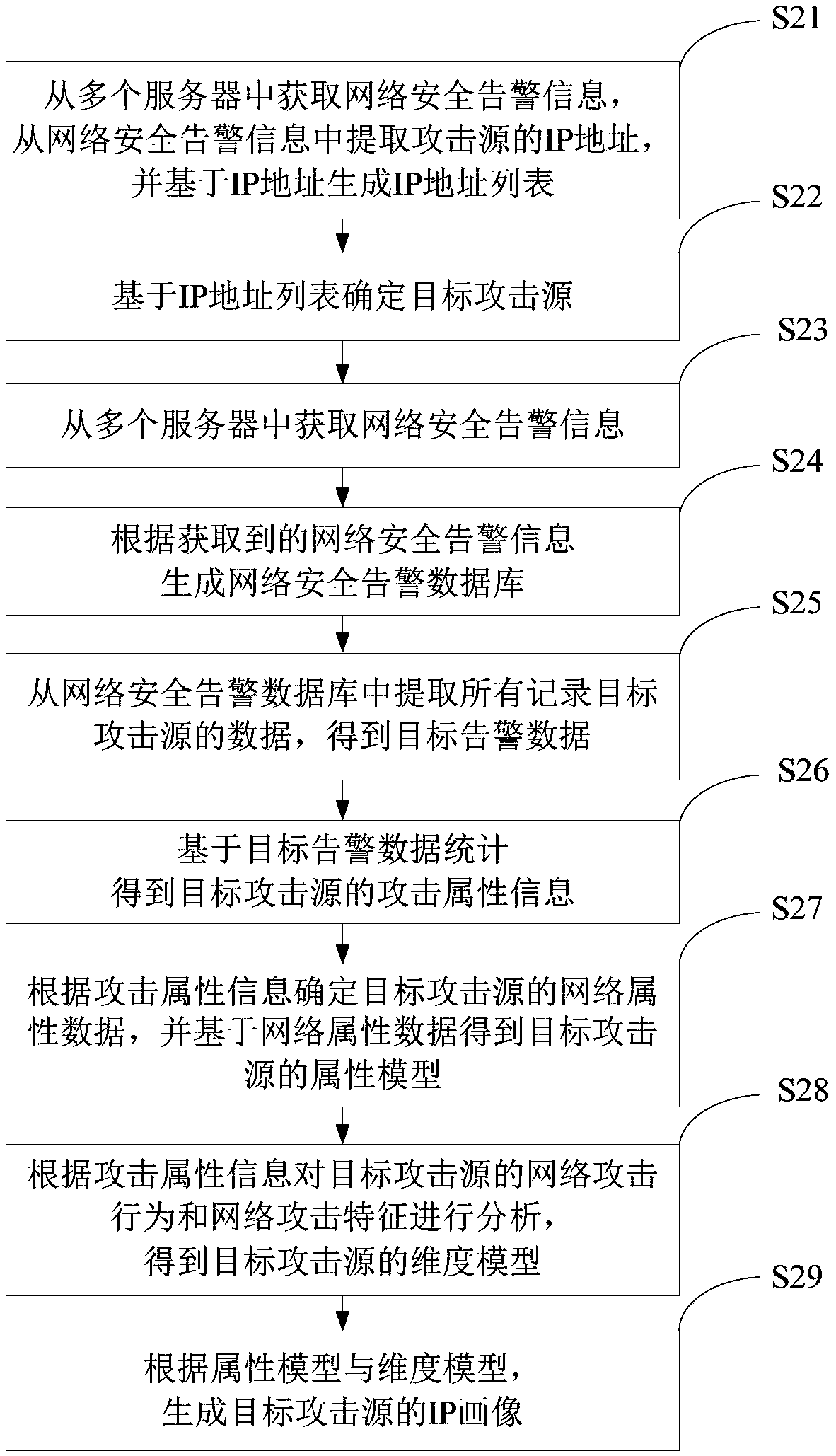
[0059] An embodiment of the present invention provides a method for generating an attack source IP portrait based on network attack behavior, such as figure 2 As shown, the method includes:
[0060] S21: Obtain network security alarm information from multiple servers, extract IP addresses of attack sources from the network security alarm information, and generate an IP address list based on the IP addresses.
[0061] As a preferred solution, the network security alarm information is alarm logs and records related to network security. In this step, the attack source IP address is extracted from the network security alarm information, and an IP address object list is generated.
[0062] S22: Determine the target attack source based on the IP address list.
[0063] It should be noted that the IP address list includes IP addresses of several attack sources. In this step, the target attack source is determined from the IP address list, and of course, the IP objects can also be ...
Embodiment 3
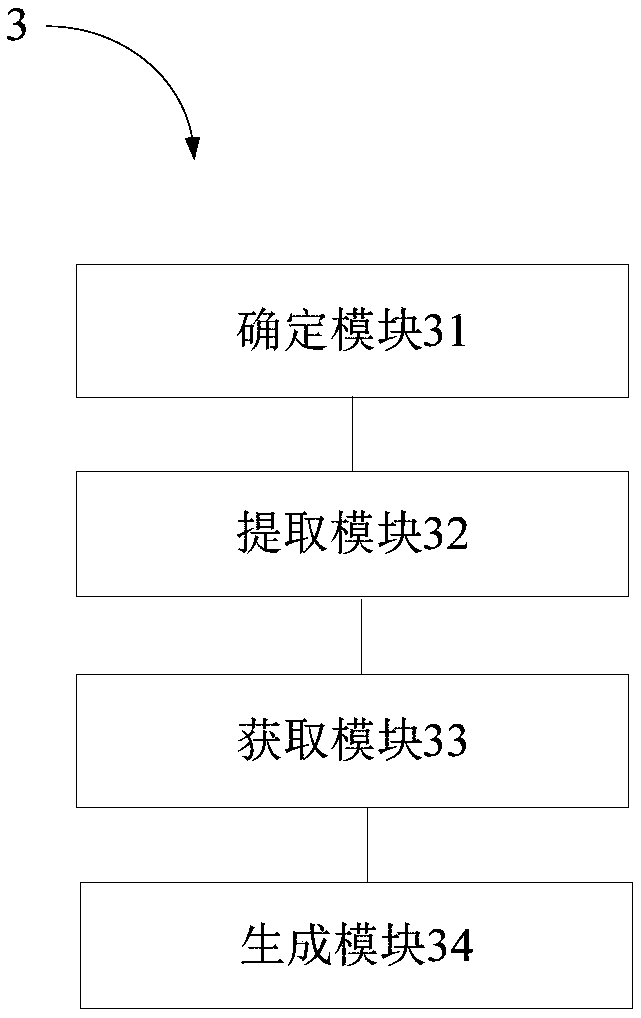
[0085] An attack source IP portrait generation device based on network attack behavior provided by an embodiment of the present invention, such as image 3 As shown, the attack source IP profile generation device 3 based on network attack behavior includes: a determination module 31 , an extraction module 32 , an acquisition module 33 and a generation module 34 .
[0086] Preferably, the determination module is used to determine the target attack source. The extracting module is used to extract all data recording target attack sources from the network security alarm database to obtain target alarm data, wherein the network security alarm database includes alarm data of multiple attack sources.
[0087] As a preferred solution, the acquisition module is used to obtain the attack attribute information of the target attack source based on statistics of the target alarm data. The generation module is used to generate the IP portrait of the target attack source according to the at...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com