Method for protecting integrity of digital vector map
An integrity protection and vector map technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of weak anti-attack ability, inability to achieve tamper recovery, inability to resist attacks of deleting and adding line primitives, etc. Accelerate the storage speed, achieve accurate recovery, and improve the speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] Below in conjunction with accompanying drawing and example technical solution of the present invention is described further:
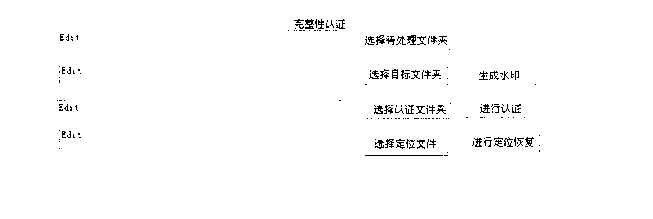
[0053] The present invention can be divided into three parts, 1. The generation process of three watermarks; 2. The hiding of the watermark in the driver layer; 3. The integrity authentication process.
[0054] 1. The watermark generation process, the steps are as follows.
[0055] Such as figure 1 The generation process of the shown watermark is divided into three paths, corresponding to the authentication watermark, location watermark and recovery watermark respectively.
[0056] (1) Generate authentication watermark
[0057] Read the vector map as a binary stream. Since we use meaningless bytes in the header file to store the watermark, we offset the pointer by 100 bytes, and then use the binary data stream of the rest of the map file as the input of MD5 for hashing. Processing, generate summary information that can uniquely identify the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com