Network alarm information clustering method based on attribute correlation
A technology of alarm information and clustering method, which is applied in the field of network security and can solve the problem of not being able to cover the whole picture of attack events
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to better understand the contents of the present invention, an example is given here.
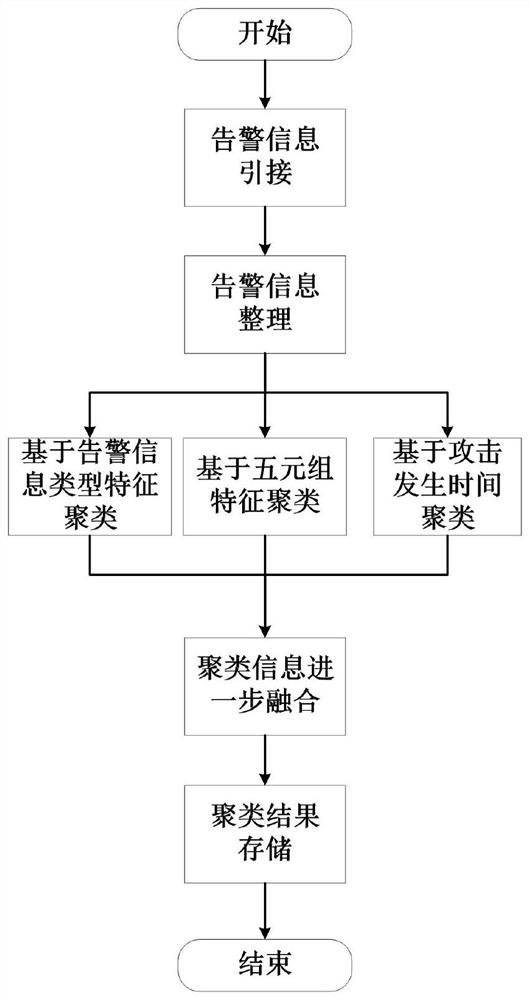
[0021] The invention discloses a network alarm information clustering method based on attribute correlation, figure 1 It is an implementation flowchart of the network alarm information clustering method based on attribute correlation of the present invention, and its specific steps include:
[0022] S1, sorting out network alarm information; due to multiple sources of network alarm information and inconsistent formats, the most extensive and representative IDMEF security event specification currently in the world is adopted to standardize the format of network alarm information. Generate network alarm information for security defense equipment and services including firewalls, anti-virus terminals, malicious traffic analysis, and email analysis, and use the IDMEF security event specification to unify the format of the information to achieve dynamic scalability and descriptio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com